Zero-trust network architecture and construction method
A network architecture and construction method technology, applied in the field of network security, can solve problems such as blurred boundaries between internal and external networks, difficulty in adapting to infrastructure, etc., and achieve the effects of convenient unified maintenance, high availability, and easy expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
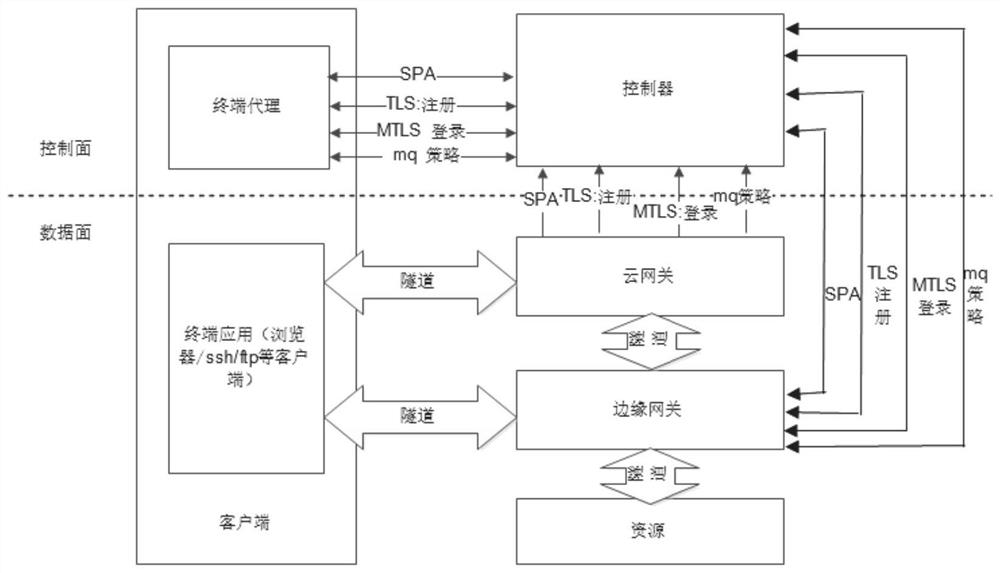
[0059] Such as figure 1 As shown, Embodiment 1 of the present disclosure provides a zero-trust network architecture. The network location boundary no longer determines access rights. Before access is allowed, all access subjects (including traditional internal and external network users and devices, etc.) Identity authentication and authorization are required to solve the security threats brought by the current enterprise network architecture with blurred boundaries.
[0060] The SDP technical architecture proposed by the International Cloud Security Alliance (CSA) includes three components: IH, AH, and SDP Controller. The relationship between the three components is divided into a control plane and a data plane. The architecture scheme adopted in this embodiment follows the two planes of the control plane and the data plane, and combines the actual business scenarios to plan four major components: the controller, the cloud gateway, the edge gateway, and the terminal agent.
...
Embodiment 2
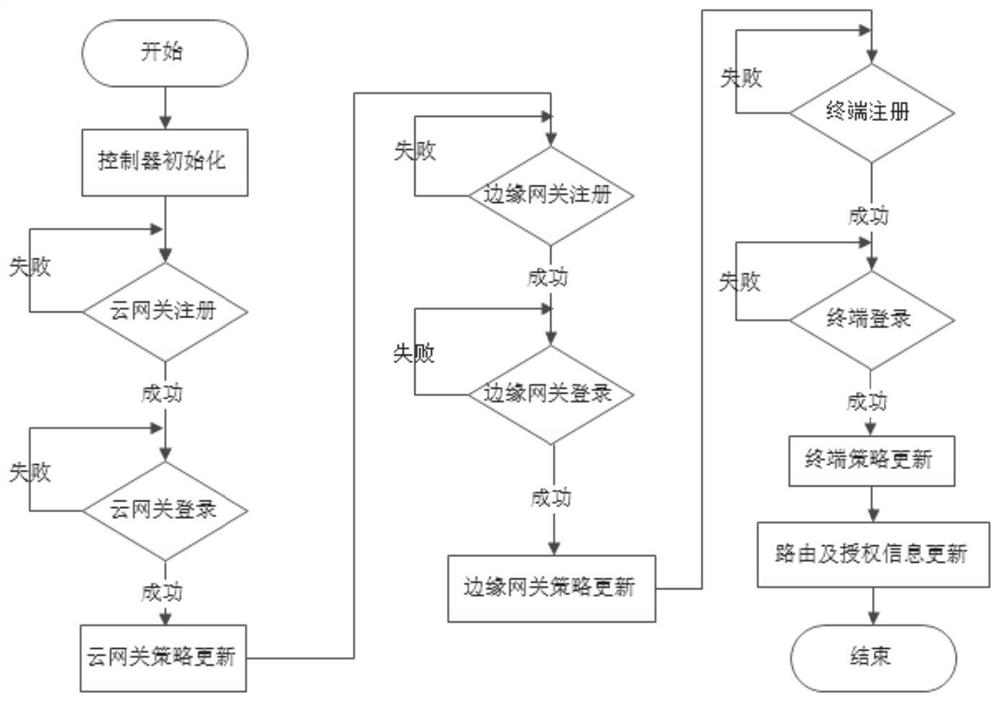
[0068] Such as figure 2 As shown, Embodiment 1 of the present disclosure provides a method for constructing a zero-trust network architecture, including:
[0069] Controller initialization process:
[0070] After the controller is installed, the organization administrator needs to log in to the controller and perform some initialization operations, including:
[0071] To add an area, the administrator needs to enter the information of the area included in the organization, mainly including the area name, description, and planned virtual IP segment (cannot conflict with the private network IP already used by the enterprise);
[0072] Add users, user information includes: name, department, mobile phone, email, etc.;
[0073] Add a cloud gateway, the cloud gateway information includes: name, cluster area, administrator mobile phone, administrator mailbox, etc.;
[0074] Add an edge gateway, the edge gateway information includes: name, organization area, administrator mobile p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com