Policy conflict detection method and system for SDN (Software Defined Network) application
A conflict detection and strategy technology, applied in the field of network information security, can solve problems such as unresolved, inability to adopt, and poor strategy scalability, and achieve the effect of easy expansion and implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
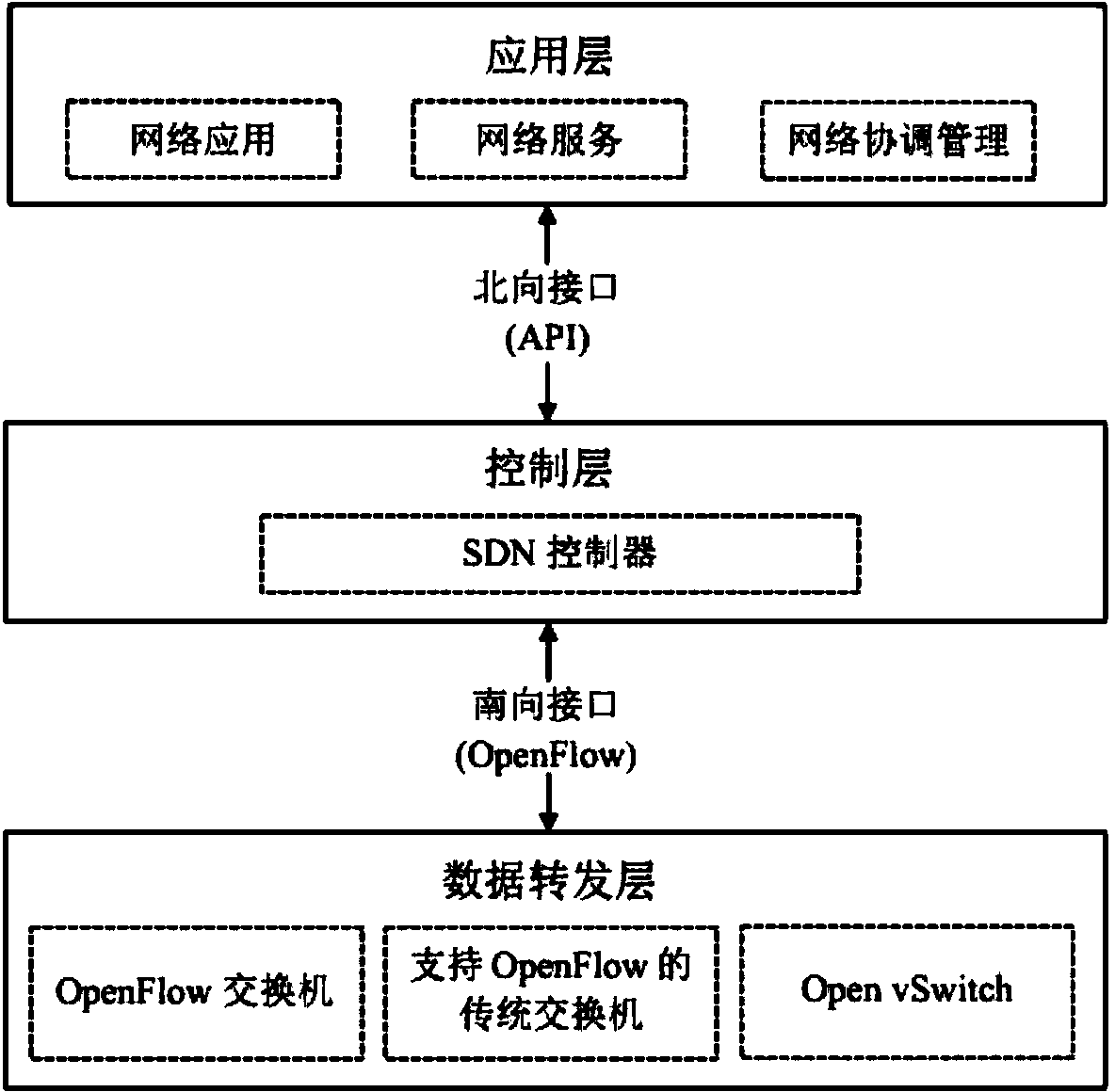
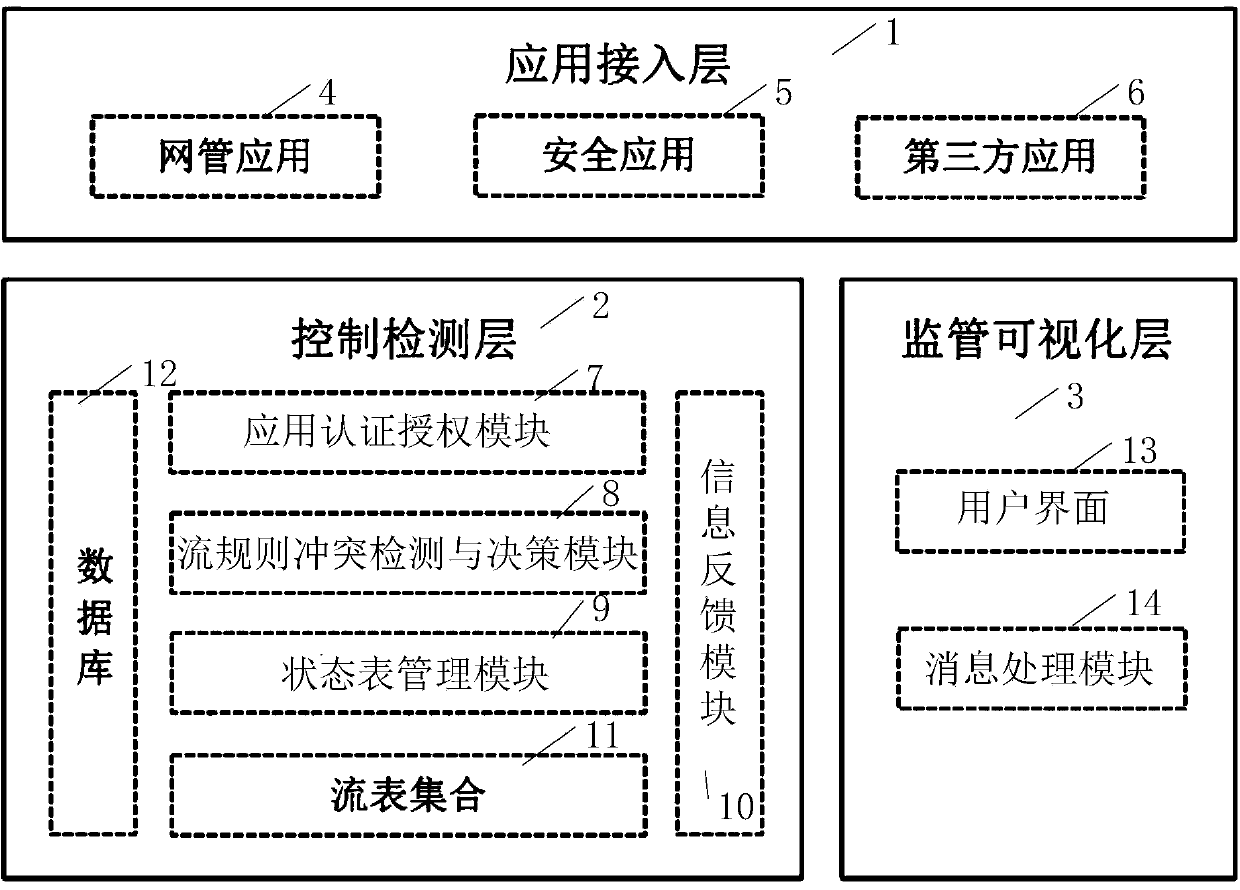
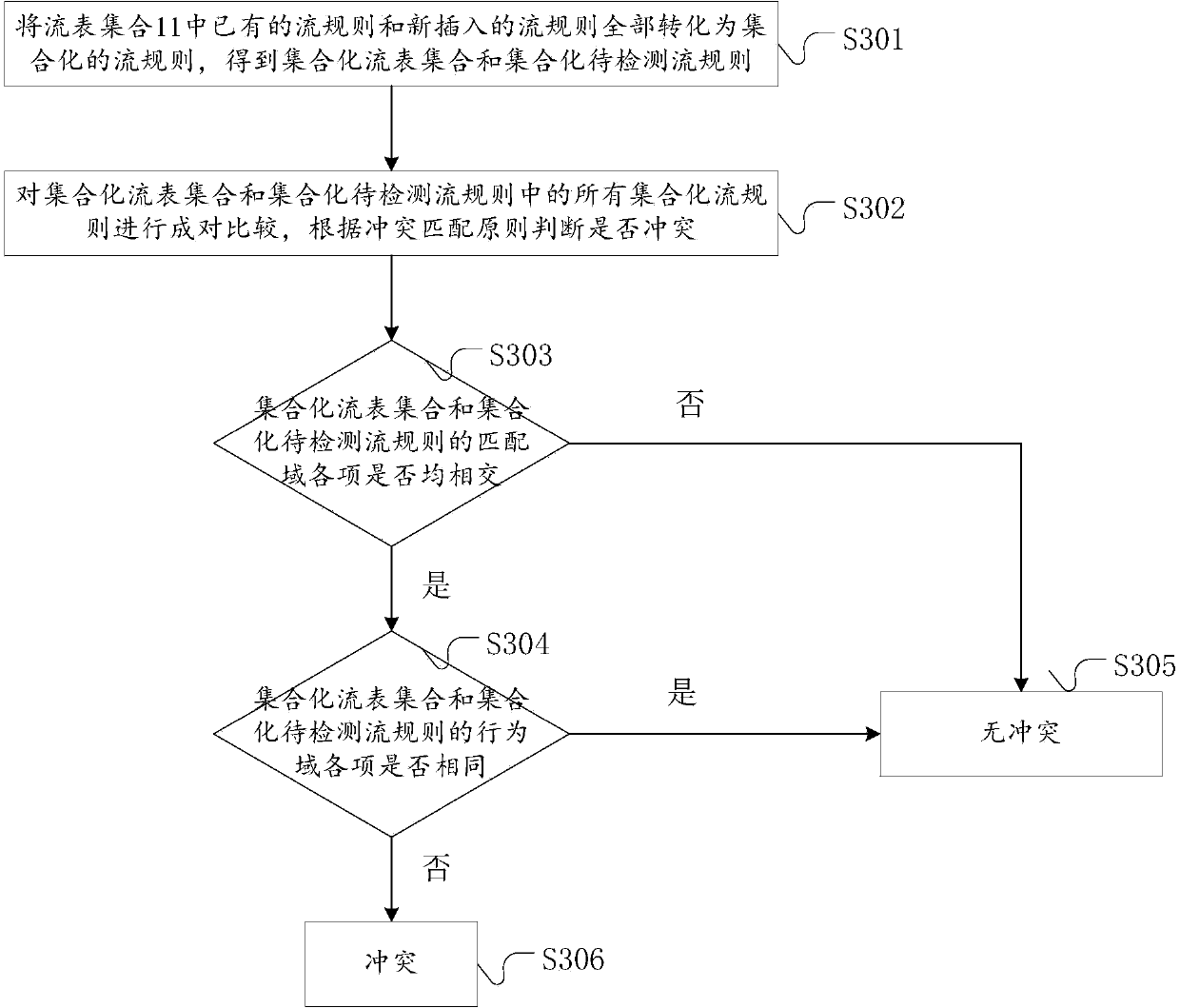
[0048] In the embodiment of the present invention, a policy conflict detection system for SDN applications is proposed, which is mainly aimed at SDN applications. It authenticates and authorizes applications that want to access the network, assigns priority, and sends streams to them according to the conflict analysis algorithm. The rule requests conflict detection, if there is a conflict, it will be mediated according to the conflict decision algorithm, and the network status will be fed back to the network management personnel in real time. In particular, the conflict detection algorithm can realize the policy conflict detection when there is an intermediate behavior such as Set in the flow rule and the policy conflict detection after the flow rules of different applications are combined. In addition, the policy conflict detection system is extended on the basis of the Java-based SDN controller (OpenDaylight), implements corresponding modules according to the design requireme...
Embodiment 2
[0105] The policy conflict detection method for SDN applications proposed by the present invention is applied in a policy conflict detection system for SDN applications. Mainly for SDN applications. The method is extended on the basis of the Java-based controller (OpenDaylight), and the corresponding system implements corresponding modules according to the design requirements, and adds functional modules in the configuration file of the controller, so as to realize automatic loading when the controller starts. The system corresponding to the method adopts a module loader (ModuleLoader) to manage each module.
[0106] In the policy conflict detection system architecture, the main implementation process is:
[0107] The control detection layer 2 receives the access authorization requests of the applications that want to access the network from the application access layer 1, assigns corresponding priorities to each application that wants to access the network according to the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com