Patents
Literature
84 results about "Runtime verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Runtime verification is a computing system analysis and execution approach based on extracting information from a running system and using it to detect and possibly react to observed behaviors satisfying or violating certain properties . Some very particular properties, such as datarace and deadlock freedom, are typically desired to be satisfied by all systems and may be best implemented algorithmically. Other properties can be more conveniently captured as formal specifications. Runtime verification specifications are typically expressed in trace predicate formalisms, such as finite state machines, regular expressions, context-free patterns, linear temporal logics, etc., or extensions of these. This allows for a less ad-hoc approach than normal testing. However, any mechanism for monitoring an executing system is considered runtime verification, including verifying against test oracles and reference implementations. When formal requirements specifications are provided, monitors are synthesized from them and infused within the system by means of instrumentation. Runtime verification can be used for many purposes, such as security or safety policy monitoring, debugging, testing, verification, validation, profiling, fault protection, behavior modification (e.g., recovery), etc. Runtime verification avoids the complexity of traditional formal verification techniques, such as model checking and theorem proving, by analyzing only one or a few execution traces and by working directly with the actual system, thus scaling up relatively well and giving more confidence in the results of the analysis (because it avoids the tedious and error-prone step of formally modelling the system), at the expense of less coverage. Moreover, through its reflective capabilities runtime verification can be made an integral part of the target system, monitoring and guiding its execution during deployment.
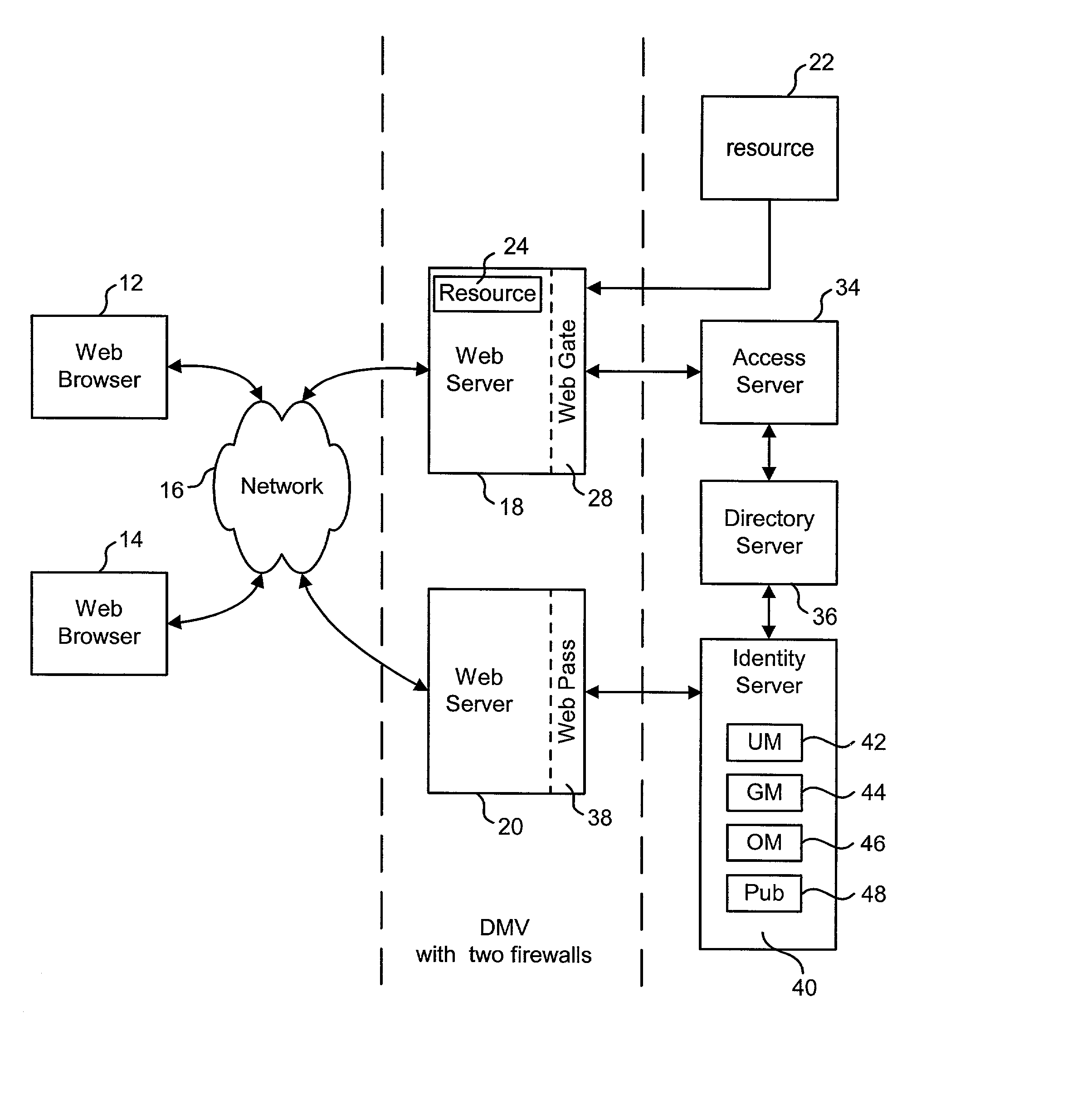
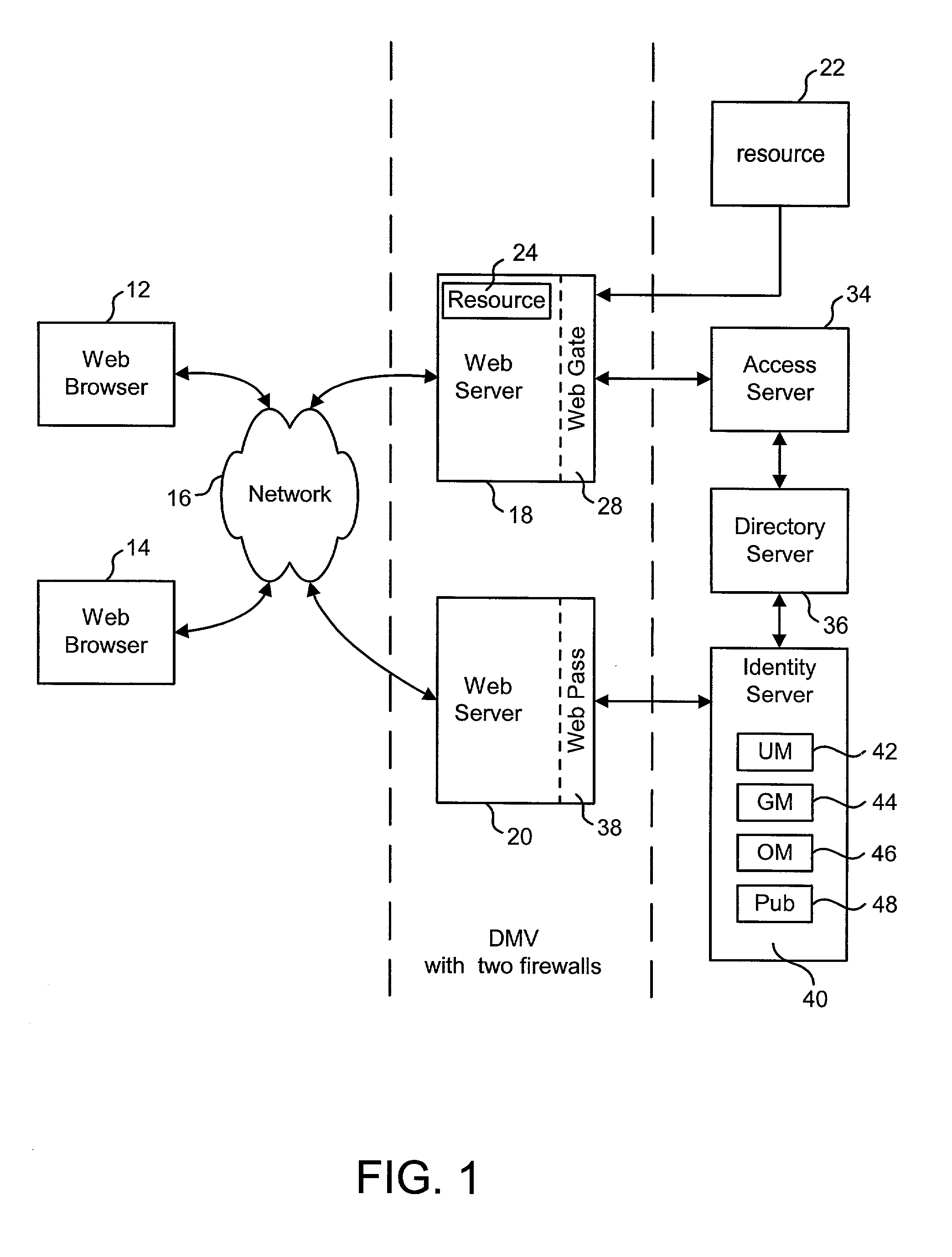
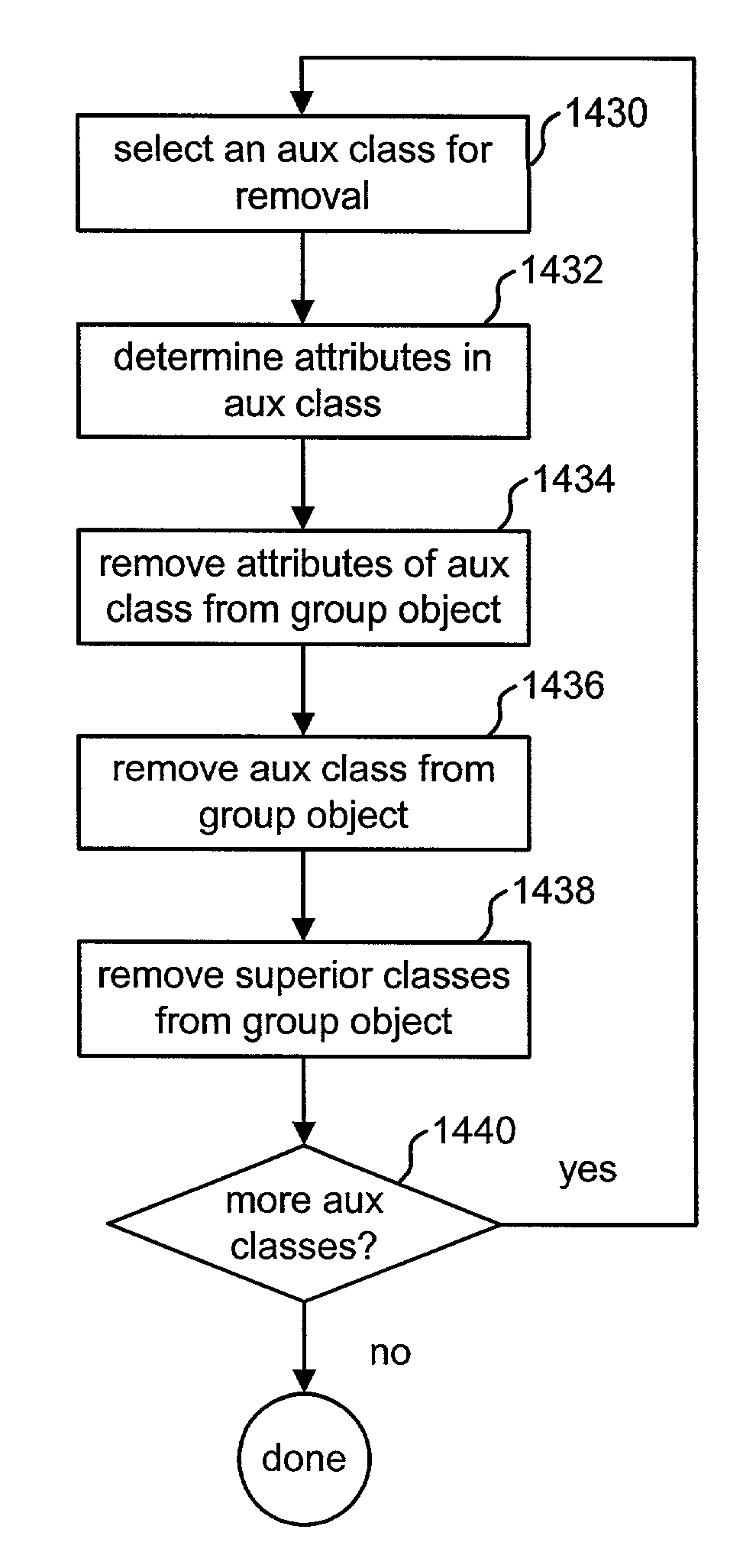
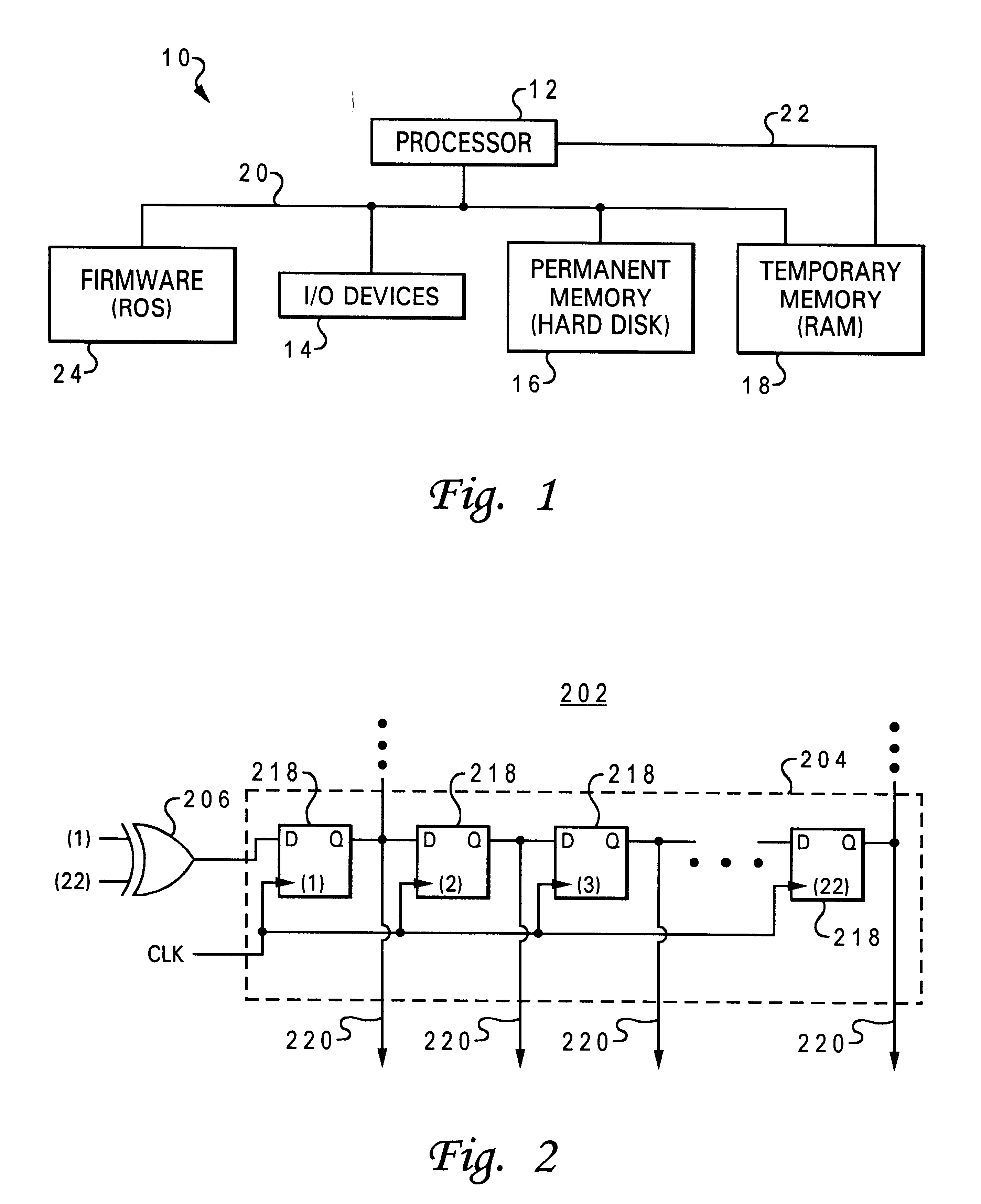
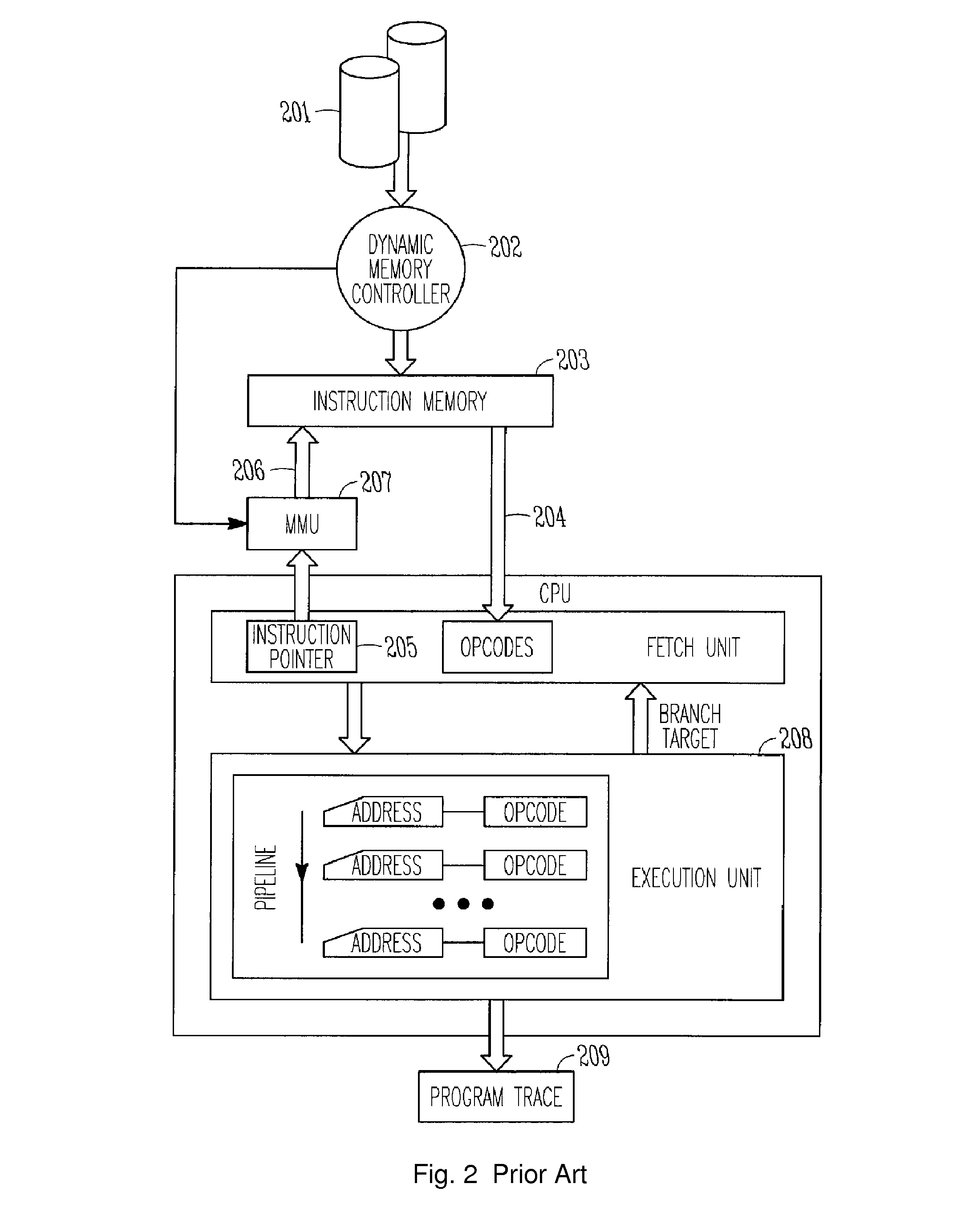
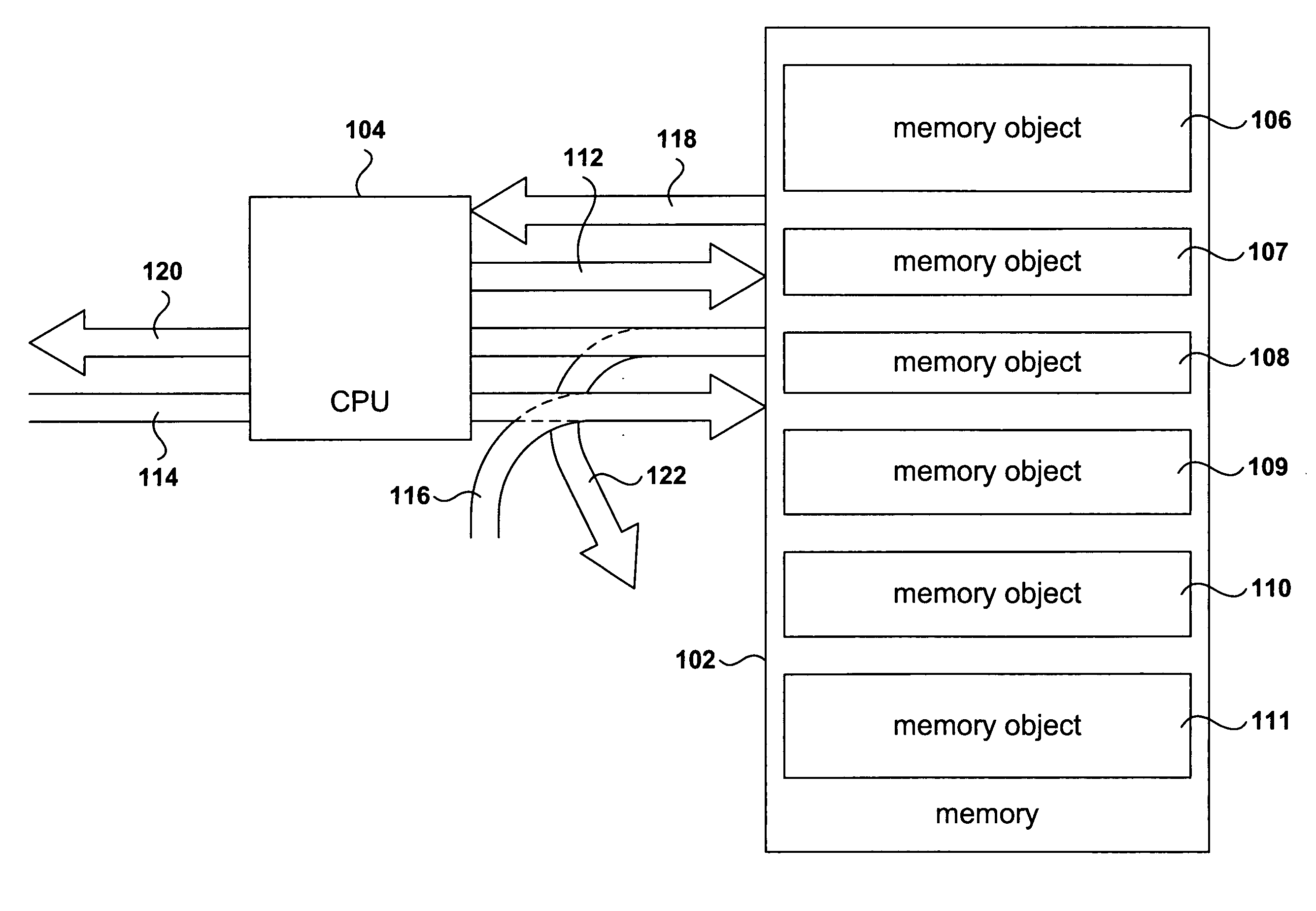
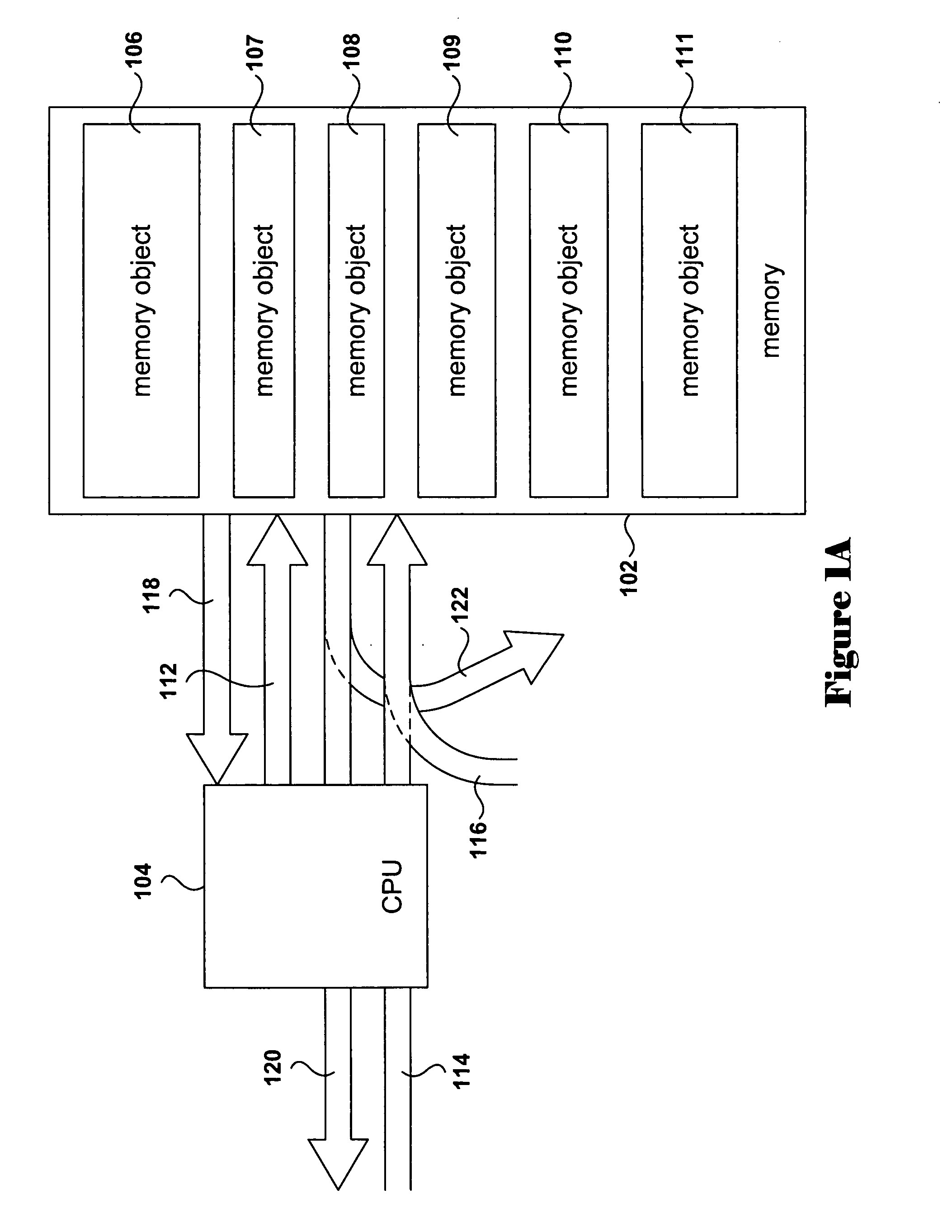
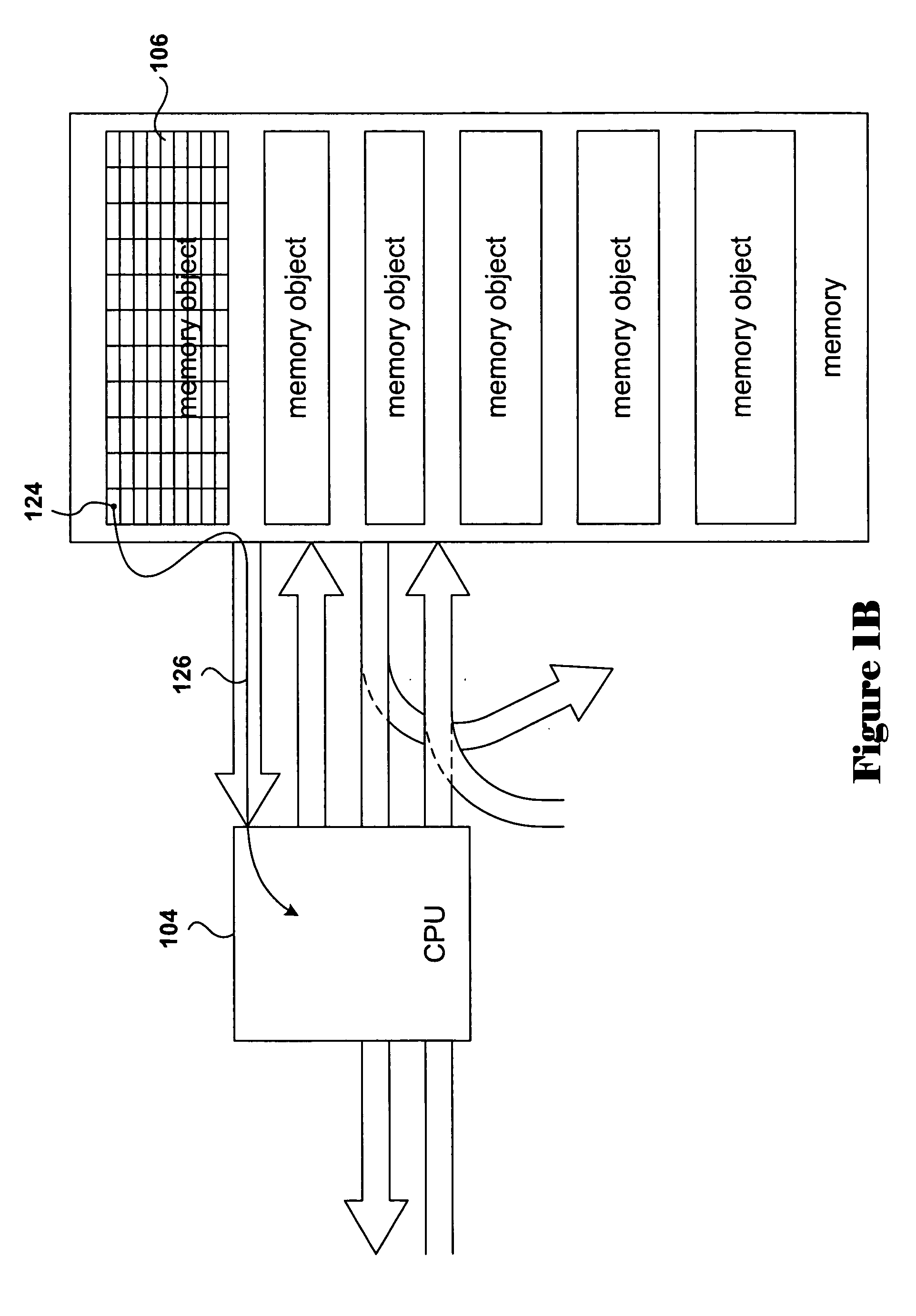
Runtime modification of entries in an identity system
ActiveUS20020138763A1Digital data processing detailsUser identity/authority verificationRuntime verificationData storing
The present invention is directed to technology for modifying groups or other types of entries after those entries have been created. In one embodiment, the invention includes modifying group objects that have already been instantiated by adding and / or removing auxiliary classes and their associated attributes. The present invention can be used with an Identity System that stores group objects in a directory. Alternatively, the present invention can be used with other types of entries, other types of systems and / or other types of data stores.
