Patents
Literature
246 results about "Cloud deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
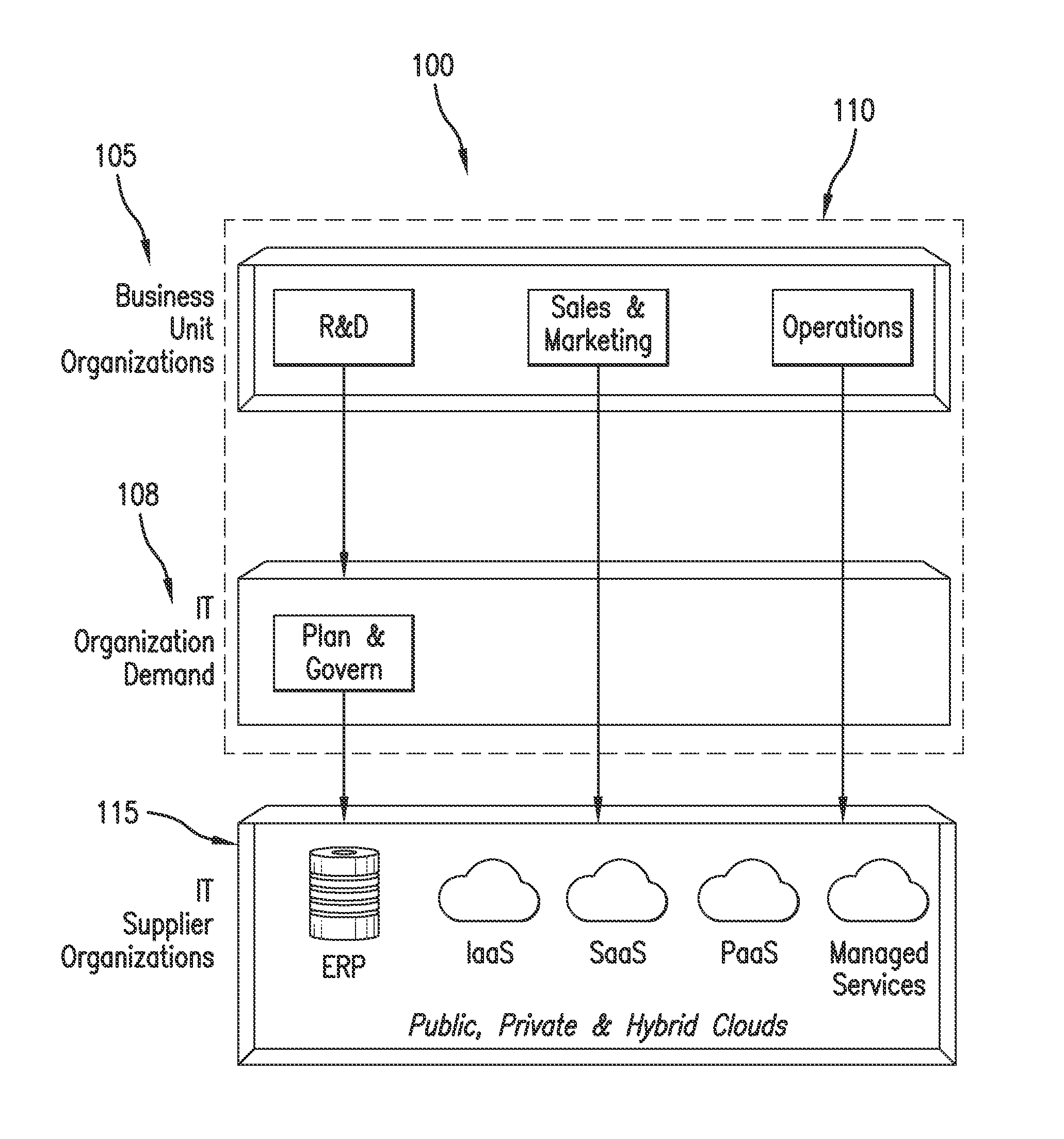
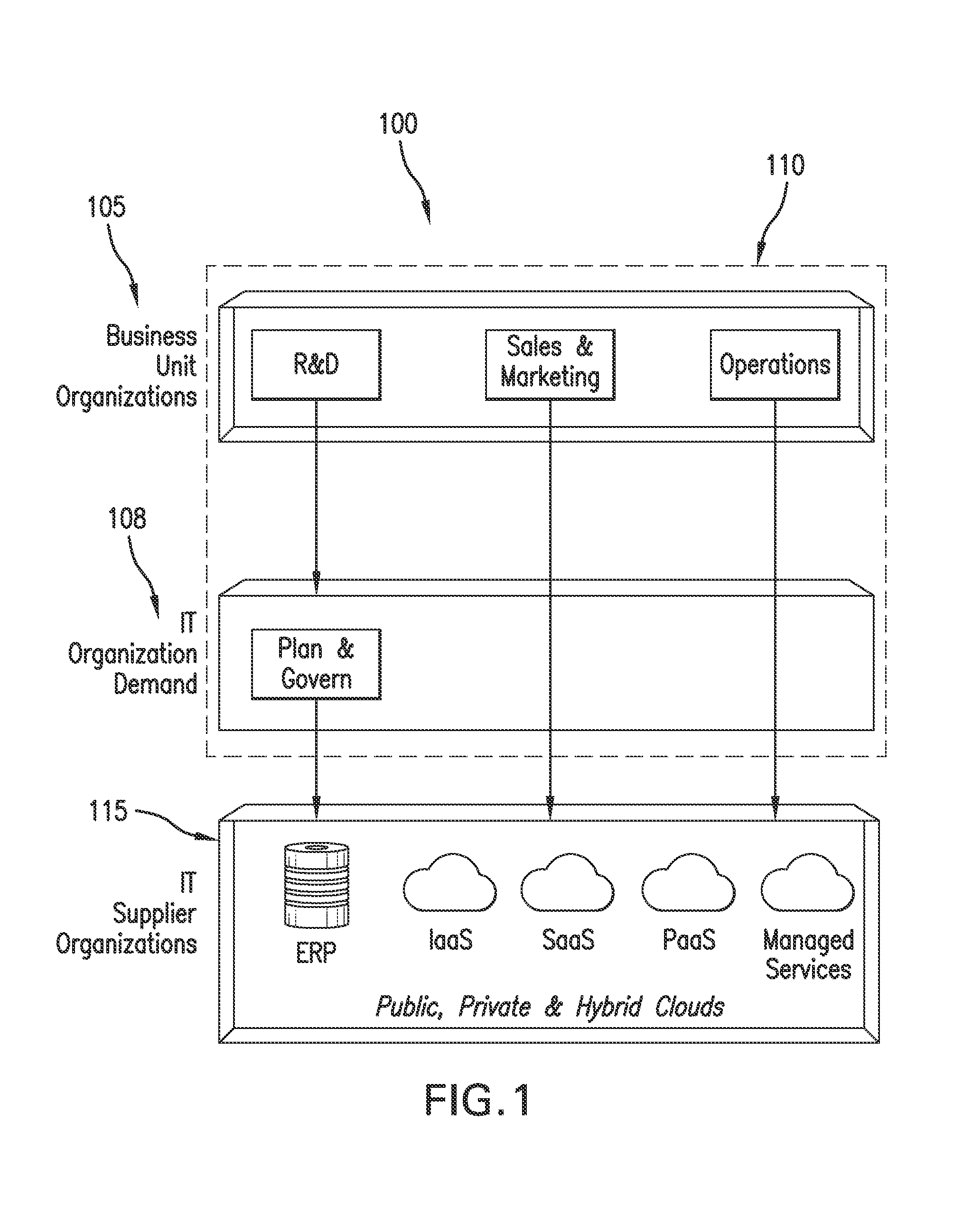
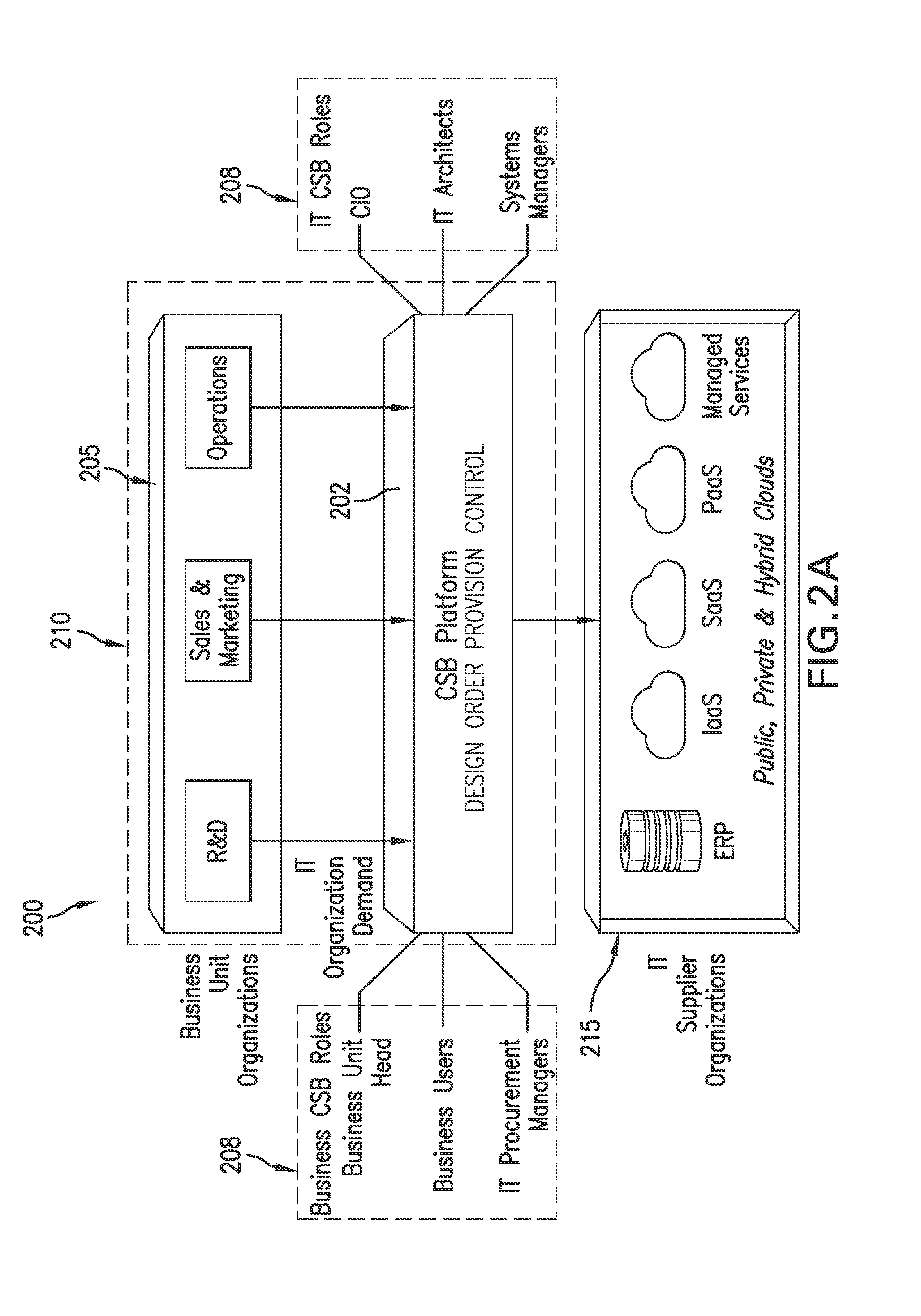
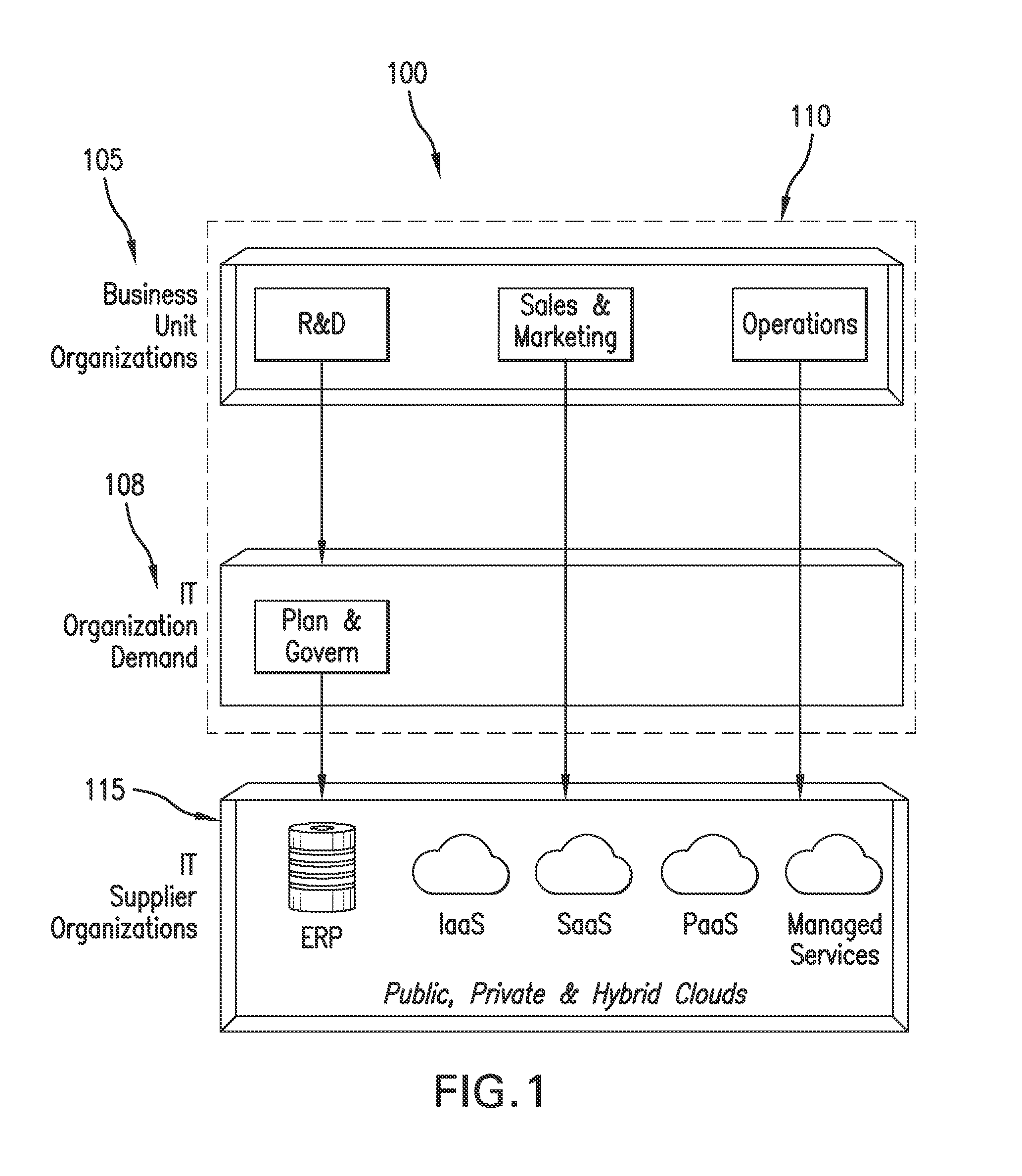
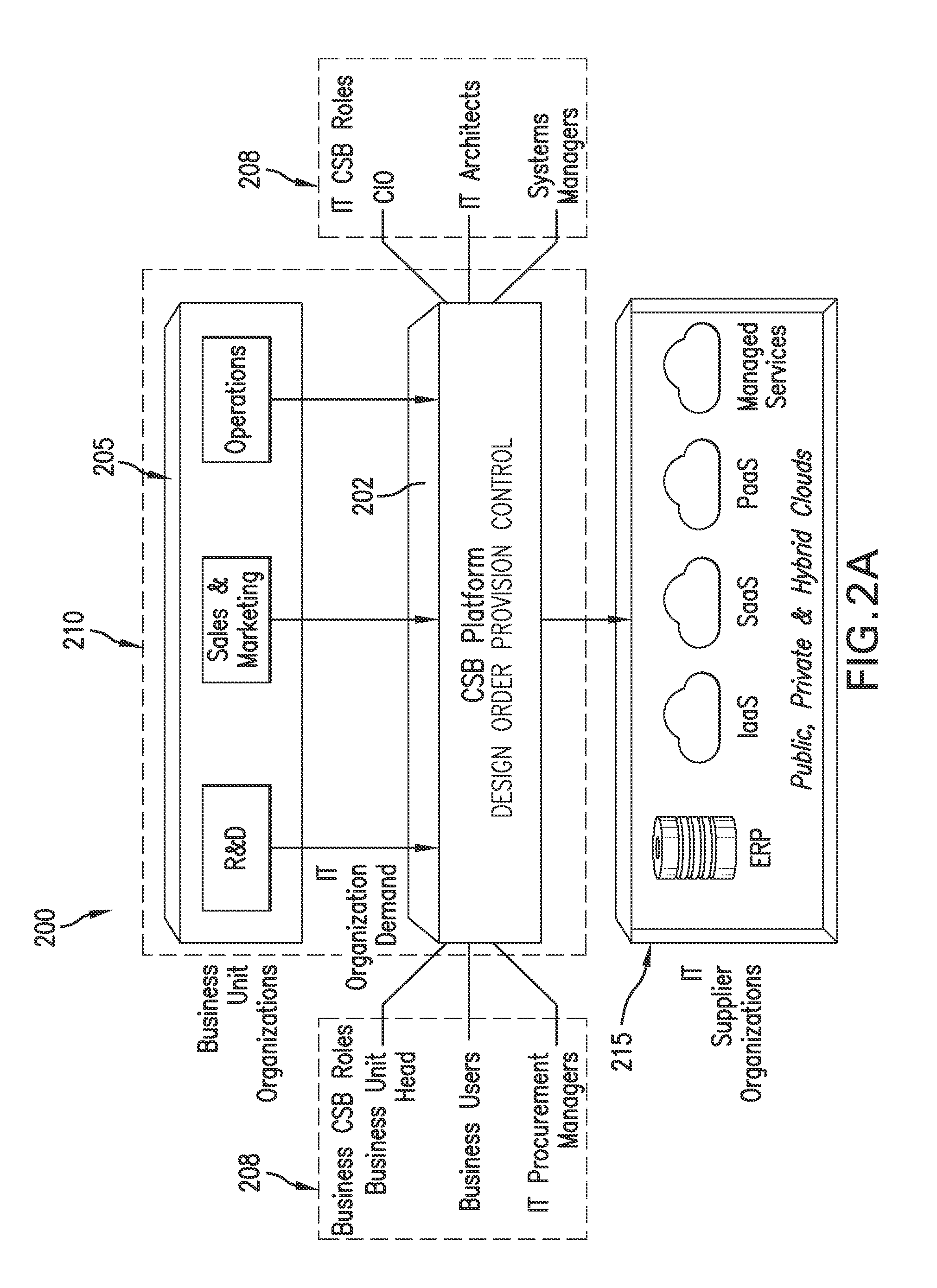
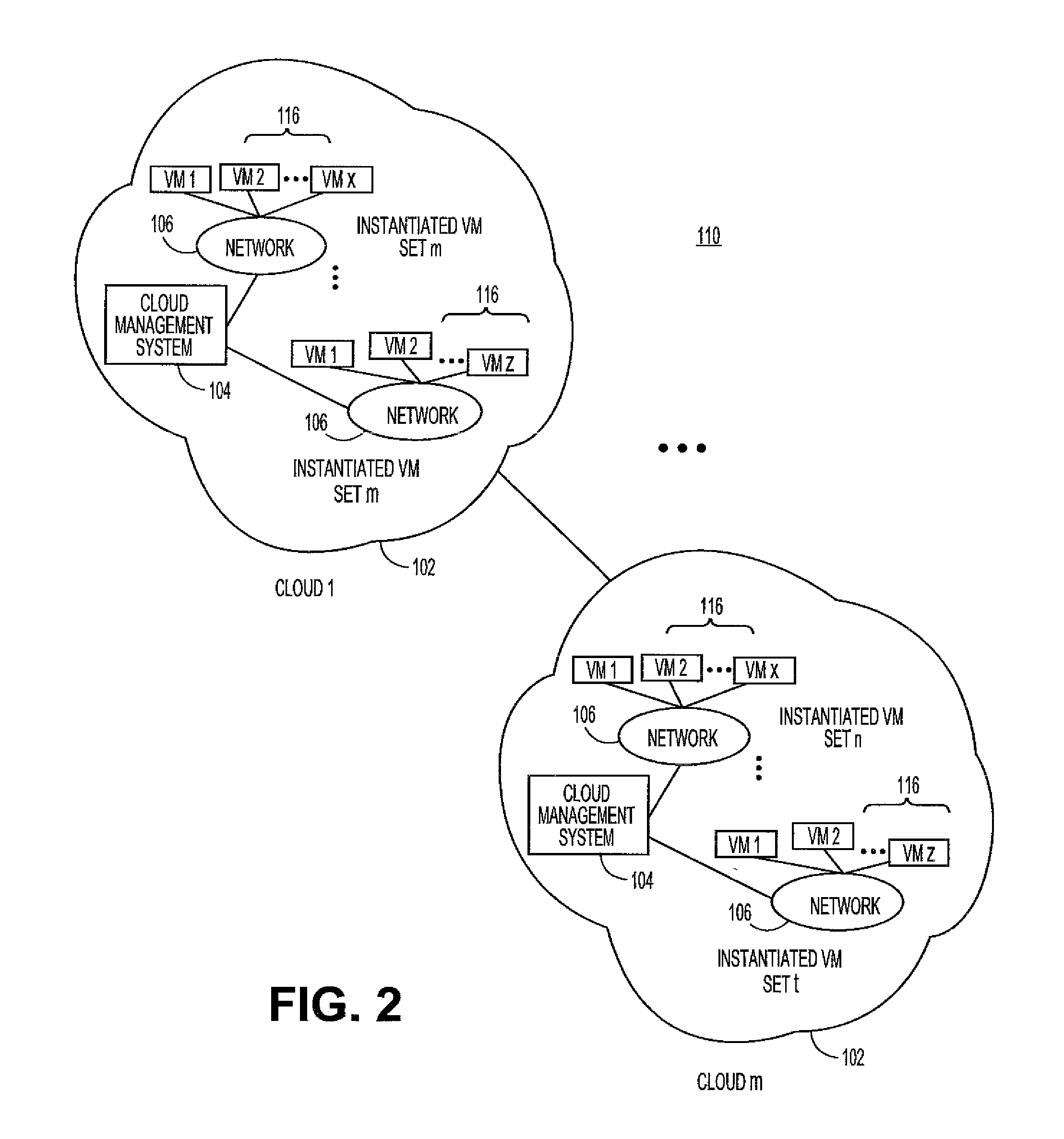
Deployment to the Cloud. Cloud deployment refers to the enablement of SaaS (software as a service), PaaS (platform as a service) or IaaS (infrastructure as a service) solutions that may be accessed on demand by end users or consumers. A cloud deployment model refers to the type of cloud computing architecture a cloud solution will be implemented on.
Assessment of best fit cloud deployment infrastructures
InactiveUS20140279201A1Enhancing cloud serviceEfficient and effectiveFinanceBuying/selling/leasing transactionsApplication softwareInformation processor
A system configured to facilitate selling hybrid cloud services comprises a plurality of user interface structures each coupled to an information processor. A first user interface structure is configured to request information characterizing deployment of an application within a current operational infrastructure. A second user interface structure is configured to display a recommended deployment infrastructure supporting migration of the application thereto. A third user interface structure is configured to display information characterizing migration of the application to the recommended deployment infrastructure. The information processor is configured to receive the current application deployment characterizing information from the first user interface structure, to determine the recommended deployment infrastructure using at least a portion of the current application deployment characterizing information, and to determine the information characterizing migration of the application to the recommended deployment infrastructure using at least a portion of the current application deployment.
