System and method for defending against mobile storage medium virus in island-like Ethernet
A mobile storage medium, Ethernet technology, applied in the field of virus defense of the internal mobile storage medium of the Ethernet, can solve problems such as complicated process, over-reliance on internal mobile storage devices, and difficulty in writing Trojan horses directly into internal mobile storage devices, so as to avoid The possible effects of a leak
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
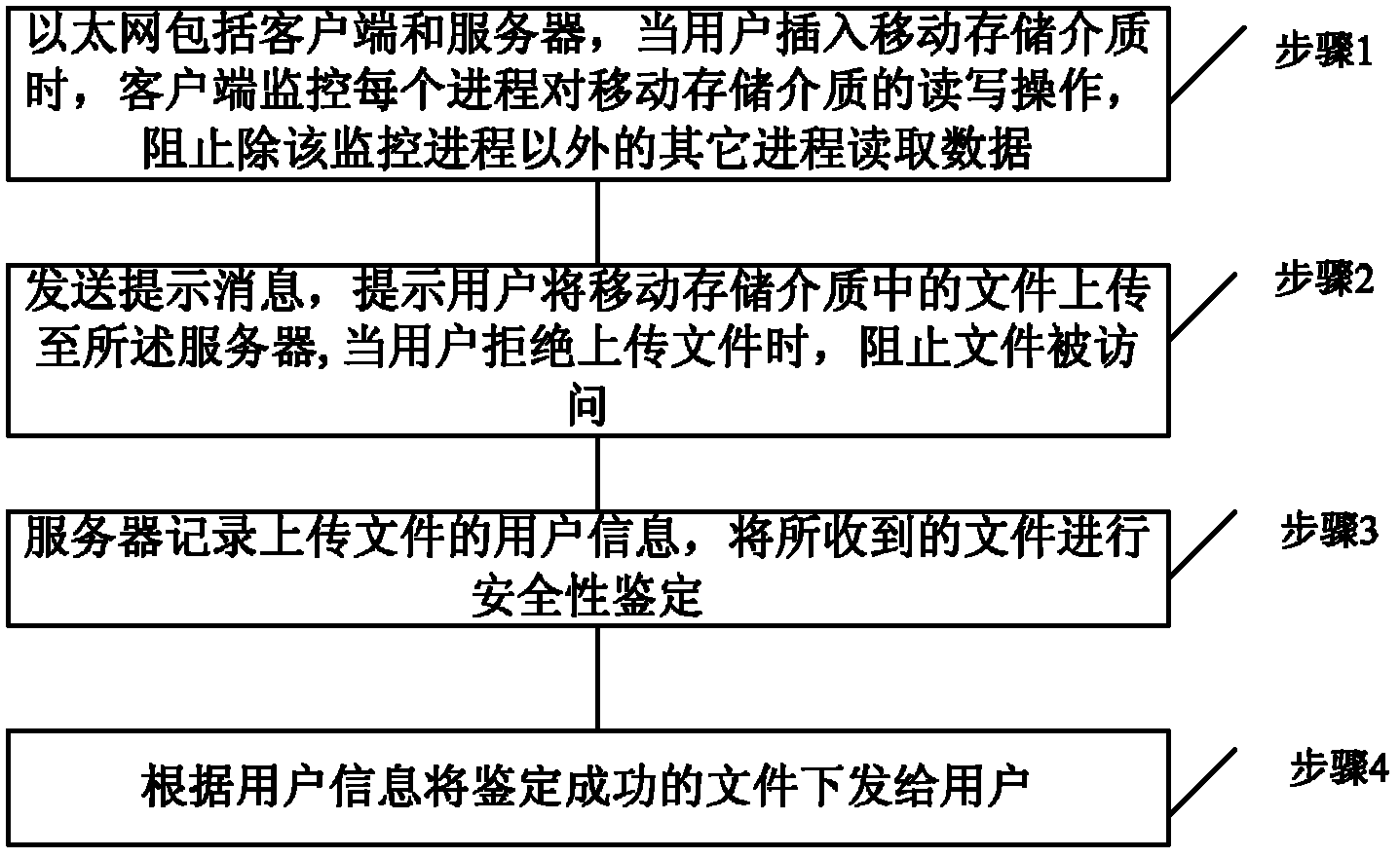