Owner:ORACLE INT CORP
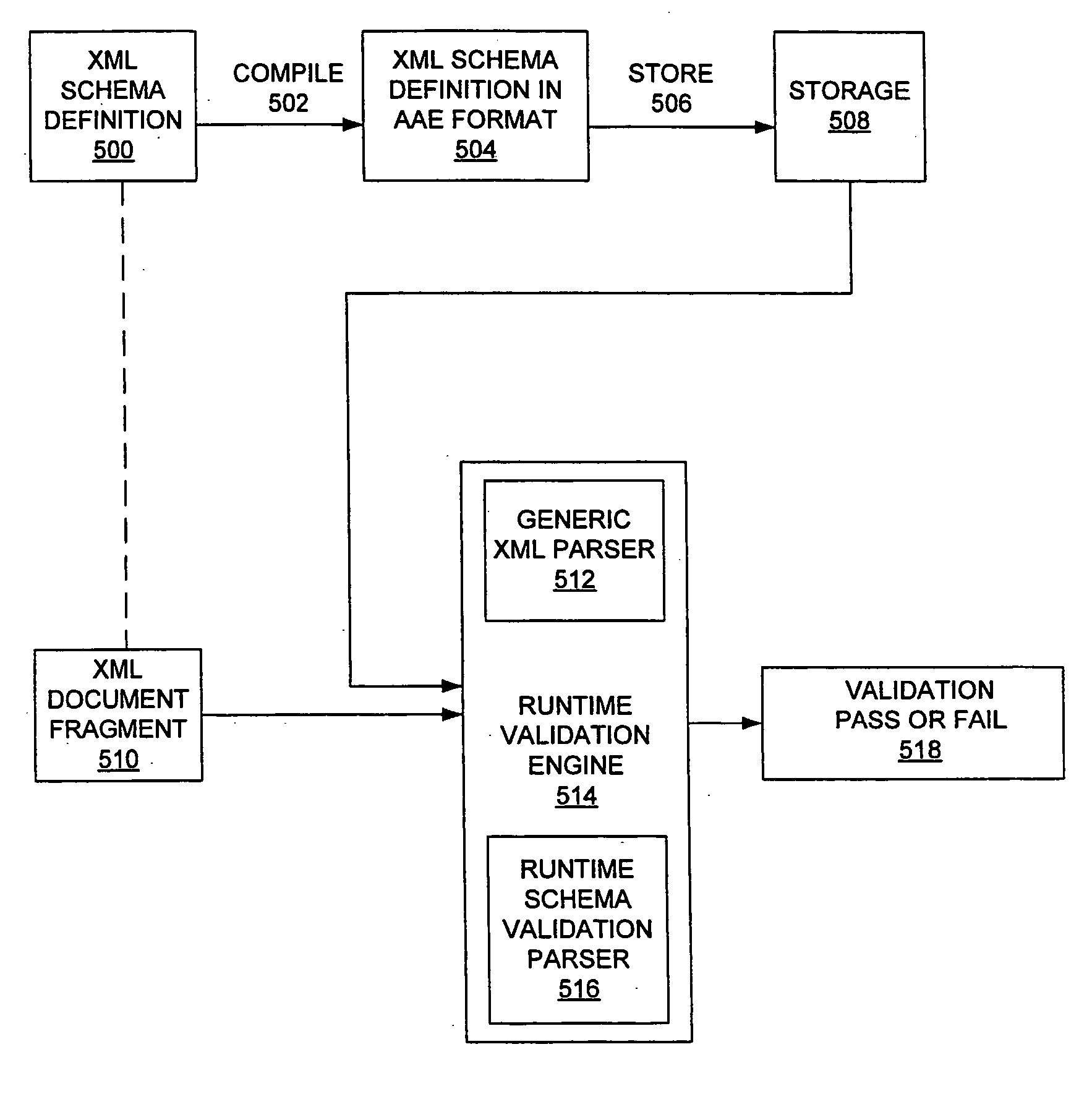
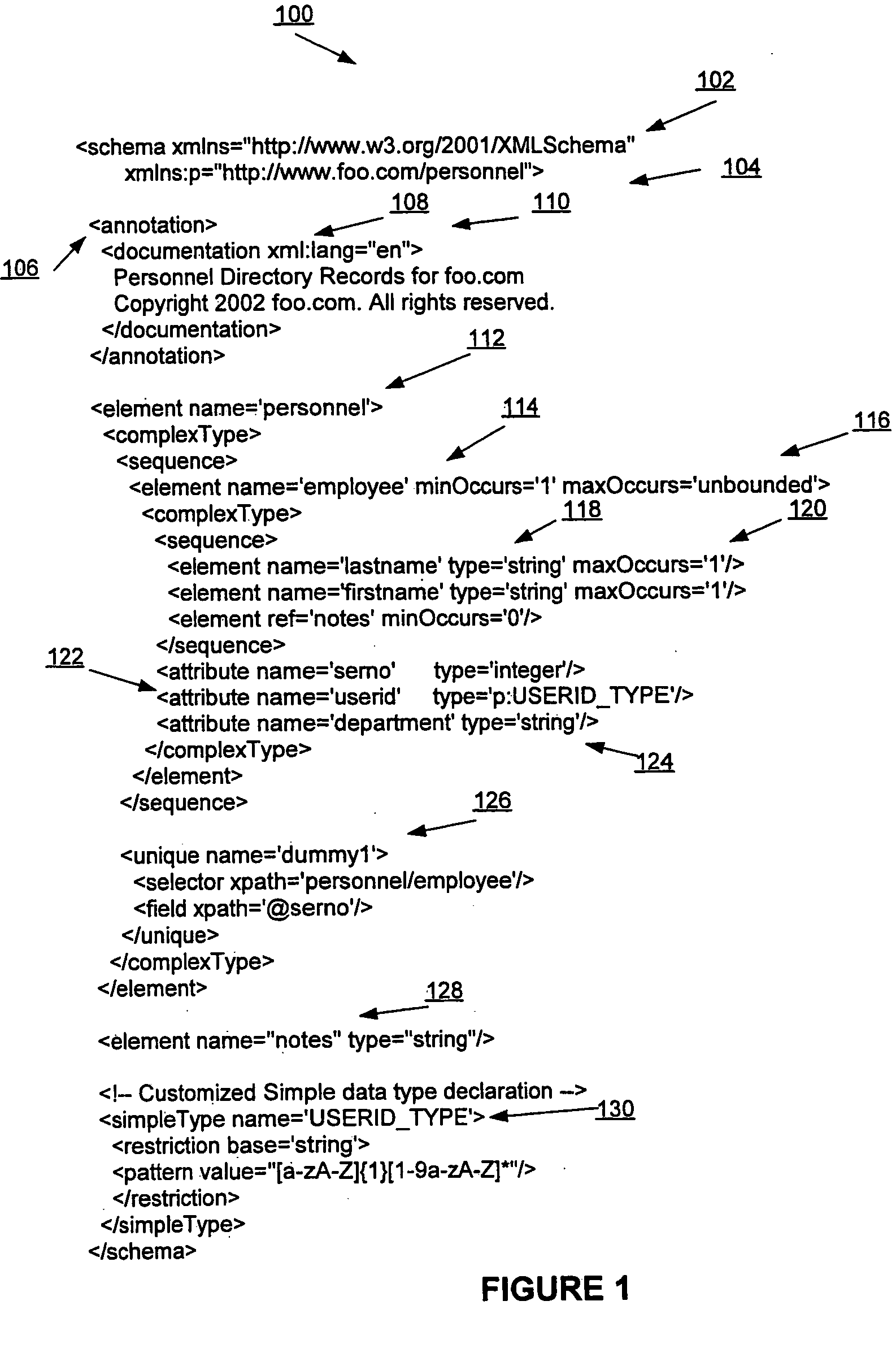
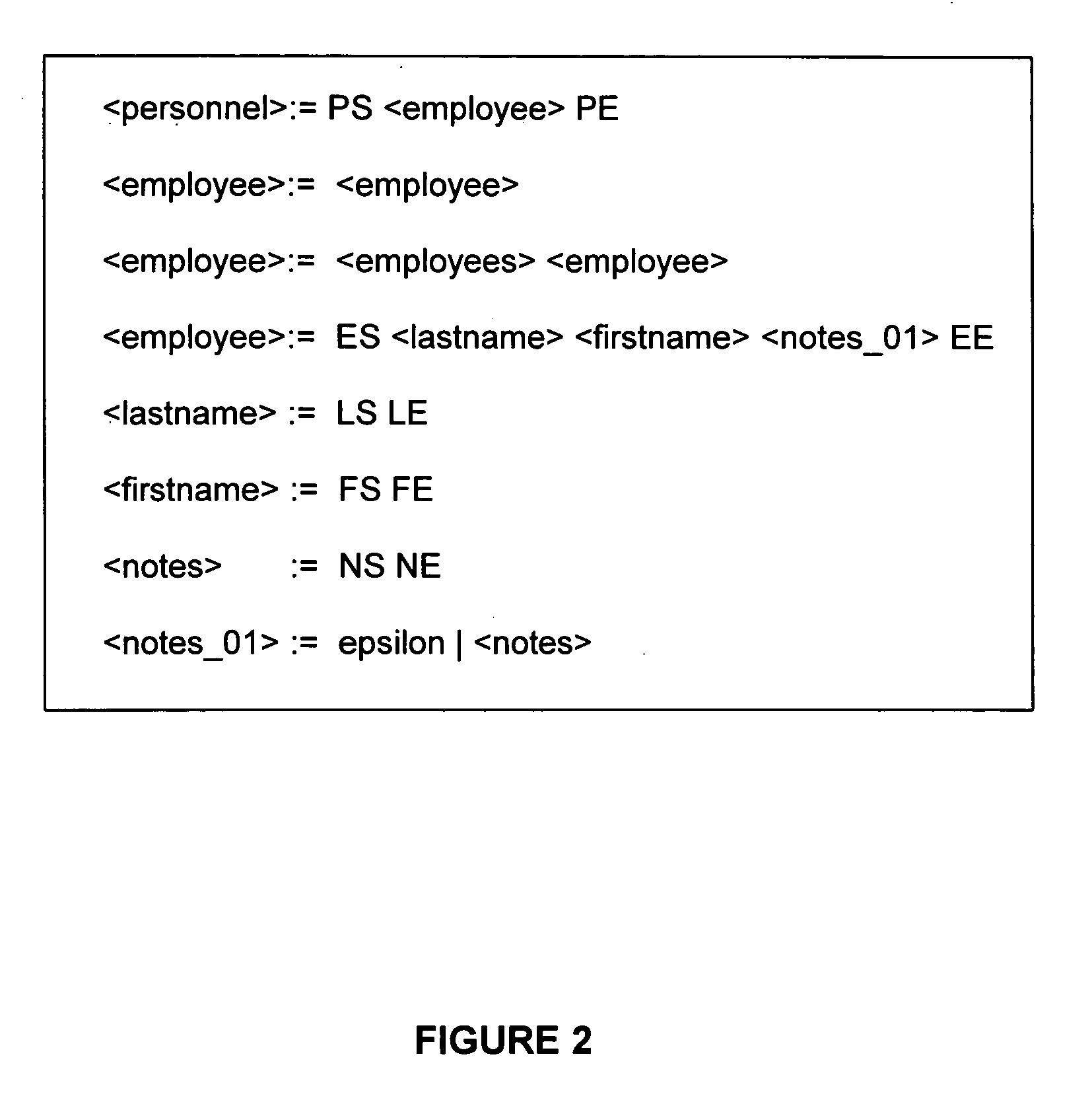
Efficient XML schema validation of XML fragments using annotated automaton encoding
InactiveUS20050177543A1Without compromising performanceSave a lot of timeDigital data processing detailsNatural language data processingXML schemaRuntime verification
A method and system for Extensible Markup Language (XML) schema validation, includes: loading an XML document into a runtime validation engine, where the runtime validation engine includes an XML schema validation parser; loading an annotated automaton encoding (AAE) for an XML schema definition into the XML schema validation parser; and validating the XML document against the XML schema definition by the XML schema validation parser utilizing the annotated automaton encoding. Each XML schema definition is compiled once into the AAE format, rather than being compiled each time an XML document is validated, and thus significant time is saved. The code for the runtime validation engine is fixed and does not vary depending on the XML schema definition, rather than varying for each XML schema definition, and thus space overhead is minimized. Flexibility in the validation process is provided without compromising performance.
Owner:IBM CORP
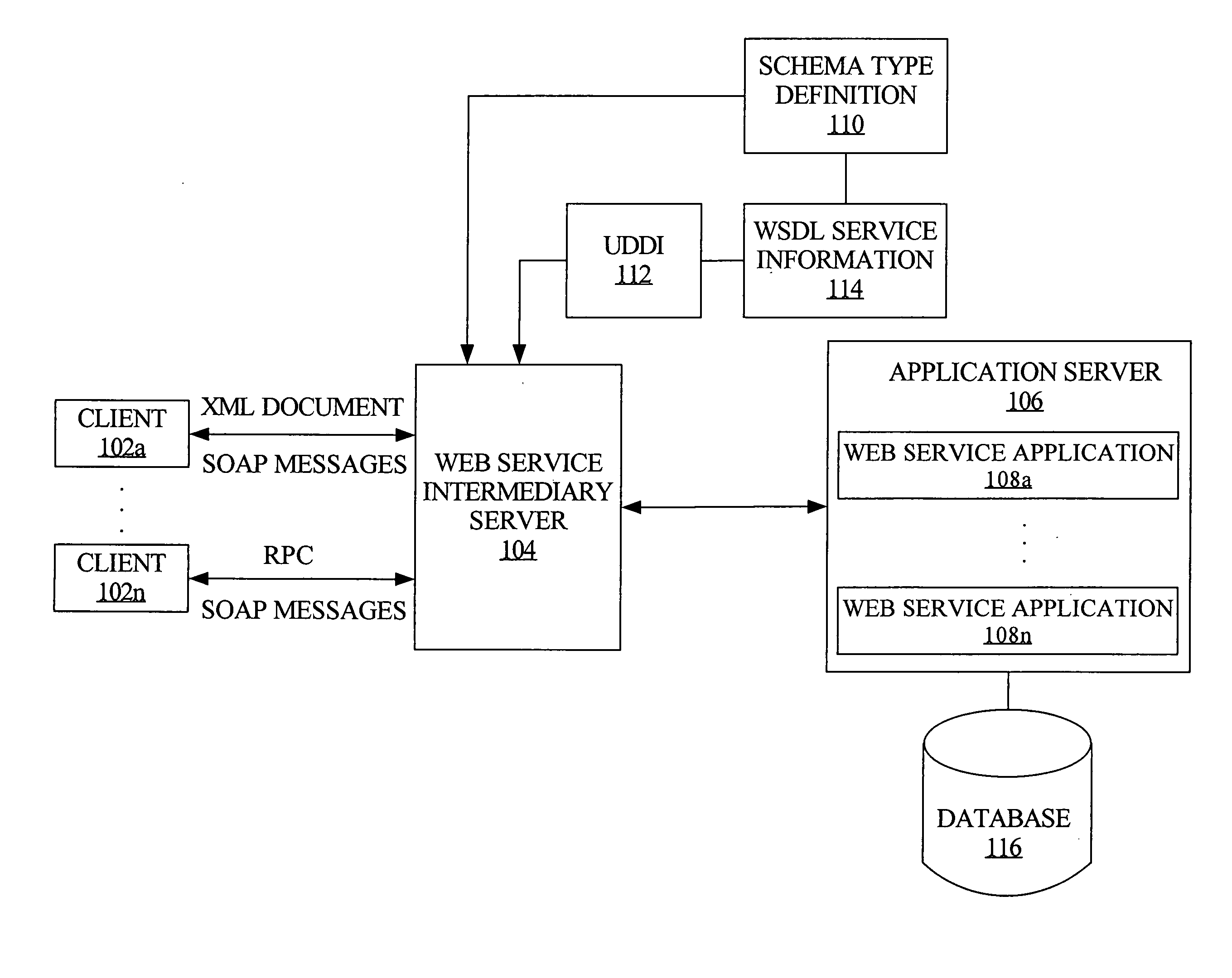
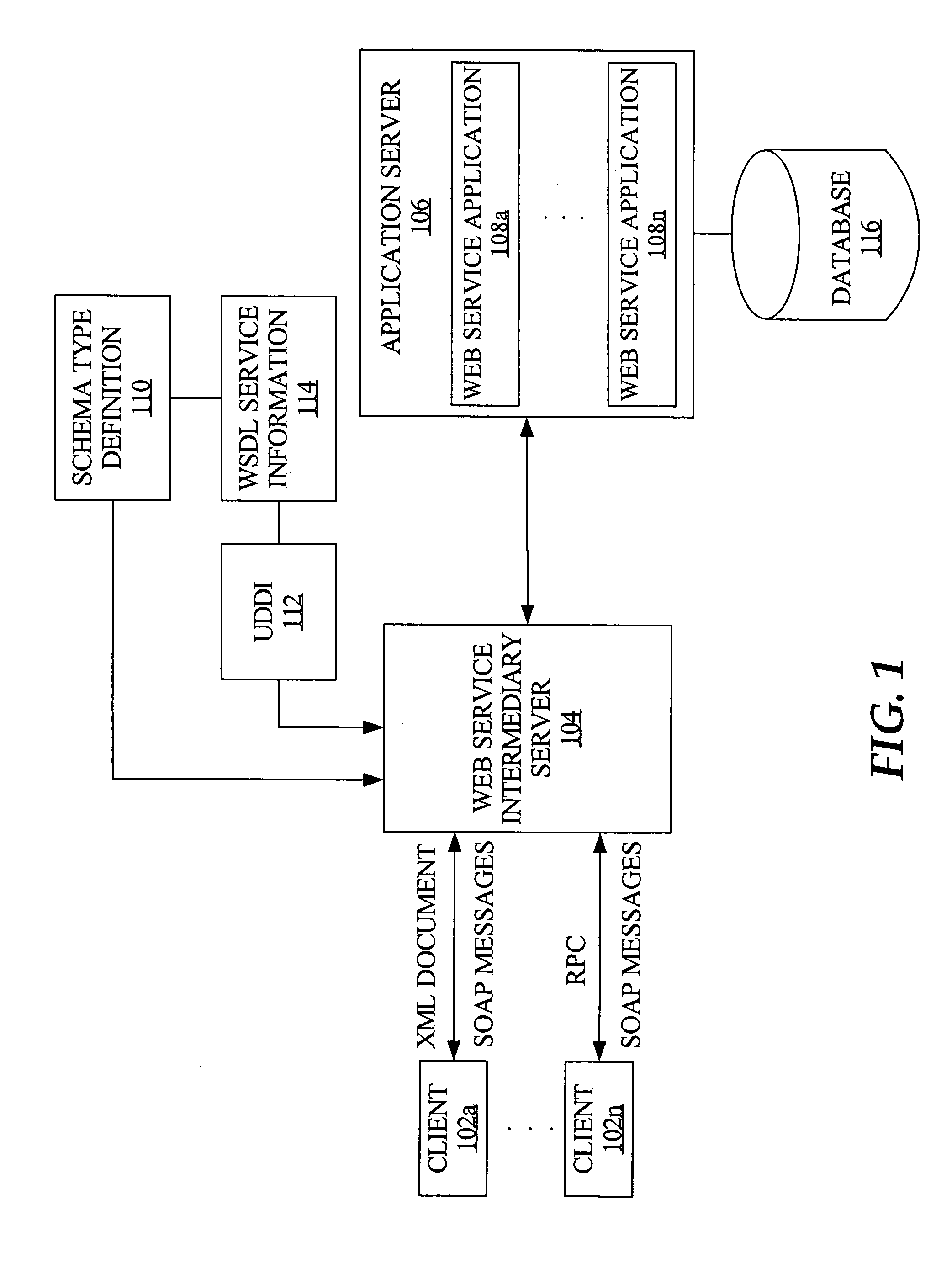
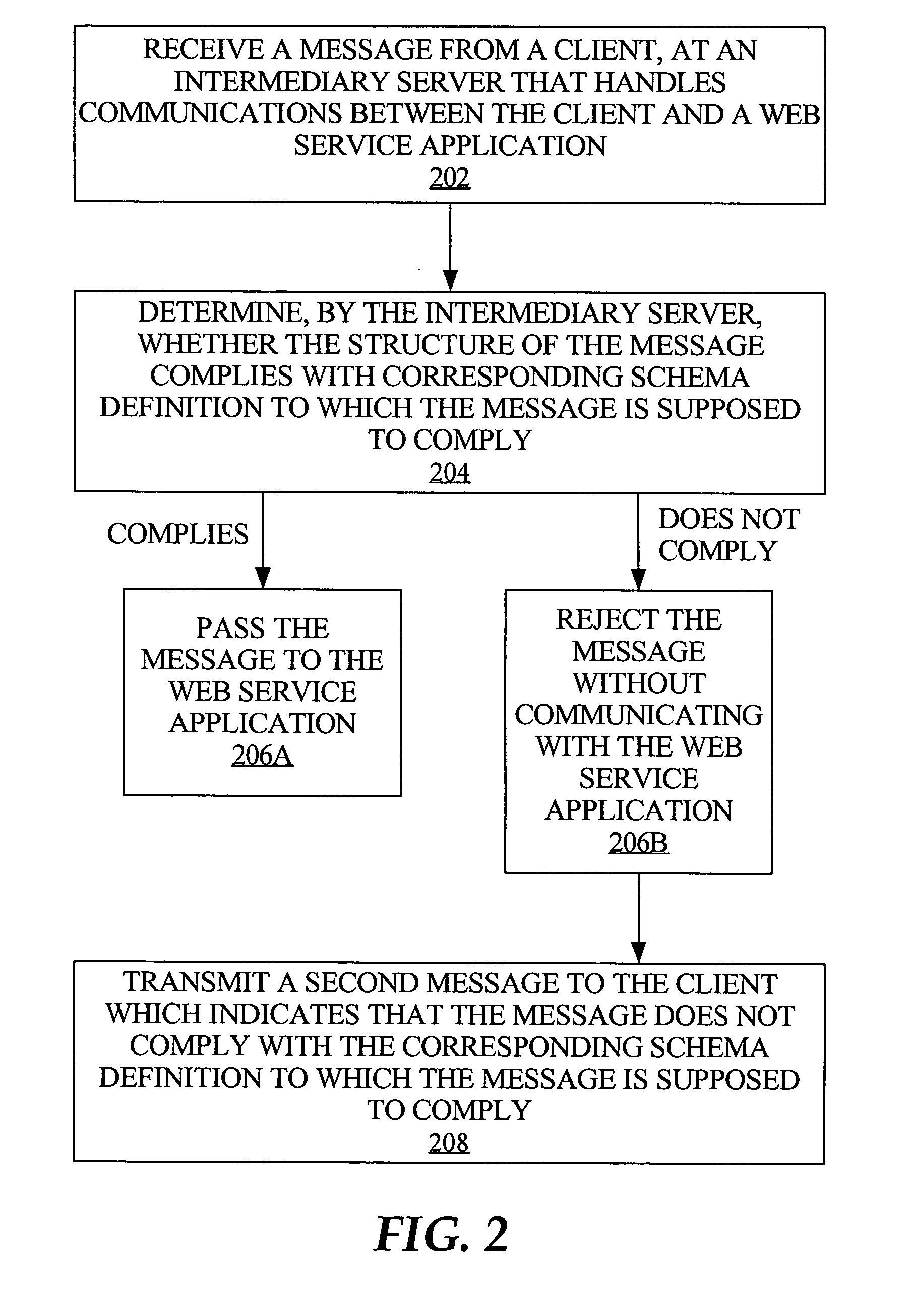
Runtime validation of messages for enhanced web service processing
ActiveUS20050198154A1Multiple digital computer combinationsElectric digital data processingWeb serviceRuntime verification
Inbound processing of web service request messages at runtime is enhanced by providing validation of the message structure against corresponding schema, at an intermediary web service server rather than at the web service application (e.g., web service application). Hence, there is minimal delay in responding to the client upon determining an invalid message structure, and unnecessary processing of invalid messages by the web service application is avoided.
Owner:ORACLE INT CORP
System and method for validating program execution at run-time using control flow signatures
ActiveUS8782435B1Little and delayProvide securityMemory architecture accessing/allocationUser identity/authority verificationComputer hardwareControl flow
A processor comprising: an instruction processing pipeline, configured to receive a sequence of instructions for execution, said sequence comprising at least one instruction including a flow control instruction which terminates the sequence; a hash generator, configured to generate a hash associated with execution of the sequence of instructions; a memory configured to securely receive a reference signature corresponding to a hash of a verified corresponding sequence of instructions; verification logic configured to determine a correspondence between the hash and the reference signature; and authorization logic configured to selectively produce a signal, in dependence on a degree of correspondence of the hash with the reference signature.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Runtime modification of entries in an identity system
ActiveUS7349912B2Digital data processing detailsMultiple digital computer combinationsRuntime verificationData storing
The present invention is directed to technology for modifying groups or other types of entries after those entries have been created. In one embodiment, the invention includes modifying group objects that have already been instantiated by adding and / or removing auxiliary classes and their associated attributes. The present invention can be used with an Identity System that stores group objects in a directory. Alternatively, the present invention can be used with other types of entries, other types of systems and / or other types of data stores.
Owner:ORACLE INT CORP
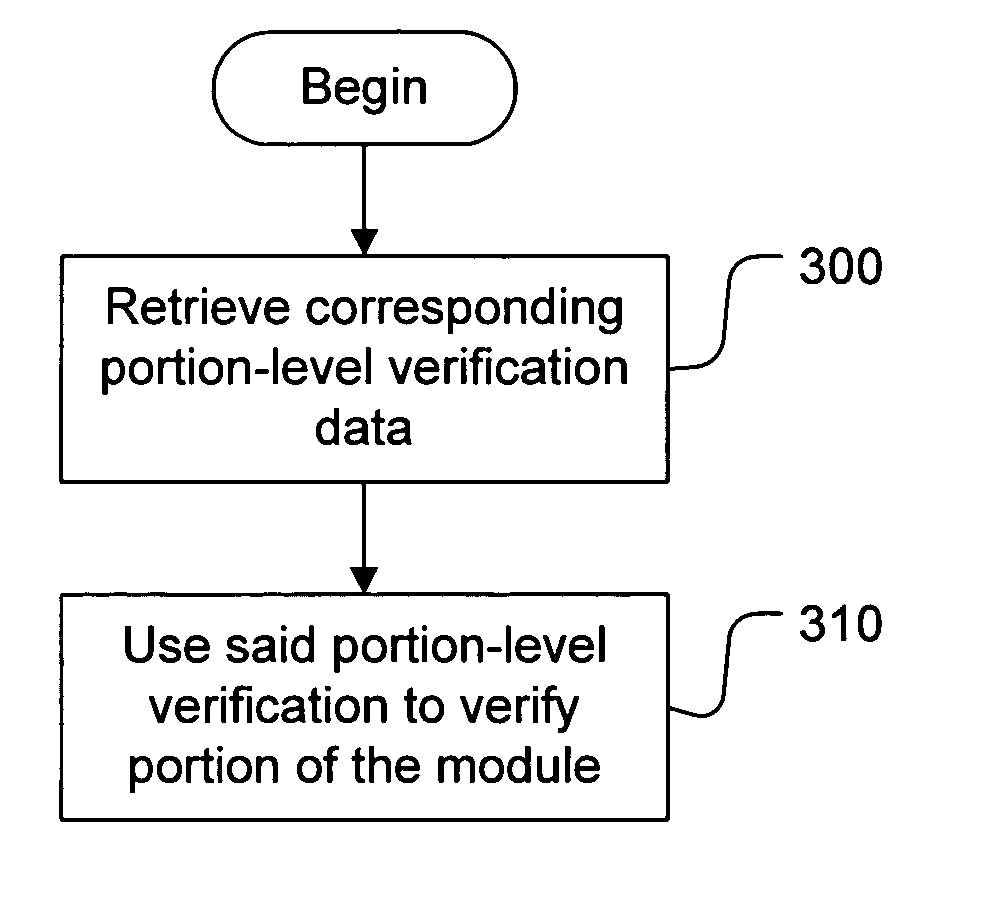
Portion-level in-memory module authentication
ActiveUS20060026569A1Efficient techniqueMaximum performanceMemory loss protectionUser identity/authority verificationOperational systemDigital signature
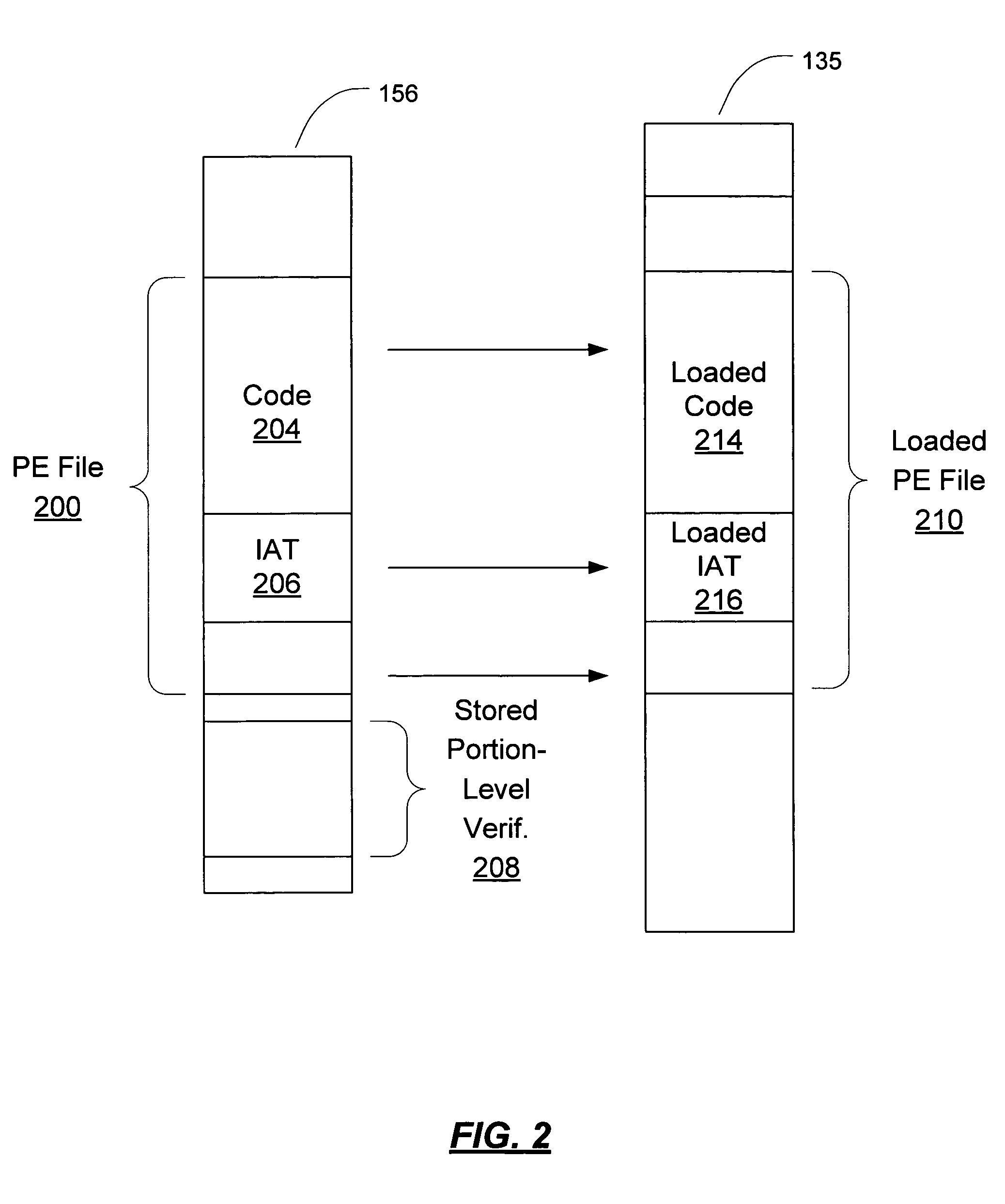
Dynamic run-time verification of a module which is loaded in memory (in whole or in part) for execution is enabled by using pre-computed portion-level verification data for portions of the module smaller than the whole (e.g. at the page-level). A portion of the module as loaded into memory for execution can be verified. Pre-computed portion-level verification data is retrieved from storage and used to verify the loaded portions of the executable. Verification data may be, for example, a digitally signed hash of the portion. Where the operating system loader has modified the portion for execution, the modifications are reversed, removing any changes performed by the operating system. If the portion has not been tampered, this will return the portion to its original pre-loaded state. This version is then used to determine validity using the pre-computed portion-level verification. Additionally, during execution of the module, new portions / pages of the module which are loaded can be verified to ensure that they have not been changed, and a list of hot pages of the module can be made, including pages to be continually reverified, in order to ensure that no malicious changes have been made in the module.
