Patents
Literature
169 results about "Wildcard character" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
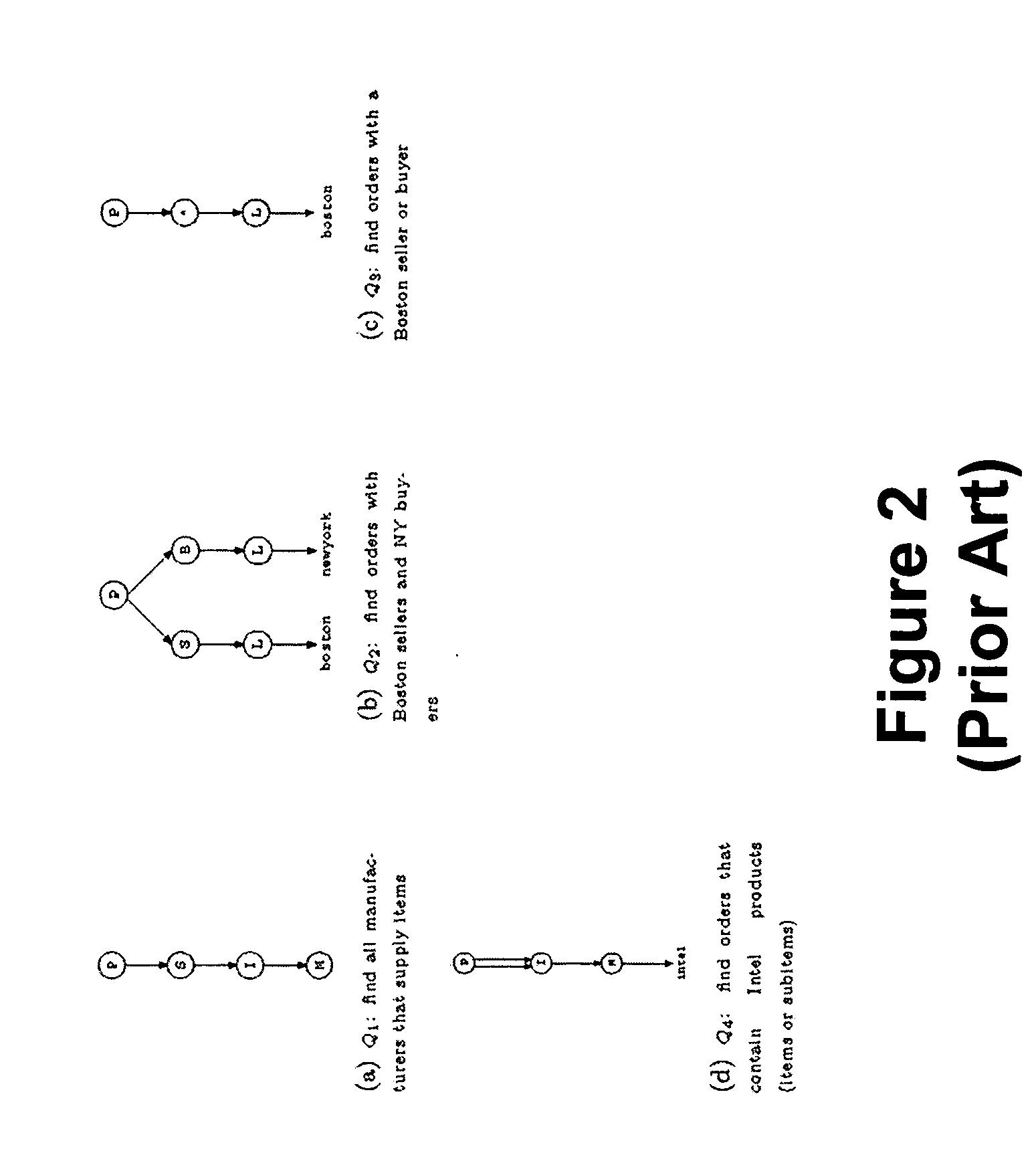
In software, a wildcard character is a kind of placeholder represented by a single character, such as an asterisk (*), which can be interpreted as a number of literal characters or an empty string. It is often used in file searches so the full name need not be typed.
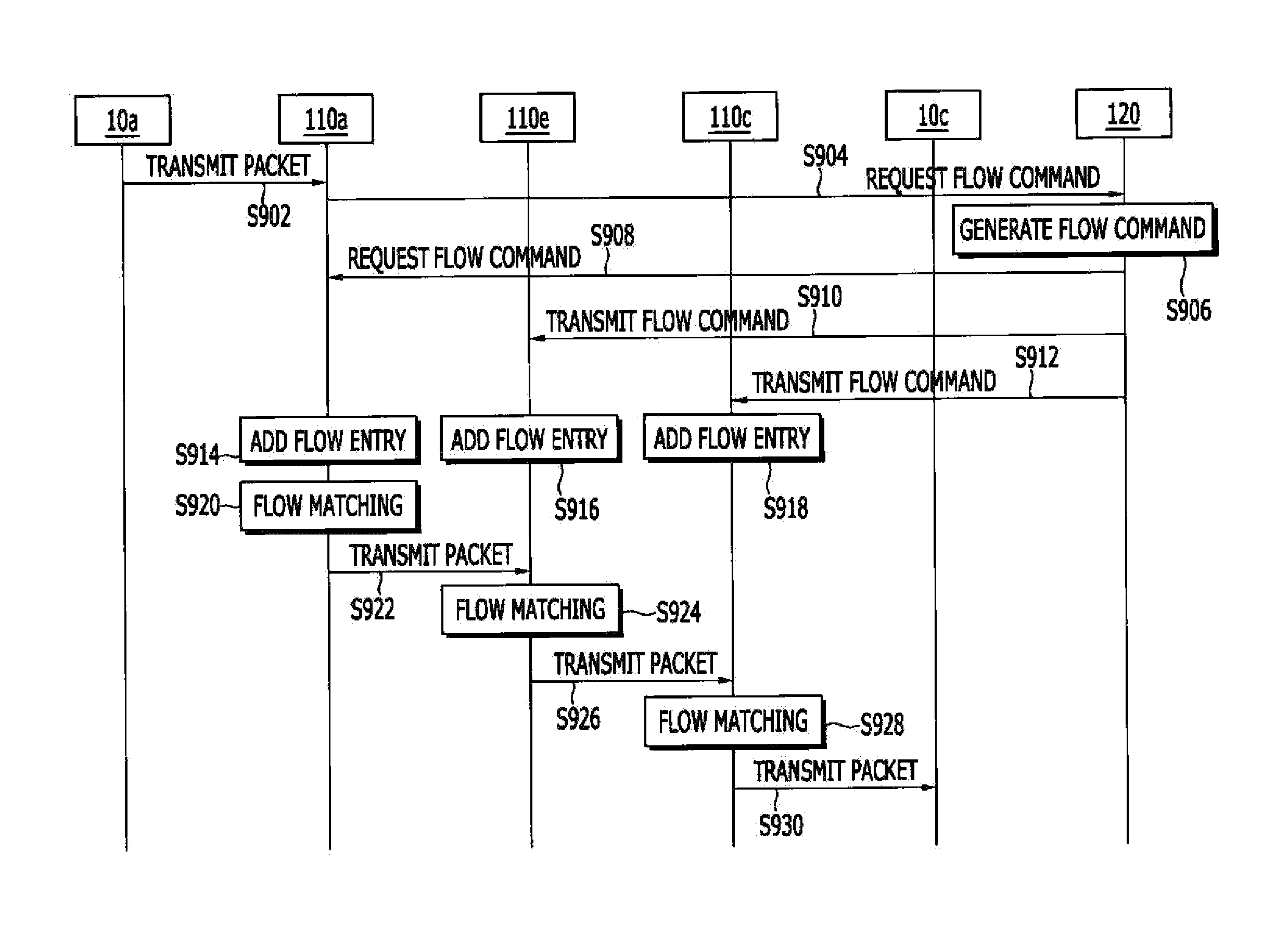
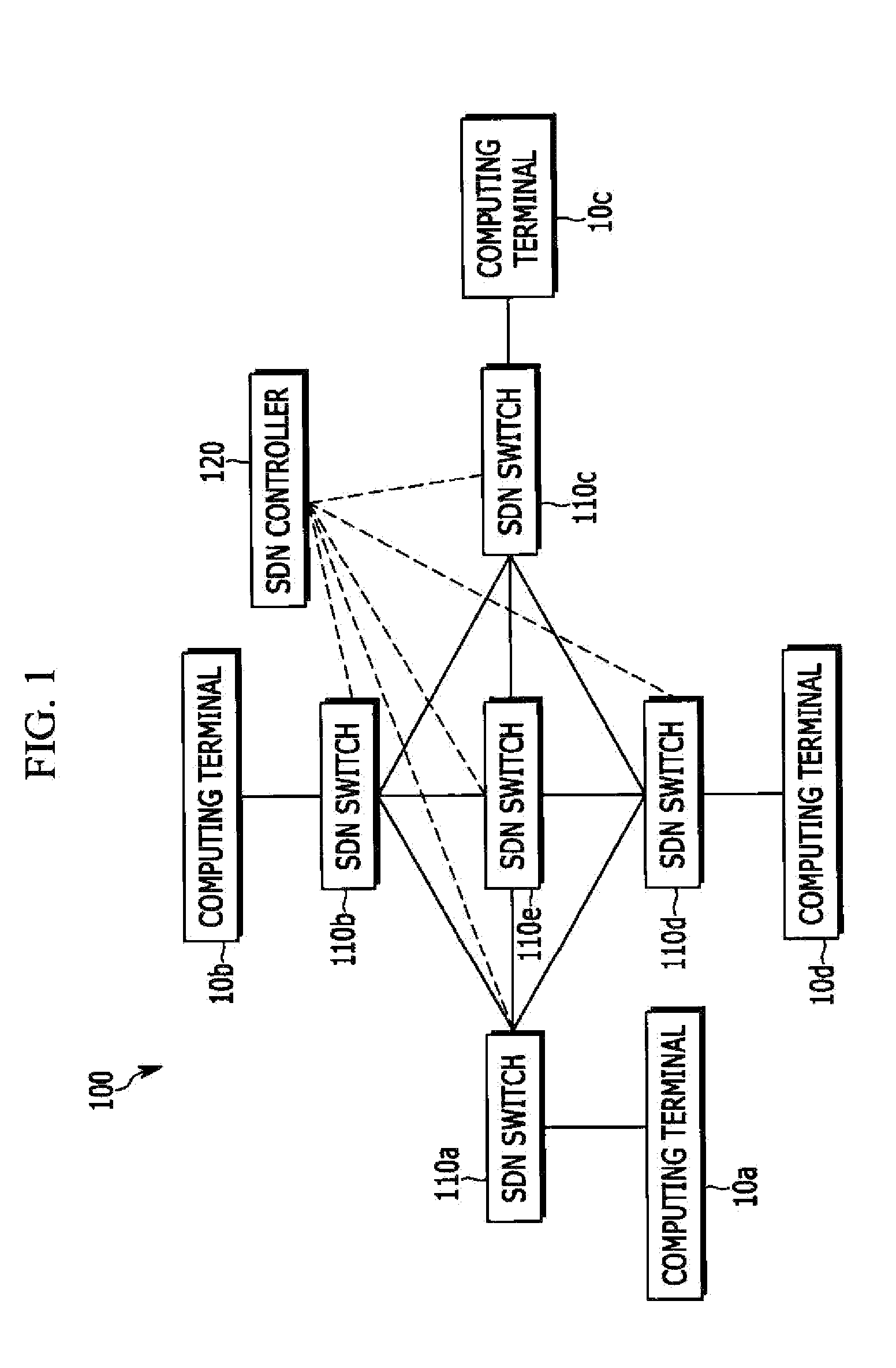
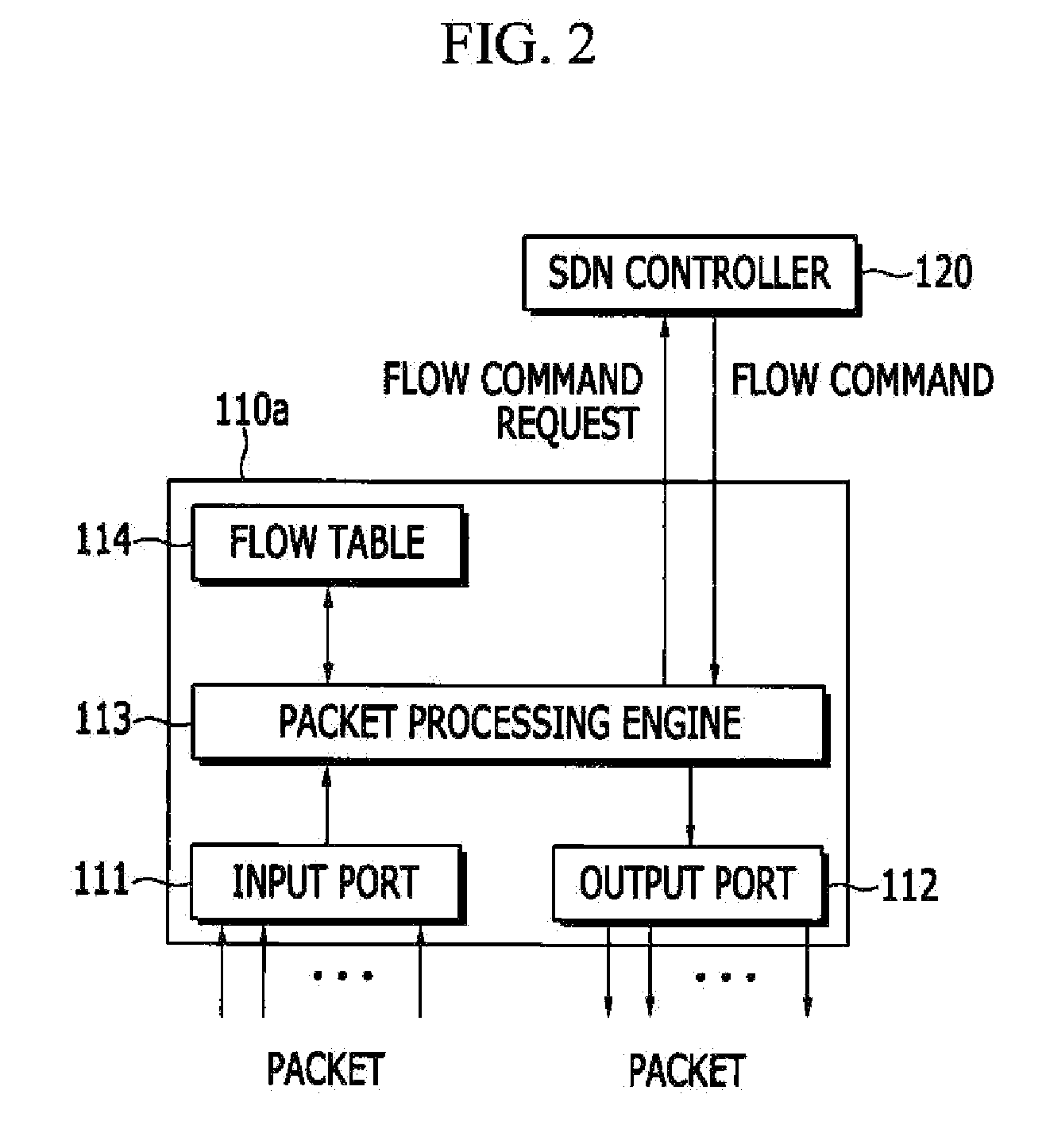
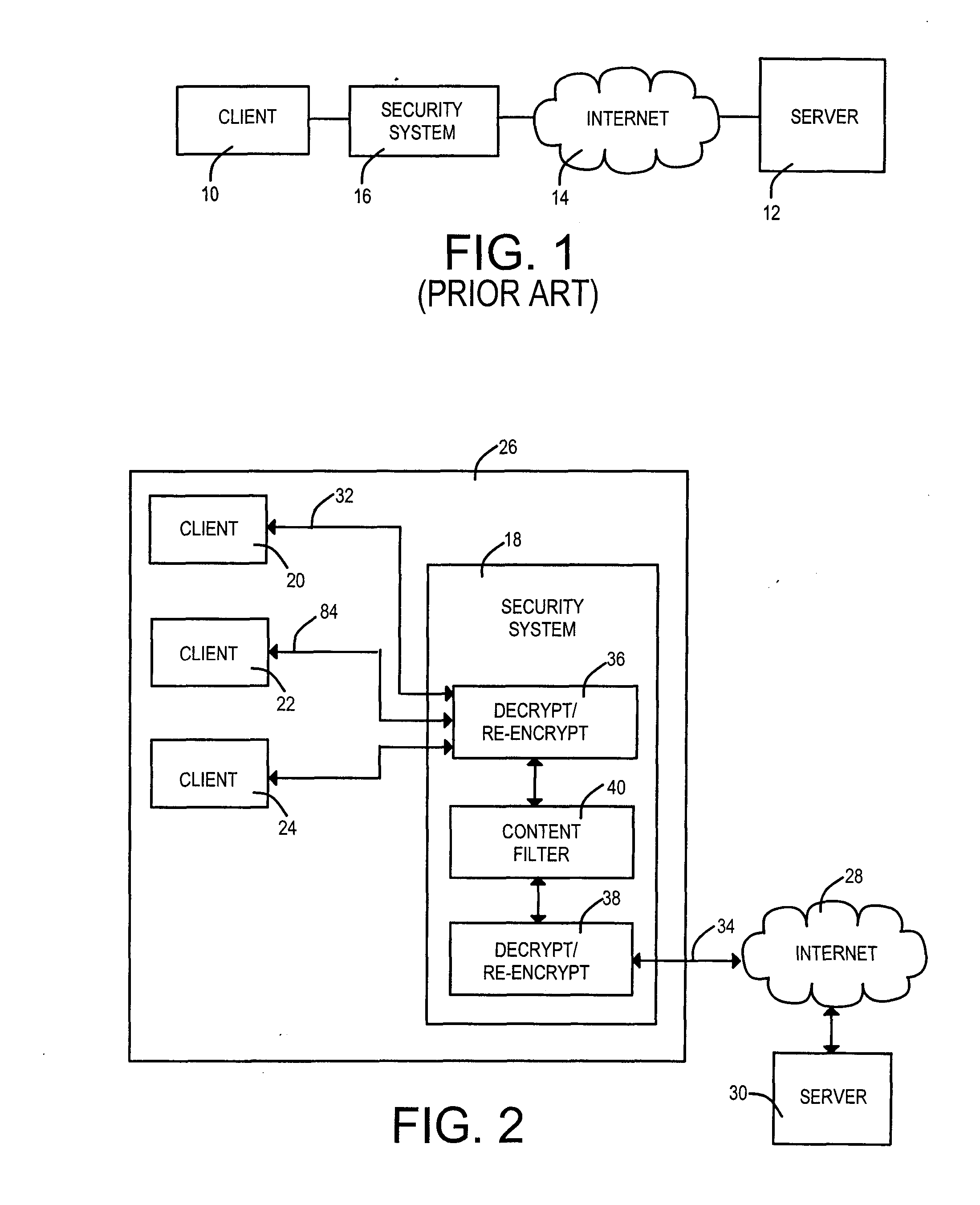
Apparatus and method for transmitting packet
In a software defined network, when an SDN switch receives a packet, the SDN switch calculates a flow entry index using a matching field value belonging to a matching rule that is extracted from the received packet and a flow matching mask field value representing whether a matching field belonging to a matching rule is a field that is designated as a wildcard, processes a packet that is received according to an action that is set to a flow entry that is matched to the flow entry index from a flow table.
Owner:ELECTRONICS & TELECOMM RES INST
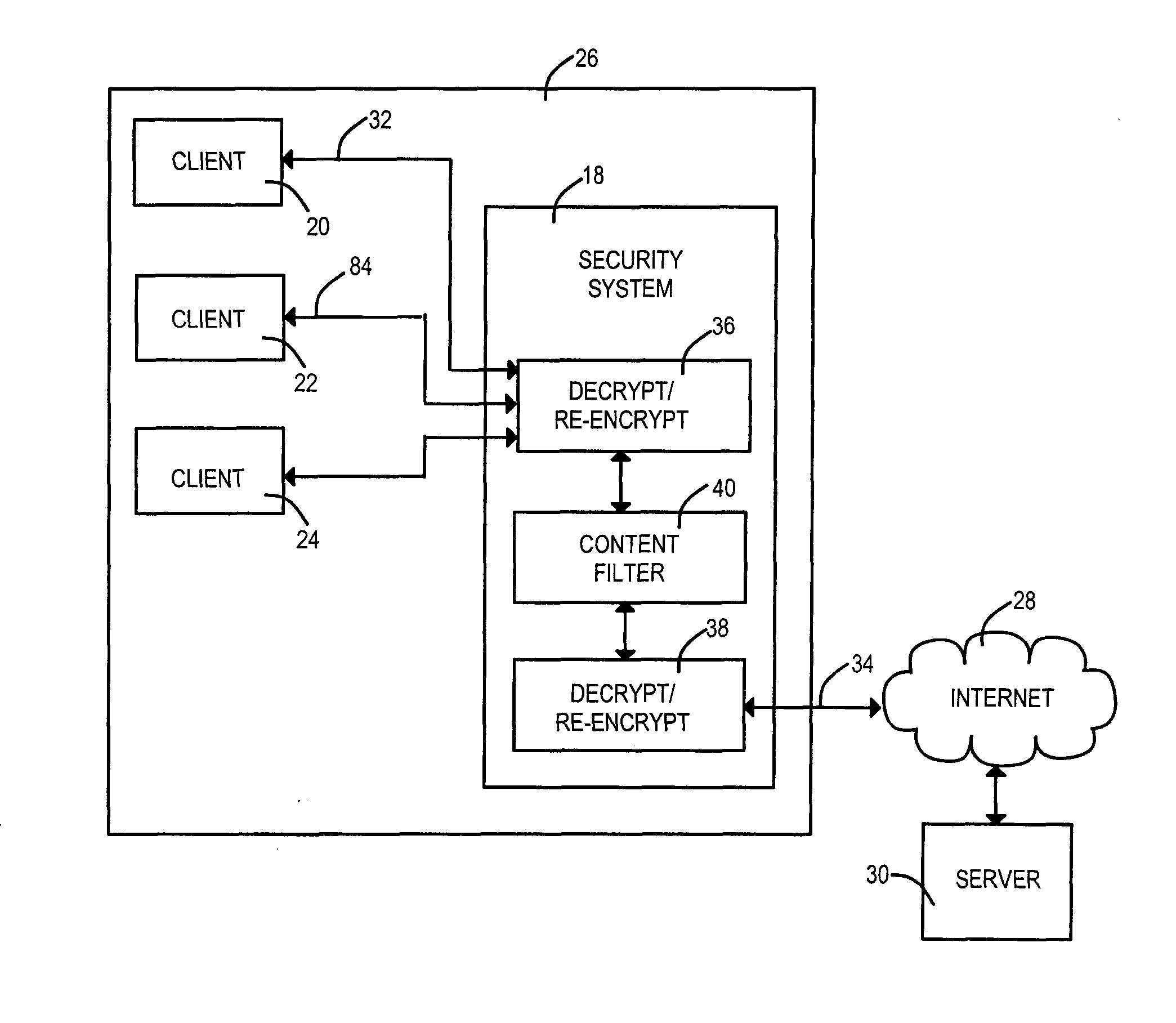
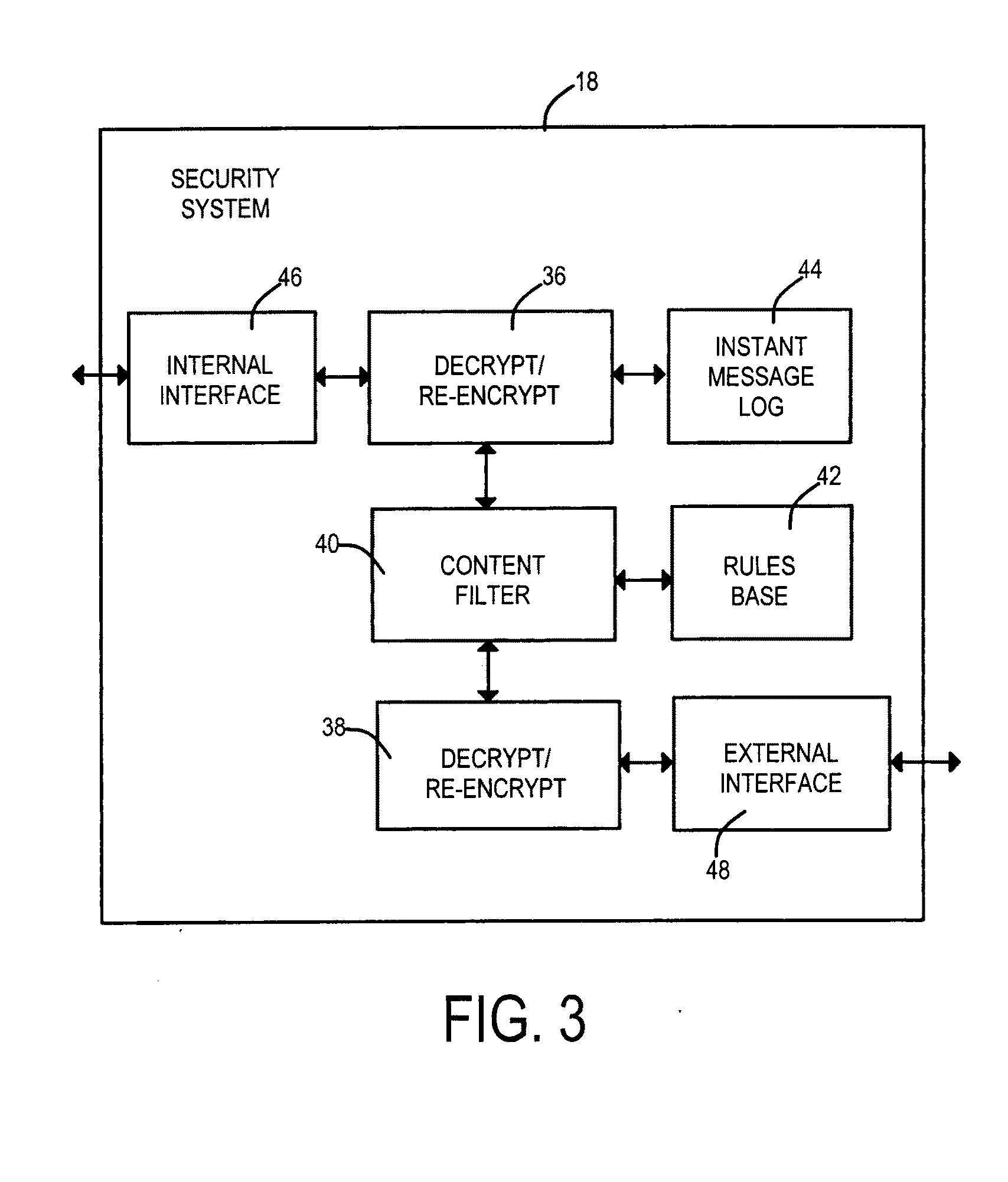
Tandem encryption connections to provide network traffic security method and apparatus
Security measures are applied to encrypted data exchanges by enabling content decryption, rule application, and content re-encryption at a network location. A certificate, self-signed or authenticated by an official Certificate Authority is obtained for and installed within the secure proxy apparatus. A link to a secure page is replaced with a link to a page having a fully qualified domain name of the proxy apparatus as the suffix. An encrypted session between the client is established between the client and the proxy apparatus without deceit in the later case. A first encryption-enabled connection is established from the first node to a content filter, while a second encryption-enabled connection is established from the content filter to the second node. Following decryption, a determination is made as to whether the content includes Undesired Data. Restricted material is blocked, while unrestricted material is re-encrypted and delivered to the destination node. For a self-signed certificate, the destination node comprises a private security system-signed root certificate installed in the destination node's Trusted Root Certification Authorities certificate store. In another aspect of the invention, at least one of encrypted Instant Messages, e-mail messages and web pages are decrypted and recorded at a location between sources and destinations of the transmissions. The look and feel is maintained of a single encrypted link between the requestor and the external source by the inventive use of a wildcard certificate within the network local to the requestor.
