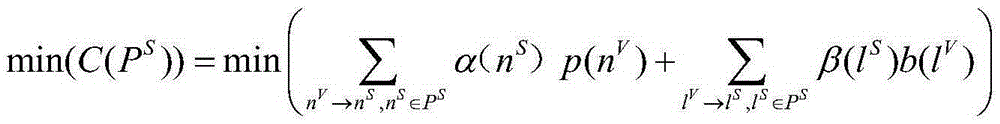Patents
Literature
456 results about "Public resource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
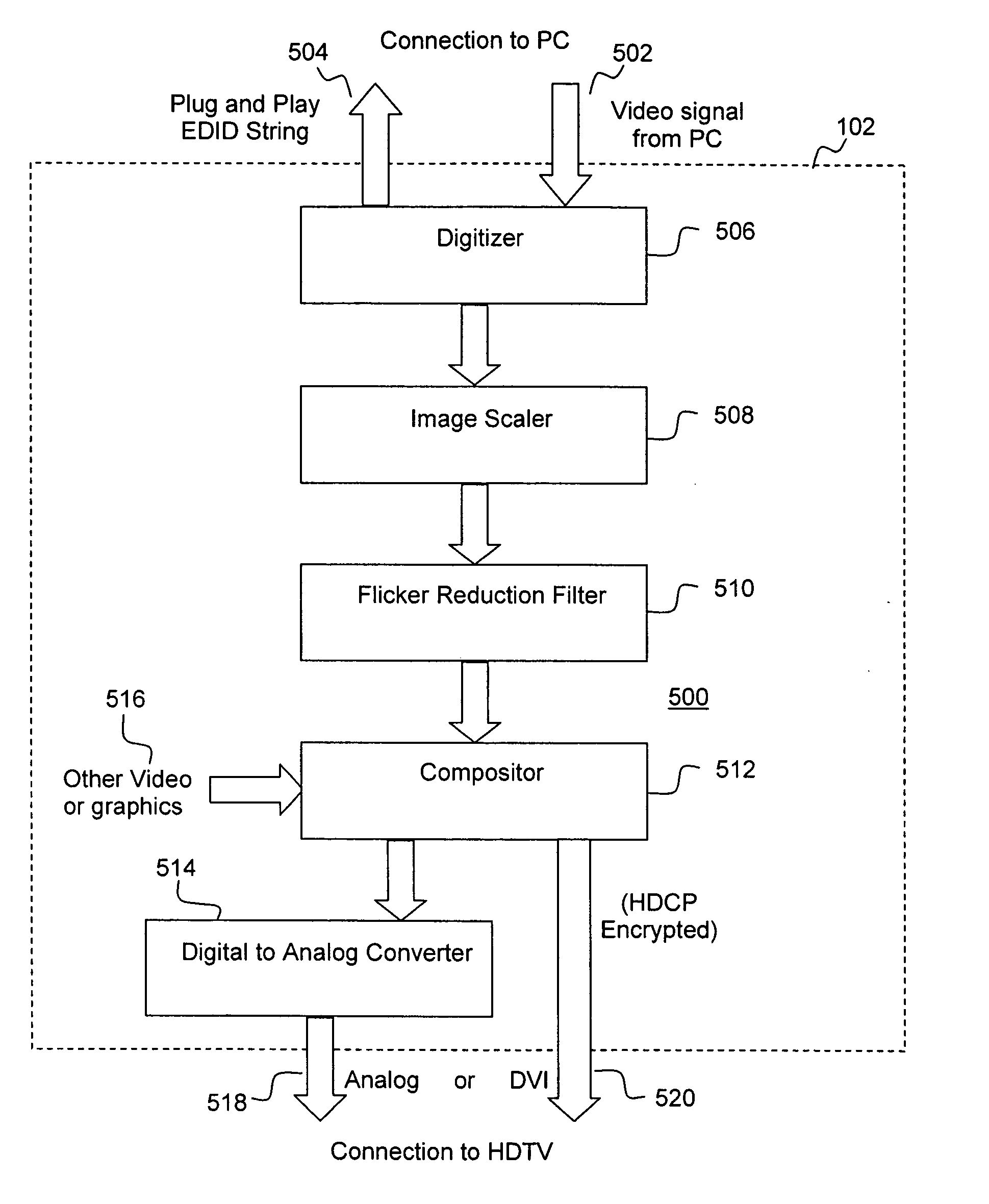
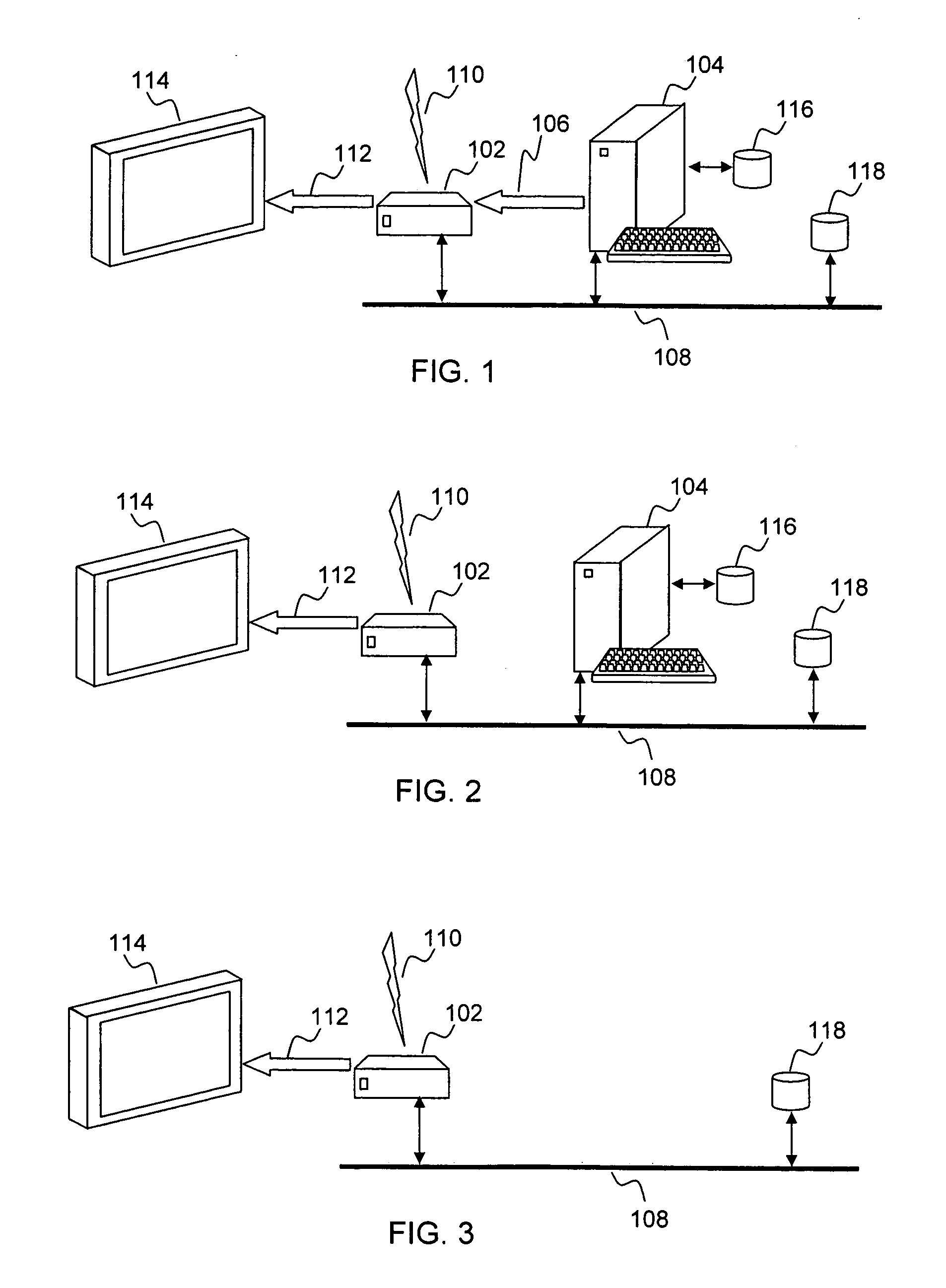
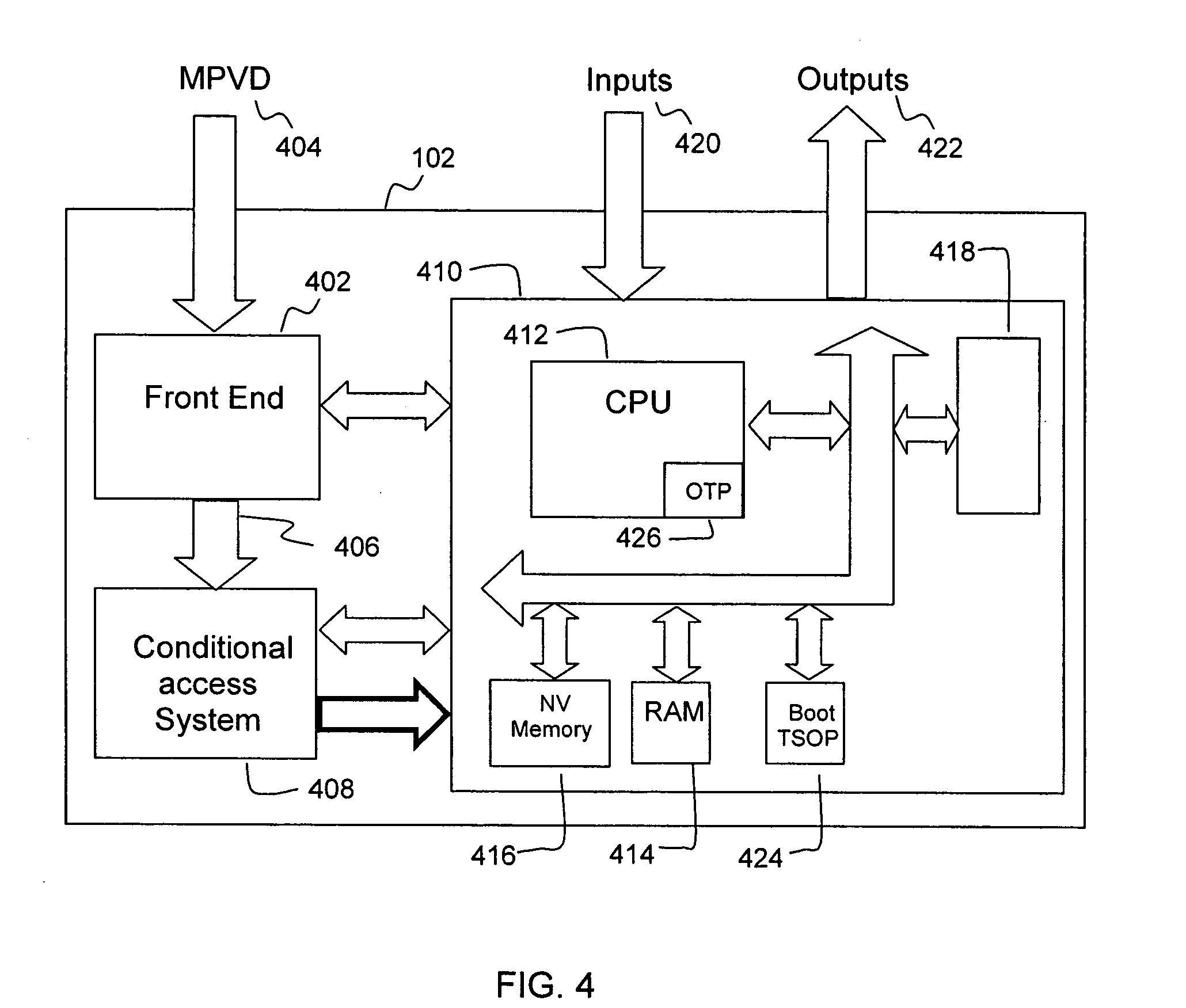
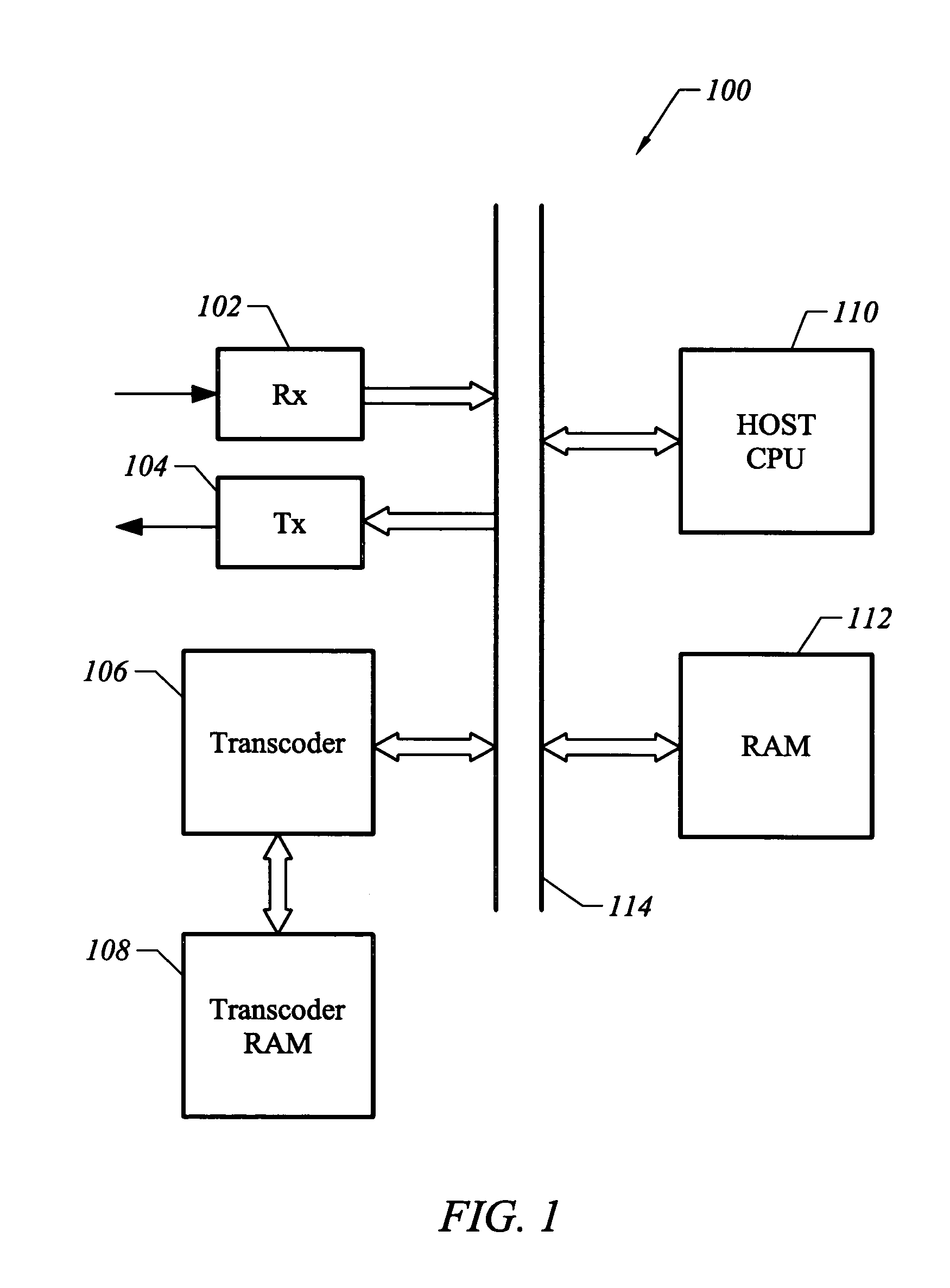
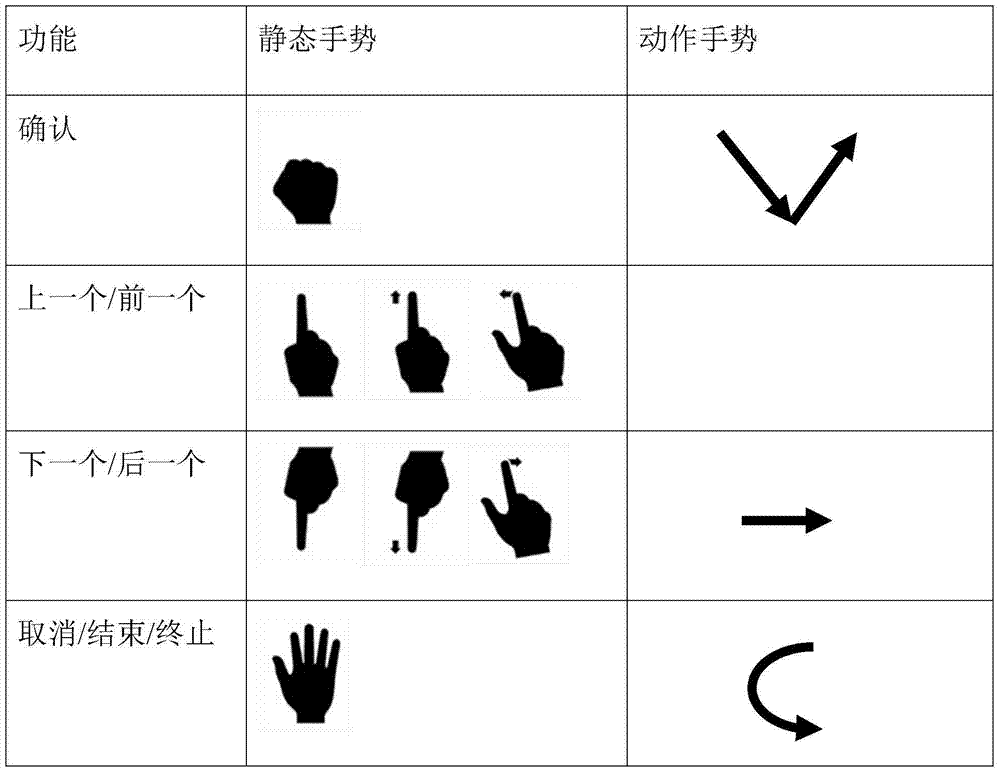
Secure integrated media center
InactiveUS20050125357A1Safe storageTelevision system detailsUnauthorized memory use protectionHard disc driveHigh definition tv
A set-top media system is disclosed which can be combined with an open architecture personal computer (PC) to provide a feature-rich secure integrated media center while meeting security rules of most major conditional access and content protection industry rules such as Cable Labs DFAST and PHILA agreements; and DTLA agreements for 5C-DTCP for IEEE1394, USB, and IP. The set-top media center and PC share common resources such as high definition display, remote control, hard disk drive, and other external unsecure storage devices. All media content is available seamlessly using a PC user interface, including controlled-content media such as high definition TV, within a PC desktop window. All controlled-content media is manipulated and managed within the set-top media system in a seamless manner. A novel mechanism is disclosed to allow controlled-content media to be stored on unsecure devices in encrypted form while overcoming the disk cloning attack problem for move operations.
Owner:SAADAT ABBAS SASAN +1
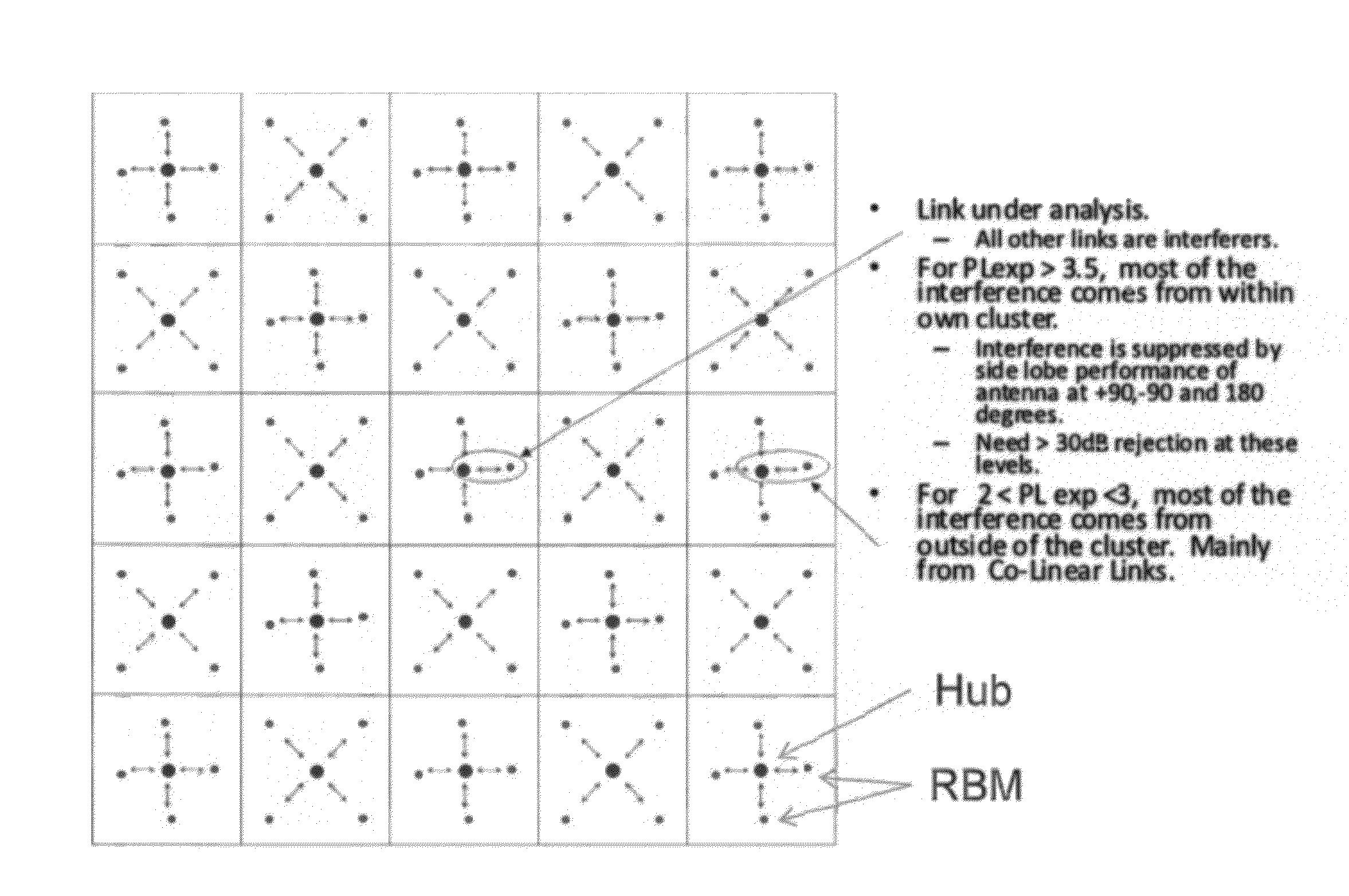
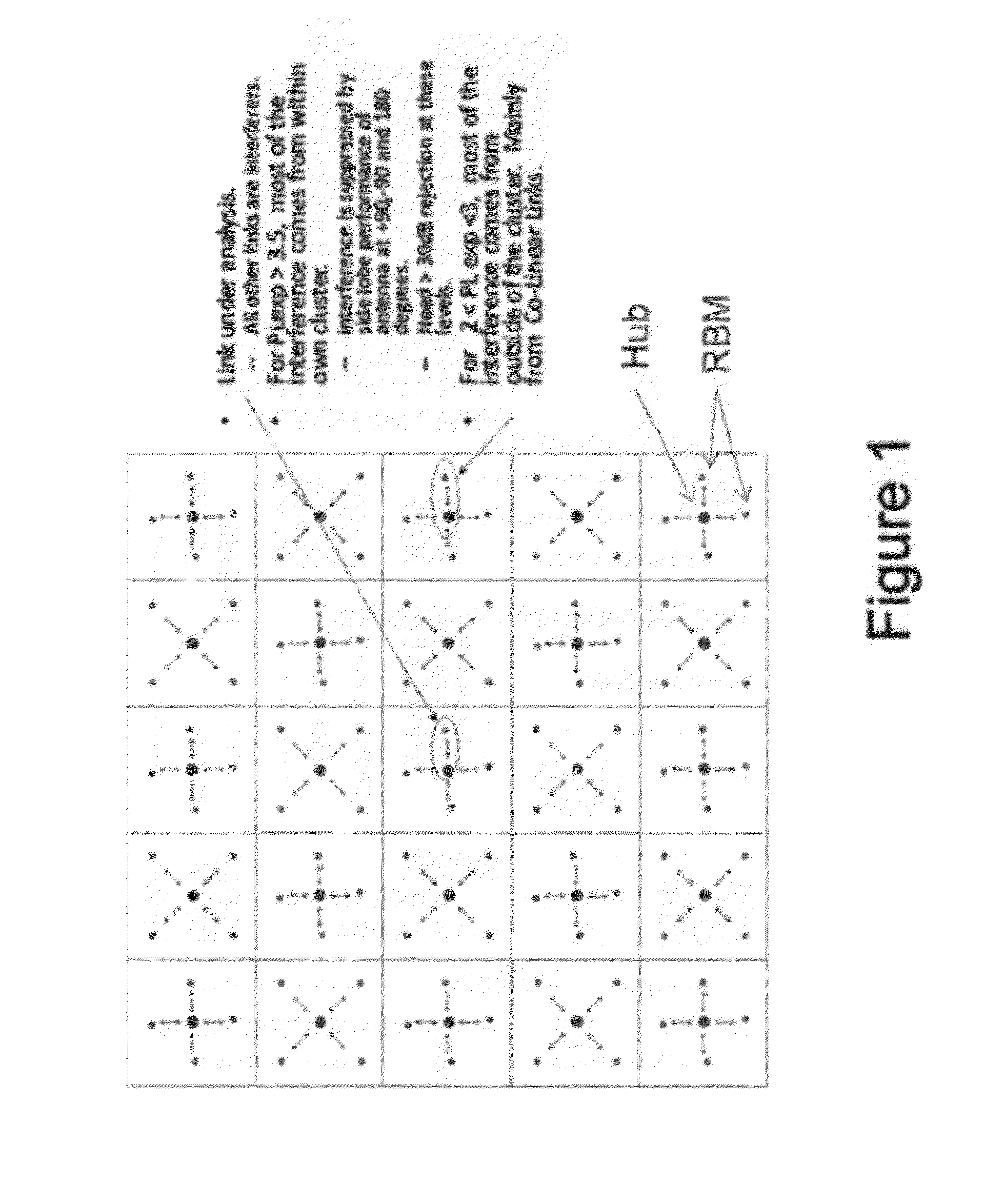
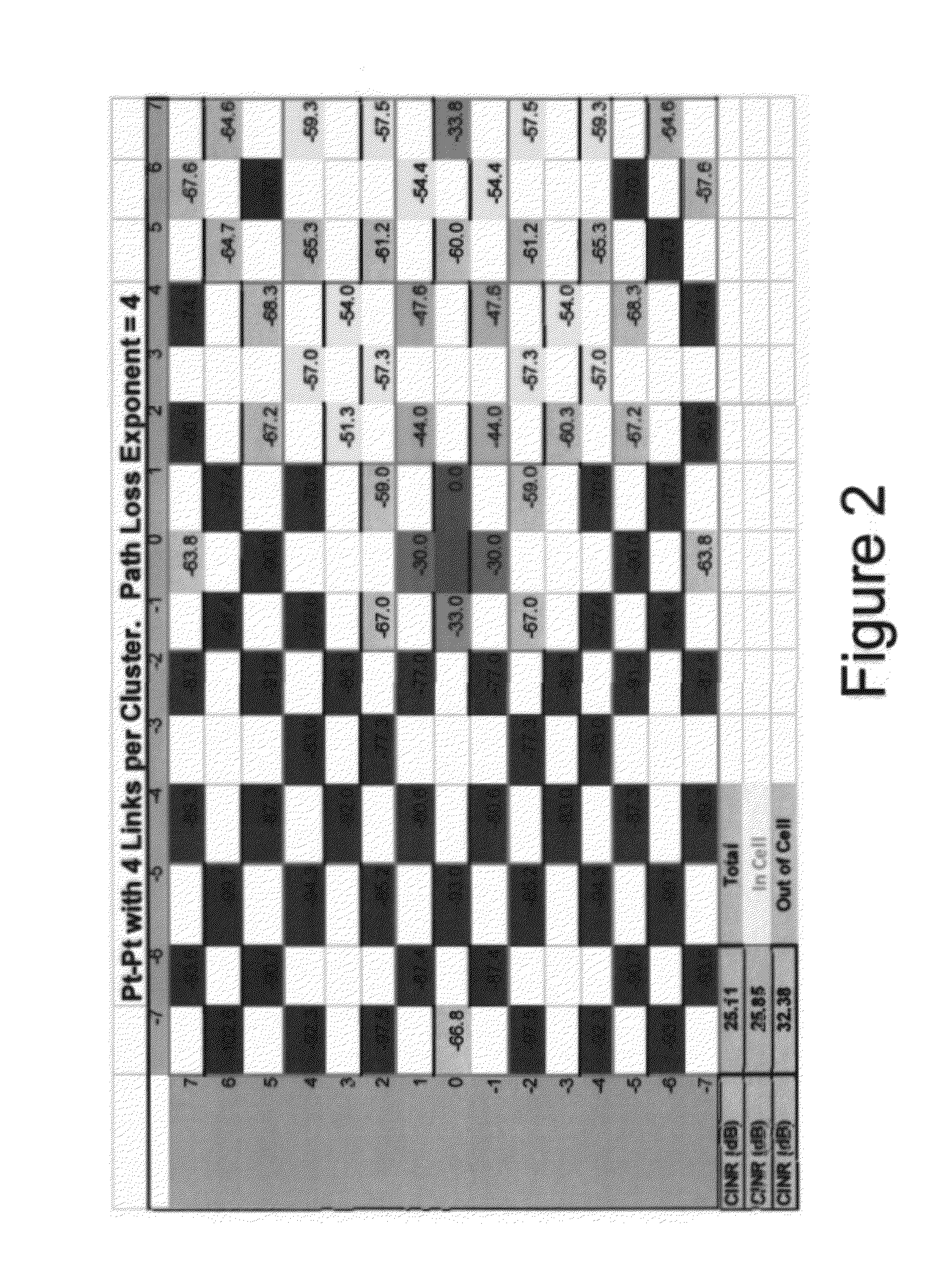
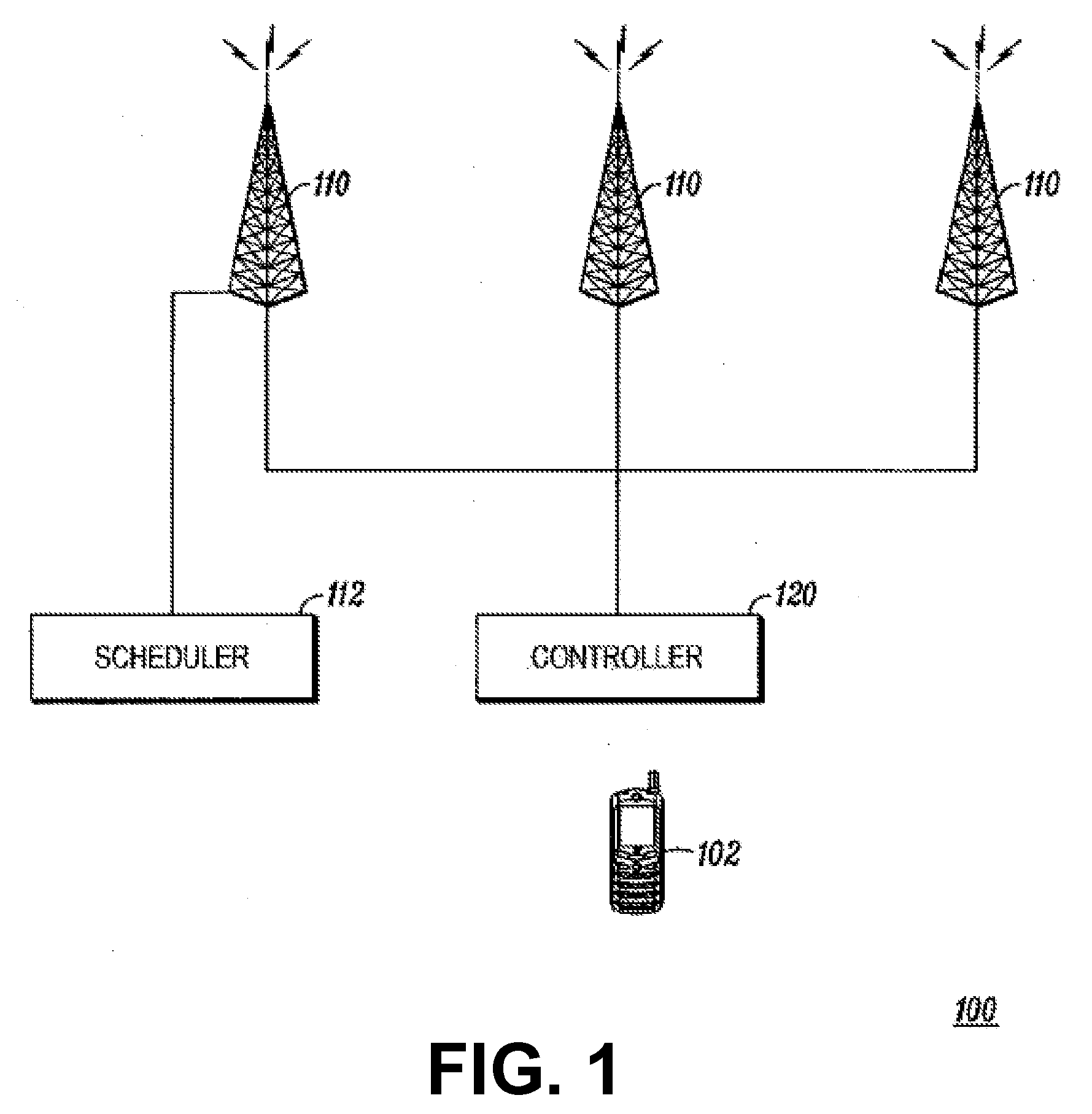
System and Method for Co-Channel Interference Measurement and Managed Adaptive Resource Allocation for Wireless Backhaul
ActiveUS20120236731A1Reduce disadvantagesReduce co-channel interferenceError preventionTransmission systemsResource blockPublic resource
A system, method, and software are provided for measuring co-channel interference in a wireless network with particular application for management of resource allocation for Non Line of Sight (NLOS) wireless backhaul in MicroCell and PicoCell networks. Given the difficulty of predicting the mutual interference between multiple links, DownLink and UpLink co-channel interference are characterized between each Hub and each Remote Backhaul Module Unit periodically during active service. Beneficially, the co-channel interference metrics are used as the basis for intelligently and adaptively managing network resources to substantially reduce interference and increase the aggregate data capacity of the network e.g. by grouping of interfering and / or non-interfering links, and managing resource block allocations accordingly, i.e. assigning common resource blocks preferentially to weakly interfering links or groups of links and allocating different resource blocks or orthogonal channels to strongly interfering links or groups of links.
