Vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in the field of network security, can solve the problems of low accuracy, detection failure, and low detection efficiency, and achieve the effects of high accuracy, avoiding detection failure, and high detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
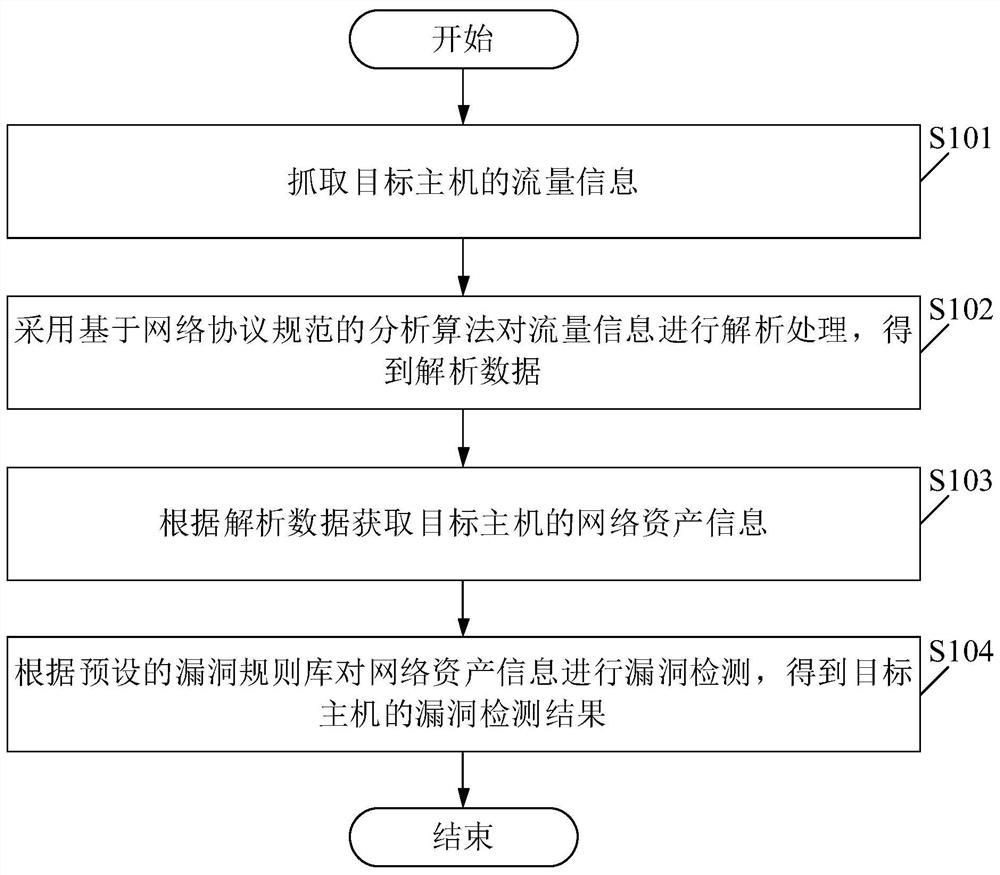
[0047] Please see figure 1 , figure 1 A schematic flowchart of a vulnerability detection method is provided for the embodiment of the present application. Among them, the vulnerability detection method includes:
[0048] S101. Capture traffic information of a target host.
[0049] In the embodiment of the present application, to capture the traffic information of the target host, there is no need to establish an additional connection with the target host, and there is no data packet interaction, so there is no impact on the network bandwidth and the target host.
[0050] In the embodiment of the present application, the execution subject of the method may be a vulnerability detection device, and the vulnerability detection device may run on the target host, which is not limited in the embodiment of the present application.
[0051] In the embodiment of the present application, the target host may specifically be a computing device such as a computer or a server, which is no...
Embodiment 2
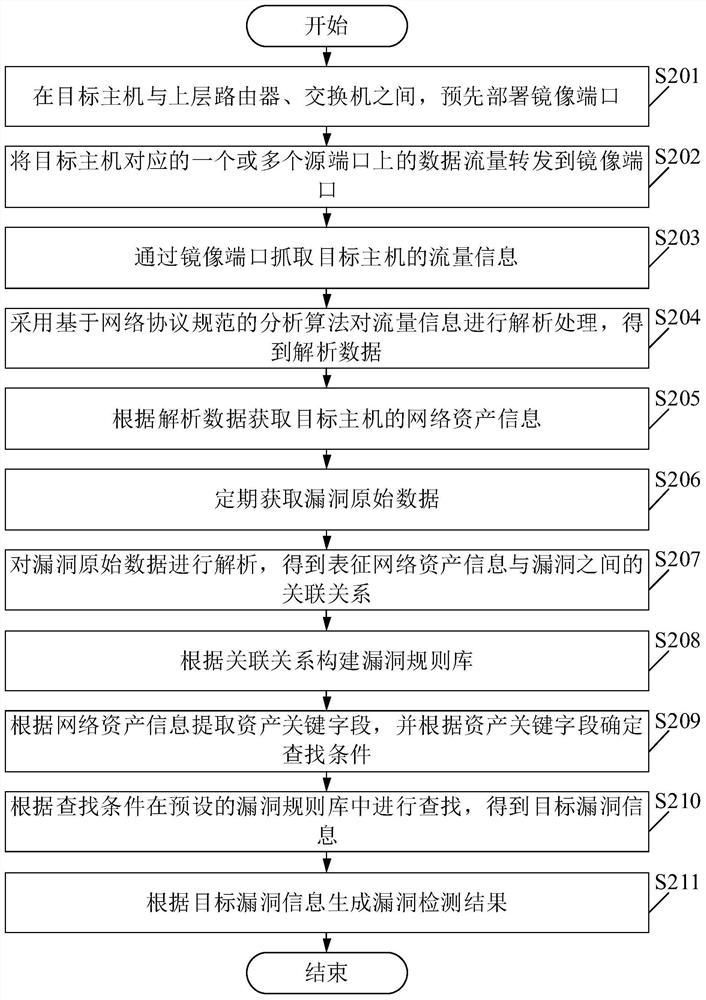
[0069] Please see figure 2 , figure 2 It is a schematic flowchart of a vulnerability detection method provided in the embodiment of the present application. Such as figure 2 As shown, wherein, the vulnerability detection method includes:
[0070] S201. Pre-deploy a mirrored port between the target host and an upper-layer router or switch.