Owner:HCL TECH LTD
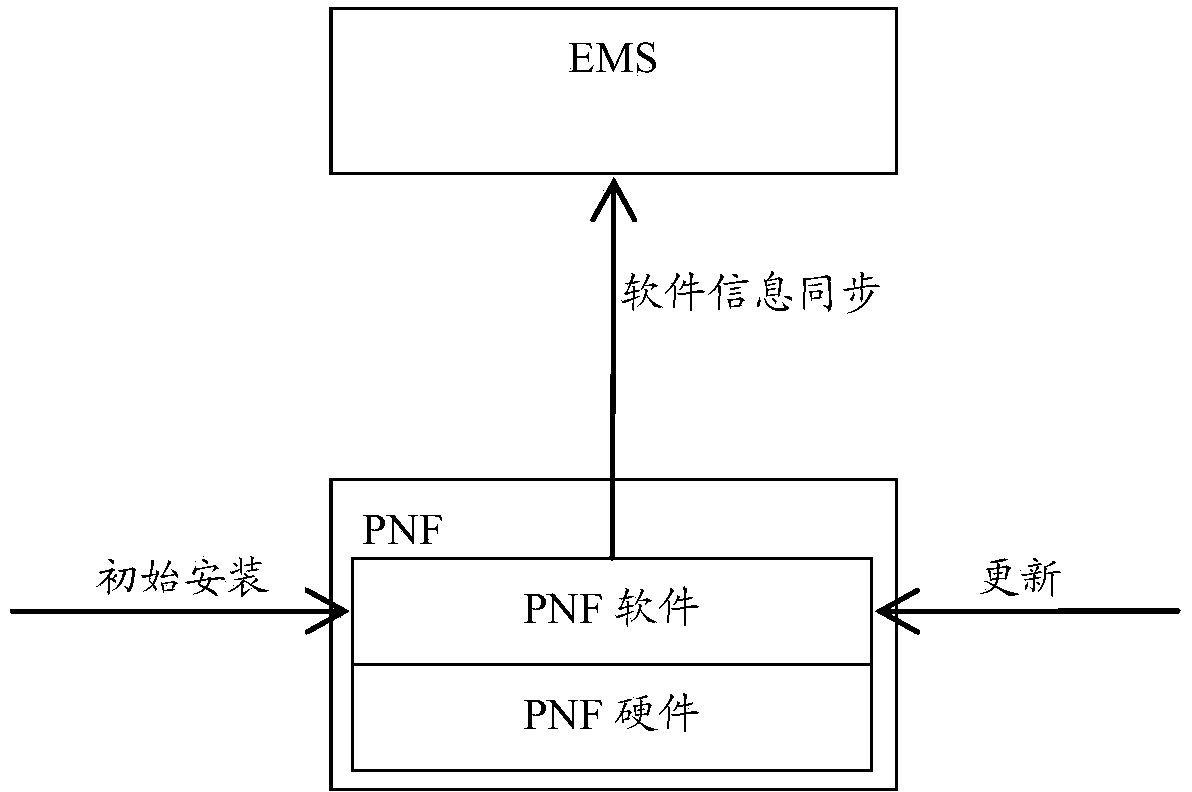
Software deployment method and system of virtual network function network element and relevant equipment
ActiveCN104253866AEnsure consistencyImprove adaptabilityData switching networksSoftware deploymentSoftware updateNetwork management
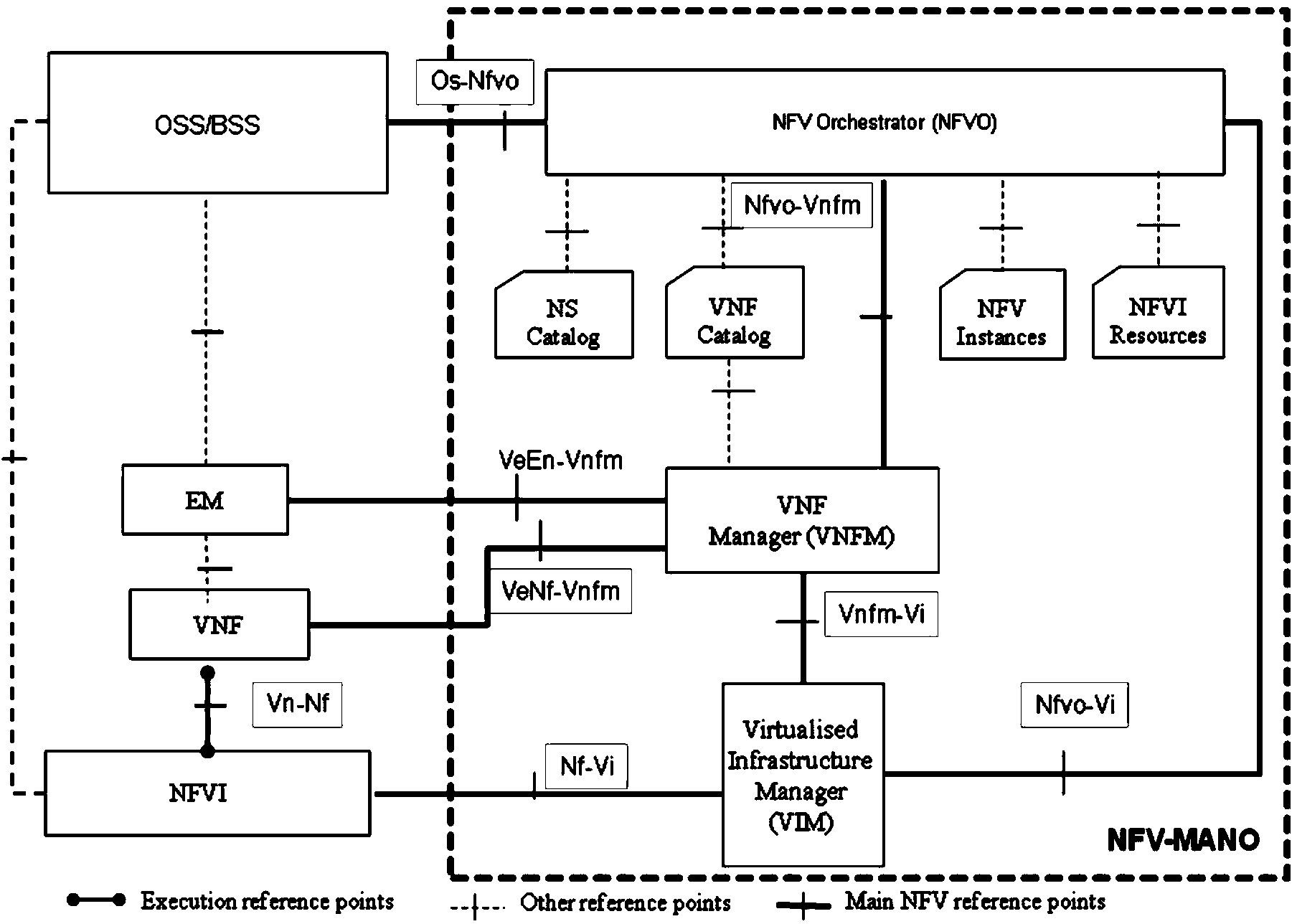
The invention provides a software deployment method and a software deployment system of a virtual network function network element and relevant equipment. According to the method, firstly, a software updating message is sent to the virtual network function network element or a network element management system corresponding to the virtual network function network element through a VNFM (virtual network function manager), and further, the virtual network function network element or the network element management system carries out software updating on the virtual network function network element according to the software updating message, and returns a software updating notification message. The VNFM updates a software version corresponding to the virtual network function network element according to the software updating notification message, and the consistency of the software version information between the virtual network function network element and the VNFM is ensured. Compared with the prior art, the software deployment method of the virtual network function network element provided by the embodiment of the invention can be used in cloud deployment scenes and has better adaptability.
Owner:HUAWEI TECH CO LTD
Systems and methods for migrating subscribed services in a cloud deployment
A decision system for providing ranked candidate cloud computing environments to customers for migration of subscribed services. The decision system can receive user usage history data and compare parameters of subscribed services on a host cloud to candidate clouds. Based on the comparison, a rank of candidate clouds for migration of the subscribed services can be determined and supplied to the customer.
Owner:RED HAT
Assessment of best fit cloud deployment infrastructures
ActiveUS20150341240A1Enhancing cloud serviceEfficient and effectiveFinanceProgram controlData miningE infrastructure
A system configured to facilitate brokering hybrid cloud services selects information requests for characterizing an information technology application. The system responses to the information requests and determines a plurality of sets of the responses each used for deriving a value of a respective one of a plurality of factor functions. The system determines a plurality of assessment results each derived using values for of a respective set of the factor functions. Each one of the assessment results characterizes a respective aspect of deploying the information technology application within a cloud environment.
Owner:HCL TECH LTD
Tracking application deployment errors via cloud logs
ActiveUS20150347264A1Hardware monitoringNon-redundant fault processingUnique identifierApplication software
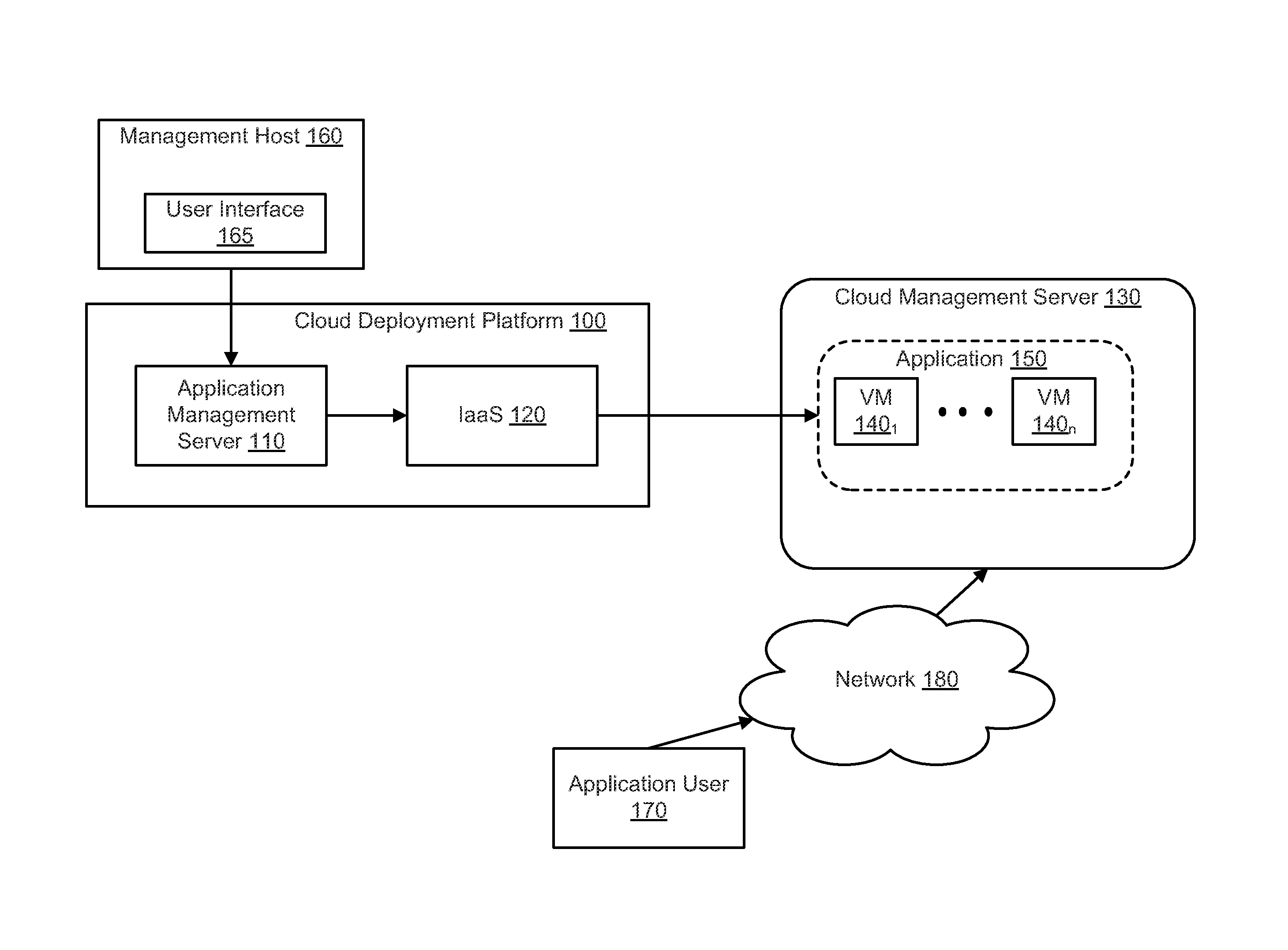
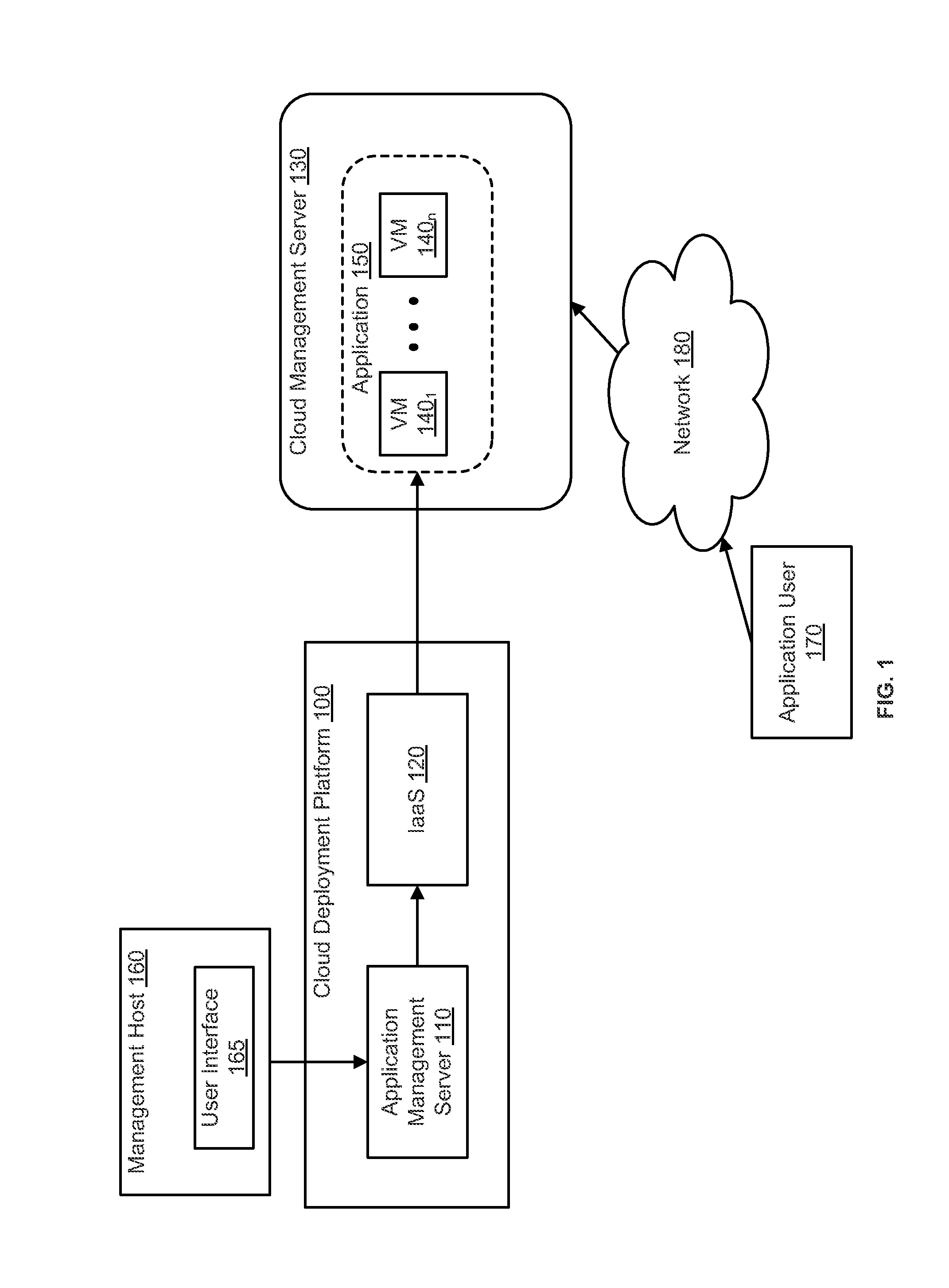
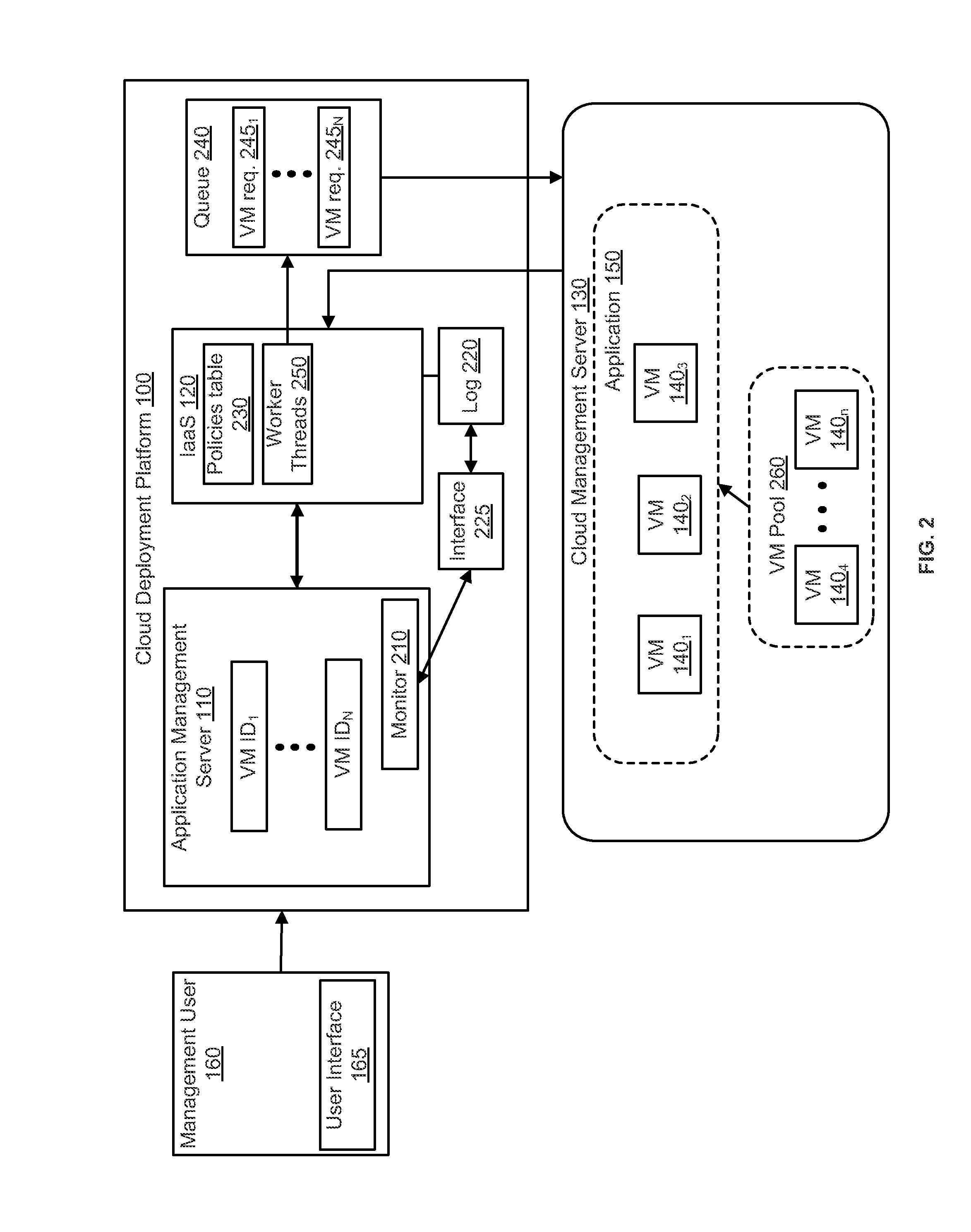
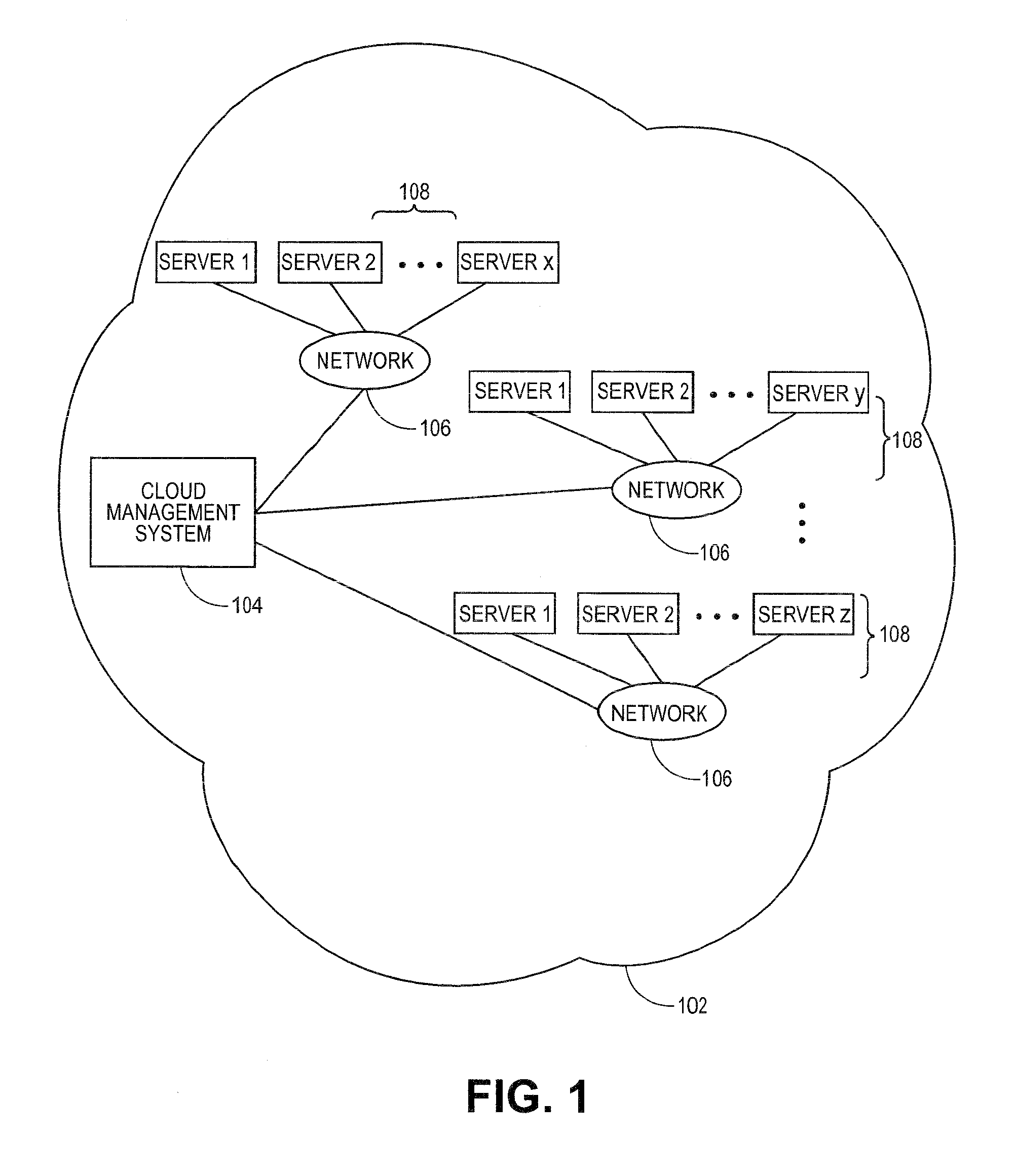
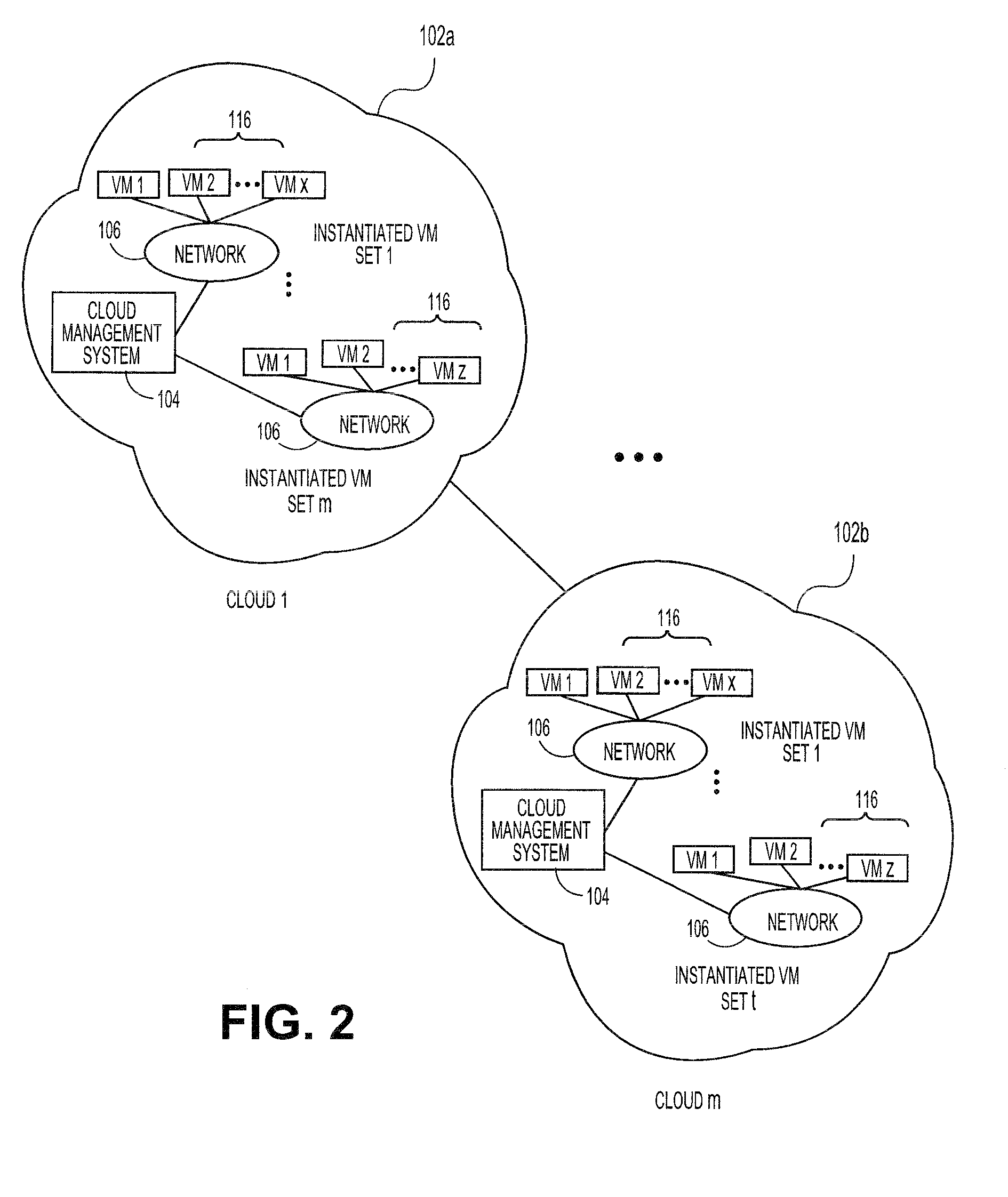
A cloud computing environment consists of a cloud deployment platform and a cloud management server configured to manage a plurality of virtual machines deployed in a cloud infrastructure. When a request to deploy an application to the cloud infrastructure is received by the cloud deployment platform, application deployment errors are monitored and tracked. A unique identifier is generated for each virtual machine, and requests to instantiate the virtual machines in the cloud infrastructure are then transmitted. A log containing error records that identify the occurrence of deployment errors is monitored based on the generated virtual machine identifiers, where the deployment errors are detected by the cloud deployment platform or the cloud management server. Based on the monitoring, error messages are generated by the cloud deployment platform.
