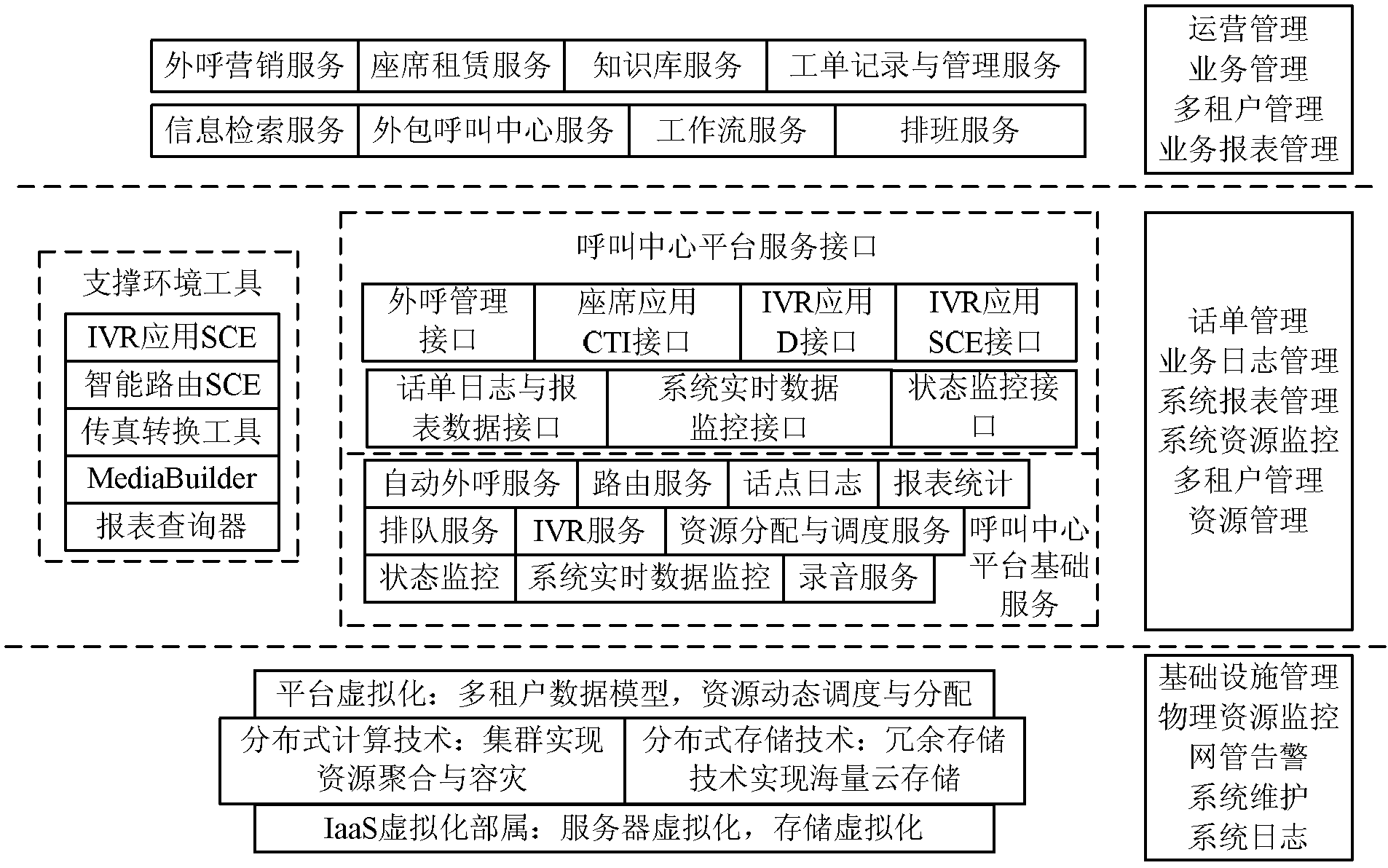
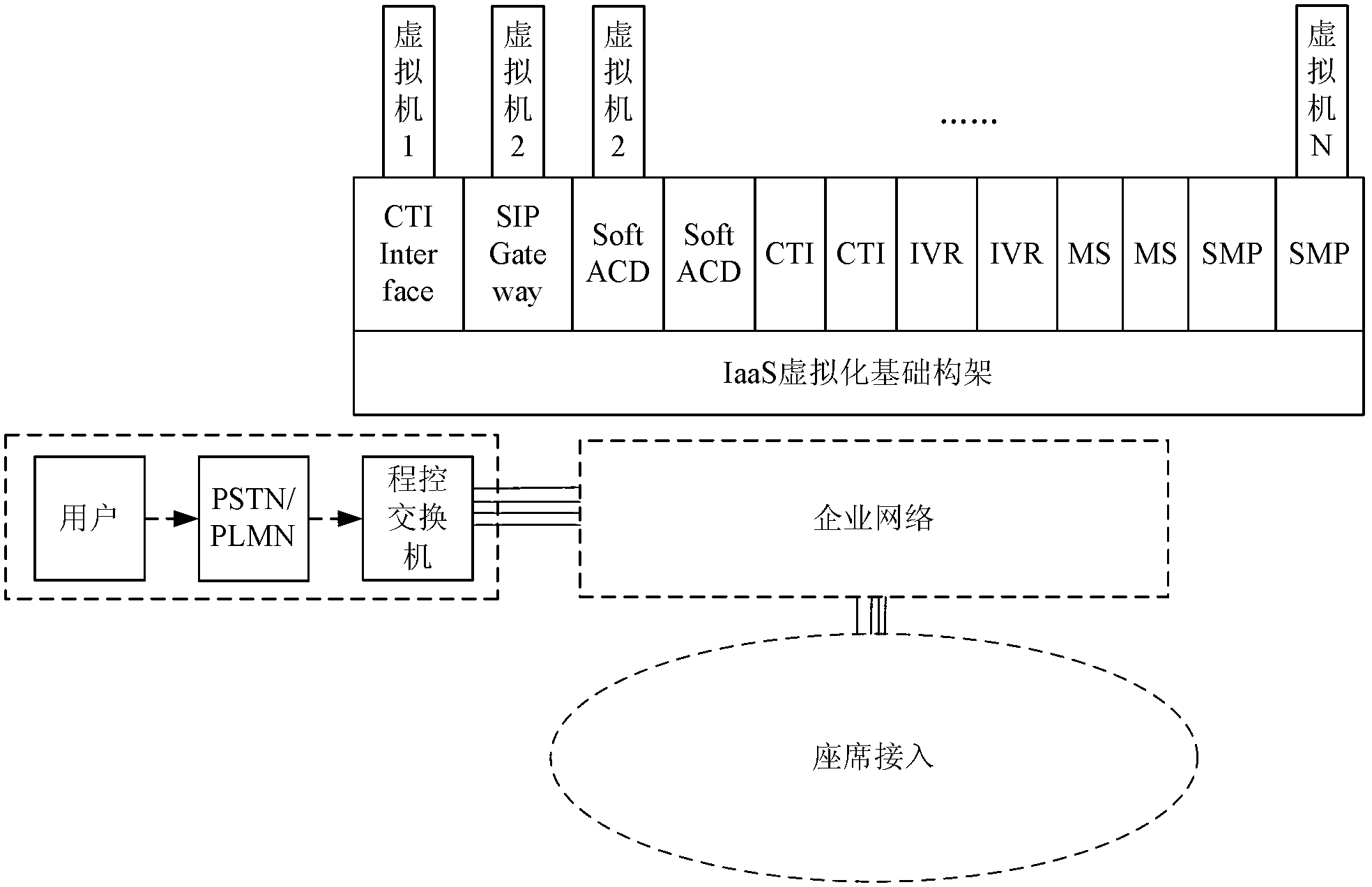
Patents
Literature
43 results about "Open network architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunications, and in the context of Federal Communications Commission's (FCC) Computer Inquiry III, Open network architecture (ONA) is the overall design of a communication carrier's basic network facilities and services to permit all users of the basic network to interconnect to specific basic network functions and interfaces on an unbundled, equal-access basis.
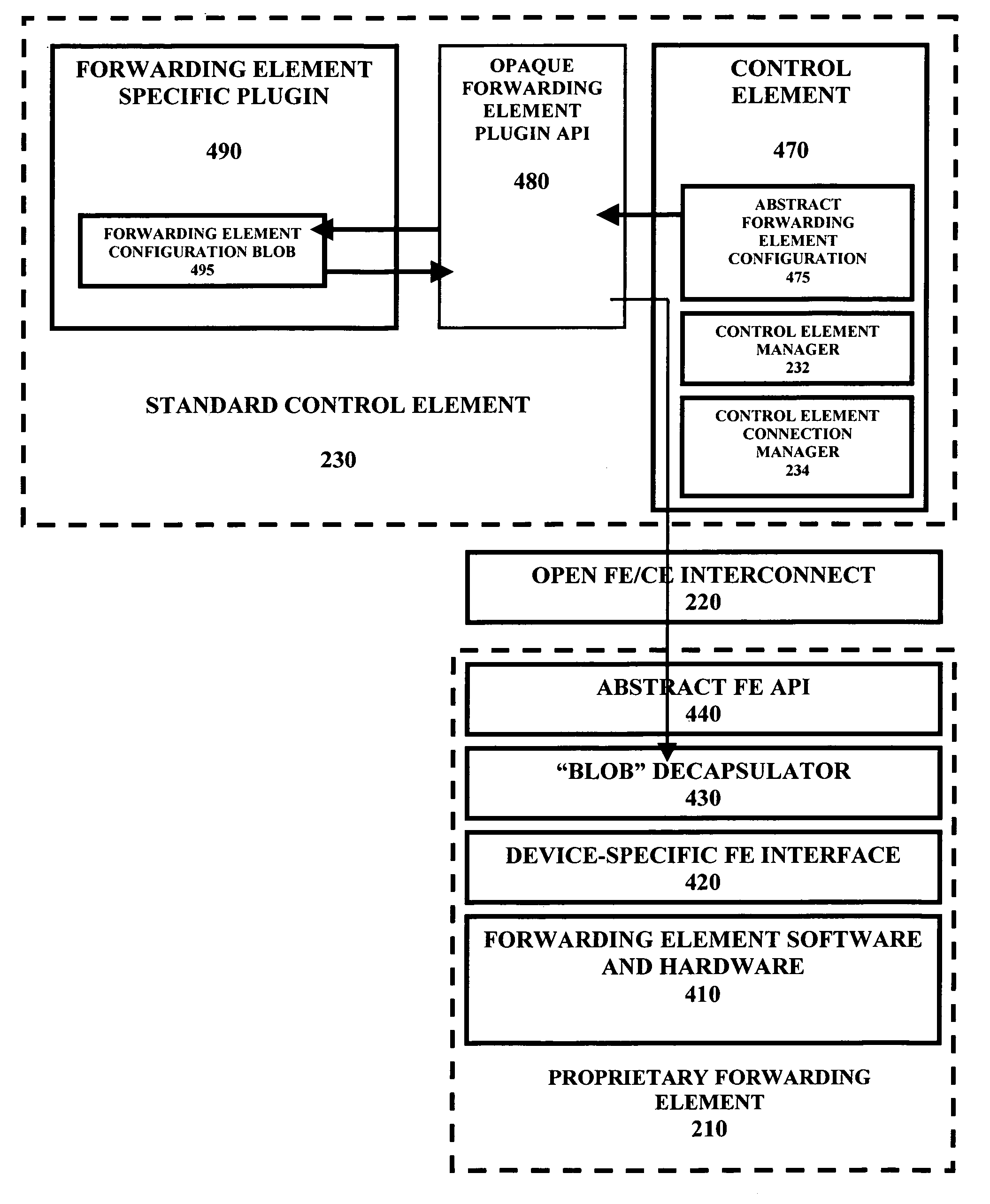
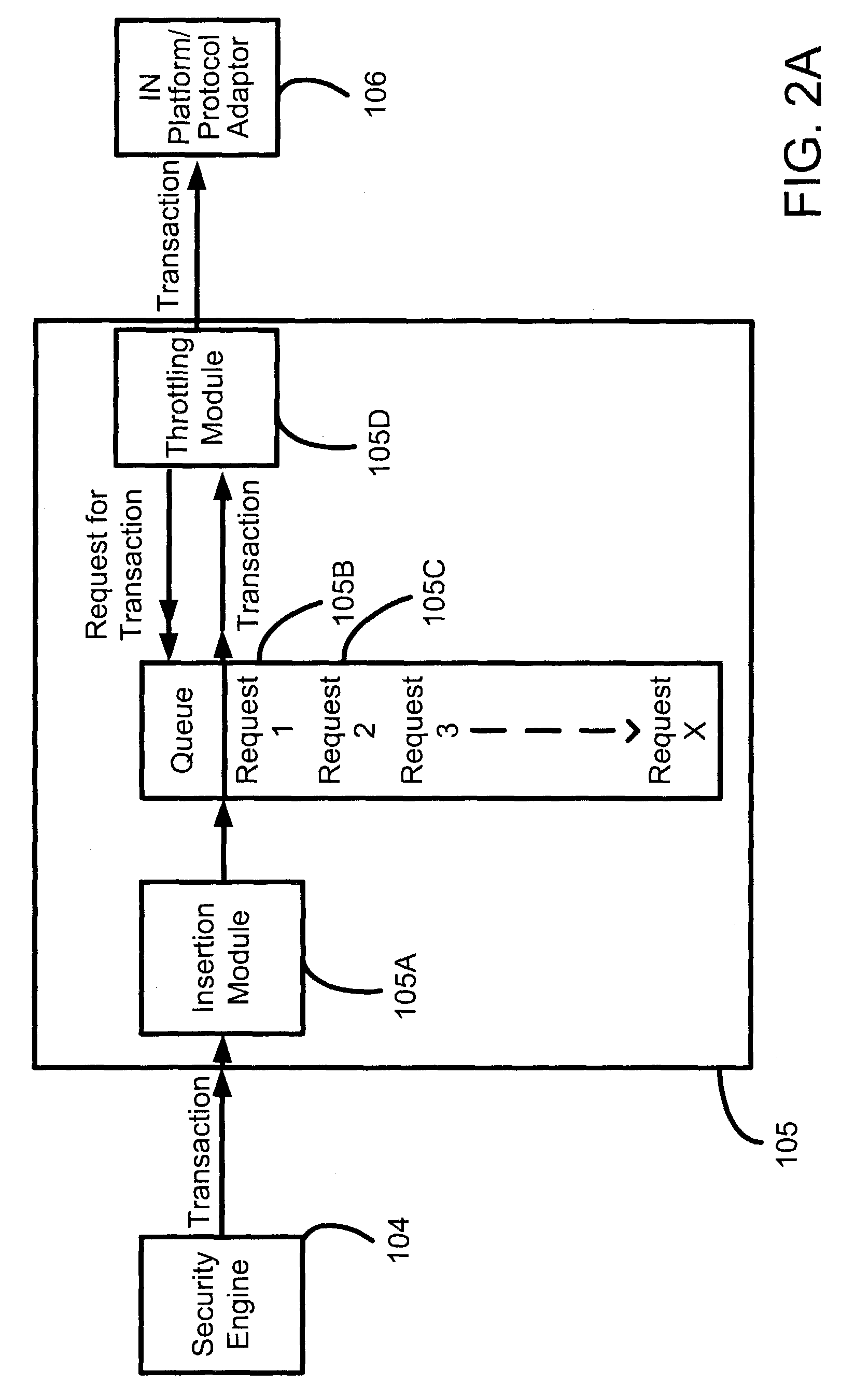
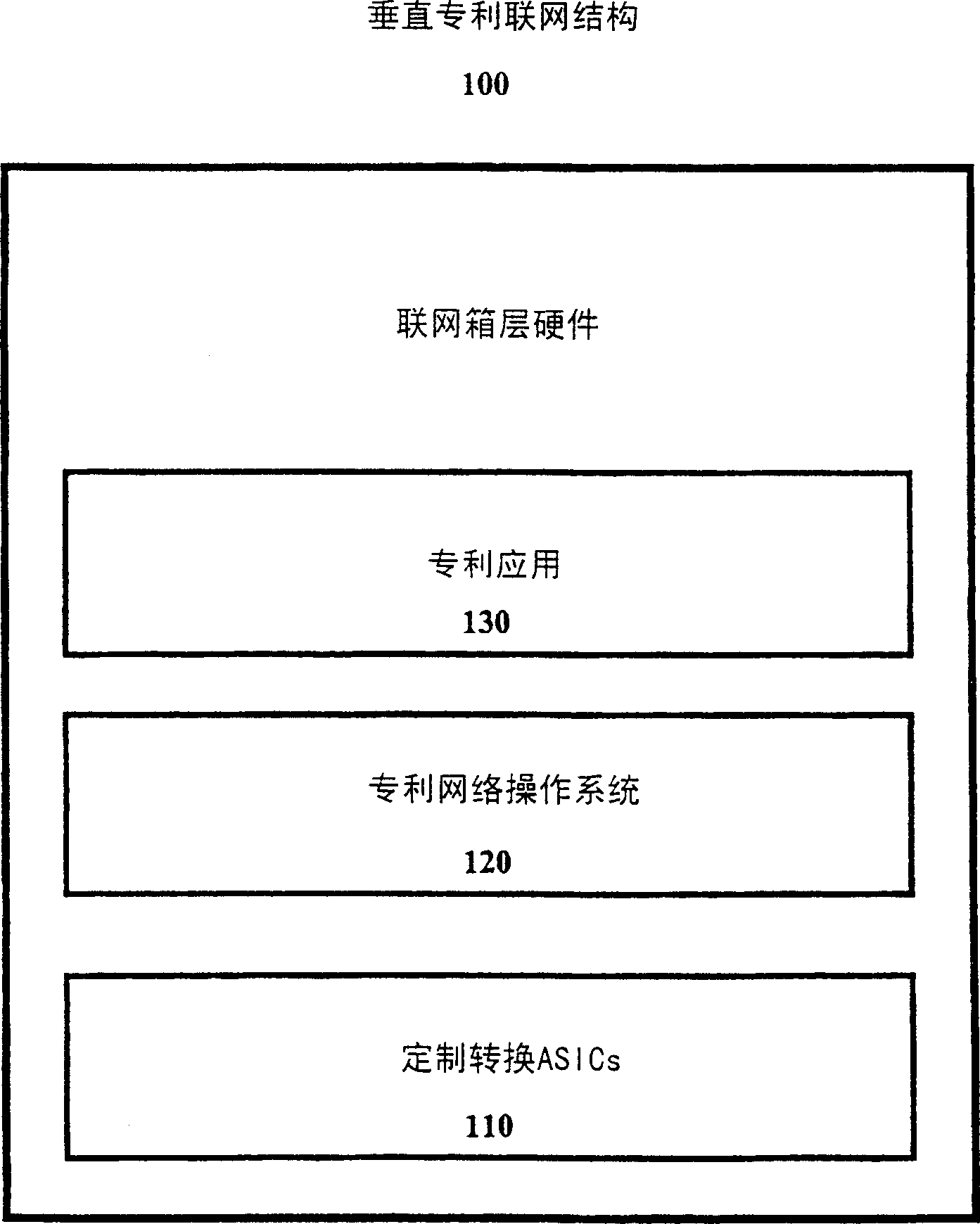
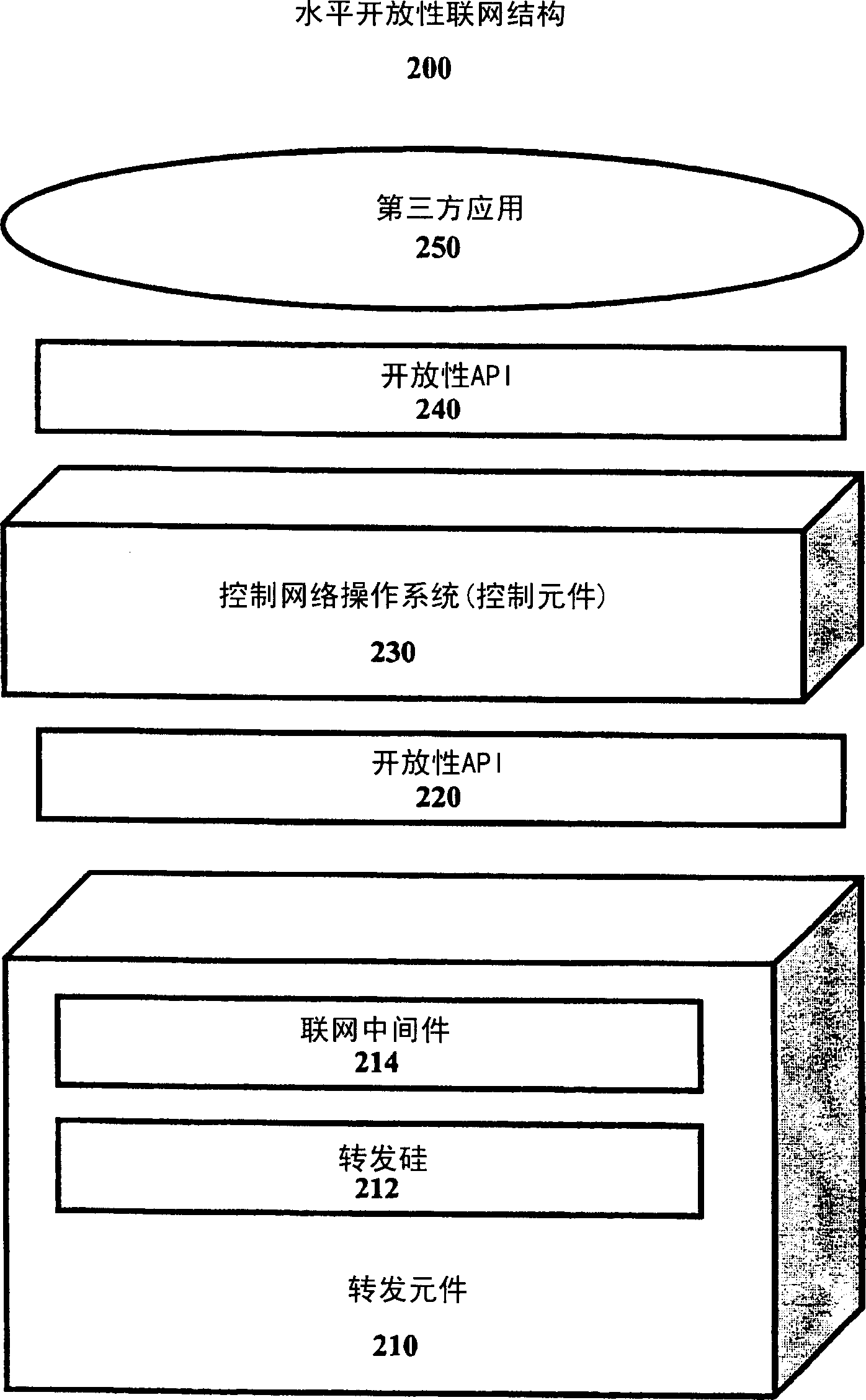
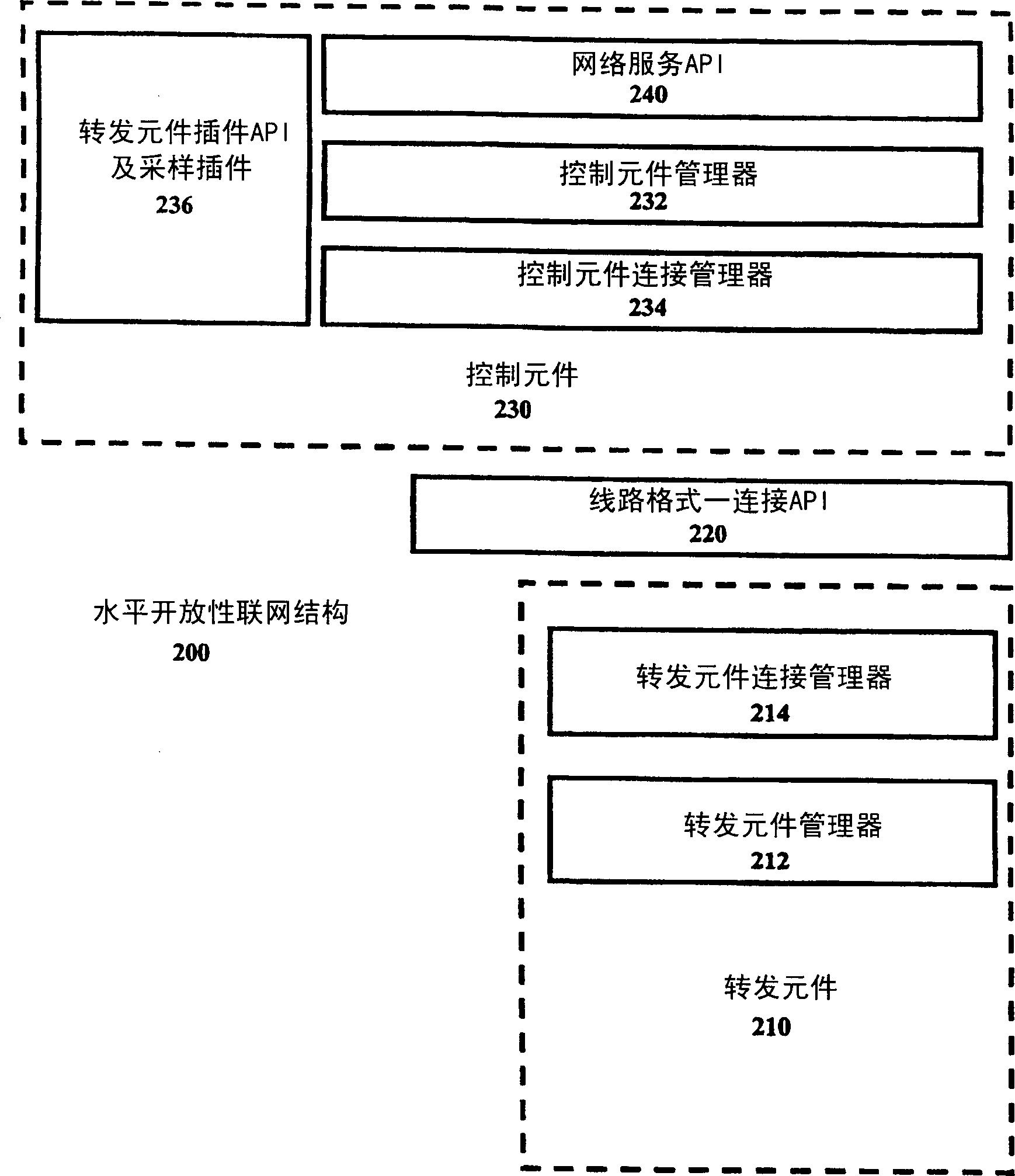
Method and apparatus for allowing proprietary forwarding elements to interoperate with standard control elements in an open architecture for network devices
InactiveUS7203740B1Multiple digital computer combinationsData switching networksData setComputer network
A computer system for allowing proprietary forwarding elements to interoperate with standard control elements in an open network architecture. The computer system comprises a forwarding element that is adapted to perform data forwarding functions in a computer network. A control element is adapted to perform network signaling and control functions in the computer network. The control element is adapted to generate a standardized data set for configuring the forwarding element. An interconnecting element operatively connects the forwarding element to the control element. A forwarding element plugin is integrated with the control element for receiving the standardized data set from the control element, translating the standardized data set into a specialized data set, and transmitting the specialized data set to the forwarding element to configure the forwarding element. The forwarding element utilizes the specialized data set to configure the forwarding element for performing data forwarding in the computer network.