Owner:BARRACUDA NETWORKS
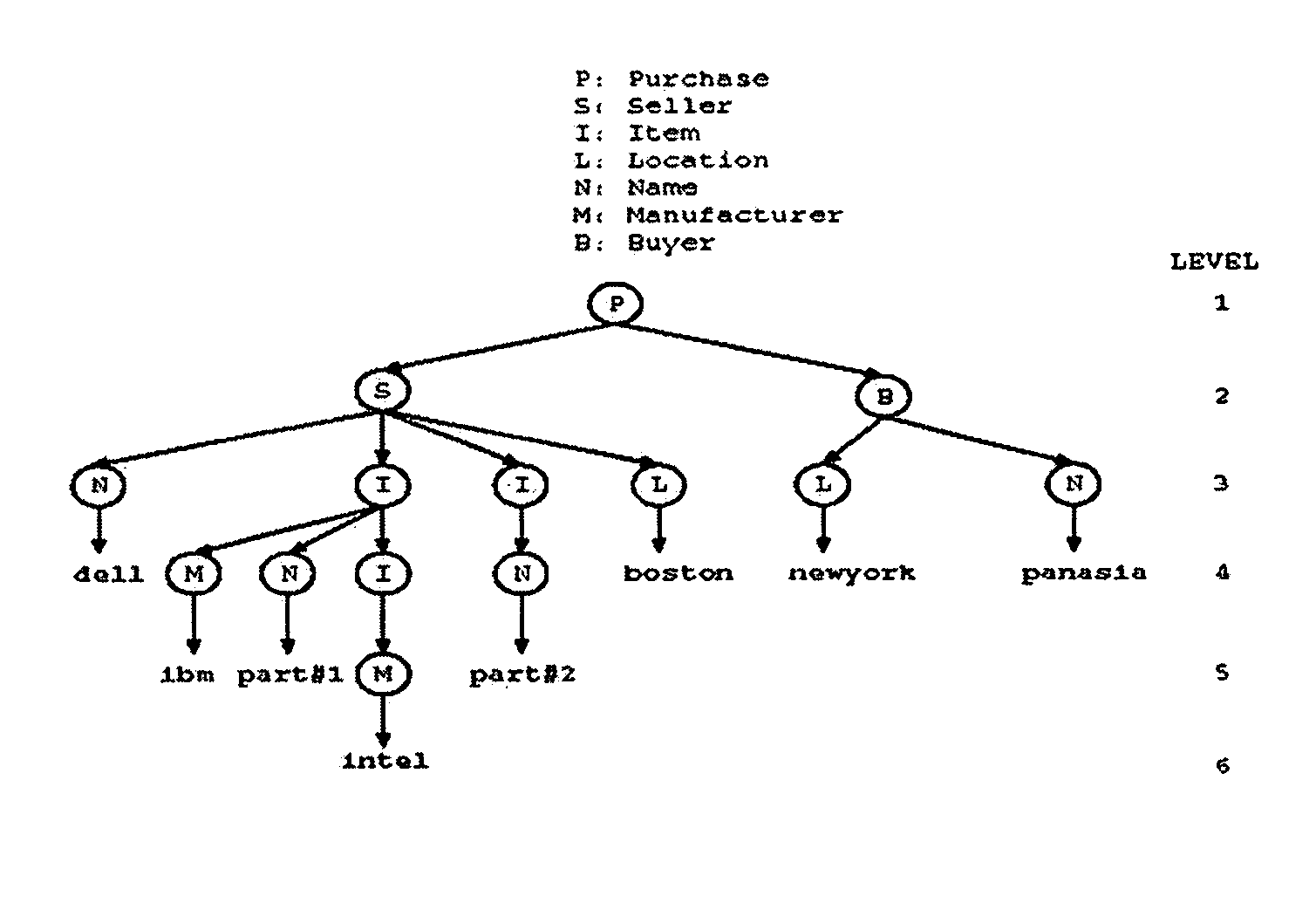
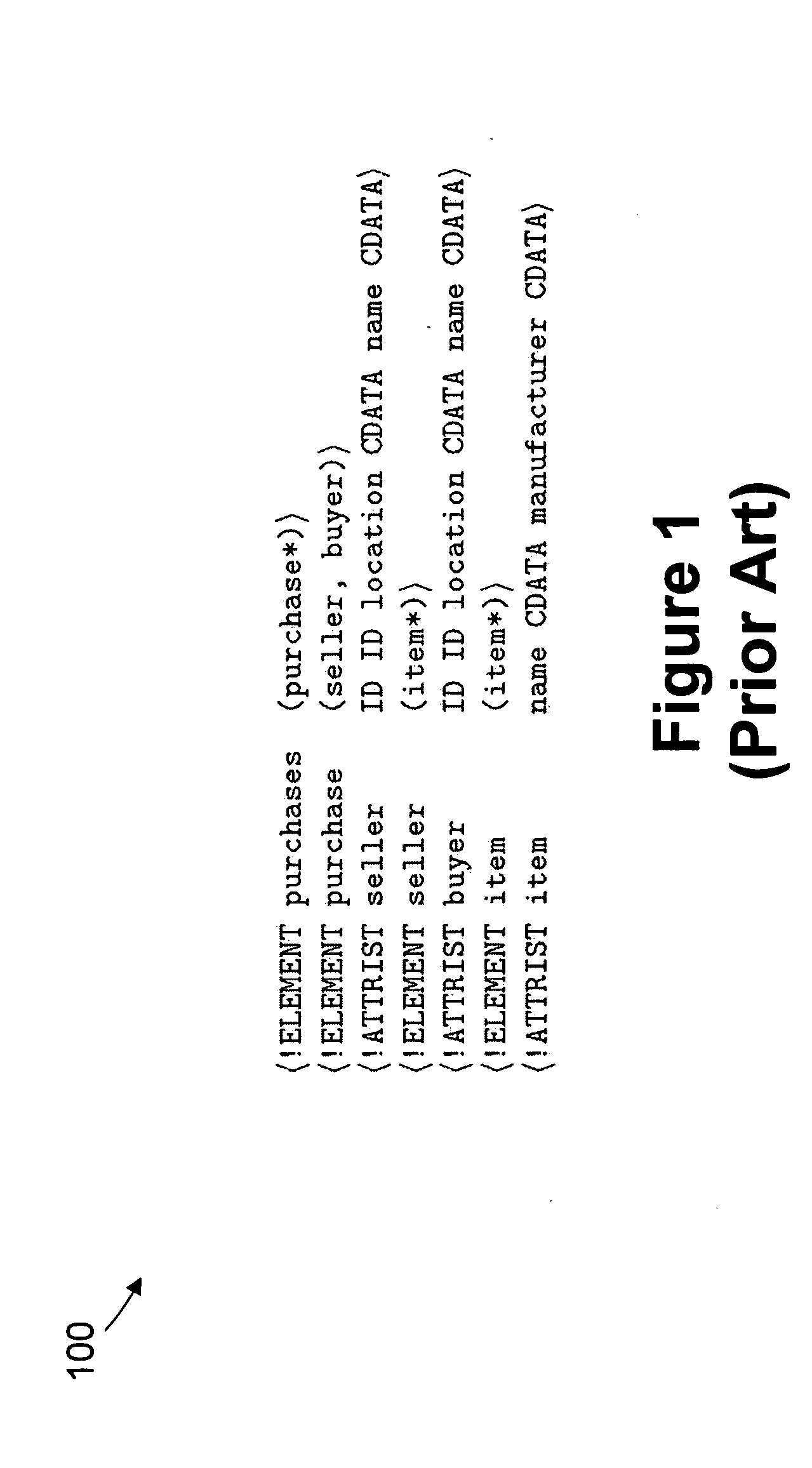
Index structure for supporting structural XML queries
InactiveUS20050114314A1Data processing applicationsSemi-structured data indexingPaper documentWildcard character
The present invention provides a ViST (or “virtual suffix tree”), which is a novel index structure for searching XML documents. By representing both XML documents and XML queries in structure-encoded sequences, it is shown that querying XML data is equivalent to finding (non-contiguous) subsequence matches. A variety of XML queries, including those with branches, or wild-cards (‘*’ and ‘ / / ’), can be expressed by structure-encoded sequences. Unlike index methods that disassemble a query into multiple sub-queries, and then join the results of these sub-queries to provide the final answers, ViST uses tree structures as the basic unit of query to avoid expensive join operations. Furthermore, ViST provides a unified index on both content and structure of the XML documents, hence it has a performance advantage over methods indexing either just content or structure. ViST supports dynamic index update, and it relies solely on B+Trees without using any specialized data structures that are not well supported by common database management systems (hereinafter referred to as “DBMSs”).
Owner:IBM CORP
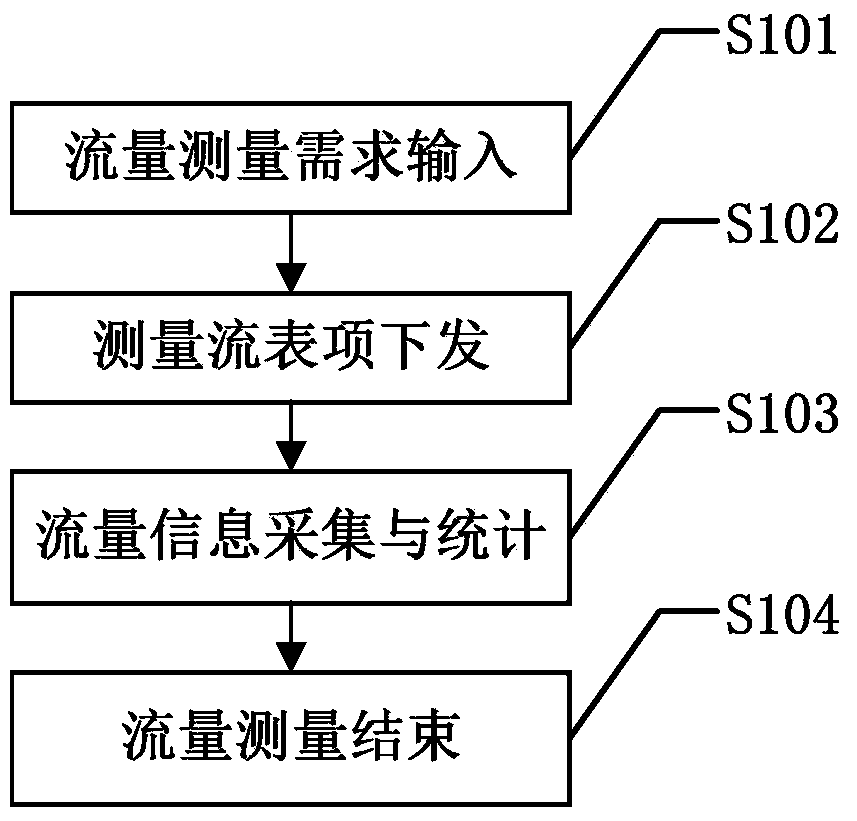
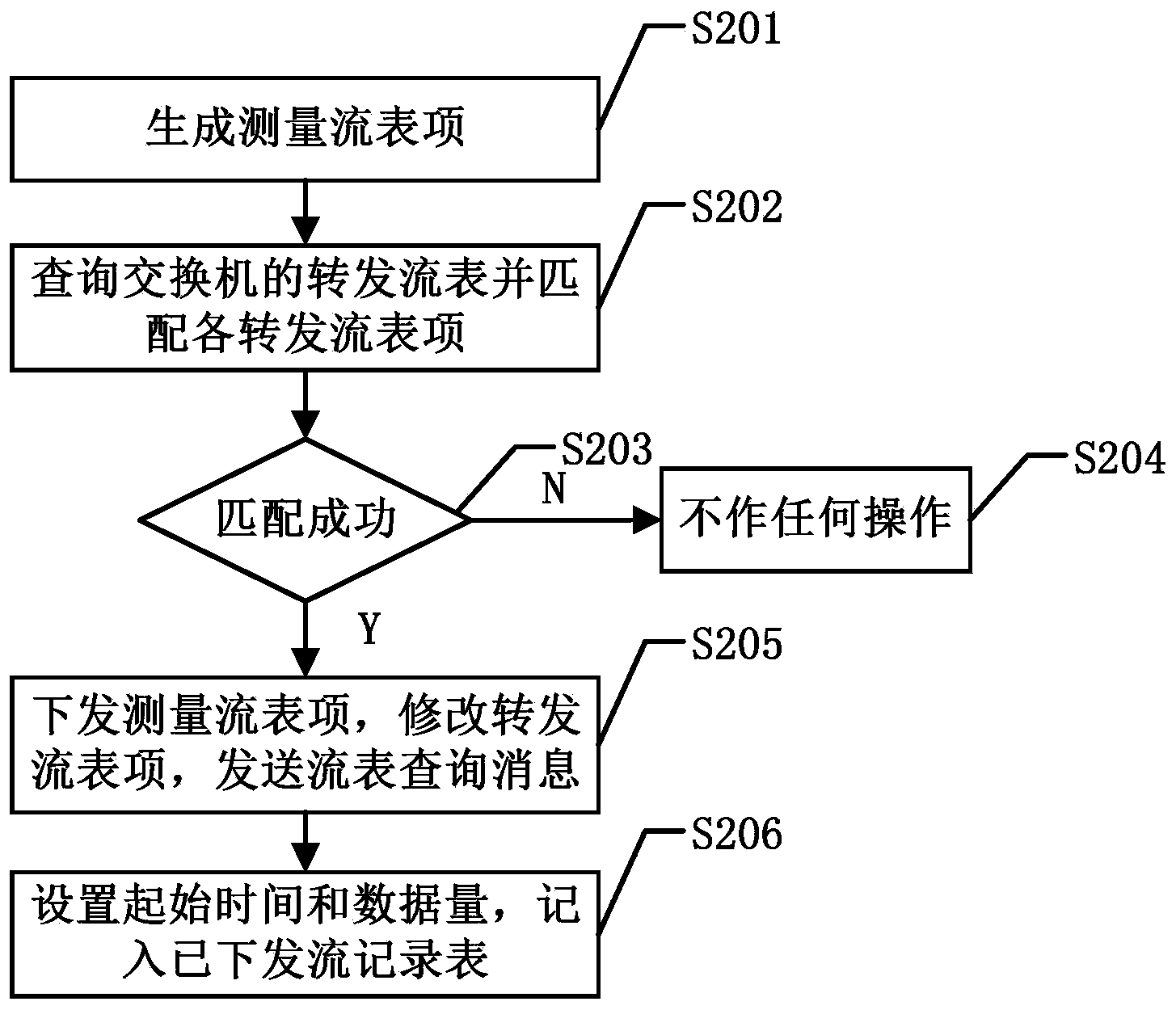
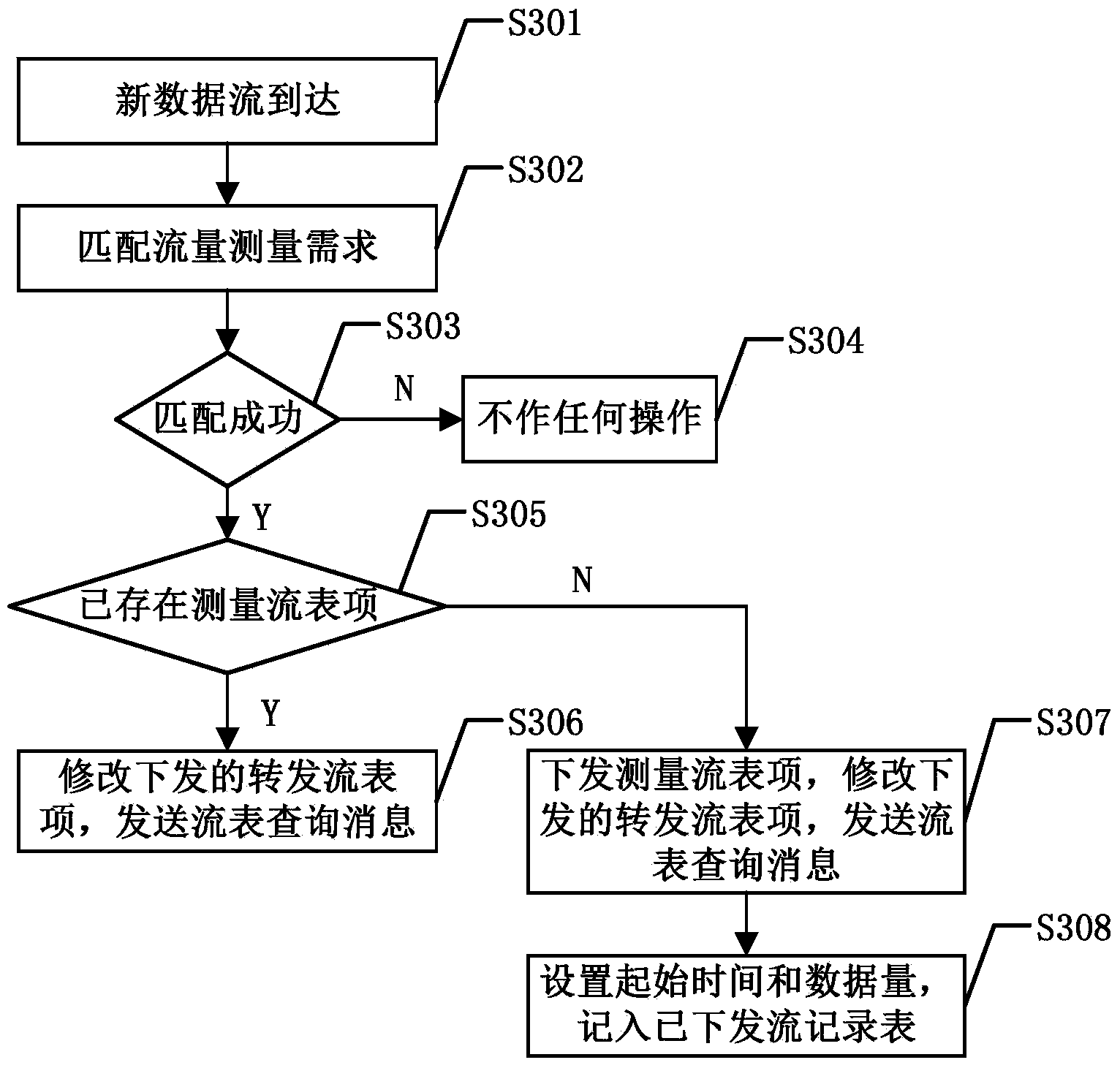
SDN (self-defending network) flow measuring method based on Open Flow
InactiveCN104243240AReduce overheadGuaranteed GranularityData switching networksData streamDischarge measurements
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
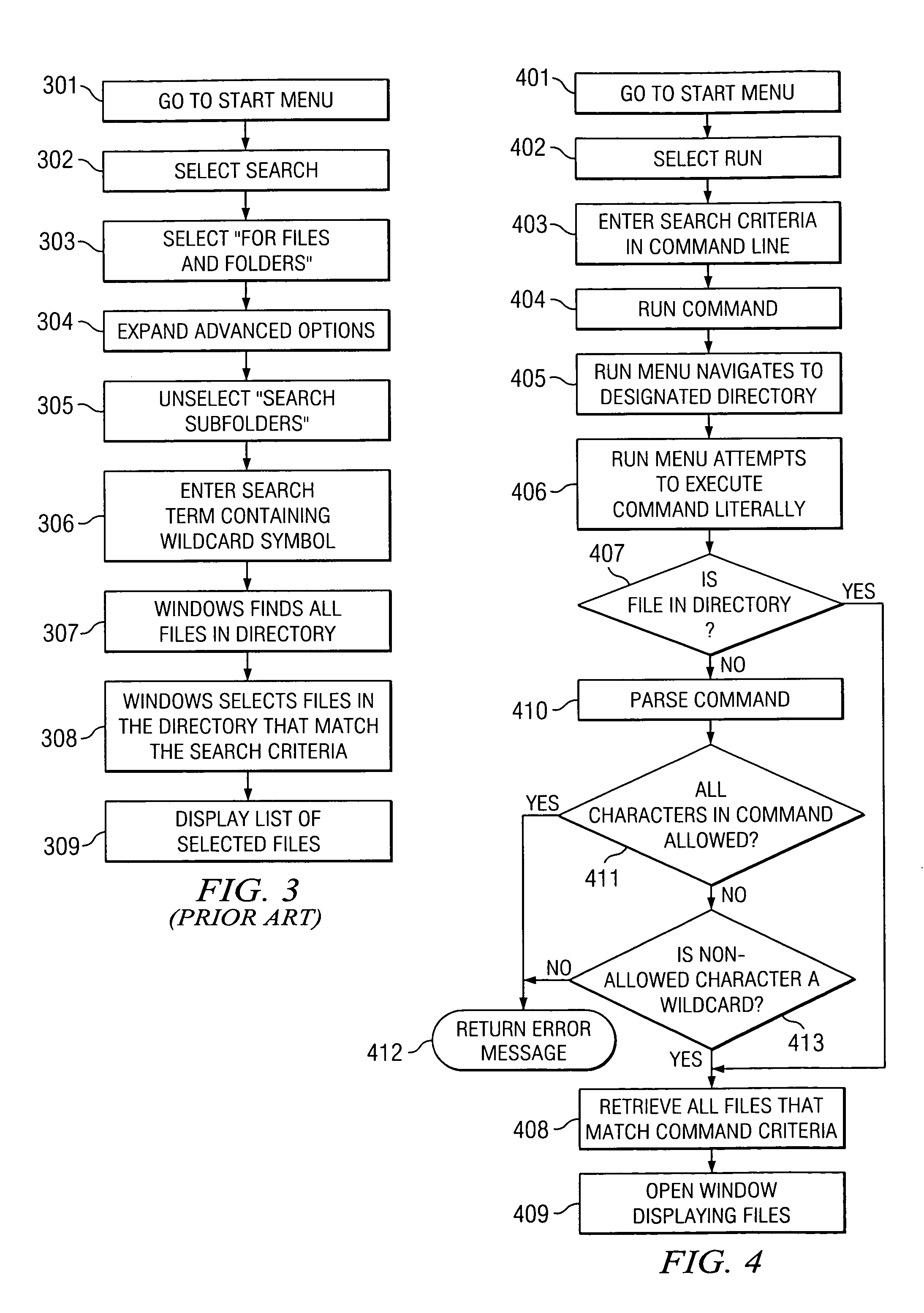
Search for specific files from the run menu
InactiveUS20050177567A1Special data processing applicationsFile systemsOperational systemWildcard character
A method, program and system for searching for files in a computer system employing a Windows operating system is provided. The invention includes receiving search criteria through a Run menu command line, wherein the Run menu is opened by selecting a Start menu, and wherein the search criteria include: a directory and at least one wildcard symbol that represents any number of unspecified characters. The wildcard symbol may represent characters in a file name or character desginating a file type. The search criteria may also include a definite identifying character (e.g., t), which may be part of the file name or file type. The invention searches the directory specified in the search criteria and retrieves a list of the files in the directory that match the search criteria. The invention then opens a window and displays the list of retrieved files.
Owner:IBM CORP
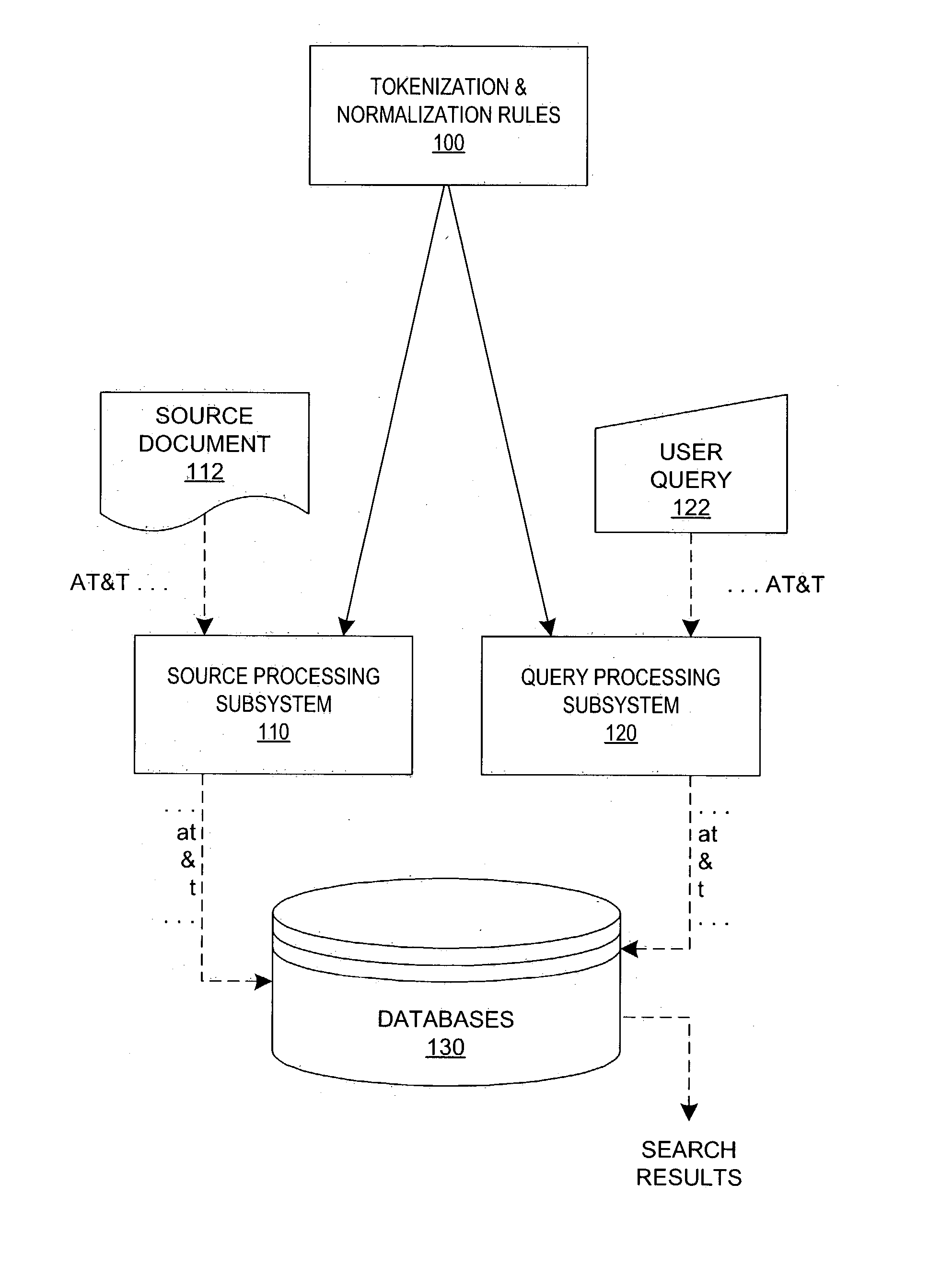
Apparatus and method for generating data useful in indexing and searching
ActiveUS20030200199A1Data processing applicationsNatural language data processingWildcard characterDocument preparation
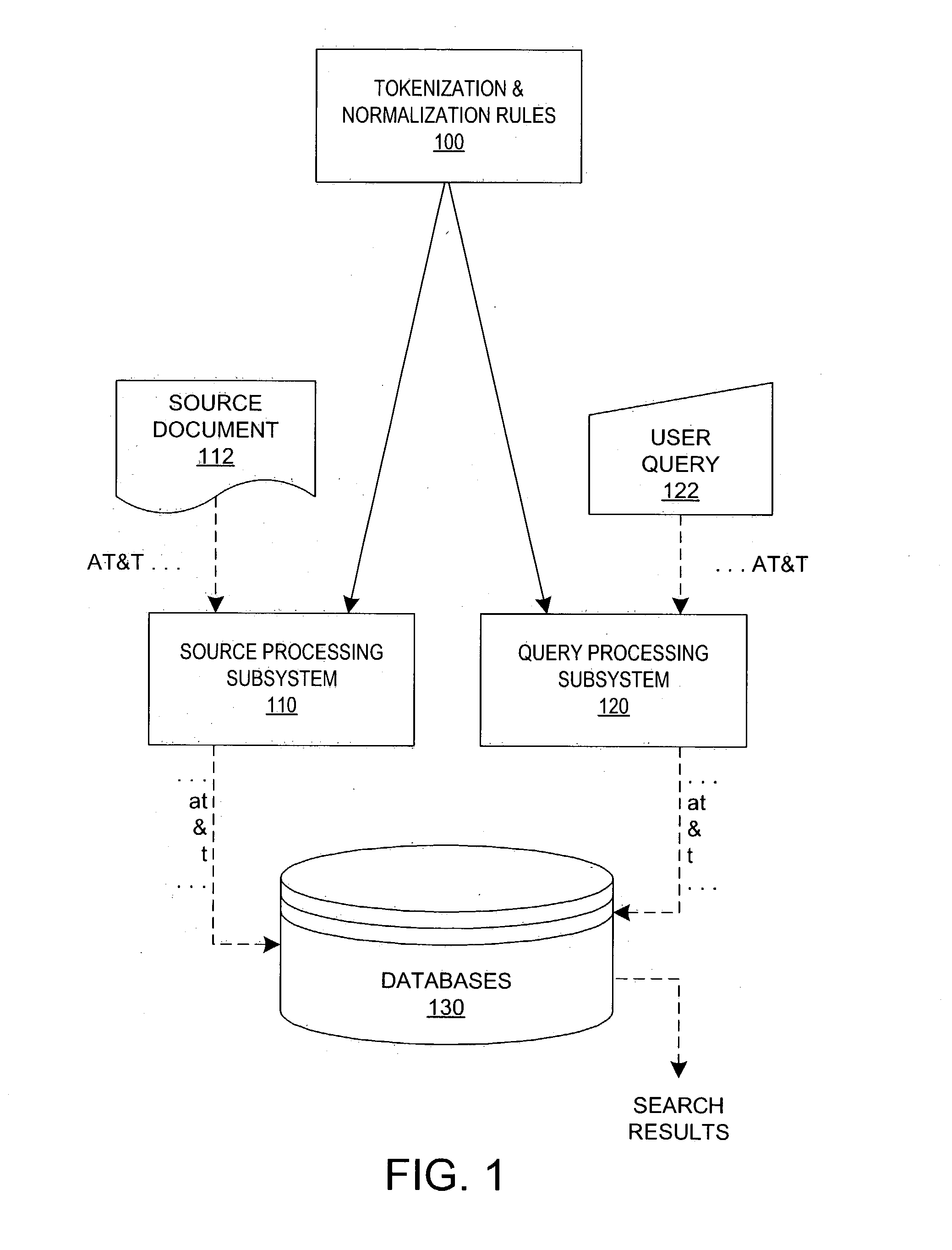
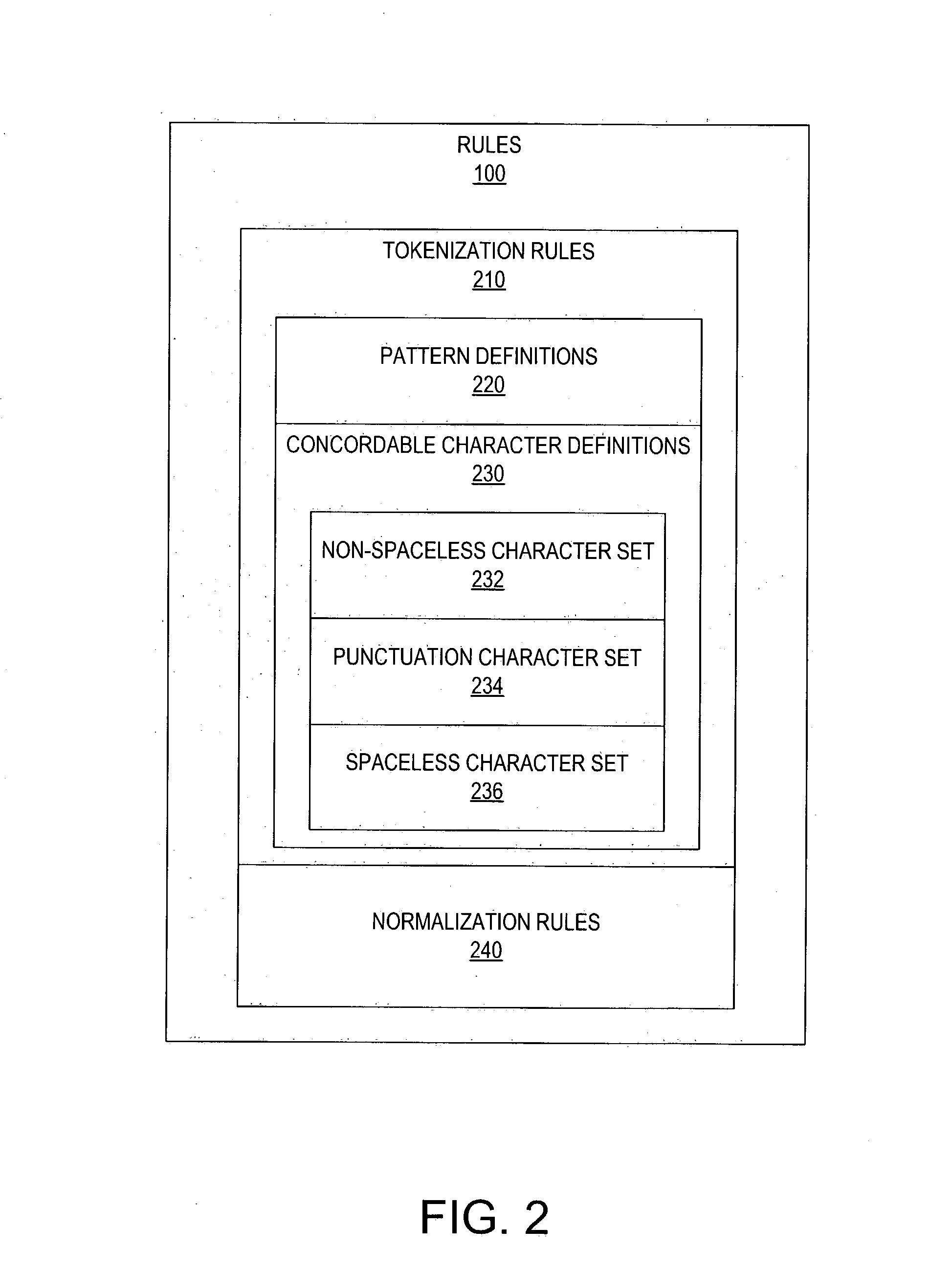
Processing of source documents to generate data for indexing, and of queries to generate data for searching, is done in accordance with retrieved tokenization rules and, if desired, retrieved normalization rules. Tokenization rules are used to define exactly what characters (letters, numbers, punctuation characters, etc.) and exactly what patterns of those characters (one or more contiguous characters, every individual character, etc.) comprise indexable and searchable units of data. Normalization rules are used to (potentially) modify the tokens created by the tokenizer in indexing and / or searching operations. Normalization accounts for things such as case-insensitive searching and language-specific nuances in which document authors can use accepted variations in the spelling of words. Query processing must employ the same tokenization and normalization rules as source processing in order for queries to accurately search the databases, and must also employ another set of concordable characters for use in the query language. This set of "reserved" characters includes characters for wildcard searching, quoted strings, field-qualified searching, range searching, and so forth.
