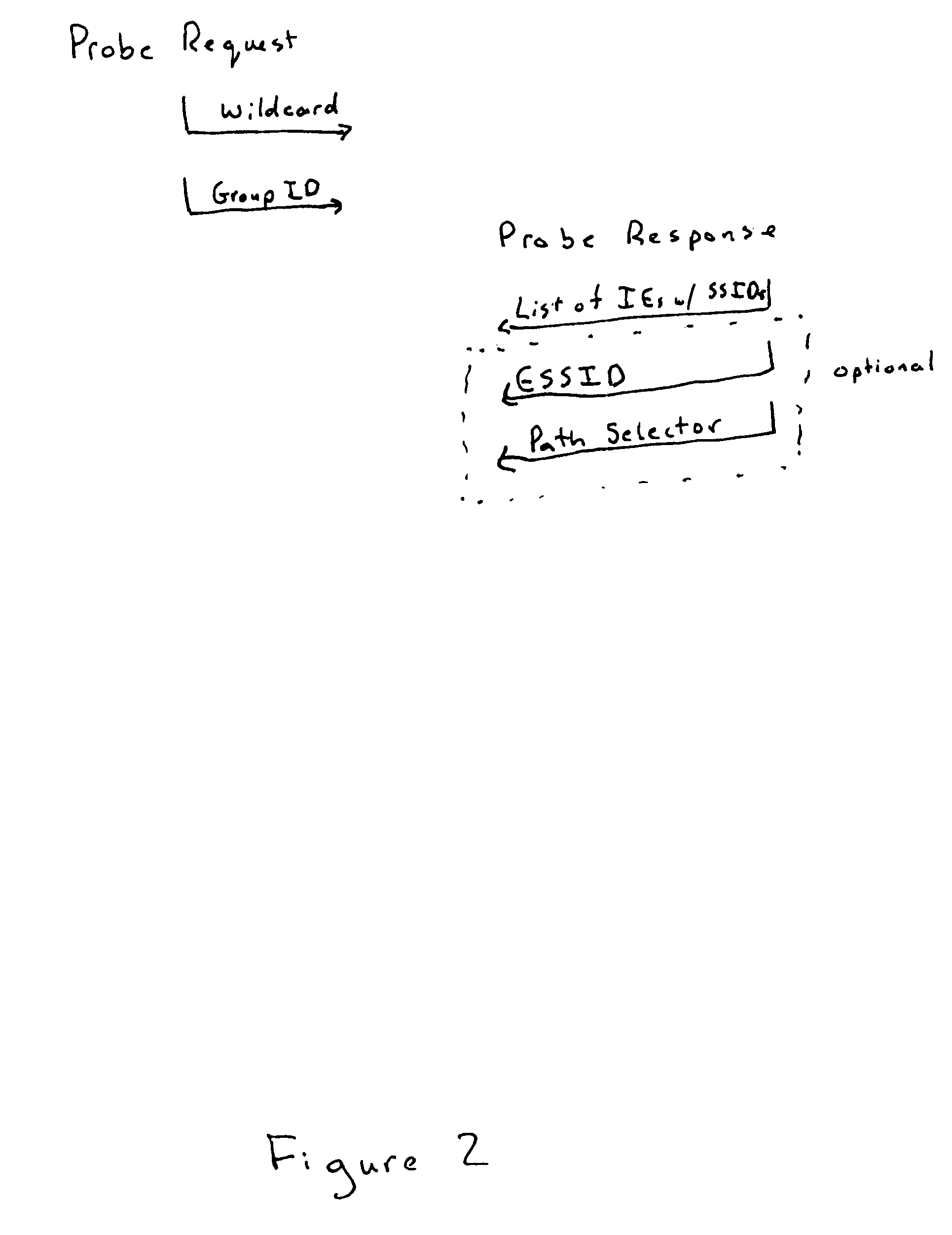Patents
Literature
183 results about "Wild card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure card-based transactions using mobile phones or other mobile devices
InactiveUS20120284194A1Easily and quickly encodedProvide securityFinancePayment architectureSmart cardMobile device
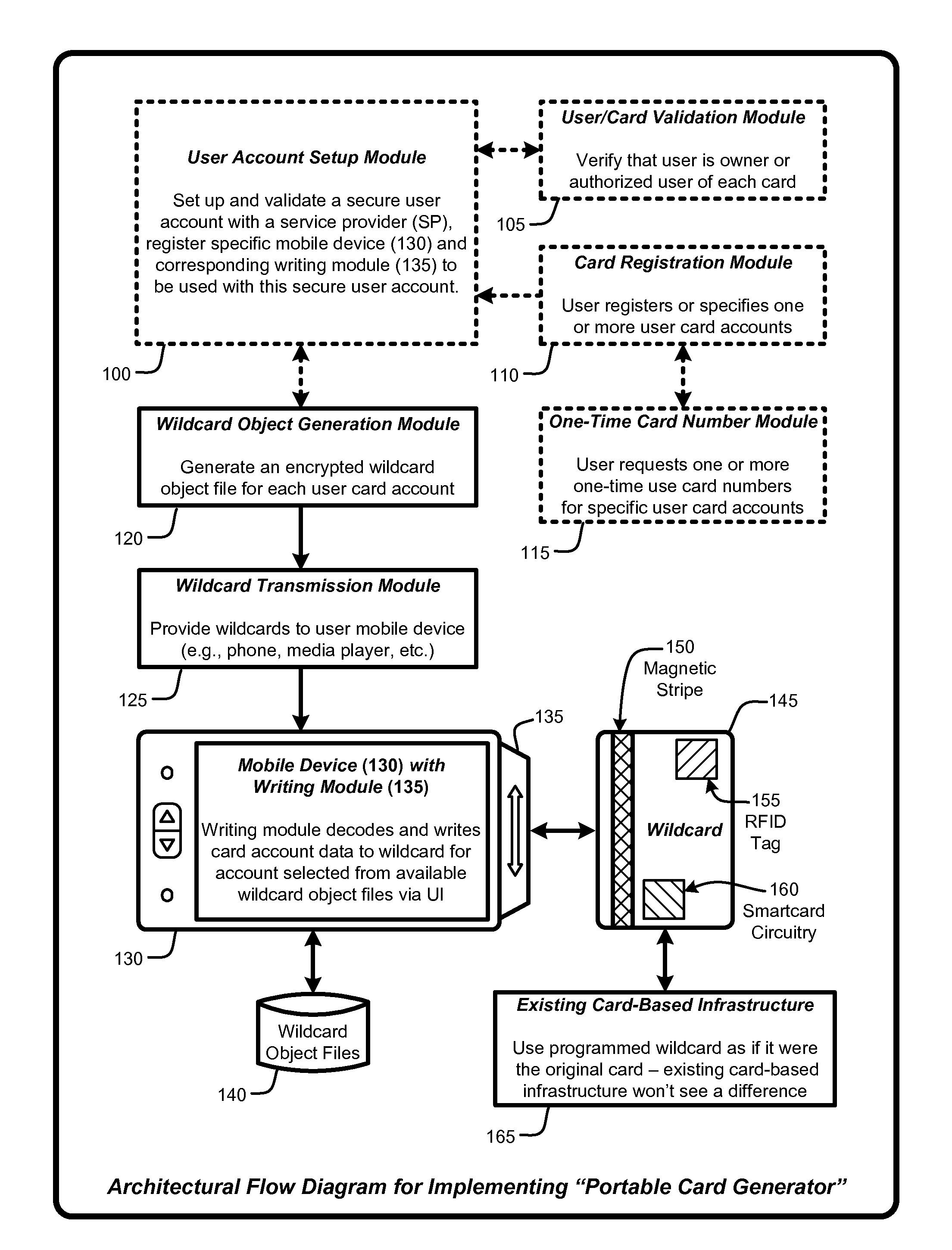
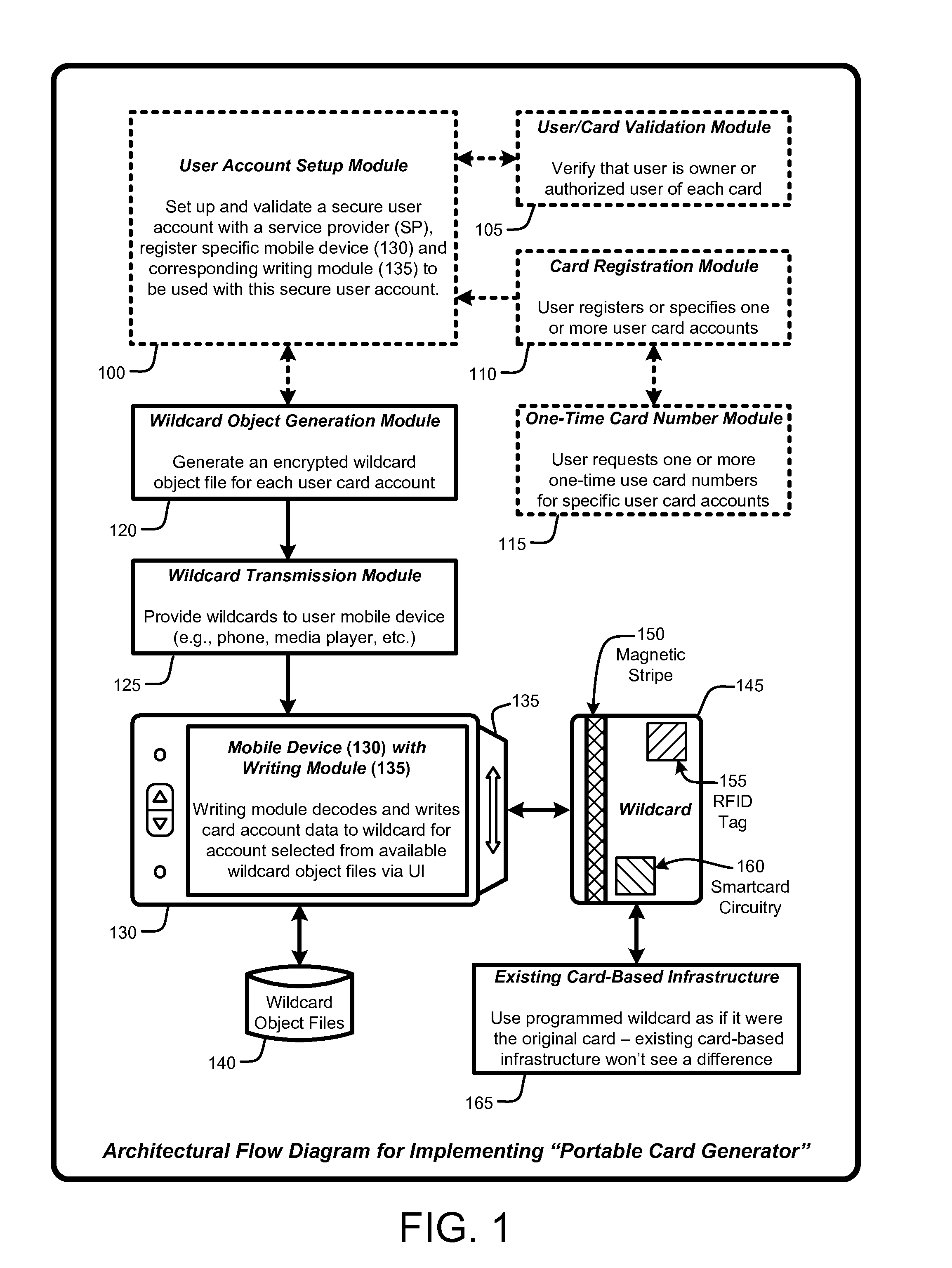
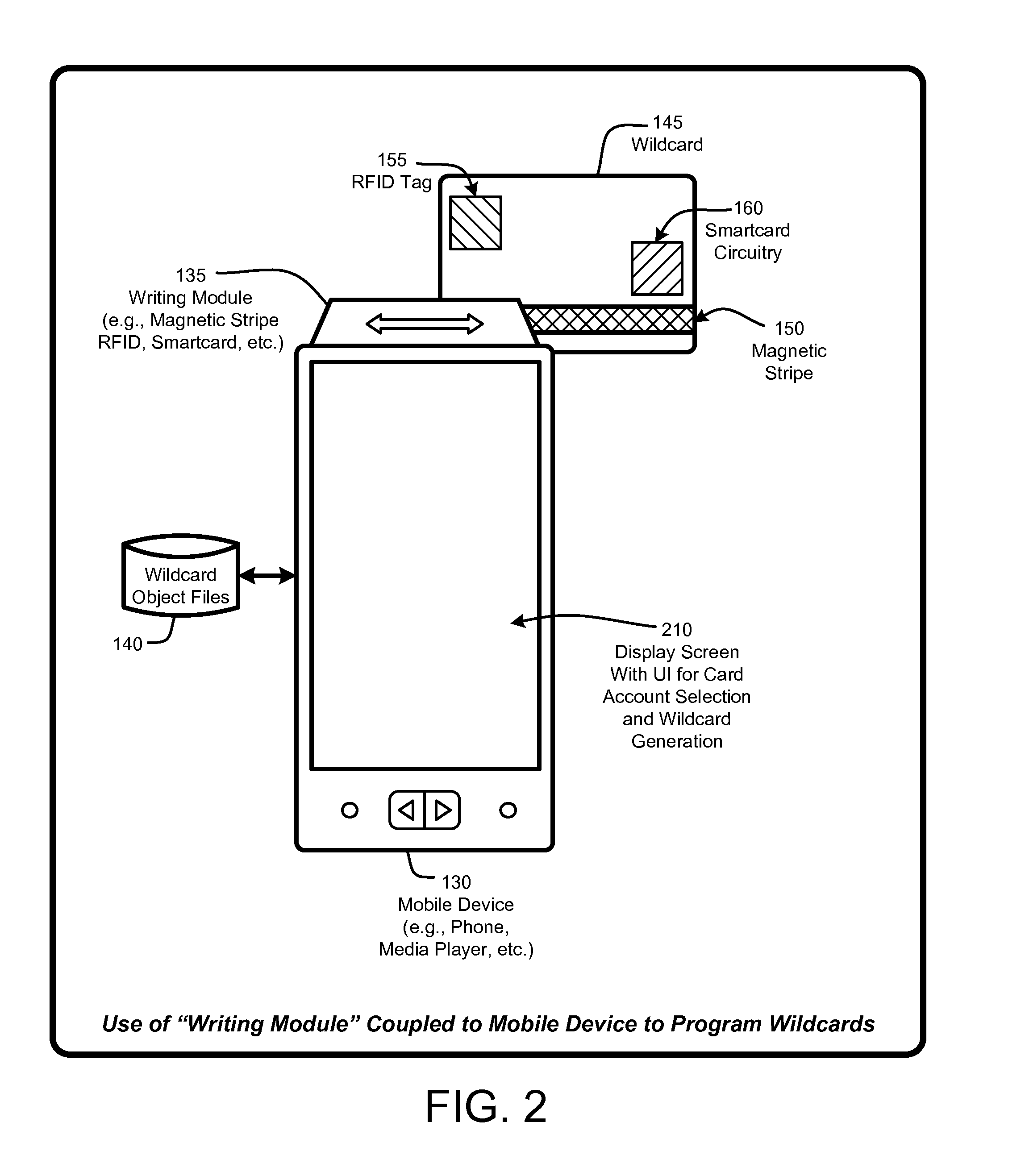
A “Portable Card Generator” is implemented within a portable device, such as a mobile phone, and provides various techniques for writing secure account information from user selected accounts to a “wildcard” having rewritable magnetic stripes, rewritable RFID tags, and / or rewritable smartcard circuitry. The account information is retrieved by the portable device from local or remote stores of user accounts. Once that account information is written, the wildcard is then available for immediate use for credit card or debit-type payments, loyalty card use, etc. Consequently, by providing a credit card sized object having a rewriteable magnetic stripe, RFID tag, and / or smartcard circuitry, in combination with account information for various credit cards, debit cards, consumer loyalty cards, insurance cards, ID cards or badges, etc., the user is no longer required to physically carry those cards in order to use the corresponding accounts within existing card-based infrastructures.
Owner:MICROSOFT TECH LICENSING LLC
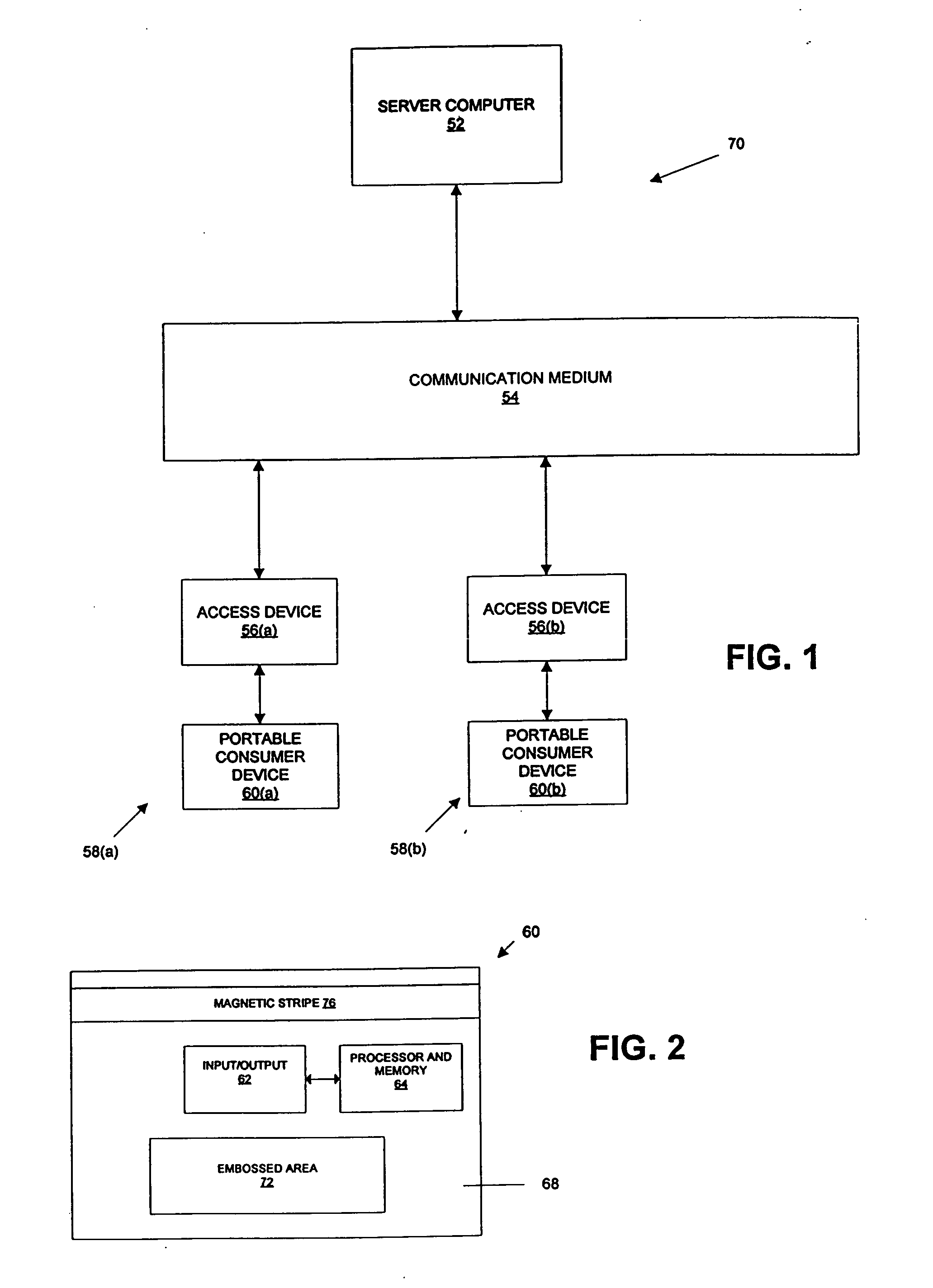
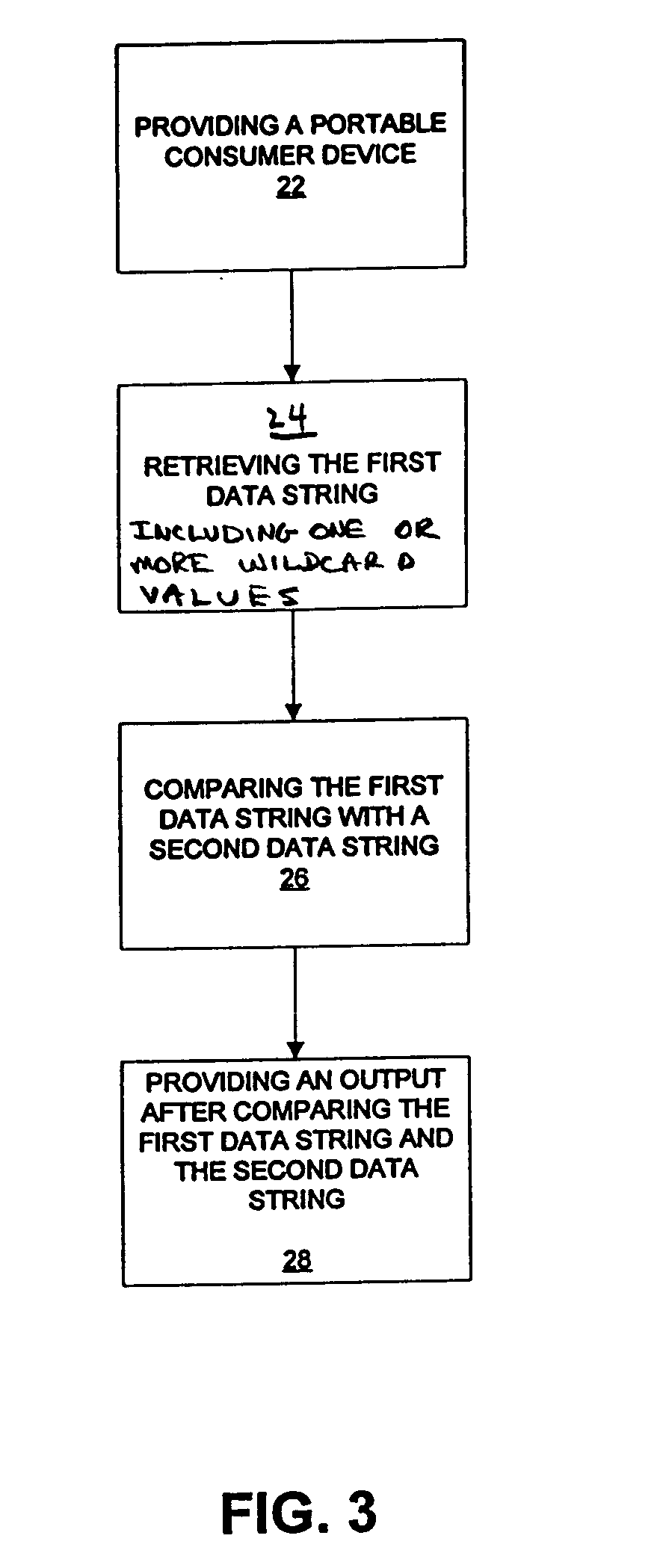
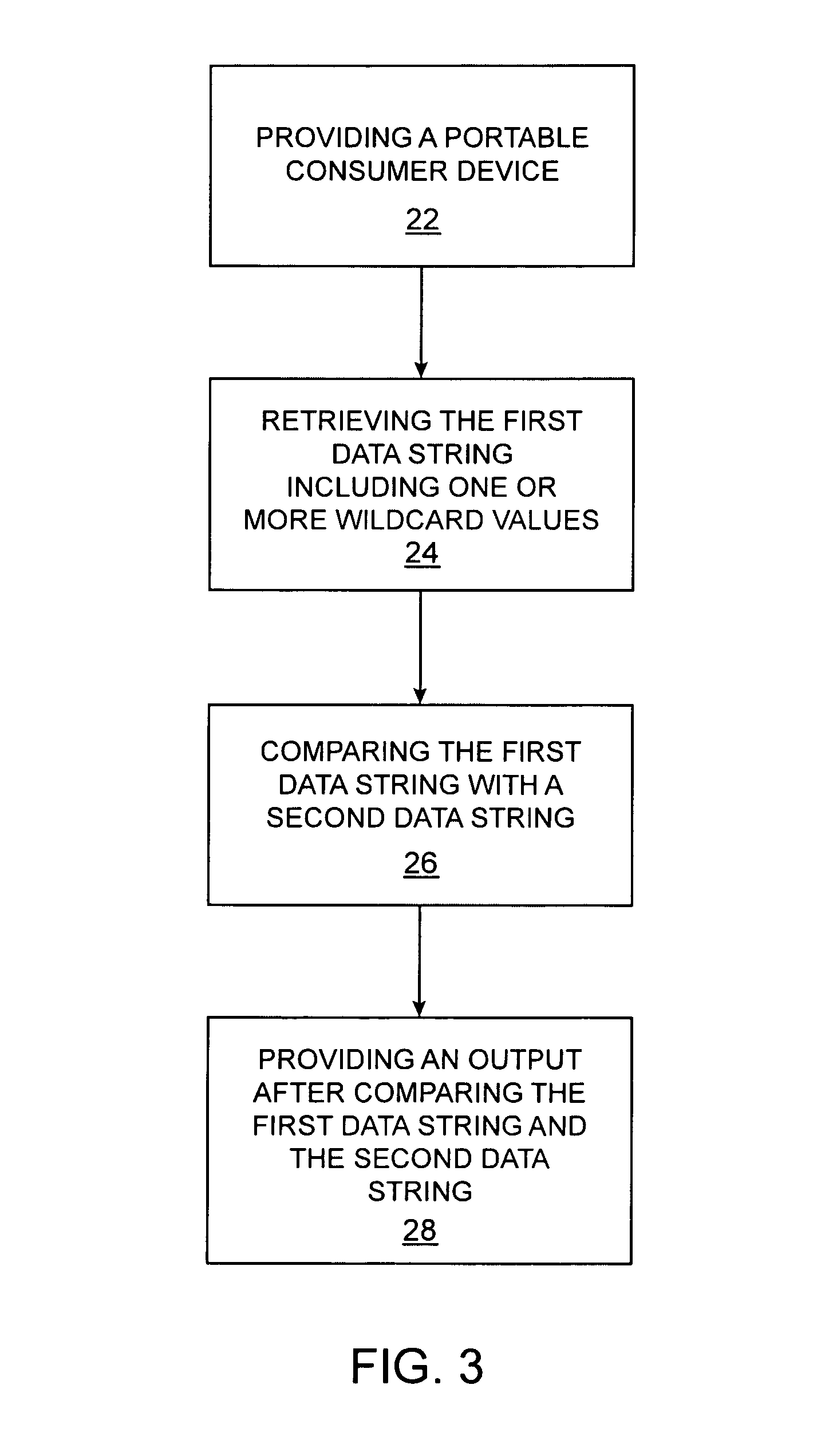
Method, system and portable consumer device using wildcard values
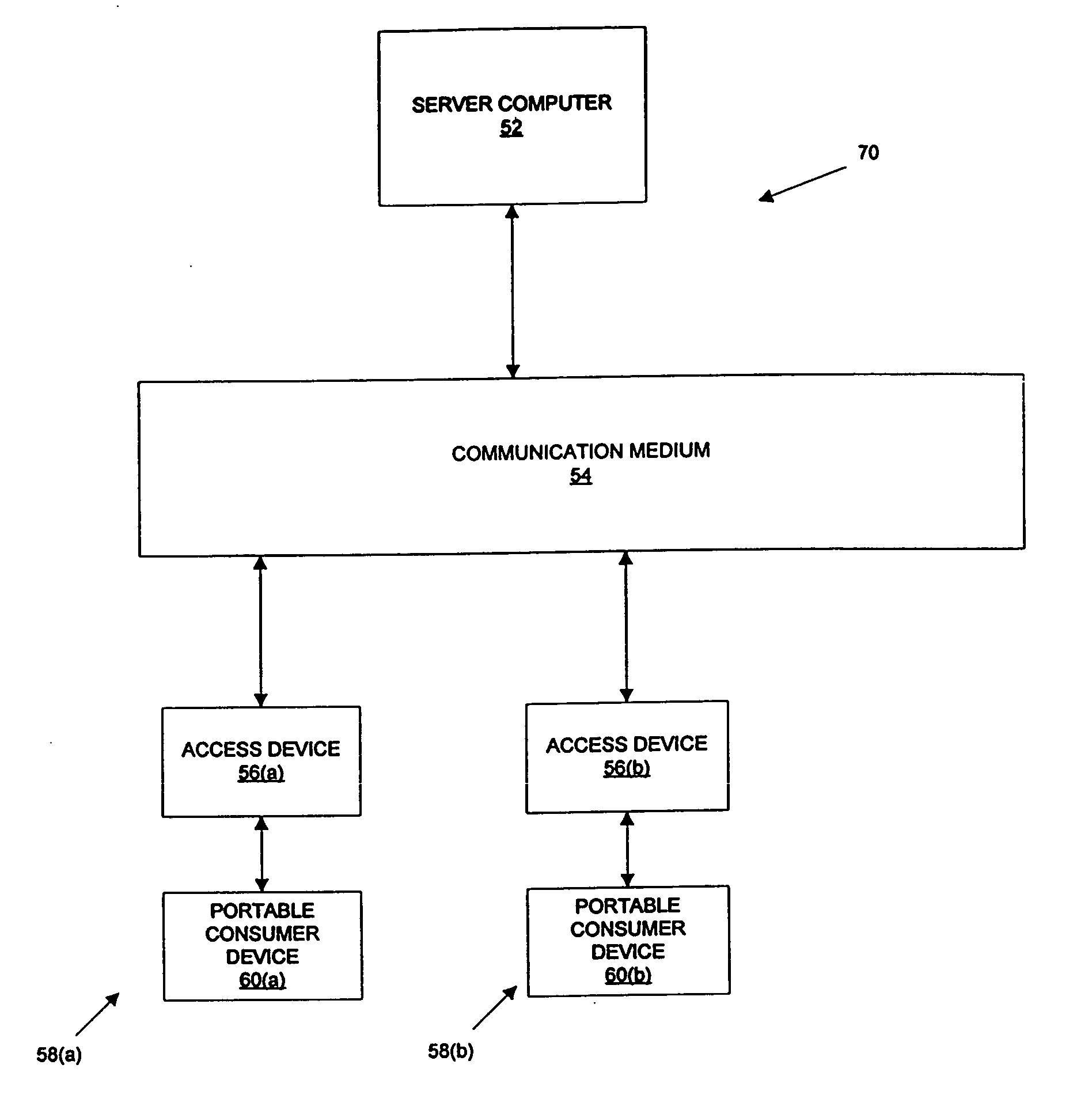
A portable consumer device is disclosed. The portable consumer device includes a body and a computer readable medium coupled to the body. The computer readable medium comprises a data string including one or more wildcard values. The data string is specifically associated with the consumer. For example, the data string may represent one or more products that the consumer prefers to use.
