Operation formal verification method and system for source code
A formal verification, source code technology, applied in the field of runtime verification methods and systems, can solve problems such as manual intervention, low degree of automation, state explosion, etc., to achieve high practicability and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
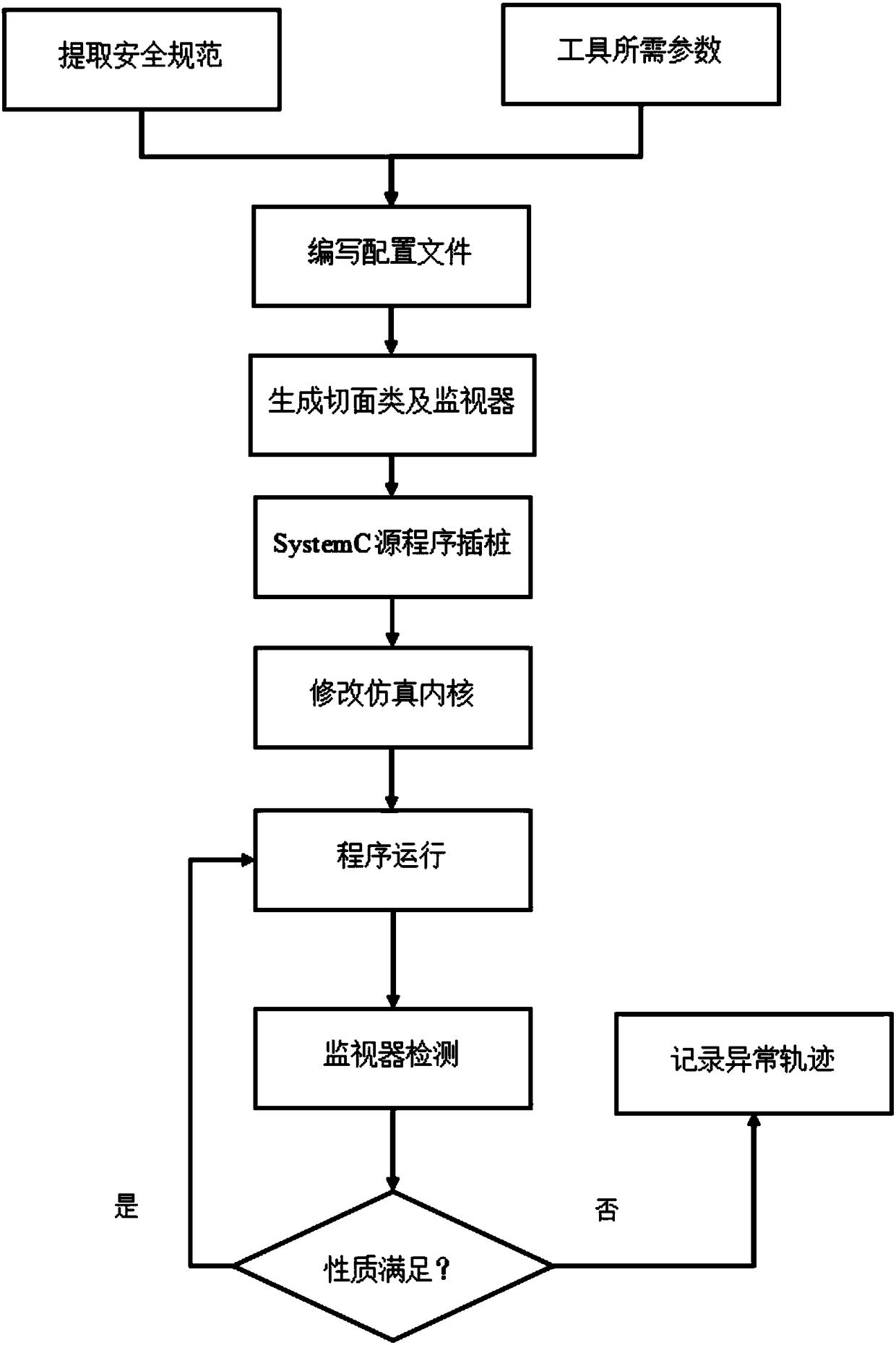
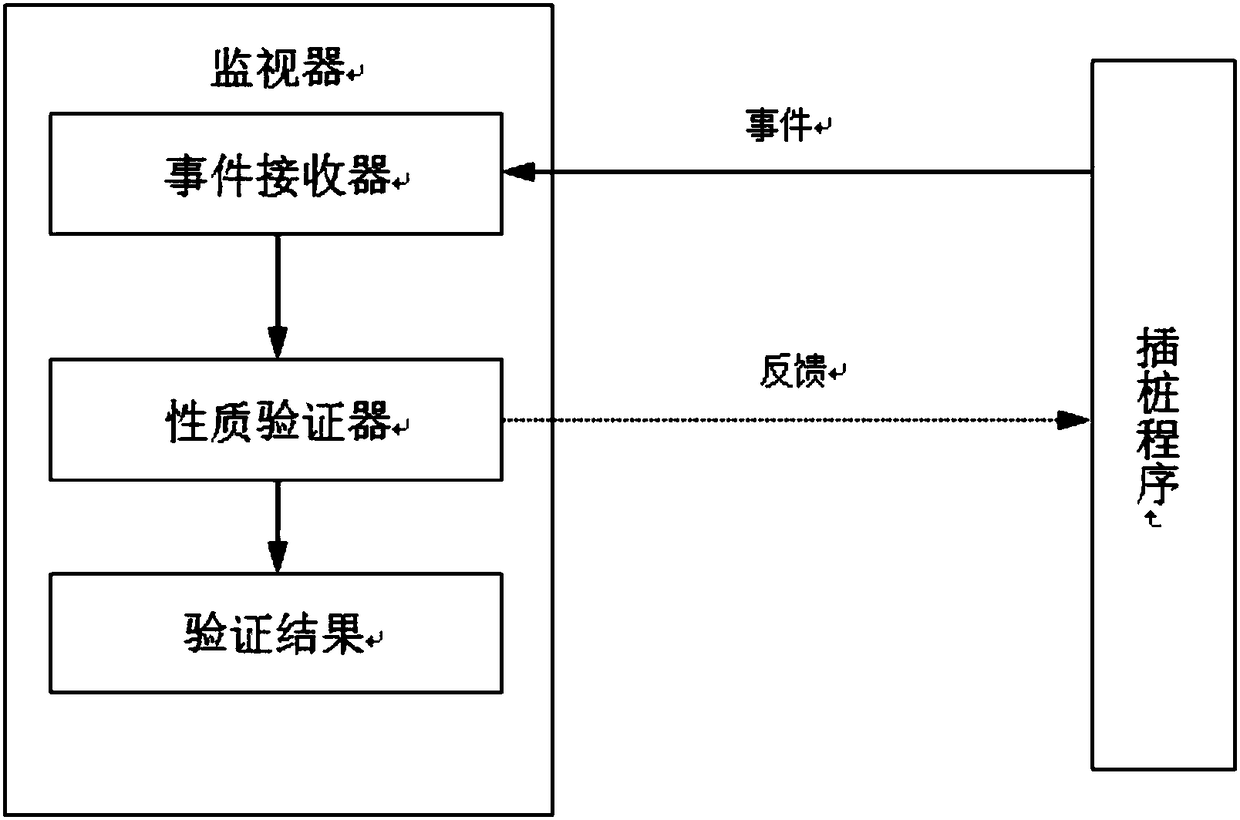
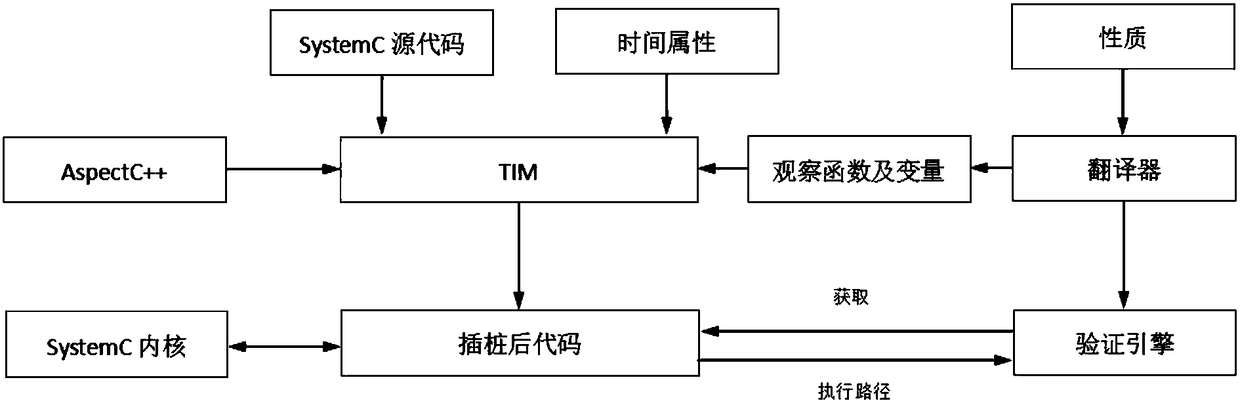
[0059] In this specific embodiment, the producer consumer program is taken as an example to perform runtime verification of the safety specifications to be met. For the producer consumer program, the producer stores data in the buffer, the consumer reads the data from the buffer, and the consumer must ensure the integrity of the data in the process of reading the data. In this embodiment, the producer stores the character string in the buffer, and the consumer reads the character string. The safety specification that needs to be met is that the character string read by the consumer is complete, that is, the program cannot appear read-only during the running process. Take part of the character string.
[0060] In this specific embodiment, the verification method for SystemC program runtime of the present invention is used to verify the safety specifications that the producer consumer program needs to meet, and the specific steps are as follows:
[0061] Step 1: Analyze the safety s...
Embodiment 2
[0086] In this specific embodiment, an ALU arithmetic logic unit program is taken as an example to perform runtime verification of the safety specifications to be met. The arithmetic logic unit program calculates the result according to the specified operand and the operation code and outputs it. If the divisor is zero during the division operation, it is necessary to find the operation error in time. In this embodiment, the monitor needs to monitor the divisor value in the division operation. If the divisor is zero, it should report an error in time to prevent serious consequences.
[0087] In this specific embodiment, the systemC program runtime verification method of the present invention is used to verify the safety specifications that the ALU arithmetic logic unit program needs to meet, and the specific steps are as follows:
[0088] Step 1: Analyze the safety regulations that the arithmetic logic unit program needs to meet. According to the calculation requirements, the foll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com