Owner:INTEL CORP
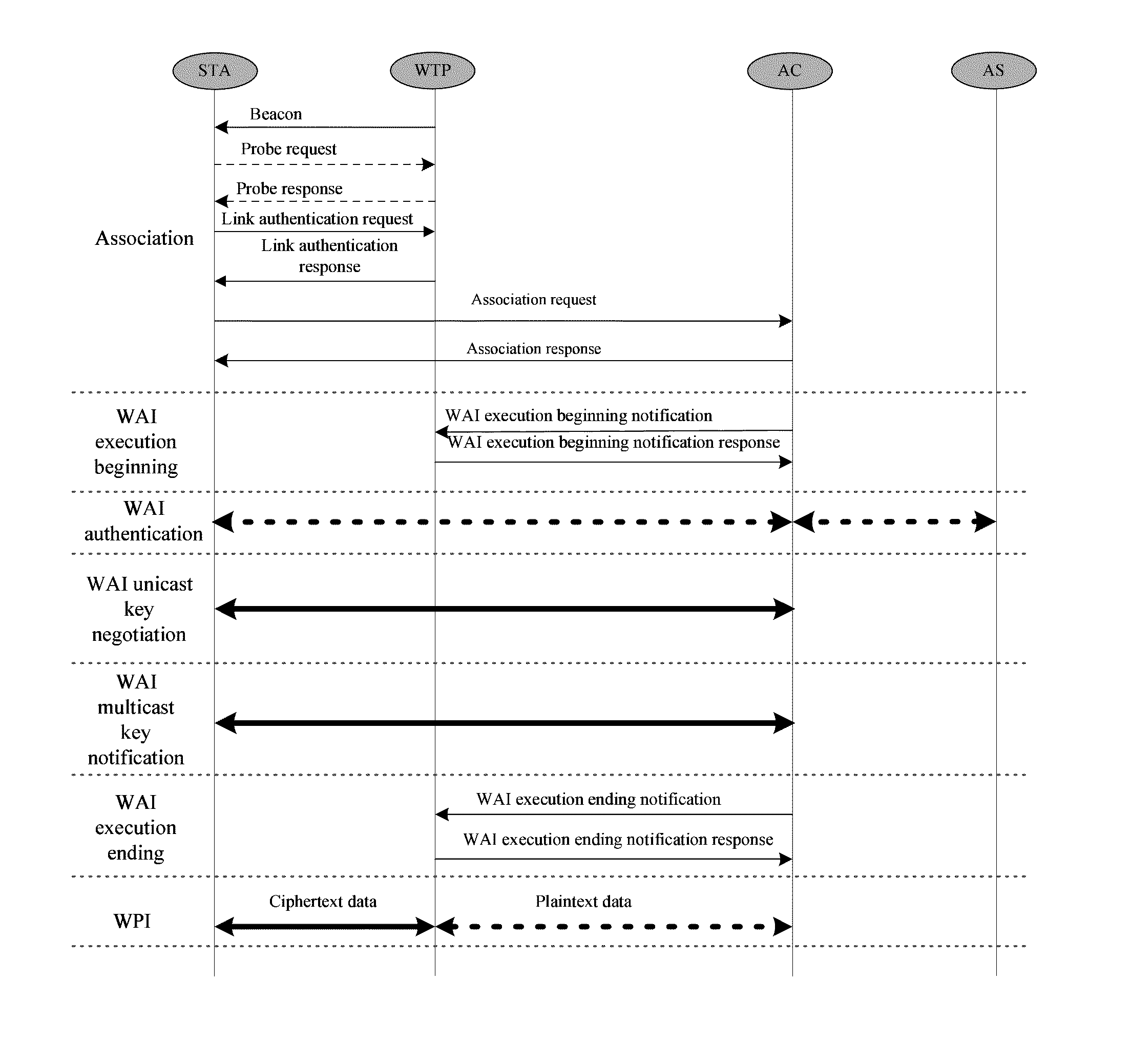
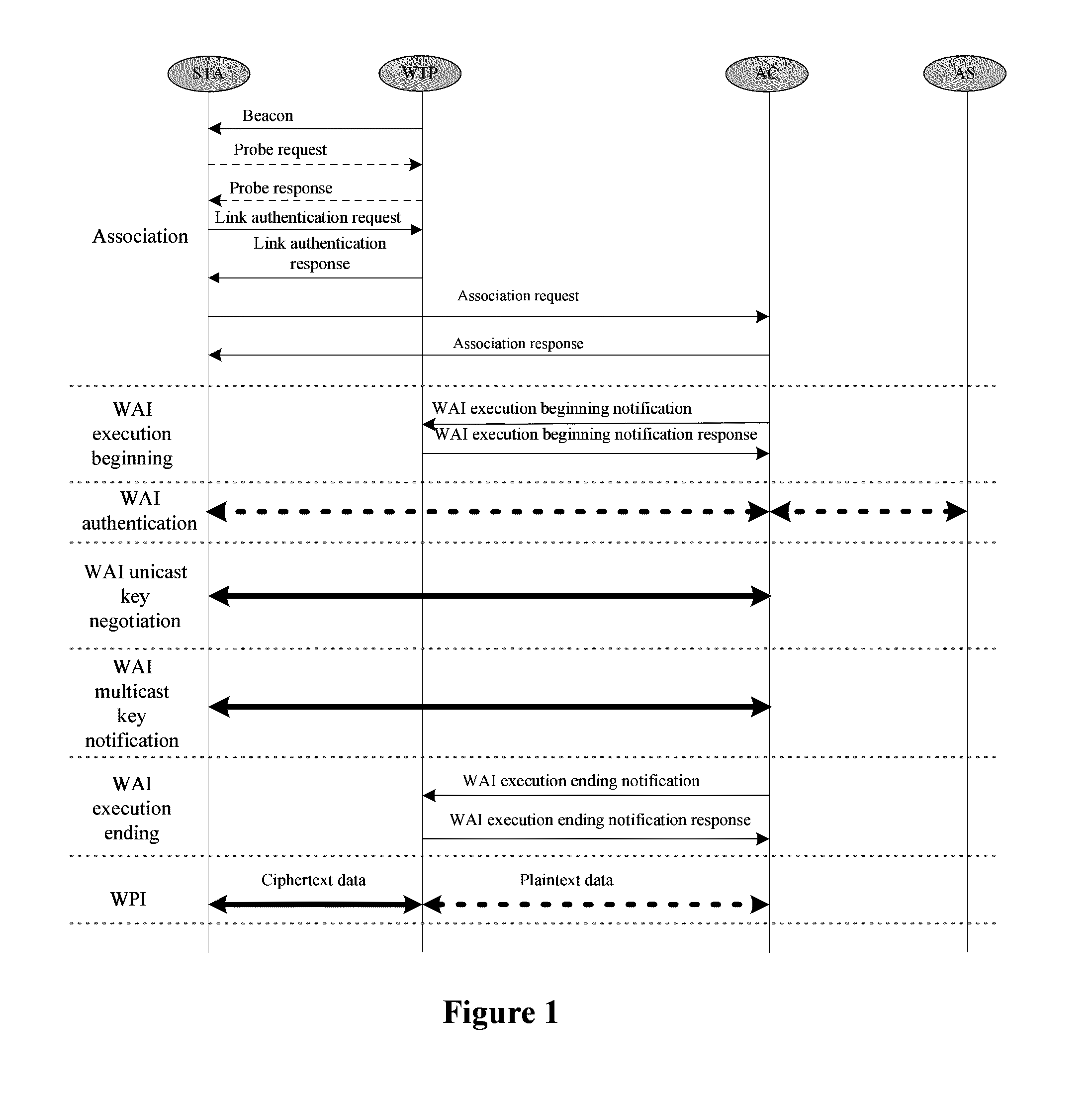
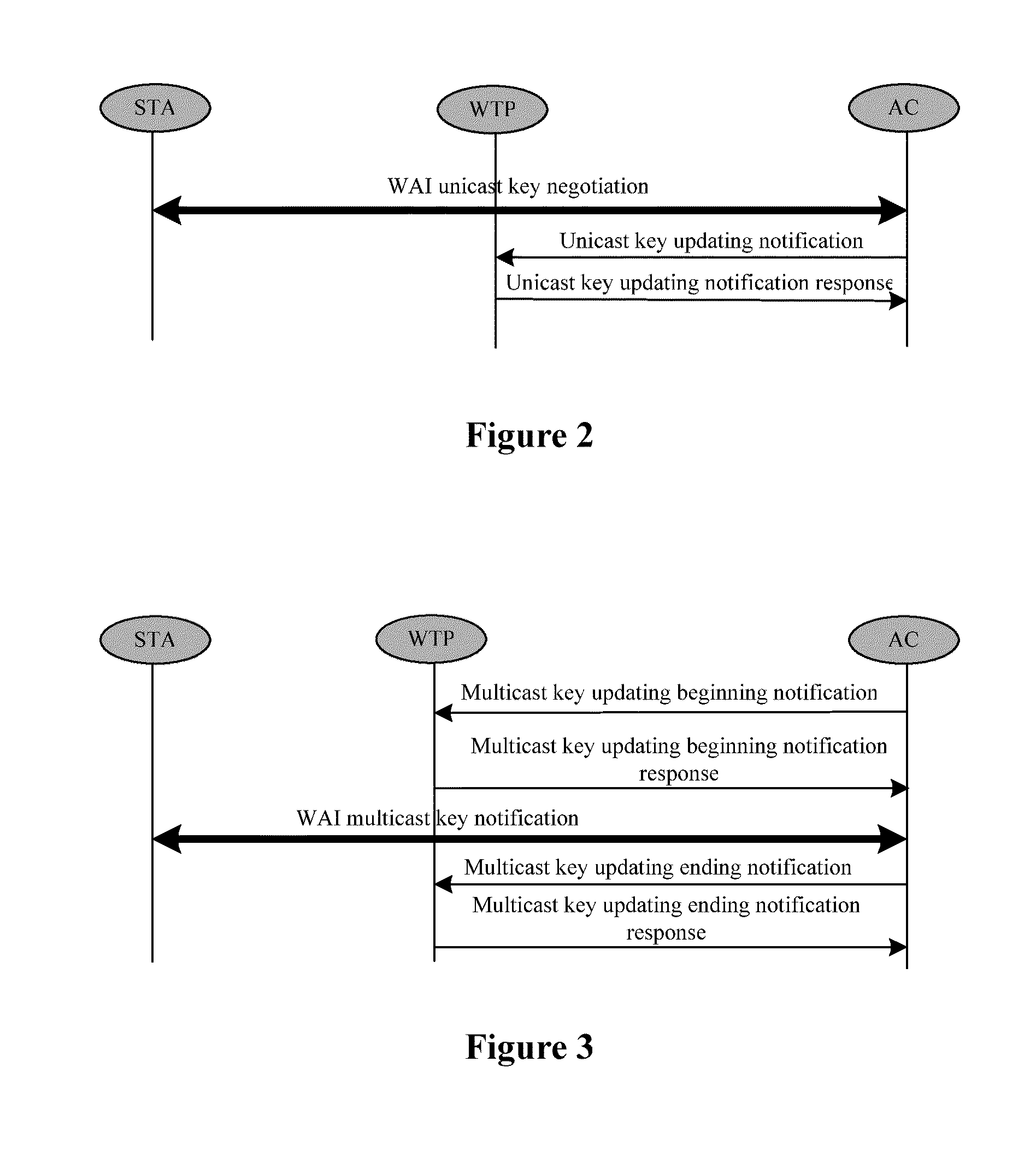
Method for implementing a convergent wireless local area network (WLAN) authentication and privacy infrastructure (WAPI) network architecture in a local MAC mode
ActiveUS9015331B2Security of the WLAN is ensuredBreak the limitationsNetwork topologiesMultiple digital computer combinationsNetwork architectureMedia access control
A method for implementing a convergent Wireless Local Area Network (WLAN) Authentication and Privacy Infrastructure (WAPI) network architecture in a local Medium Access Control (MAC) mode is provided and includes the following steps: the MAC function and WAPI function of Access Point (AP) are divided between Wireless Terminal Point (WTP) and Access Controller (AC) to construct a local MAC mode; the convergence of WAPI protocol and the convergent WLAN network architecture is implemented in the local MAC mode; the process of association and connection between Station (STA), WTP and AC is performed; the process of notification of the beginning of the execution of the WLAN Authentication Infrastructure (WAI) protocol between AC and WTP is performed; the process of the execution of the WAI protocol between STA and AC is performed; the process of notification of the end of the execution of the WAI protocol between AC and WTP is performed; the process of encrypted communication between WTP and STA is performed by use of WPI.
Owner:CHINA IWNCOMM
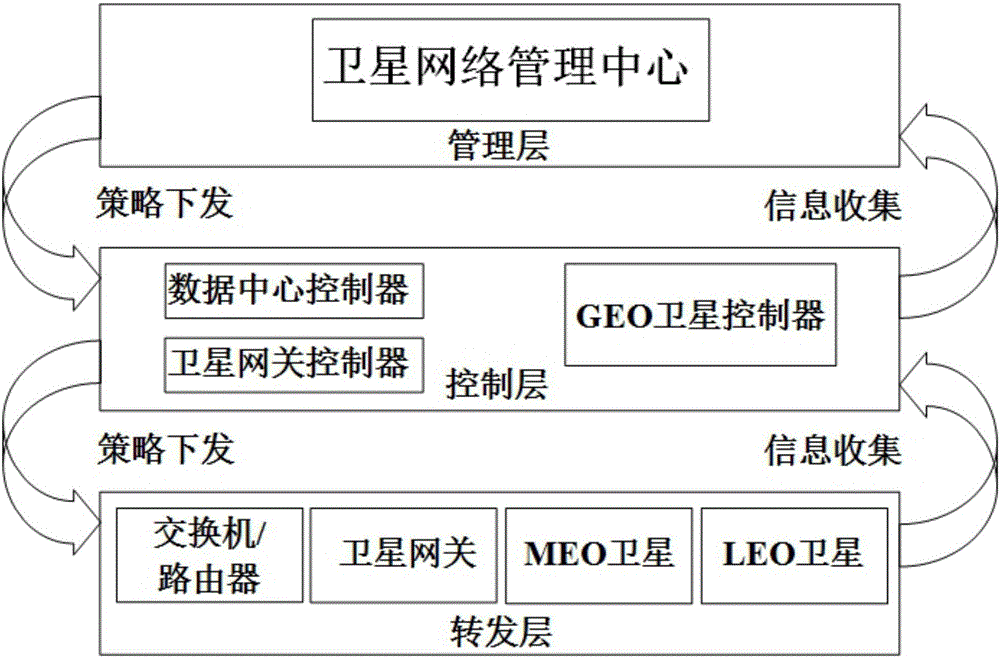
Air-ground integrated network architecture and data transmission method based on SDN and NFV technology
InactiveCN106059650AIncrease profitRealize on-demand servicesRadio transmissionData switching networksControl layerNetwork link
The invention discloses an air-ground integrated network architecture based on a software defined network and network function virtualization. According to the system architecture, the entire network consists of a ground network part and a space network part, and is divided in a unified manner into a management layer, a control layer and a forwarding layer. The management layer is responsible for registering and querying the network status and network service functions of the ground part and the space part in the air-ground integrated network and making routing, security, billing, service call and resource management strategies. The control layer consists of a ground part and a space part, and is responsible for controlling data forwarding according to the strategies of the management layer and collecting the information of network links and network service functions. The forwarding layer consists of a ground part and a space part, and is responsible for forwarding data and providing network service functions. The architecture uses a software defined network and an idea of network function virtualization, and efficient information transmission control and on-demand satellite service providing are realized in an air-ground integrated network.
Owner:BEIJING JIAOTONG UNIV
Communication network realized by network architecture based on separation of control surfaces and media surface
InactiveCN102045692ARealize resource releaseNetwork traffic/resource managementConnection managementProcessor registerRadio access network
The invention relates to a communication network realized by a network architecture based on the separation of control surfaces and media surface. The communication network comprises a radio access network, an access node which is connected between the radio access network and a packet data network and is used for data switching, and a mobility management node connected with the access node and the radio access network. The communication network also comprises an identity location register (ILR)and the packet data network which are connected with the access node, wherein the access node provides an access service for a terminal, distributes a route mart directing to the access node for the terminal, maintains the mapping information of the terminal and a correspondence node, registers on an ILR in the terminal location, unregisters and queries the RID of the terminal and realizes the routing and forwarding of the data message; the ILR is used for receiving a registration request and an unregistration request of the ILR home user terminal, maintaining the AID-RID mapping information of the home user terminal and returning the RID corresponding to the AID of the terminal in the request to the party sending a query request after receiving the search request about the RID of the terminal. The communication network can avoid alternate routing and does not change the application context of the terminal.
Owner:ZTE CORP
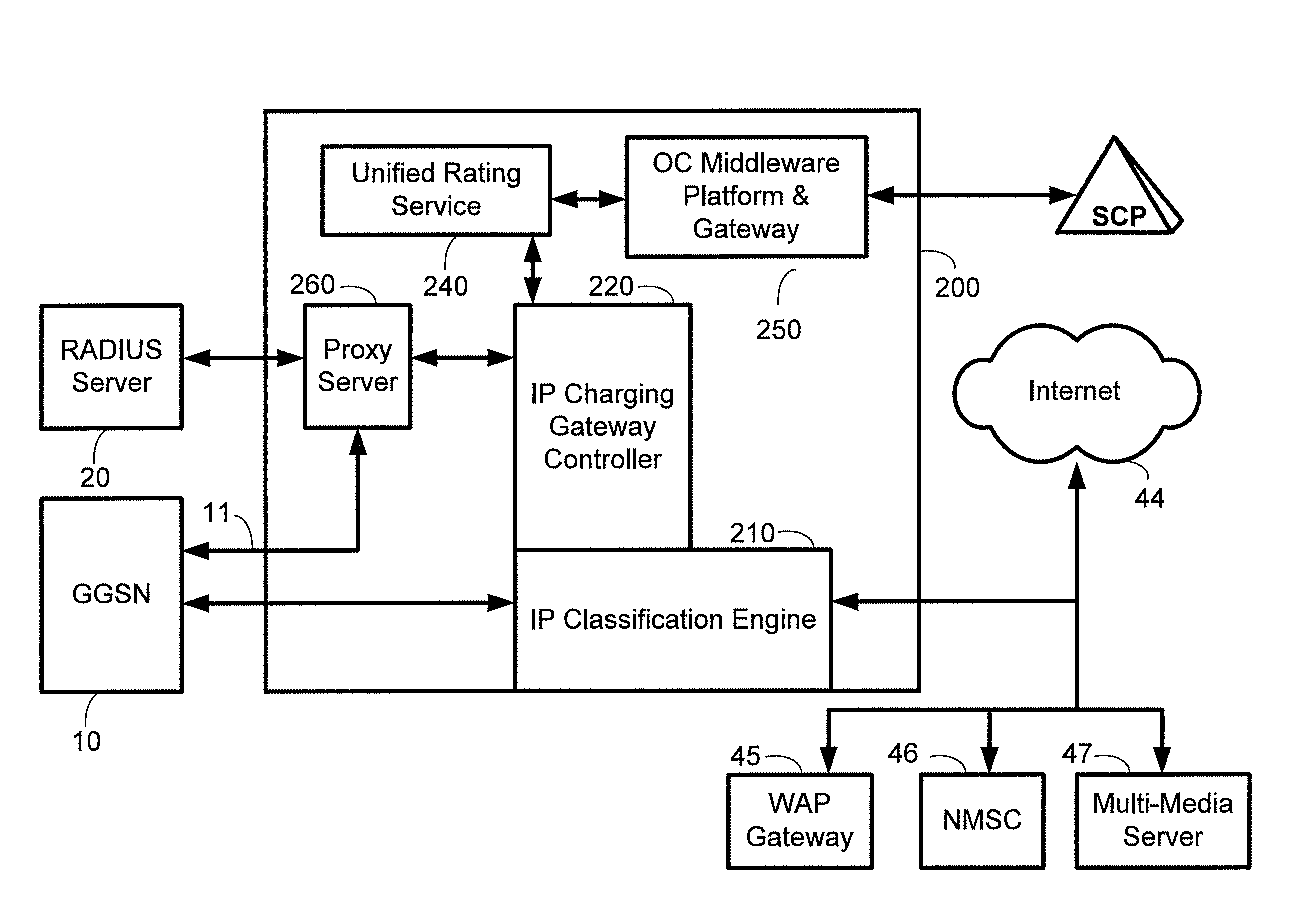
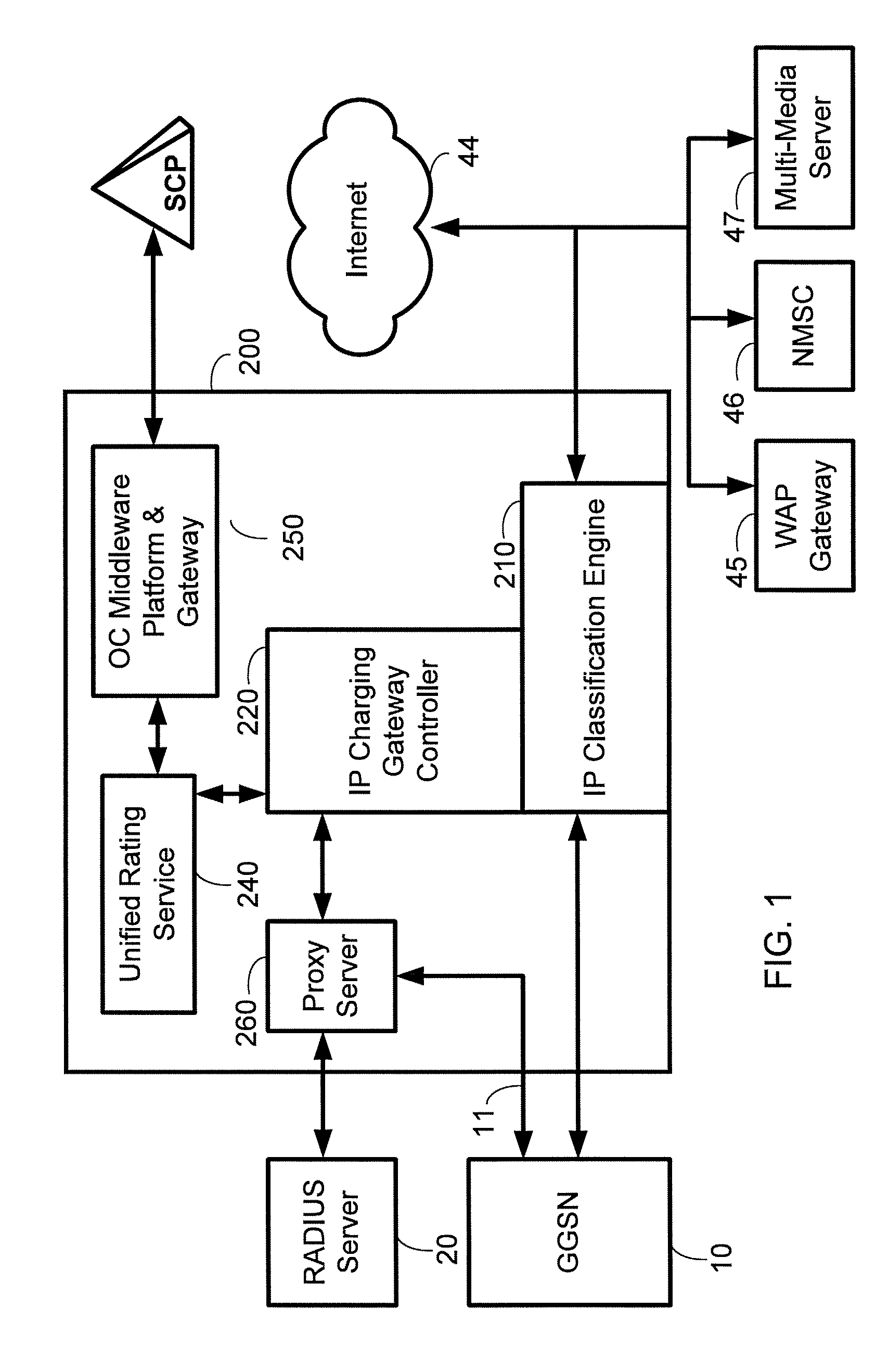
Method for implementing an internet protocol (IP) charging and rating middleware platform and gateway system
InactiveUS7457865B2Metering/charging/biilling arrangementsMultiple digital computer combinationsInternet protocol suiteTelecommunications network
A method and a system for enabling a telecommunication network operators to transparently intermediate P data flow, by providing a highly scalable, and superior data classification method for implementing policy based filtering, forwarding, accounting and / or monitoring of informational packets of interest; and indeed, is intended to exploit the resiliency of open network architecture and lessen the requisite dependency on proprietary network elements services and other such systems.
