Patents
Literature
112results about How to "Reduce the burden of use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
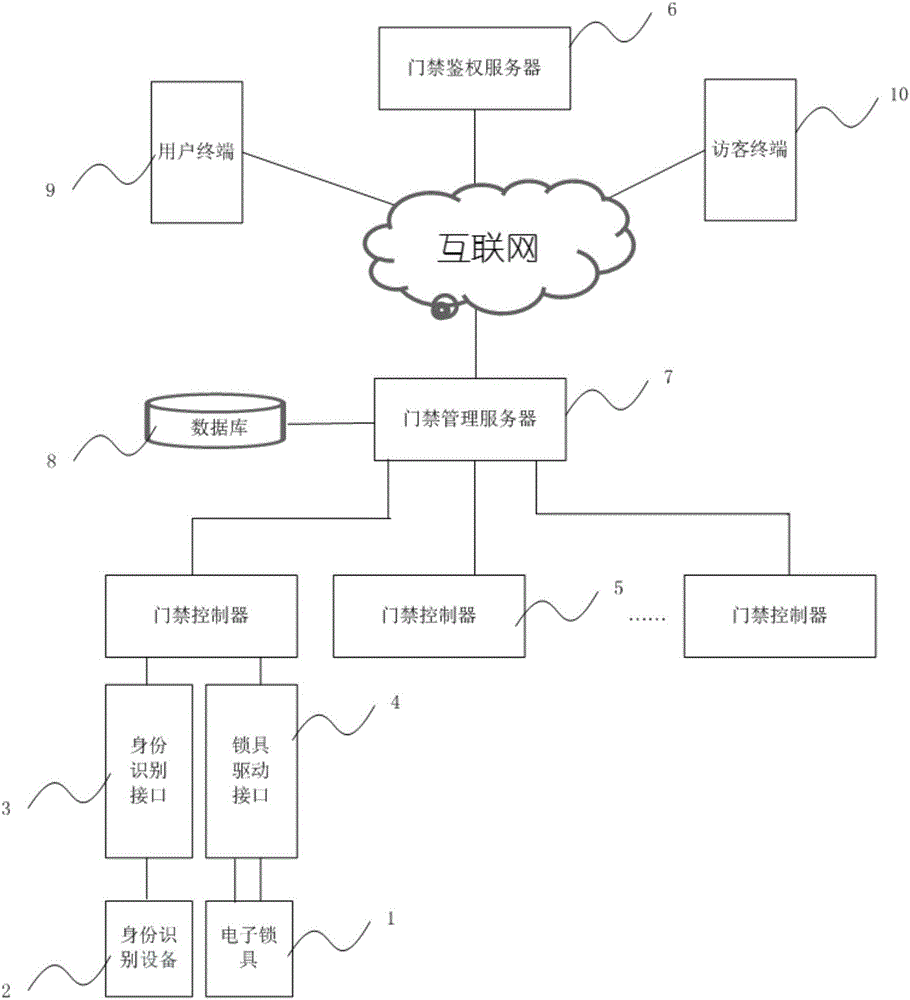
Method for connecting mobile terminal to network, mobile terminal and terminal equipment
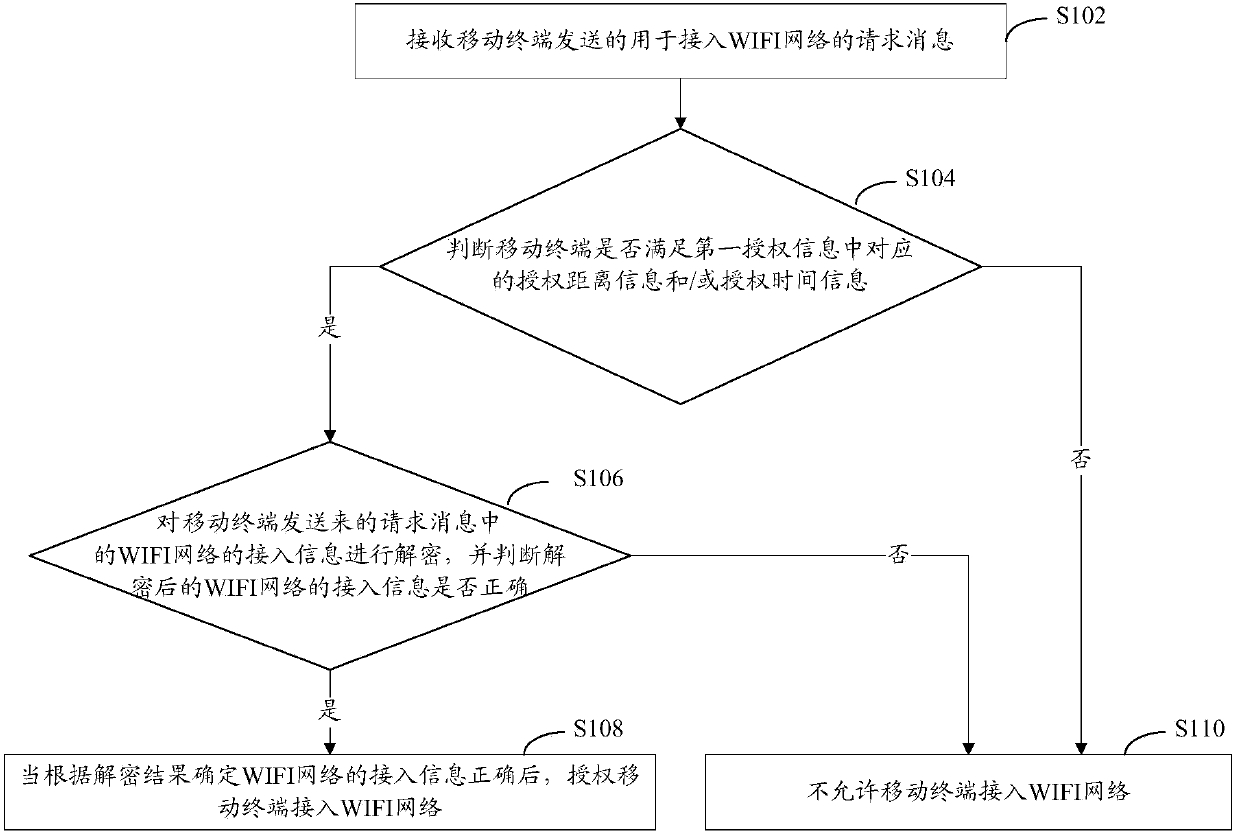
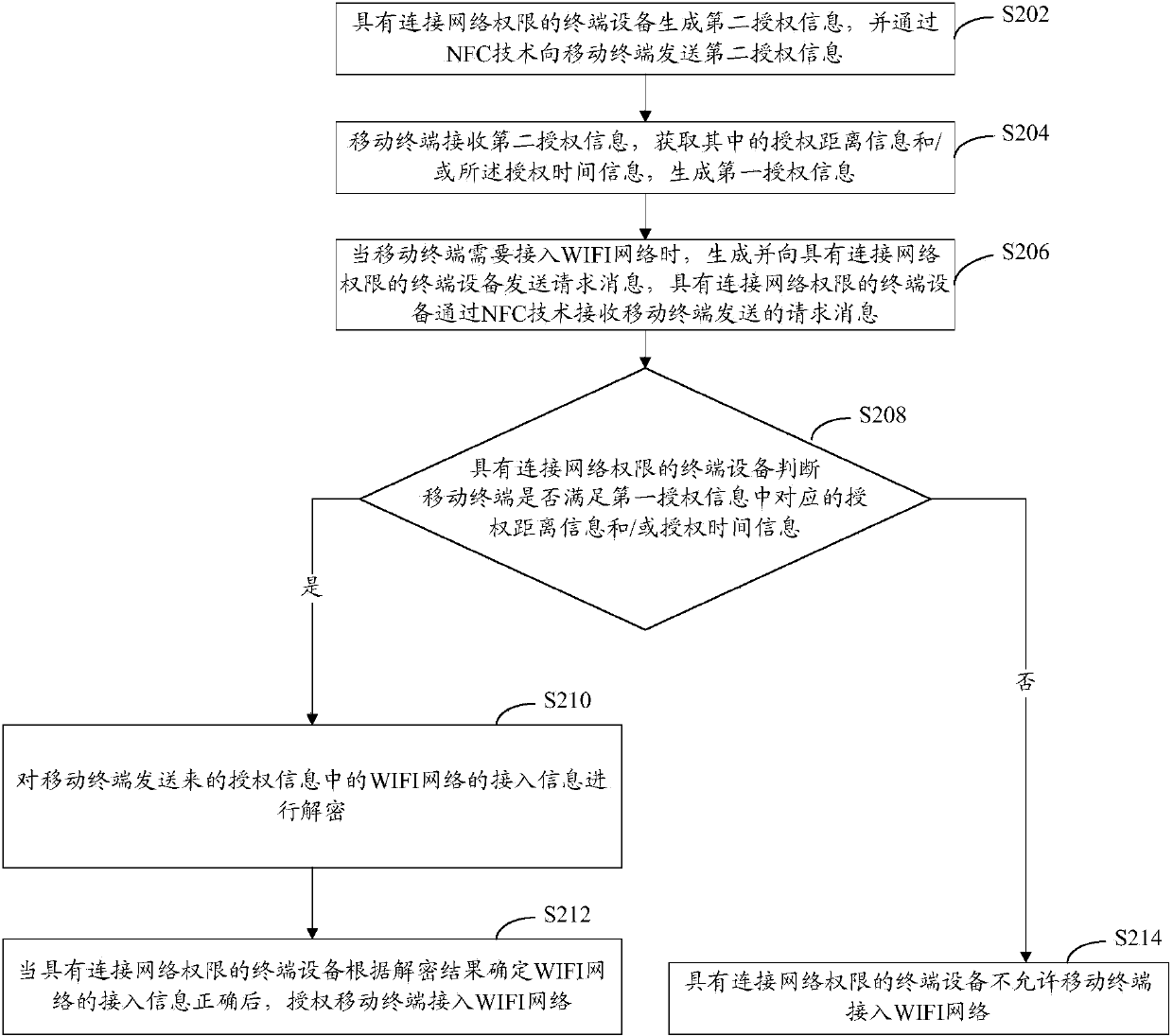
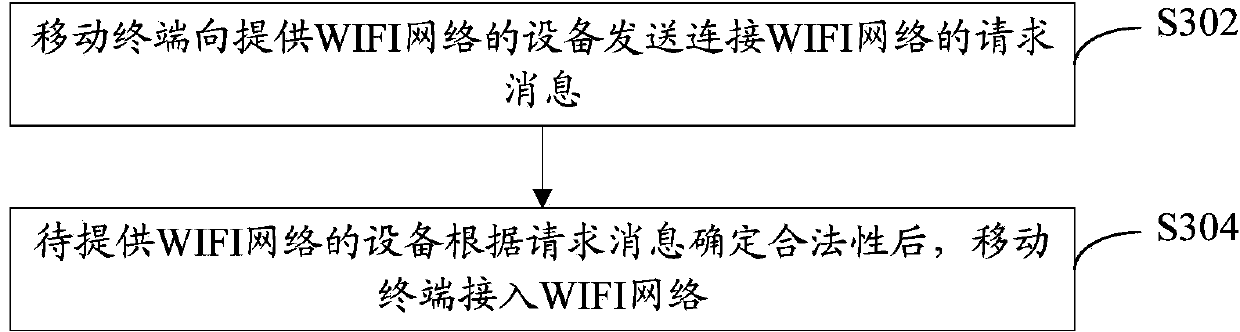
ActiveCN103476030AImprove access efficiencyReduce the burden of useNetwork topologiesConnection managementTime informationWifi network
The embodiment of the invention provides a method for connecting a mobile terminal to a network, a mobile terminal and terminal equipment. The method comprises the following steps: receiving a request message which is transmitted by the mobile terminal and used for accessing into a WIFI (wireless fidelity) network, wherein the request message also comprises first authorization information besides access information of the encrypted WIFI network, judging whether the mobile terminal meets corresponding authorization distance information and / or authorization time information in the first authorization information, and if so, decrypting the access information of the WIFI network; authorizing the mobile terminal to be accessed into the WIFI network after correct access information of the WIFI network is determined according to the decryption result. By adopting the scheme disclosed by the embodiment of the invention, the access efficiency of the WIFI network is improved; leakage of the access information of the WIFI network is avoided; the safety of the WIFI network is also guaranteed.
Owner:XIAOMI INC
Realization method of data encryption in hard disk
InactiveCN102053925AReduce overheadReduce use costUnauthorized memory use protectionSpecial data processing applicationsFile systemHabit
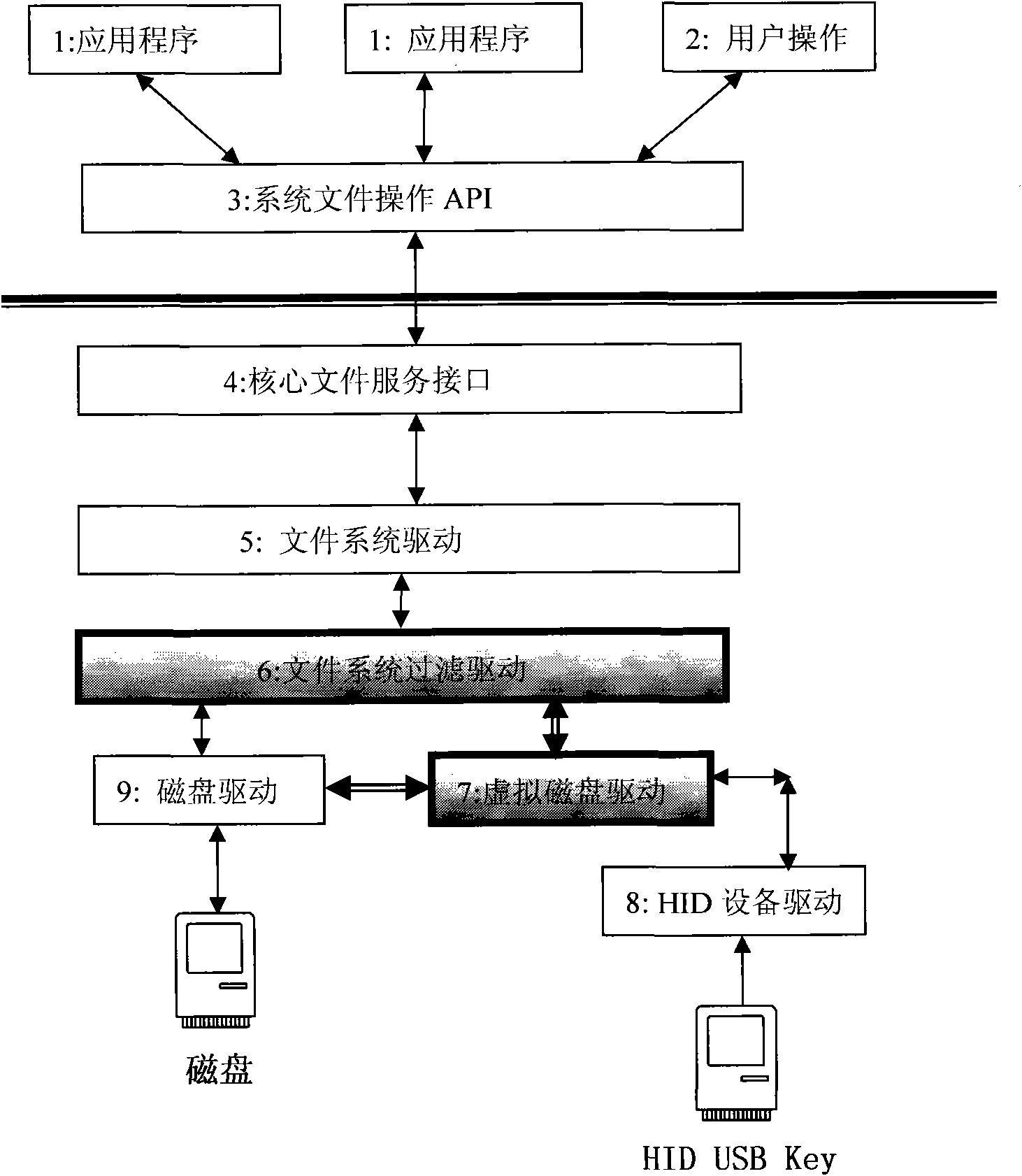
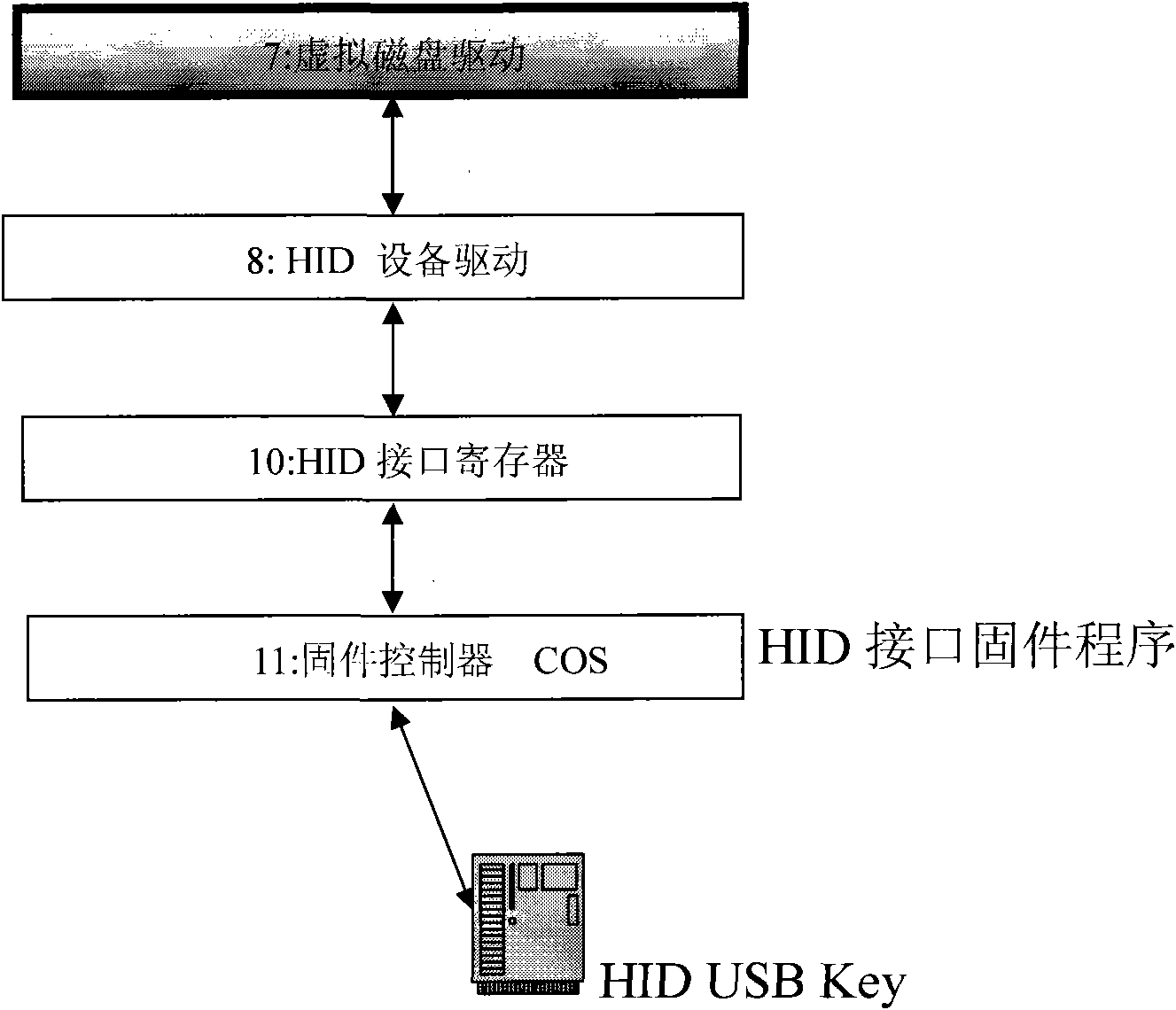
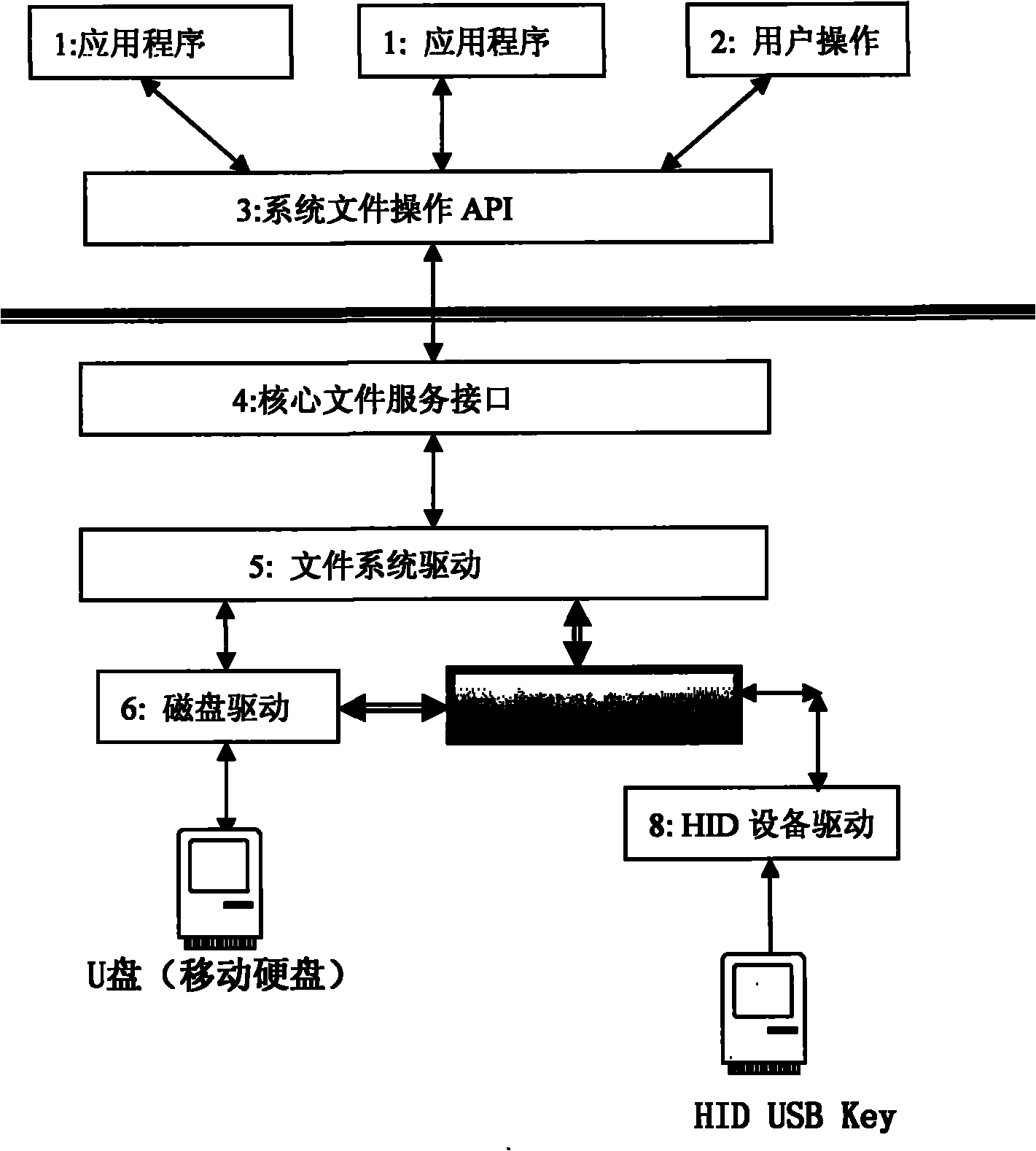
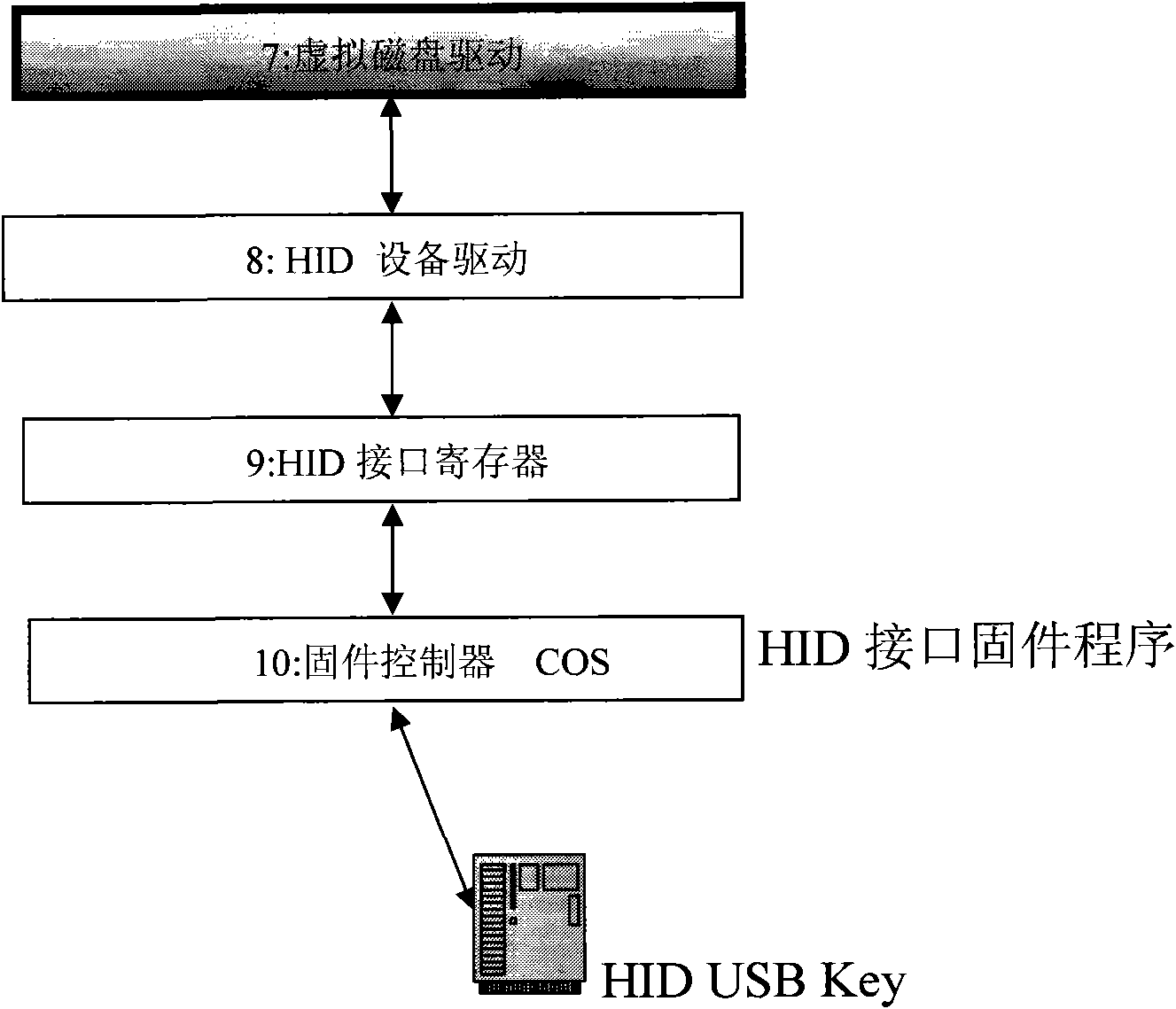
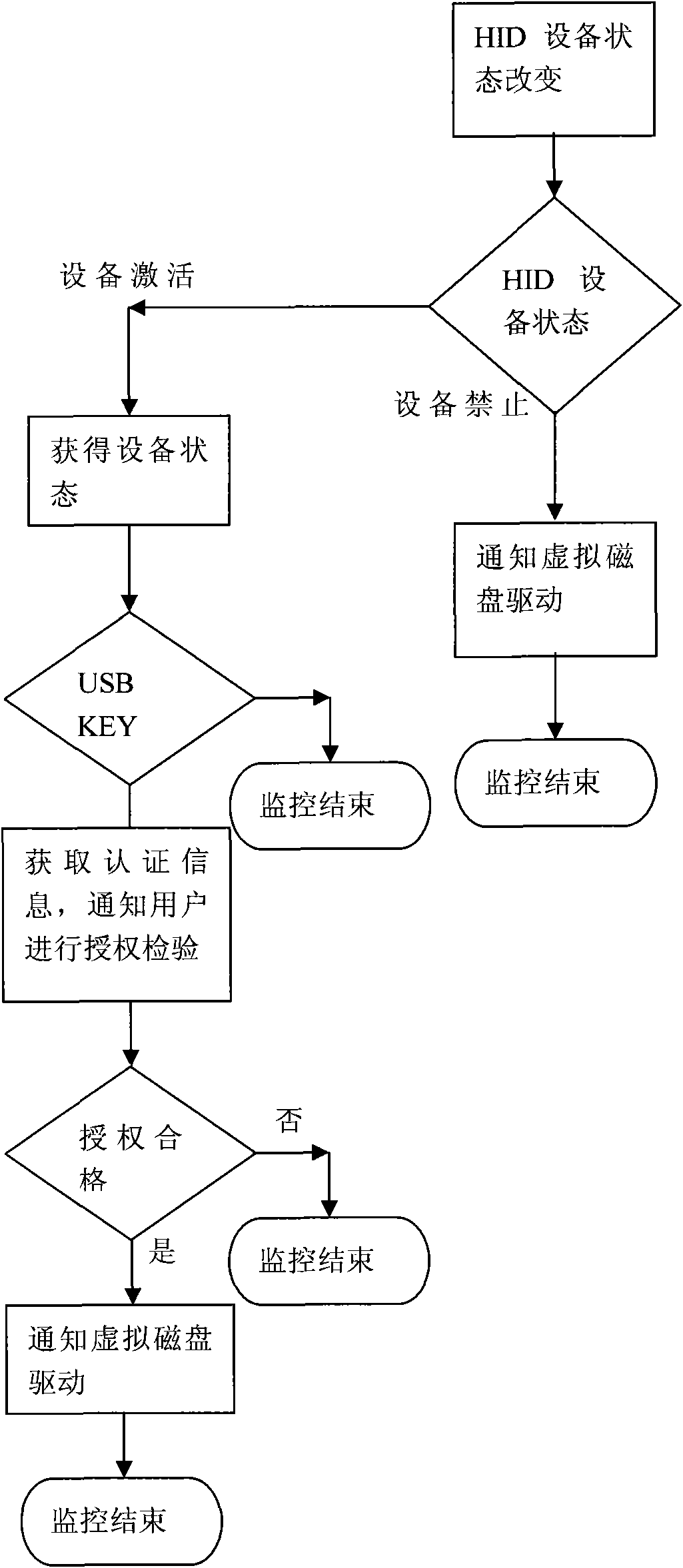
The invention provides a realization method of data encryption in a hard disk, comprising the following steps: monitoring the status of a USB (universal serial bus) Key in real time, performing identity authentication by using an authorized USB Key and obtaining a secret key; storing the protected data in a protected catalog, mapping the space of the protected catalog into a virtual disc when the authorized authentication is successful, encrypting the data written into the disc and deciphering the data read from the disc; using an unprotected catalog as the common disc catalog; and hiding the virtual disc to prevent the access of the protected catalog and the protected data when the authorized USB Key is absent. The data stored in the virtual disc storage area of the protected catalog is encrypted forever, and is automatically decrypted in a memory when being used by a user. The method provided by the invention has the advantages that various discs and various file system can be supported, the traditional data use habit and application program behavior are not changed, and users do not need to purchase new disc devices.
