ADSL wireless router, method and system for using the same to realize captive portal under bridge pattern
A technology of wireless routers and captive portals, applied in transmission systems, electrical components, telephone communications, etc., can solve the problems that ADSL wireless routers cannot realize captive portal authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0072] Linux Netfilter (firewall) is an important module component of the Linux kernel. Its task is to perform packet filtering actions, including INPUT (input), OUTPUT (output) and FORWARD (forwarding) chains, used to process input, output and Forward packets. Using this framework, you can also customize the kernel data packet processing process and provide a registration hook function mechanism. For example, if you register a hook function under the FORWARD chain, all data packets passing through the FORWARD chain will pass through the custom hook function to implement data packet processing. Customized analysis processing and transformation.
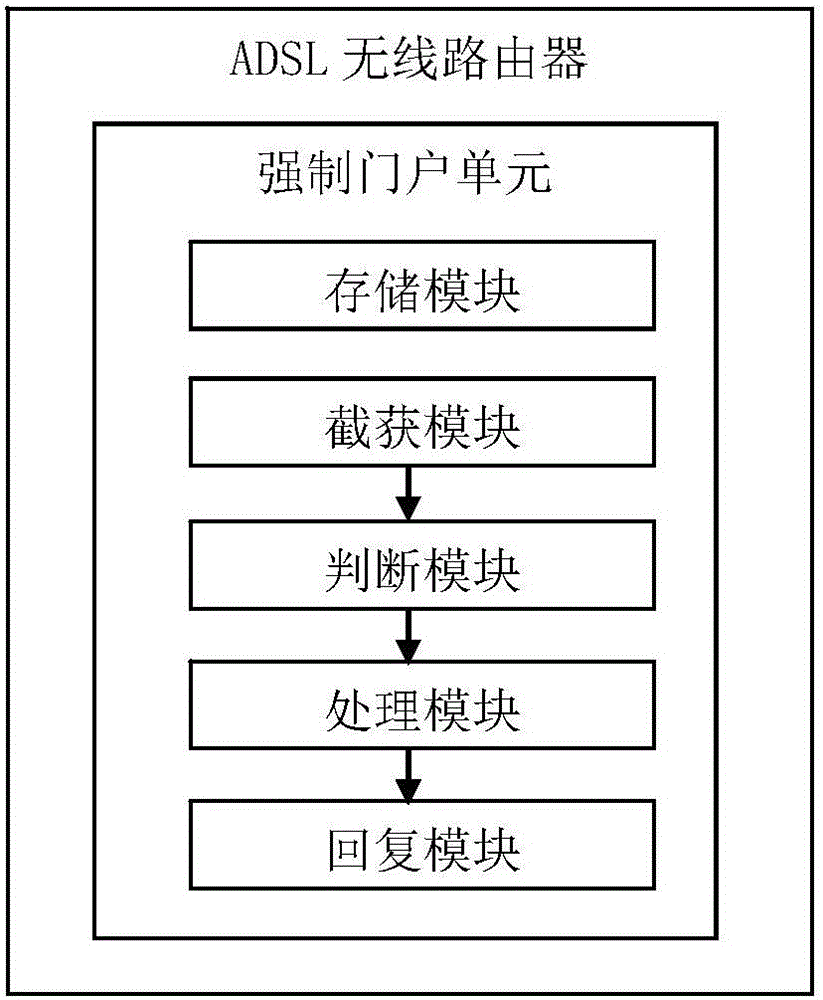
[0073] In order to solve the problem that the existing ADSL wireless router does not have DHCP service and domain name agent in bridge mode, and cannot realize the captive portal authentication through domain name agent deception, such as figure 1 As shown, the present invention provides a kind of ADSL wireless router, in described r...
Embodiment 2
[0102] When implementing captive portal authentication, there are still some special situations. You can connect to the network you need without mandatory authentication. There are the following special situations:
[0103] 1. Some network addresses do not require captive portal authentication, such as the router owner’s merchant’s website, etc.;
[0104] 2. Some clients do not require captive portal authentication, such as router owner clients;
[0105] 3. Some subnets do not require captive portal authentication, and routers can have multiple subnetworks. Some subnets are used to provide public network services, and these subnets require captive portal authentication; other subnets are used to provide router owners internal Using , this subnet does not require captive portal authentication.