Owner:VISA USA INC (US)
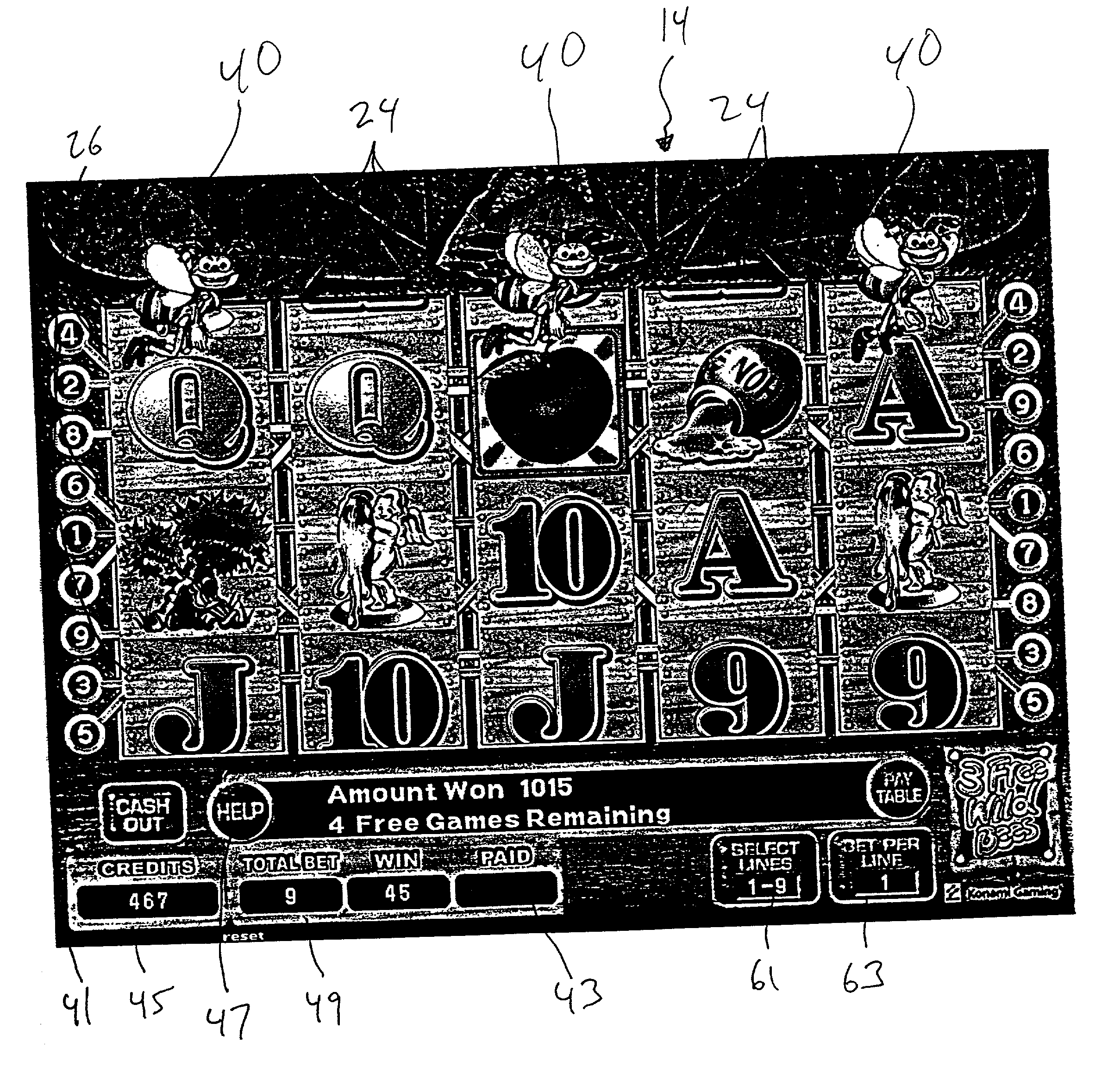
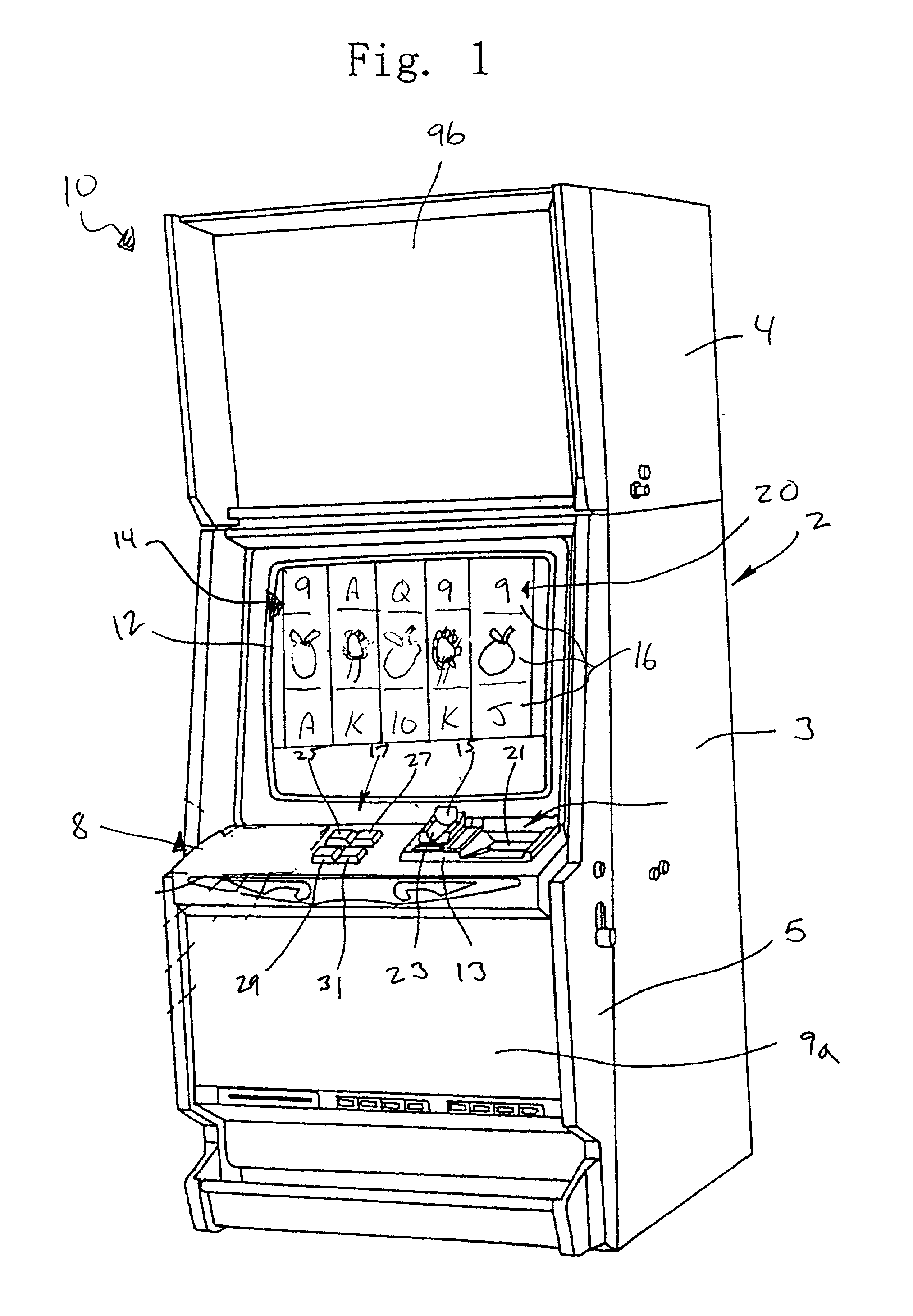
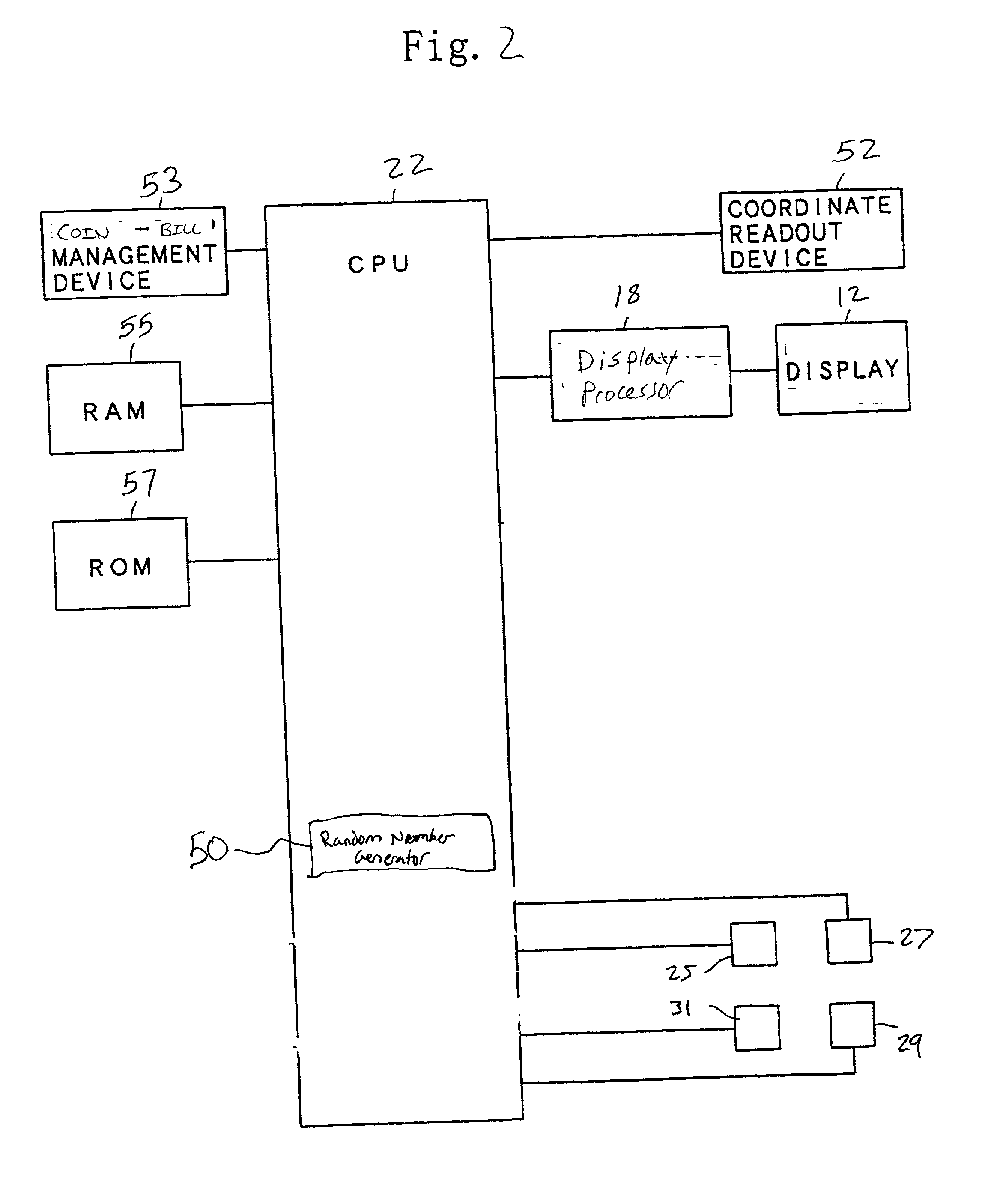
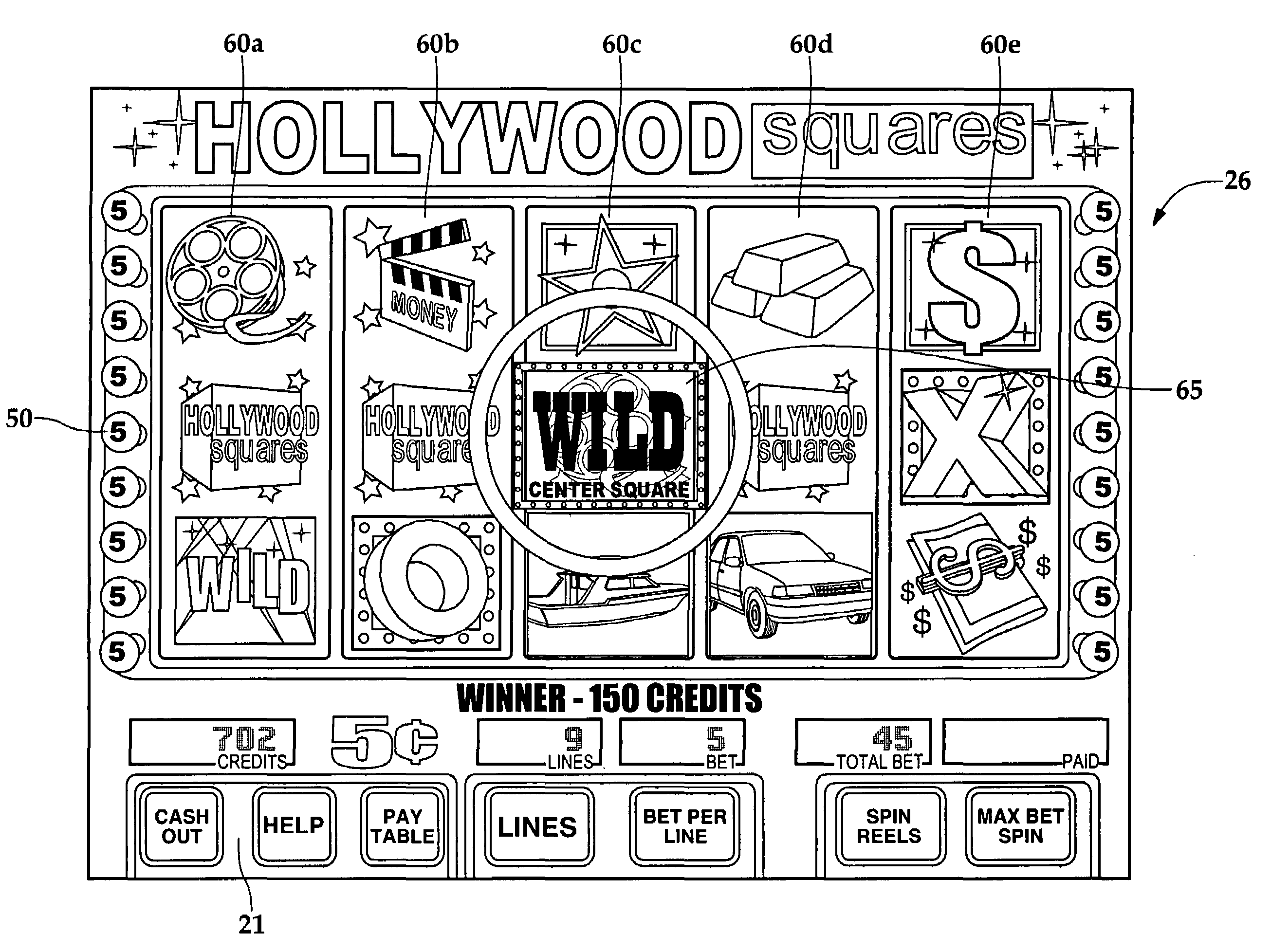
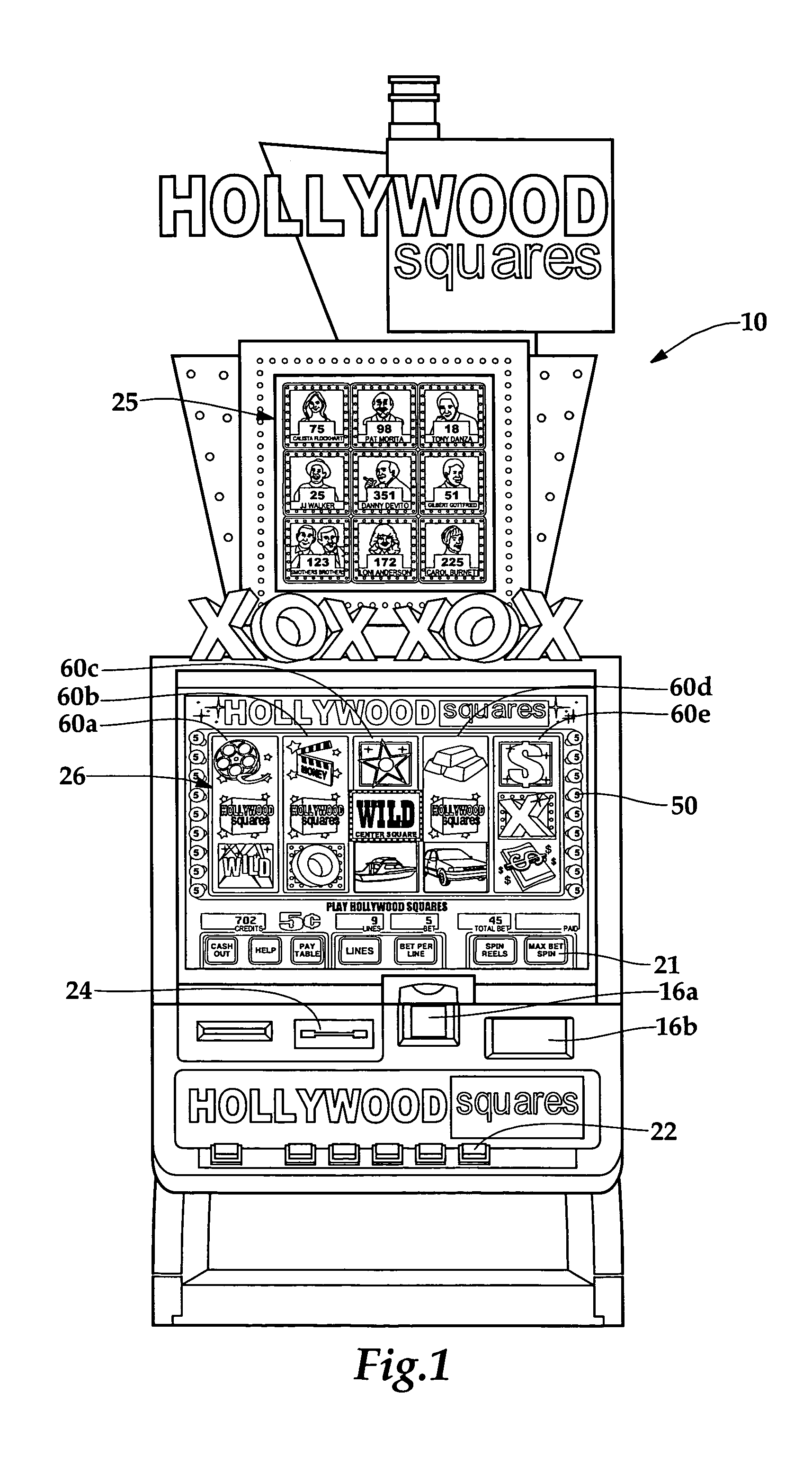
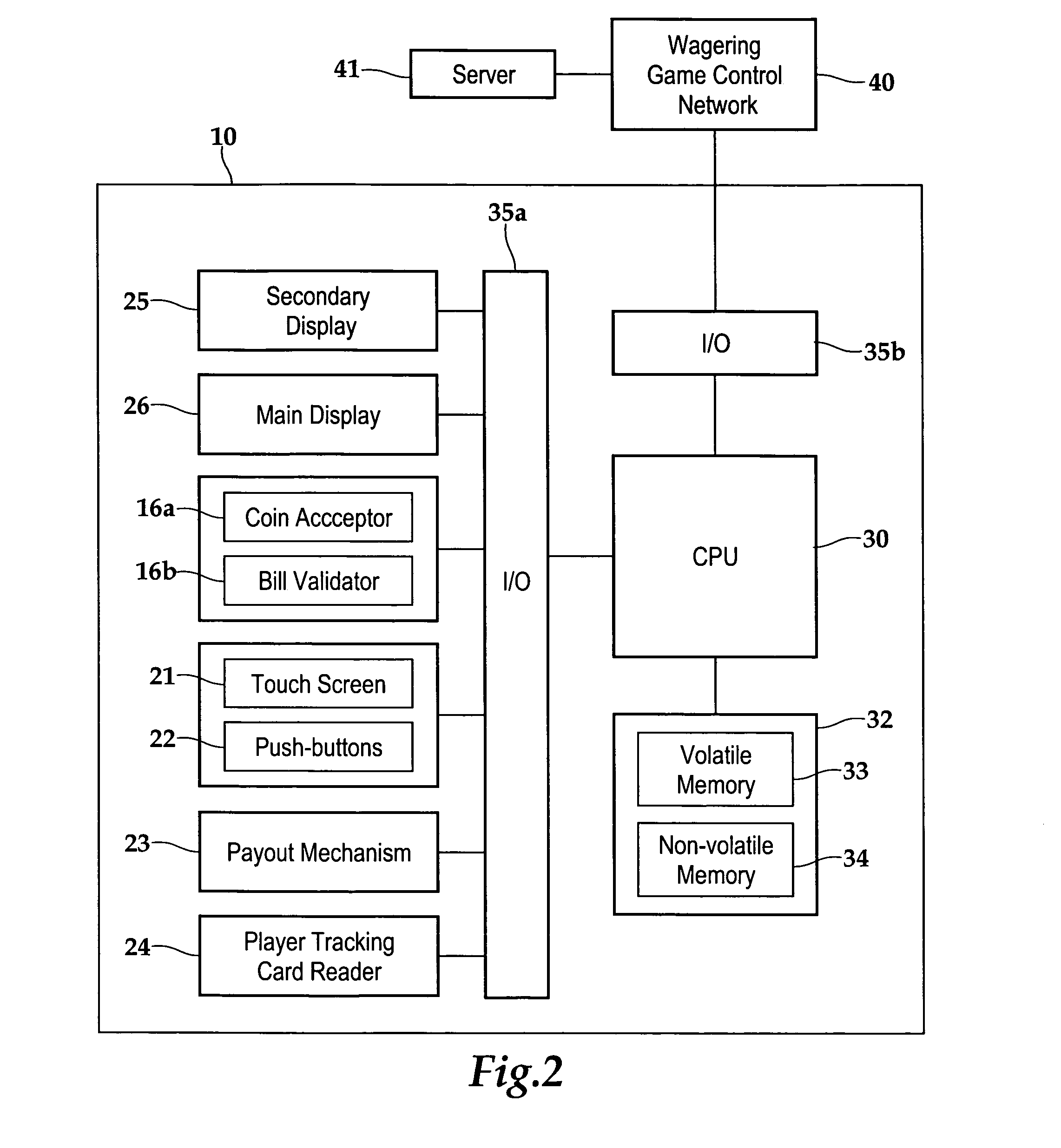
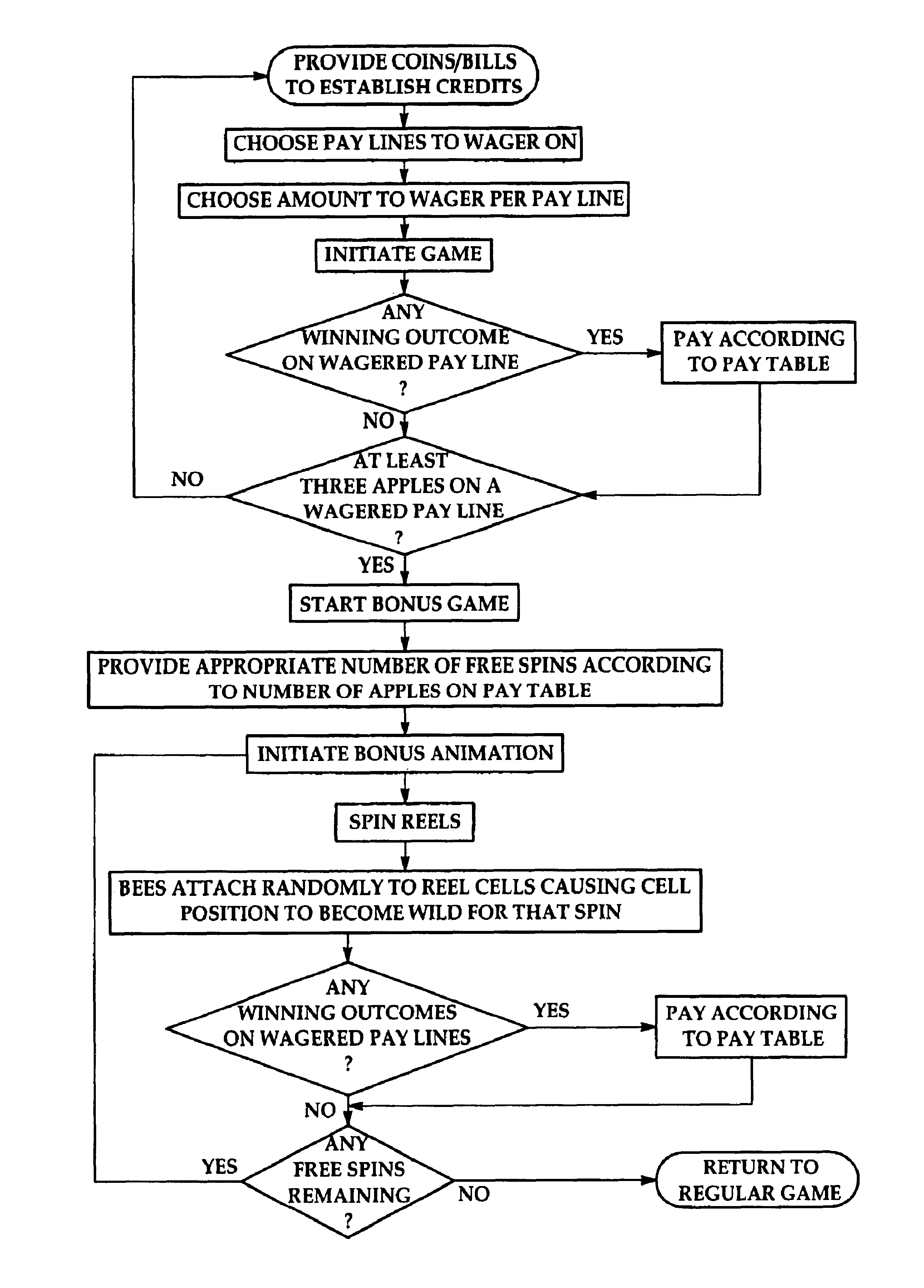
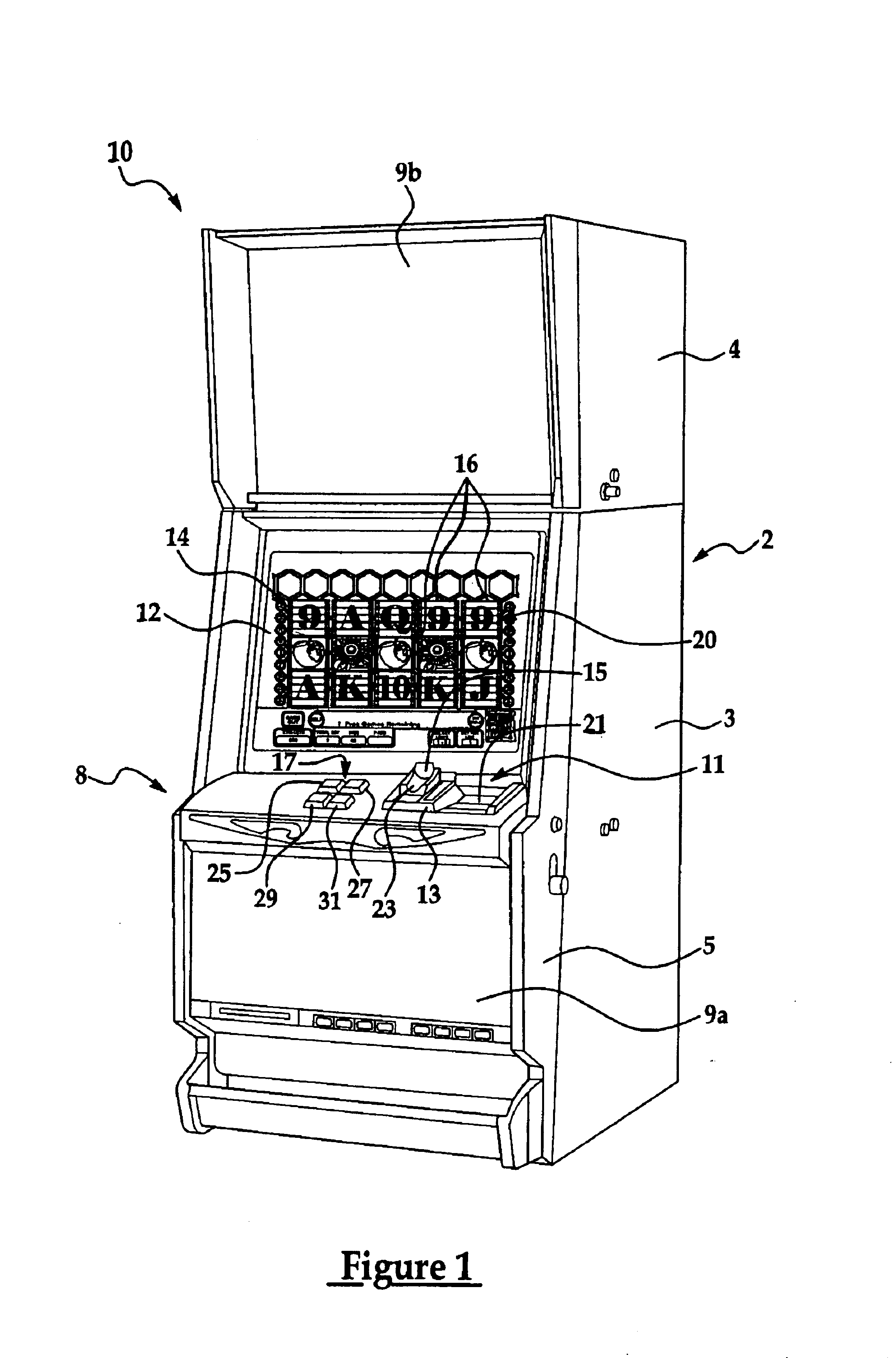
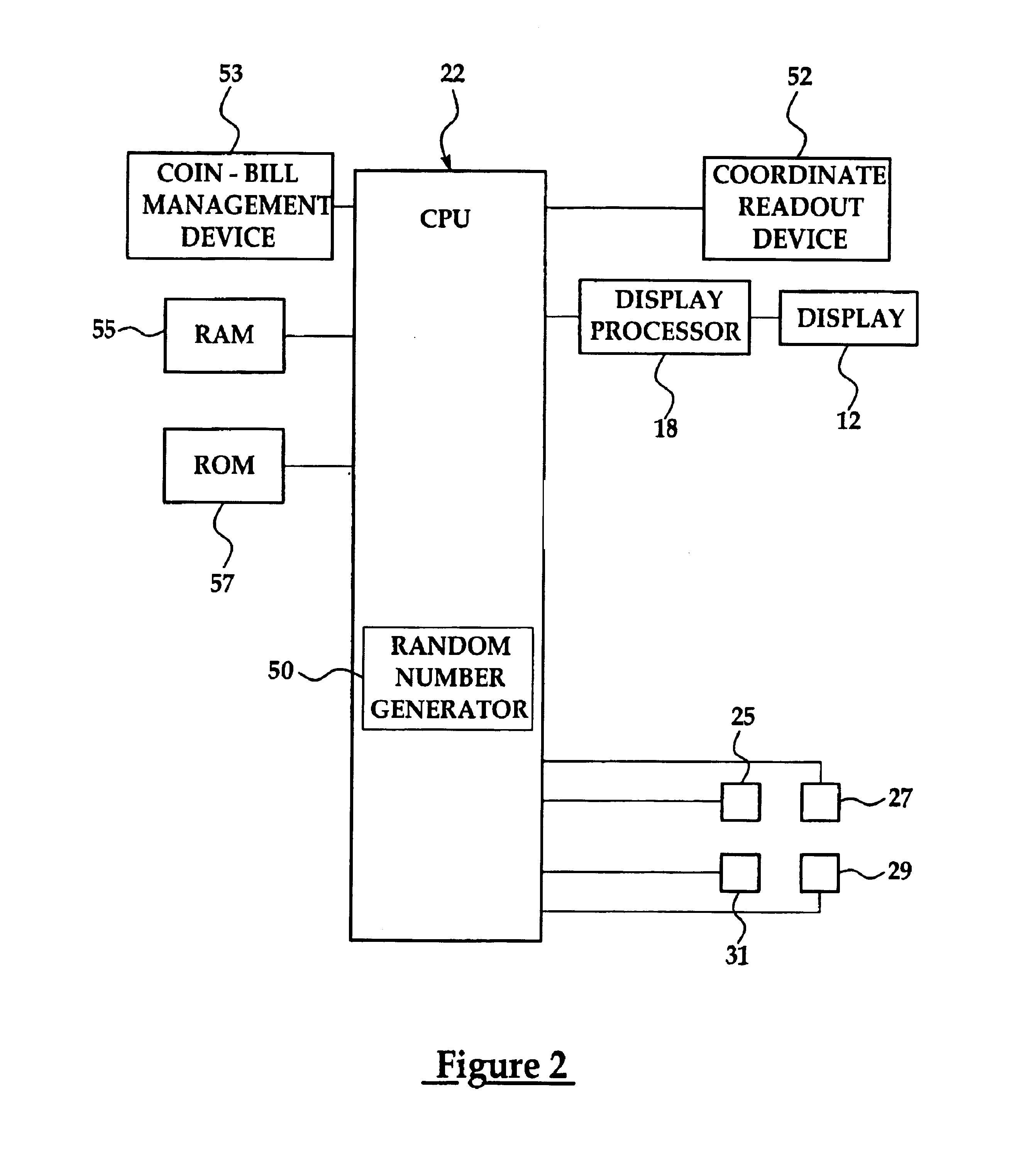
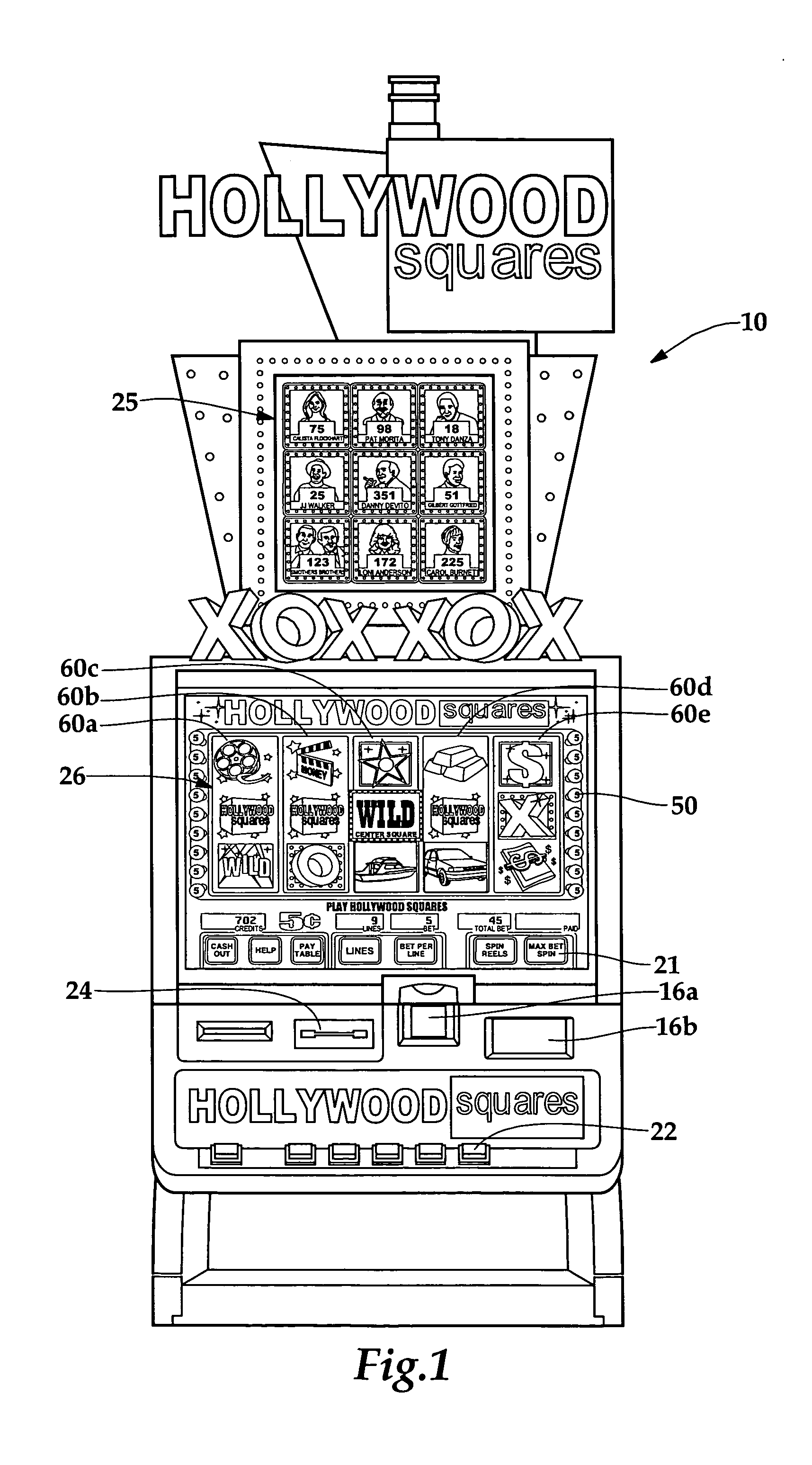
Gaming machine having dynamic bonus feature
InactiveUS20030069062A1Enjoyable for userApparatus for meter-controlled dispensingVideo gamesGame elementComputer science
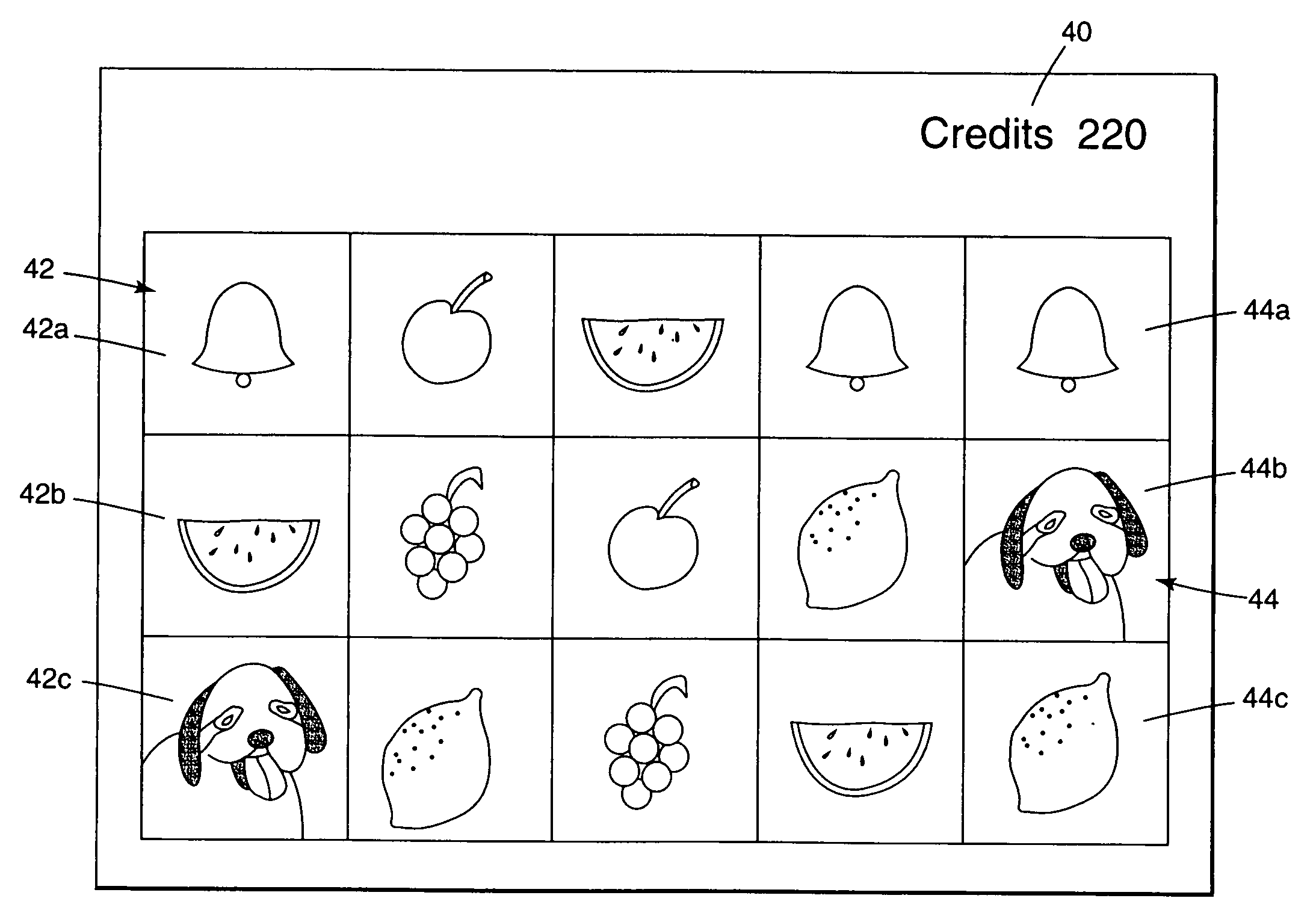
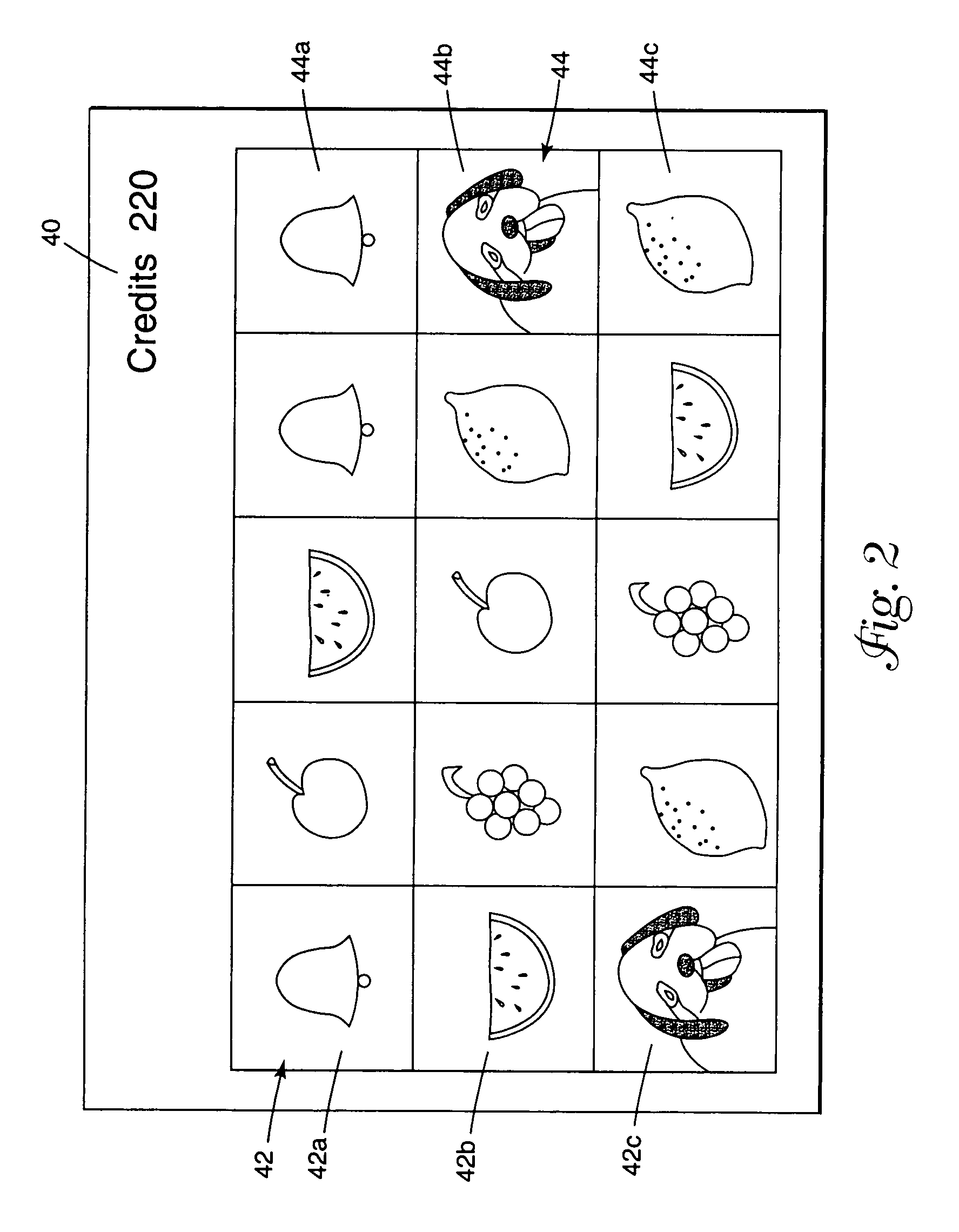
A gaming machine and a method of playing the game which includes randomly displaying a plurality of game elements (20) in a grid (14) of cells (16) to produce a normal random display with one element (20) in each of the cells (16). A bonus random display of the game elements (20) is initiated in response to a triggering combination (30) of three apple symbols appearing in the cells (16). Once this occurs, a sound is played to convey the beginning of the bonus round, and the sound is preferably of bees. In the bonus round, a plurality of the cells (16) is designated as wild cells (34) for the bonus random display and a wild card (40) is positioned over the wild cell (34) such that the wild card (40) conceals the game element (20) disposed within the wild cell (34). The bonus random display is repeated for a predetermined number of rounds.