Owner:DOW JONES REUTERS BUSINESS INTERACTIVE
Method and appliance for XML policy matching
ActiveUS20090037379A1Digital data information retrievalSpecial data processing applicationsStreaming XMLTheoretical computer science
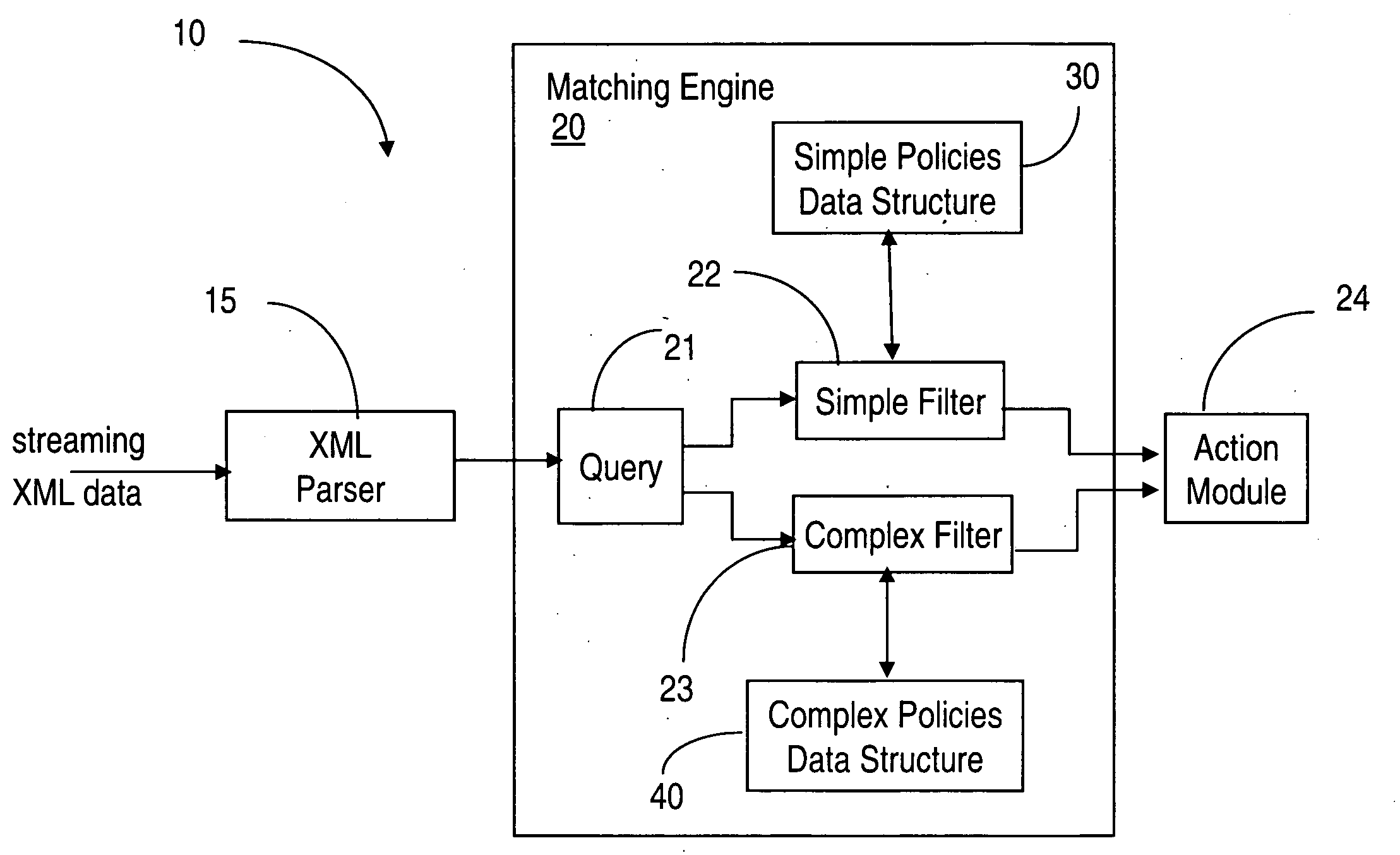
An XML matching engine and method are provided, where policy rules expressed using XPath / XQuery policies are matched to streaming XML documents. Two distinct data structures are used: a combined modified DFA data structure for storing simple XPath queries (no wildcards or descendents) and a modified AFilter structure for storing complex queries (with wildcards or / and descendents). As the matching engine receives XML tags from XML parser, matching is performed in both structures in parallel.
Owner:RPX CORP
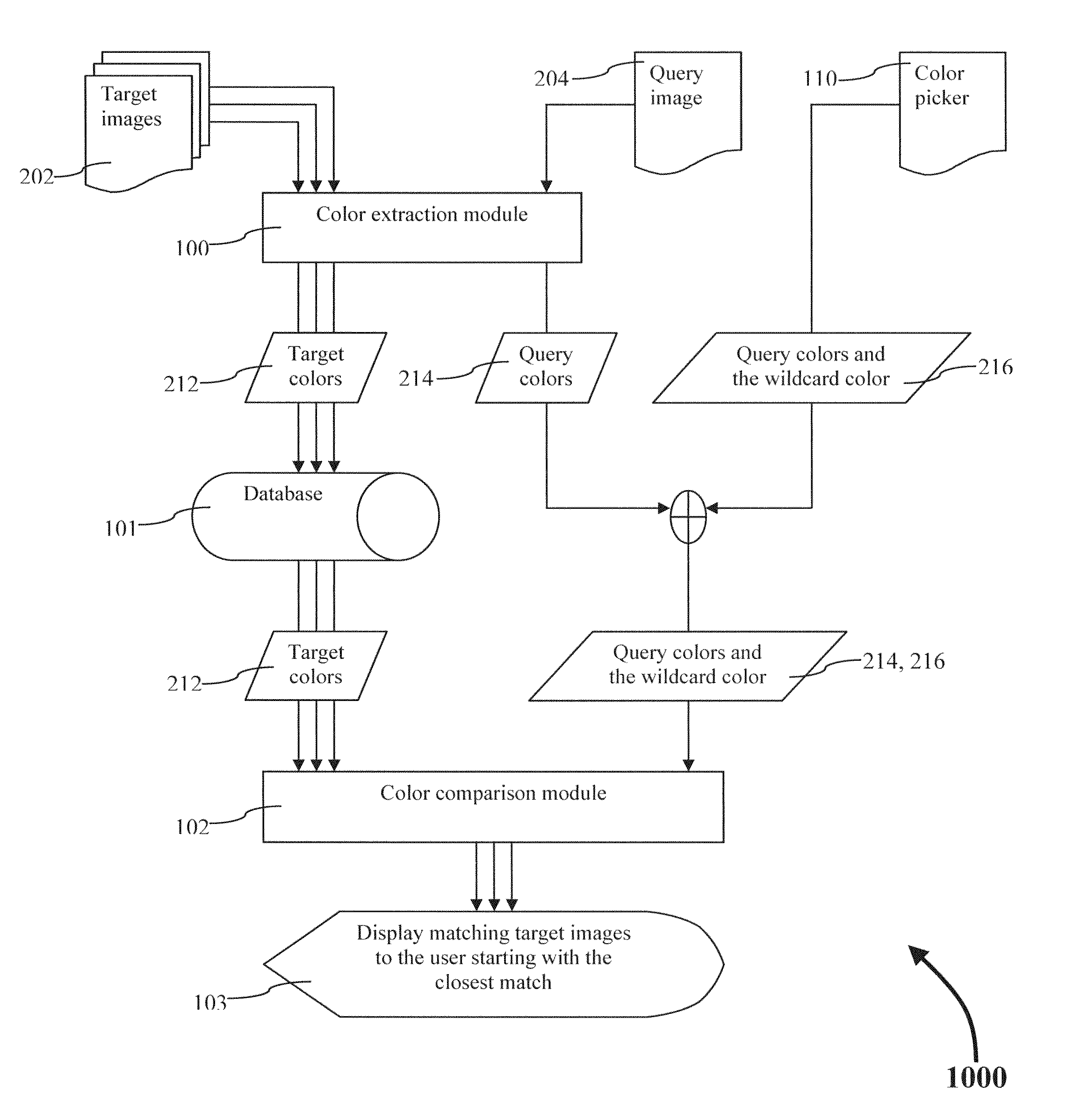
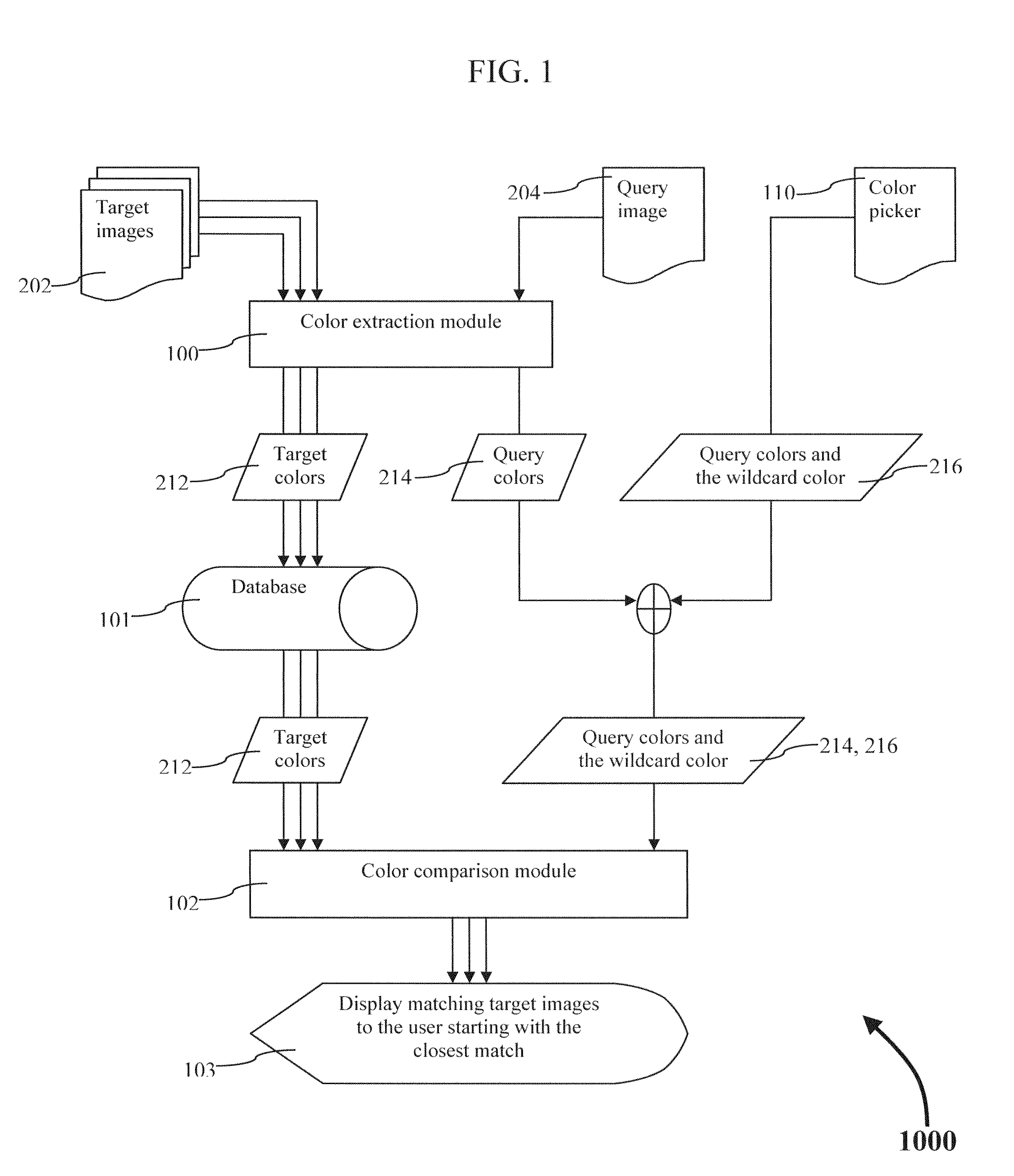
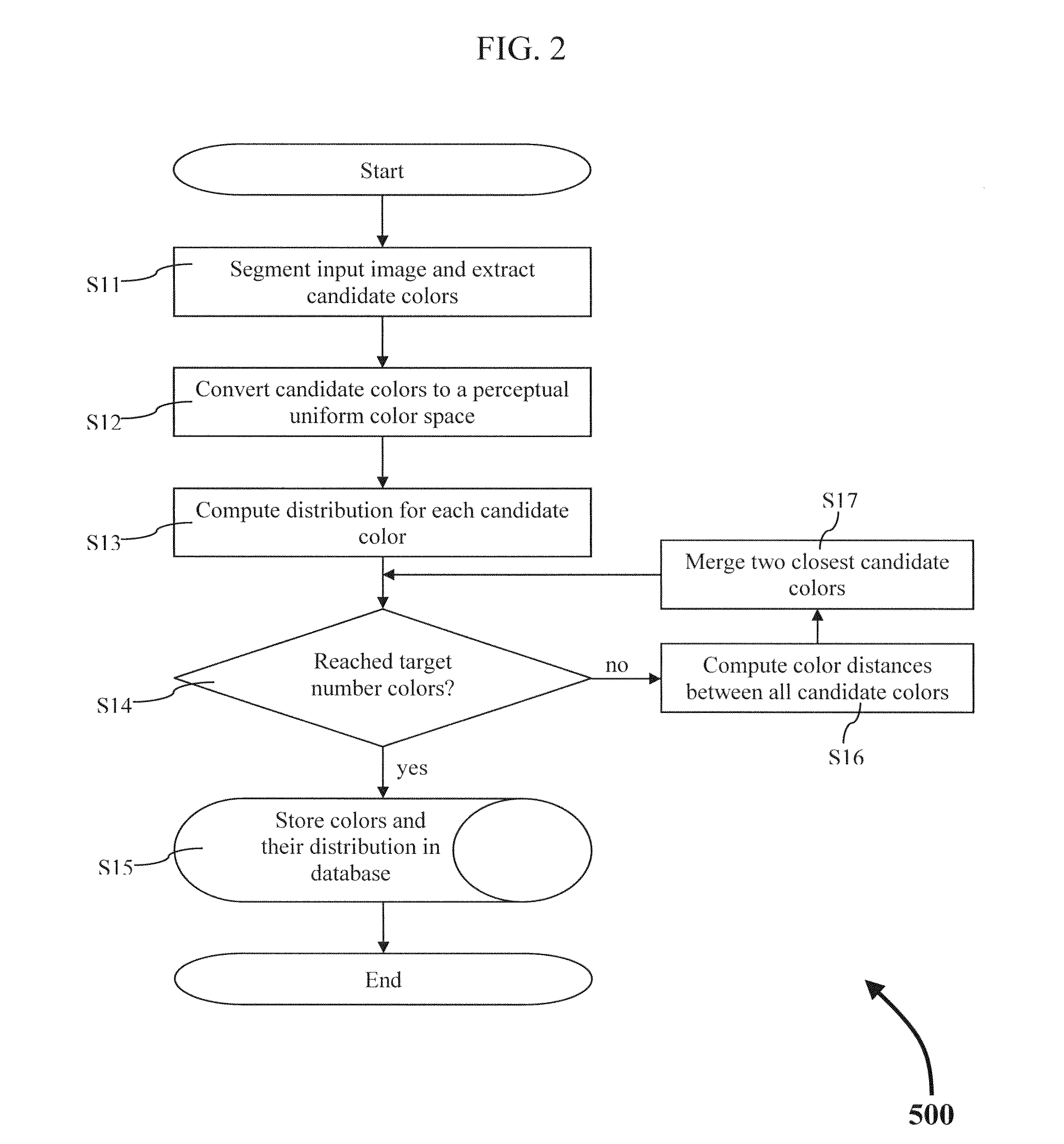
Wildcard color searching
ActiveUS20140334722A1Method is fastEasy to useImage analysisCharacter and pattern recognitionPattern recognitionWildcard character
A method of extracting the dominant colors from a set of target images and storing those colors in a database is described. A method of comparing colors stored in a database with a set of colors extracted from a query image. Also, a method of comparing colors stored in the database with a set of colors defined by a user using a color picker. The user defined colors may or may not include a wildcard color. The list of matching database images may or may no be filtered using metadata.
Owner:IDEE
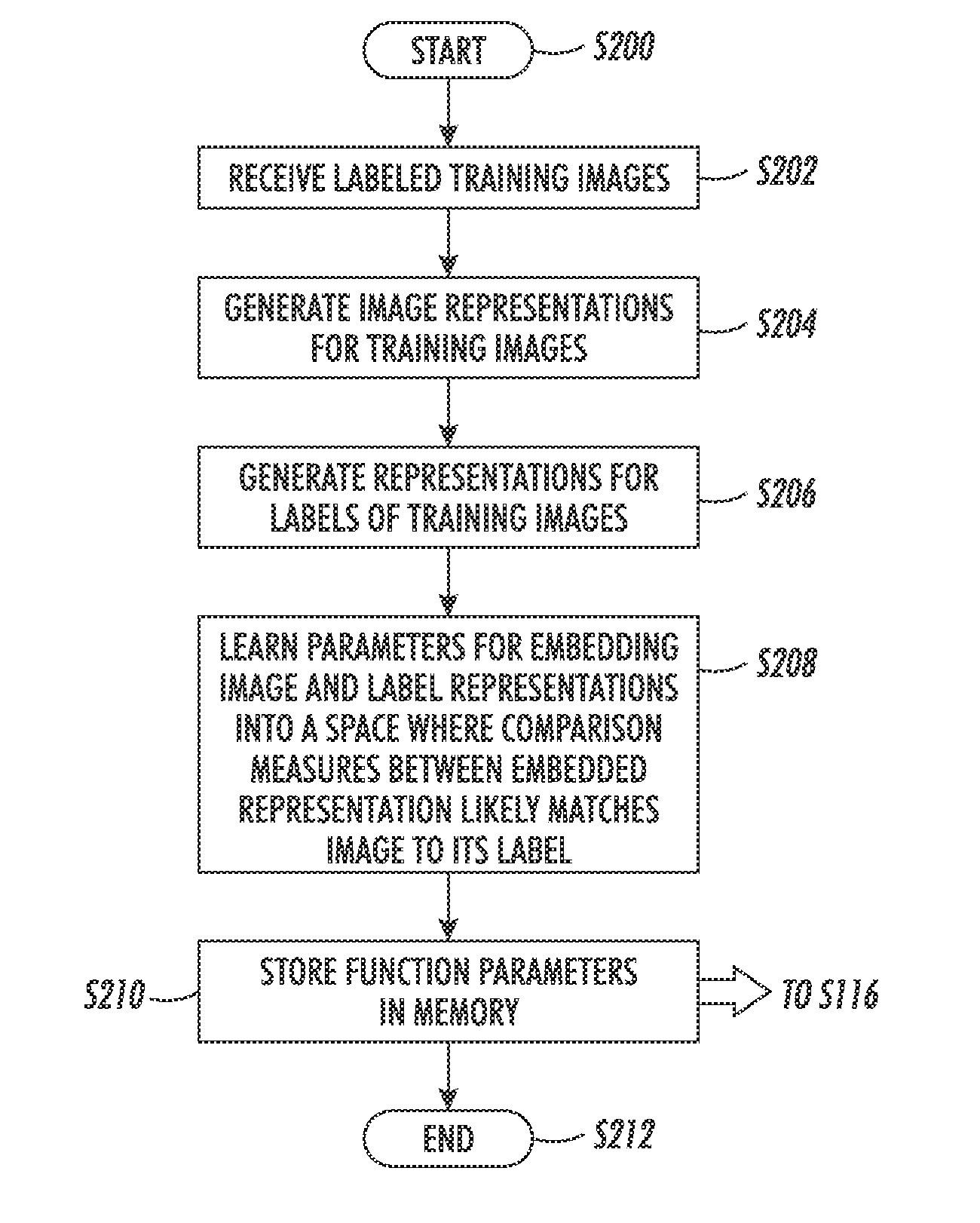
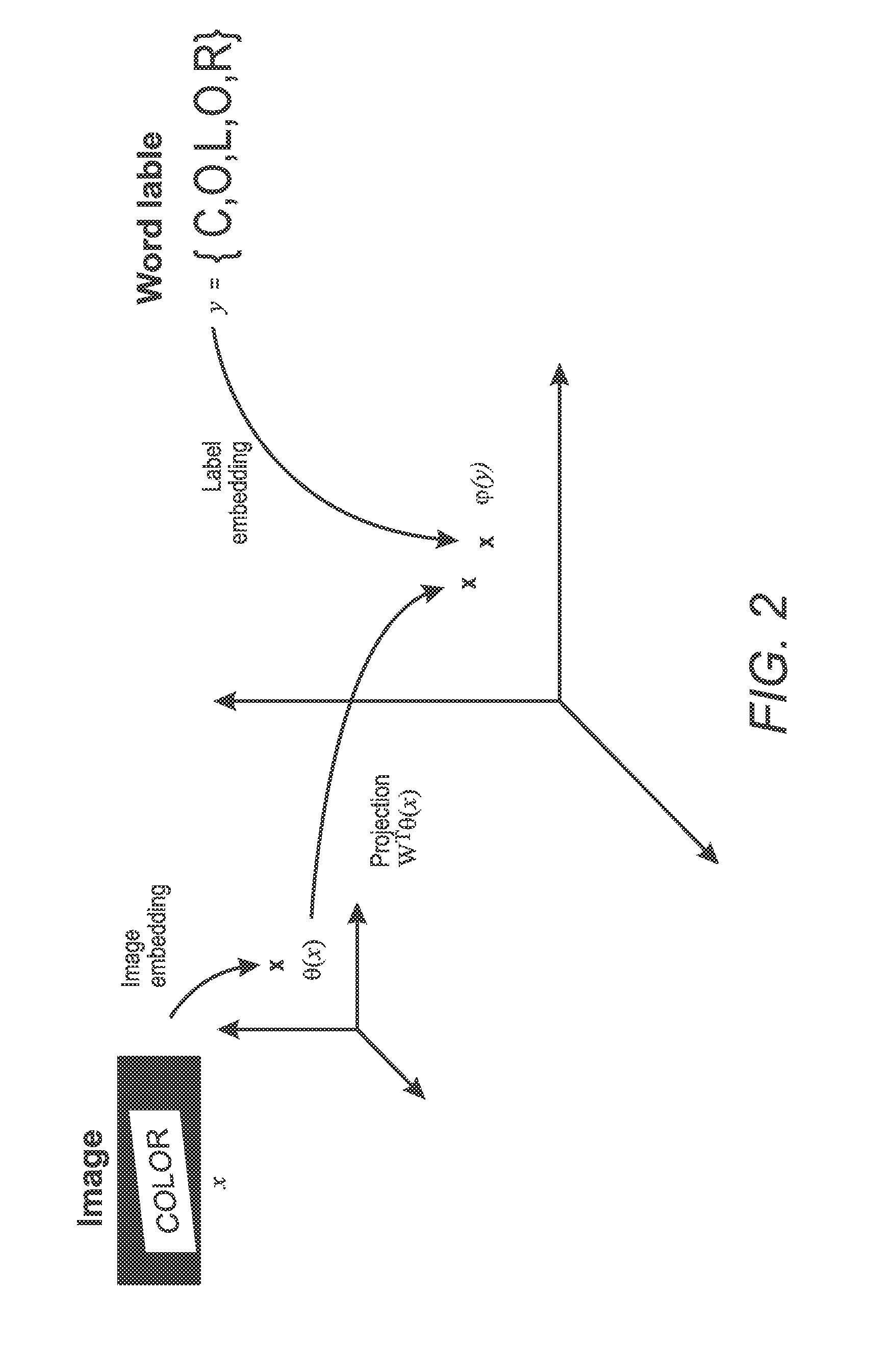
Method and system to perform text-to-image queries with wildcards
A system and method for comparing a text image with or without a wildcard character and a character string are provided. The method includes embedding a character string into a vectorial space by extracting a set of features from the character string and generating a character string representation based on the extracted features, such as a spatial pyramid bag of characters (SPBOC) representation. A text image is embedded into a vectorial space by extracting a set of features from the text image and generating a text image representation based on the text image extracted features. A similarity between the text image representation and the character string representation is computed, which includes computing a function of the text image representation and character string representation.