[0071] S202. Forward the data traffic on one or more source ports corresponding to the target host to the mirror port.
[0072] In the embodiment of the present application, when the vulnerability detection method based on passive traffic is adopted, in the network topology, it is usually deployed between the target host and the upper-layer router and switch, and the port mirroring function is used to transfer the data traffic on one or more source ports to Forward to the mirror port directly connected to the system, and monitor and analyze the user traffic of the target host through the mirror port, so as to obtain the message data ...
Embodiment 3
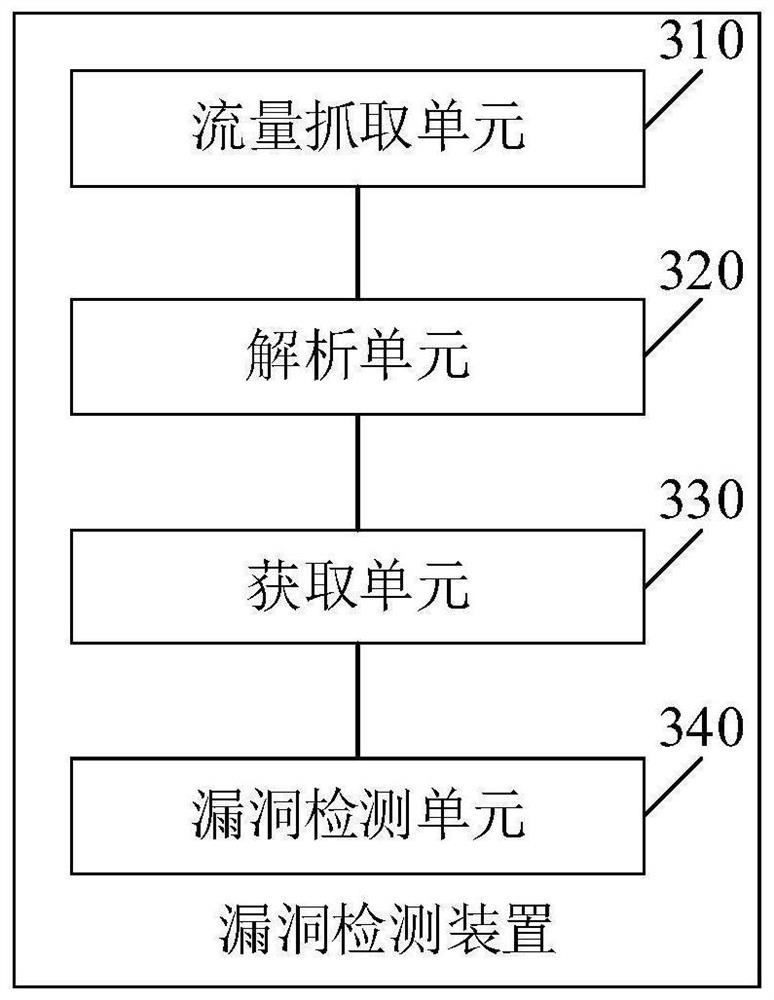
[0099] Please see image 3 , image 3 It is a schematic structural diagram of a vulnerability detection device provided in an embodiment of the present application. Such as image 3 As shown, the vulnerability detection device includes:
[0100] A traffic capture unit 310, configured to capture the traffic information of the target host;
[0101] An analysis unit 320, configured to analyze and process the flow information by using an analysis algorithm based on network protocol specifications to obtain analysis data;
[0102] An acquisition unit 330, configured to acquire the network asset information of the target host according to the analysis data;
[0103] The vulnerability detection unit 340 is configured to perform vulnerability detection on network asset information according to a preset vulnerability rule base, and obtain a vulnerability detection result of the target host.
[0104] In the embodiment of the present application, for the explanation of the vulnerabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com