Owner:KONAMI GAMING
Wagering game with predetermined location for wild-card feature
InactiveUS7237775B2Card gamesApparatus for meter-controlled dispensingArray data structureEngineering
Owner:BALLY GAMING INC
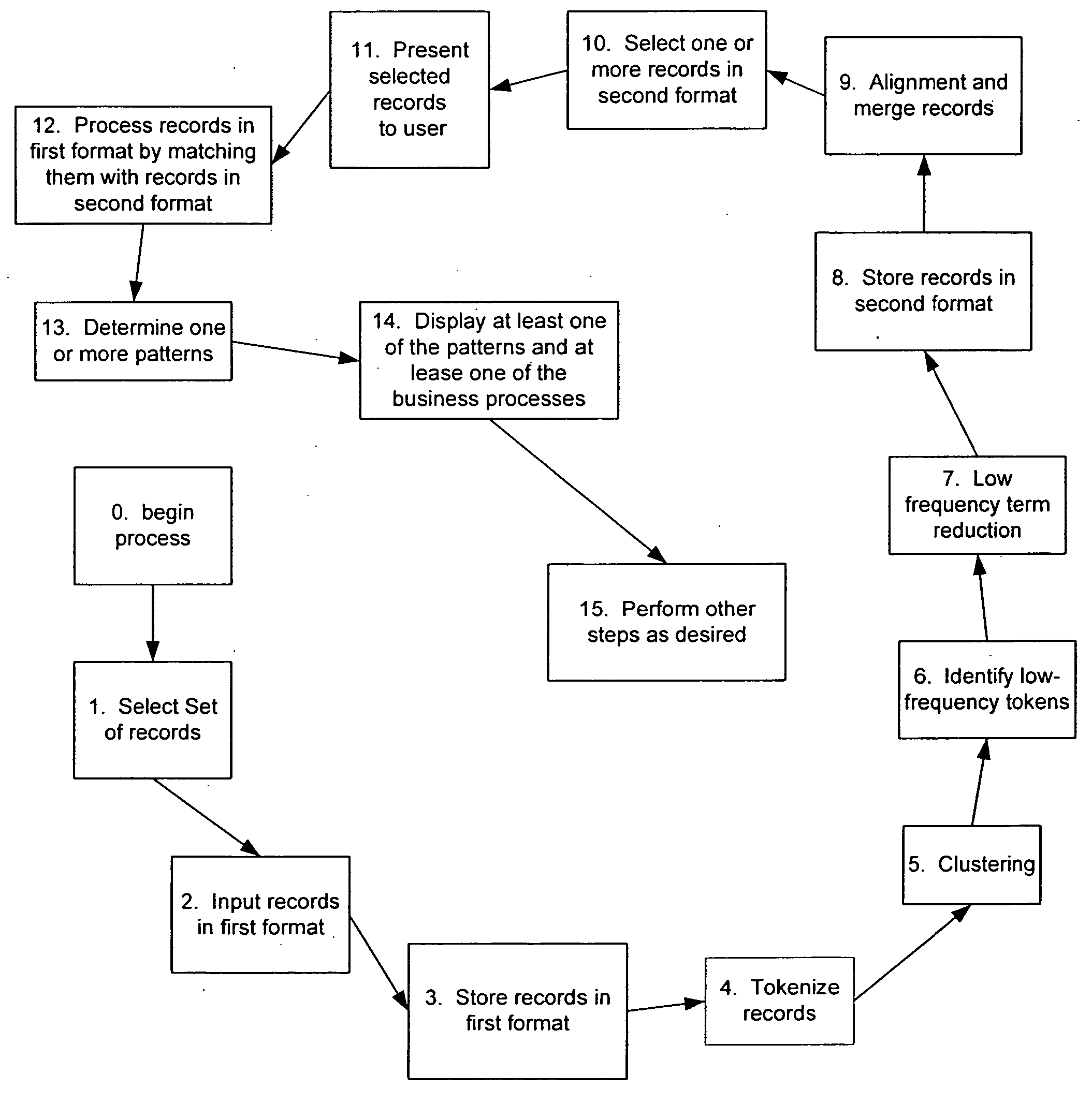
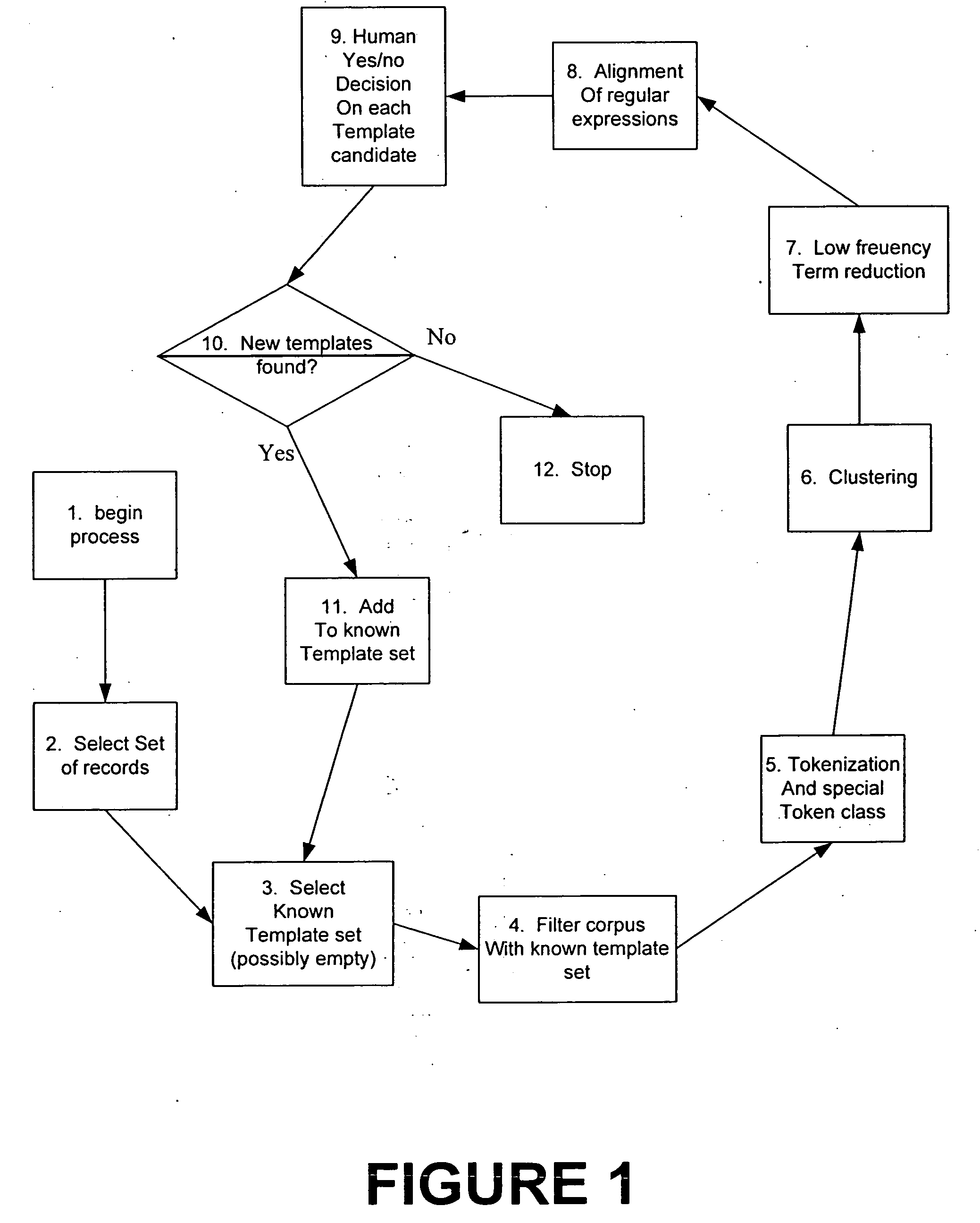
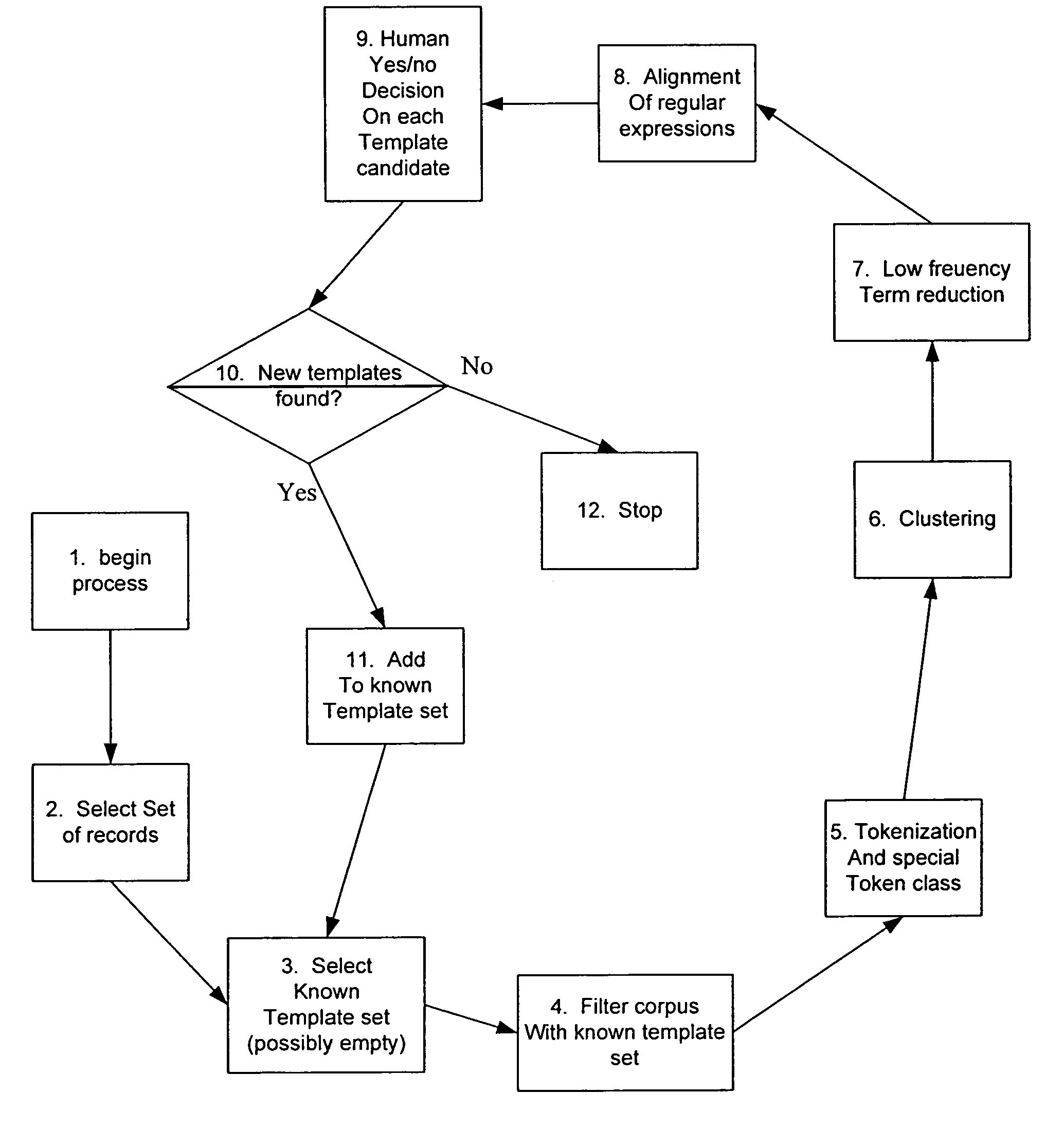
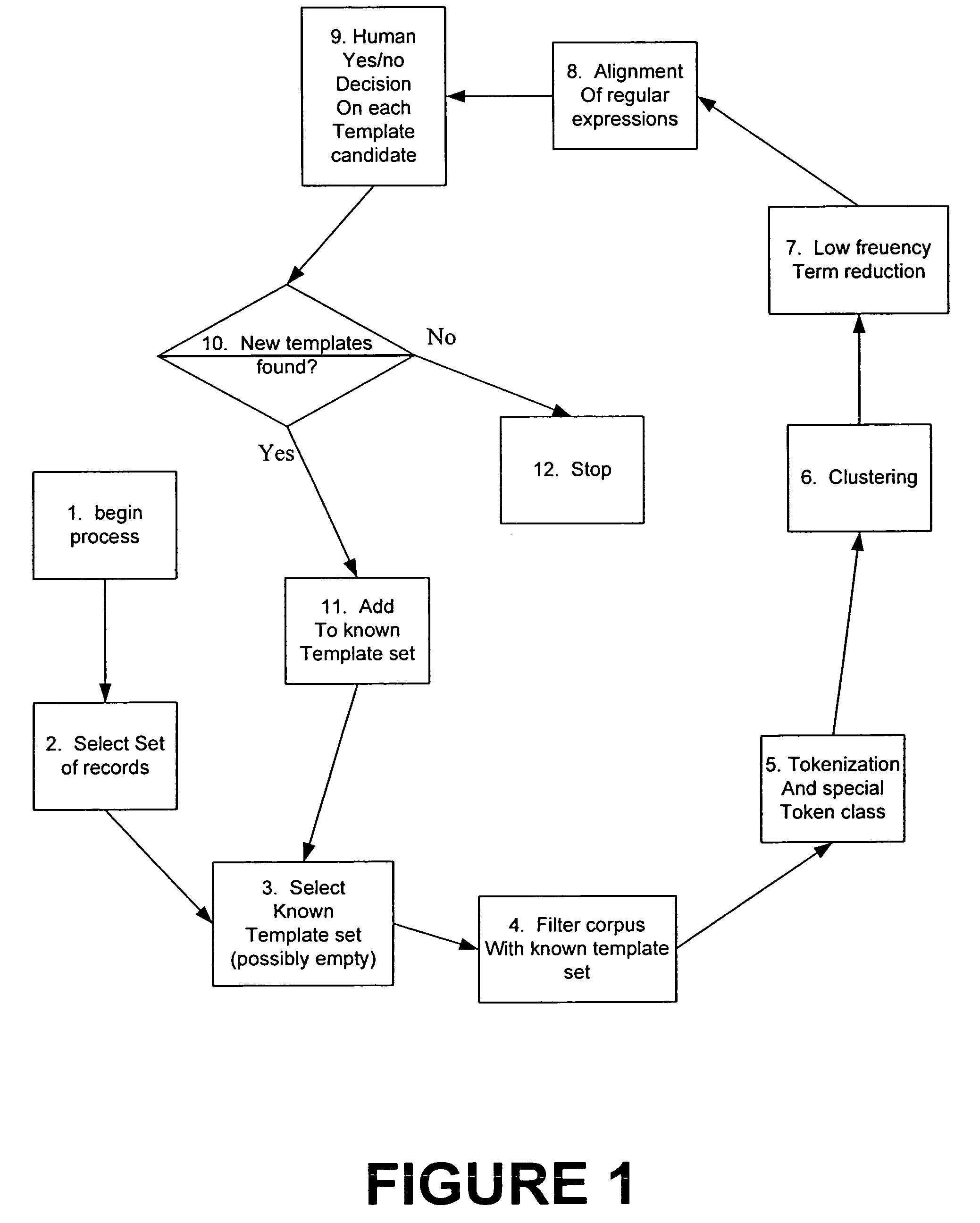
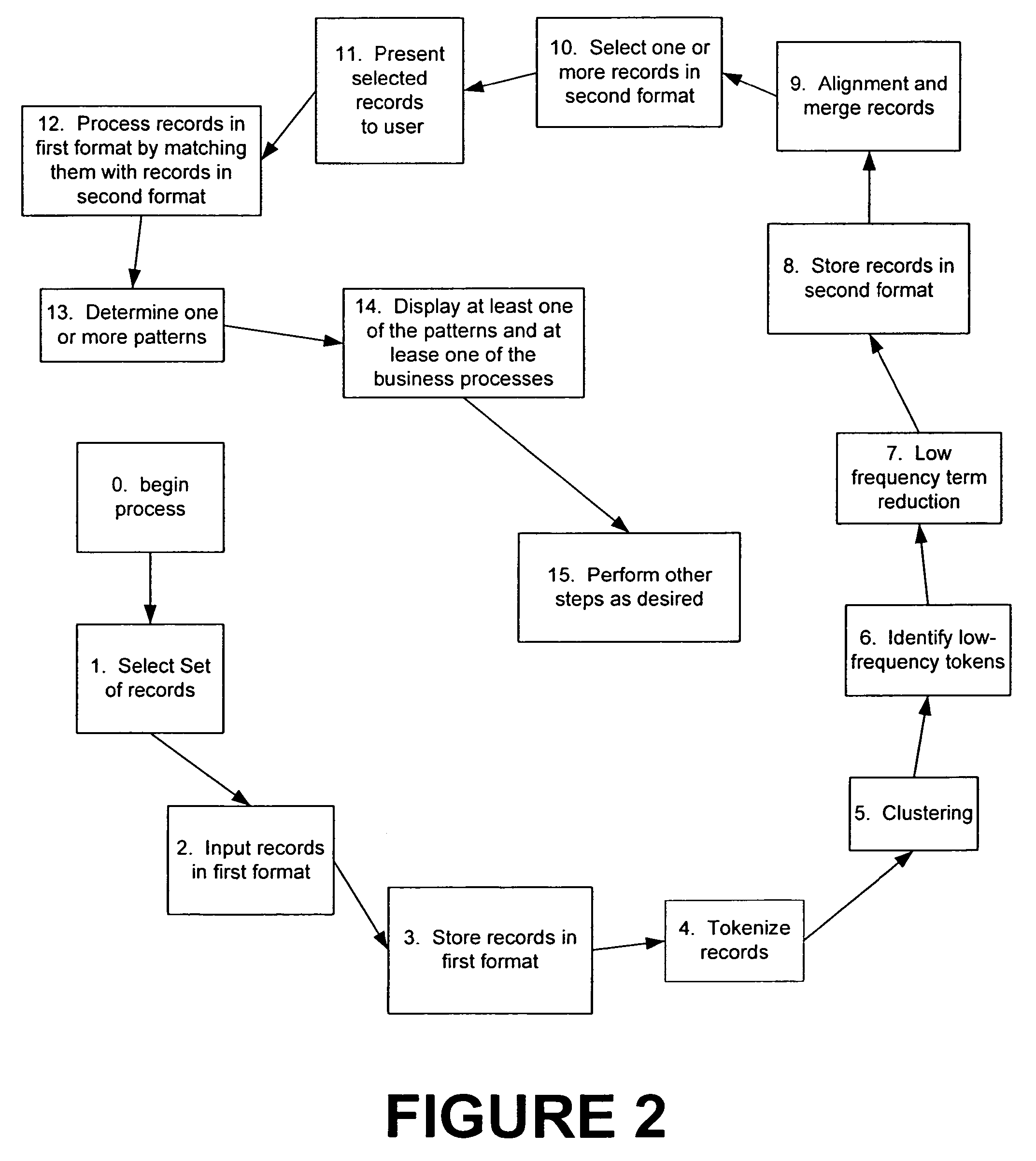
System and method for processing semi-structured business data using selected template designs
InactiveUS20050065967A1Easy to useEasy to analyzeDigital data information retrievalData processing applicationsSemi-structured dataTemplate design
A method for processing semi-structured data. The method includes receiving semi-structured data into a first format from a real business process. Preferably, the semi-structured data are machine generated. The method includes tokenizing the semi-structured data into a second format and storing the semi-structured data in the second format into one or more memories and clustering the tokenized data to form a plurality of clusters. The method also includes identifying a selected low frequency term in each of the clusters, and processing at least two of the clusters and the associated selected low frequency terms to form a single template for the at least two of the clusters. In a preferred embodiment, the method replaces the selected low frequency term with a wild card character.