Owner:VMWARE INC
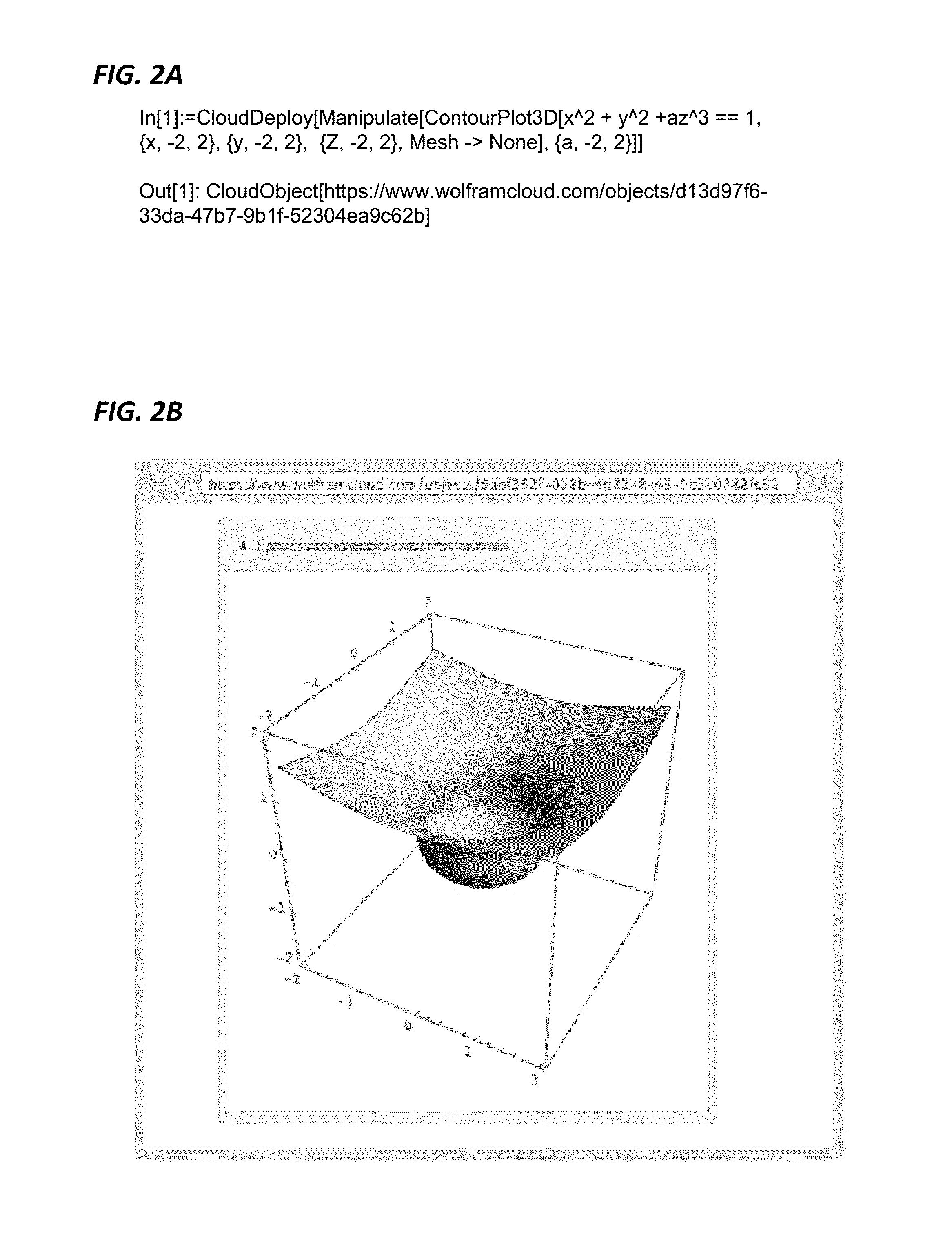
Methods and systems for cloud computing
In a method for cloud deployment, programmer input in a programming language is received, the programmer input including i) a built-in function corresponding to making electronic objects accessible on a network, and ii) a parameter indicating an electronic object. The programmer input is evaluated to cause the electronic object to be stored on a server and made accessible via a network coupled to the server.
Owner:WOLFRAM RESEARCH
Extending infrastructure security to services in a cloud computing environment
InactiveUS20140317716A1SSO is facilitatedDigital data processing detailsMultiple digital computer combinationsTrust relationshipBase exchange
A cloud deployment appliance (or other platform-as-a-service (IPAS) infrastructure software) includes a mechanism to deploy a product as a “shared service” to the cloud, as well as to enable the product to establish a trust relationship between itself and the appliance or IPAS. The mechanism further enables multiple products deployed to the cloud to form trust relationships with each other (despite the fact that each deployment and each product typically, by the nature of the cloud deployment, are intended to be isolated from one another). In addition, once deployed and provisioned into the cloud, a shared service can become part of a single sign-on (SSO) domain automatically. SSO is facilitated using a token-based exchange. Once a product registers with a token service, it can participate in SSO. This approach enables enforcement of consistent access control policy across product boundaries, and without requiring a user to perform any configuration.
Owner:IBM CORP
Monitoring cloud-runtime operations
ActiveUS20120072579A1Well formedError detection/correctionDigital computer detailsCloud baseRuntime verification
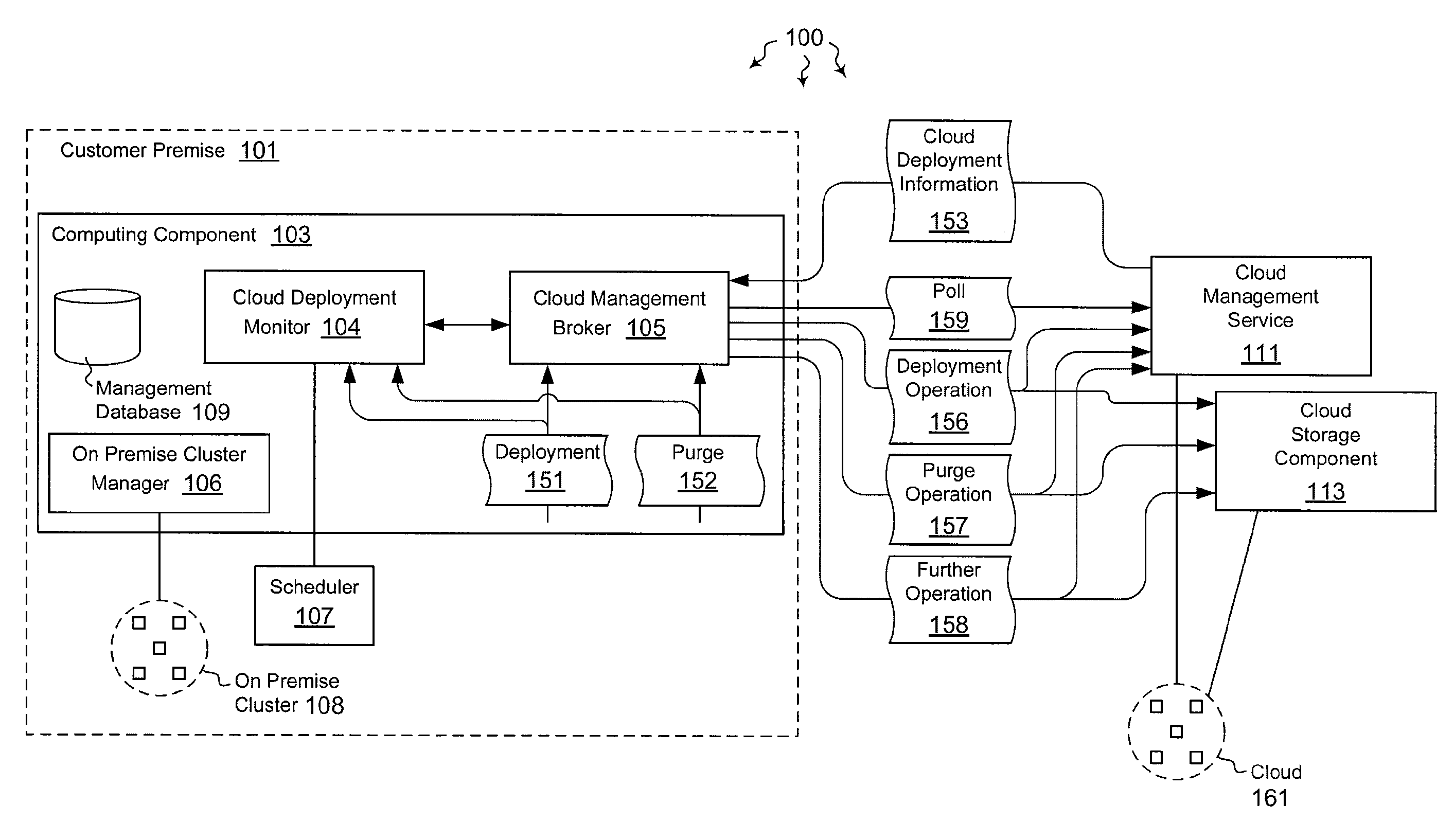
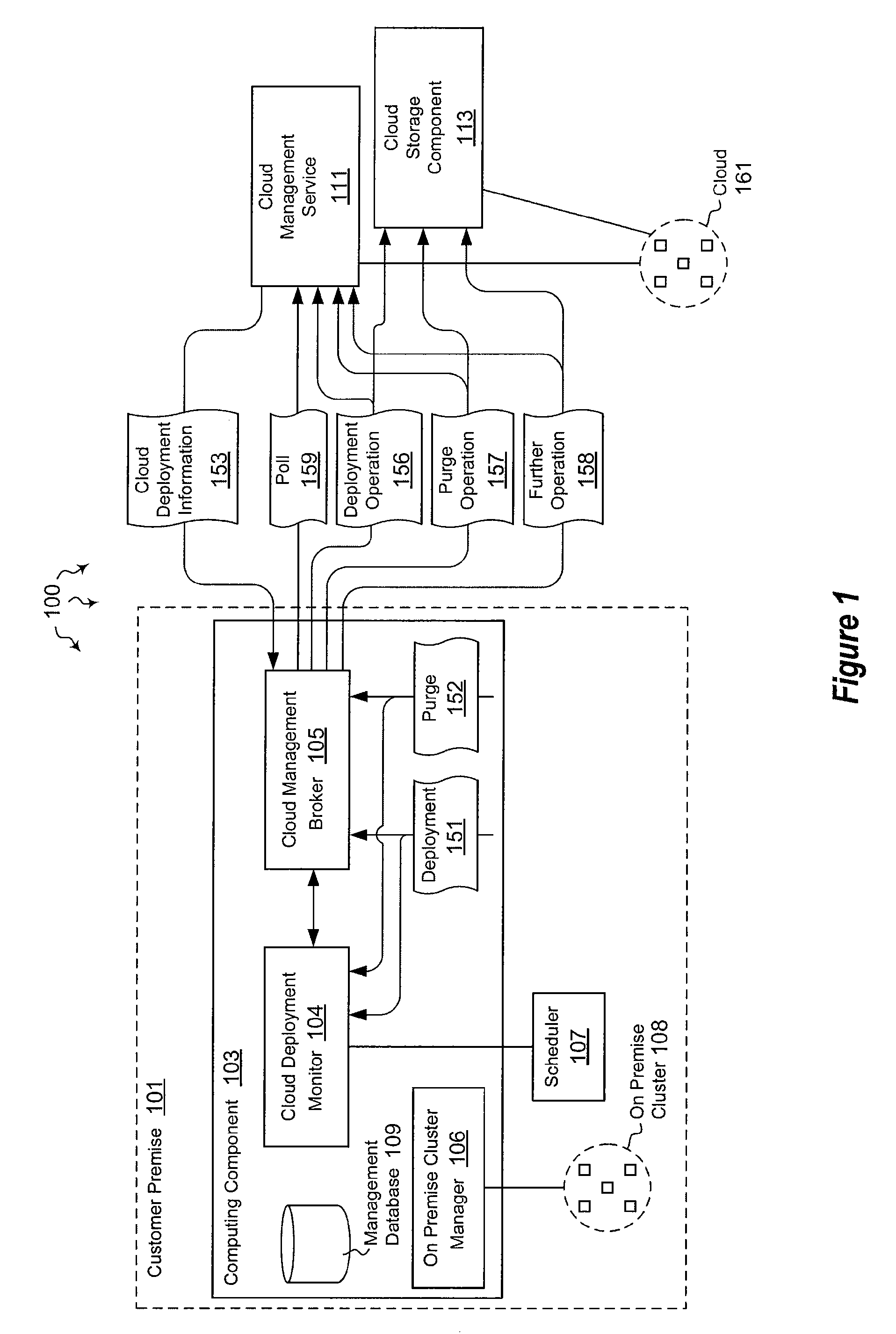
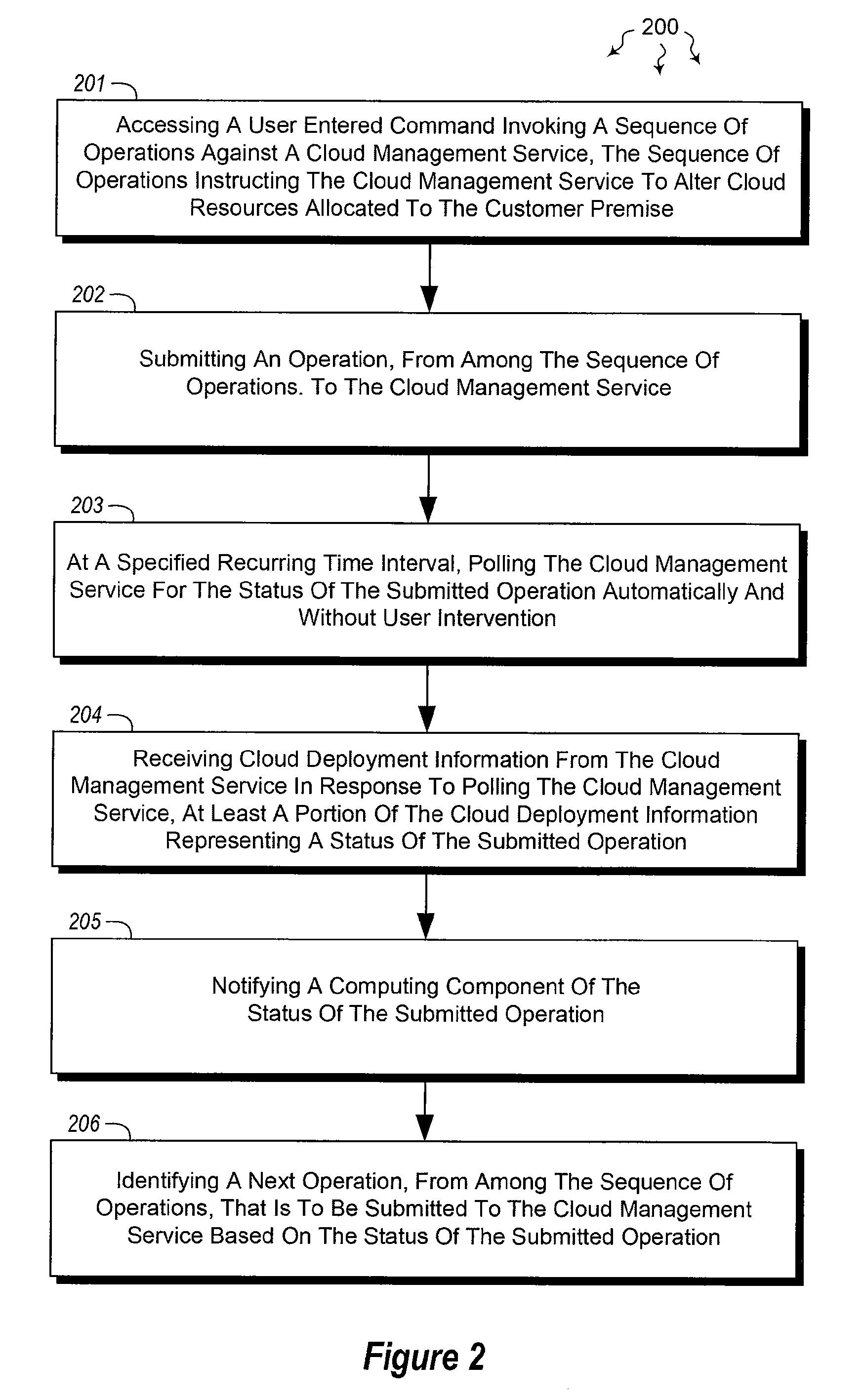
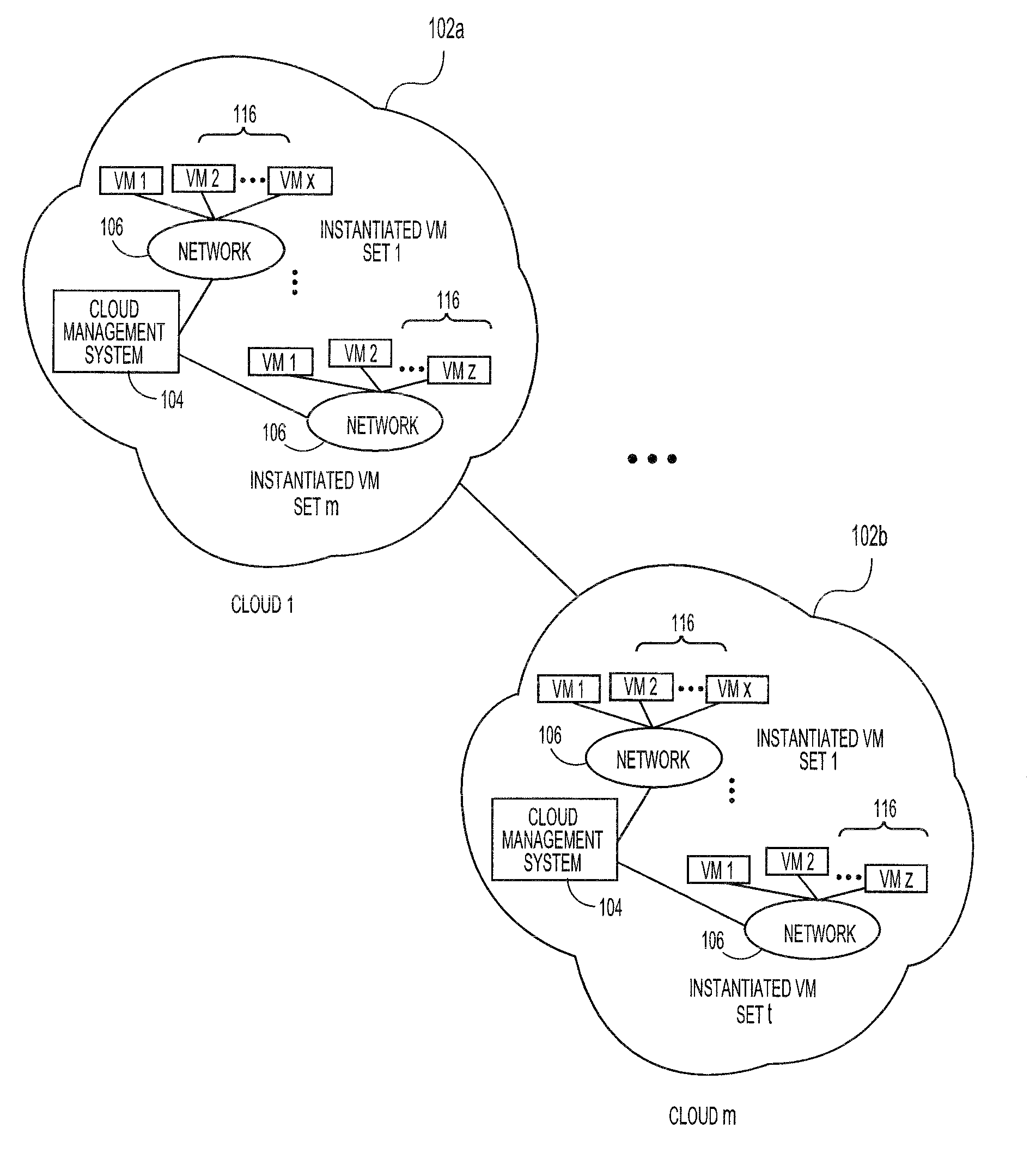
The present invention extends to methods, systems, and computer program products for monitoring cloud-runtime operations. Embodiments of the invention include an infrastructure for initiating and monitoring (e.g., asynchronous) cloud-runtime operations. In some embodiments, cloud-runtime operations are included in a sequence of operations (e.g., in a workflow) for deploying or purging cloud based resources for a customer premise. Accordingly, monitored operations include creating cloud deployments, growing cloud deployments, shrinking cloud deployments, and deleting cloud deployments. Cloud deployments can be reliably deleted when a workflow is aborted, to prevent accrual of unexpected charges.
Owner:MICROSOFT TECH LICENSING LLC
Assessment of best fit cloud deployment infrastructures
ActiveUS20140317166A1Good serviceEfficient and effectiveFinanceProgram controlData miningRequest for information
A system configured to facilitate brokering hybrid cloud services selects information requests for characterizing an information technology application. The system responses to the information requests and determines a plurality of sets of the responses each used for deriving a value of a respective one of a plurality of factor functions. The system determines a plurality of assessment results each derived using values for of a respective set of the factor functions. Each one of the assessment results characterizes a respective aspect of deploying the information technology application within a cloud environment.
Owner:HCL TECH LTD
Systems and methods for identifying service dependencies in a cloud deployment
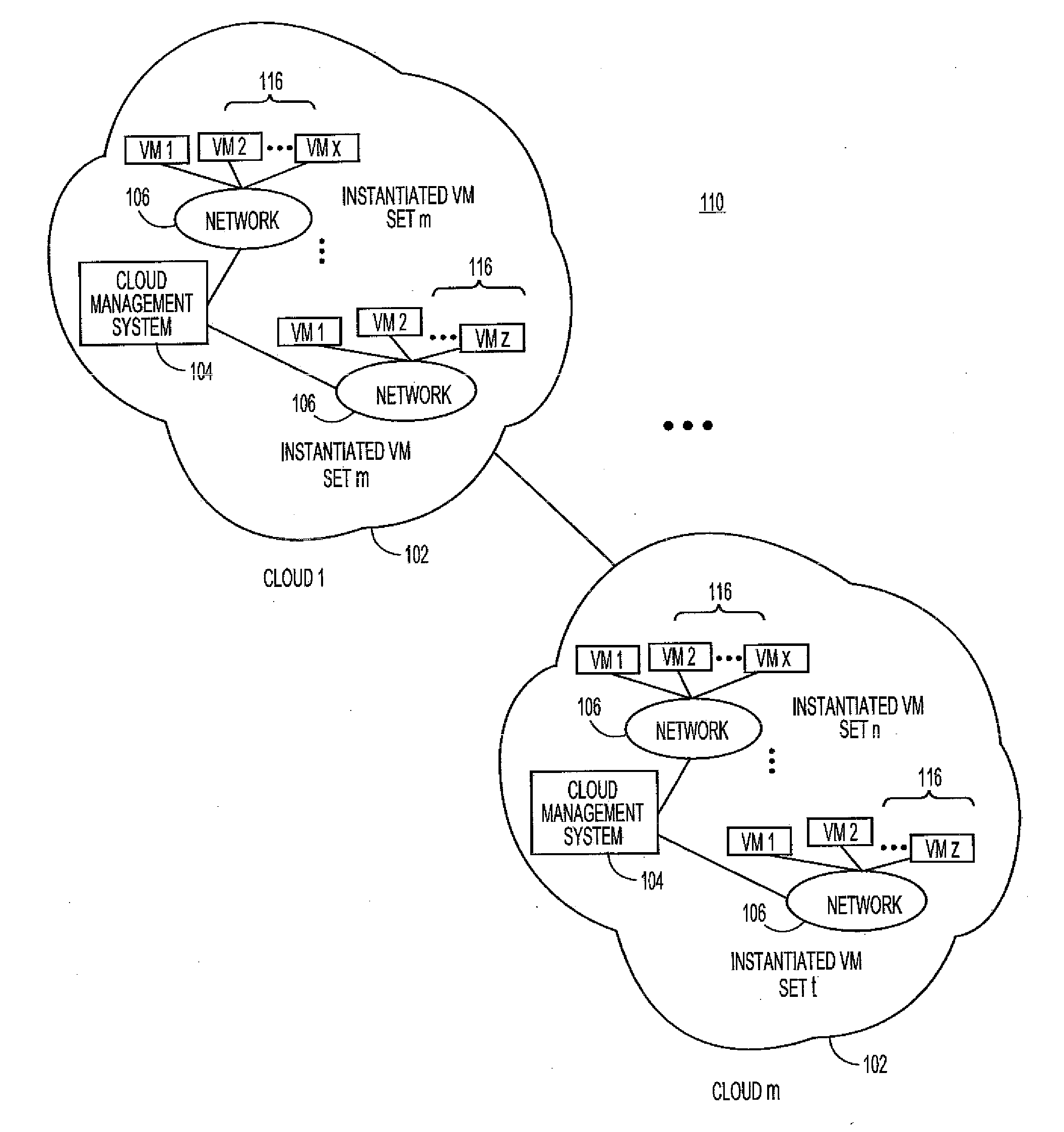
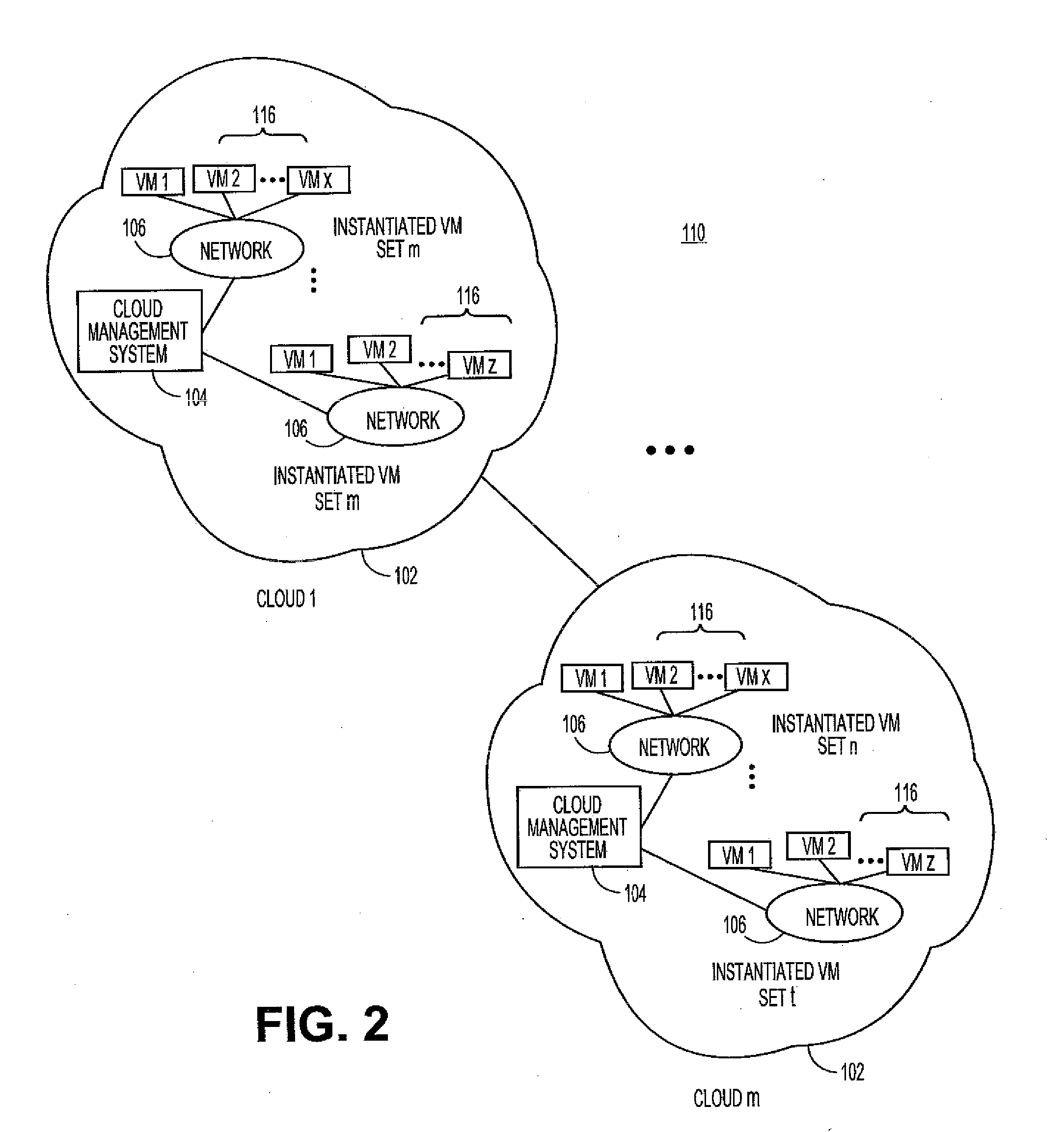
Embodiments relate to systems and methods for identifying service dependencies in a cloud deployment. In particular, a deployment module can receive usage data from a host cloud comprising data related to end user operation of a set of services in the host cloud as well as service dependencies among the set of services. In embodiments, the deployment module can determine candidate target clouds in which to deploy the set of services. Further, in embodiments, the deployment module can determine whether the candidate target clouds have a capacity to support the set of services, as well as whether services within the candidate target clouds are compatible based on the service dependencies.
