Security control method of event-driven network control system under multi-network attack
A network control system, network attack technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems that affect the effective operation of the system, reduce system performance, and the security of network information cannot be guaranteed. and energy consumption, stable operation, and the effect of saving network bandwidth resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
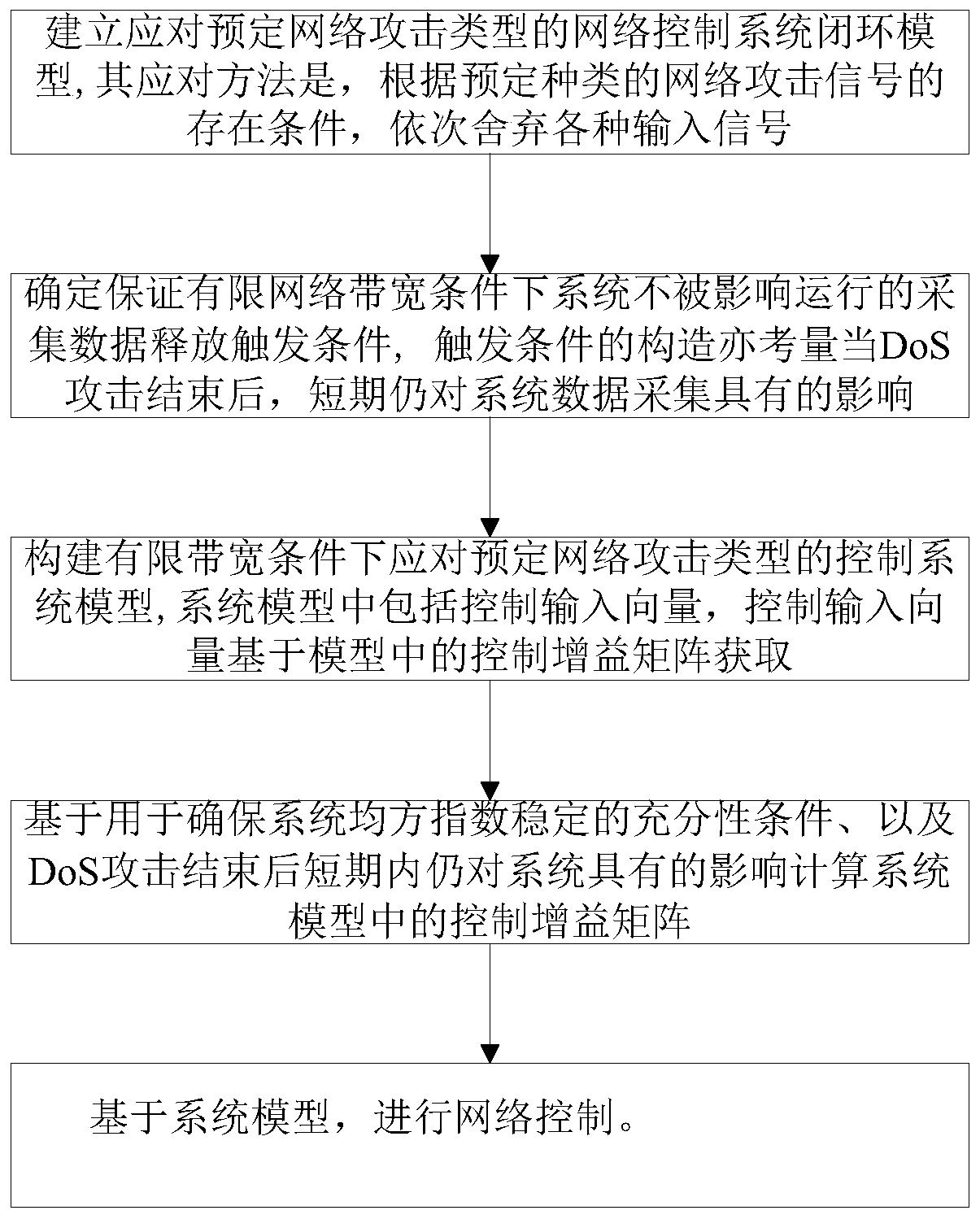
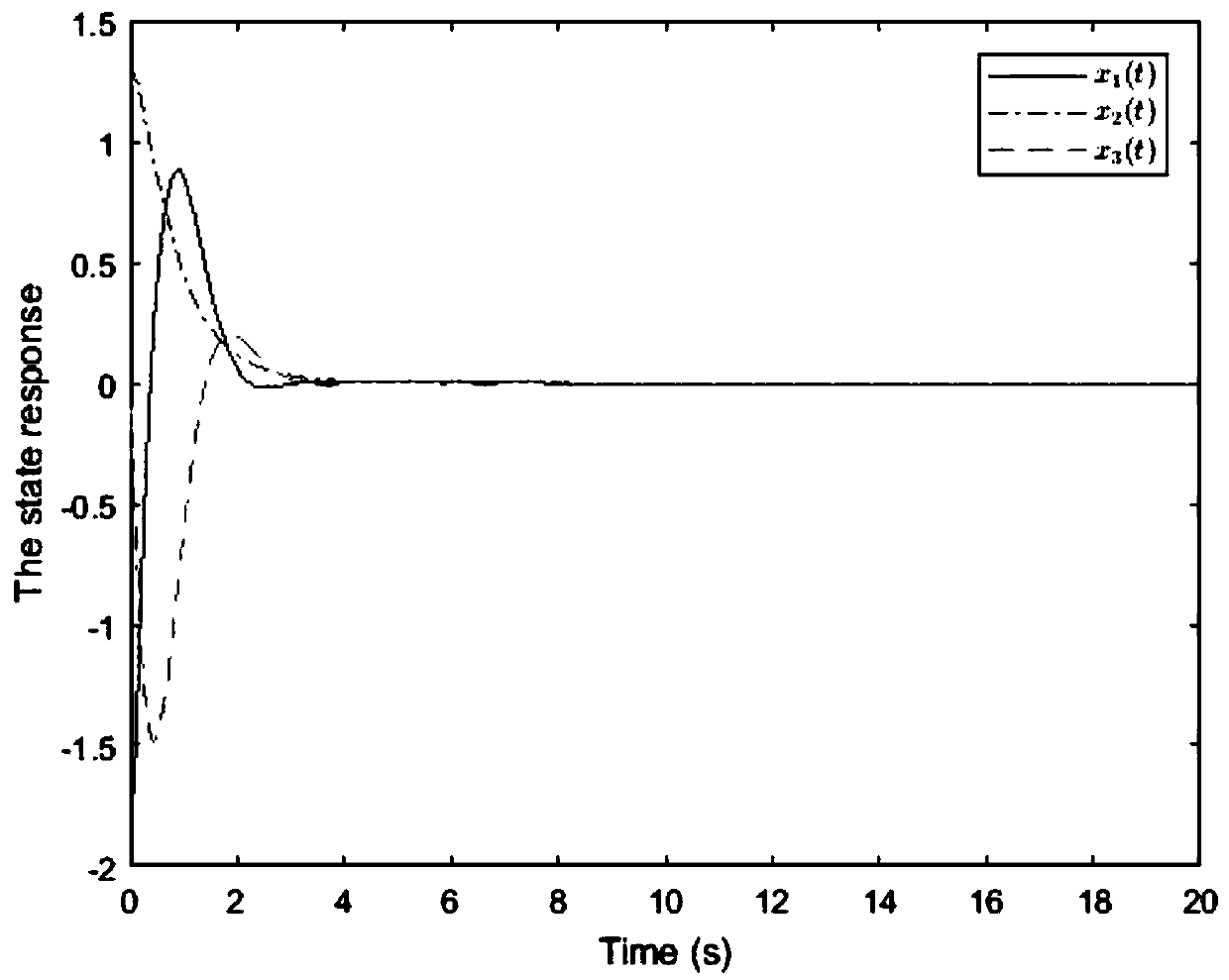