Owner:OPENSPAN
Method of playing a poker game
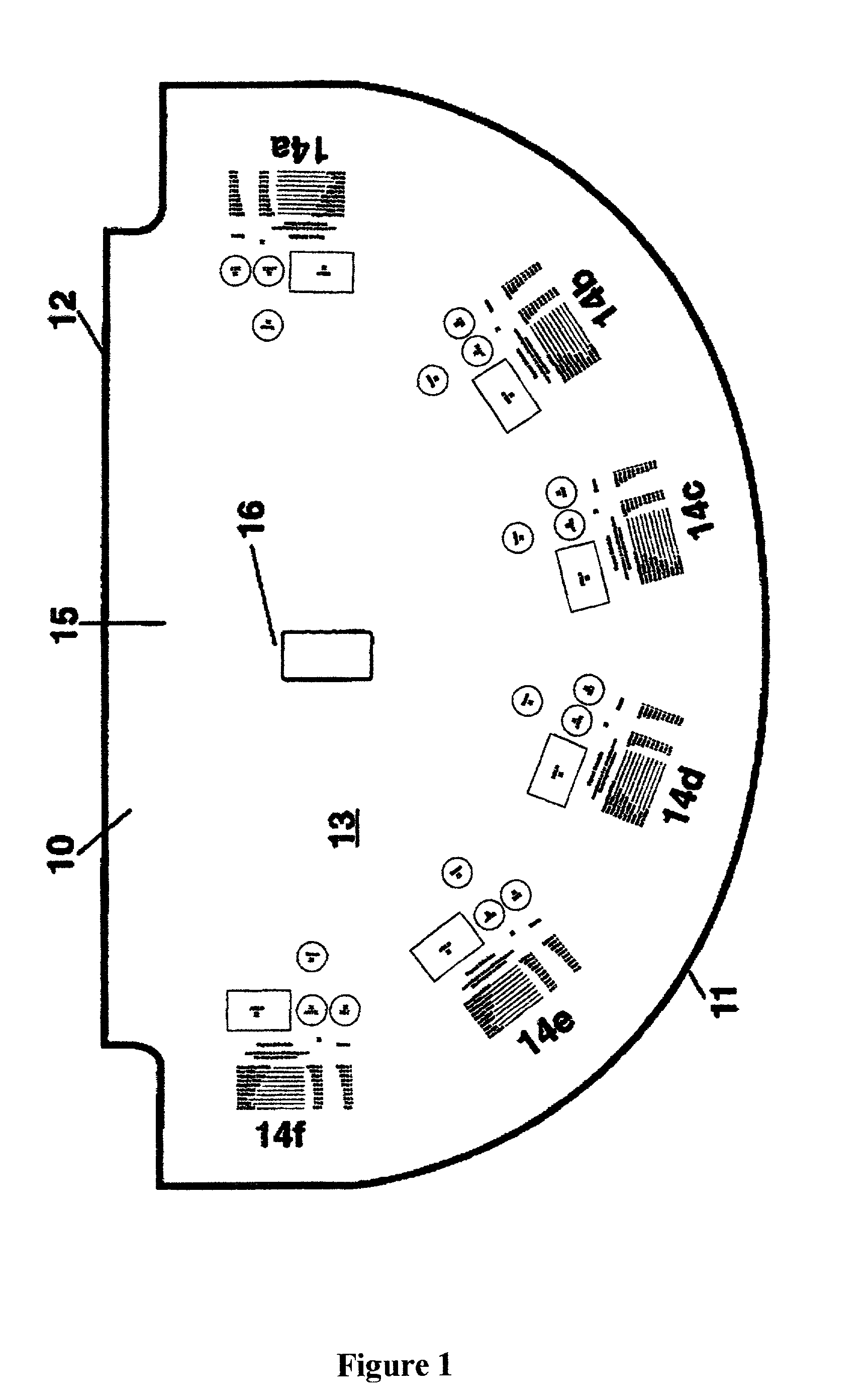
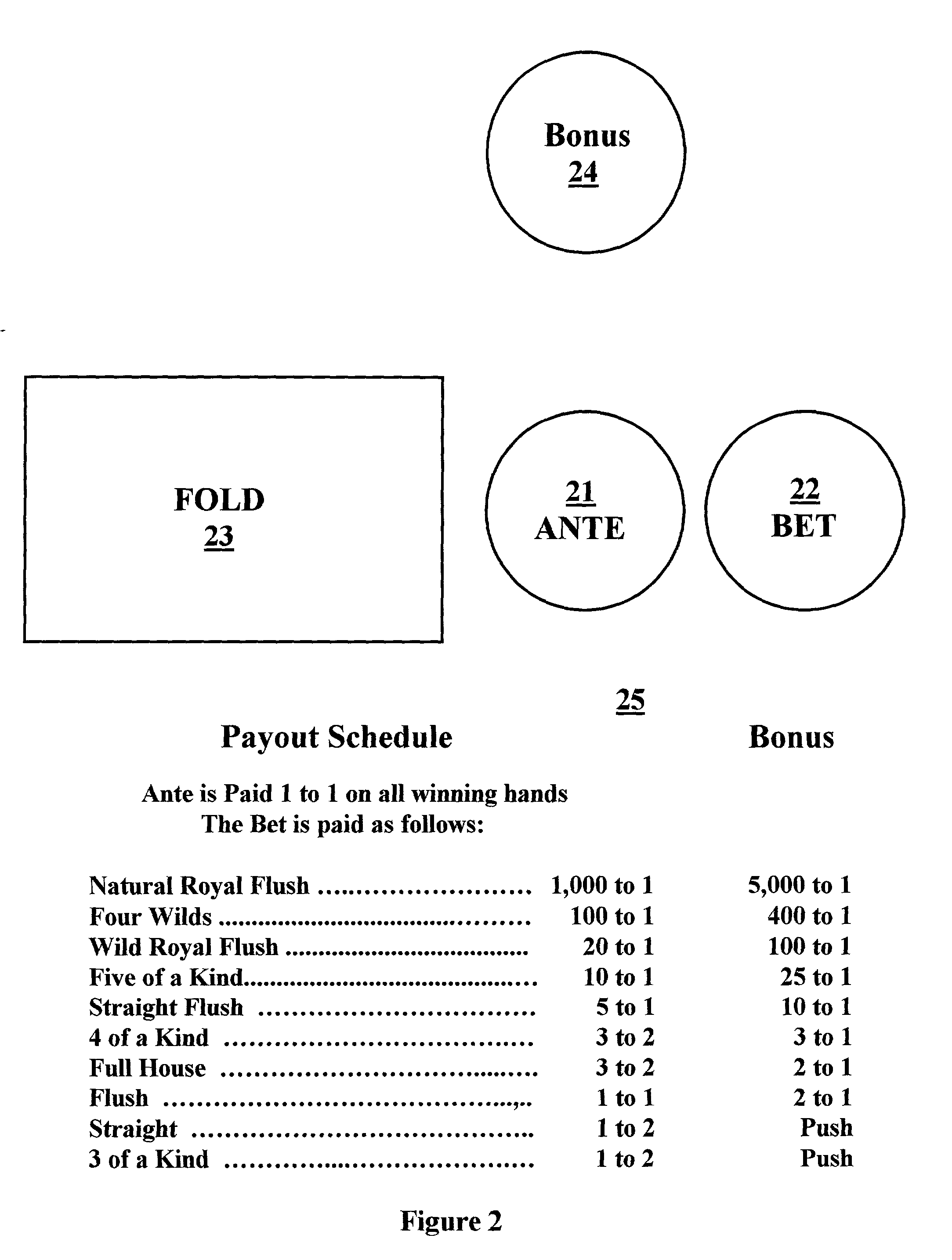
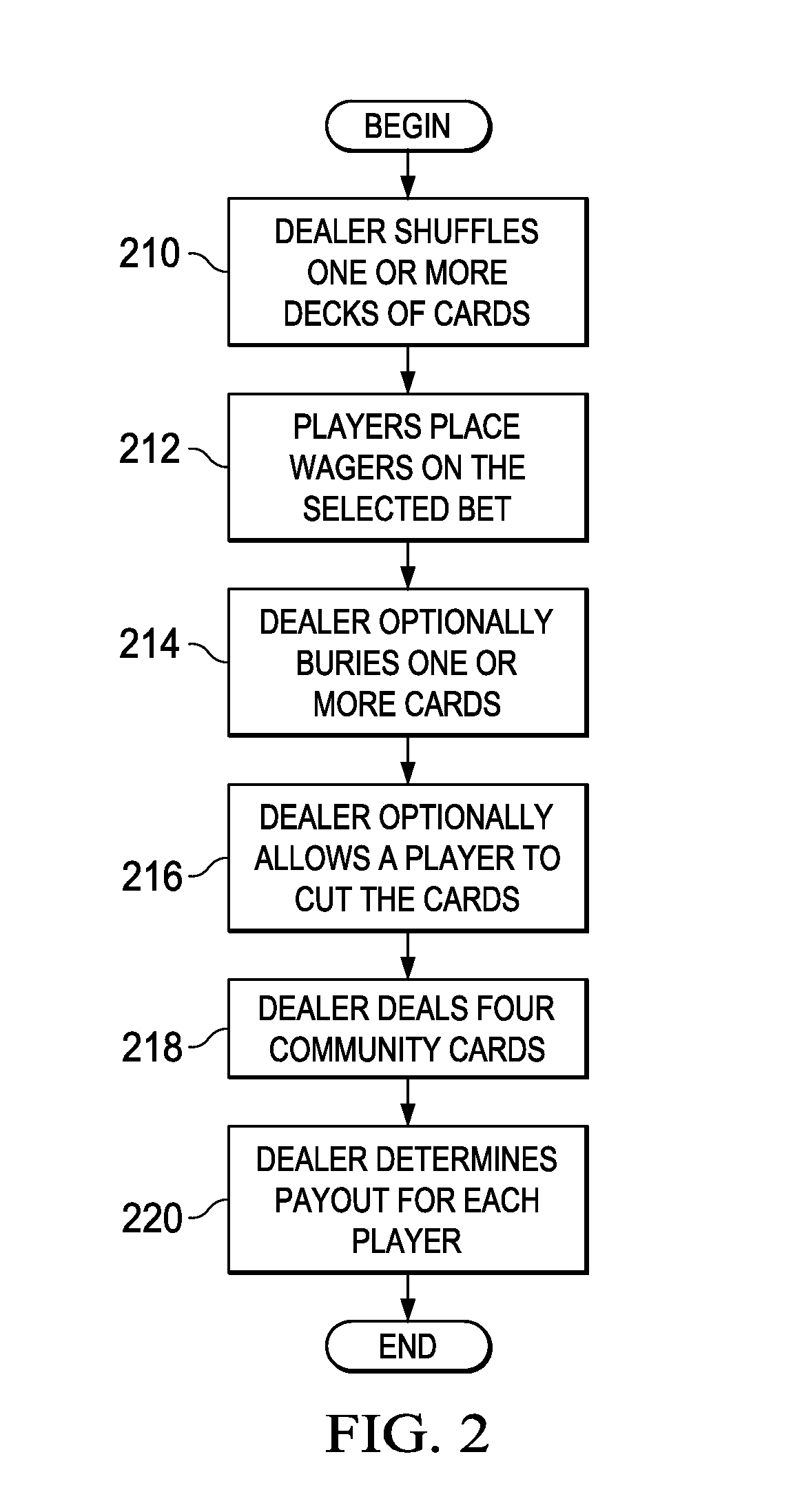
A poker variation game involving multiple wagers and the utilization of a wild card. Cards are dealt by the dealer, two cards face down to each player and one community wild card dealt face up. Players inspect their cards and determine whether to fold, or to make a second bet. The variation provides the improvements of allowing the rank of the wild card to be different for every deal, and provides that each player gets at least one wild card on every hand. All bets are ultimately resolved according to a predetermined payout schedule.
Owner:WELLS JEFFREY MICHAEL
Hardware-enforced loop-level hard zoning for fibre channel switch fabric
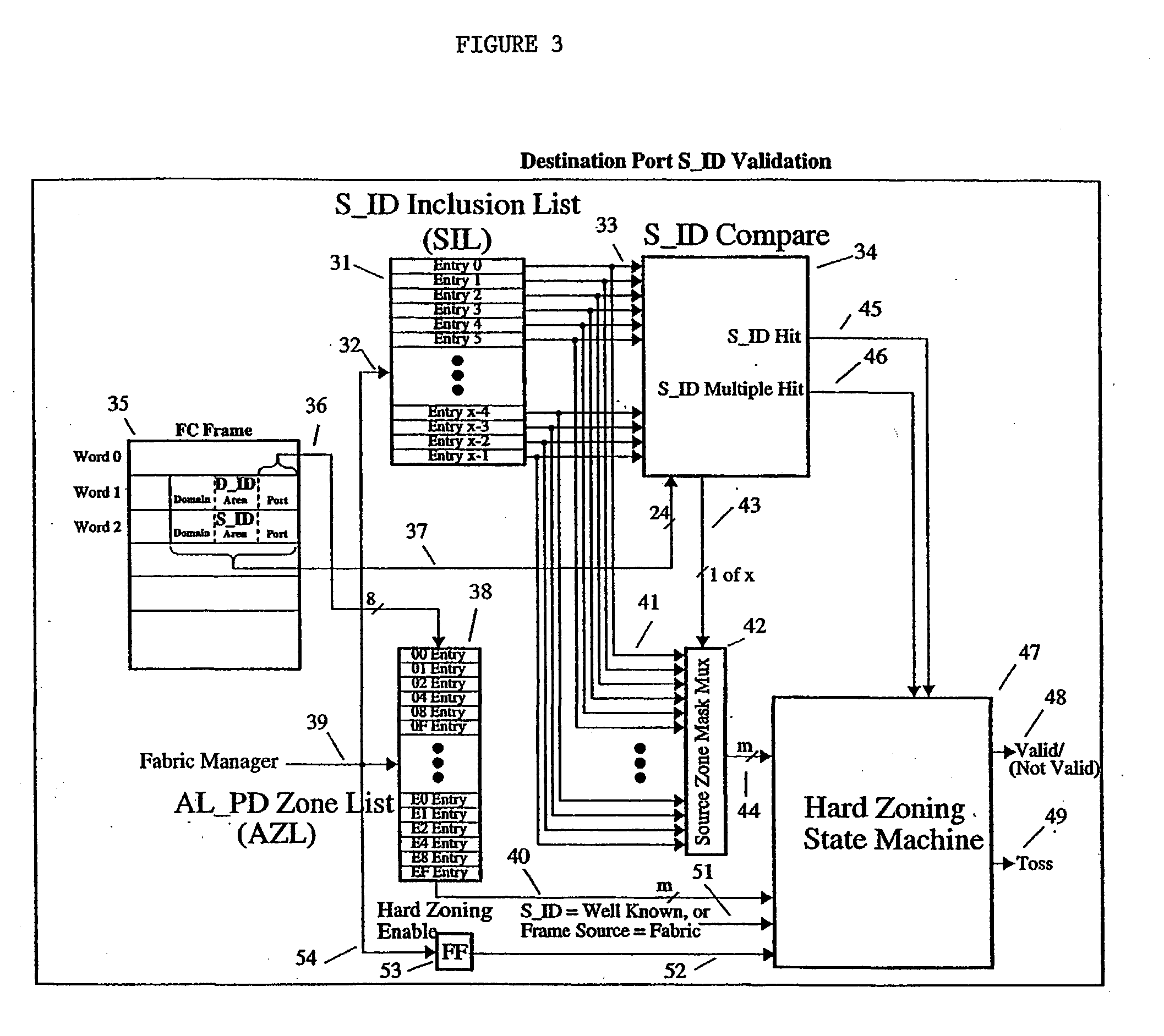
ActiveUS20030179748A1Data processing applicationsData taking preventionEngineeringFibre Channel switch
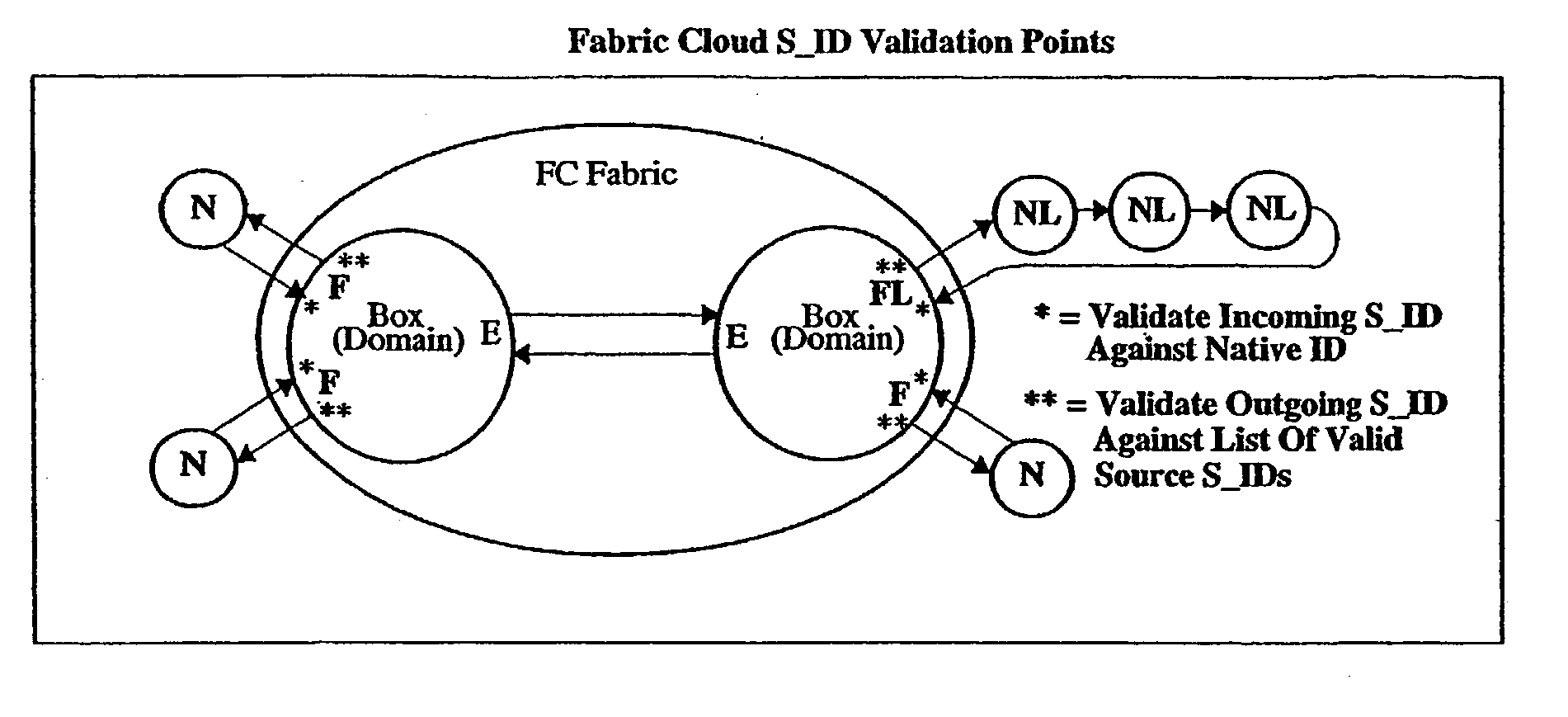
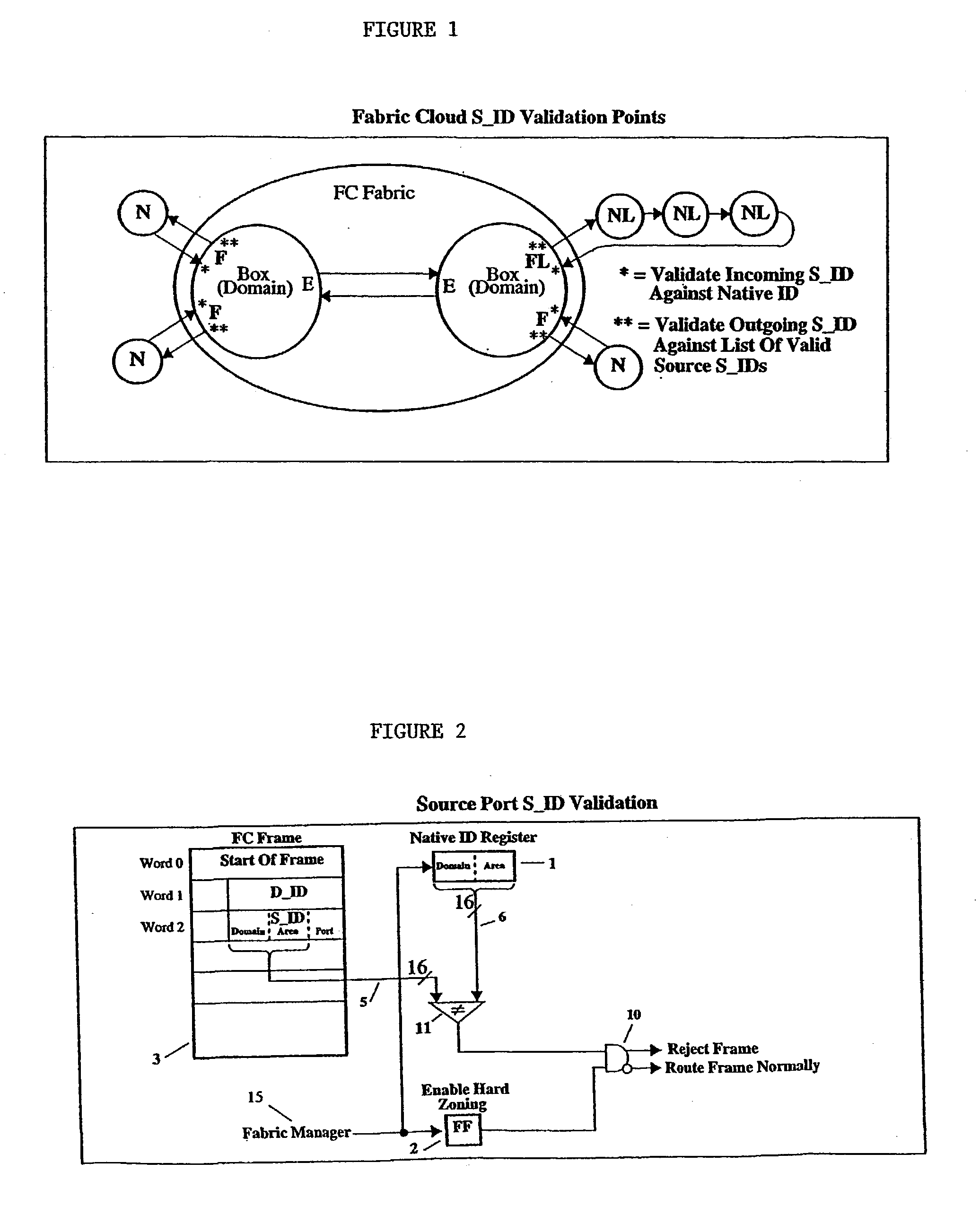
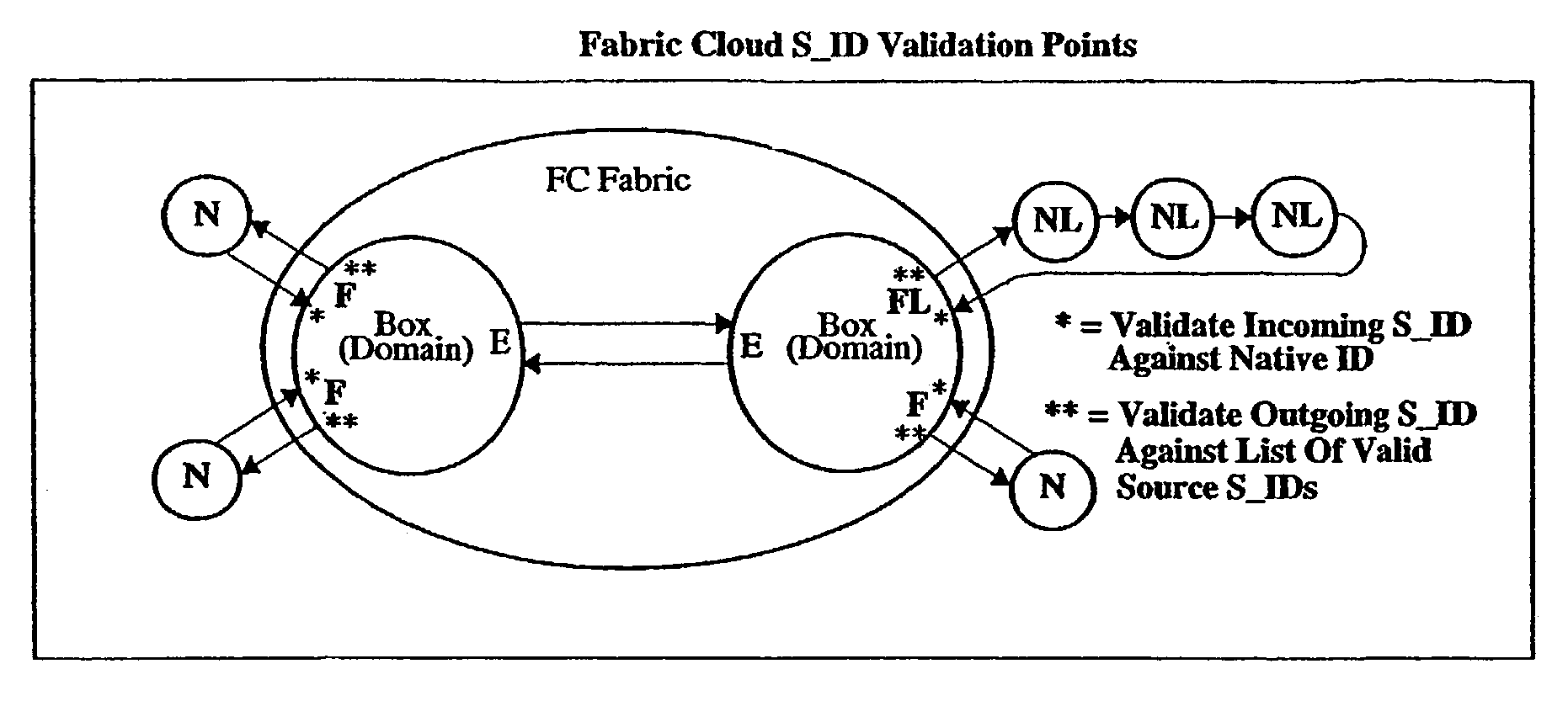
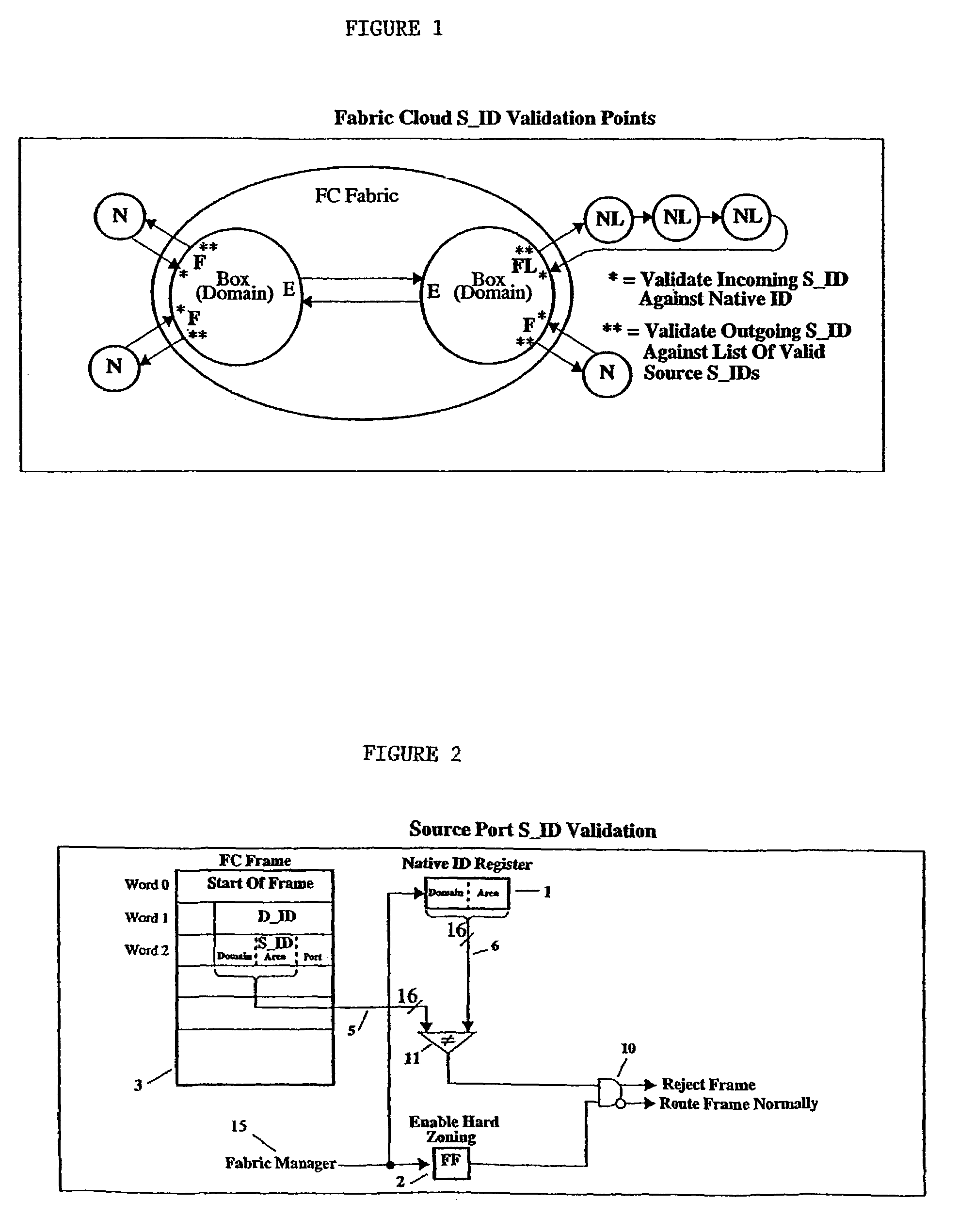
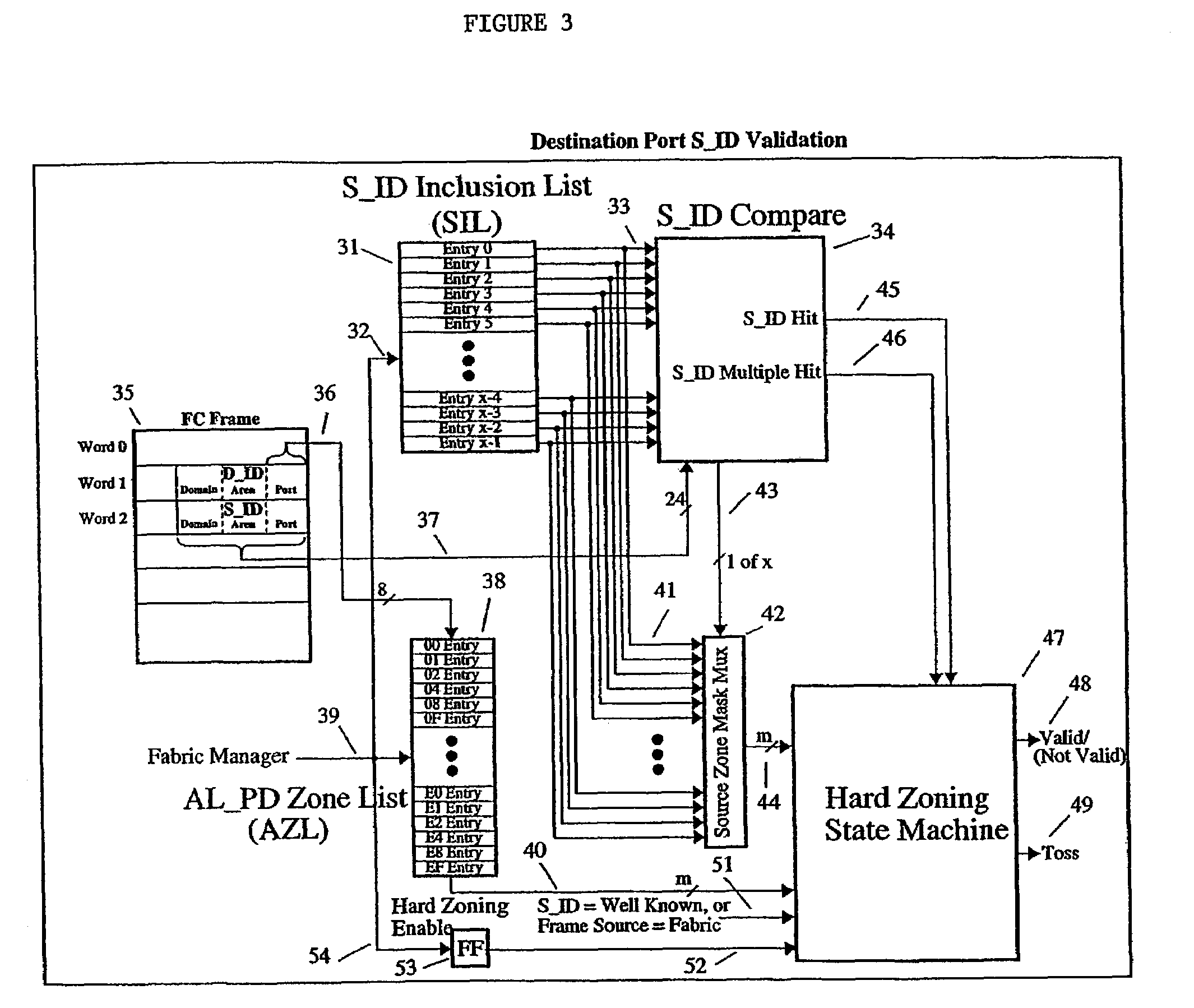
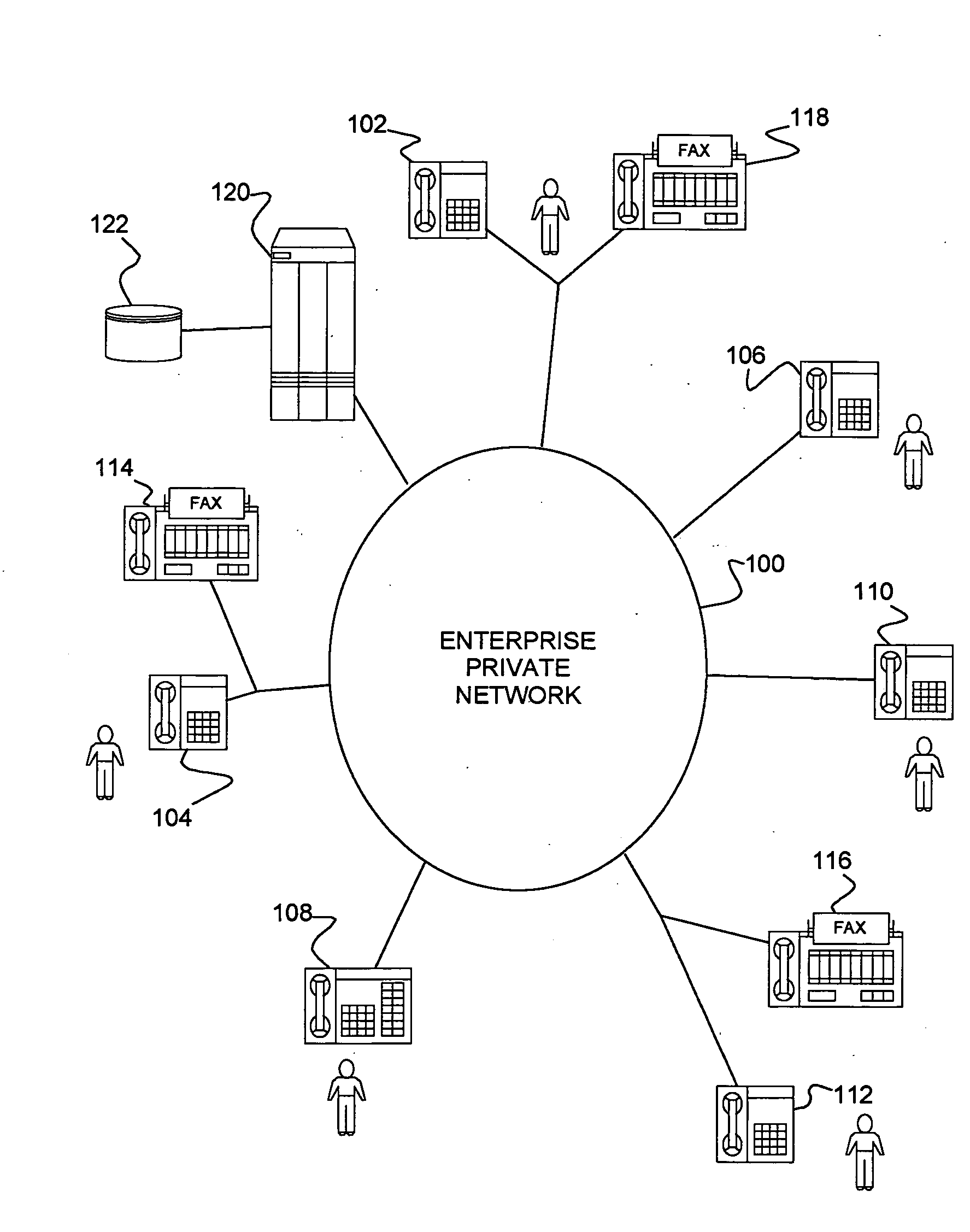
Hardware-enforced zoning is provided in Fibre Channel switches to protect against breaching of assigned zones in a switch network which can occur with software-based zoning techniques. The invention provides logic for performing a hardware-based validation of the Source ID S_ID of frames both at the point where the frame enters the Fibre Channel fabric, and at the point where the frame leaves the fabric. The S_ID is verified against an inclusion list or table of allowable S_IDs, which can be unique for each fabric port. The invention provides a way to increase the range of sources an inclusion table can express, by implementing wild cards, on an entry-by entry basis. If the S_ID is valid, it will enter the fabric and route normally. If invalid, the frame will not be routed but will be disposed of by the fabric according to FC rules. This prevents incorrect S_IDs from breaching the table-driven zoning at the point where frames exit the fabric, to prevent unauthorized access to devices connected to the switch network.