Owner:BLINQ NETWORKS
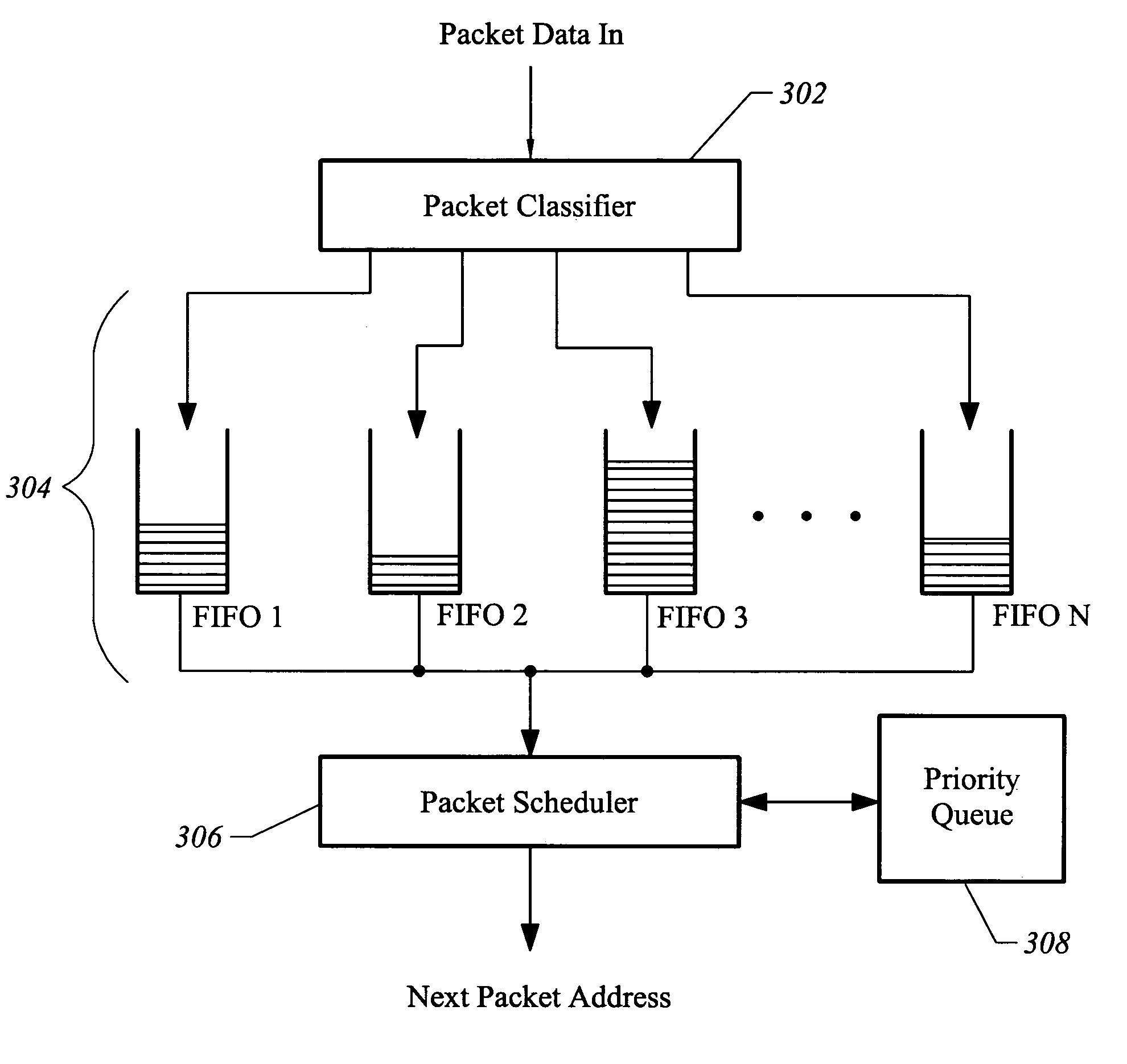
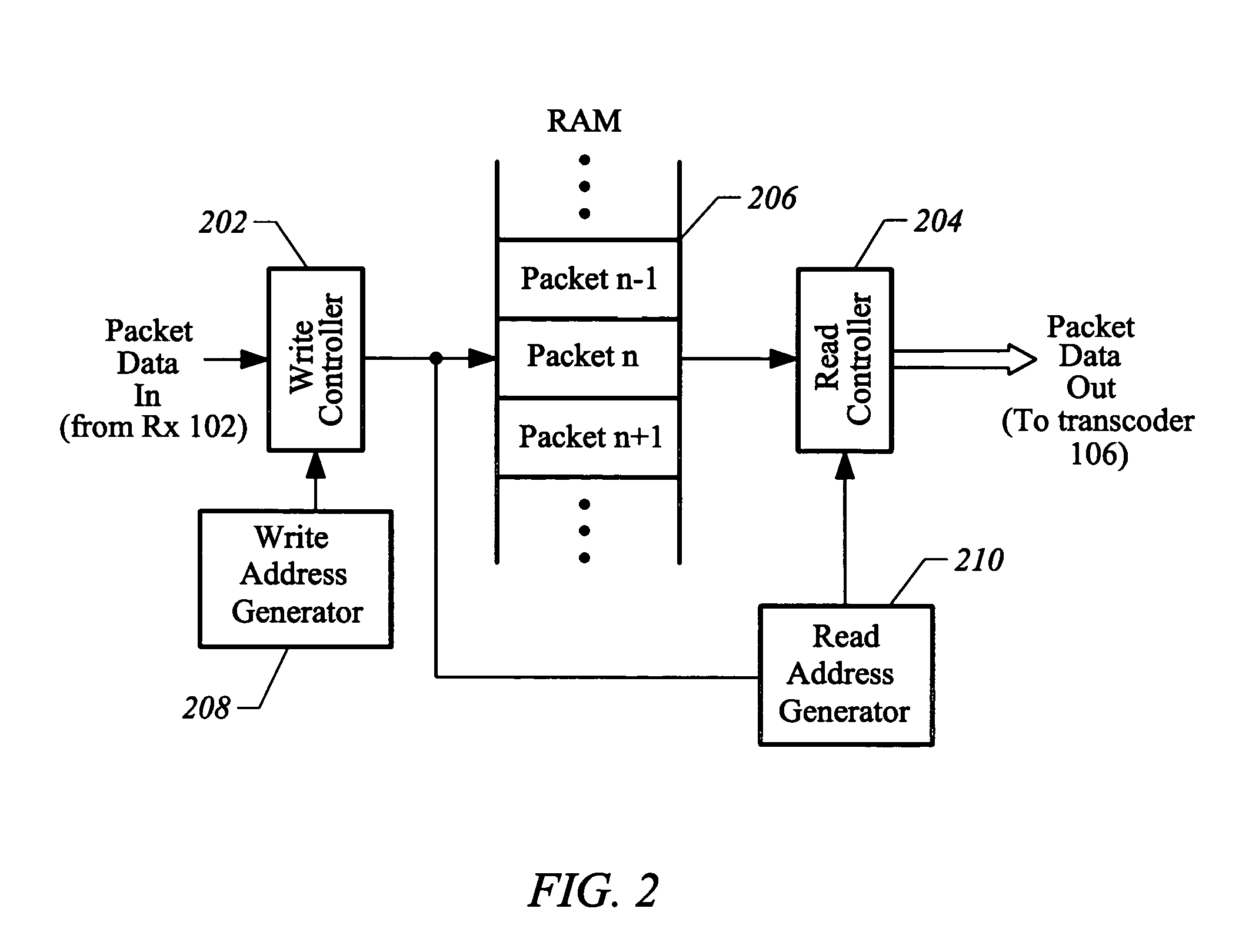
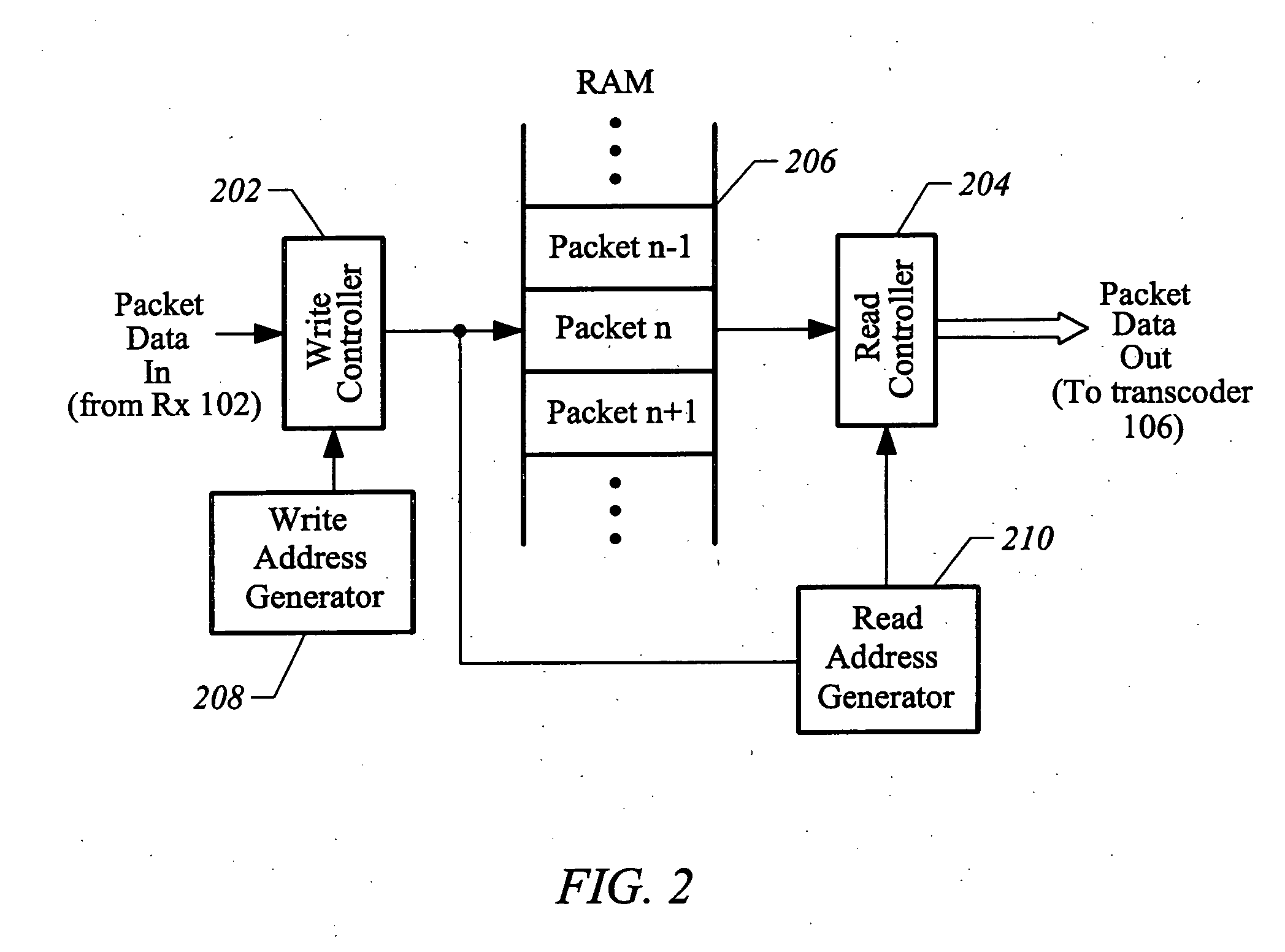
Method and apparatus for time-multiplexed processing of multiple digital video programs
ActiveUS7046677B2Less spaceLow costTelevision system detailsColor television detailsDigital videoData stream
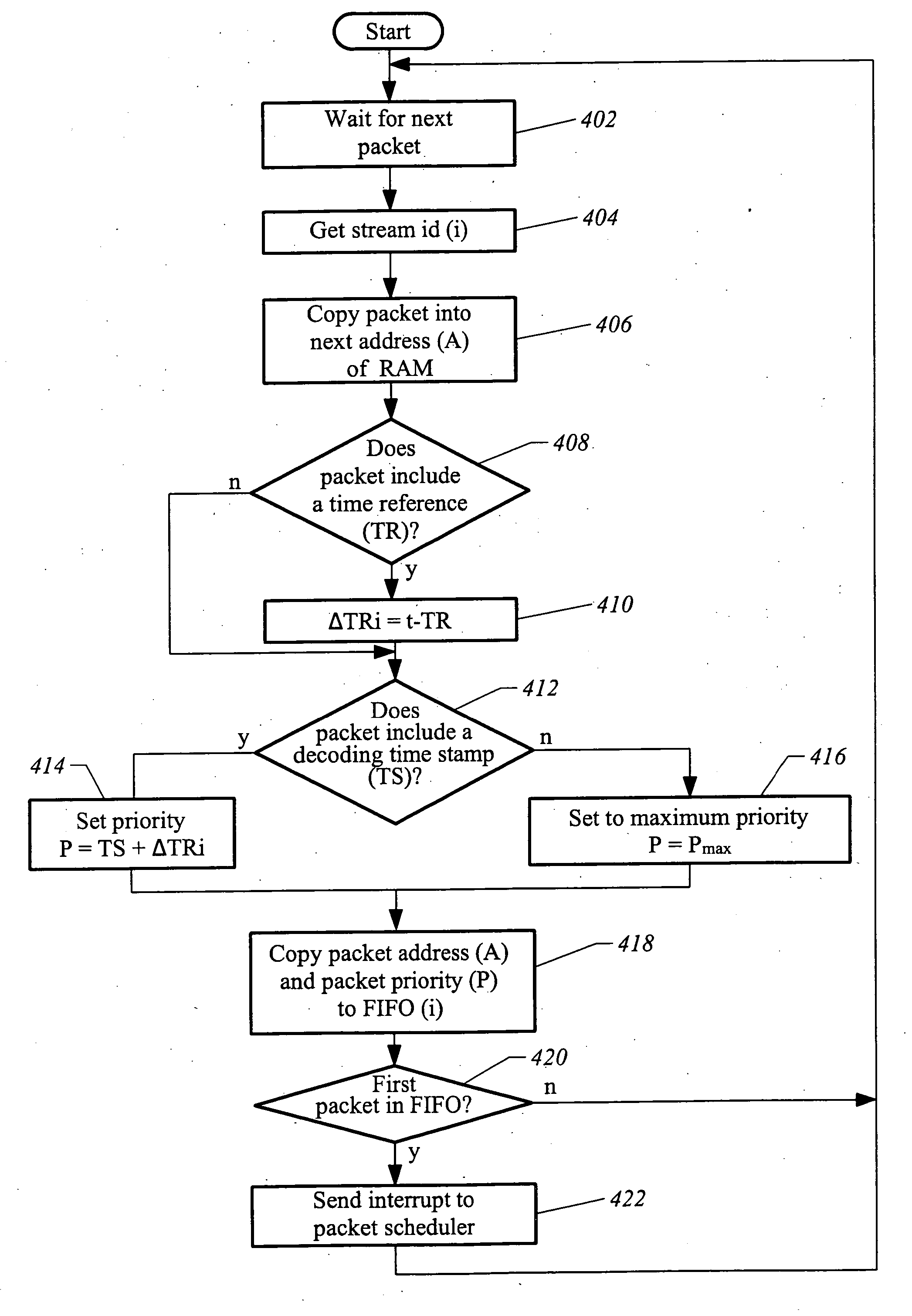
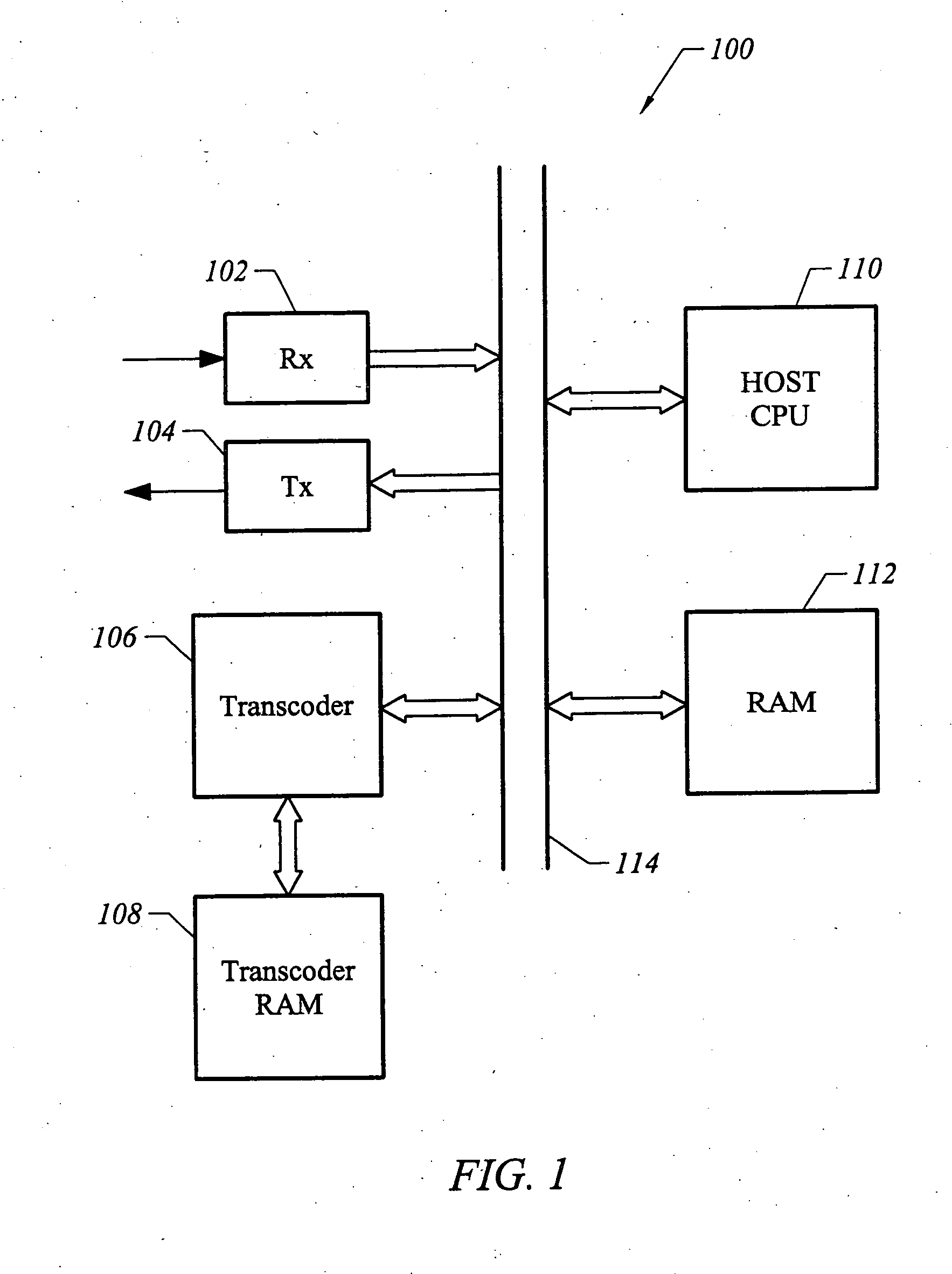
The present invention relates generally to the processing of multiple data streams with common resources. More particularly, this invention relates to a technique for time-multiplexed processing of, for example, multiple digital video programs. In one embodiment, an exemplary method provides for time-multiplexed processing of a set of digital streams includes storing each received packet in a random access memory. For each stream, the deadline for the arrival of the next packet at the receiver is determined and a priority based on the deadline is assigned. The stream with the highest assigned priority is identified as an identified stream. In some embodiments, the processing state of the identified stream is then restored. One or more packets of data corresponding to the identified stream are retrieved from random access memory to produce retrieved packets. The processing state is saved after the retrieved packets have been processed.