Owner:许燕
U disk encryption method
InactiveCN101877246AReduce overheadReduce use costRead-only memoriesUnauthorized memory use protectionFile systemDisk encryption theory
The invention provides a U disk (mobile hard disk) encryption method which monitors the USB Hey state in real time, carries out identity verification and obtains a key by authorized USB Key, wherein the protected U disk (mobile hard disk) is divided into a protective area and a non-protective area; the protective area is mapped into a virtual disk when the authorized verification is passed, data wrote into the disk is encrypted and the data read from the disk is decrypted; the non-protective area is still used as a common U disk (mobile hard disk). When the USB Key does not exist, the protective area cannot be accessed. The data stored in the protective area of the U disk (mobile hard disk) is encrypted forever, and is automatically decrypted in a memory when being used by a user. The invention supports the U disks (mobile hard disks) and file systems of all types, does not change the use habit of conventional data and the action of application programs of users, and does not require the users to buy new U disk (mobile hard disk) equipment.
Owner:许燕
Three-network convergence oriented digital home network architecture
ActiveCN102064959ARealize interconnectionReduce the burden of useNetwork connectionsSmart applianceNetwork architecture
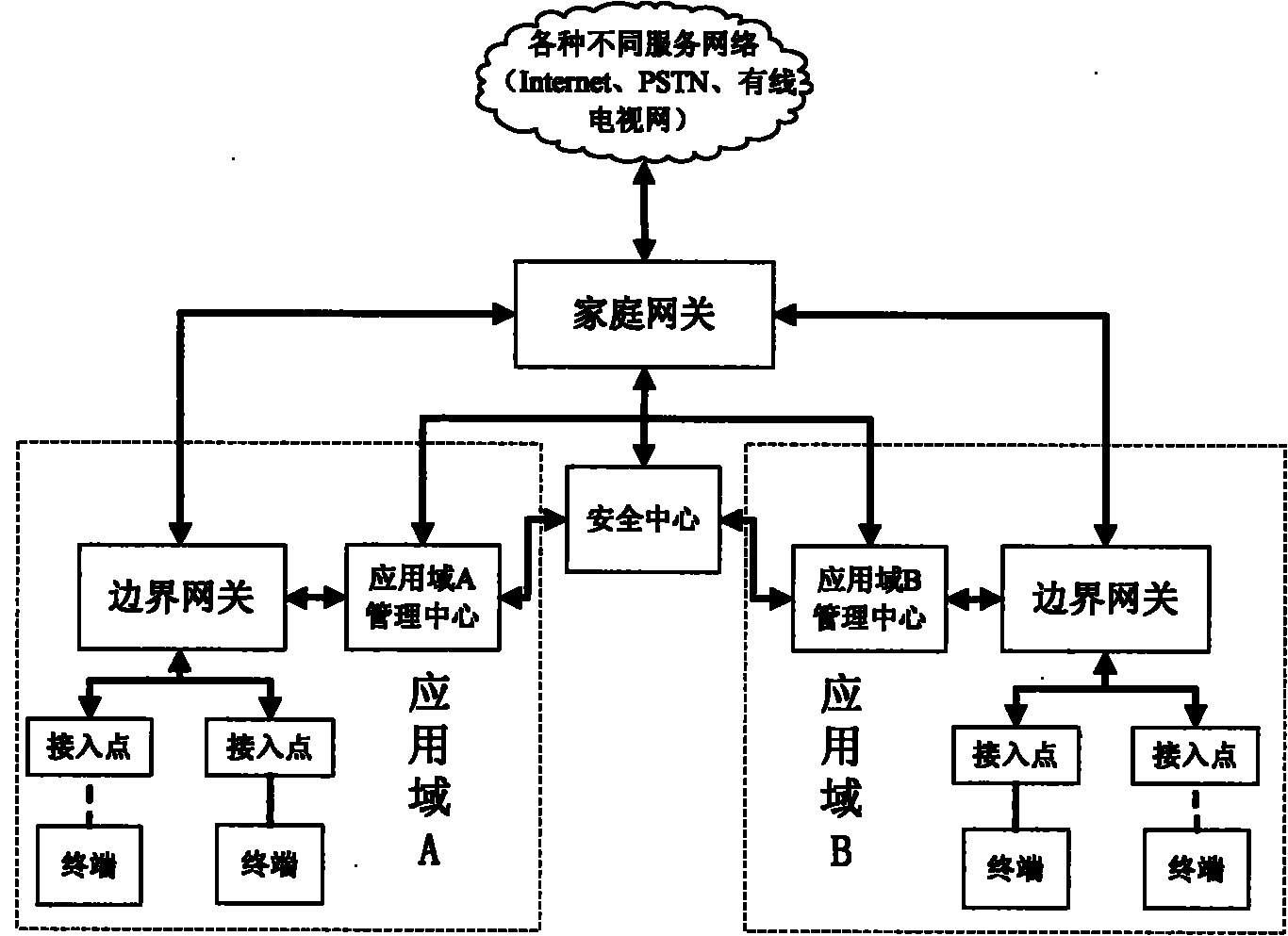
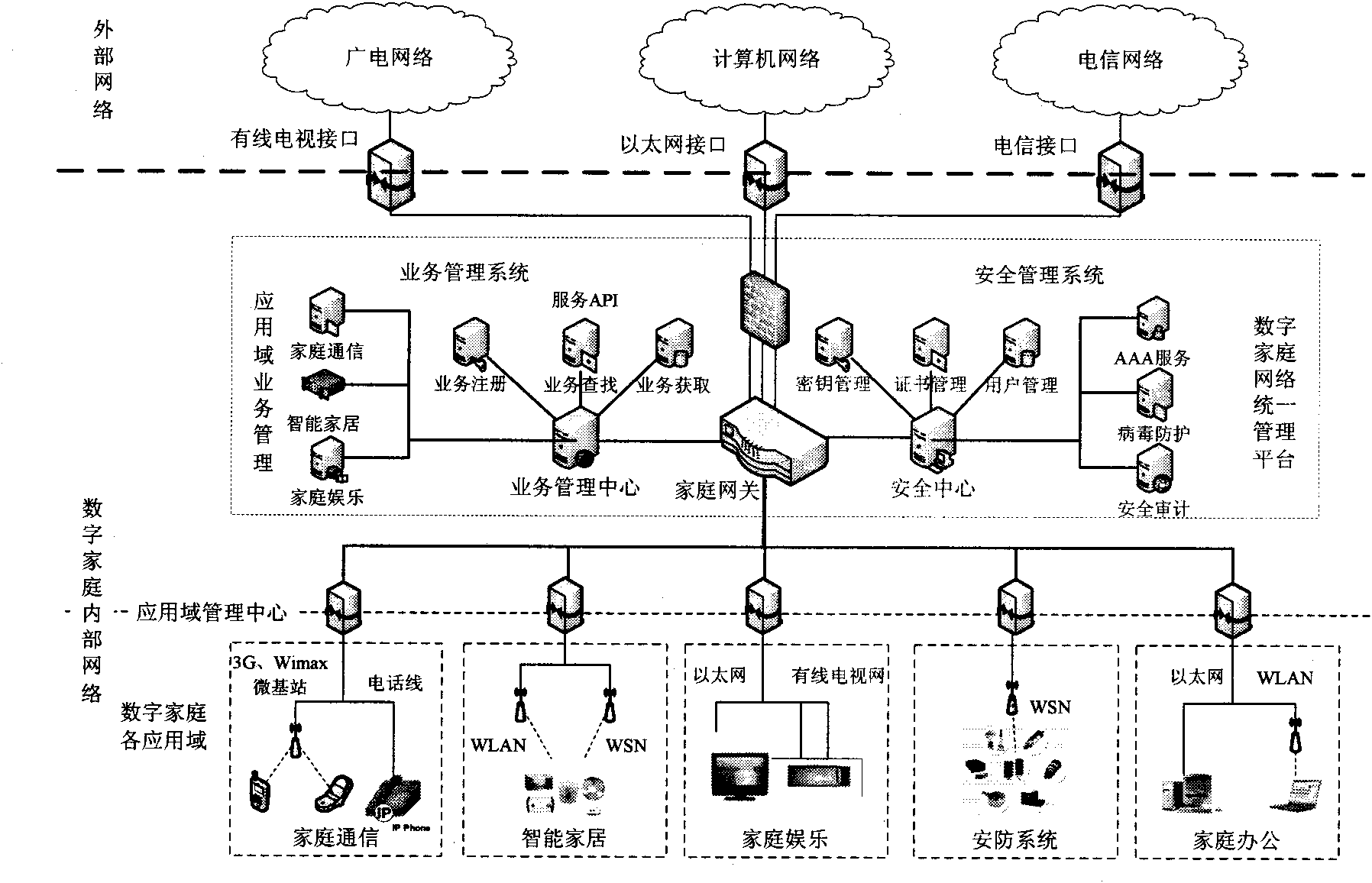
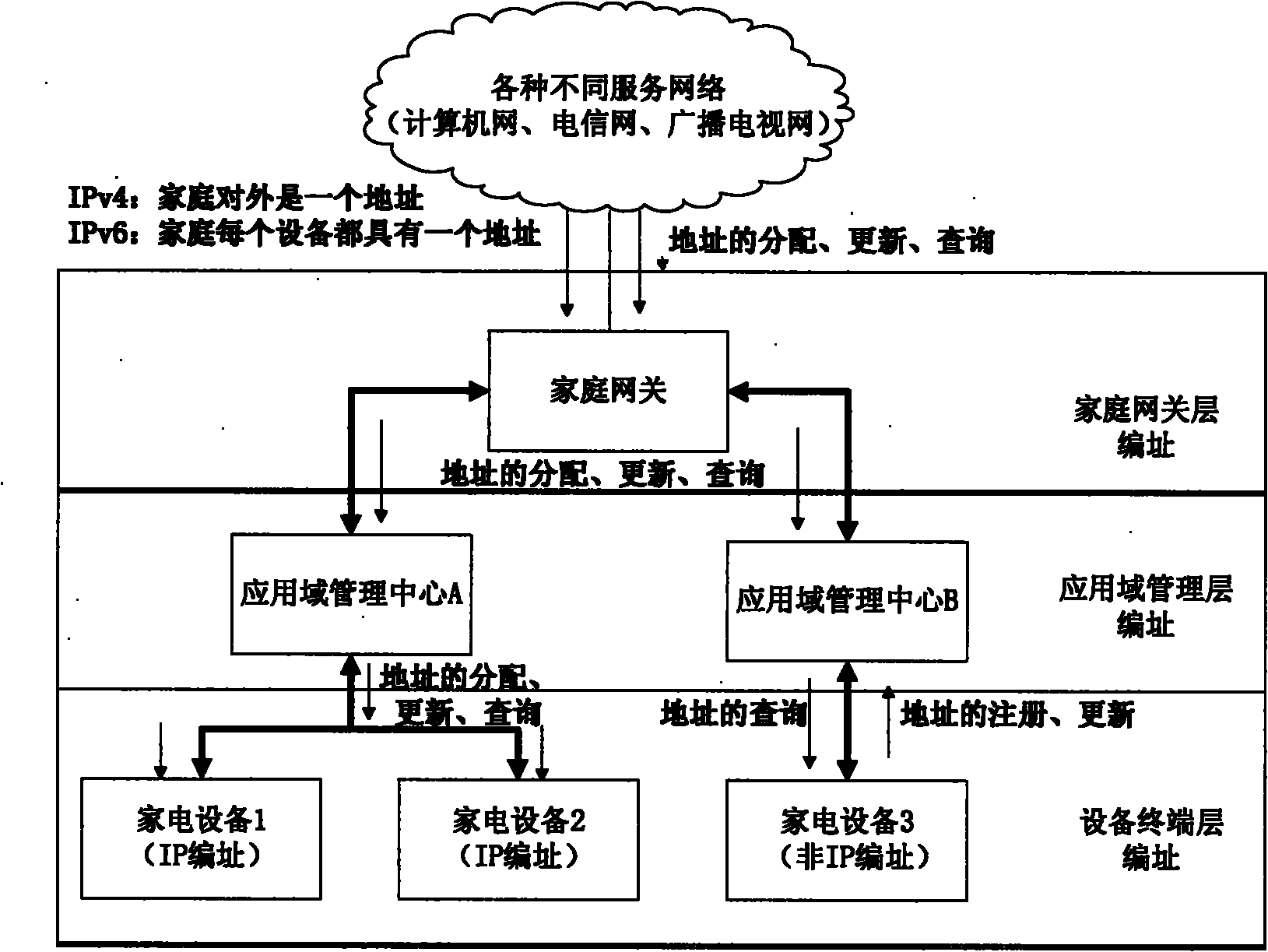
The invention discloses a three-network convergence oriented digital home network architecture. In the architecture, the network is partitioned into different application domains according to the digital home service requirements, information terminal devices with similar home services and similar function requirements are connected in the same application domain, and all terminal devices in the domain and services provided by the all terminal devices are managed by an application domain management center, thereby lightening the burden of a home gateway in managing specific services, and simultaneously being favorable for effective unified management of resources in the application domains. The digital home network architecture is composed of information terminal devices and intelligent home appliances, a network connection device, a digital home application domain management center and a home gateway. Based on the network architecture, the invention provides an addressing scheme and a communication method for a three-network convergence based digital home network architecture layering device, and realizes interconnection and intercommunication among digital home devices.
