Detection method and detection device for attack in spray pattern
A mode and detection module technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as detection failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
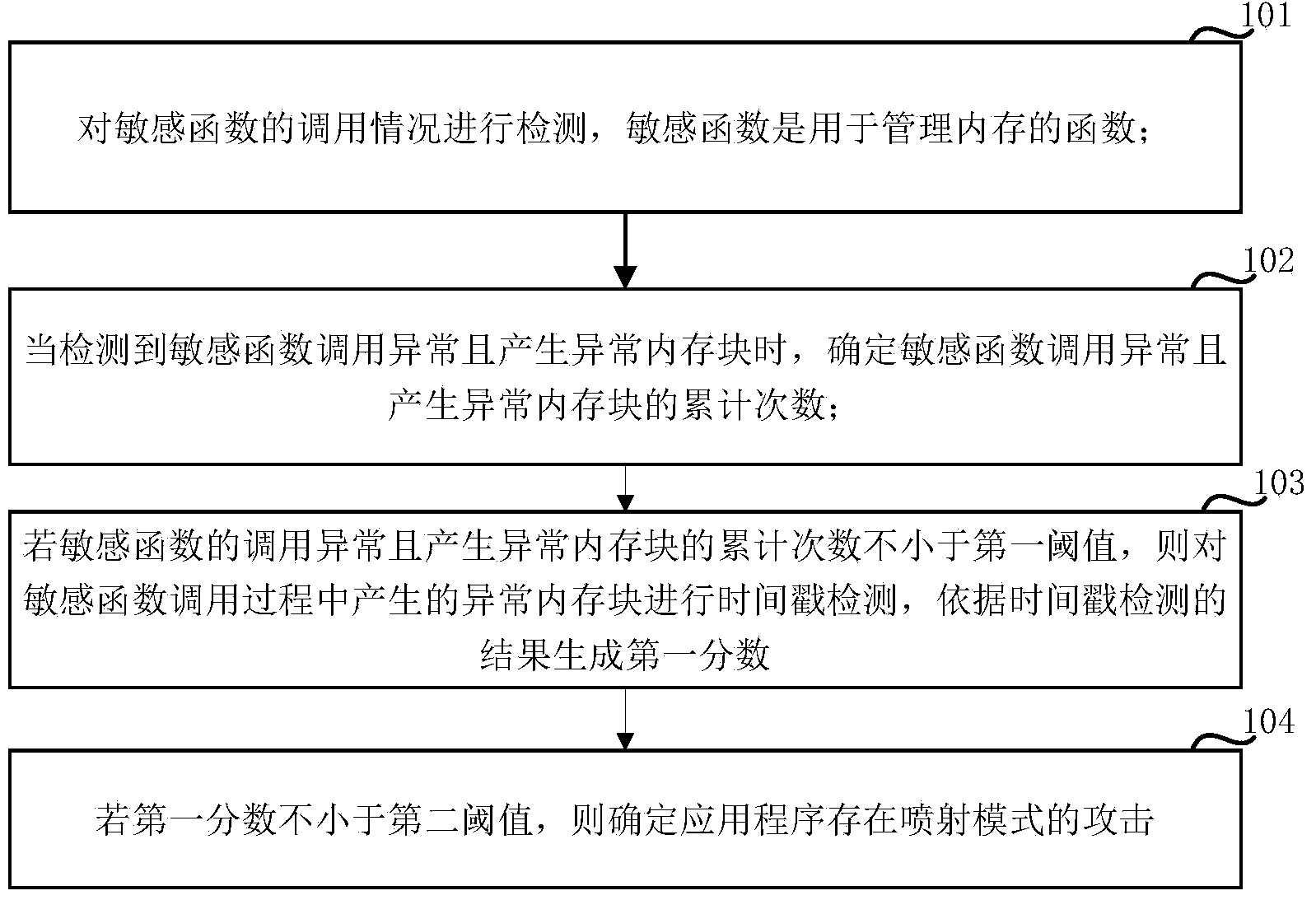
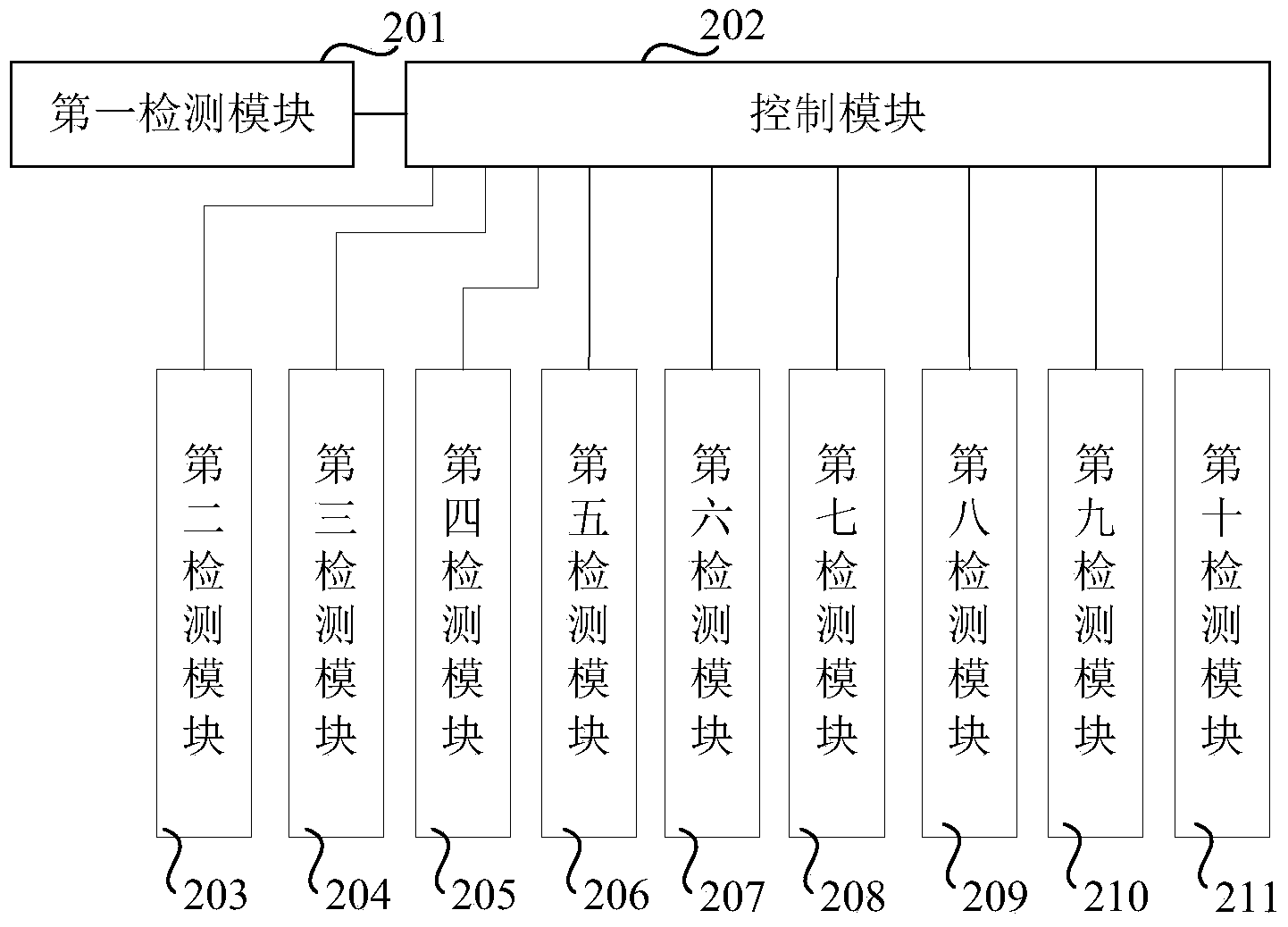
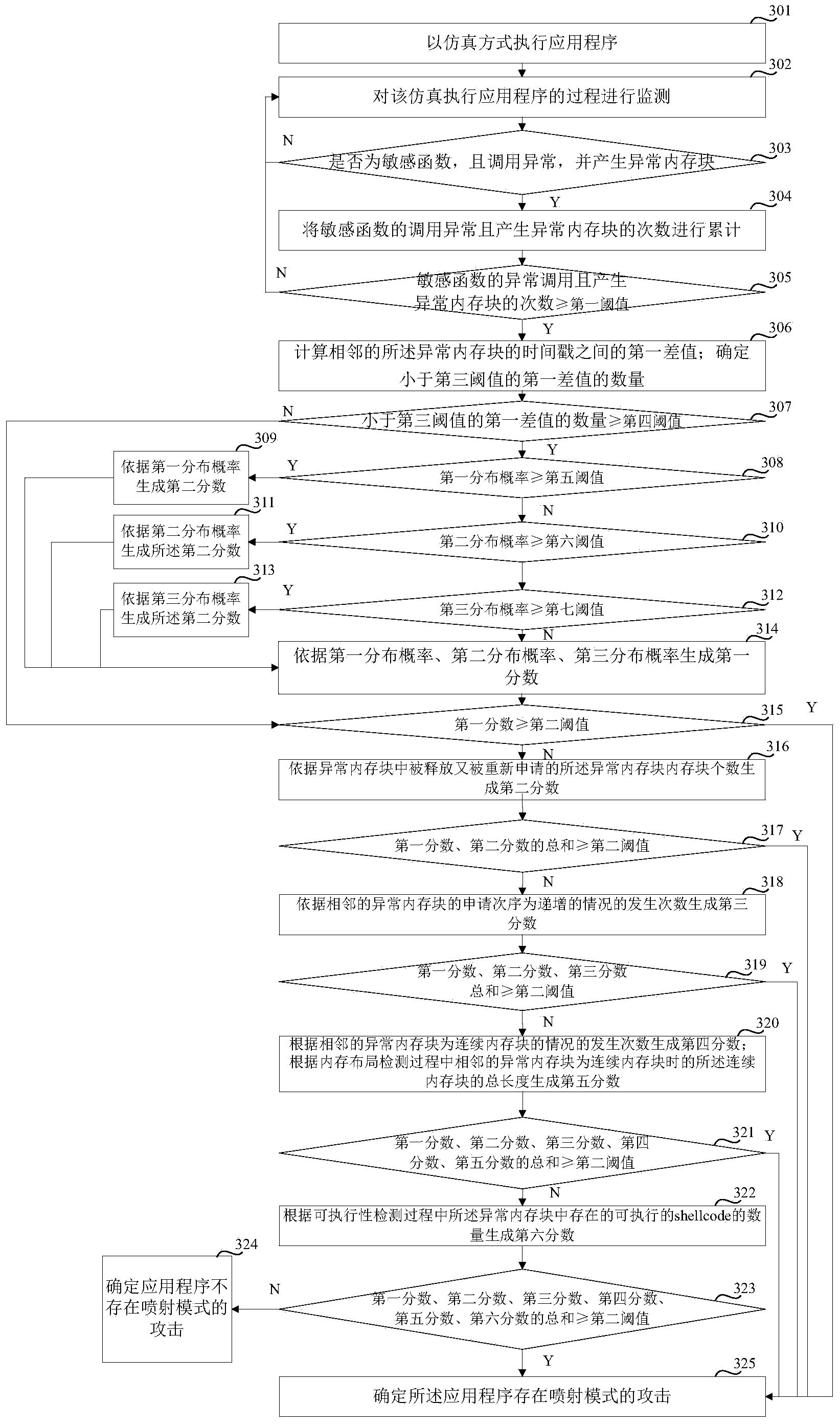
[0106] Embodiments of the present invention provide a method and device for detecting a spray mode attack, which executes an application program in a simulation manner, and detects the calling of a sensitive function during the execution of the application program, and the sensitive function is a function used to manage memory; when When an abnormal call to a sensitive function is detected and an abnormal memory block is generated, determine the cumulative number of times the sensitive function is called abnormally and the abnormal memory block is generated; The abnormal memory block generated during the function call is subjected to timestamp detection, and the first score is generated according to the result of the timestamp detection; if the first score is not less than the second threshold, it is determined that the application program has a spray mode attack. Since the time stamp of the abnormal memory block can be detected to determine whether there is a spray mode attack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com