Owner:IMAGINE COMM
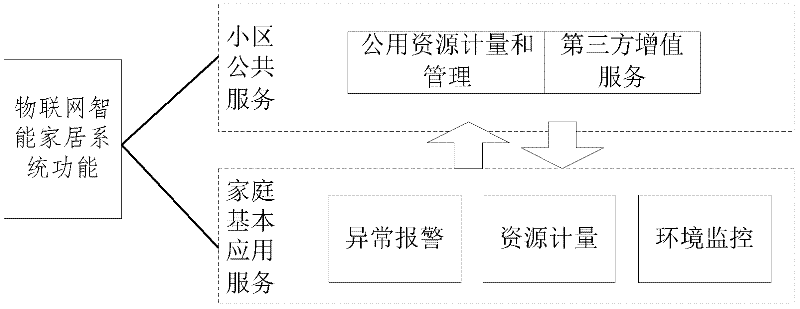
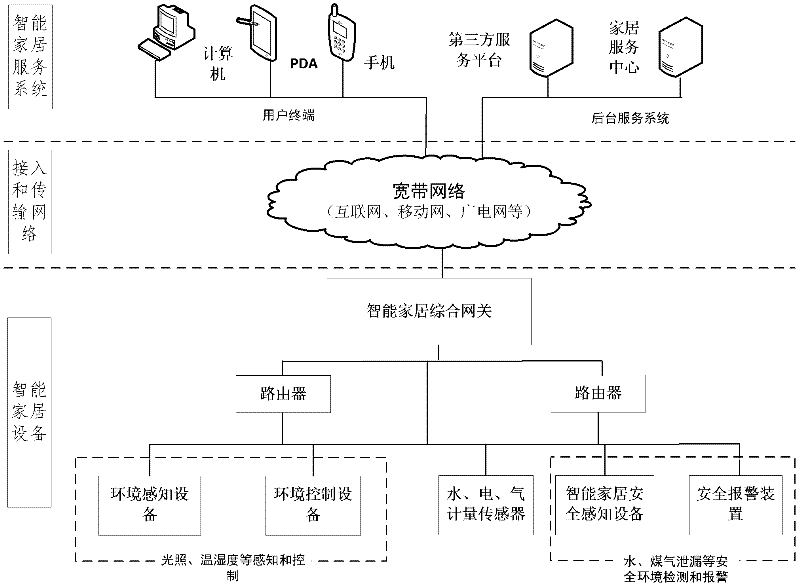
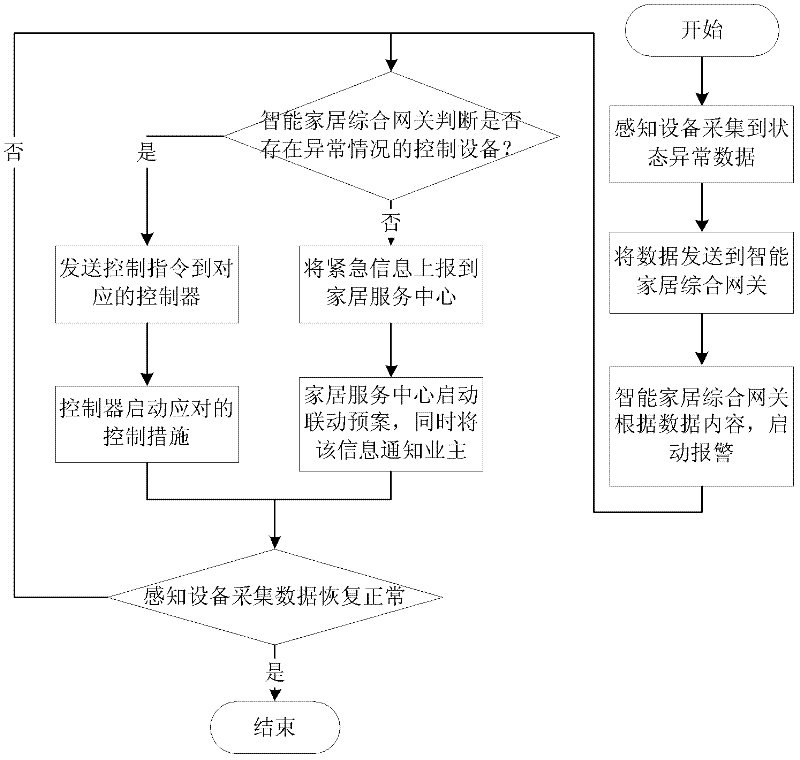
Internet of things intelligent home system and method
The invention discloses an Internet of things intelligent home system and a method. The system comprises intelligent home equipment, an access and transmission network and an intelligent home service system, wherein the intelligent home equipment comprises sensing equipment, control equipment, an alarm device, a router and an intelligent home comprehensive gateway; the access and transmission network is a remote transmission broadband network for finishing interaction between the intelligent home service system and a background service system; and the intelligent home service system comprises a user terminal and the background service system. According to the method, the Internet of things intelligent home system is divided into an intelligent home basic service and a cell public service; the intelligent home basic service comprises abnormal situation alarming, environment monitoring and home energy metering; and the cell public service comprises public resource metering, comprehensive data acquisition and analysis, management and optimization and other services supplied by a third party. The Internet of things intelligent home system can alarm abnormal situations, monitor environments, meter home energy and comprehensively manage and control home information, so that the security of the system is guaranteed.
Owner:感知企银科技(无锡)有限责任公司
Method for realizing intelligent nursing for living of old men
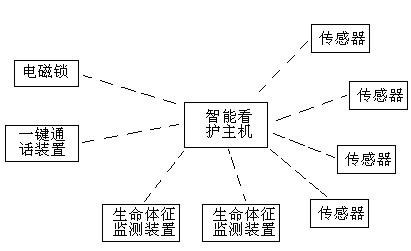
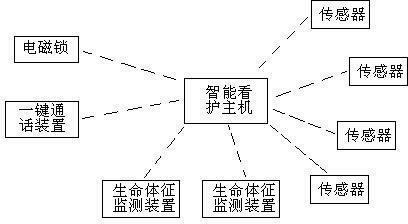
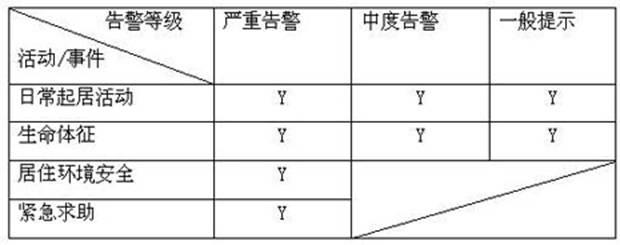
The invention relates to a method for realizing intelligent nursing for the living of old men, which is characterized in that the method comprises an intelligent nursing host as well as a plurality of sensors, a vital sign monitoring device and a push-to-talk device that are in communication with the intelligent nursing host, wherein the intelligent nursing host receives the data of the sensors and the vital sign monitoring device, calculates base lines of all alarm situation parameters through a multi-parameter base line algorithm, compares the base lines and a threshold set in a system, alarms and classifies the comparison result and informs the comparison result to a designated subscriber. According to the method, the activities such as the daily routine, the physical conditions and the emergency as well as the anomalous events of the home-care old men can be monitored, recorded and alarmed, so that relatives and friends or communities or social public resources can give the rescue or intervention for the old men timely, thereby improving the independence of the old men and the living quality of the old men and family members of the old men.
Owner:ECARE SMARTTECH INC
Sharing resources in a wireless communication system
InactiveUS20070274288A1Transmission path divisionData switching by path configurationCommunications systemPublic resource
Owner:MOTOROLA INC
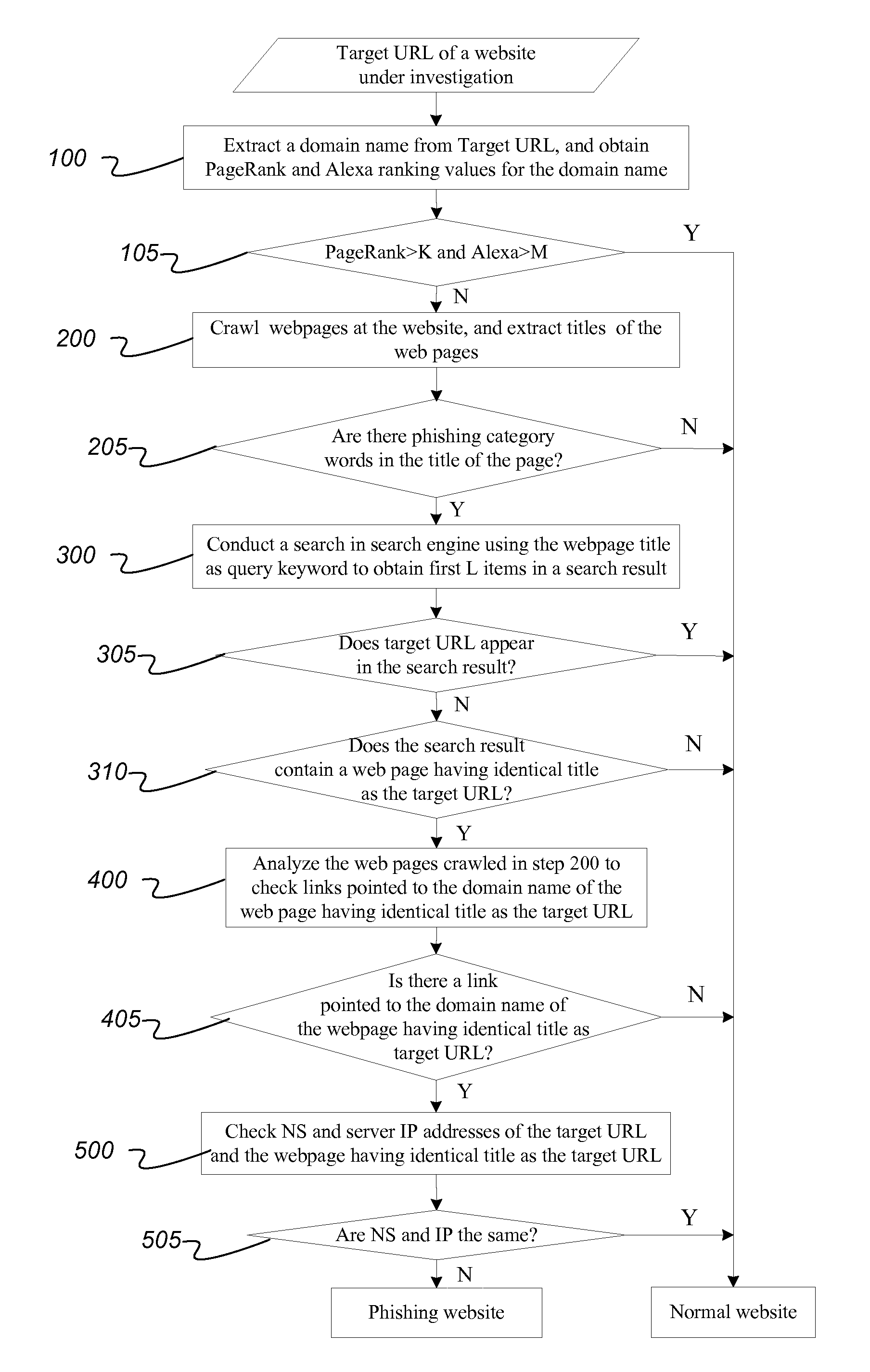
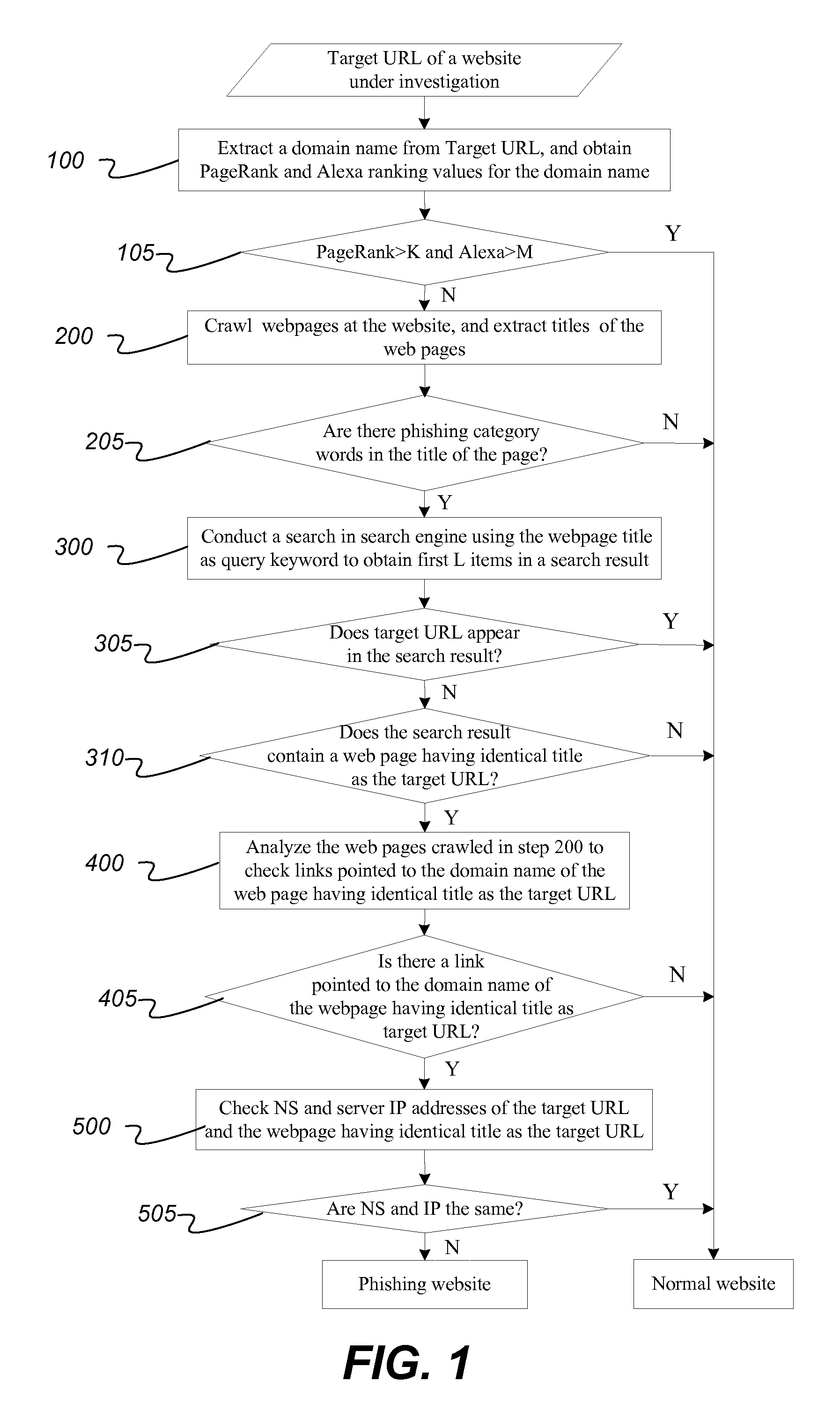
Method for detecting phishing website without depending on samples
ActiveUS20150200963A1Easy to useOvercome difficultiesWeb data indexingMemory loss protectionDomain nameIp address
A method for detecting a phishing website includes extracting a domain name from a target URL of a web page under investigation, and querying PageRank and / or Alexa ranking of the domain name; extracting a title character string from the title of the web page and matching the character string to phishing sensitive words; using the title of web page as a keyword to search on a search engine; querying whether Target URL and the web page in the search result with a same title as the web page under investigation have the same domain name server NS and server IP address to determine whether the website is a phishing website. The disclosed method utilizes common features of phishing websites and public resources on the Internet, and overcomes the difficulty in collecting phishing website samples, and is well adapted to detecting phishing aimed at new target websites.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
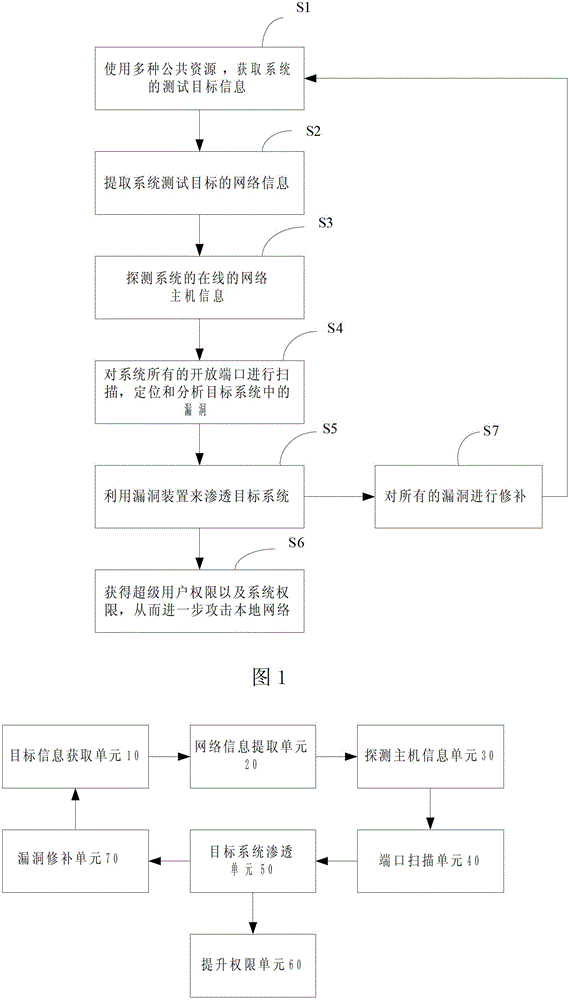
Method and device for system penetration testing
ActiveCN104009881ASpotting weaknessesDiscover securityData switching networksSystem testingPublic resource
The invention discloses a method for system penetration testing, comprising the following steps: S1, test target information of a system is acquired by use of a variety of public resources; S2, network information of a system test target is extracted; S3, online network host information of the system is detected; S4, all open ports of the system are scanned, and all services are enumerated through all the ports to position and analyze a loophole in the target system; and S5, the target system is penetrated by a loophole device. The invention further discloses a device for system penetration testing. By adopting the method and the device, provided by the invention, for system penetration testing, through static analysis of a source code, on one hand, potential risks can be identified, software can be detected from inside, and the safety of the code can be improved, and on the other hand, the quality of the code can be further improved, and the software security can be greatly improved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
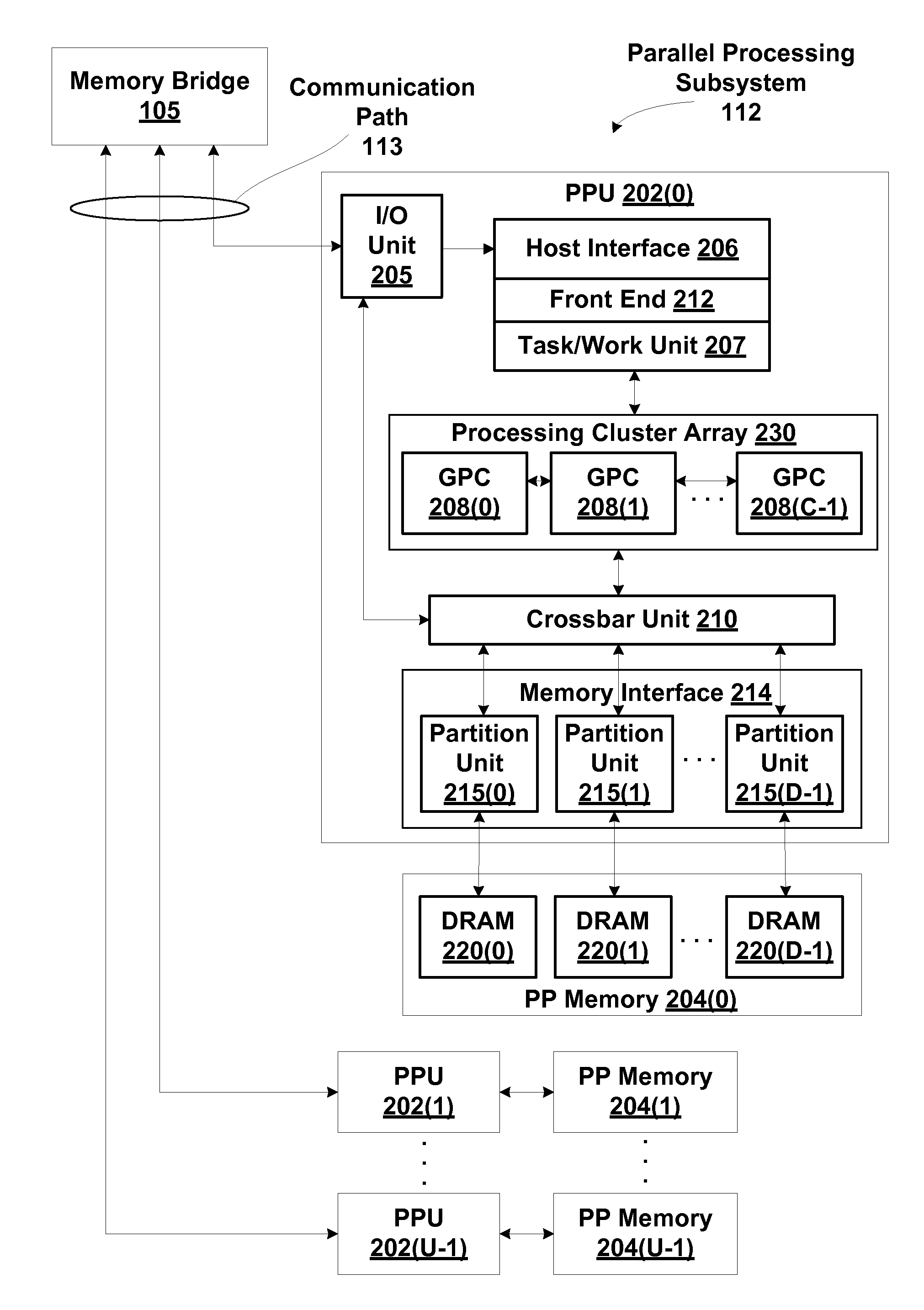
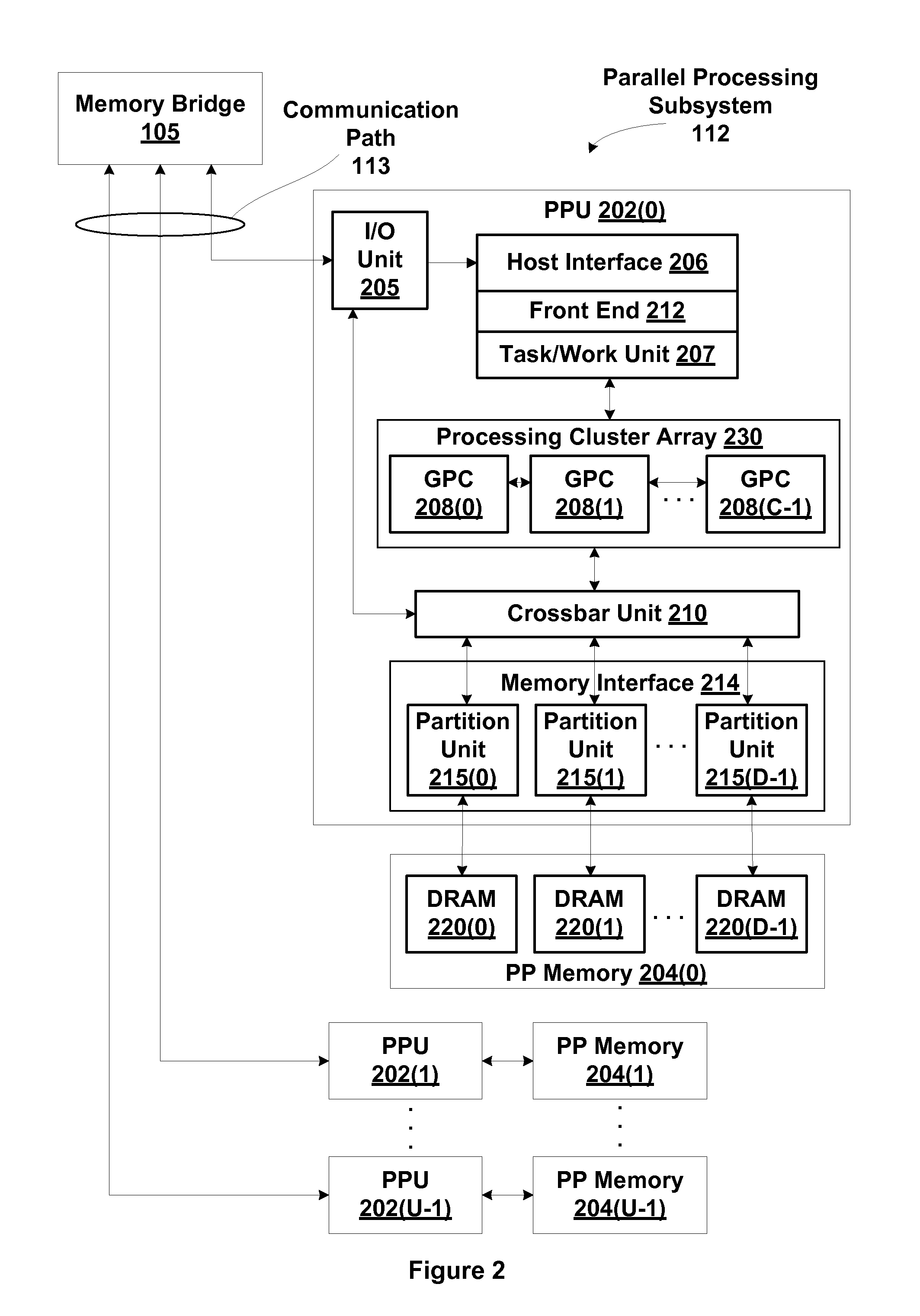
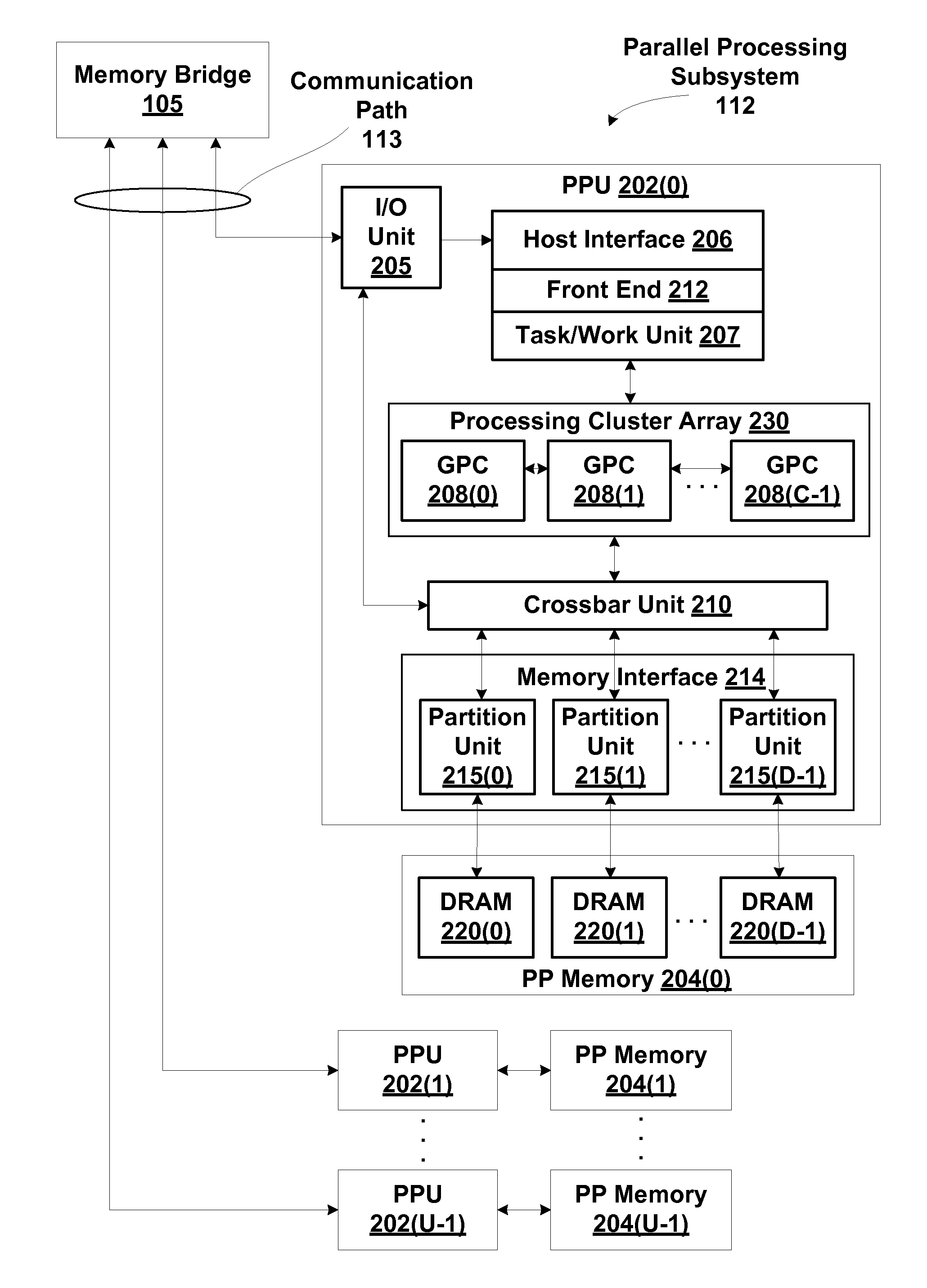
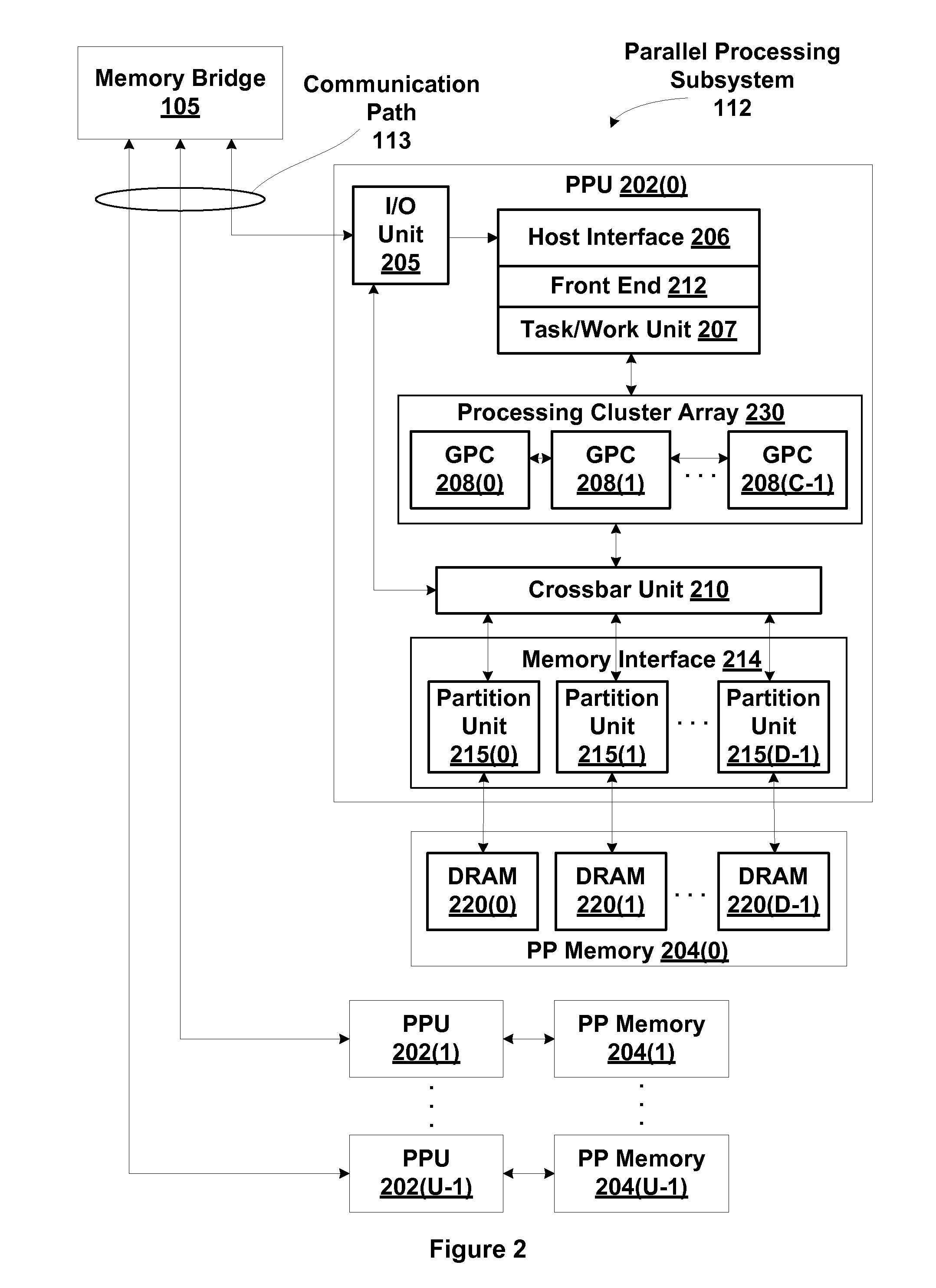
Mechanism for tracking age of common resource requests within a resource management subsystem
One embodiment of the present disclosure sets forth an effective way to maintain fairness and order in the scheduling of common resource access requests related to replay operations. Specifically, a streaming multiprocessor (SM) includes a total order queue (TOQ) configured to schedule the access requests over one or more execution cycles. Access requests are allowed to make forward progress when needed common resources have been allocated to the request. Where multiple access requests require the same common resource, priority is given to the older access request. Access requests may be placed in a sleep state pending availability of certain common resources. Deadlock may be avoided by allowing an older access request to steal resources from a younger resource request. One advantage of the disclosed technique is that older common resource access requests are not repeatedly blocked from making forward progress by newer access requests.