Owner:MICROSOFT TECH LICENSING LLC
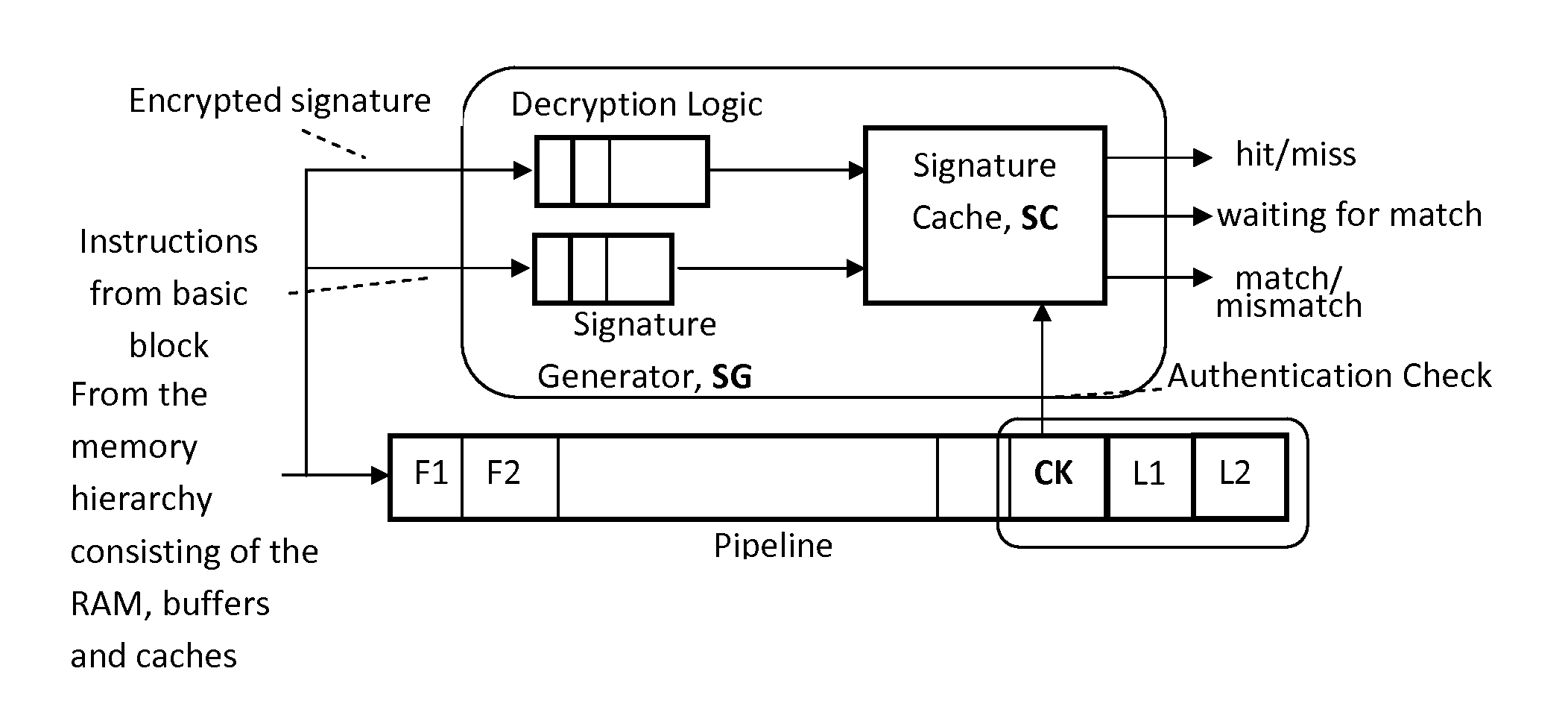
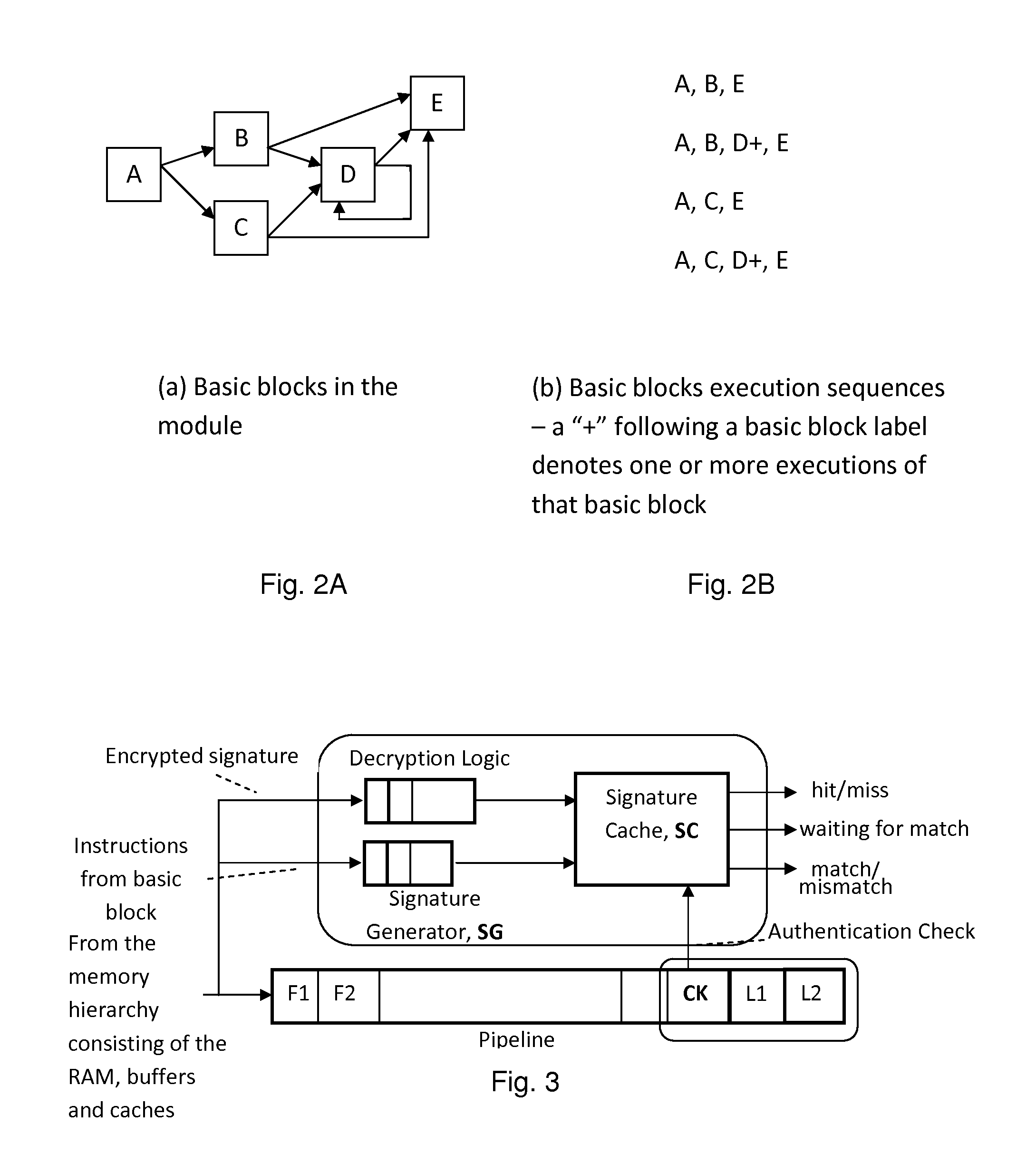
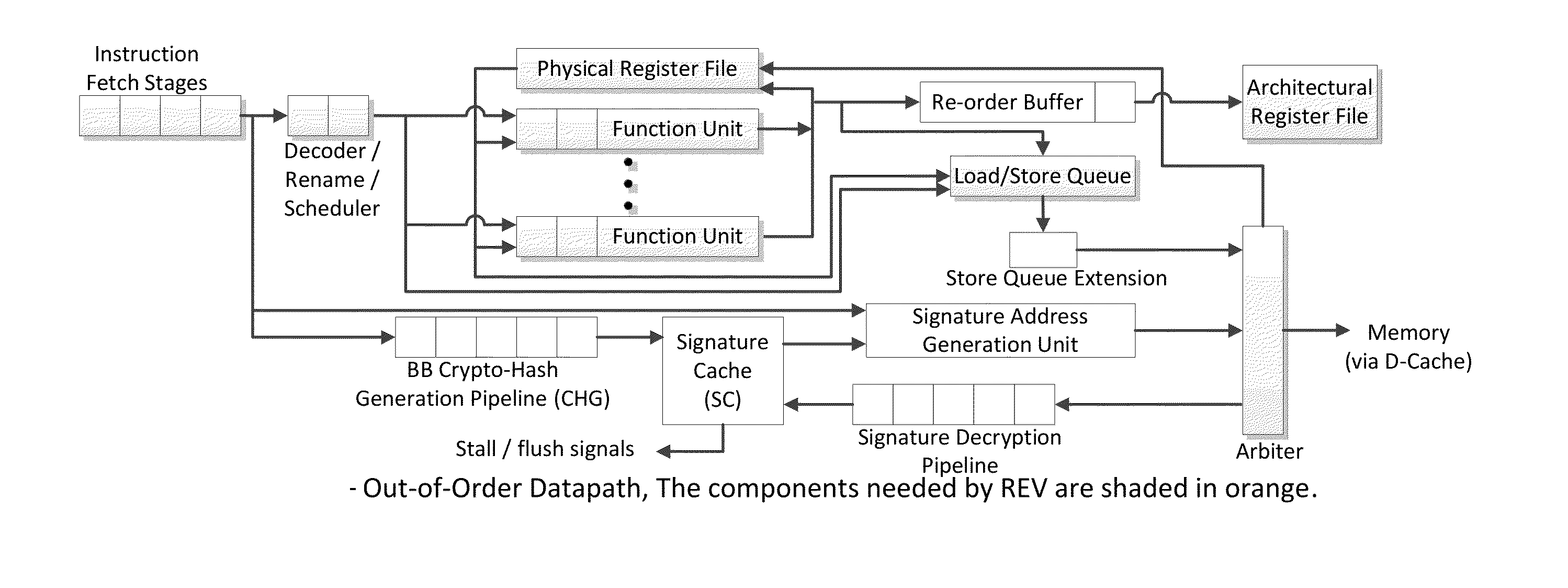
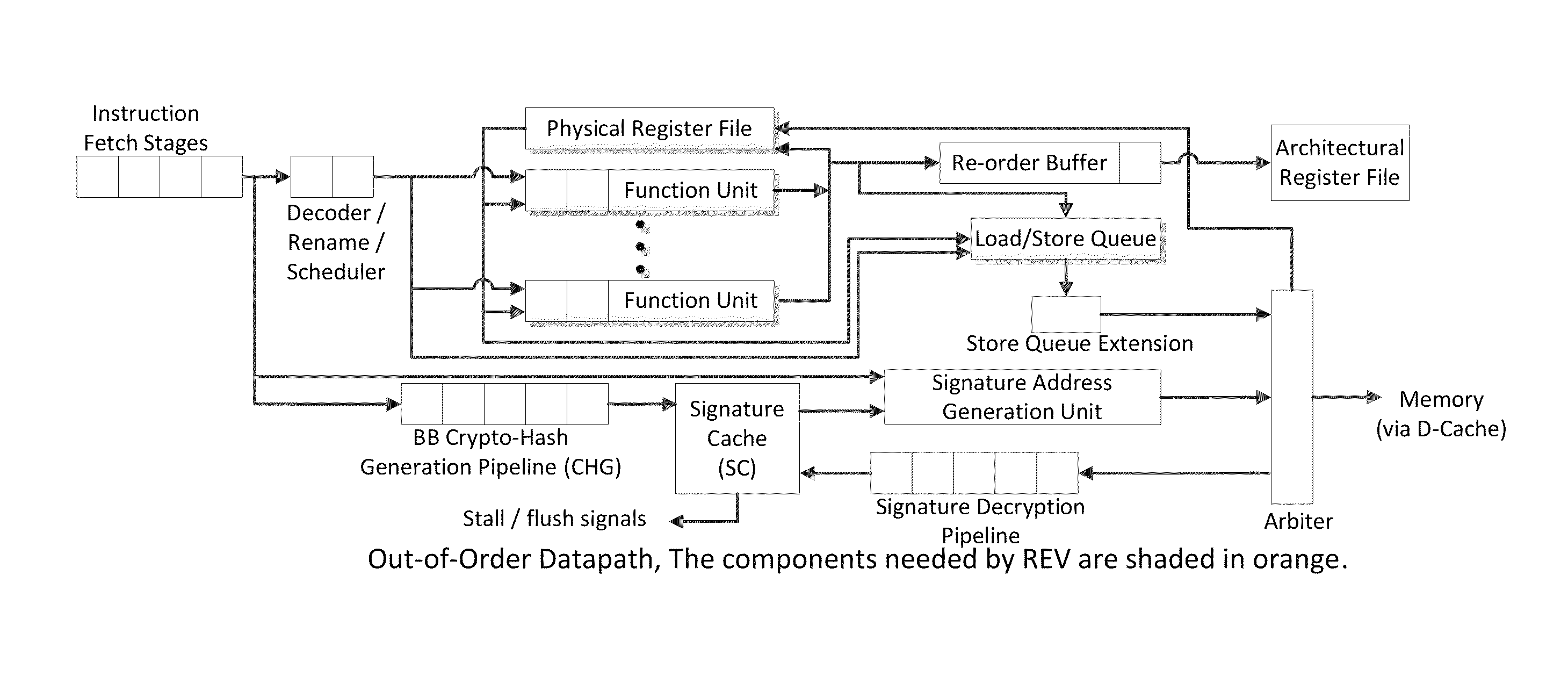
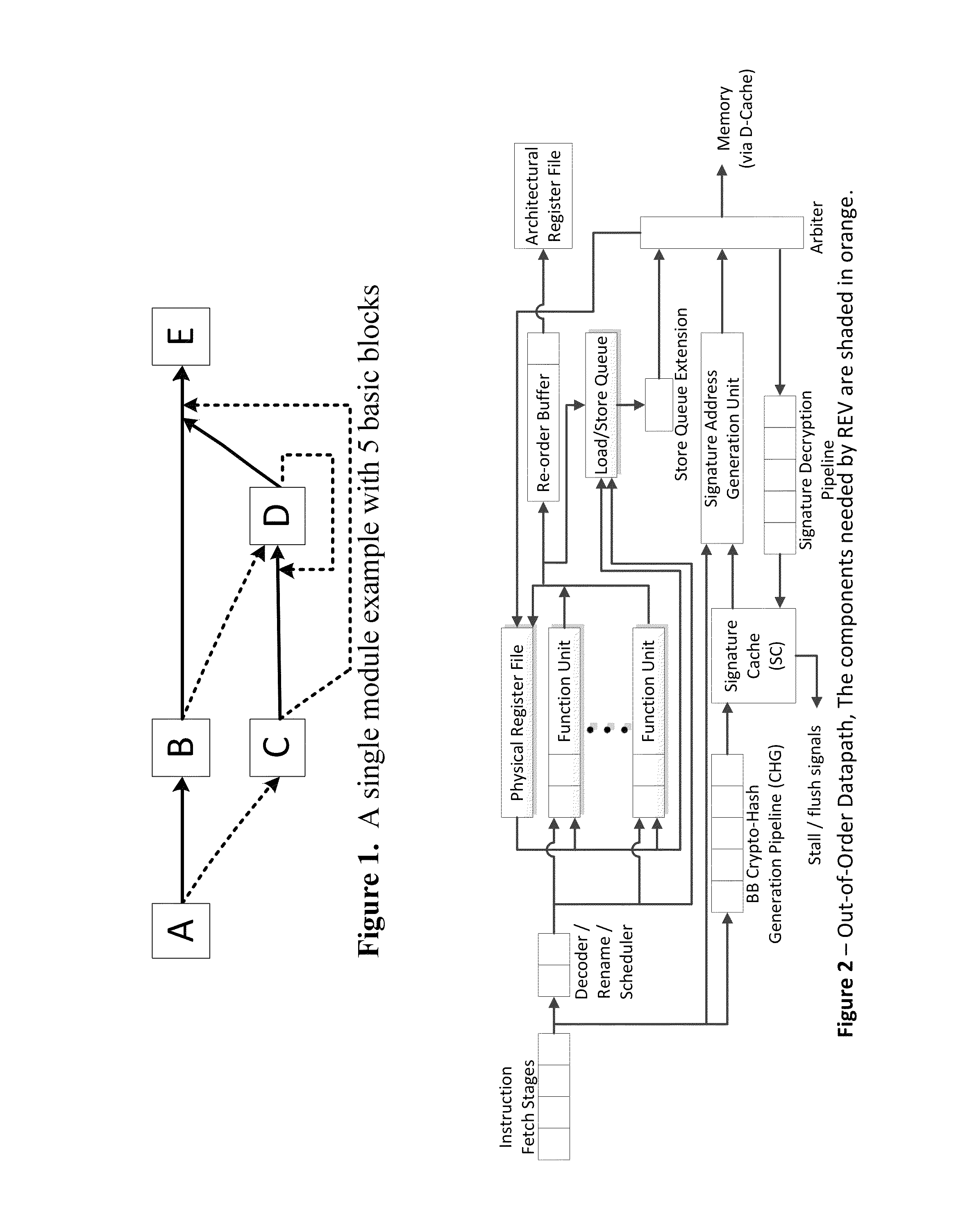
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082327A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
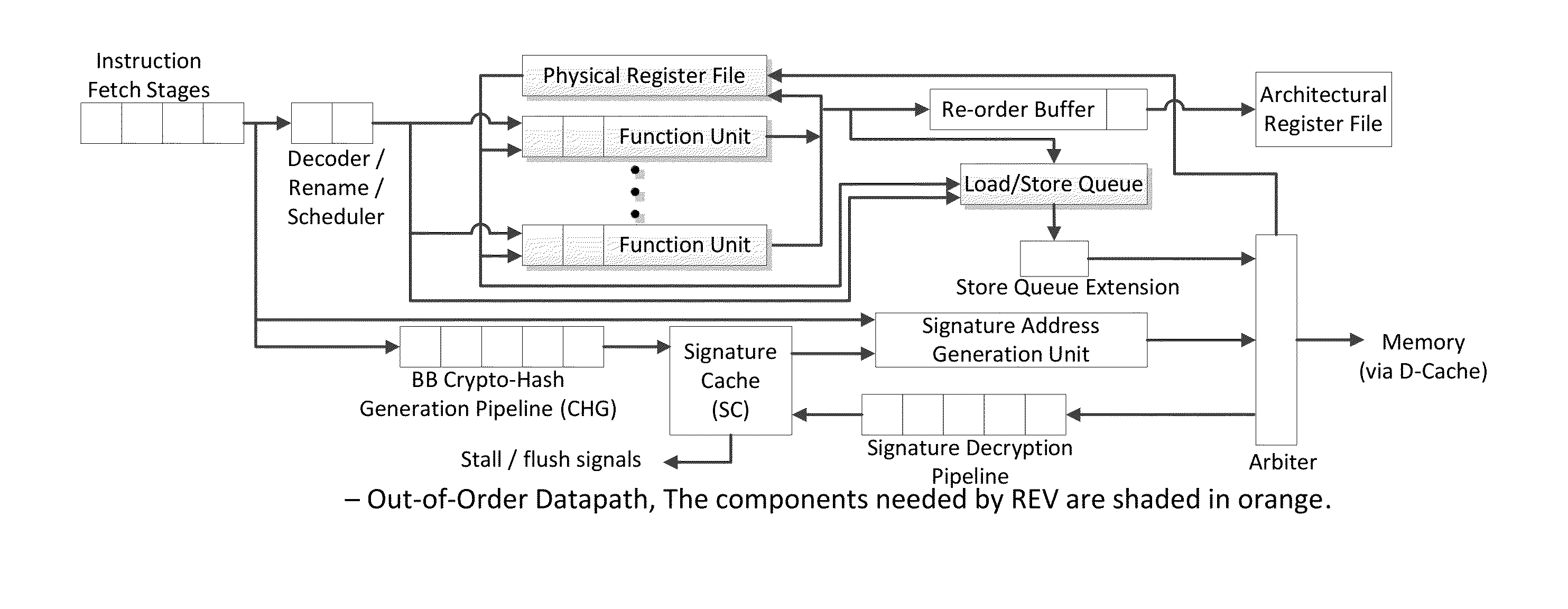
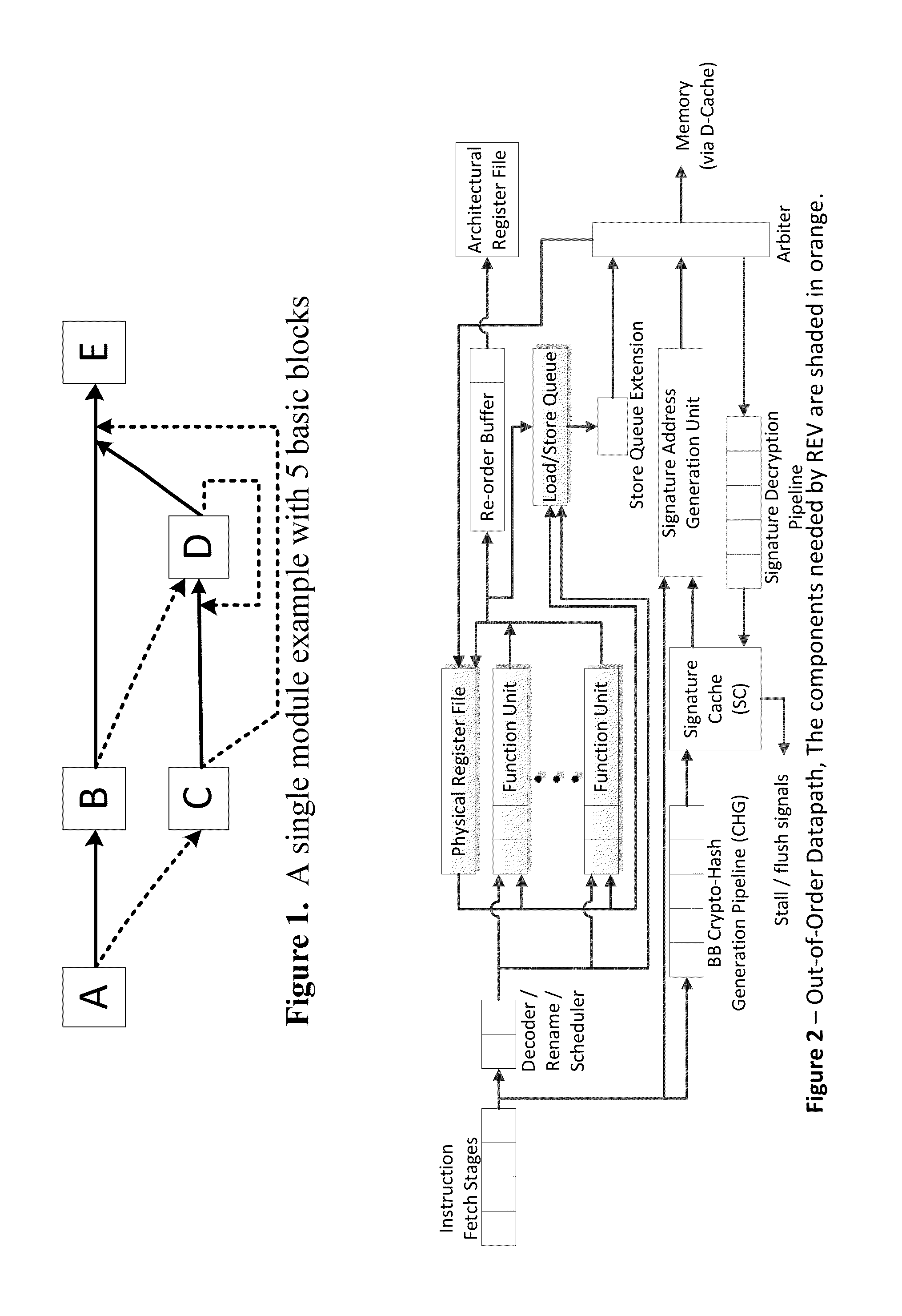
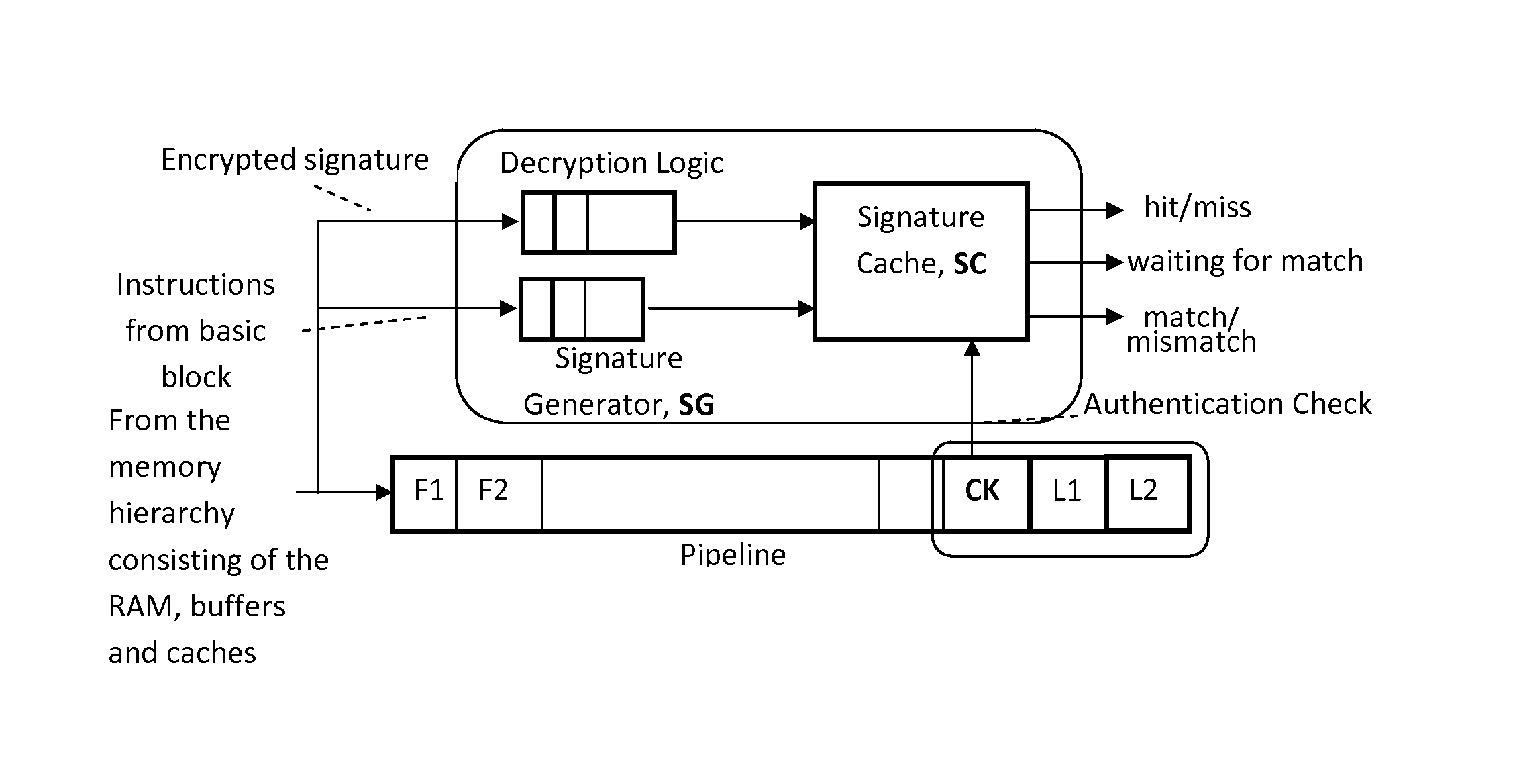
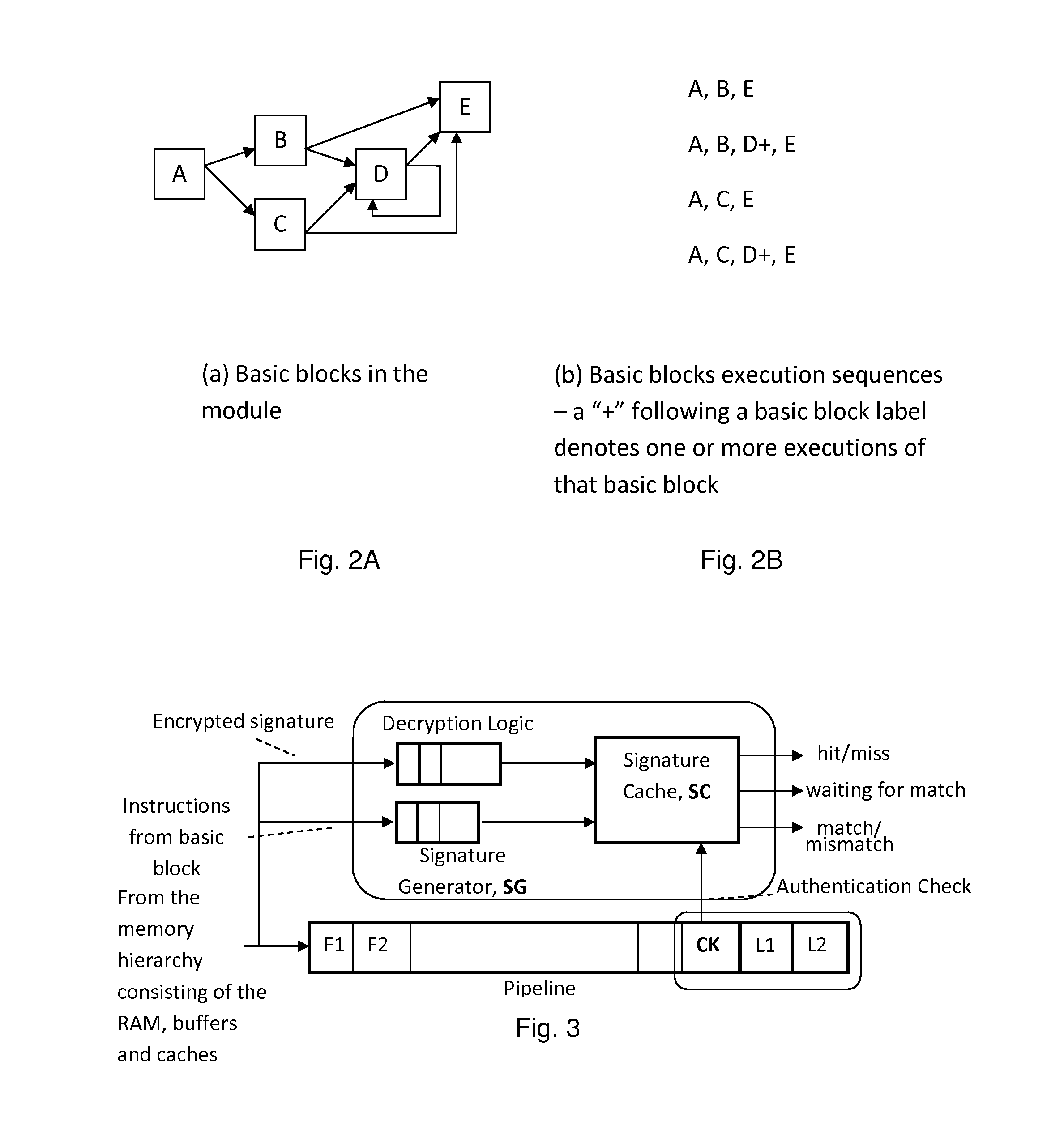
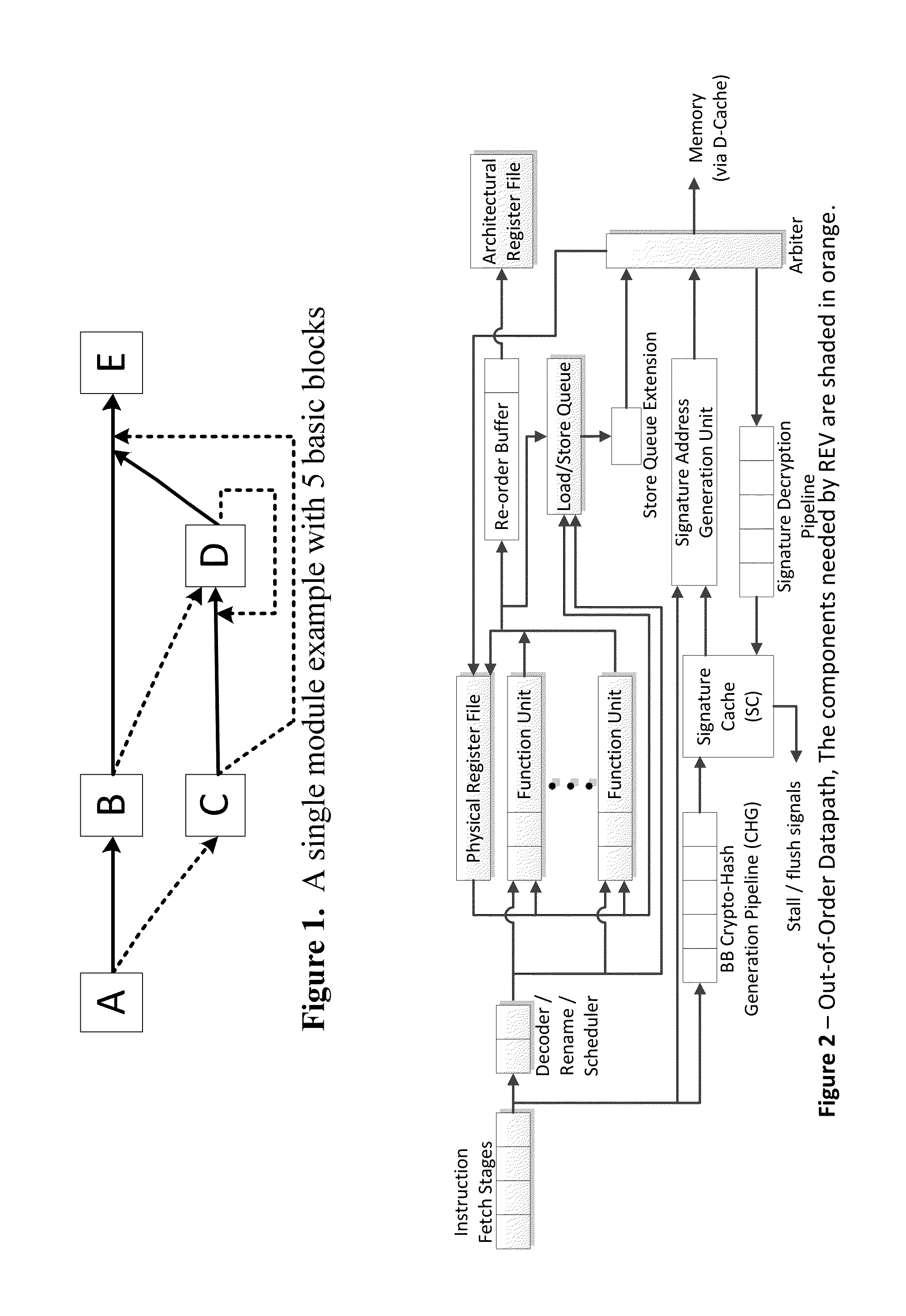
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
System and method for validating program execution at run-time using control flow signatures
ActiveUS20140325239A1Optimization mechanismSimple technologyMemory architecture accessing/allocationUnauthorized memory use protectionComputer architectureRuntime verification
A processor comprising: an instruction processing pipeline, configured to receive a sequence of instructions for execution, said sequence comprising at least one instruction including a flow control instruction which terminates the sequence; a hash generator, configured to generate a hash associated with execution of the sequence of instructions; a memory configured to securely receive a reference signature corresponding to a hash of a verified corresponding sequence of instructions; verification logic configured to determine a correspondence between the hash and the reference signature; and authorization logic configured to selectively produce a signal, in dependence on a degree of correspondence of the hash with the reference signature.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
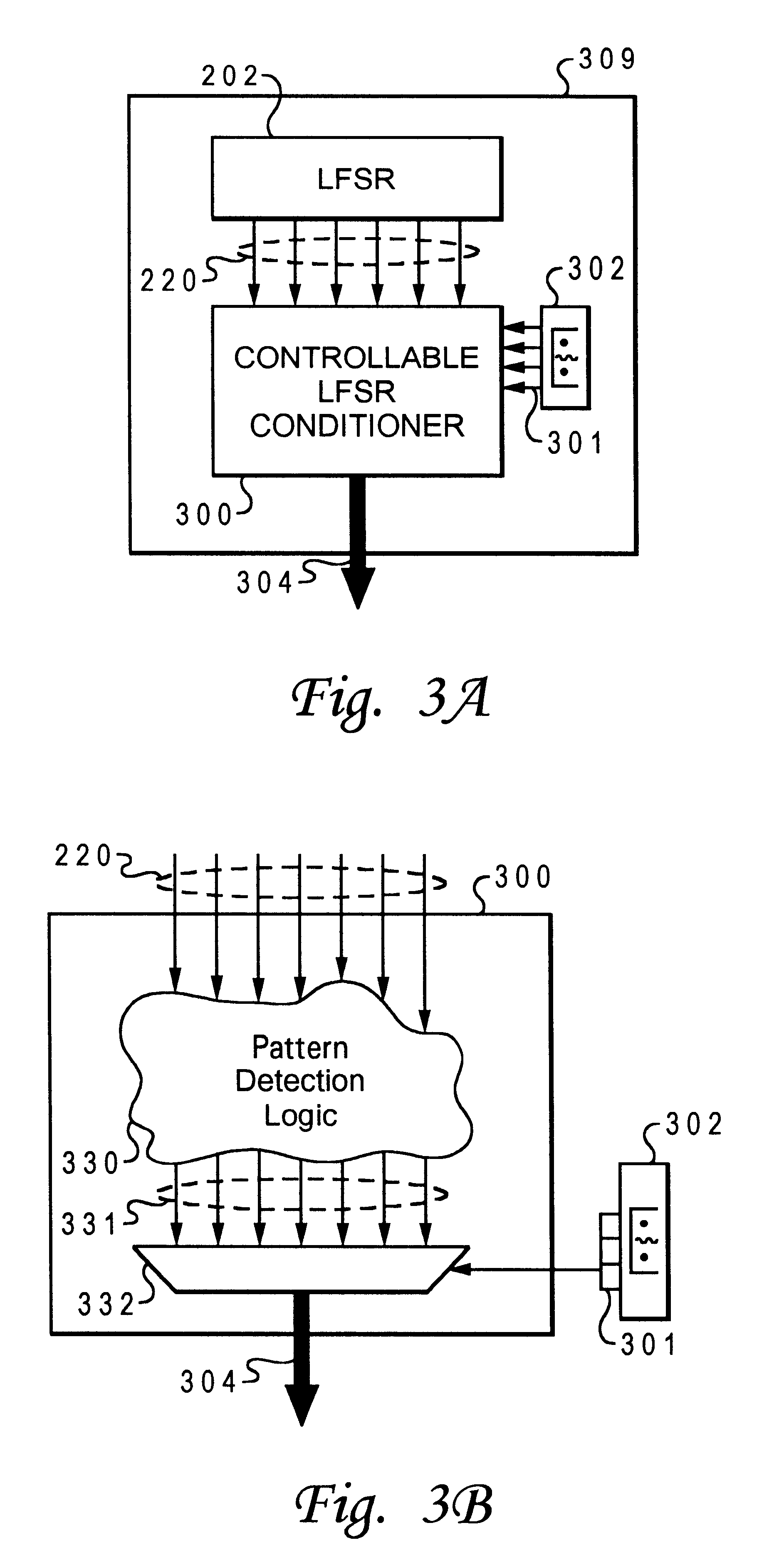
Method and system for run-time logic verification of operations in digital systems
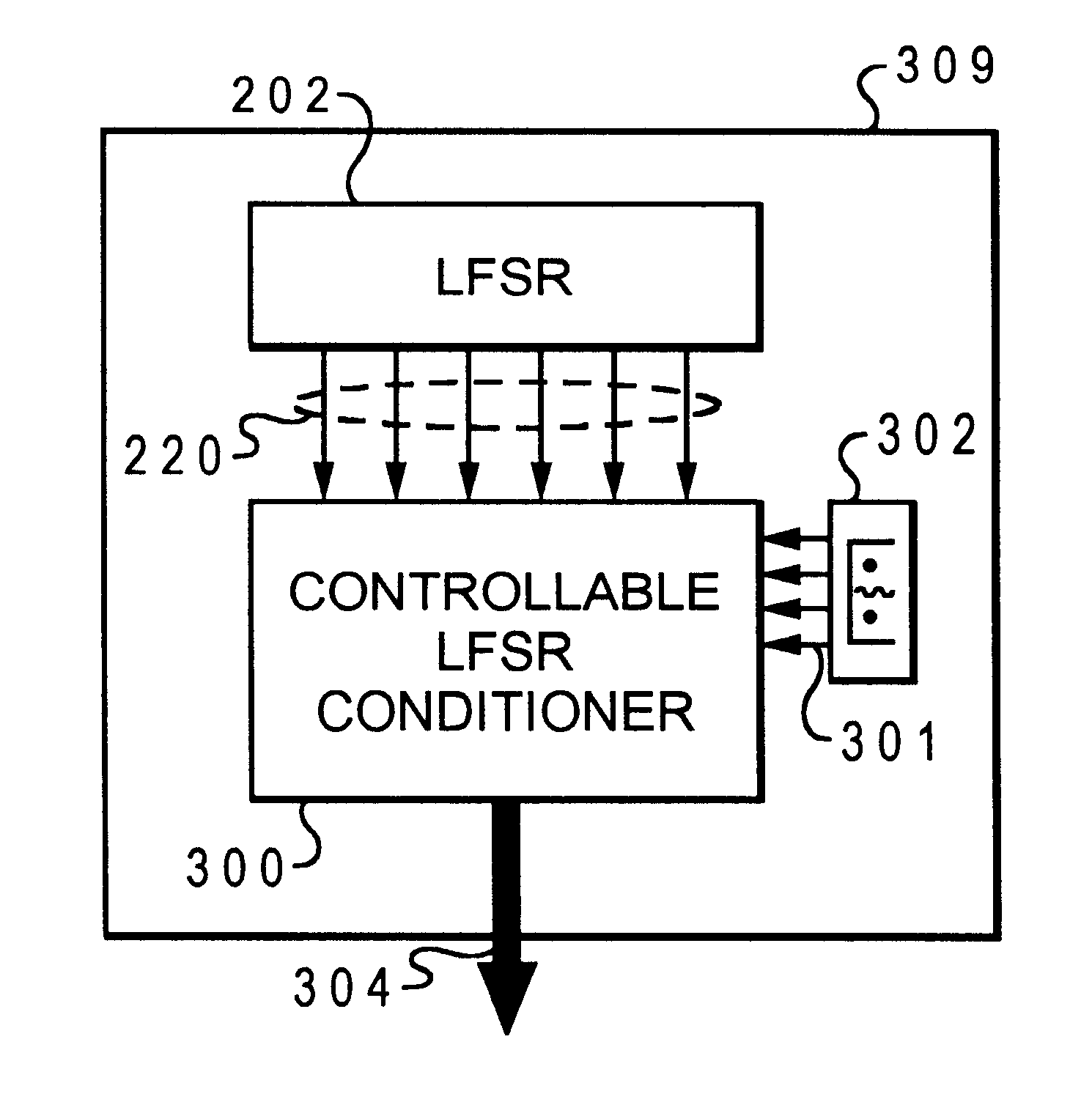
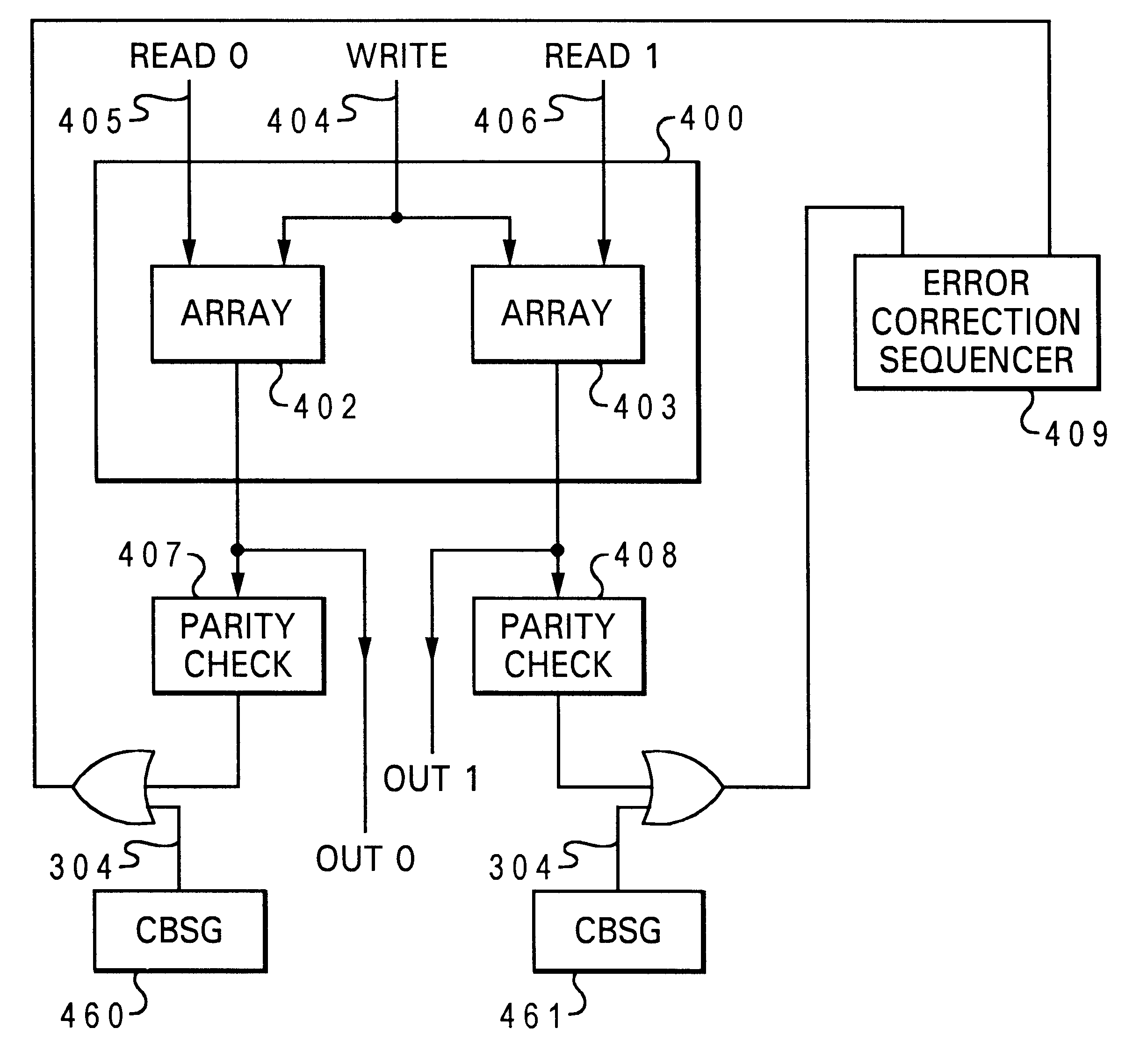
InactiveUS6590929B1Random number generatorsError detection/correctionRuntime verificationRunning time
A system for controllable run-time verification of operations in a logic structure of a digital system. The system comprises a controllable bit stream generator which produces a controlled bit stream output. The controlled bit stream output corresponds to a bit sequence which instantiates a verification of operations within the logic structure. The system also comprises means for coupling the controlled bit stream output to the logic structure to verify the operations of the logic structure.
Owner:IBM CORP
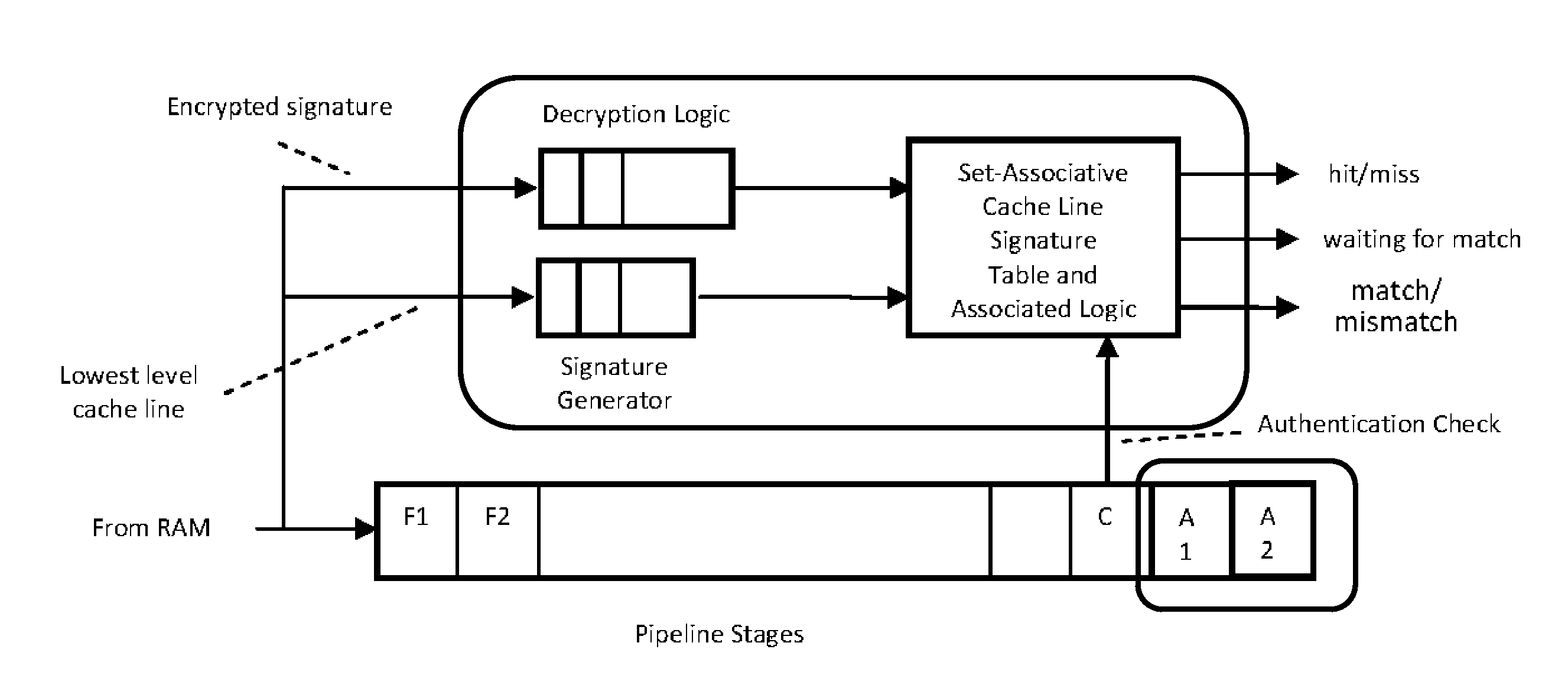
System and method for validating program execution at run-time
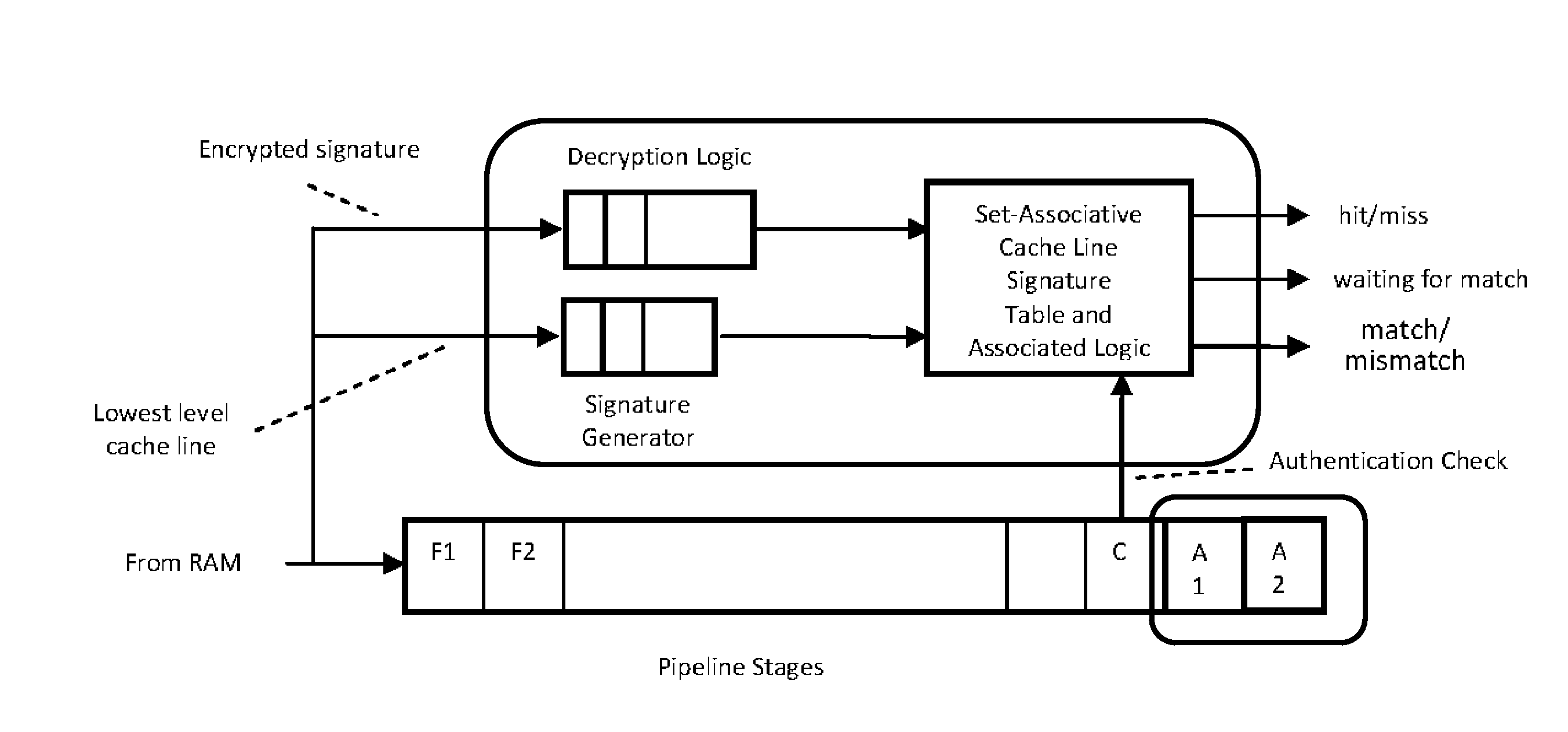
ActiveUS8782434B1Avoid procrastinationLong executionUser identity/authority verificationDigital computer detailsDigital signatureRuntime verification