Owner:XIDIAN UNIV
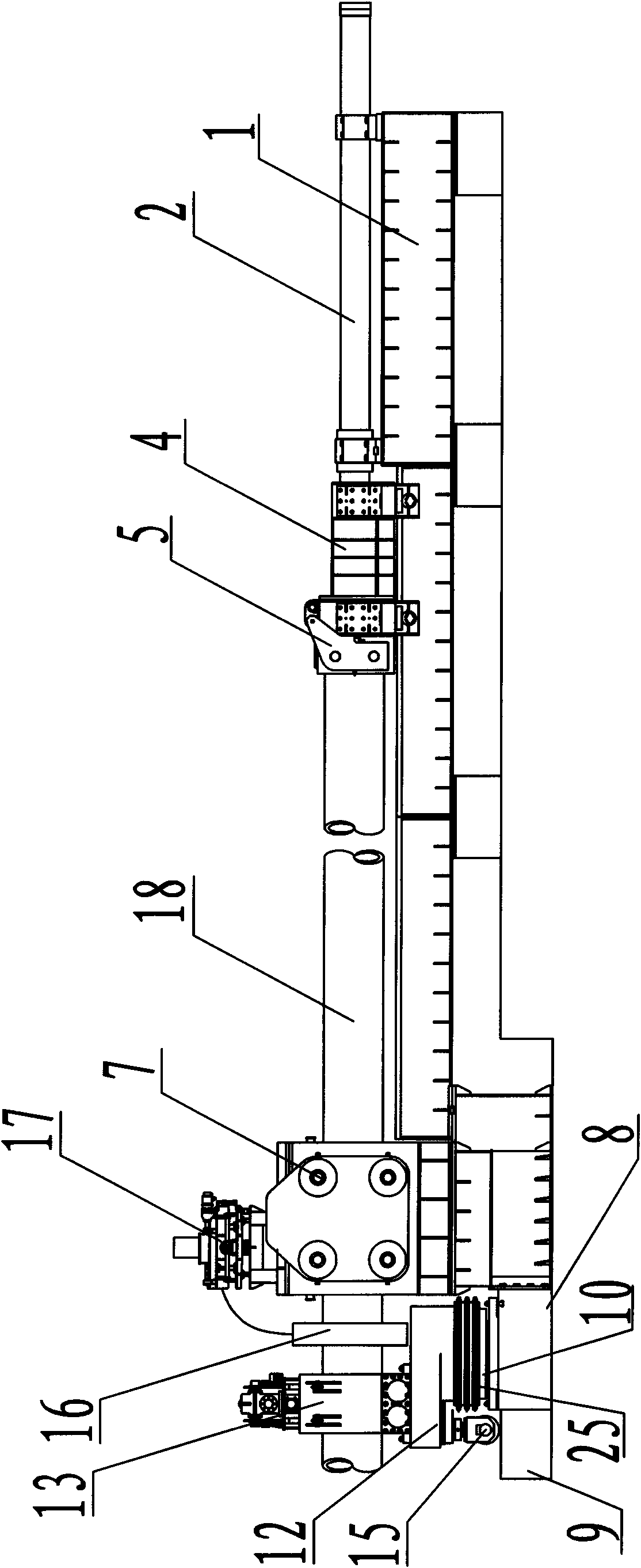
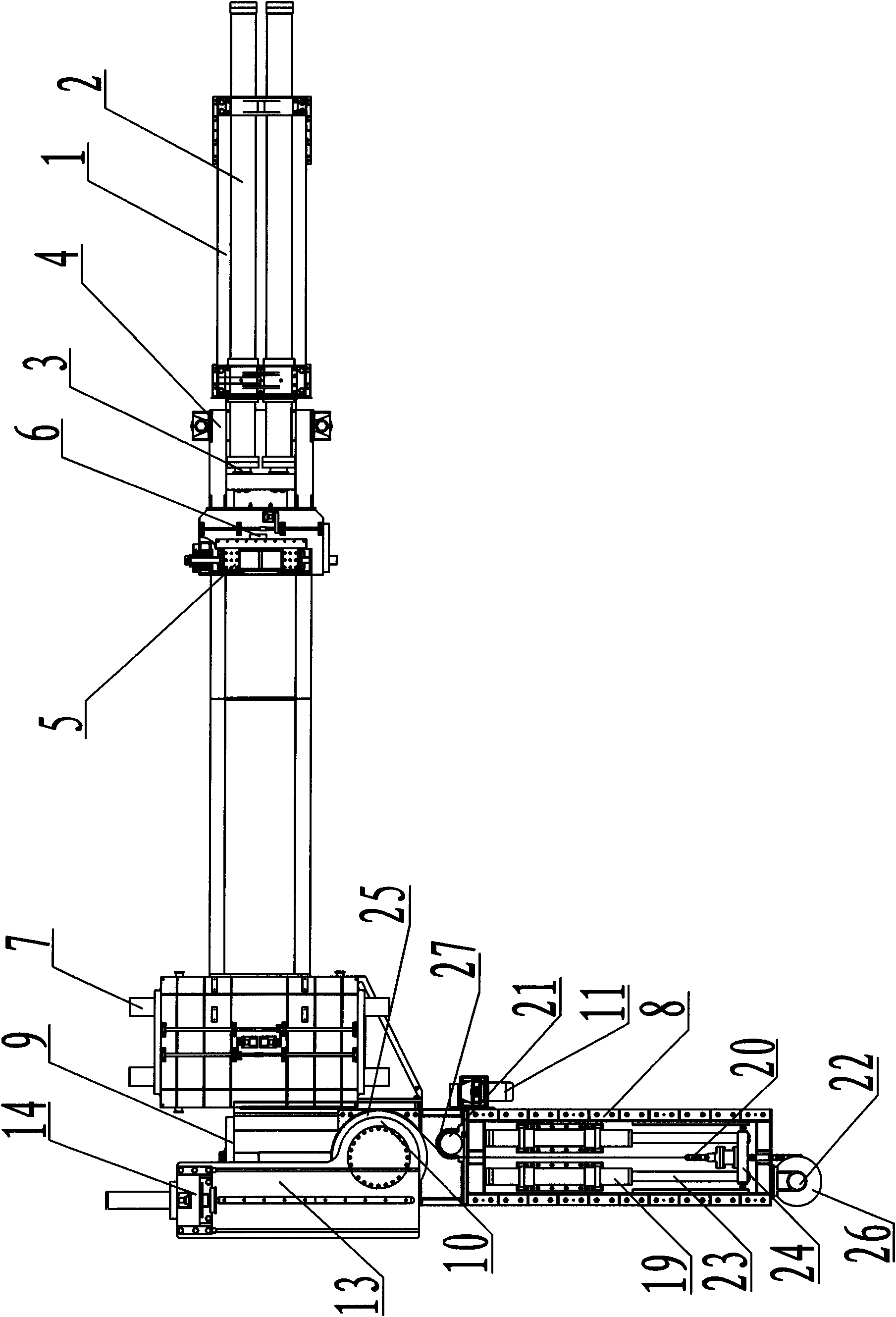
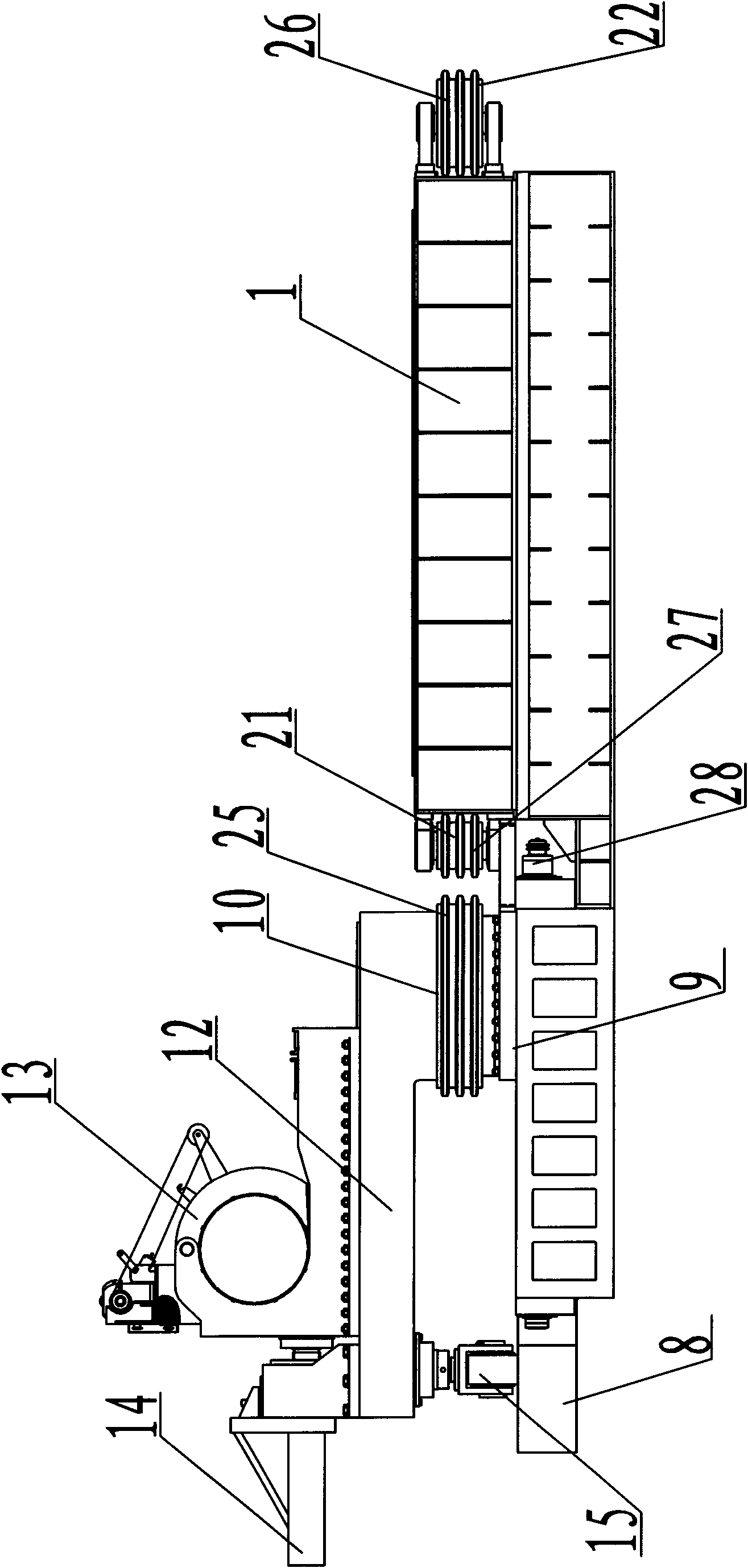
Large-diameter small-bending radius medium frequency pipe bender
InactiveCN101987331AControl the amount of outer wall thinningExtended service lifeMedium frequencyBend radius
The invention discloses a large-diameter small-bending radius medium frequency pipe bender. The pipe bender comprises a Iathe bed, wherein the back end of the Iathe bed is provided with a pushing cylinder; the piston rod of the pushing cylinder is connected with a back pusher; the front end of the Iathe bed is provided with a guide roller device and a travelling mechanism supporting base; a spindle mounting base is arranged on the travelling mechanism supporting base in a sliding manner; a spindle is arranged on the spindle mounting base in a rotating manner; the spindle is provided with a rotary arm; the rotary arm is provided with a front chuck and a front chuck adjusting device; the rotary arm is supported on the spindle mounting base through a support roller arranged on the lower end of the rotary arm; and the travelling mechanism supporting base is provided with an anti-bending-moment cylinder, and the anti-bending-moment cylinder is connected with the spindle through a transmission chain. The invention has the following advantages: the thickness reduction of the outer wall of the elbow can be effectively controlled; the large-diameter small-bending radius elbow can be directly prepared without performing secondary welding to the elbow; the manufacturing cost can be reduced, the service life of the elbow can be increased, and the burden for using the elbow of the enterprise can be reduced.
Owner:JIANGSU SUNCO BOILER
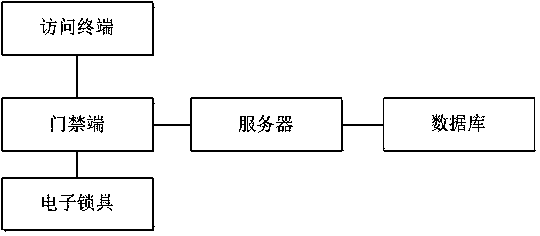
Two-dimensional code based access control system and door opening method
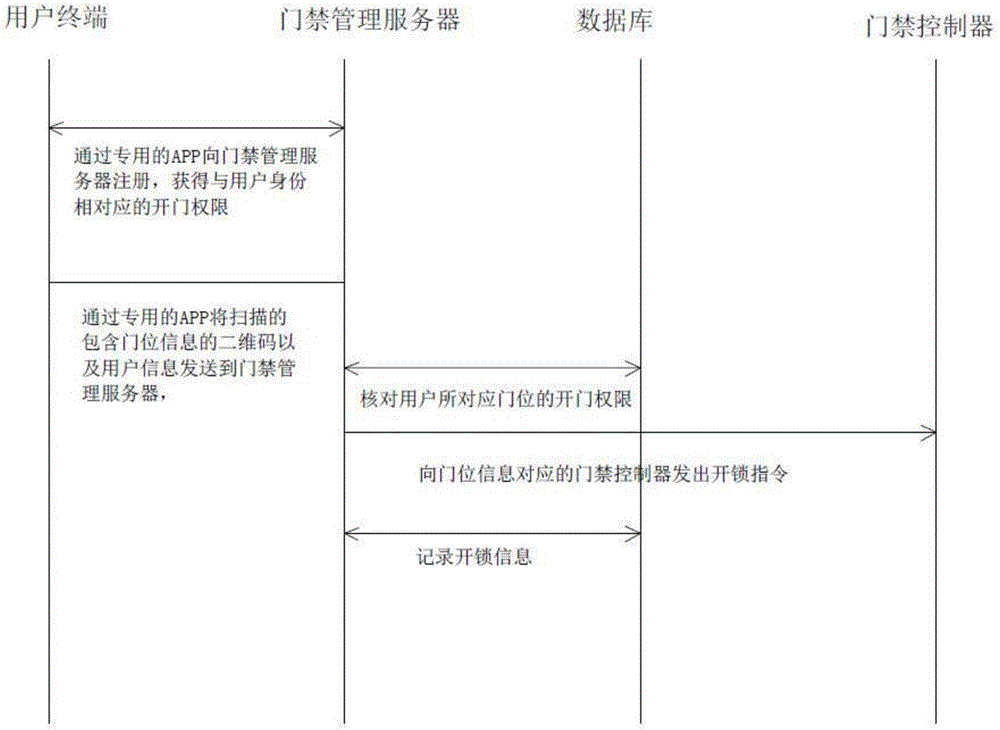
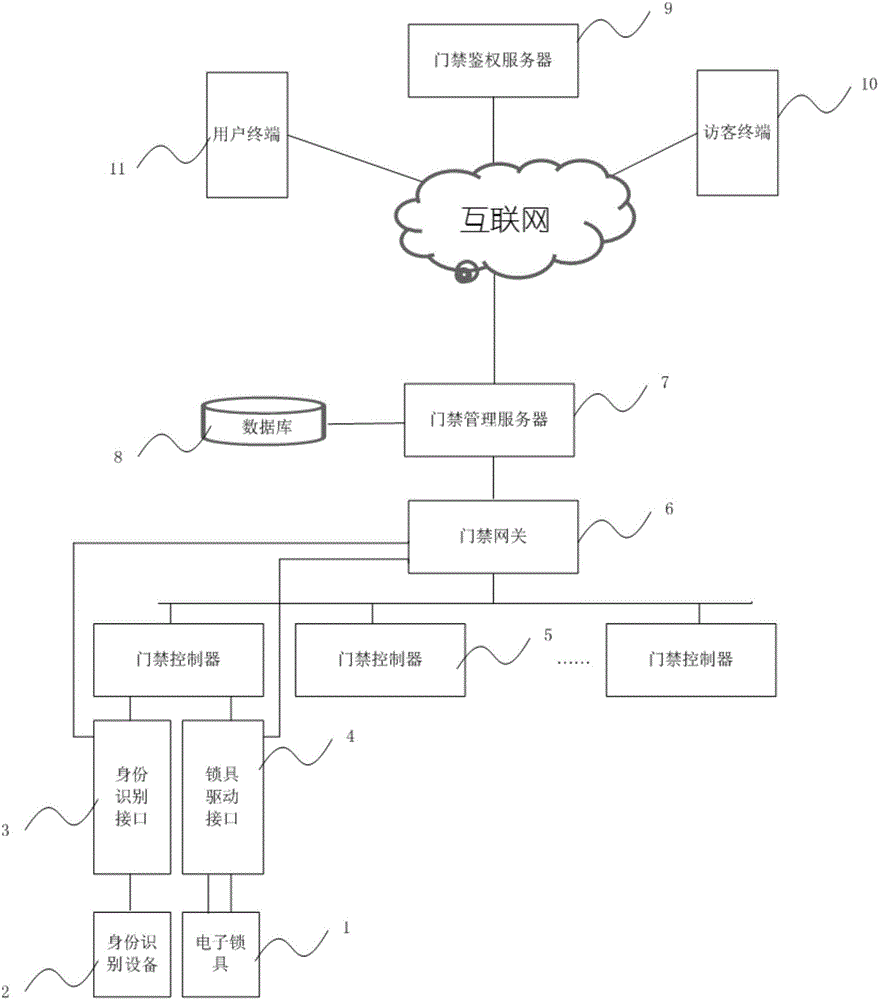
PendingCN106204866AEasy accessReduce the burden of useIndividual entry/exit registersDimensional modelingComputer terminal
The invention relates to a two-dimensional code based access control system and a door opening method. A scanned two-dimensional code containing door position encoding information and user information are sent to an access control management server through a special APP, and an unlocking instruction is sent to an access control controller corresponding to the door position encoding information after the access control management server checks the door opening permission information of a door position corresponding to a user. By the adoption of the two-dimensional code based access control system and the door opening method, the two-dimensional code containing door position encoding information and arranged nearby an access control is identified, the access control system can be simply, conveniently, quickly and comprehensively record in-out information of persons. A mobile terminal with a two-dimensional code which cannot be identified can be forbidden or alarmed, and the working amount of security personnel can be decreased while a community safety management effect can be effectively improved.
Owner:BEIJING UPVALUE INTPROP CONSULTANTSCO
Two-dimensional code based access control system and door opening method
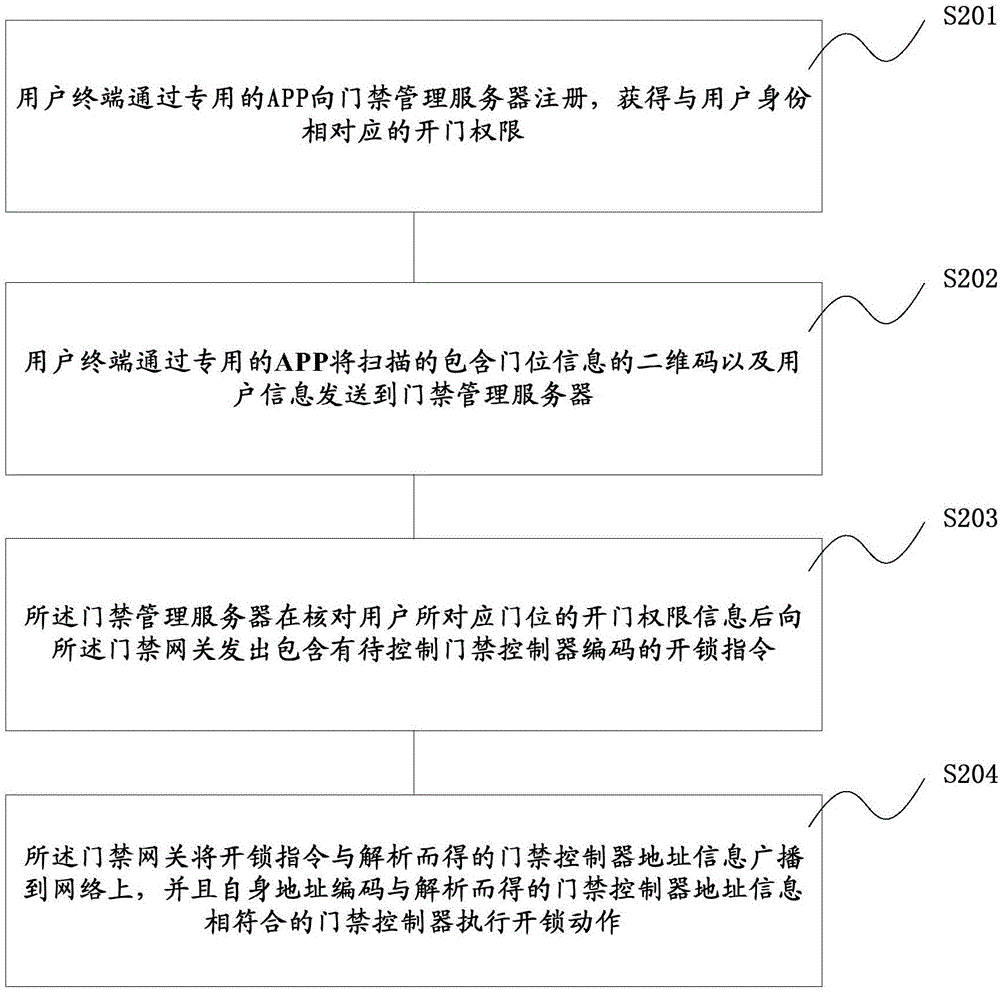
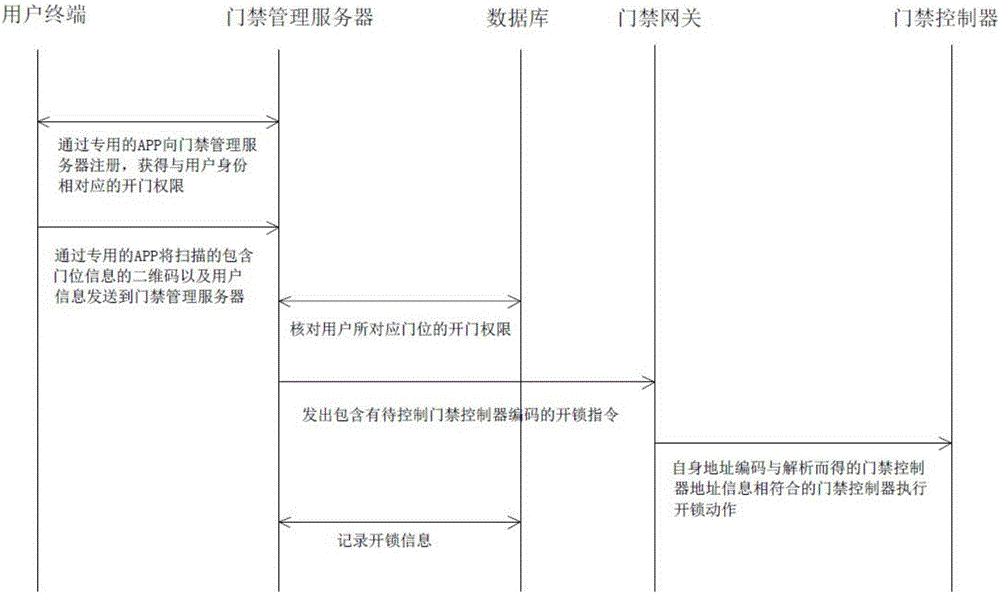
InactiveCN106327649AEasy accessReduce the burden of useIndividual entry/exit registersDimensional modelingComputer terminal
The invention relates to a two-dimensional code based access control system and a door opening method. The method includes: sending a scanned door position number information containing two-dimensional code and user information to an access control management server through a special APP, and sending a to-be-controlled access control controller code containing unlock instruction to an access control gateway after the access control management server checks door opening permission information of a door position corresponding to a user. The two-dimensional code based access control system and the door opening method have advantages that by recognition of the door position number information containing two-dimensional code close to access control, access information can be recorded by the access control system simply, conveniently and comprehensively; access forbidding or alarming can be realized if mobile terminals cannot be recognized by the two-dimensional code, and workload of security personnel can be relieved while community safety management effects are improved effectively.
Owner:BEIJING UPVALUE INTPROP CONSULTANTSCO
Sports standard reaching testing system and method
PendingCN108877889AReduce the burden of useReduce radiationPhysical therapies and activitiesData processing applicationsConfiguration designData information
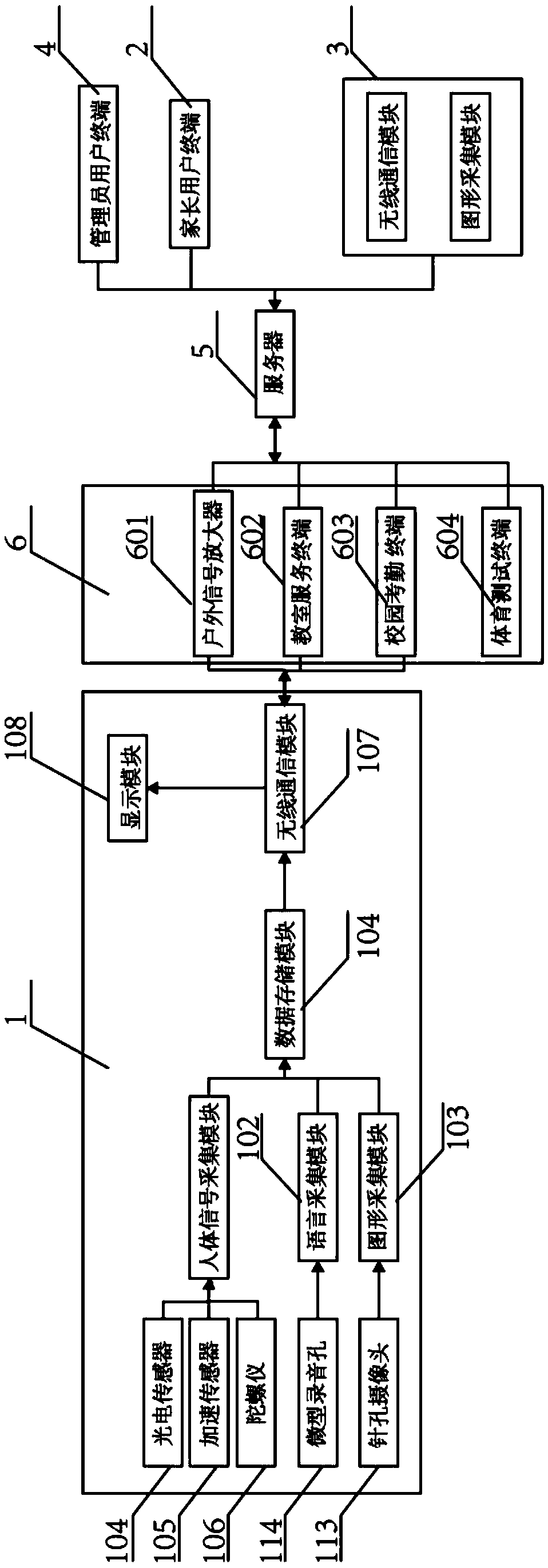
The invention discloses a sports standard reaching testing system and method, and the system comprises a user terminal, a signal collection terminal and a server. The user terminal comprises a studentuser terminal, a parent user terminal, a teacher user terminal, and a manager user terminal. The system is characterized in that the server is provided with a health file database; when a student enrolls in a school, a basic health file is built; the student user terminal is a wristband, and is worn by a student, and transmits the collected data to the server through the signal collection terminal; the parent user terminal and the teacher user terminal visit the server to obtain the student information correlated with their own; the manager user terminal manages all data information through the access to the server, and has the set authority for access to other user terminals; and the database transmits a copy of the data to the parent user terminal while transmitting the data to the student user terminal. The system module has the flexible configuration and combination capability, and the configuration design gives full consideration to the reliability and stability problems which may be caused by the outdoor, distributed and network environment factors.