Owner:NVIDIA CORP
Allocation method and device for resource pool
ActiveCN102761469AEnsure reasonable planningTake advantage ofNetwork traffic/resource managementData switching networksResource poolPublic resource
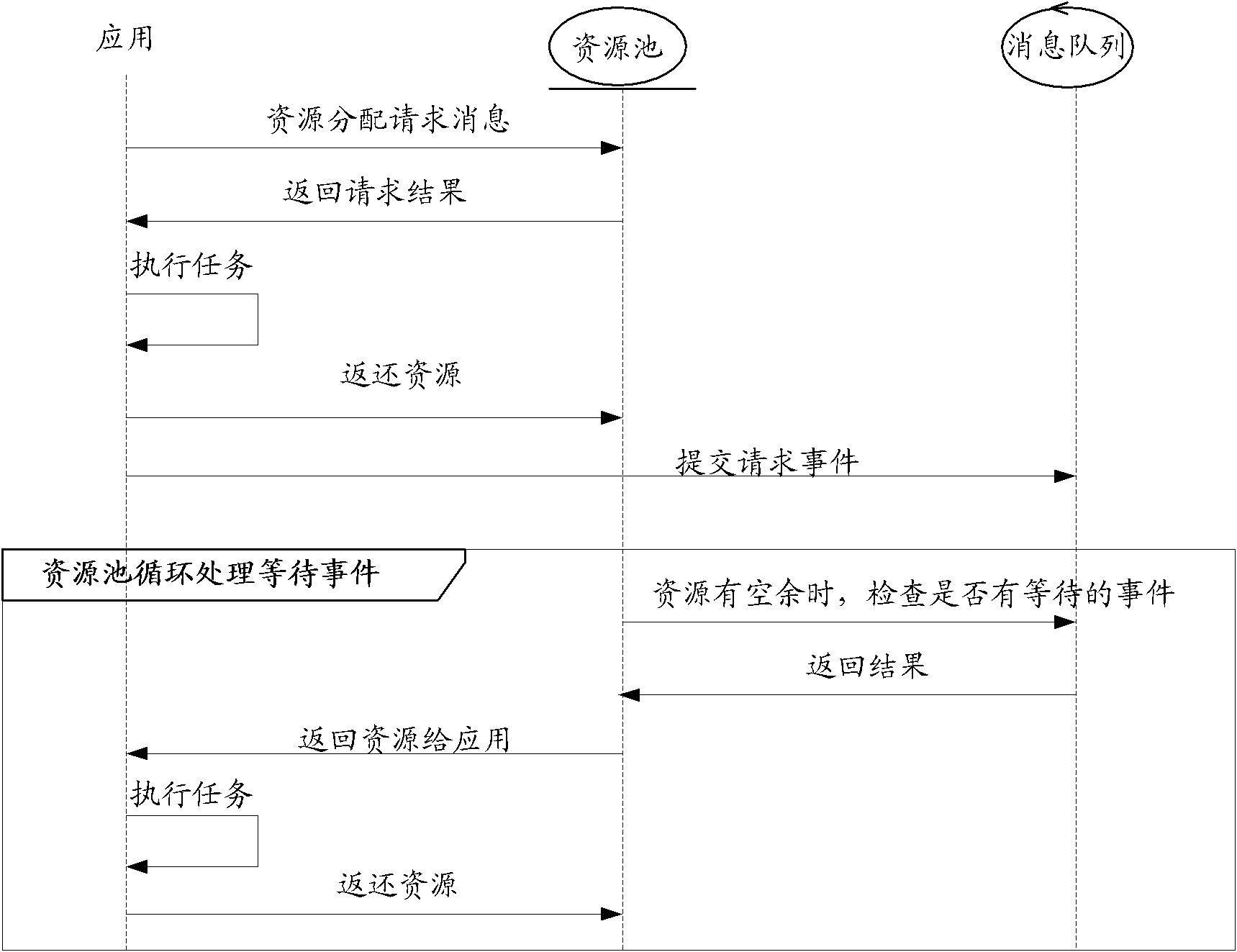
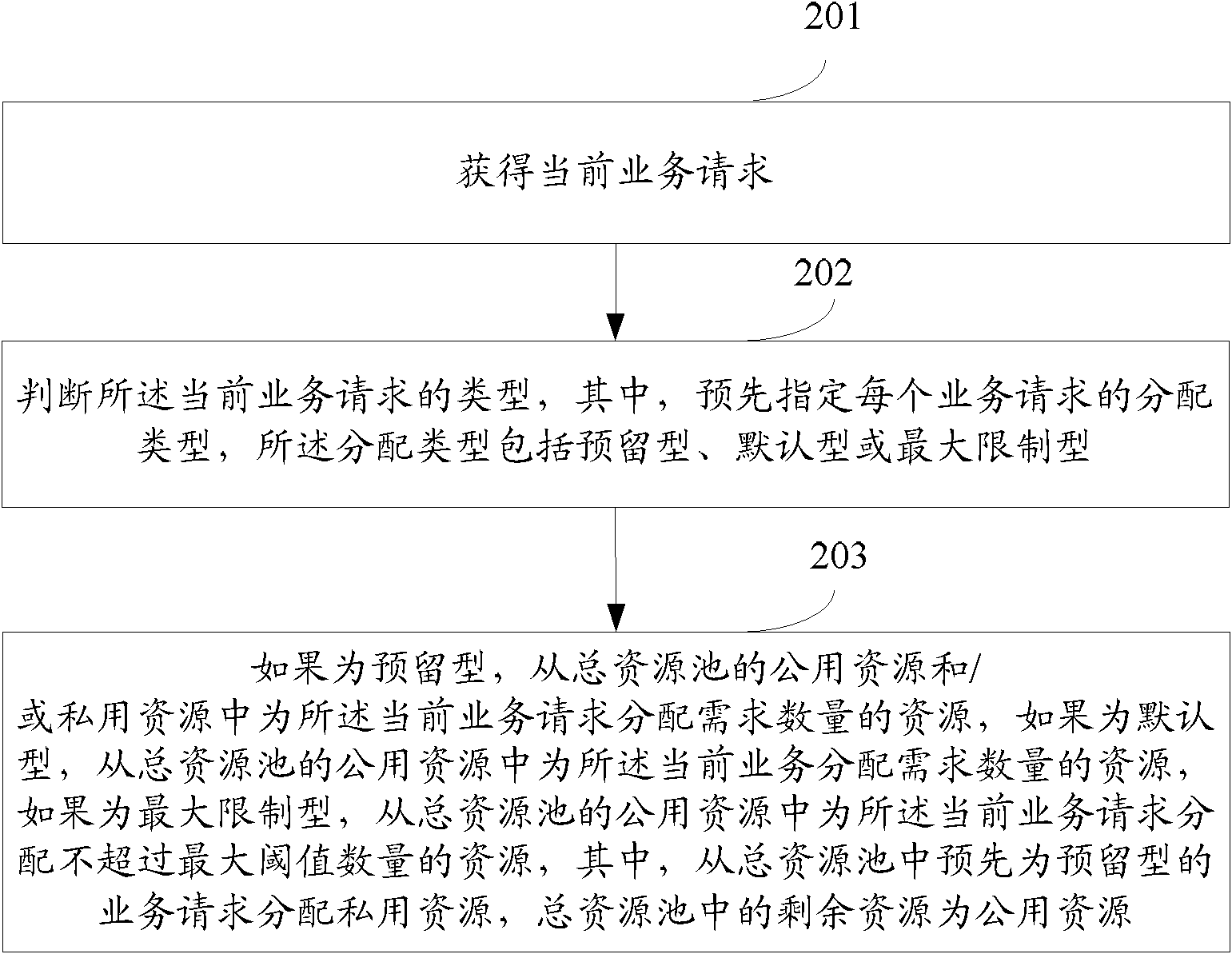
The embodiment of the application discloses an allocation method and device for a resource pool, wherein the allocation method comprises the following steps: acquiring a current business request; judging the allocation type of the current business request; if the allocation type is reserved type, allocating the required quantity of resources for the current business request from public resources and / or private resources of the total resource pool; if the allocation type is default type, allocating the required quantity of resources for the current business request from the public resources of the total resource pool; and if the allocation type is maximum limit type, allocating the resources which do not exceed the maximum threshold quantity for the current business request from the public resources of the total resource pool. According to the embodiment of the application, the utilization rate of the resource pool can be improved.
Owner:阿里巴巴(中国)网络技术有限公司
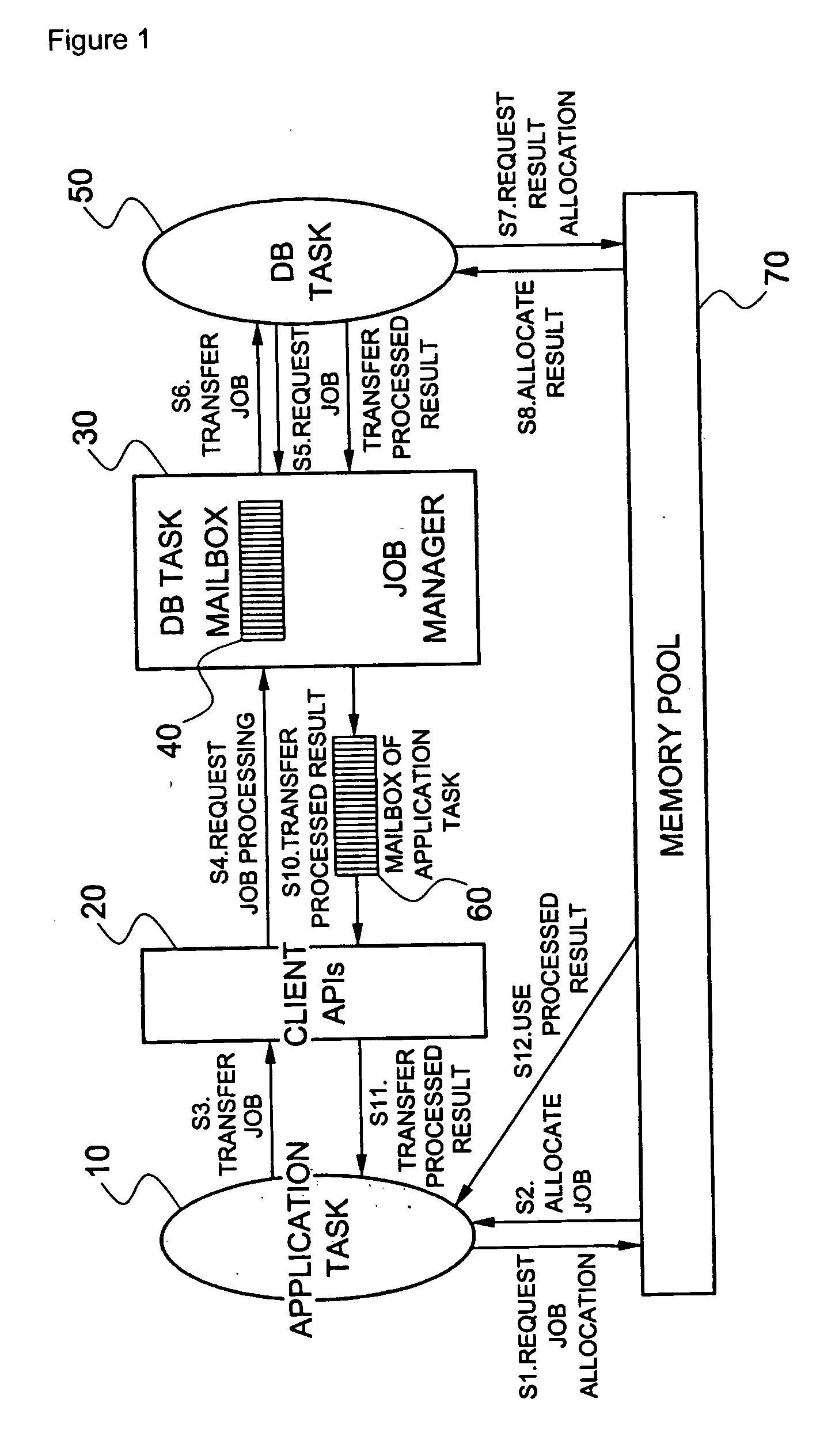
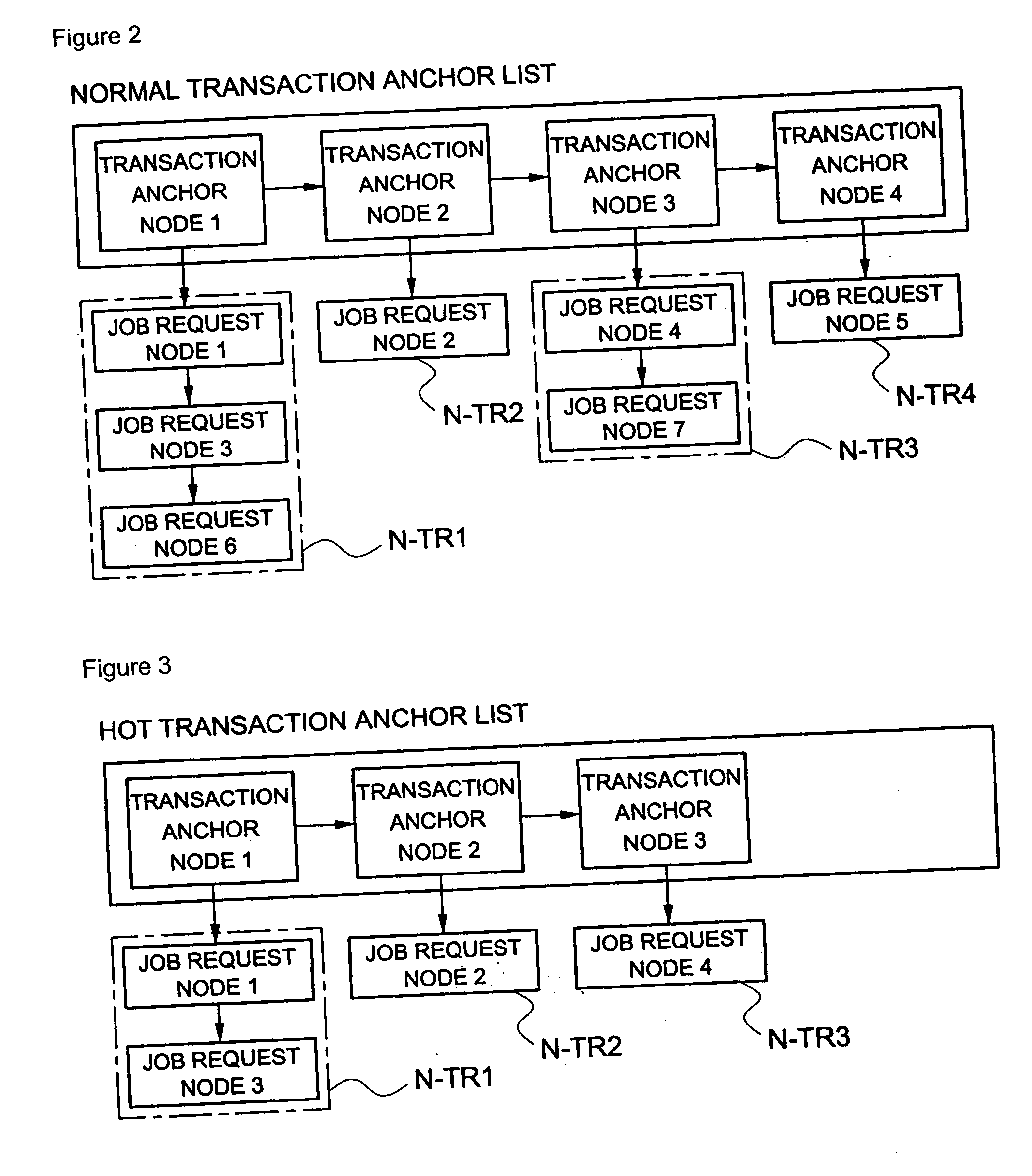
Method of scheduling jobs using database management system for real-time processing
InactiveUS20060206894A1Easy to handleSuitable for processingProgram control using stored programsMultiprogramming arrangementsOperation schedulingPublic resource
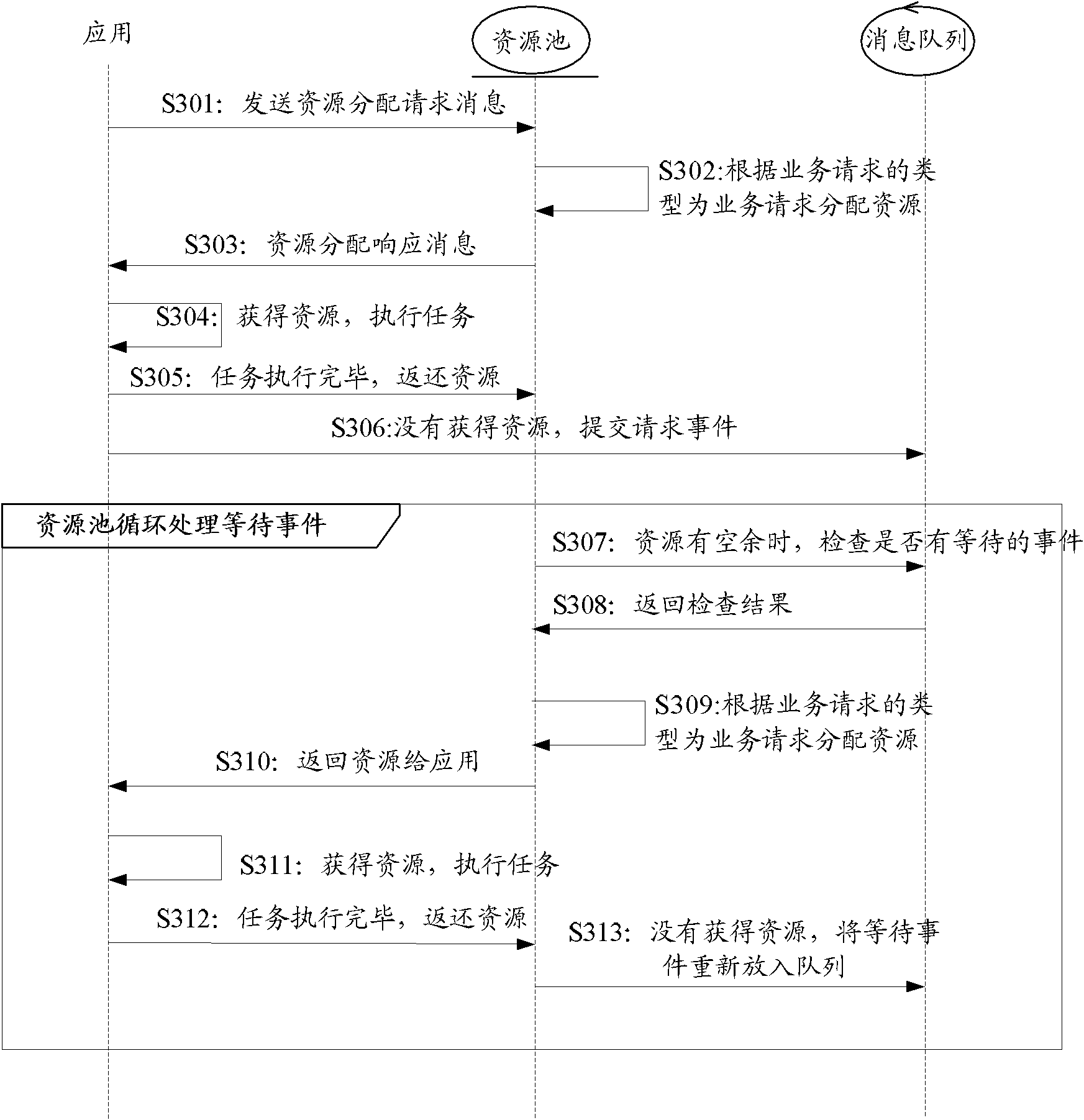
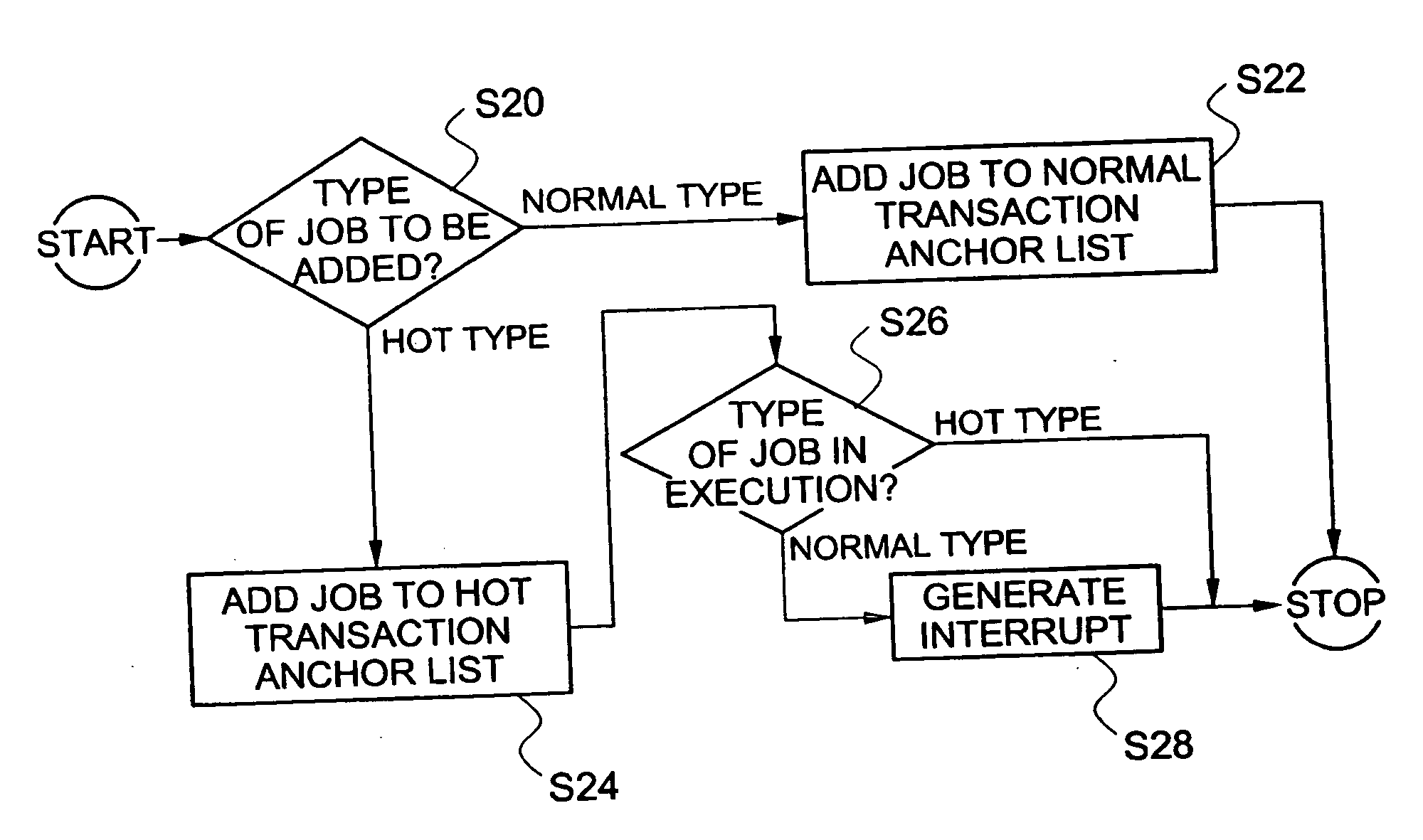
A method of scheduling jobs in real time using a database management system is provided. An application task classifies jobs as any one transaction type of a hot type and a normal type. A processing area in a memory pool that is a common resource is allocated to the application task, and the job is transferred to a database job manager through a client application program interface (API). The job manager loads a request node of the job in a list of a transaction type corresponding to the job, of a mailbox of the DB task, which classifies job request nodes as the hot type and the normal type with respect to the type of transaction and manages the nodes, so that the job request node can be scheduled in units of transactions. The job manager transfers the job request nodes loaded in the mailbox for the DB task, one by one to the DB task so that the job request nodes can be processed in units of transactions in a manner in which a job corresponding to a hot-type transaction is processed with a priority over a job corresponding to a normal-type transaction, and between jobs of an identical truncation type, jobs are processed in order of job requesting time. The DB task loads through the job manager, the processing result of the job in a mailbox of the application task which requested the processing of the job, so that the corresponding application task can use the processing result in the future.