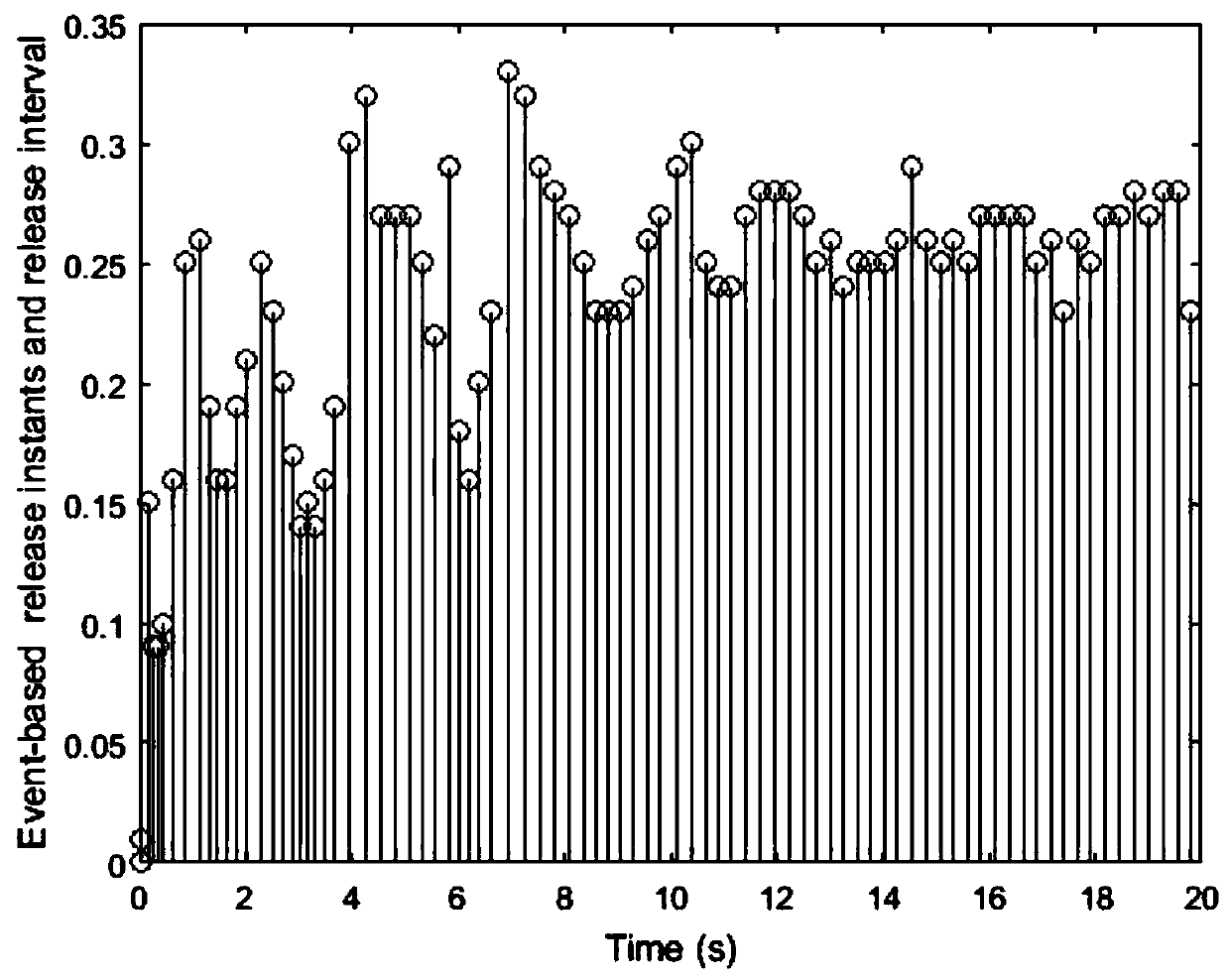
[0107] 1. Considering the impact of network deception attack, replay attack and DoS attack in turn, establish a closed-loop model of network control system:
[0108] (1) The NCS object described in (1) is described by the following linear state equation:
[0109]
[0110] where A and B are coefficient matrices, is the system state vector, is the control input vector, and the corresponding state feedback controller is
[0111] u(t)=Kx(t)(2)
[0112] where .K∈R m×n is the gain matrix of the controller to be designed.
[0113] (2) Considering the impact of network spoofing attacks, the input of the controller under the influence of network spoofing attacks is
[0114] x D (t)=α(t)f(x(t))+(1-α(t))x(t k h) (3)
[0115] Among them, h represents a fixed sampling period, t k h represents the moment when the sensor releases data (t k ∈{1,2,3,...}), f(x(t)) is a nonlinear function assumed to represent a network spoofing attack signal and subject to the following nonlinear...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com