Network security monitoring method for industrial control system
An industrial control system and network security technology, applied in the field of information security, can solve problems such as inability to limit malicious illegal operations, inadequate implementation of management measures, inconvenient daily operation and maintenance, and achieve the effect of solving security threats.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
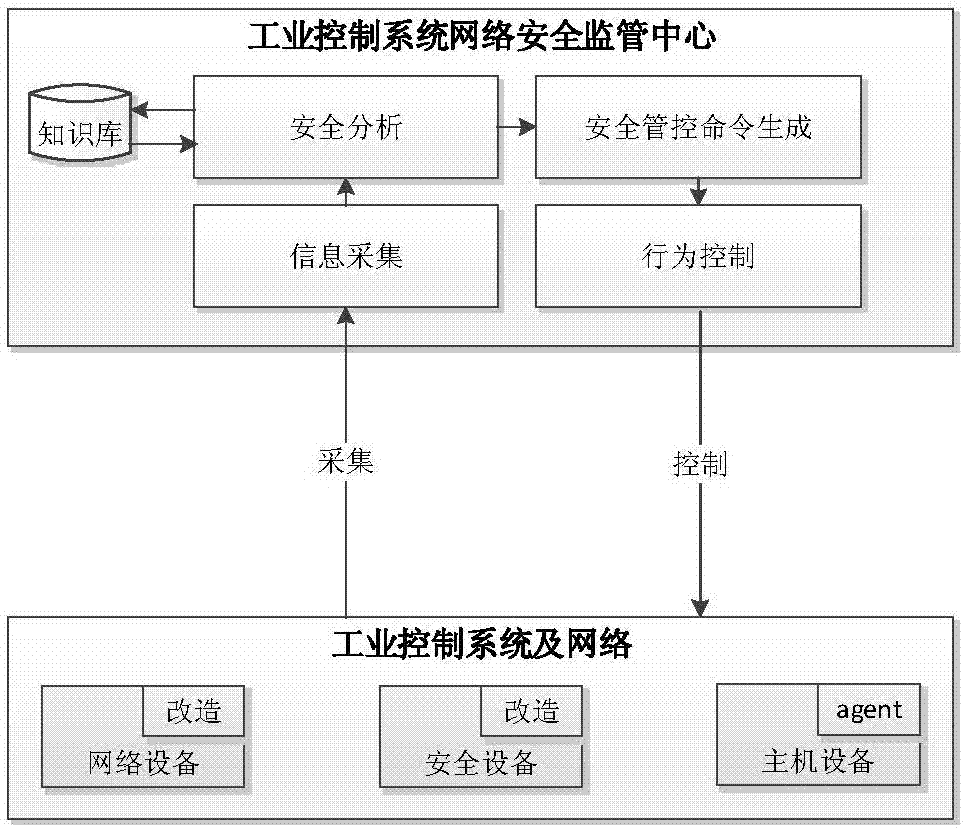
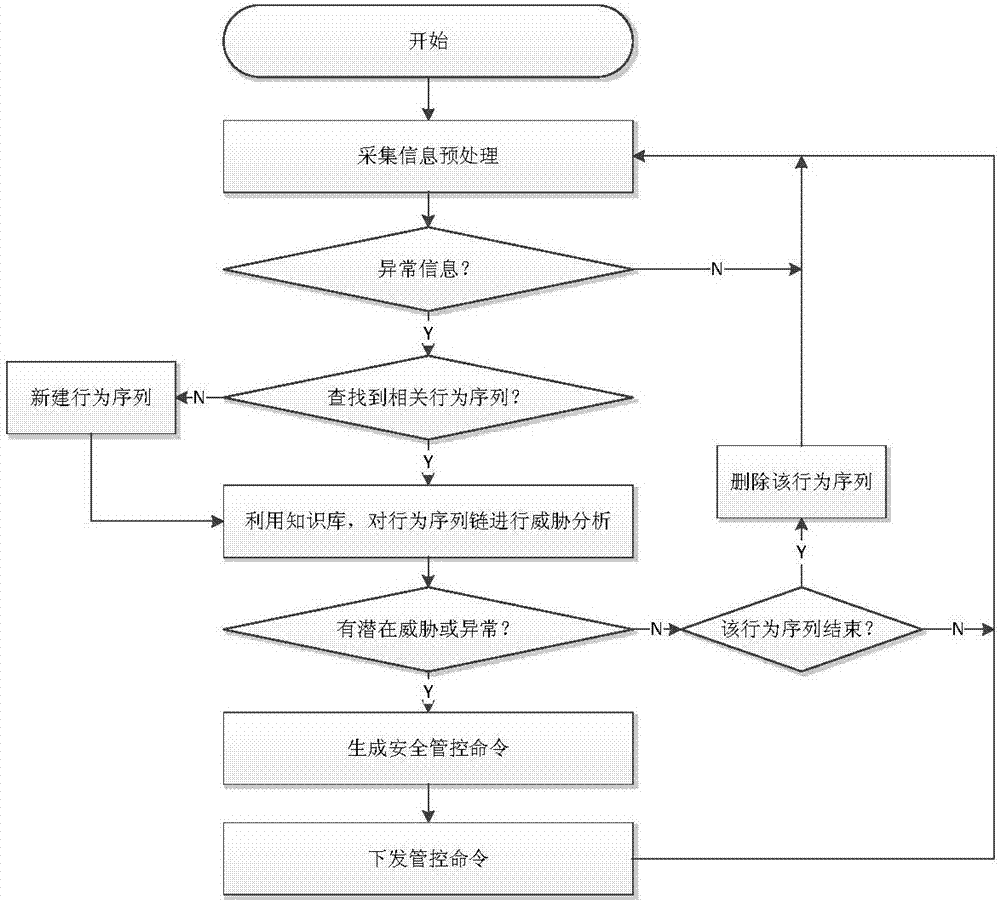
[0031] Such as figure 1 As shown, a network security monitoring method for industrial control systems includes the following steps:
[0032] Step 1, collecting relevant information of the internal monitoring object of the industrial control system;
[0033] Step 2, performing security analysis on the collected relevant information;
[0034] Step 3: When the analysis finds potential abnormal behaviors, relevant security control commands are generated and sent to relevant monitoring objects for execution to block abnormal behaviors.
[0035] In this embodiment, the monitoring objects include network equipment, security equipment, and host equipment. The network equipment refers to an industrial control switch, which actively obtains switch related information through snmp, such as network port status information, and obtains switch through snmptrap Security events that occur, such as access events such as network port up and network port down, illegal MAC access events, and us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com