Owner:RED HAT
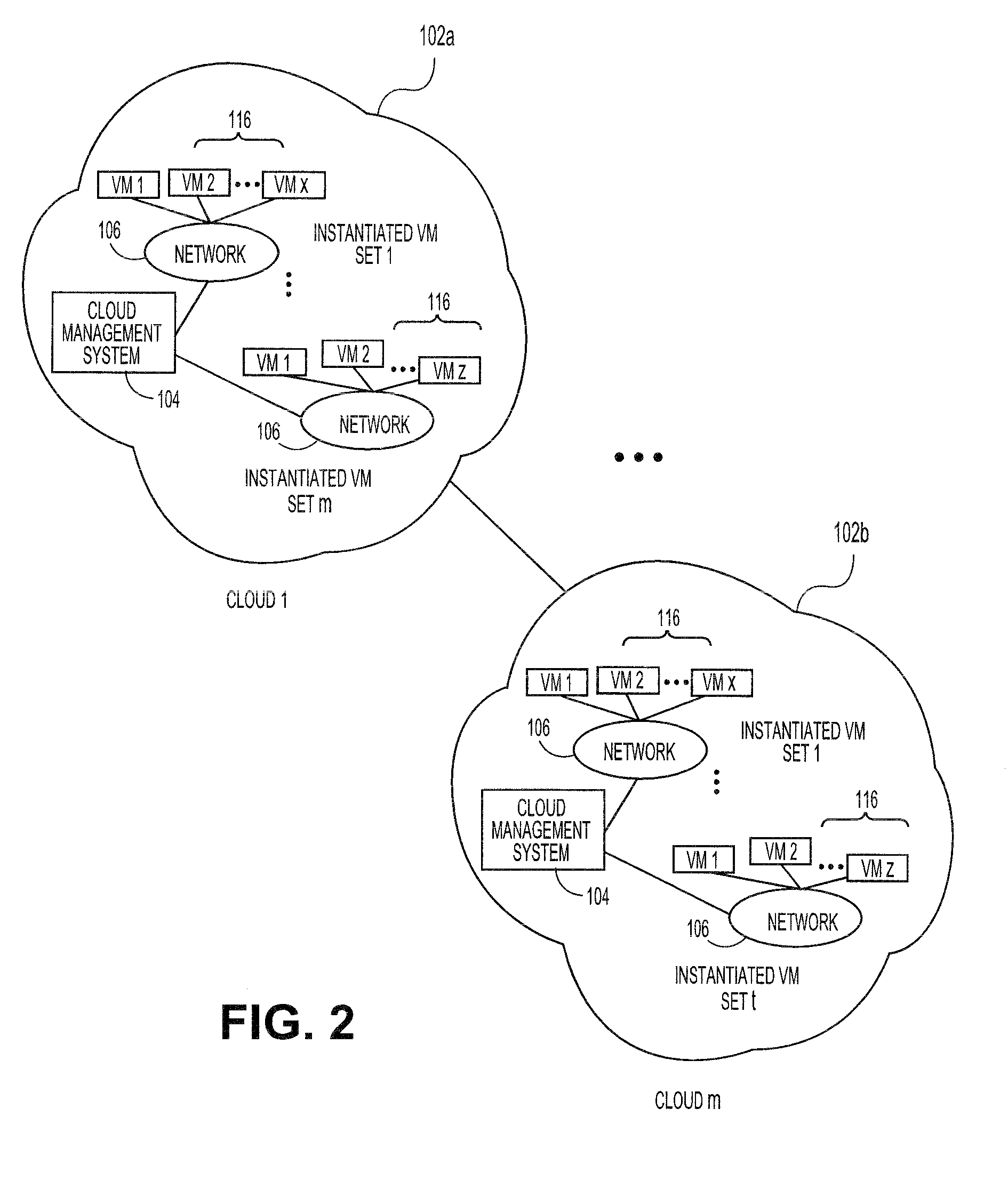
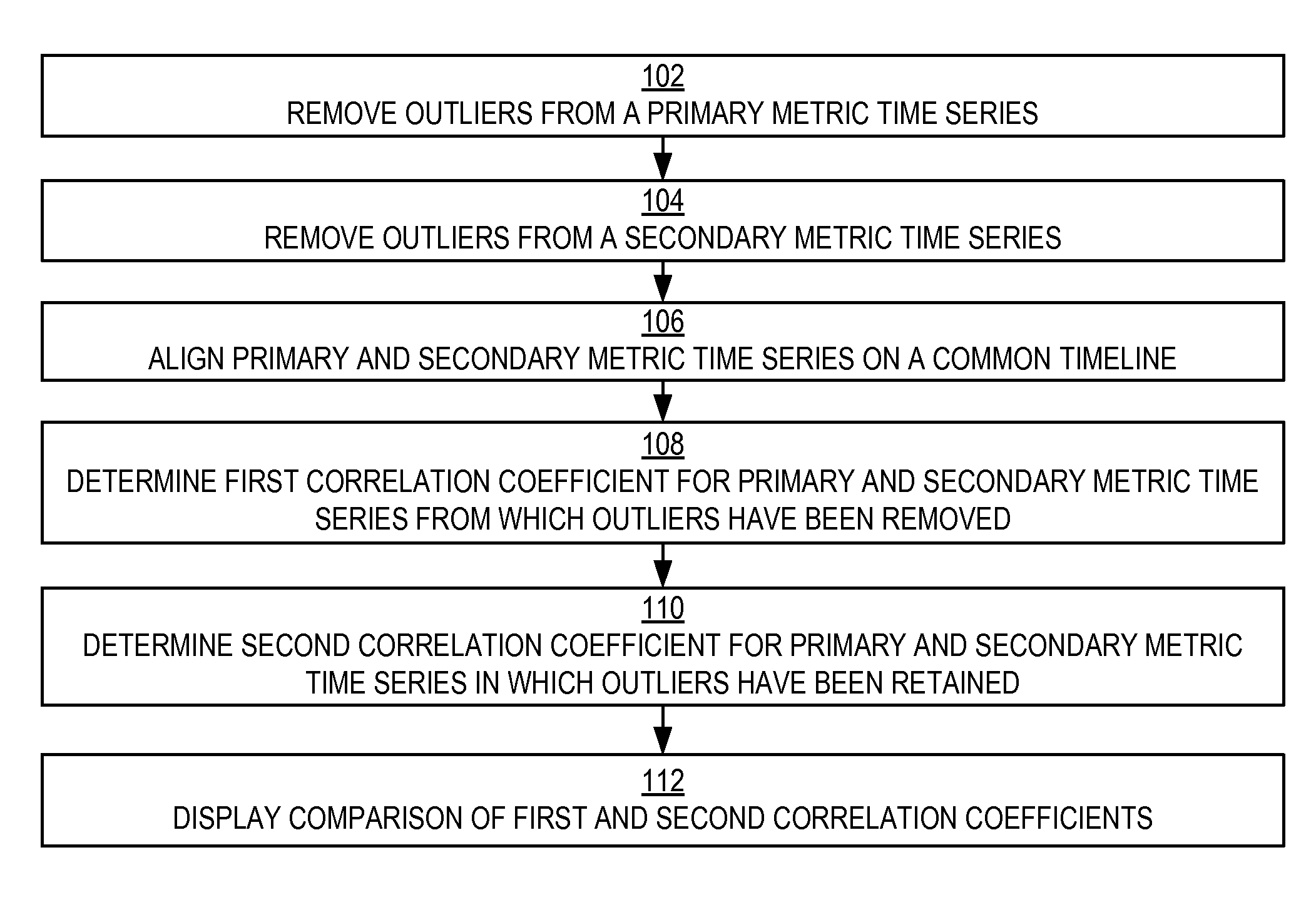
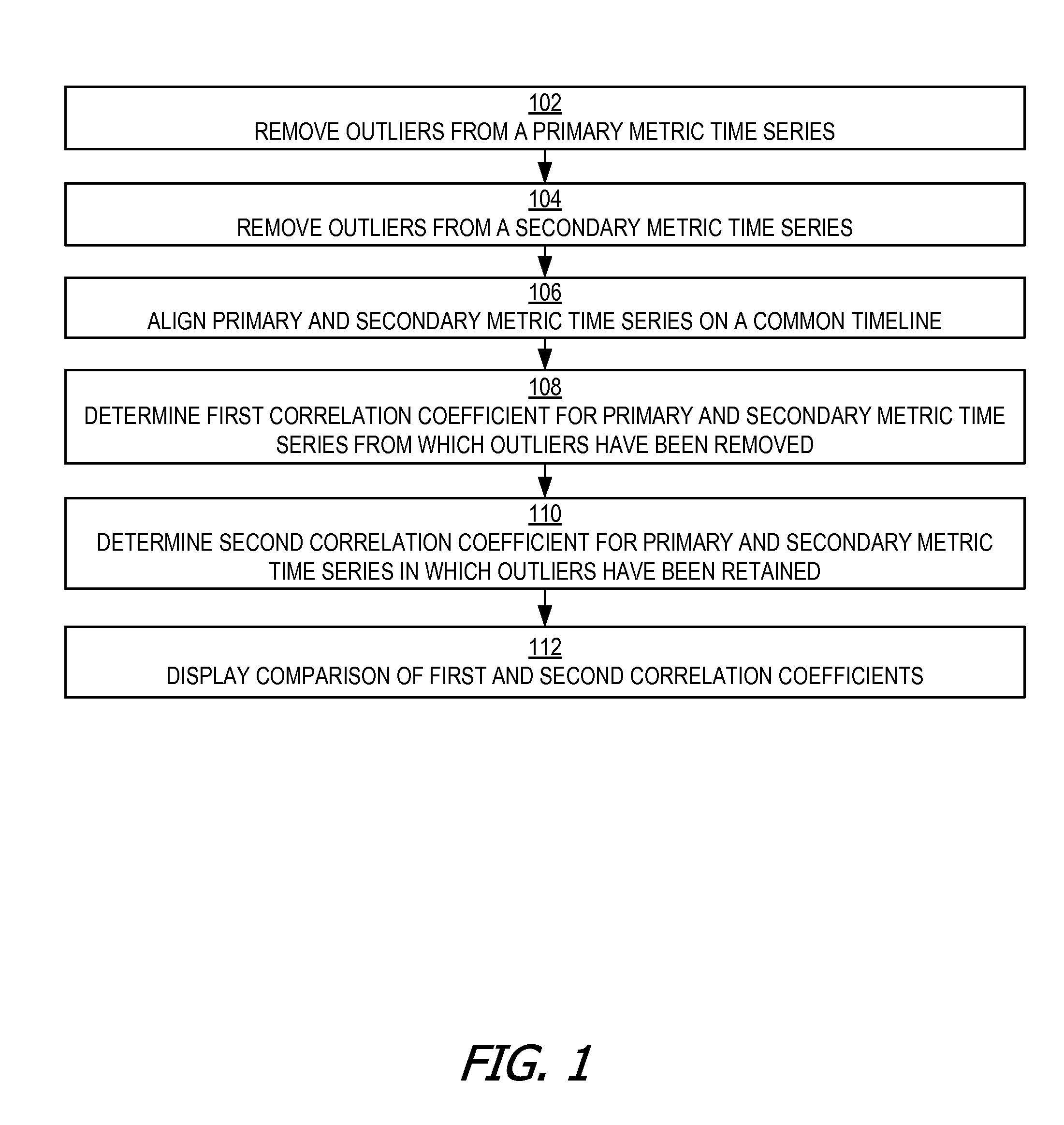
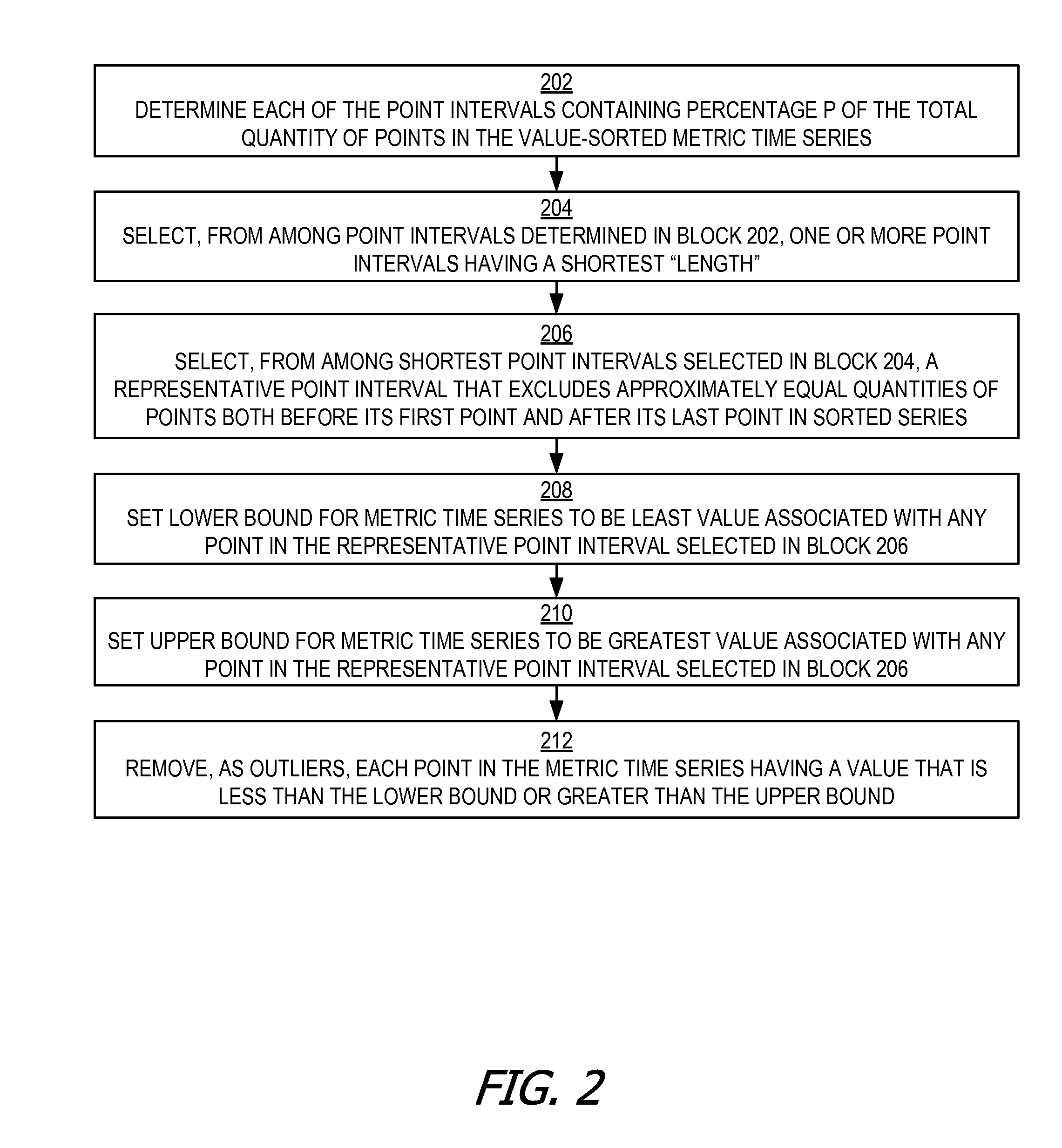
Metric time series correlation by outlier removal based on maximum concentration interval
InactiveUS20160092516A1Good correlationImprove representationDigital data information retrievalDigital data processing detailsMetric timeComputer science
A correlation relationship between two metric time series is determined after removing the impact of outlying metric values (“outliers”) that are unimportant for analytical purposes. Each of the metric time series can represent values of different system metrics obtained by mining data gathered through the monitoring of cloud deployments. The outliers can be determined based on a maximum concentration interval of the data. Removing the impact of the outliers enhances the correlation of the metric time series and provides a better representation of the correlation relationship.
Owner:ORACLE INT CORP
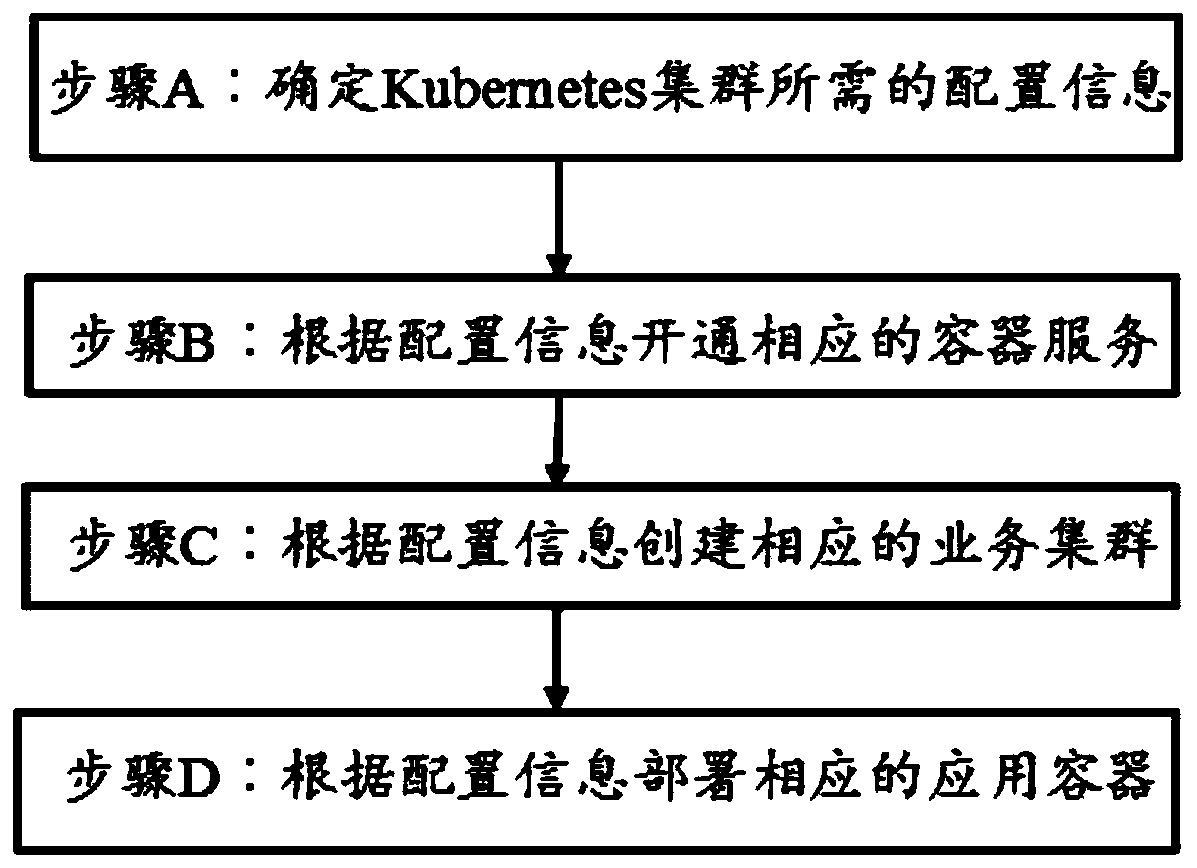
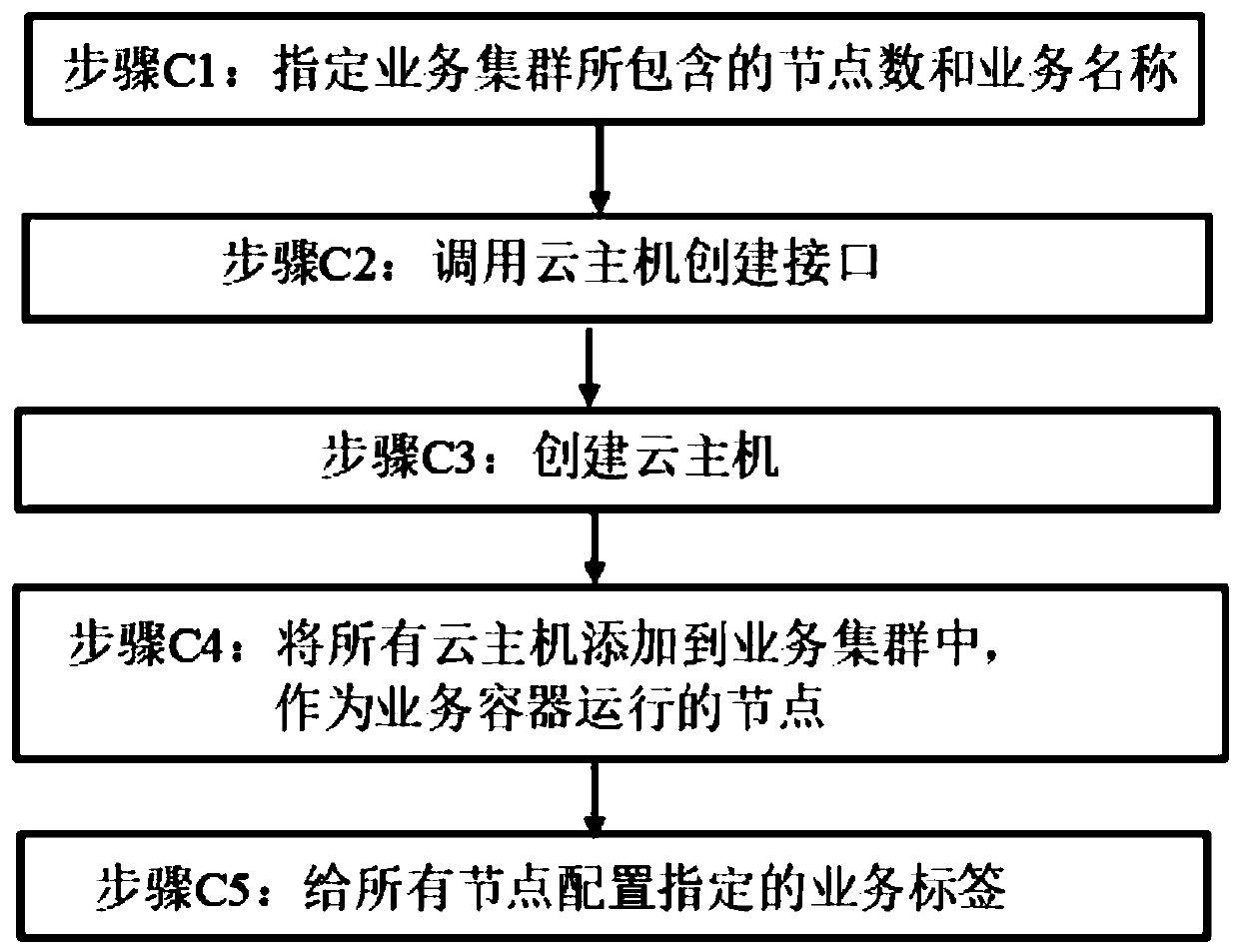
Management method and device based on Kubernetes cluster and computer readable storage medium
PendingCN110531987AEasy to manageResource allocationData switching networksDistributed computingCloud deployment
The invention relates to the technical field of cloud deployment, and provides a management method and device based on a Kubernetes cluster and a computer readable storage medium. The method comprisesthe following steps: determining configuration information required by the Kubernetes cluster, opening a container service, creating a service cluster, and deploying an application container; whereinthe step of opening the container service comprises the step of creating a control cluster in a specified VPC, and the configuration information comprises configuration information of basic resources, configuration information of a cluster scale, configuration information of a cluster network and configuration information of Kubernetes applications. The technical problem of how to switch from cloud host deployment to containerized deployment is solved. By means of the technical scheme, only the service cluster needs to be created, containerized services can be deployed in the service cluster,a user does not need to master professional knowledge of Kubernetes, the learning cost of the user is reduced, and service management is facilitated.
