Real person identity verification method
An identity verification method, a technology of a real person, applied in the field of identity verification, can solve the problems that fingerprints need to be entered in advance, computer face recognition needs to enter face images in advance, and the use of stolen documents to apply for a card can achieve low rejection rate and improve accuracy , conducive to the effect of promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
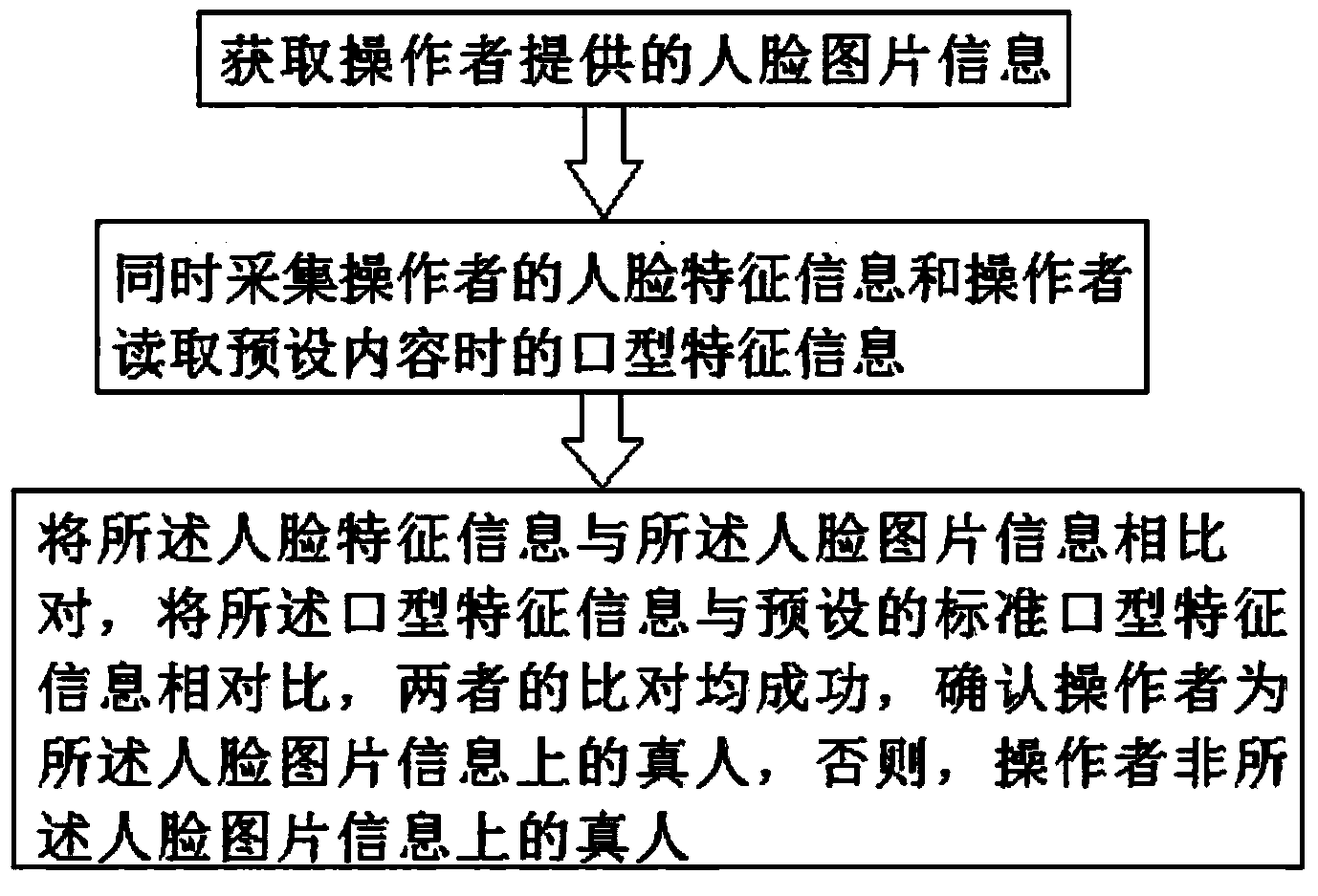
[0020] see figure 1 As shown, a real-person authentication method includes the following steps:
[0021] Step A1: Obtain the face picture information provided by the operator.
[0022] In step A1 of the real-person identity verification method of the present invention, the face picture information comes from a valid certificate with a photo provided by the operator, such as an ID card, a student card, a passport, etc., and the valid certificate is scanned by a certificate scanning tool. Obtain face image information and other information.
[0023] Step A2: In the case of good environmental factors such as light, simultaneously collect the operator's facial feature information and mouth-shaped feature information when the operator reads the preset content.
