Network threat analysis method and system
A technology of threat analysis and network, which is applied in the field of network threat analysis system, can solve the problems of missed reporting, excessive requirements of security management personnel, high false alarm rate, etc., and achieve the effect of effective threat monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
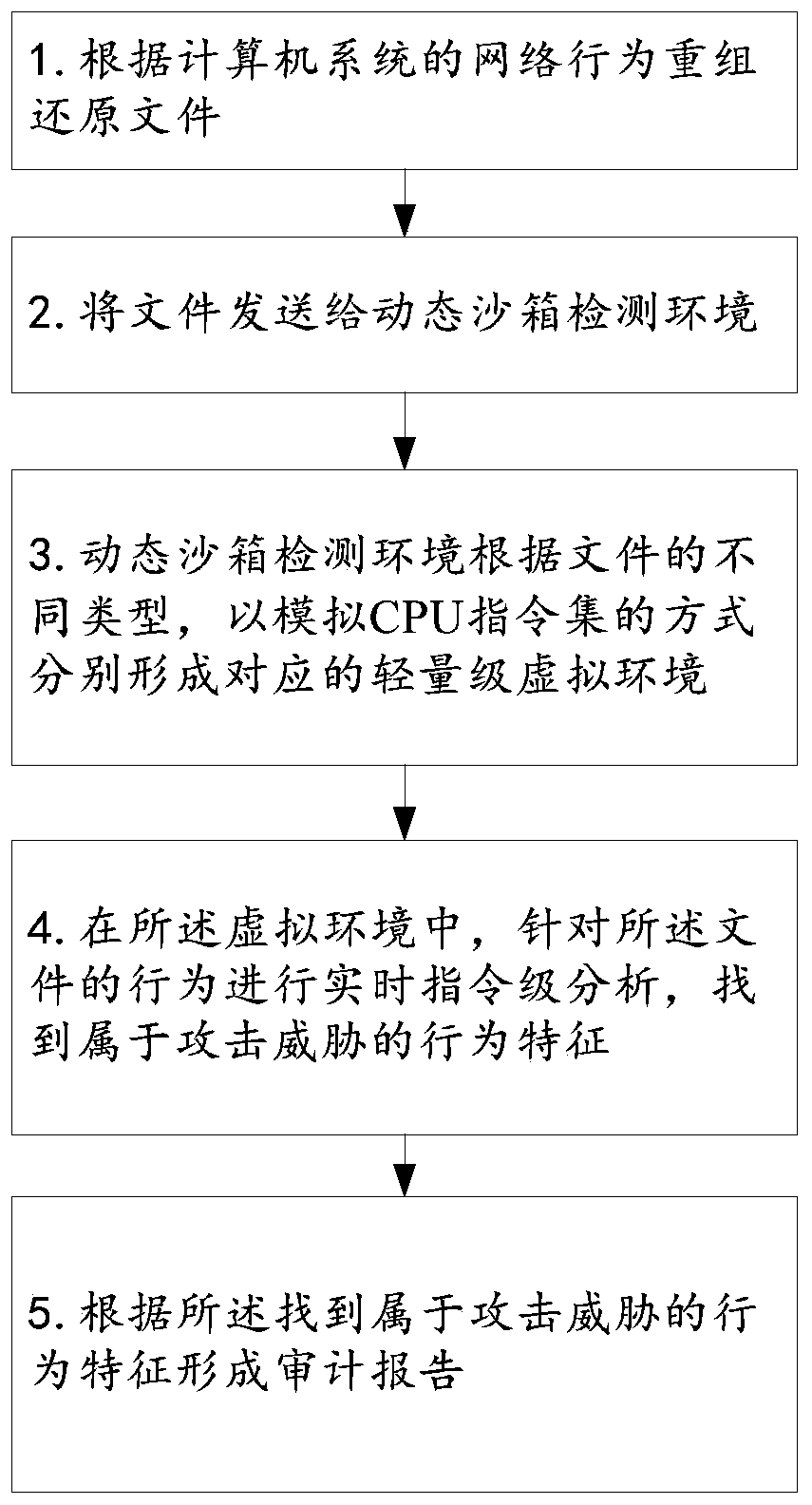
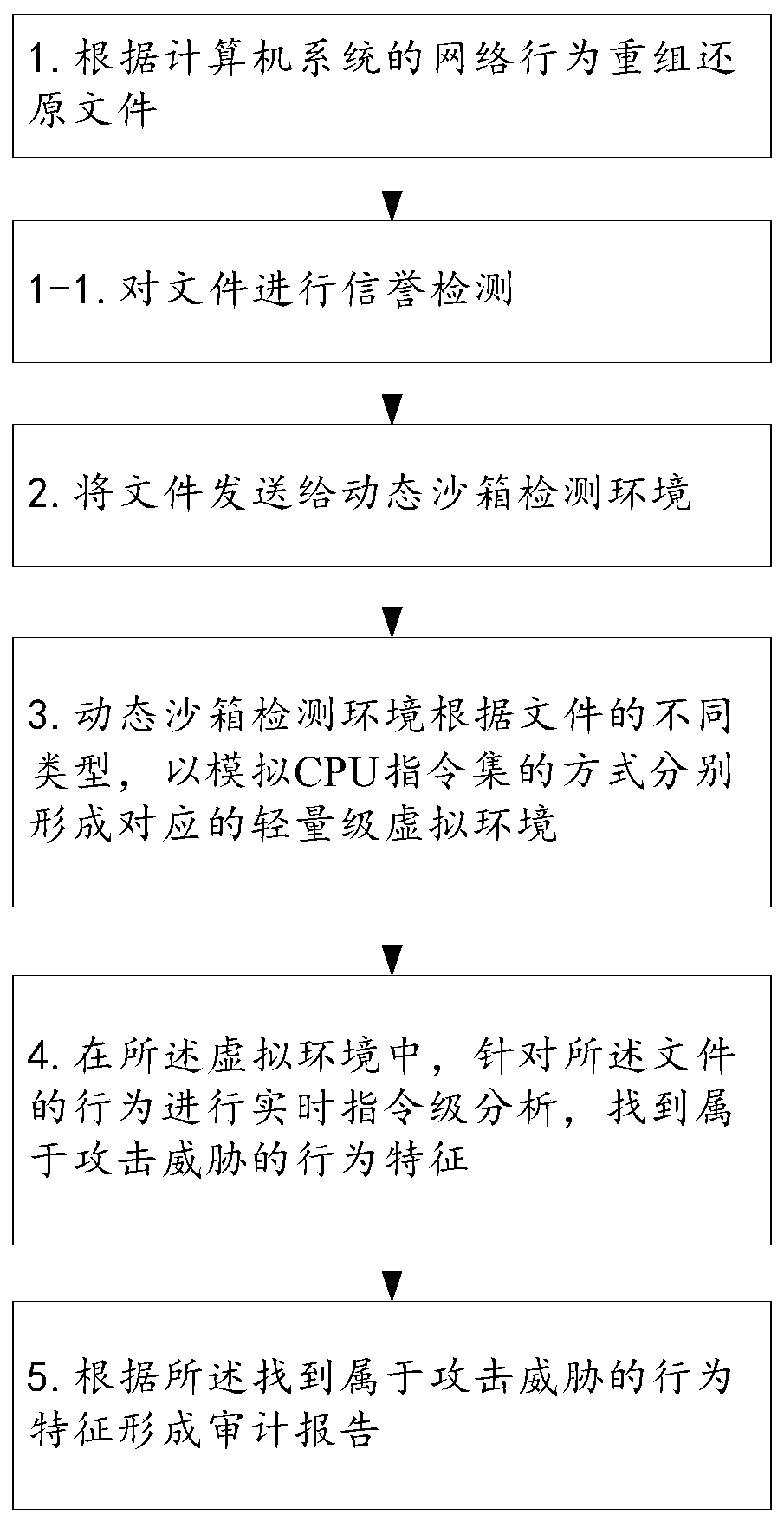
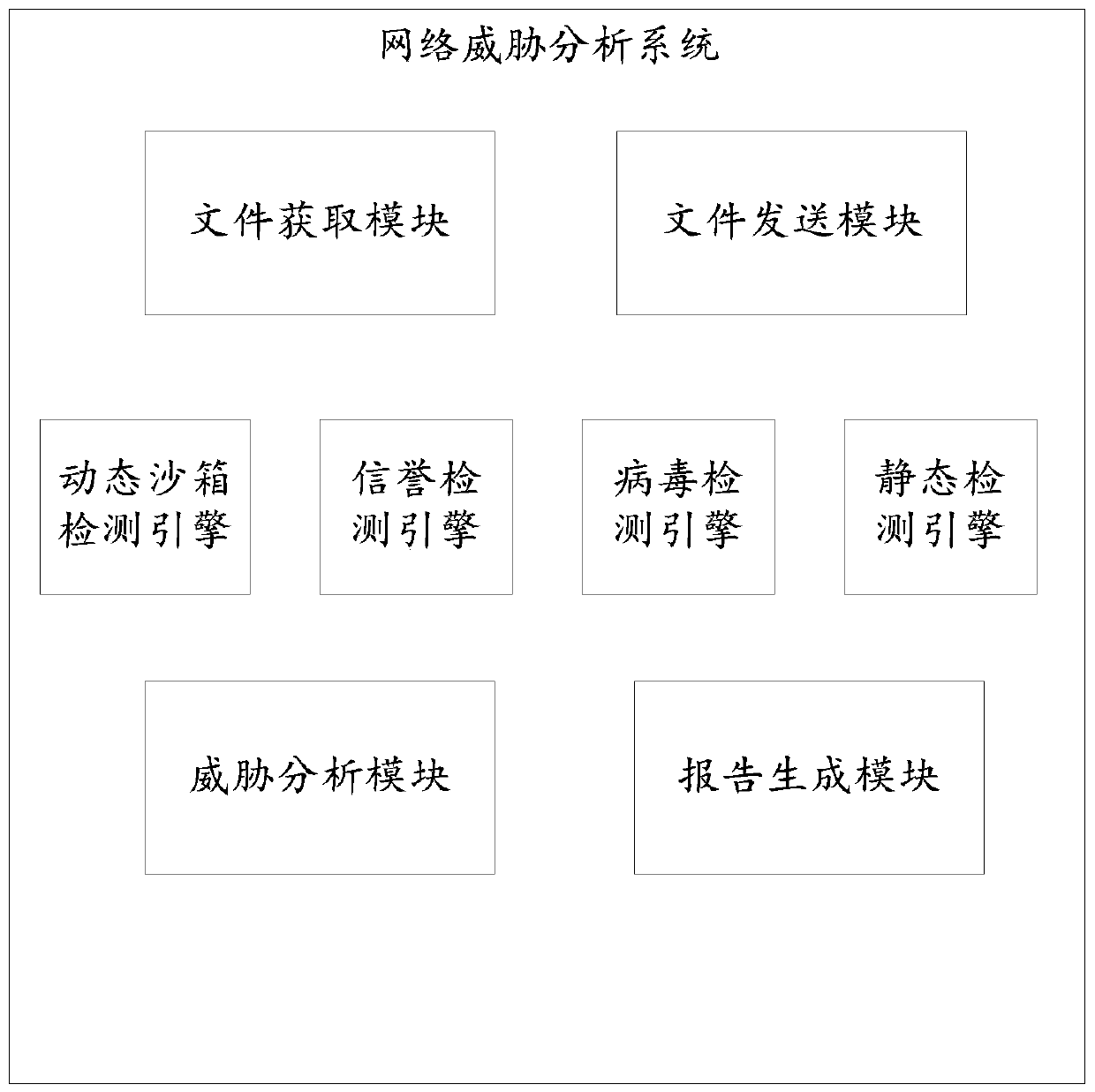
[0040] Aiming at the problems existing in the prior art, the embodiment of the present invention provides a method for network threat analysis, such as figure 1 As shown, the method may specifically include the following steps:
[0041] Step 1. Reorganize the restore file according to the network behavior of the computer system.
[0042] Specifically, from the analysis of the attack path of advanced sustainable threats, the vast majority of attacks come from web surfing, phishing emails, and file sharing. Based on this monitoring system, the decoding and restoration capabilities of the above related application protocols are provided, specifically including: HTTP, SMTP, POP3, IMAP, FTP, etc.
[0043] Furthermore, in order to detect threats more accurately, the analysis system takes into account the attack characteristics of advanced persistent threats, and performs a complete file restoration analysis on key file types. The system supports the following file decoding:
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com