Owner:PING AN TECH (SHENZHEN) CO LTD
Indentifying service dependencies in a cloud deployment
Embodiments relate to systems and methods for identifying service dependencies in a cloud deployment. In particular, a deployment module can receive usage data from a host cloud comprising data related to end user operation of a set of services in the host cloud as well as service dependencies among the set of services. In embodiments, the deployment module can determine candidate target clouds in which to deploy the set of services. Further, in embodiments, the deployment module can determine whether the candidate target clouds have a capacity to support the set of services, as well as whether services within the candidate target clouds are compatible based on the service dependencies.
Owner:RED HAT
Application-based security rights in cloud environments
ActiveUS20170041347A1Optimization rangeTransmissionProgram/content distribution protectionApplication softwareService provisioning
This disclosure provides the ability for a cloud application to specify its security requirements, to ability to have those requirements evaluated, e.g., against a specific cloud deployment environment, and the ability to enable the application to control a cloud-based security assurance service to provision additional security technology in the cloud to support deployment (or re-deployment elsewhere) of the application if the environment does not have the necessary topology and security resources deployed. To this end, the application queries the service by passing a set of application-based security rights. If the security capabilities provided by the security assurance service are sufficient or better than the application's security rights, the application functions normally. If, however, the security environment established by the security assurance service is insufficient for the application, the application is afforded one or more remediation options, e.g., issuing a request to upgrade the security environment, or the like.
Owner:HCL TECH LTD
Assessment of best fit cloud deployment infrastructures
ActiveUS9813318B2Good serviceEfficient and effectiveFinanceBuying/selling/leasing transactionsApplication softwareData mining
A system configured to facilitate brokering hybrid cloud services selects information requests for characterizing an information technology application. The system responses to the information requests and determines a plurality of sets of the responses each used for deriving a value of a respective one of a plurality of factor functions. The system determines a plurality of assessment results each derived using values for of a respective set of the factor functions. Each one of the assessment results characterizes a respective aspect of deploying the information technology application within a cloud environment.
Owner:HCL TECH LTD
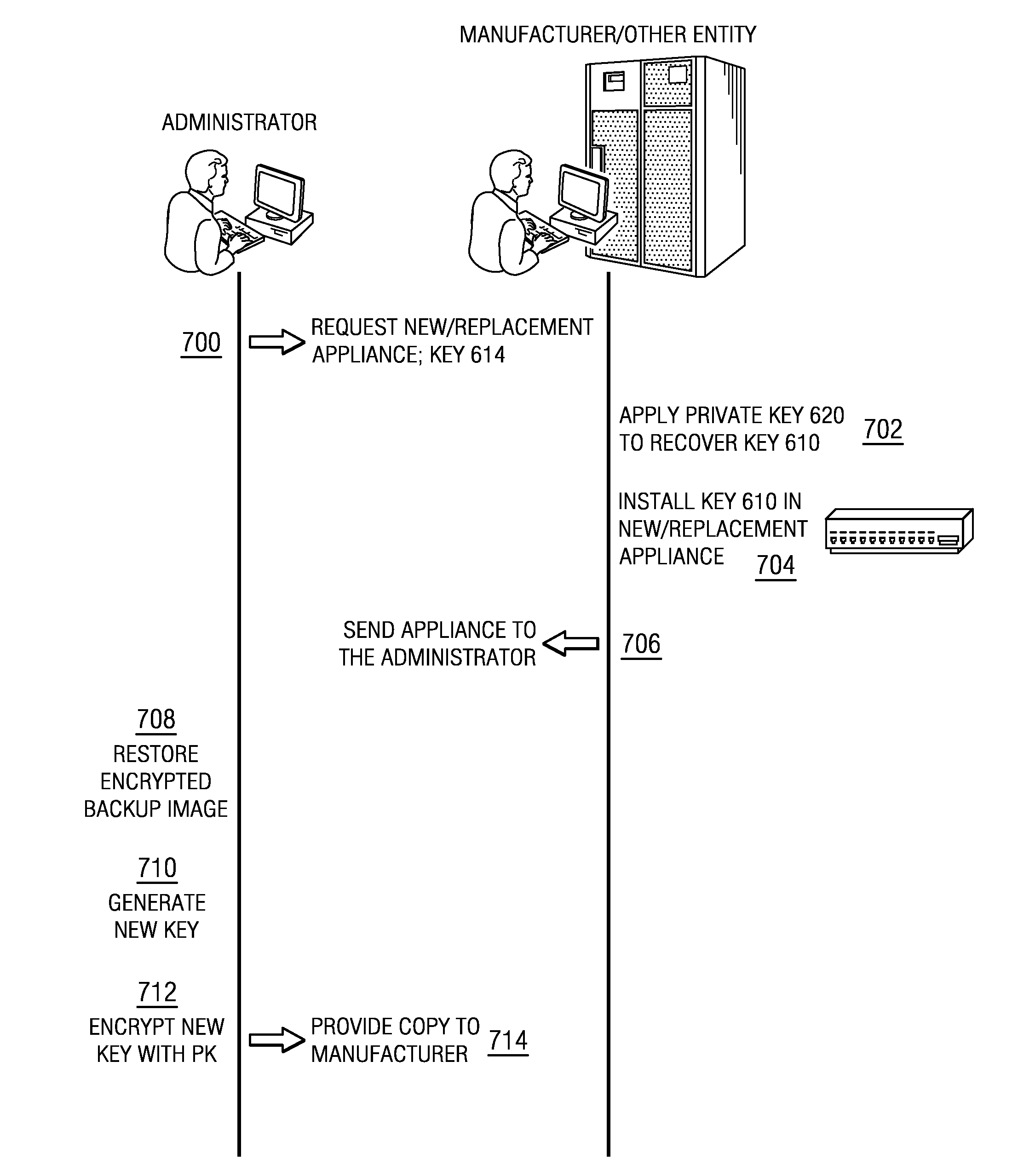
Backup and restore in a secure appliance with integrity and confidentiality
A cloud deployment appliance includes a key stored internally and that is used during restore to decrypt encrypted backup images. That key is not available to an administrator of the appliance; instead, the administrator receives a “value” that has been generated externally to the appliance and, in particular, by applying a public key of a public key pair to the key. The value is possessed by the administrator, but it does not expose the key. Upon a given occurrence, such as a disk failure in the appliance, the administrator uses the value to obtain” the key, which is then used to restore an encrypted backup image. The key is obtained by having the administrator provide the value to an entity, e.g., the appliance manufacturer, who then recovers the key for the administrator (by applying the private key of the public key pair).
Owner:DROPBOX
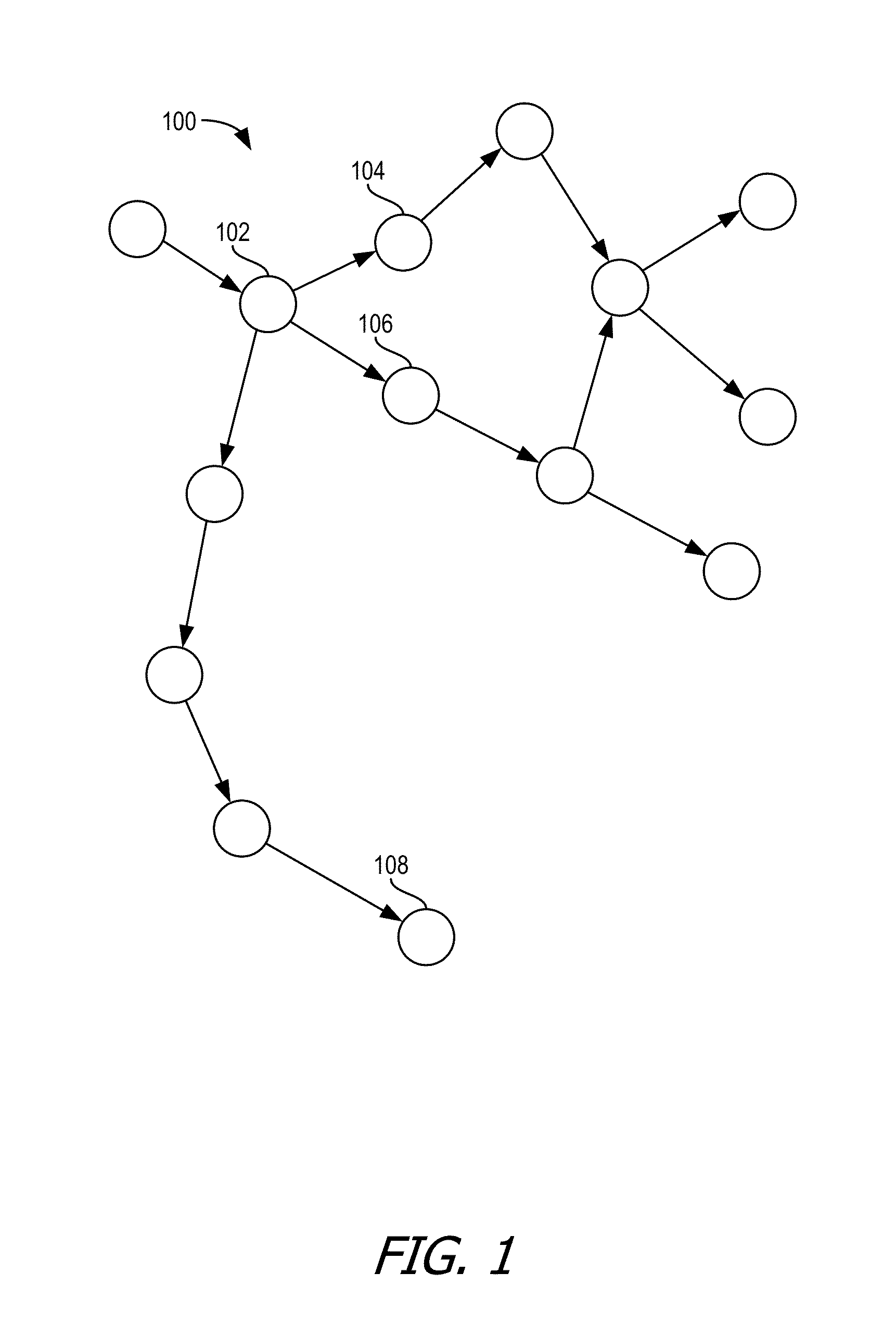
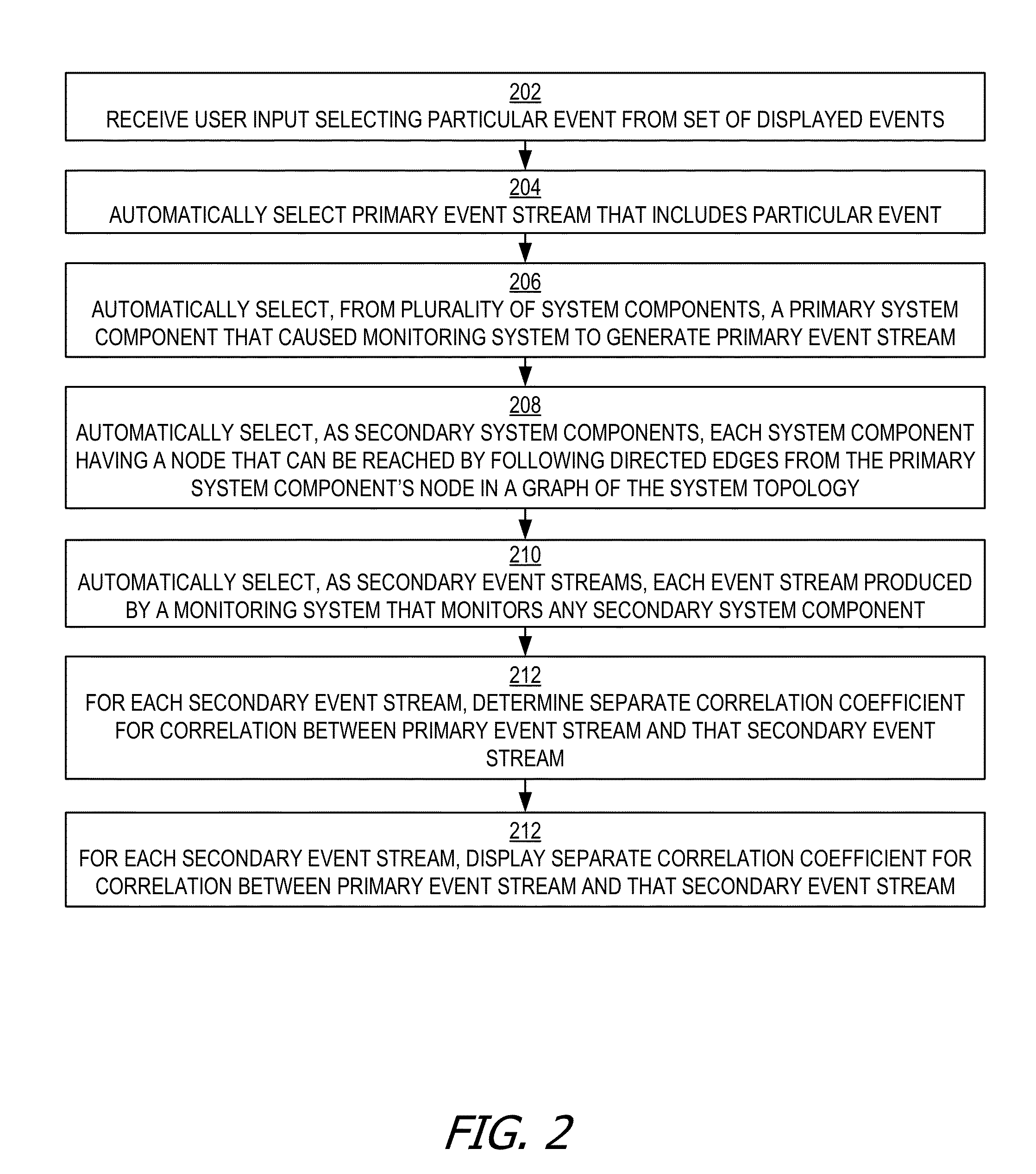
Statistical pattern correlation of events in cloud deployments using codebook approach
ActiveUS20160094422A1Improve insightsGood informationDigital computer detailsData switching networksMonitoring systemSystem topology
Correlations between patterns of events generated by various separate components within a cloud deployment are statistically determined. The determinations of the correlations can be based on dependencies between the components as indicated by a system topology graph including the components. The patterns correlated can be patterns of events from event streams generated by monitoring systems that monitor the components. The events in the event streams can represent changes over time in component state, behavior, or problem occurrence. Because the quantity of components within such a cloud deployment can be enormous, the quantity of events generated by the monitoring systems over a significant period of time can be voluminous.
Owner:ORACLE INT CORP +1
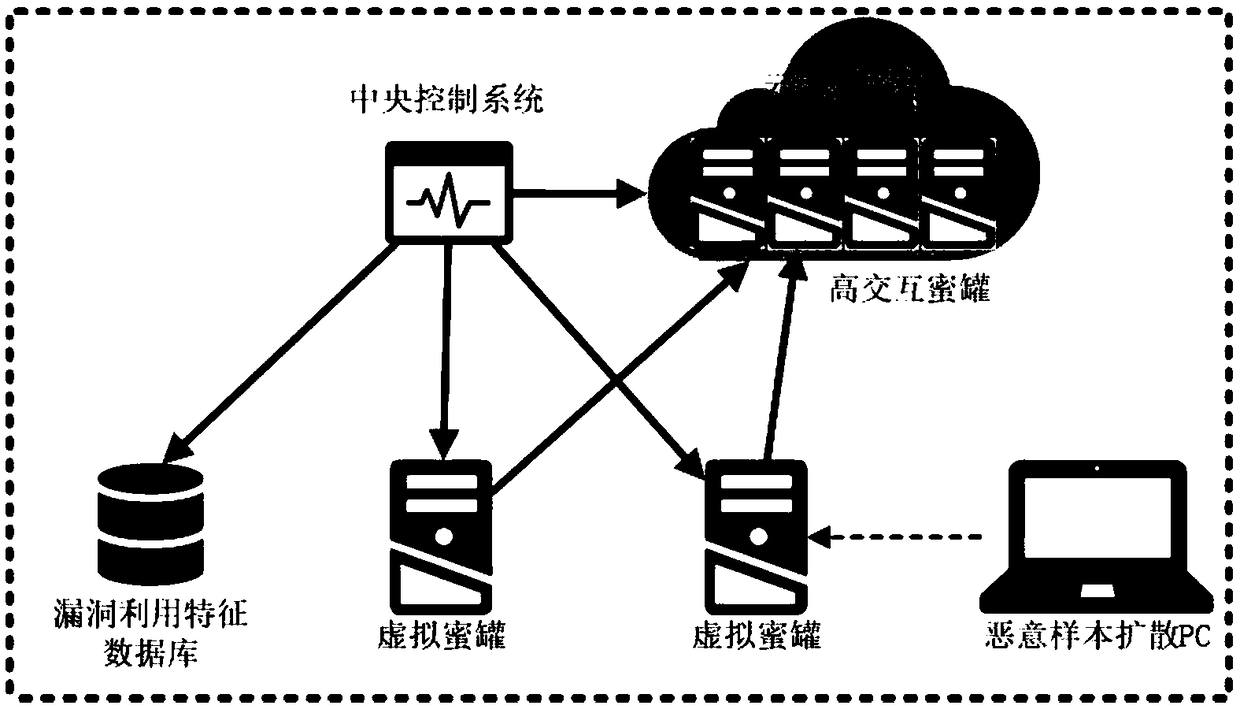
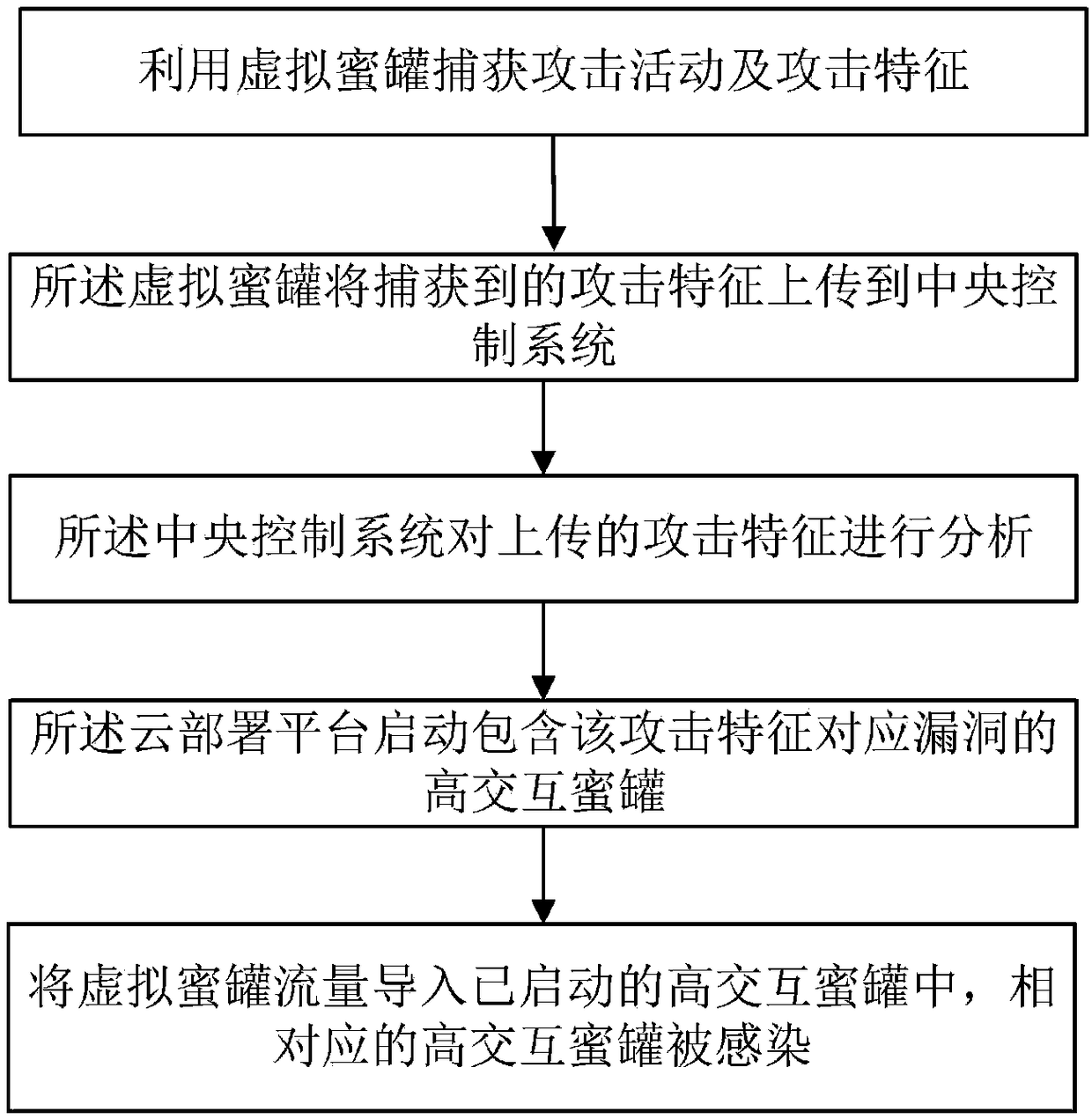
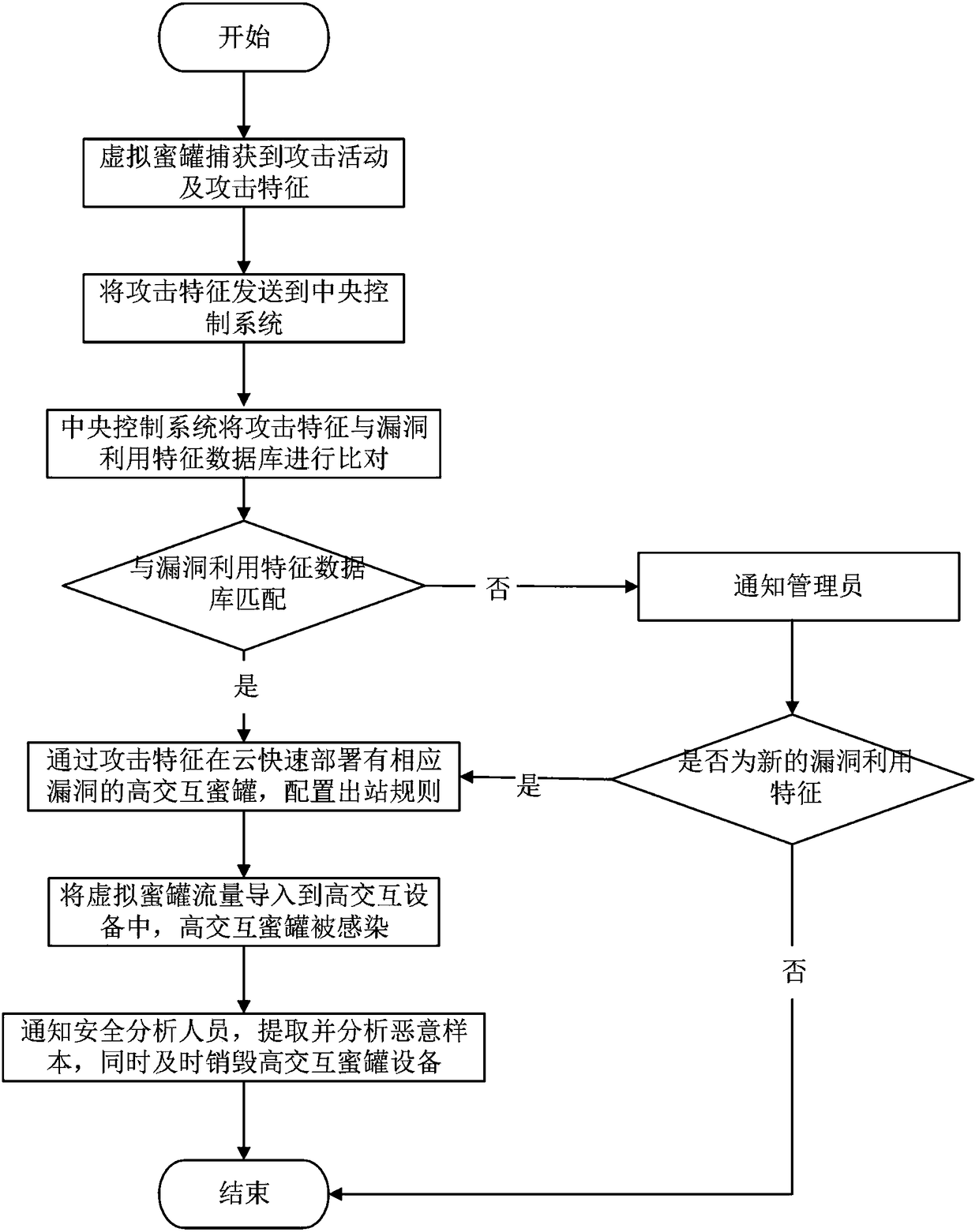
Device and method for specifically and dynamically deploying and capturing malicious samples by using honeypot
The application relates to a device and a method for specifically and dynamically deploying and capturing malicious samples by using a honeypot. The device comprises a virtual honeypot, a central control system and a cloud deployment platform. The method comprises the following steps: capturing attack activities and attack features by using the virtual honeypot; uploading the captured attack features to the central control system by the honeypot; analyzing the uploaded attack features by the central control system; starting a high interaction honeypot of vulnerabilities corresponding to the attack features by the cloud deployment platform; and importing virtual honeypot traffic into the started high interaction honeypot, wherein the corresponding high interaction honeypot is infected. According to the device and the method, a low interaction honeypot cooperates with the high interaction honeypot based on a vulnerability service or system; the malicious samples are detected rapidly by using the low interaction honeypot; the high interaction honeypot based on the vulnerability service or system is deployed rapidly by the cloud deployment platform; and the high interaction honeypot based on the vulnerability service or system cooperates with the low interaction honeypot to realize capturing of the malicious samples.