Owner:CONDUENT BUSINESS SERVICES LLC
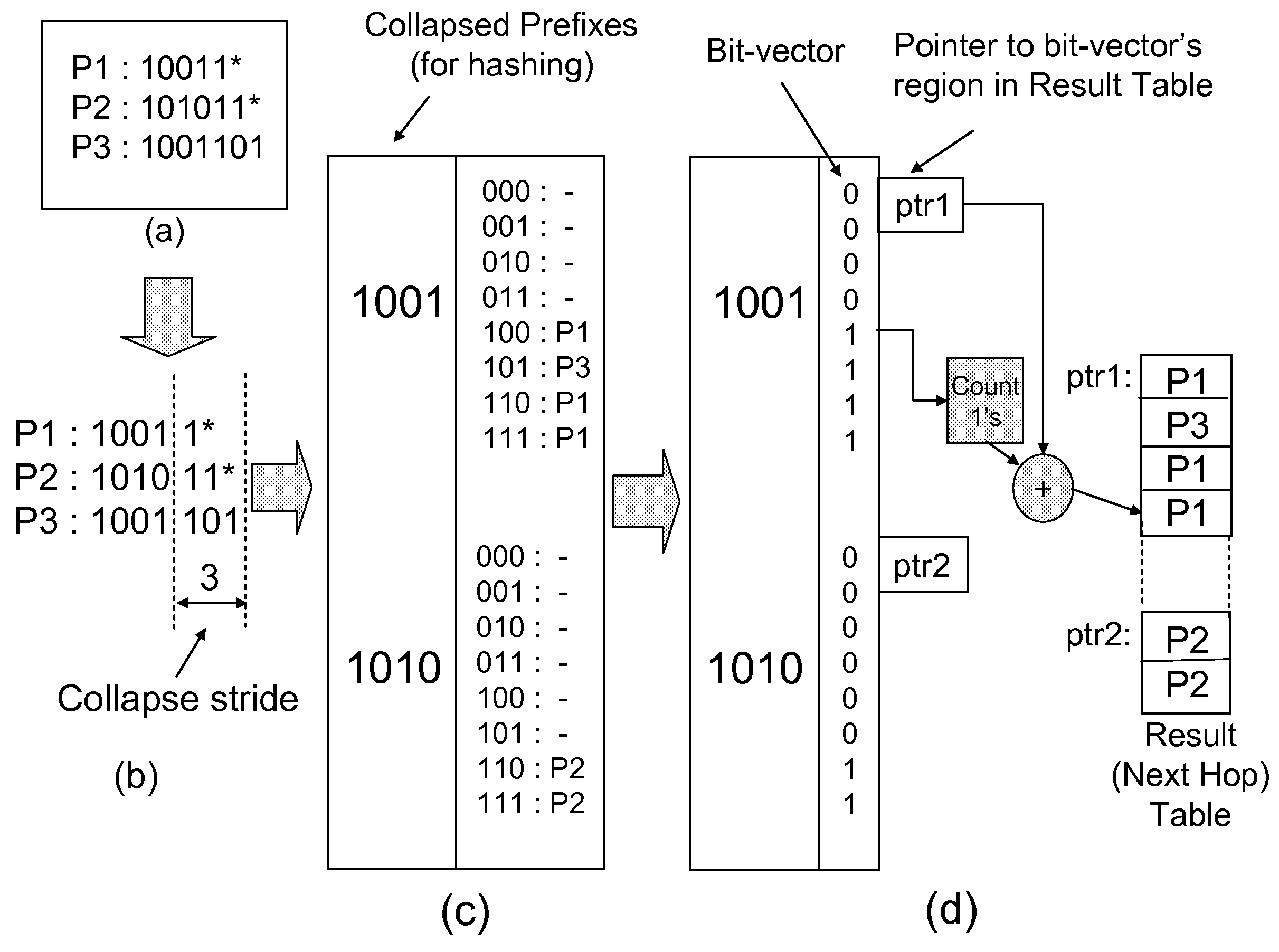
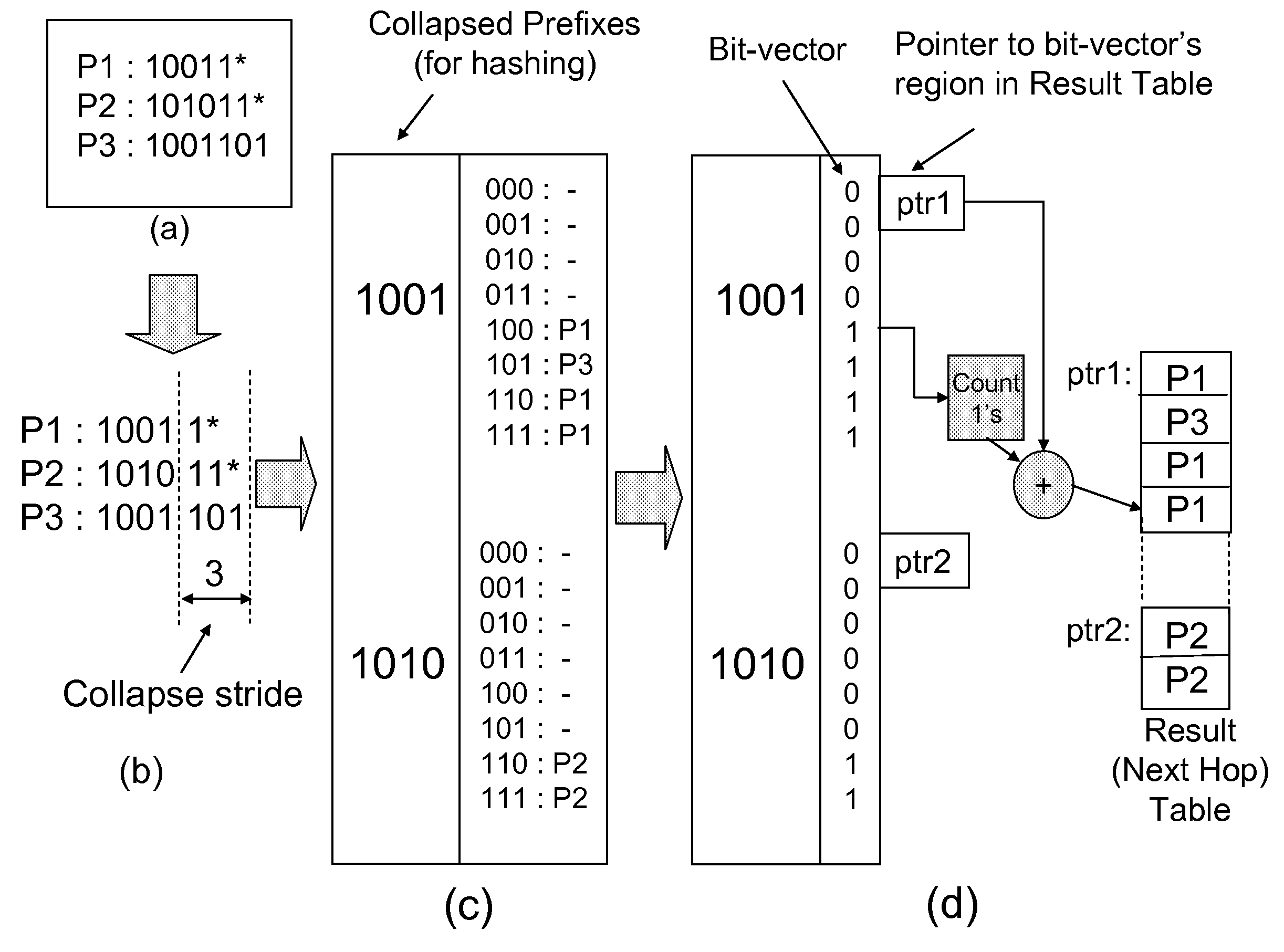
Storage-efficient and collision-free hash-based packet processing architecture and method
InactiveUS20070136331A1Eliminating false positivesLess storageData processing applicationsDigital data information retrievalHardware complexityWildcard character
An architecture and method for data storage and retrieval which also addresses a number of key problems associated with systems employing hash-based techniques. The architecture and method employs a collision-free hashing scheme called Bloomier filter while eliminates its false positives in a storage efficient way. Wildcard support is added through the use of a scheme called prefix collapsing, while introducing only a small additional storage requirement and reduced hardware complexity. Real update traces indicate that both fast and incremental updates are provided—features generally not available in prior-art collision-free hashing schemes.
Owner:NEC CORP
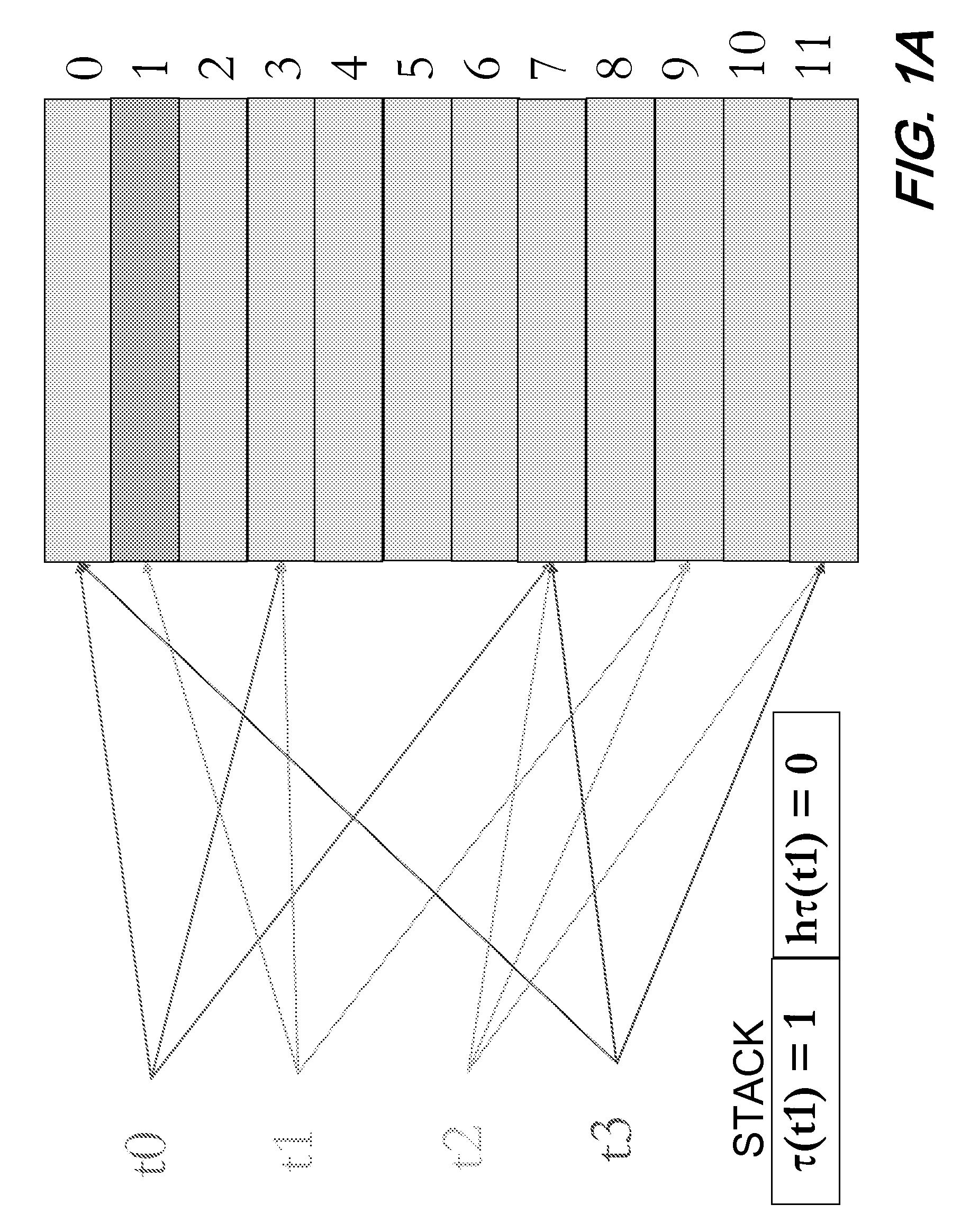
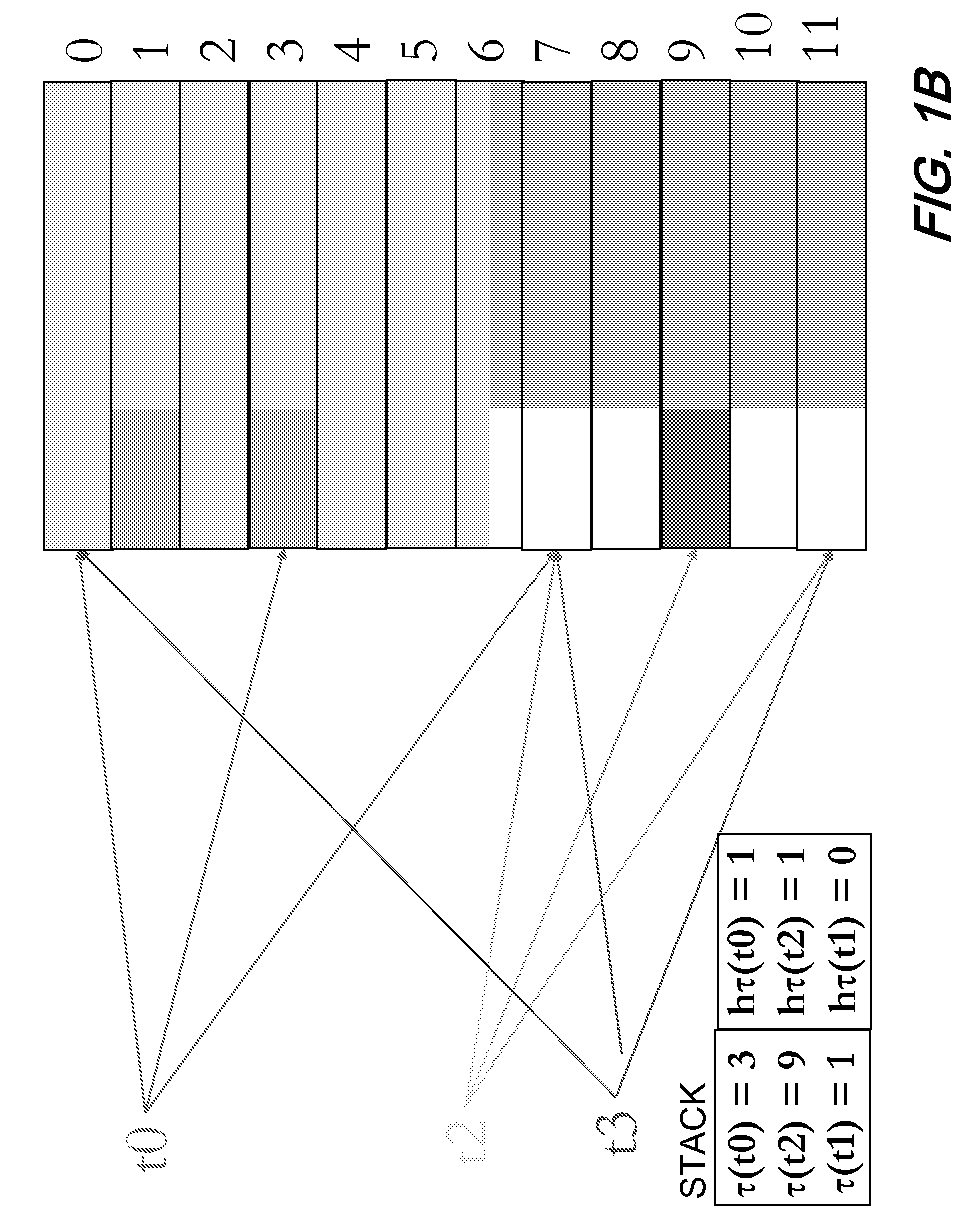
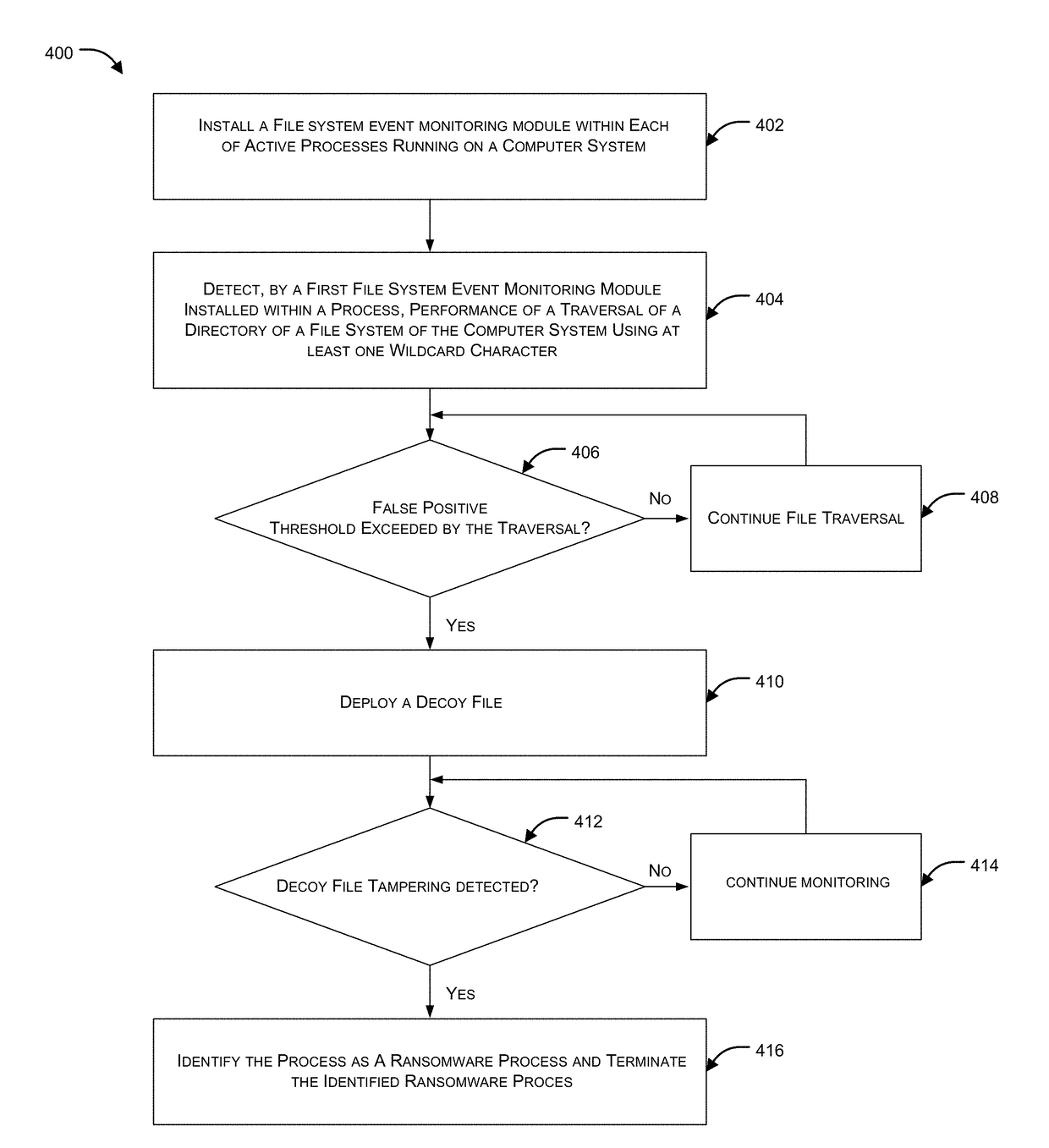
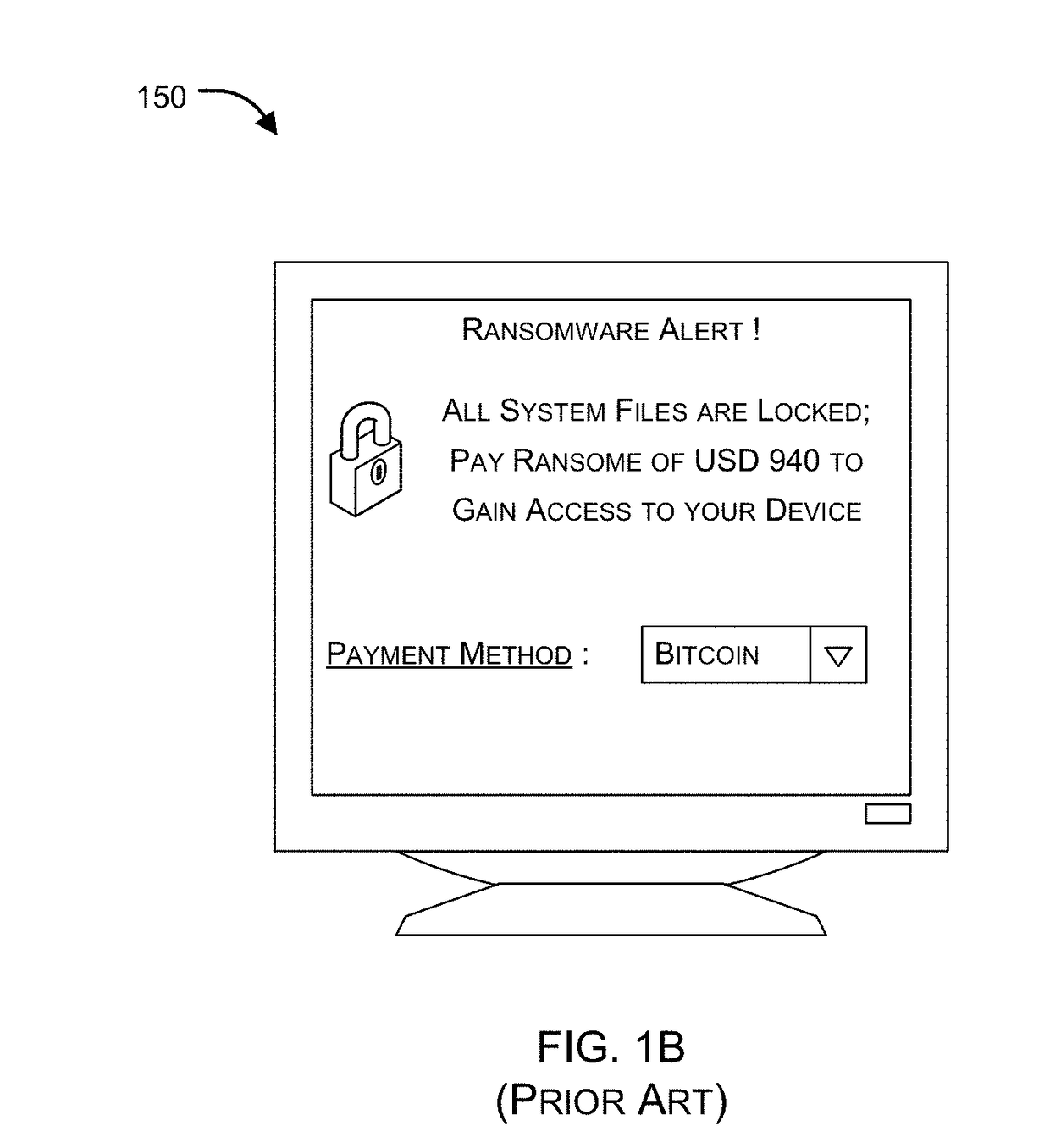
Ransomware detection and damage mitigation
Systems and methods for file encrypting malware detection are provided. According to one embodiment, a monitoring module is installed within active processes running on a computer system by a kernel mode driver. Performance of a directory traversal operation on a directory of the computer system is detected by a monitoring module of a first process of the multiple active processes in which a parameter of the traversal operation includes a wildcard character. When a number of wildcard-based directory traversal operations performed by the first process exceeds a threshold, a decoy file is deployed by the monitoring module within the directory and the driver is notified. The driver monitors for and detects an attempt by the first process to tamper with the decoy file by intercepting and evaluating file system operations. Responsive to detection of the attempt, the first process is confirmed to be a malware process and is terminated.
Owner:FORTINET
Storage-efficient and collision-free hash-based packet processing architecture and method
InactiveUS7653670B2Eliminating false positivesLess storageData processing applicationsDigital data information retrievalComputer architectureHardware complexity
Owner:NEC CORP
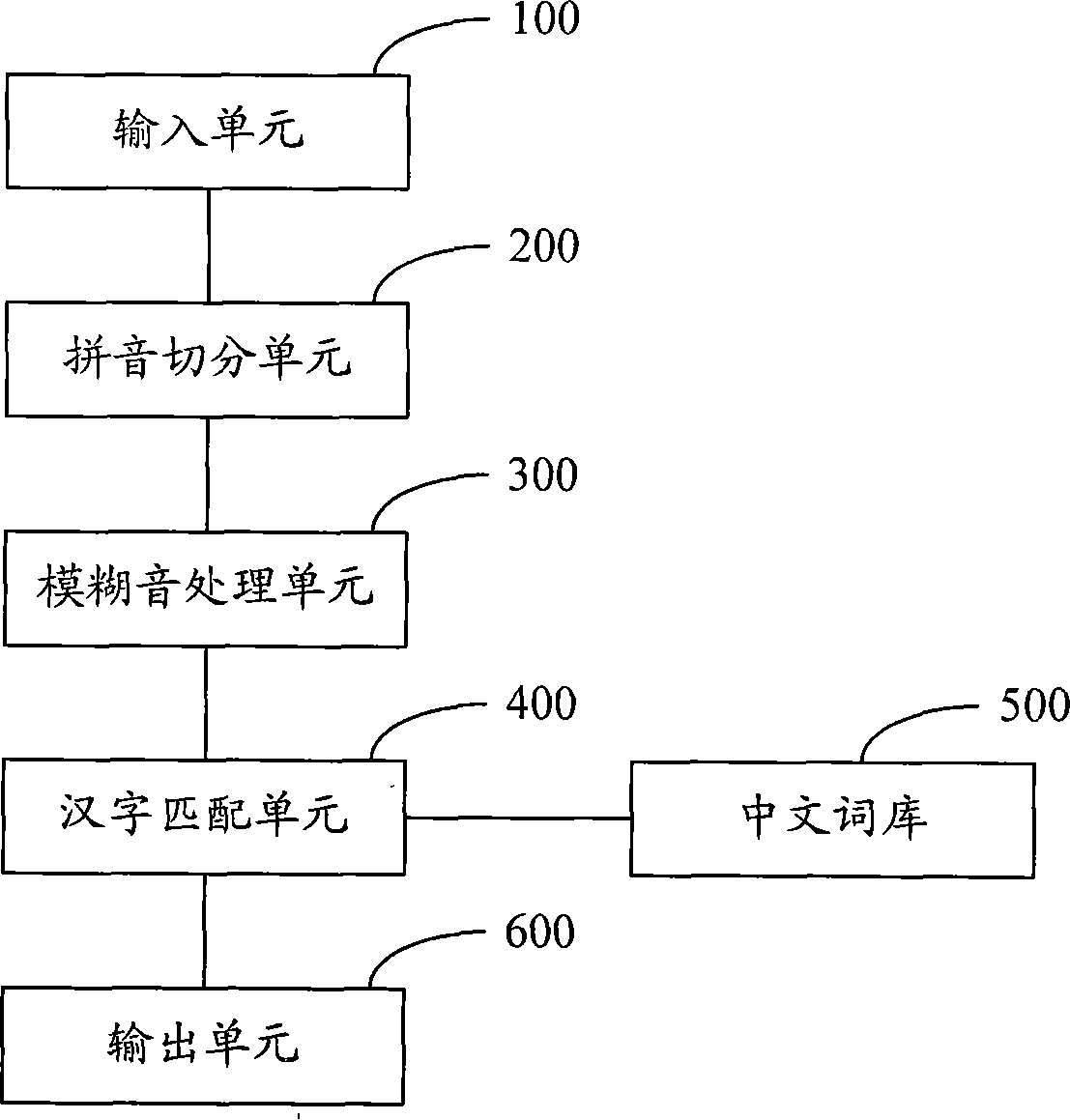
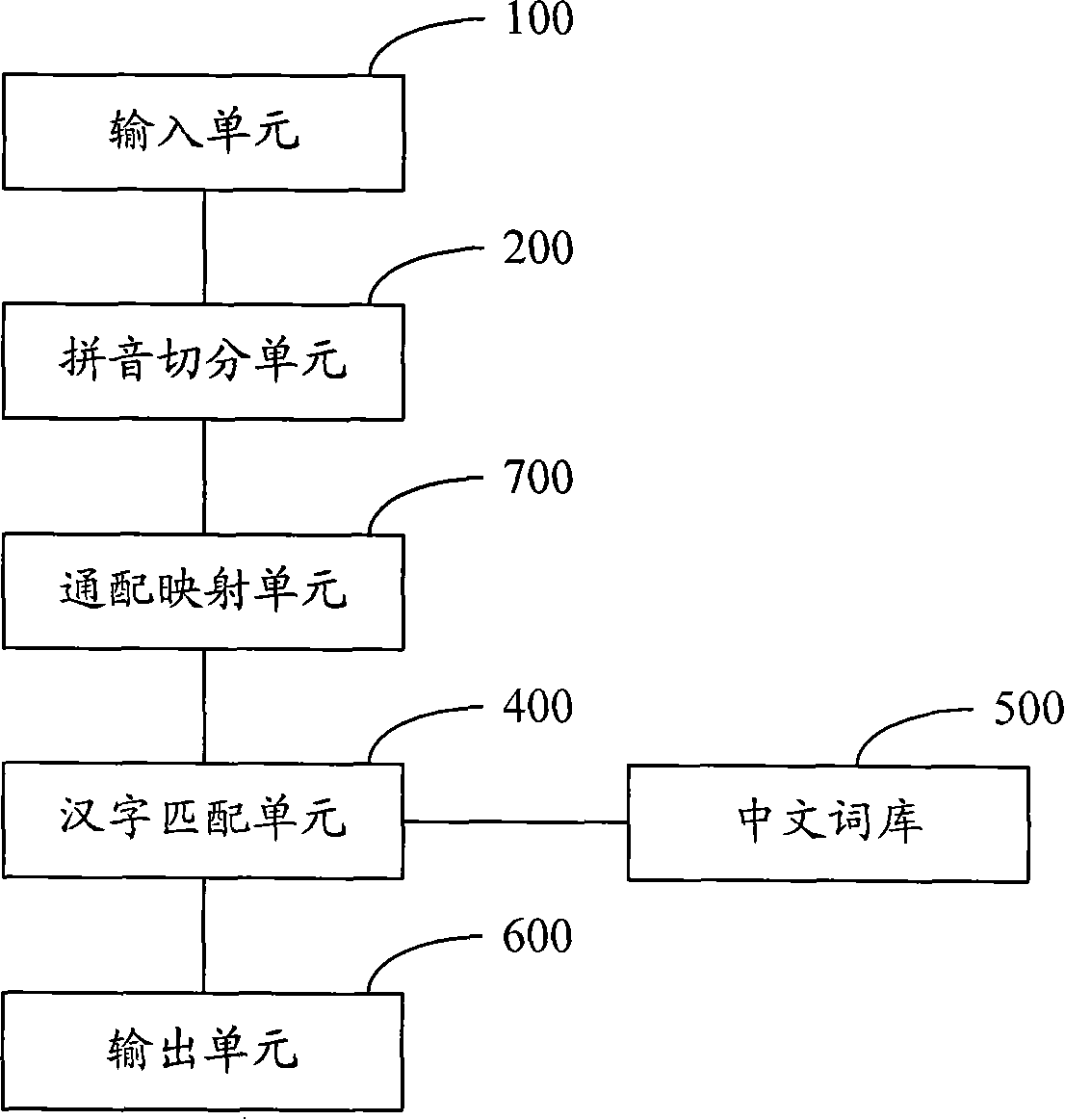
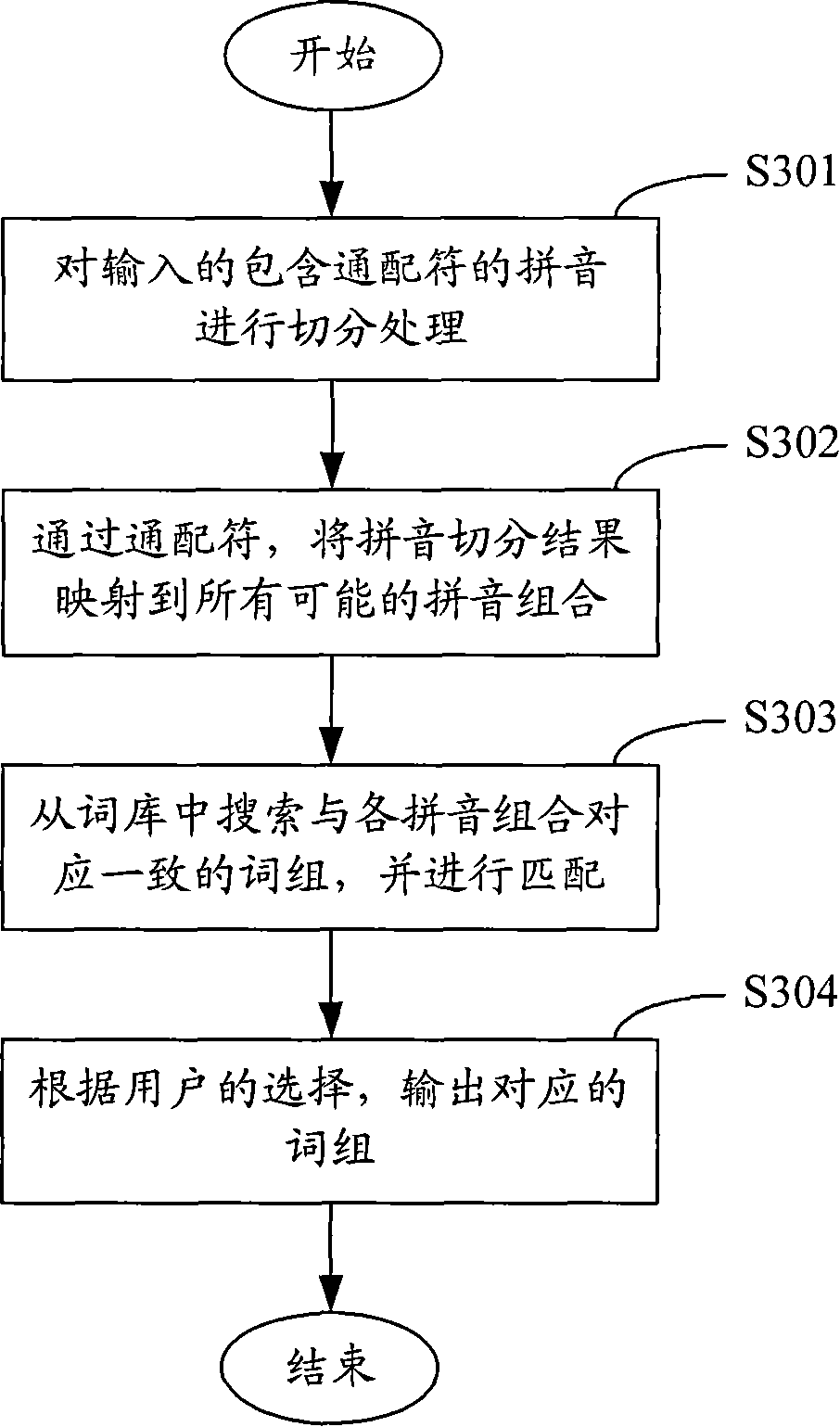
Chinese phonetic input method and system
ActiveCN101192108AImprove intelligenceSpecial data processing applicationsInput/output processes for data processingInformation processingUser input
The invention provides a Pinyin input method and a system thereof which relates to the Chinese information processing filed. The method comprises the following steps that: A. the Pinyin comprising a wildcard to be inputted is syncopated; B. the Pinyin syncopate result is mapped on a corresponding Pinyin combination by the wildcard; C. Chinese phrases corresponding to Pinyin combinations are searched in a Chinese word database and the search results are displayed on a candidate frame; D. Chinese phrases are outputted according to what a user chooses from the search results in the candidate frame. The invention provides choices for a user by mapping the Pinyin syncopate results to all possible Pinyin combinations and searching the Chinese phrases matching the Pinyin combinations in the Chinese word database; therefore, when one or a plurality of Pinyin among the Pinyin inputted by the user is uncertain, the invention can quickly and accurately output the Chinese phrase according to the Pinyin, which improves the intelligence of Pinyin input method.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for efficiently mapping error messages to unique identifiers
InactiveUS20060112127A1Reverse engineeringSpecial data processing applicationsComputer hardwareError reporting
A method and computer product for mapping an error message to an identifier to enable error reporting is provided. An error message hash vector is associated with a resource ID and a resource module. When an error message is displayed, substrings of text in the message are hashed and matched to a corresponding hash vector. The substrings are defined as text that is between the start of the message and wildcard string (a string that is dynamically inserted at runtime), between a wildcard string and the end of the message, or between two wildcard strings. Based on the hash of these substrings, error messages can be quickly and efficiently mapped to a corresponding resource ID and module, which can then be reported.
