Network access control method for comprehensive safety management of inner network
A technology for network access and comprehensive management, applied in the field of network access control in the comprehensive management of intranet security, which can solve the problems of consuming network resources, unable to "discover illegal devices, and the system unable to find illegal terminals."
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described below in conjunction with the accompanying drawings and implementation examples.
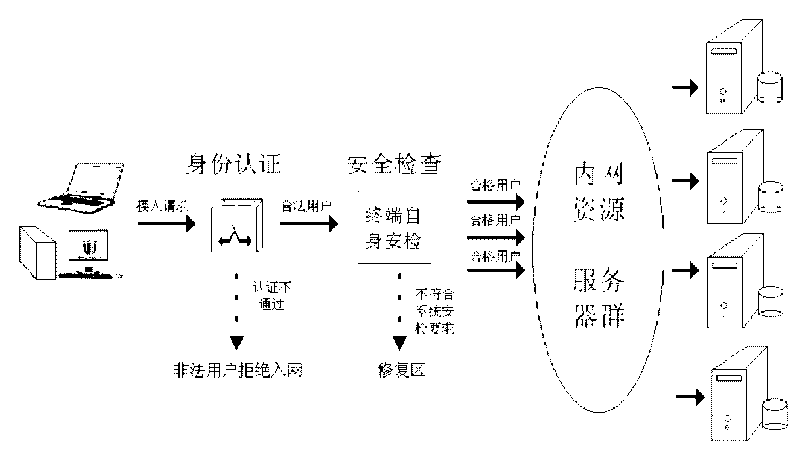
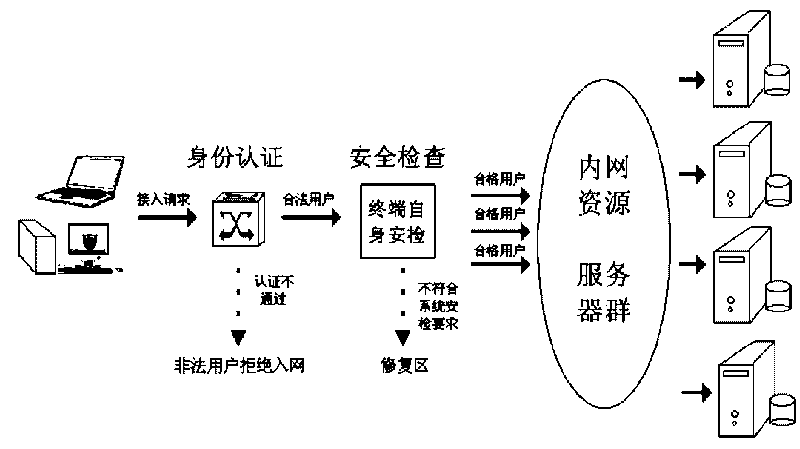
[0022] Such as figure 1 As shown, the present invention uses the network access control technology to shift the control target to the computer terminal. Starting from the terminal, through the security policy specified by the administrator, the security detection is performed on the host computer connected to the internal network, and the unsafe computer access is automatically rejected. into the internal network until these computers comply with the security policy within the network. The architecture adopted is the client / server (C / S) mode, and the management adopts the browser / server (B / S) mode. The administrator can log in to the intranet security management system through the webpage and issue security policies to the terminal. Realize terminal security management and control. More specifically, the present invention is characterized ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com