Owner:北京经纬信安科技有限公司
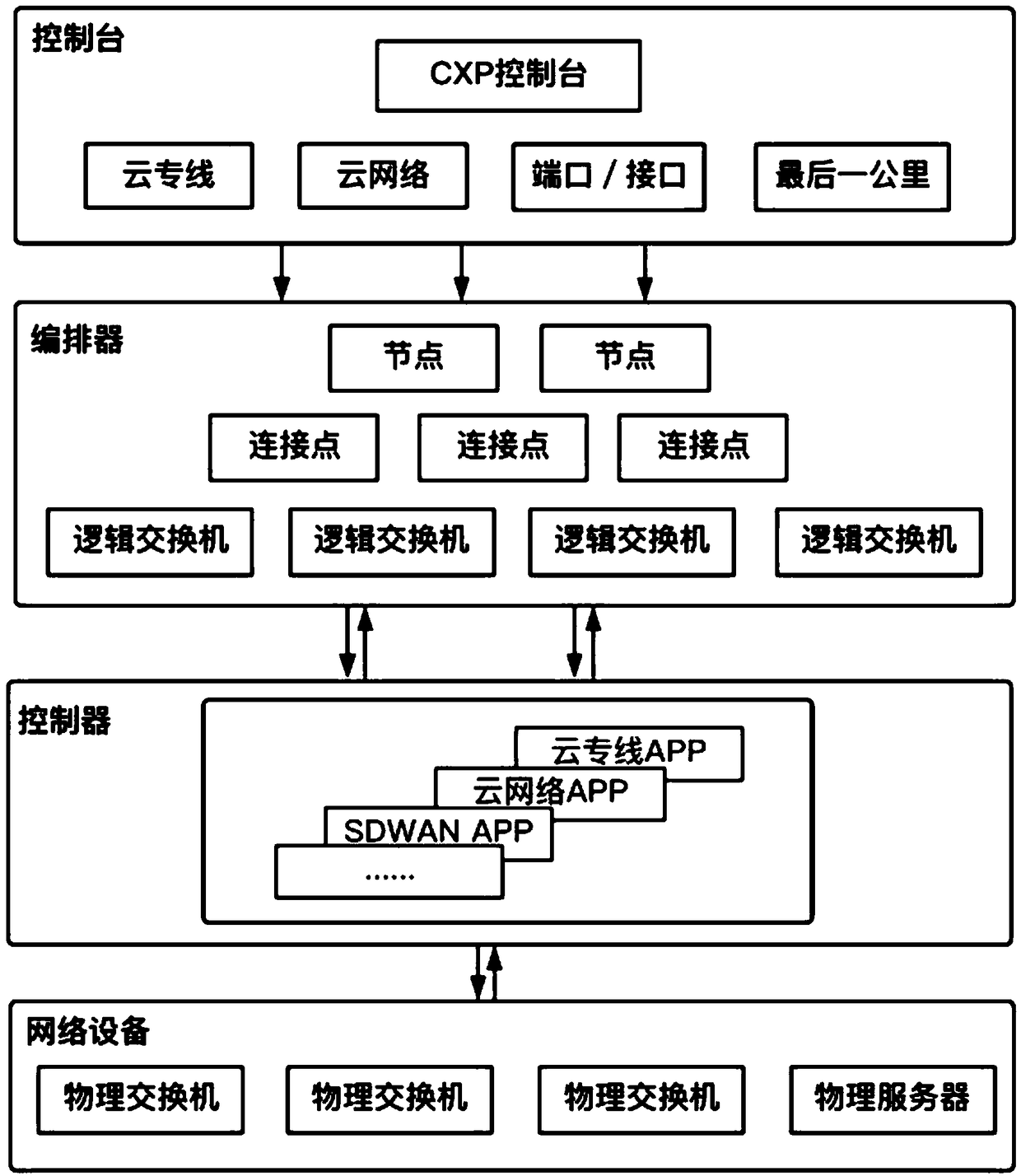
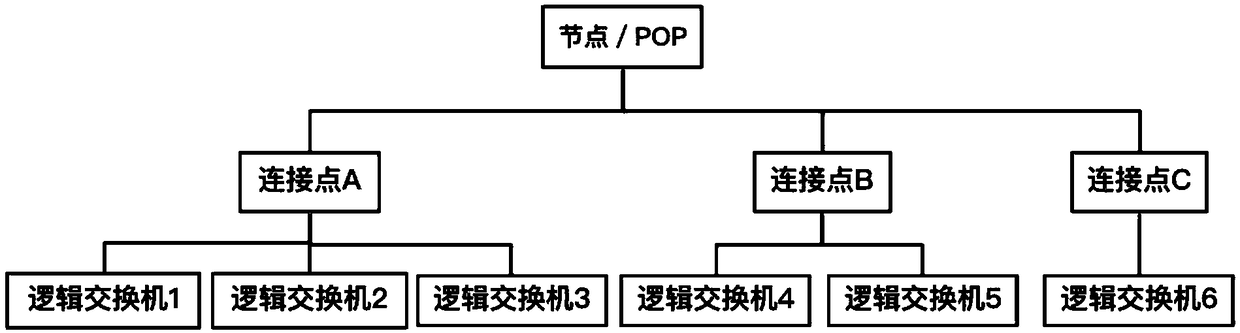
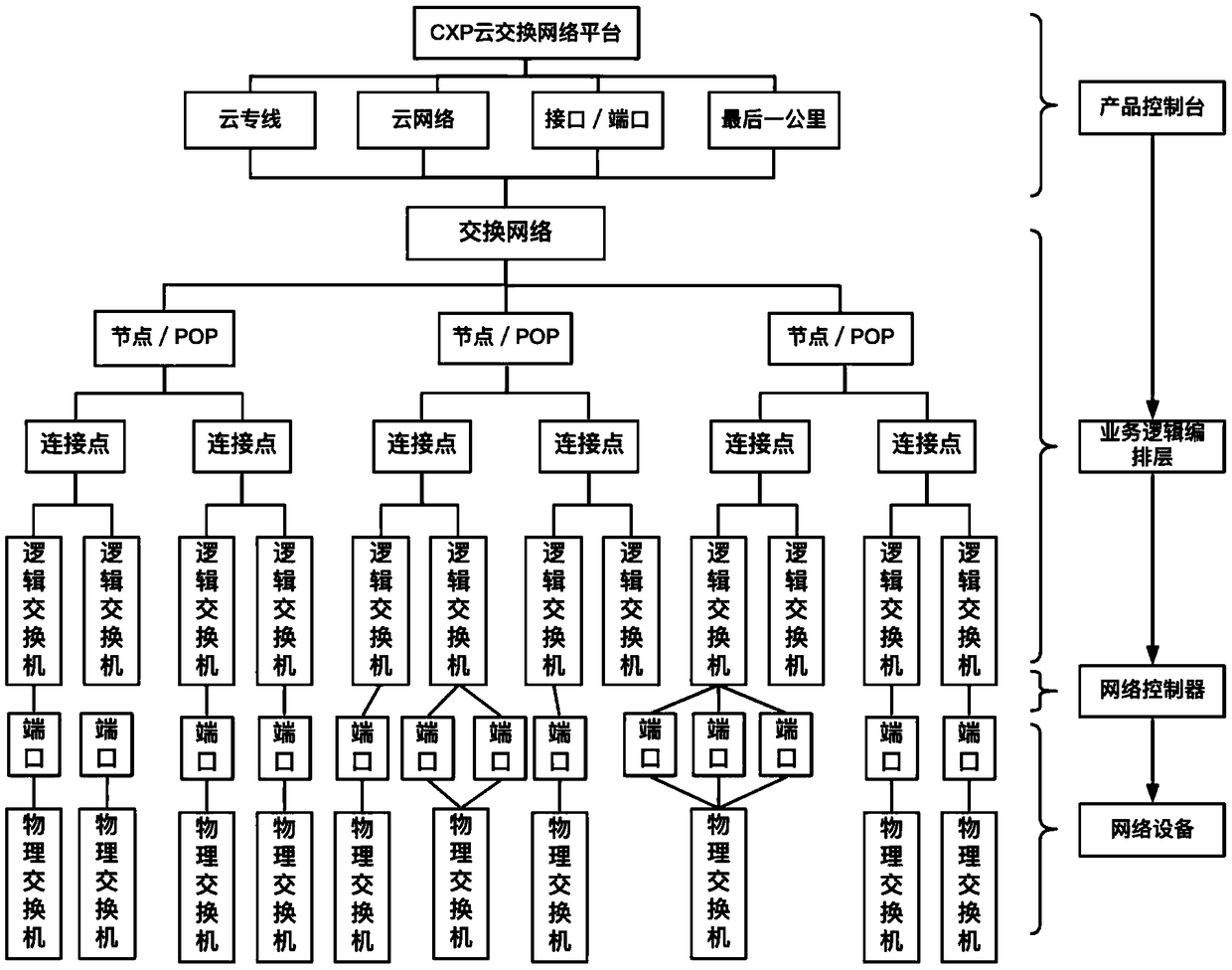
Cloud exchange network platform based on SDN/NFV
InactiveCN109218099AEfficient network connection serviceSecure Internet Connection ServiceData switching networksNetwork ConvergenceExchange network
The invention provides a cloud exchange network platform based on SDN / NFV. The cloud exchange network platform is used for constructing a private network for enterprises, which is used for realizing converged interconnection and hybrid cloud of various regional networks within the enterprises. The cloud exchange network platform comprises a console, which is used for receiving demand information input by a user for network configuration; An orchestrator, configured to determine a control strategy and a node corresponding to the control strategy according to the demand information; The controller is used for automatically configuring the network according to the control strategy sent by the choreographer and the node corresponding to the control strategy; A network device for deploying thenode, switch, or server to enable the network configured by the controller to support services of different access attributes. The cloud exchange network platform mentioned above can help enterprisesto quickly build private networks, realize enterprise network convergence, and provide a network environment for hybrid cloud deployment.
Owner:犀思云(苏州)云计算有限公司
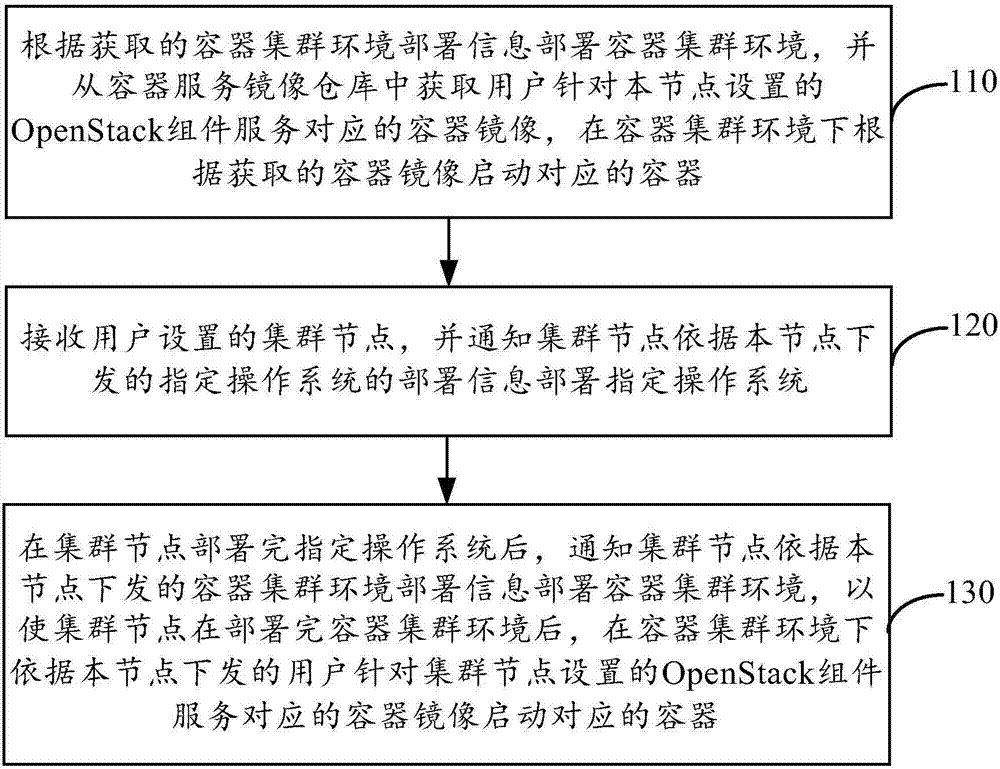
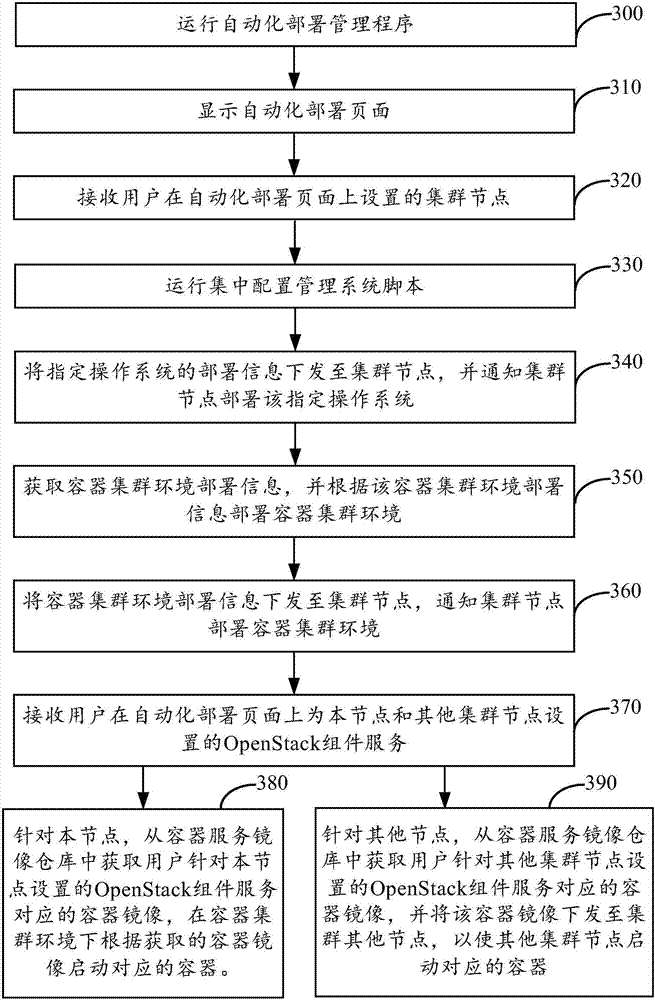
Private cloud deployment method and private cloud deployment device
ActiveCN106878385AImprove stabilityImprove acceleration performanceInput/output to record carriersData switching networksOperational systemNode deployment
The invention provides a private cloud deployment method. The method comprises steps: a container cluster environment is deployed according to acquired container cluster environment deployment information, a container mirror corresponding to OpenStack module service set for the node by a user is acquired from a container service mirror warehouse, and a corresponding container is started according to the acquired container mirror in the container cluster environment; a cluster node set by the user is received, and the cluster node is announced to deploy a specified operation system according to the specified operation system deployment information issued according to the node; and after the cluster node deploys the specified operation system, the cluster node is announced to deploy the container cluster environment according to the container cluster environment deployment information issued according to the node, and thus, after the cluster node deploys the container cluster environment, the corresponding container is started. Thus, a cluster mode and a container technology can be adopted for private cloud deployment, the stability and the expansibility for the private cloud deployment can be improved, and the private cloud deployment efficiency is improved.
Owner:NEW H3C TECH CO LTD
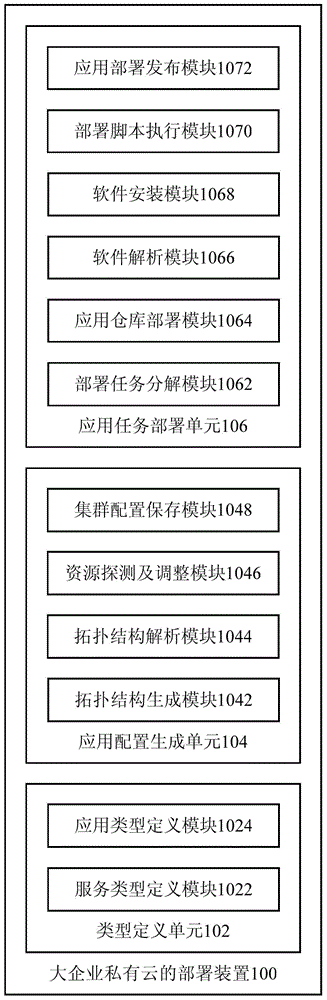
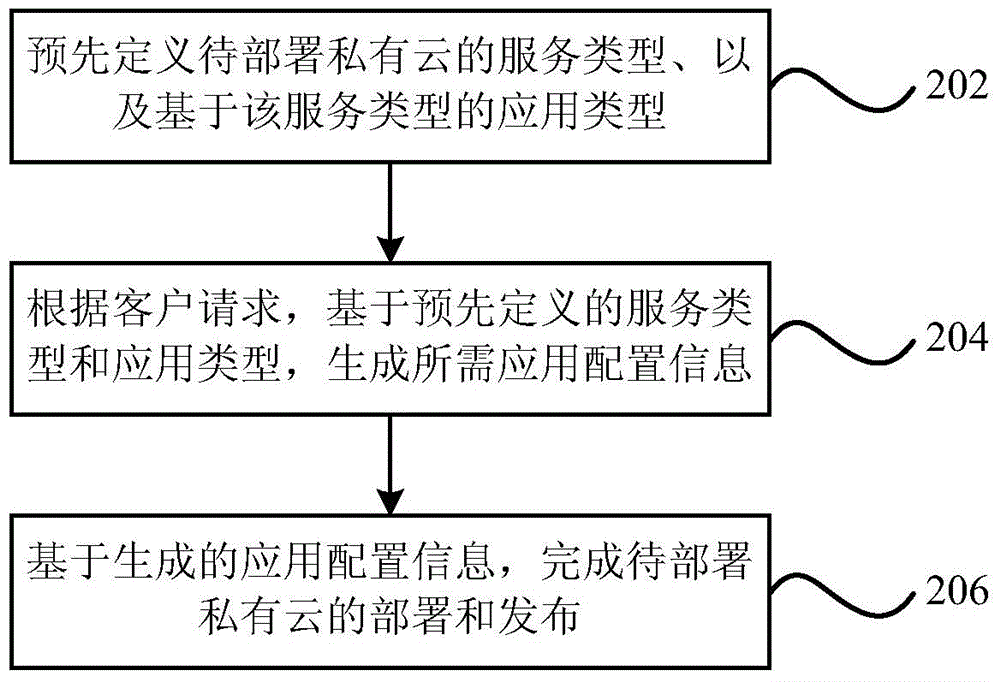
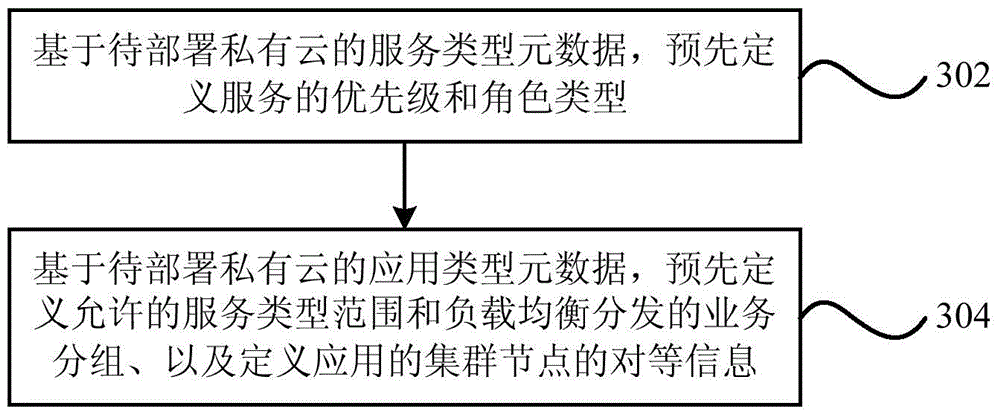
Deployment apparatus and deployment method for large enterprise private cloud
The present invention provides a deployment apparatus for a large enterprise private cloud. The apparatus includes: a type defining unit, which is used to pre-define a service type of the private cloud to be deployed, and an application type based on the service type; an application configuration generating unit, which is used to generate required application configuration information based on the pre-defined service type and application type according to a client request; and an application task deployment unit, which is used to complete the deployment and release of the private cloud to be deployed based on the generated application configuration information. The present invention also provides a deployment method for the large enterprise private cloud. According to the technical scheme of the present invention, a multi-object type private cloud deployment is realized by a full utilization of a single object type based on an existing deployment method for the private cloud, and a universal and unified deployment thinking is established, wherein, the universal and unified deployment thinking faces to the development for the large enterprise private cloud participated by the multi-object type metadata.
Owner:YONYOU NETWORK TECH CO LTD
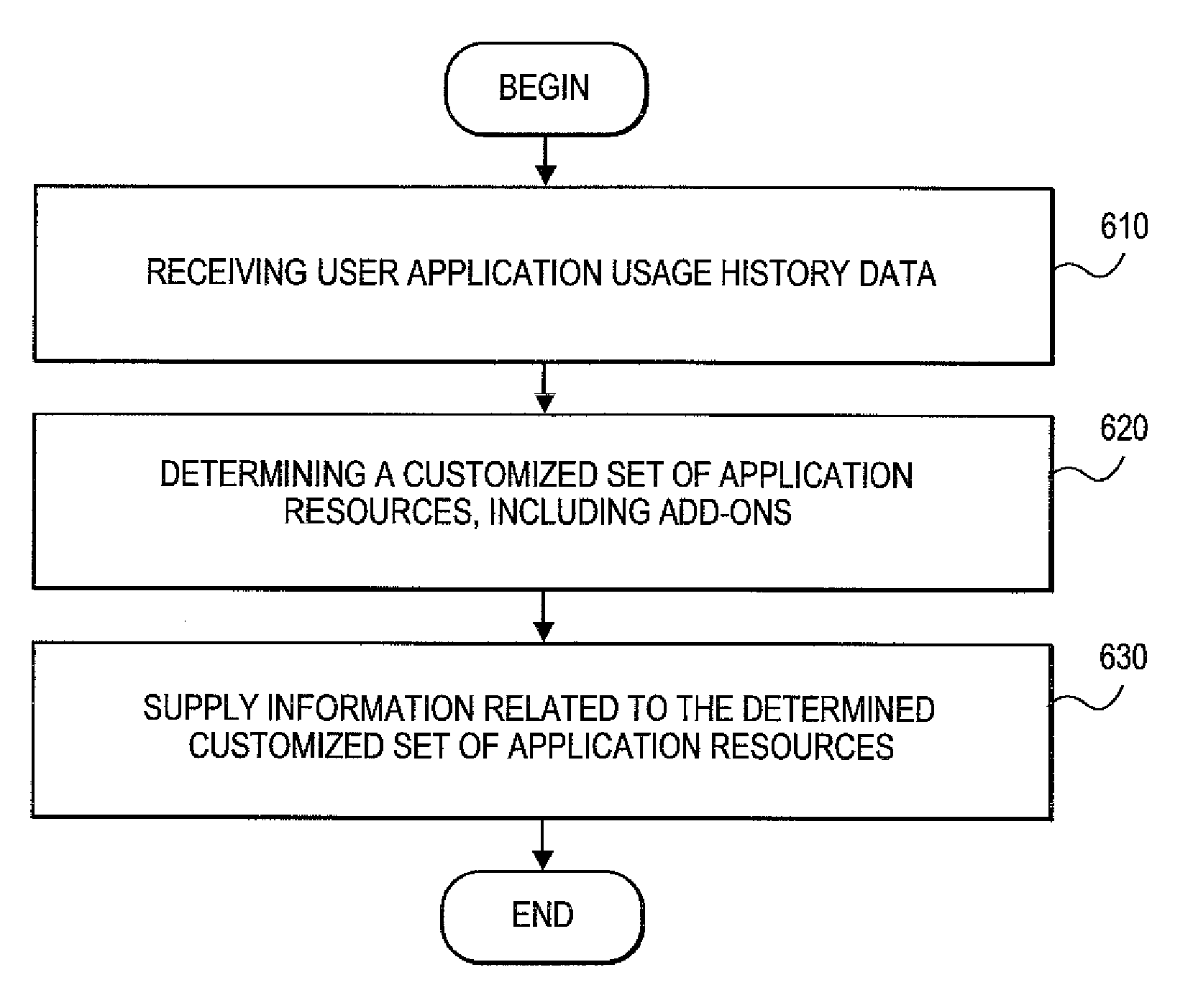
Generating customized build options for cloud deployment matching usage profile against cloud infrastructure options
A decision system for providing customized application build options to users of a cloud computing environment. The decision system can receive user usage history data and determine a customized set of application resources based on the usage history data. Information about the customized set of application resources can then be supplied to the user.