Owner:QLOGIC LLC
Method, system and portable consumer device using wildcard values
A portable consumer device is disclosed. The portable consumer device includes a body and a computer readable medium coupled to the body. The computer readable medium comprises a data string including one or more wildcard values. The data string is specifically associated with the consumer. For example, the data string may represent one or more products that the consumer prefers to use.
Owner:VISA USA INC (US)
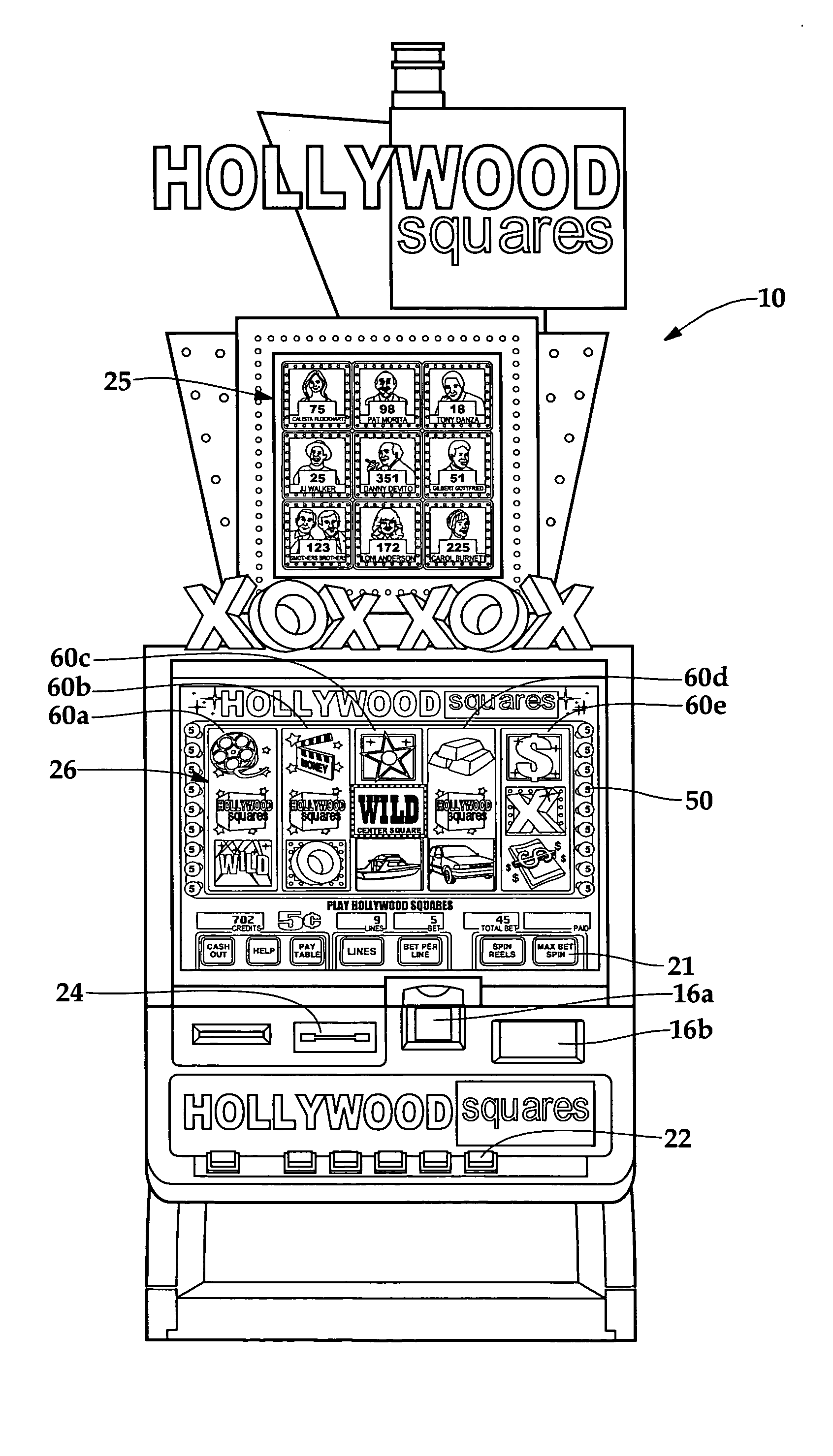
Video gaming system with wild card system and bonus system
InactiveUS7559837B1Novel featuresCard gamesApparatus for meter-controlled dispensingDisplay deviceWild card
A gaming system for producing a unique bonusing event is described. The method includes the step of a player placing a wager on a reel-slot-type video game and displaying a plurality of randomly selected game symbols on the game display. Upon the occurrence of a triggering event, such as a winning or losing combination of symbols, randomly selecting a number of wild symbol positions, and location of the wild symbol positions on the screen display. The wild symbol positions are then converted to wild symbols, and the game is scored using the original game symbols and wild symbols.
Owner:IGT
Hardware-enforced loop-level hard zoning for fibre channel switch fabric
ActiveUS7248580B2Improve integrityImprove securityData processing applicationsData taking preventionFibre Channel switchComputer science
Hardware-enforced zoning is provided in Fibre Channel switches to protect against breaching of assigned zones in a switch network which can occur with software-based zoning techniques. The invention provides logic for performing a hardware-based validation of the Source ID S_ID of frames both at the point where the frame enters the Fibre Channel fabric, and at the point where the frame leaves the fabric. The S_ID is verified against an inclusion list or table of allowable S_IDs, which can be unique for each fabric port. The invention provides a way to increase the range of sources an inclusion table can express, by implementing wild cards, on an entry-by entry basis. If the S_ID is valid, it will enter the fabric and route normally. If invalid, the frame will not be routed but will be disposed of by the fabric according to FC rules. This prevents incorrect S_IDs from breaching the table-driven zoning at the point where frames exit the fabric, to prevent unauthorized access to devices connected to the switch network.
Owner:QLOGIC LLC
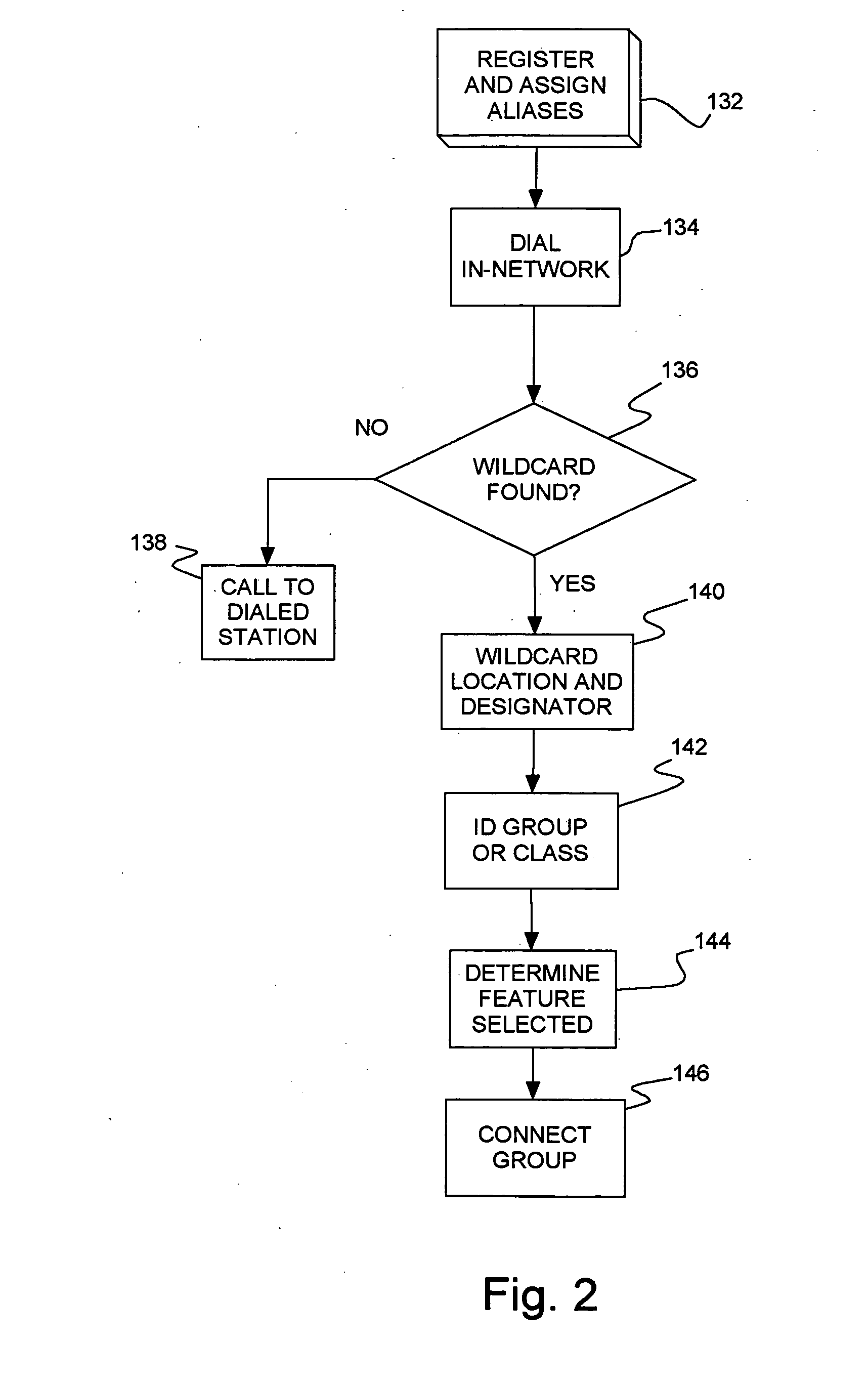
Private communications network with wildcard dialing
InactiveUS20080043972A1Simplify usingSpecial service for subscribersPrivate communicationConference call
A private communications network and method of managing calls in a private communications network. Connected communications devices register with the network and are assigned aliases, with aliases for groups of registered devices sharing one or more common digits. Dialing strings for in-network calls are monitored for inclusion of a wildcard (e.g., *) which are treated as a “don't care.” The wildcard invokes group features, such as placing a conference call, invoking a hunting feature and invoking a pickup feature. The call is distributed / connected to the group corresponding to the remaining digits.
Owner:UNIFY INC
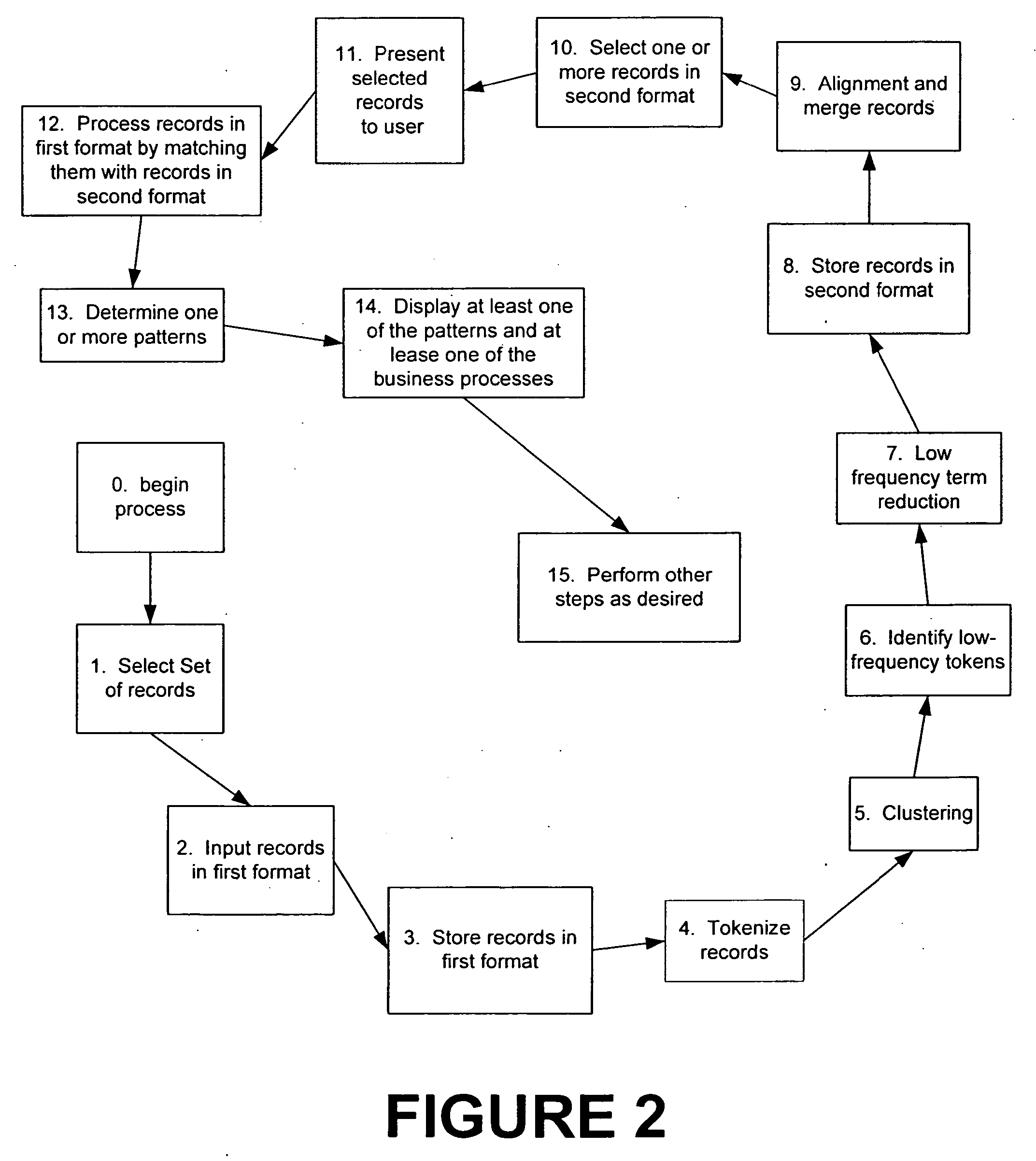
System and method for processing semi-structured business data using selected template designs
InactiveUS7389306B2Poor classification resultLow costDigital data information retrievalData processing applicationsSemi-structured dataTemplate design
Owner:OPENSPAN
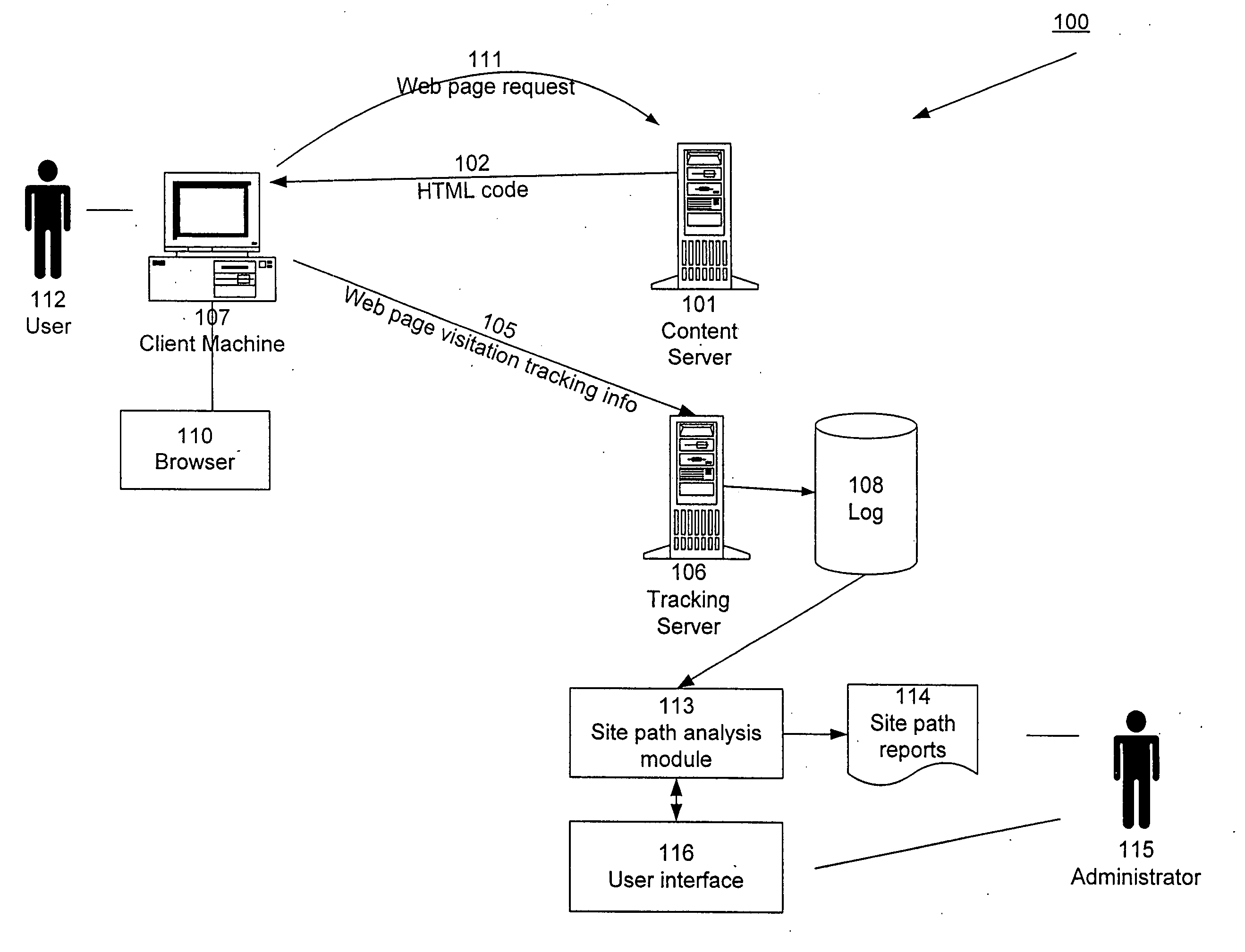
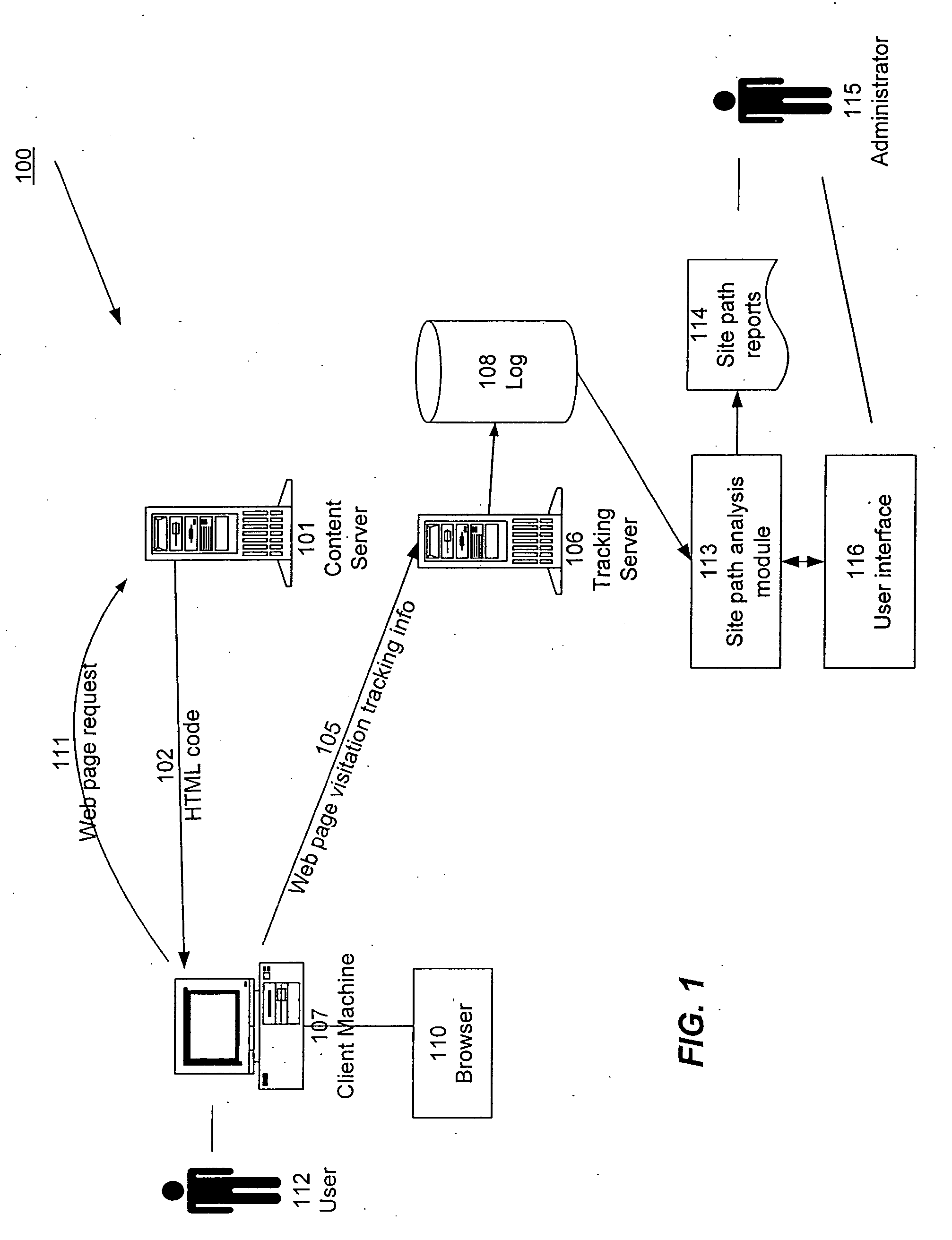
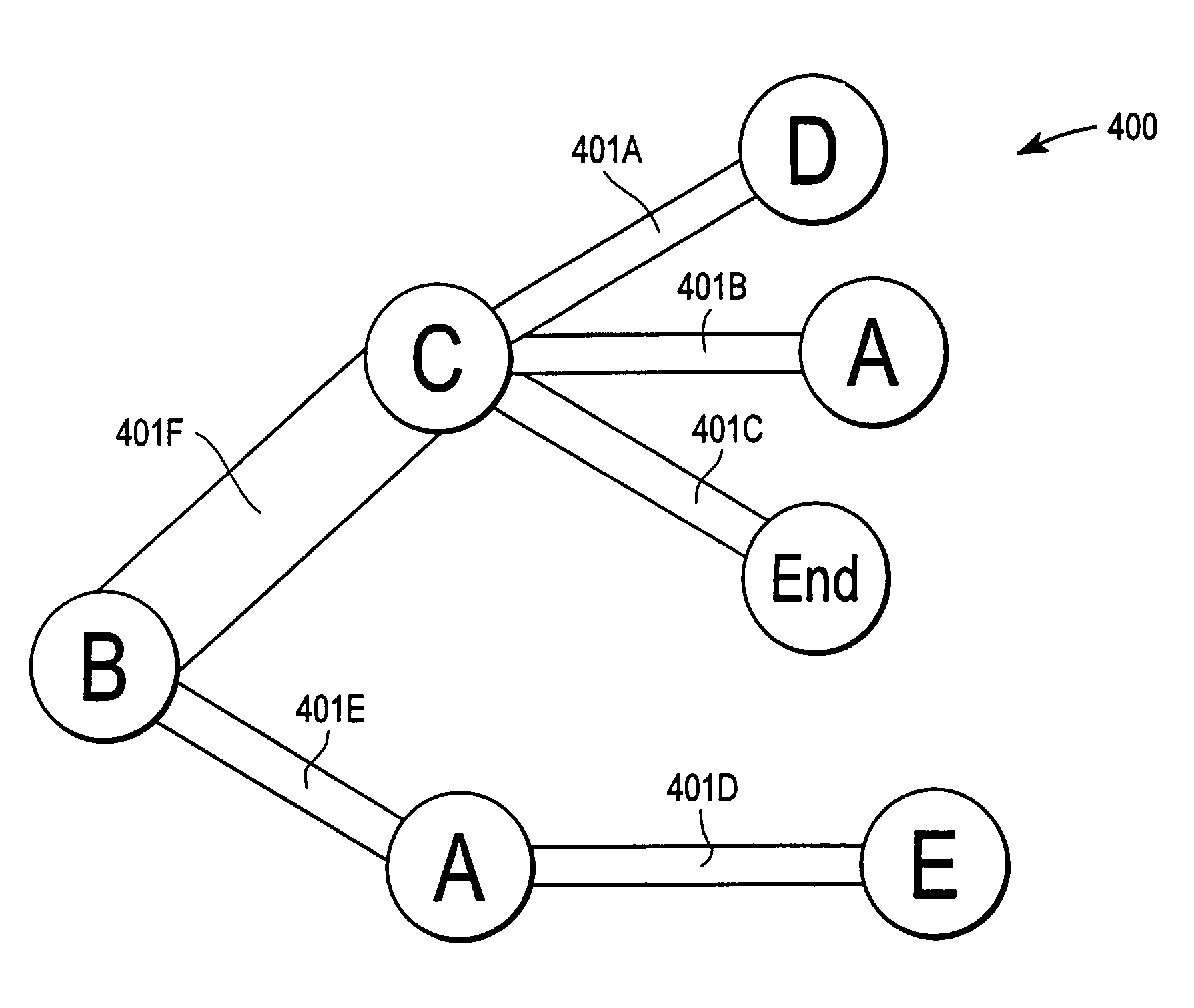
Capturing and presenting site visitation path data
ActiveUS20060149728A1Easy to understandMeaningful analysisDigital data information retrievalHardware monitoringWeb siteFrequency of occurrence
Node sequence data, such as website visitation records, are filtered, analyzed, and summarized in reports. An administrator can designate particular target paths of interest in terms of a checkpoint node sequence. Node sequences are filtered based on the checkpoint node sequence, without regard to any additional or tangential nodes appearing in the sequences. In addition, node sequences can be specified in terms of specific nodes of interest along with wild cards. Reports depict the relative frequency of occurrence of node sequences using visual indicators such as line thickness and / or color.
Owner:ADOBE INC
Gaming machine having dynamic bonus feature
InactiveUS6939228B2Enjoyable for userCard gamesApparatus for meter-controlled dispensingEngineeringGame element
A gaming machine and a method of playing the game which includes randomly displaying a plurality of game elements (20) in a grid (14) of cells (16) to produce a normal random display with one element (20) in each of the cells (16). A bonus random display of the game elements (20) is initiated in response to a triggering combination (30) of three apple symbols appearing in the cells (16). Once this occurs, a sound is played to convey the beginning of the bonus round, and the sound is preferably of bees. In the bonus round, a plurality of the cells (16) is designated as wild cells (34) for the bonus random display and a wild card (40) is positioned over the wild cell (34) such that the wild card (40) conceals the game element (20) disposed within the wild cell (34). The bonus random display is repeated for a predetermined number of rounds.
