Access control verification method based on two-dimensional code
A verification method and two-dimensional code technology, which is applied to instruments, time registers, single input port/output port registers, etc., can solve the problems of difficult statistics of personnel access, potential safety hazards, and low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] In order to make the above objects, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below in conjunction with the accompanying drawings.
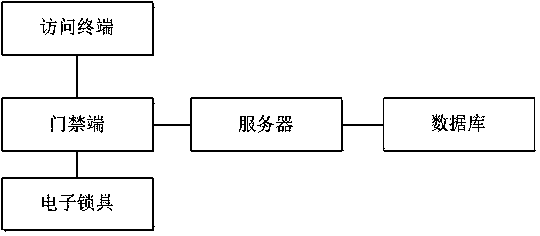
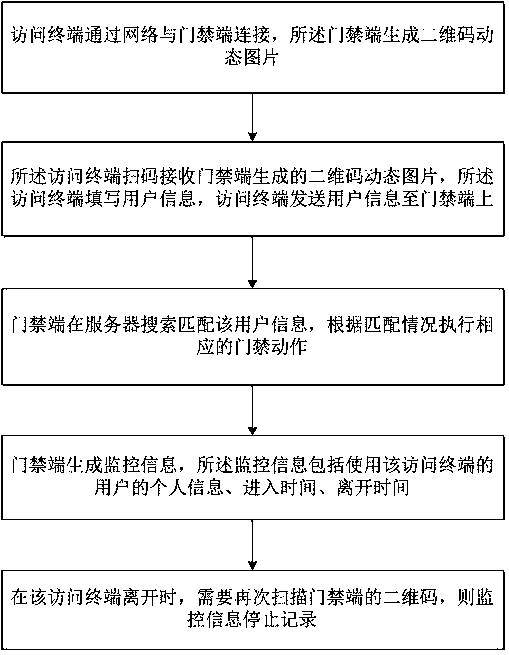
[0017] see figure 1 , an access control verification method based on a two-dimensional code, including an access terminal, a server, an access control terminal, an electronic lock set on the door, and a database storing multiple user information, the access terminal is connected to the access control terminal through a network, and the access control terminal Generate a QR code dynamic picture, and the access control terminal is equipped with a display screen. After the access terminal is connected to the access control terminal through the network, the access terminal can send an access request to the access control terminal, and the access control terminal generates a dynamic QR code image after receiving it, and displays it screen d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com