Owner:FUSIONSOFT
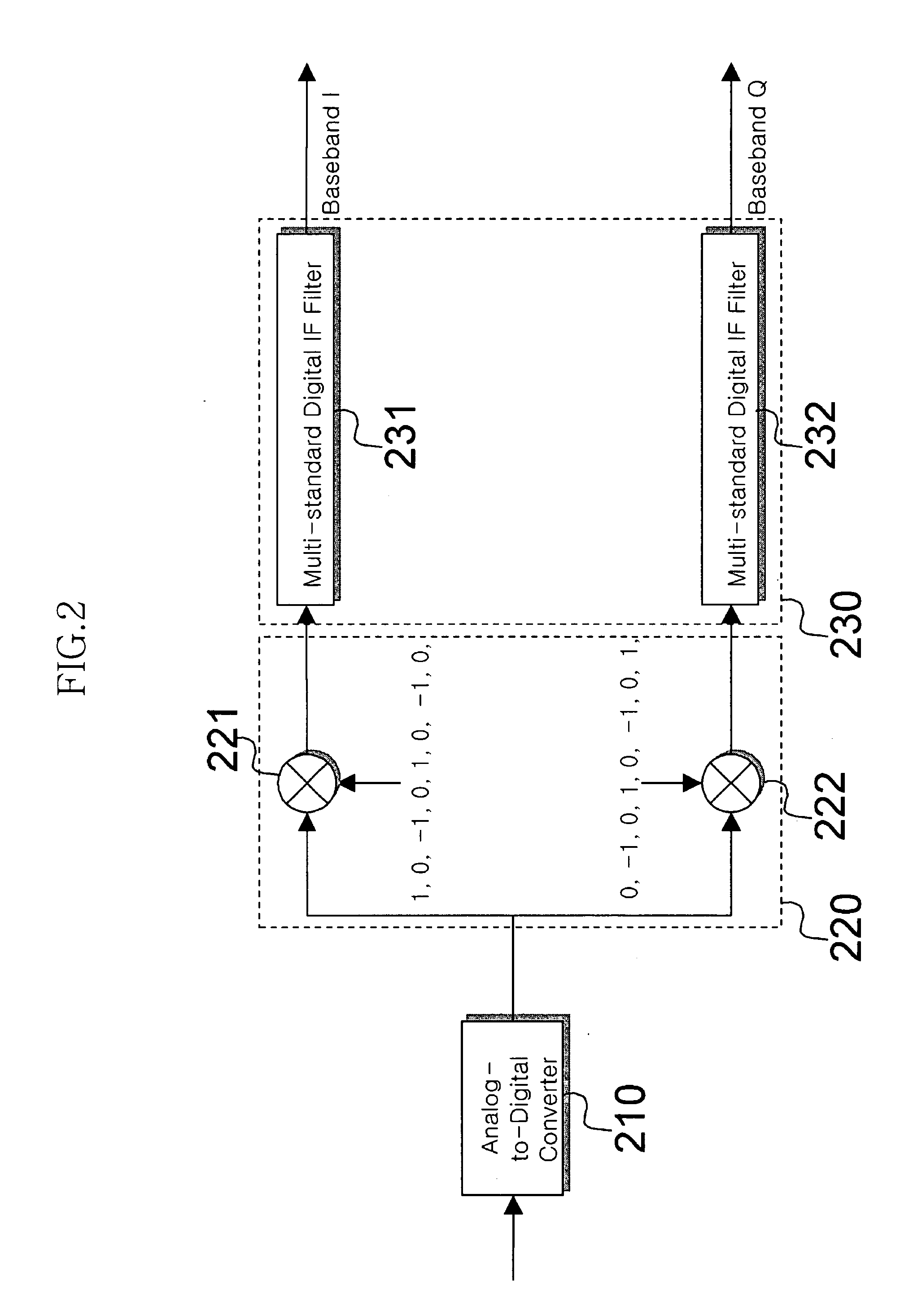
Digital filter for software-defined radio system, digital intermediate frequency signal processing apparatus having the digital filter, and method thereof
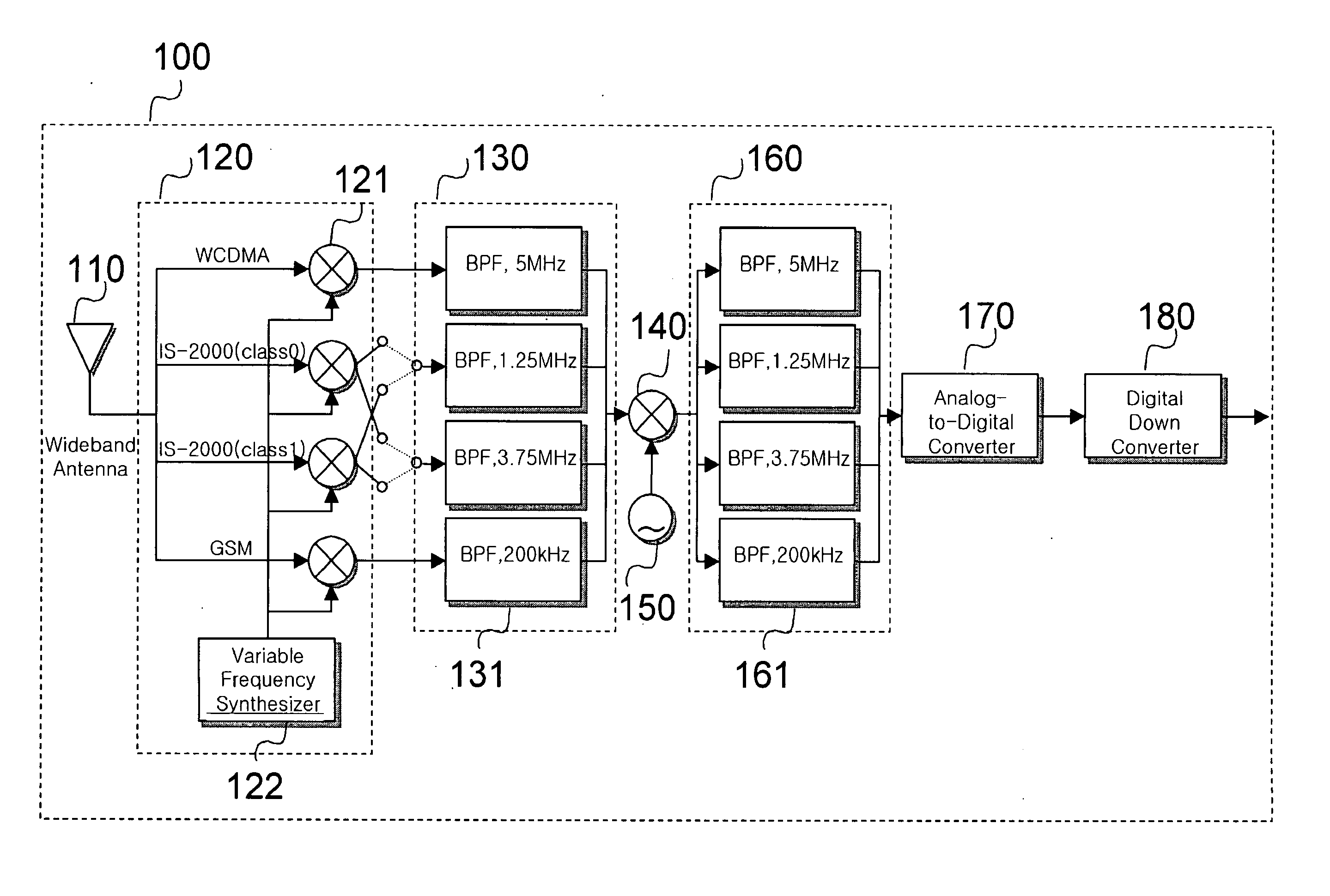
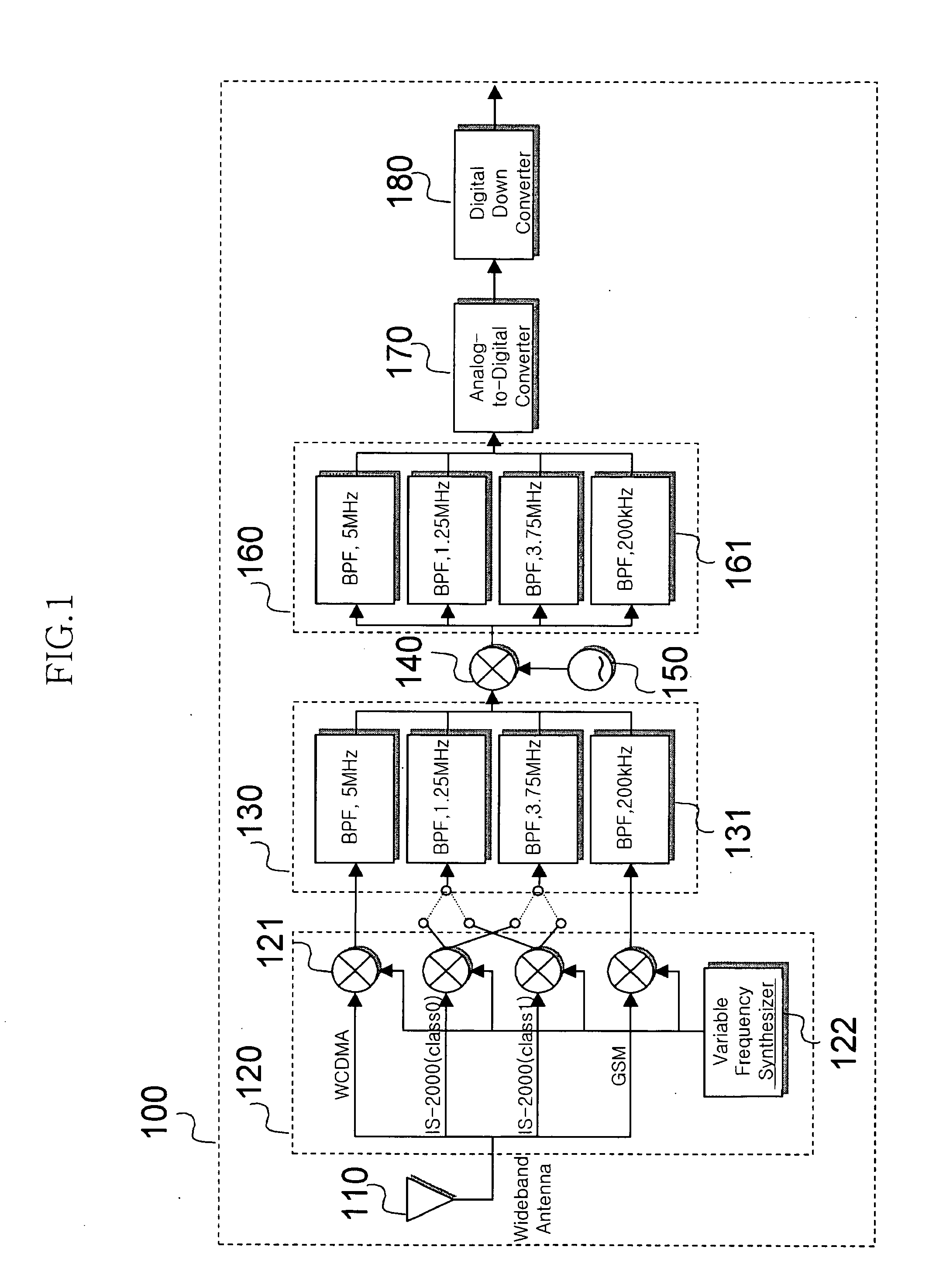
InactiveUS20050032480A1Low costMinimizes filter structureMultiple modulation transmitter/receiver arrangementsCommunications systemSoftware define radio
Disclosed is a receiver digital filter for a digital IF signal processor suitable for the specification of each communication standard in a communication system that supports at least one communication standard. The filter for each standard is constructed as one block, and includes a block for externally implementing the constructed block. The coefficient of the digital filter constructed in one block is implemented with an external input or an internal filter coefficient calculator by a basic filter building block. In this manner, the common resources required in the digital filter used in each communication standard are shared, and only the additionally required resources are selectively implemented. Since the shared resources are calculated by dynamic programming, a considerably smaller number of additional resources are required.
Owner:ELECTRONICS & TELECOMM RES INST
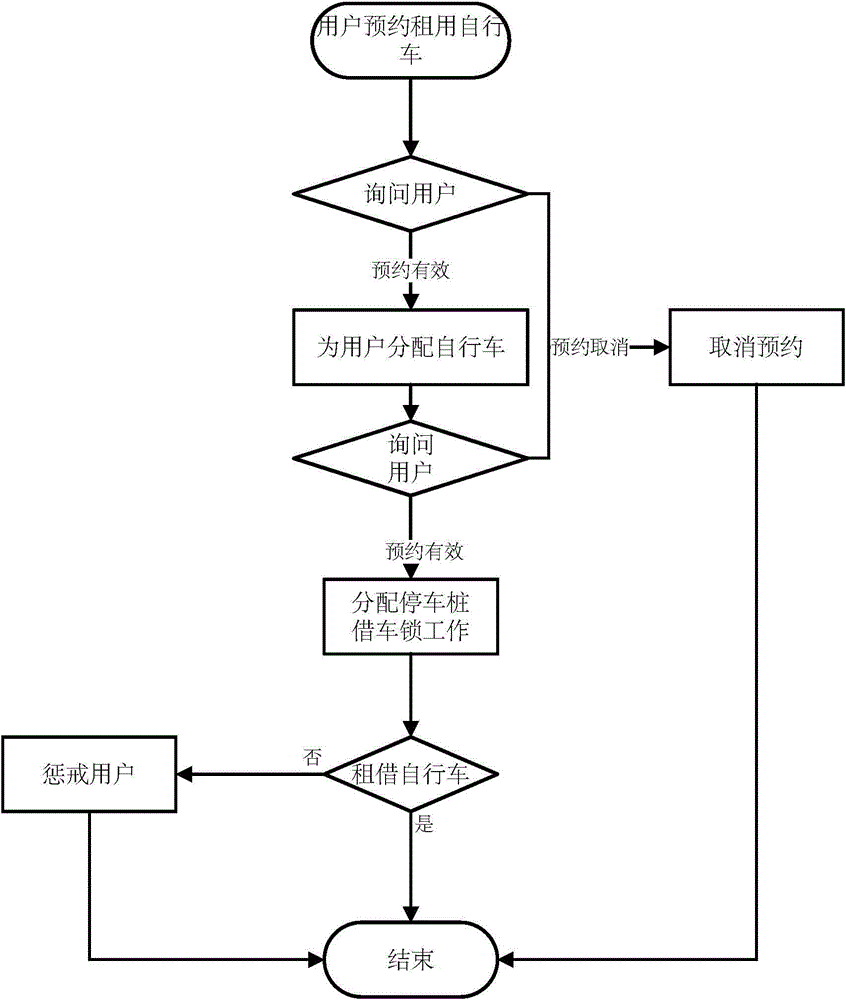
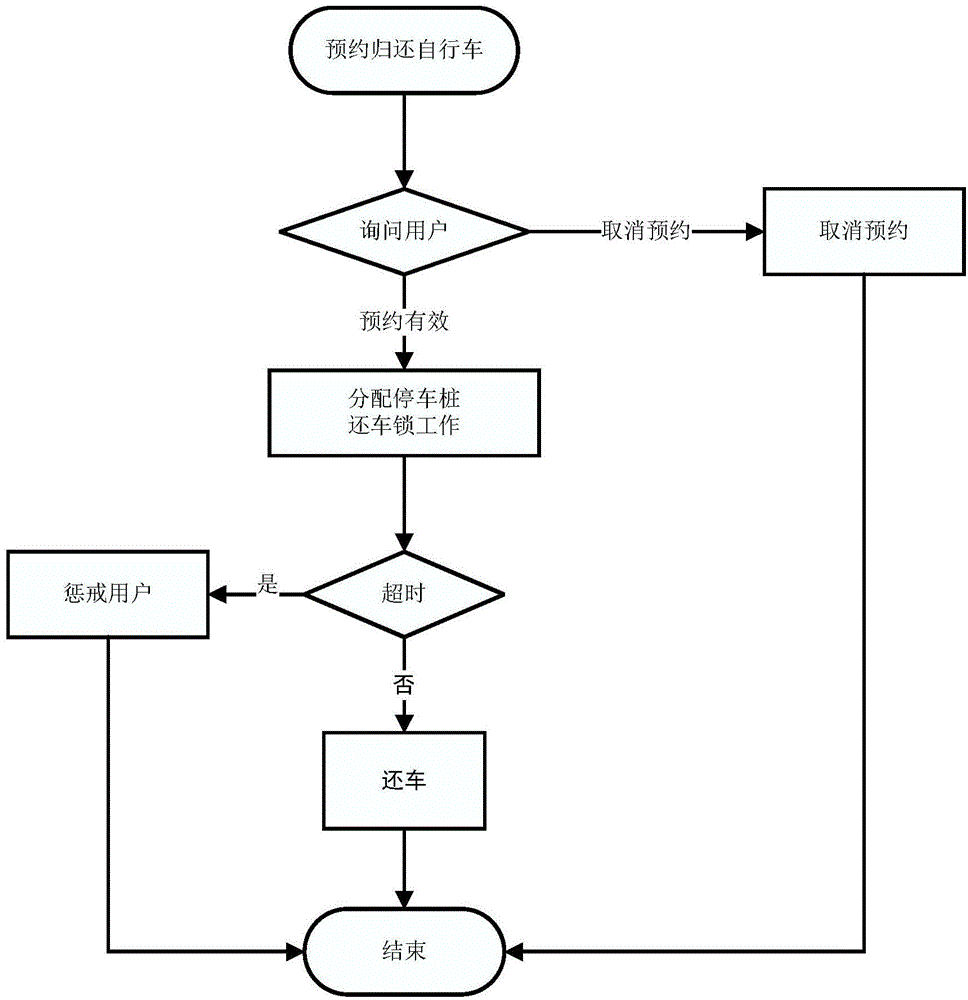
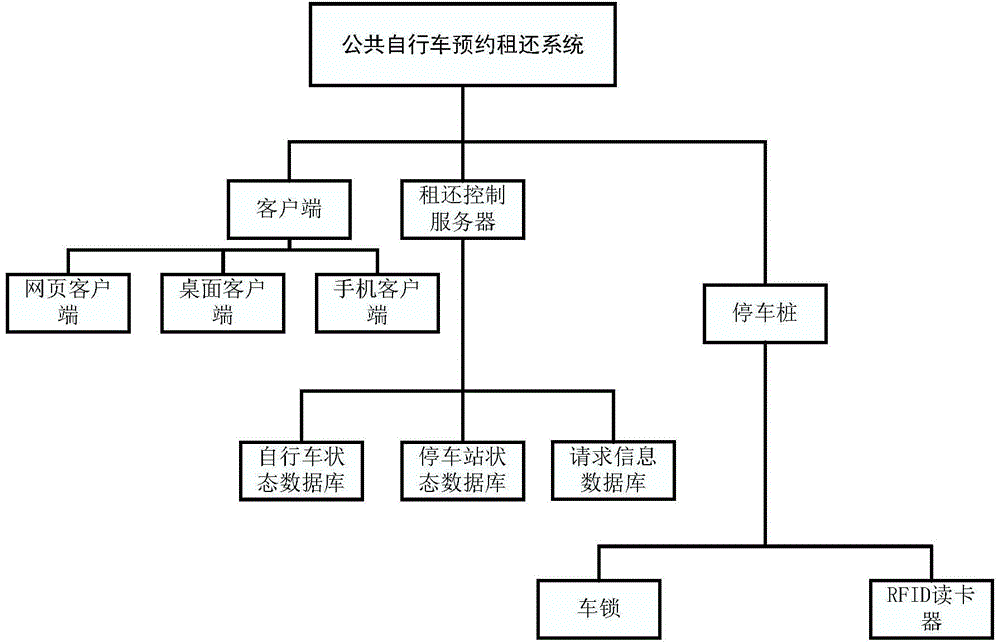
Public bicycle ordering, renting and returning system and realizing method thereof
InactiveCN104464104AImprove management efficiencyImprove resource utilizationApparatus for meter-controlled dispensingSpecial data processing applicationsParking spacePublic resource
The invention relates to a public bicycle renting system and a realizing method of the public bicycle renting system, in particular to a public bicycle ordering, renting and returning system and a realizing method of the public bicycle ordering, renting and returning system. The public bicycle ordering, renting and returning system comprises a public bicycle, a client side, an identity authentication module, a renting and returning control server and a parking pile, wherein the parking pile comprises a lock and an identity authentication module recognition device, the renting and returning control server is used for storing and processing user information, and it is guaranteed that a user can successfully order, rent or return the bicycle through the method that the bicycle or the parking pile is reserved for the user. The public bicycle ordering, renting and returning system and the realizing method of the public bicycle ordering, renting and returning system can predict the demand conditions of public bicycles and parking lots, so that a management company can dispatch the public bicycles in time to balance public resources according to the demand, and the management efficiency of a public bicycle company and the utilization rate of public resources can be improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Master baseboard management controller election and replacement sub-system enabling decentralized resource management control
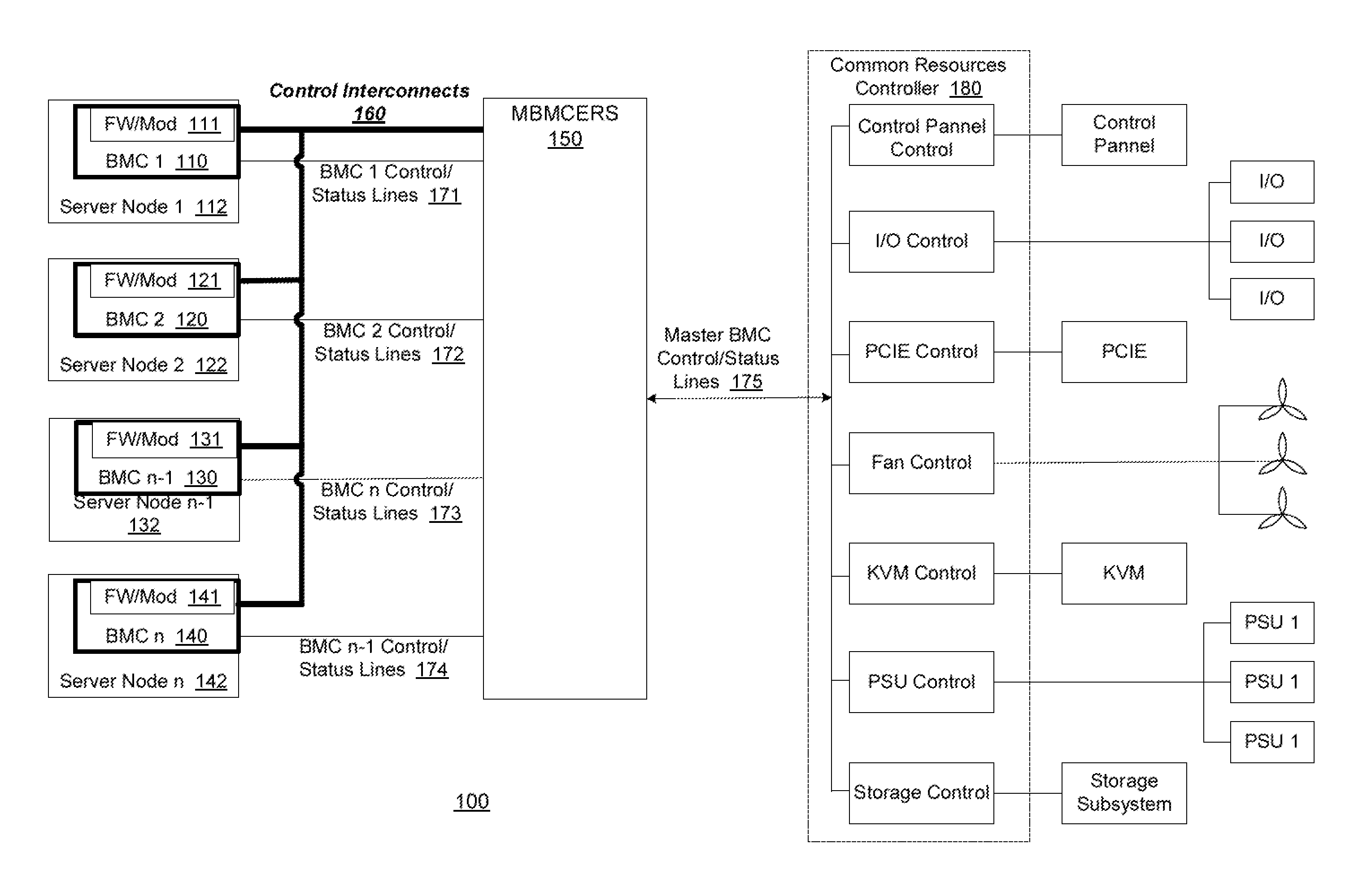
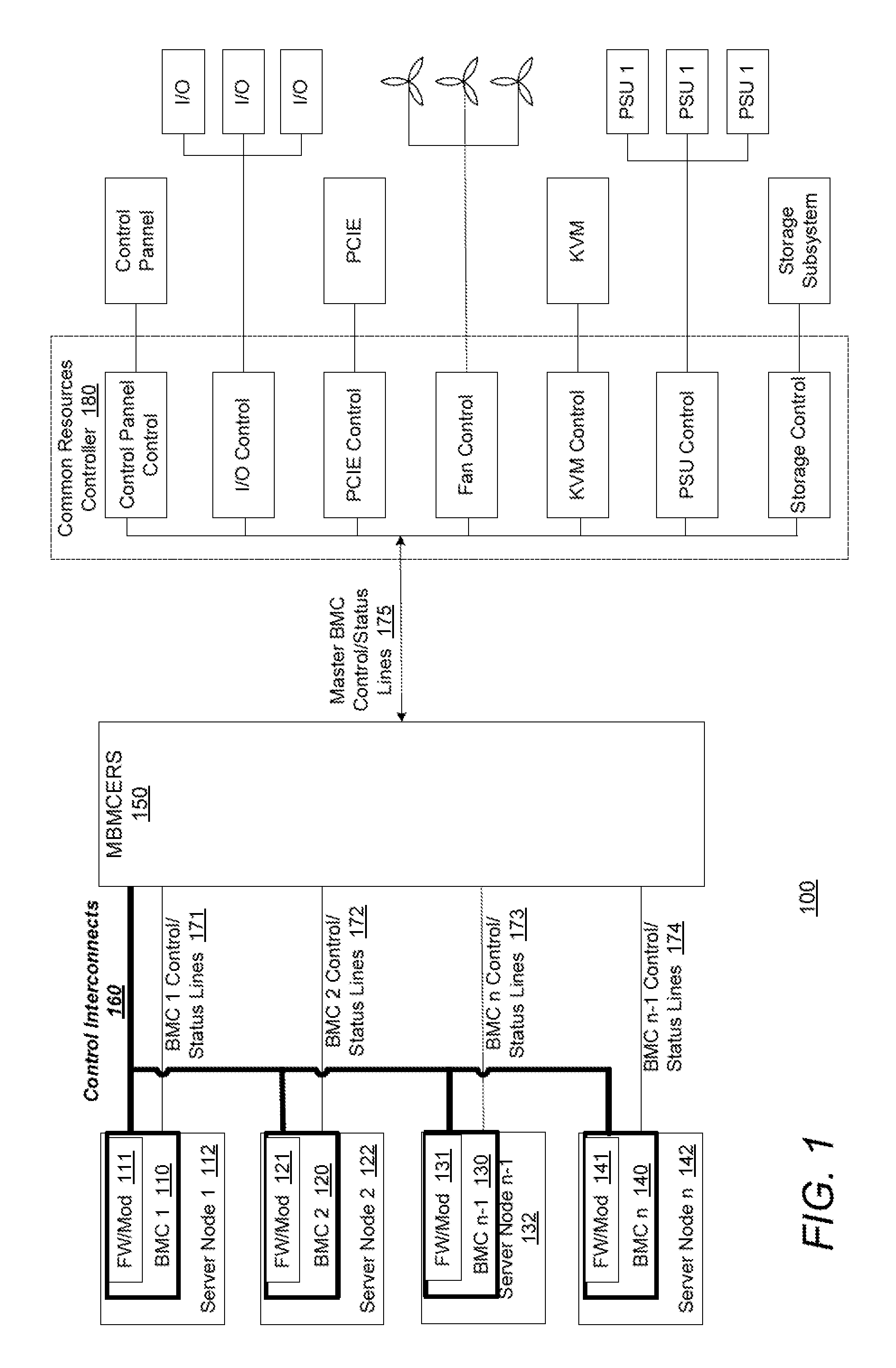
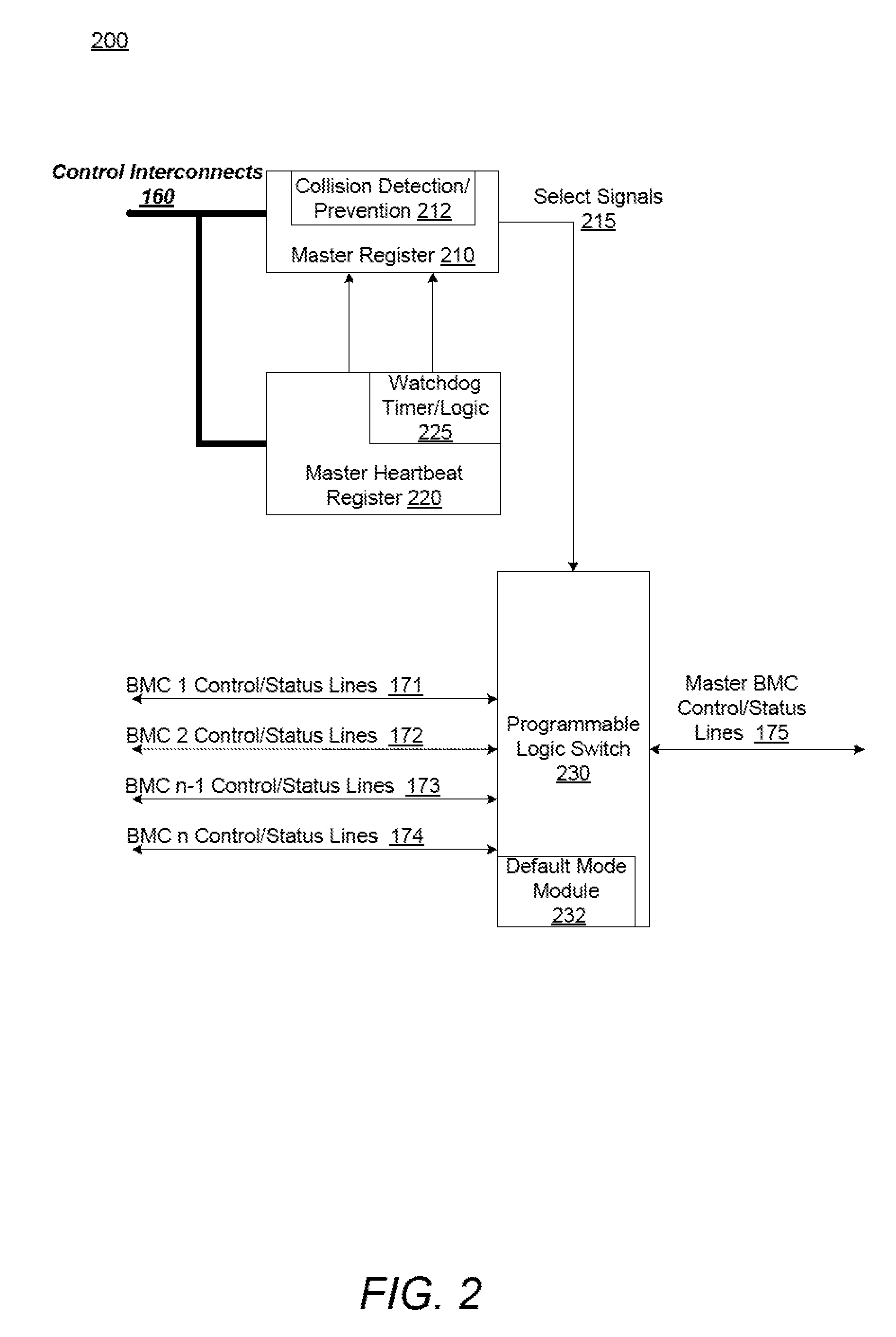
An information handling system and method of a master baseboard management controller election and replacement sub-system (MBMCERS) enables decentralized resource management control via the elected master baseboard management controller (BMC). The information handling system includes a plurality of server nodes, each having a BMC capable of controlling a plurality of shared common resources among the plurality of server nodes. Each BMC has a unique BMC identification. A master register stores BMC identification that has been elected as the master BMC to control the shared common resources. The master BMC relinquishes control of the shared common resources when the master register is placed in the reset state. When the master register is in the reset state, any one of the BMCs can elect to become a replacement master BMC.
