Negotiation method of authentication and key negotiation algorithm, network side equipment and user equipment
A network-side device and key negotiation technology, which is applied in the field of negotiation between network-side devices and user devices, authentication and key agreement algorithms, can solve problems such as equipment discarding, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
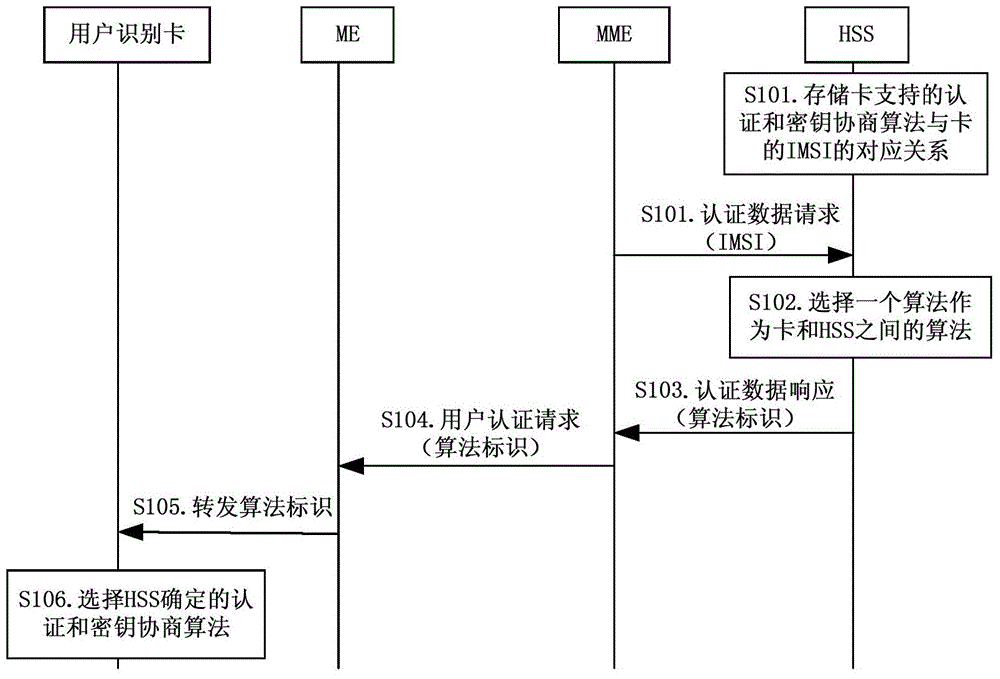
[0135] In this embodiment, according to the reported IMSI of the Subscriber Identity Card, the HSS searches for the IMSI corresponding to the IMSI of the Subscriber Identity Card from the pre-stored IMSI of the Subscriber Identity Card and the corresponding relationship between the authentication and key agreement algorithms that it can support. Authentication and key agreement algorithm, and select an authentication and key agreement algorithm that can be supported by both the user identification card and the HSS as the authentication and key agreement algorithm between the user identification card and the HSS. For details, refer to figure 1 , figure 1 It is a schematic flowchart of an authentication and key agreement algorithm in Embodiment 1 of the present invention, and the method includes the following steps:
[0136] Step S101: storing the corresponding relationship between the IMSI of the subscriber identity card and the authentication and key agreement algorithms it ca...
Embodiment 2
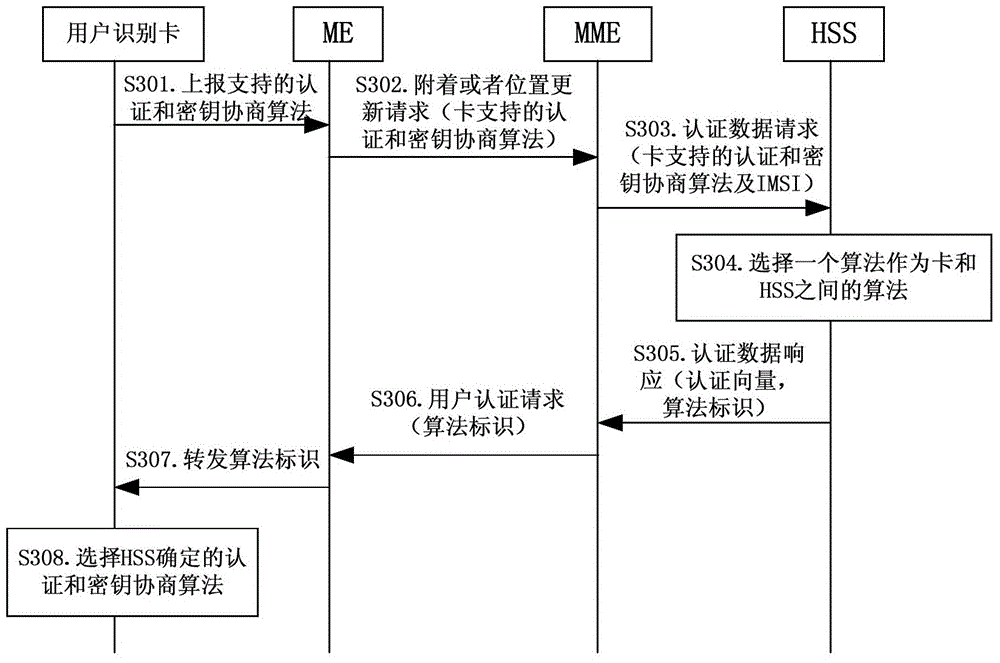
[0150] In this implementation, the HSS selects an authentication and key agreement algorithm that can be supported by both the subscriber identity card and the HSS according to the information of the authentication and key agreement algorithm reported by the subscriber identity card, as the authentication and key agreement algorithm between the subscriber identity card and the HSS. Key agreement algorithm, please refer to image 3 , image 3 It is a schematic flow diagram of the authentication and key agreement algorithm in Embodiment 2 of the present invention, and the method includes the following steps:
[0151] Step S301: the subscriber identity card reports the authentication and key agreement algorithm information it can support to the ME.
[0152] Step S302: After the ME receives the information about the authentication and key agreement algorithms it can support reported by the subscriber identity card, it sends an attach or location update message to the MME, and the...
Embodiment 3
[0164] In this implementation, the subscriber identity card protects the authentication and key agreement algorithm information it can support and then reports it to the network side. The protection method can be: use its own private key to sign the information or use the key shared by the card and HSS to calculate the HMAC value for the authentication and key agreement algorithm information supported by the user identification card and then report it to the network. When the HSS receives the information of the protected authentication and key agreement algorithm reported by the user identification card, it first verifies the signature or HMAC value, and only after the verification is successful, it selects an authentication and key that both the user identification card and the HSS can support. Negotiation algorithm, as the authentication and key agreement algorithm between the subscriber identity card and HSS, please refer to Figure 4 , Figure 4 It is a schematic flow dia...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com