A pipelined processor comprising a cache memory system, fetching instructions for execution from a portion of said cache memory system, an instruction commencing processing before a digital signature of the cache line that contained the instruction is verified against a reference signature of the cache line, the verification being done at the point of decoding, dispatching, or committing execution of the instruction, the reference signature being stored in an encrypted form in the processor's memory, and the key for decrypting the said reference signature being stored in a secure storage location. The instruction processing proceeds when the two signatures exactly match and, where further instruction processing is suspended or processing modified on a mismatch of the two said signatures.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
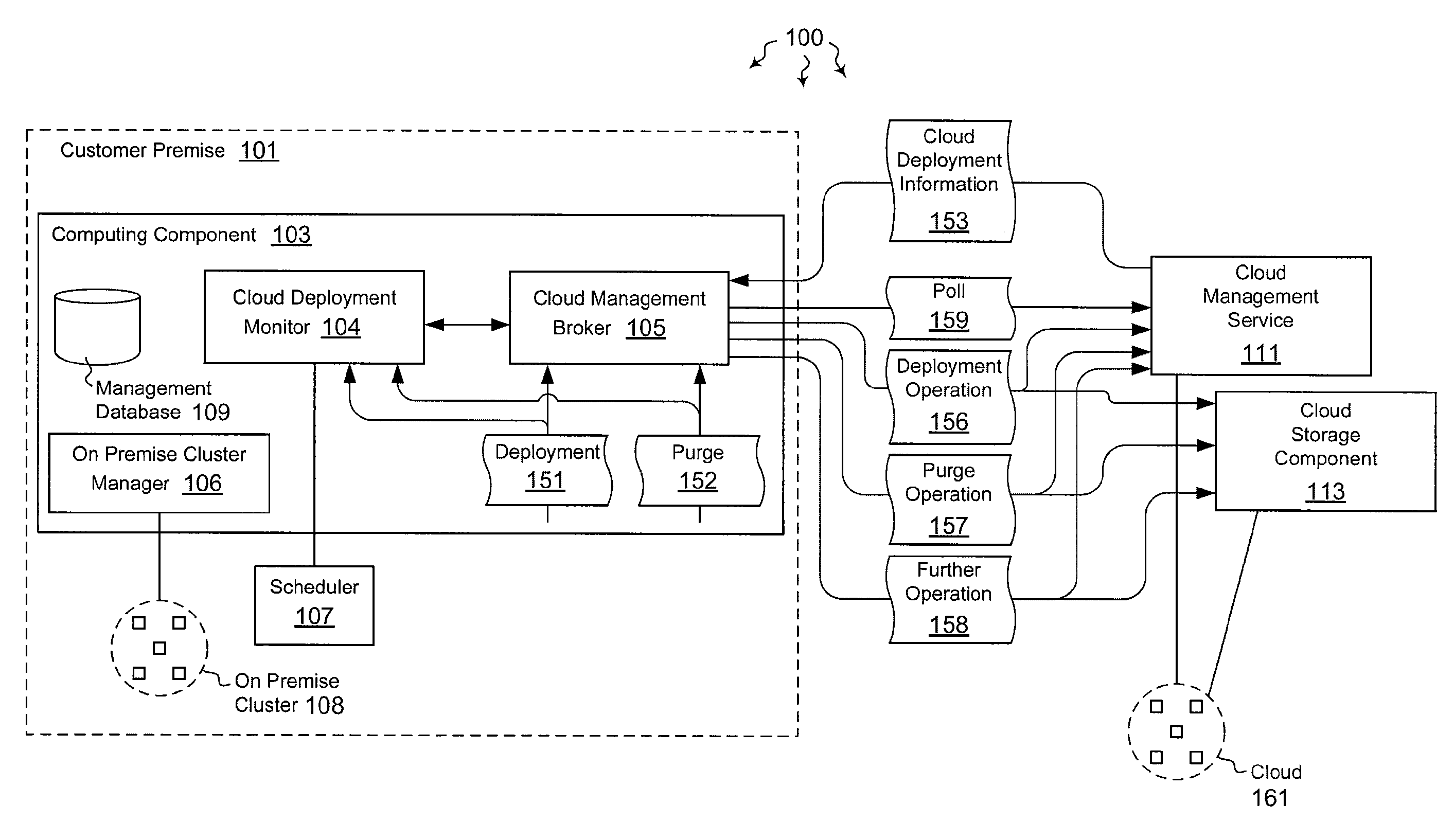
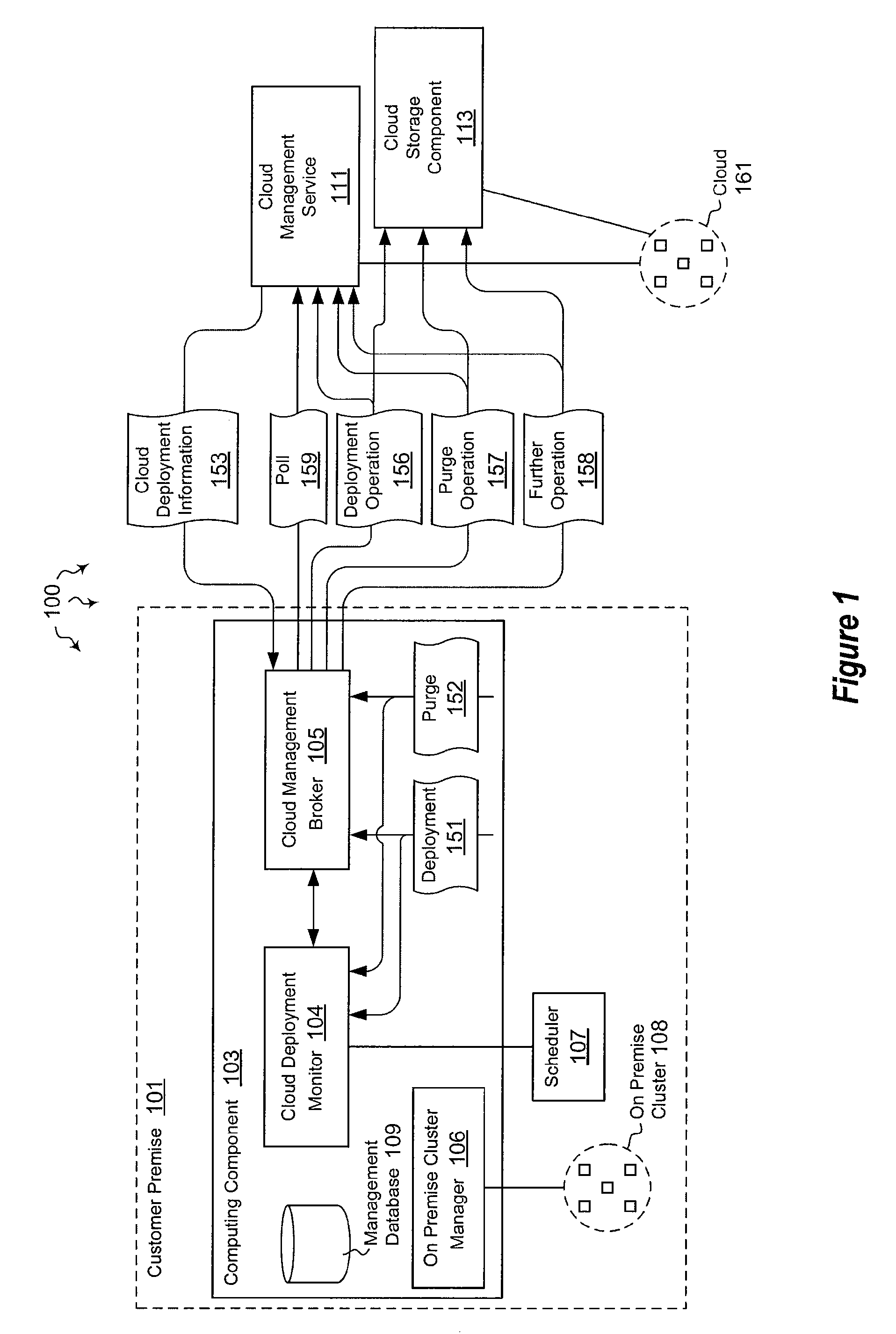
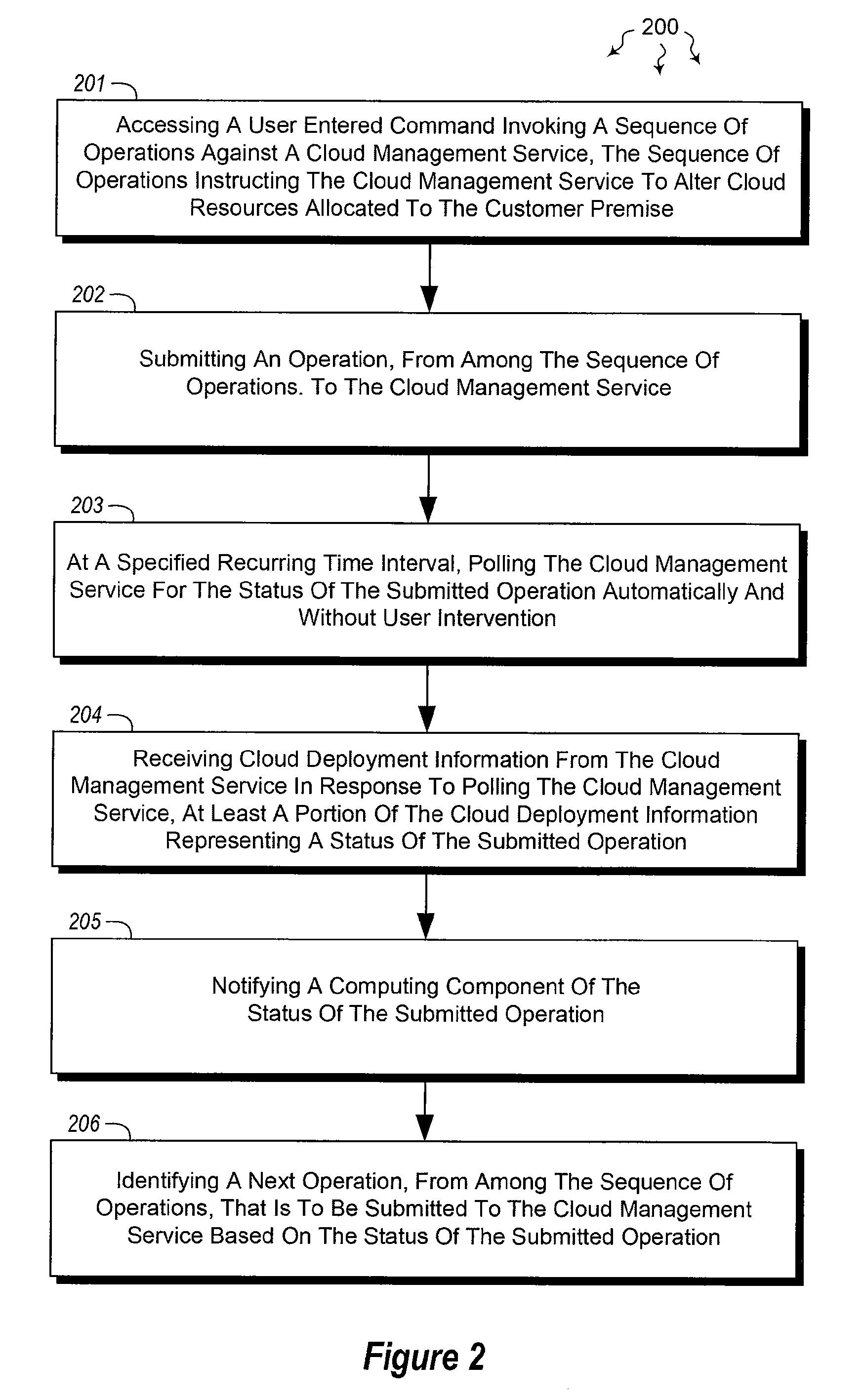
Monitoring cloud-runtime operations
ActiveUS20120072579A1Well formedError detection/correctionDigital computer detailsCloud baseRuntime verification
The present invention extends to methods, systems, and computer program products for monitoring cloud-runtime operations. Embodiments of the invention include an infrastructure for initiating and monitoring (e.g., asynchronous) cloud-runtime operations. In some embodiments, cloud-runtime operations are included in a sequence of operations (e.g., in a workflow) for deploying or purging cloud based resources for a customer premise. Accordingly, monitored operations include creating cloud deployments, growing cloud deployments, shrinking cloud deployments, and deleting cloud deployments. Cloud deployments can be reliably deleted when a workflow is aborted, to prevent accrual of unexpected charges.
Owner:MICROSOFT TECH LICENSING LLC
Authenticatable software modules
InactiveUS20050188214A1Authentication is convenientUnauthorized memory use protectionHardware monitoringRuntime verificationRunning time
In various embodiments of the present invention, a first software entity, such as a program, routine, library, or module, authenticates a second software entity by extracting an authentication block from memory, validating the extracted authentication block, and comparing a value stored in the authentication block with a computable or pre-computed authentication value in order to authenticate the second software entity. In certain alternative embodiments, a program can authenticate itself at run-time. Additional embodiments of the present invention include methods for constructing and inserting authentication blocks into software entities to facilitate authentication by the authentication methods that represent embodiments of the present invention.