Owner:RED HAT
Automatic symptom data collection in cloud deployment
ActiveUS20180234288A1Non-redundant fault processingData switching networksData harvestingCollections data
Apparatuses, methods, and computer-readable media regard automatic symptom data collection in cloud deployment. The method includes detecting a failure, determining when to trigger symptom data collection for collecting information about the failure, and transmitting an indication of the triggering of the symptom data collection to a management function of the virtual network function.
Owner:NOKIA SOLUTIONS & NETWORKS OY
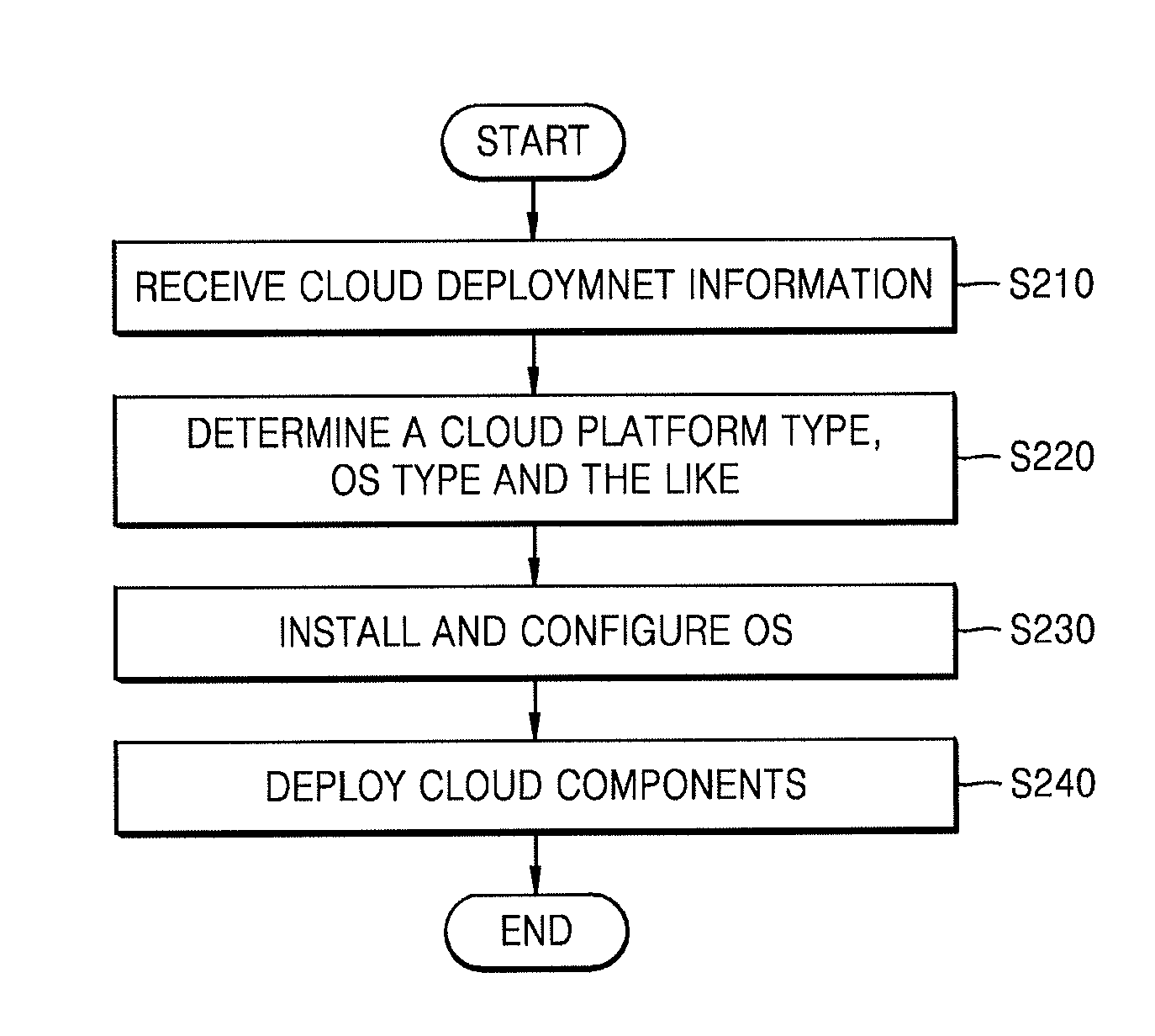
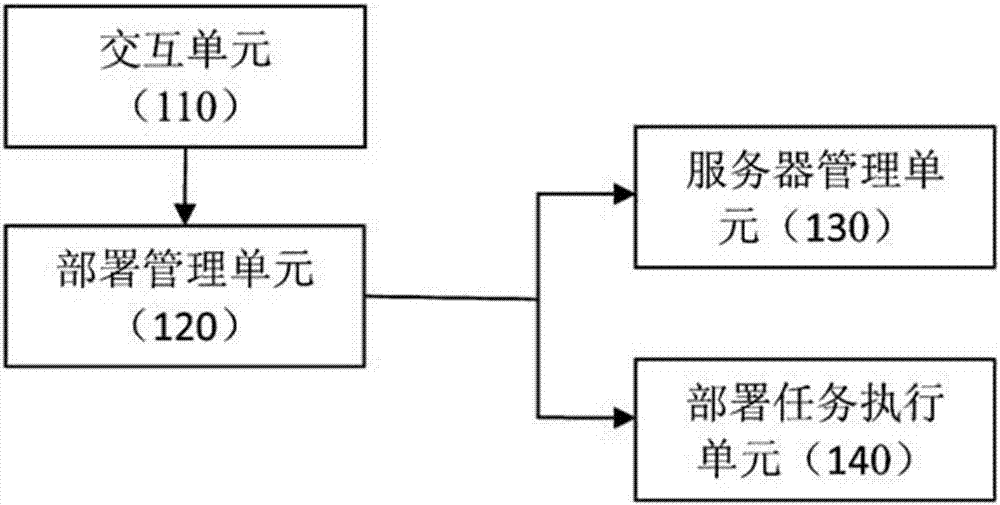
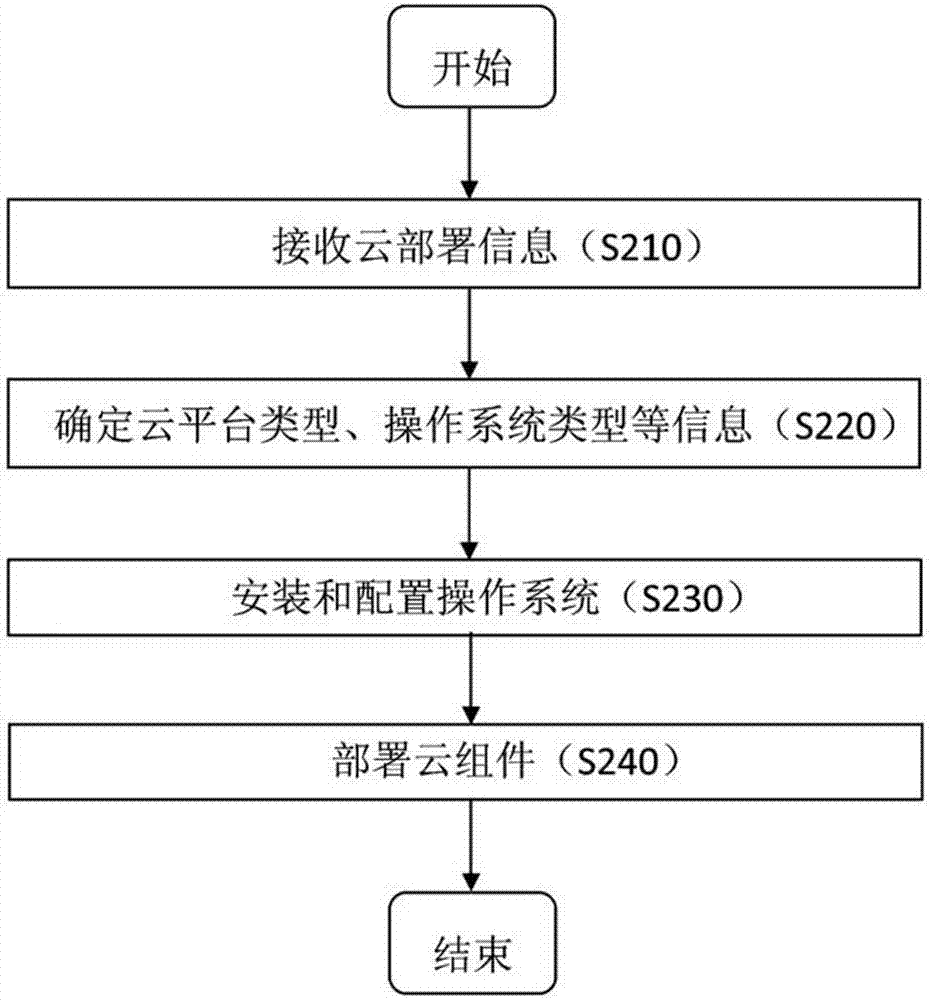
System and method for automatically deploying cloud
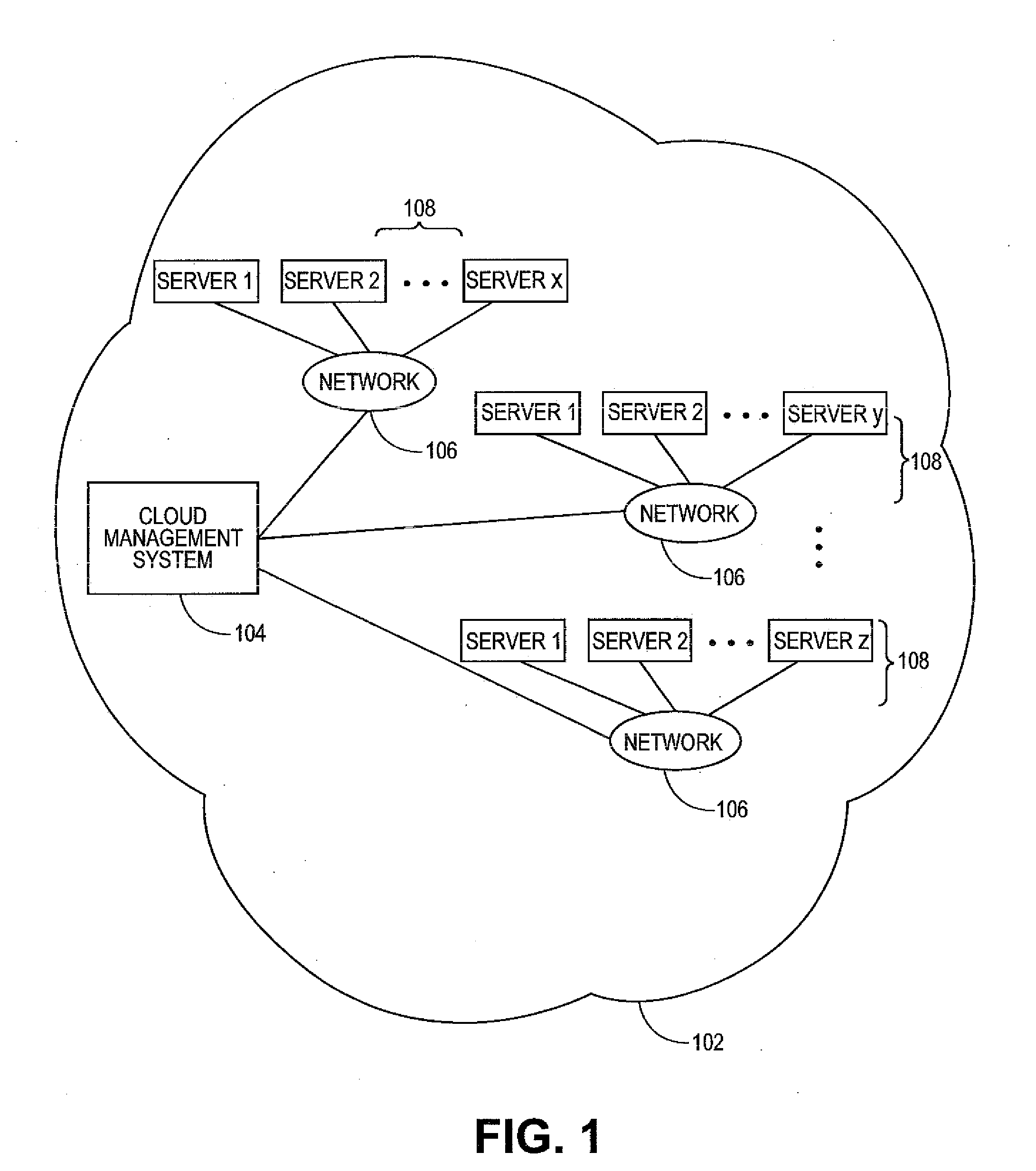
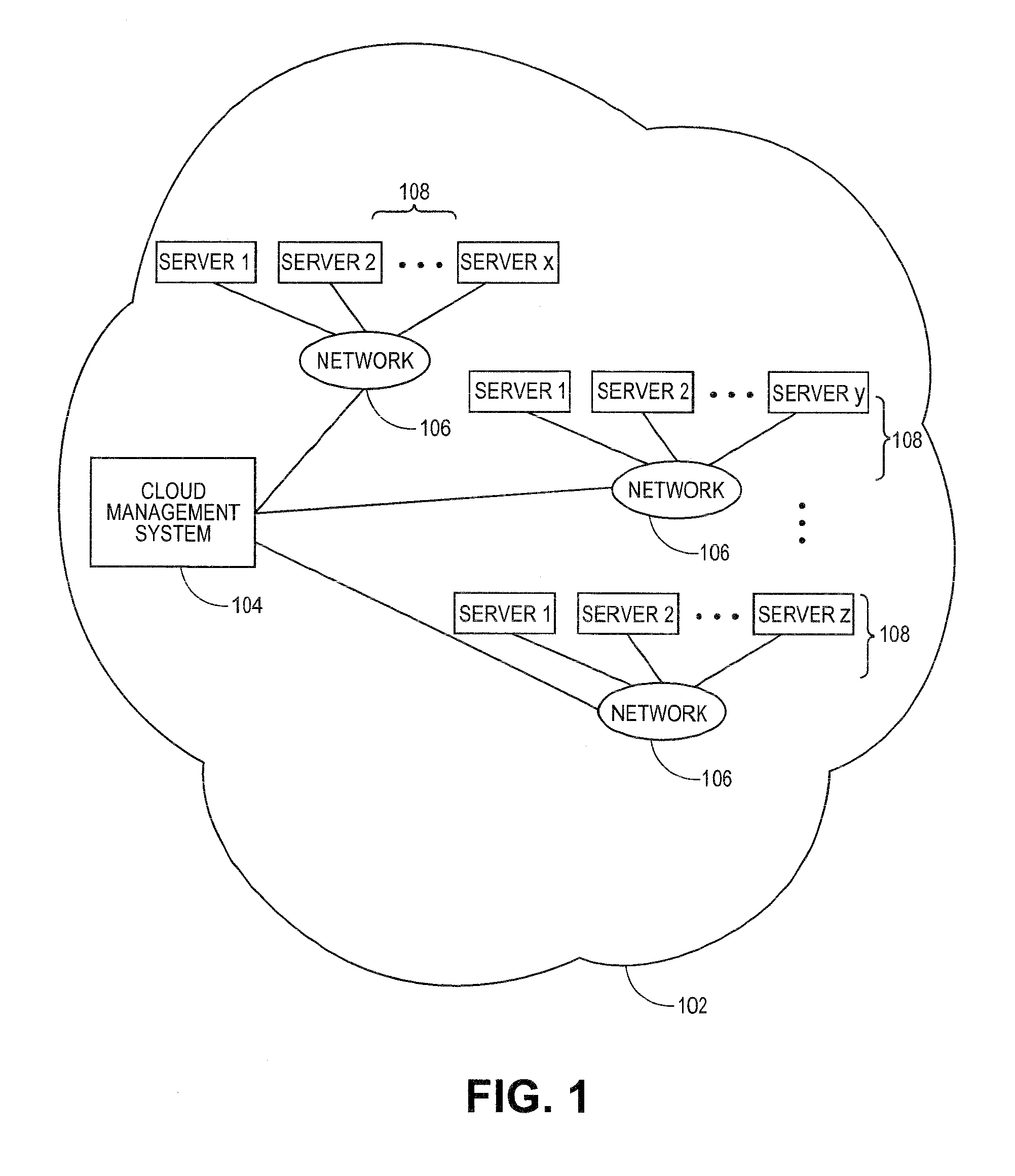
A system for automatically deploying a cloud includes an interface, a deployment manager, a server manager, and a deployment task executor. The interface receives cloud deployment information which includes a cloud platform type, an operating system (OS) type, at least one server at which cloud to be deployed, and a node type subordinate to the cloud platform type of the at least one server. The deployment manager determines cloud components matching the node type subordinate to the cloud platform type as cloud components to be deployed at the at least one server. The server manager pushes an OS installation file and a configuration file matching the OS type for installation at least one server. The deployment task executor deploys the determined cloud components at the at least one server.
Owner:SAMSUNG ELECTRONICS CO LTD
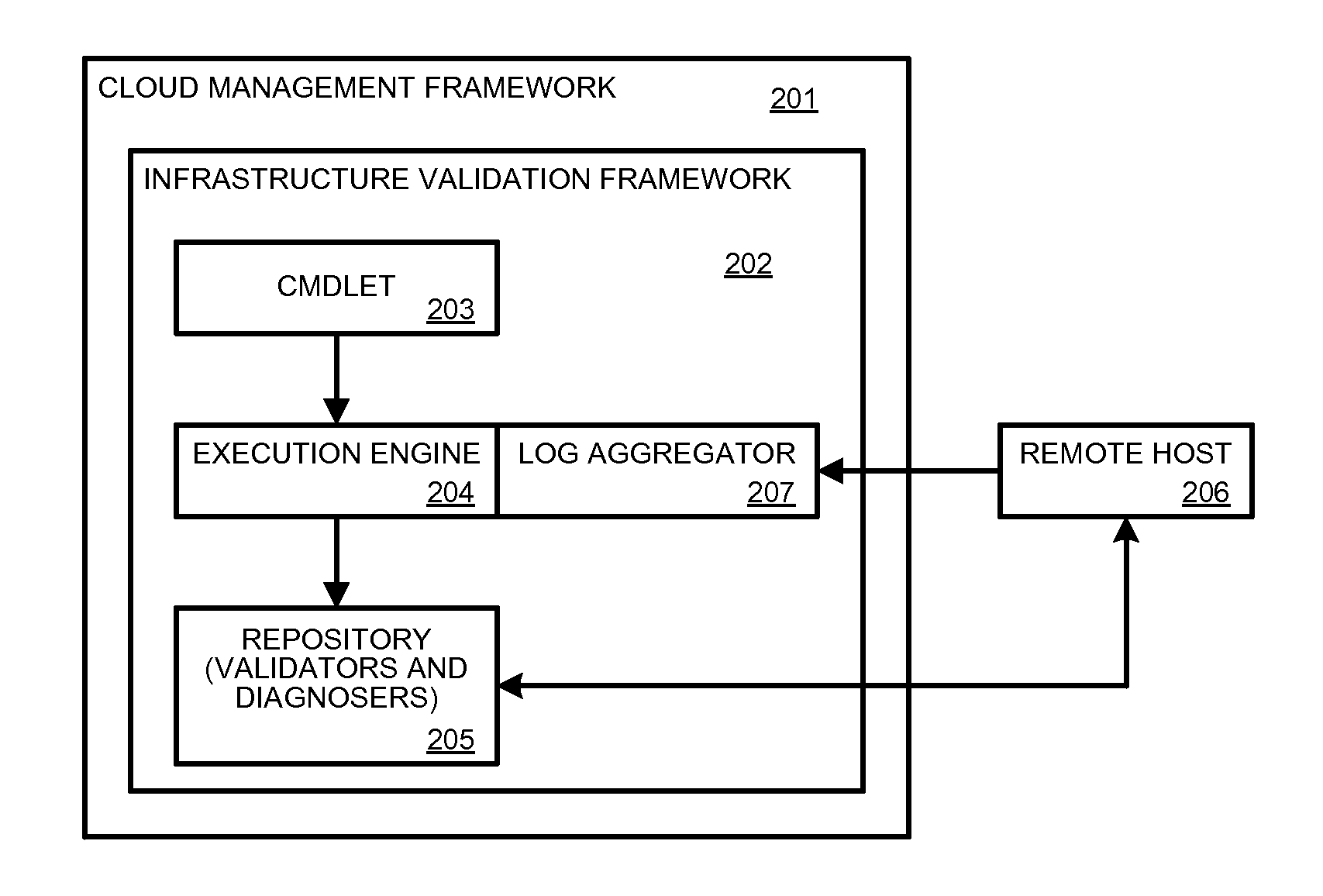
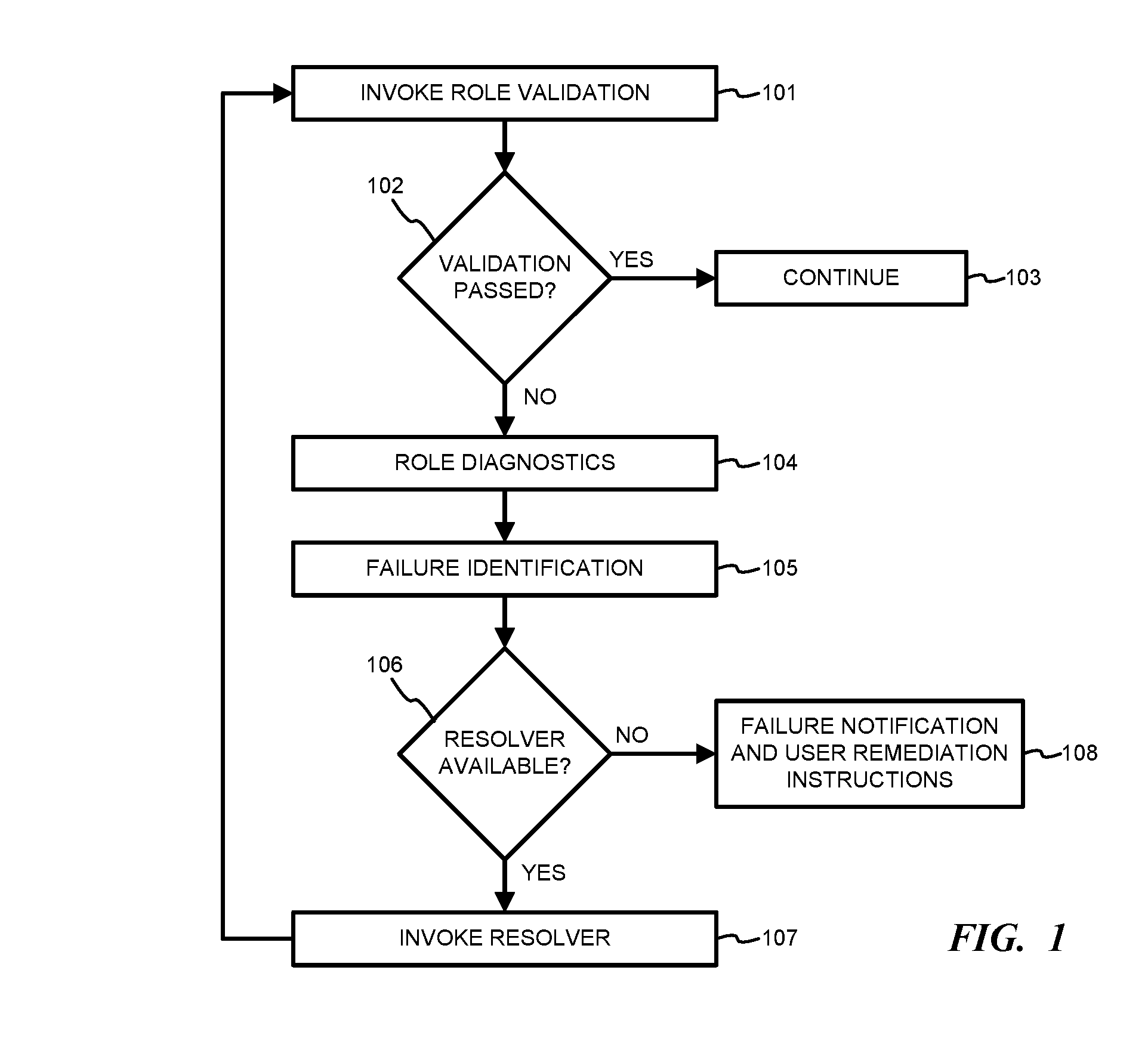
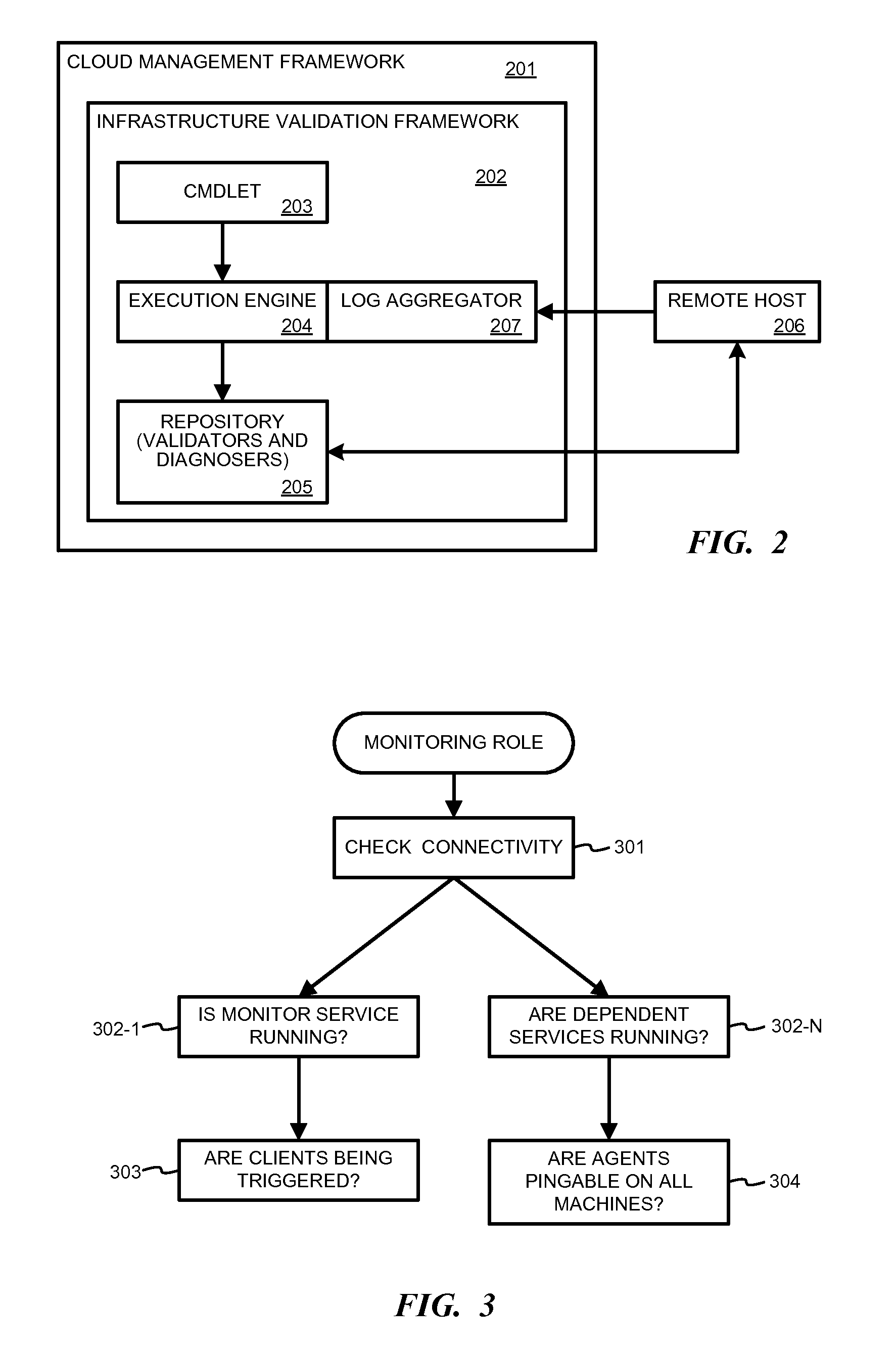
Cloud deployment infrastructure validation engine
ActiveUS9471474B2Quick installationSoftware testing/debuggingNon-redundant fault processingSelf-healingValidator
Embodiments of the invention provide a set of validators that can be used to determine whether an installation is operating within desired parameters and is in compliance with any requirements. The validators may be provided with a software application or release, for example, and may be run during and / or after installation to test the application operation. A set of self-healing operations may be triggered when faults are detected by the validators. This allows a software application to auto-diagnose and auto-self-heal any detected faults.
