Heapspray detection method based on intermediate command dynamic instrumentation
A technology of intermediate instructions and detection methods, applied in computer security devices, instruments, calculations, etc., can solve the problems of low accuracy and large system overhead, and achieve the effect of improving accuracy and reducing system overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
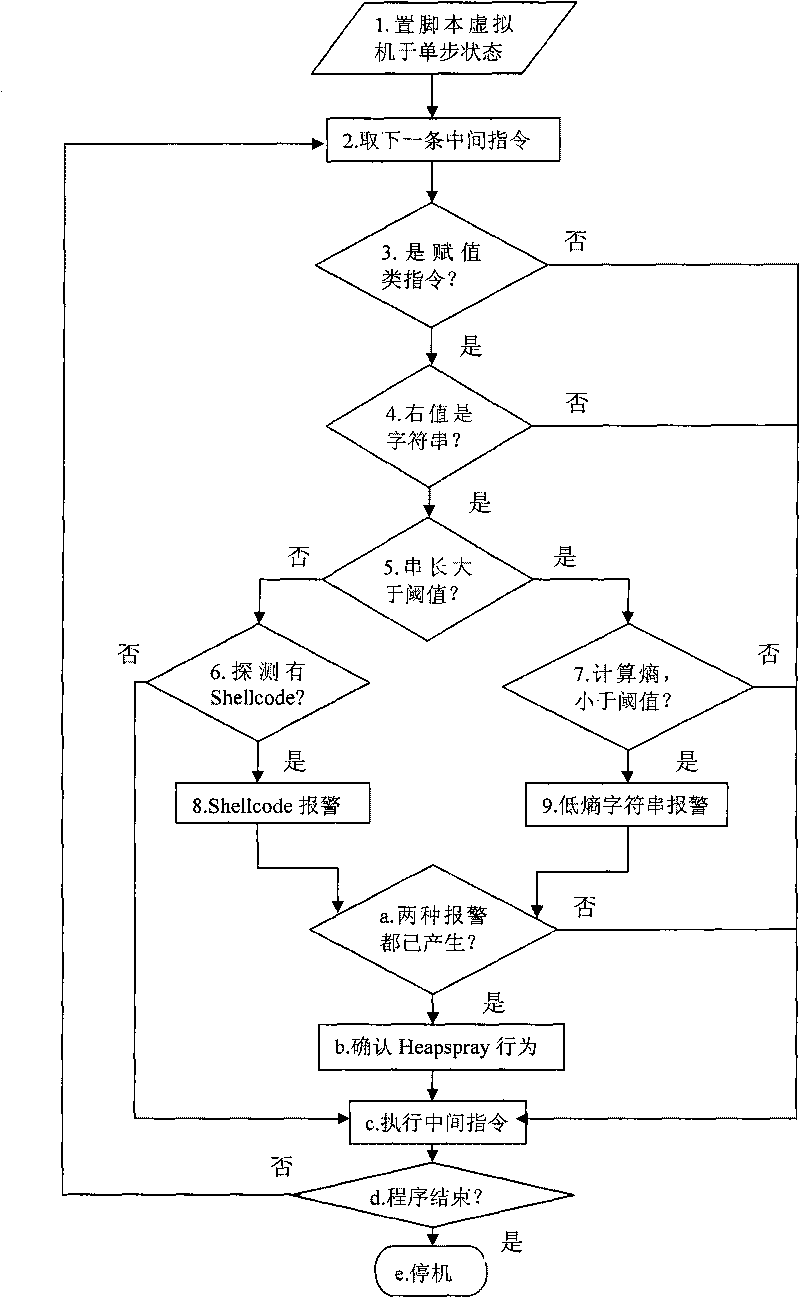
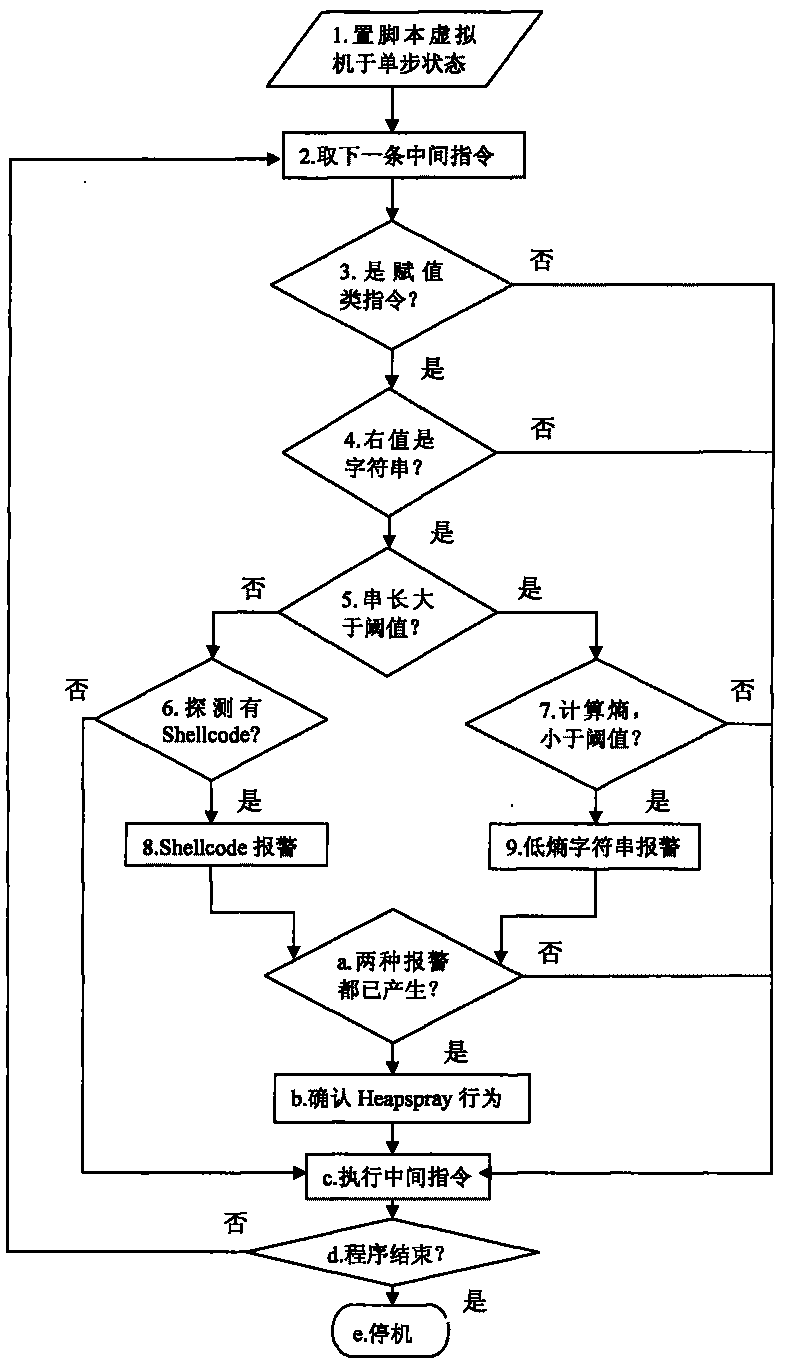
[0023] The following takes the most widely used JavaScript execution engine in web pages as an example to describe the detection method in detail.
[0024] The specific implementation process of a Heapspray detection method based on dynamic intermediate instruction instrumentation is as follows:
[0025] 1. Switch the JavaScript virtual machine to the single-step tracking state, and register a Handler function at the same time, so that the single-step virtual machine will call this Handler function before executing an intermediate instruction every time. (correspond figure 1 Step 1) in
[0026] 2. Make the global variable hasShellcode=lowEntropy=0, and input the JavaScript script in the web page into the JavaScript virtual machine for execution;
[0027] 3. Since the Handler function is registered in advance, in each step of the virtual machine execution process, we can use the Handler function to complete the acquisition and inspection of the instructions to be executed; (c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com