Owner:HEWLETT PACKARD DEV CO LP
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082329A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Method and system for generating a normalized configuration model
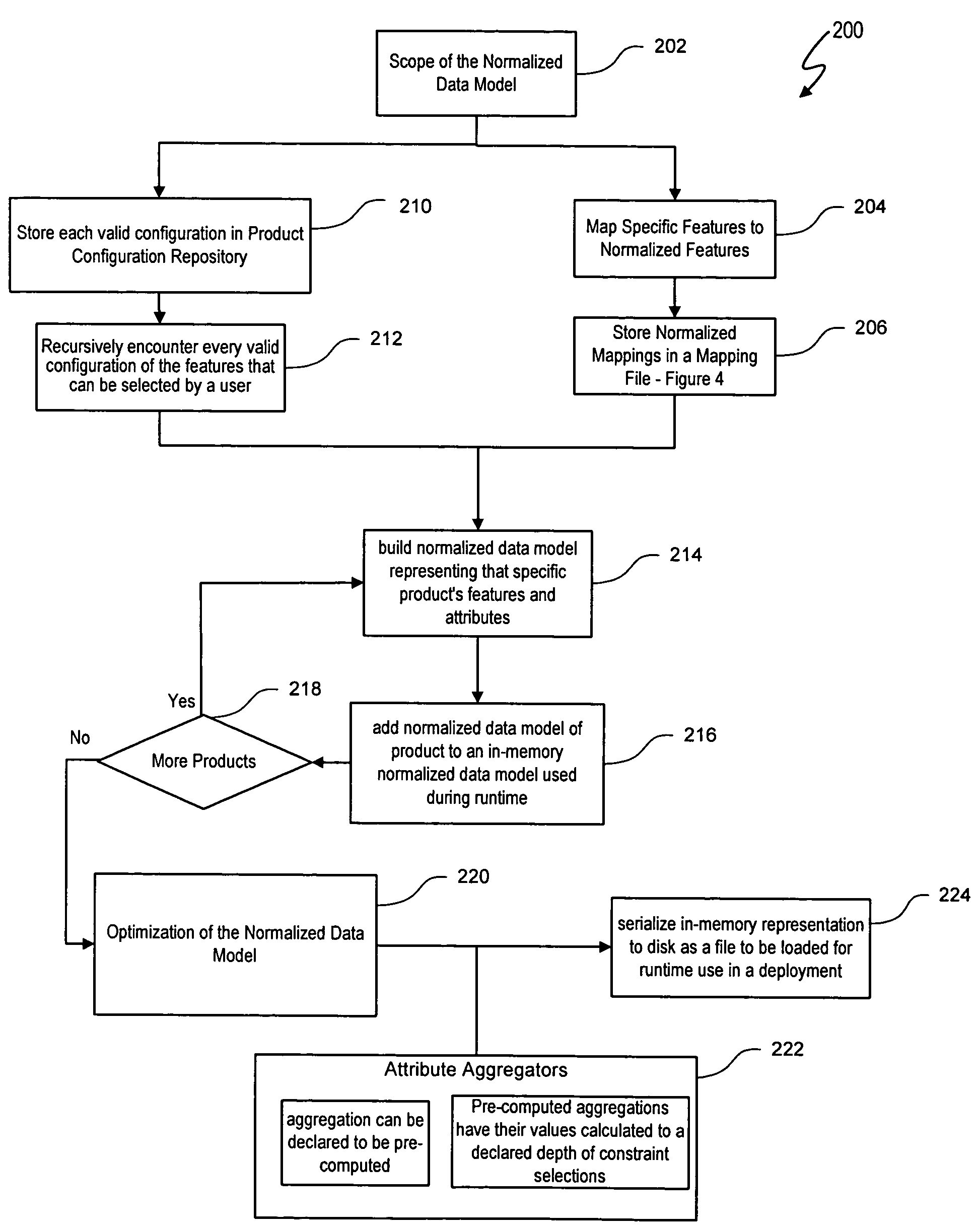
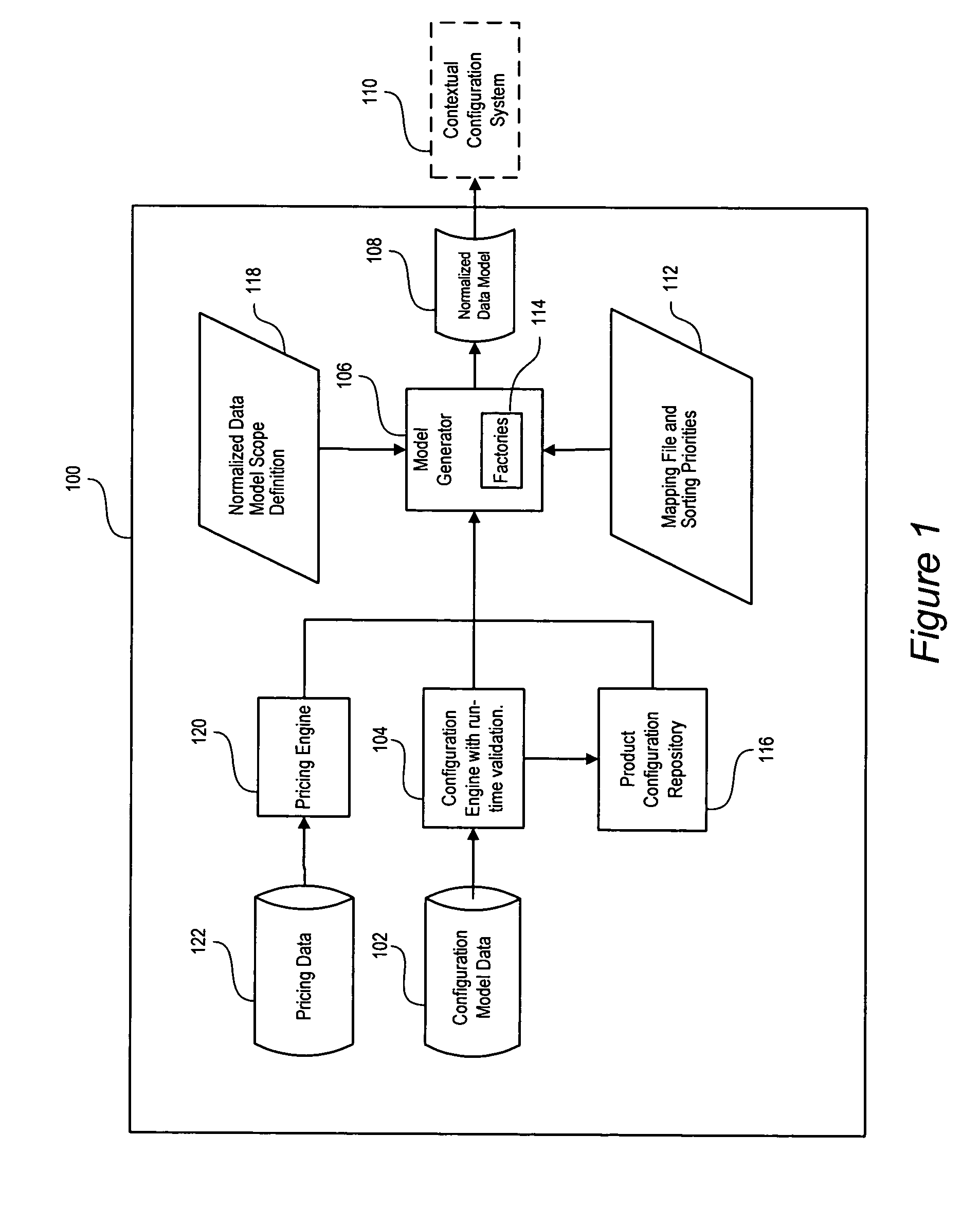
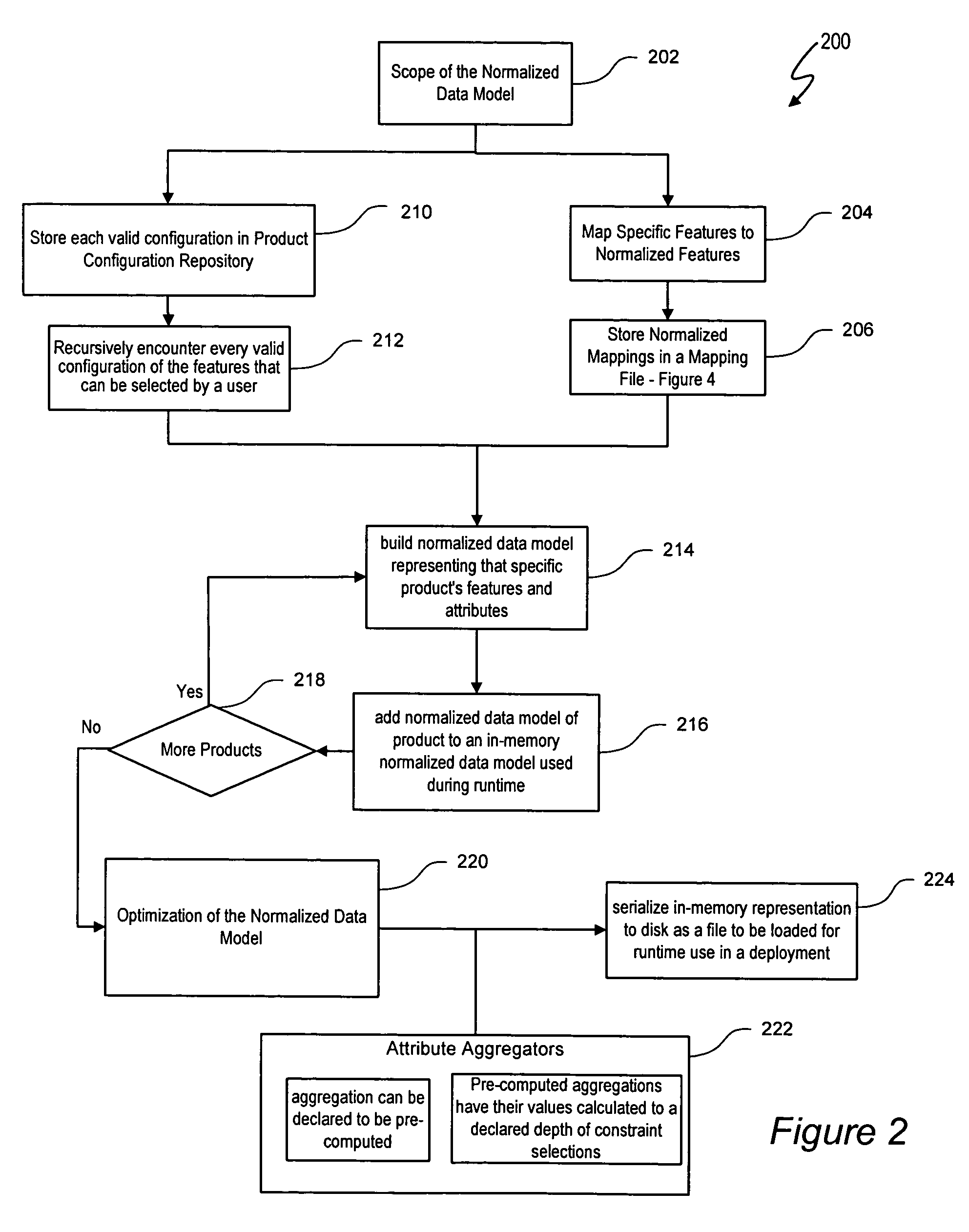
Normalized data models are programmatically generated from a combination of product configuration model data, product configuration engine runtime validation, normalized data mappings, and settings files declaring the scope of model content. A master model generation process effectively transforms conventional configuration data into normalized configuration data. The normalized configuration data allows a user to, for example, conduct comparative product configurations. In one embodiment, a normalized model generation process generates normalized data model representing attributes and normalized features of a product. In one embodiment, the normalized configuration data model is then added to in-memory data structures used during runtime contextual configuration analysis, thus reducing the total number of data items preserved as efficiencies result from eliminating duplication and effective use of search structures. In-memory representation of the normalized configuration data model can then be serialized to disk as a file to be loaded for runtime use in a deployment.
Owner:VERSATA DEV GROUP
Method and system for run-time logic verification of operations in digital systems in response to a plurality of parameters
InactiveUS6457147B1Electronic circuit testingError detection/correctionRuntime verificationTheoretical computer science
A system for run-time verification of operations within a logic structure of a digital system. The system comprises of a controllable bit stream generator for simulating an occurrence of a data travelling through said logic structure at a desired time. It also comprises of means for selecting a characteristic of the data where the characteristic includes how to verify the logic structure, and means for verifying the logic structure utilizing a combination of a controlled bit stream output of the controllable bit stream generator and the characteristic of the data.
Owner:IBM CORP
Method and device for verification of code module in virtual machine
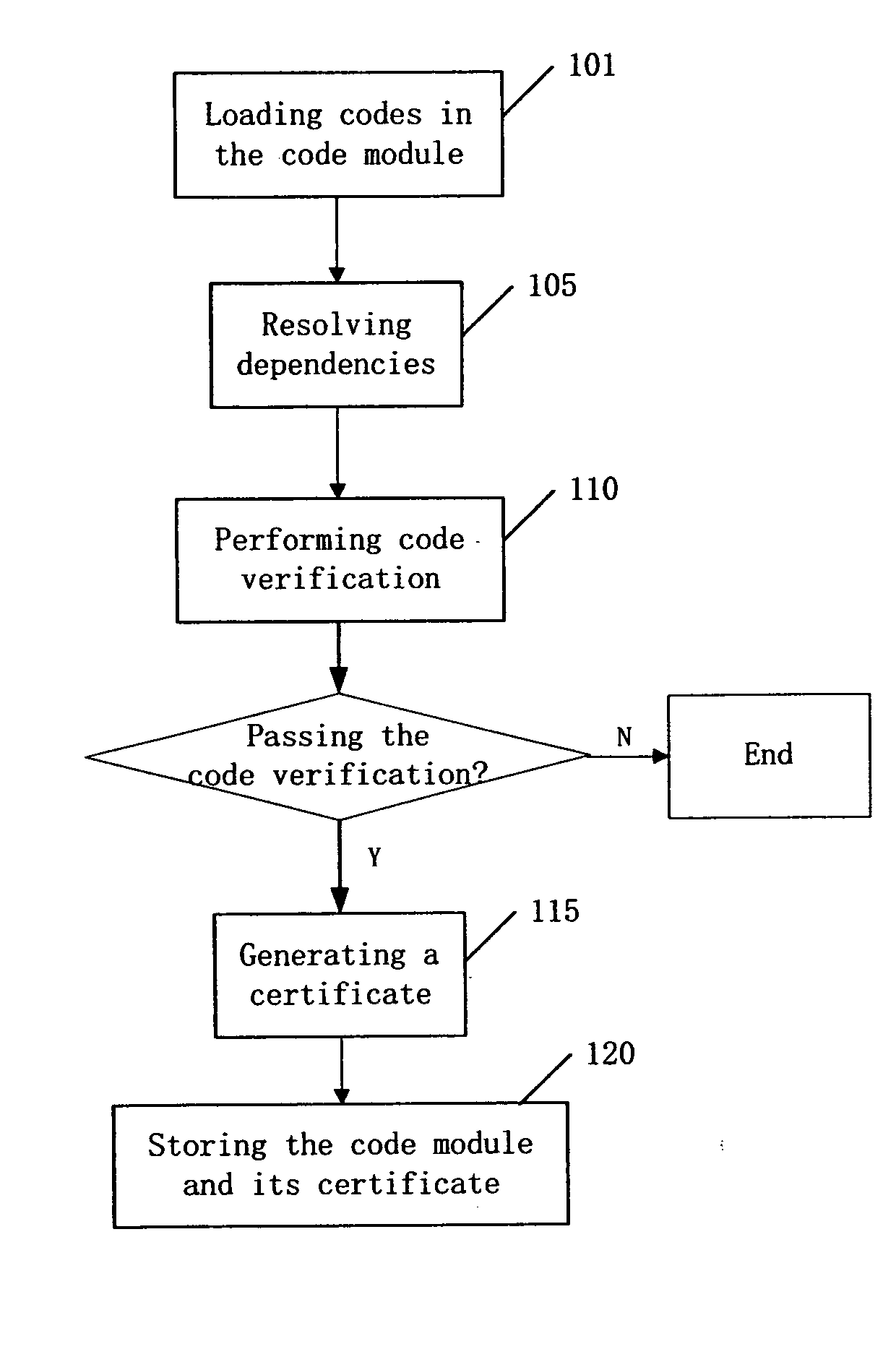
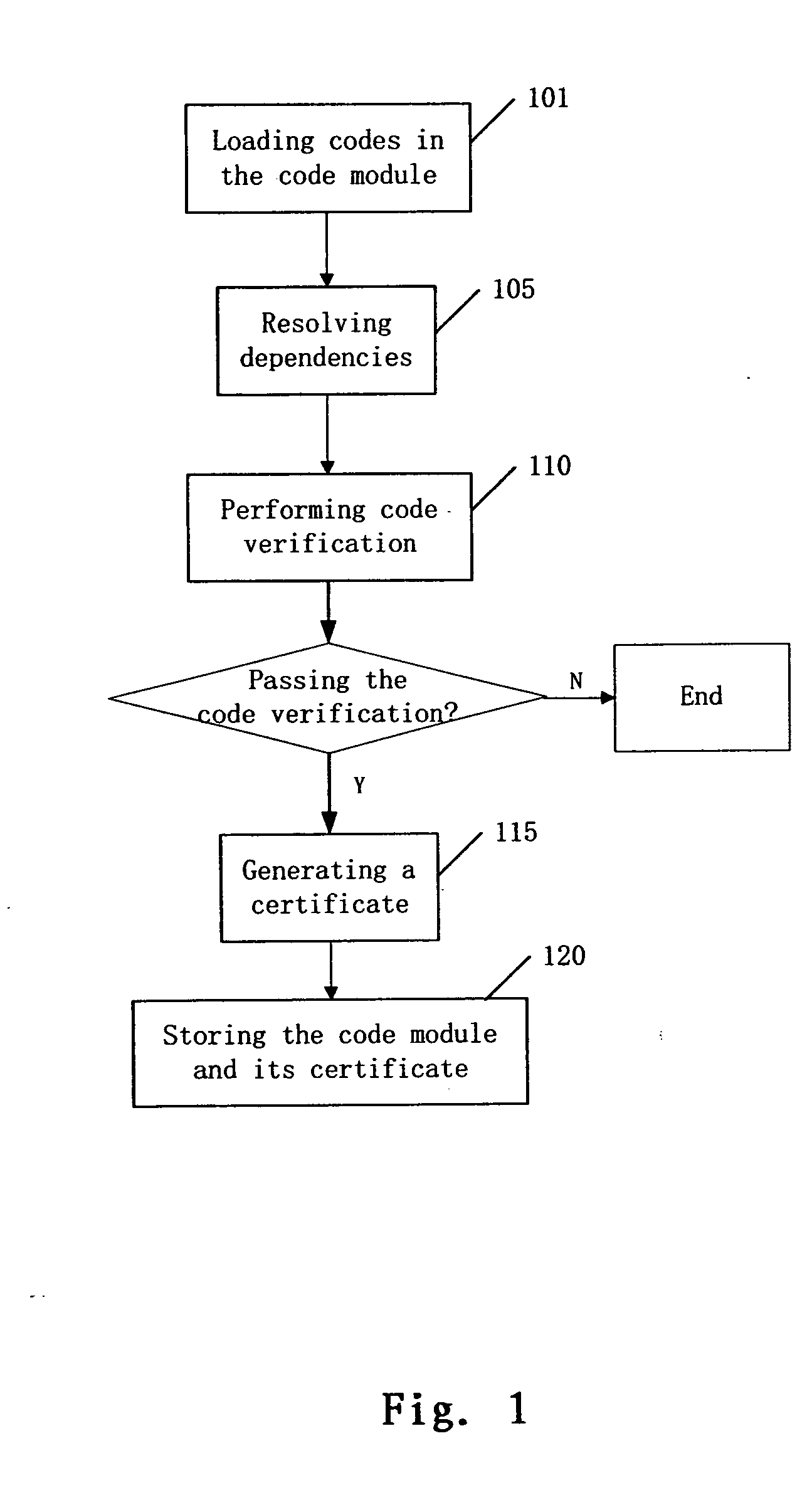
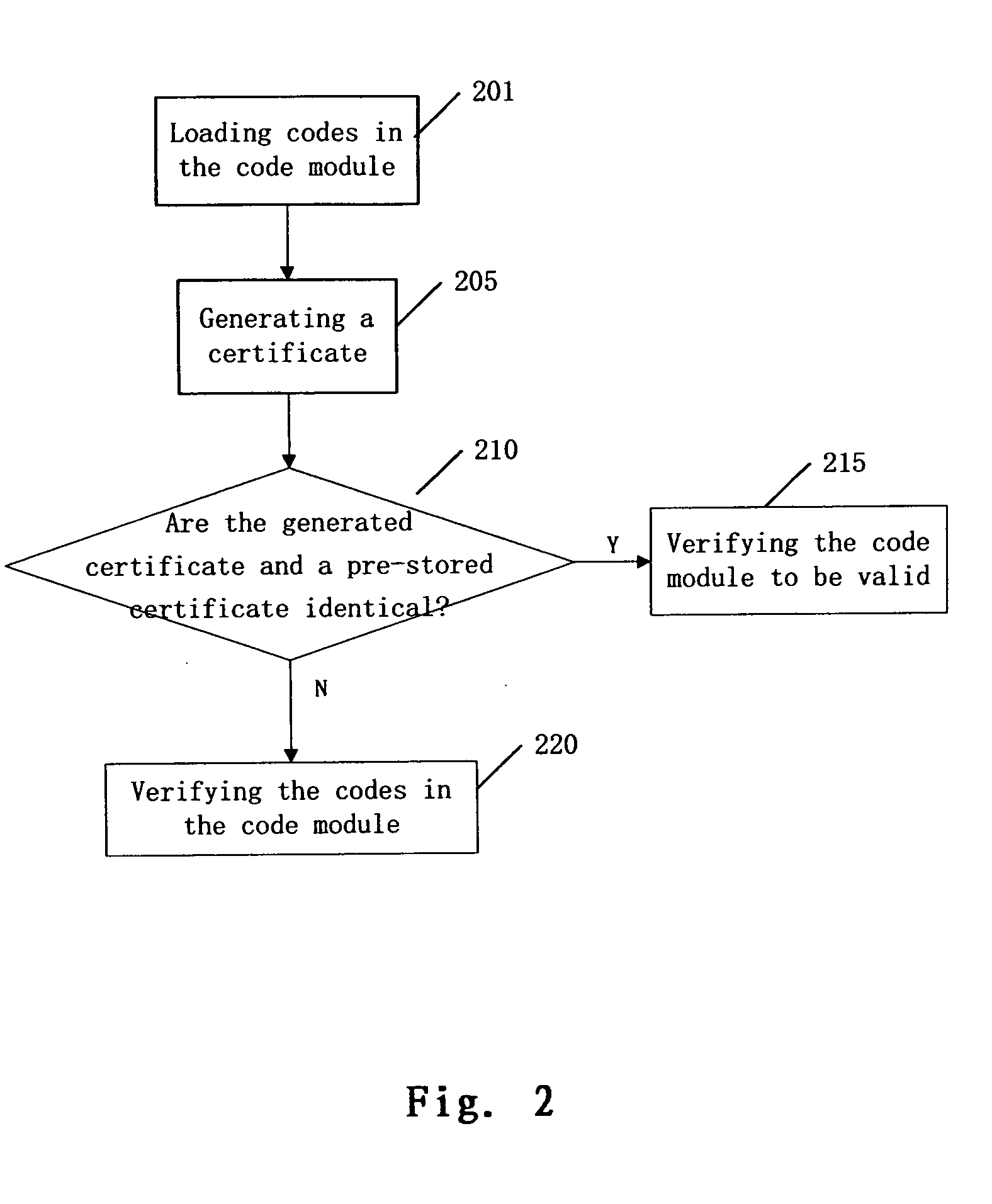
InactiveUS20080209556A1Unnecessary to performReduce run-time overheadMemory loss protectionDigital data processing detailsCode moduleRuntime verification
A method for pre-verification of a code module when the code module is installed or updated in a virtual machine, comprising: loading codes in the installed or updated code module; performing code verification on the codes in the code module; if the code verification is passed, generating a certificate of the code module; and storing the code module passing the code verification and its certificate. The present invention also discloses a method for verification of a code module at runtime of the code module in a virtual machine, comprising loading codes in the code module; generating a certificate of the code module based on the loaded codes; if the generated certificate of the code module and a pre-stored certificate of the code module are identical, verifying the code module to be valid; otherwise performing a pre-verification on the code module.
Owner:IBM CORP
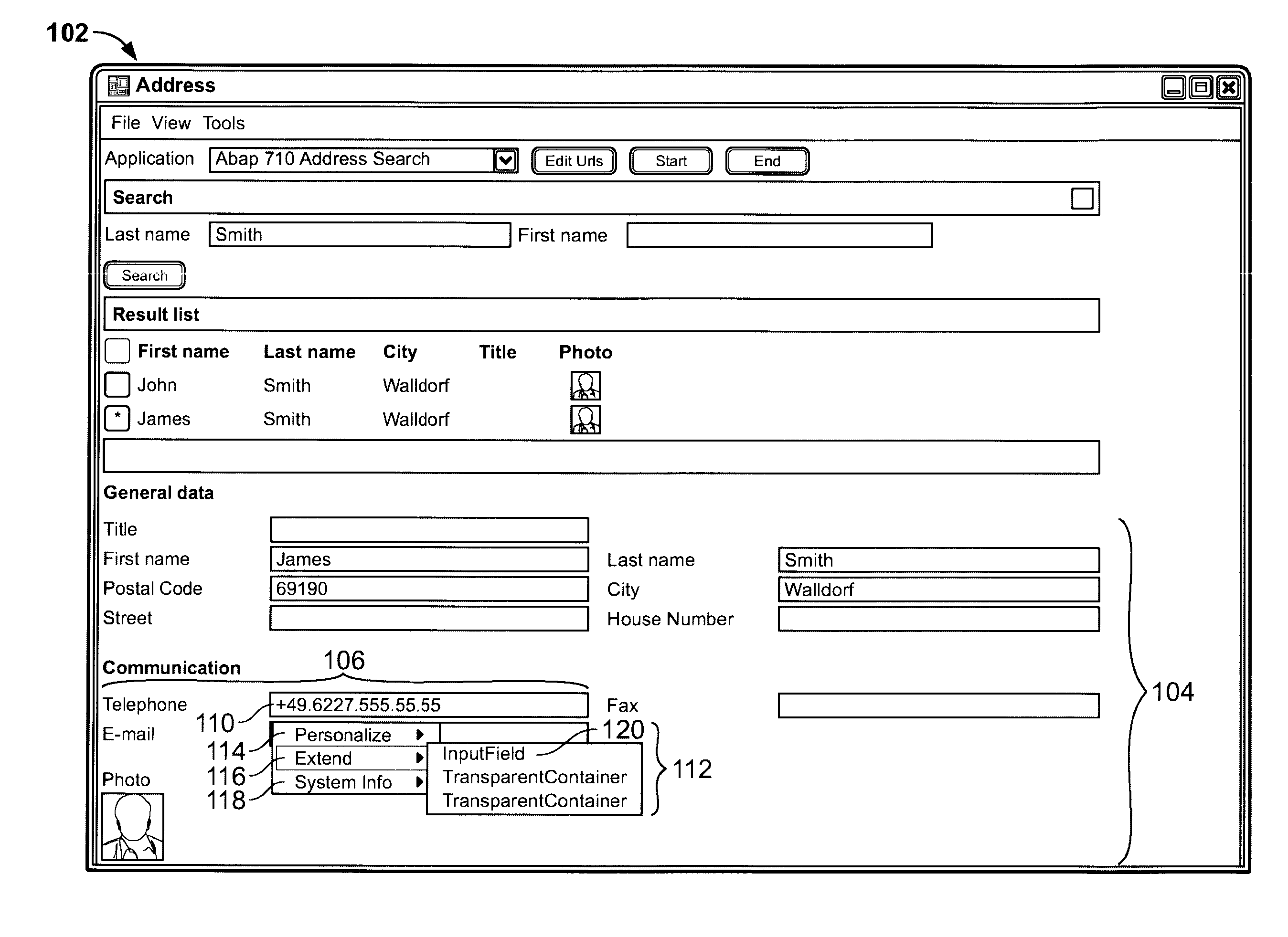
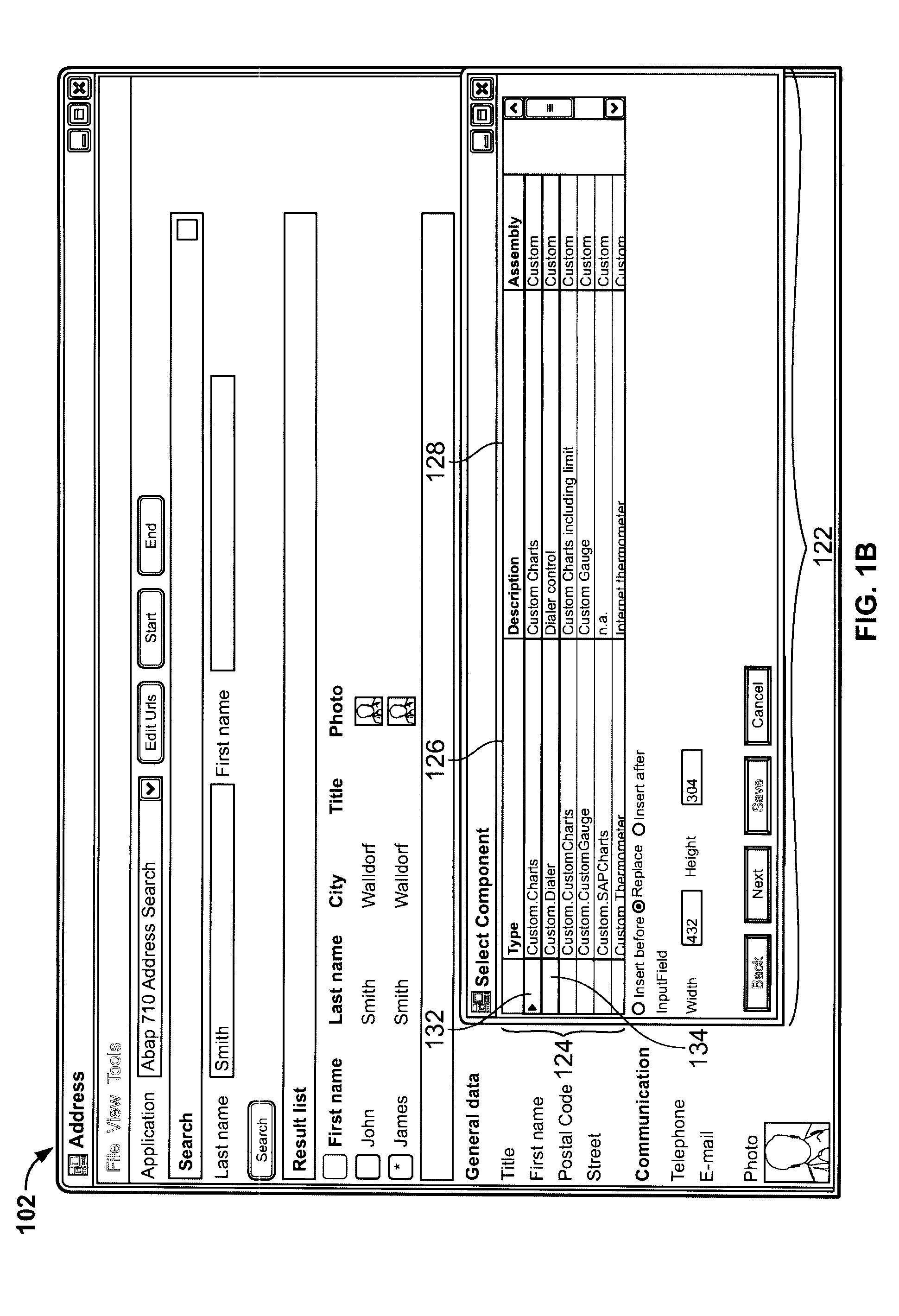
Runtime Modification of Client User Controls
ActiveUS20080016555A1Digital data processing detailsUser identity/authority verificationGraphicsGraphical user interface
Methods and apparatus, including computer program products, for modifying a user interface of a client application. A method includes rendering a graphical user interface of a client application having a first and second control coupled to the client application, receiving user-generated input characterizing a request to modify the first control and a selection of a third control; exchanging the first control with the third control; rendering the graphical user interface of the client application as having the third control in lieu of the first control; receiving user-generated input characterizing interaction with the second control; and rendering the third control to reflect the interaction with the second control.