Owner:北京华创互联科技股份有限公司
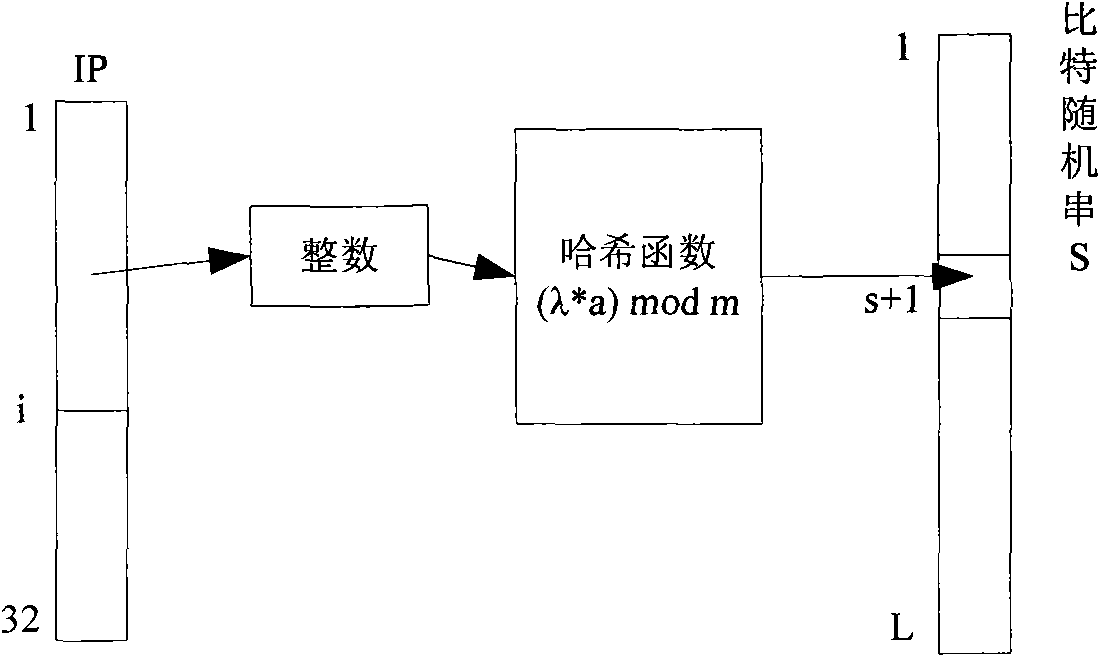
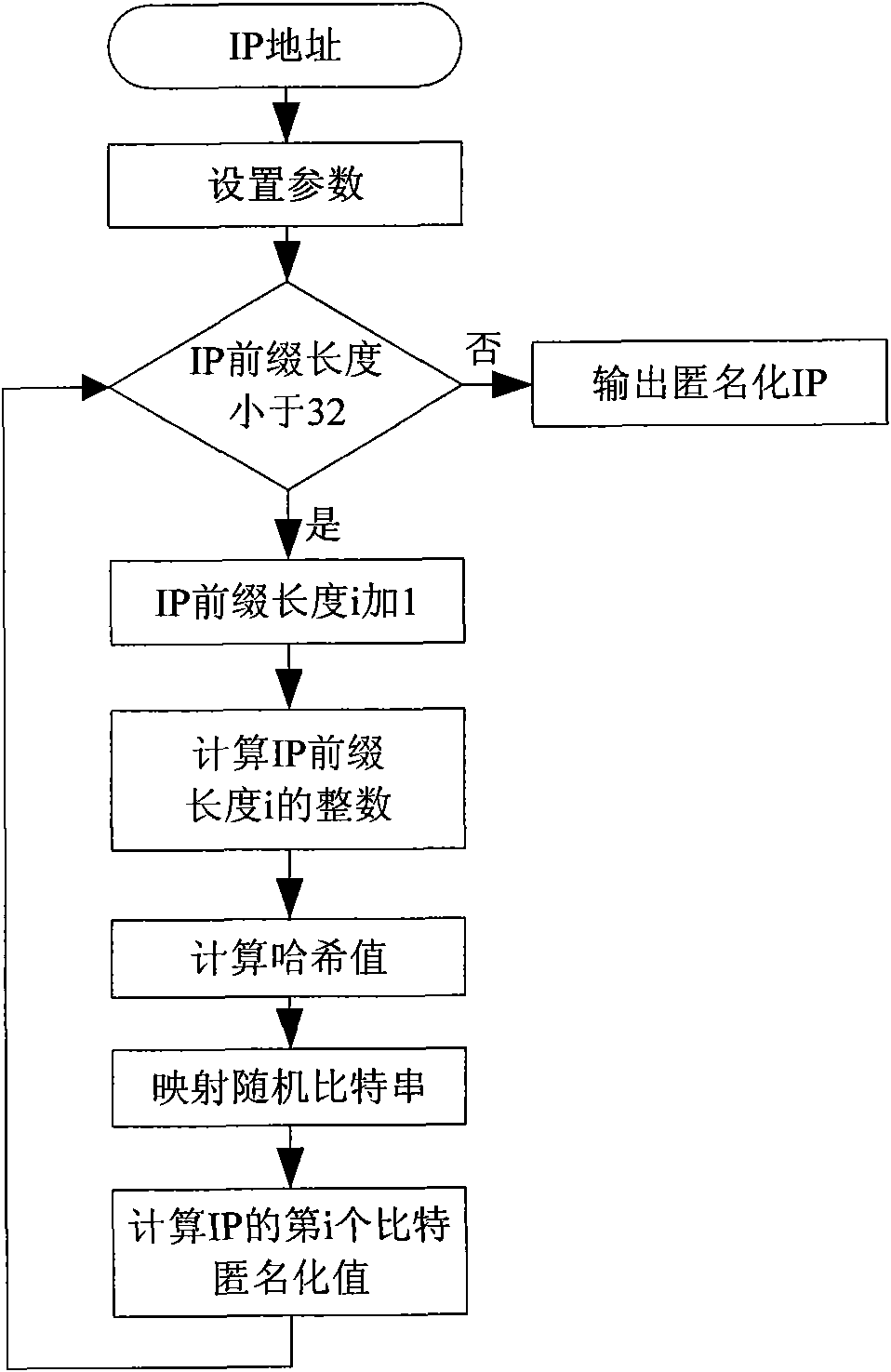
Anonymization method for reserving network address prefix combining bit string and hash function
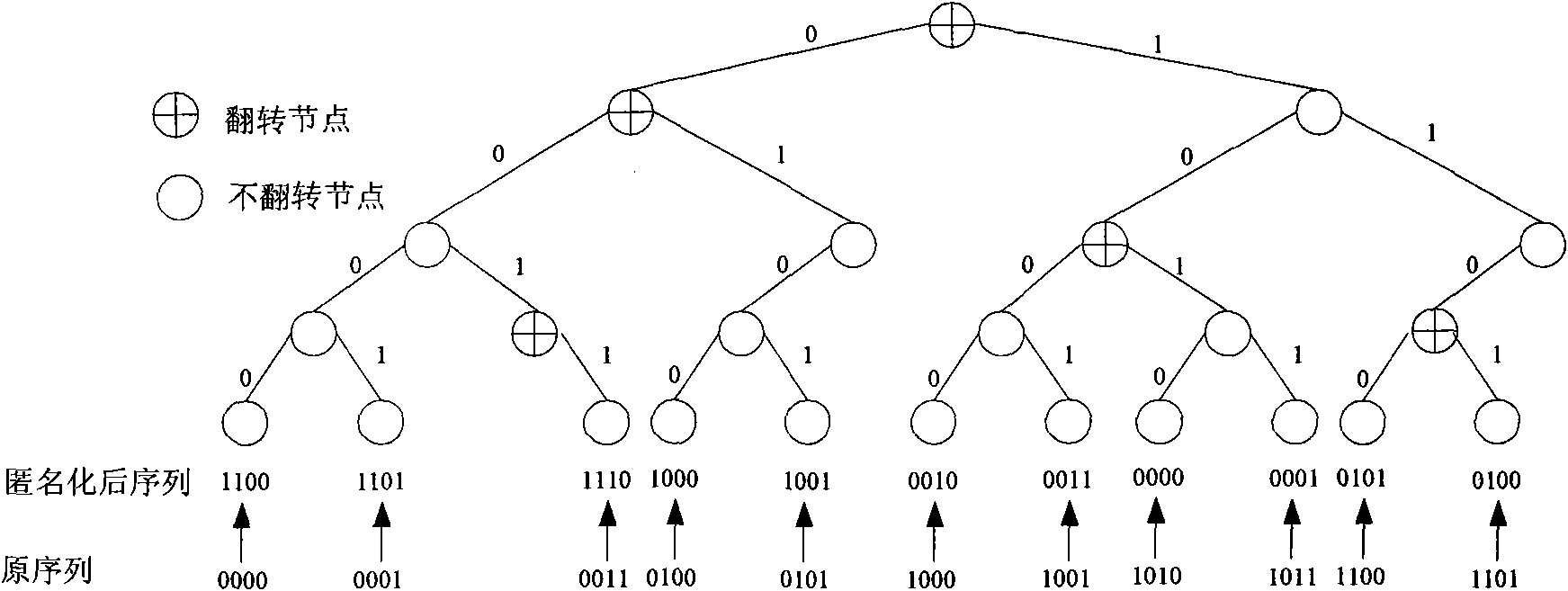
The invention discloses an anonymization method for reserving a network address prefix combining a bit string and the hash function. The anonymization method is characterized by defining an address prefix hash function which takes a decimal integer corresponding to an IP address prefix bit string as input and a random bit string, wherein the IP address prefix bit string with the length of i of the IP address prefixes is generated to a hash value by the address prefix hash function; then searching for a bit value on hash value position corresponding to the random bit string; carrying out XOR operation on the bit value and the number i bit of the IP address which needs to be anonymized; taking the result after the XOR operation as an anonymization bit of the number i bit of the IP address; and adopting the method for processing each bit of the IP address so as to realize anonymization processing to the entire IP address. The invention separates an encryption function and a mapping function, enhances the execution efficiency of the method when being compared with traditional methods, and reduces the memory space needed by the random bit string at the same time.
Owner:HAIAN CHANGDA TECH TRANSFER CENT +1
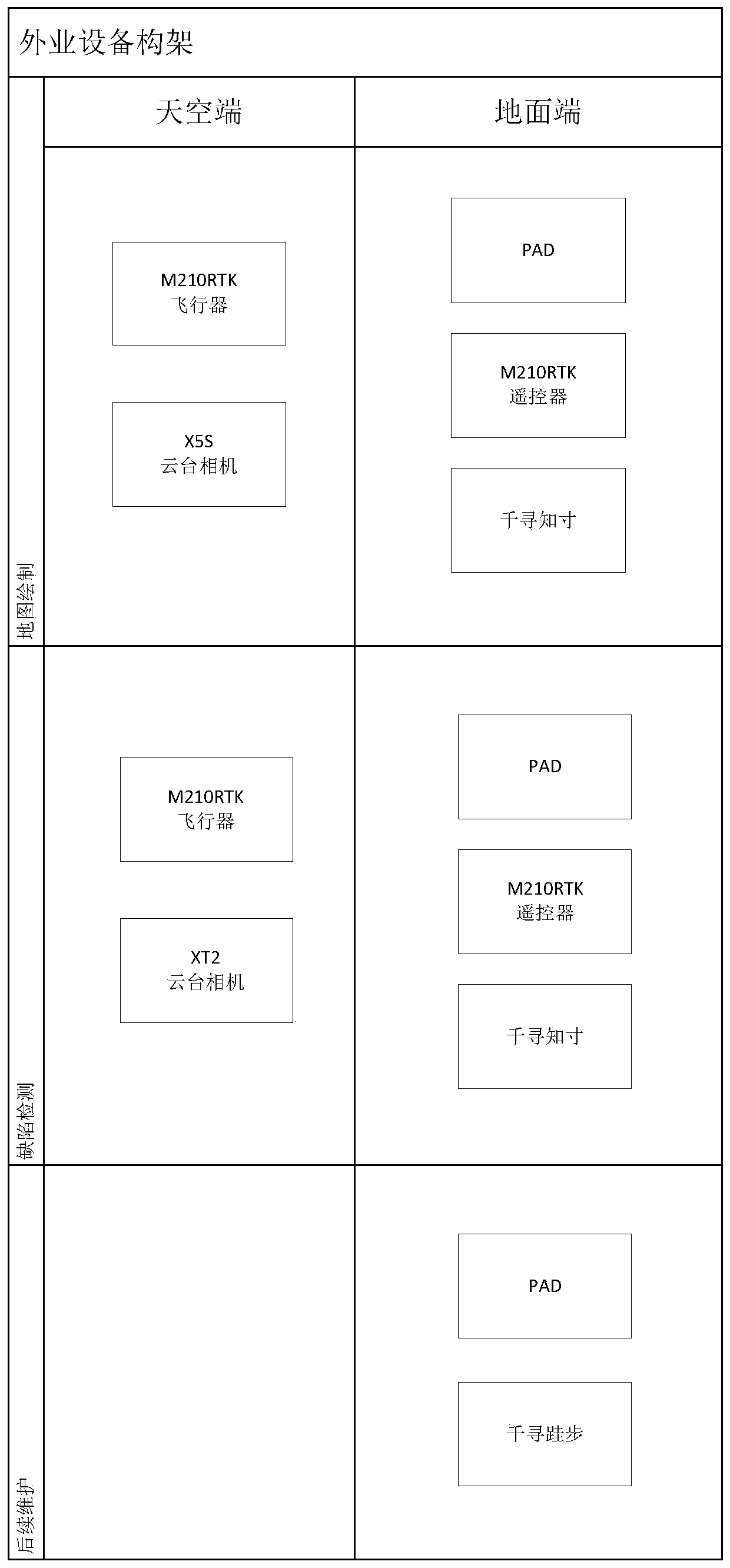
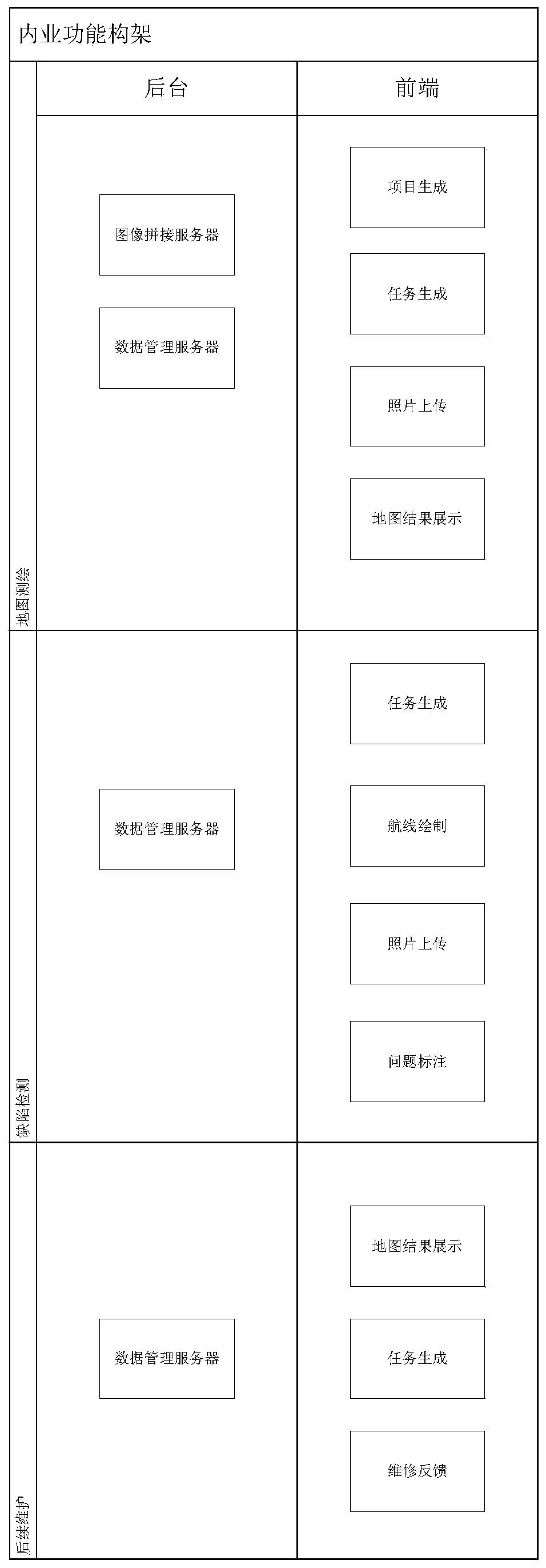
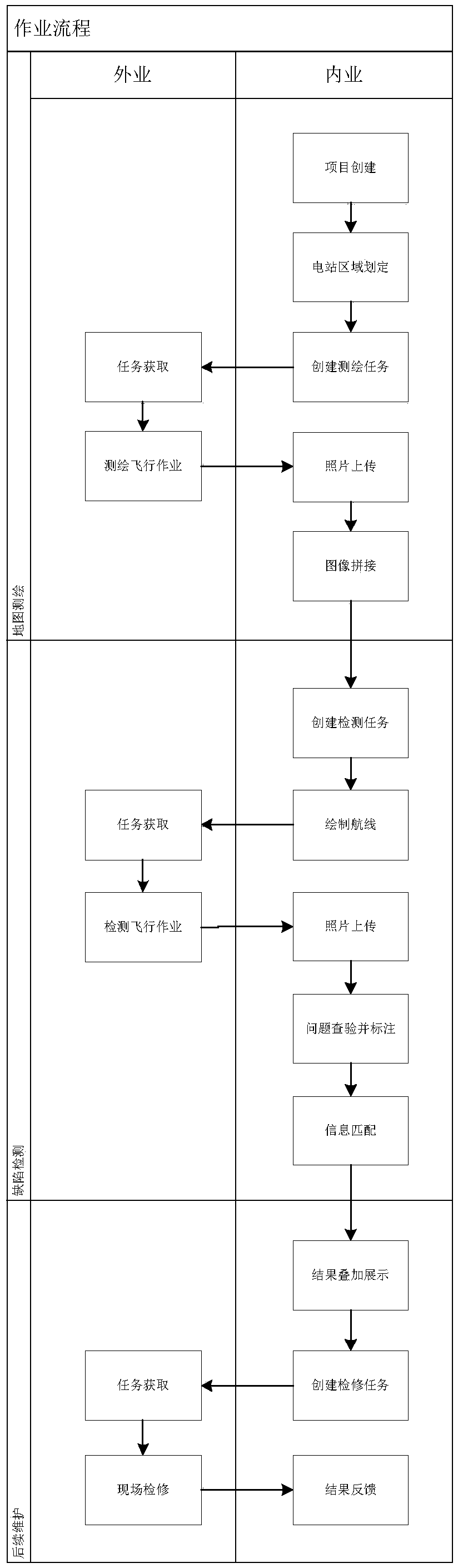
Centralized photovoltaic power station battery assembly defect inspection system based on multi-rotor drone
ActiveCN110470279AEnsure safetyReduce the burden of useRadiation pyrometryPhotovoltaic monitoringUncrewed vehiclePhotovoltaic power station
The invention discloses a centralized photovoltaic power station battery assembly defect inspection system based on a multi-rotor drone, which belongs to the technical field of centralized photovoltaic power station maintenance equipment. A four-rotor drone with RTK equipment is used to carry a high-definition camera for shooting. According to the photos, a high-definition map of the entire powerstation is stitched, an inspection route is drawn on the map and sent to the drone, the drone flies in accordance with the route and takes photos of the assembly, the shooting result is uploaded to abackstage, problems found by a detector in the shooting result can accurately correspond to the map, the whole detection process has a high automatic degree, the use burden of a user is low, all results are digitalized, traceable, and easy to view, the detector does not detect each assembly manually, the detection efficiency is greatly improved, the safety of the detector is ensured at the same time, the power station health condition can be intuitively presented for an owner, and cleaning or maintenance operations can be arranged in time.
Owner:SHANGHAI BOONRAY INTELLIGENT TECH CO LTD
Method and device of recommending network for mobile phone
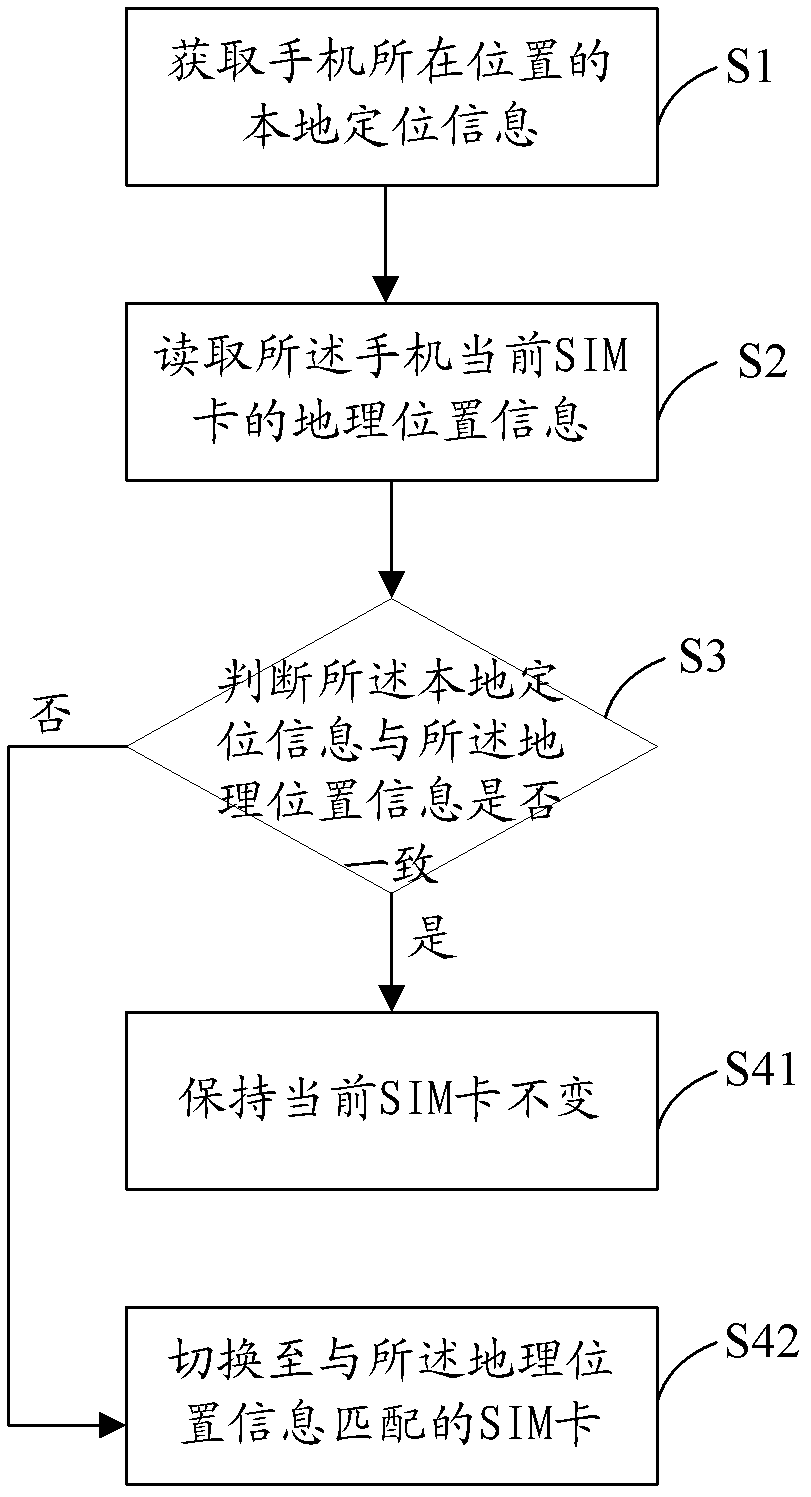
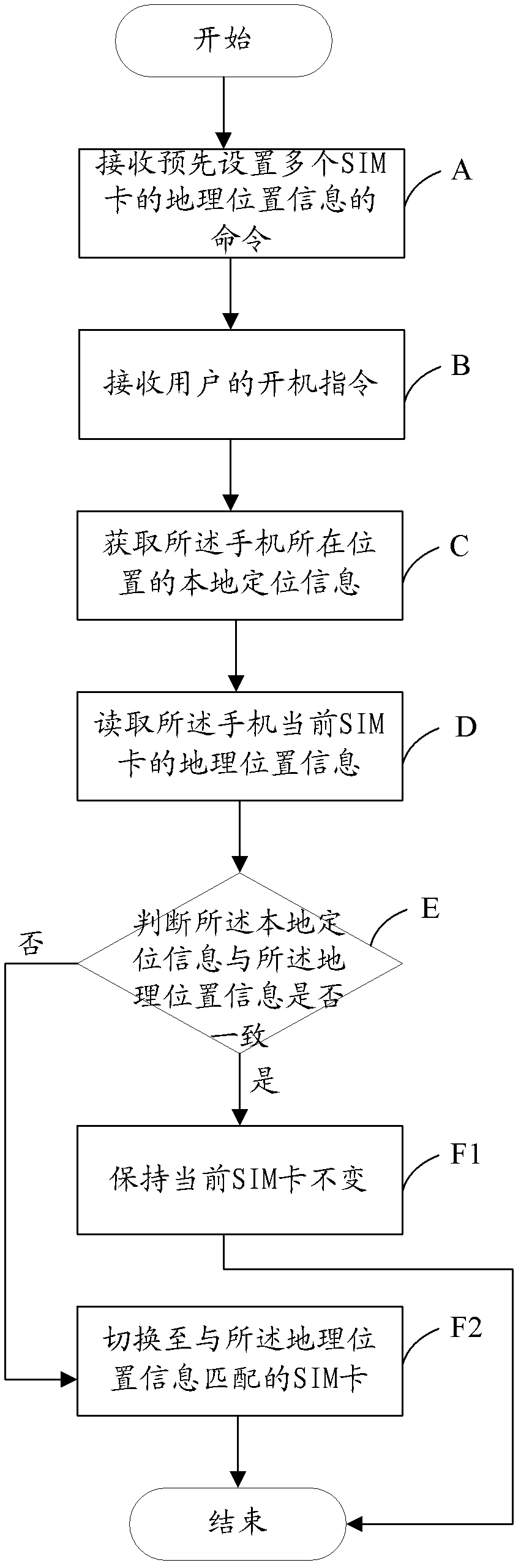
InactiveCN102448012AReduce the burden of useLocation information based serviceGeolocationSubscriber identity module
The invention discloses a method and device for recommending a network for a mobile phone. The mobile phone is internally provided with a plurality of SIM (Subscriber Identity Module) cards. The method comprises the following steps of: S1, obtaining local positioning information of the position of the mobile phone; S2, reading geographic position information of the current SIM card of the mobile phone; S3, judging whether the local positioning information is identical to the geographic position information or not; if so, executing the step S41; otherwise, executing the step S42; S41, keeping the current SIM card unchanged and finishing the step; and S42, switching to a SIM card which is matched with the geographic position information. According to the method, by judging whether the local positioning information of the position of the mobile phone is identical to the geographic position information of the current SIM card, the SIM card which is matched with the geographic position information is found; the technical scheme provided by the invention can be used for helping a user to judge the local SIM card of the current position, so that the use load of the user is reduced.