Owner:MICROSOFT TECH LICENSING LLC
Automatic question-answering method and system
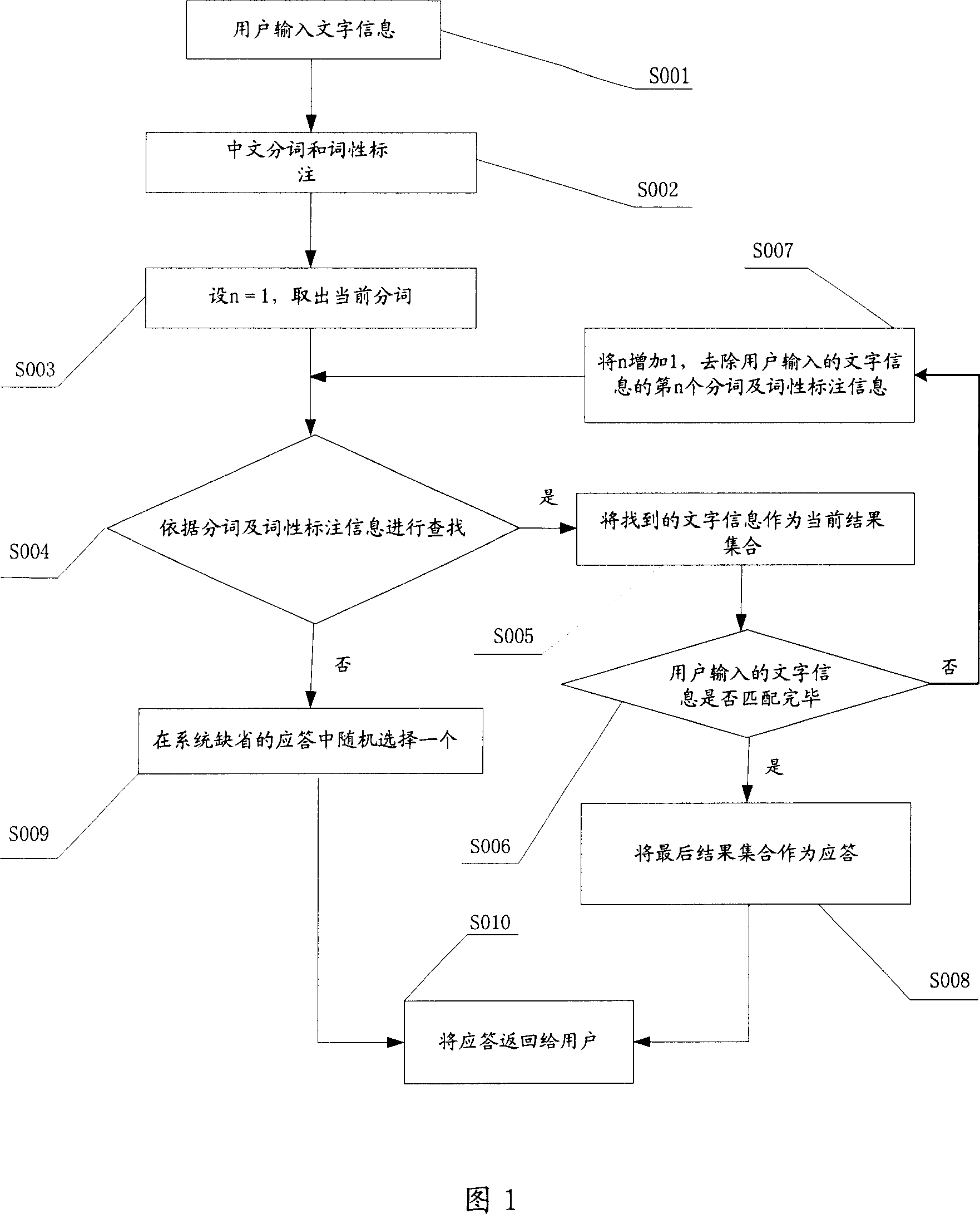
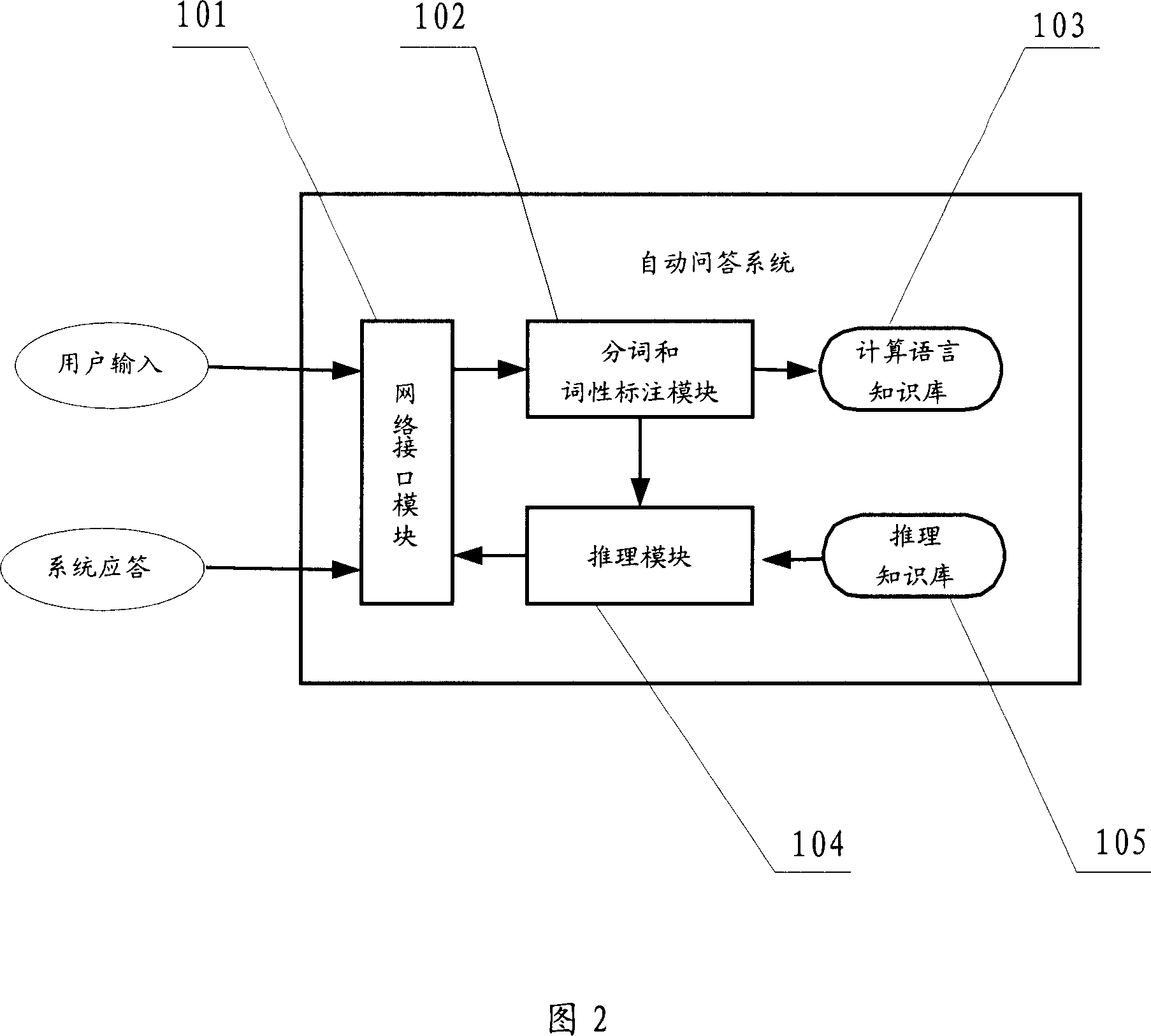
ActiveCN101030267AImprove accuracyIncrease content reachKnowledge representationSpecial data processing applicationsPattern matchingWildcard character
An automatically question-answering method includes dividing inputted writing information, carrying out seeking according to divided result, updating result set by utilizing matched seek-result, judging whether match of inputted writing information is finished or not and selecting the answer according to result set if said match is finished. The system used for realizing said method is also disclosed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
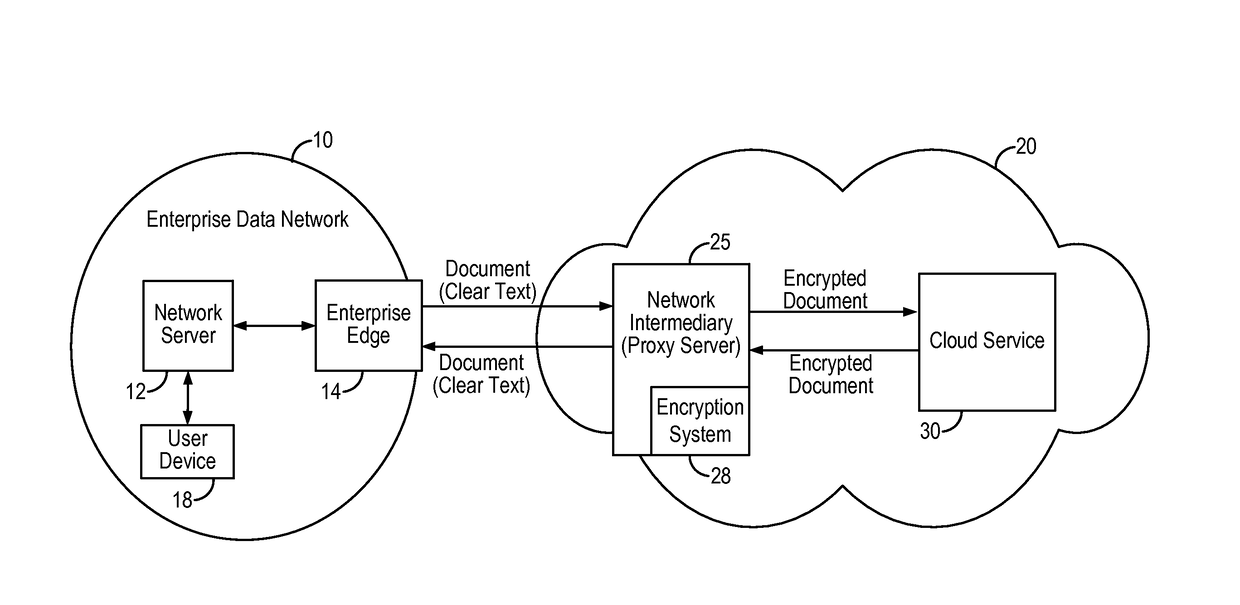
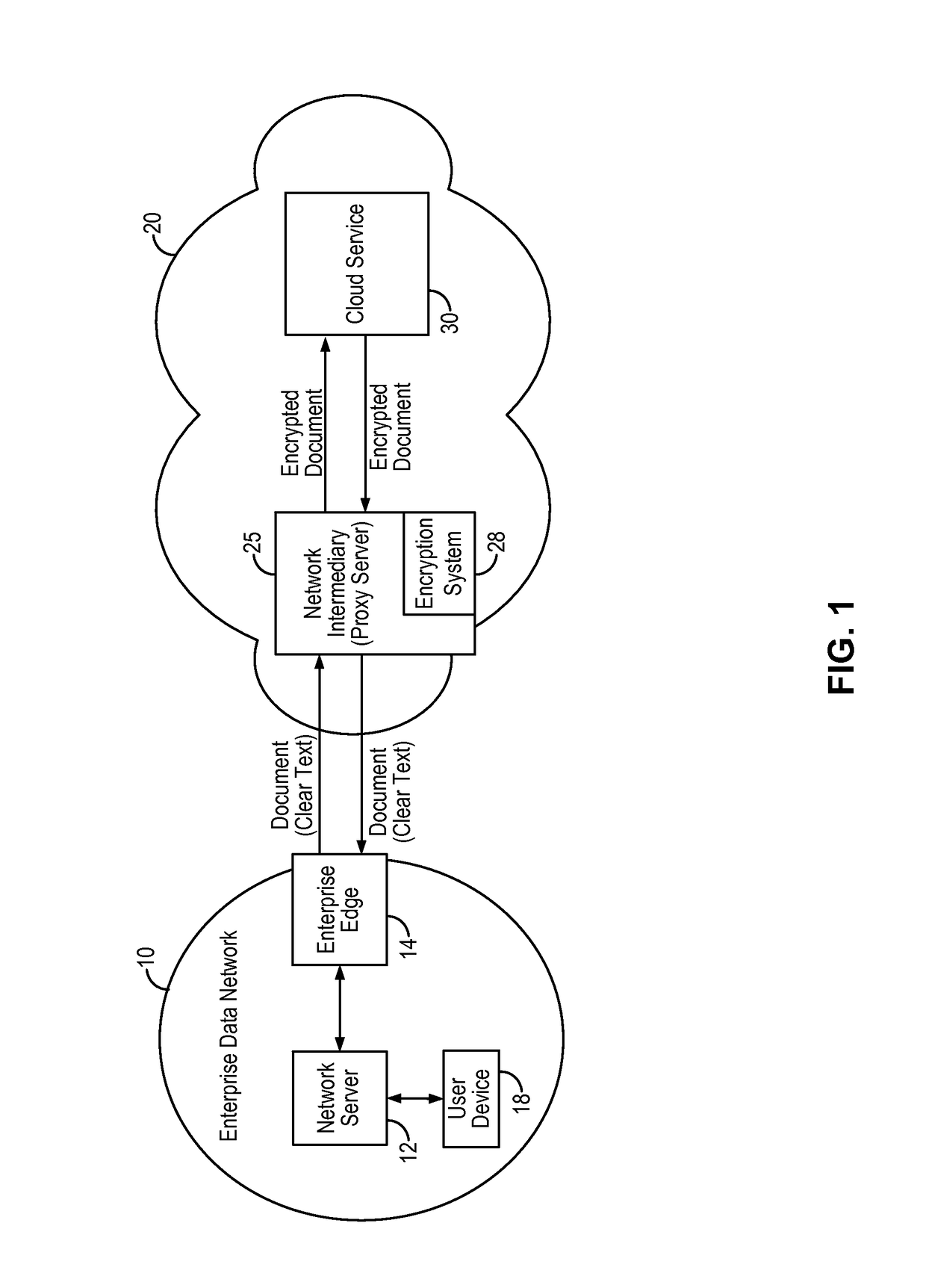
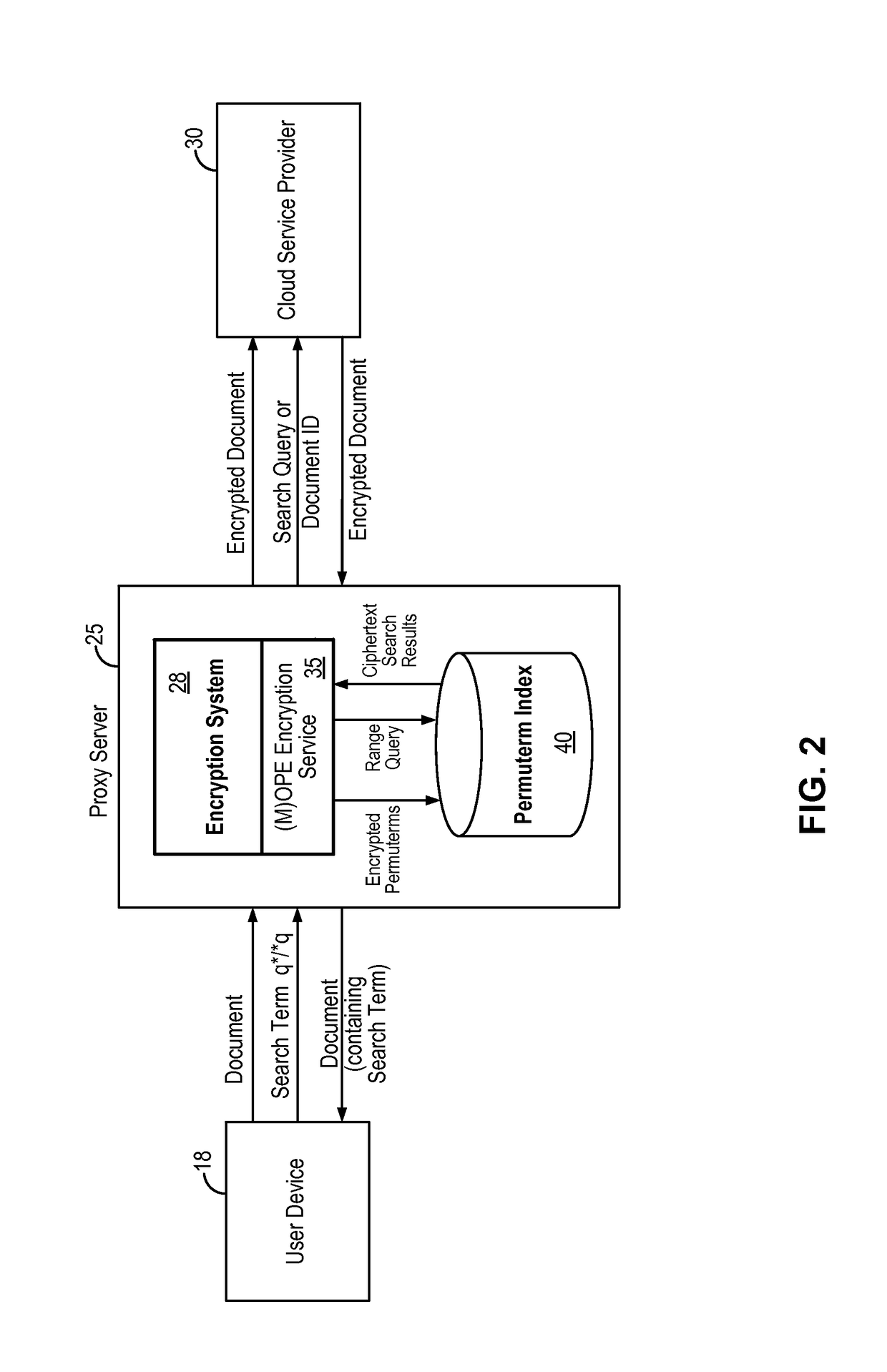
Wildcard search in encrypted text using order preserving encryption
A encrypted text wildcard search method enables wildcard search of encrypted text by using a permuterm index storing permuted keyword strings that are encrypted using an order preserving encryption algorithm. The permuted keyword strings are encrypted using an order preserving encryption algorithm or a modular order preserving encryption algorithm and stored in the permuterm index. In response to a search query containing a wildcard search term, the encrypted text wildcard search method transforms the wildcard search term to a permuted search term having a prefix search format. The permuted search term having the prefix search format is then used to perform a range query of the permuterm index to retrieve permuted keyword strings having ciphertext values that fall within the range query. In some embodiments, the encrypted text wildcard search method enables prefix search, suffix search, inner-wildcard search, substring search and multiple wildcard search of encrypted text.
Owner:SKYHIGH SECURITY LLC
Learning and using generalized string patterns for information extraction
InactiveUS7299228B2Data processing applicationsUnstructured textual data retrievalPattern matchingAlgorithm
Owner:SERVICENOW INC
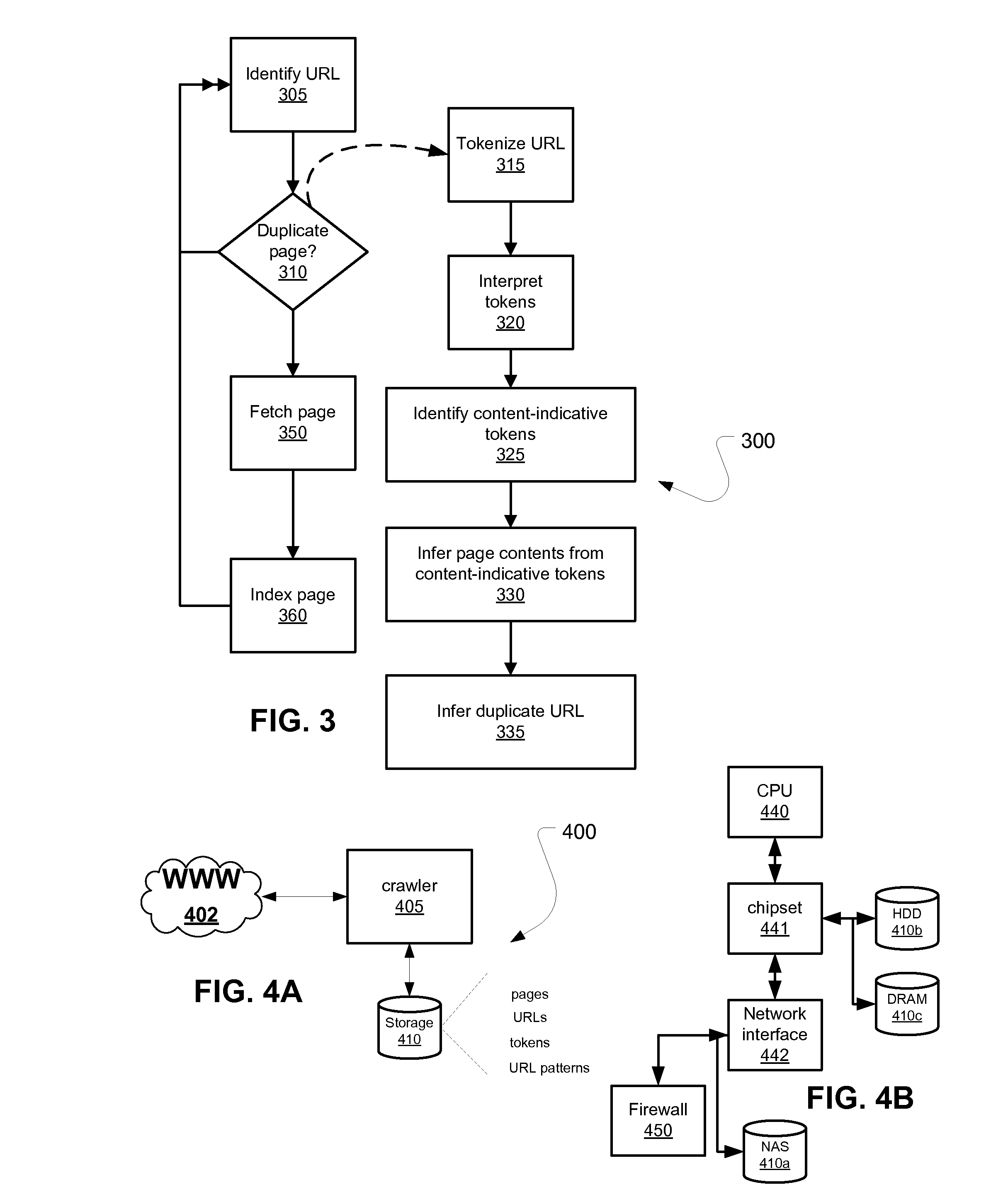
Systems and methods for tokenizing and interpreting uniform resource locators
ActiveUS20090327304A1Digital data processing detailsSpecial data processing applicationsHeuristicTheoretical computer science
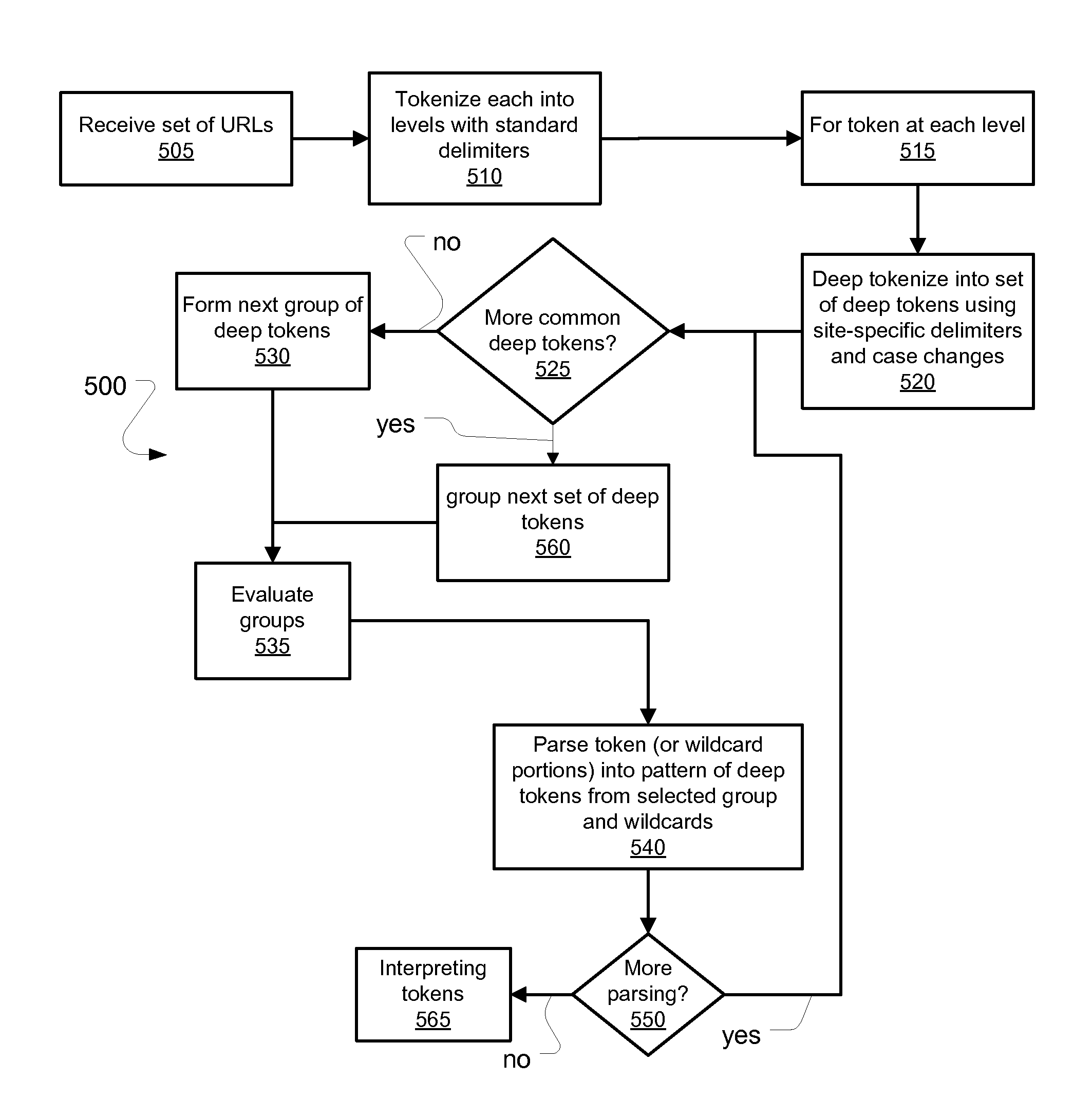
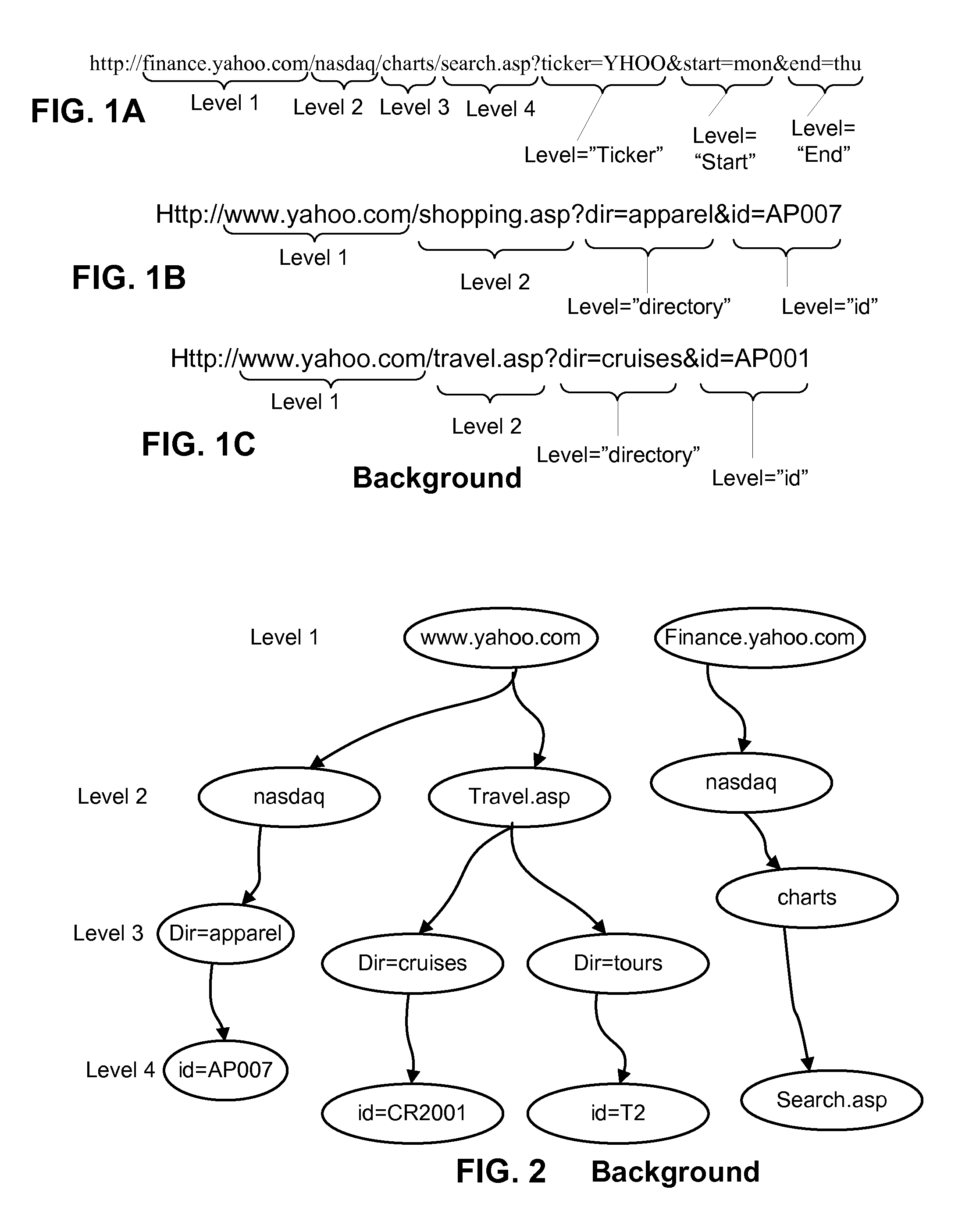
Aspects include methods, computer readable storing instructions for such methods, and systems for processing text strings such as URLs that comprise patterns of parameters and values for such parameters, delimited in a site-specific manner. Such aspects provide for accepting a number of text strings that are expected to have a common delimiting strategy, then deeply tokenizing those text strings to arrive at a set of tokens from which are selected anchor tokens used to form patterns having the anchor tokens separated by wildcard portions for recursive processing. The patterns formed can be mapped to a tree of nodes. Information concerning relationships between nodes and between tokens within a given node, as well as other heuristics concerning which tokens are parameters and which are values can be used as observed events for producing probabilities that certain tokens are parameters or values, using a dynamic programming algorithm, such as a Viterbi algorithm.