Owner:SAP AG
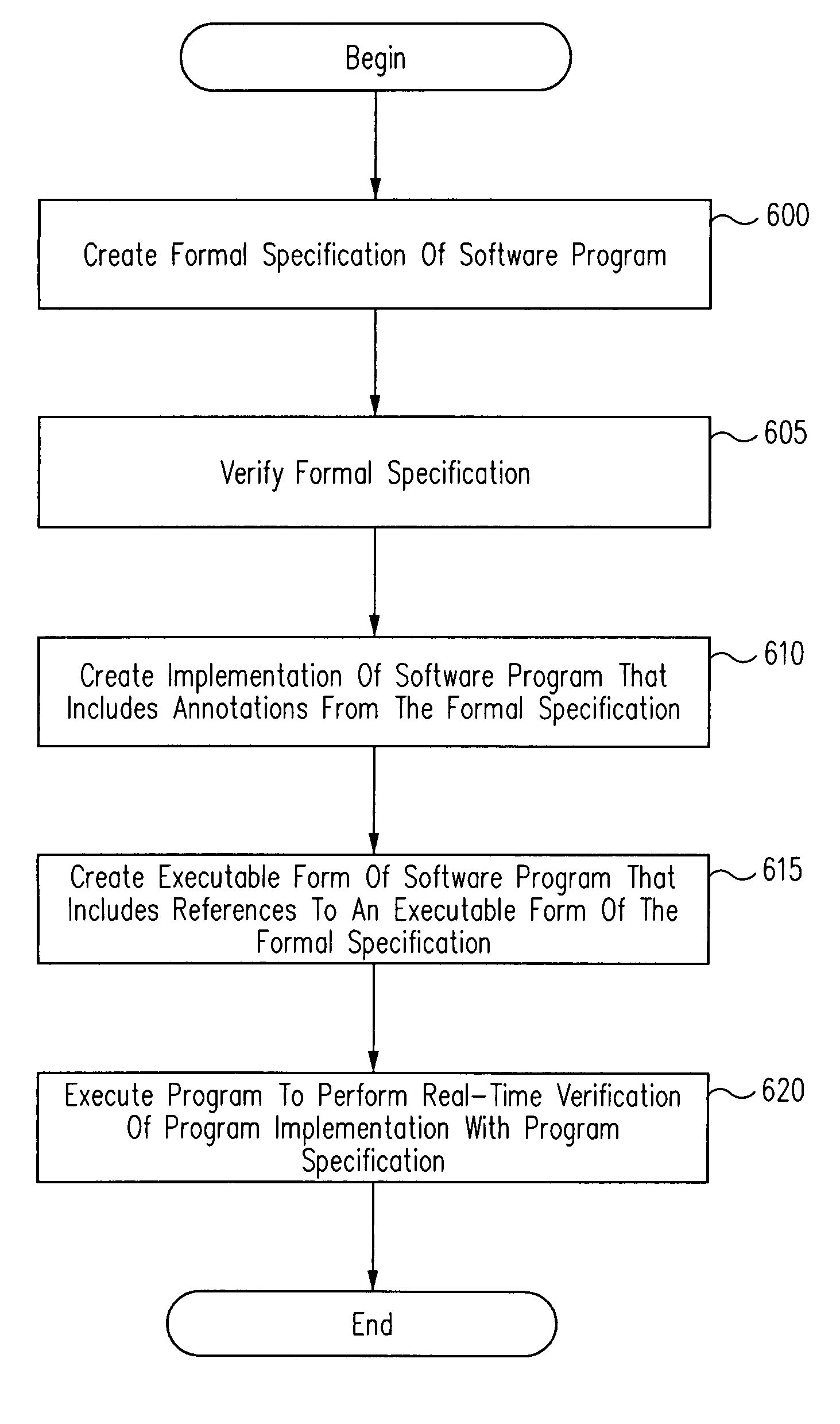
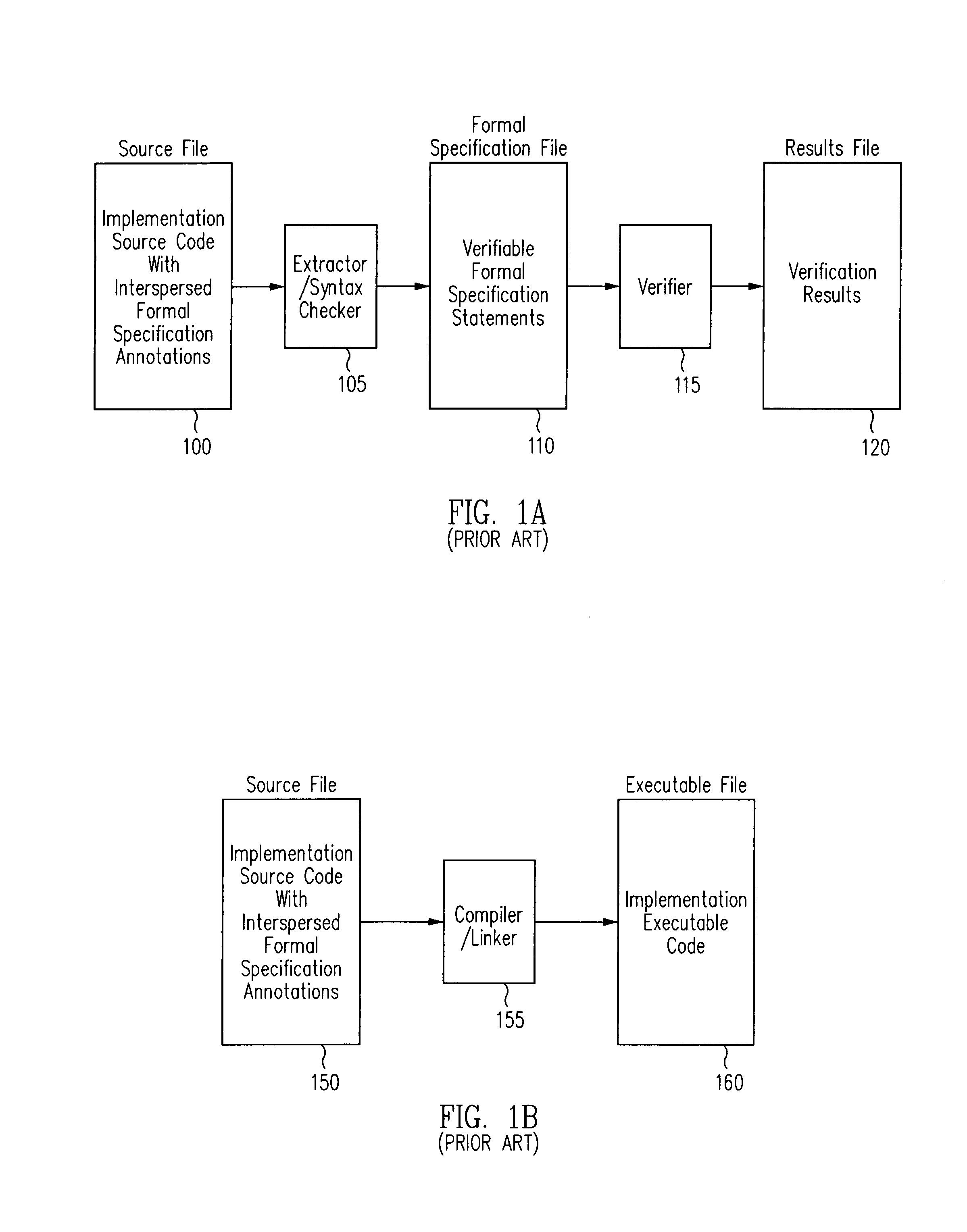
Run-time verification of annotated software code
Verification of a software program may be automated by receiving a program source file comprising program source code and at least one formal specification annotation, extracting the at least one formal specification annotation from the program source file, compiling the program source code and linking the compiled program and the at least one extracted formal specification annotation to create an executable program that includes at least one reference to an executable formal specification module. According to one aspect, a virtual machine includes a target virtual machine for executing one or more program implementation instructions, and a formal virtual machine for executing one or more formal specification modules corresponding to one or more program implementation instructions and configured to call a formal specification module, and to compare a first result obtained by executing the program implementation instructions with a second result obtained by the call to the formal specification module.
Owner:ORACLE INT CORP
System and method for validating program execution at run-time
ActiveUS20140325238A1Long executionLittle and delayUnauthorized memory use protectionHardware monitoringDigital signatureRuntime verification
A pipelined processor comprising a cache memory system, fetching instructions for execution from a portion of said cache memory system, an instruction commencing processing before a digital signature of the cache line that contained the instruction is verified against a reference signature of the cache line, the verification being done at the point of decoding, dispatching, or committing execution of the instruction, the reference signature being stored in an encrypted form in the processor's memory, and the key for decrypting the said reference signature being stored in a secure storage location. The instruction processing proceeds when the two signatures exactly match and, where further instruction processing is suspended or processing modified on a mismatch of the two said signatures.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Graphical user interface that is convertible at runtime
InactiveUS7904821B1Cathode-ray tube indicatorsExecution for user interfacesGraphicsGraphical user interface
An embodiment provides a method to change a graphical user interface in a way that supports runtime modification of an application's GUI without access to the application source code and / or needs no recompilation / restart of the application executable. This method allows the end-user to make runtime modifications of a widget's attributes and / or runtime conversion of widgets into different types of widgets.
Owner:TERTITSKI LEONID M +1
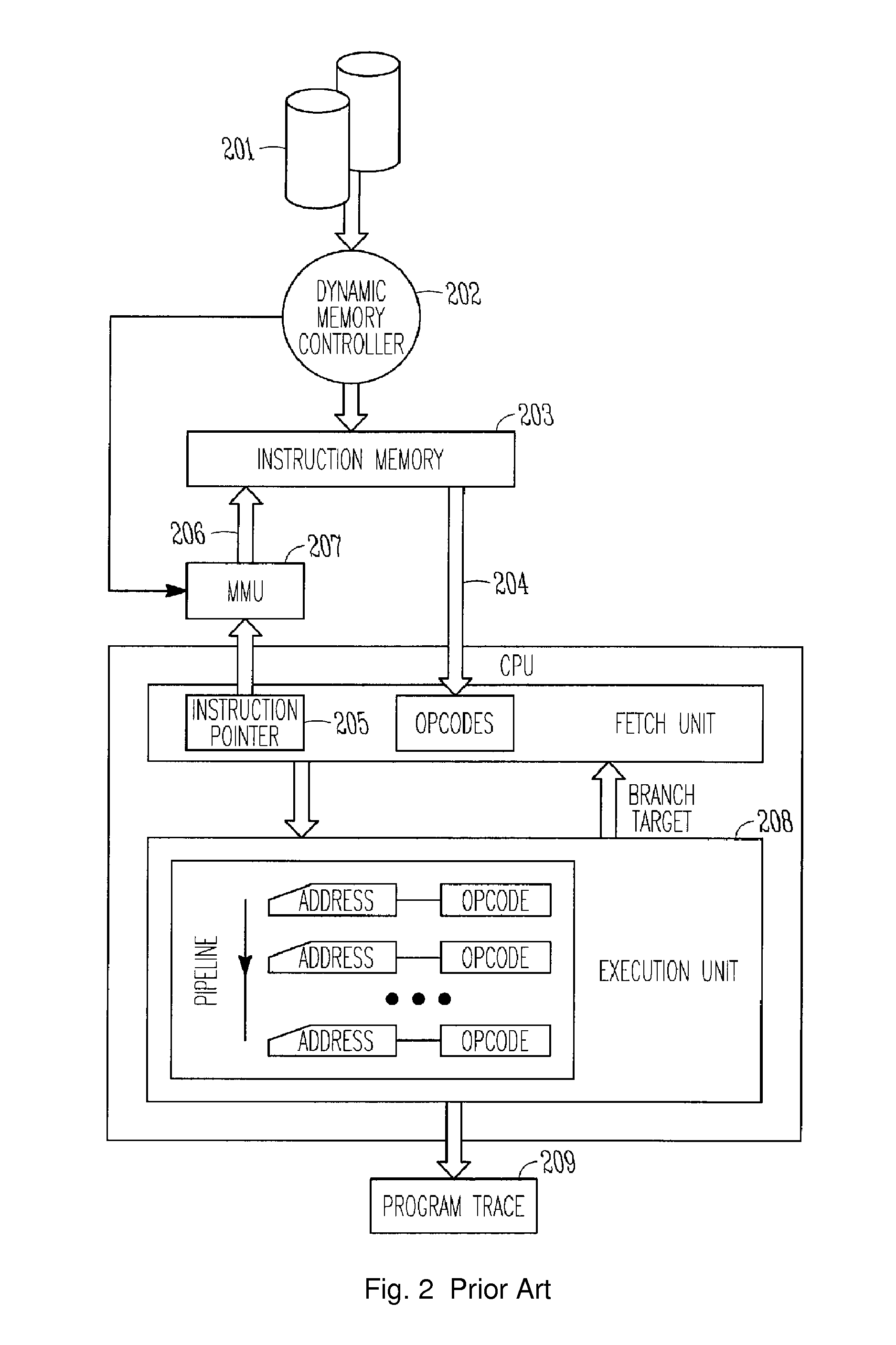
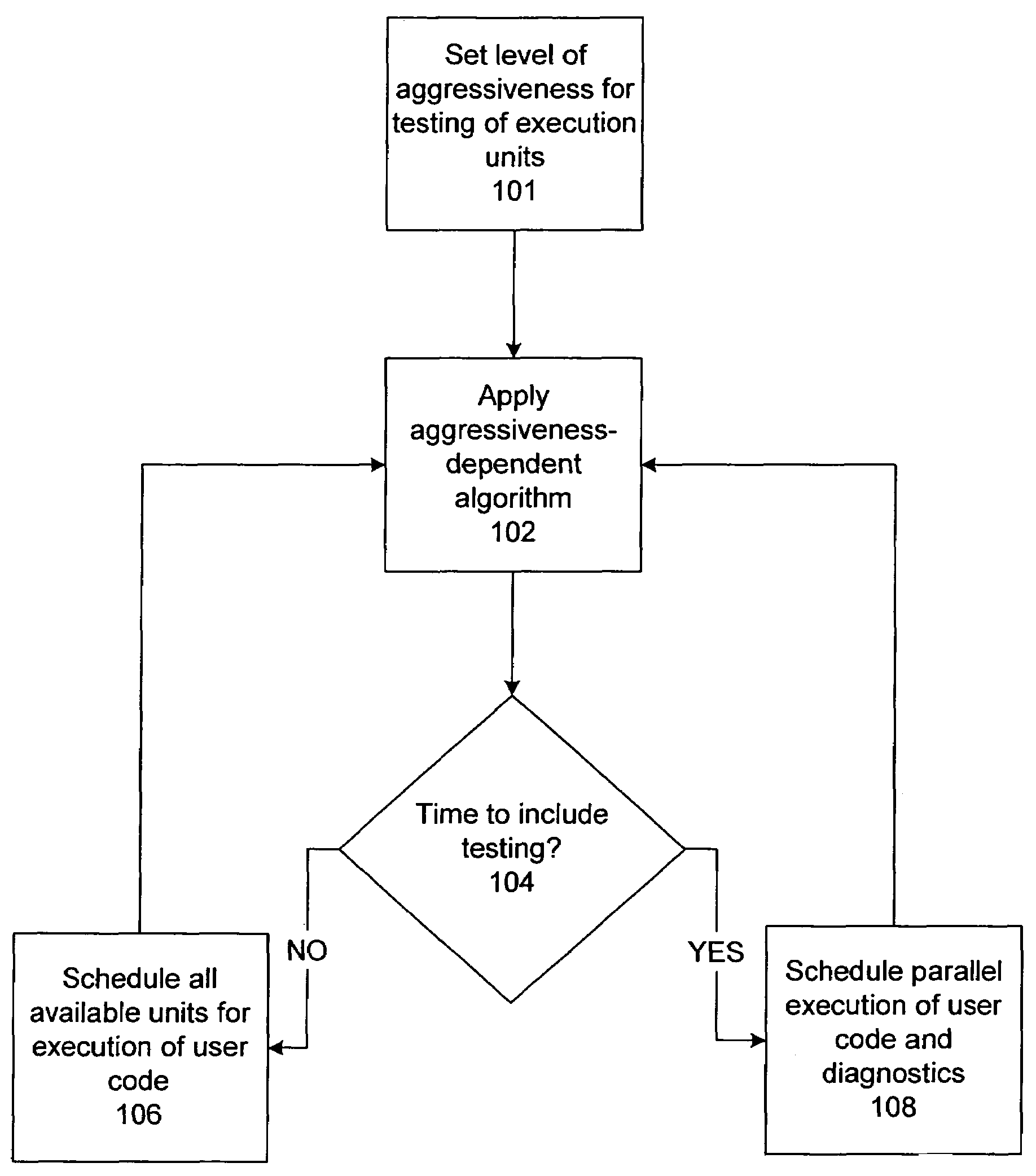
Runtime quality verification of execution units
InactiveUS7415700B2Program initiation/switchingFunctional testingRuntime verificationParallel computing
One embodiment disclosed relates to a method of compiling a program to be executed on a target microprocessor with multiple execution units of a same type. The method includes selecting one of the execution units for testing and scheduling the parallel execution of program code and diagnostics code. The diagnostic code is scheduled to be executed on the selected execution unit. The program code is scheduled to be executed on remaining execution units of the same type.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
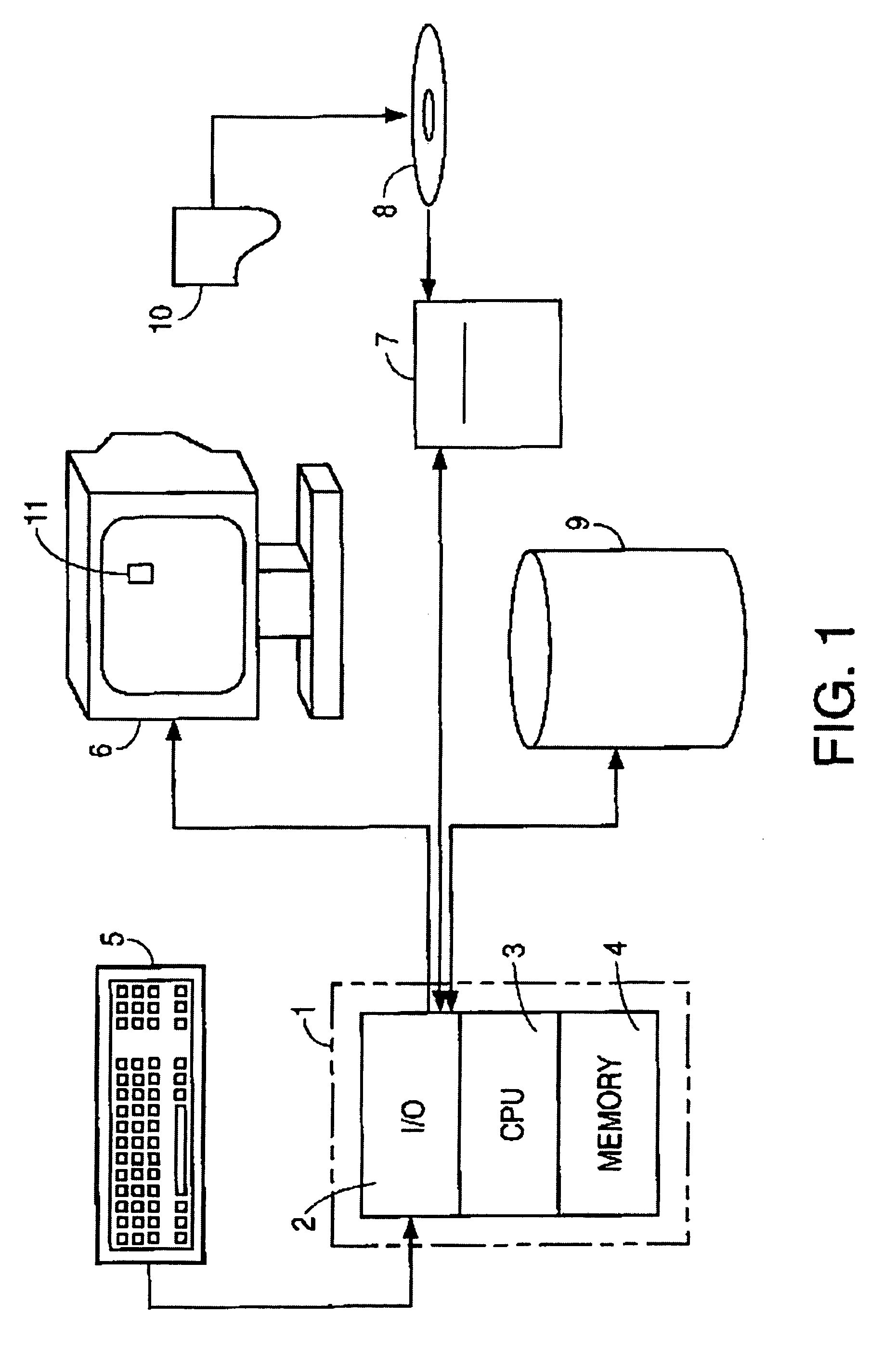
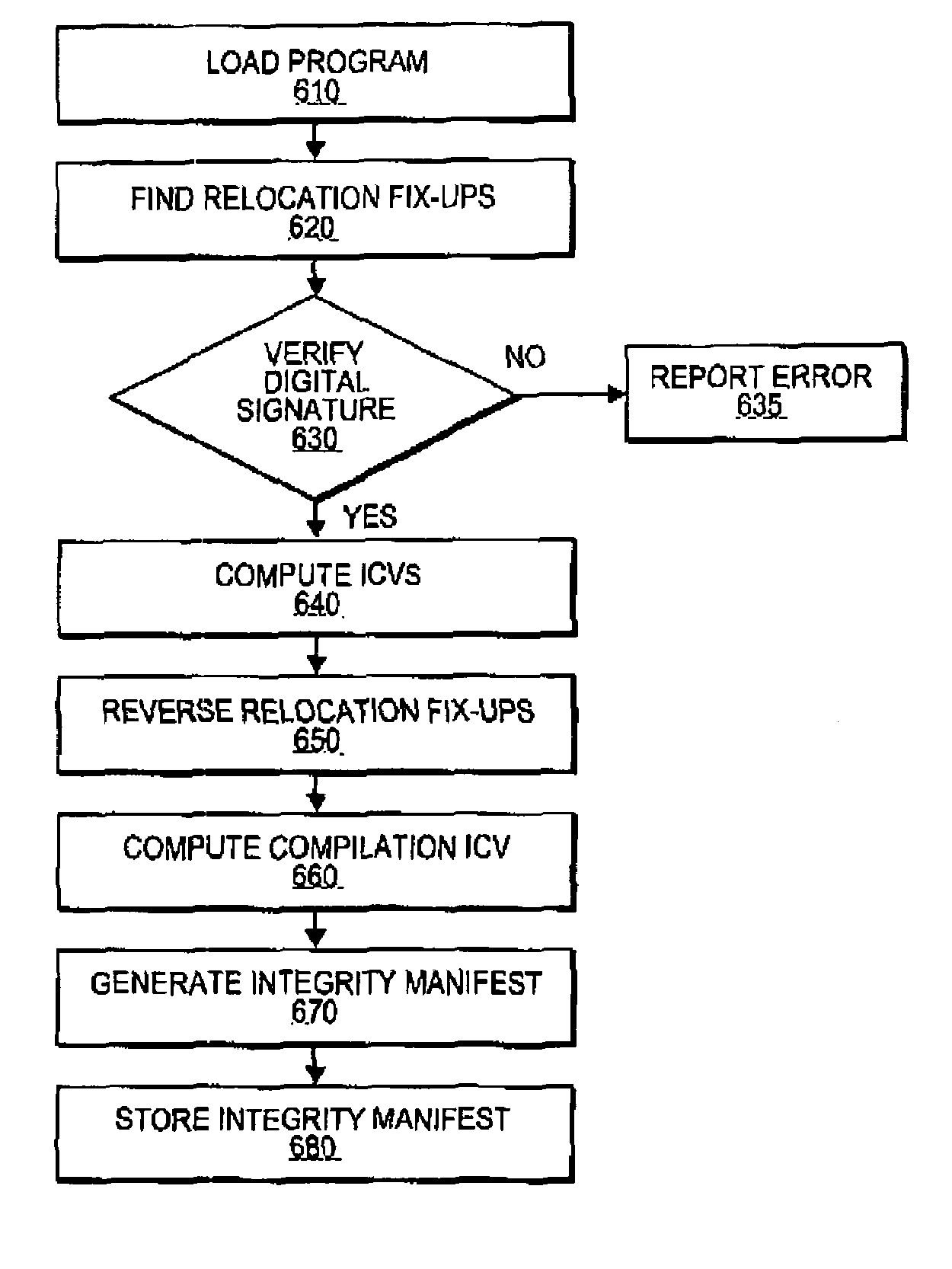
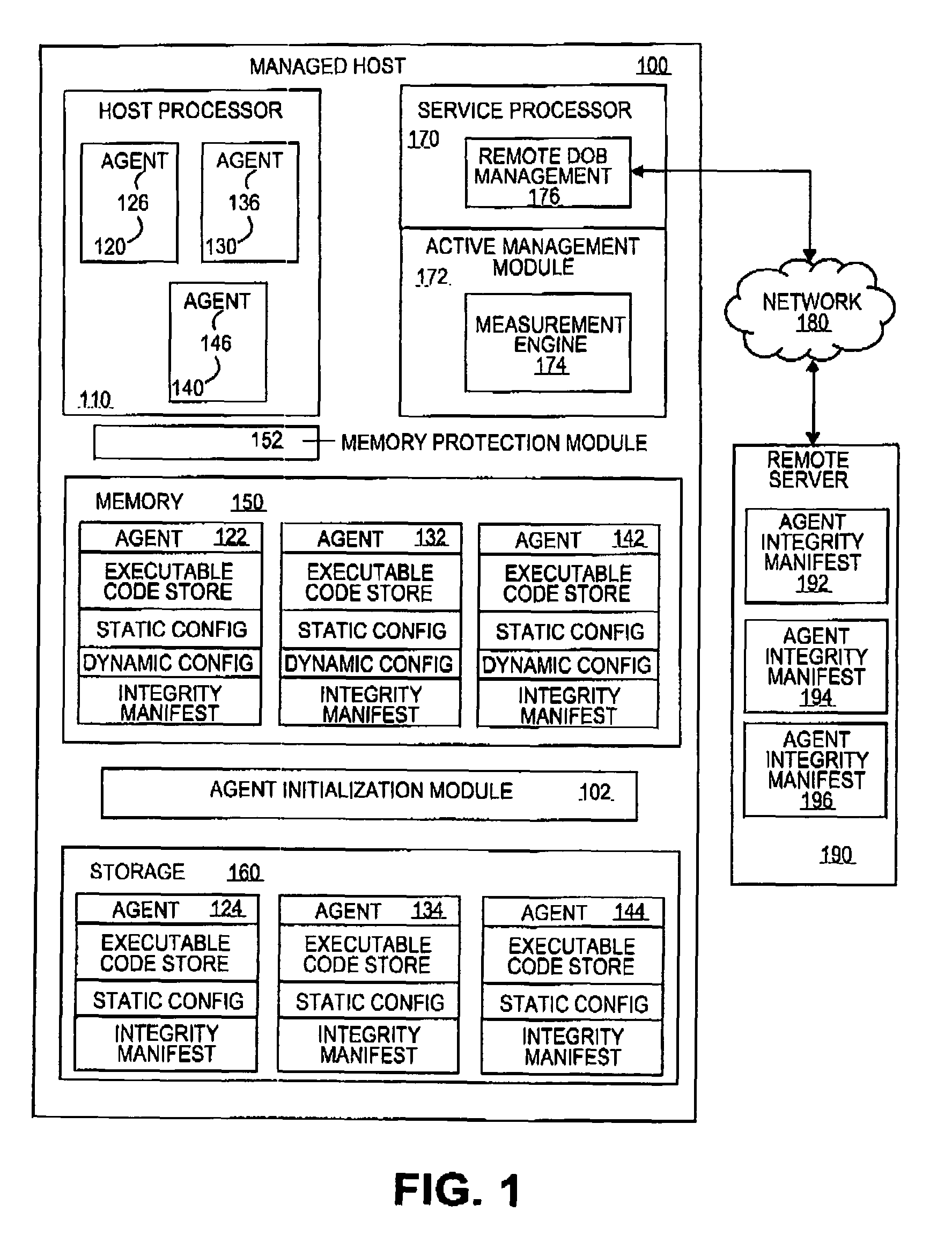
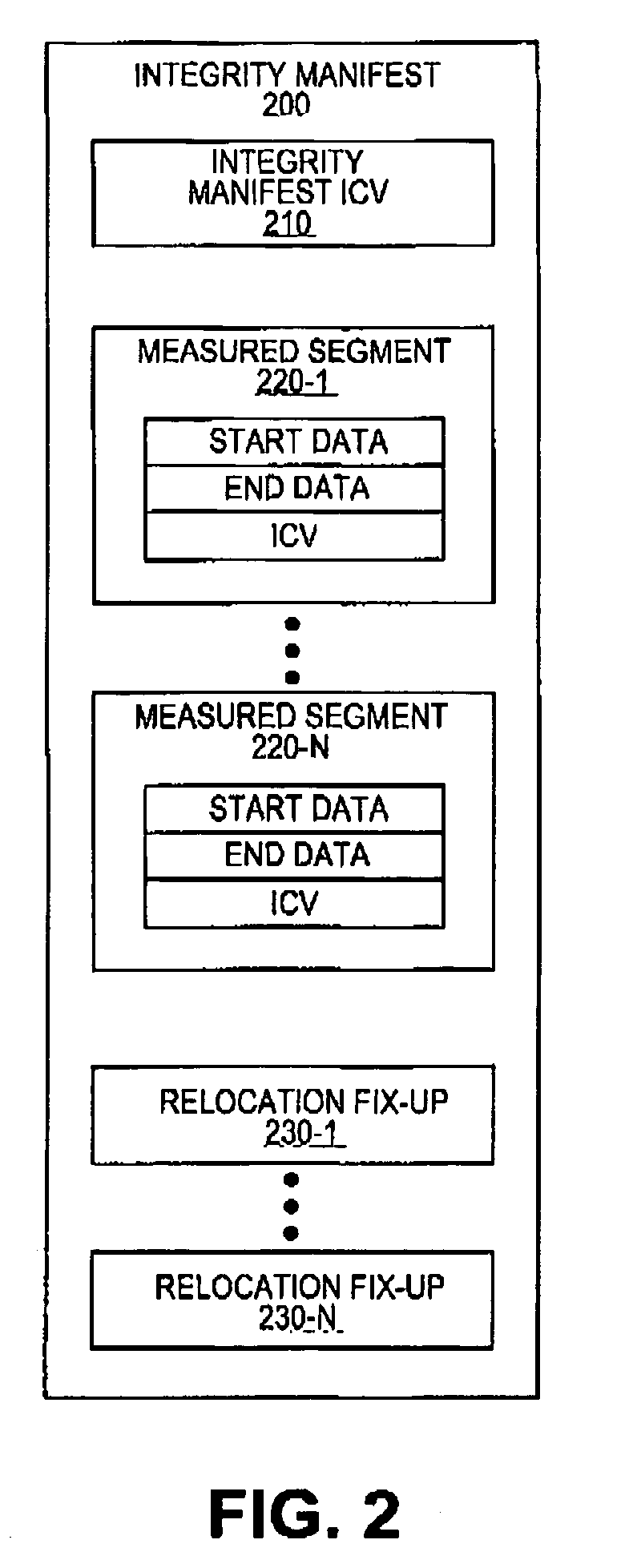
Dynamic generation of integrity manifest for run-time verification of software program
ActiveUS8364973B2Memory loss protectionUnauthorized memory use protectionComputer hardwareRuntime verification
A measurement engine generates an integrity manifest for a software program and uses it to perform active platform observation. The integrity manifest indicates an integrity check value for a section of the program's code. The measurement engine computes a comparison value on the program's image in memory and determines if the comparison value matches the expected integrity check value. If the values do not match, the program's image is determined to be modified, and appropriate remedial action may be triggered.