Owner:SHENZHEN SANG FEI CONSUMER COMM CO LTD
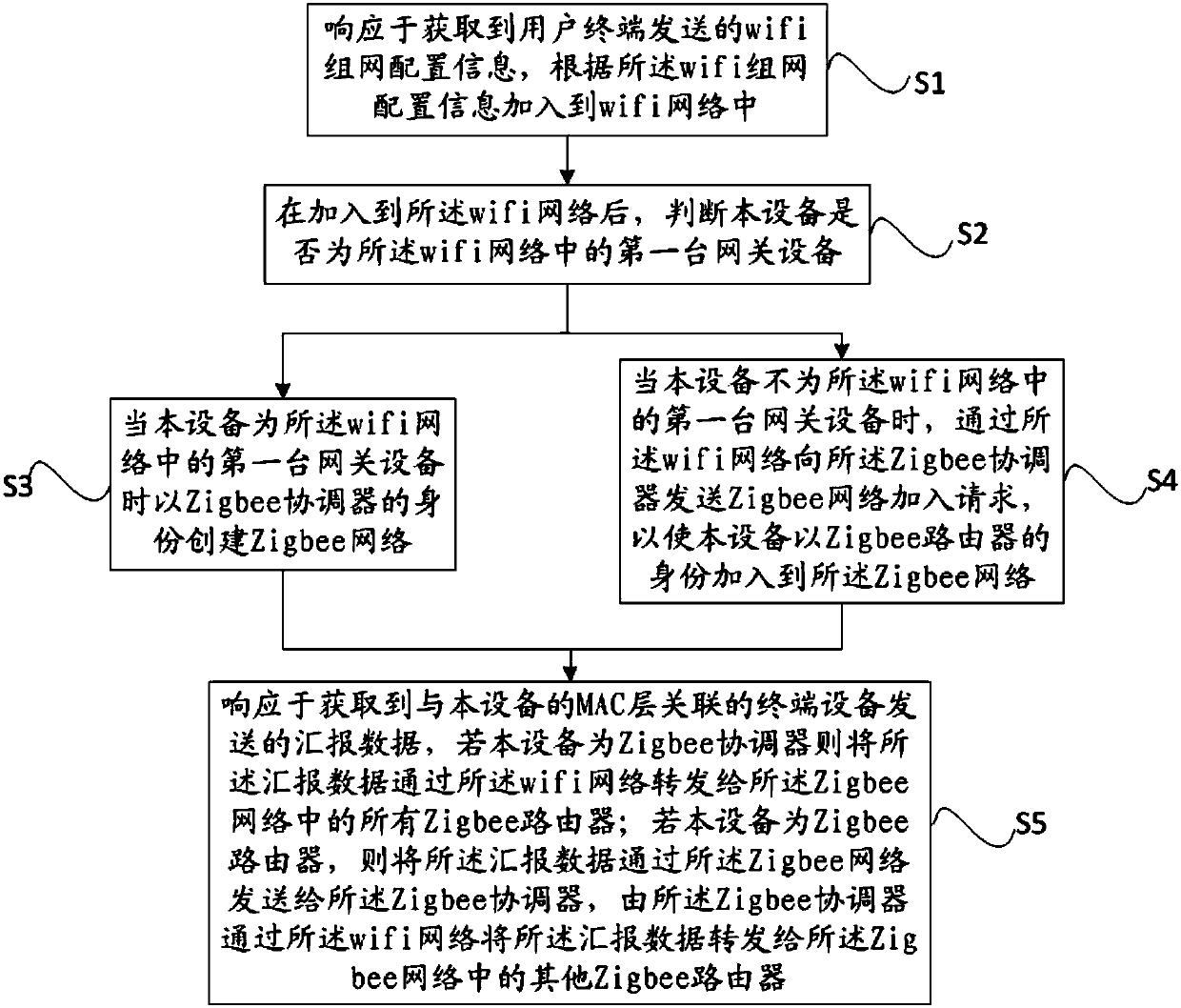
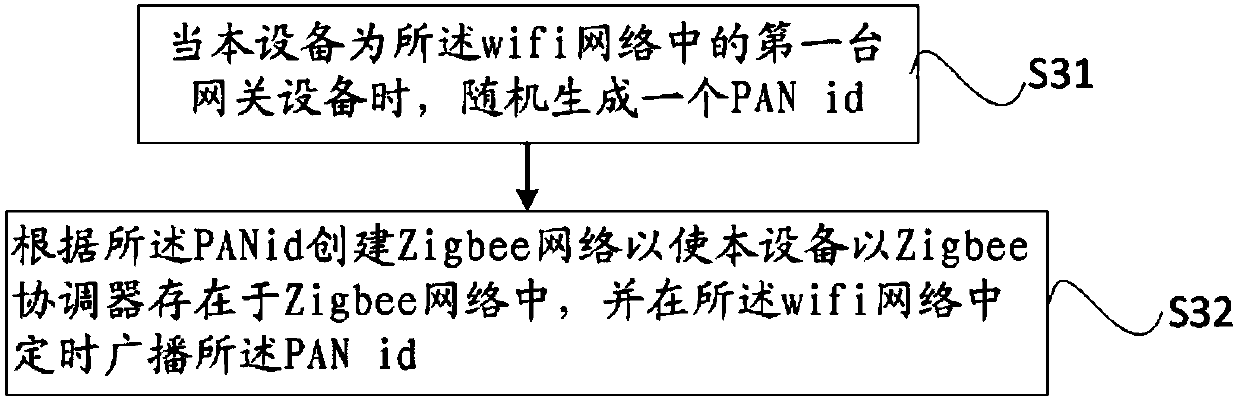
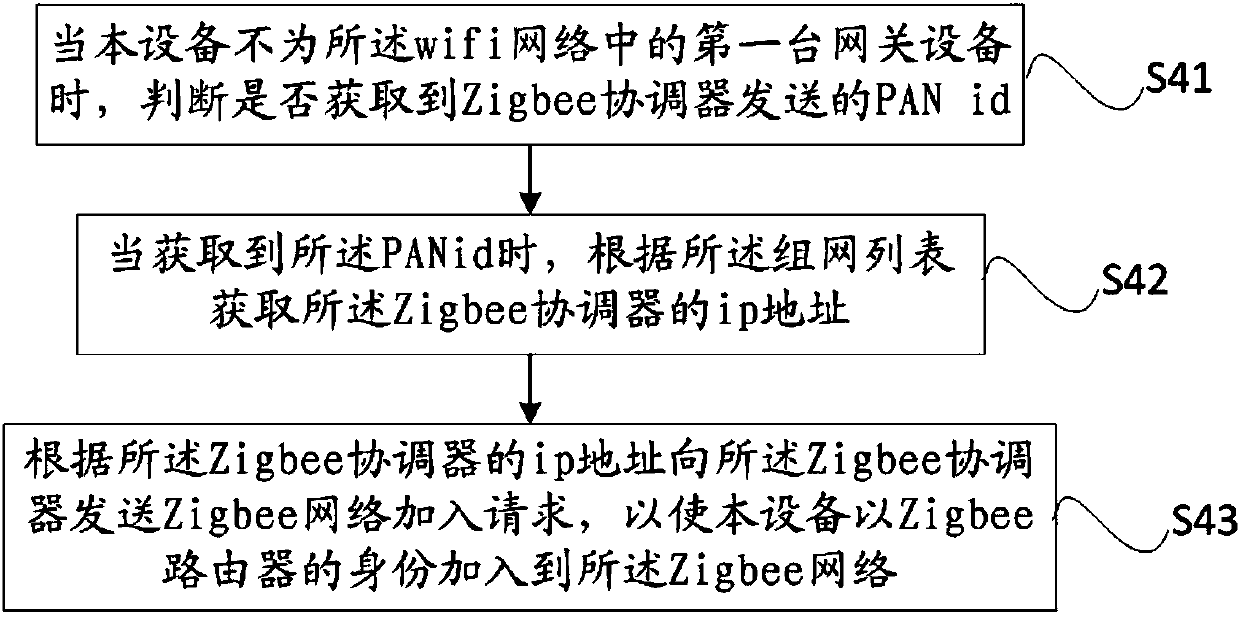
Data sharing method of Zigbee network, gateway equipment and Zigbee network system
InactiveCN107682857AReduce the burden of useAssess restrictionNetwork topologiesWifi networkTerminal equipment
The invention provides a data sharing method of a Zigbee network, gateway equipment and a Zigbee network system. A wifi network is used to make each piece of gateway equipment form a same Zigbee network. If the equipment is a Zigbee coordinator, reported data is forwarded to all Zigbee routers in the Zigbee network through the wifi network. If the equipment is the Zigbee router, the reported datais sent to the Zigbee coordinator through the Zigbee network, and the Zigbee coordinator forwards the reported data to the other Zigbee routers in the Zigbee network through the wifi network so that the Zigbee coordinator and the Zigbee routers in the Zigbee network can share data. Through the data sharing method of the Zigbee network provided in the invention, a user can acquire the reported dataof all terminal equipment through selecting any one piece of gateway equipment. For the user, a whole household network is an integral body, and the user does not need to care which terminal equipment is associated with which gateway equipment so that a usage burden of the user is reduced.
Owner:TP-LINK
Electric vehicle power battery cooling device
PendingCN108539324AAvoid damageExtended service lifeBattery isolationSecondary cellsPower batteryHeat conducting
The invention discloses an electric vehicle power battery cooling device. The device comprises a mounting plate and an air blower and a battery storage box which are arranged on the mounting plate, wherein the air blower is connected with an air inlet in the upper portion of one side of the battery storage box through an air guiding tube, and an air outlet pipe is arranged at the bottom of the other side of the battery storage box; a water tank is arranged at one side of the battery storage box, a cavity of the water tank is filled with cooling water, one end of the water tank is fixedly connected with the battery storage box, the other end of the water tank is provided with a semiconductor refrigeration sheet and a cooling fan which are used for reducing the temperature of the cooling water in the water tank; a heat conducting rod is arranged in the water tank, the end portion of the heat conducting rod penetrates through the water tank and the sidewall of the air guiding tube and extends into the air guiding tube, and a set of symmetrical meshy heat conducting sheets are arranged at the end portion of the heat conducting rod.
Owner:SHANGHAI DIANJI UNIV
Filtering device capable of achieving automatic cleaning and clothing treating equipment
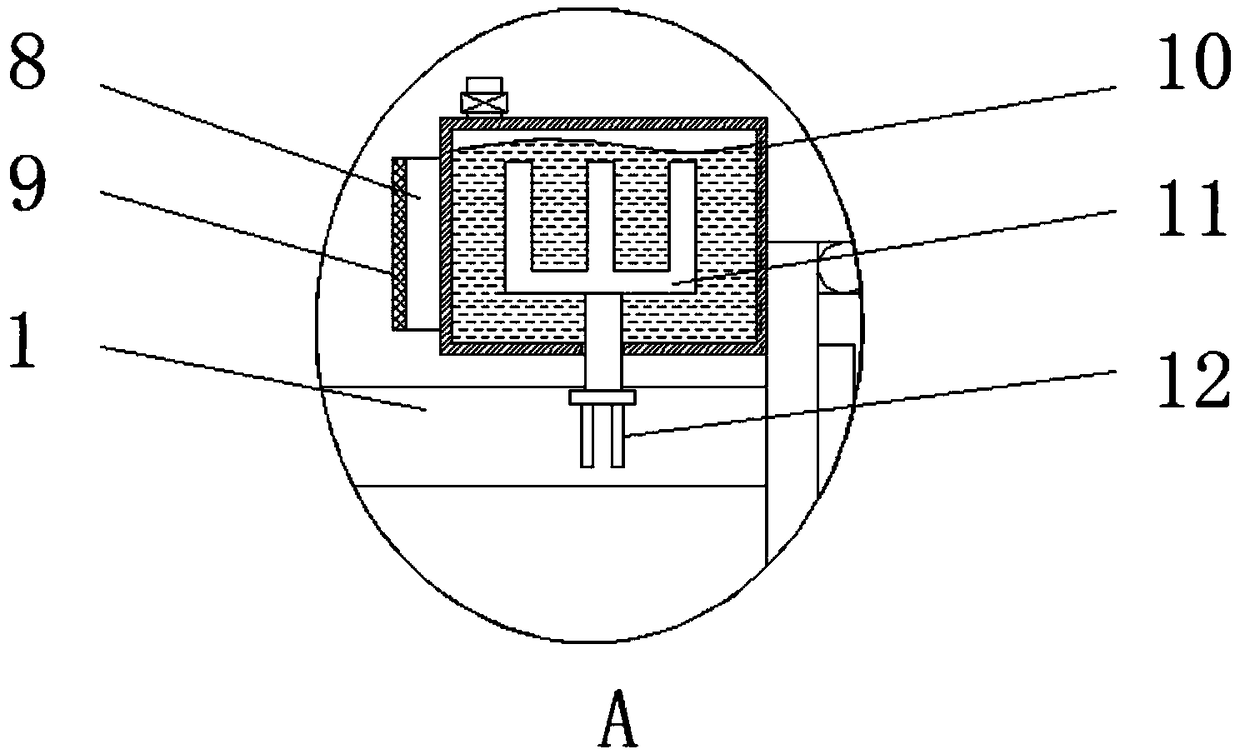
ActiveCN109750471AReduce the burden of useAvoid lint cloggingTextiles and paperCleaning using liquidsScrapWaste management
Owner:QINGDAO HAIER WASHING ELECTRIC APPLIANCES CO LTD +1
One-object one-code commodity anti-counterfeiting and tracing system based on digital watermark two-dimensional code
PendingCN109754037ANo increase in anti-counterfeiting costsRobustCo-operative working arrangementsComputer generationDigital watermarking
The invention discloses a one-object one-code commodity anti-counterfeiting and tracing system based on a digital watermark two-dimensional code. The system comprises a small commodity anti-counterfeiting and tracing system based on a digital watermark two-dimensional code and a tracing and checking WeChat program, a WeChat official account based on the digital watermark two-dimensional code and the tracing and checking WeChat program, and an application program based on the digital watermark two-dimensional code and the mobile phone tracing and checking program. Aiming at the problem that a general two-dimensional code technology cannot distinguish information authenticity and prevent counterfeiting, on the basis that a server computer generates a standard two-dimensional code, a productcode with one object one code is used as digital watermark information to be hidden in the two-dimensional code to generate an anti-counterfeiting label. Consumers purchase commodities, using a sourcetracing and checking WeChat applet or a source tracing and checking WeChat official account or a mobile phone terminal source tracing and checking application program to carry out digital watermark identification and reading on the two-dimensional code on the anti-counterfeit label. Traceability checking is carried out according to the existence of digital watermark information (product codes), the anti-counterfeiting traceability capability of the two-dimensional code is improved, and the double effects of effective counterfeiting prevention, tamper prevention and accurate tracking are achieved.
Owner:CHENGDU YUFEI INFORMATION ENG
Base station, cleaning robot system and method for cleaning cleaning robot
PendingCN111134582ARealize automatic cleaningReduce the burden of useCarpet cleanersFloor cleanersRobotic systemsEngineering
The invention discloses a base station, a cleaning robot system and a method for cleaning a cleaning robot. The base station comprises a base station body and a cleaning device arranged on the base station body, the base station body is configured to allow the cleaning robot to move on the base station body in the front-back direction, and the cleaning device is configured to clean different partsof the base station body along a mopping and wiping piece by means of the movement of the cleaning robot in the front-back direction on the base station body. The cleaning robot moves on the base station in the front-back direction, so that the cleaning device of the base station can relatively move along the mopping and wiping piece, and then the purpose of cleaning different parts of the mopping and wiping piece is achieved; therefore, automatic cleaning of the mopping and wiping pieces of various types can be achieved, the cleaning device is particularly suitable for traditional mopping and wiping pieces attached to a robot shell, the use burden of a user is relieved, and the use experience of the user is improved.
Owner:YUNJING INTELLIGENCE TECH (DONGGUAN) CO LTD
Chinese character input methods and terminals
InactiveCN103092362AFast inputSimple inputInput/output processes for data processingChinese charactersVirtual keyboard
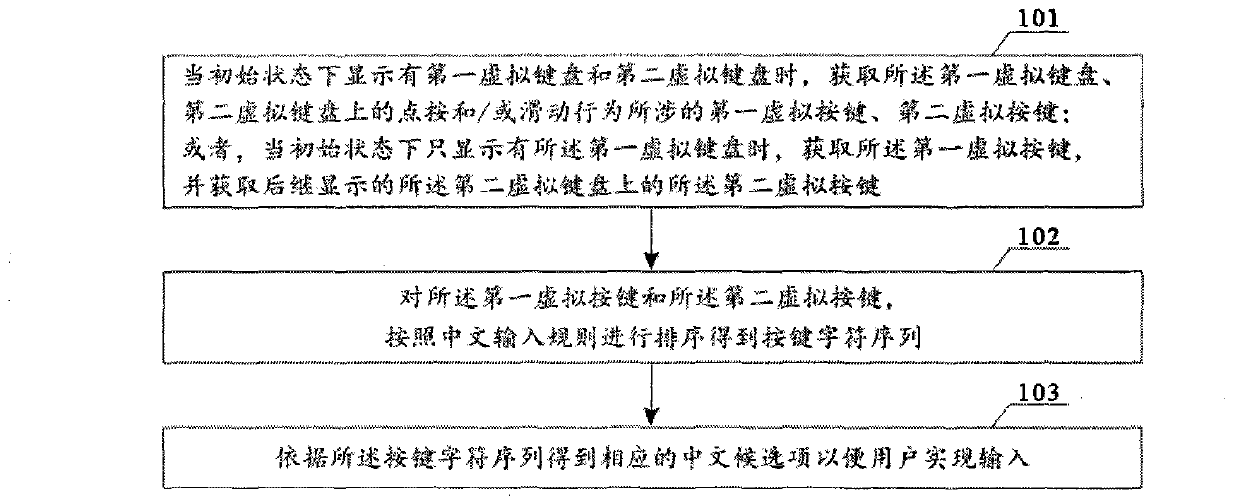
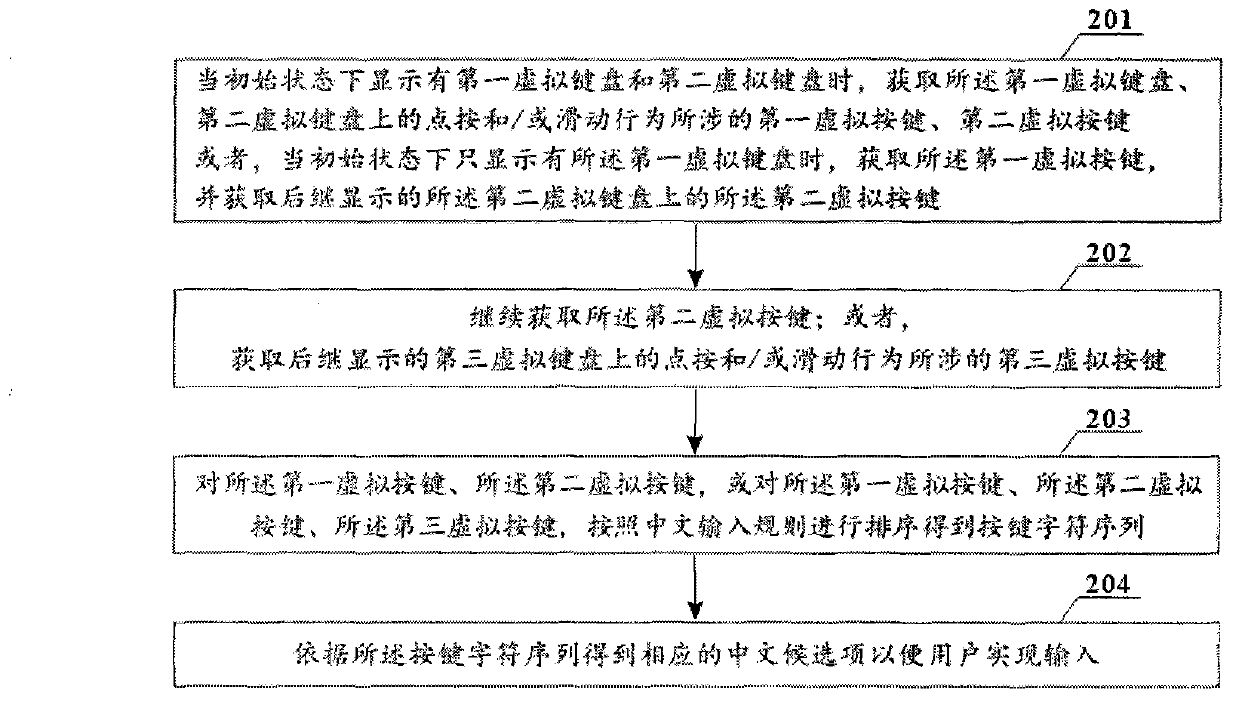
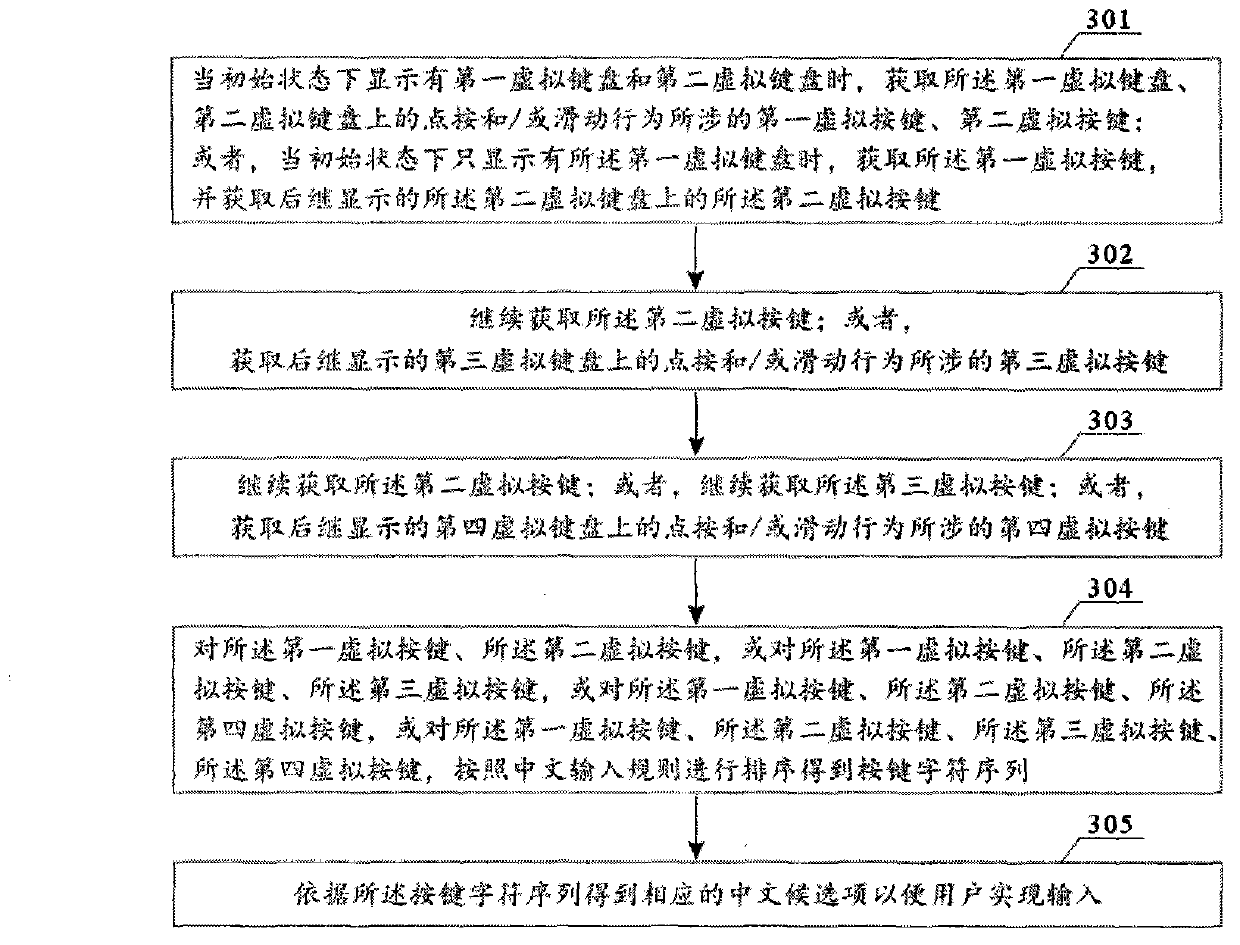
The invention provides a Chinese character input method. According to the Chinese character input method, first and second virtual keys related to point-clicking and / or sliding behaviors on first and second virtual keyboards are acquired to form a key character sequence, so that Chinese characters are input in point-clicking and / or sliding ways. The invention also provides other two Chinese character input methods, three Chinese character input terminals, three virtual keyboard display methods and a virtual keyboard layout. Trajectories of point-clicking and / or sliding the same finals are relatively fixed, so that a user can naturally know the position(s) of the next one or more virtual keys after point-clicking and / or sliding the virtual keys on the first virtual keyboard without looking for the virtual keys everywhere to quickly finish the operation of point-clicking and / or sliding input of the Chinese characters. Difficulty in the use of the user is lowered, input speed is increased, and input efficiency is improved.
