Anonymization method for reserving network address prefix combining bit string and hash function
A technology of hash function and network address, which is applied in the field of anonymization of network address prefix reserved by the combination of bit string and hash function. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
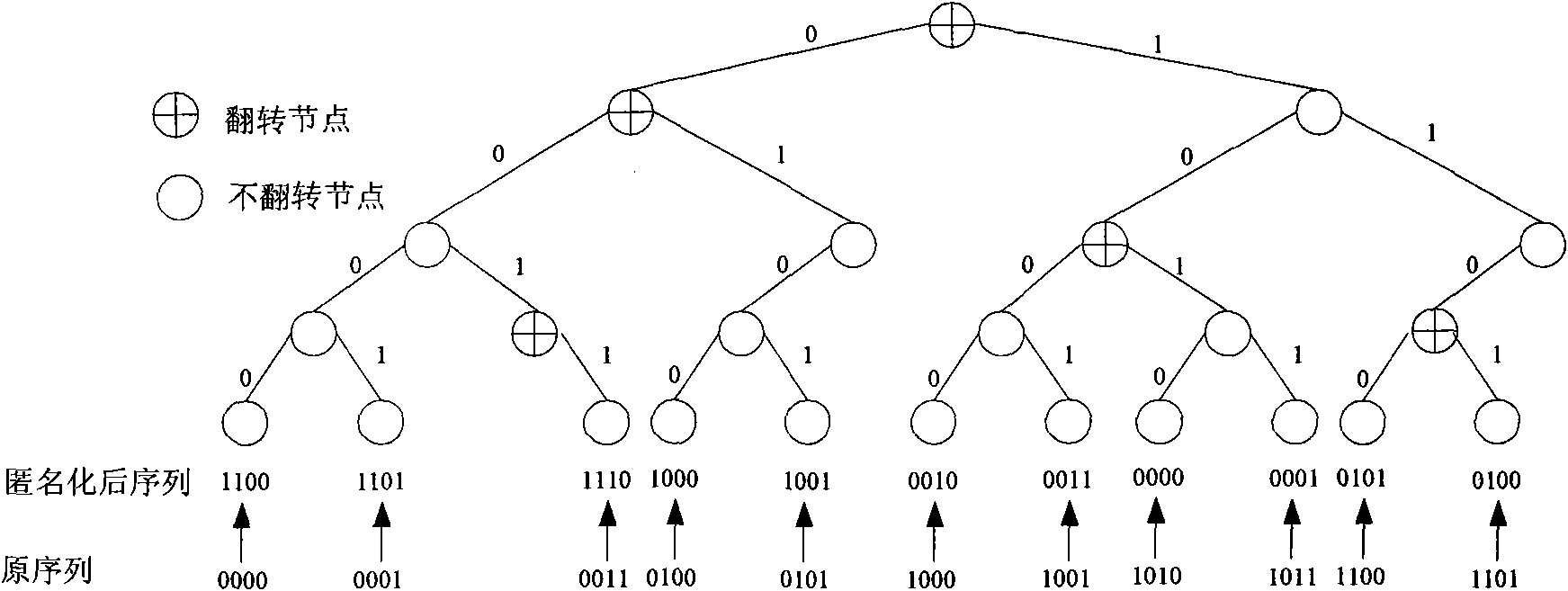
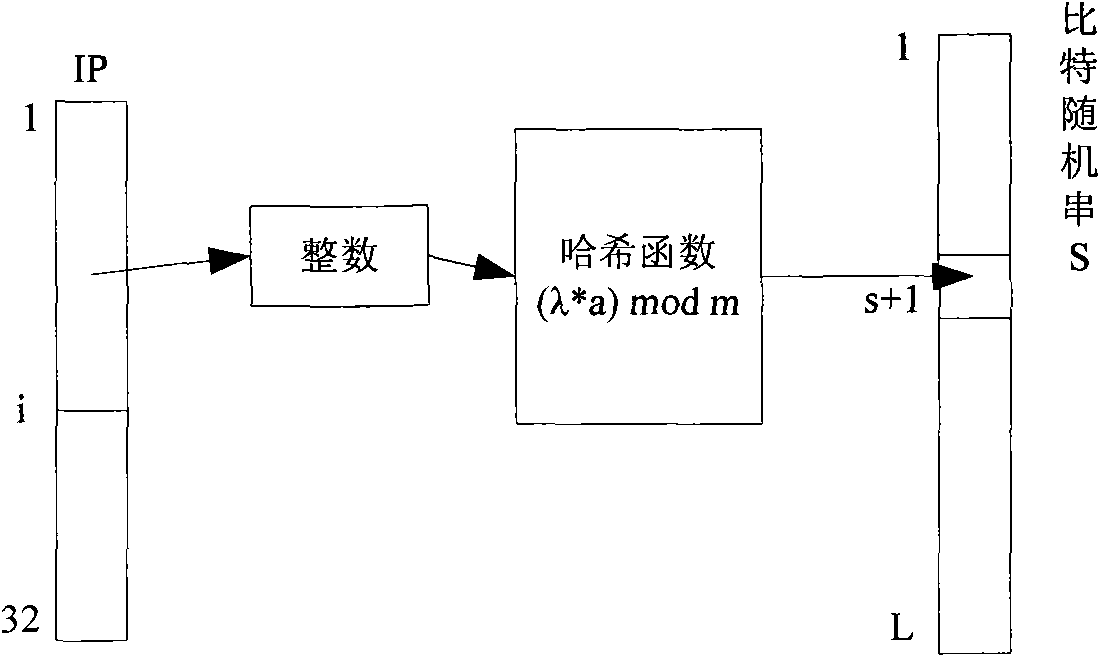
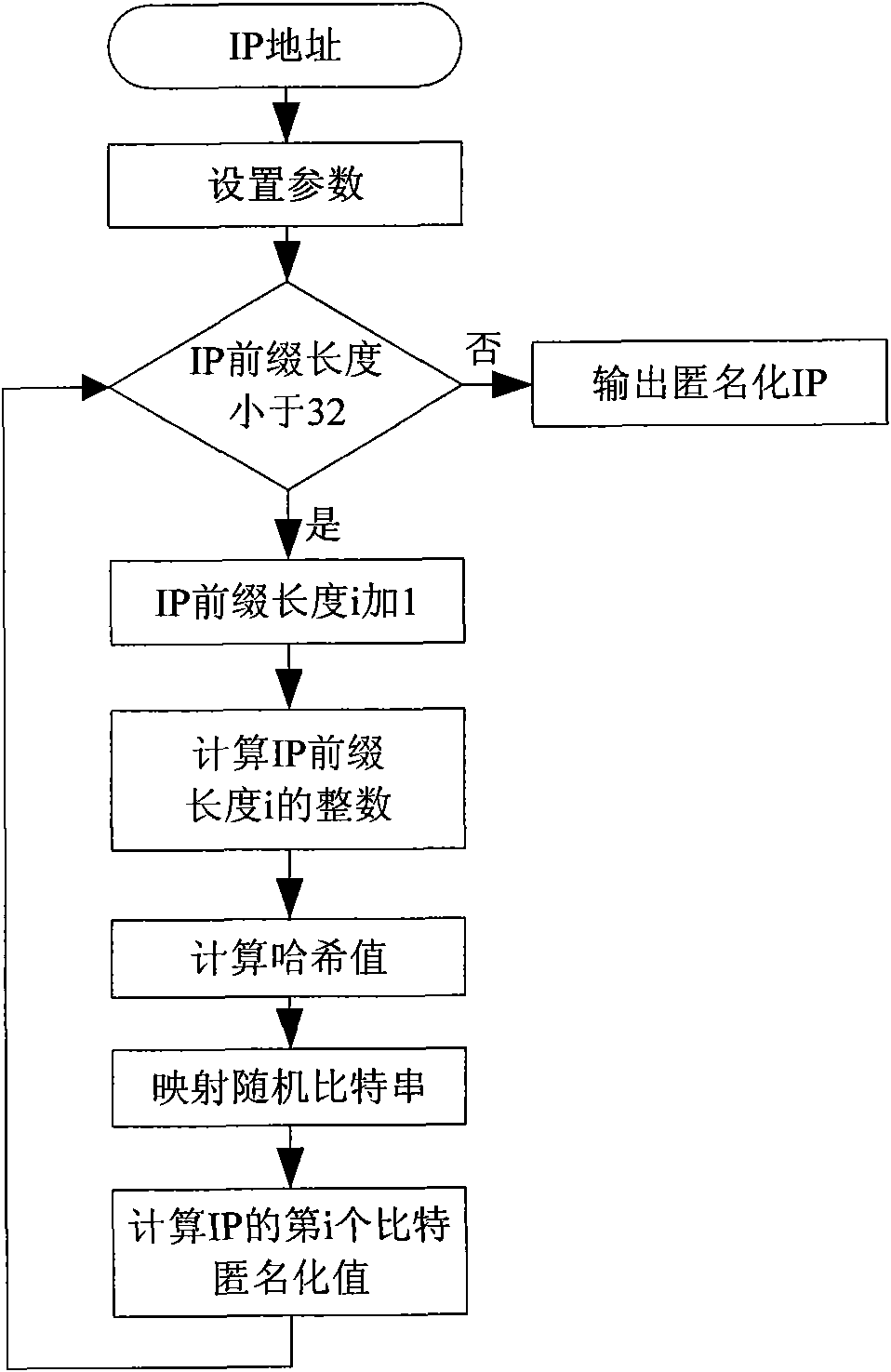
[0039] An anonymization method for network address prefix retention combining a bit string and a hash function, characterized by defining an address prefix hash function that takes the decimal integer corresponding to the IP address prefix bit string as input, and a random bit string, address The prefix hash function generates a hash value from the IP address prefix bit string whose IP address prefix length is i, and then finds the bit value at the corresponding hash value position on the random bit string, and matches the bit value with the IP address that needs to be anonymized. The i-th bit of the address is XORed, and the result after the XOR is taken as the anonymized bit of the i-th bit of the IP address. The specific technical steps for anonymizing IP addresses are as follows:
[0040] Step 1: Set parameters
[0041] Set a random bit string S of length L, where L is a positive integer greater than or equal to 32, define an address prefix hash function as (λ·a) mod m, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com