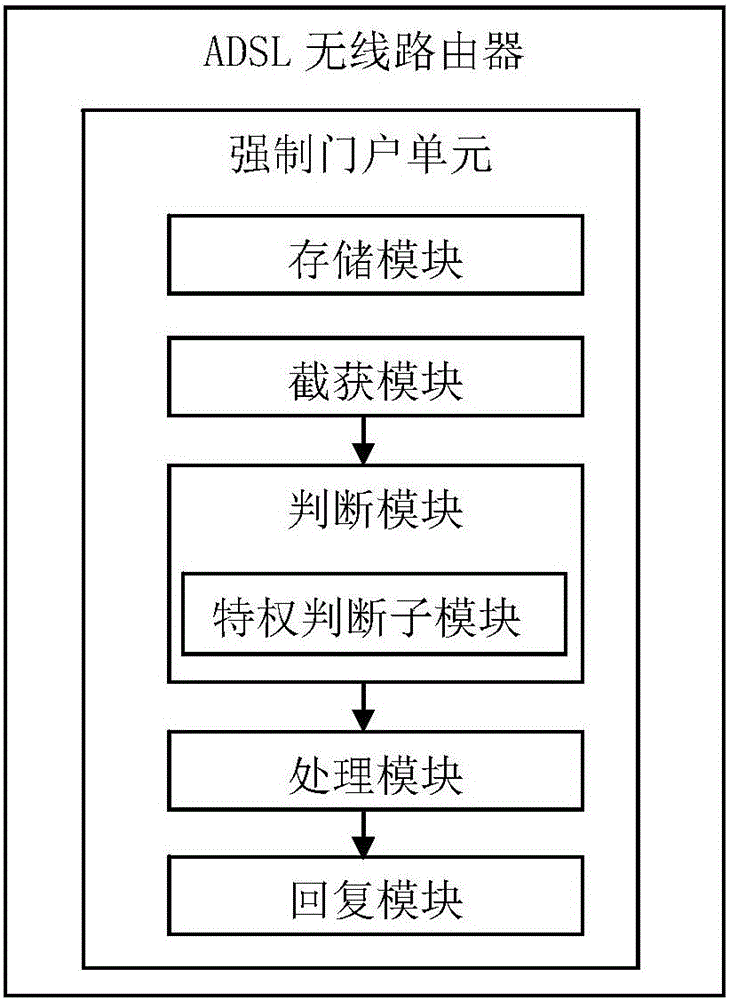
[0106] Captive portal authentication is not required in order to implement special cases such as figure 2 As shown, the ADSL wireless router provided by the present embodiment basica...
Embodiment 3
[0133] Data packets come in from different interfaces. For example, it can be set as, for example, packets coming in from interface ra0 indicate that they are data packets coming in from the wireless port, and they are also uplink packets that need to be forwarded; packets coming in from interface eth2 indicate that they are The data packets coming in from the wired WAN port are downlink packets, which are returned to the user’s request. For the downlink packets, the module will let them all go and not process them.
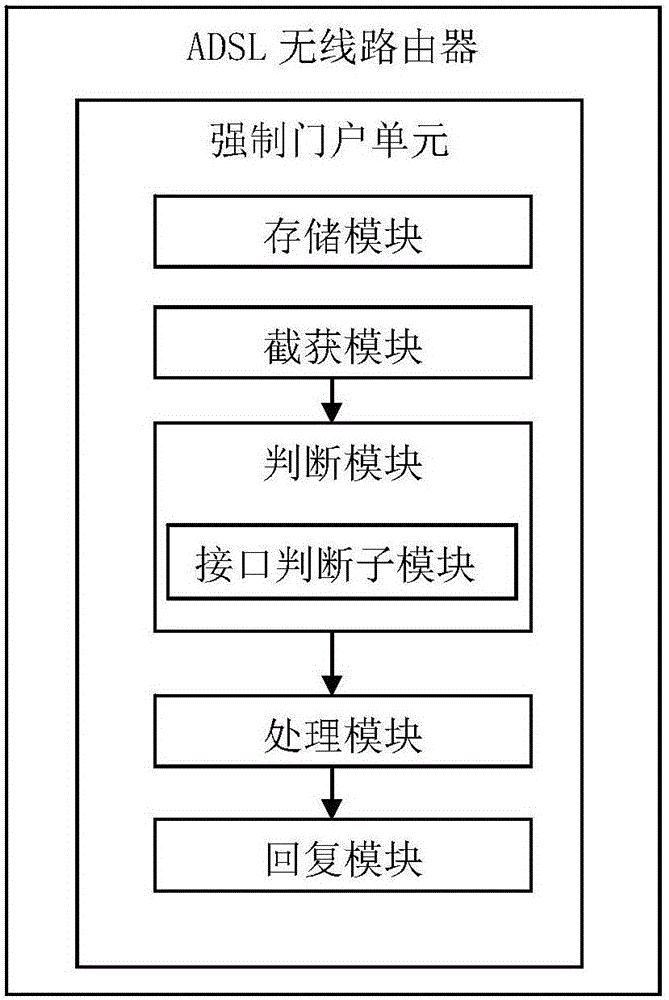
[0134] Such as image 3 As shown, the router provided in this embodiment is basically the same as that in Embodiment 1, the difference is:
[0135] The judgment module also includes:
[0136] The interface judging sub-module is used for judging that the data packet enters the interface, and if the packet enters through the wired interface, the data packet is passed over.
[0137] After the data message enters the router, the data message enters the interface to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com