Owner:KONAMI GAMING
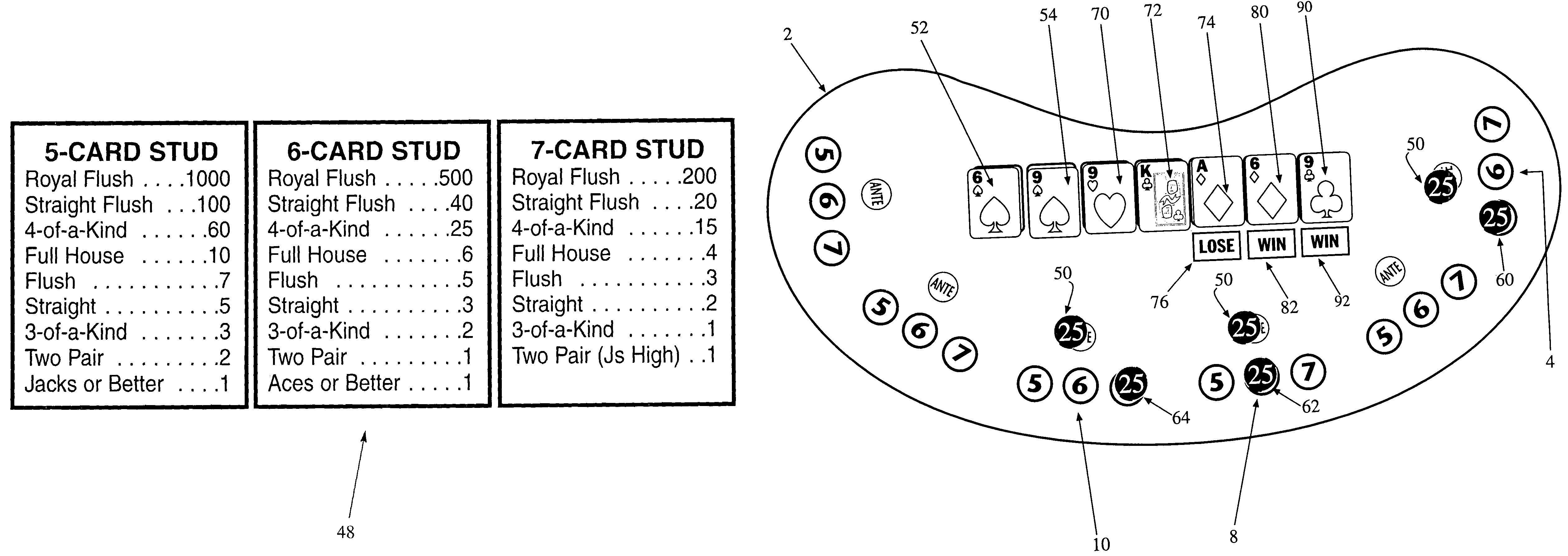
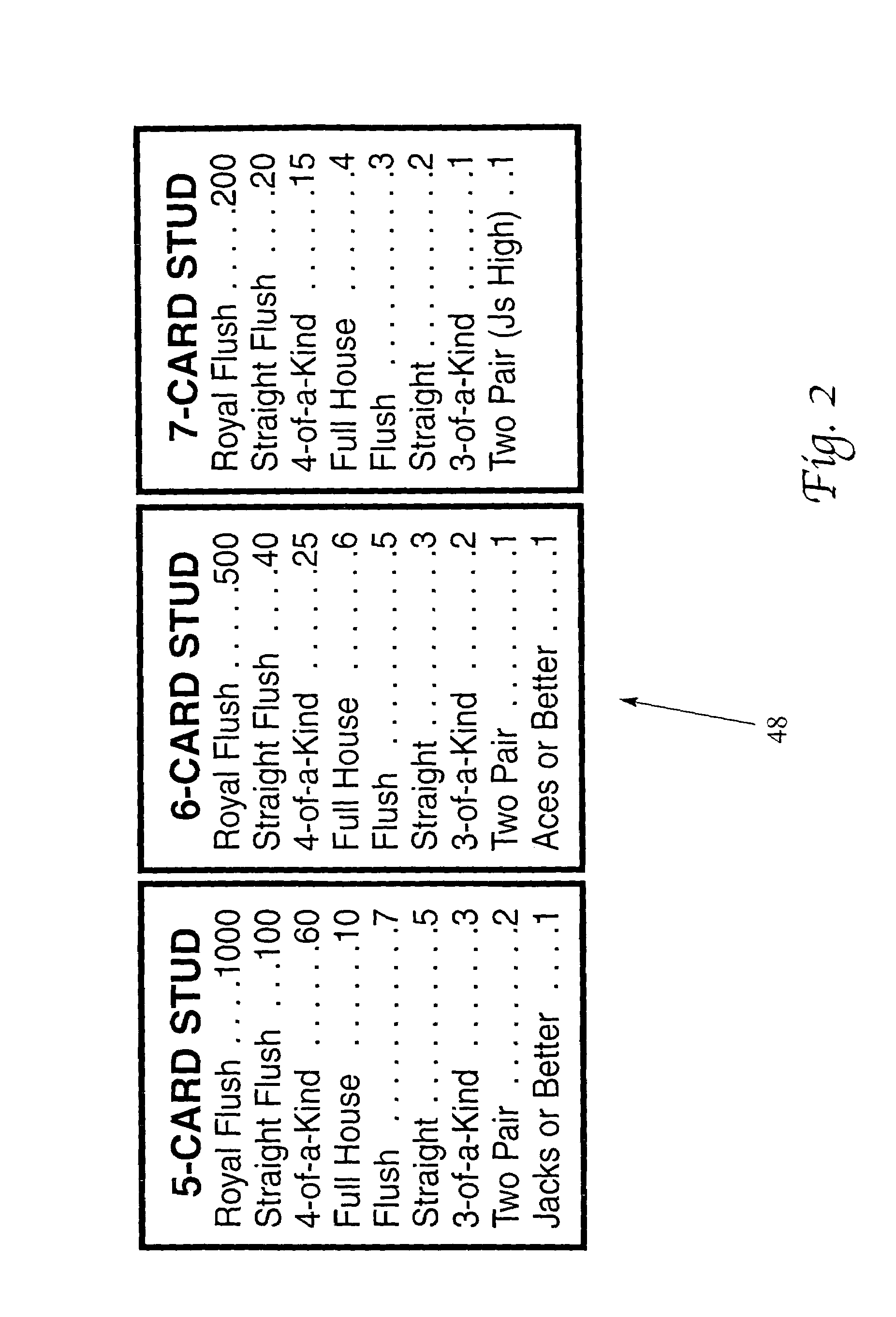
Casino poker table game with choice of stud hands
A player places an ante wager to participate in the play of the underlying card game. An initial deal of at least one communal partial hand of poker consisting of at least one card is dealt from a single (or multiple) standard deck(s) of cards, standard deck(s) of cards with certain cards removed, or standard deck(s) of cards that is augmented by wild cards or jokers, especially with a partial communal hand consisting of two face-up cards. The player is directed to consider the partial hand and is then directed to choose to play the partial hand as either a 5-card stud game, a 6-card stud game, or a 7-card stud game by placing an additional Play wager on a particular Play Bet circle (i.e., the 5-card game, the 6-card game or the 7-card stud game. Three additional community cards are then dealt face up to complete the 5-card stud hand, and subsequently a 4th and 5th community card. Each wagered hand would then be compared to a predetermined pay table (for the specific game play selected by the player) and winnings would be awarded for certain predetermined combinations or ranks.
Owner:IGT
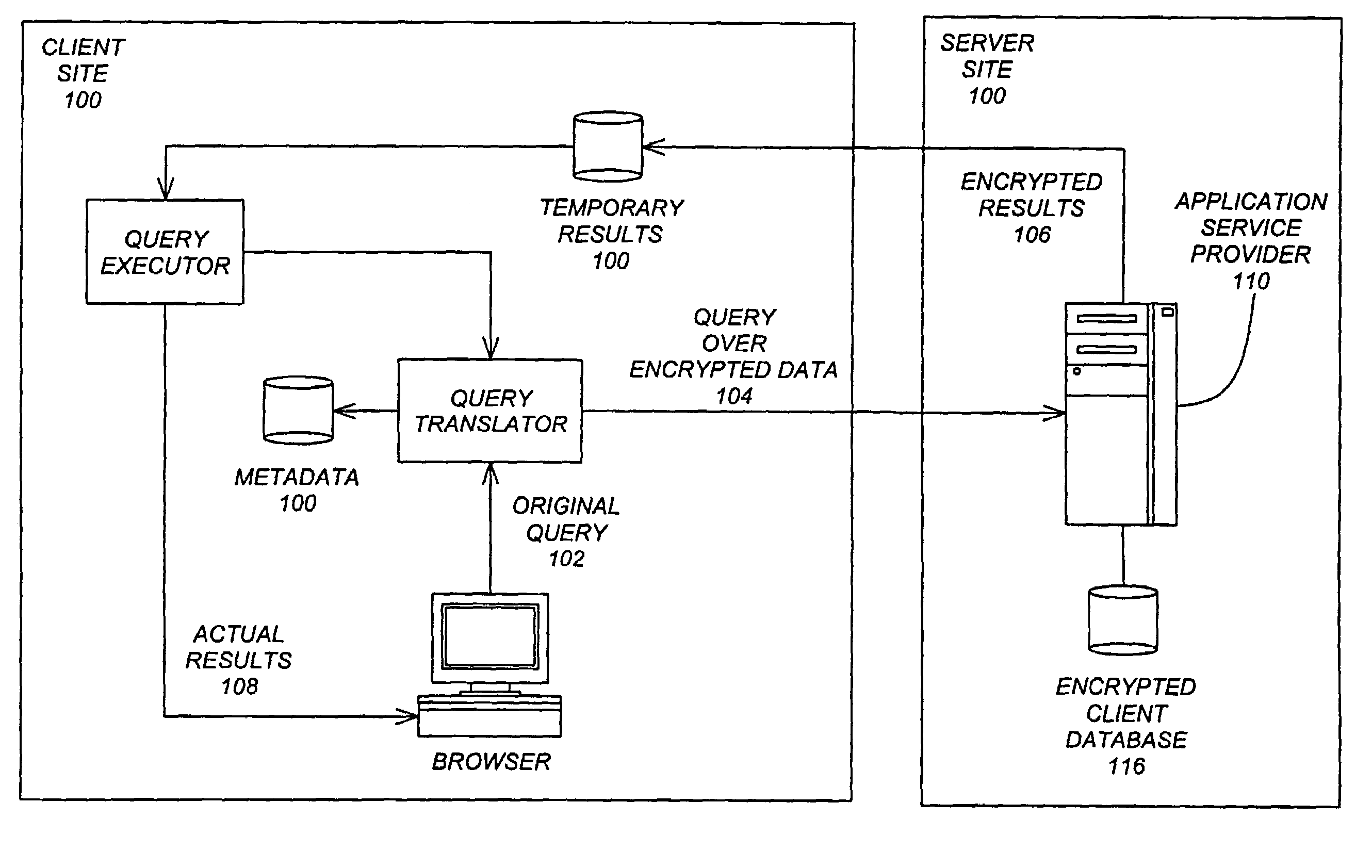
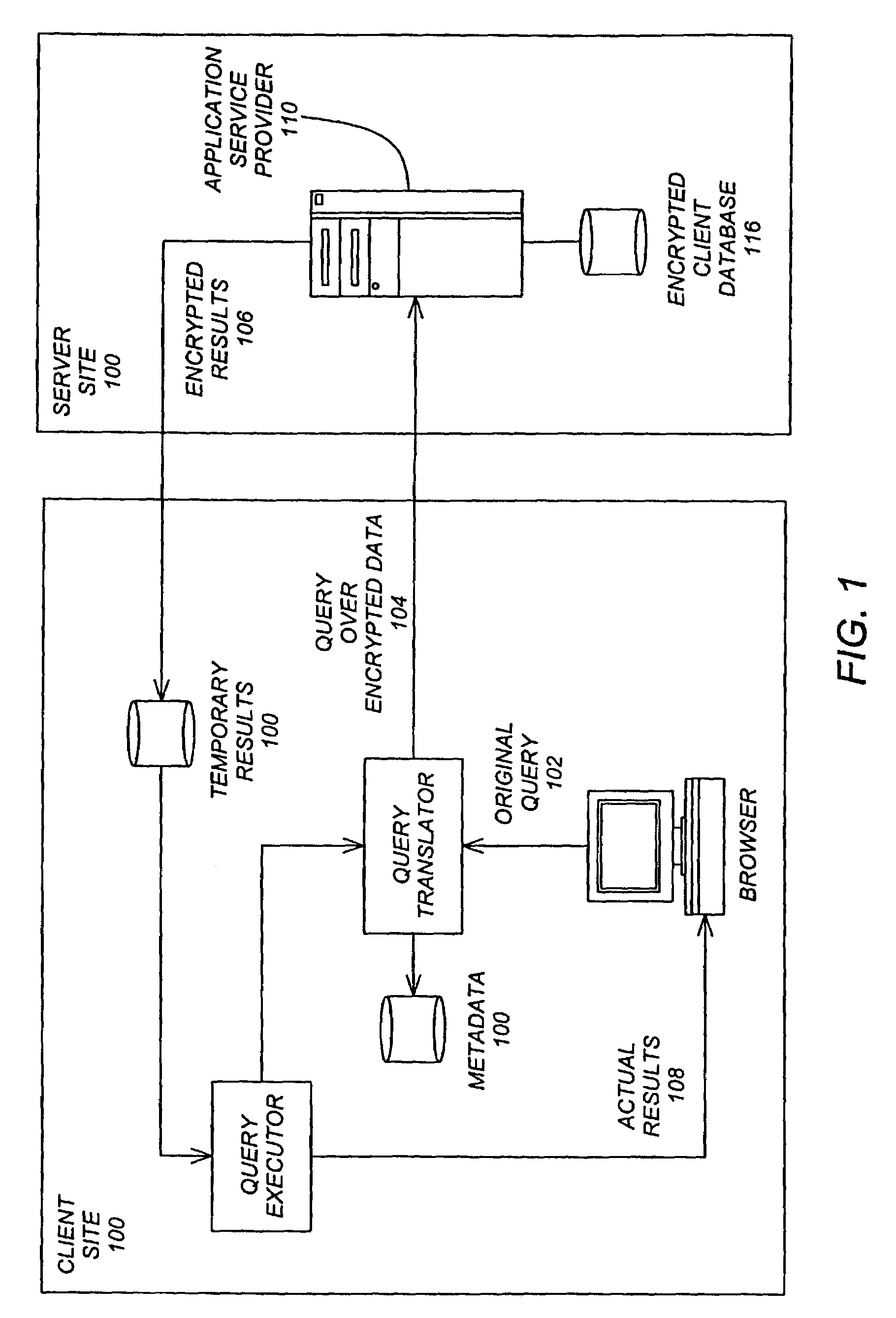
Querying encrypted data in a relational database system
ActiveUS7500111B2Key distribution for secure communicationDigital data information retrievalRelational databaseClient-side
A client-server relational database system, wherein data from the client computer is encrypted by the client computer and hosted by the server computer, the encrypted data is operated upon by the server computer, using one or more operators selected from a group of operators comprising: (a) inequality logic operators, (b) aggregation operators, and (c) wildcard matching operators, to produce an intermediate results set, the intermediate results set is sent from the server computer to the client computer, and the intermediate results set is decrypted and filtered by the client computer to produce actual results. The group of operators is limited because the encrypted results set, when decrypted, includes inaccuracies therein. The client computer applies a set of correction procedures to the decrypted results set to remove the inaccuracies therein.
Owner:IBM CORP
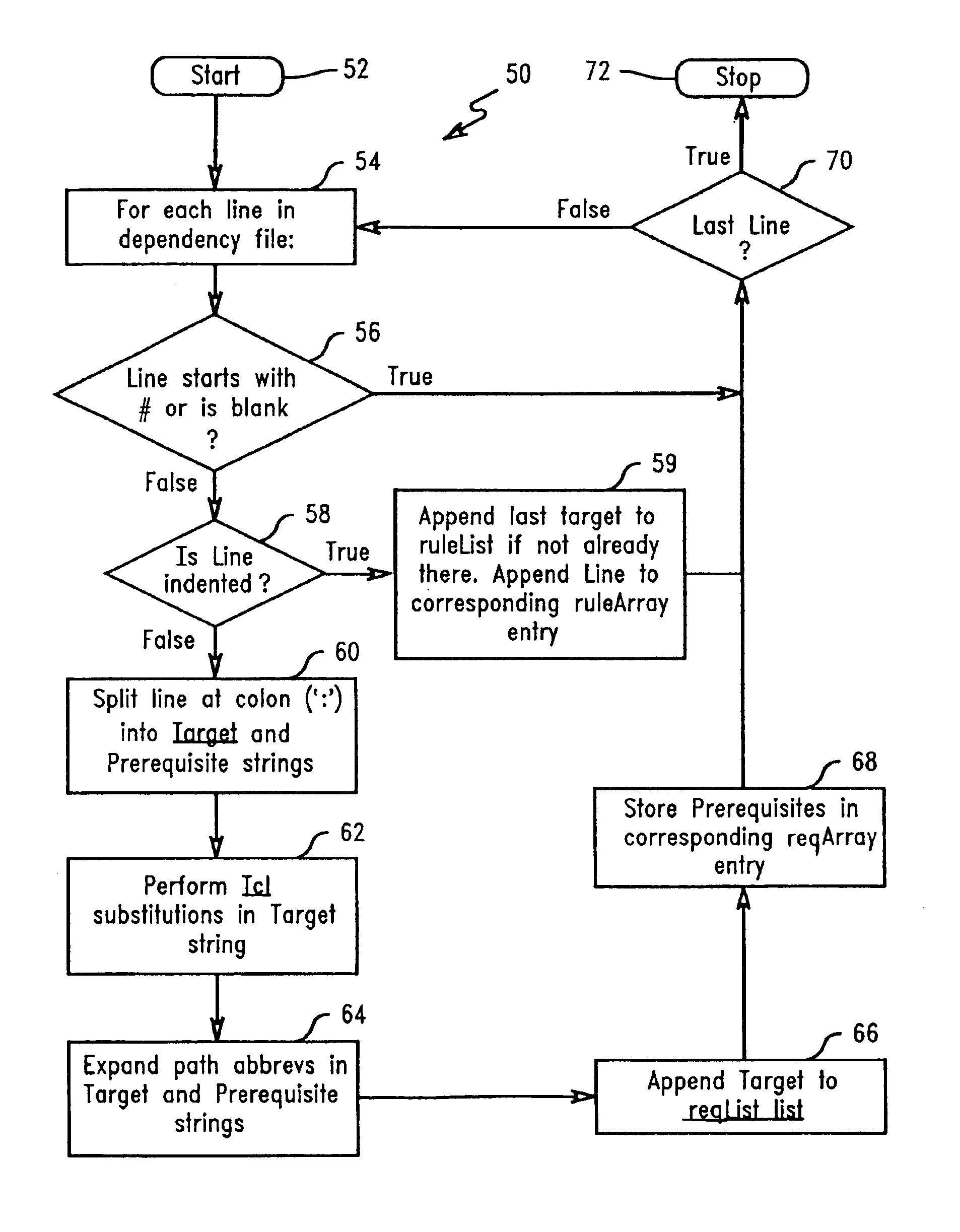
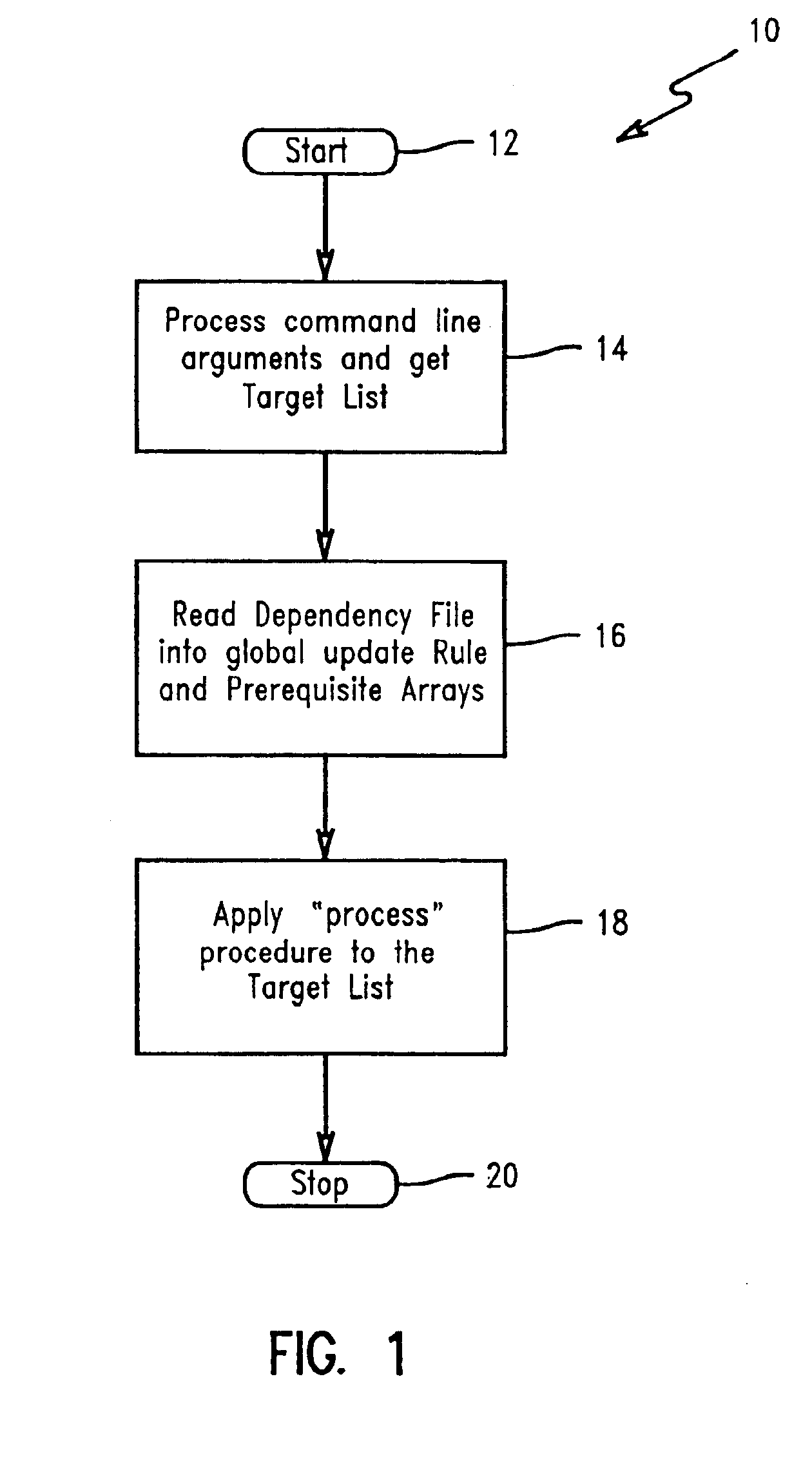
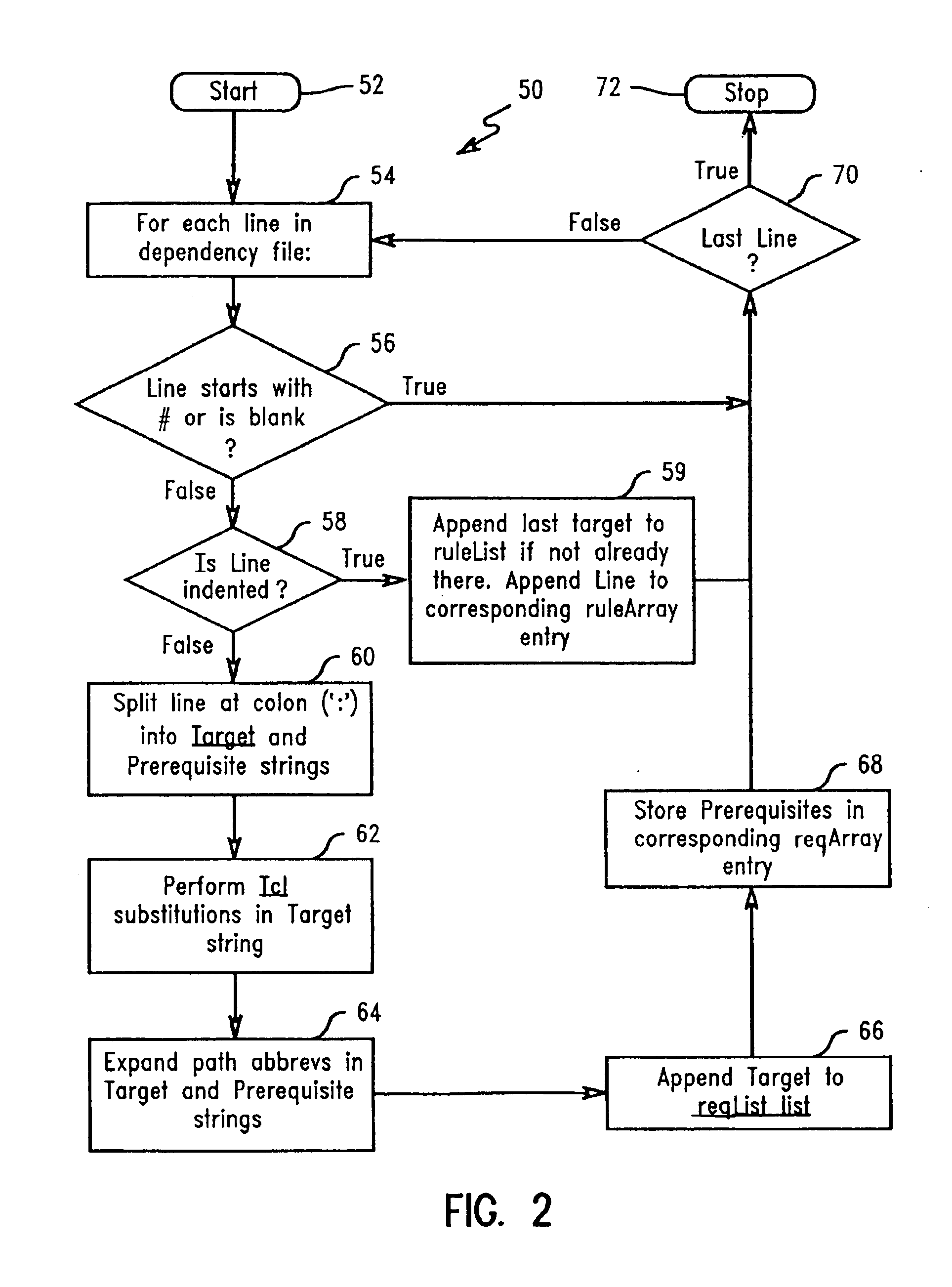
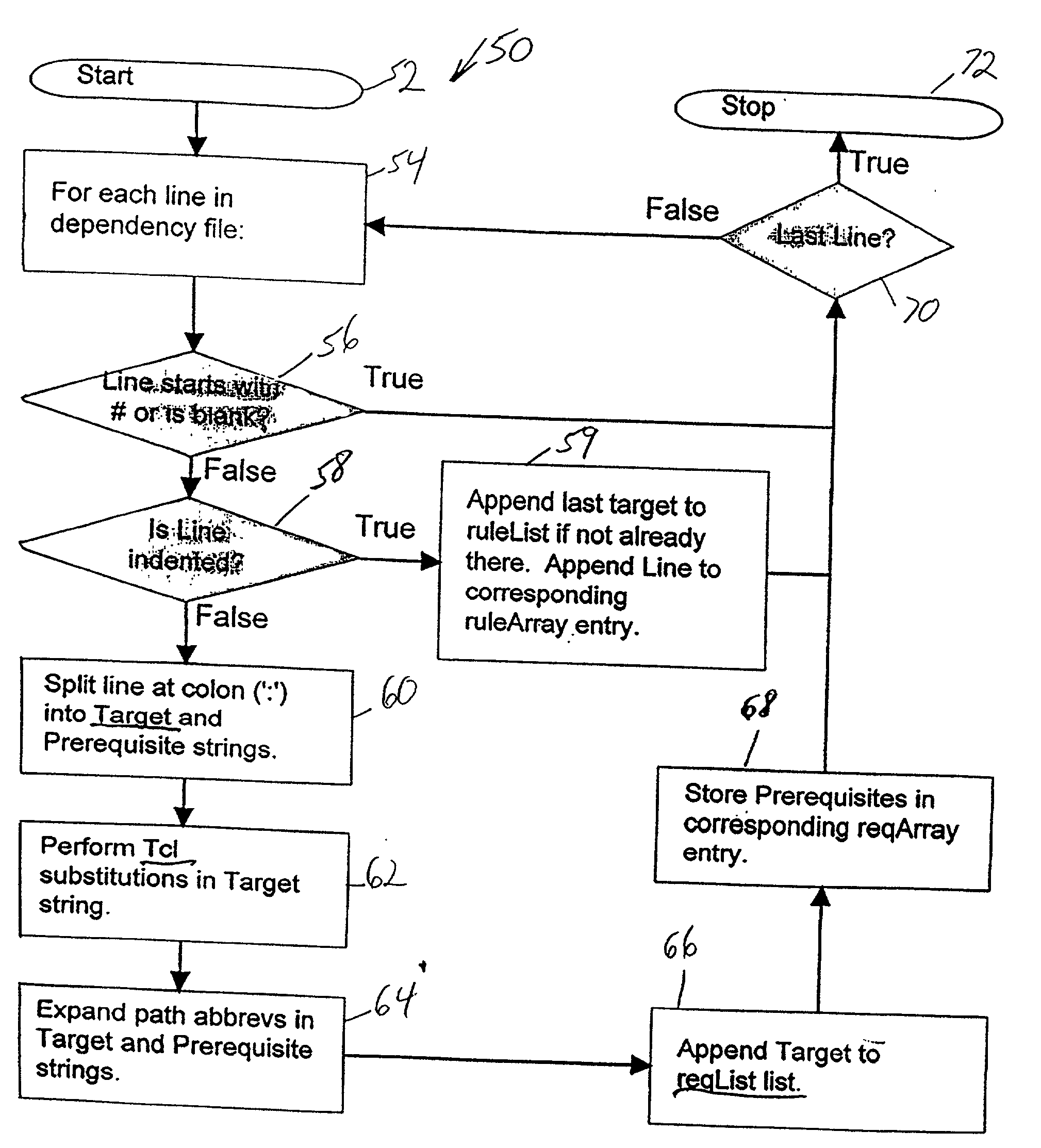
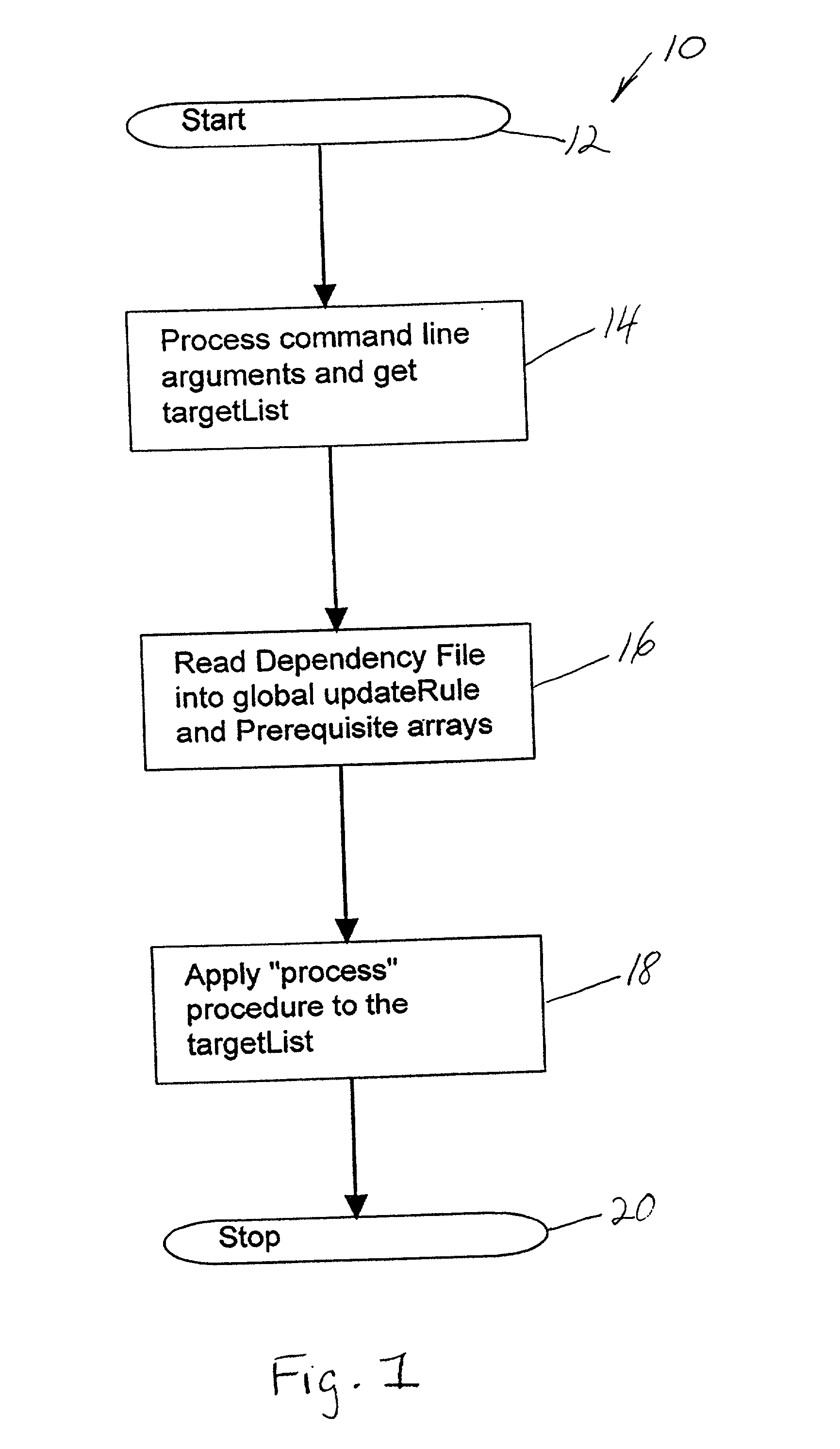
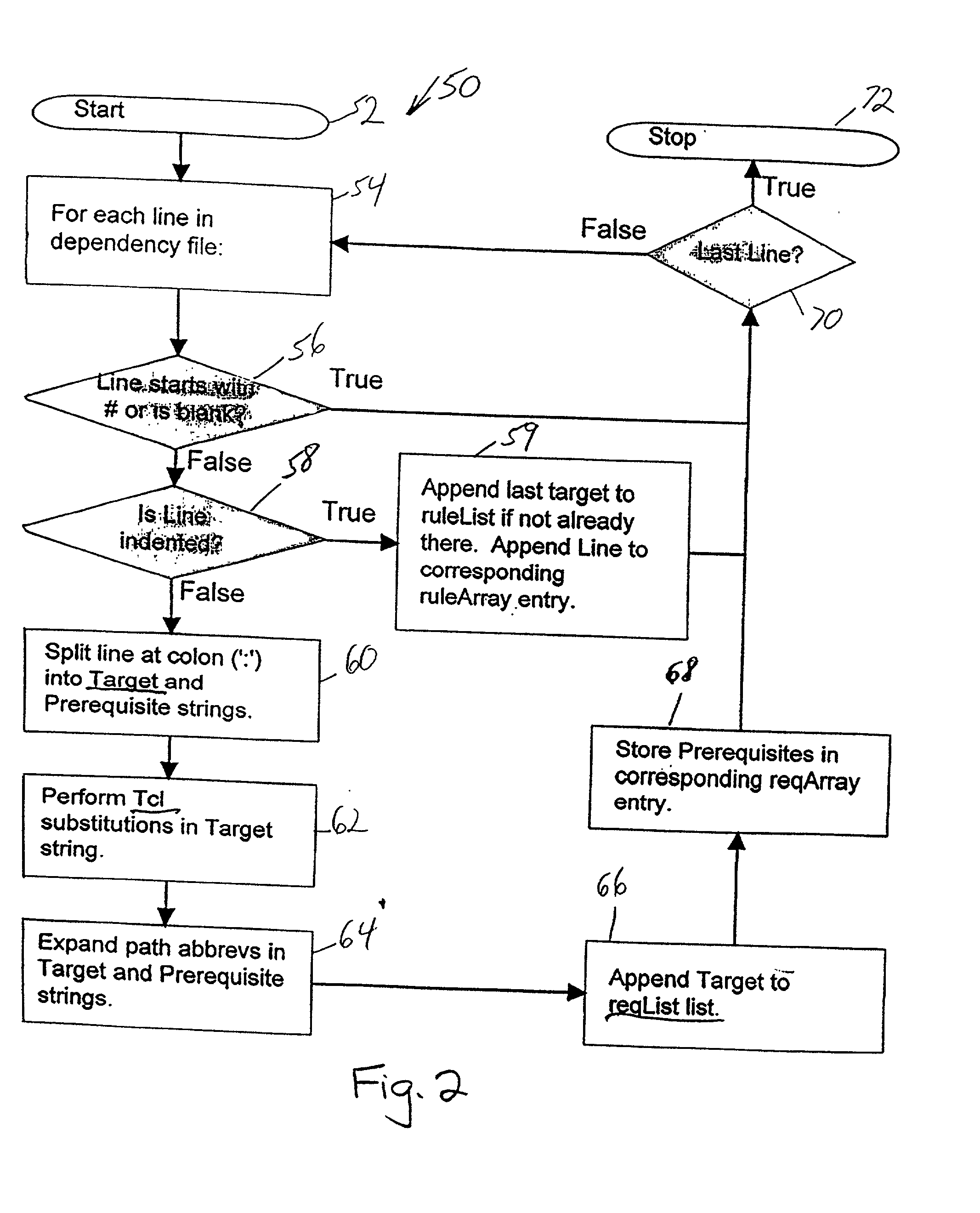
Dependency specification using target patterns
InactiveUS6961931B2Version controlSpecific program execution arrangementsScripting languageObject code
A method for generating changes and updating existing files and code in a computer program, wherein the method comprises reading existing source code and existing object code in the computer program. Then, reading a plurality of associated files to the source code, and executing a utility program. The utility program updates the target source code and the object code associated with the target source code. Targets may be specified with either glob-type patterns using the standard shell wild cards, or regular expression patterns. The utility program also includes scripting language and can specify particular characters to search for in the target code and the associated code. A target code list is generated for the source code and the associated object code by using the utility program, and the target code and the associated code are updated by employing a search technique specified in the utility program.
