Similarity match based rapid detection method for malicious shellcode
A technology of similarity matching and detection method, which is applied in the field of fast detection of malicious shellcode based on similarity matching, can solve the problems of high false negative events, etc., and achieve the effects of improving throughput, reducing detection processing consumption, and increasing detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings.
[0021] The present invention includes:
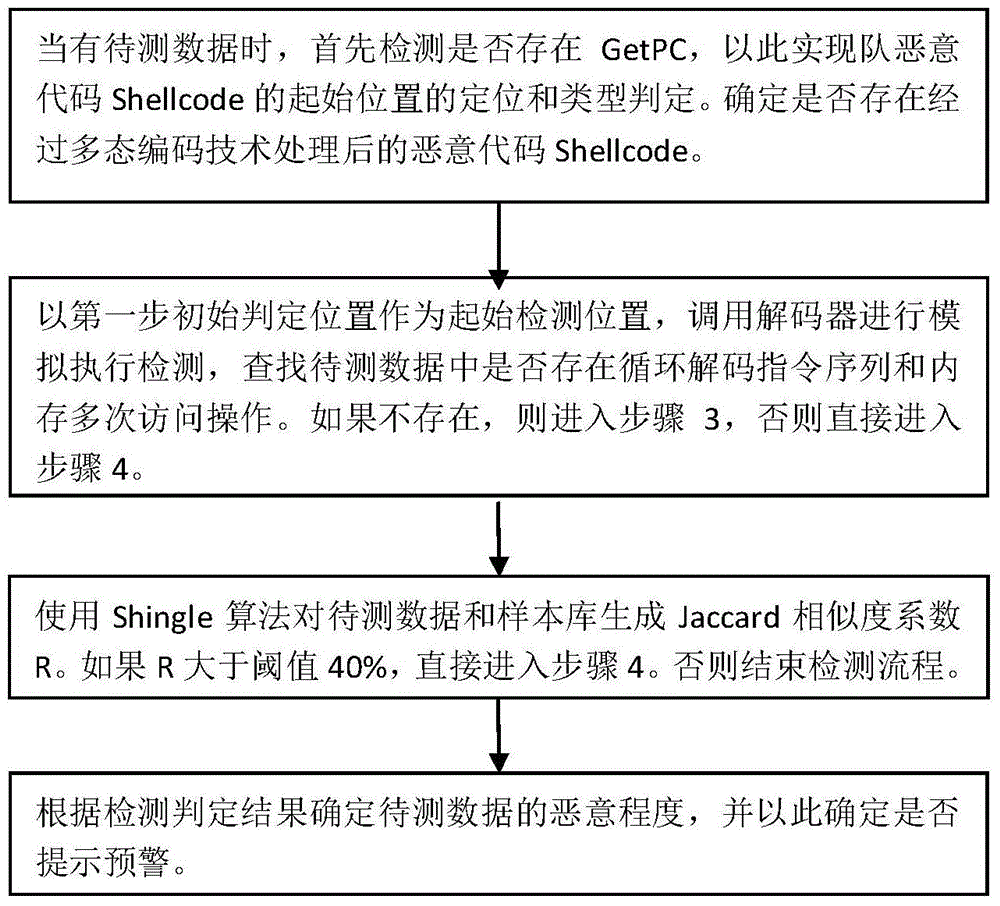
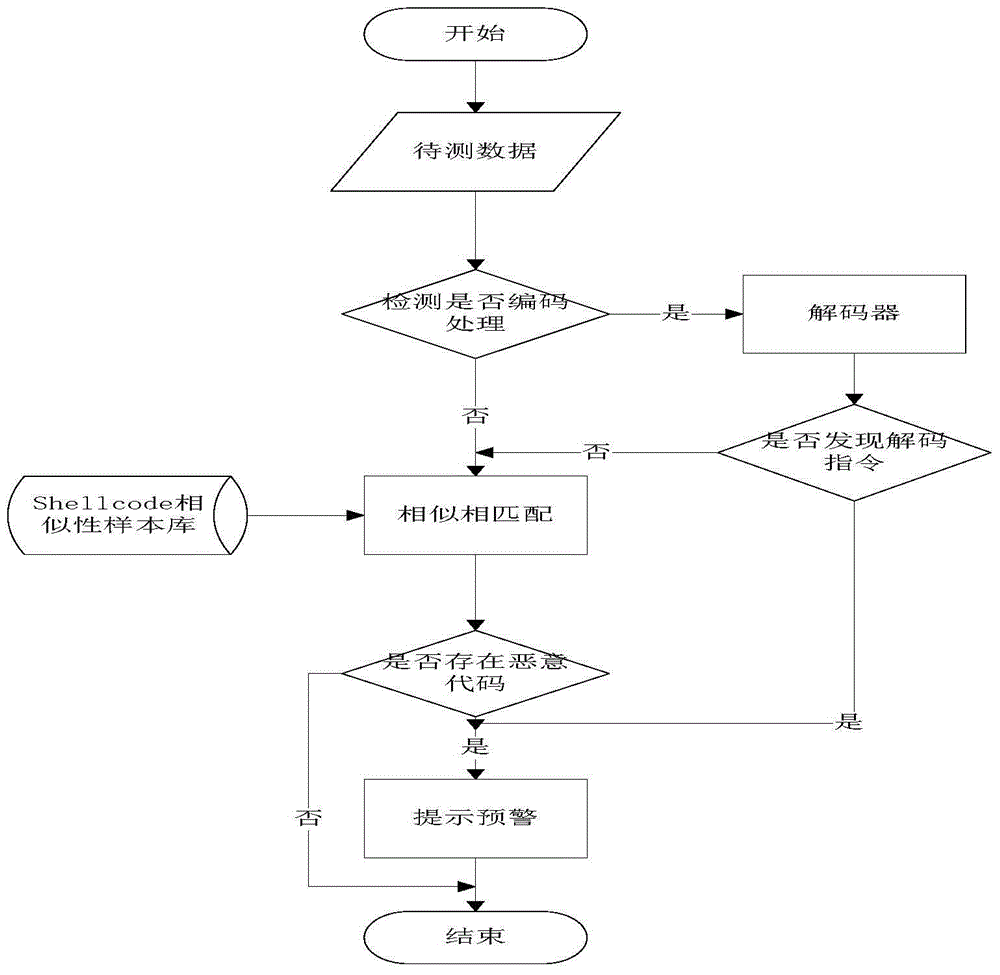
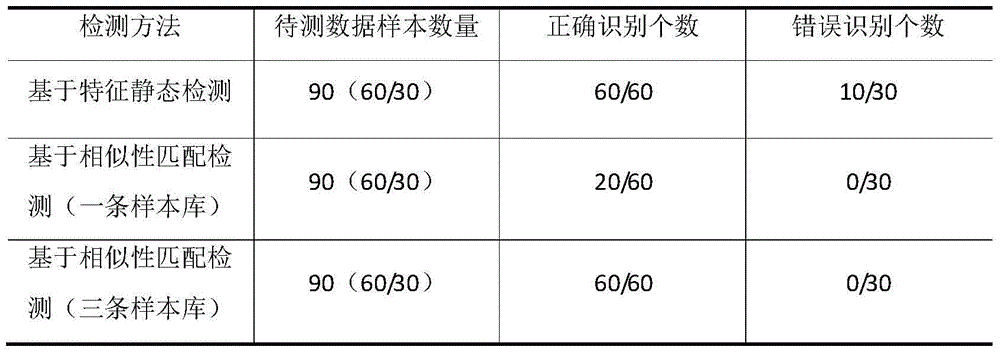
[0022] Step 1: When testing the data to be tested, a simple judgment will be made on the data to be tested based on similarity matching detection technology to determine whether there are suspicious GetPC and floating-point operation instructions such as call, jmp, and fnstenv instructions. According to the judgment result, if there is a suspicious instruction, it should use encoding processing, and determine the start of the simulation execution detection position using the decoder, improve the execution efficiency of the simulator, and reduce the detection scale of the data to be tested. When these steps are completed, go to step 2;
[0023] Step 2: At the initial detection position determined in the first step, call the decoder to perform simulated execution detection, and find out whether there are loop decoding instruction...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com