Owner:王道平
Data security controlling system and implementation method of system
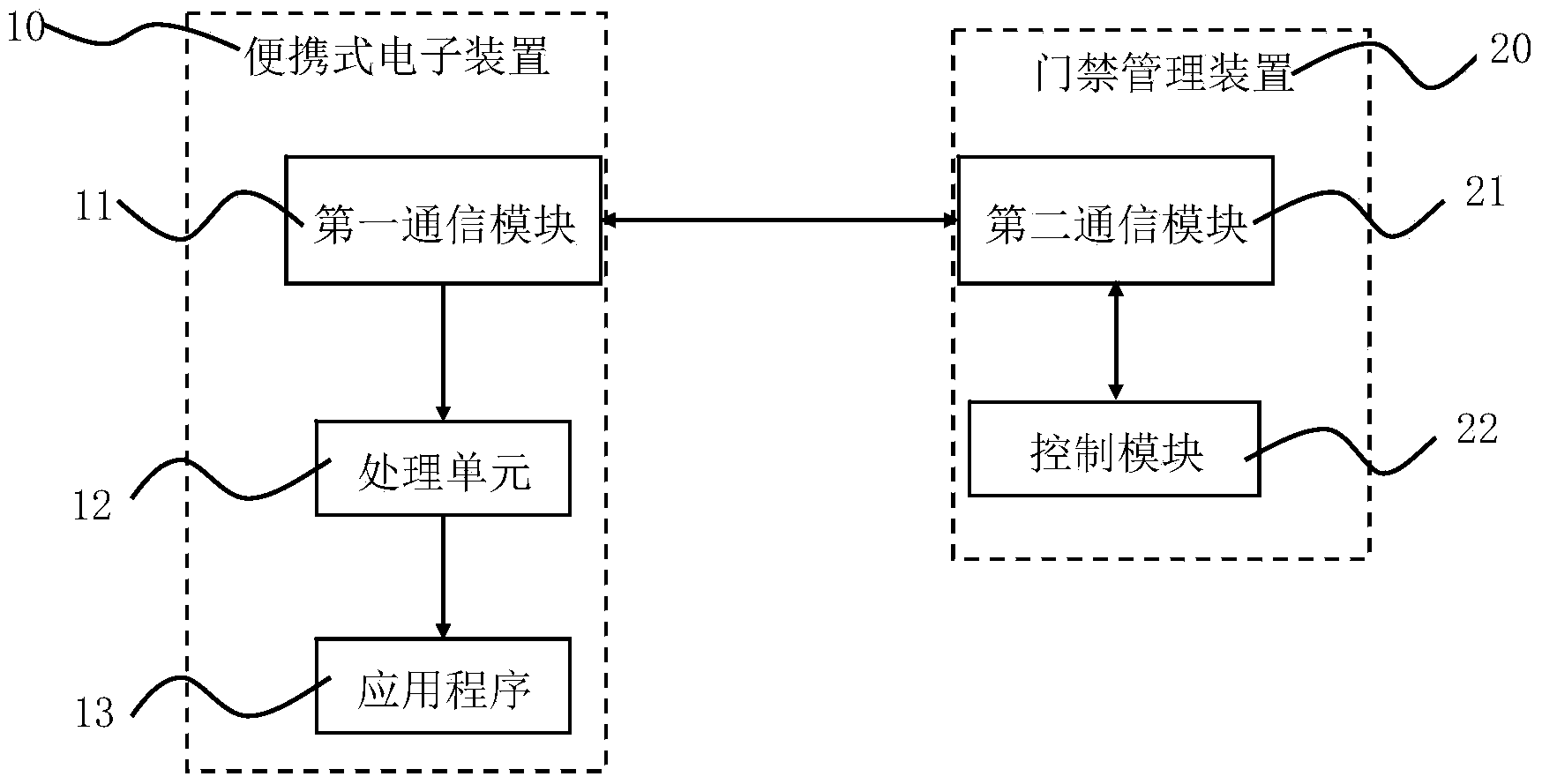
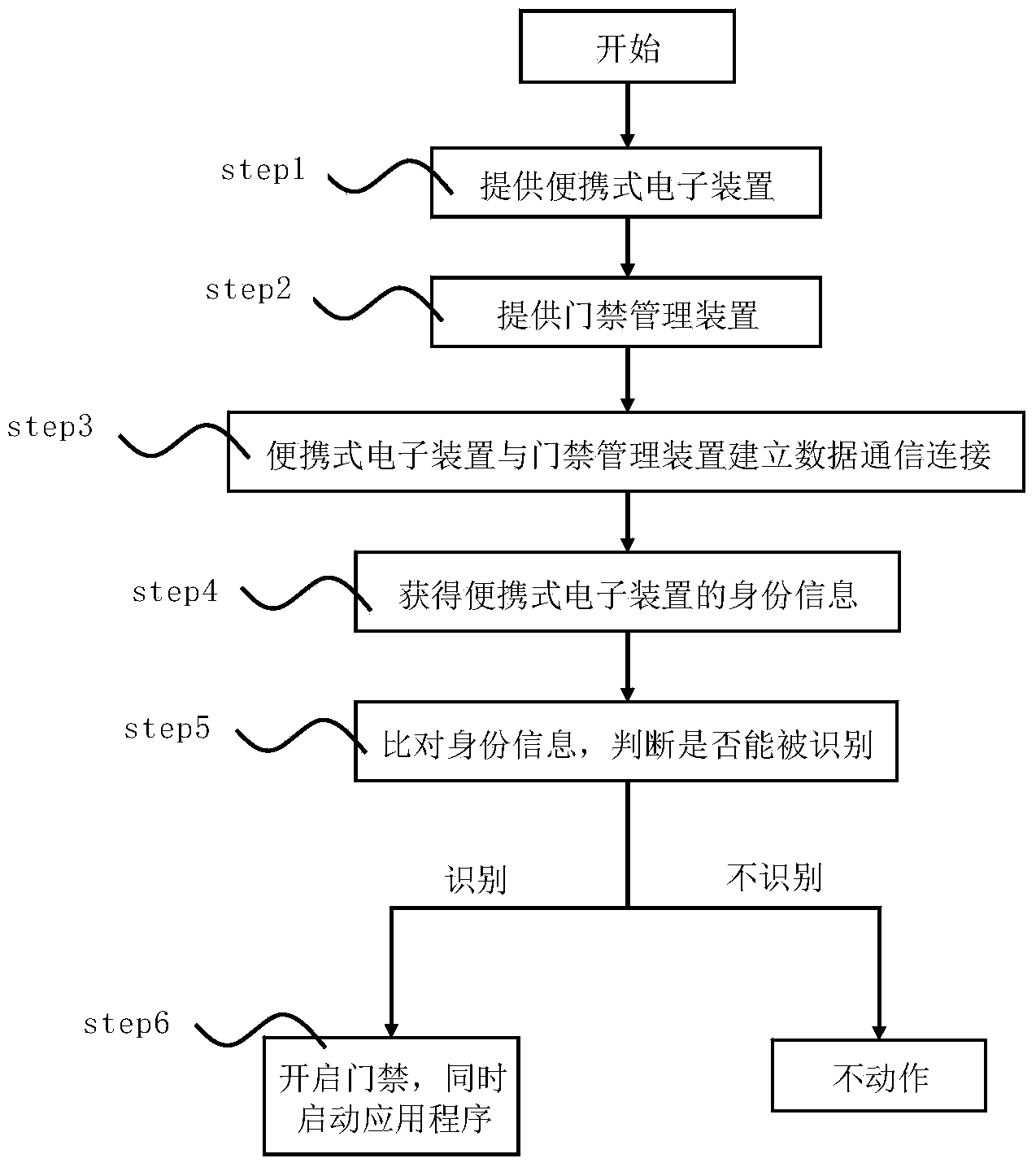
InactiveCN103942864AReduce the burden of useSafe and effective maintenanceIndividual entry/exit registersData connectionControl signal
The invention discloses a data security controlling system and an implementation method of the system. The data security controlling system comprises a portable electronic device, an application program and an access control management device, wherein the portable electronic device comprises a first communication module; the access control management device comprises a second communication module and a control module; the second communication module and the first communication module are used for performing data communication and reading identity information; the control module is used for receiving the identity information and comparing the identity information with preset identity information stored in the control module; if the identity information is identified by the access control management device, the control module is used for outputting instructions and controlling the access control management device to output control signals to the portable electronic device, so that the portable electronic device is used for starting the application program. According to the data security controlling system, data connecting, photographing and other functions of the portable electronic device are closed by the application program, so that the portable electronic device entering a secret area is incapable of uploading and downloading secret data, so that the security of the secret data of the company is effectively protected.
Owner:QISDA SUZHOU +1
Method for promoting online group purchase activity, calculation device readable storage medium and calculation device
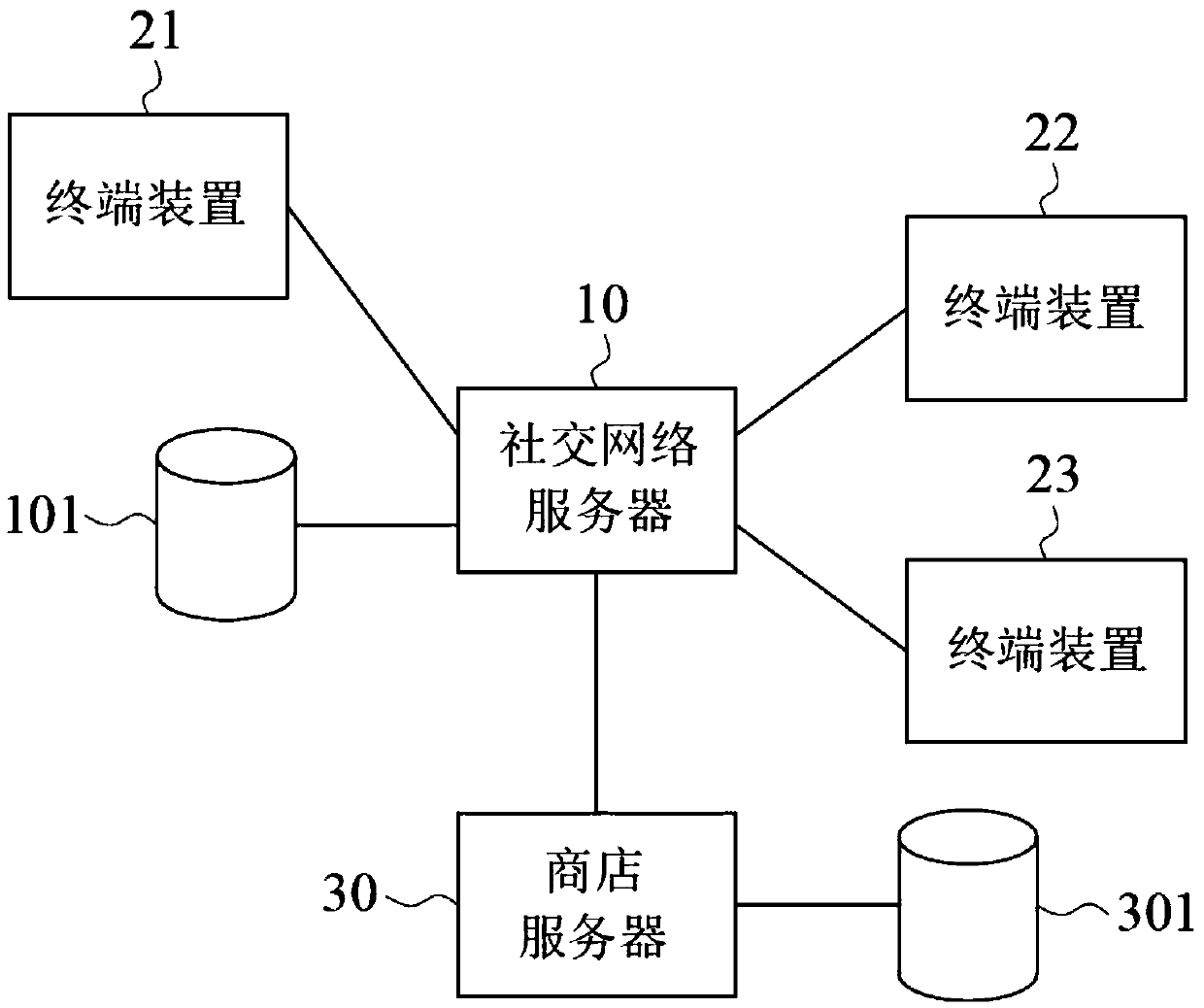
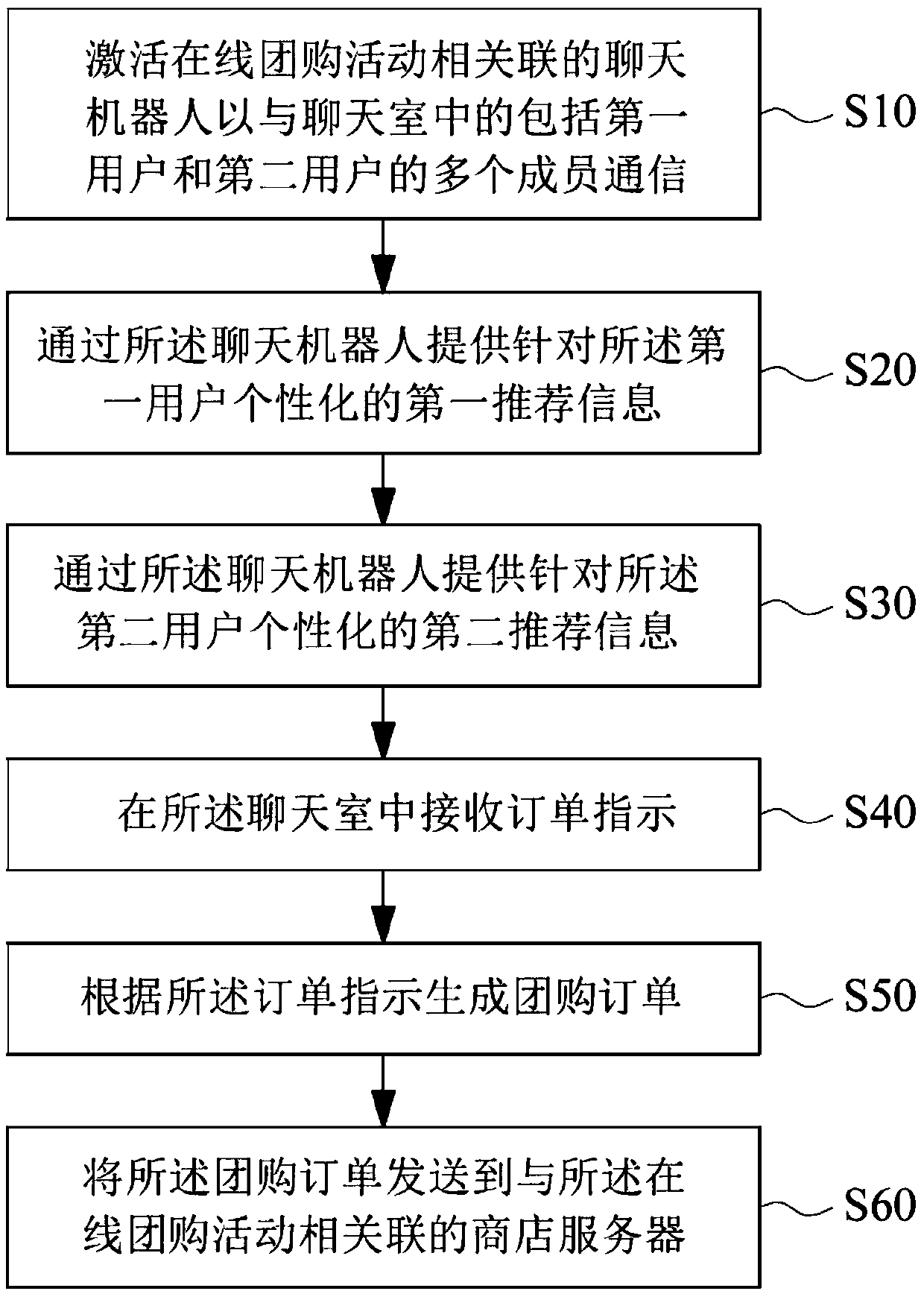
ActiveCN110874750AReduce the burden of useImprove experienceBuying/selling/leasing transactionsMarketingPersonalizationChat room
The present invention provides a method of facilitating an online group purchase activity, comprising the steps of activating a chat robot to communicate with a plurality of parts in a chat room of asocial networking service provided by a social networking server, where the chat robot is associated with the online group purchase activity and the plurality of parts include a first user and a second user. And providing personalized first recommendation information for the first user for the first user through the chat robot. And second recommendation information personalized for the second useris provided for the second user through the chat robot. And receiving an order indication in the chat room, wherein the order indication comprises a first order indication from the first user and a second order indication from the second user. And generating a group purchase order according to the order indication. And sending the group purchase order to a store server associated with the onlinegroup purchase activity.
Owner:LINE CORPORATION
Integrated self-driven full-textile gesture recognition data glove
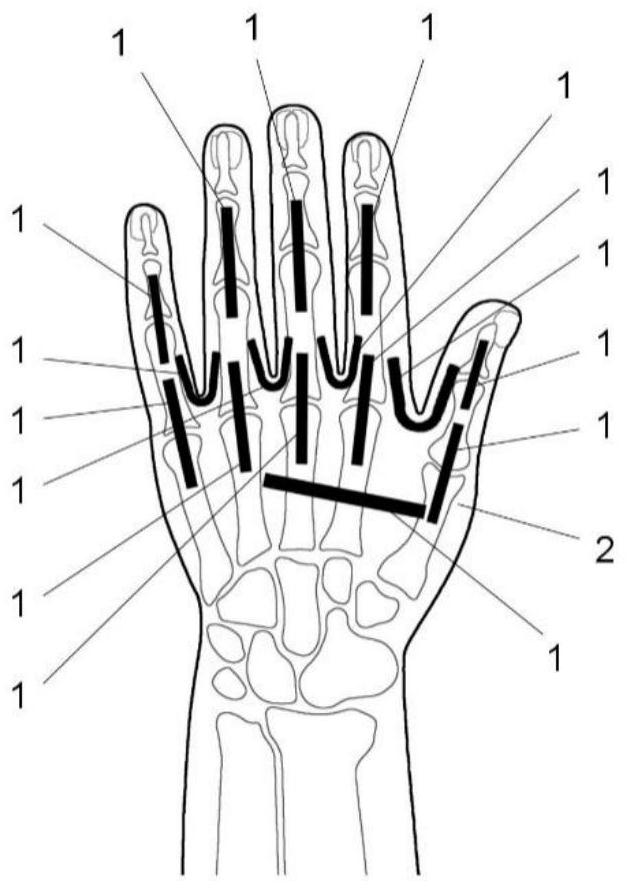
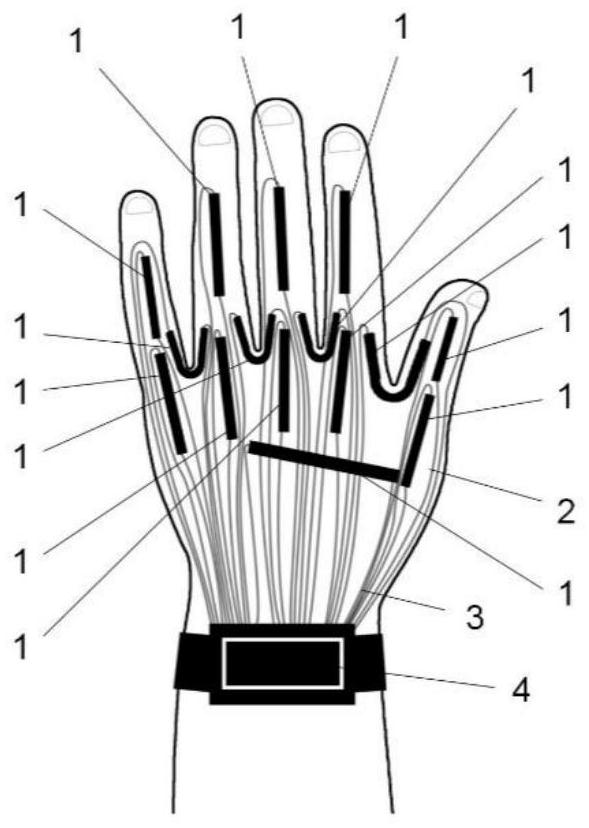
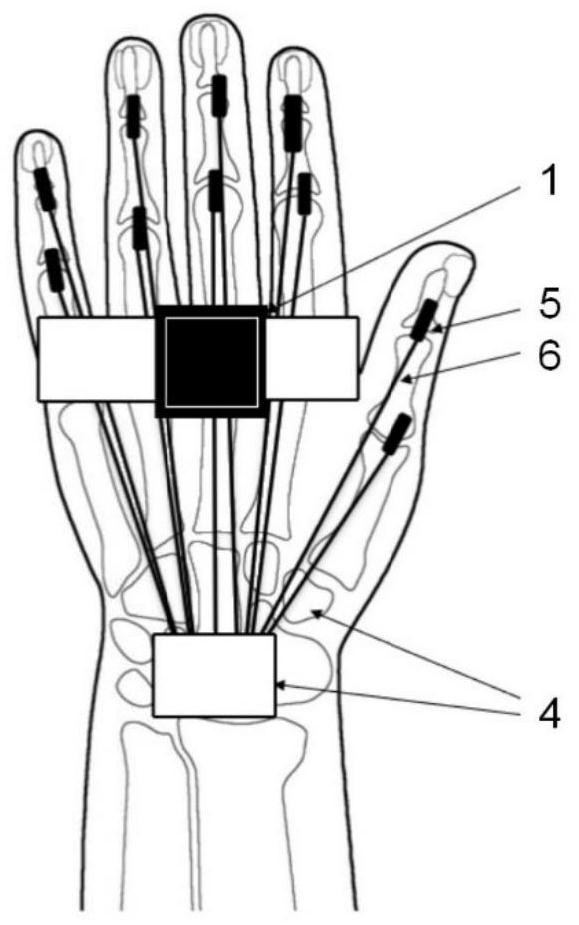
ActiveCN111665937ARealize structural integrationEase of mass productionInput/output for user-computer interactionGlovesControl circuitElectrically conducting yarn
The invention discloses an integrated self-driven full-textile gesture recognition data glove, which is characterized by comprising a glove base body, self-powered strain sensing parts and flexible weak-sensitive conductive yarns, wherein basic yarns for weaving the glove base body are elastic insulating yarns; the self-powered strain sensing parts are arranged in a plurality of sensing areas of the glove base body; and the self-powered strain sensing parts are connected with a control circuit through the flexible weak-sensitive conductive yarns. The sensor of the data glove is flexibly fiberized under the condition that the electrical property is met, so that the mechanical property for a textile weaving process is met, and the sensing detection and the structure integration of a glove material are realized, and the possibility of batch production is improved. Meanwhile, the self-driven passivity of the detection circuit can effectively reduce the burden of equipment and simplify thecircuit, and avoids the use limitation caused by charging or battery replacement.
Owner:DONGHUA UNIV
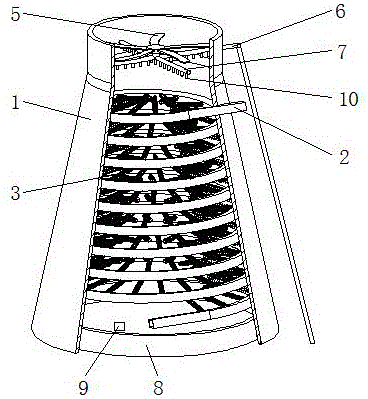
Efficient water cooling tower
ActiveCN106839804ASpeed up coolingImprove cooling efficiencyTrickle coolersNuclear engineeringWater quality
The invention relates to an efficient water cooling tower, and belongs to the technical field of cooling equipment. The efficient water cooling tower comprises a tower body with a conic opening, a cooling system and a heat radiation system. The cooling system is arranged in a surrounding manner to be closely attached to the inner wall of the tower body and is evenly distributed in the space in the tower body. A water inlet and a water outlet of the cooling system are both arranged outside the tower, and the part, in the tower, of the cooling system is in a totally closed type. The heat radiation system is arranged at the upper end and the lower end of the tower body, and the heat radiation effect of the cooling system is accelerated. According to the efficient water cooling tower, high-temperature circulating water is guided into the cooling system, the cooling system is utilized for absorbing, transmitting and treating heat in the circulating water, the heat in the circulating water is transferred to the cooling system, and the heat radiation system carries out heat radiation on the cooling system. During cooling, the circulating water is only in direct contact with the totally-closed inner wall of the cooling system, and the evaporation amount of the circulating water can be almost ignored. By means of a cooling method, the circulating water can be efficiently cooled, meanwhile, the quality of water quality generated after cooling is considered, and the cooling mode of the prior art is directly broken through.
