Searchable encryption method based on wildcard character in cloud storage safety
An encryption method and wildcard technology, applied in computer security devices, special data processing applications, instruments, etc., can solve the problems of non-negligible false positive probability, false positive of Bloom filter, spelling mistakes, etc., and achieve flexible user authorization and revocation , good privacy protection, and the effect of eliminating error probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
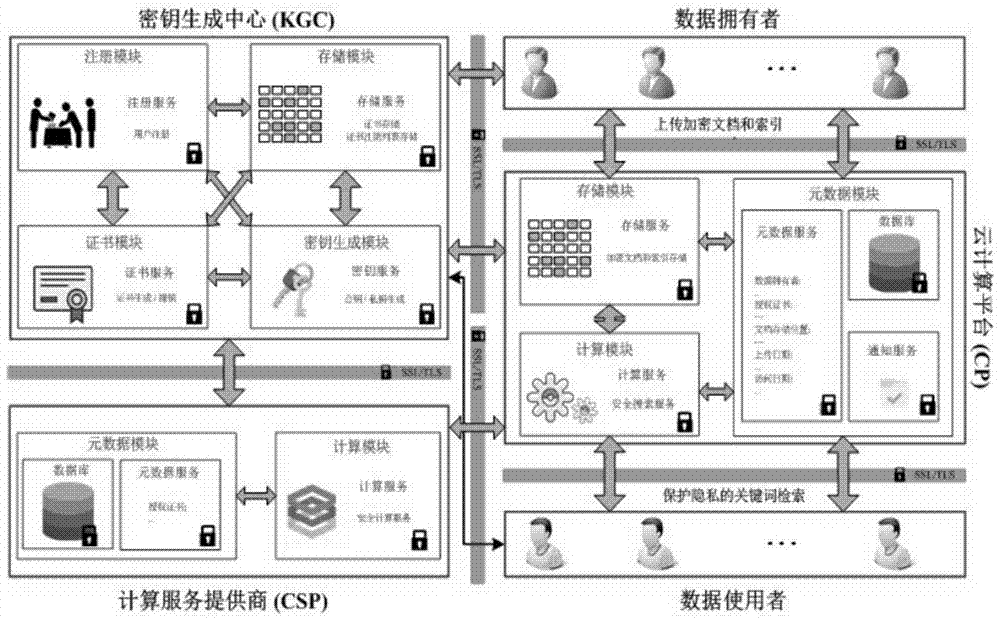
[0044] like figure 1 Shown is a system structure block diagram of an embodiment of the present invention, wherein:
[0045] The Key Generation Center (KGC) is fully trusted and is responsible for managing and distributing the public / private keys generated in the system. KGC includes registration unit, key generation unit, certificate unit and storage unit. The registration unit provides registration services for system users. The key generation unit generates public keys / keys for the system and users. The certificate unit is responsible for providing certificate generation and revocation services. The storage unit is responsible for storing certificates and revocation lists.
[0046] The Cloud Computing Platform (CP) stores users' encrypted documents and is responsible for performing data retrieval operations. CP includes storage unit, computing u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com