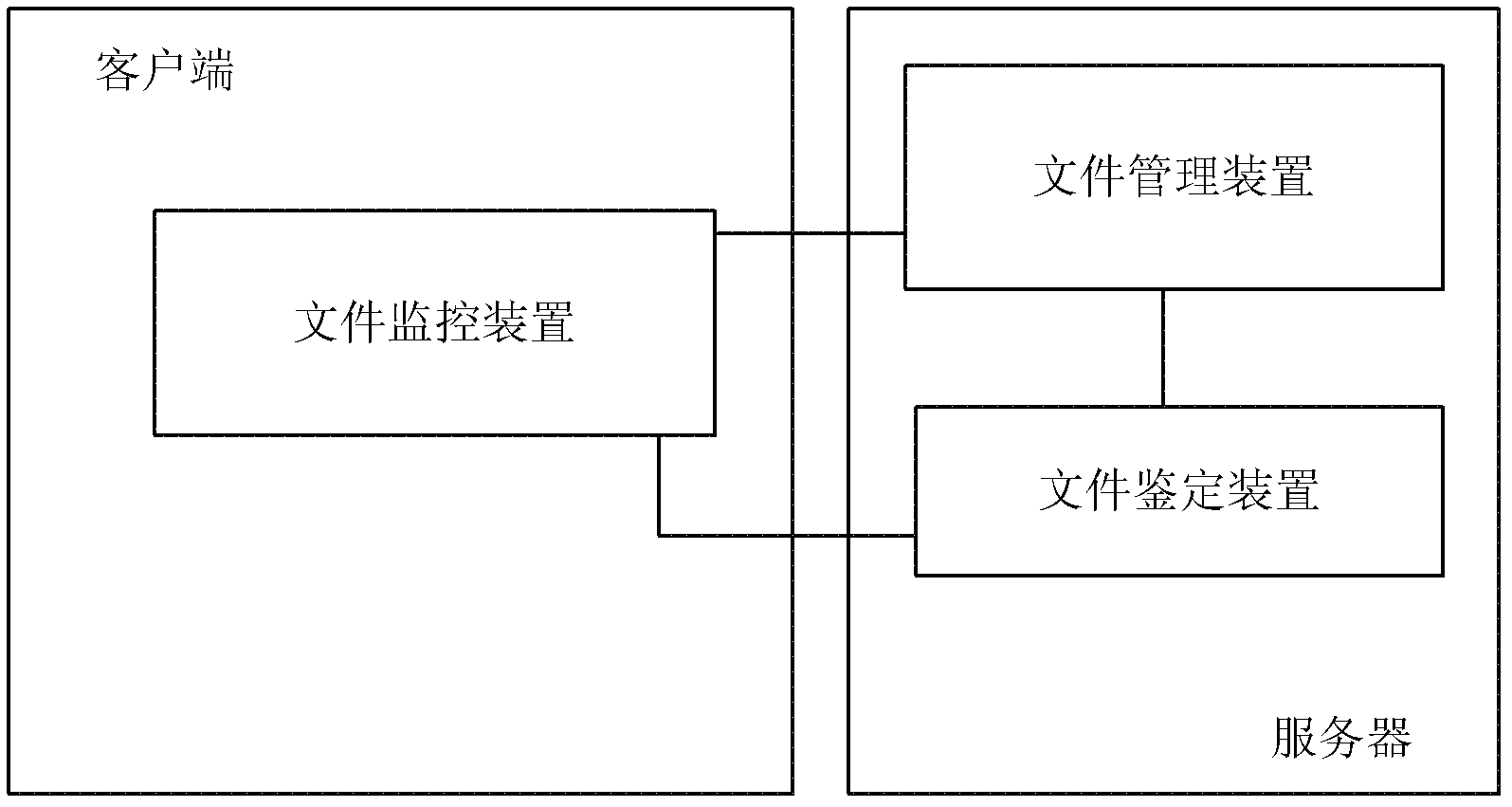
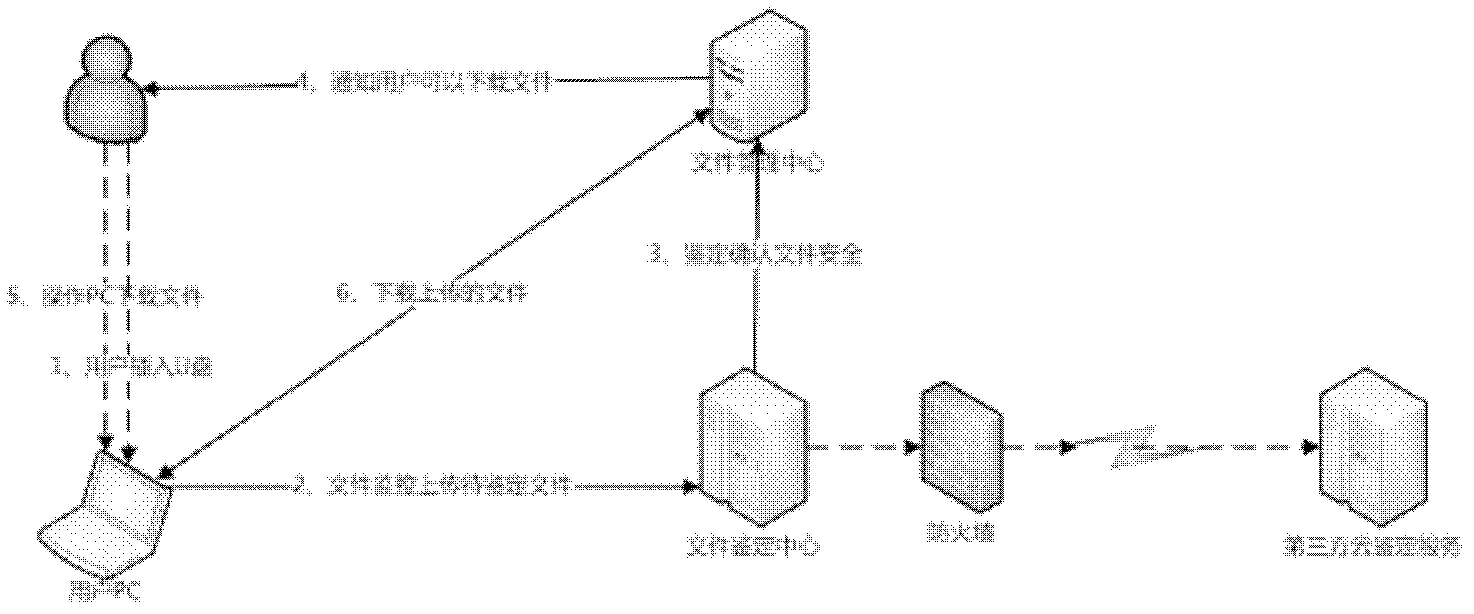
[0032] Such as figure 1 As shown, the present invention provides a method for defending against removable storage medium viruses in an island-type Ethernet, and the Ethernet includes a client and a server. When a user inserts a removable storage medium, the client monitors each process's read and write operations to the removable storage medium , prevent other processes from reading data (step 1) except the monitoring process, and send a prompt message to prompt the user to upload the file in the removable storage medium to the server, and when the user refuses to upload the file, prevent the file from being accessed ( Step 2); the server records the user information of the uploaded file, and conducts security authentication on the received file (step 3); sends the successfully authenticated file to the user according to the user information (step 4).
[0033] In the process of file downloading in step 4, the server may notify the user to download the file, and download the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com