Owner:REDKNEE INC
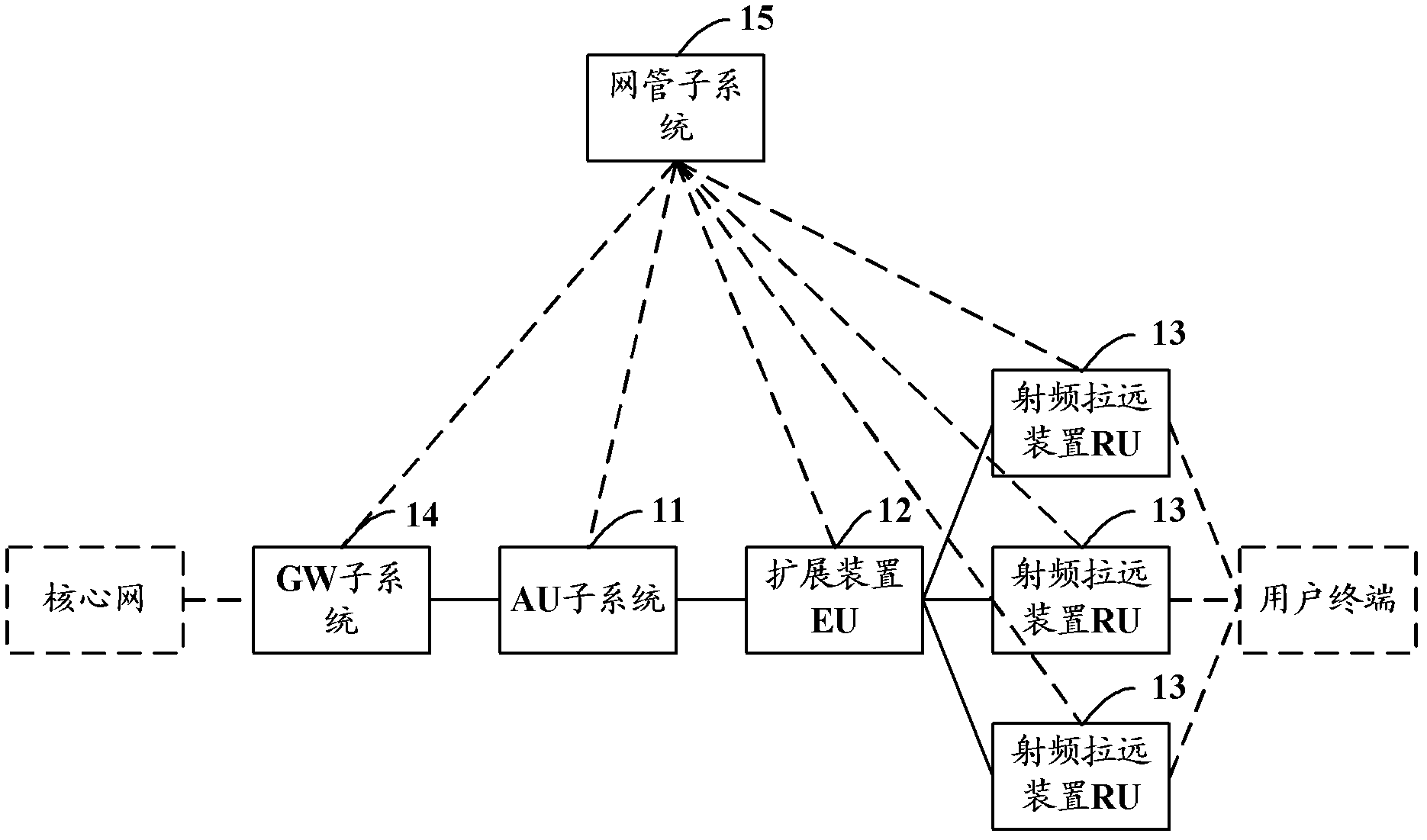
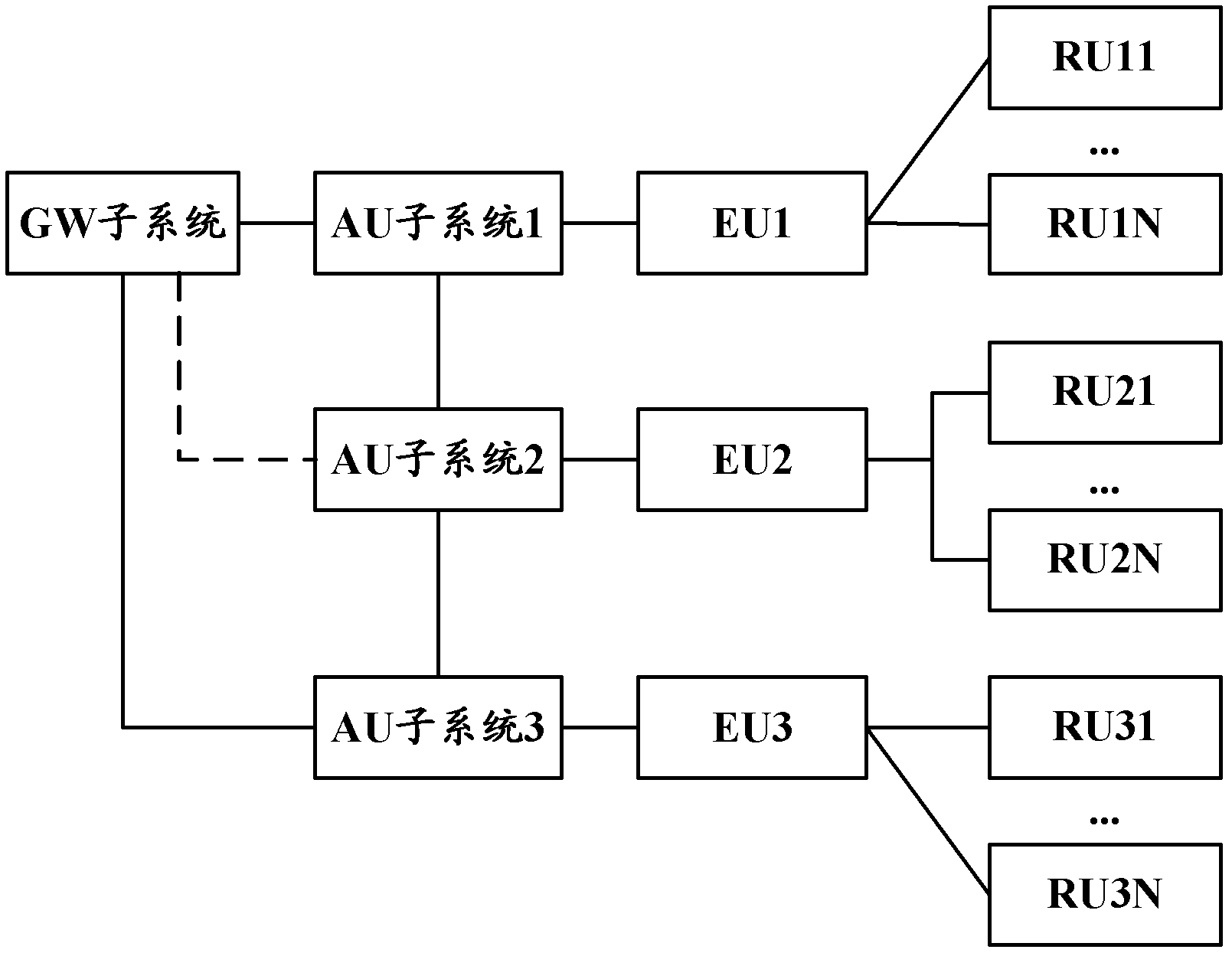
Wireless communication system and method for flat network architecture and extend unit
The invention discloses a wireless communication system and a wireless communication method for a flat network architecture, and an extend unit. The wireless communication system comprises access unit (AU) subsystems, the EU and at least one radio remote unit (RU) connected with the EU. The EU is used for converting a downlink baseband high-speed signal transmitted by the AU subsystem into a downlink sub-baseband low-speed signal, and transmitting the downlink sub-baseband low-speed signal to the RU, so that the EU can be connected with the RU by a low-speed transmission link such as a category-5 cable, indoor coverage is facilitated, and difficulty and cost in network deployment are reduced; the wireless communication system supports the concatenation and stacking mode of the AU subsystems, so that the capacity extensibility of the system is improved; and in addition, the wireless communication system also can comprise a gateway (GW) subsystem, and the function of a radio network controller (RNC) is shifted down to the GW subsystem and the AU subsystem to further disintegrate and simplify the structure of the whole communication system, so that a network processing time delay and a transmission time delay are shortened.
Owner:COMBA TELECOM SYST CHINA LTD
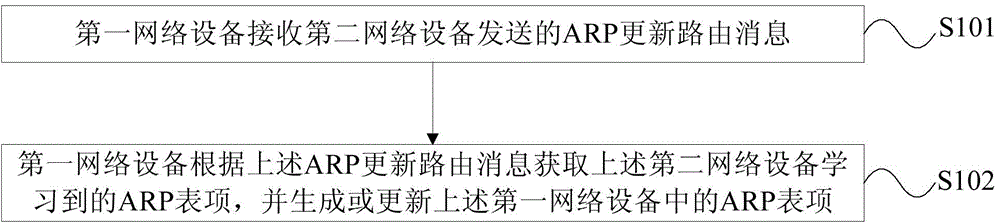
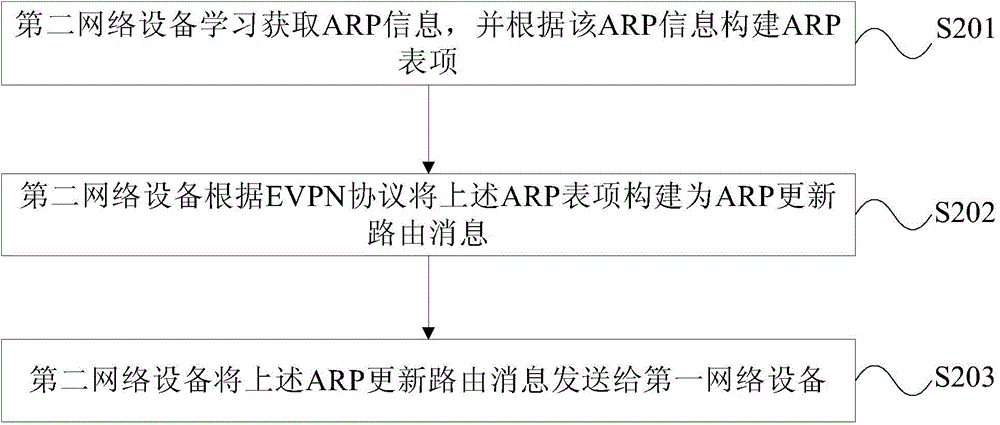
Distributed gateway backup processing method and network equipment
InactiveCN105790996ASave resourcesSimple configurationNetworks interconnectionNetwork connectionsAddress Resolution ProtocolPrivate network
The embodiment of the invention provides a distributed gateway backup processing method and network equipment. The method comprises the following steps that: first network equipment receives an ARP (Address Resolution Protocol) update route message sent by second network equipment, wherein the ARP update route message is constructed according an EVPN (Ethernet Virtual Private Network) protocol; and the first network equipment acquires ARP table entries learned by the second network equipment according to the ARP update route message, and generates or updates the ARP table entries in the first network equipment, wherein in a first virtual local area network (VLAN), the first network equipment is currently a non-DF (non-Designated Forwarder) elected according to the EVPN protocol, and the second network equipment is currently a DF (Designated Forwarder) elected according to the EVPN protocol. In the embodiment of the invention, selection of active and standby gateways and backup of ARP information can be finished through network architecture of an EVPN without establishment of a special channel for electing active and standby gateway equipment or establishment of a special channel for backing up the ARP message, so that resources are saved; configuration is simplified; and the operation and maintenance difficulty is lowered.
Owner:北京华为朗新科技有限责任公司
Pure IP calling system based on a cloud computing platform and IMS network architecture
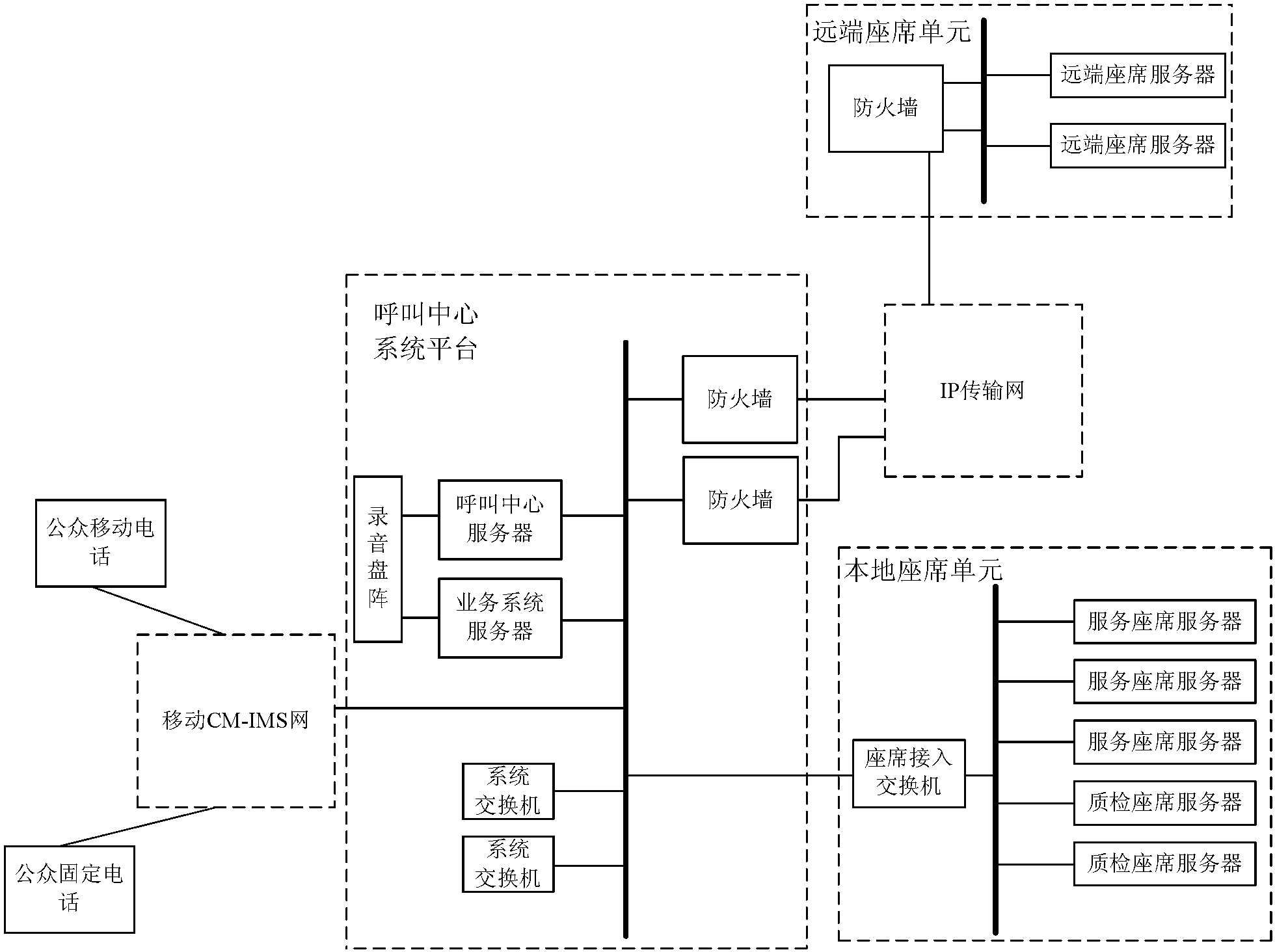
ActiveCN103269344ATrunk line shortenedEfficient and stable solutionSpecial service for subscribersData switching networksM-governmentNetwork architecture
The invention relates to a calling system, in particular to a pure IP calling system based on a cloud computing platform and an IMS network architecture. The calling system aims at solving the problems in achieving calling center services on a CS domain that a relaying circuit is long, a computer room occupies a large space, and a system is poor in expansion capacity. B public mobile phones and C public mobile phones in the calling center system are all connected to a mobile CM-IMS net, a calling center server, a service system server and A system switches are all connected to the mobile CM-IMS net through a transmission bus, the calling center server, the service system server and the A system switches are all connected to an IP transmission network, and D far end seat servers are all connected to the IP transmission network through a firewall. The application range of the pure IP calling system covers industries of governments and public services, for example, the industries of municipal administration, police, traffic management, energy and the like which are high in information application degree.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
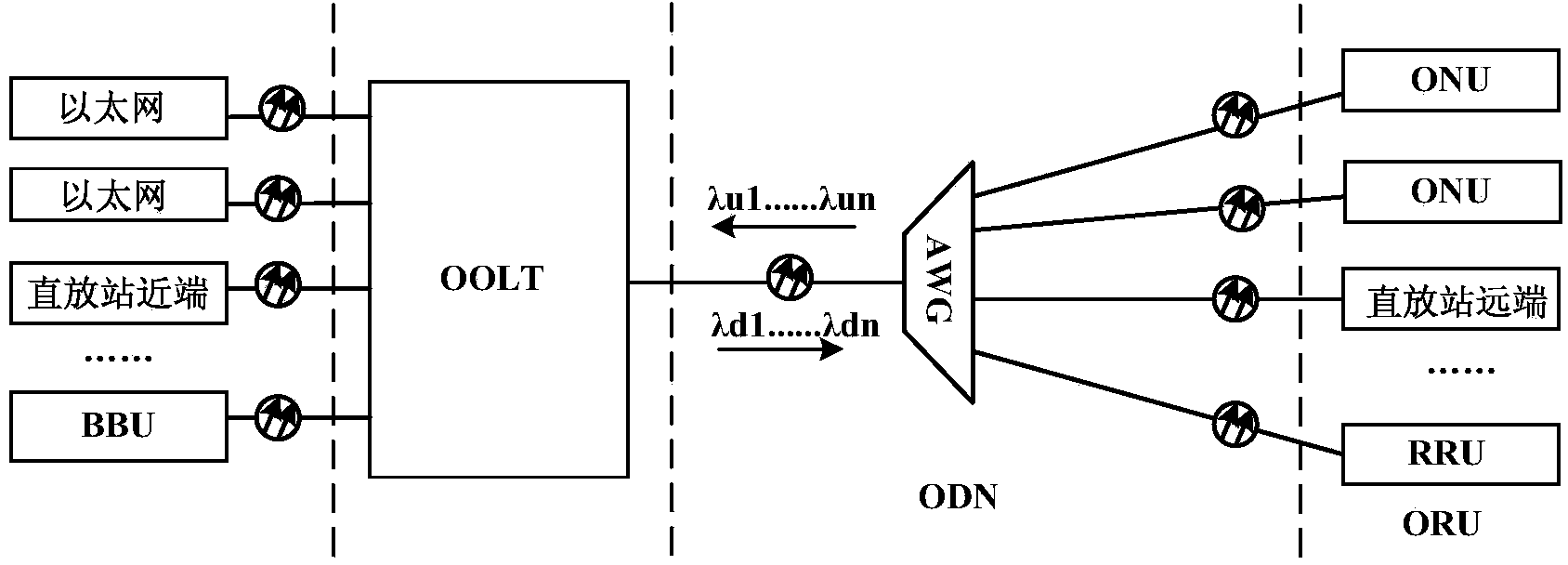
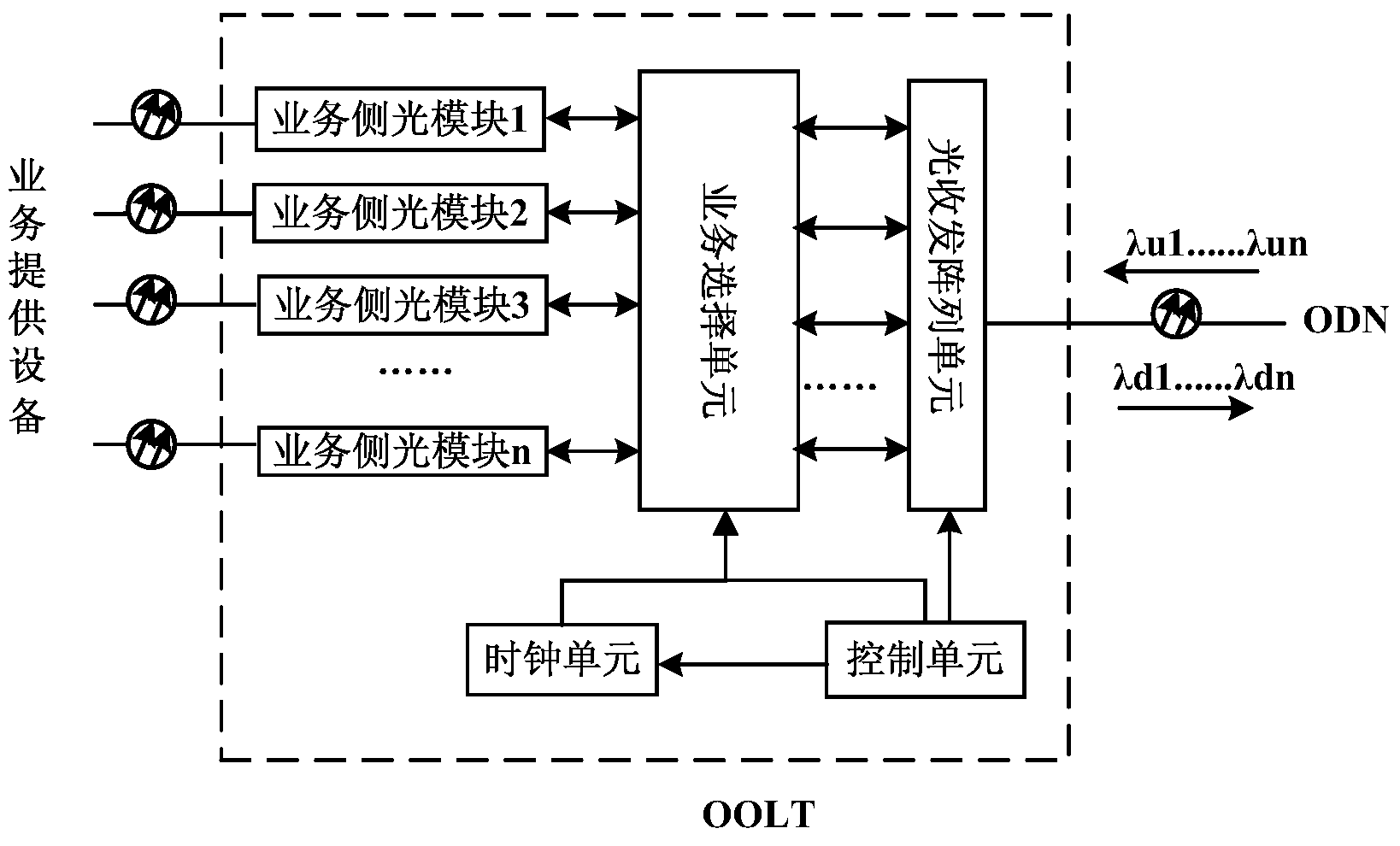
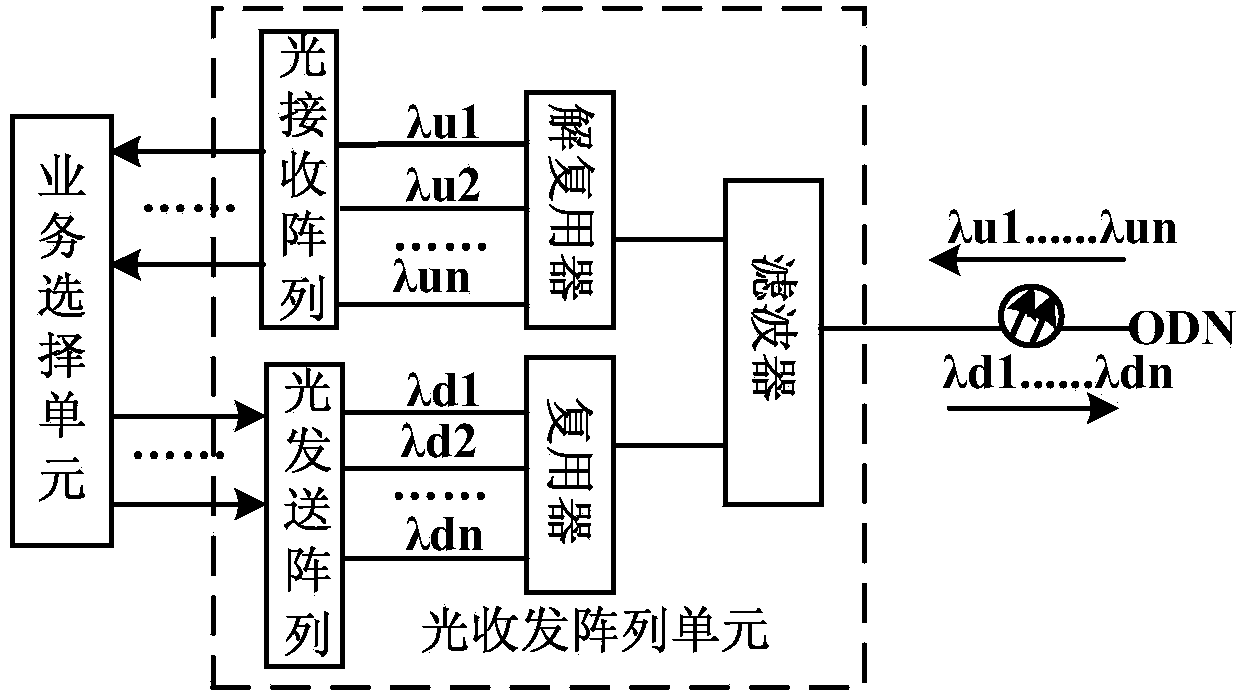
Open network architecture based on wavelength division PON system, and signal transmission method
ActiveCN104023282AImprove resource utilizationIncrease opennessMultiplex system selection arrangementsWavelength-division multiplex systemsOptical ModuleNetwork architecture
The invention discloses an open network architecture based on a wavelength division PON system, and a signal transmission method, and relates to the field of a PON optical access technology. The network architecture comprises a control unit, a service selection unit, an optical transceiving array unit, a clock unit and a plurality of service side optical modules. The control unit is respectively connected with the service selection unit, the optical transceiving array unit and the clock unit; each service side optical module is connected with a service provider device; the service selection unit is provided with a plurality of service data channels; each service side optical module is connected with the optical transceiving array unit through the data channels corresponding to services; and the optical transceiving array unit is connected with the optical modules of all ORU devices through an AWG. According to the invention, multiple different services can be accessed to the same optical access basic facility in an integrated mode, uplink and downlink signal transmission of multiple different services can be finished; and the service access capability is quite high, the application scope is quite wide, resources can be shared, and the application cost is quite low.