Owner:DELL PROD LP
Parking information system
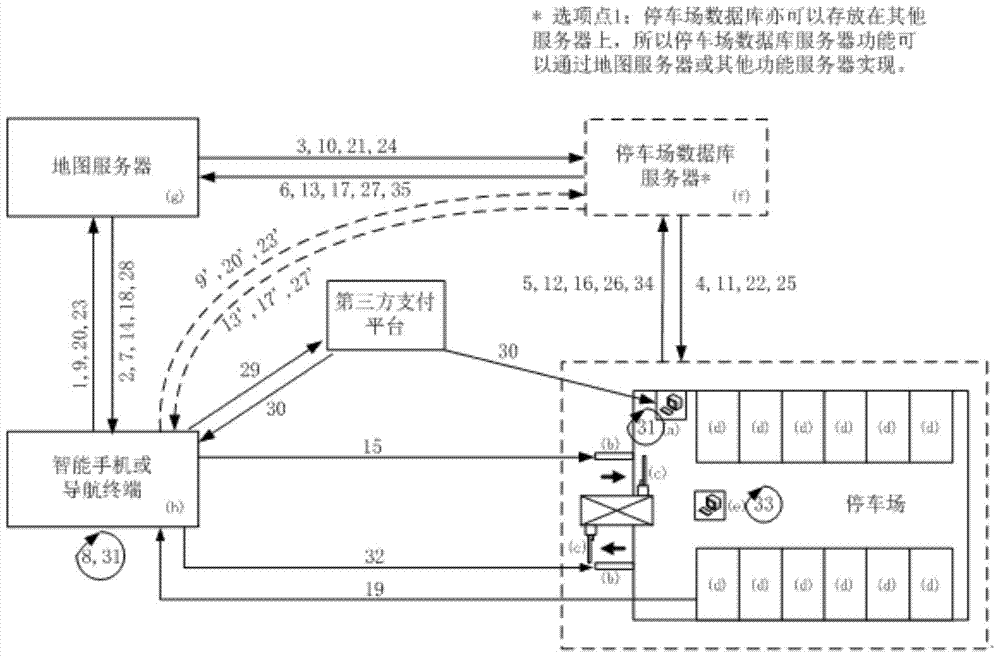
ActiveCN104851318AImprove accuracyImprove recycling efficiencyTicket-issuing apparatusIndication of parksing free spacesGeolocationPublic resource
The invention relates to a parking information system comprising: a, a parking lot management system terminal; b, an automatic card dispenser, card reading box or two-dimension code scanner; c, entrance and exit gates; d, parking spaces respectively with a parking space two-dimension code; e, a parking lot payment terminal; f, a parking lot database server; g, a map server; and h, a smart phone or navigation terminal. Information such as the geographical location, the number of empty parking spaces and the parking fee of a parking lot and online map information are integrated to improve the accuracy of the parking guidance function among online map navigation functions. The information about a parking lot is accurately released in real time and effectively managed to improve the recycling efficiency of the parking spaces in the parking lot and improve the user experience of drivers in the appointment and payment processes. The user experience of drivers in the process of parking lot and parking space confirmation is improved through functions such as confirmation with voice and gestures. Finally, the time is reduced for drivers, fuel consumption is reduced, and the use efficiency of parking lots and other public resources of the society is improved.
Owner:李丹
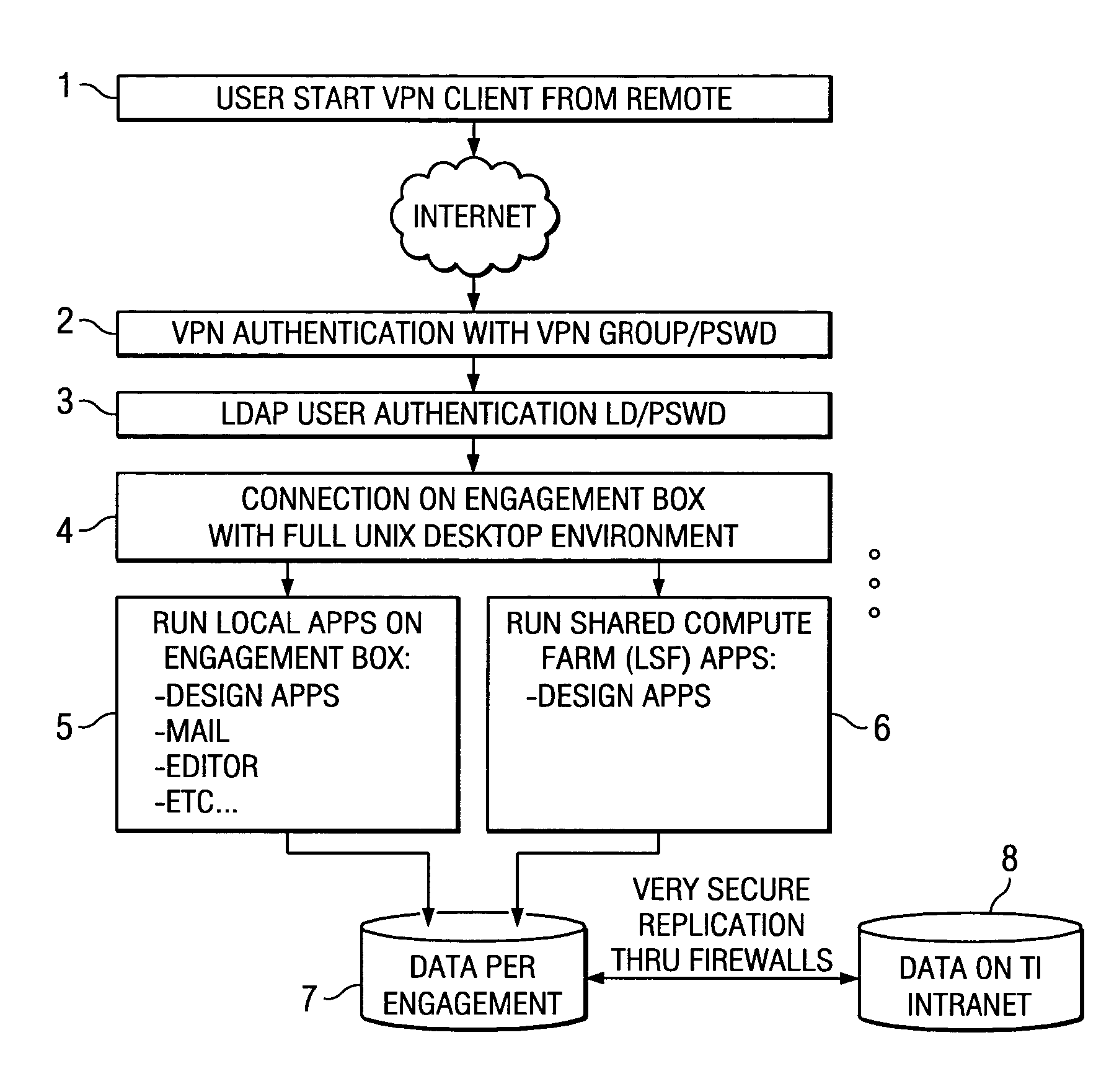
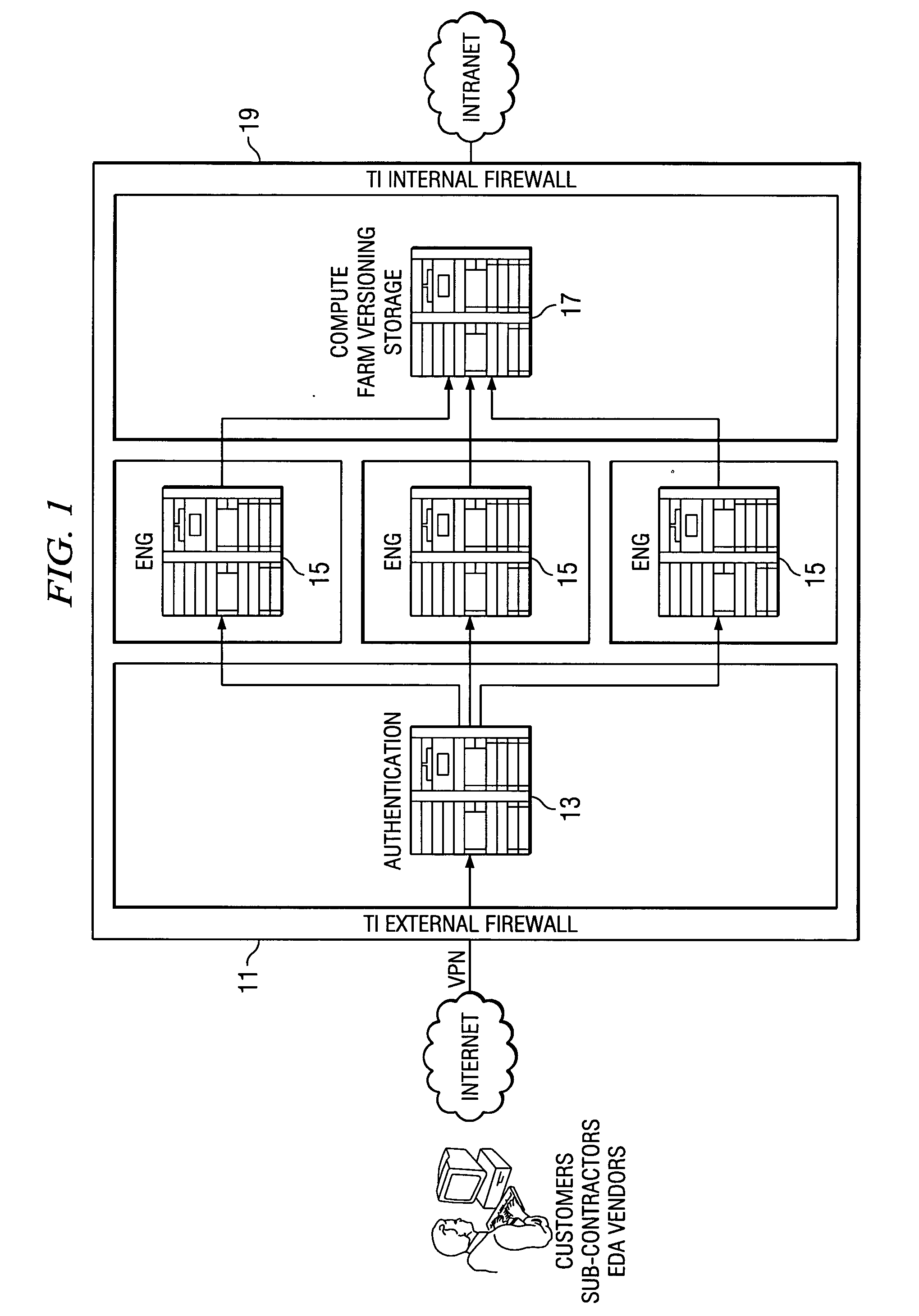
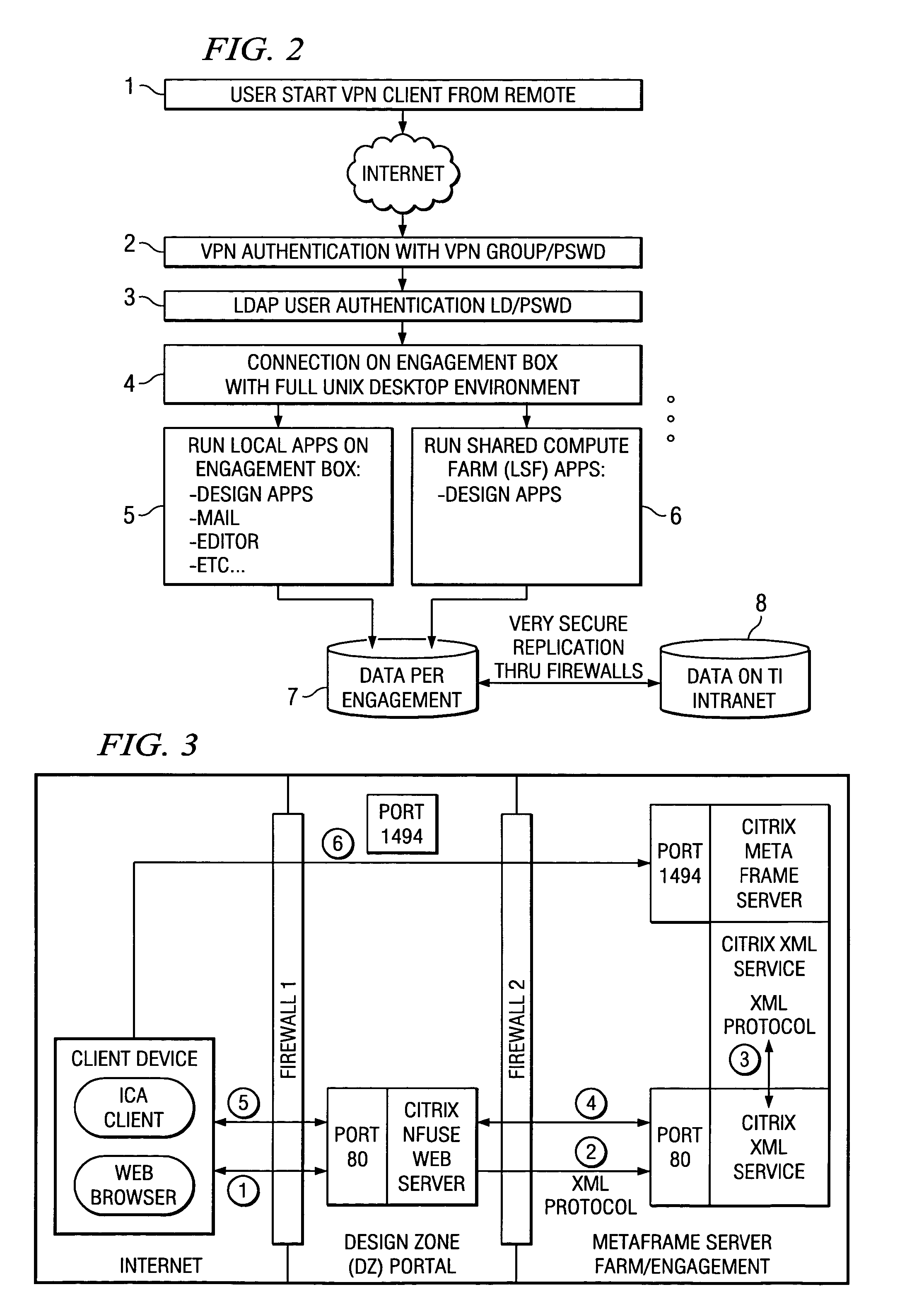
Method and system for access to development environment of another in a secure zone
ActiveUS20040221179A1User identity/authority verificationData switching by path configurationProgram managementPublic resource
A "Design Zones" system provides a highly secure common resource computing environment or design zone with services on the common resource or design zone being protected by multiple layers of security to engagement boxes with the computing environment where the partners can work simultaneously in multiple teams, run simulation tests, emulate software problems and share in a secure zone with just the remote display going back to the engagement box and therefore to the partner outside the owner. A method is described herein to provide access to EDA licenses managed by software daemon manager running on license servers inside an Intranet separated from the design zone by a firewall without opening all TCP inbound connections inside the TI Intranet for ports greater than 1023 from all the hosts in contractor or design zone on which EDA applications are run comprises a license proxy server inside the design zone that acts as a relay agent and route all the connections from contractor zone into the owner's Intranet.
Owner:TEXAS INSTR INC
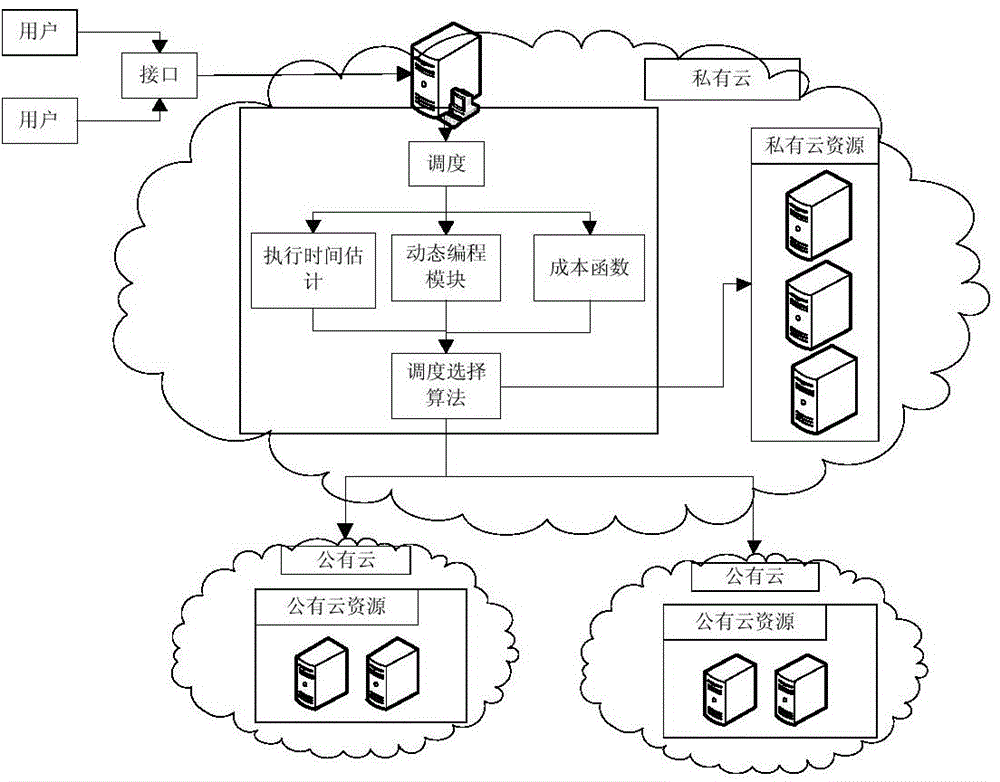
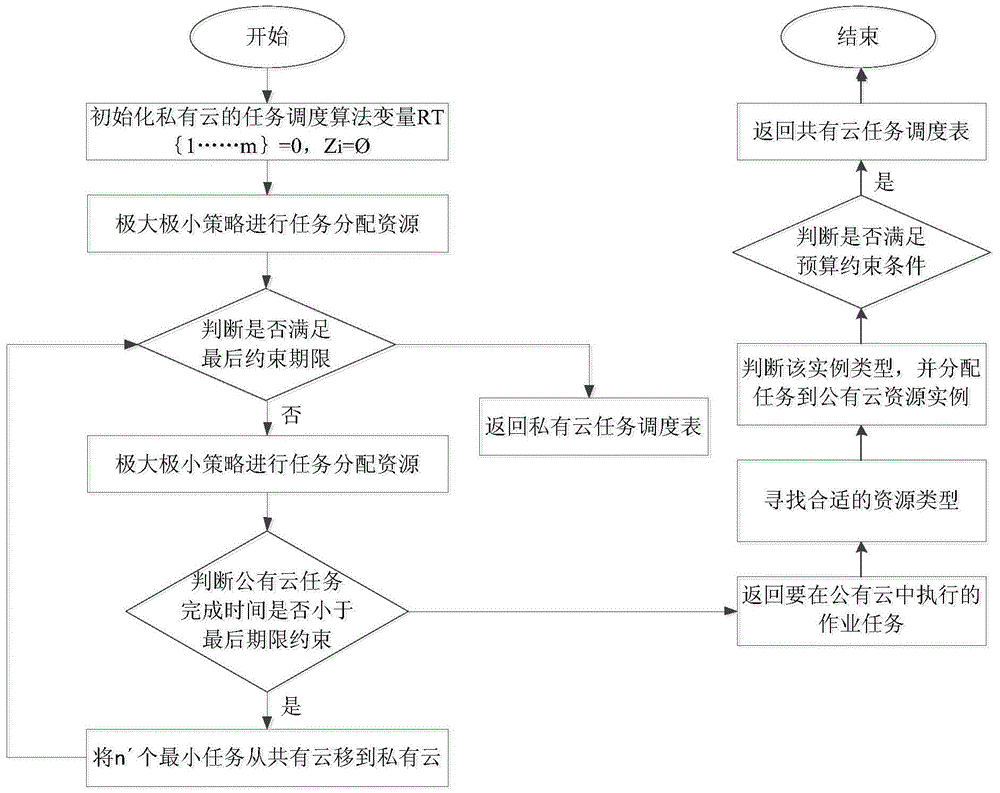
Multi QoS (quality of service)-constrained parallel task scheduling cost optimizing method under mixed cloud environment
InactiveCN104102544AResource allocationConcurrent instruction executionQuality of servicePublic resource
The invention relates to a multi QoS (quality of service)-constrained parallel task scheduling cost optimizing method under a mixed cloud environment. The method comprises the steps of task scheduling of a private cloud, task rescheduling and the minimizing of the leasing cost of public resources. In the task scheduling of the private cloud, resources are distributed for the tasks according to the improved maximal and minimum strategies, and a fast heuristic algorithm-TSOPR is provided. The task rescheduling step is finished by an RSD algorithm and comprises steps of deciding the task type distributed to a public cloud, judging whether the public cloud can meet the final time constraint and the budget constraint or not; generating a scheduling table for the task in the submitted operation by a system if all constraint conditions are met. The leasing cost of the public cloud resources can be minimized under the premise that the budget control constraint is met.
