Block chain authority management method and system
A permission management and blockchain technology, applied in the blockchain field, can solve problems such as uncontrollable and flood attacks, and achieve the effect of facilitating auditing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
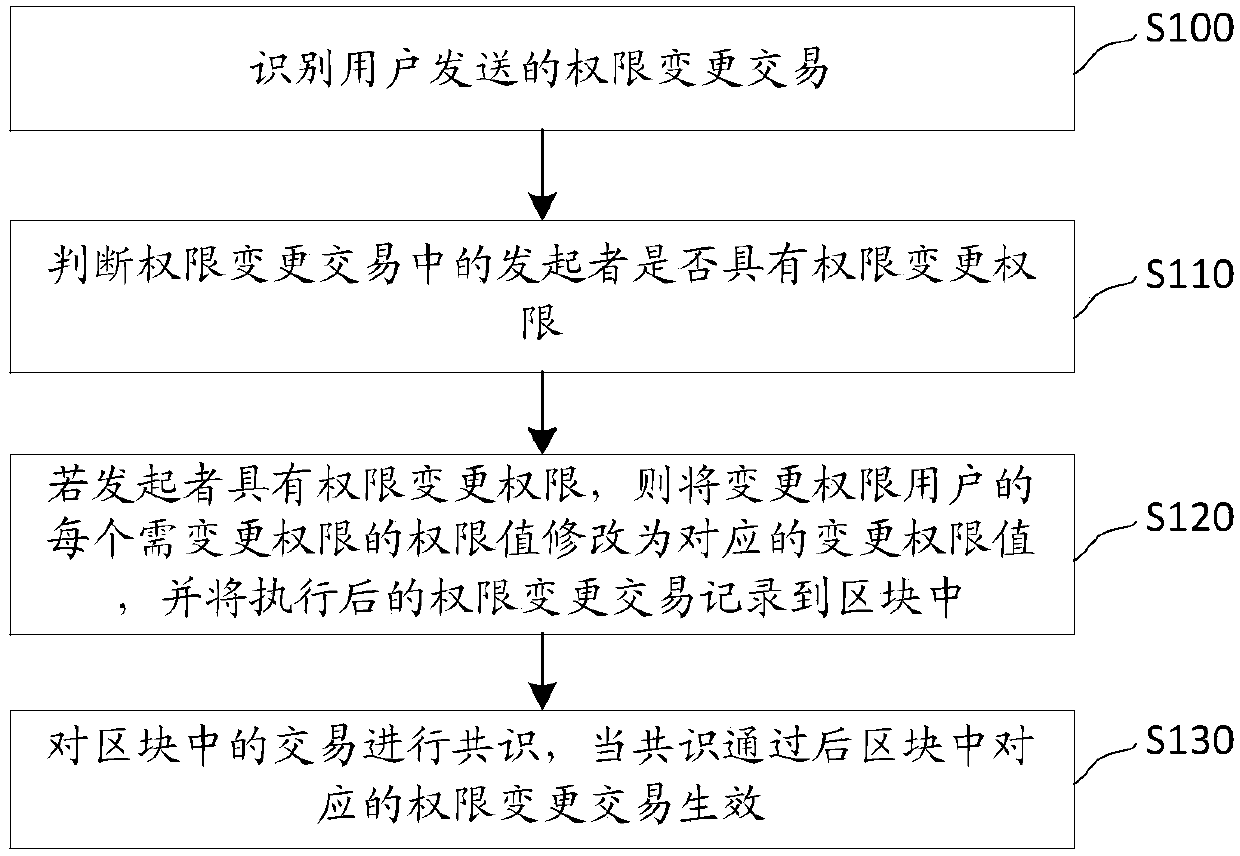
[0089] Among them, the permission information corresponding to this judgment method is stored in the smart contract. The specific implementation is as follows:
[0090] 1. Writing a smart contract is called a permission smart contract.
[0091] 2. Write the permission smart contract into the genesis block.
[0092] 3. Assign a specific address to the permission smart contract.
[0093] After the above steps, the permission information will be saved in the storage area (storage) of the permission smart contract. Changes to permission information will result in changes to the contract storage area, resulting in changes to the state tree (State Trie), resulting in changes to the hash of the block. In this embodiment, the state tree can be used as verification information of permissions. Due to the adoption of the smart contract, external users can directly call the interface in the smart contract to query the permission information. It is exactly the same as the ordinary sma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com