Owner:FENGHUO COMM SCI & TECH CO LTD
Method for implementing an Open Charging (OC) middleware platform and gateway system
InactiveUS7801171B2Lessen IN platform 's network impactEasy to chargeAccounting/billing servicesUnauthorised/fraudulent call preventionThird partyMiddleware
The art of present discloses a method and system for enabling mobile network operators to collect charging information from various other network elements; and indeed, is intended to exploit the resiliency of open network architecture and lessen the requisite dependency on proprietary network elements services and billing systems. The Open Charging (OC) middleware platform and gateway system interacts with proprietary network elements and effectually creates a unifying, enabling layer in mobile networks. Indeed, the art is directed at permitting mobile subscriber access to, among others, third party content and services with the simplicity and convenience of such charges appearing on either mobile phone bill, or decremented from said mobile subscriber's pre-paid account.
Owner:REDKNEE INC
Extensible data center network architecture and implementation method
ActiveCN103327095AFirmly connectedImprove scalabilityTransmissionData center network architecturesExtensibility
The invention discloses an extensible data center network architecture. An optical exchanger is adopted to replace a traditional electric exchanger. A machine frame (6), a ToR exchanger (5), a polymerization exchanger (4), a core exchanger (3) and a content exchanger (2) inside a data center are respectively grouped into different assemblies, then the assemblies are placed on a group of adjacent nodes in a backbone network in a remote and distributed mode, the data among the assemblies are switched and transmitted through optical fibers in the backbone networks, and therefore simplification of inside connection in the center of the data is effectively utilized and the extendibility of the data center network architecture is strengthened by means of a plurality of network infrastructures. The extensible data center network architecture further discloses an implementation method of the data center network architecture, grouping of the machine frame, determination of the number of the exchangers, placement of the assemblies, and solving problems of service routes are all summed up into an integral linear program, then a mathematical tool is utilized to carry out solving or the architecture is designed according to a heuristic algorithm, the design is flexible, and adaptability is strong.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
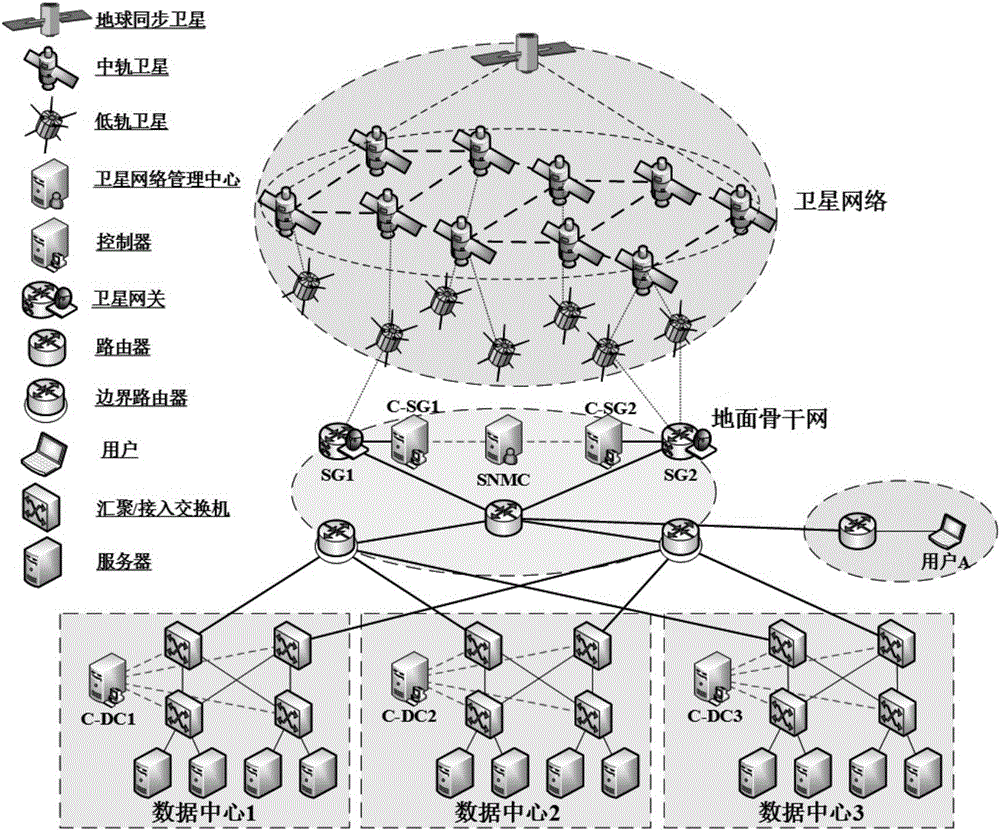
Core-based satellite network architecture
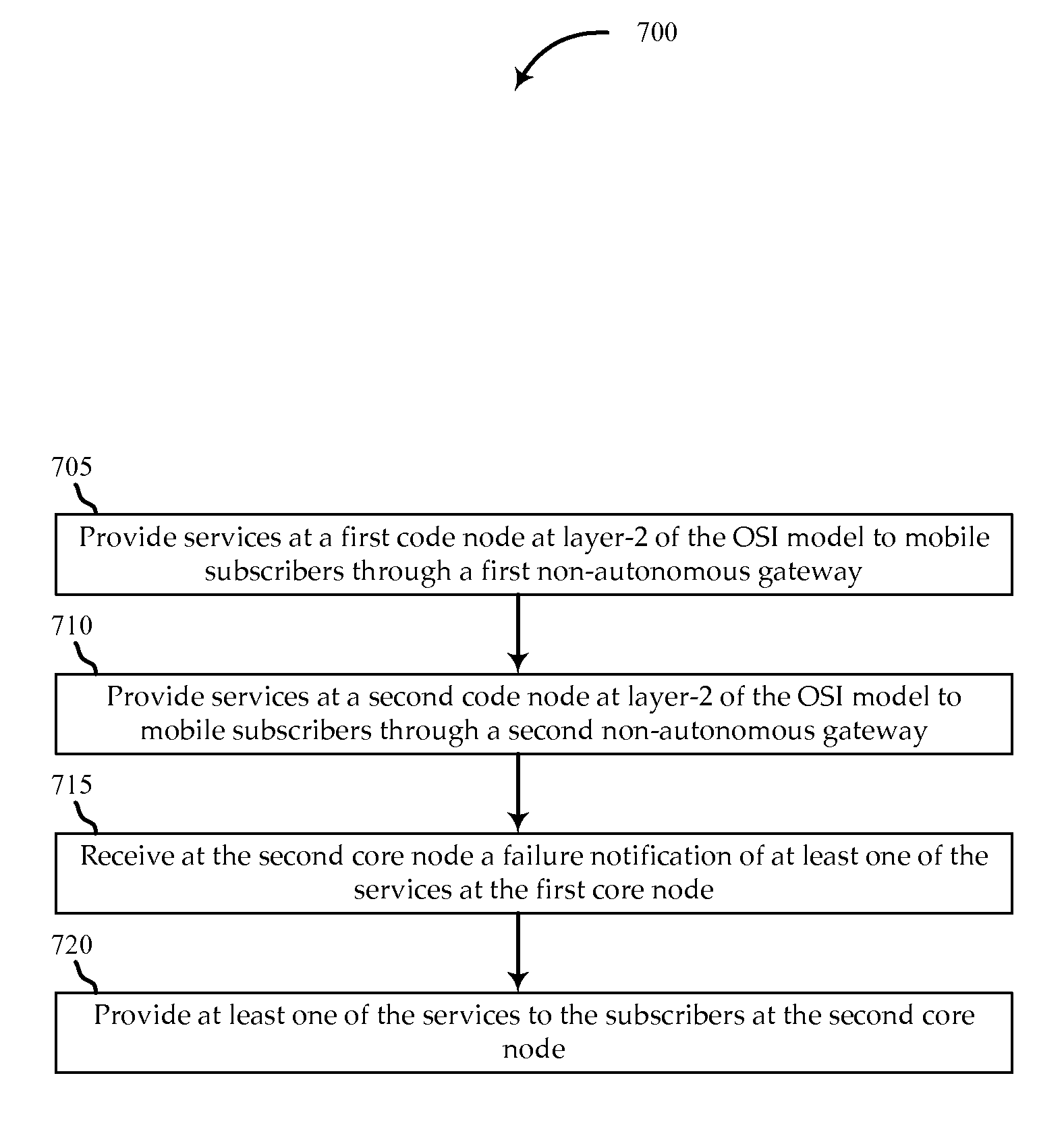
Systems and methods for implementing a satellite network, are described. The system includes satellite gateways in communication with subscribers over a satellite communication network. The satellite gateways send network communications to the subscribers and receive network communications from the subscribers. The system further includes a first core node in communication with at least one of the satellite gateways. The first core node provides networking services, at L2, to a first subset of subscribers. The system further includes a second core node in communication, at L2, with one of the satellite gateways and the first core node. The second core node provides the networking services, at layer-2 of the OSI model, to a second subset of the subscribers. In response to failure of at least one of the networking services in the first core node, the second core node providing the at least one of the services to the first subset of the subscribers.
Owner:VIASAT INC
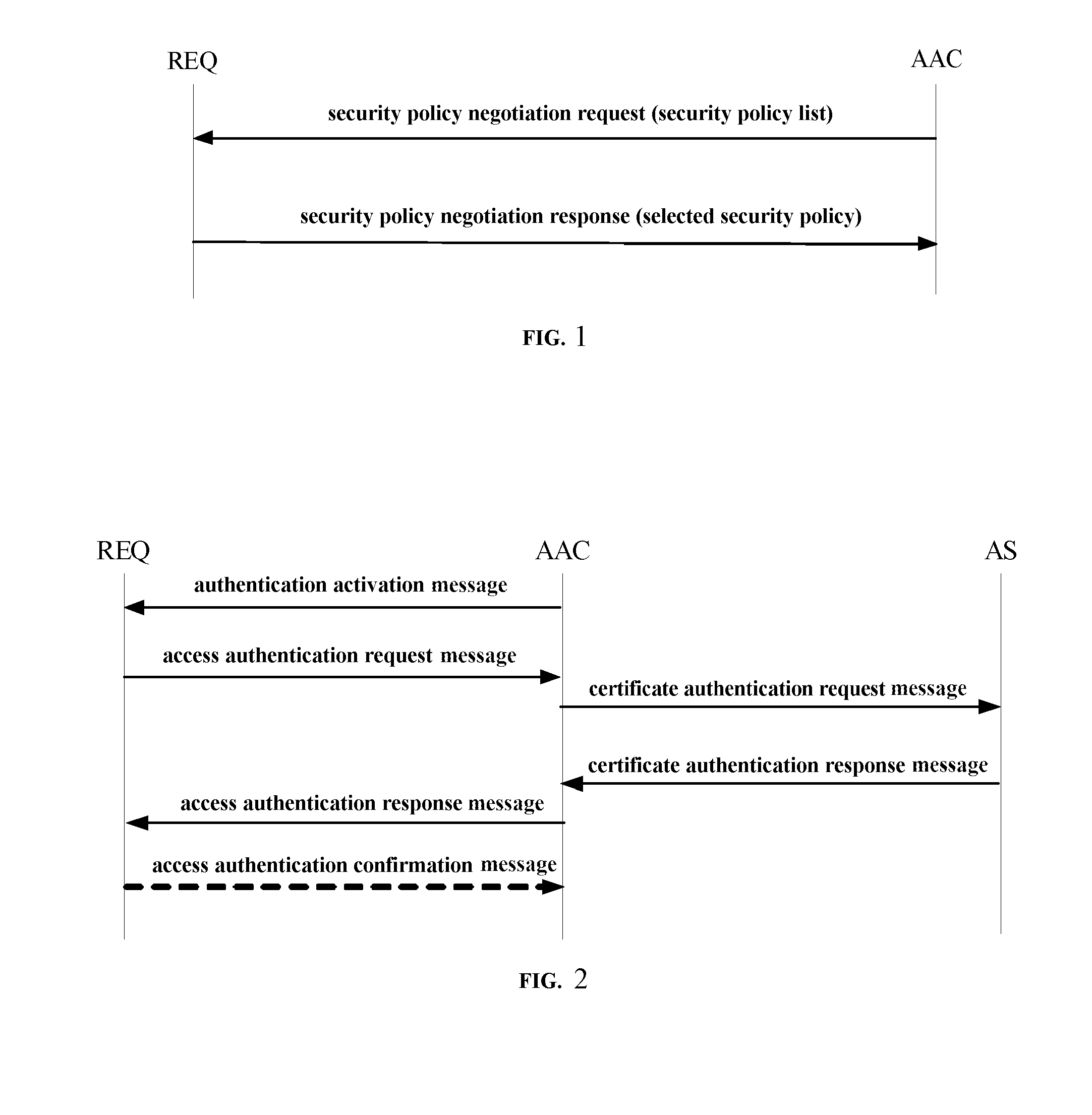
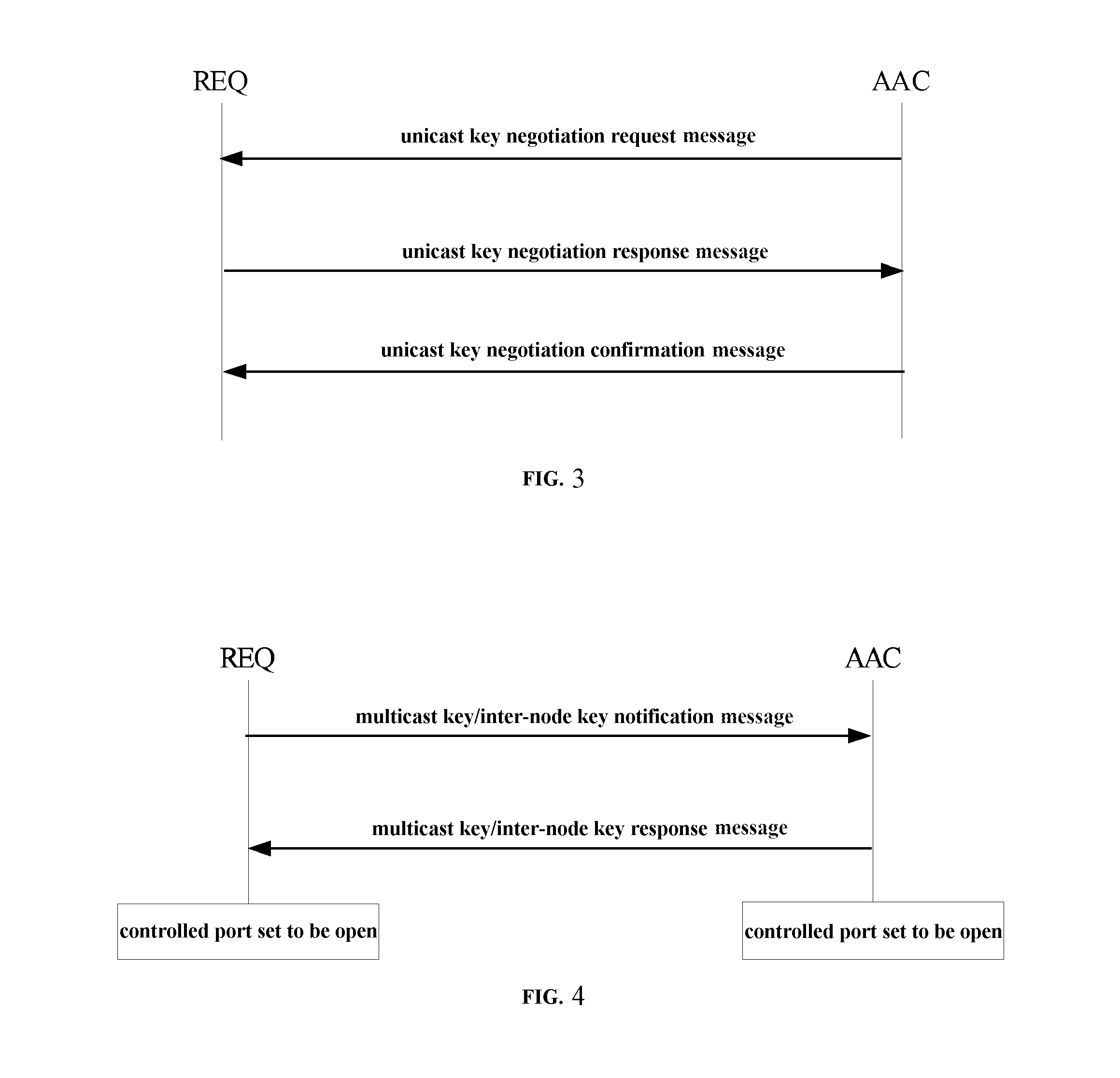
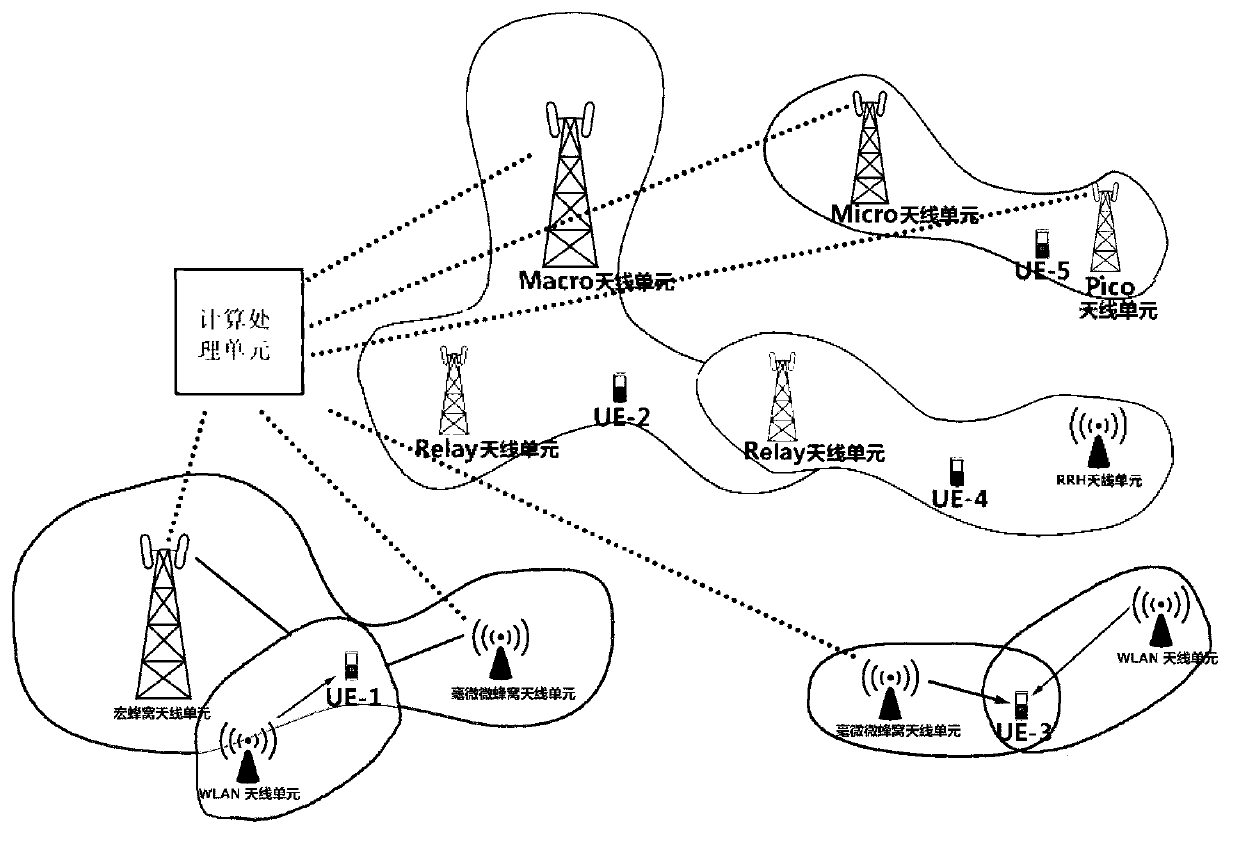
Security access control method and system for wired local area network
ActiveUS20120151554A1Improve good performanceAvoid difficult choicesKey distribution for secure communicationUser identity/authority verificationNetwork architectureControl equipment
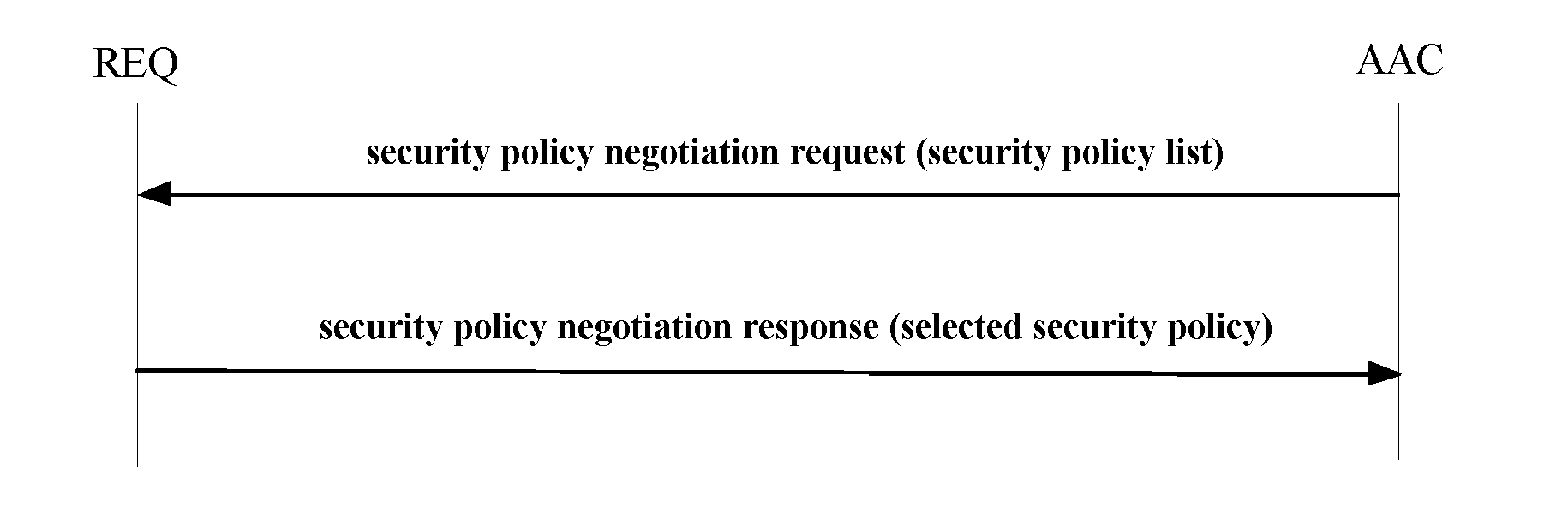
The present invention relates to a security access control method and system for wired local area network, the method includes the following steps: 1) a requester (REQ) negotiates the security policy with an authentication access controller (AAC); 2) the requester (REQ) and the authentication access controller (AAC) authenticate the identity; 3) the requester (REQ) negotiates the key with the authentication access controller (AAC). The direct identity authentication between the user and the network access control device is realized by the present invention; the negotiation and the dynamic update of the session key for the link layer data protection are realized; a variety of network architectures such as the enterprise network, the telecommunication network are supported; the scalability is good, the multiple authentication methods are supported; the authentication protocols with different security levels are supported, the requirements of the various subscribers are satisfied; the sub-modules of the protocol are independent, flexible, and easy to be accepted or rejected.