Owner:WUHAN UNIV OF TECH
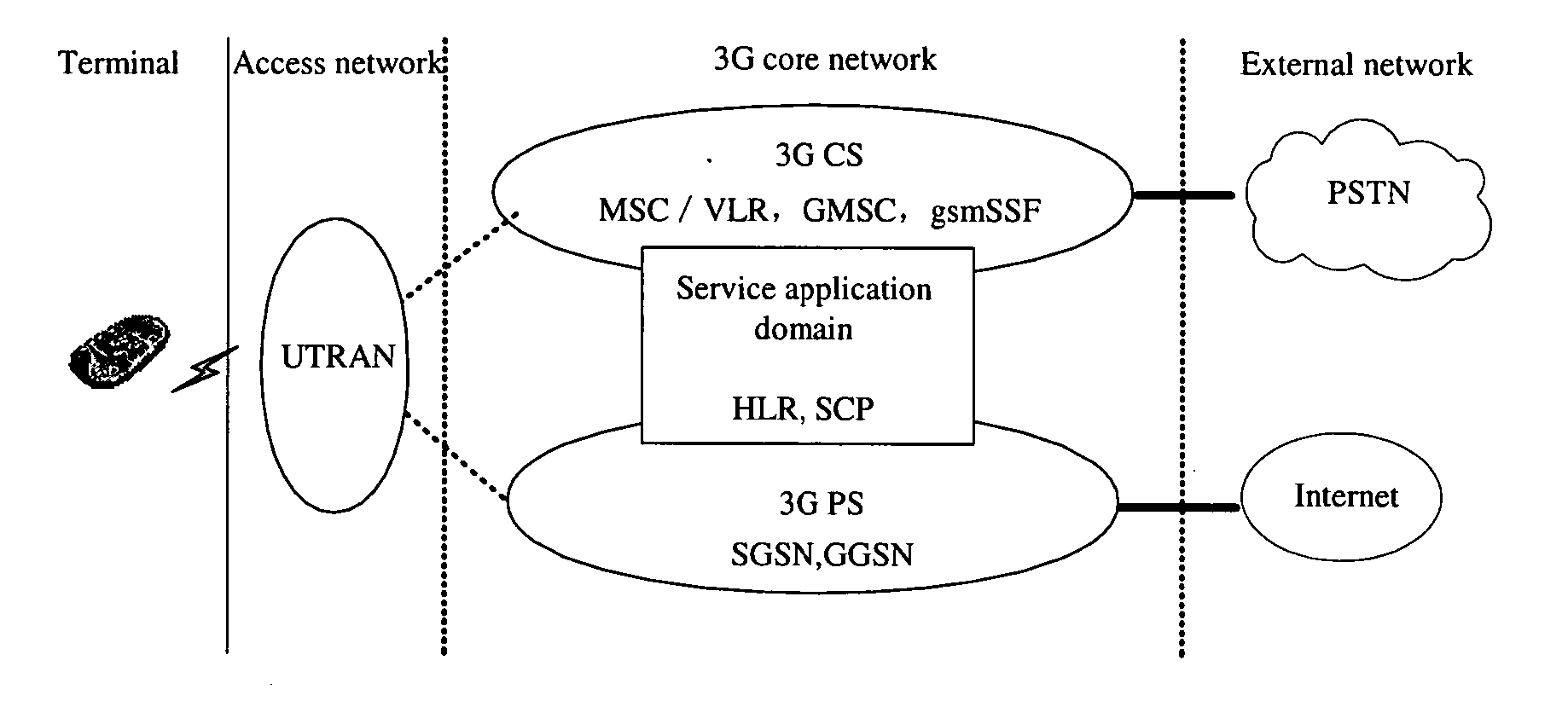
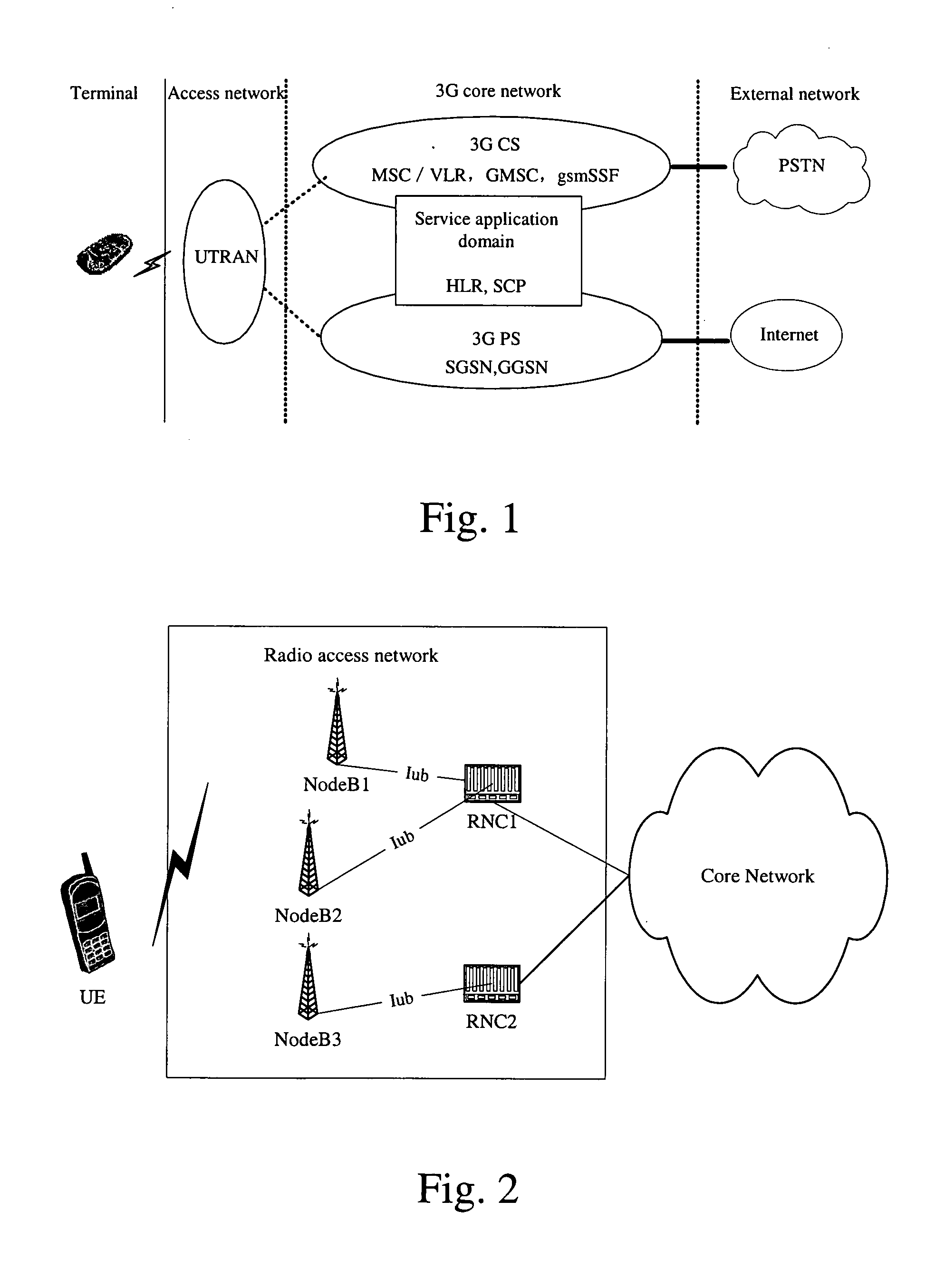
Method of optimizing soft handover between radio network controllers
InactiveUS20050119004A1Increased complexityIncrease the areaRadio/inductive link selection arrangementsWireless communicationRadio networksPublic resource
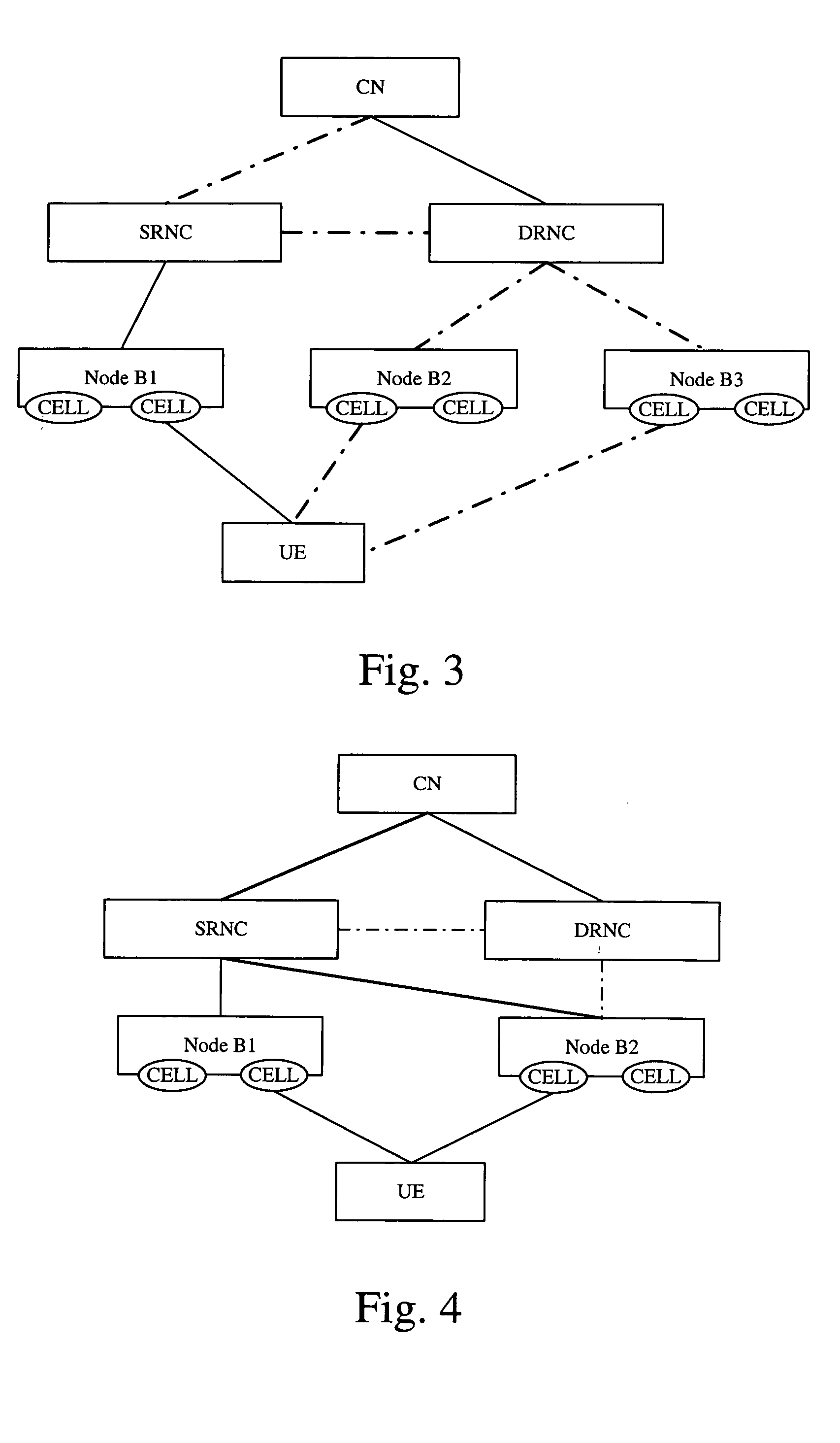
The invention discloses a method of optimizing soft handover between Radio Network Controllers (RNCs). The method comprises: (a) UE measuring signals of co-frequency neighbor cell to obtain a measuring result, and reporting the measuring result to a SRNC; (b) The SRNC making a handover decision to determine whether to make a soft handover; if yes, then determining whether said SRNC has right to dispatch common resources of a target Node B; (c) If having the right to dispatch common resources of Node B, said SRNC applying for required common resources of the target Node B to a specific functional entity that controls the common resources; according to status of current use of common resources of said target Node B, said specific functional entity responding whether the common resources are available, if yes, then establishing a connection between said SRNC and said target Node B, and initiating a soft handover within the RNC. The method makes handover complexity reduced greatly, and the handover reliability, stability and success rate is raised.
Owner:HUAWEI TECH CO LTD
Method and device for allocating resources
ActiveCN102340875ASimplify the scheduling processLow reassignment rateMultiple modulation transmitter/receiver arrangementsNetwork traffic/resource managementResource blockCarrier signal
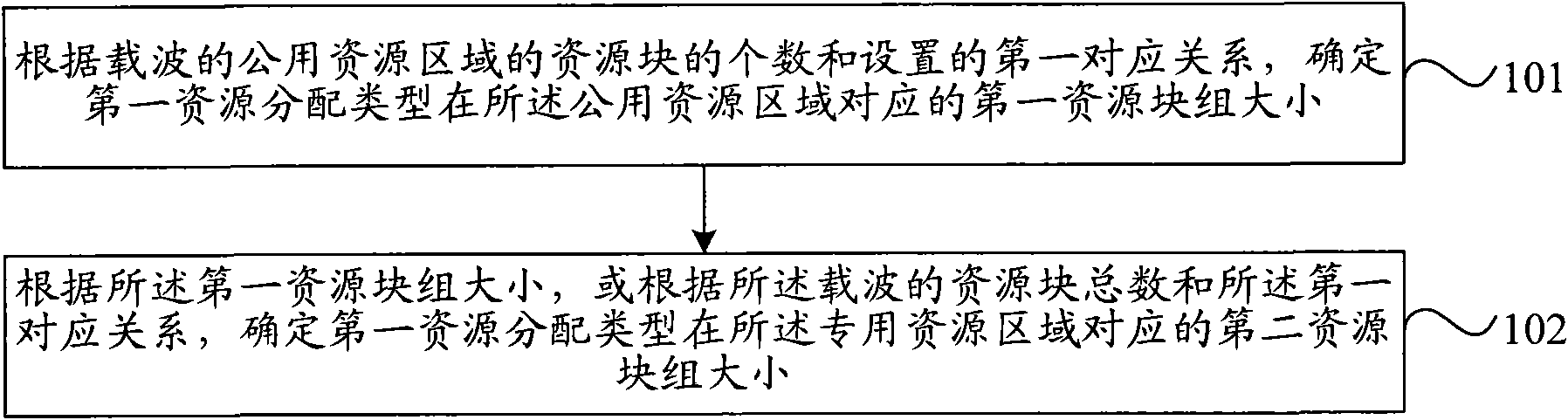
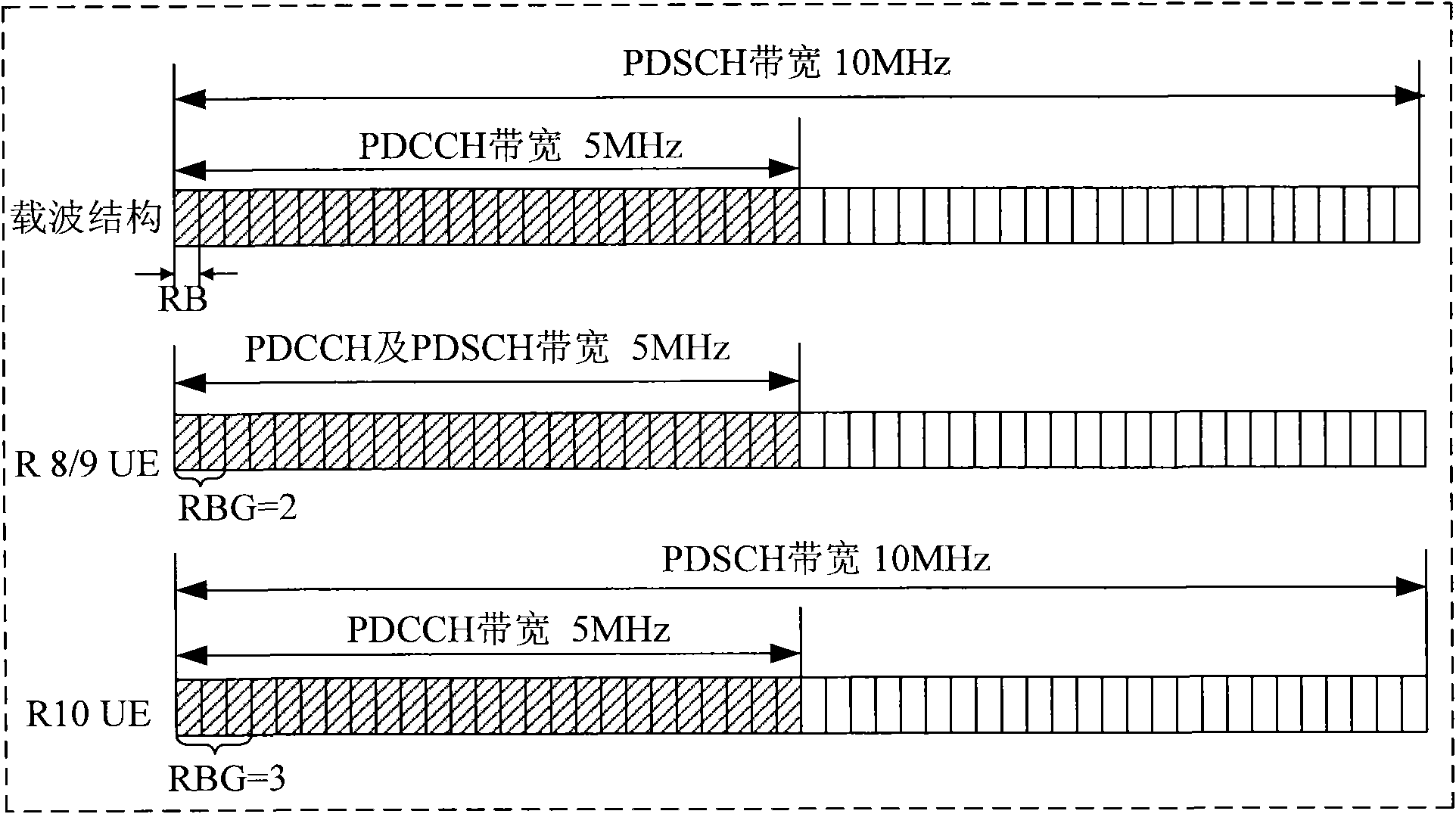
The invention discloses a method and device for allocating resources. The method comprises the steps of: determining the size of a first resource block group corresponding to a first resource allocation type in public resource regions according to the number of resource blocks of the public resource regions of carriers and a set first corresponding relationship; dividing the resource blocks of all the public resource regions of the carriers into one or more resource block groups according to the size of the first resource block group; determining the size of a second resource block group corresponding to the first resource allocation type in a special resource region according to the size of the first resource block group or the total number of the resource blocks of the carriers and the first corresponding relationship; and dividing the resource blocks of the special resource region of the carriers into one or more resource block groups according to the size of the second resource block group. According to the embodiment of the invention, the size of the resource block group is determined in accordance with the number of the resource blocks of the public resource regions, so that the scheduling process is simple, the resource repeated allocation rate is low, and the bandwidth resource is saved.
Owner:HUAWEI TECH CO LTD
Integration electronic lesson preparation system and method
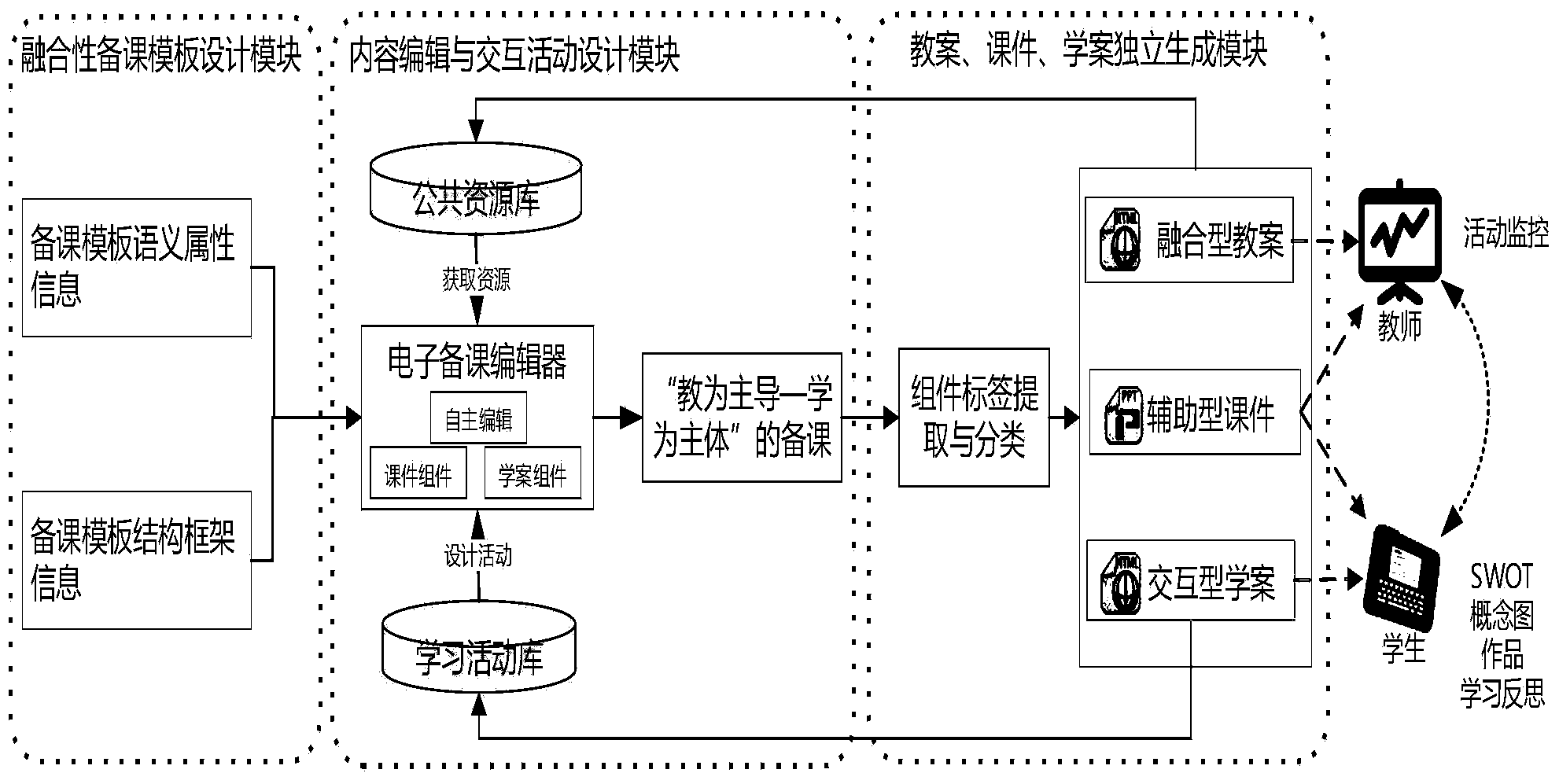
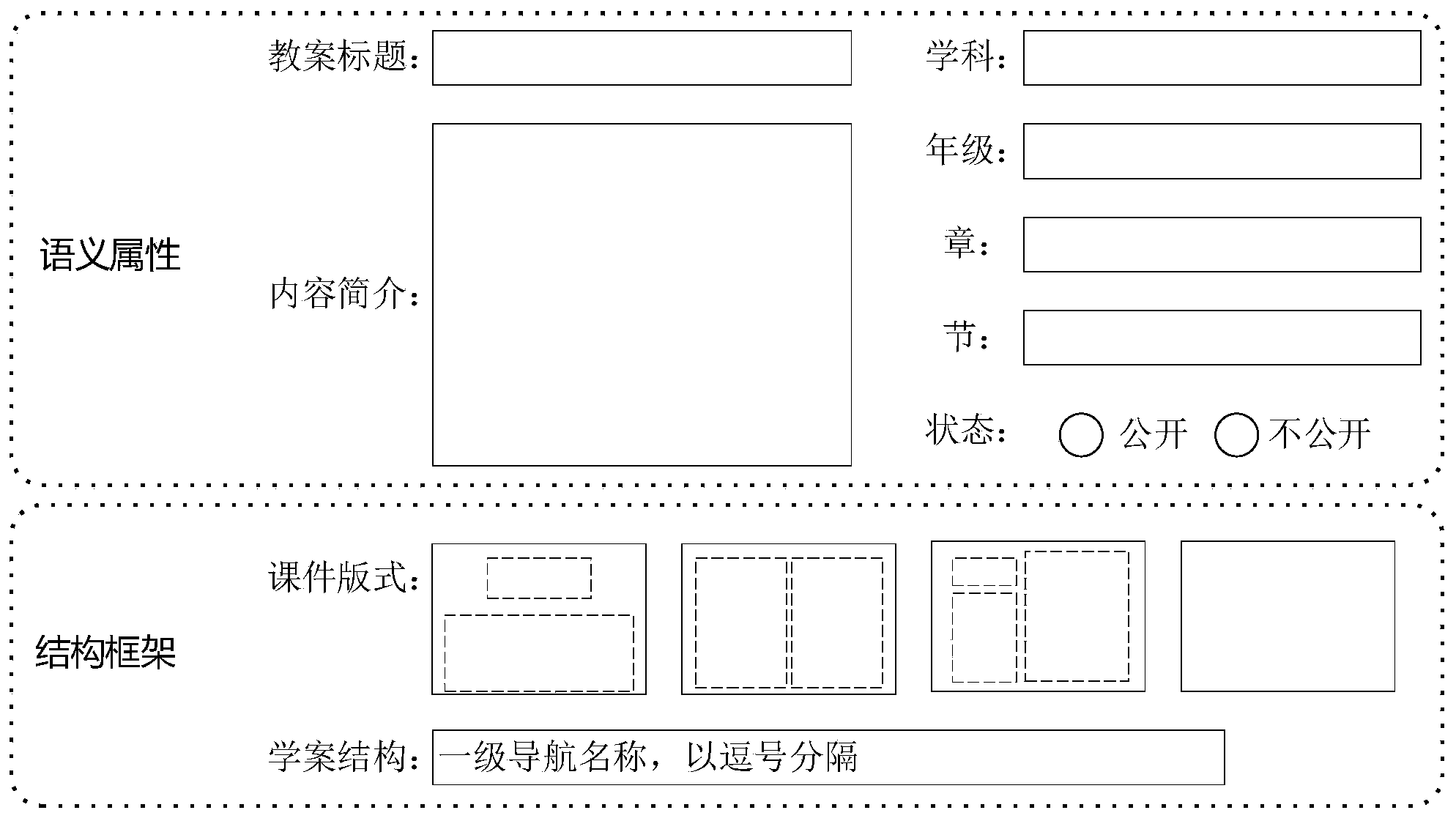
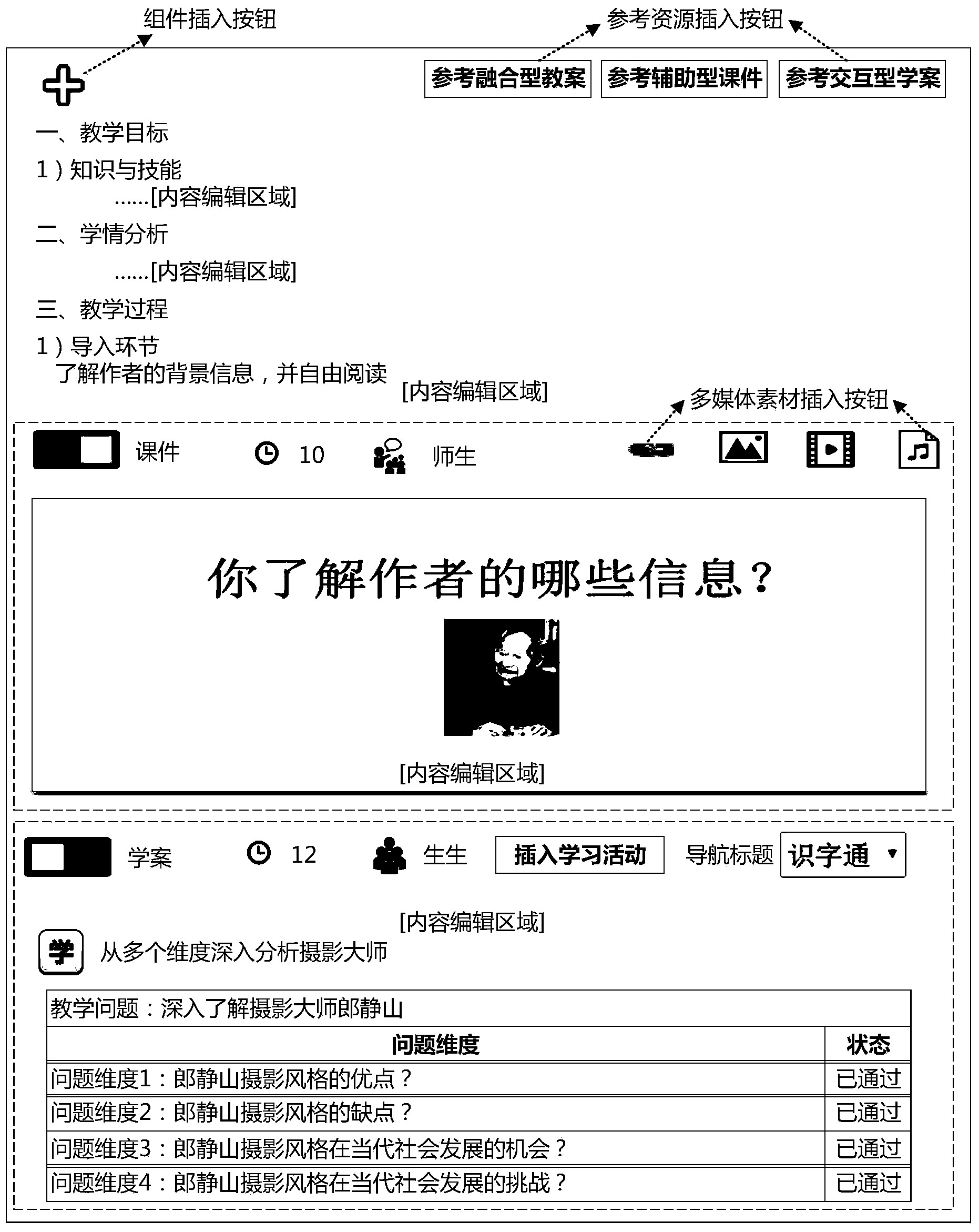
ActiveCN104183166AReduce the burden of lesson preparationAids in Lesson DesignElectrical appliancesPublic resourceLibrary science
The invention provides an electronic lesson preparation system and method which integrate teaching plans, courseware and learning plans. The electronic lesson preparation system mainly comprises an integration lesson preparation template design module, a content editing and interactive activity design module, a learning activity library, a public resource library and a teaching plan, courseware and learning plan independent generation module. Through semantic attribute information and framework information of a designed lesson preparation template, content in the public resource library and content in the learning activity library are designed or called to design less preparation content and classroom interactive activities, a courseware module and a learning plan module are extracted to generate a lesson preparation finished product including an integration teaching plan, auxiliary courseware and an interactive learning plan. The electronic lesson preparation system and method are convenient to operate, flexible in application and integral in design, and enables a user to select the lesson preparation template to complete the three-in-one lesson preparation finished product according to requirements of the user. Multiple achievements of the integration teaching plan, the auxiliary courseware, the interactive learning plan and the like can be generated through one time of lesson preparation, so that job involvement time is saved for teachers.