Owner:海宁萃智智能机器人有限公司
Handheld medical infant atomizer and atomizing mask
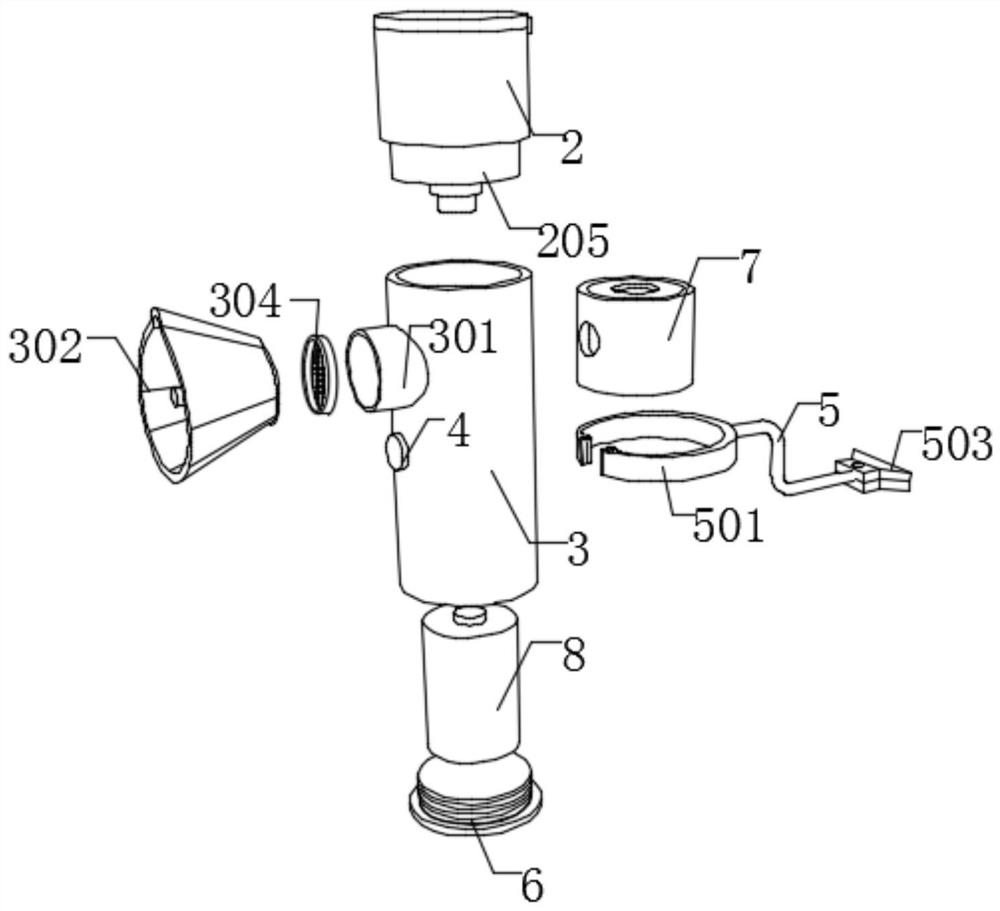
InactiveCN113368348AReduce the burden of useAchieve the purpose of treatmentRespiratory masksMedical devicesRubber ringAnatomical structures
The invention discloses a handheld medical infant atomizer and an atomizing mask. The handheld medical infant atomizer comprises a device body; the device body comprises a liquid medicine cup, an atomizer handle and a switch; one side of the liquid medicine cup is fixedly connected with one side of a fixing block; a cup cover is arranged on one side of the fixing block; the bottom of the cup cover is connected with two sets of rubber rings in a sleeved mode; the two sets of rubber rings are distributed at equal intervals; the bottom of the cup cover is clamped into the liquid medicine cup; the outer walls of the two sets of rubber rings are attached to the inner wall of the liquid medicine cup; scale marks are arranged on one side of the outer wall of the liquid medicine cup; and the bottom of the liquid medicine cup is fixedly connected with the top of a connecting block. Due to mutual combination of the various parts, the device can be used in all child hospitals, is also suitable for household use of infants needing atomization treatment, has the function that most atomizers in the market atomize liquid medicine into small particles and deposit the small particles in the lungs through inhalation to achieve the treatment purpose, and also has the functions of pacifying, preventing backflow, being ultra-silence and enabling a mask of an anatomical structure to be tightly attached to the face of a sick child.
Owner:THE WEST CHINA SECOND UNIV HOSPITAL OF SICHUAN
Upper limb exoskeleton device with bamboo-like structure
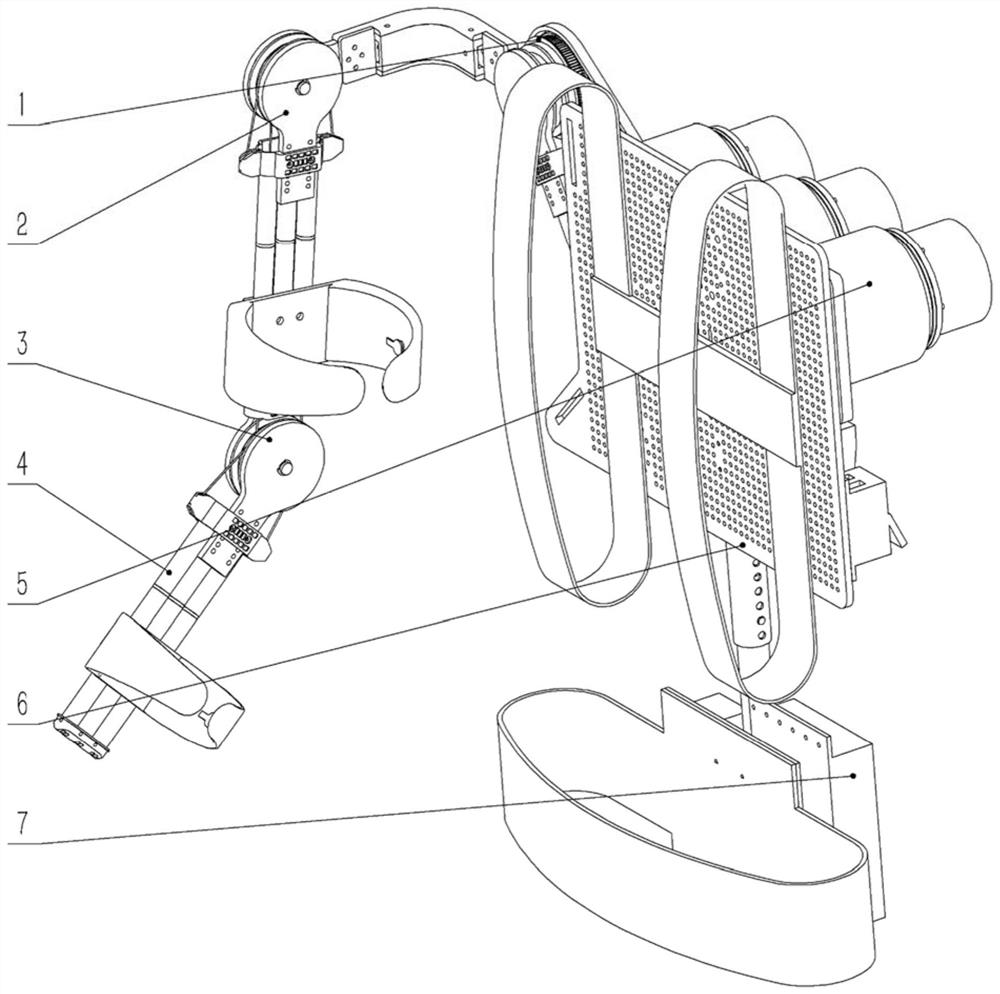
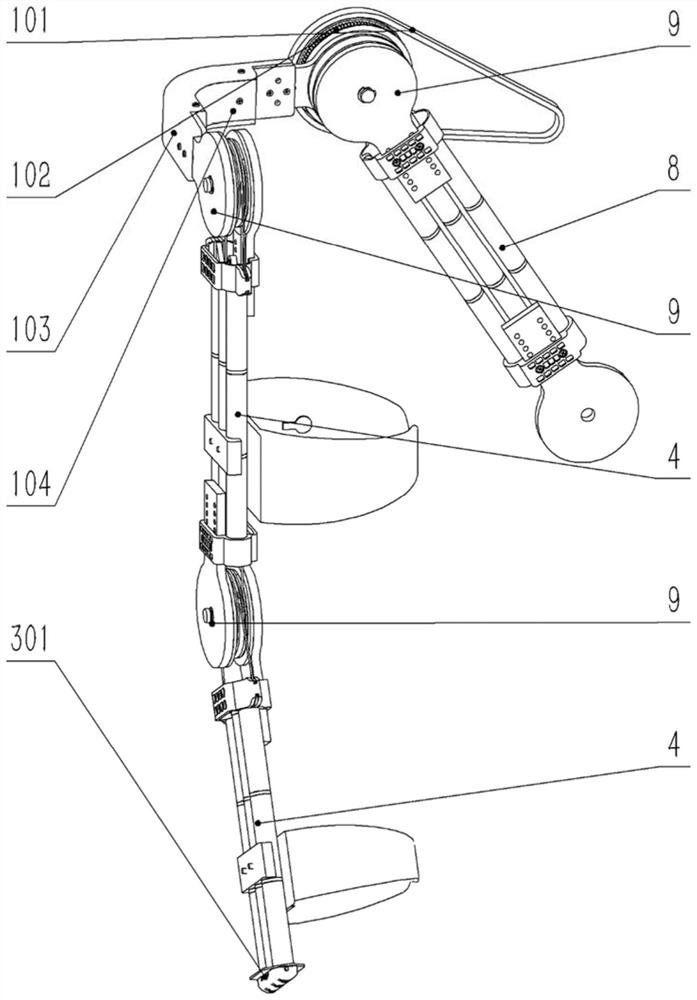
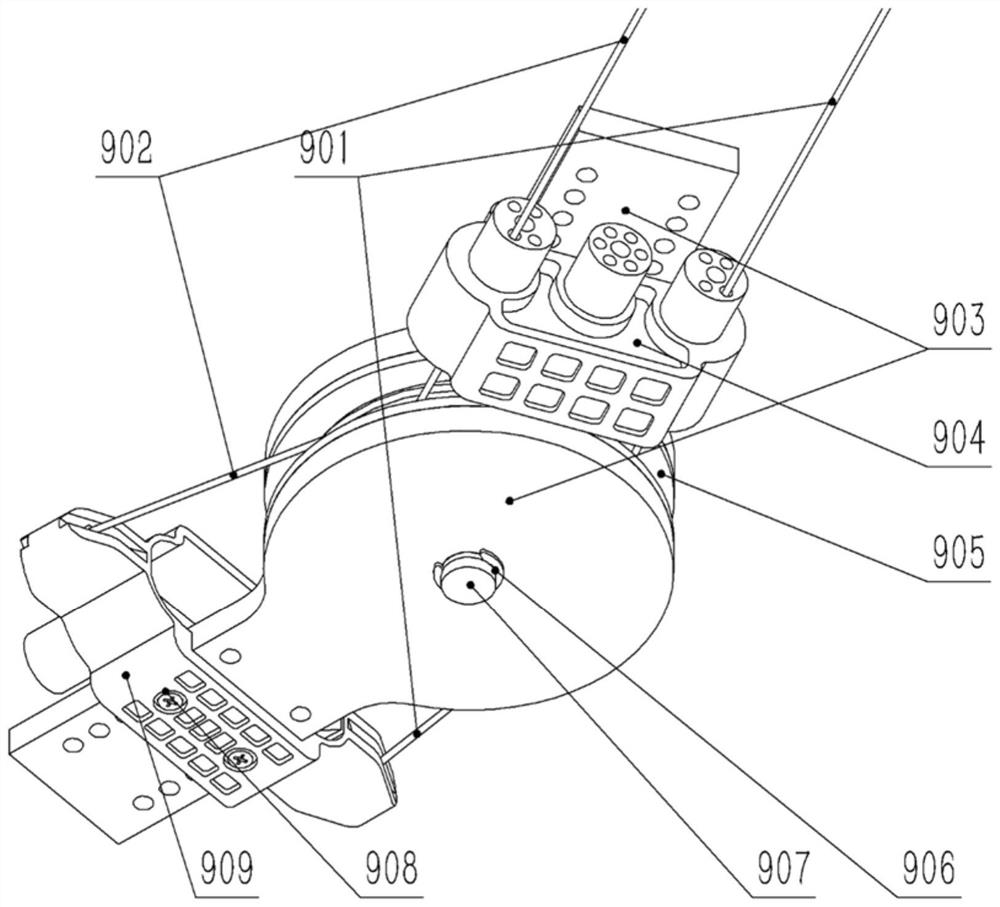
ActiveCN112077827ALight in massReduce volumeProgramme-controlled manipulatorJointsInterference fitEngineering
The invention provides an upper limb exoskeleton device with a bamboo-like structure. The upper limb exoskeleton device comprises a shoulder adduction and abduction joint (1), a shoulder flexion and extension joint (2), an elbow flexion and extension joint (3), a bamboo-like structure mechanical arm (4), a driving module (5), a back plate support (6) and an electrical system (7), wherein the shoulder adduction and abduction joint (1) is connected to the shoulder flexion and extension joint (2) through an L-shaped workpiece; the shoulder flexion and extension joint (2) is connected to the elbowflexion and extension joint (3); the bamboo-like structure mechanical arm (4) is in interference fit with the elbow flexion and extension joint (3); and the driving module (5) is connected to the shoulder adduction and abduction joint (1), the shoulder flexion and extension joint (2) and the elbow flexion and extension joint (3). Compared with a traditional rod piece mechanical arm, the bamboo-like mechanical arm can meet the rigidity requirement with lighter mass and smaller size. In addition, an internal cavity also has the functions of planning a rope path or internally arranging other parts and the like.
Owner:SHANGHAI JIAO TONG UNIV
Trunk injecting pesticide for preventing corythucha ciliate, and preparation method and application thereof
ActiveCN106797951ARealize precise prevention and controlIncrease profitBiocideDead animal preservationSurface-active agentsSolvent
The invention discloses a trunk injecting pesticide for preventing corythucha ciliate, and a preparation method and application thereof. The trunk injecting pesticide for preventing the corythucha ciliate is long in effective time, and compared with sprayed pesticides used at present, the trunk injecting pesticide is good in effect, saves both time and labor, and avoids pollution to the environment; the preparation method is simple in process and low in costs; the application is free from the influence of weather and tree body heights, and the pesticide enters a plant body completely, does not hurt natural enemies, and can be used for a long time. The trunk injecting pesticide disclosed by the invention is durable and stable in effect; hydrolysis is difficult to happen; the defect that current trunk injections need preparing while used is effectively avoided; and the using burden of a user is relieved, so that the trunk injecting pesticide is suitable for industrial production. The trunk injecting pesticide for preventing the corythucha ciliate is prepared from the following raw materials in percentage by weight: 1 to 50 percent of thiacloprid raw powder, 0.1 to 20 percent of acephate raw powder, 1 to 10 percent of a surface active agent, and the balance is a solvent.
Owner:SHANDONG FOREST SCI RES INST
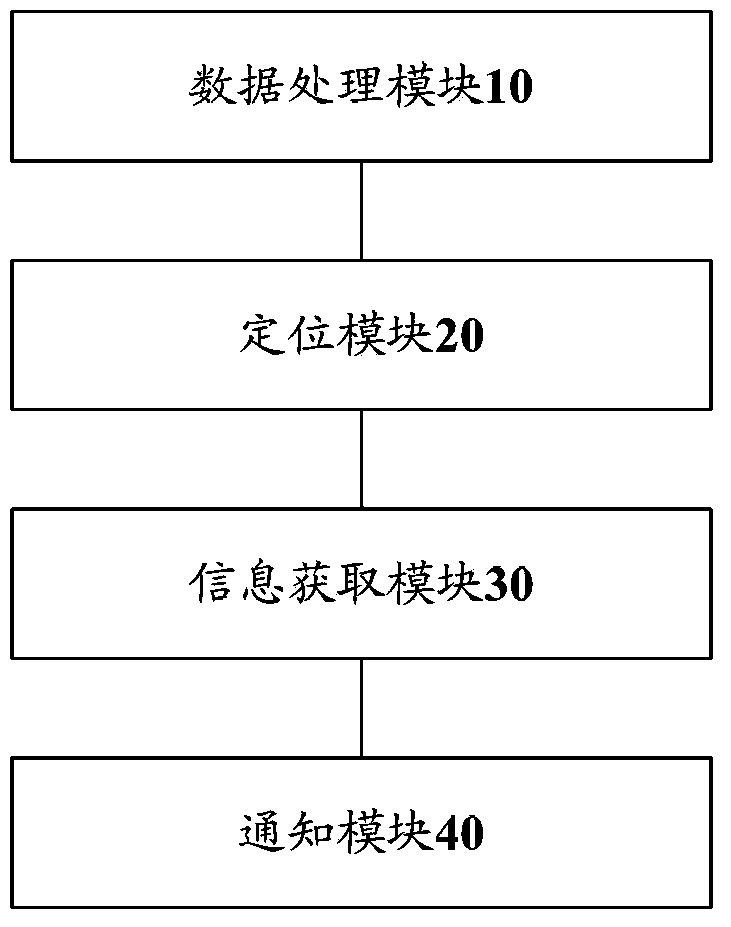
Information synchronization system and method
ActiveCN103546508AReduce the burden of useImprove user experienceTransmissionResource informationInformation gain
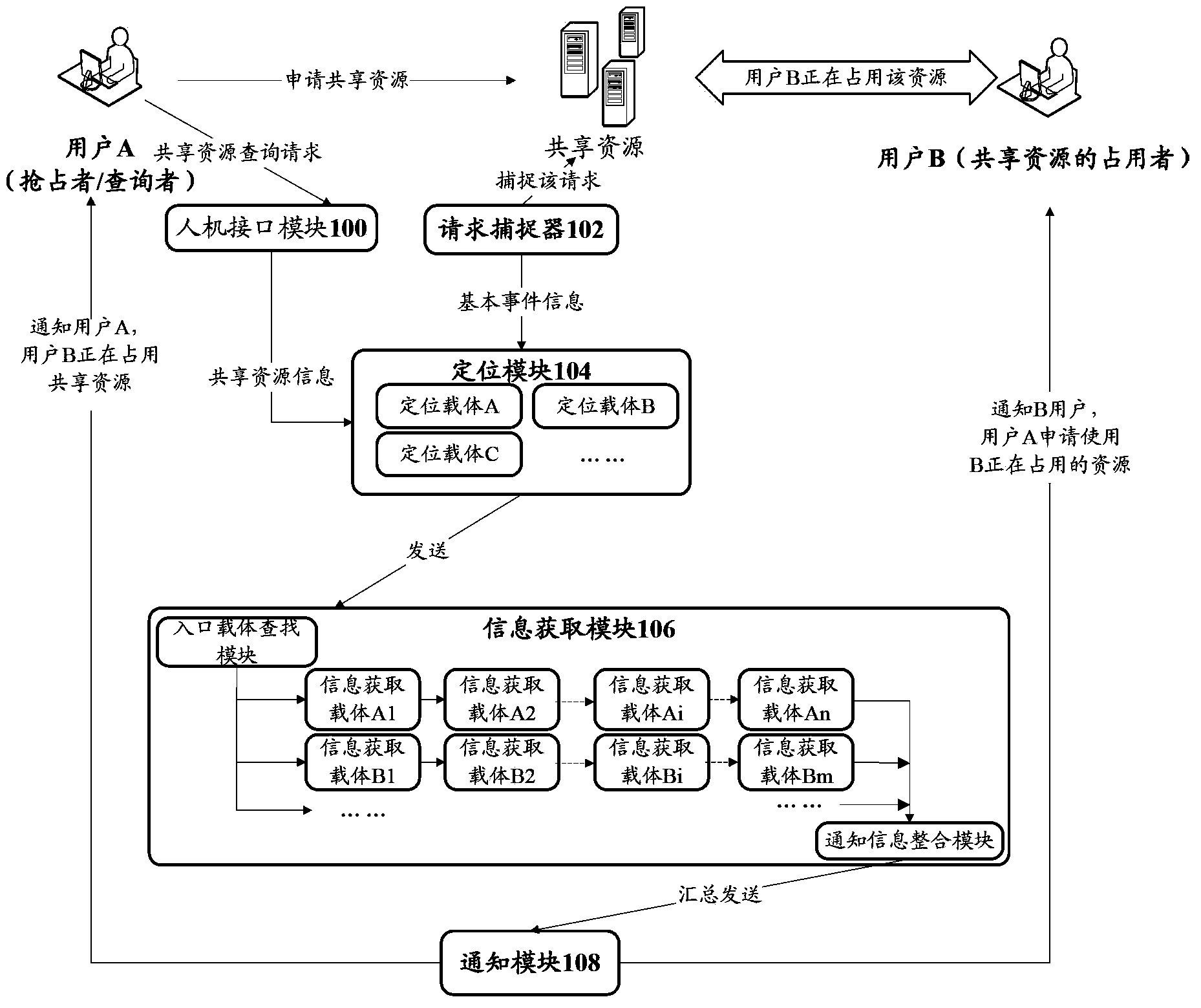
The invention provides an information synchronization system and method. The system comprises a data processing module, a positioning module, an information acquiring module and a notifying module. The data processing module acquires shared resource information and / or requester information of shared resources of a distributed system and transmits the information to the positioning module. The positioning module is used for acquiring an identification of a requester of the shared information and / or the identification of an occupier of the shared resources according to the requester information and transmitting the identification to the information acquiring module. The information acquiring module is used for respectively converting the identification of the requester of the shared information and / or the identification of the occupier of the shared resources into corresponding the occupier attribute information identification and / or the requester attribute information identification and transmitting the occupier attribute information identification and / or the requester attribute information identification to the notifying module. The notifying module is used for notifying sharing state of the shared resources. By the system, positioning of the shared resource occupier and sharing of state of the shared information can be achieved conveniently.