Owner:CHINA IWNCOMM
Communication system based on frameless network architecture and networking method
ActiveCN103108331ARealize mutual conversionSuppress interferenceNetwork planningNetwork architectureMobility management
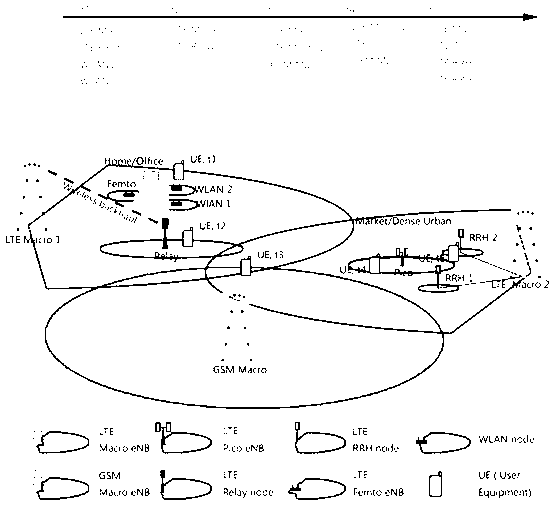
The invention relates to the technical field of wireless communication, in particular to a communication system based on a frameless network architecture and a networking method. According to the communication system based on the frameless network architecture and the networking method, a user-centered service set formed by antenna elements is constructed through new resource dimensionalities, namely the antenna elements and calculating and processing elements, and wireless resource management, mobile management, service unloading management, extensive coordination management between the antenna elements of different types and the like are carried out according to the service set. A traditional community setting and regional dividing mode is eliminated by the communication system based on the frameless network architecture and the networking method, then requirements of user terminals are taken as the center, and users have a dominant right of resource allocation. The wireless network networking problem when a large number of base stations of different kinds coexist and are intensively allocated is solved. Therefore, powerful technical support to the development of mobile wireless communication technique is supplied by the communication system based on the frameless network architecture and the networking method.
Owner:BEIJING UNIV OF POSTS & TELECOMM
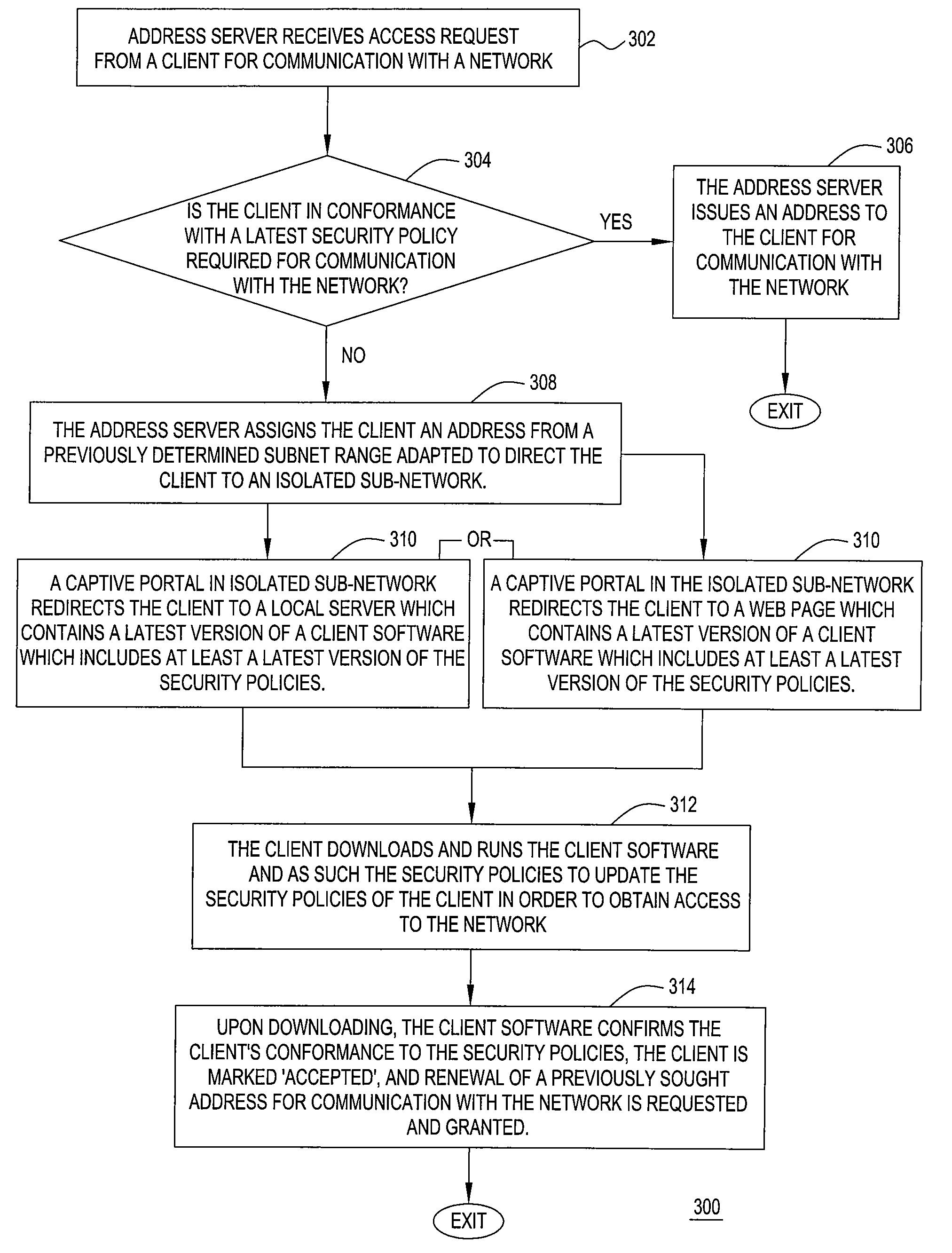
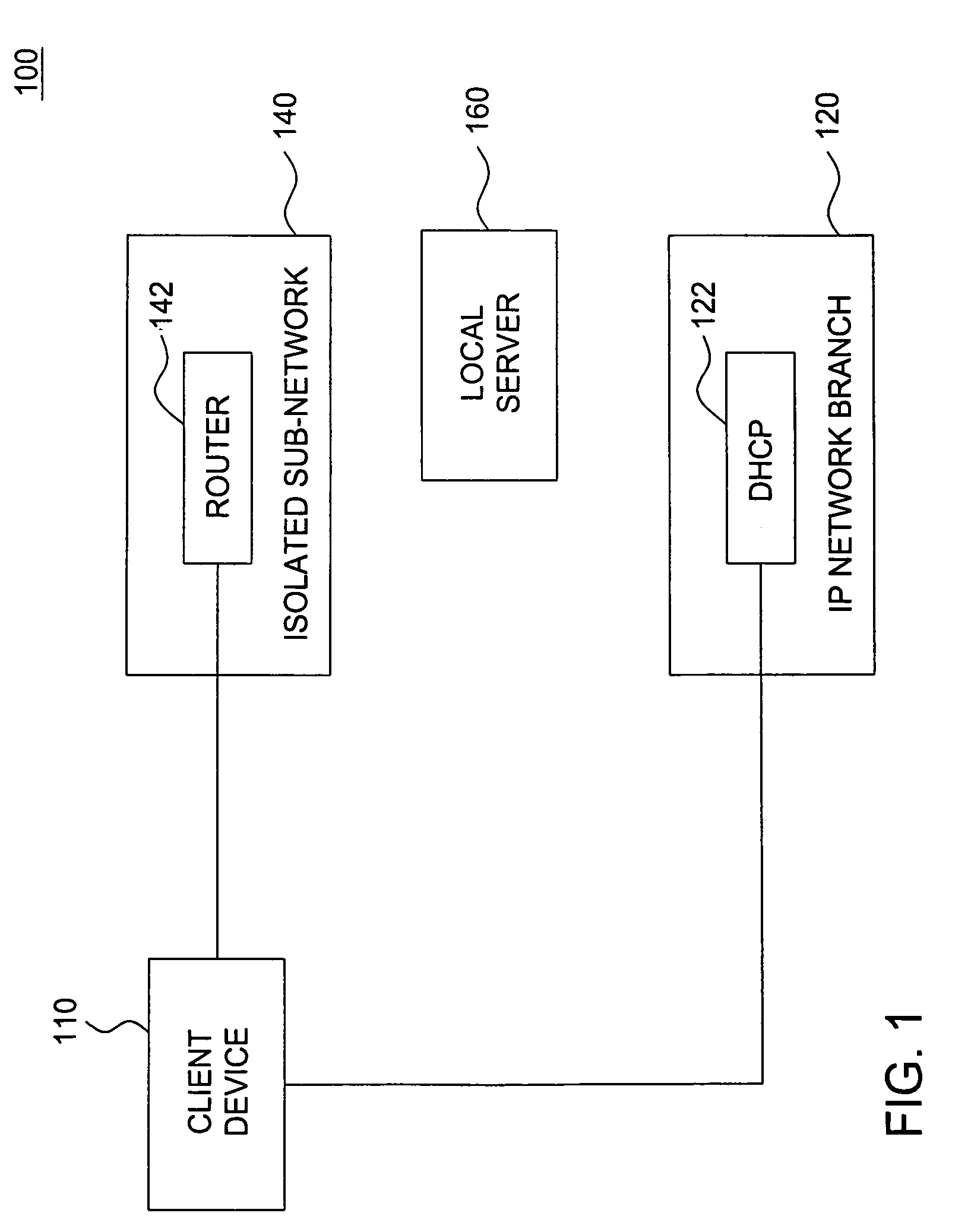
Method, apparatus and network architecture for enforcing security policies using an isolated subnet
ActiveUS7877786B2Digital data processing detailsMultiple digital computer combinationsWeb siteNetwork architecture
A method for enforcing security policies required to gain access to a network includes determining if a client desiring a connection to the network is in conformance with a current version of the security policies, and if a client is not in conformance with a current version of the security policies, denying the client access to the network and directing the client to an isolated sub-network for accessing a current version of the security policies. In one embodiment of the present invention an address server isolates non-conforming clients from the network and the network resources by directing non-conforming clients to an isolated sub-network. The isolated sub-network further directs the non-conforming clients to, for example, a local server or web-site for accessing a current version of the security policies.
Owner:PROVEN NETWORKS LLC +1
Multi-user access selection method under centralized network architecture
ActiveCN105722190AReduce processing overheadImprove timelinessAssess restrictionMacro base stationsNetwork architecture
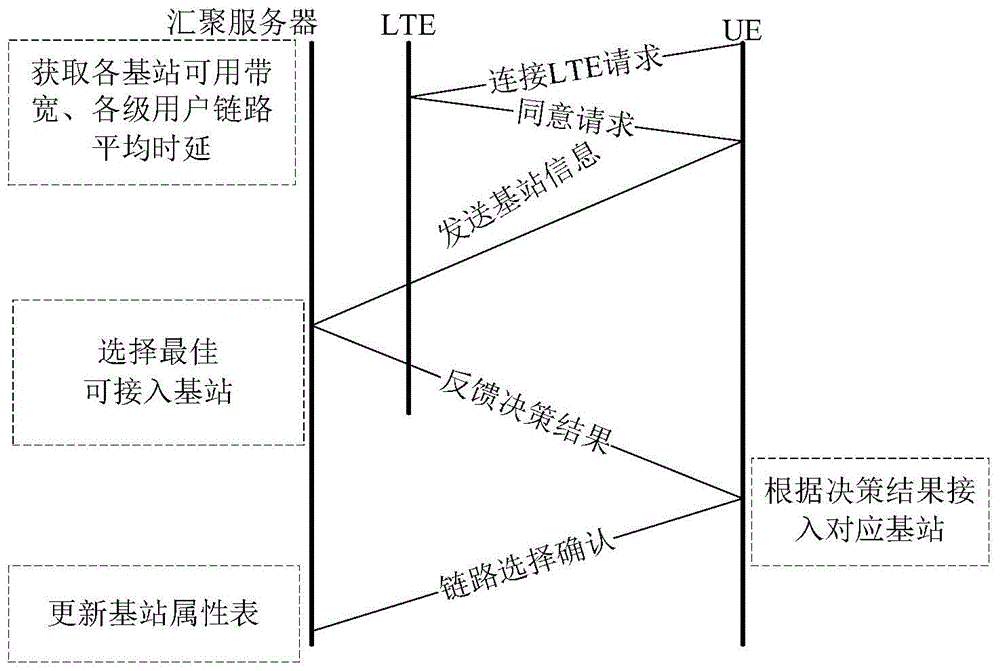
The invention discloses a multi-use access selection method under centralized network architecture. The method comprises that (1), when users enter into cells for the first time, a user terminal automatically connects with macro base station links; the user terminal synchronously receives signal strengths of periphery base stations, base station ID information and base station type information; (2), the signal strengths of the base stations, the ID information corresponding to the base stations, base station type information and user Qos demand signs are sent to a convergence server through the macro base station links; (3), the convergence server evaluates and marks networks available for access according to the signal strength, available bandwidth, same-level user link delay of each base station, and selects the base stations corresponding to the networks with the highest marks as the proposed access base stations of the user terminal; and (4), the users access corresponding base stations according to selection results. According to the user access selection method provided by the invention, the Qos demands of different users can be satisfied well; the problem that the latter user squeezes the bandwidth of the former user is solved; and the load balance degrees of the homogeneous base stations are improved.
Owner:HUAZHONG UNIV OF SCI & TECH
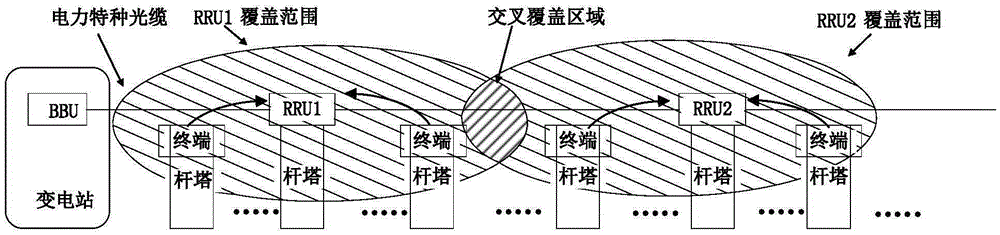
4G private network cell interference coordination method for electric power transmission scene
ActiveCN105391510AReduce distractionsImprove resource utilizationOrthogonal multiplexWireless communicationElectric power transmissionPrivate network
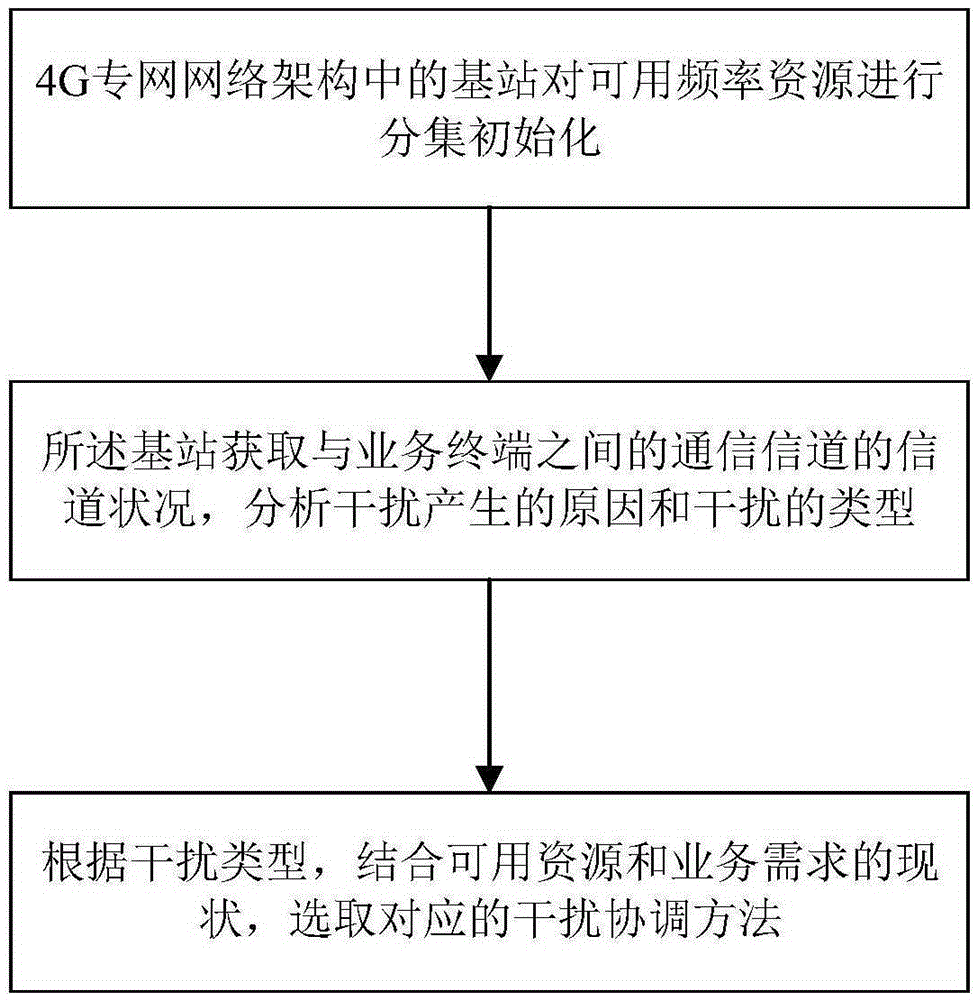
The invention provides a 4G private network cell interference coordination method for an electric power transmission scene. The 4G private network cell interference coordination method comprises the steps that: (1) a base station in a 4G private network architecture performs diversity initialization on available frequency resources; (2) the base station obtains channel conditions of communication channels between the base station and a service terminal, and analyzes causes and types of interference; (3) and a corresponding coordination method is selected according to the interference type through combining the available resources and service requirements. A frequency subset in the interference coordination method provided by the invention is partitioned by adopting a dynamic partitioning method, the frequency utilization rate is improved, and the communication channel quality is ensured.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Multichannel transmission 5G network architecture based on SDN and data transmission method
ActiveCN107277858AIncrease data transfer rateAlleviate data traffic pressureNetwork traffic/resource managementConnection managementNetwork architectureG-network
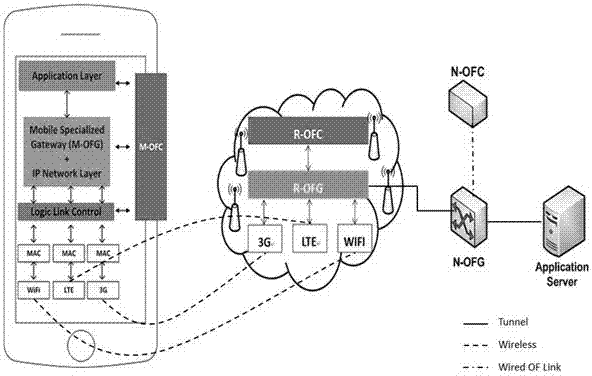
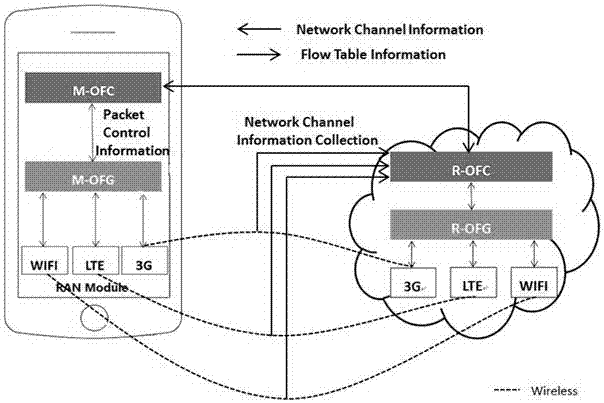
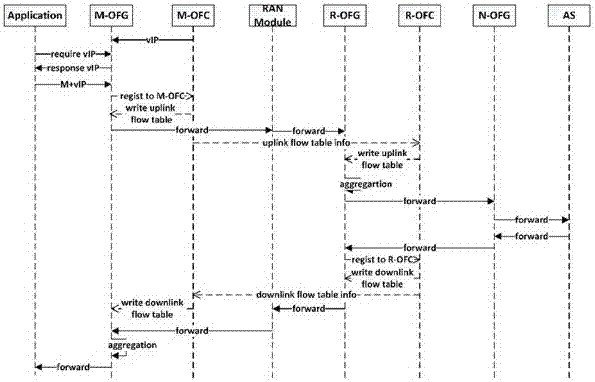
The invention relates to a multichannel transmission 5G network architecture based on SDN. The 5G network architecture comprises a mobile device, a wireless access network (RAN) device and a core network, the mobile device is provided with an OpenFlow controller (M-OFC) and an OpenFlow gateway (M-OFG); the wireless access network device (RAN) is defined with an OpenFlow controller (R-OFC) and an OpenFlow gateway (R-OFG); the core network is defined with an OpenFlow controller (N-OFC) and an OpenFlow gateway (N-OFG); and flow table information is shared on a sending side and a receiving side, so that the separation and combination of data packets are matched with each other, the data transmission rate of the 5G network is greatly improved, and the network architecture effectively relieves the data flow pressure of network bearer and improves the user experience in a mobile network environment.