Owner:INTEL CORP
Continuous run-time validation of program execution: a practical approach
ActiveUS9063721B2Easy to integrateTolerable performance overheadConcurrent instruction executionInternal/peripheral component protectionPre validationControl flow
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
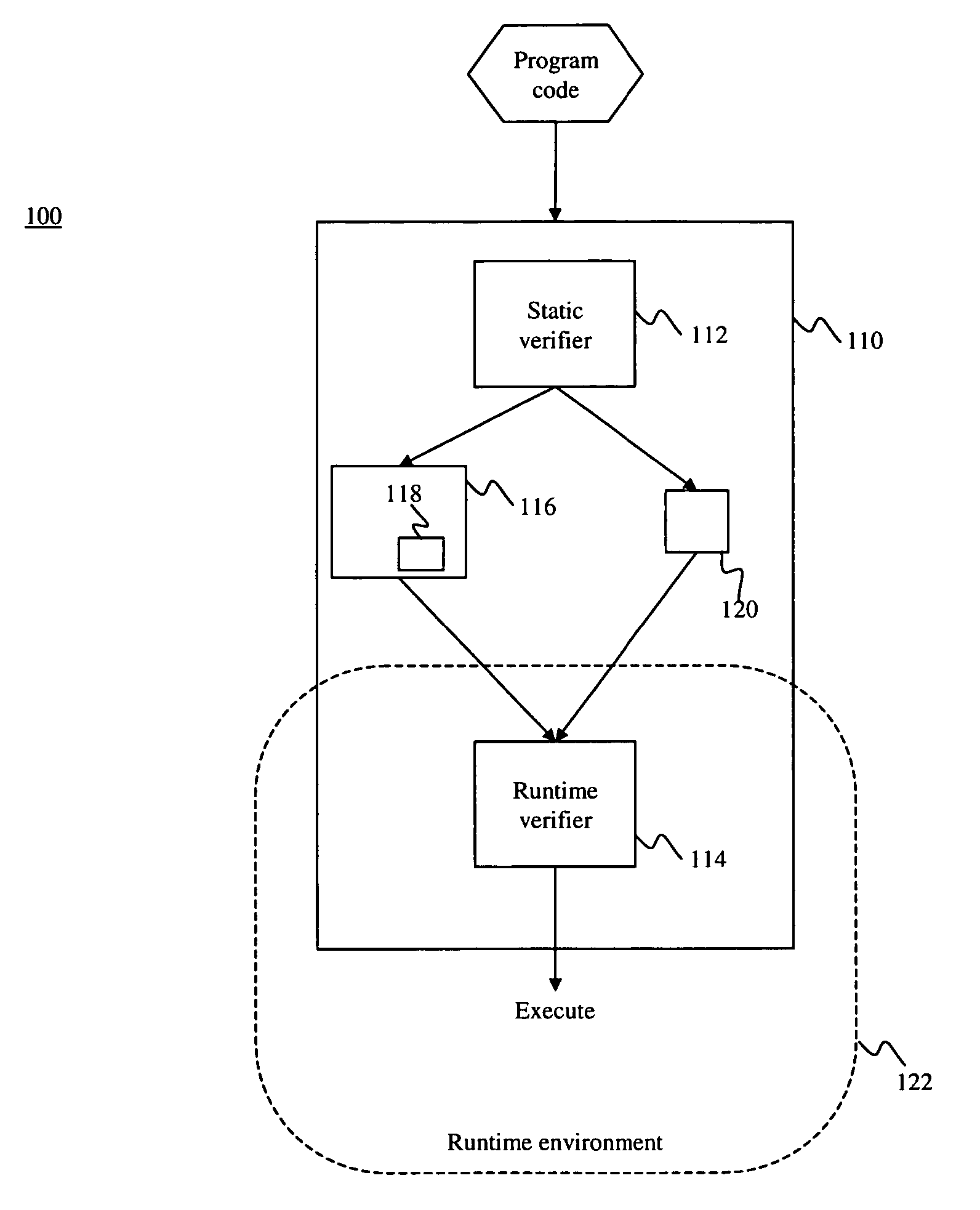
System and method for compiling program code ahead of time
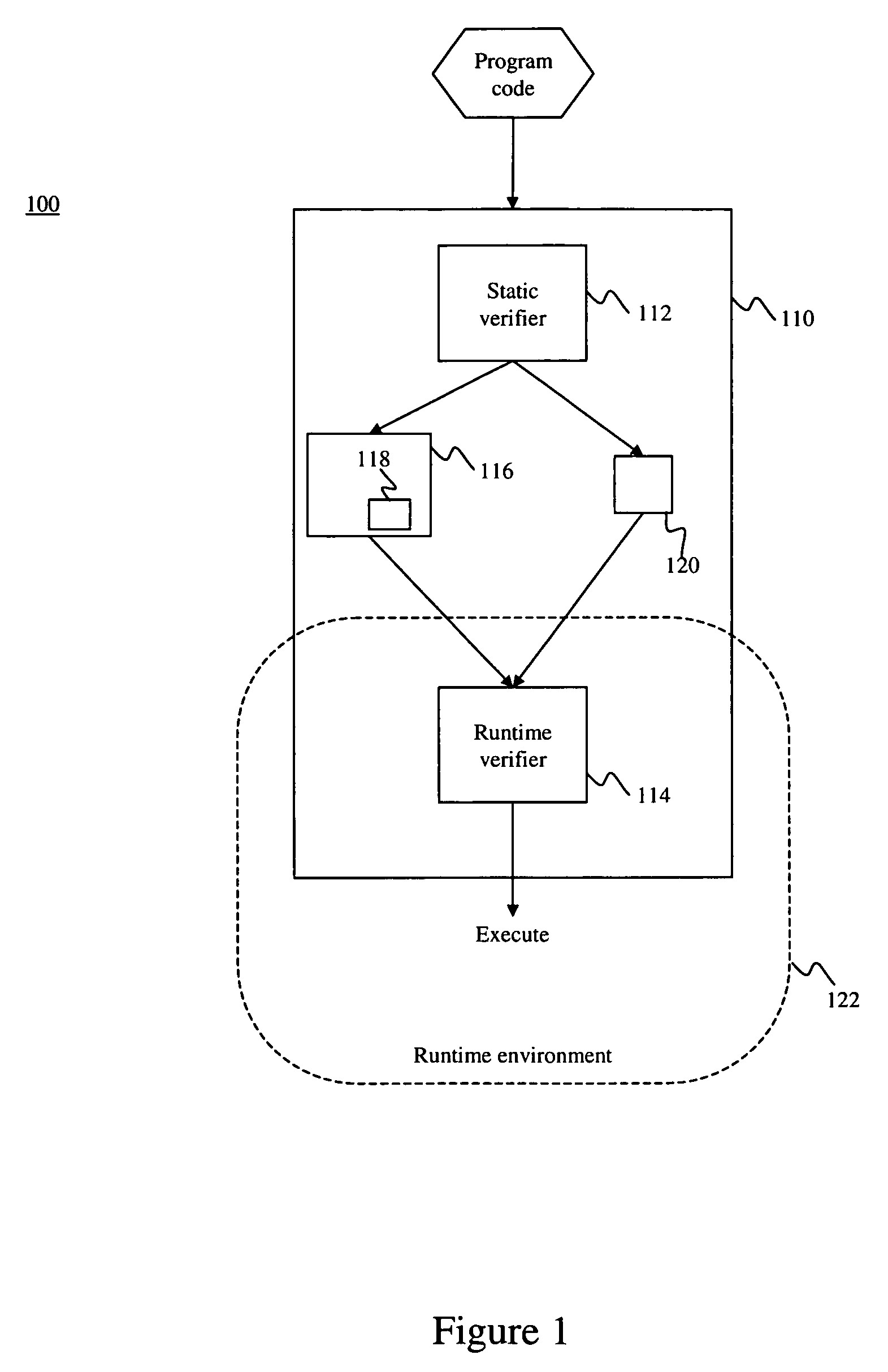
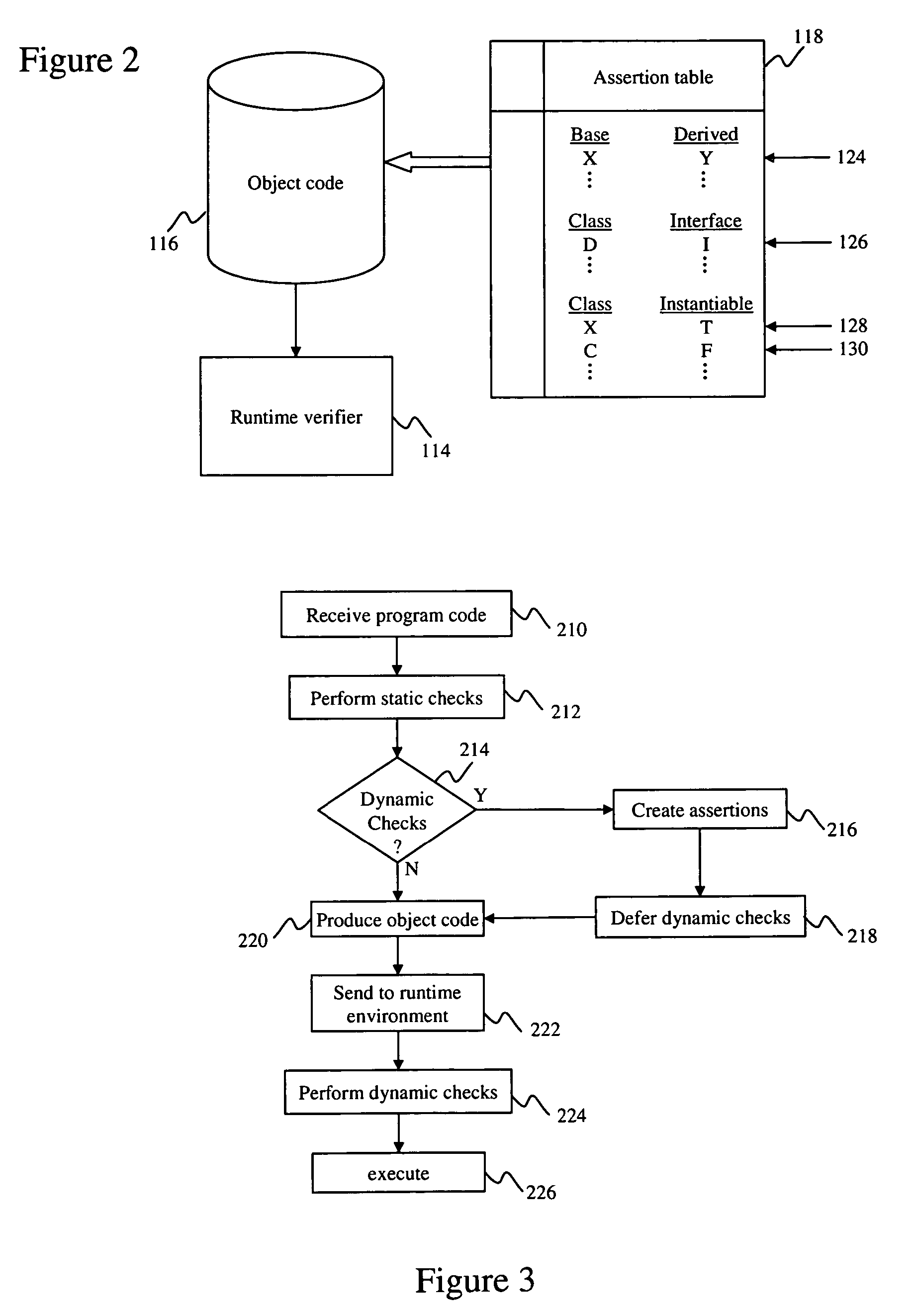
ActiveUS20070022411A1Improve efficiencySpecific program execution arrangementsMemory systemsStatic checkRuntime verification
A system is disclosed for compiling program code. The system provides a compiler that includes a static verifier and a runtime verifier. The static verifier performs static checks on the program code and produces object code corresponding to the program code. The runtime verifier receives the object code and performs dynamic checks on the object code in a platform dependent environment. The resulting object code can subsequently be executed.
Owner:RED HAT
Detecting computer system simulation errors
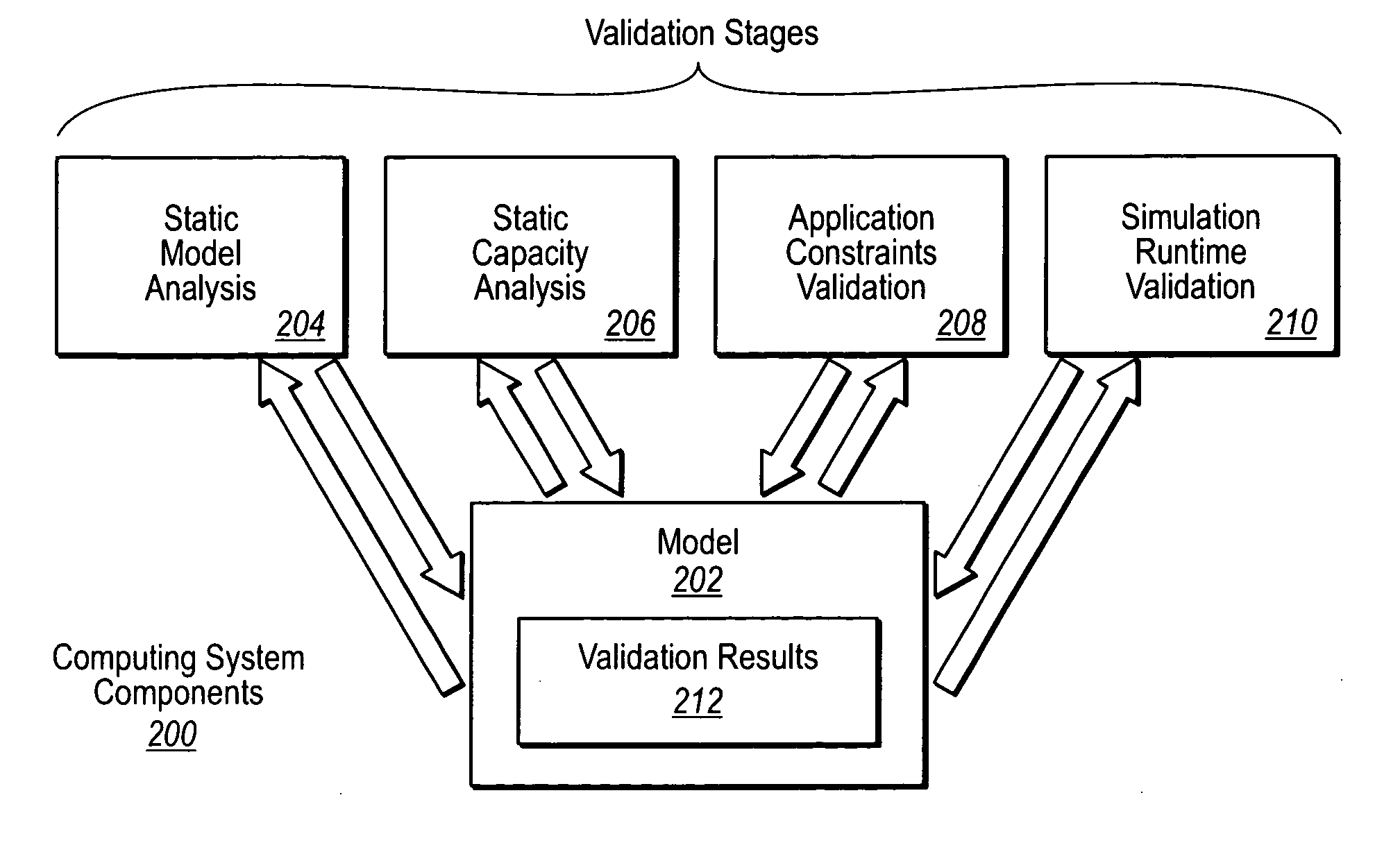
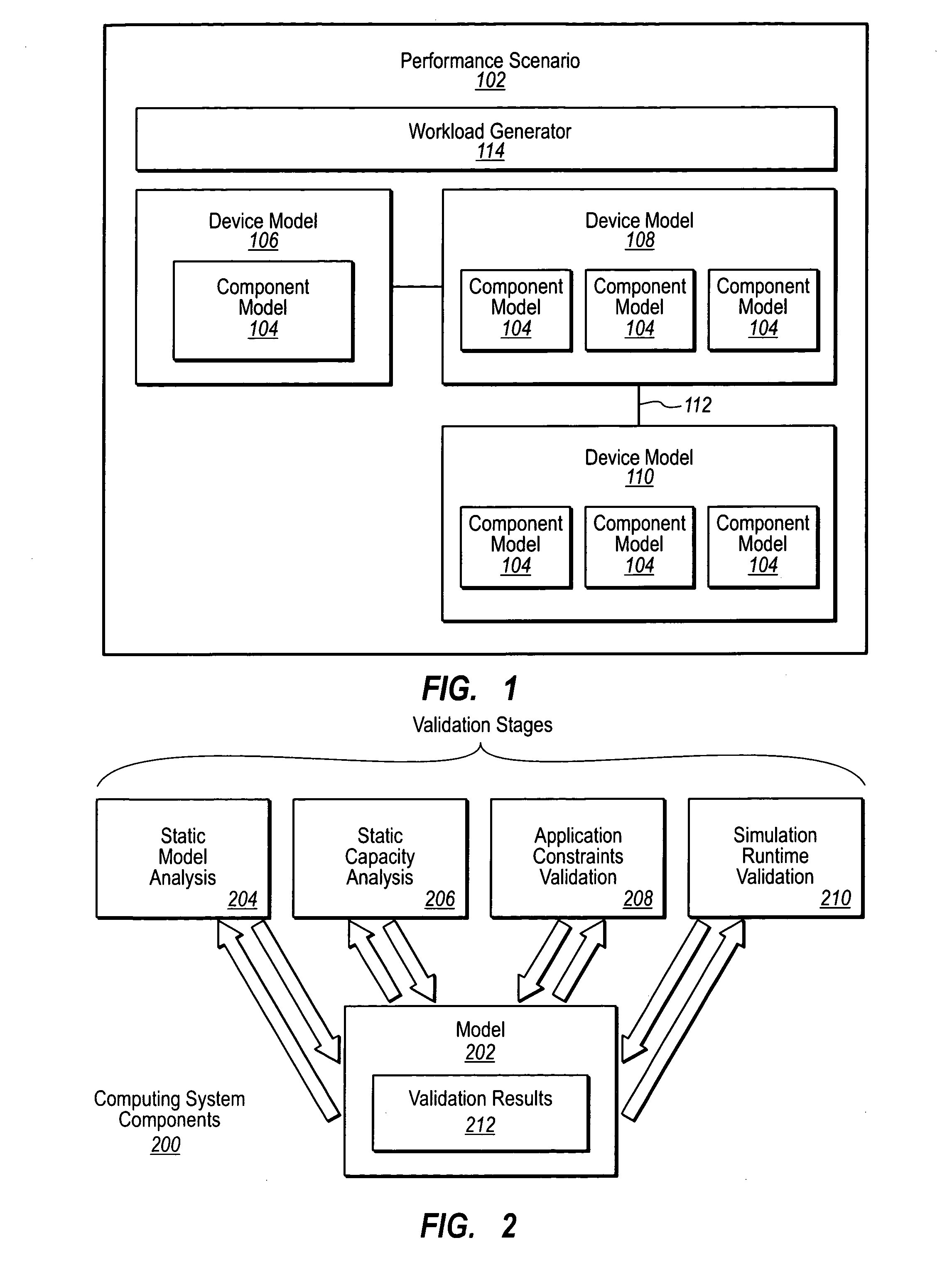
InactiveUS20070233448A1Computation using non-denominational number representationDesign optimisation/simulationRuntime verificationParallel computing
Validating simulation models. A computing environment includes a performance scenario of a system. The performance scenario includes device models defining device behavior and / or capacity. The performance scenario further includes interconnections between one or more device models. A static model analysis of the system is performed. The static model analysis analyzes at least one of configuration of device models defined by the performance scenario or interconnection of device models defined by the performance scenario. A static capacity analysis to analyze device model limitations as they relate to statically defined performance scenario characteristics is performed. An application constraints validation can be performed. This includes comparing the performance scenario to software deployment best practices and rules related to models similar to the performance scenario. A simulation runtime validation may also be performed to evaluate dynamic device usage and latencies to simulate the system.
Owner:MICROSOFT TECH LICENSING LLC
Operation formal verification method and system for source code
ActiveCN108536581AImprove securityImprove reliabilitySoftware testing/debuggingValidation methodsRuntime verification
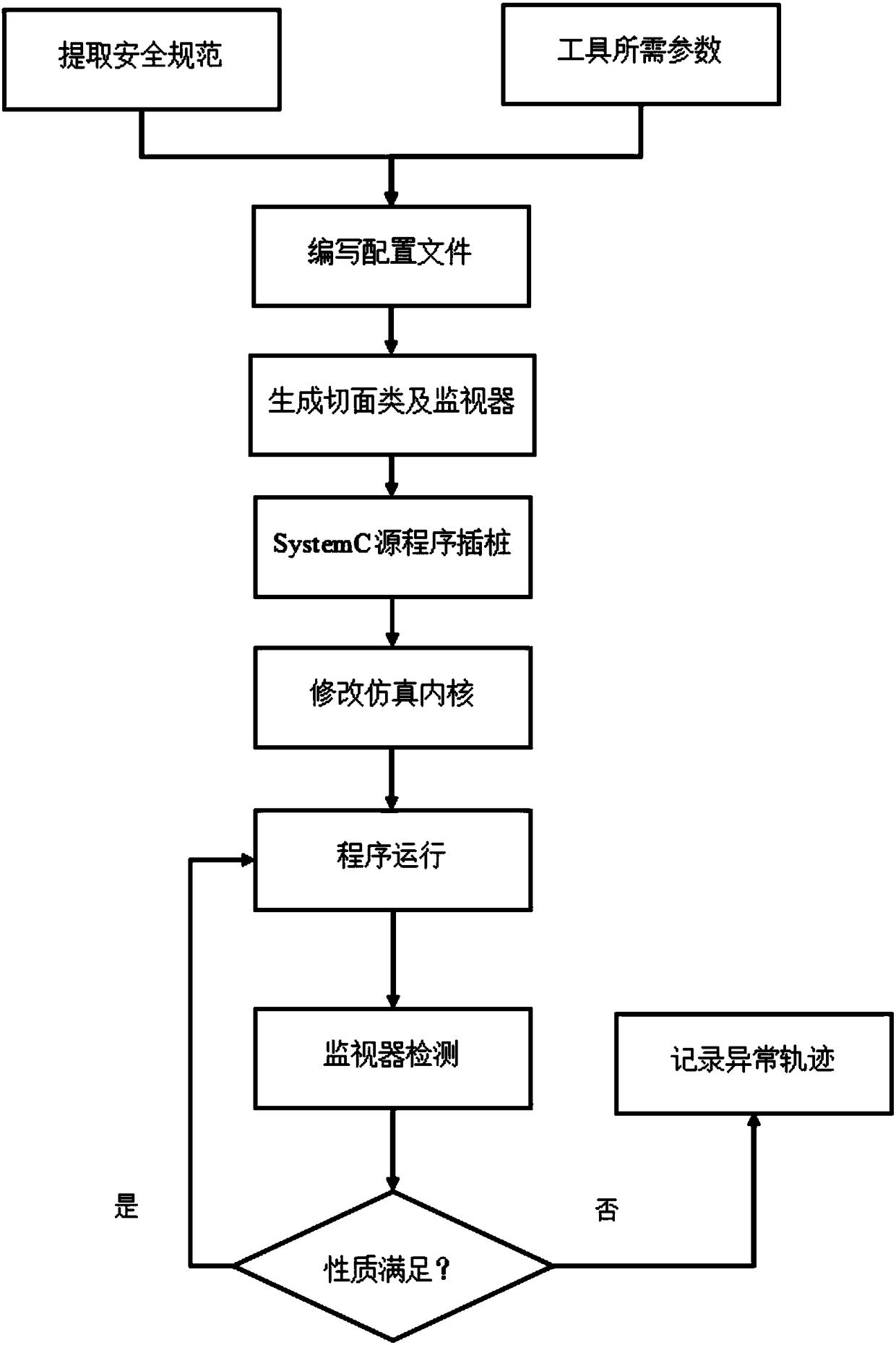
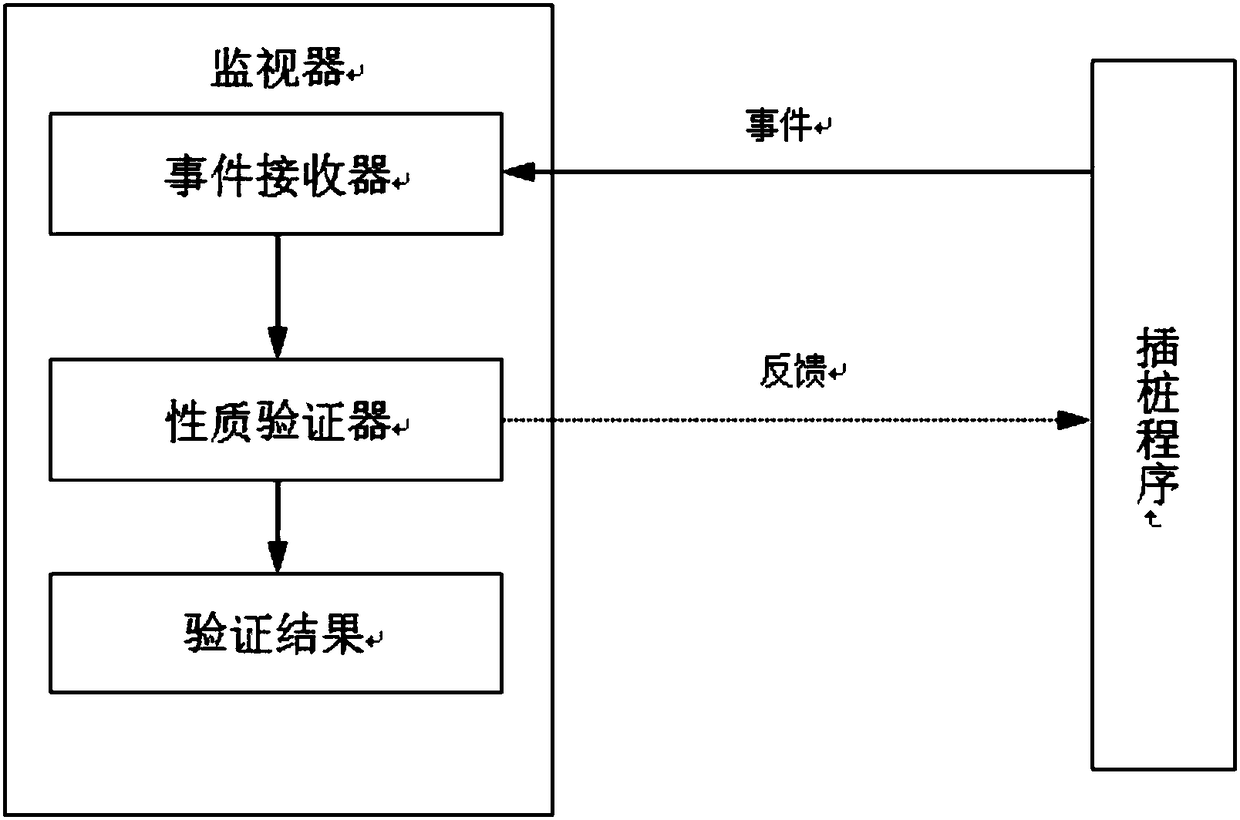
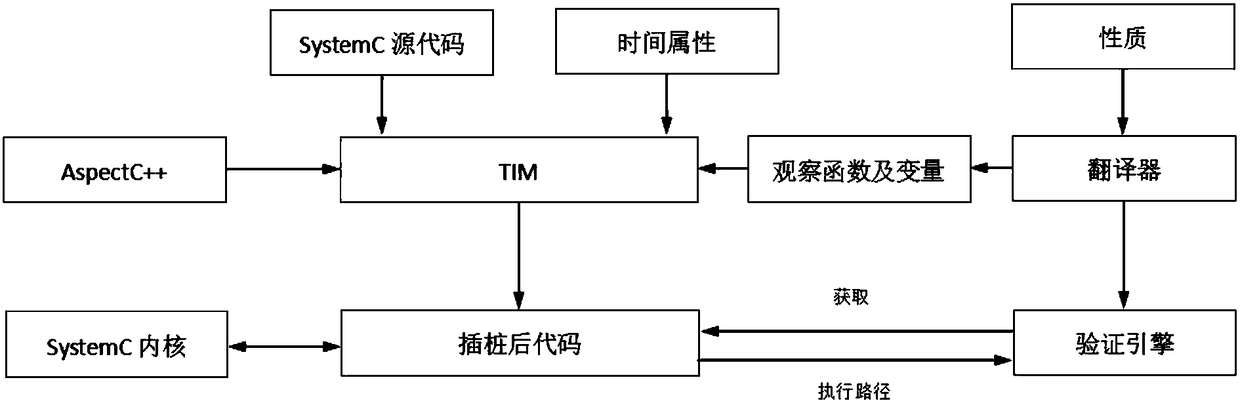
The invention discloses an operation formal verification method and system for a source code. The method comprises the following steps: according to properties to be met by a source program, and parameters required by a tool, writing a configuration file for generating a monitor and a section; according to the written configuration file, automatically generating the monitor and the section by using an operation verification tool; according to the generated section, putting an involved variable into the source program; modifying a simulation kernel to be adaptive to an operation verification method; monitoring a source program operation state after column insertion in real time by using the generated monitor; performing formal verification on properties by the monitor according to a programoperation track, and if a route violating verification properties is resulted, carrying out recording to automatic repairing of programs. The method disclosed by the invention can be applied to formal verification on embedded systems and large-size software systems, and the software security and reliability can be improved.
Owner:EAST CHINA NORMAL UNIV
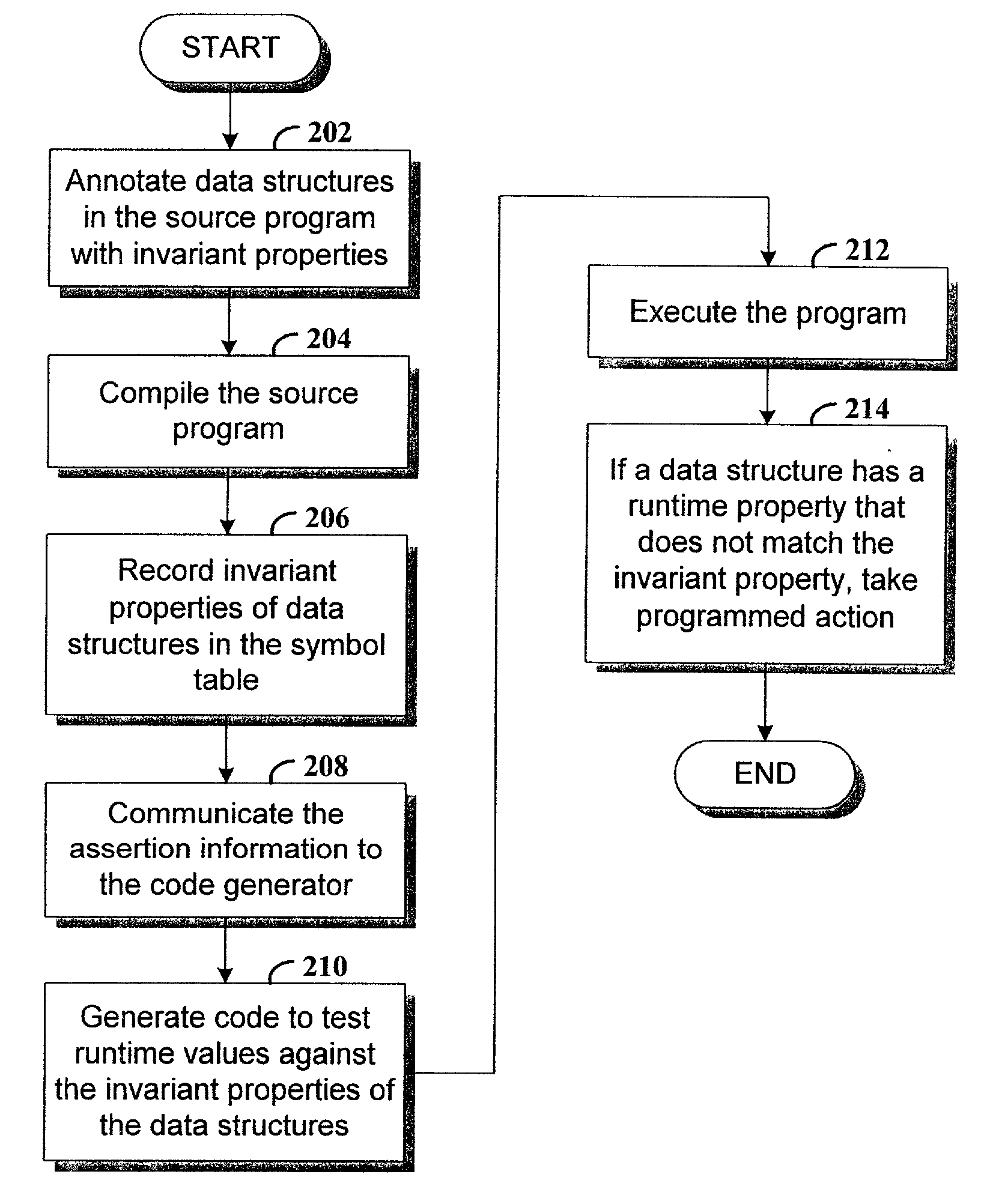
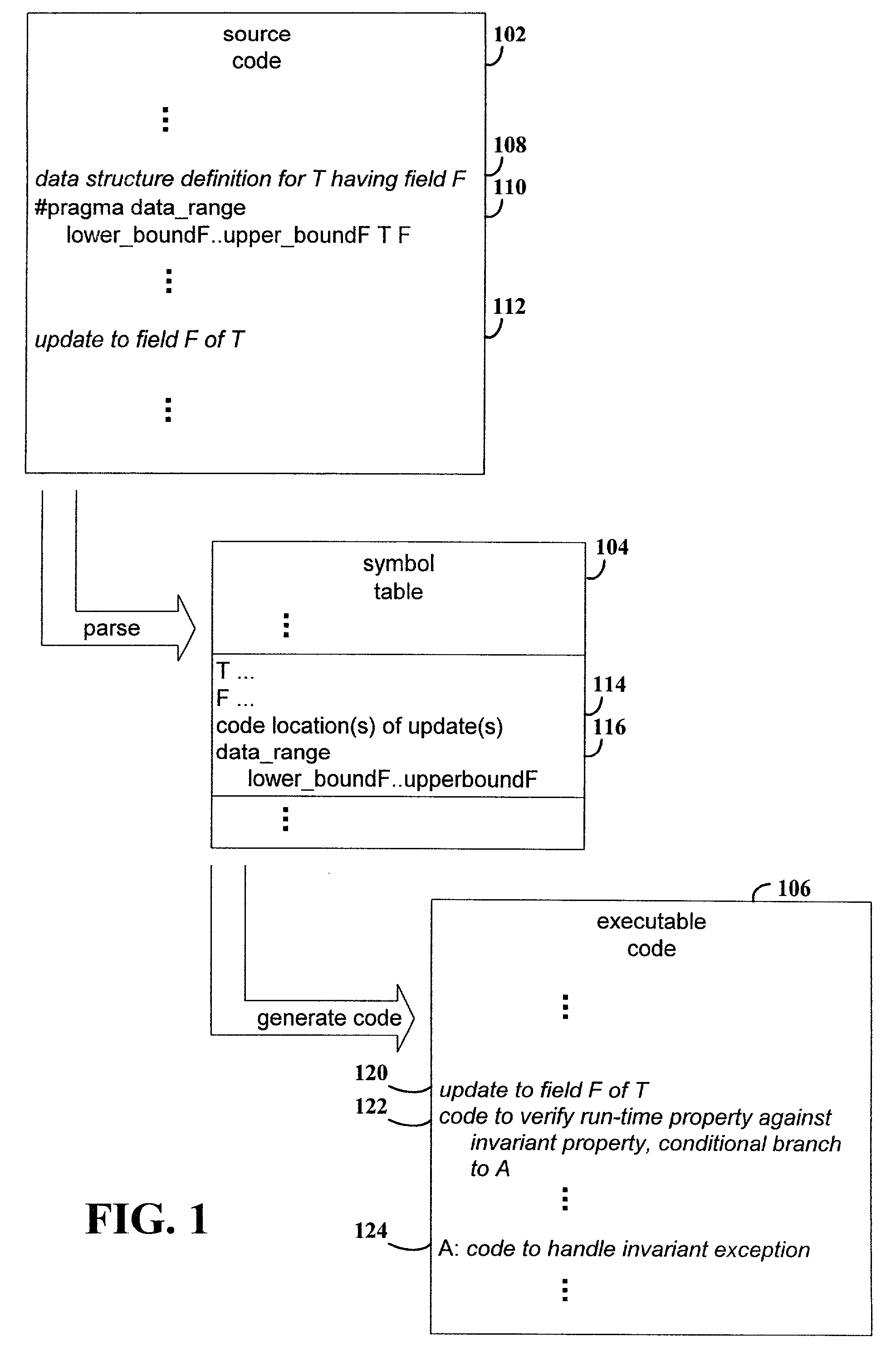
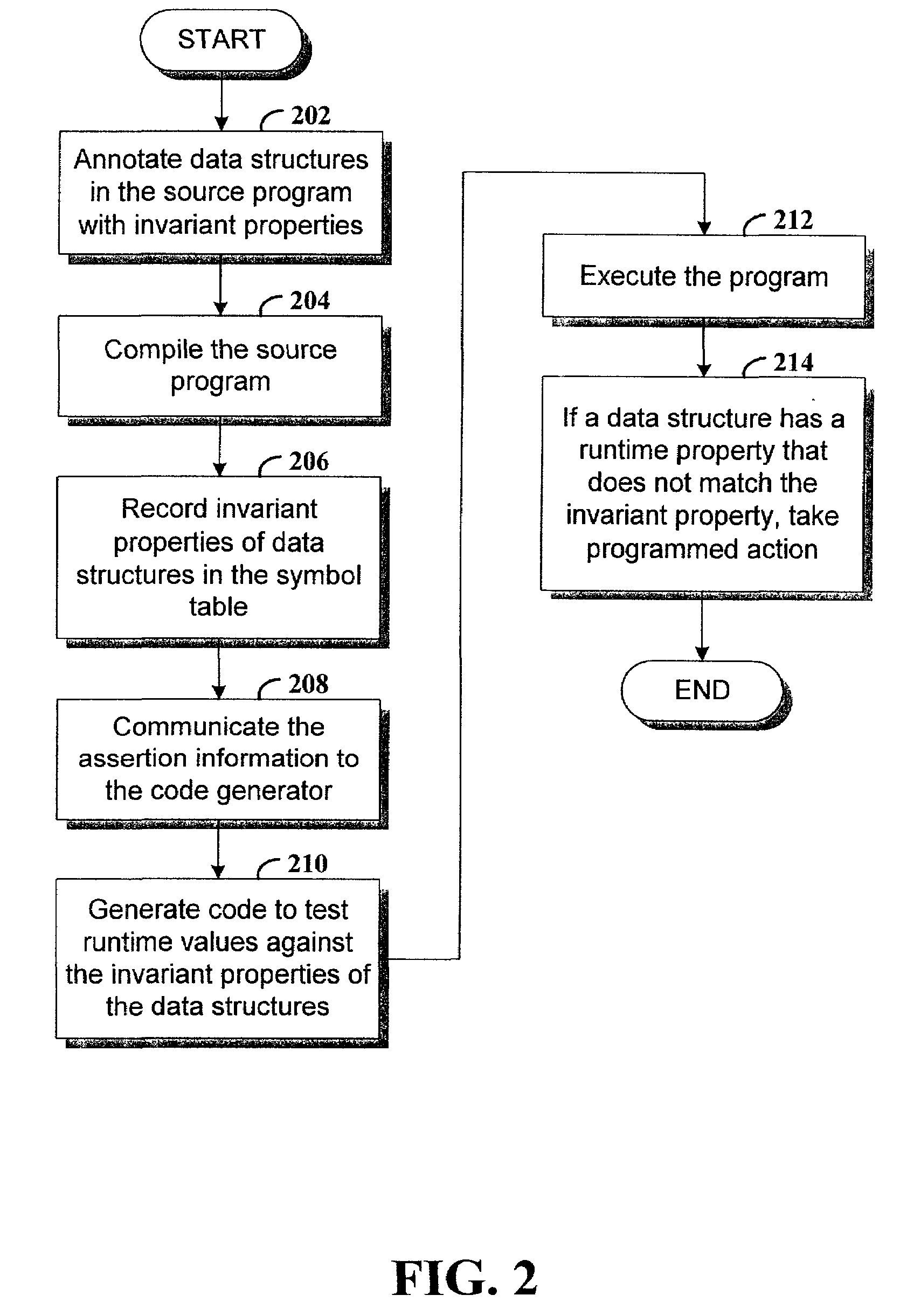
Specifying an invariant property (range of addresses) in the annotation in source code of the computer program
InactiveUS7013460B2Error detection/correctionEmergency protective arrangements for automatic disconnectionRuntime verificationSource code
Method and apparatus for verifying at runtime an invariant property of a data structure. In various example embodiments, code that verifies whether a runtime value of the data structure is consistent with the invariant property is automatically generated in response to an annotation of the data structure in the source code. In executing the program, the runtime value of the data structure is compared to the invariant property in the automatically generated code. If the runtime property is inconsistent with the invariant property, the program branches to exception handler code.