Owner:ADVANCED NEW TECH CO LTD
Watchband antenna for wearable wireless system
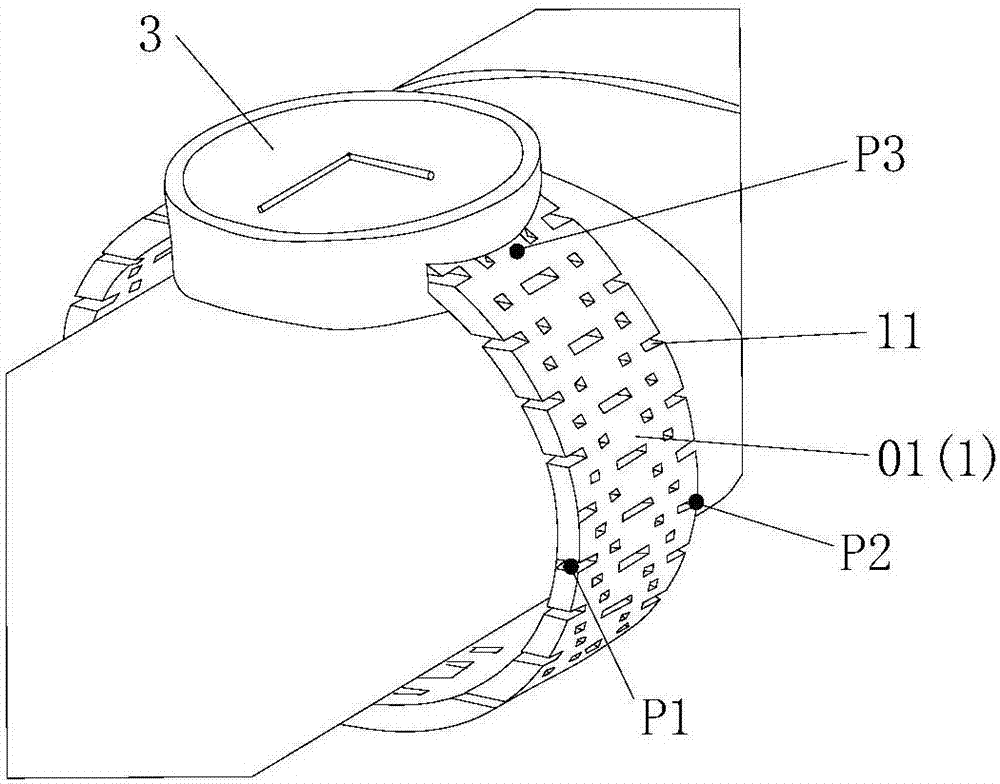
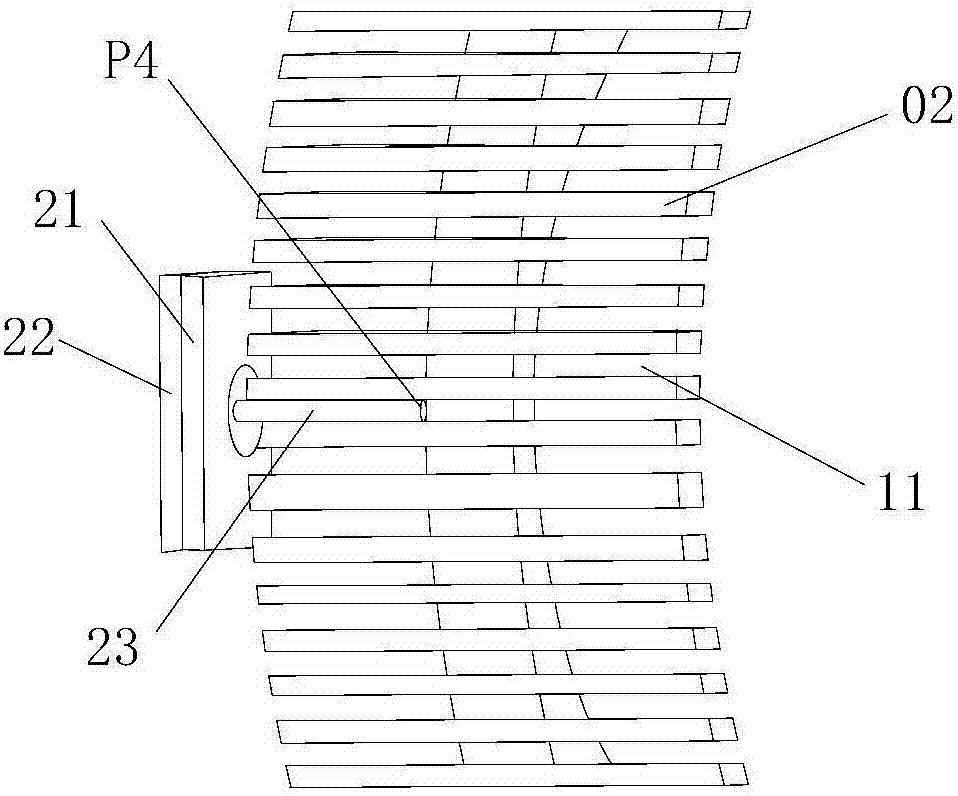
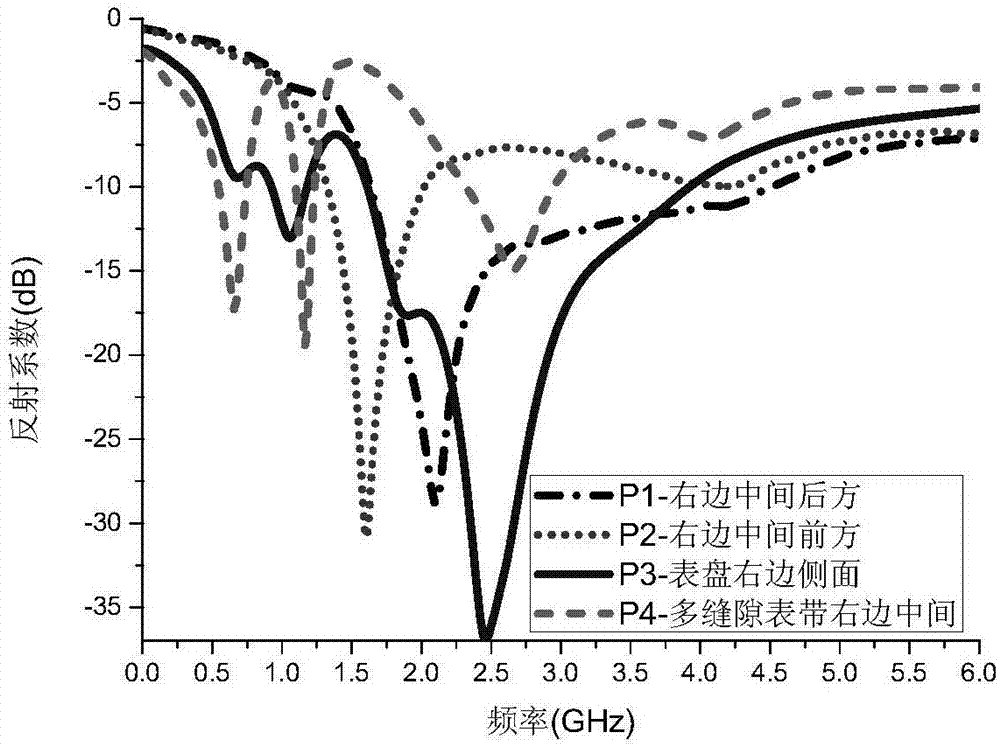
ActiveCN106898874AEasy to installStable structureRadiating elements structural formsBraceletsDielectric substrateMaterials science
The invention provides a watchband antenna for a wearable wireless system, including a watchband and a feed device arranged on the watchband. The watchband is made of a metallic material and is provided with at least one gap. The feed device includes a microstrip dielectric substrate, a metal ground disposed on the microstrip dielectric substrate, and a feed probe. The feed probe penetrates the metal ground and the microstrip dielectric substrate and is inserted into and connected in the gap in the watchband. The watchband antenna is easy to install, solid in structure, low in price, light in weight and small in size, and reduces the burden on users. With the watchband antenna structure, the antenna radiation is achieved, and the selection range of the wearable wireless system antenna is expanded.
Owner:NAT UNIV OF DEFENSE TECH
Display system and method of screen
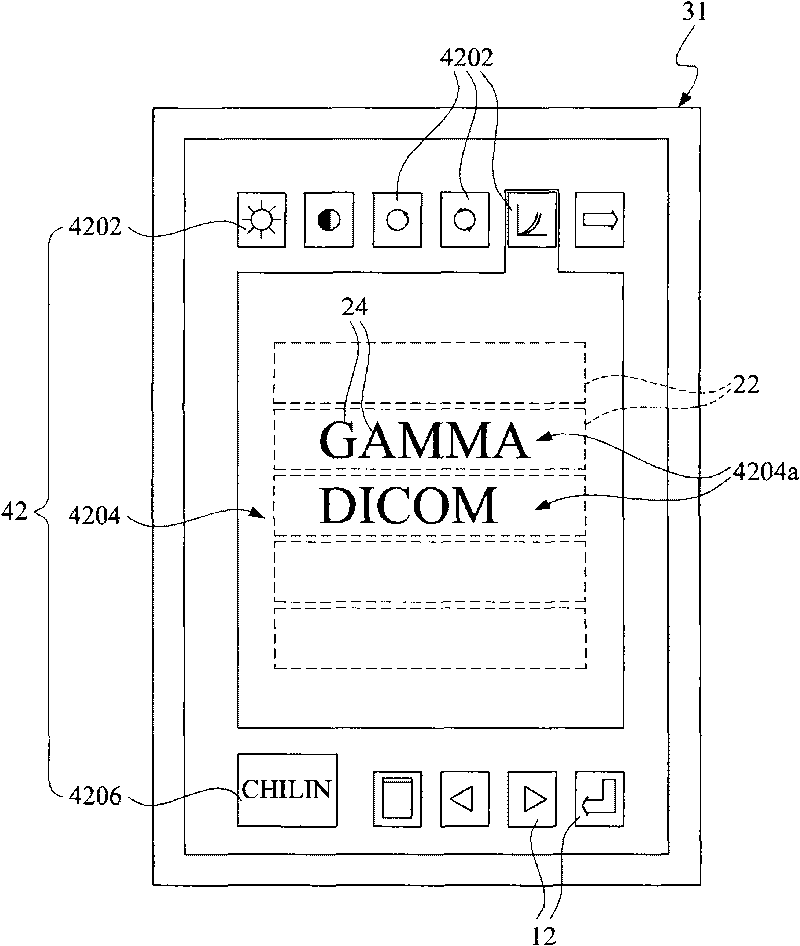
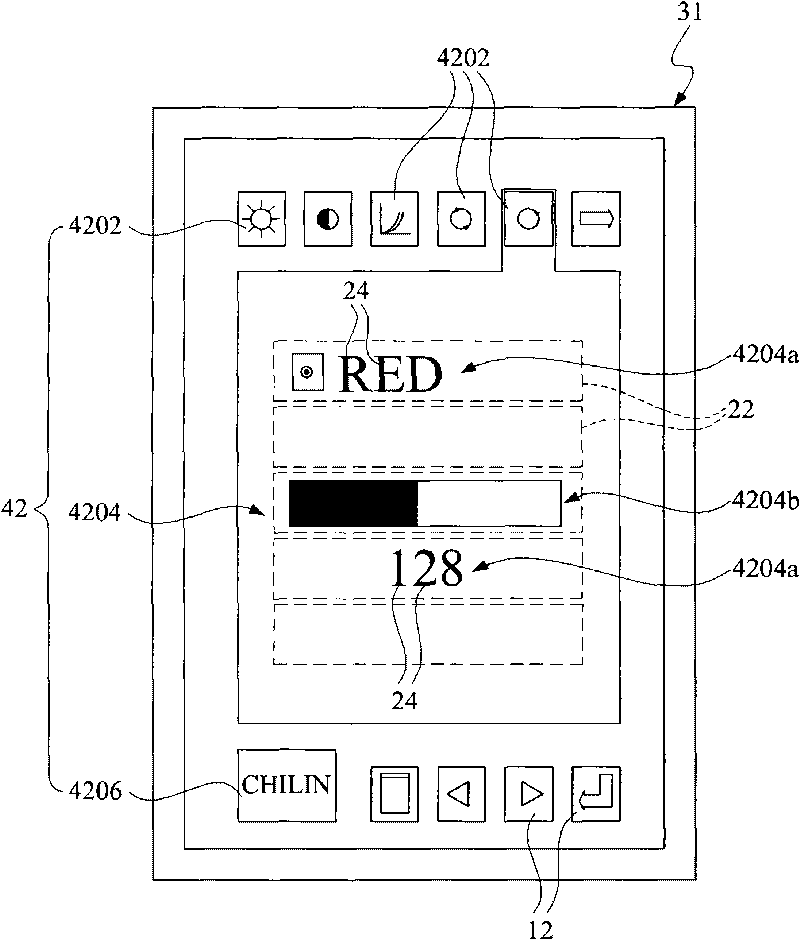
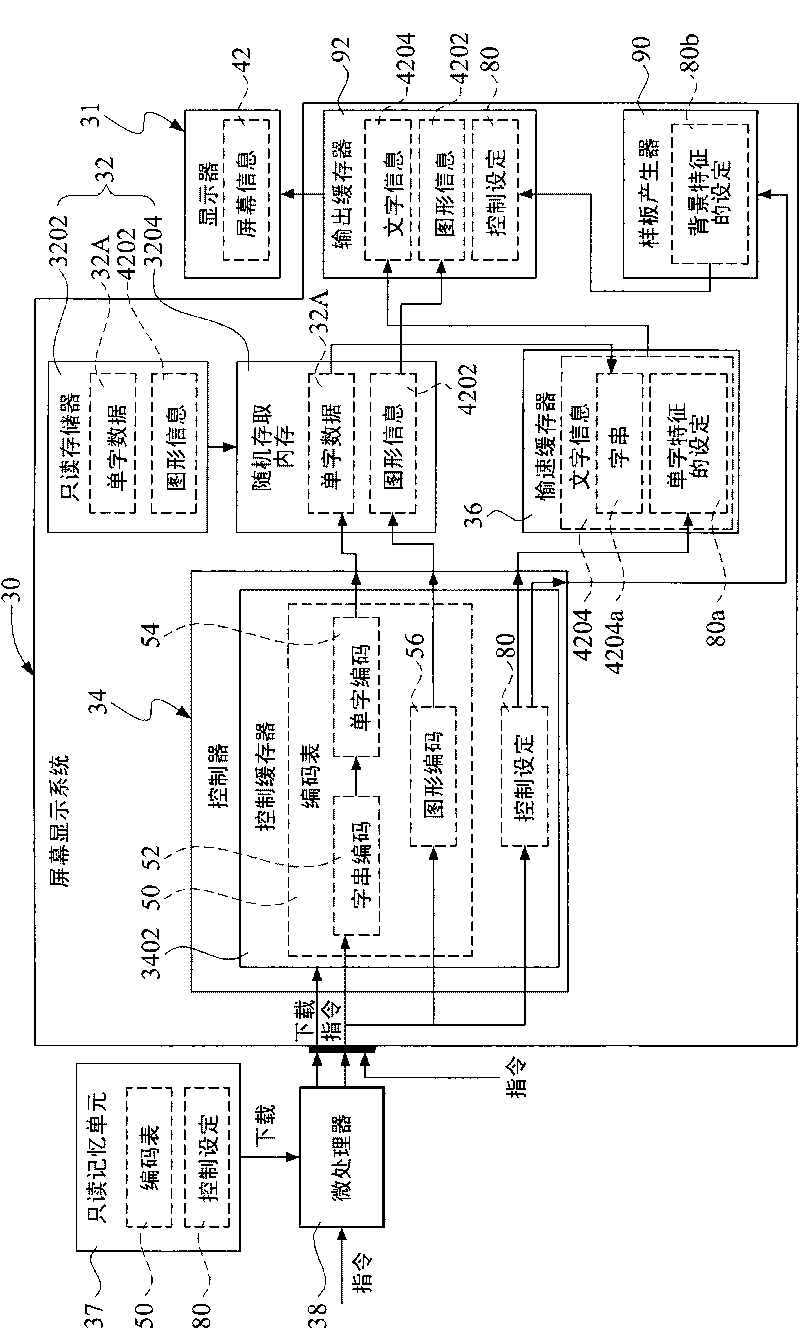
The invention discloses display system and method of a screen, which are used for controlling on screen display (OSD) of a display and correspondingly displaying screen information, wherein the screen information mainly contains graphical information and character information corresponding to the graphical information; the character information is provided with a plurality of rows of display lines which can display a plurality of character strings consisting of individual characters or degree bar charts; aiming at the display of the character strings, a controller captures individual character data prestored in a memory to further form the character strings according to character string codes and individual character codes in a code table, and then displays the character strings from the picture of the display; in addition, the colors of the character strings come from the controller without being memorized in a memory, therefore, necessary individual character data are only memorizedin the memory and used for subsequent different character strings to repeatedly download and use and memory resources cannot be wasted due to fully memorizing the data.
Owner:SHIN DER MING
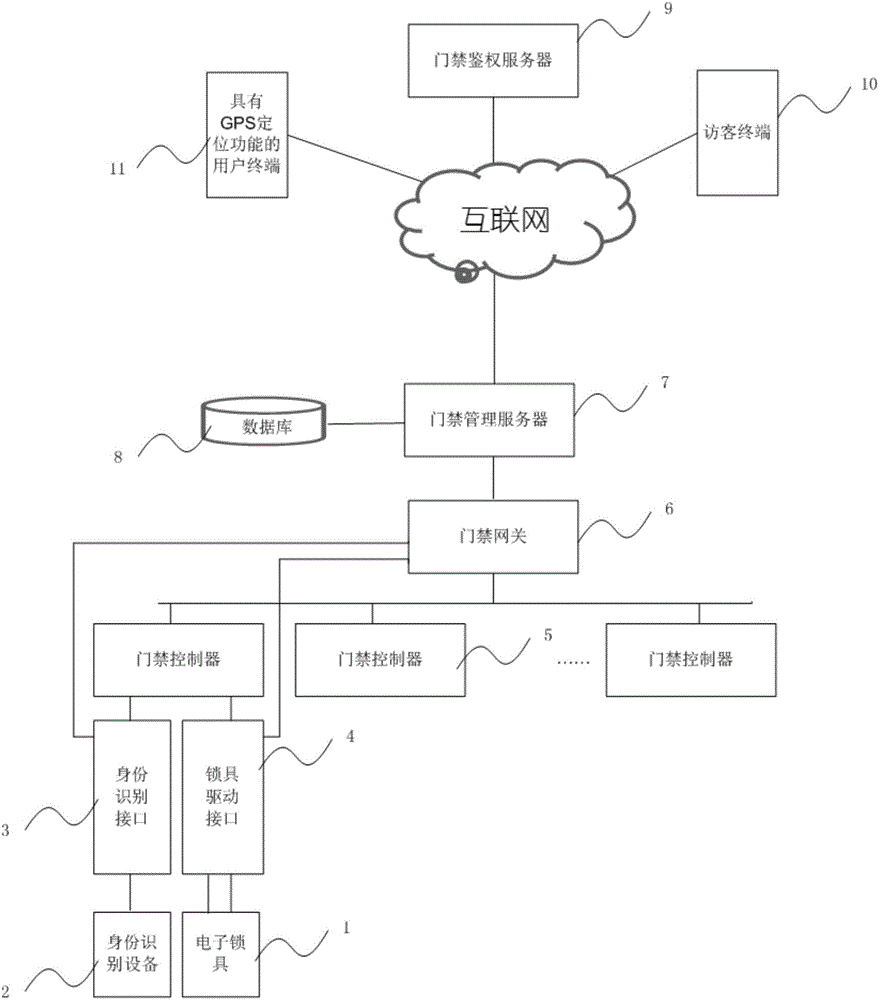
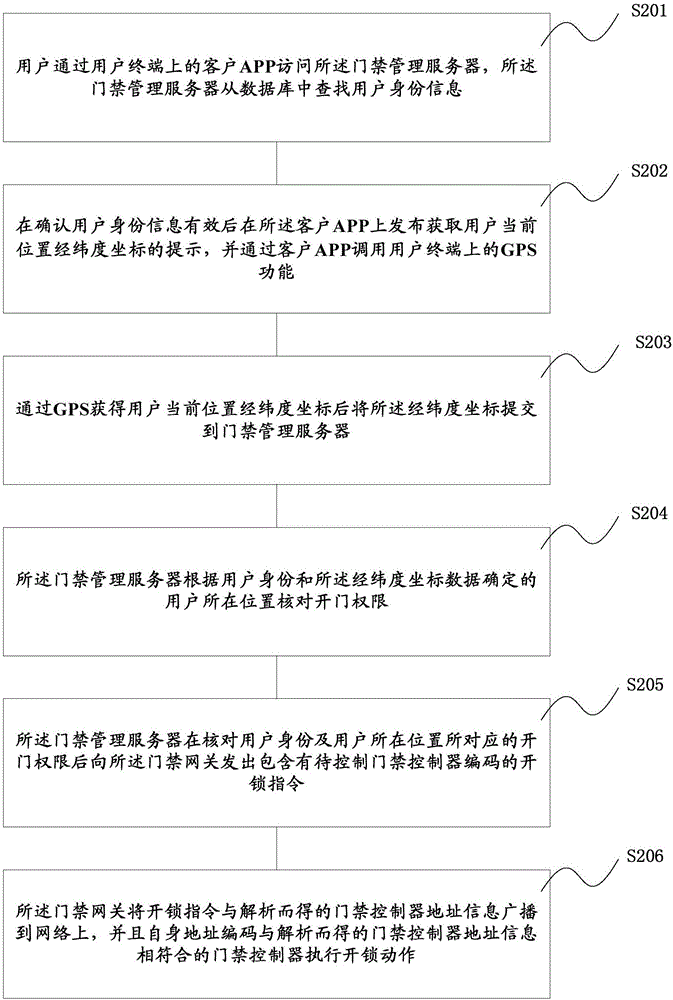
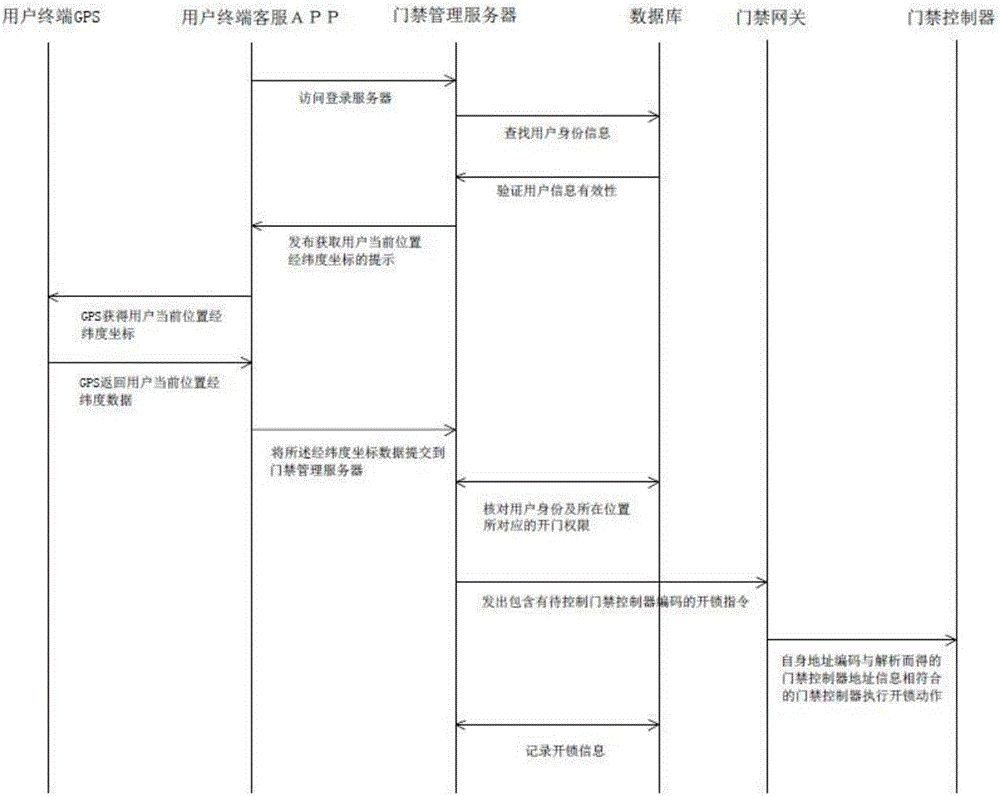
Access control system and door opening method based on GPS (global positioning system) positioning
InactiveCN106296948AEasy accessReduce the burden of useIndividual entry/exit registersUser needsWorkload
The invention relates to an access control system and a door opening method based on GPS (global positioning system) positioning. According to a mode that the position of a user is acquired through a GPS and the user enters the access control system after identity verification, the user needs not to take any ID / IC card or a note in a paper form, or the user is not required to download an extra electronic note, so that the use burden of the user is reduced, and the user enters the access control system conveniently. According to the access control system and the door opening method based on the GPS positioning, the user can automatically open the door without carrying out any operation after the position of the user is acquired by the GPS and the identity is verified, the door can be opened automatically when the user with the permission approaches the door, and meanwhile, the access control system can record access information of people simply, rapidly and comprehensively; the system can forbid access of users without permission or give an alarm, so that the effect of access control security management is effectively improved, and the workload of security personnel is reduced.
Owner:BEIJING UPVALUE INTPROP CONSULTANTSCO
Cell phone matched with Bluetooth earphone through curing and using method thereof
InactiveCN103401964AAvoid lossEasy to answerTelephone set constructionsComputer hardwareBattery capacity
The invention discloses a cell phone matched with a Bluetooth earphone through curing. The cell phone comprises a shell, and a main controller and a touch switch for plugging the Bluetooth earphone to trigger the main controller which are arranged at the interior of the shell, a cell phone Bluetooth module and a power supply module which are connected with the main controller; the cell phone also comprises the Bluetooth earphone; and the Bluetooth earphone comprises an earphone Bluetooth module matched with the cell phone Bluetooth module in a one-to-one manner. Meanwhile, the invention further discloses a using method of the cell phone matched with the Bluetooth earphone through curing. The cell phone is matched with the Bluetooth earphone in a one-to-one manner through curing, and the Bluetooth earphone can be charged through a cell phone power supply at any time, so that a matching flow is not required when the Bluetooth earphone is used, the cell phone is convenient to use and solves troubles of some people caused by matching flow; and moreover, the Bluetooth earphone is small in volume and lighter in weight after the capacity of a battery is reduced, the using burden of a user is reduced, the comfort is improved, and the trouble that the Bluetooth earphone is charged independently is solved.
Owner:江海
Access control verification method based on two-dimensional code
InactiveCN107767511AReduce the burden of useEasy accessIndividual entry/exit registersValidation methodsEntry time
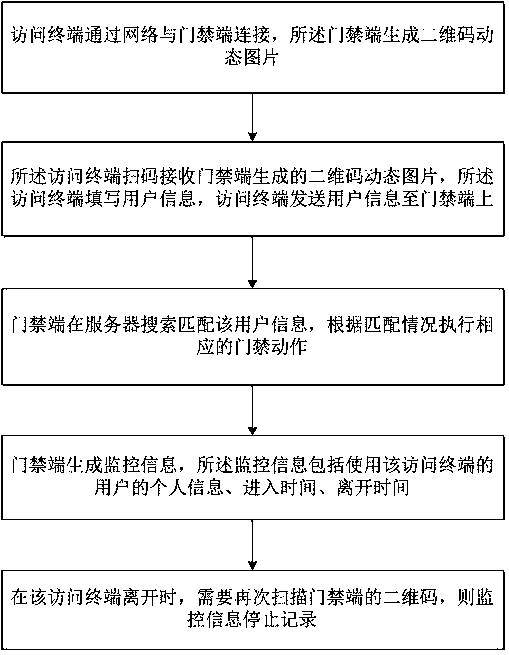
The invention relates to an access control verification method based on a two-dimensional code. The access control verification method comprises the following steps: (1) connecting an accessing terminal with an access control end through a network and generating a two-dimensional code dynamic picture at the access control end; (2) screening the code by the accessing terminal to receive the two-dimensional code dynamic picture generated by the access control end and filling user information by the accessing terminal; sending the user information to the access control end through the accessing terminal; (3) searching and matching the user information on a server by the access control end and carrying out corresponding access control actions according to a matching result; (4) generating monitoring information at the access control end, wherein the monitoring information comprises personal information, entering time and leaving time of a user of the accessing terminal; (5) when the accessing terminal leaves away, scanning the two-dimensional code of the access control end again and stopping recording the monitoring information. According to the access control verification method basedon the two-dimensional code, the utilization burdens of the user are alleviated and the user can conveniently enter an access control system; materials are saved and environment protection is facilitated; the information of people who enter and leave away can be rapidly recorded and is convenient to wholly count, so that conditions of people who enter and leave away are grasped and the safety ofthe access control system is improved.
Owner:徐下兵
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com