Owner:XIDIAN UNIV
IP dynamically bound wireless network construction method and corresponding network architecture
ActiveCN106488525AAchieve sharingRealize the value of informatizationAssess restrictionNetwork topologiesTelecommunicationsNetwork architecture
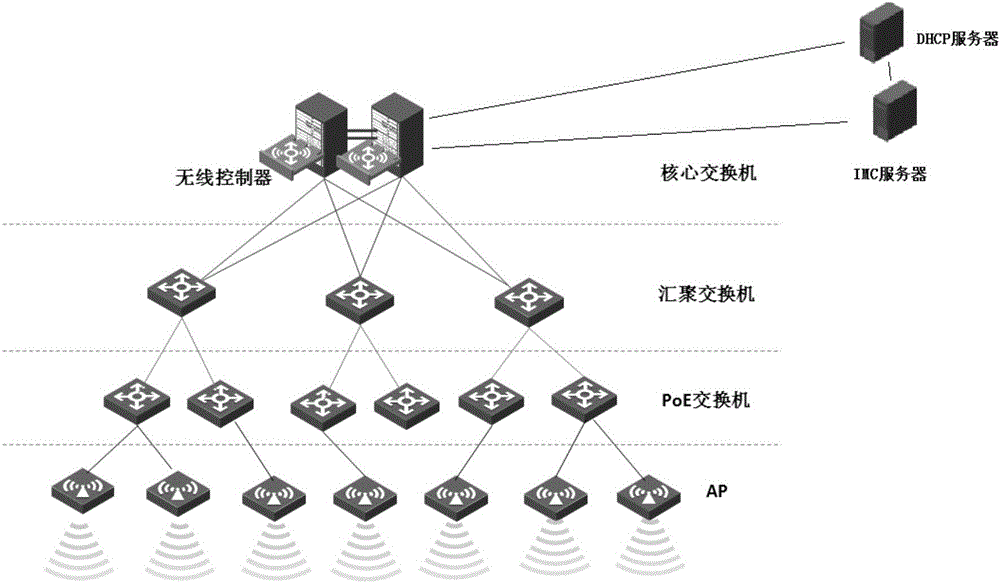
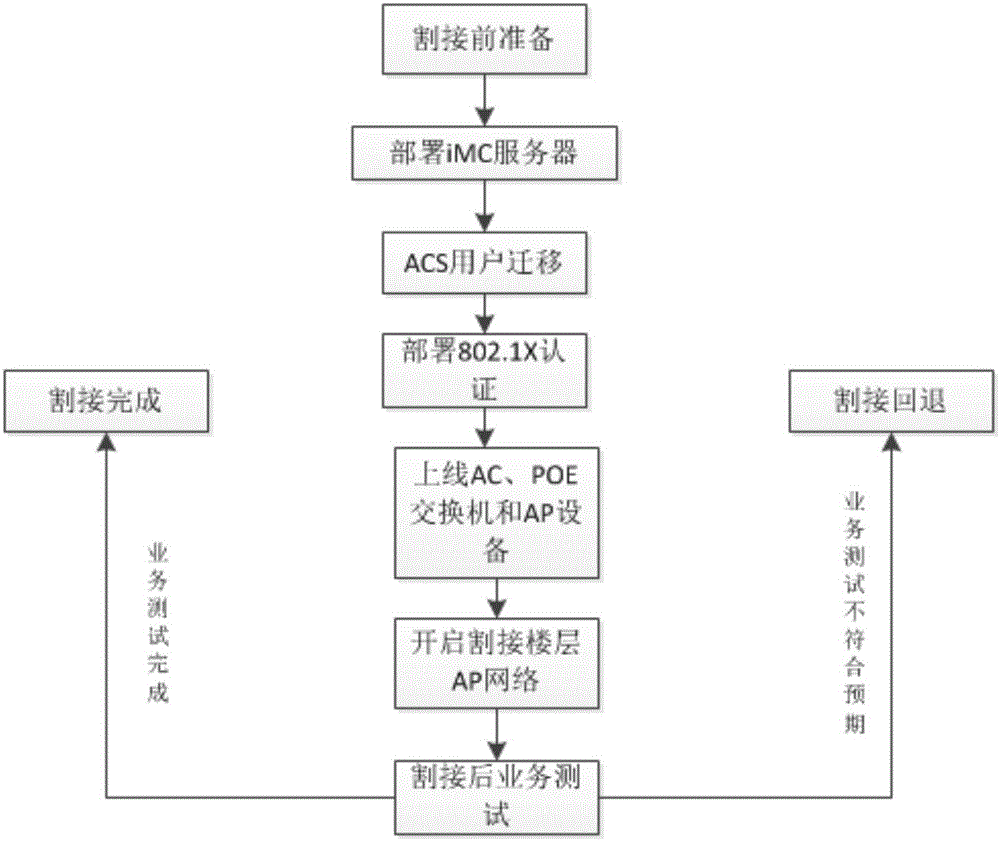
The invention discloses an IP dynamically bound wireless network construction method and a corresponding network architecture. The wireless network construction method of the invention deploys wireless access equipment AP at each target room, deploys POE power supply switches at various target floors, and converges the power supply switches to aggregation switches, wherein each aggregation switch is respectively connected to a core switch, and the core switch is provided with a wireless controller AC board card; an IMC server and a DHCP server are set up at an isolation area and fixed IP which is bound with an MAC is distributed for internal staff. After the network architecture of the invention is constructed, staff within a coverage area can use a notebook, a tablet compute (PAD), a smartphone and other mobile terminals with a wireless access function to access the network through a wireless network, and through a unified wireless channel, one person has one number can be ensured and in-building roaming can be achieved.
Owner:STATE GRID INFORMATION & TELECOMM BRANCH +1
Flexible indoor network architecture design and resource allocation method
InactiveCN107426037AImprove space reuse rateFlexible Design PatternsData switching networksNetwork architectureEnvironmental perception
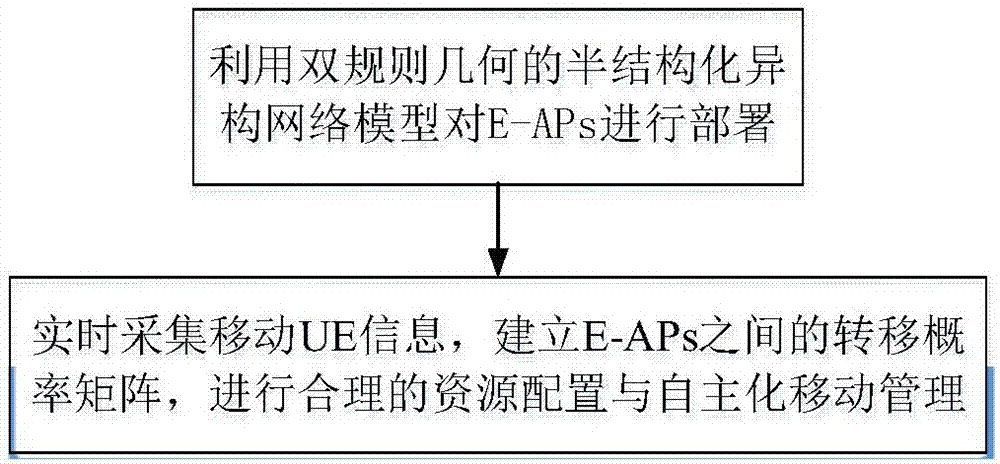
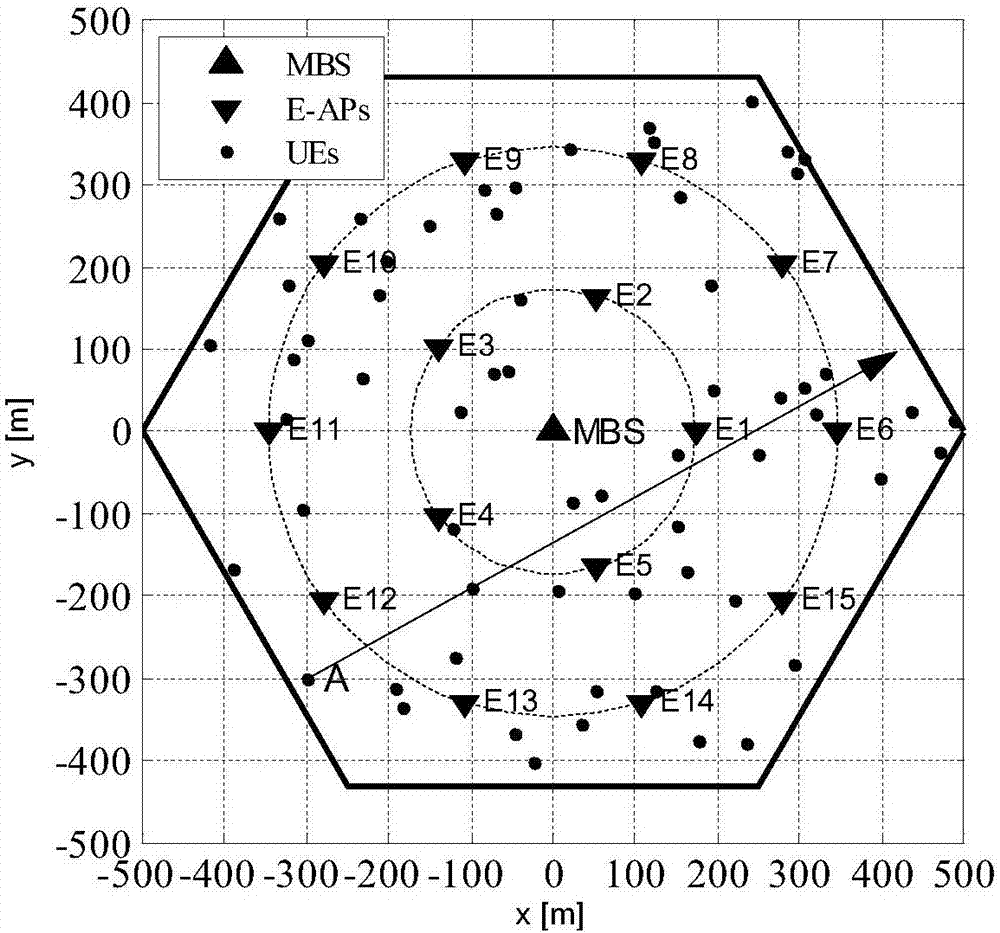
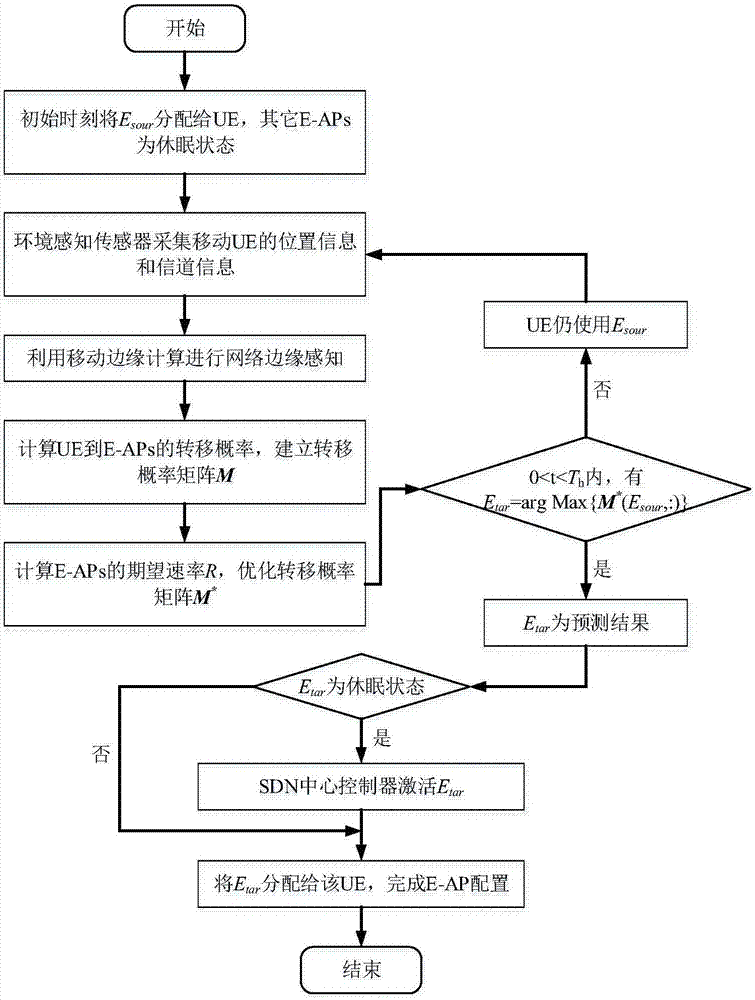
The invention discloses a flexible indoor network architecture design and a resource allocation method. According to the method, a large number of evolved access points (E-AP) (Evoluted Access Point) with low power consumption and low cost and adopting double-rule geometric distribution are introduced, the central idea of a software defined network SDN (Software Defined Network) is used for controlling the E-APs to realize indoor software defined extended network architecture. A reasonable resource configuration and automatic mobile management scheme suitable for the communication of a large number of indoor mobile devices is provided. In the scheme, the information of mobile UE (User Equipment) is collected by the combined use of the E-APs and an environmental perception sensor, the E-APs are configured in combination with an expected speed and a transition probability matrix, a higher speed at the moment is ensured, and the allocation of the E-APs at the next moment can be predicted in advance, thereby shortening the delay and realizing seamless connection. The method is a combination of communication and computing, which can guarantee a higher communication rate, better communication quality and more flexible network architecture.
Owner:NANJING UNIV OF POSTS & TELECOMM
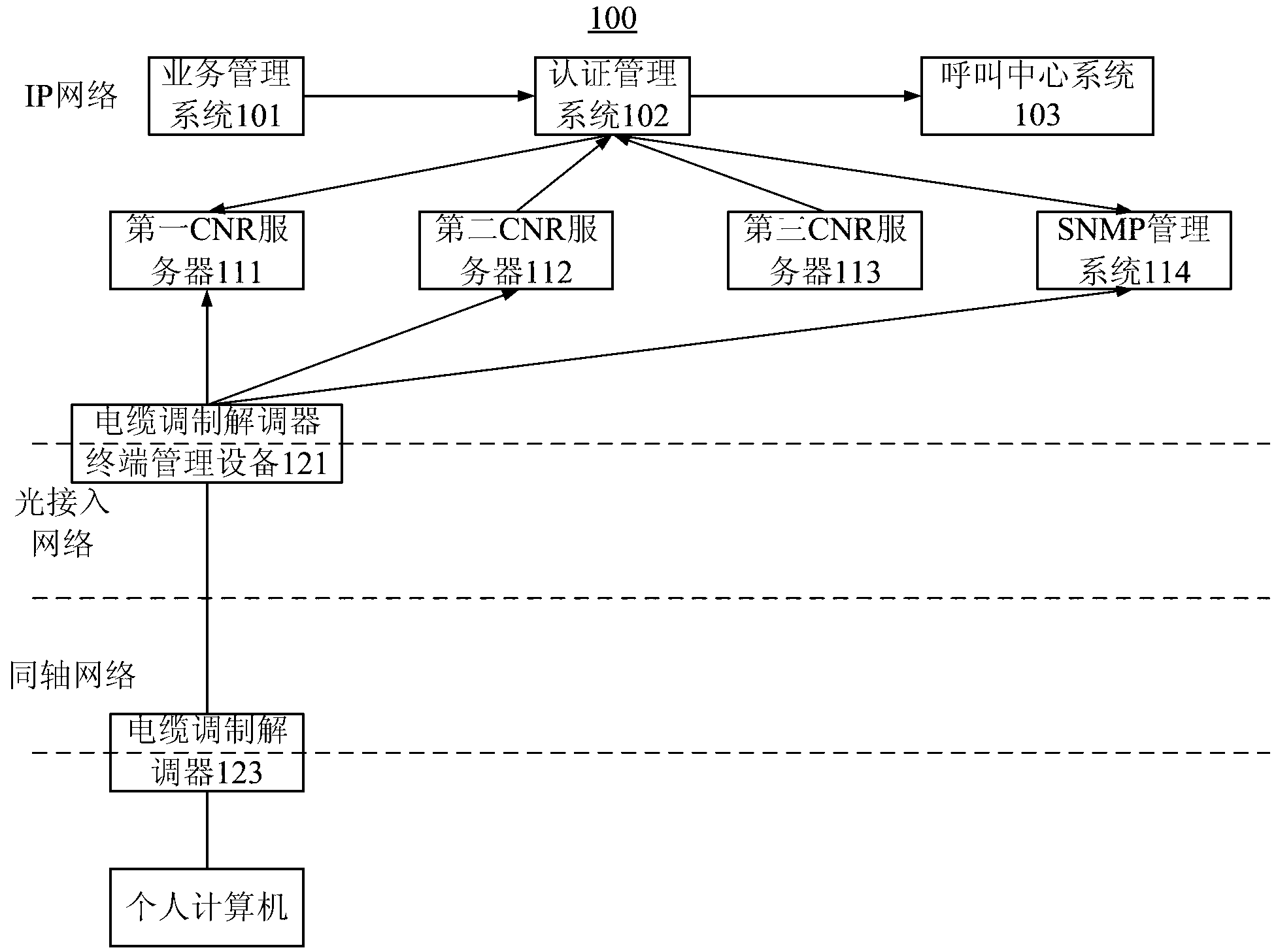
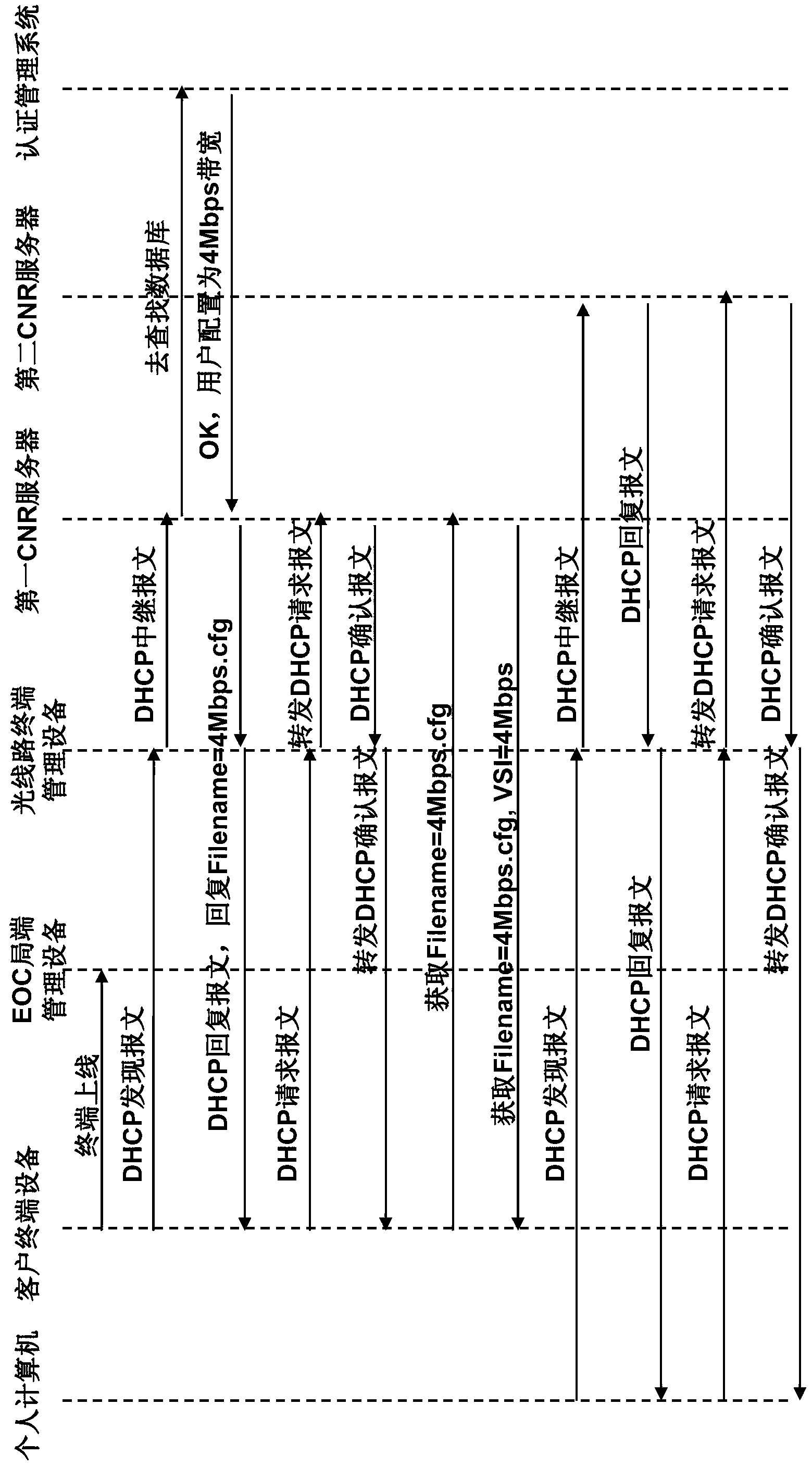
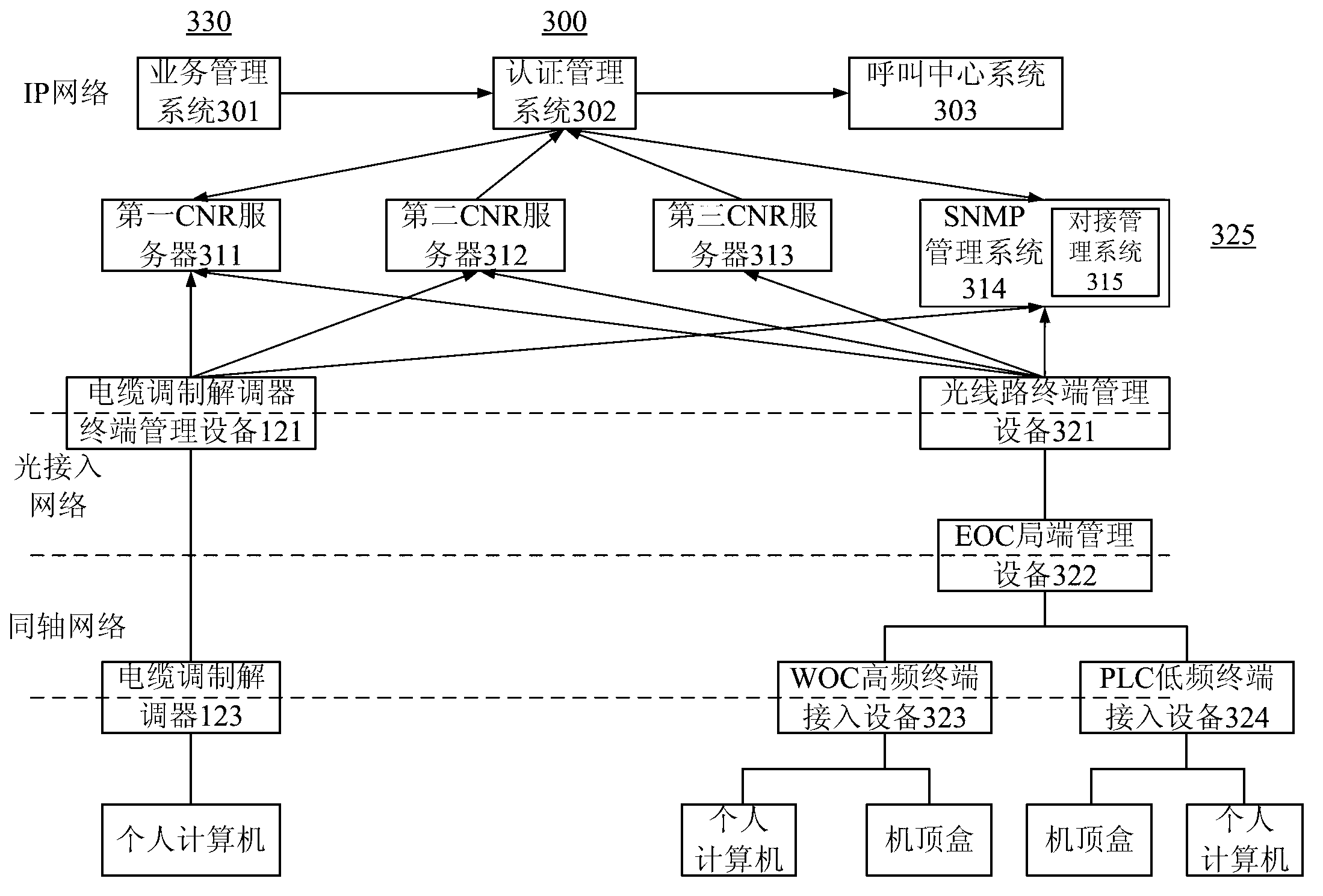
Next generation broadcasting network (NGB) access network architecture system and butt joint method of Ethernet over coax (EOC) network management system and business operation support system (BOSS)
ActiveCN103312696ASharing benefitsImprove stabilityData switching by path configurationBusiness managementBusiness operation support system
The invention provides a next generation broadcasting network (NGB) access network architecture system and a butt joint method of an Ethernet over coax (EOC) network management system and a business operation support system (BOSS). The NGB access network architecture system comprises a business management system, an authentication management system connected with the business management system, a call-center system connected with the authentication management system, three China national ratio (CNR) servers which are connected with the authentication management system and respective serve customer terminal equipments with the types of cable modems, personal computers and set top boxes, and a simple network management protocol (SNMP) management system which is connected with the authentication management system and used for carrying out SNMP configuration on the various customer terminal equipments; and the architecture system also comprises a butt joint management system used for taking part in the butt joint with the authentication management system so as to complete authentication, optical line terminal management equipment connected with all the CNR servers and the SNMP management system, EOC local side management equipment connected with the optical line terminal management equipment, and customer terminal access equipment connected with the EOC local side management equipment. The architecture system and the butt joint method enable all EOC access technologies to be suitable for the BOSS, thus reducing the butt joint cost and the technical risk, and reducing the access difficulty.