Owner:BEIJING NORMAL UNIVERSITY
Urban functional domain detection method and system by means of microblog position information
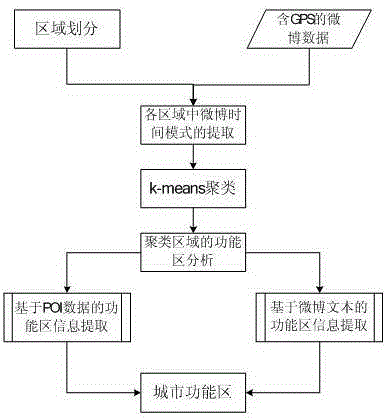
InactiveCN105183870AEasy accessAvoid access difficultiesResourcesSpecial data processing applicationsDecision makerMicroblogging
Provided is an urban functional domain detection method by means of microblog position information. The method comprises the steps that a survey region is selected, grid division and division of microblog time periods are conducted on the survey region, functional domains where various regions belong to are predicted according to microblog data for multiple days; the microblog data for multiple days are separated according to working days and weekends, and clustering regions and corresponding functional domain research results are updated; functional domain verification is conducted according to POI data in all the clustering regions, functional domain verification is conducted according to microblog text data in microblog time mode peak points of all the clustering regions, and functional domain verification is conducted according to subject terms of microblogs in all the clustering regions. According to the urban functional domain detection method by means of the microblog position information, the urban functional domains are explored by means of the microblogs containing the position information, data acquisition is convenient, the verification results are effective and rapid, the cost is reduced, the method can be used for detecting change tendency of the urban functional domains, and the method can help urbanists and decision makers to conduct scheming on public service, public resources and the like.
Owner:WUHAN UNIV
Mapping algorithm adopted in wireless network virtualization environment
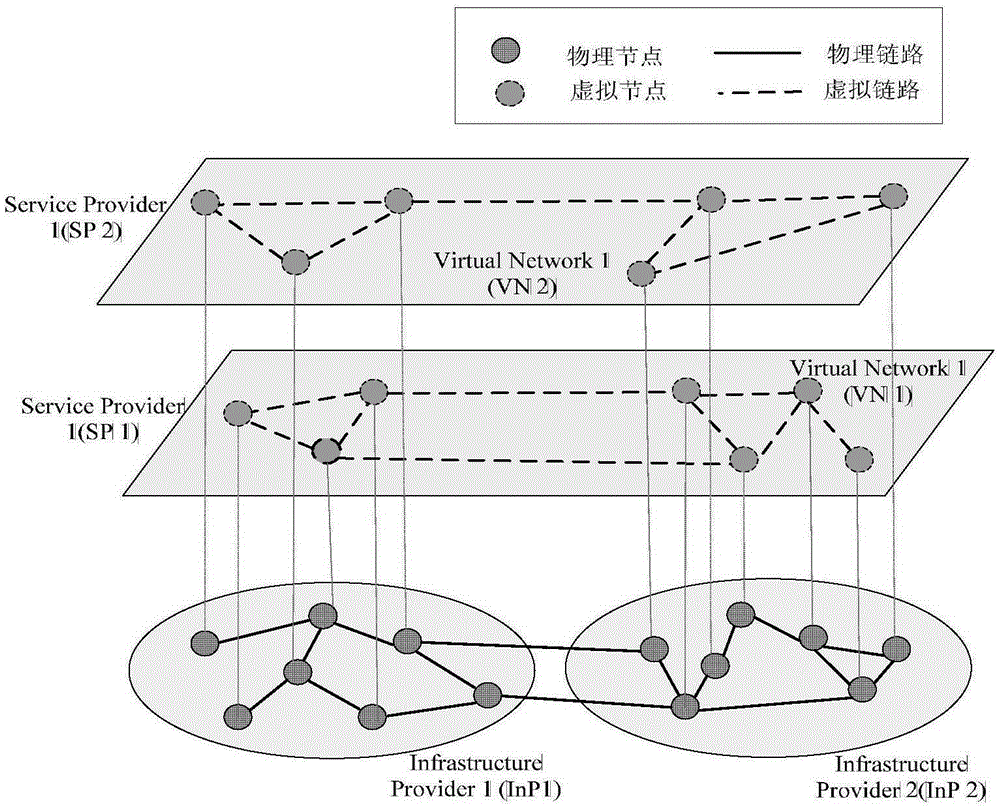
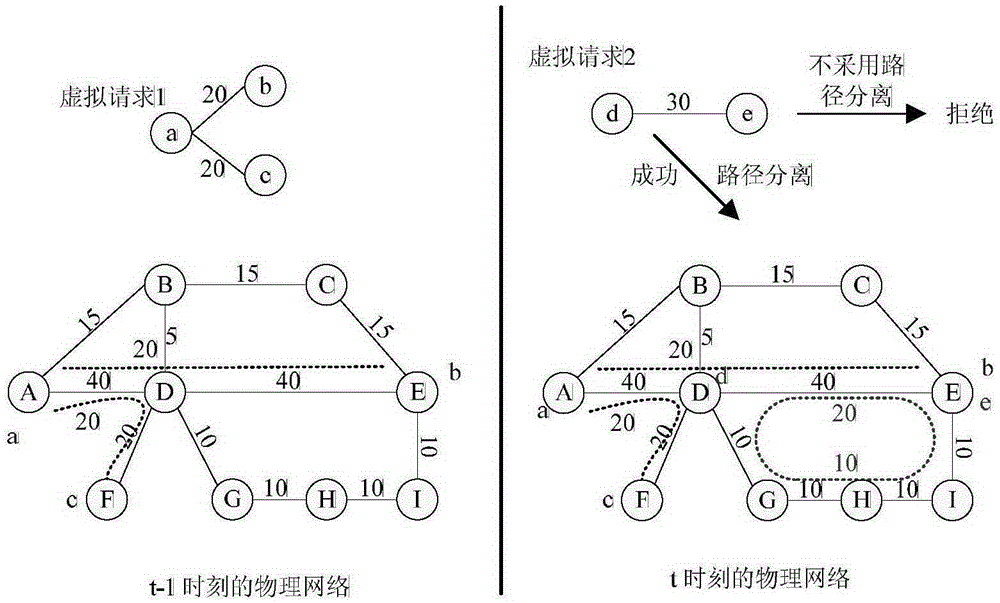
ActiveCN105337834AImprove utilization efficiencyIncrease the chance of successful mappingNetworks interconnectionNetwork planningFrequency spectrumWireless network virtualization
The invention discloses a mapping algorithm adopted in a wireless network virtualization environment. The mapping algorithm aims to solve the problem of existing wireless network virtualization mapping algorithms that public resources including bandwidth and frequency spectrum which can be shared between different basic facilities within a certain range and private resources including power and computing capacity which only belong to fixed hardware equipment and can not be shared are not well defined and distinguished. The mapping algorithm is capable of realizing joint optimization of power resources and frequency spectrum resources, interaction between power resources and frequency spectrum resources is comprehensively considered, the cost function of virtual network mapping is established by defining unit resource cost for reflecting the physical network loading level, mapping cost minimization is taken as the optimization object, physical network load balancing is achieved, path separation is adopted during virtual network mapping, and the utilization efficiency of physical resources is improved and the success rate of virtual network mapping is increased.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
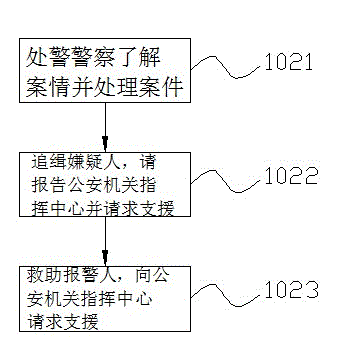
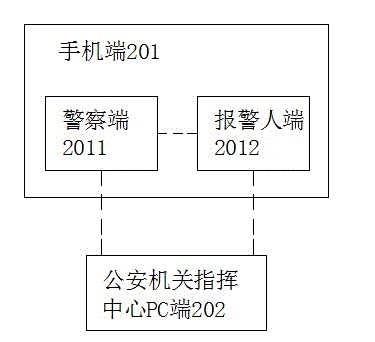
Mobile phone alarming method and system
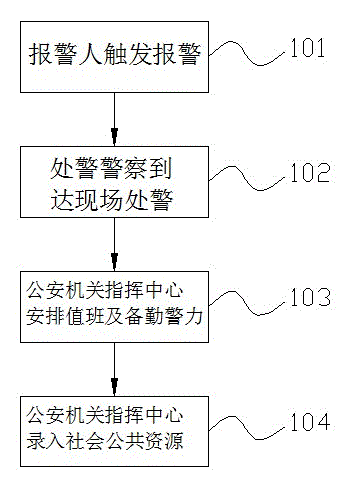
InactiveCN104616461AGood synergyAdd supportData processing applicationsAlarmsPersonal computerPublic resource
The invention discloses a mobile phone alarming method. The method includes the steps that an alarm person trigger the alarm and audio and video alarm information is uploaded to a PC (Personal Computer) end of a command center of a public security bureau and mobile phone ends of police on duty and police on standby guard 2 kilometers around the alarm person; handling police arrive at the scene of a case for handling the case; the command center of the public security bureau arranges the number of police on duty and police on standby guard according to the average number of daily alarming and alarm tasks; the command center of the public security bureau enters all data of public resources for future use. According to the mobile phone alarming method, the need of police on duty at all levels is omitted, the command center of the municipal public security bureau directly receives and handles all kinds of cases, and case information is directly assigned to police, so that the case handling rate is high; the position of the alarm person is directly showed for facilitating case handling, police cooperation and support and the grasp of police strength by the superior.
Owner:伍军旭
Method and apparatus for time-multiplexed processing of multiple digital video programs
ActiveUS20060165088A1Less spaceLow costTelevision system detailsColor television detailsDigital videoData stream
The present invention relates generally to the processing of multiple data streams with common resources. More particularly, this invention relates to a technique for time-multiplexed processing o, for example, multiple digital video programs. In one embodiment, an exemplary method provides for time-multiplexed processing of a set of digital streams includes storing each received packet in a random access memory. For each stream, the deadline for the arrival of the next packet at the receiver is determined and a priority based on the deadline is assigned. The stream with the highest assigned priority is identified as an identified stream. In some embodiments, the processing state of the identified stream is then restored. One or more packets of data corresponding to the identified stream are retrieved from random access memory to produce retrieved packets. The processing state is saved after the retrieved packets have been processed.
Owner:IMAGINE COMM
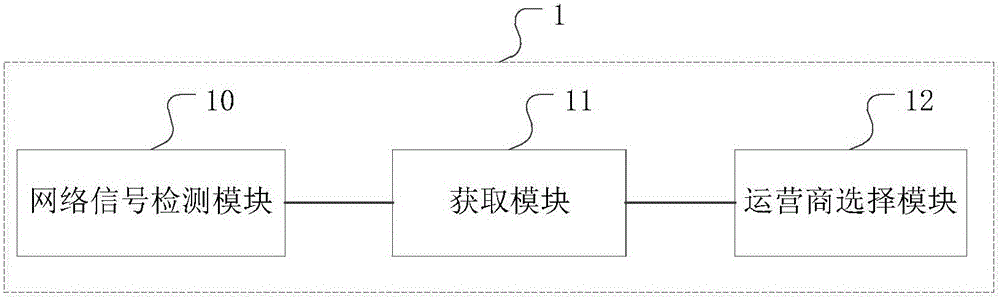
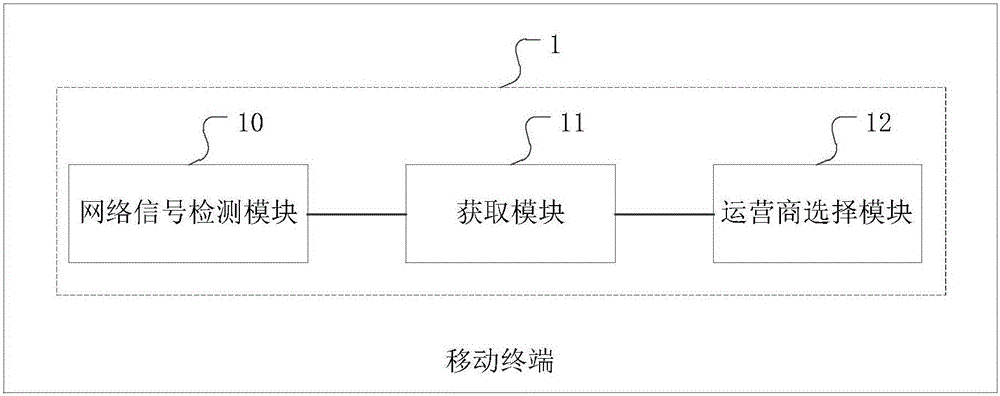
Method and device for selecting operator based on e-SIM () card and mobile terminal
ActiveCN105873013AEfficient use ofAssess restrictionNetwork data managementPublic resourceComputer terminal
The invention discloses a method for selecting an operator based on an e-SIM (embedded Subscriber Identity Module) card. The method comprises the following steps: performing current network signal detection on acquired communication data of operators in a current environment of a user to obtain a current network signal detection result, wherein the operators are all included in an operator list in a mobile terminal of the user, and the operator list at least includes two kinds of operators; acquiring current running parameters of the mobile terminal; and selecting a corresponding operator from the operator list according to the current running parameters and the current network signal detection result. Through adoption of the method, an appropriate operator can be selected for the user according to an actual demand, and public resources can be utilized better. Moreover, the invention also discloses a device for selecting an operator based on the e-SIM card, and a mobile terminal.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
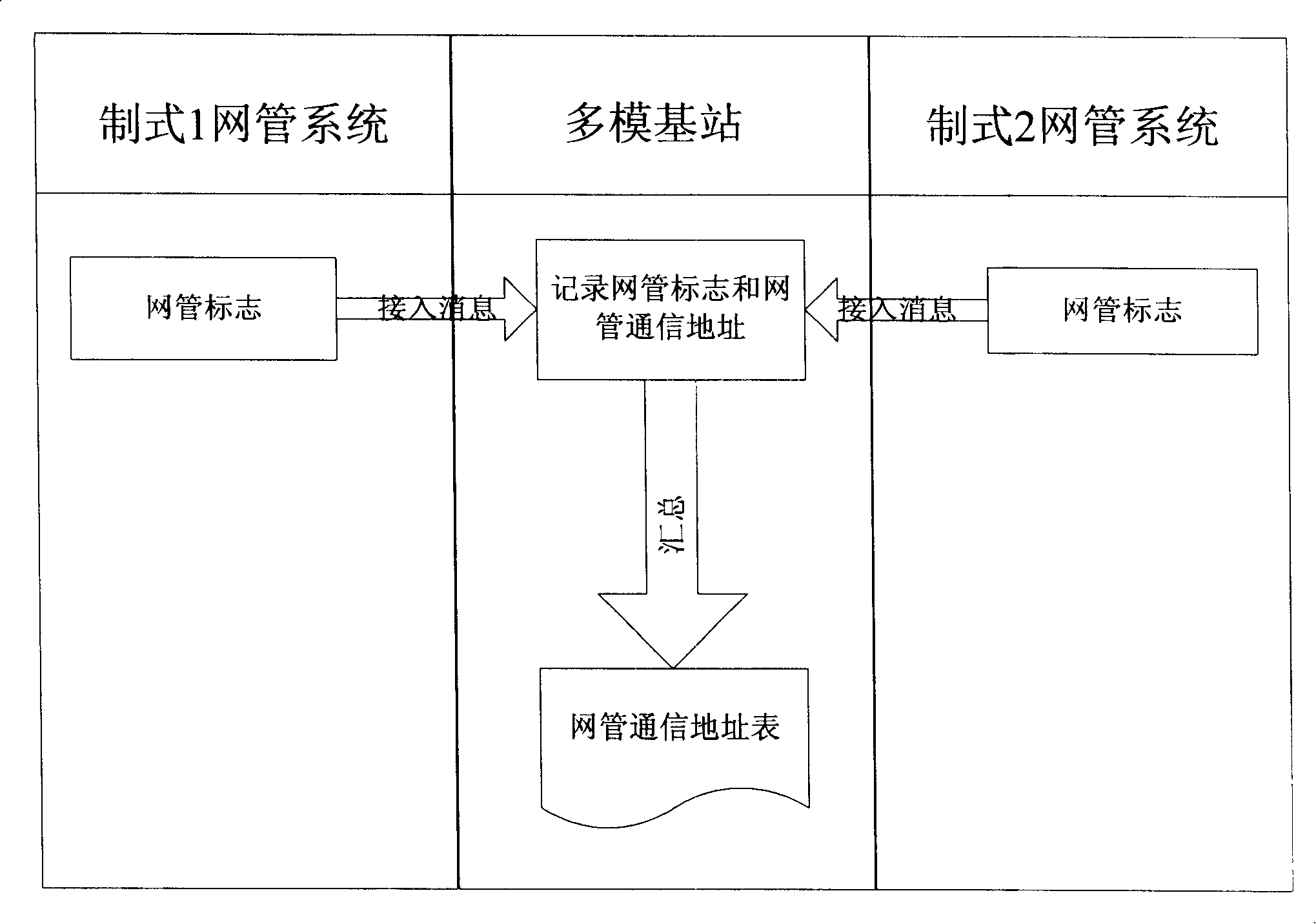
An operation and maintenance method and system for multi-mode base station in wireless communication system
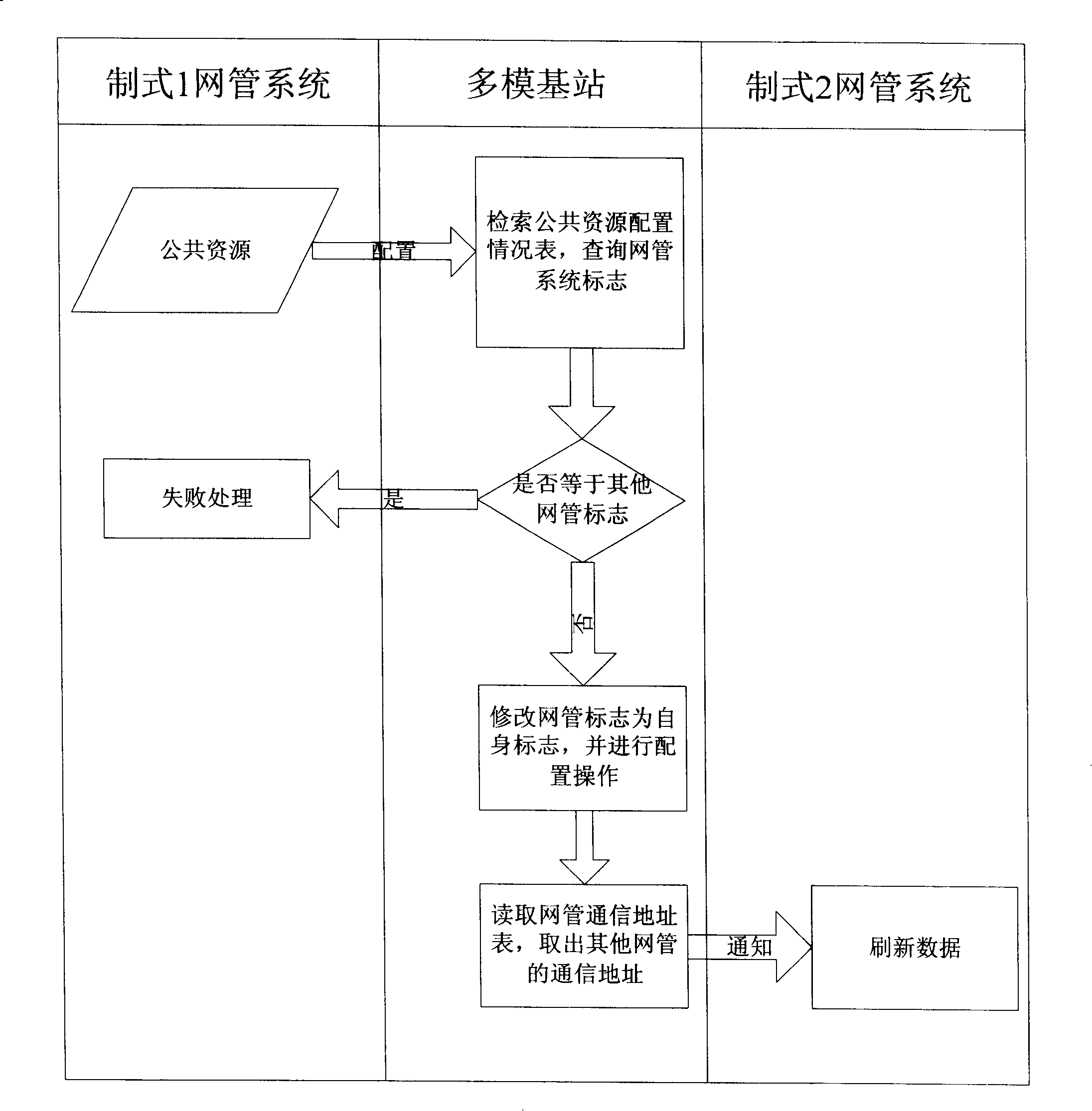
InactiveCN101192948AImprove operator friendlinessRadio/inductive link selection arrangementsData switching networksCommunications systemNetwork management
The invention relates to a multimode base station operation and maintenance method in a wireless communication system, which comprises the following steps: a setting step in which a symbol without a network management system, the symbols of the network management systems in various systems and the public resource configuration information are set and a configuration step in which the network management system applies the configuration and operation and maintenance to the public resources. The invention has the advantages that the network management systems in various systems can independently manage the public resources of the base station without causing the conflicts compared with the prior art; the network management system in one system can immediately inform other network management systems after modifying the public resources, thus increasing the operation friendliness of the network management system.
Owner:ZTE CORP
Explicit outband signaling method in a wireless network supporting cognitive radio technology
ActiveUS20070207737A1Interference minimizationNetwork traffic/resource managementConnection managementTelecommunicationsCurrent channel
An explicit outband signaling method for detecting sharable resources for management of public resources in a wireless network supporting Cognitive Radio (CR) technology. To this end, the invention transmits state information for the current channel to a CR system in order to enable communication of the CR users, whose communication with the CR system is impossible due to an influence of an incumbent system, thereby allowing the CR system to stop the use of the interference channel, and to provide a corresponding service with another channel.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Resource management subsystem that maintains fairness and order
One embodiment of the present disclosure sets forth an effective way to maintain fairness and order in the scheduling of common resource access requests related to replay operations. Specifically, a streaming multiprocessor (SM) includes a total order queue (TOQ) configured to schedule the access requests over one or more execution cycles. Access requests are allowed to make forward progress when needed common resources have been allocated to the request. Where multiple access requests require the same common resource, priority is given to the older access request. Access requests may be placed in a sleep state pending availability of certain common resources. Deadlock may be avoided by allowing an older access request to steal resources from a younger resource request. One advantage of the disclosed technique is that older common resource access requests are not repeatedly blocked from making forward progress by newer access requests.
Owner:NVIDIA CORP
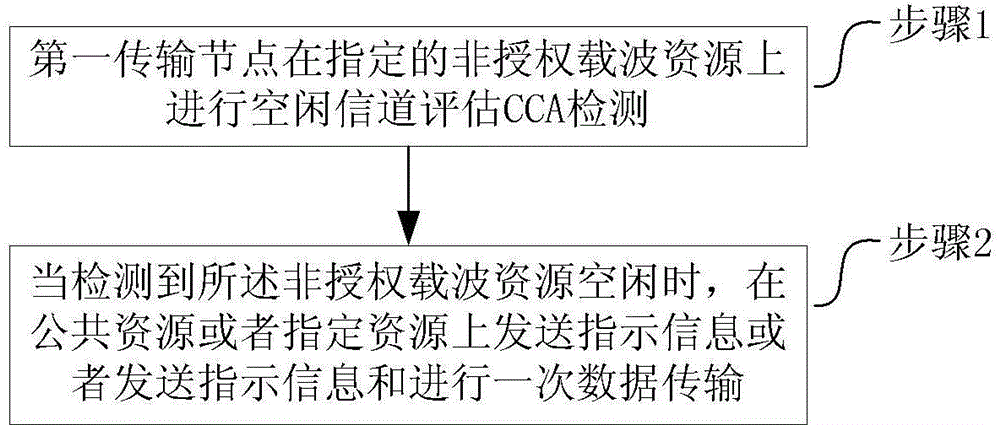
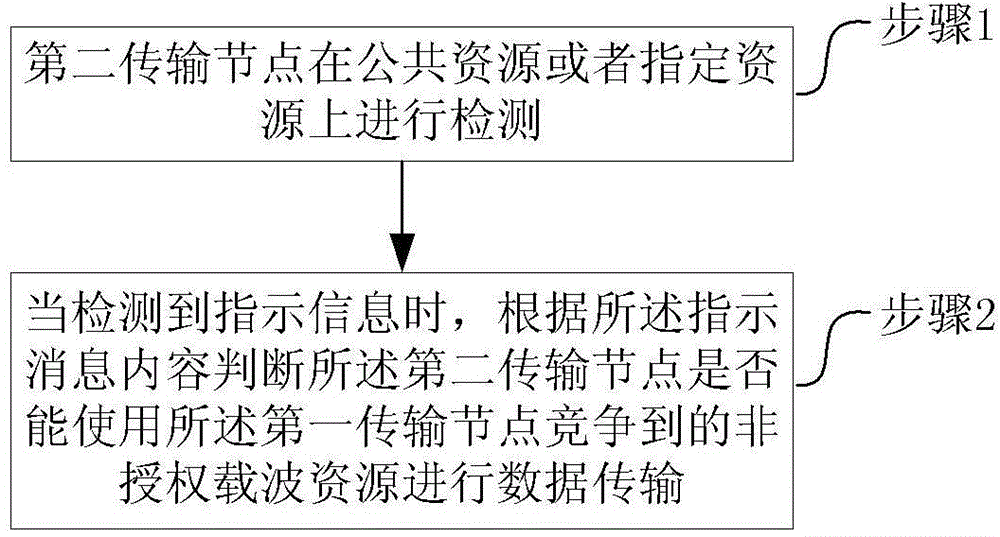
Unauthorized resource transmission method and device
InactiveCN106160967AIncrease profitExact channel conditionTransmission path multiple useHigh level techniquesCarrier signalPublic resource
The invention discloses an unauthorized resource transmission method and device. Processing steps implemented by a first transmission node are as follows: implementing CCA detection on an assigned unauthorized carrier resource by the first transmission node, and sending indicating information or sending the indicating information and implementing data transmission on a public resource or an assigned resource for once when detecting that the unauthorized carrier resource is idle, wherein the indicating information is used for notifying that the unauthorized carrier resource has been occupied; and the processing steps implemented by a second transmission node are as follows: implementing detection on the public resource or an assigned resource by the second transmission node, and judging whether the second transmission node can use the unauthorized carrier resource competed by the first transmission node to implement data transmission according to contents of the indicating information when the indicating information is detected. By adopting the scheme disclosed by the embodiment of the invention, the use ratio of the unauthorized carrier resource can be greatly increased.
Owner:ZTE CORP
Intelligent property management system based on internet of things
InactiveCN105550952AQuickly handle repairsFast processing activityData processing applicationsThe InternetPublic resource
Owner:CHONGQING SHENGXIN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com