Owner:R2 SOLUTIONS
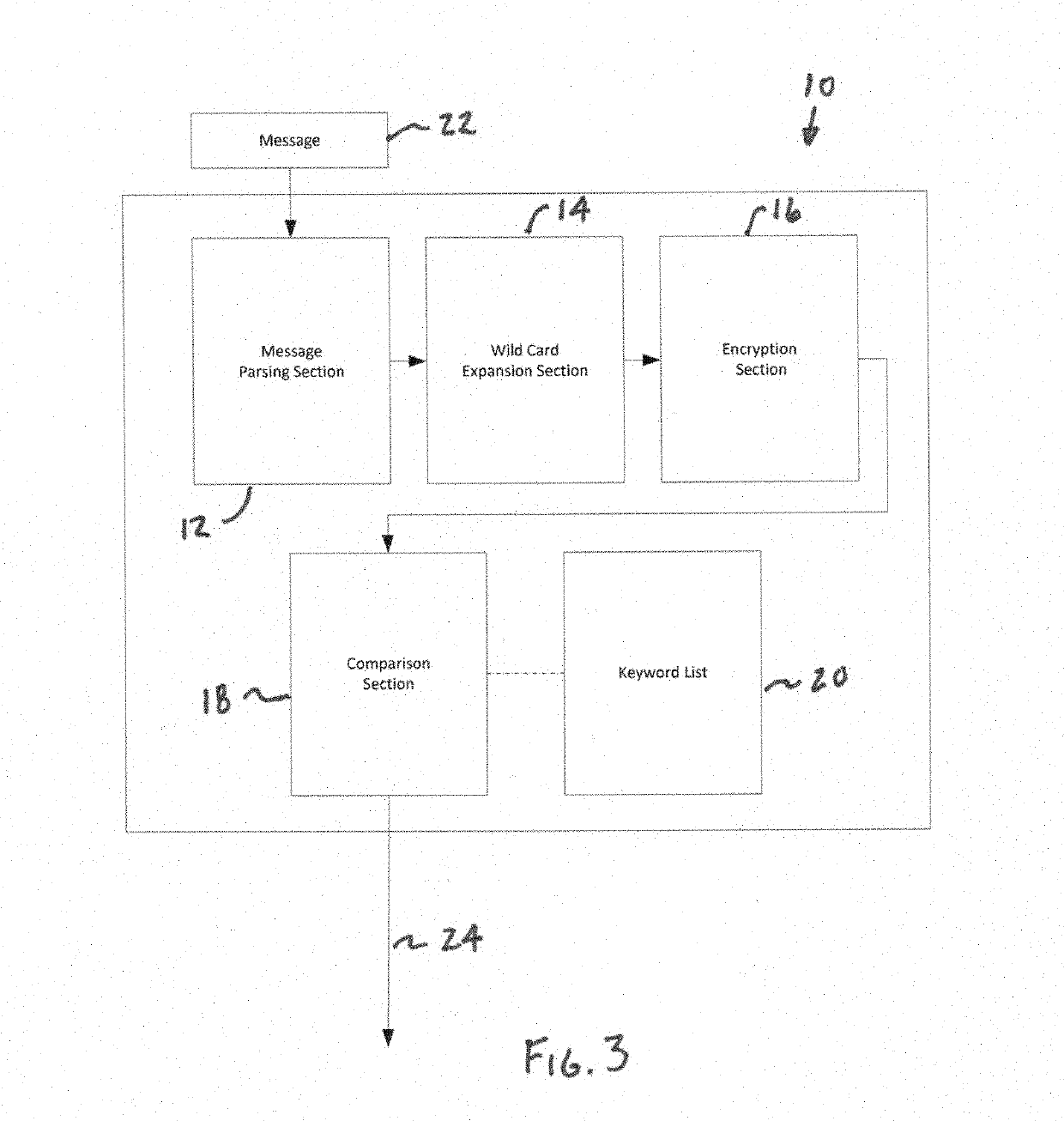
Computer system data guard
InactiveUS20190121998A1Easy to implementReduce resource consumptionDigital data protectionComputer hardwareComputerized system
An advanced data guard with an encrypted keyword list that allows wild card constructions in the encrypted keyword list without the need to perform any decryption of the keyword list. The data guard may include a message parsing section that extracts individual words from a message, a wild card expansion section that expands each extracted message word into an expanded list of all possible wild card constructions, an encryption section that encrypts the individual message words in the expanded list to produce an encrypted list and a comparison section that compares each word in the encrypted message list against each encrypted word in the encrypted keyword list. The result of the comparison section may be presented to a rules engine to determine the appropriate action, which may include, for example, prohibiting or permitting transmission of the message, sending an alarm and / or logging the event.
Owner:DORNERWORKS
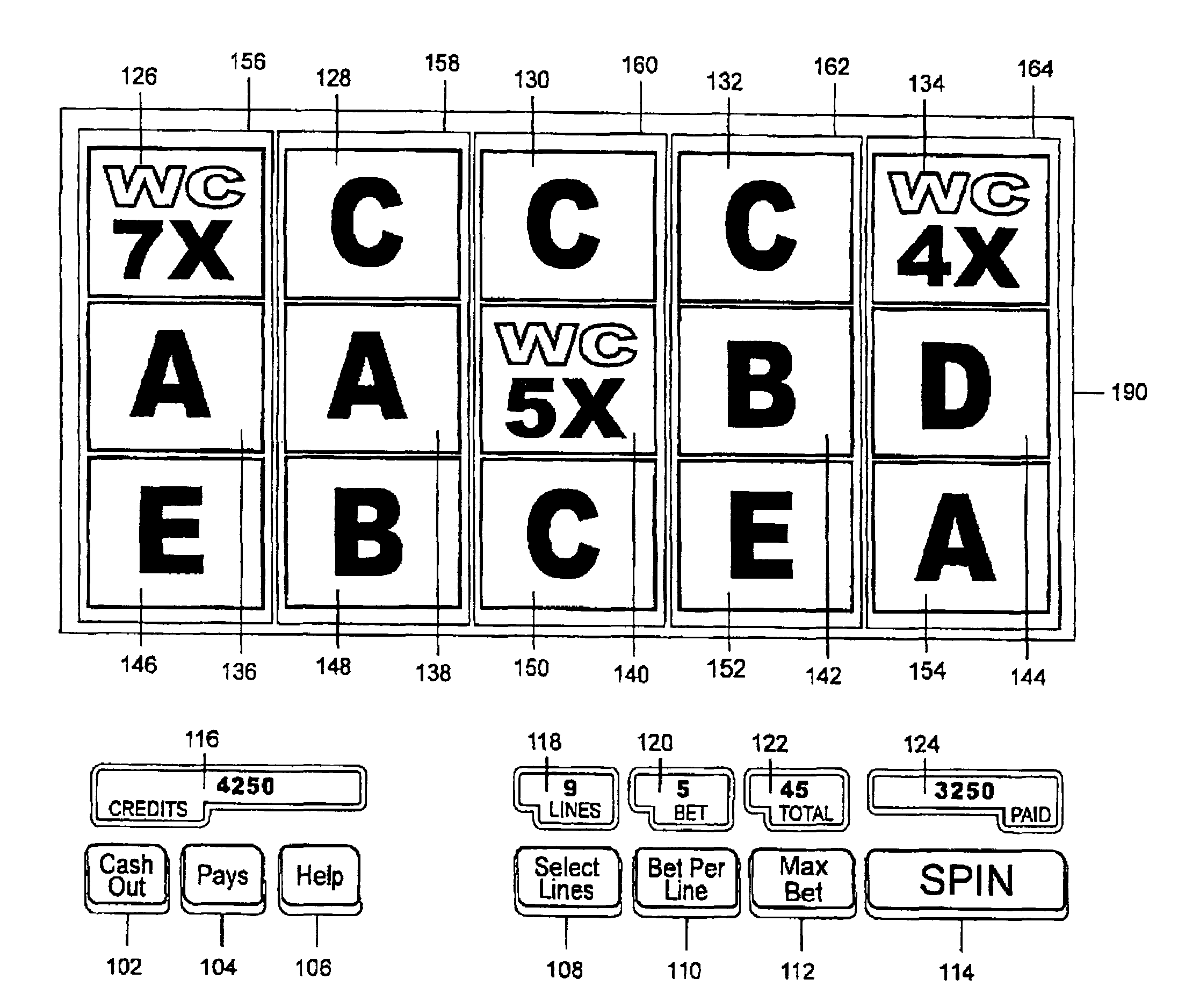
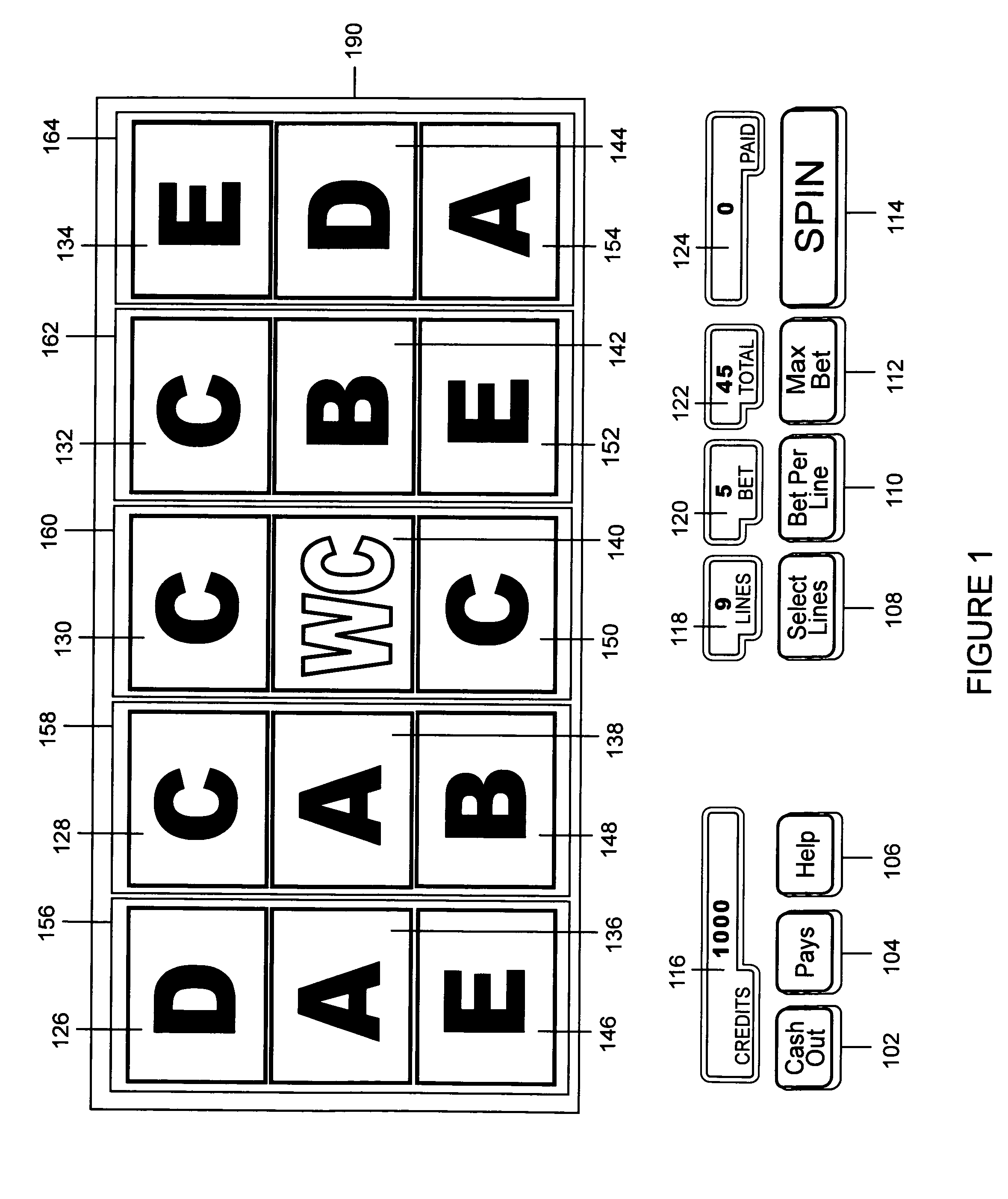
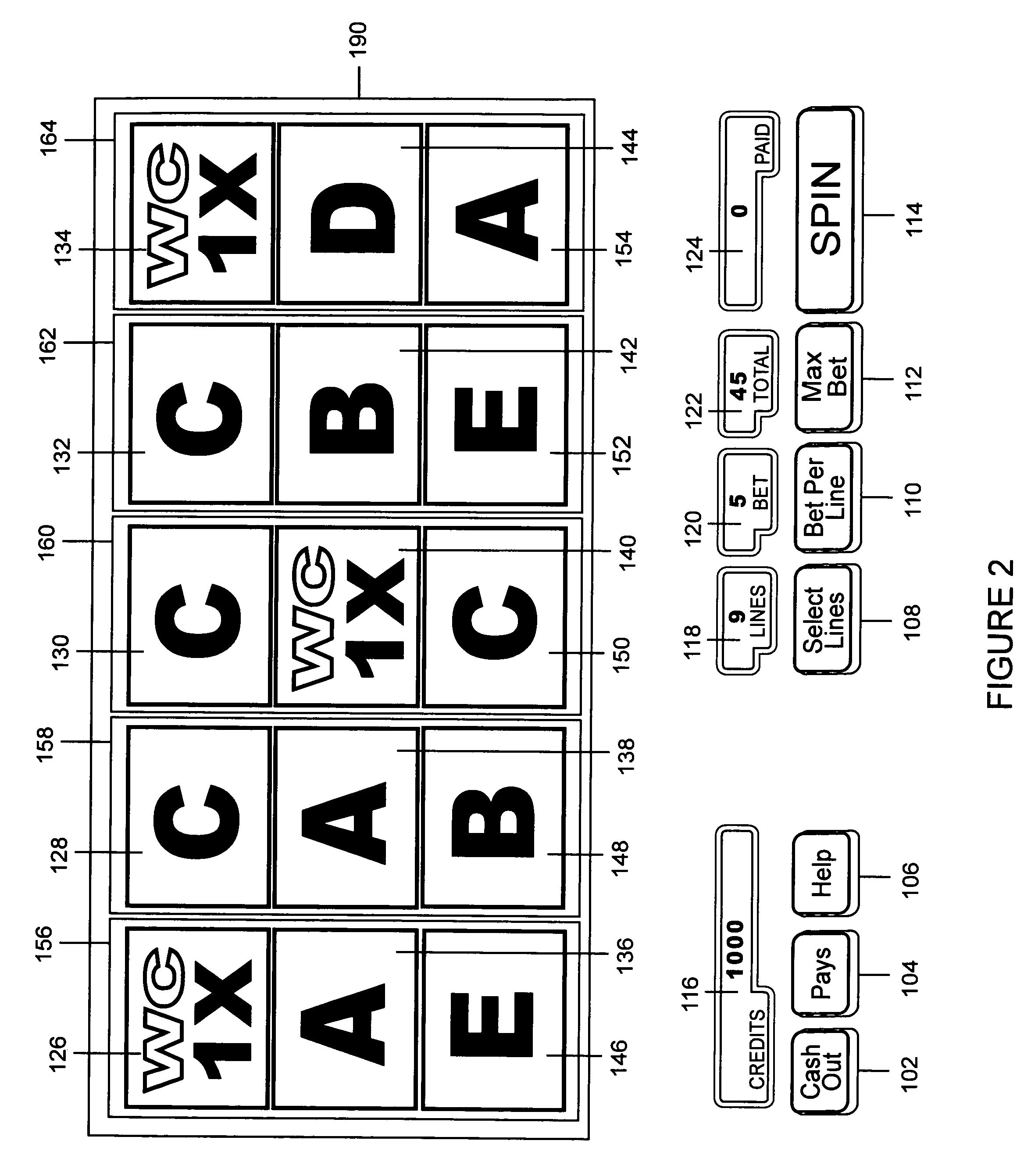
Method of playing a slot machine game with using wildcard symbols with randomly displayed multiplier values
ActiveUS7530894B1Card gamesApparatus for meter-controlled dispensingWildcard characterArtificial intelligence
Owner:PTT
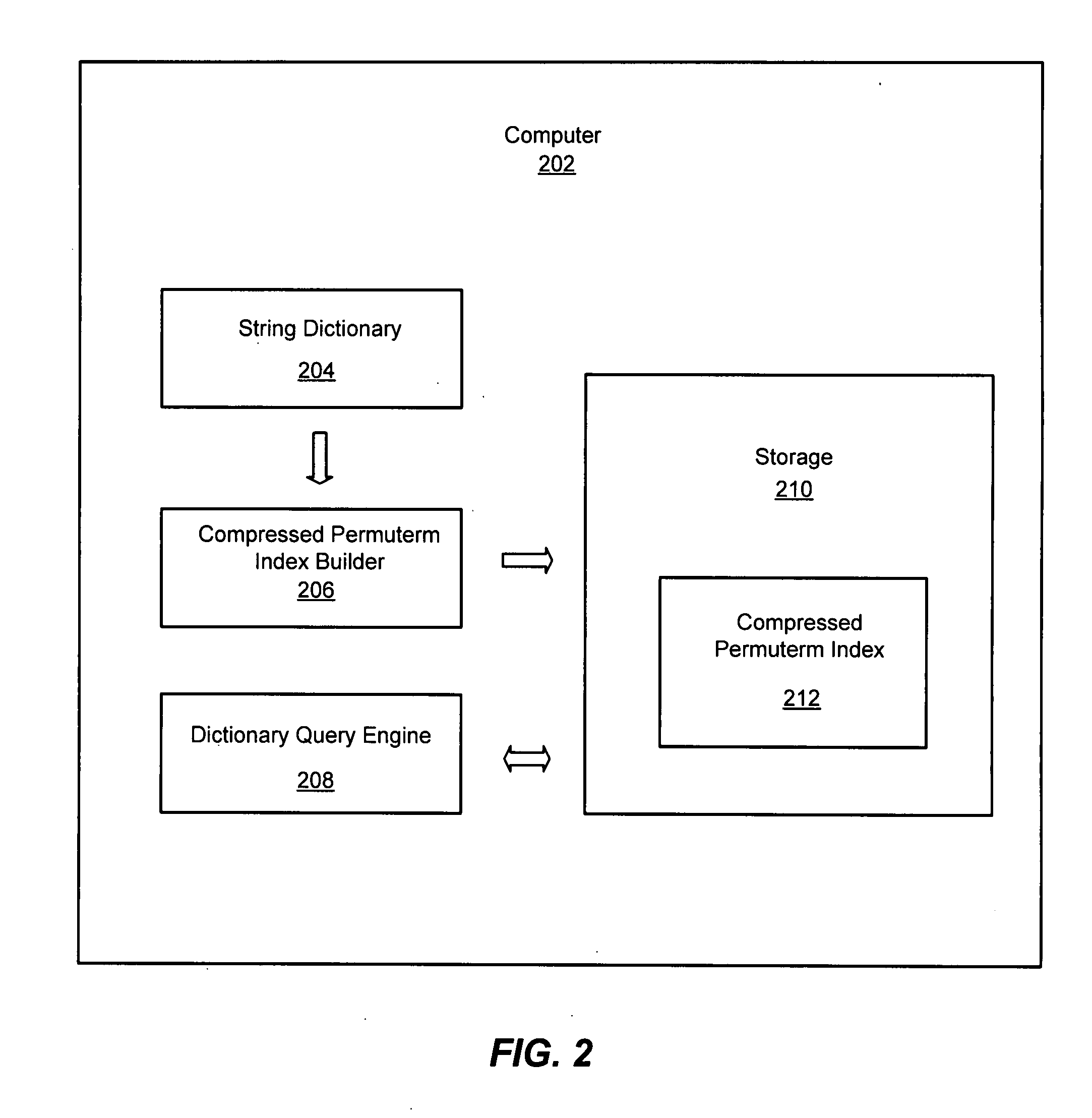
System and method for string processing and searching using a compressed permuterm index
InactiveUS20090063465A1Loss in space efficiencyLoss in time efficiencyDigital data information retrievalSpecial data processing applicationsWildcard characterString processing
An improved system and method for string processing and searching using a compressed permuterm index is provided. To build a compressed permuterm index for a string dictionary, an index builder constructs a unique string from a collection of strings of a dictionary sorted in lexicographic order and then builds a compressed permuterm index to support queries over the unique string. A dictionary query engine supports several types of wild-card queries over the string dictionary by performing a backward search modified with a CyclicLF operation over the compressed permuterm index. These queries may used to implement other queries including a membership query, a prefix query, a suffix query, a prefix-suffix query, a query for an exact or substring match, a rank query, a select query and so forth. String processing and searching tasks may accurately be performed for sophisticated queries in optimal time and compressed space.