Owner:上海云视科技股份有限公司
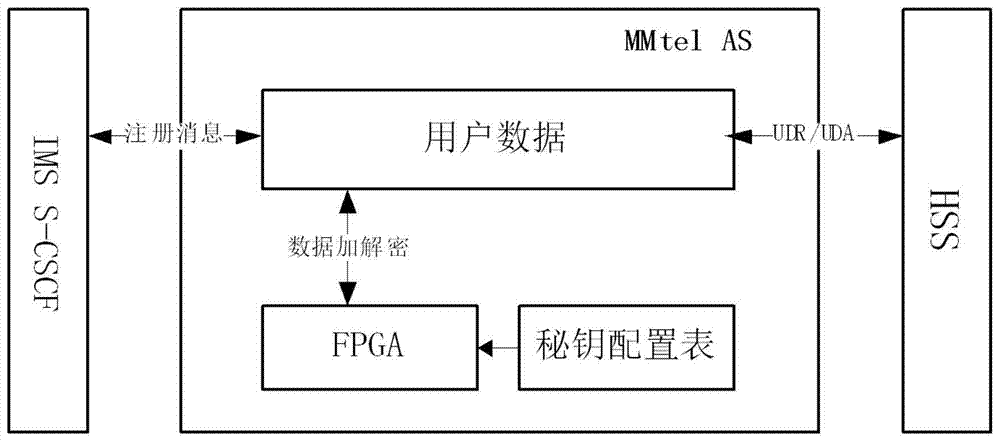
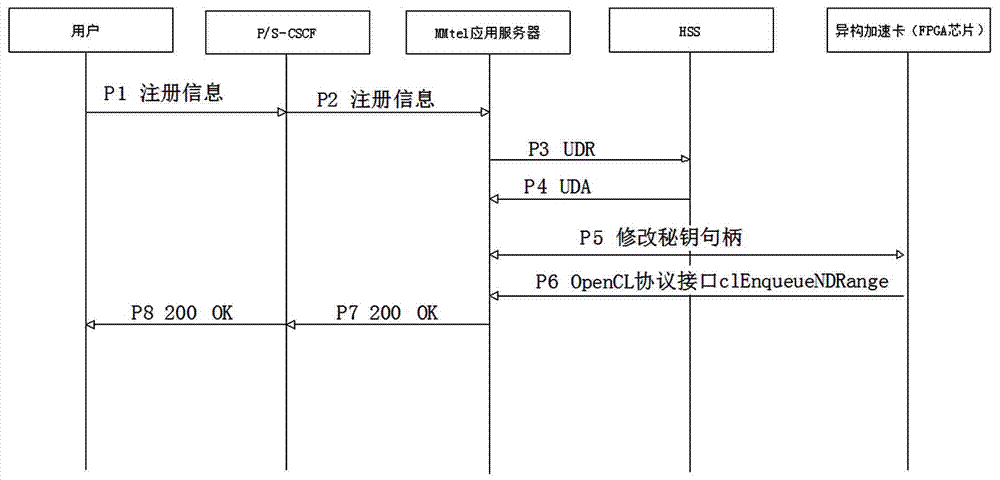
Key configurable system and method in MMtel (MultiMedia Telephony) application server
ActiveCN107172099AImprove reliabilityPracticalKey distribution for secure communicationSecurity arrangementSession controlStructure of Management Information
The invention discloses a key configurable system and method in an MMtel (MultiMedia Telephony) application server. The key configurable system is based on an IMS (IP Multimedia Subsystem) network architecture, and structurally comprises a home subscriber server (HSS), an MMtel application server and a serving-call session control function (S-CSCF) node which are sequentially connected, wherein the MMtel application server is internally configured with a heterogeneous acceleration card, and the heterogeneous acceleration card is used for performing encryption on registered user data in the IMS network architecture. Compared with the prior art, the key configurable system and method in the MMtel application server apply the heterogeneous acceleration card to the MMtel application server, a value range of a key handle is set in a background database on the MMtel, the flexible adaptability of generation of the key handle is ensured, and thus the randomness of generation of the key handle is guaranteed, thereby being high in practicability, wide in application range and easy to popularize.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
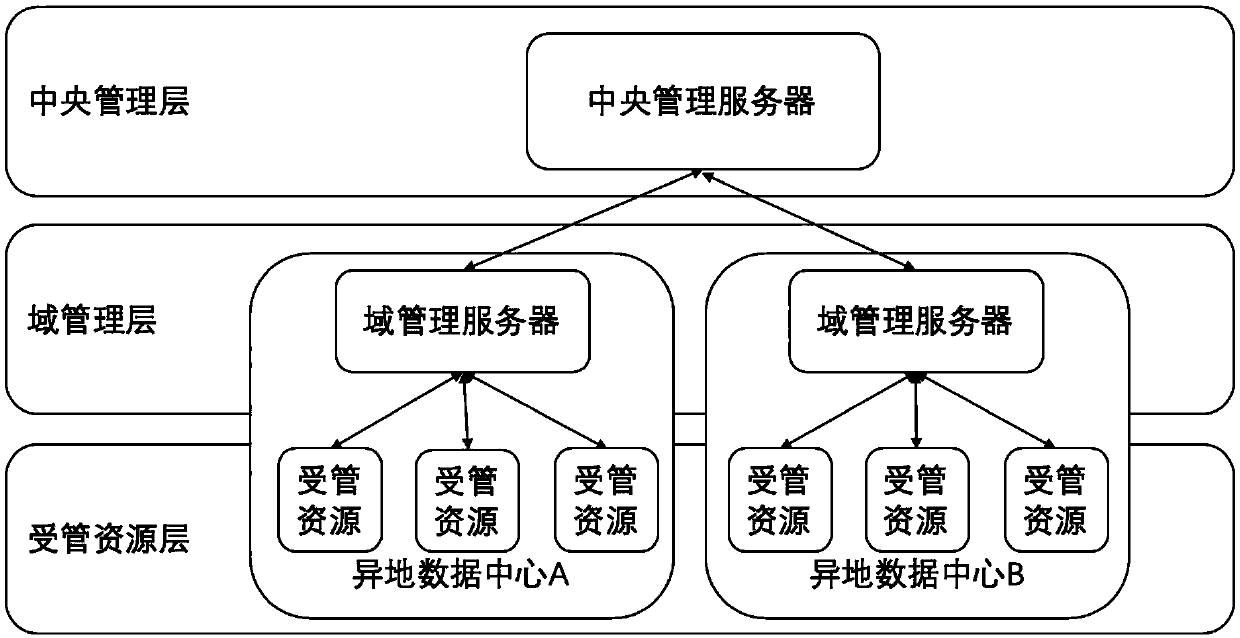
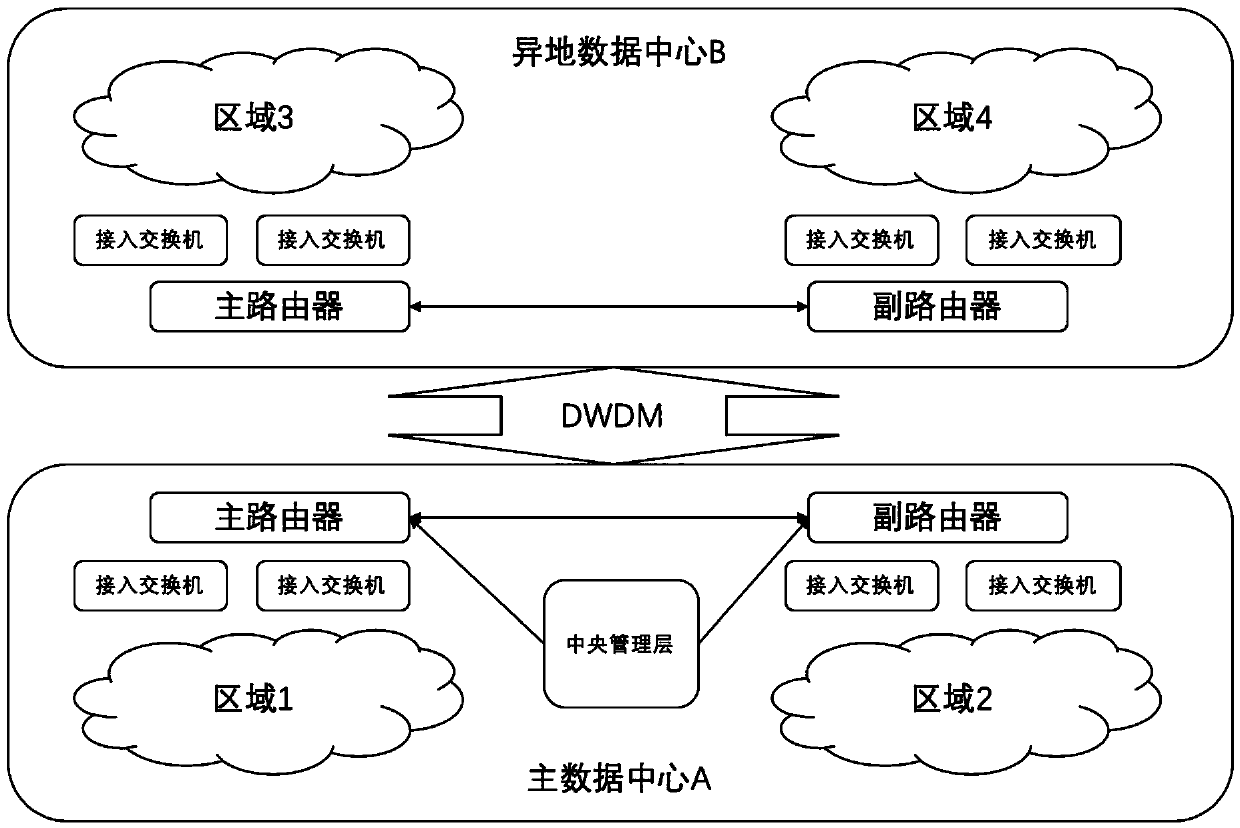
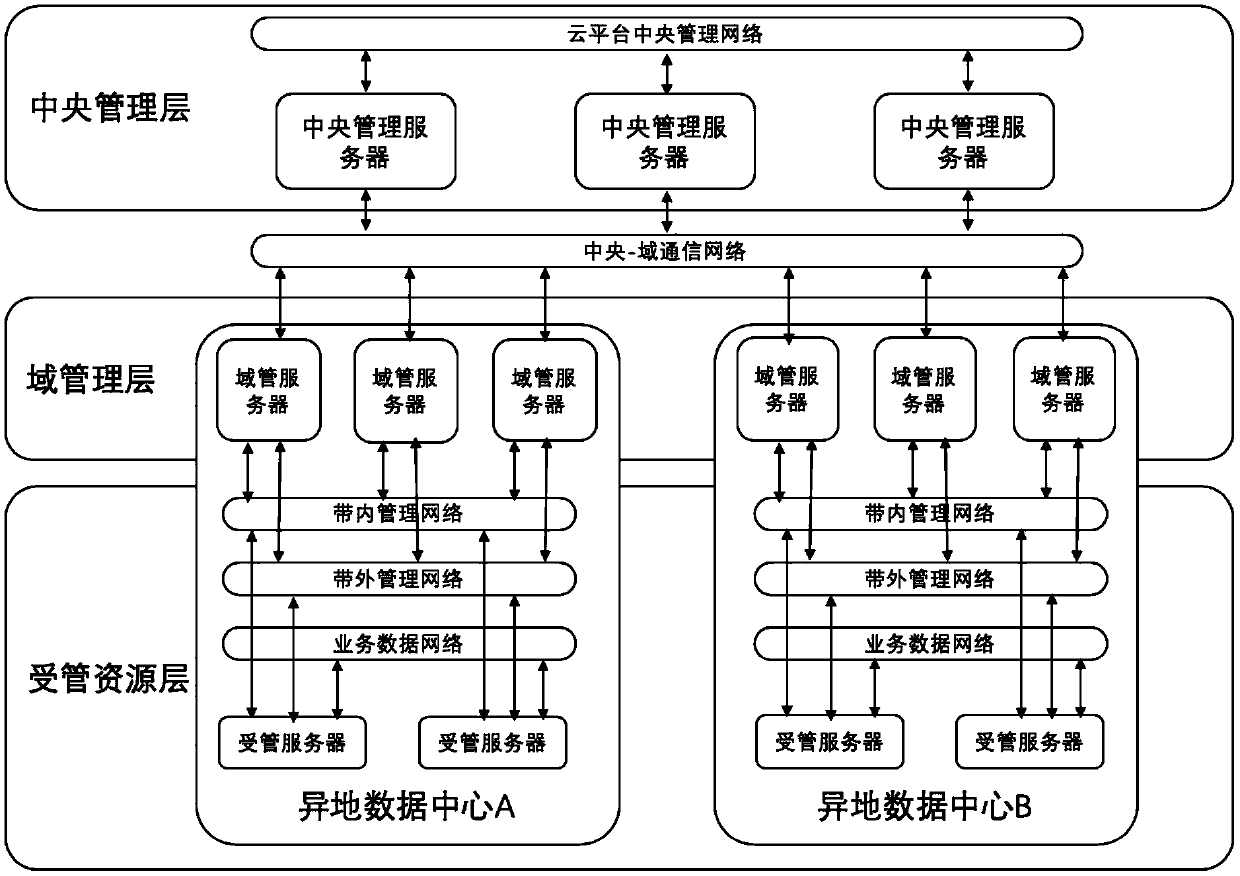
Remote-place cloud data center management system based on three-layer network architecture
ActiveCN109547239AReduce the number of channelsEnsure communication securityNetworks interconnectionNetwork architectureDirect communication
The invention discloses a remote-place cloud data center management system based on a three-layer network architecture. The system includes a central management layer, a domain management layer and amanaged resource layer. The central management layer deploys all function component modules, is responsible for global resource management and cloud service operation management, and contains variousfront-end realization functions of cloud data centers and data storage functions. The domain management layer realizes isolation on direct communication of the managed resource layer and the central management layer, and is used for playing a role of a connecting link between all the remote-place cloud data centers and the central management. The managed resource layer is basic architecture resources of each remote-place cloud data center, and includes managed servers, storage, a tape library, network equipment and a firewall. According to the management system disclosed by the invention, massive management traffic is carried at the domain management layer and the managed resource layer through a design of a three-layer model and the domain management layer, thus flow dividing of loads ofthe central management layer is carried out, and high scalability of multi-data-center large-scale cloud deployment is realized.
Owner:赵显涛 +1
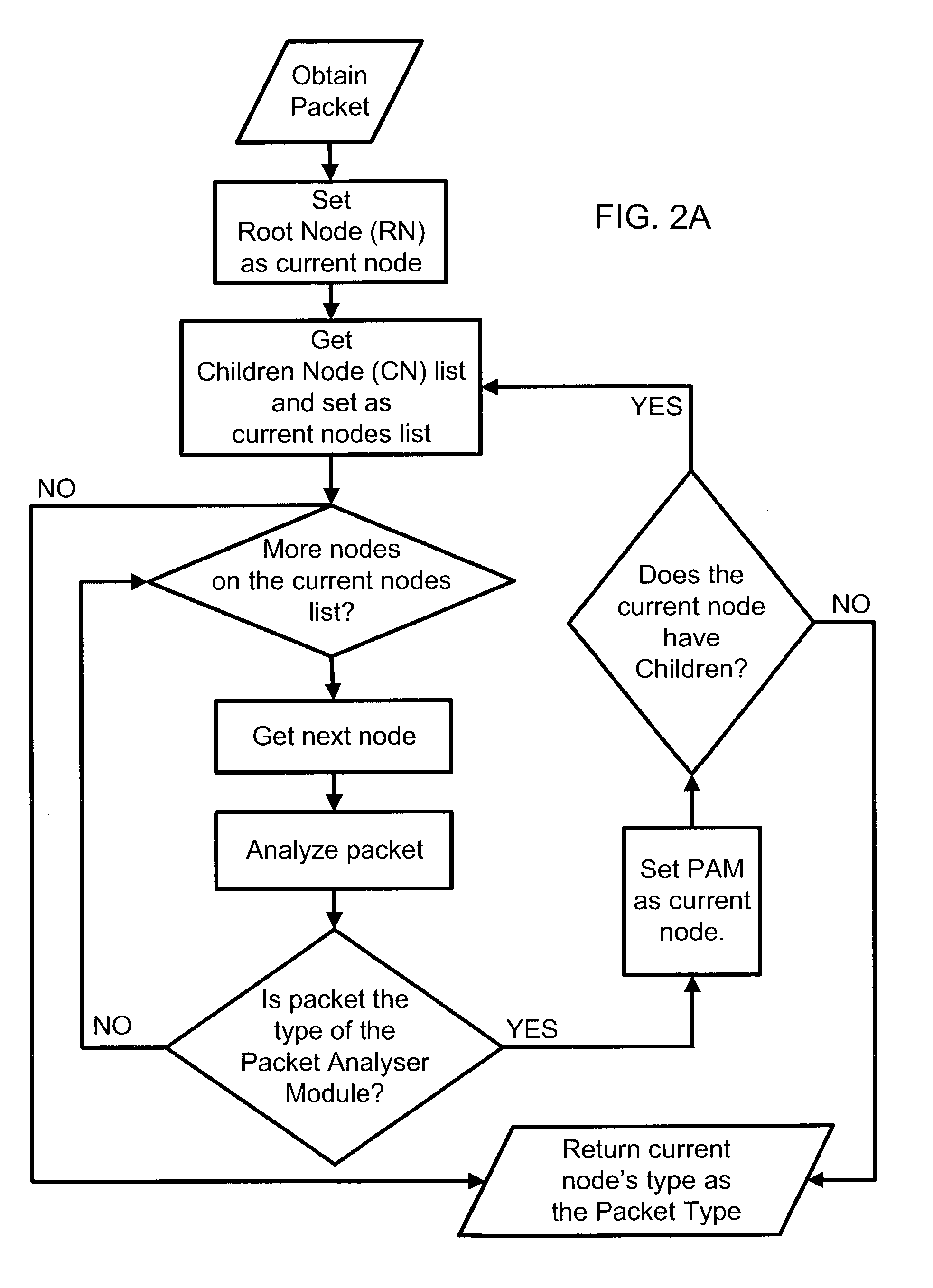
Method and apparatus for proprietary data forwarding in open architecture for network devices
A computer system for allowing proprietary forwarding elements to interoperate with standard control elements in an open network architecture. The computer system comprises a forwarding element that is adapted to perform data forwarding functions in a computer network. A control element is adapted to perform network signaling and control functions in the computer network. The control element is adapted to generate a standardized data set for configuring the forwarding element. An interconnecting element operatively connects the forwarding element to the control element. A forwarding element plugin is integrated with the control element for receiving the standardized data set from the control element, translating the standardized data set into a specialized data set, and transmitting the specialized data set to the forwarding element to configure the forwarding element. The forwarding element utilizes the specialized data set to configure the forwarding element for performing data forwarding in the computer network.
Owner:INTEL CORP
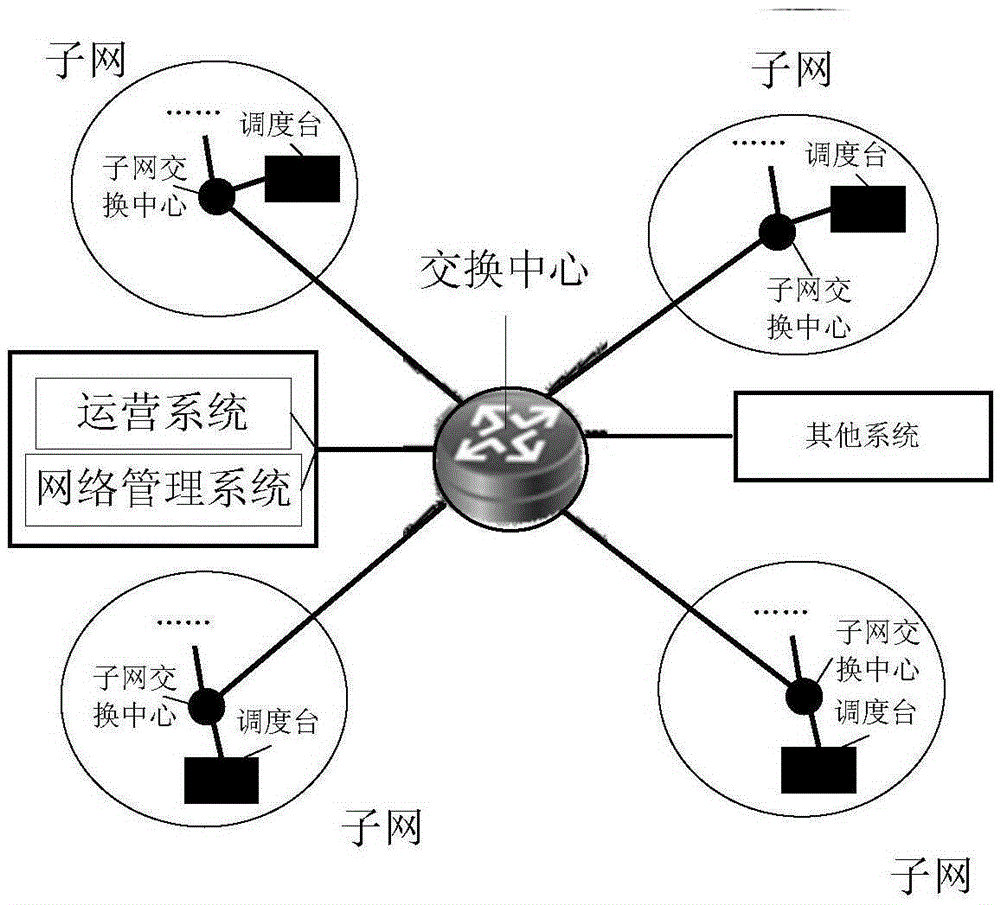
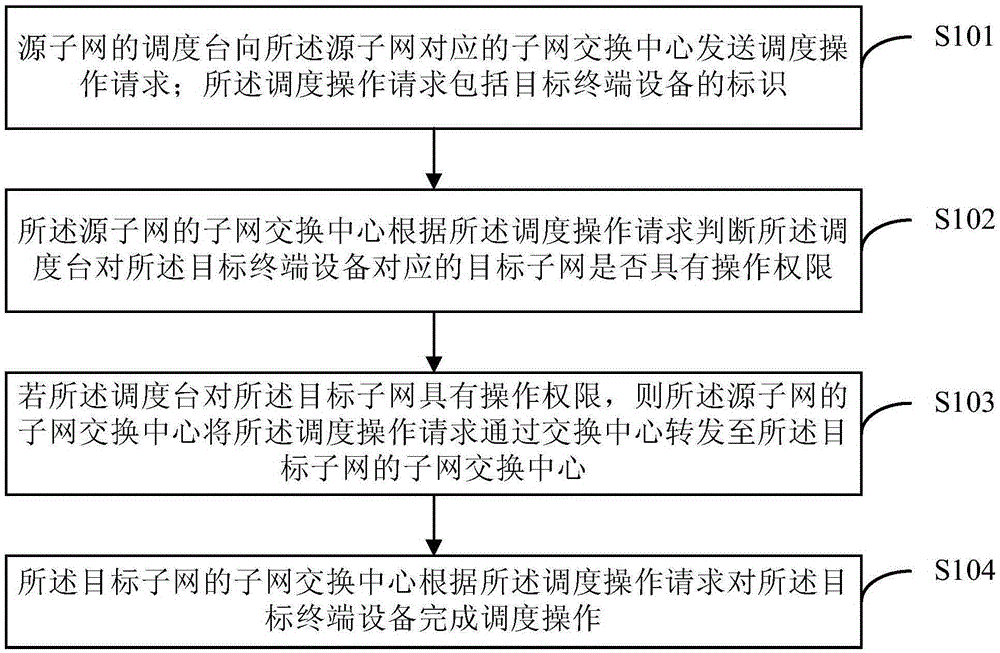
Distributed network architecture and dispatching method of distributed network architecture
The invention provides a distributed network architecture and a dispatching method of the distributed network architecture. The distributed network architecture comprises a switching center, at least one subnet, an operating system and a network management system; wherein each subnet, operating system and network management system are respectively connected with the switching center; each subnet comprises a subnet switching center and a dispatching station connected with the subnet switching center; the operating system is used for synchronizing the account data in the distributed network architecture to each subnet switching center; the network management system is used for managing the network parameters of the switching center, the subnet switching center of each subnet and the dispatching station of each subnet; the subnet switching centers in each subnet are used for routing and switching services within the subnet; service interworking between the subnets can be realized through the switching centers; and the dispatching station of each subnet is used for managing the terminal equipments in the subnets, and the management scope and the upper and lower level relationship of the dispatching stations can be adjusted according to the need of management, therefore, the delay caused by the network deployment can be reduced.