Owner:IBM CORP
Wagering game with predetermined location for wild-card feature
InactiveUS20050288090A1Card gamesApparatus for meter-controlled dispensingArray data structureEngineering
Owner:BALLY GAMING INC
System and method for providing user input information to multiple independent, concurrent applications
ActiveUS20050185773A1Sure easyAutomatic call-answering/message-recording/conversation-recordingCalled number recording/indicationKey pressingUser input
In a system for providing user input information to multiple independent, concurrent applications, the applications send subscription messages to a device receiving user input such as a telephone receiving key presses from a keypad. Each subscription message identifies a pattern of user input that the application is to be notified of. The device monitors the user input to identify the occurrence of the identified patterns. When a specified pattern of user input is detected, the device notifies the corresponding application via a signaling channel linking the application with the device. The subscription messages use regular expressions including various formats to specify the patterns of interest, such as a single digit (explicitly or wildcard), one of a set of digits, a range of digits, and a repeating pattern of digits. The subscription messages can also contain tags associated with the regular expressions, which are returned to the application upon reporting the occurrence of a pattern to enable the application to readily identify the context of the notification.
Owner:DIALOGIC INC
Portable electronic bingo device
An electronic bingo device used for dispensing bingo cards and tracking the cards for bingo during play. The apparatus is equipped with a conventional computer hardware platform and software tailored to track a bingo game by use of a game key with memory for storing data representative of a set of bingo game data including winning patterns and wild cards used during each game. In addition, a player's allocation of bingo cards is stored on the game key. Bingo cards stored in the device corresponding to the number allocated are used for game play. As the player enters the numbers are called out in the bingo hall. The device monitors each card for bingo.
Owner:ARROW INT INC
Capturing and presenting site visitation path data
ActiveUS7792844B2Understanding sequential relationshipEasy to understandDigital data processing detailsHardware monitoringFrequency of occurrenceComputer science
Node sequence data, such as website visitation records, are filtered, analyzed, and summarized in reports. An administrator can designate particular target paths of interest in terms of a checkpoint node sequence. Node sequences are filtered based on the checkpoint node sequence, without regard to any additional or tangential nodes appearing in the sequences. In addition, node sequences can be specified in terms of specific nodes of interest along with wild cards. Reports depict the relative frequency of occurrence of node sequences using visual indicators such as line thickness and / or color.
Owner:ADOBE SYST INC
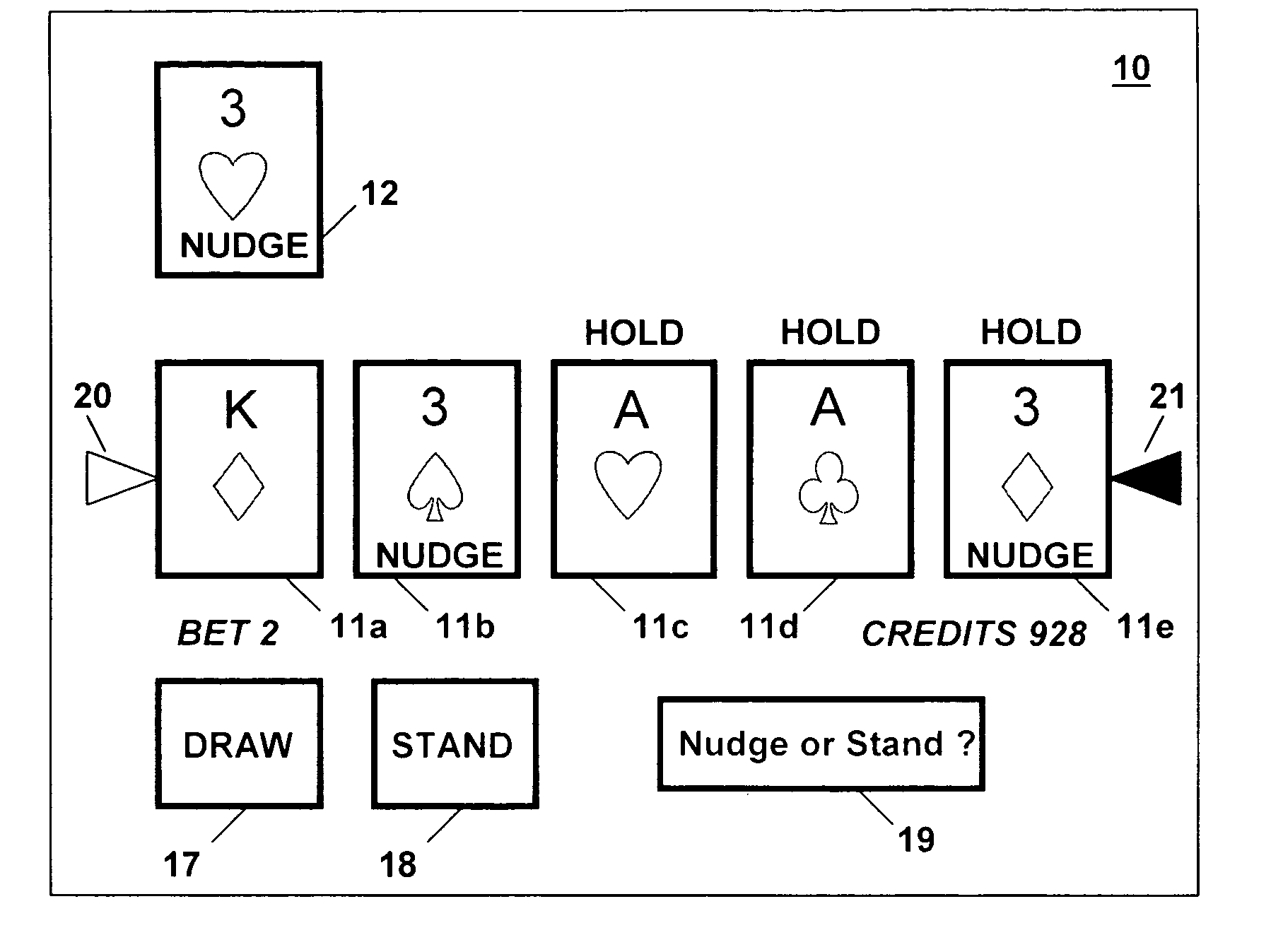
Method for playing poker with additional card draws
InactiveUS7222856B2Control moreMore of participationCard gamesApparatus for meter-controlled dispensingComputer hardwareGame play
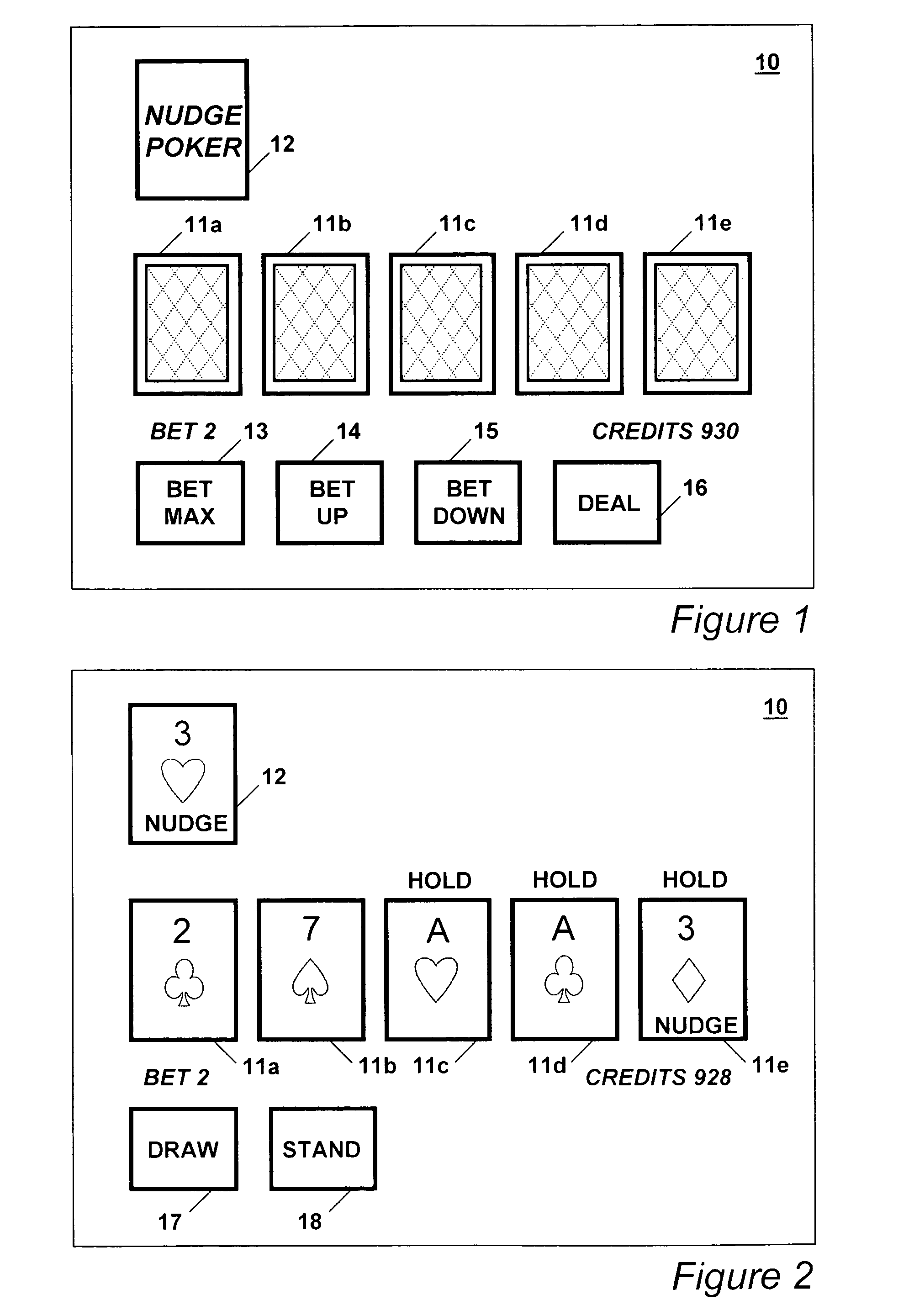
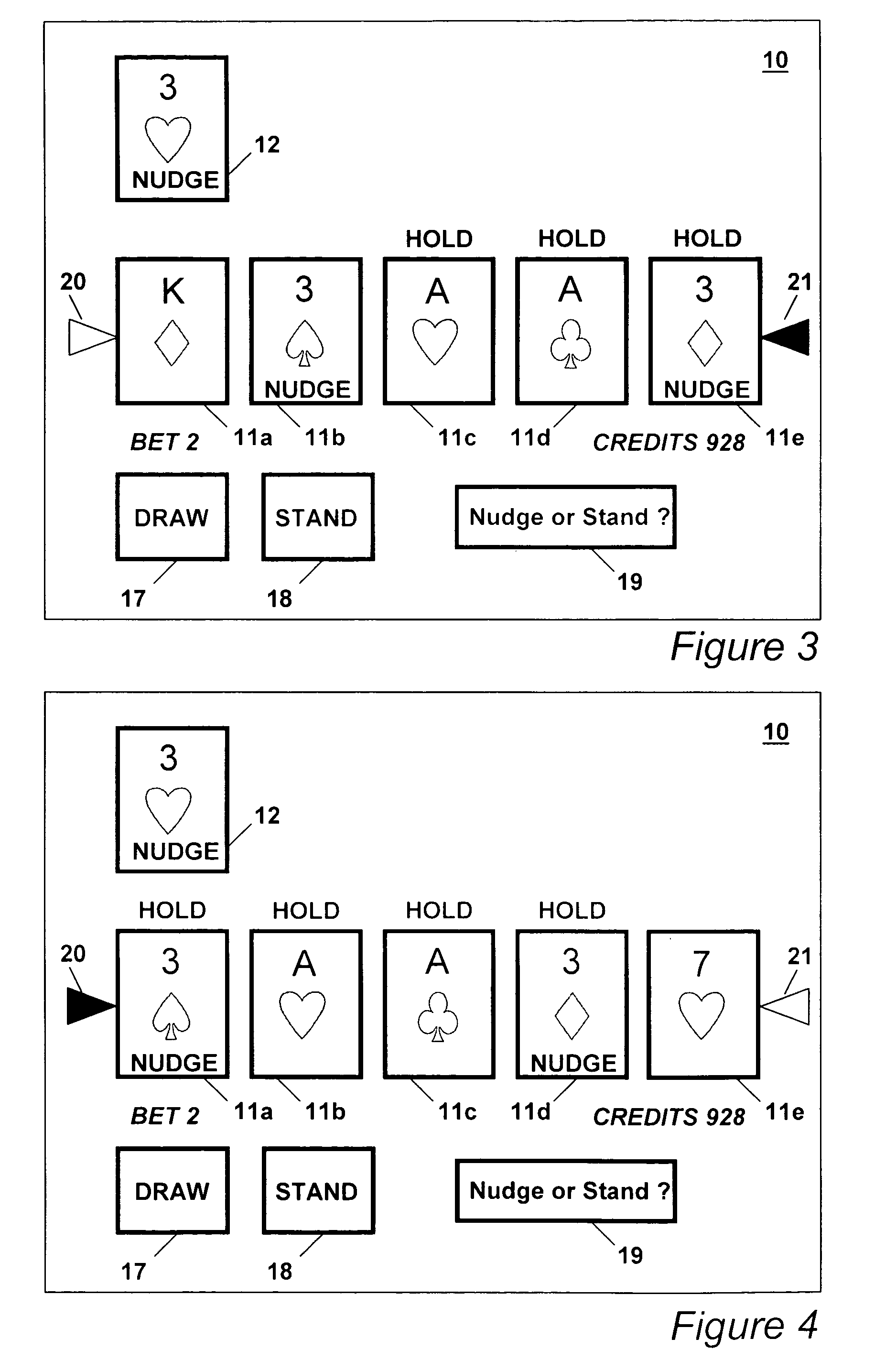
An improved poker game is disclosed that provides a player with an initial five card poker hand plus an indication of additional nudge cards. Four cards in a deck having the same face value, but not suit, are the nudge cards. For each nudge card that a player is initially dealt or receives thereafter during the course of game play the player receives an option to replace a card in their hand. The nudge cards may also be single cards or wild cards.
Owner:GAMETECH INT
Method and device for updating contract signing and configuration of access point name
ActiveCN101790150AReduce overheadImprove data transfer performanceAssess restrictionSecurity arrangementRogue access pointNetwork data
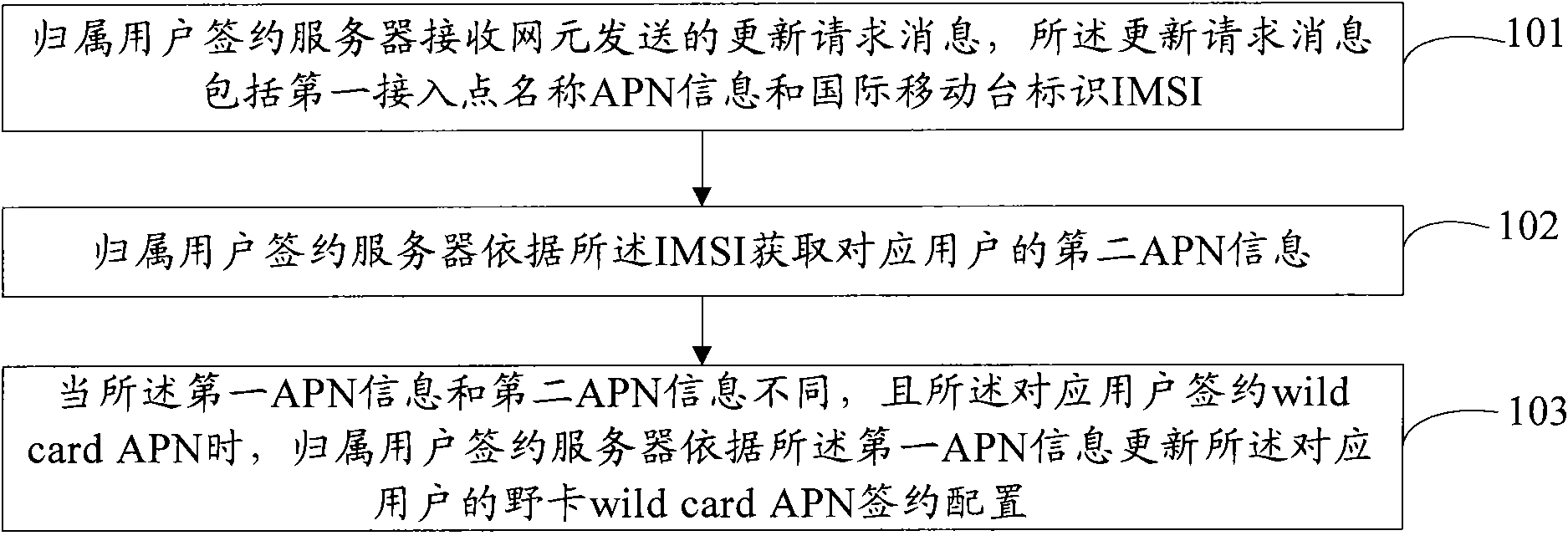
The embodiment of the invention discloses a method and a device for updating contract signing and configuration of an access point name. The method comprises the following steps: receiving an updating request massage sent by a network element, wherein the updating request massage comprises first access point name APN information, PDNGW information of a grouped data network gate and identification IMSI of an international mobile station; acquiring second APN information corresponding to a user according to the IMSI; when the first APN information is different from the second APN information, and the corresponding user is signed with a wild card APN, for updating the signing configuration of the wild card APN of the corresponding user according to the first APN information. The embodiment of the invention can reduce the unnecessary signaling interactive operation between signed server of the affiliation user and other network elements, can improve network data transmission performance, and reduce the unnecessary expense of affiliation user server.
Owner:HUAWEI TECH CO LTD
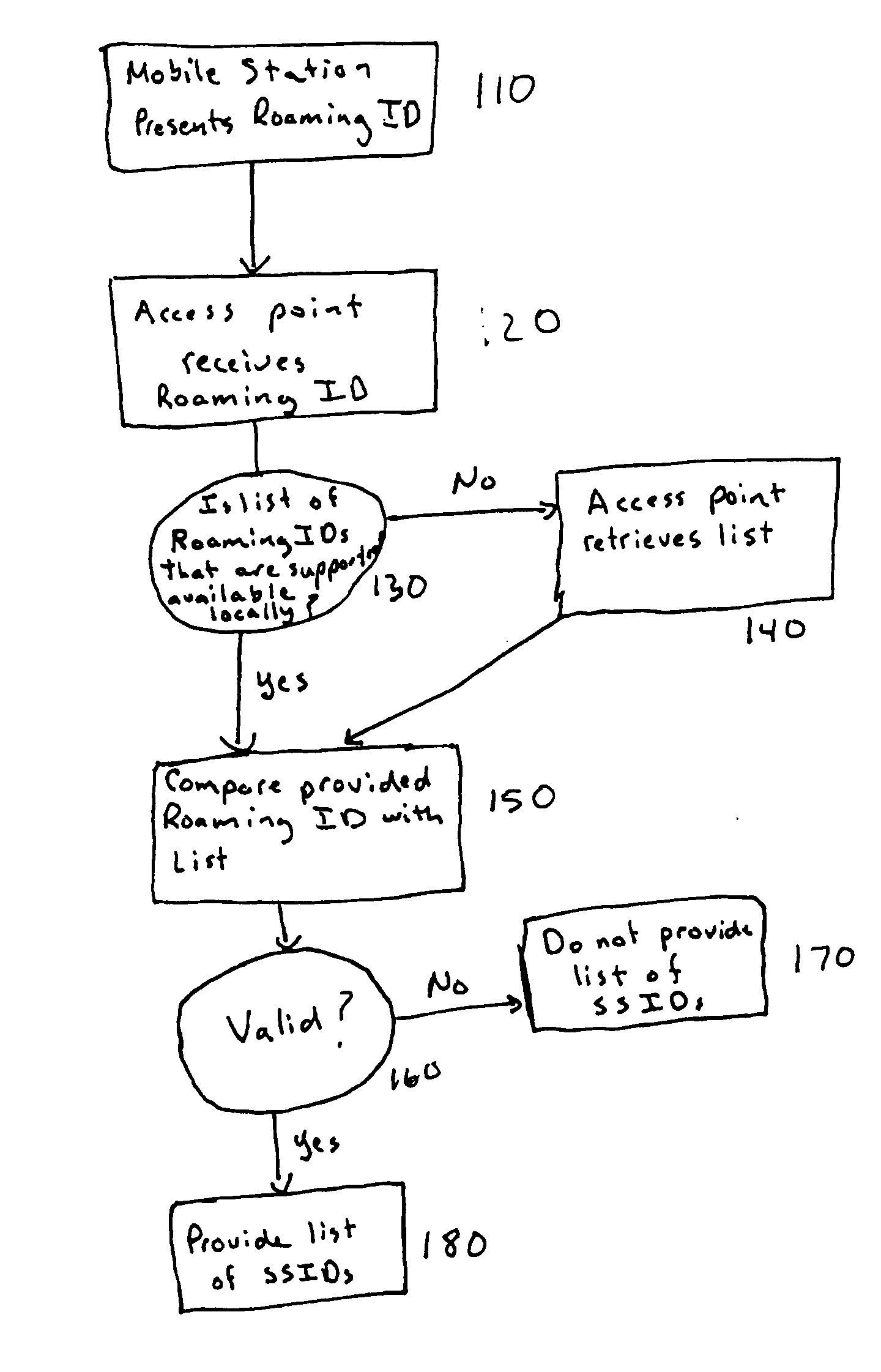
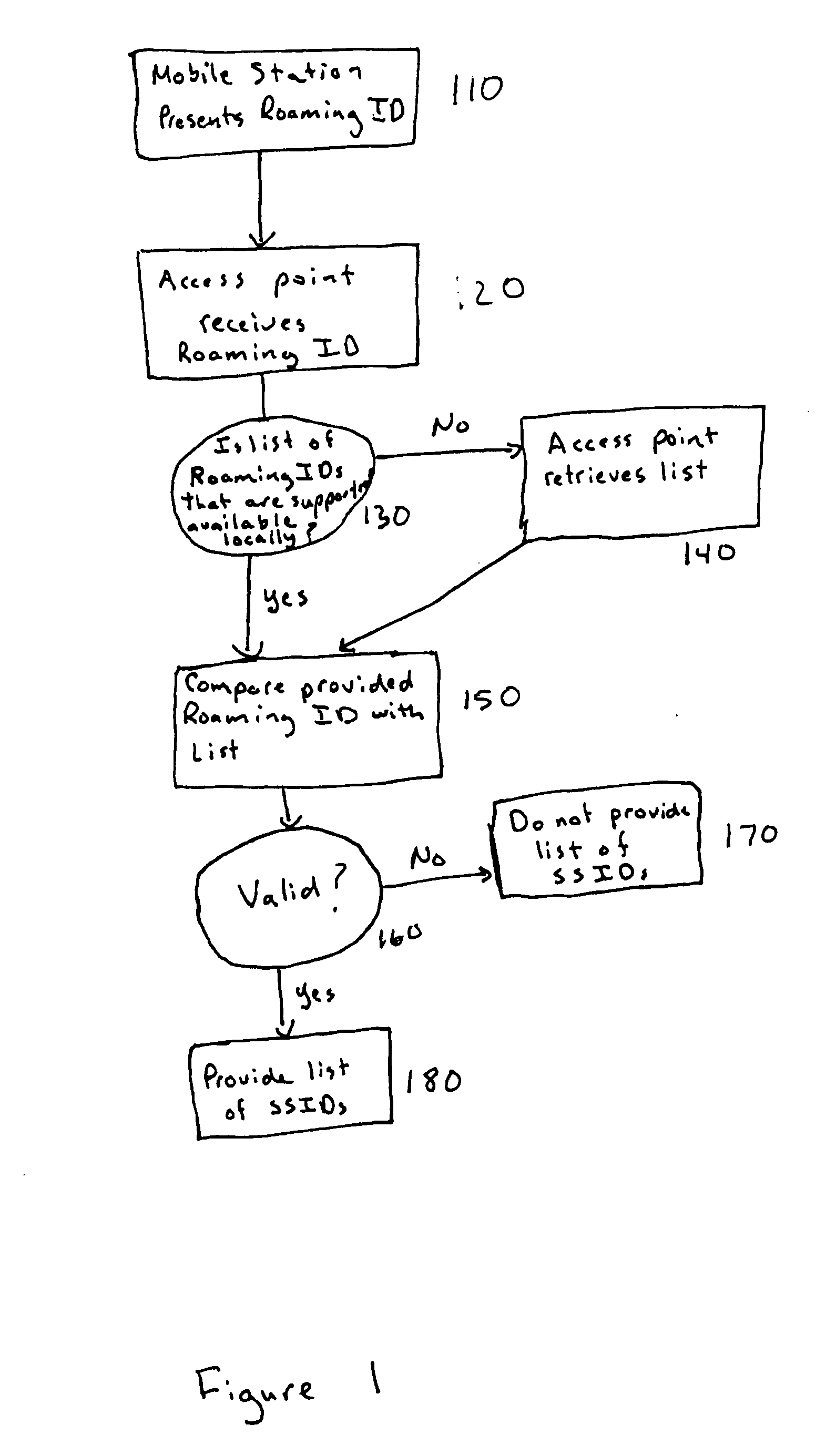
Secure identification of roaming rights prior to authentication/association
InactiveUS20070184832A1Assess restrictionRadio/inductive link selection arrangementsAuthenticationE infrastructure
A mechanism to enable secure identification of roaming rights prior to authentication / association is provided. The mechanism may include using a Roaming ID, and may also include the use of wild cards and group IDs to reduce the length of transmissions. The mechanism may further employ public key infrastructure and puzzles to further enhance security and reduce the risk of denial of service attacks.