Owner:OATH INC
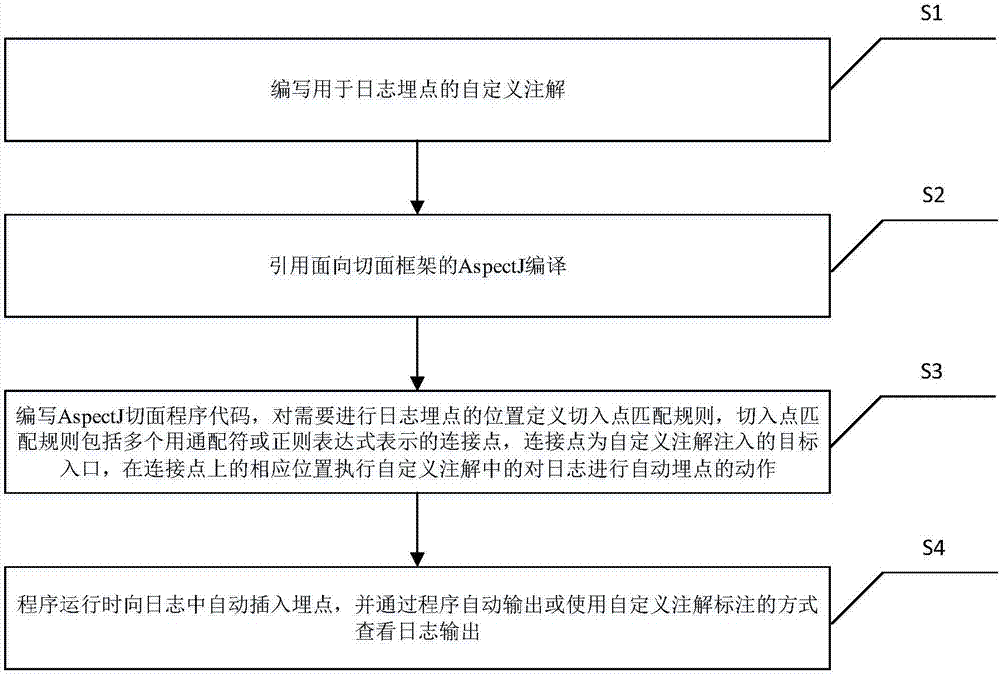
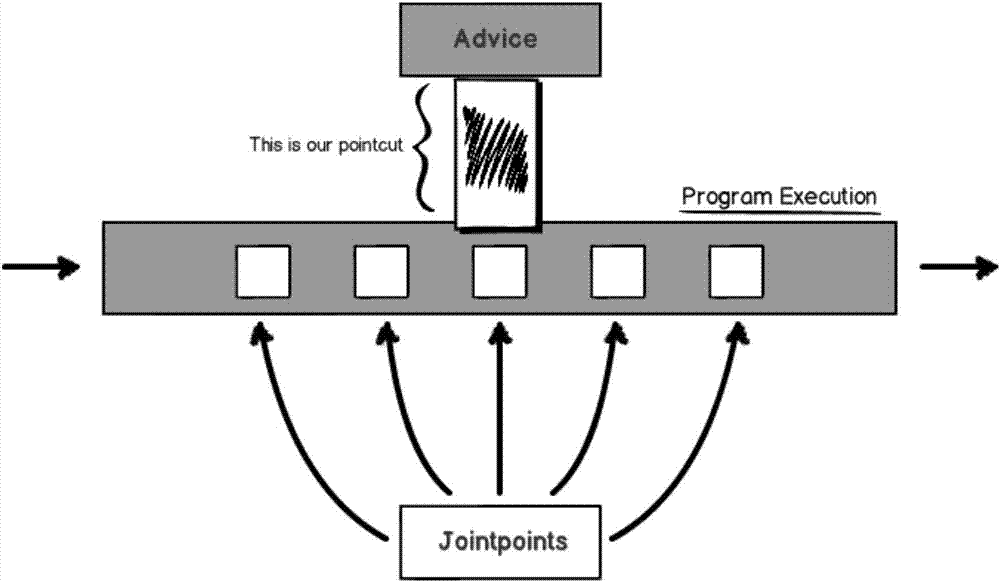
Automatic log point burying method and system based on AOP and AspectJ for Android terminal
ActiveCN106970789AEasy to readEasy to analyzeSoftware engineeringSpecific program execution arrangementsEntry pointAspectJ
The invention discloses an automatic log point burying method and system based on AOP and AspectJ for an Android terminal. The method comprises the steps that self-defined annotations for log point burying are written; an AspectJ compiling mode of an aspect-oriented framework is introduced; an AspectJ aspect program code is written, and entry point matching rules are defined for positions where log point burying needs to be performed, wherein the entry point matching rules include multiple connection points expressed with wildcard characters or regular expressions, the connection points are target entrances injected by the self-defined annotations, and an automatic point burying action is performed on logs in the self-defined annotations at the corresponding positions of the connection points; and during running of a program, buried points are automatically interposed into the logs, and the logs are automatically output through the program or log output is viewed by use of the self-defined annotations. Through the method, automatic log point burying is realized, styles of the logs are unified, the development quantity is increased by use of the annotation mode, the code development quantity can be effectively reduced, code decoupling is realized, and development efficiency is improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
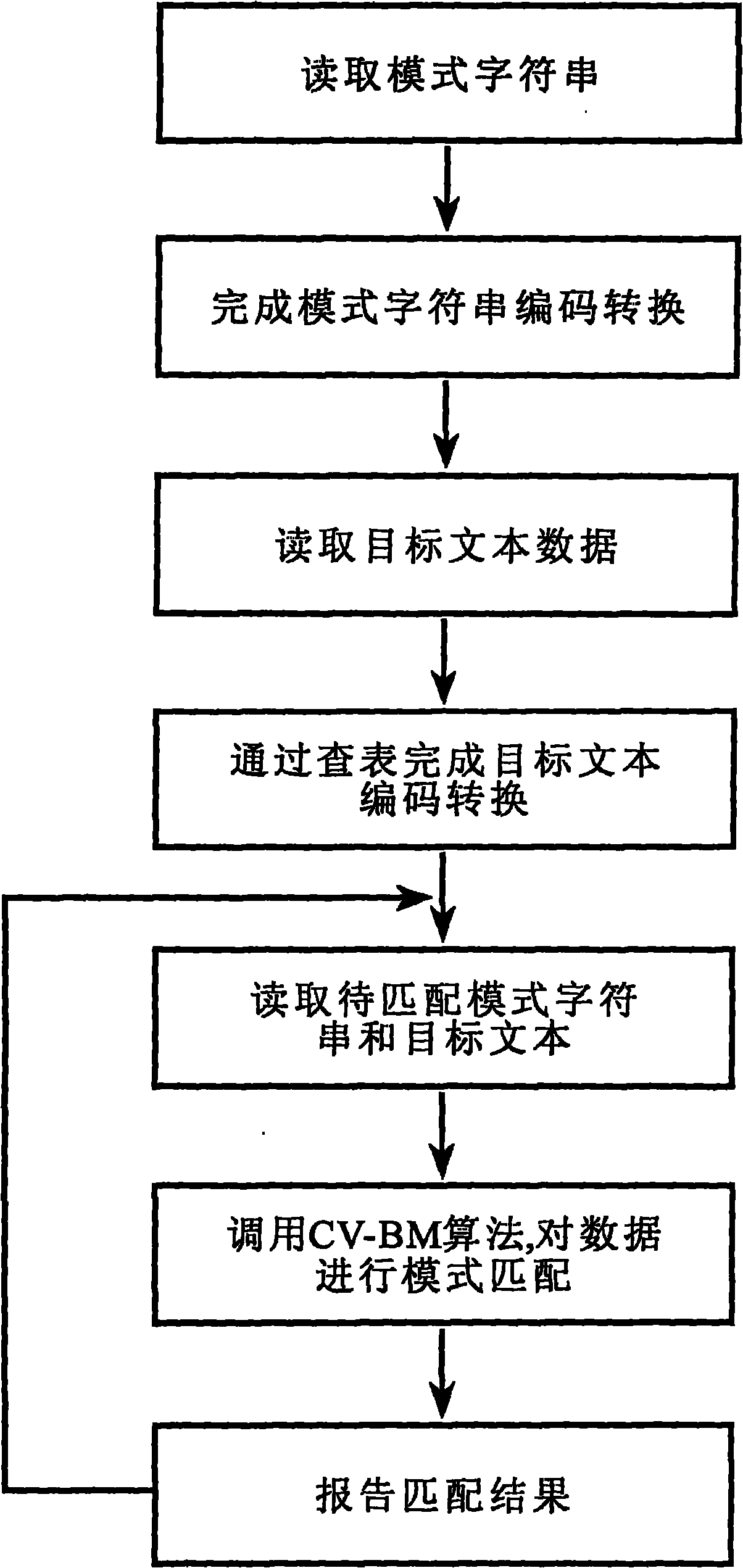
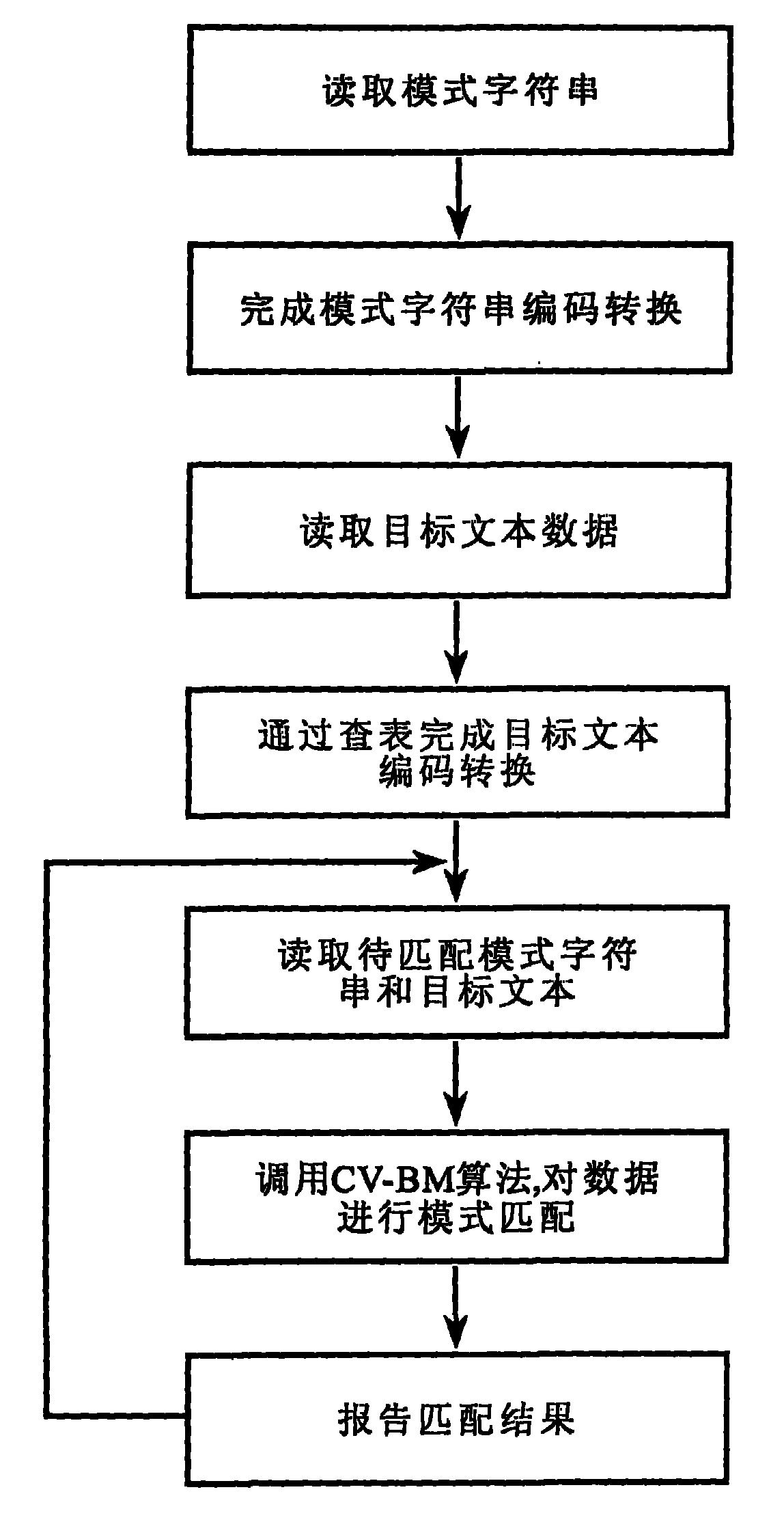
Chinese variation text matching recognition method
ActiveCN101976253AResolve hard-to-match situationsQuick matchSpecial data processing applicationsChinese charactersTheoretical computer science
The invention relates to a Chinese variation text matching recognition method. The method comprises the following steps of: performing special encoding conversion on a target text and a mode character string to improve the similarity of texts; adding proper wildcard characters into the converted mode character string according to the structural characteristics of Chinese characters in the mode character string; and matching by using a precise character string matching algorithm (namely a CV-BM algorithm). The method solves the problems of the replacement of characters with similar shapes in the variation text and the matching difficulty based on the replacement of wrongly written characters with similar shapes. The problems of the replacement of the characters with the similar shapes in the variation text and the matching difficulty based on the replacement of wrongly written characters with the similar shapes can be solved. Compared with an image partitioning recognition method, the method has smaller time and space complexities, is more suitable for the quick matching of Chinese character information in a high-speed network data transmission environment, and can be widely applied to systems needing to match the Chinese character information, such as an intrusion prevention system, an information retrieval system and the like.
Owner:重庆智载科技有限公司
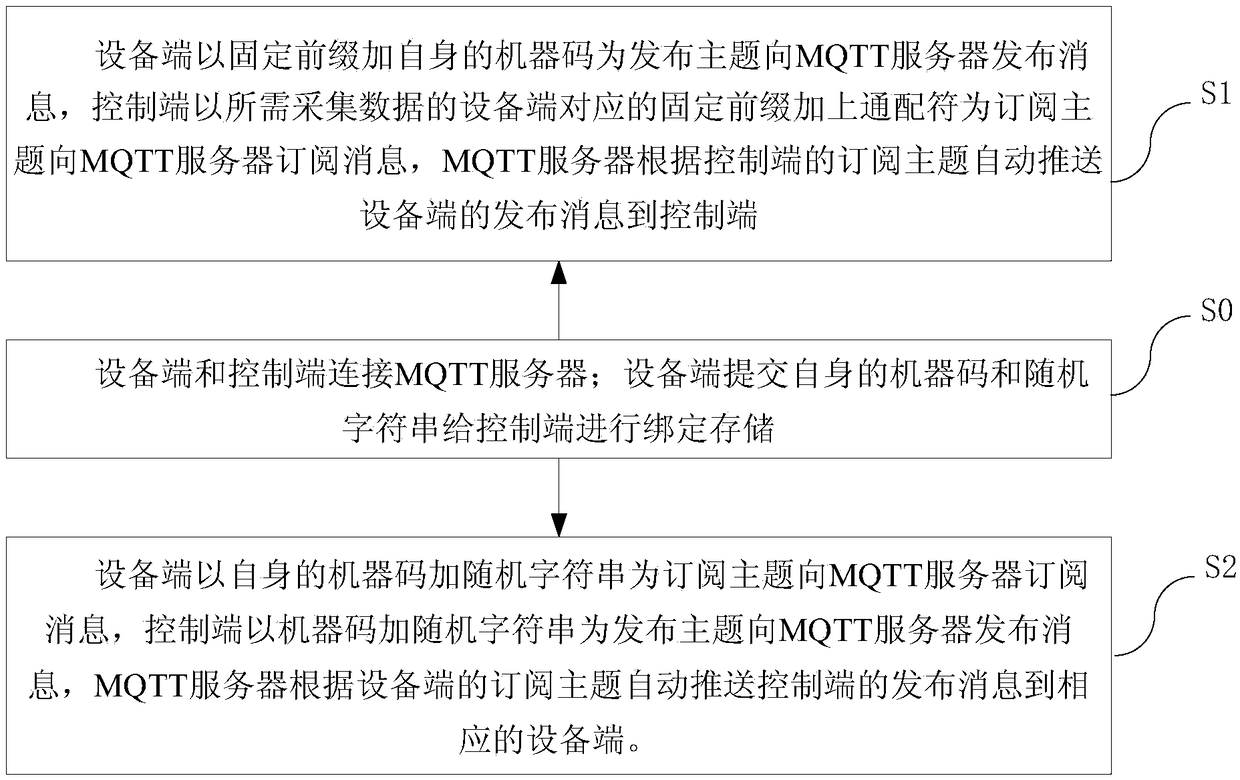
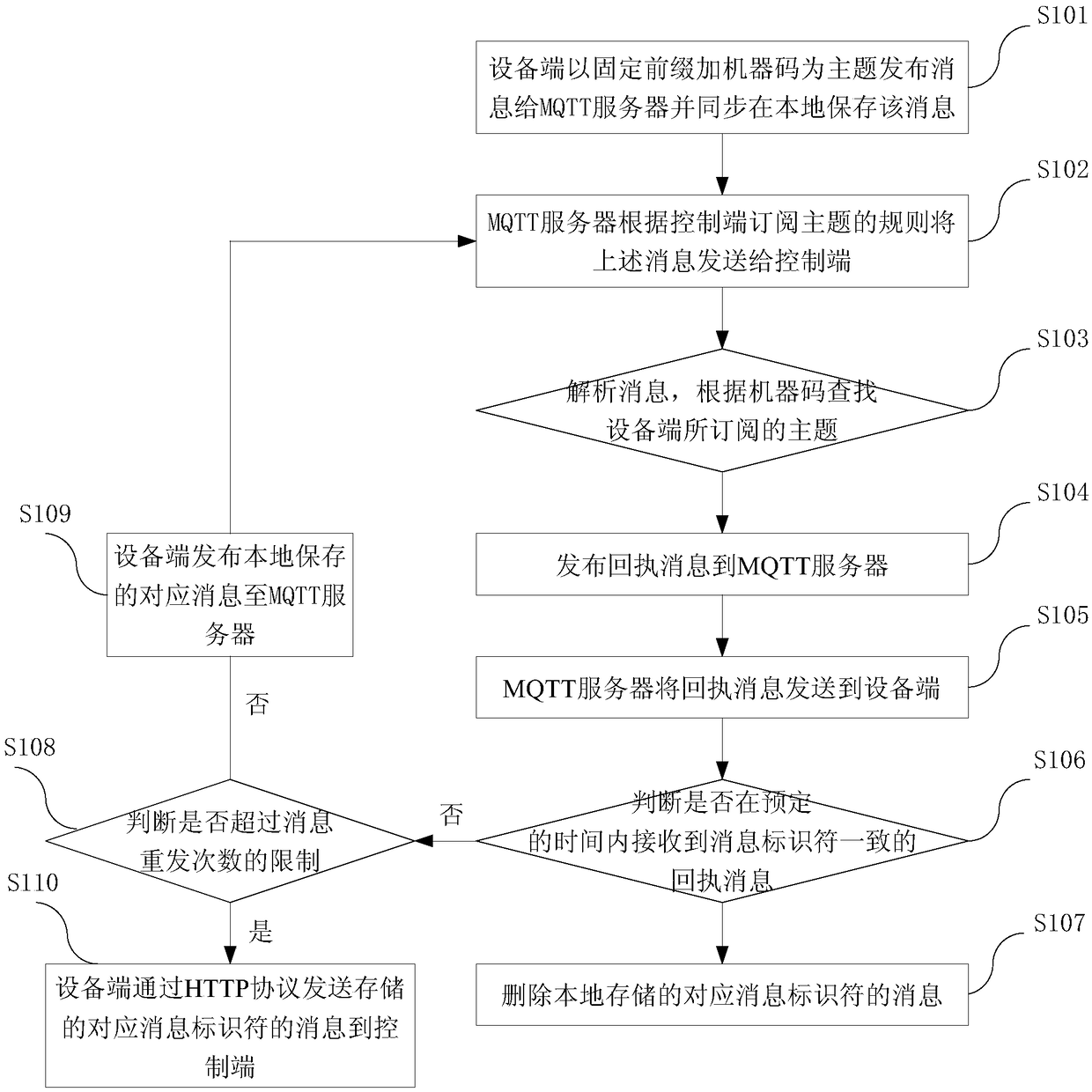
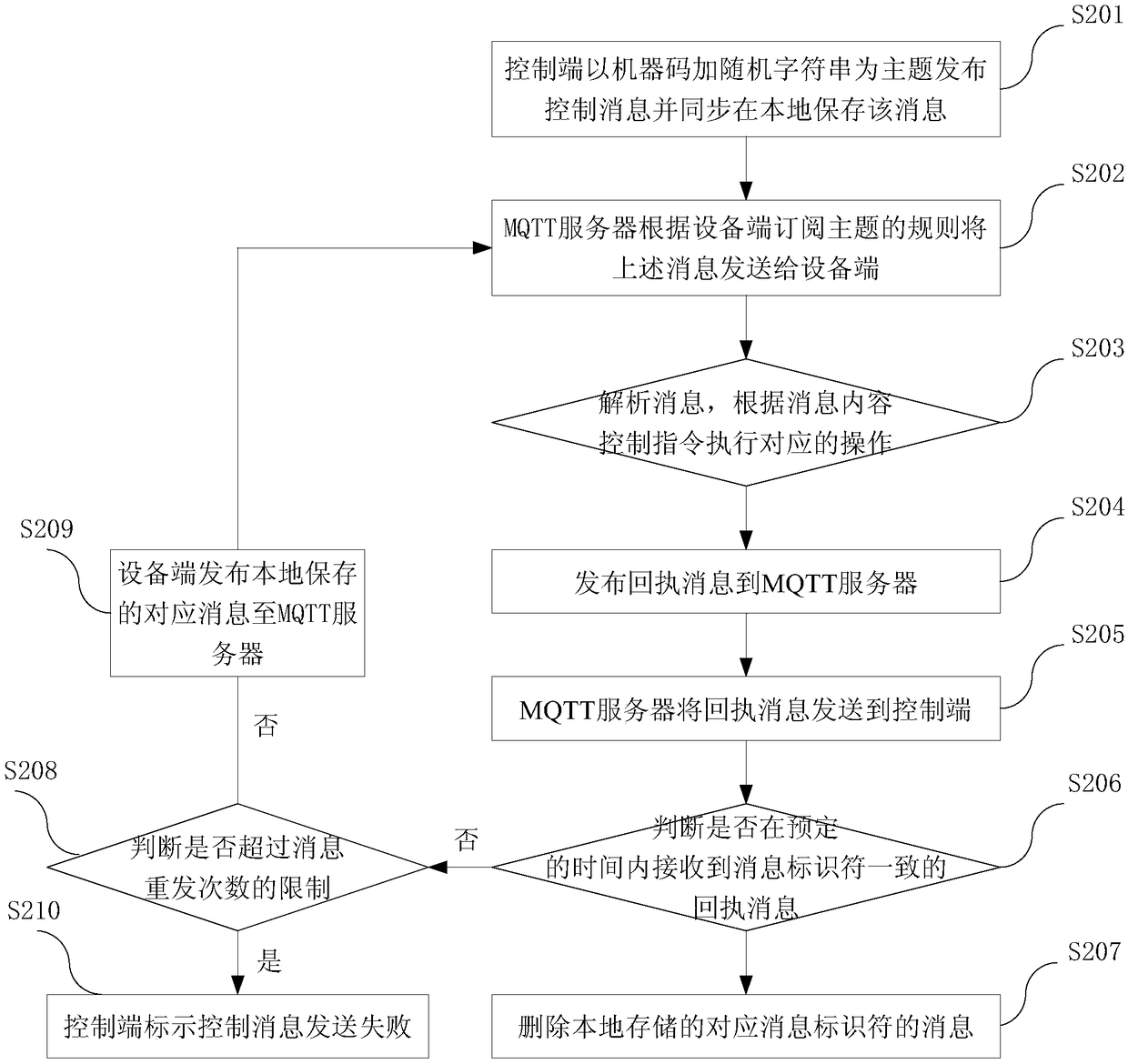
Data collection and remote control method and system
InactiveCN108965447AFully automatic sendingAutomatic receivingNatural language data processingTransmissionRemote controlData acquisition
The invention relates to the field of network communication, and provides a data collection and remote control method aiming at the problem that during existing data collection and remote control, release and subscription of a subject need predetermined parameters. The method comprises the steps as follows: an equipment end and a control end are connected with an MQTT server; the equipment end submits an own machine code and a random character string to the control end to perform binding storage; the equipment end releases a message to the MQTT server by using a fixed prefix and the own machine code as a release subject, and the control end subscribes to the message from the MQTT server by using the fixed prefix and a wildcard character as a subscription subject; and the equipment subscribes to the message from the MQTT server by using the own machine code and the random character string as the subscription subject, the control end releases the message to the MQTT server by using the subscription subject of the equipment as a release subject, and the MQTT server automatically pushes the message according to the subscription subject and the release subject. The method and the systemprovided by the invention are applicable to data collection and remote control of the intelligent equipment.
Owner:四川爱创科技有限公司
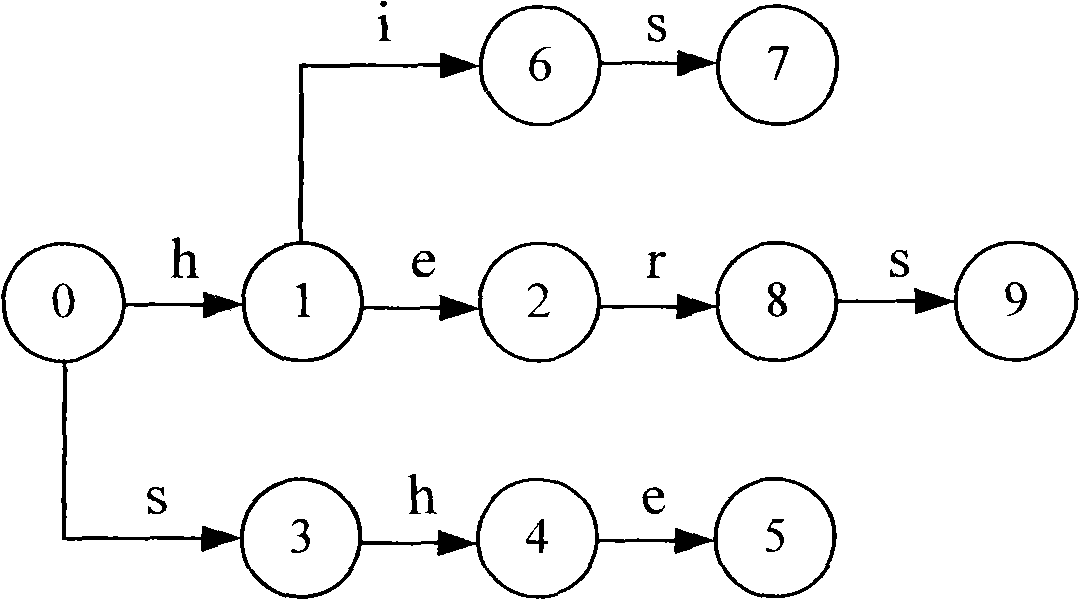
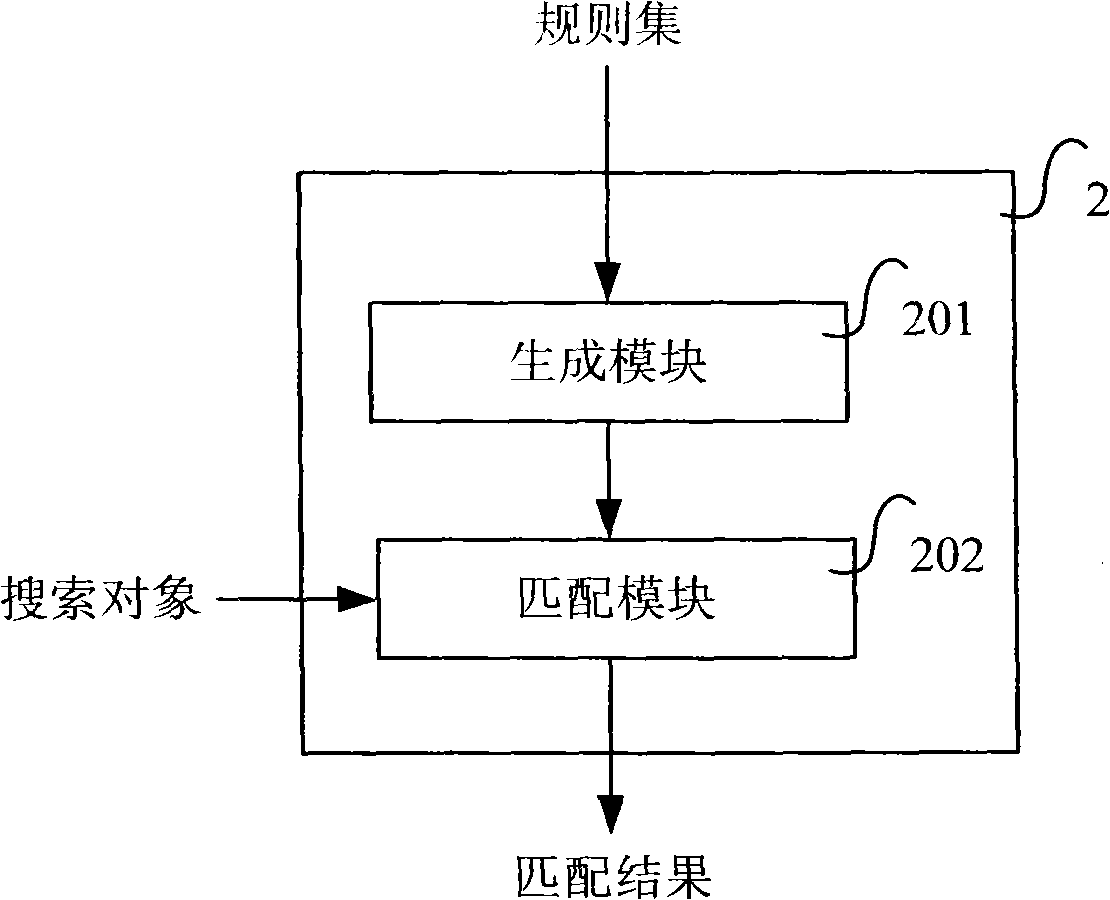
Parallel multi-mode matching method and system therefor
InactiveCN101286988AOvercome the inability to handle matching of non-deterministic rules containing wildcardsImprove efficiencySpecial data processing applicationsSecuring communicationAlgorithmMatch rule
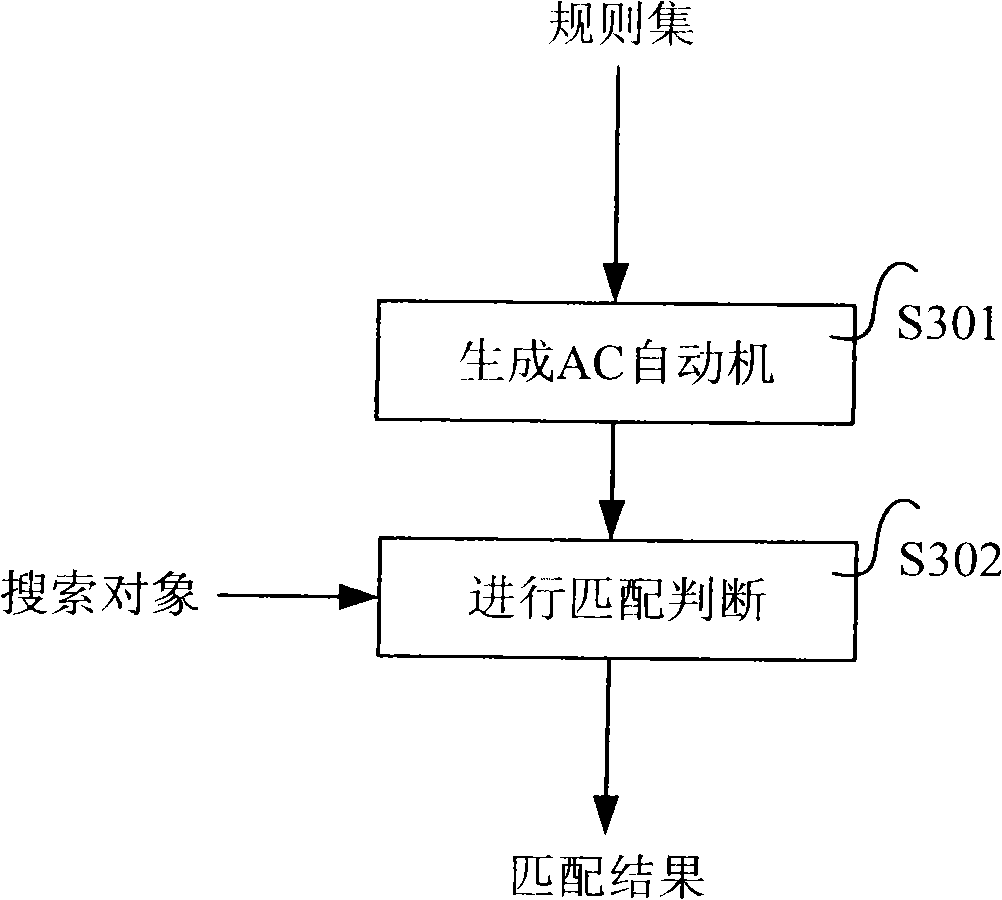
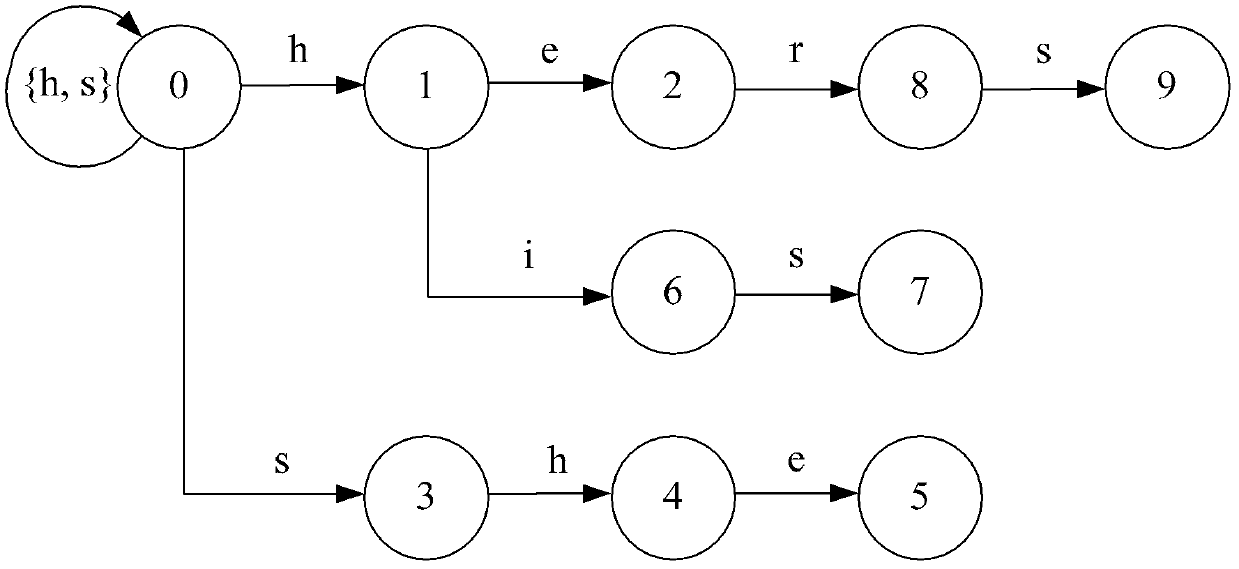
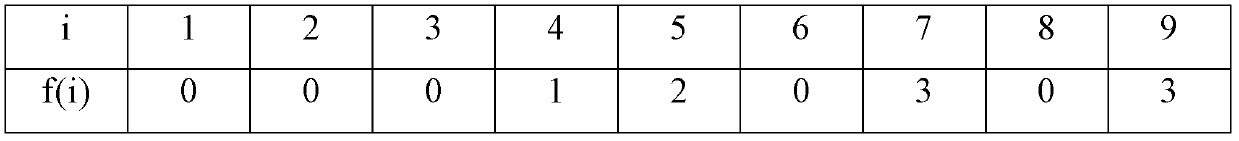
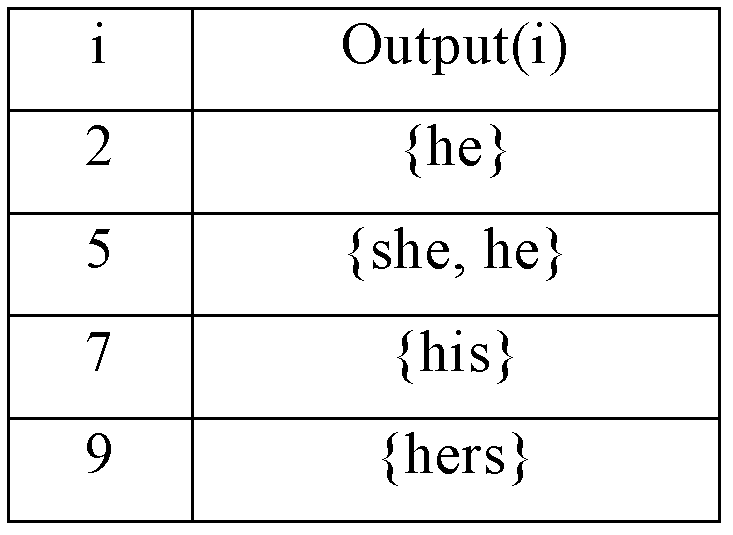
The invention relates to a parallel multi-mode matching method and a system. The system comprises a generation module and a matching module, wherein, the generation module is used for reading a rule set including matching rules; matching rules comprising asterisk wildcards in the rule set are divided into sub rules of the matching rules from the asterisk wildcards; the sub rules exclude the asterisk wildcards; matching rules excluding asterisk wildcards in the rule set are the sub rules of the matching rules; all sub rules are generated into an AC automaton according to AC algorithms and output from the AC automaton; the matching module is used for reading a search object and the AC automaton which is applied to searching according to the AC algorithms; whether the search object matches all sub rules of the matching rules according to the sequence of the sub rules in the matching rules is judged; if so, the search object matches the matching rules, and matching results are output, thereby not only retaining the high efficiency of the AC algorithms, but also matching indefinite rules comprising the asterisk wildcards.
