Memory malicious code detection method based on processor tracking
A malicious code detection and processor technology, which is applied in the field of memory malicious code detection based on processor tracking, can solve the problems that cannot be analyzed, cannot be guaranteed to obtain a complete target code trusted control flow graph, and cannot fully analyze all behaviors of the program.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
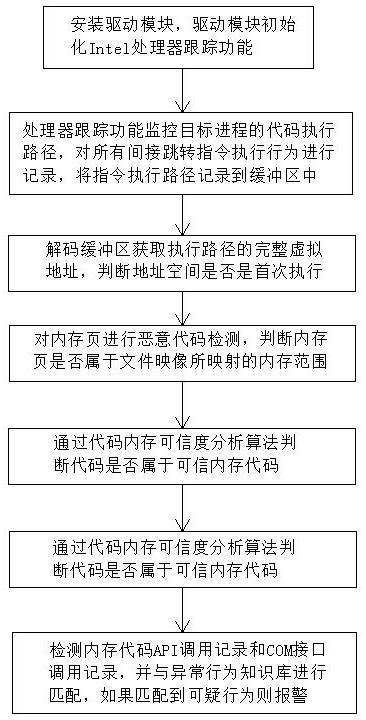
[0042] see figure 1 , a memory malicious code detection method based on processor tracking, comprising the following steps:
[0043] a. Install the driver module, register the callback processing routines for starting and exiting processes and threads in the kernel, record all started threads, processes and file information in the process callback routine, record the CR3 register information of the process, and initialize the driver module Intel processor trace function, configure physical memory buffer and interrupt processing routine for each CPU core and start processor trace function;
[0044] b. The processor tracking function monitors the code execution path of the target process, records the execution behavior of all indirect jump instructions, records the instruction execution path into the buffer, and triggers the interrupt processing routine when the buffer is full. Switch the backup buffer during the process and start malicious code analysis;
[0045] c. Decode th...
Embodiment 2
[0051] see figure 1 , a memory malicious code detection method based on processor tracking, comprising the following steps:
[0052] a. Install the driver module, register the callback processing routines for starting and exiting processes and threads in the kernel, record all started threads, processes and file information in the process callback routine, record the CR3 register information of the process, and initialize the driver module Intel processor trace function, configure physical memory buffer and interrupt processing routine for each CPU core and start processor trace function;
[0053] b. The processor tracking function monitors the code execution path of the target process, records the execution behavior of all indirect jump instructions, records the instruction execution path into the buffer, and triggers the interrupt processing routine when the buffer is full. Switch the backup buffer during the process, and start malicious code analysis;
[0054] c. Decode t...
Embodiment 3
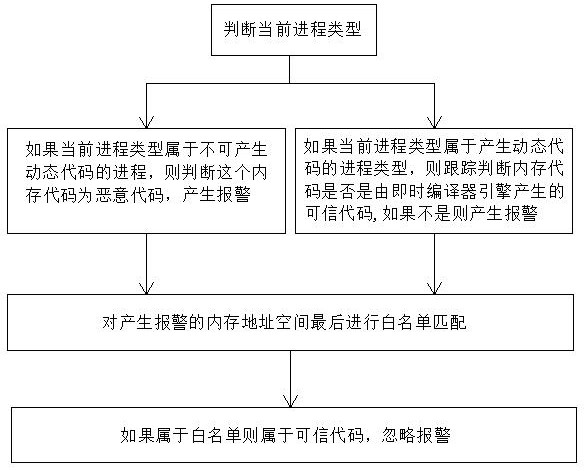
[0061] see figure 1 and figure 2 , a memory malicious code detection method based on processor tracking, comprising the following steps:
[0062] a. Install the driver module, register the callback processing routines for starting and exiting processes and threads in the kernel, record all started threads, processes and file information in the process callback routine, record the CR3 register information of the process, and initialize the driver module Intel processor trace function, configure physical memory buffer and interrupt processing routine for each CPU core and start processor trace function;
[0063] b. The processor tracking function monitors the code execution path of the target process, records the execution behavior of all indirect jump instructions, records the instruction execution path into the buffer, and triggers the interrupt processing routine when the buffer is full. Switch the backup buffer during the process and start malicious code analysis;
[006...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com