Realization method of data encryption in hard disk
A data encryption and realization method technology, applied in the direction of electrical digital data processing, special data processing applications, instruments, etc., can solve problems such as poor product compatibility, inaccessible data, troubles, etc., to save equipment use costs, reduce learning costs, Ease of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to describe in detail the structure of the present invention and the effect achieved, the following preferred embodiments are now given and described as follows in conjunction with the accompanying drawings:
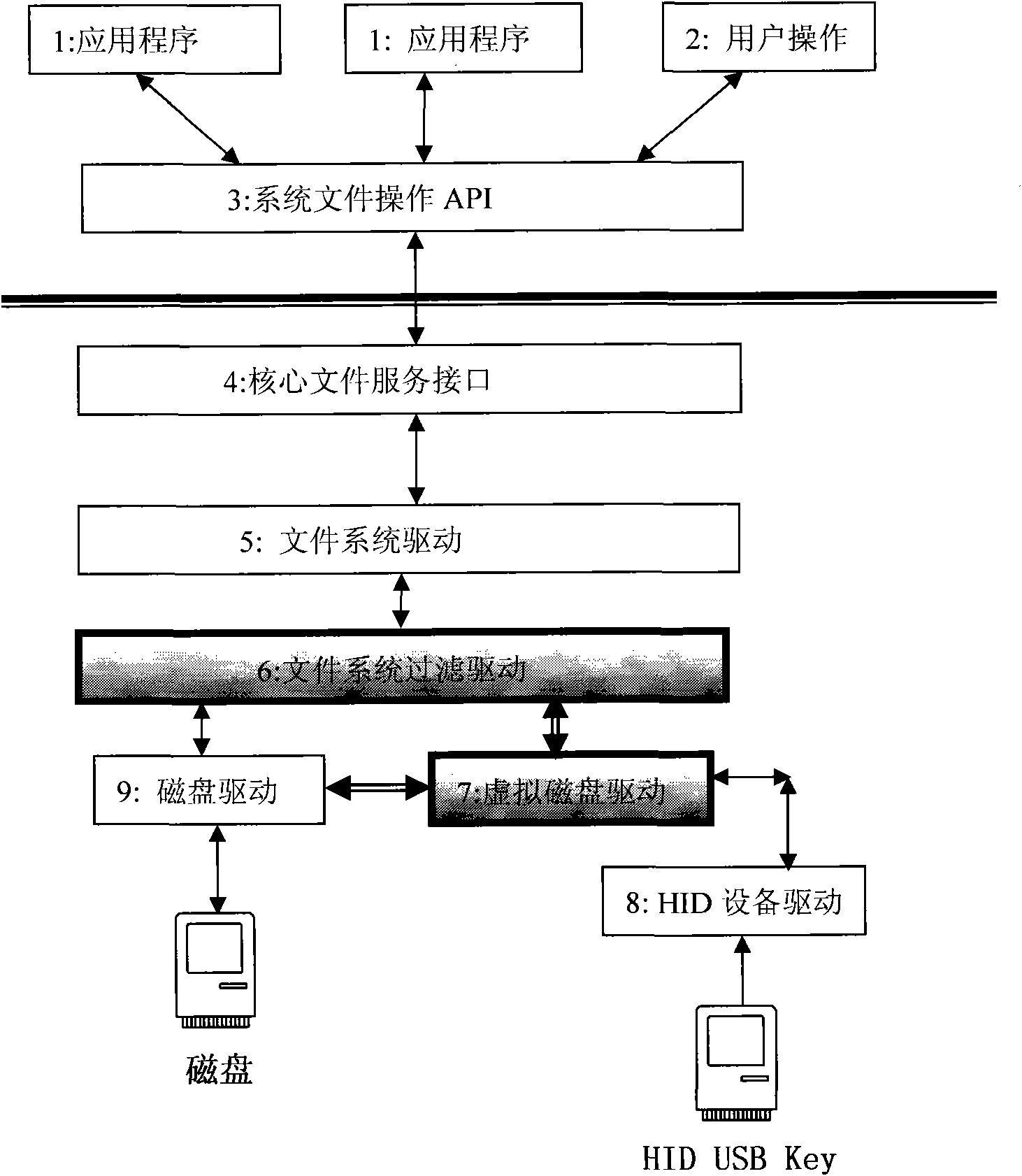
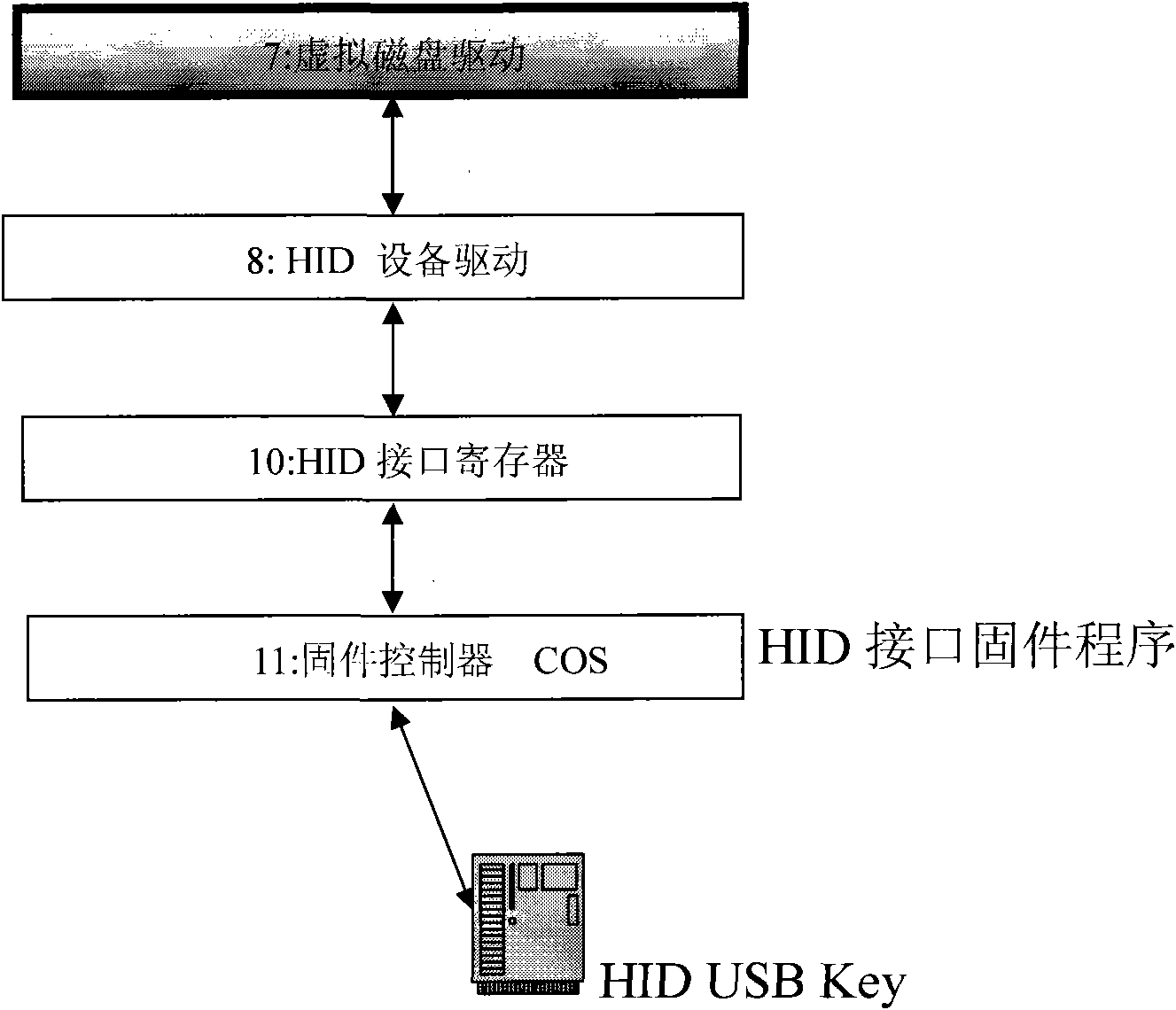
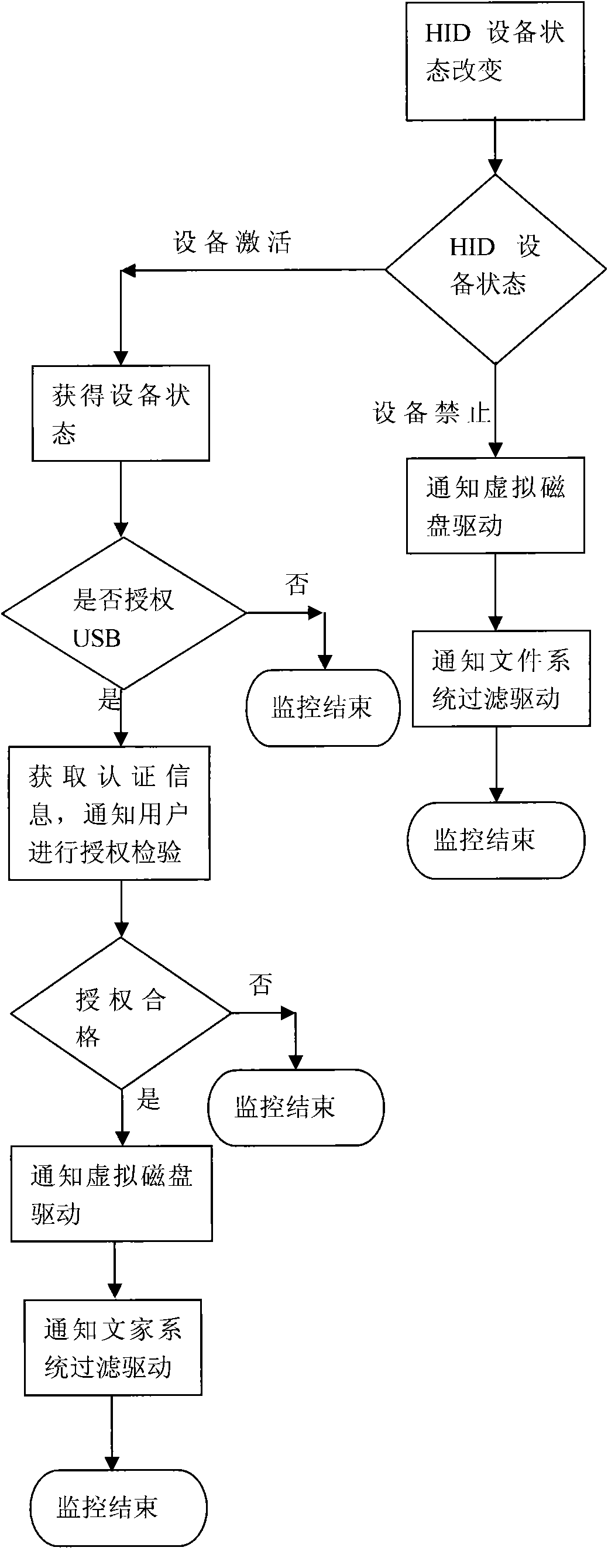
[0035] figure 1 In , applications and user operations interact with the system file interface, and the system file interface converts the request into a kernel state file service request. These requests are first sent to the file system driver, the file system driver transfers the request to the file system filter driver, and the filter driver filters the file request, the unauthorized file request will be directly rejected, and then the authorized request is distributed to the corresponding disk Device driver; after the virtual disk receives the access request, it maps the request and then transfers it to the actual disk driver; the filter driver and the virtual disk driver operate according to the current state of the HID USB Key. If the Key does not e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com