Owner:HEWLETT PACKARD DEV CO LP
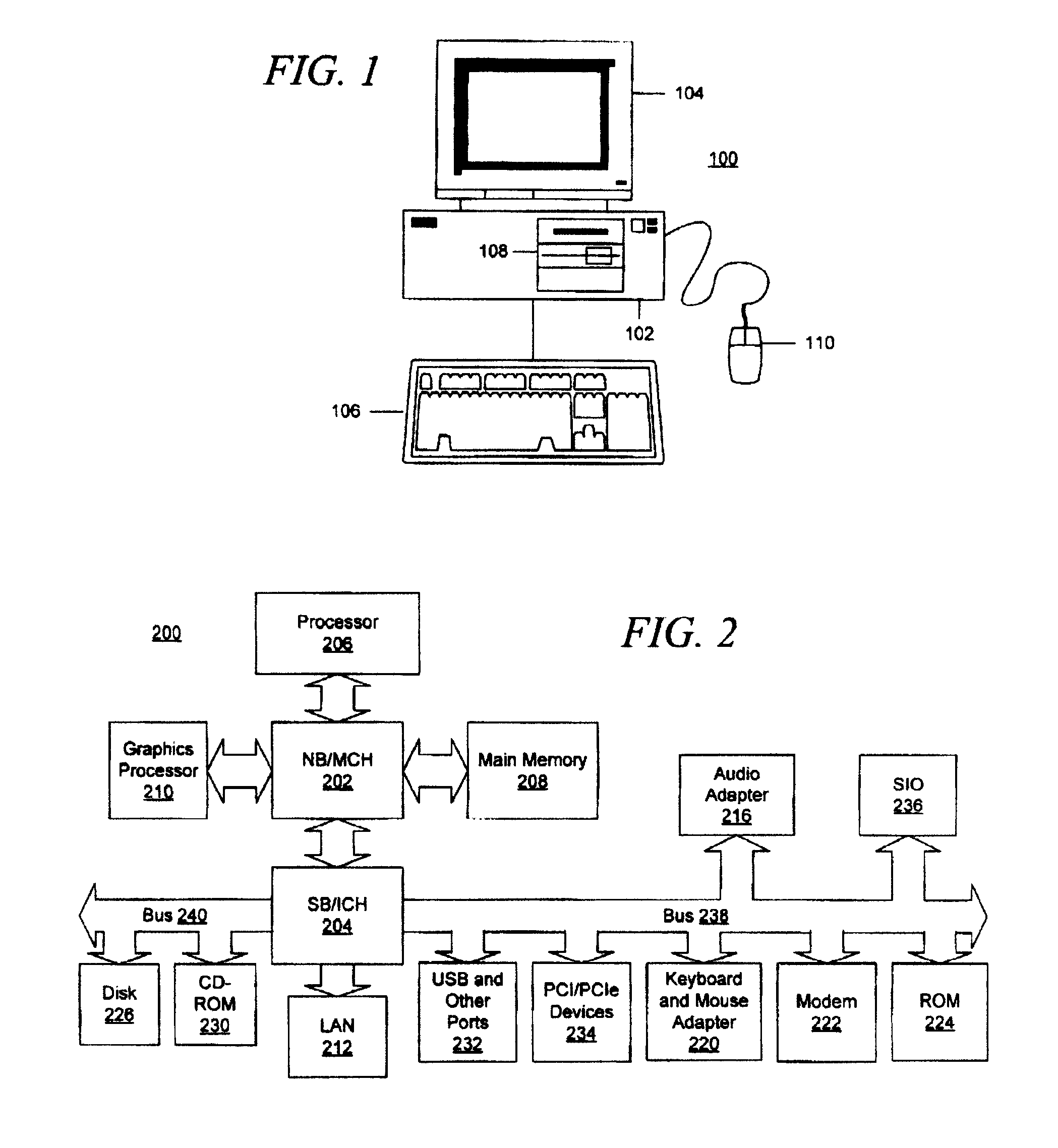
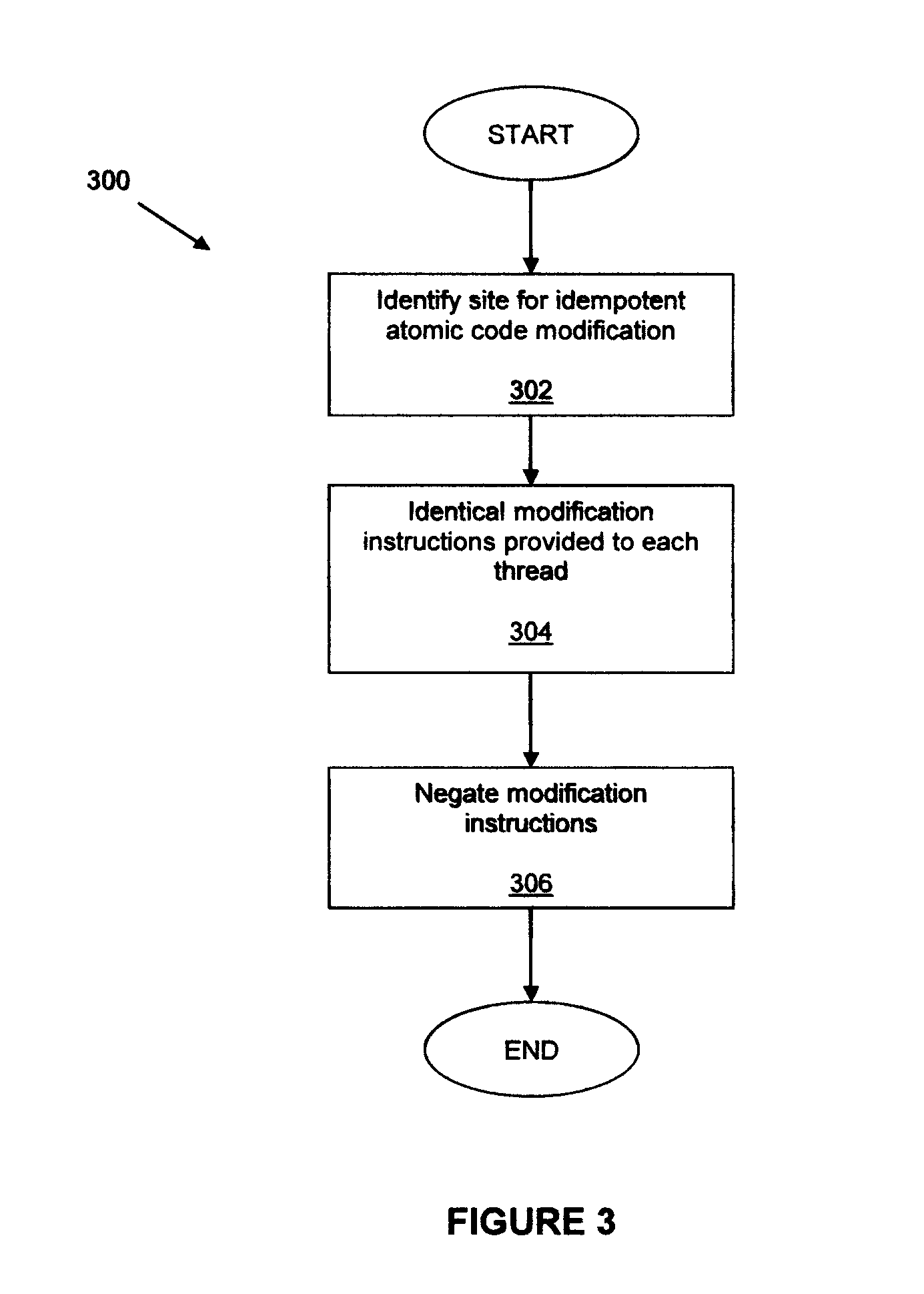
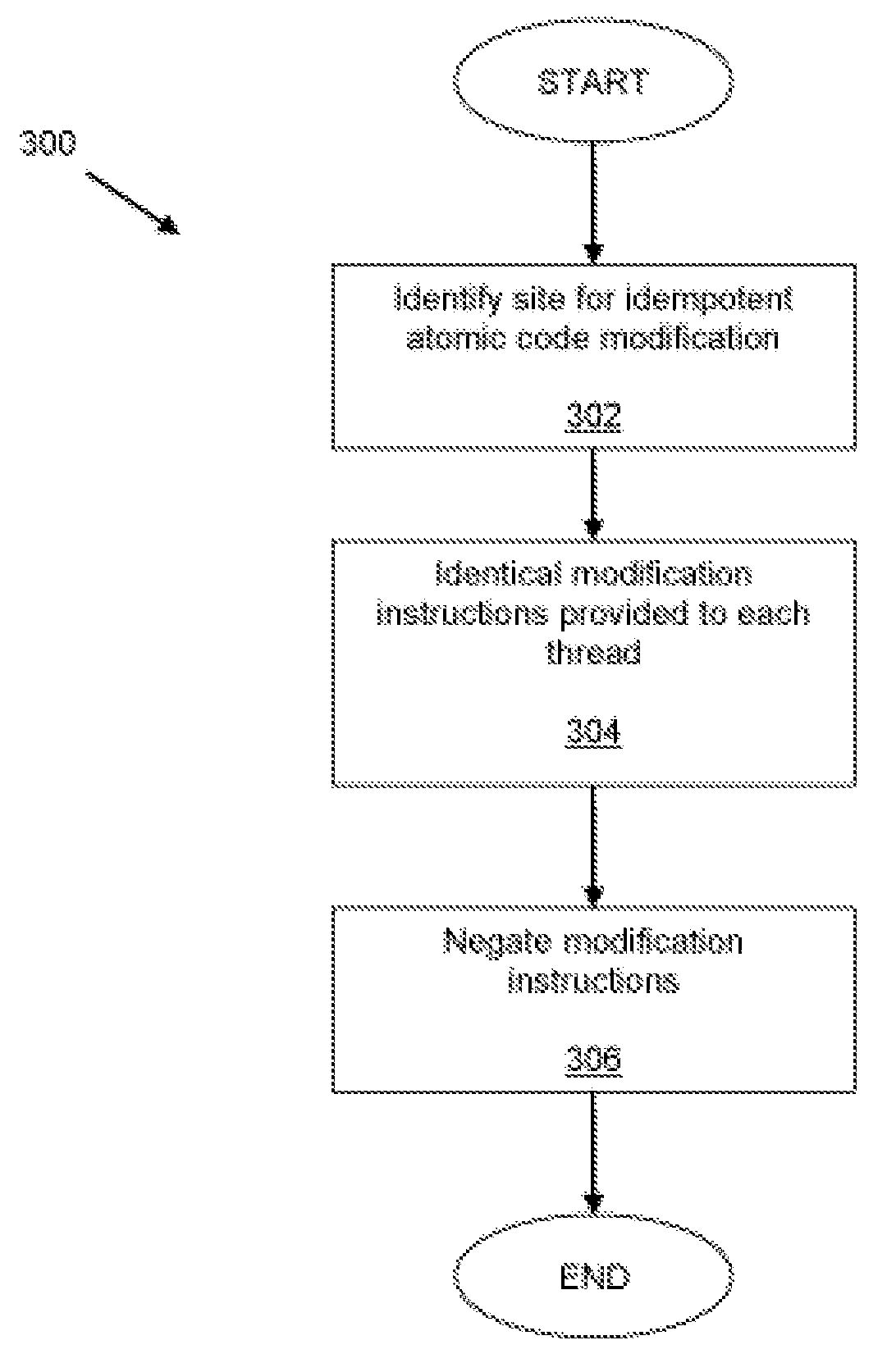
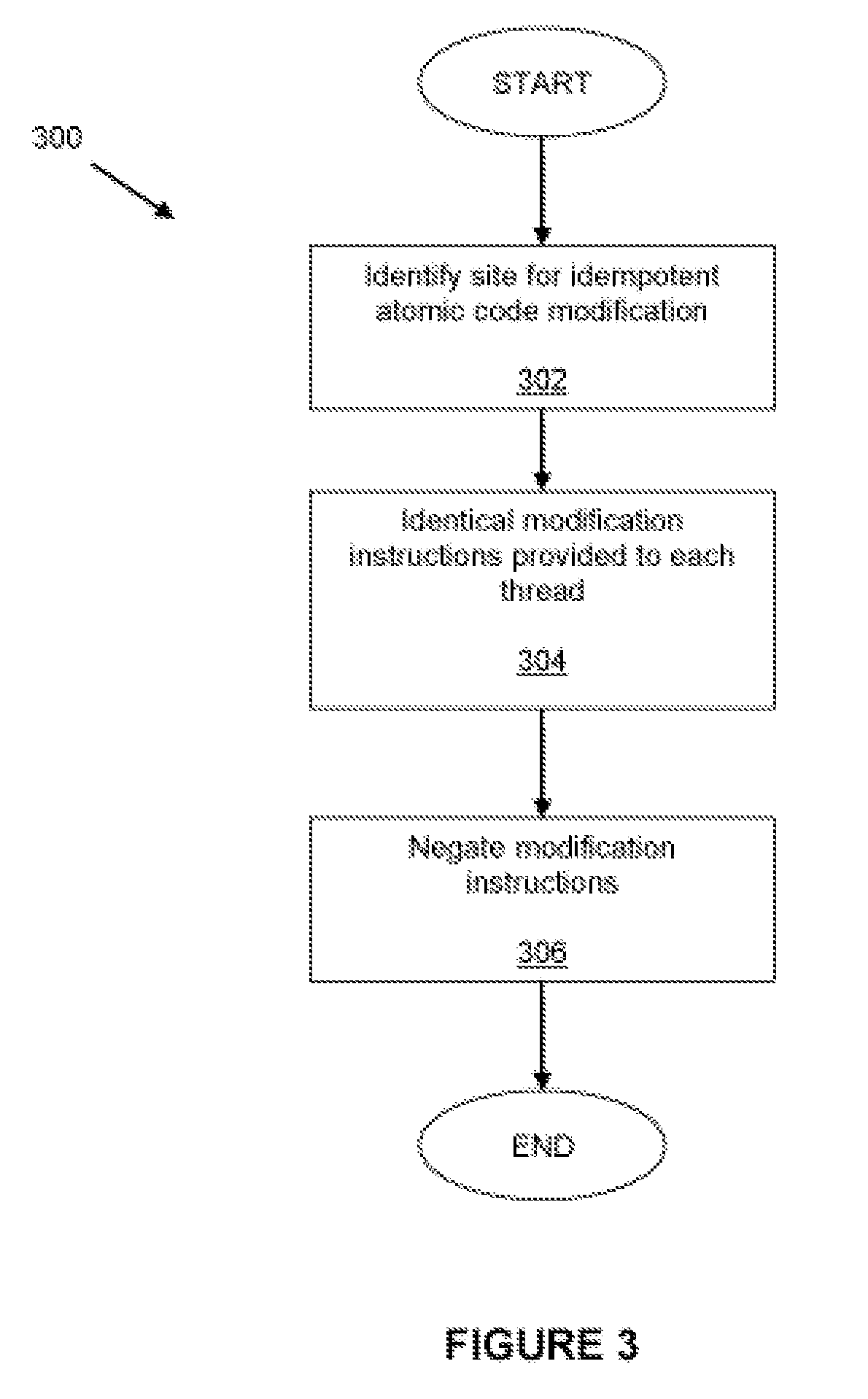
Runtime code modification in a multi-threaded environment
A code region forming part of a computer program is modified during execution of the computer program by a plurality of threads. In one aspect, identical modification instructions are provided to each thread for modifying a site in the code region having a desirable idempotent atomic modification, and the modification instructions direct each thread to make the desirable idempotent atomic modification. In another aspect, a thread is selected to modify the code region, each thread other than the selected thread is directed to execute an alternative execution path that generates output identical to the output of the code region after the code region has been modified, and, responsive to directing each thread other than the selected thread, the selected thread is directed to modify the code region.
Owner:IBM CORP
Runtime code modification in a multi-threaded environment
InactiveUS20080052498A1Digital computer detailsSpecific program execution arrangementsRuntime verificationParallel computing
A code region forming part of a computer program is modified during execution of the computer program by a plurality of threads. In one aspect, identical modification instructions are provided to each thread for modifying a site in the code region having a desirable idempotent atomic modification, and the modification instructions direct each thread to make the desirable idempotent atomic modification. In another aspect, a thread is selected to modify the code region, each thread other than the selected thread is directed to execute an alternative execution path that generates output identical to the output of the code region after the code region has been modified, and, responsive to directing each thread other than the selected thread, the selected thread is directed to modify the code region.
Owner:IBM CORP
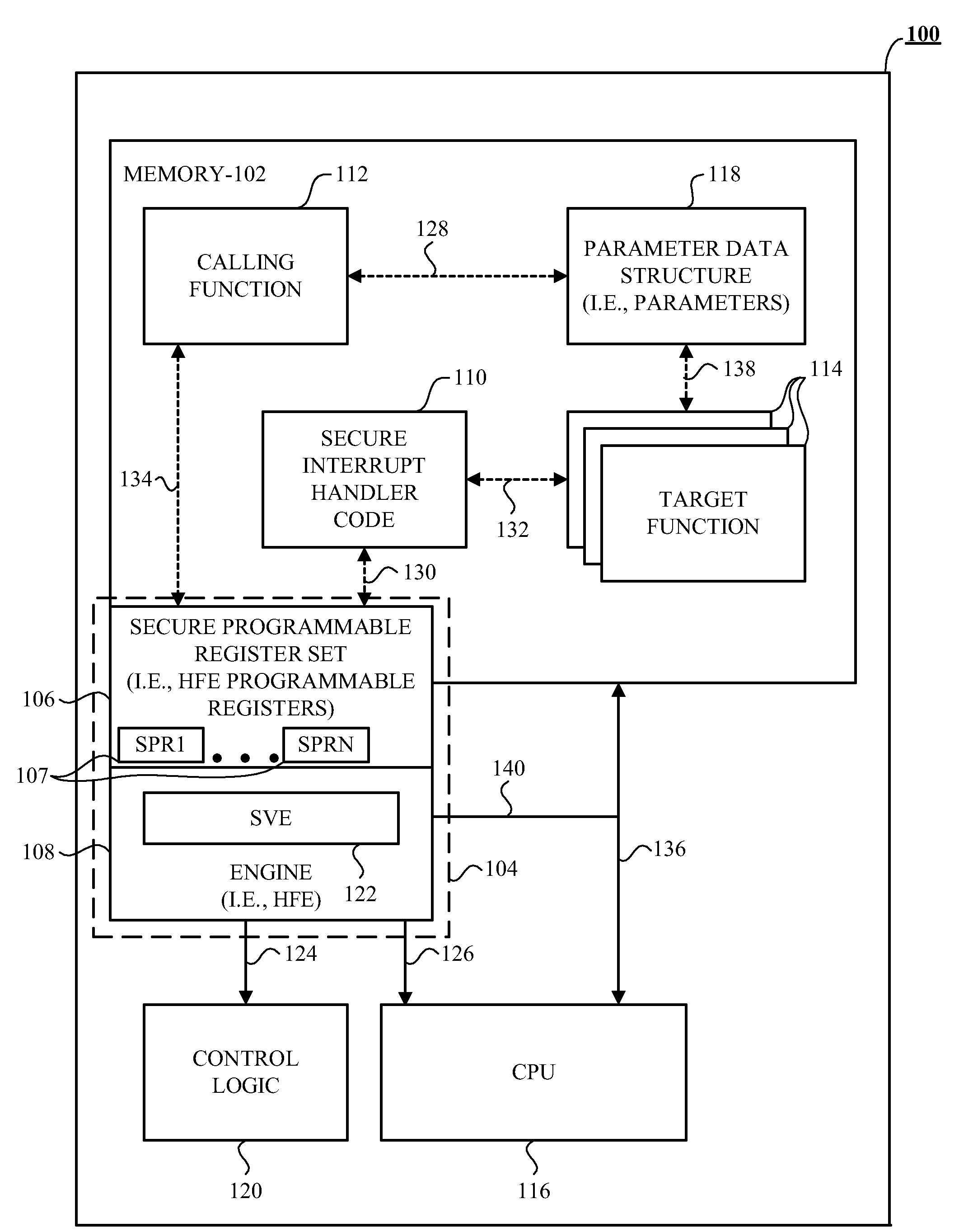
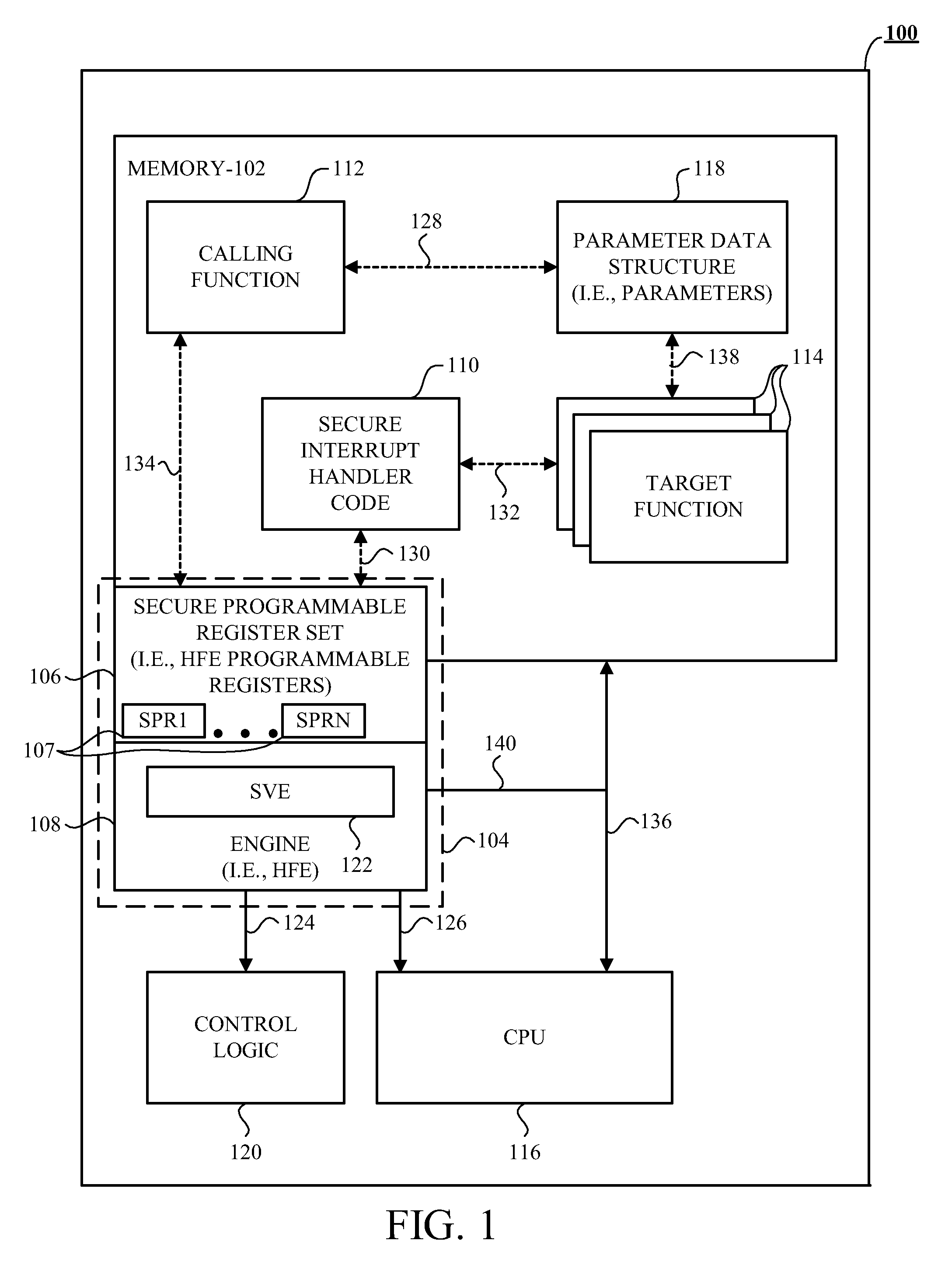
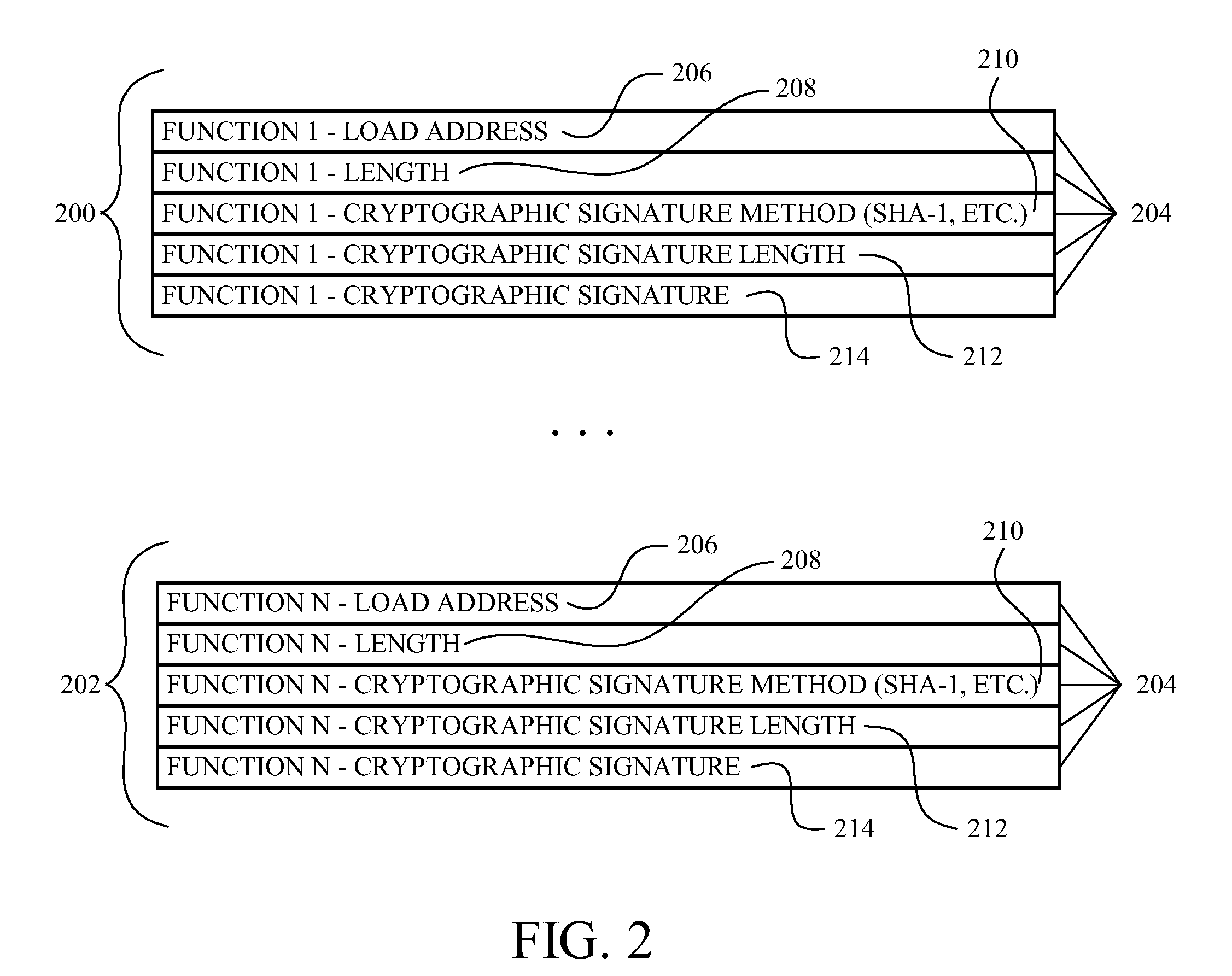
Method, Apparatus, and Device for Providing Security Among a Calling Function and a Target Function
ActiveUS20100106979A1User identity/authority verificationUnauthorized memory use protectionRuntime verificationInterrupt handler
The device and accompanying apparatus and method provides security among a calling function, such as an any executable code, and at least one target function, such as any executable code that the calling function wishes to have execute. In one example, the device includes an engine operative to perform run-time verification of the signatures of secure interrupt handler code and at least one target function before allowing execution of the at least one target function. If both the secure interrupt handler code's signature and the at least one target function's signature are successfully verified, the at least one target function is allowed to execute.
Owner:ADVANCED MICRO DEVICES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com