Attack detection method for cloud platform virtual equipment and electronic device
A technology for virtual device and attack detection, applied in the field of system security, can solve problems such as poor scalability, wrong model construction, lack of device specification details, etc., to achieve the effect of reducing performance overhead and improving detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
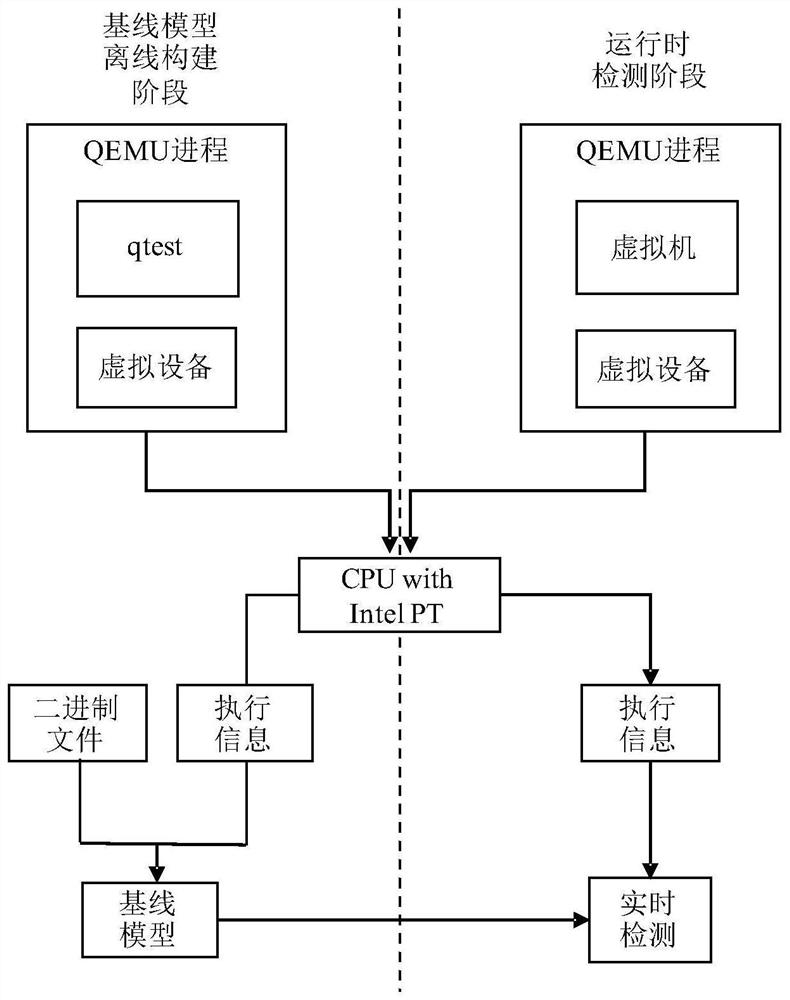
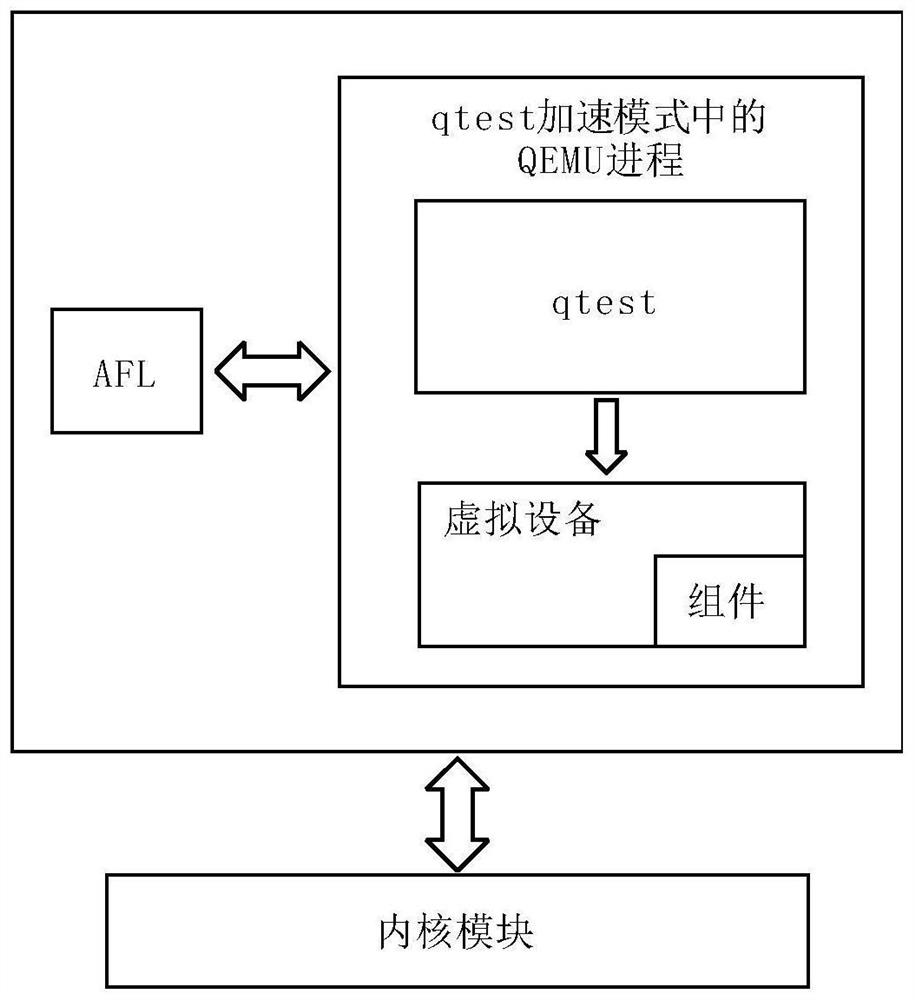
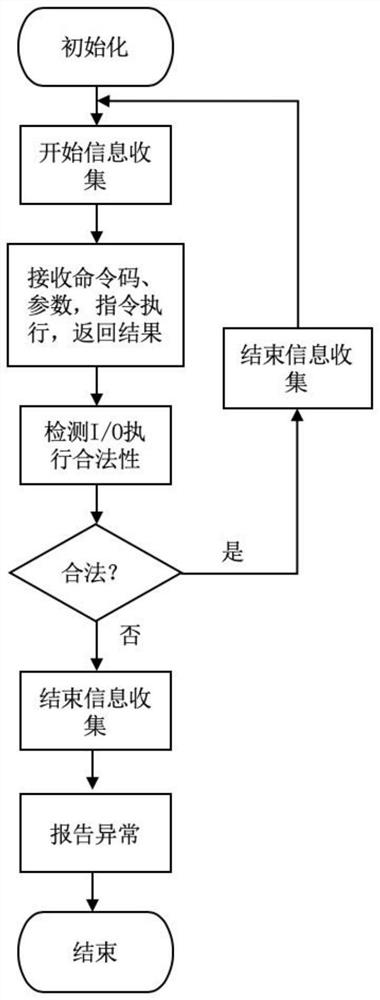
[0035] In order to make researchers in the technical field understand the present invention more comprehensively, the core technology in the present invention will be described in detail below in conjunction with the drawings and embodiments.
[0036] An attack detection system aimed at cloud platform virtual devices, the content of which includes:
[0037] 1) Execute information collection module
[0038] This module uses high-precision, low-overhead IntelPT hardware technology to collect data packets related to control flow during the execution of I / O instructions, and process them as execution information. Execution information in the present invention is jump information that affects control flow transfer, including conditional jump information and indirect jump information. Among them, the conditional jump has multiple target addresses, and some branches will not be reached during the normal execution of the program, but due to program logic loopholes and branch conditio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com