Owner:BEIJING VENUS INFORMATION TECH
Method and device for constructing AC (aho-corasick) state machine
The invention provides a method and a device for constructing an AC (aho-corasick) state machine. The method comprises the following steps of: setting each wildcard character in each search mode as a specific character; constructing a keyword tree according to each search model; copying a goto function table of wildcard character nodes to brother state nodes, and recording input characters (transferred to the brother state nodes) as to-be-excluded characters; when a recognizing that an uncertain goto function exists, processing the uncertain goto function so as to exclude the uncertain goto function until no uncertain goto function is recognized; and excluding all to-be-excluded characters corresponding to the brother state nodes from the wildcard characters. According to the method and device for constructing the AC (aho-corasick) state machine disclosed by the invention, the AC state machine can deal with wildcard characters.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
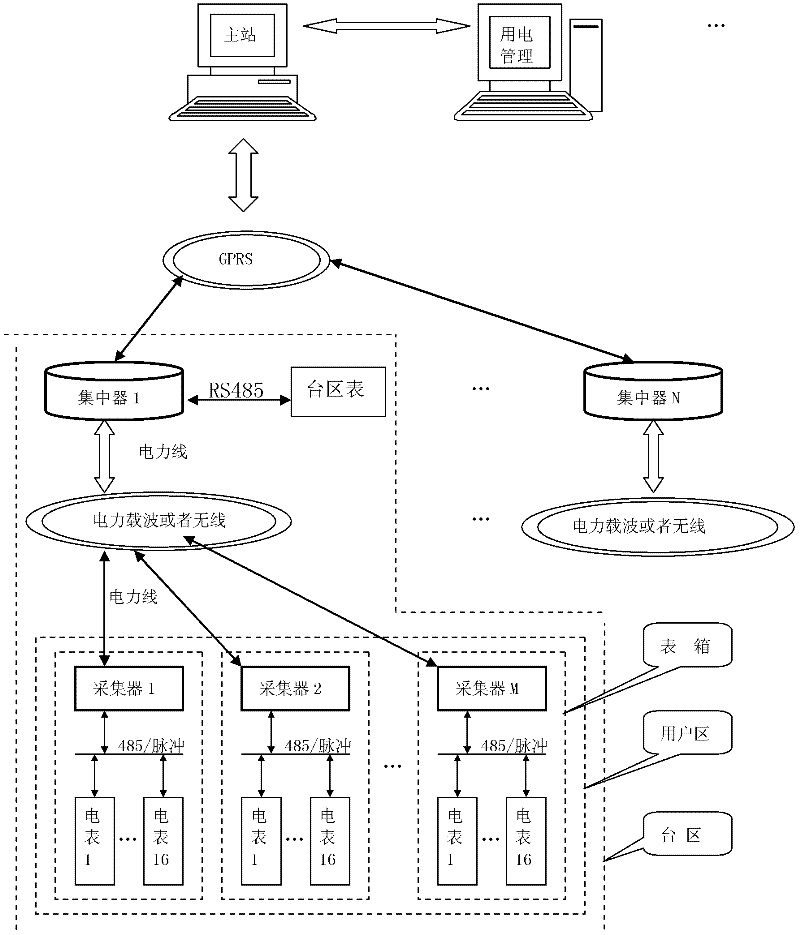
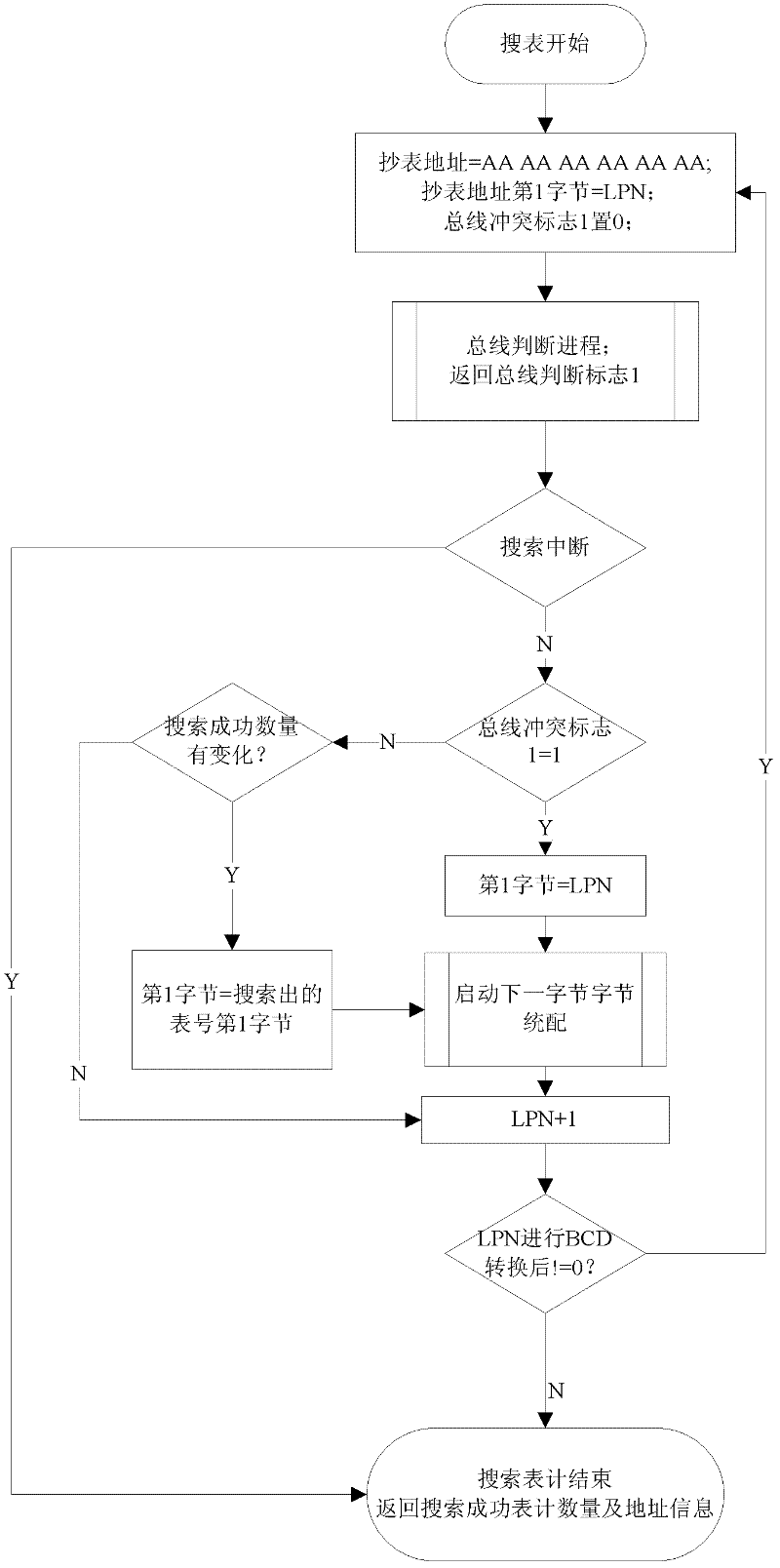
Automatic meter searching method for intelligent power grid
InactiveCN102339300AGuaranteed accuracyNo additional costSpecial data processing applicationsSmart gridPower grid
The invention relates to an automatic meter searching method for an intelligent power grid, which comprises the following steps of: acquiring and storing addresses of electric meters of all residents; starting to search and initializing meter searching information; replacing all the addresses with a wildcard character A to carry out meter reading and judging whether data is received on a transmission bus or not; and sequentially sending out meter reading commands and sequentially determining the addresses of the electric energy meters from the lowest level to the highest level. The automatic meter searching method for the intelligent power grid has the advantages that the accuracy of the information of the electric meters of the residents can be ensured; the automatic meter searching method for the intelligent power grid is convenient and rapid; and additional cost does not need to be added.
Owner:HANGZHOU SUNRISE TECH
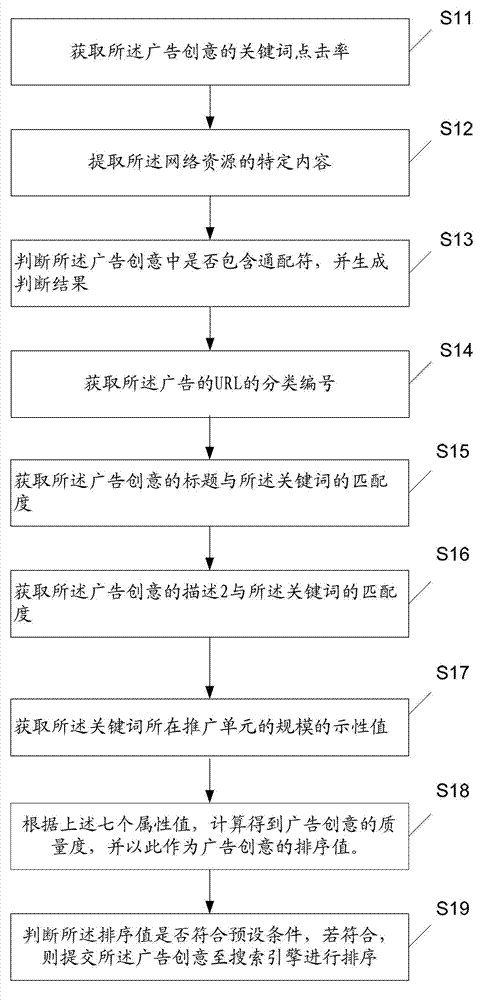
Target data sequencing method and target data sequencing device
InactiveCN103034718AImprove sorting efficiencyImprove efficiencySpecial data processing applicationsWildcard characterUniform resource locator
The invention discloses a target data sequencing method and a target data sequencing device. The method comprises the following steps of acquiring seven attribution values of target data; calculating a sequence value of the target data according to the seven attribution values; and judging whether the sequence value conforms to a preset condition or not, and submitting the target data to a sequencing system to be sequenced if the sequence value conforms to the preset condition, wherein the seven attribution values are sequentially key word click rate of the target data, a matching mode indicator value of a key word in a searching engine, whether a wildcard character is contained in the target data or not, classification number of a website uniform resource locator (URL) of the target data, matching degree of a title of the target data and the key word, matching degree of description of the target data and the key word, and a scale indicator value of a unit in which the key word is located. By utilizing the method and the device, the efficiency for submitting the target data to the sequencing system can be increased, so that the sequencing efficiency of the sequencing system for the target data can be increased.
Owner:北京博雅立方科技有限公司
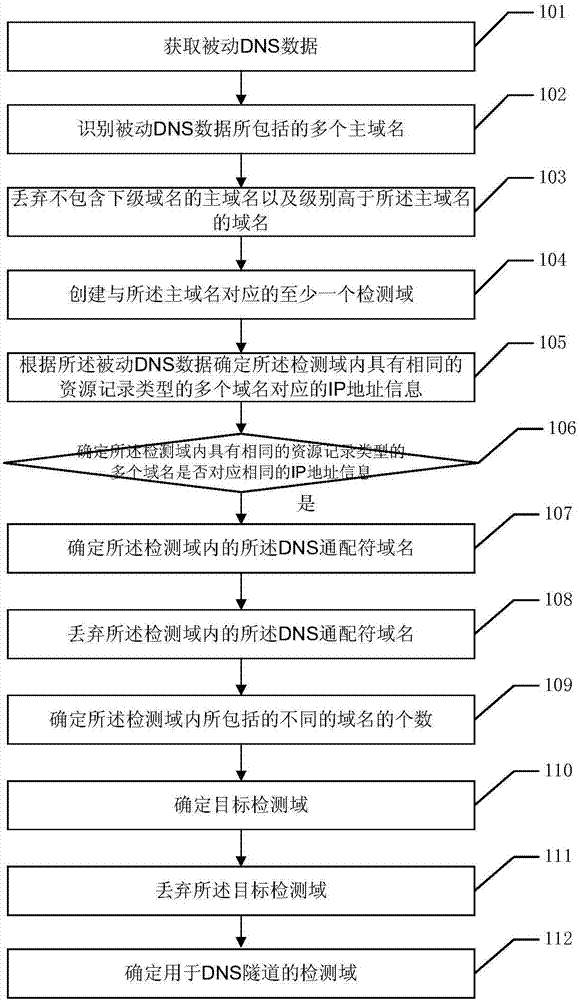
DNS tunnel detection method and DNS tunnel detection device
ActiveCN107547488AAvoid violationsAvoid DNS Tunneling SituationsTransmissionDomain nameWildcard character
The embodiment of the invention discloses a DNS tunnel detection method and a DNS tunnel detection device. The method comprises the steps of recognizing a plurality of main domain names included by passive DNS data; building at least one detection domain corresponding to the main domain names, wherein the number of the domain names included by the detection domain is less than or equal to a firstthreshold; if the detection domain comprises a DNS wildcard character domain name, discarding the DNS wildcard character domain name in the detection domain; and recognizing the detection domain applied to a DNS tunnel. According to the method and the device provided by the invention, user information of a client is not involved during a detection process, so that invasion of privacy is avoided, alot of insignificant sub-domain name records Wildcard can be discarded, records generated by Wildcard are filtered out, and the situation that lots of abnormal sub-domain names exist under one domainby lots of the insignificant records can be eliminated; if the detection domain applied to the DNS tunnel is determined, defense can be performed on the detection domain applied to the DNS tunnel, and thus the situation that a malicious client builds the DNS tunnel with an external DNS is avoided, and security during a data transmission process is ensured.
Owner:HUAWEI TECH CO LTD
Systems and methods for partial matching searches of encrypted retained data
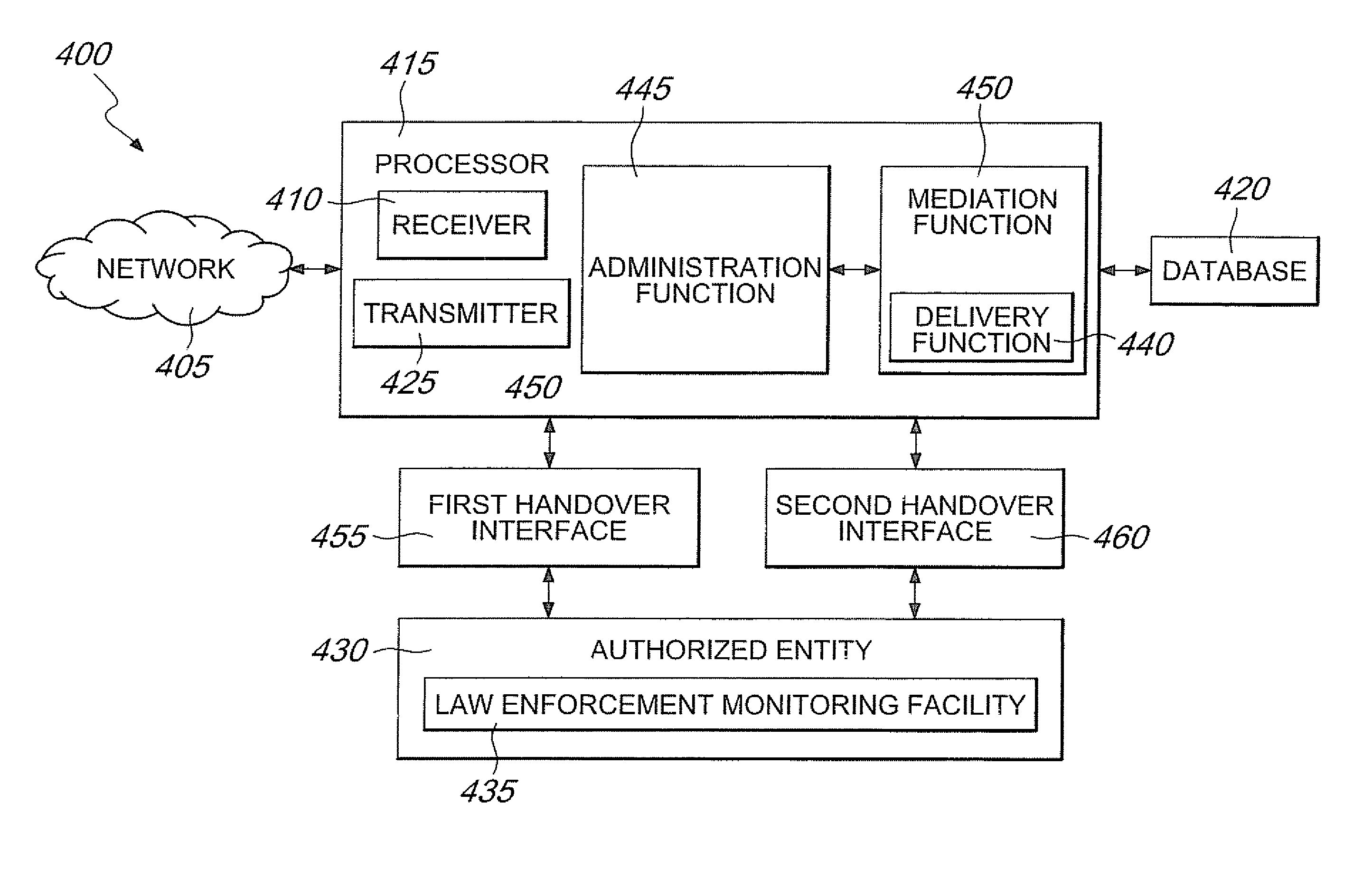
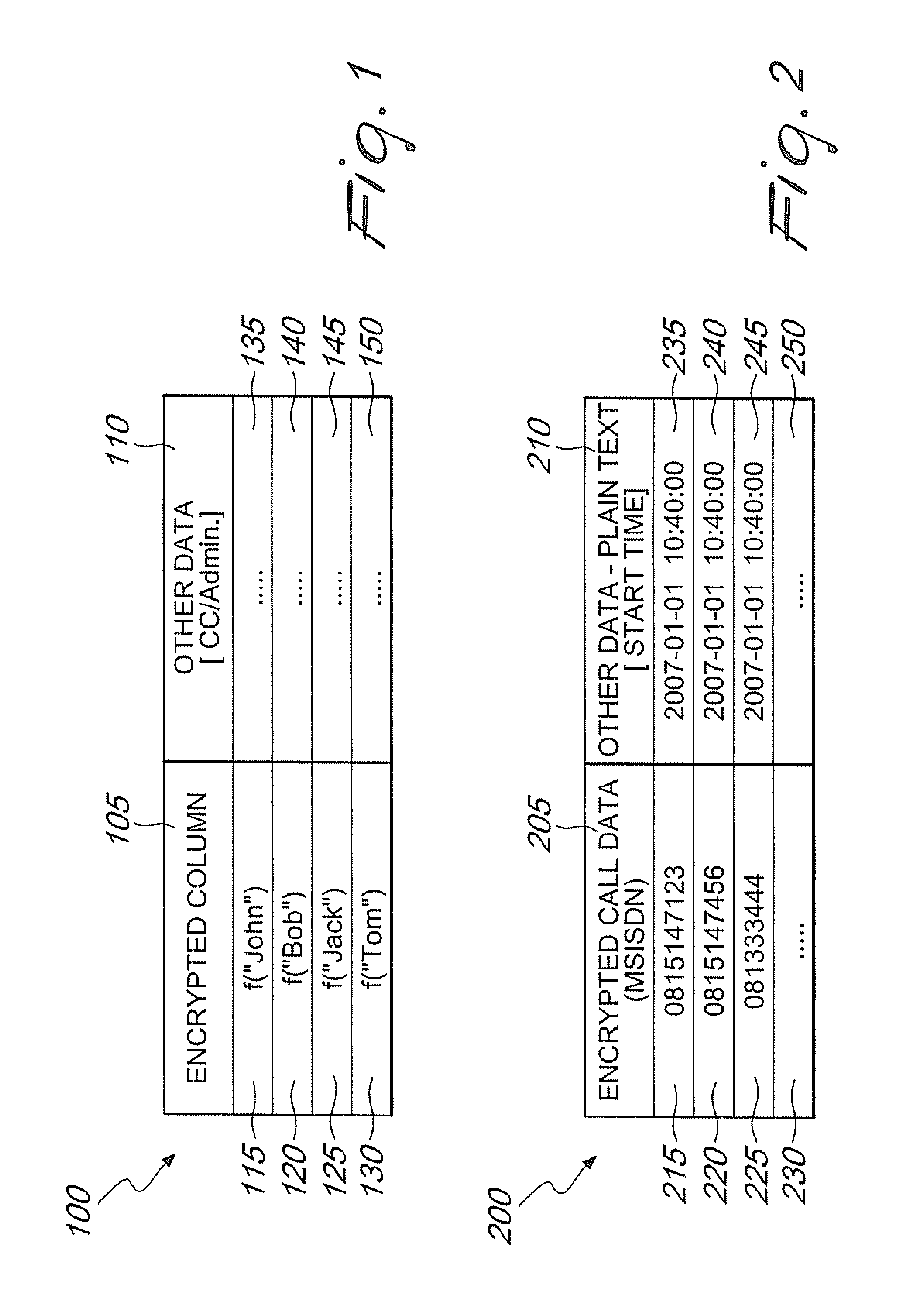
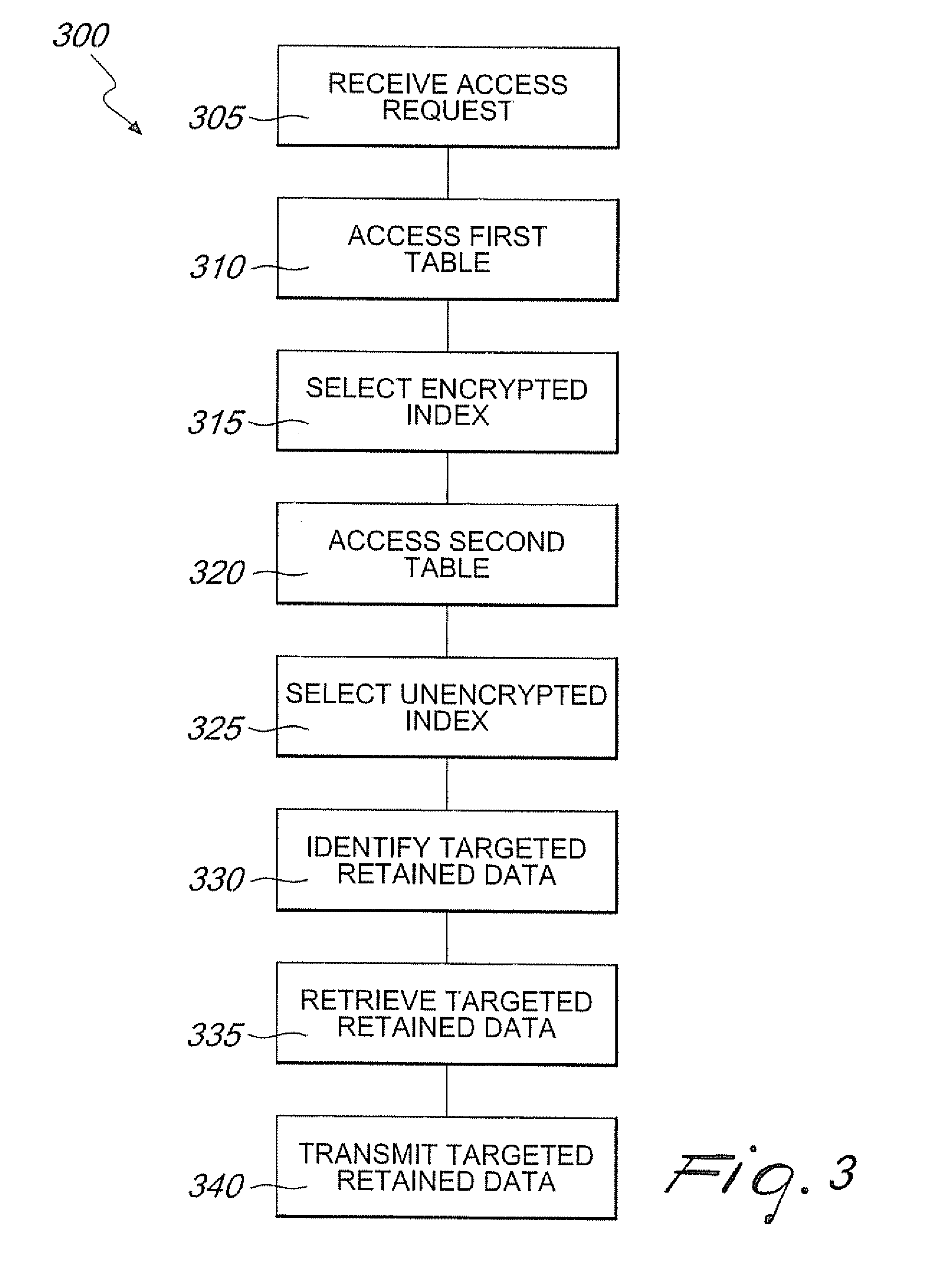
ActiveUS20100211800A1Maintain securityIncrease speedDigital data processing detailsUnauthorized memory use protectionWildcard characterData system
Systems and methods are provided for encryption allowing partial matching searches to retrieve data that is retained in a database. A user identification number or other characteristic is stored in unencrypted form such that a wildcard search may be performed to retrieve one or more encrypted indexes associated with the unencrypted user identification. These encrypted indexes are then unencrypted by use of a key to determined their associated unencrypted index and corresponding targeted retained data. The targeted retained data may then be accessed by an authorized entity such as a law enforcement agency.
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com