Owner:NOKIA CORP
Applying configuration group information to target configuration information
InactiveUS7096256B1Multiple digital computer combinationsData switching networksConfigfsComputer science
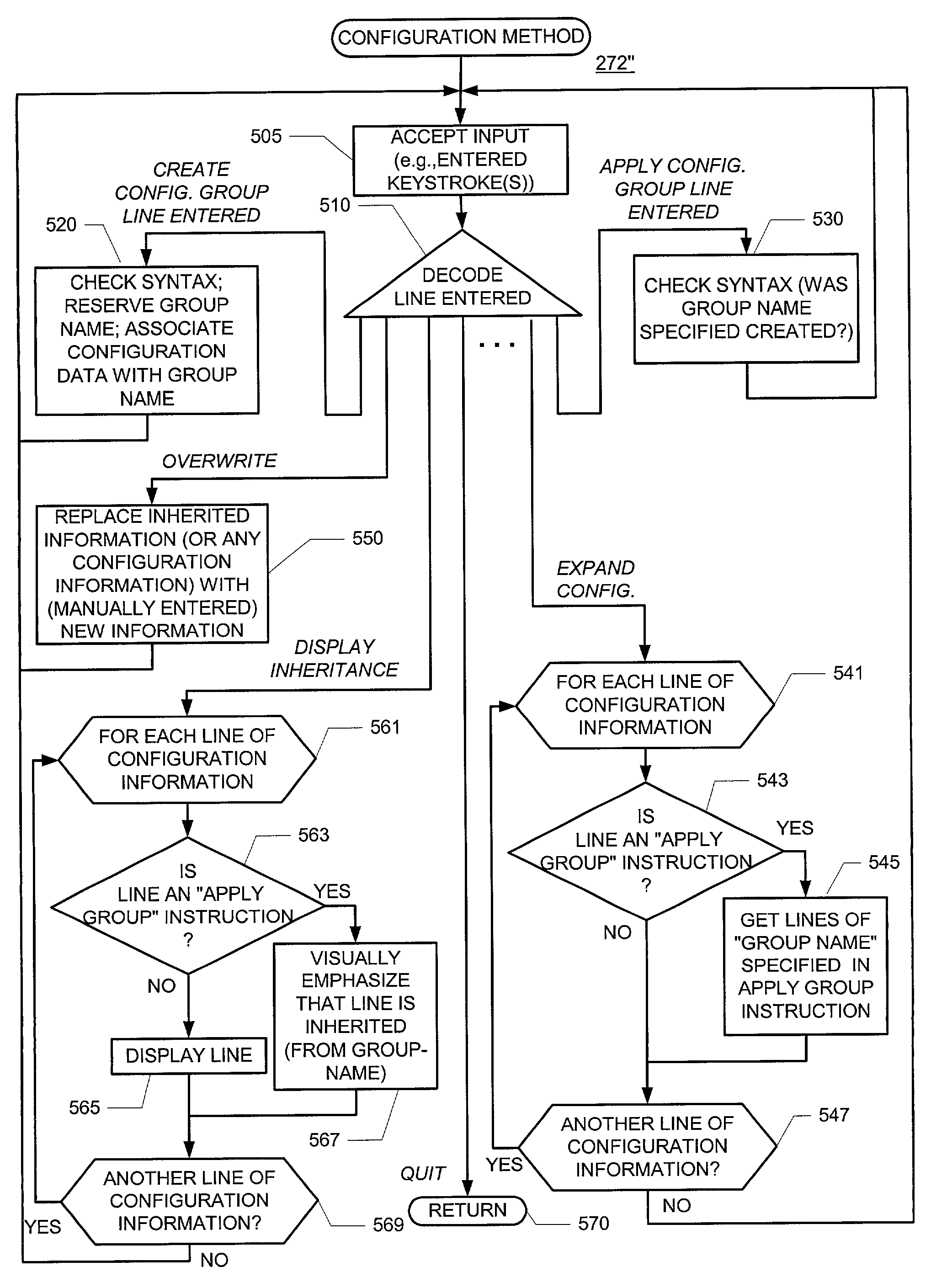
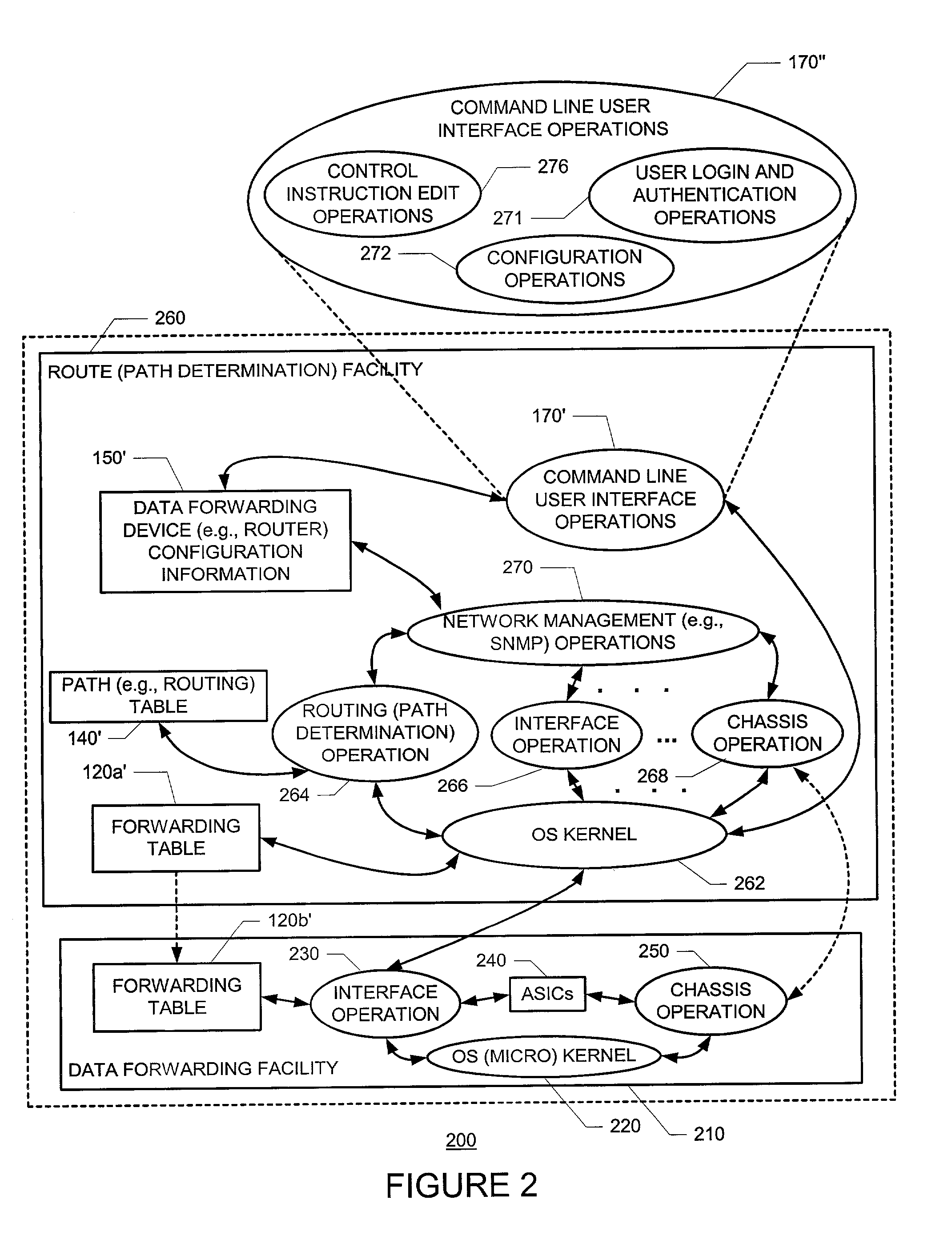
An interface permitting users (i) to create a group (also referred to as a “source”) containing configuration statements and (ii) to direct the inheritance of that group's statements in the rest of the configuration information (also referred to as a “target”). The same group can be applied to different sections of the configuration information. Different sections of one group's configuration statements can be inherited in different places in the configuration information. Supporting such configuration groups allows users to create smaller, more logically constructed configuration files, thereby making it easier to configure and maintain data forwarding device software. For example, users can group together statements that are repeated in many places in the configuration, such as when configuring interfaces, and thereby limit updates to just the group. Users can also use wildcards in a configuration group to allow configuration information of the configuration group to be inherited by any object(s) in the target configuration that matches a wildcard expression.
Owner:JUMIPER NETWORKS INC
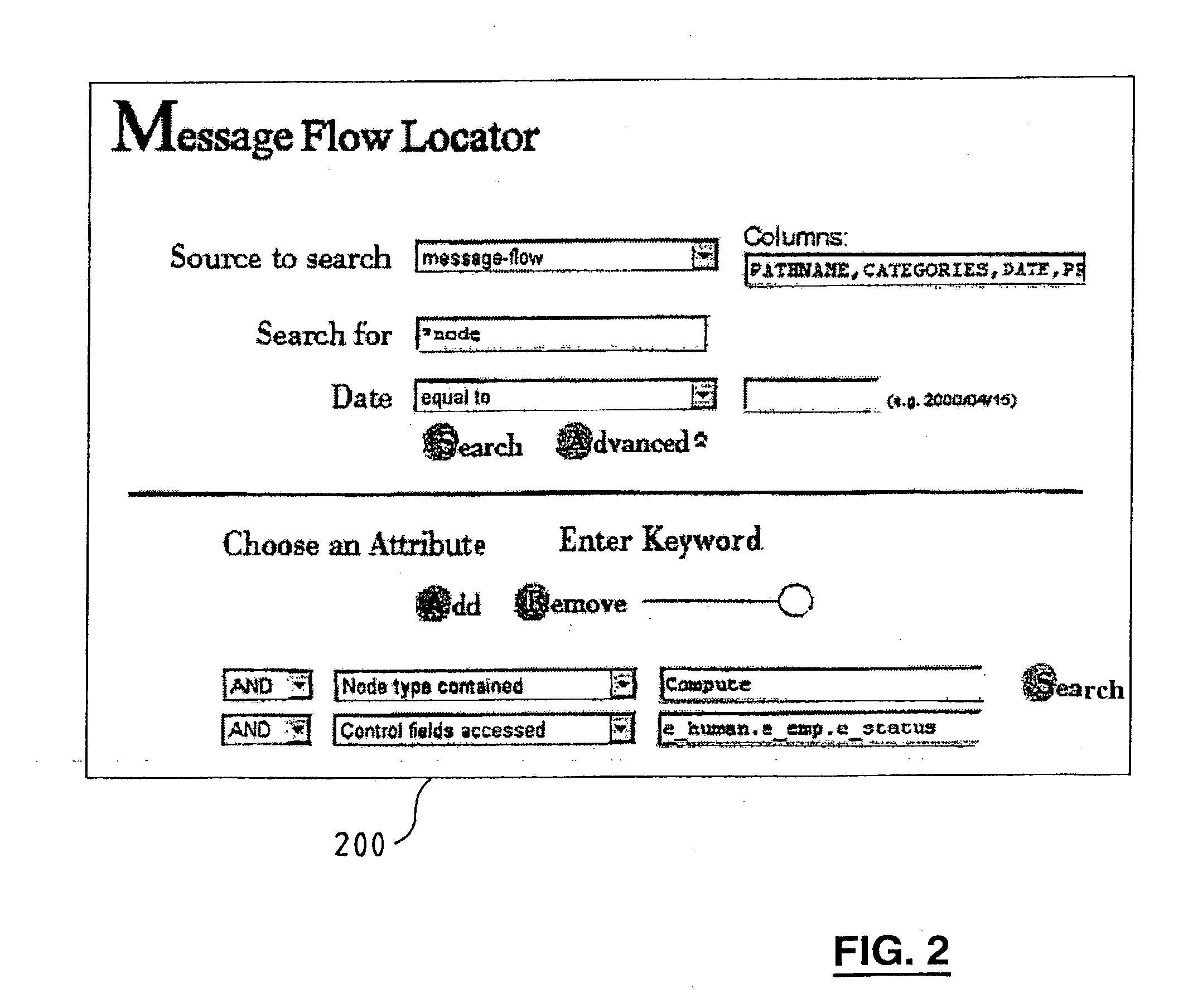
Flow composition model searching
An arrangement and method for flow composition model searching by holding in a repository (120) records (130) of flow composition models containing information representative of predetermined flow composition model characteristics thereof, specifying (200) information representative of desired ones of the predetermined flow composition model characteristics, and retrieving from the repository flow control model records matching the specified information. The FCM characteristics may include Message Flow, Work Flow and Connector characteristics. The specified information may include wild card characters. This provides the advantage that a new specification of flow characteristics, derived from the general model FCM, is used. Hence using it enables the application of search, reuse, compare, etc., on any present and future FCM realization.
Owner:IBM CORP
Card game suitable for casino play
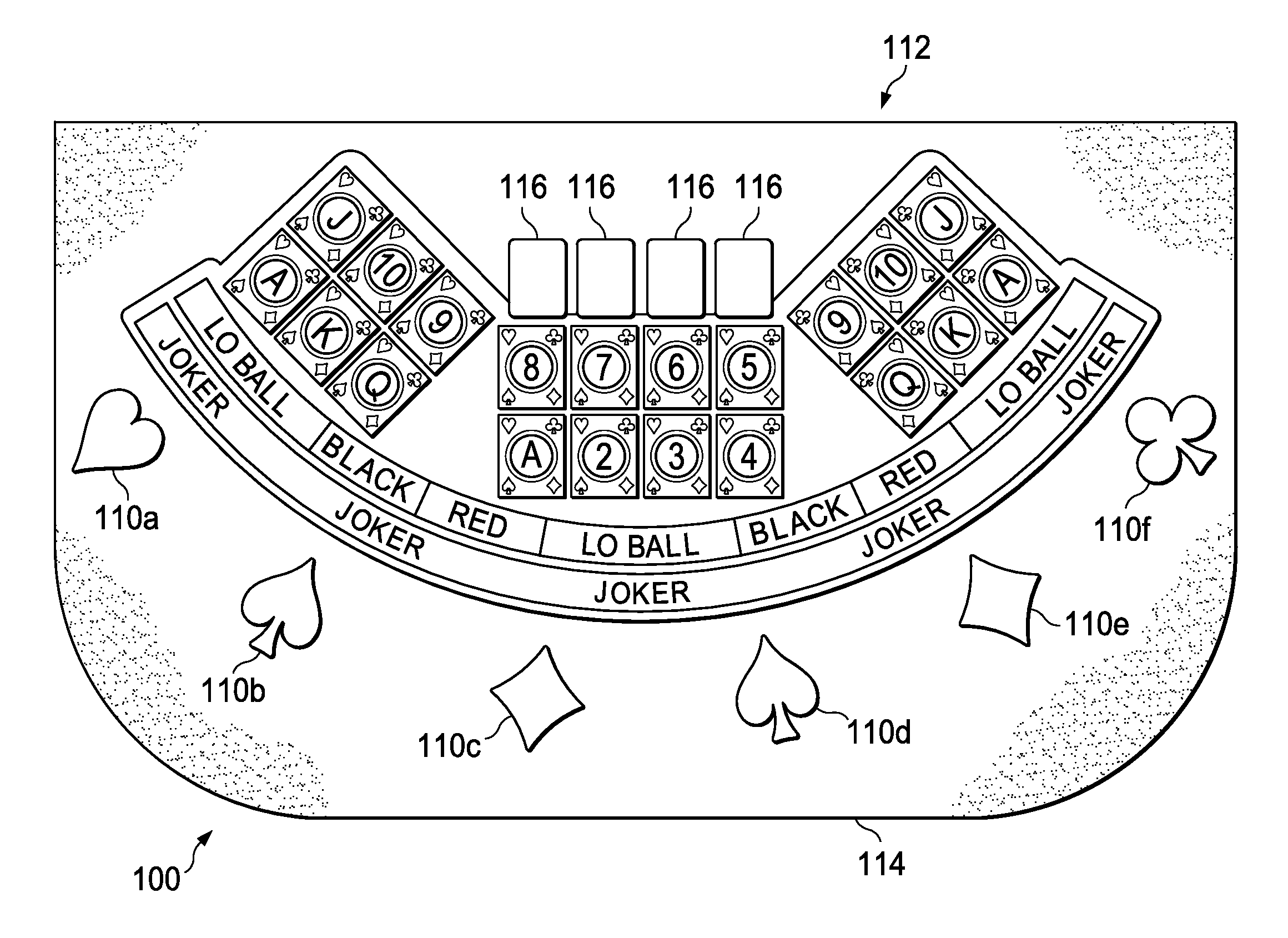
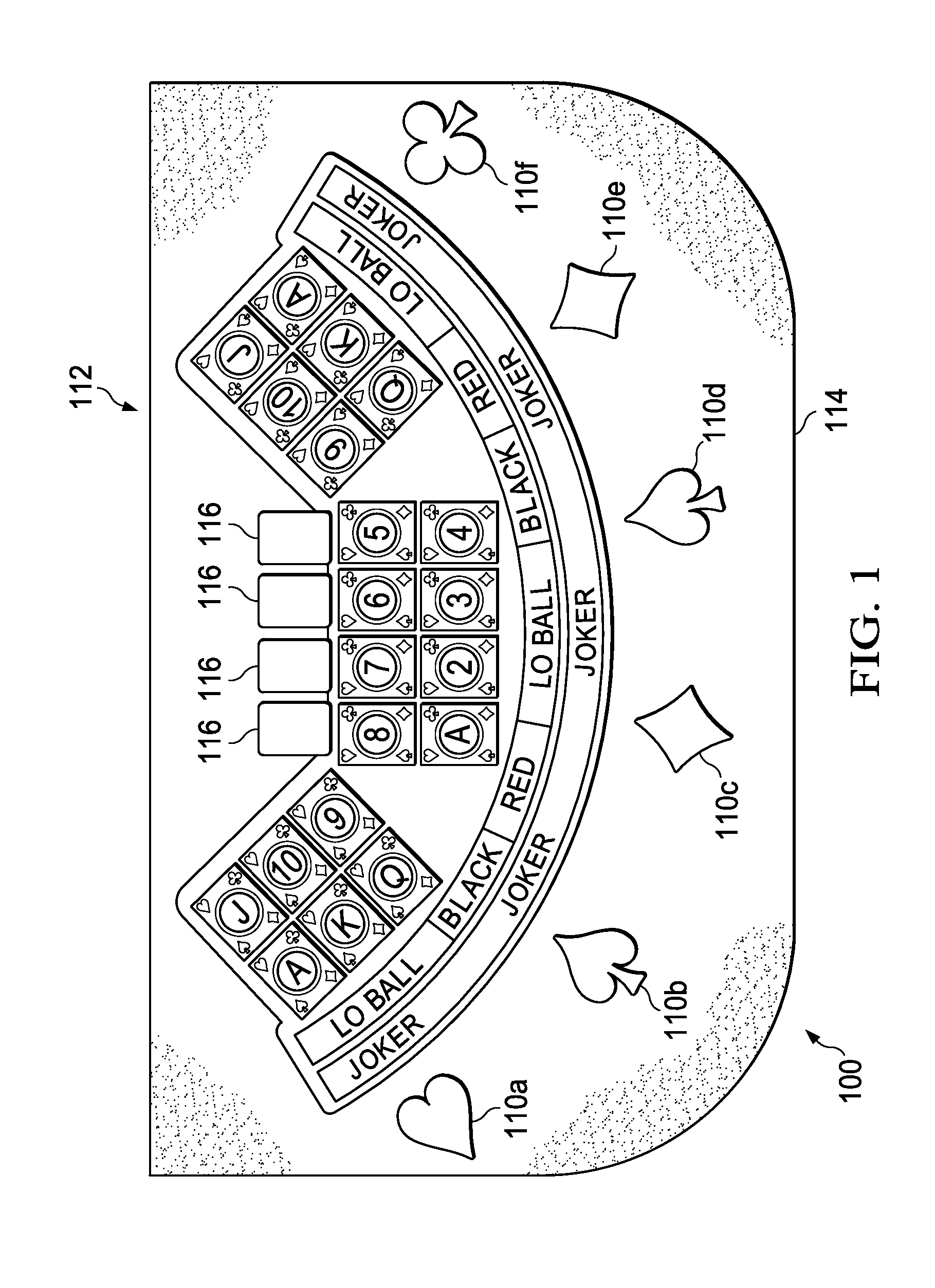
System and method for playing a card game is provided. An embodiment for play in a casino using a standard deck of cards comprises allowing a player to place a wager on a selected card value, a wild card value, black, red, or lo ball. Community cards are dealt face up and winning hands are paid according to a predetermined payout schedule. Wagers on a selected card values and wild card values have predetermined payout values for specific winning hands. Black and red wagers have predetermined payout values if all of the community cards are black or red, respectively. Lo ball wagers have a predetermined payout value if all of the community cards are less than or equal to a predetermined value, such as 8. In another embodiment, the card game may be implemented in a computer system having a video display terminal.
Owner:WORLDWIDE GAMING
Method and system for providing information for identifying callers based on a partial number
InactiveUS7200211B1Improve abilitiesSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingExact matchPersonalization
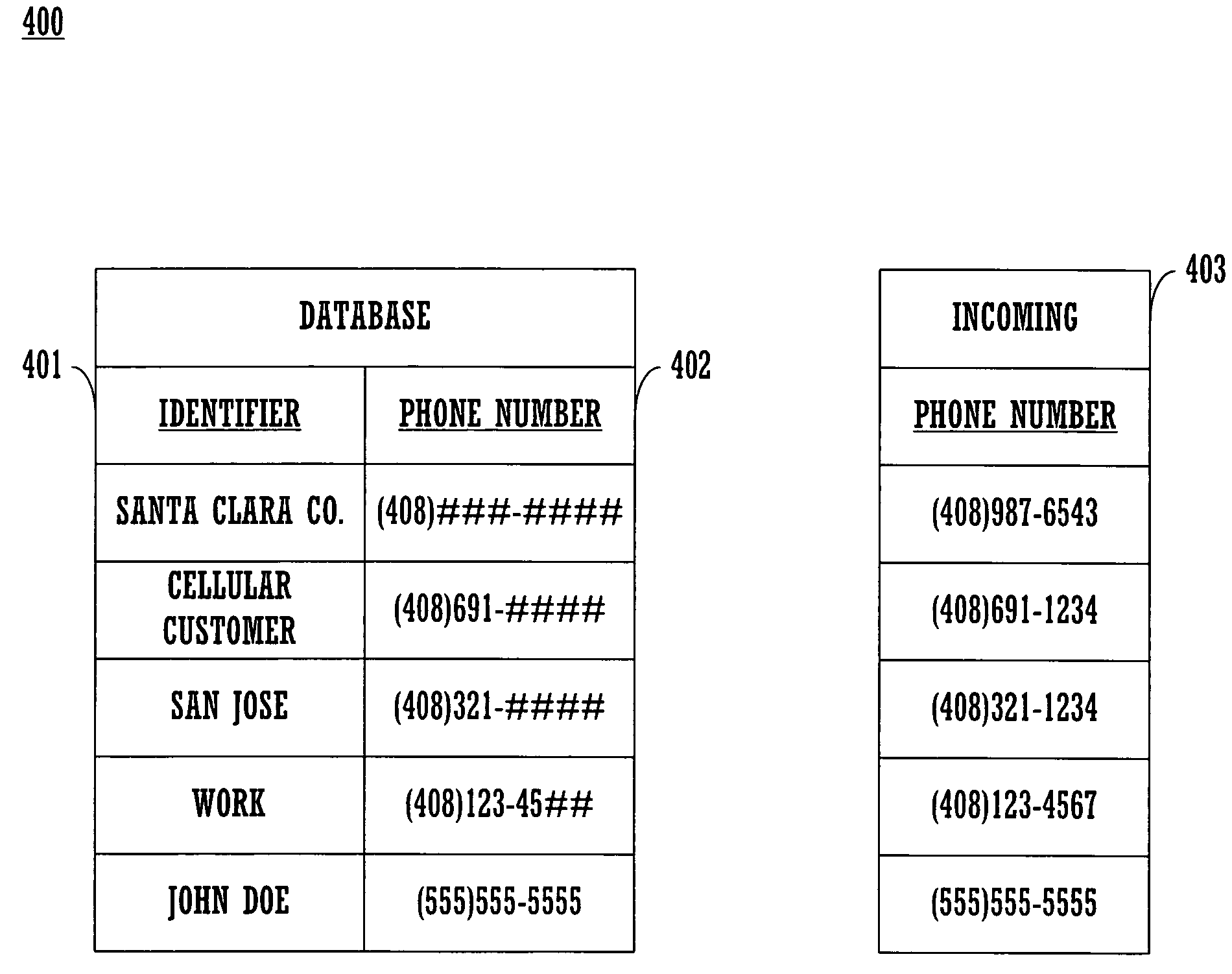
Embodiments of the present invention include a caller identification system and method for identifying a caller with a partial phone number look-up table. The caller identification system comprises a database that stores received calls and can be personalized to include information specific to partial phone numbers. In one embodiment, the caller identification system disclosed can be integrated into a cellular phone. In this embodiment, an incoming call initiates a search in a database to retrieve information about the caller. If a match is found, the identity of the caller is displayed. When an exact match is not found, a search for a partial match is executed with wild card values and information about the partial match is displayed. Information for a partial match can be personalized or pre-programmed into the caller ID system such as the city associated with a particular area code or prefix.
Owner:GOOGLE LLC
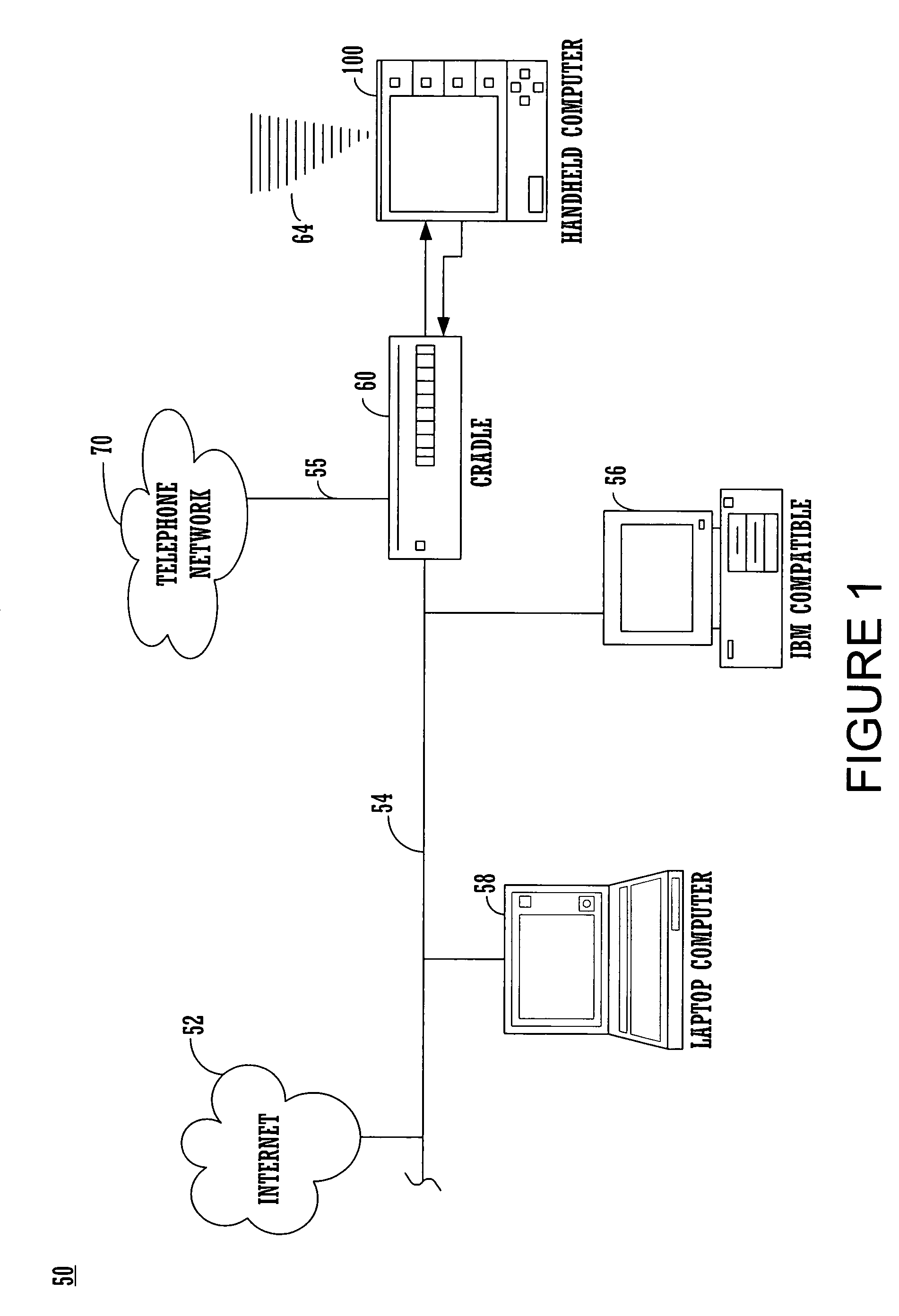
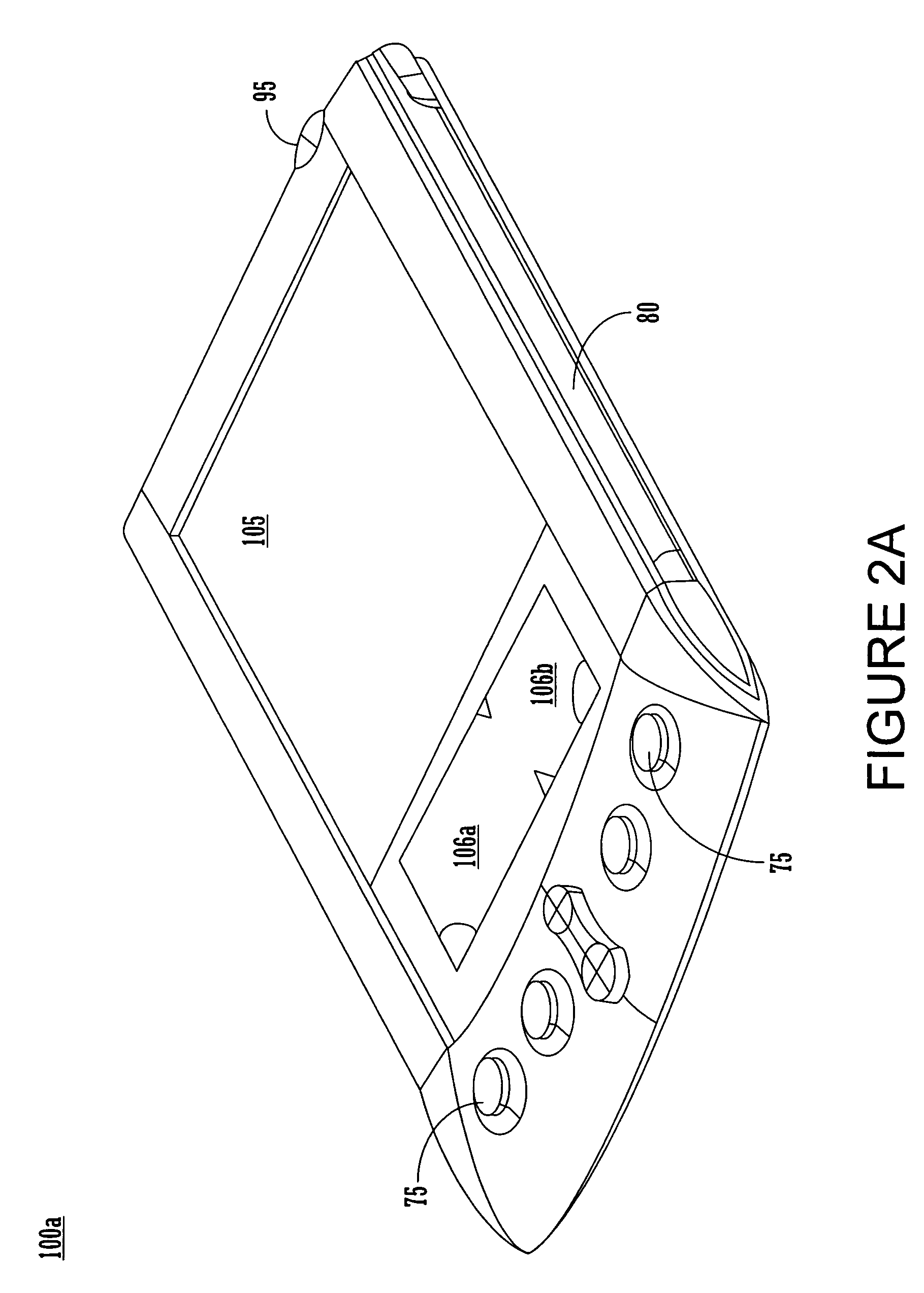
Dependency specification using target patterns
InactiveUS20020129347A1Efficiently findVersion controlSpecific program execution arrangementsScripting languageObject code
A method for generating changes and updating existing files and code in a computer program, wherein the method comprises reading existing source code and existing object code in the computer program. Then, reading a plurality of associated files to the source code, and executing a utility program. The utility program updates the target source code and the object code associated with the target source code. Targets may be specified with either glob-type patterns using the standard shell wild cards, or regular expression patterns. The utility program also includes scripting language and can specify particular characters to search for in the target code and the associated code. A target code list is generated for the source code and the associated object code by using the utility program, and the target code and the associated code are updated by employing a search technique specified in the utility program.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com