Owner:CHENGDU TD TECH LTD
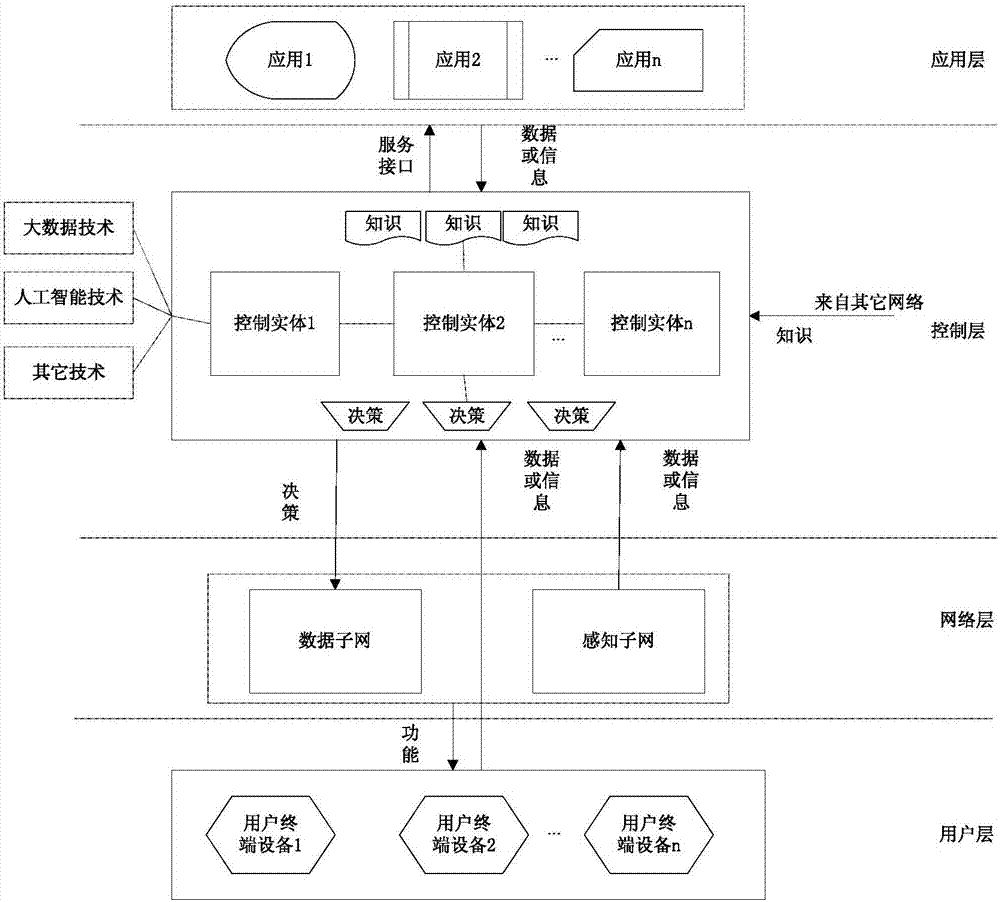
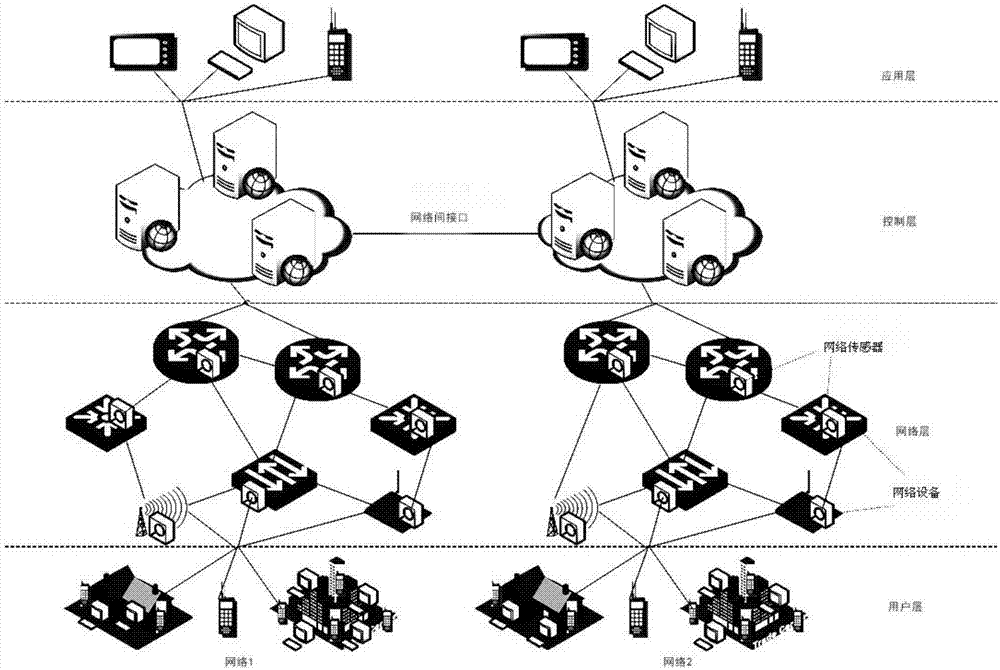
Network architecture of artificial-like network and implementation method
ActiveCN107425997ABest robustnessGood functionNetworks interconnectionControl layerNetwork architecture
The invention discloses a network architecture of an artificial-like network and an implementation method, and relates to the field of network architecture. The network architecture herein includes a user layer, a network layer, a control layer and an application layer. The user layer is intended for providing information to the control layer. The network layer is intended for transmitting and receiving data, executing a command from the control layer, sensing network state, environment information and knowledge of other networks, and handling the network state, the environment information and the knowledge of other networks to the control layer. The control layer is intended for acquiring and processing the information from the application layer, the user layer and the network layer, and saving the processed information and the knowledge of the other networks, and the control layer is also intended for generating knowledge associated with the network state and decisions, and adding the knowledge associated with the network state and decisions to a database. A control entity is intended for based on the current network state, obtaining decisions, performing decision-making rehearsal by simulation, estimating optimal time for implementing the decisions, implementing the decisions, evaluating the decisions and feedbacking the decisions. The application layer is intended for receiving the information provided by the control layer and providing required information to the control layer. According to the invention, the network architecture herein can increase the robustness of the network, enhances defense against network attacks, and provide quality functions and performances.
Owner:FENGHUO COMM SCI & TECH CO LTD
Intelligent door lock safety management system based on open architecture
InactiveCN111243137AUser identity/authority verificationIndividual entry/exit registersSafety management systemsEncryption decryption
The invention relates to the technical field of intelligent door lock safety management, and discloses an intelligent door lock safety management system based on an open architecture. The intelligentdoor lock safety management system comprises intelligent door lock control equipment Pi running intelligent door lock control system software, a local server Si running the intelligent door lock safety management system software, and a mobile terminal Ui. When the user on the mobile terminal Ui sends an unlocking request to the intelligent door lock control system of the intelligent door lock control equipment Pi, the intelligent door lock safety management system of the local server Si verifies the identity of the user on the mobile terminal Ui, only when the identity of the user passes the safety verification of the intelligent door lock safety management system, the user is allowed to unlock the intelligent door lock through the intelligent door lock control system of the intelligent door lock control equipment Pi, i.e. the identity verification and unlocking work of the intelligent door lock is realized under an open network architecture. The technical problem that the present intelligent door lock safety management system cannot guarantee safety of encryption and decryption processes in the open architecture can be solved.
Owner:汪洵
Sensing network control layer, sensing network architecture and construction method thereof
InactiveCN108880911AStrong computing powerReduce communication delayData switching networksWireless communicationNetwork controlNetwork architecture
The invention discloses a sensing network control layer, a sensing network architecture and a construction method thereof. The sensing network control layer is arranged in a physical network sensing layer; all nodes of an Internet of Things sensing layer communicate with a physical network gateway through the sensing network control layer; the sensing network control layer comprises: a plurality of control nodes; the control nodes are all screened out from the nodes of the Internet of Things sensing layer; the links between the control nodes are all screened ou from the links of the Internetof Things sensing layer; the screening of the control nodes and the links satisfies the following conditions: the energy of each control node is greater than a set energy threshold; the moving speed of each control node is less than a set speed threshold; the total number of control nodes is less than a set number threshold; non control nodes of the Internet of Things sensing layer communicate with the physical network gateway through the control nodes; and if a link is added to the sensing network control layer, the link is connected, and the two nodes of the link are also in the sensing network control layer.
Owner:SHANDONG UNIV
User access method based on SDN (Software Defined Network) and Hotspot2.0 for use under novel network architecture
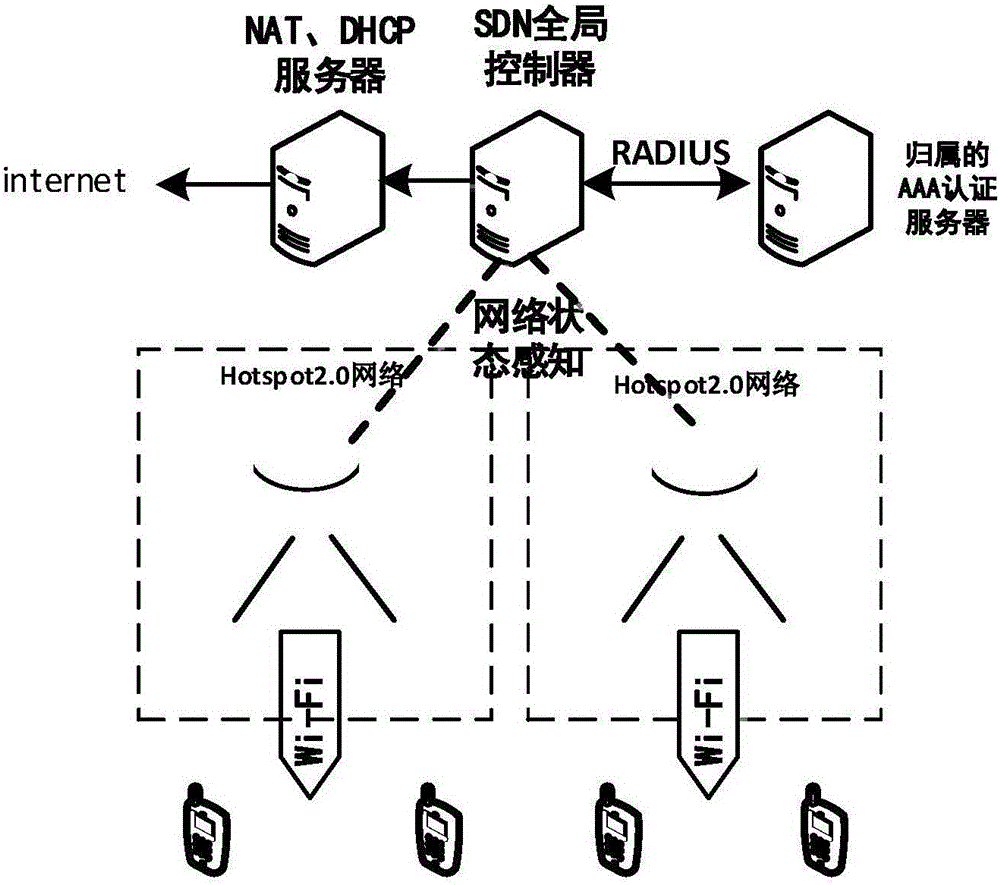
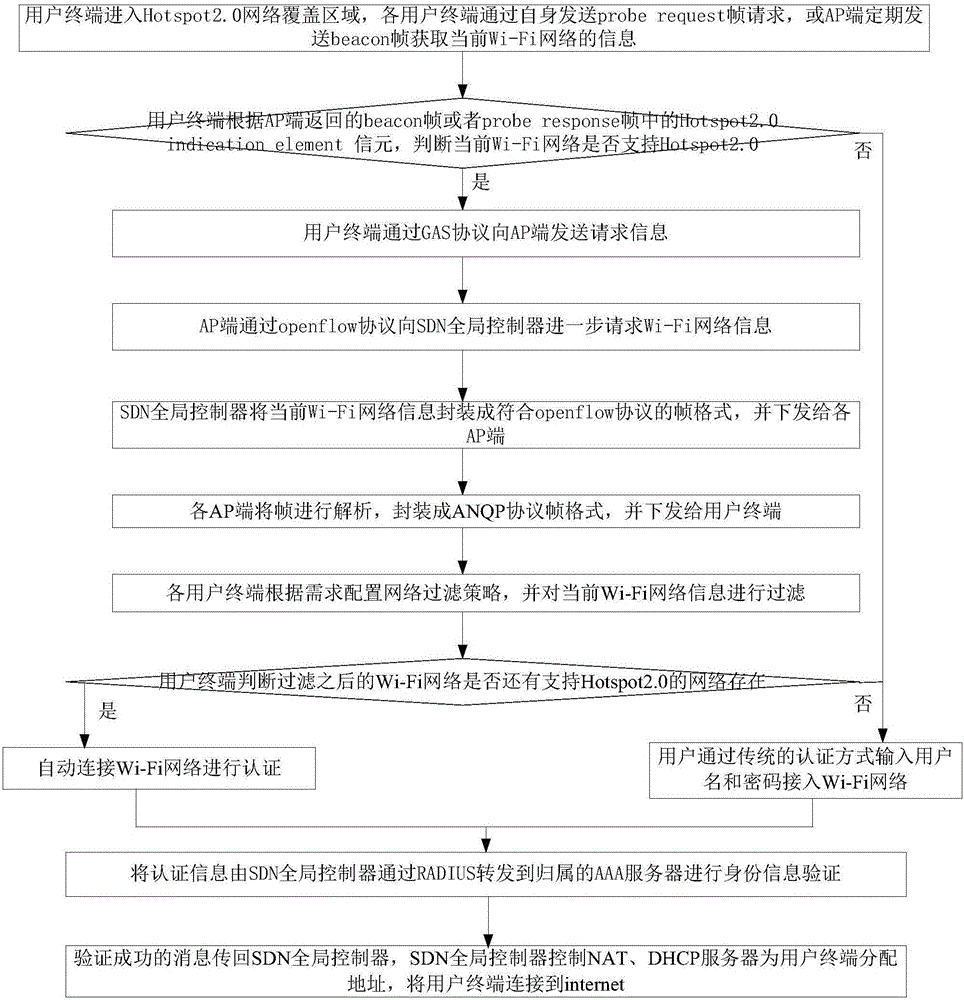
ActiveCN105979555AImprove controllabilitySolve the problem of information sourcesWireless communicationThe InternetNetwork architecture
The invention discloses a user access method based on an SDN (Software Defined Network) and Hotspot2.0 for use under novel network architecture, and belongs to the field of wireless communications. The user access method comprises the following specific steps that: users judge whether a current Wi-Fi (Wireless Fidelity) network supports Hotspot2.0 or not; if so, the users send requests to an SDN global controller through AP (Access Point) ends; the SDN global controller issues current Wi-Fi network information to the AP ends, and the AP ends resolve frames, package the resolved frames into an ANQP (Access Network Query Protocol) frame format, and issue the packaged frames to the users; the users configure a network filtering strategy according to demands, and filter the current Wi-Fi network information; the users judge whether the network of which the current Wi-Fi network information is filtered still supports Hotspot2.0 or not, and if so, the users automatically connect to the Wi-Fi network for authentication; otherwise, the users access the Wi-Fi network in a conventional way; the SDN global controller verifies identity information through RADIUS; and user terminals are connected to the Internet after successful verification. The user access method has the advantages that an SDN technology is combined with a Hotspot2.0 technology, so that the problem of information sources of newly-added information elements in the Hotspot2.0 is solved. Meanwhile, the SDN has higher controllability specific to the networks, and seamless fusion between a honeycomb network and the Wi-Fi network is ensured better.
Owner:BEIJING UNIV OF POSTS & TELECOMM
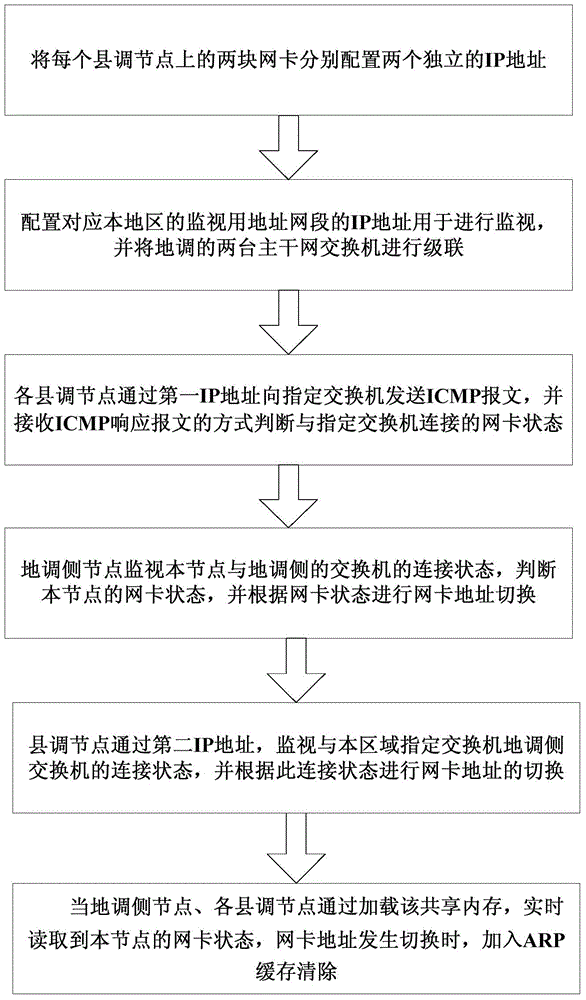
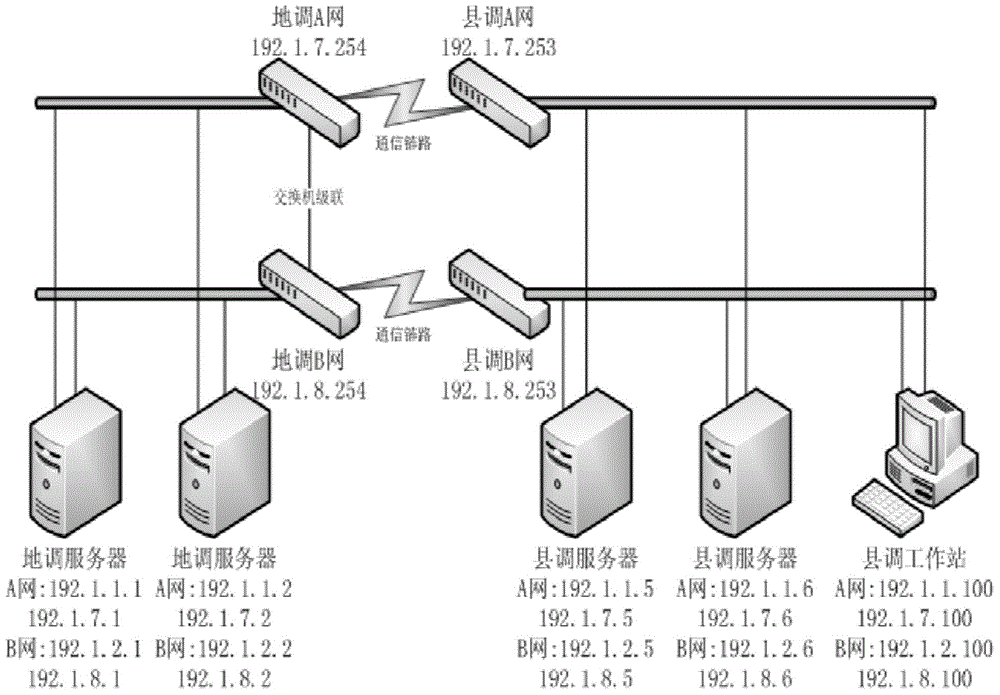
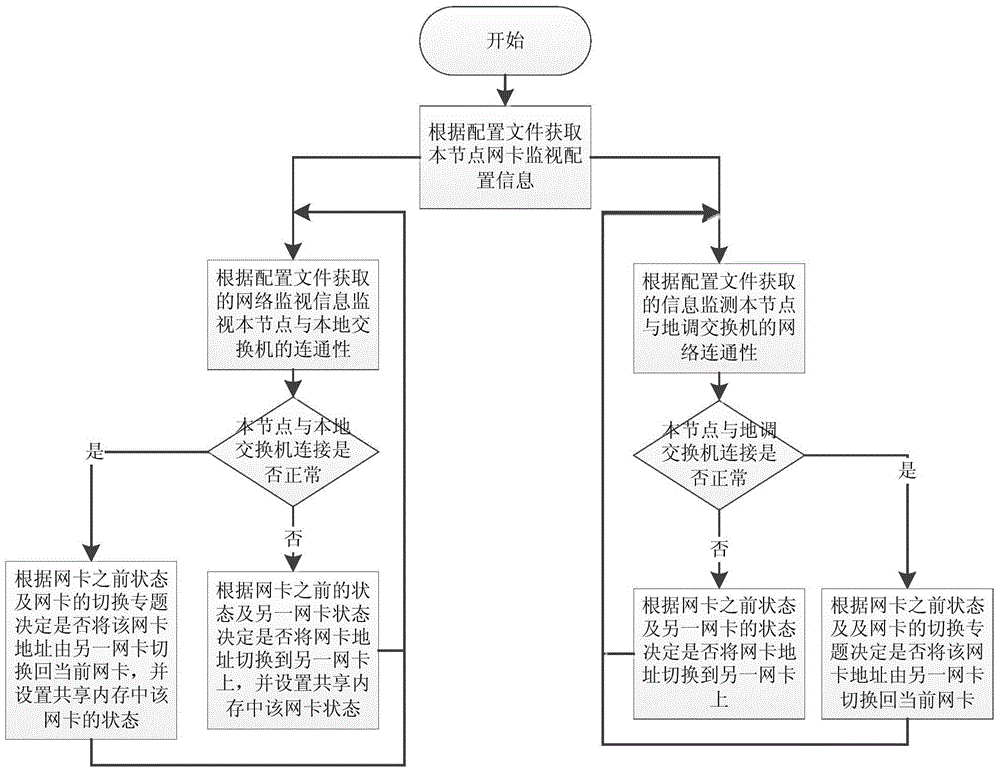
Network interface card state monitoring and address switching method of region-county integrated network architecture
ActiveCN104320294ARealize redundancy and mutual backupData switching networksNetwork architectureNetwork interface controller
The invention discloses a network interface card state monitoring and address switching method of a region-county integrated network architecture. County scheduling node send ICMP messages to local switches and receive ICMP response messages, and all nodes can accurately determine the network interface card states of local nodes and switching the communication addresses of the nodes according to the network interface card states so as to realize redundancy mutual backup of networks; and at the same time, through sending the ICMP messages to region scheduling (specific) switches and receiving the ICMP response messages, the county scheduling nodes can determine the connection states of the local nodes with region scheduling nodes and switching the communication addresses of the local nodes according to the connection states so as to ensure that system nodes can still communicate with each other normally even if only one link works normally between the region scheduling nodes and the county scheduling nodes, and realize the network redundancy mutual backup on the region-county integrated system network architecture. Therefore, the method provided by the invention has good application prospect.
Owner:NARI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com