Shellcode detection method based on virtual execution
A technology of virtual execution and code detection, applied in the field of network information security, can solve the problems of insufficient detection success rate and insufficient detection speed of static detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make it easy to understand the technical means, creation features, achieved goals and effects of the present invention, the present invention will be further described below with reference to the specific figures.
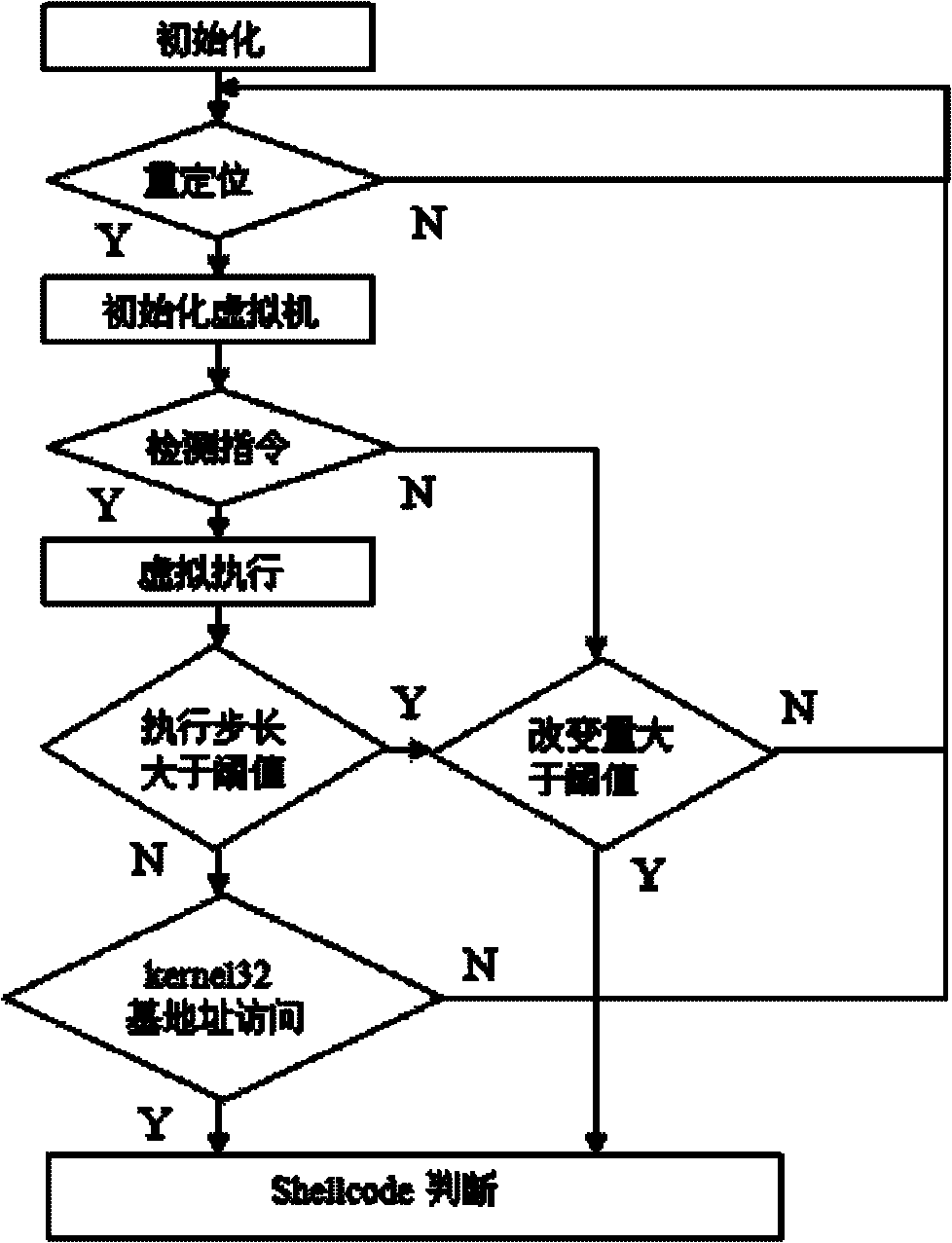
[0025] The virtual execution-based attack code detection method provided by the present invention adopts the dynamic virtual execution technology, and includes the following steps:
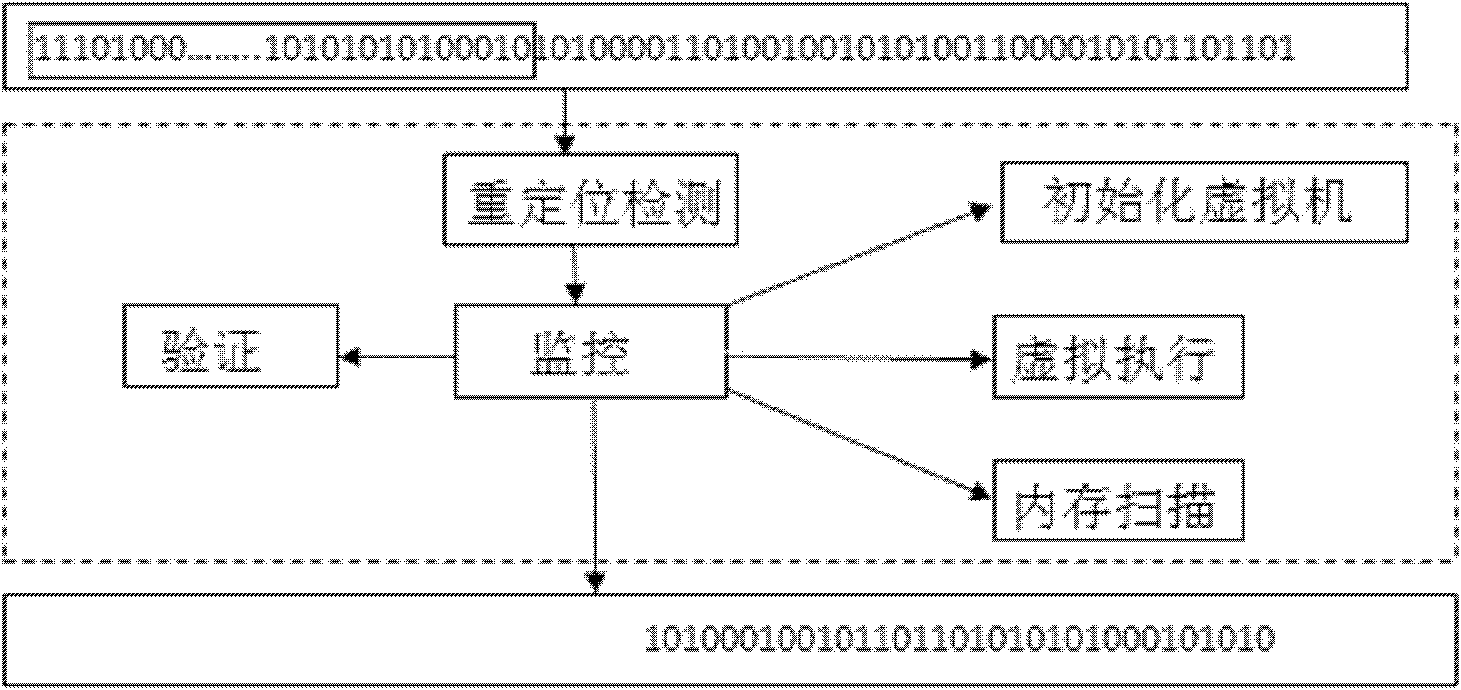
[0026] (1) Scan the network byte stream and determine whether there is a relocation instruction;
[0027] (2) After the relocation instruction is scanned, the virtual machine is initialized, and the network byte stream is put into the virtual machine for controlled execution from this instruction. The virtual machine in this step is a process filled with nop instructions, and the load address is Configurable;
[0028] (3) During the virtual execution process, the state of the virtual execution is dynamically monitored, and whether there is an attack code is judged a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com