Detecting system and method for shellcode based on memory searching
A detection system and search algorithm technology, which is applied in the field of network security intrusion detection and defense, can solve problems such as complex formats, poor compatibility, and inability to be parsed by analysis tools, and achieve the effect of improving the detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred embodiments of the present invention are given below in conjunction with the accompanying drawings to describe the technical solution of the present invention in detail.
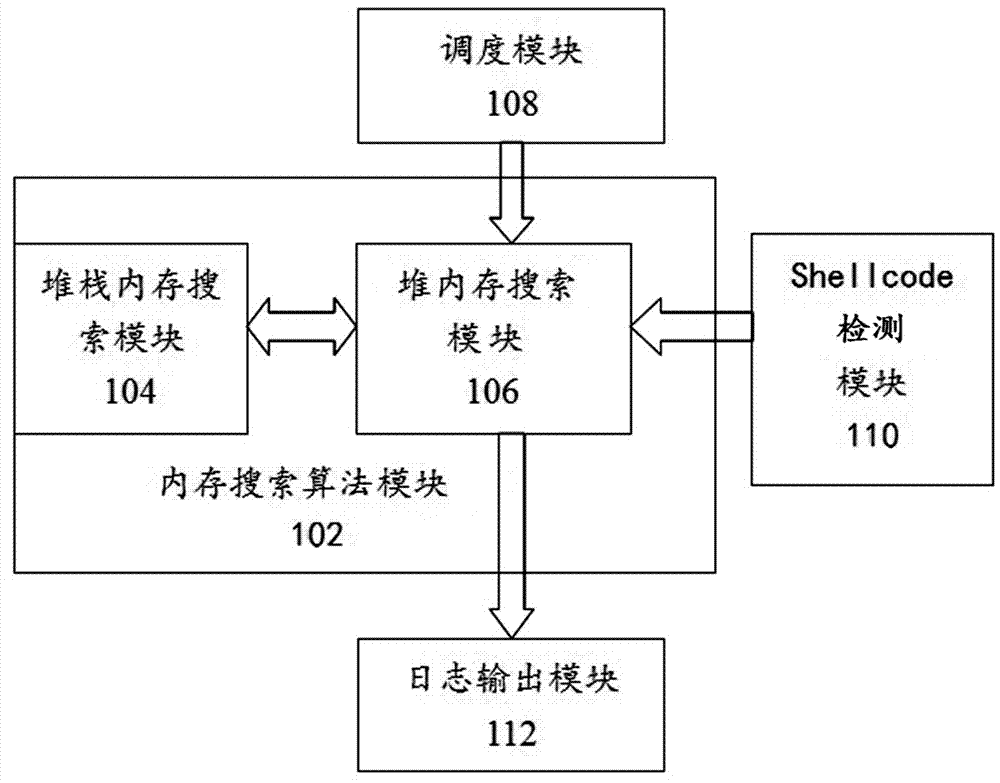
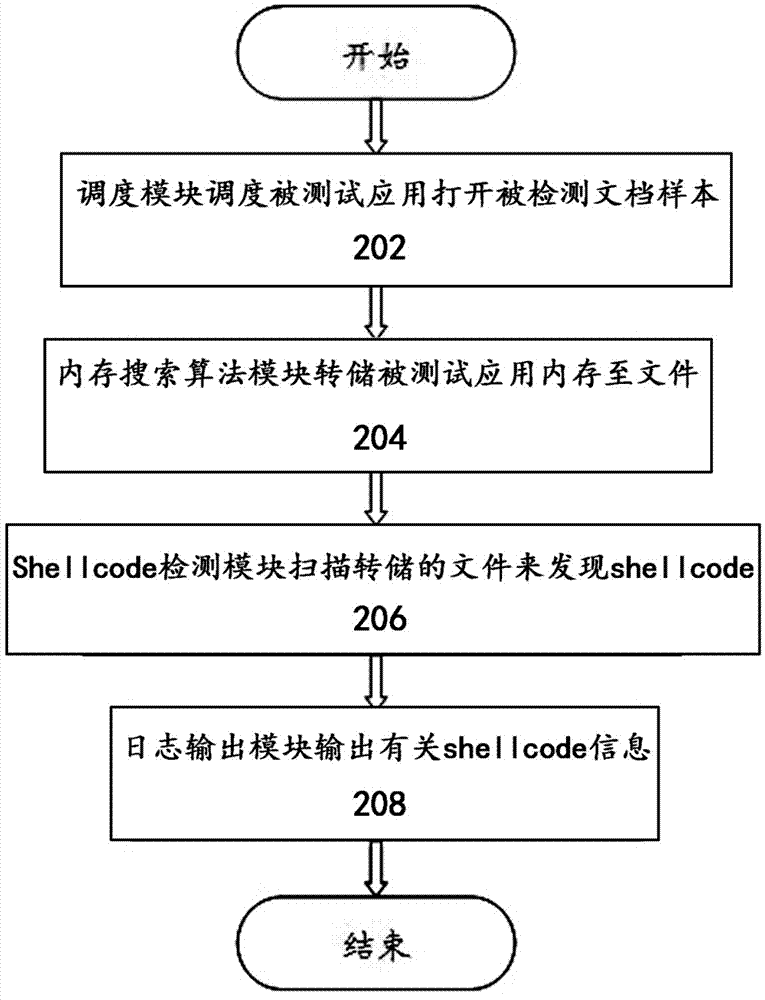
[0029] refer to figure 1 , which shows a block diagram of a shellcode detection system based on memory search according to an implementation example of the present invention. Please note that throughout the specification and claims, "application" and "software" have the same meaning and can be used interchangeably. In the embodiment of the present invention, the detection system of the shellcode based on memory search runs in the Windows operating system. However, as a general detection and testing system, the detection system for shellcode based on memory search can run in any operating system.
[0030] The detection system of the shellcode based on memory search includes stack memory search module 104, heap memory search module 106, scheduling module 108, shellcode detection module 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com