Owner:MICROSOFT TECH LICENSING LLC
Low-frequency crawler identification method and device
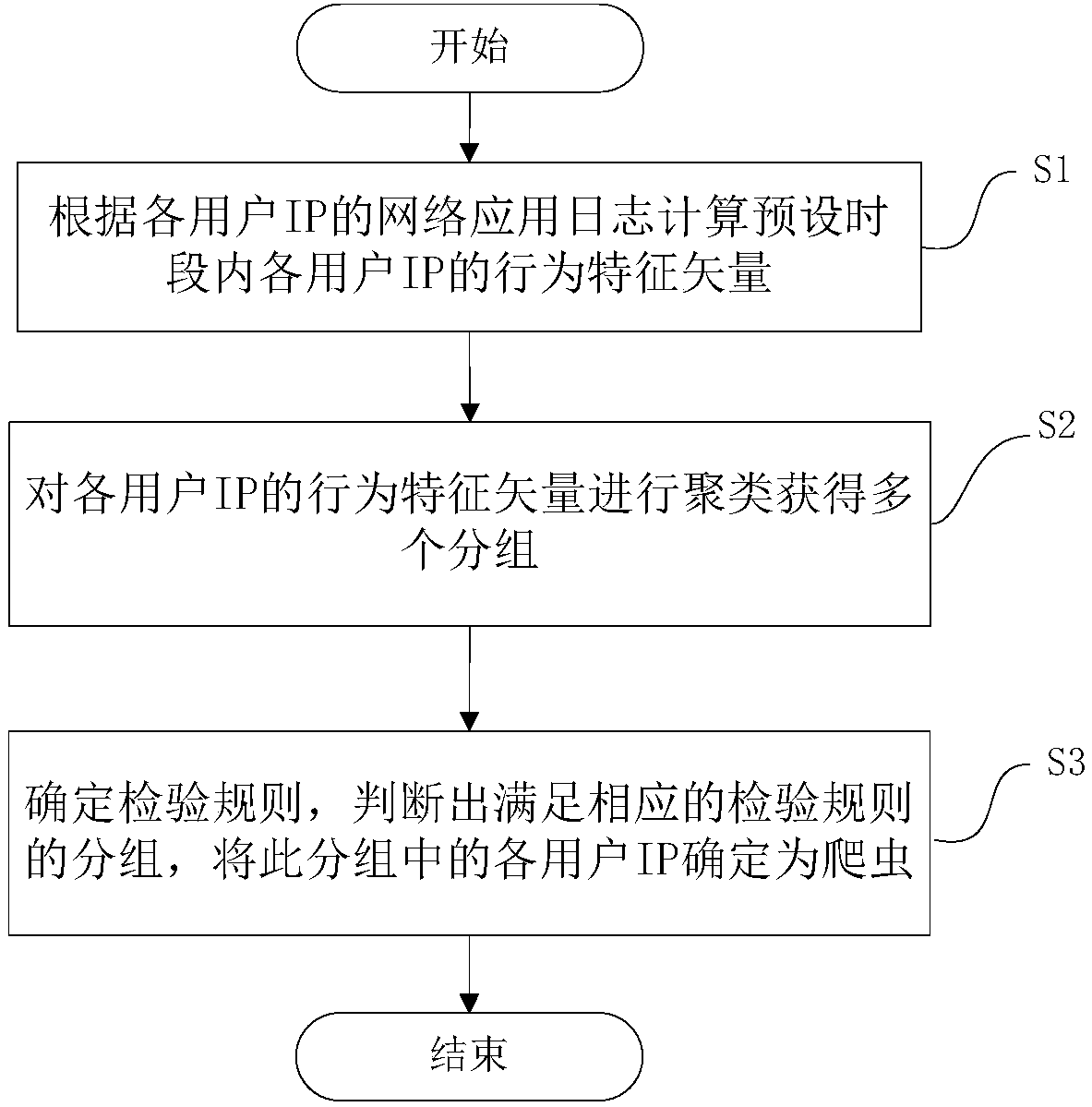
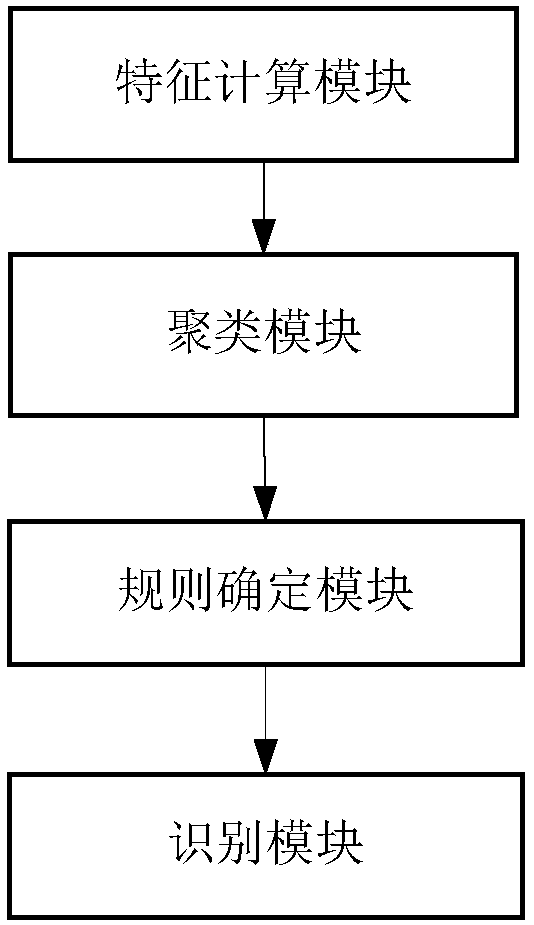
ActiveCN107800684AEfficient identificationAddressing Gang ThreatsTransmissionFeature vectorData mining
The invention discloses a low-frequency crawler identification method and device. The method comprises the following steps: computing a behavior feature vector of each user IP in preset time slot according to a network application log of each user IP, clustering the behavior feature vector of each user IP to acquire multiple clusters, judging out the cluster satisfying the corresponding inspectionrule, and determining each user IP in this cluster as the crawler. The device comprises a feature computing module, a clustering module, a rule determining module, and an identification module. Through the invention disclosed by the invention, the low-frequency crawler can be effectively identified, and the problem that the traditional security product cannot identity gang threat, low-frequency threat, relevancy threat and persistent threat can be solved; the public cloud or private cloud deployment is supported, the threat identification and blocking can be performed without changing networktopology and embedding any code; the butt-joint of custom blocking interface is supported, and the normal running of the original service cannot be influenced even if the deployment environment is completely switched off under the extreme case.
Owner:BEIJING SHU AN XINYUN TECH CO LTD
Automatic discovery and automatic deployment method of cloud host
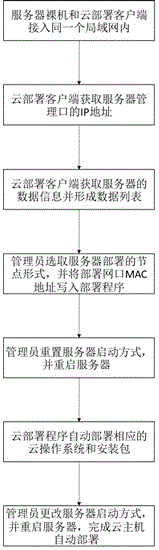
ActiveCN106790467AReduce manual transcriptionReduce the process of manually transcribing server informationBootstrappingProgram loading/initiatingIp addressClient-side
The invention provides an automatic discovery and automatic deployment method of a cloud host. The method comprises the following steps: a cloud deployment client monitors ARP broadcast information of a server in a local area network, analyzes an IP address of the server, logs in the server to obtain an MAC address of a server deployment network port, and writes the MAC address in a cloud deployment program, so that the cloud deployment program automatically deploy a corresponding cloud operation system and an installation package on a cloud deployment node according to the MAC address of the deployment network port, therefore the information of an administrator to manually record the information of the server is reduced, the installation of the operation system and the installation package is automatically accomplished, and the large-scale automatic discovery and automatic deployment of server bare computers are realized.
Owner:武汉白虹软件科技有限公司
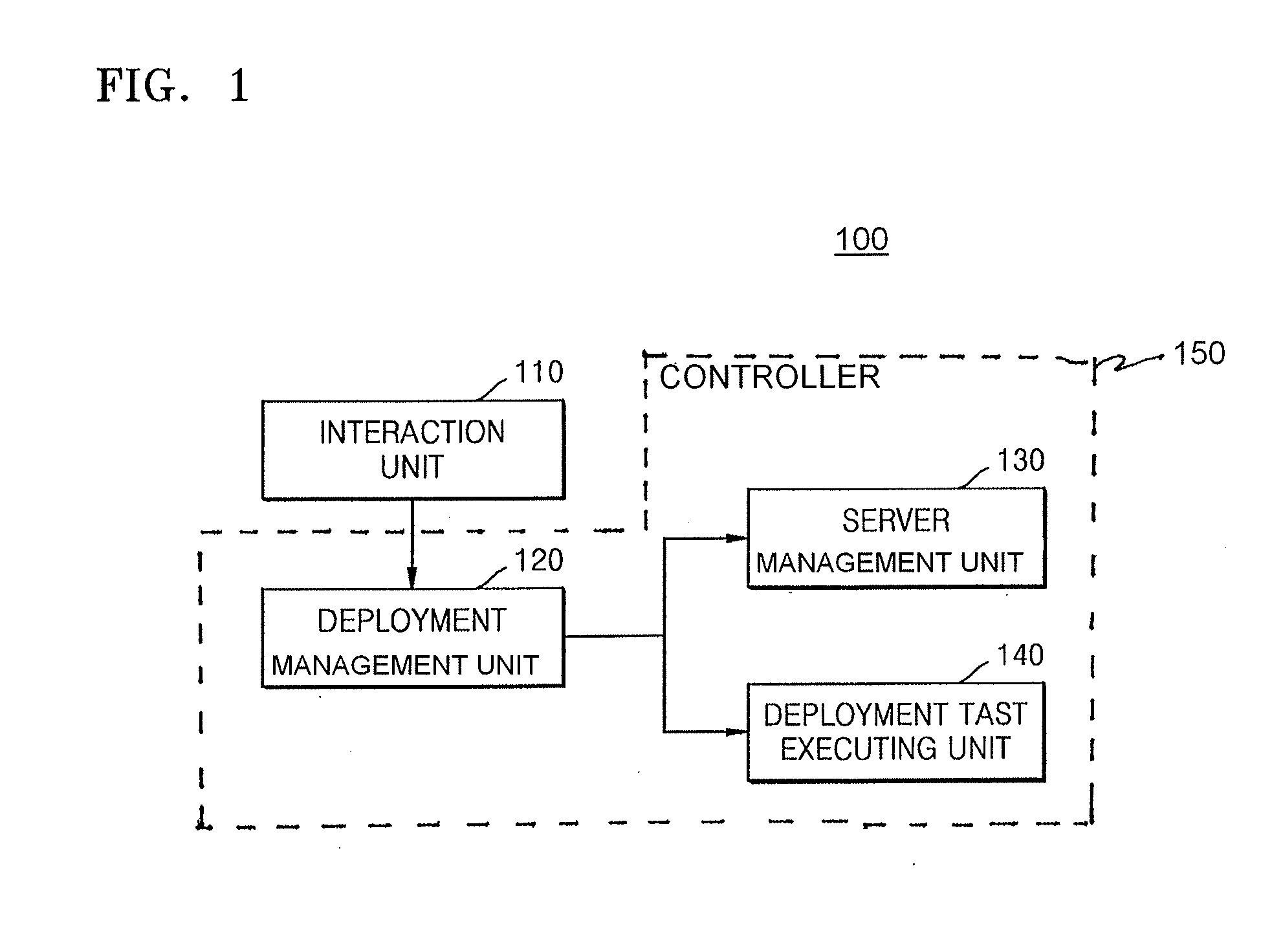
Cloud automated deployment system and method
InactiveCN106878334AImplement deploymentImprove good performanceTransmissionSoftware deploymentOperational systemExecution unit
The invention provides a cloud automated deployment system and method. The system comprises an interaction unit used for receiving cloud deployment information from a user; a deployment management unit used for determining the type of a cloud platform, the type of an operating system, a server which needs to deploy a cloud, the node type of the server under the cloud platform type based on the cloud deployment information, and determining a cloud component that is adapted to the node type under the cloud platform type as the cloud component needed to be deployed by the server; a server management unit used for pushing an installation file and a configuration file of the operating system that is adapted to the determined operating system type to the server which needs to deploy the cloud, so as to install and configure the operating system on the server which needs to deploy the cloud; and a deployment task execution unit used for deploying the determined cloud component on the server on which the operating system is installed and configured.
Owner:西安三星电子研究有限公司 +1
Software cross-cloud deployment method, computer device and storage medium
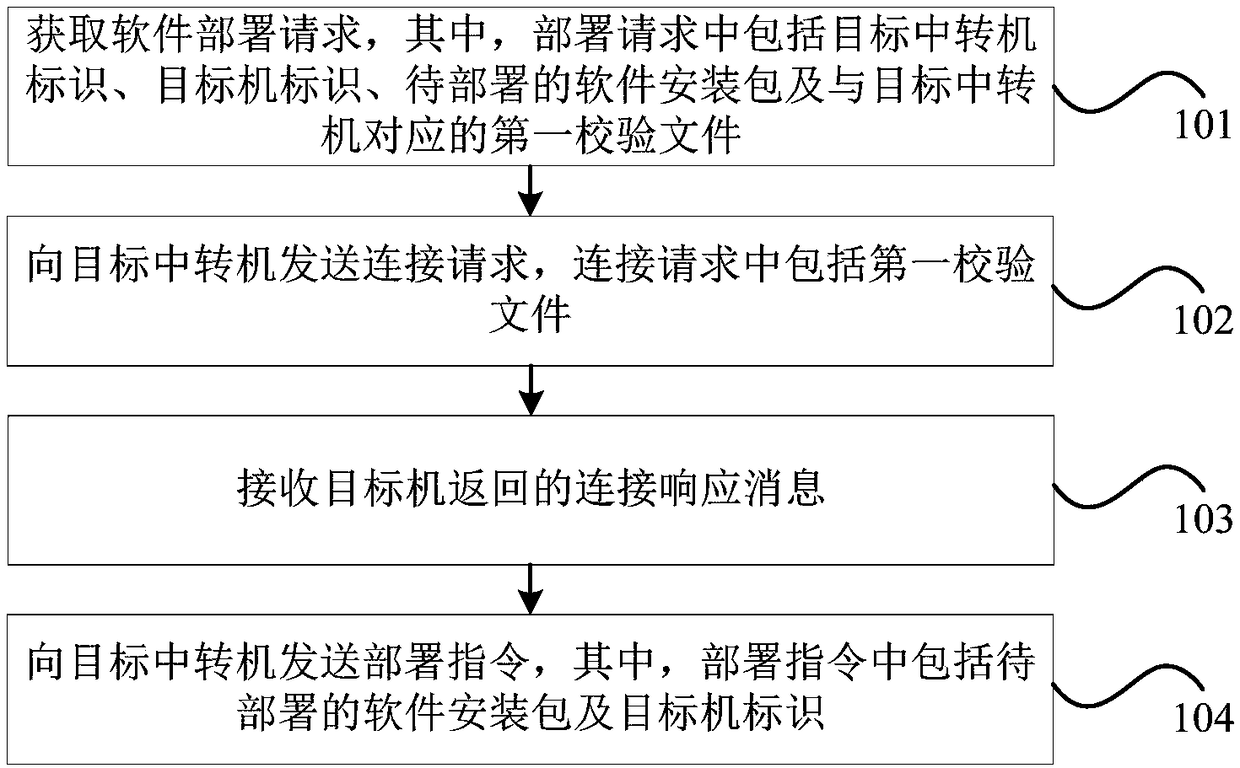
ActiveCN108509203AImplement automatic deploymentHigh speedTransmissionSoftware deploymentSoftwareCloud deployment
The invention provides a software cross-cloud deployment method, a deployment server and a storage medium. The method comprises the steps of obtaining a software deployment request, wherein the deployment request comprises a target transfer machine identifier, a target machine identifier, a to-be-deployed software installation package and a first check file corresponding to a target machine; sending a connection request to a target transfer machine, wherein the connection request comprises the first check file; receiving a connection response message returned by the target machine; and sendinga deployment instruction to the target transfer machine, wherein the deployment instruction comprises the to-be-deployed software installation package and the target machine identifier. Through the method, automatic deployment of a software installation task can be realized; cross-cloud batch task deployment is facilitated; the task deployment speed and efficiency are improved; and the technicalproblems of complex installation process and poor flexibility in the prior art are solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
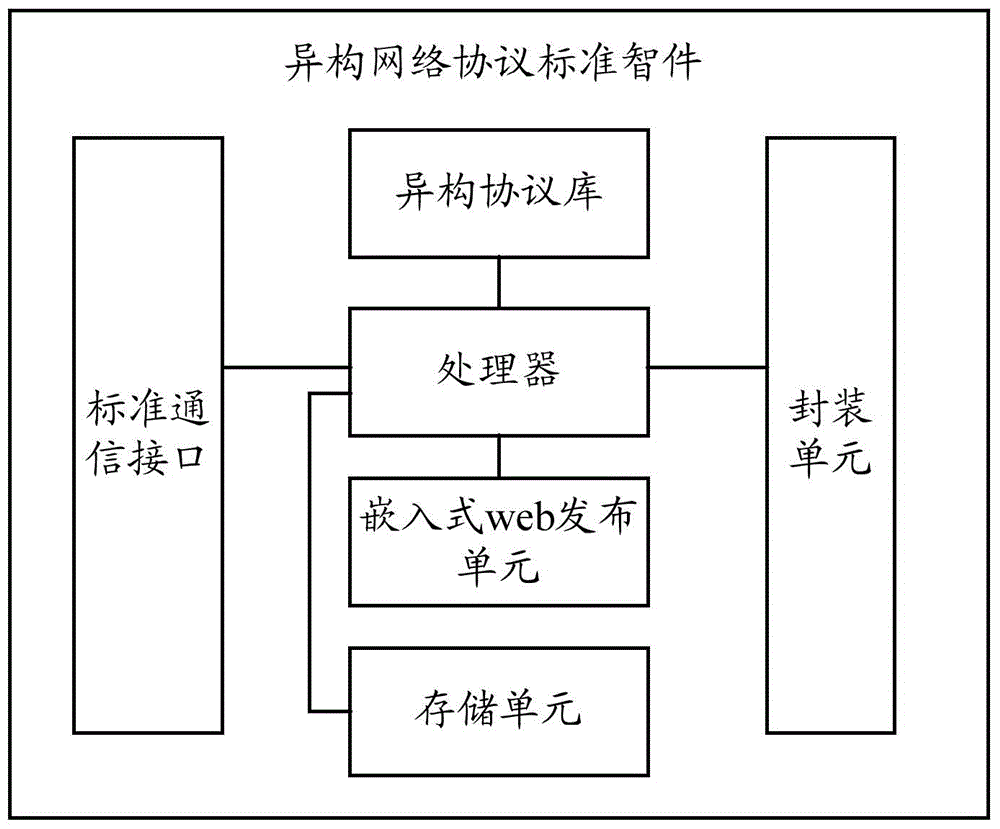
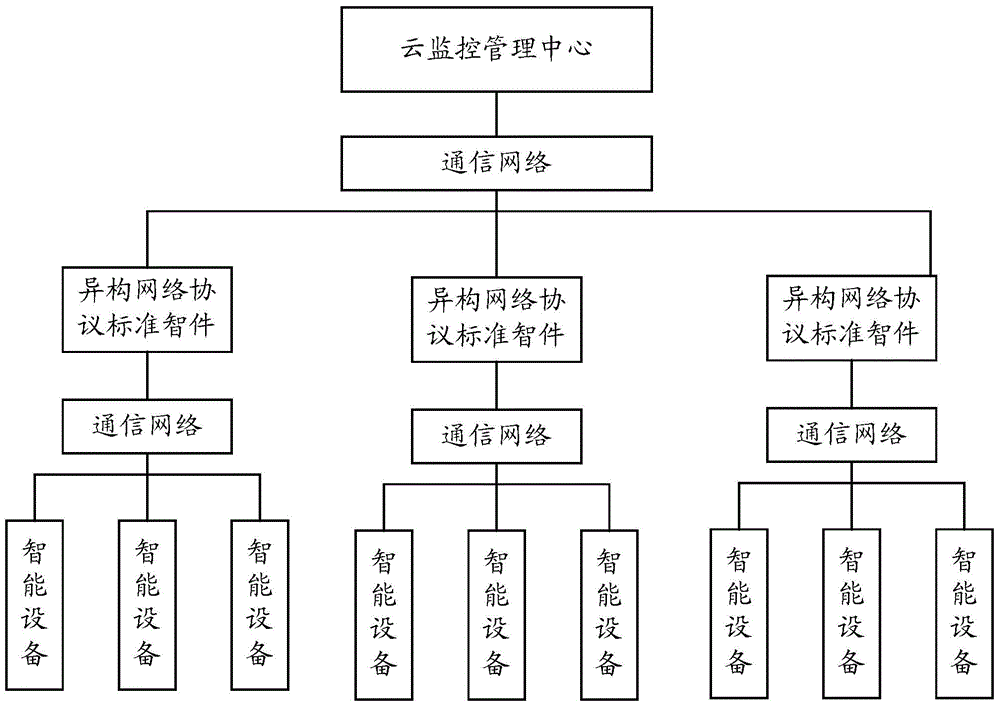
Heterogeneous network protocol standard knowledgeware, cloud monitoring and management system and method
ActiveCN104660596ARealize real-time monitoringSlow processingTransmissionCommunication interfaceTechnical standard
The invention provides heterogeneous network protocol standard knowledgeware, a cloud monitoring and management system and a method. The heterogeneous network protocol standard knowledgeware comprises a heterogeneous protocol library, a standard communication interface, a processor, a packaging unit and an embedded web release unit. The heterogeneous network protocol standard knowledgeware, the cloud monitoring and management system and the method have the advantages as follows: the heterogeneous network protocol standard knowledgeware is deployed for each network node, adopts a standardized input mode and is compatible with more types of intelligent devices; the heterogeneous network protocol standard knowledgeware adopts a standardized output mode, so as to bring convenience for cloud deployment; in addition, the heterogeneous network protocol standard knowledgeware adopts the heterogeneous protocol library and a multi-thread processing mechanism, so as to effectively reduce the processing speed of a cloud management server, improve the data acquisition and processing speed, and realize real-time monitoring for all intelligent devices.
Owner:CHANGZHOU MACRO UNION NETWORK DATA INFORMATION SAFETY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com