[0024] In step A2 of the real person identity verification method of the present invention, the preset content is any character or any combination of characters in a plurality of random characters, letters or numbers, and...
Embodiment 2
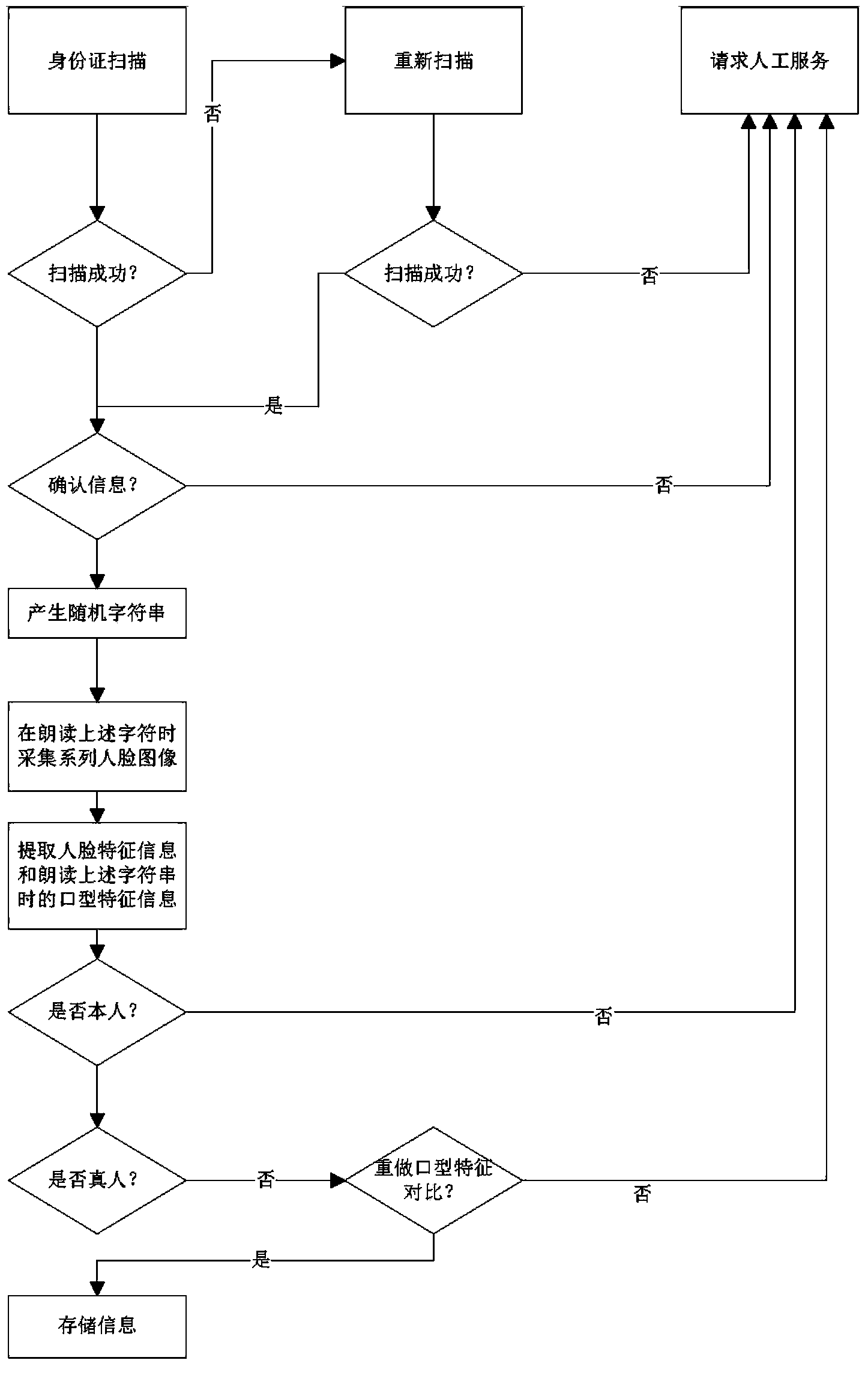
[0031] A real person identity verification method, comprising the following steps:
[0032] Step B1: Obtain the face picture information provided by the operator.
[0033] In step B1 of the real-person identity verification method of the present invention, the face picture information comes from a valid certificate provided by the operator. In this embodiment, the valid certificate is an ID card; the operator provides the face picture information At the same time, the identification information is provided, and according to the identification information, the authenticity of the identification identity or whether it is a preset identity that does not provide real-person identity verification is confirmed.
[0034] Step B2: Obtain the ID card information of the operator from the information database of the public security department. The ID card information includes the photo of the ID card, and compare the face image information with the photo of the ID card. If the comparison...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com