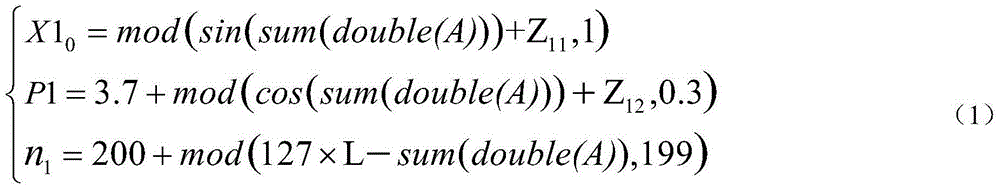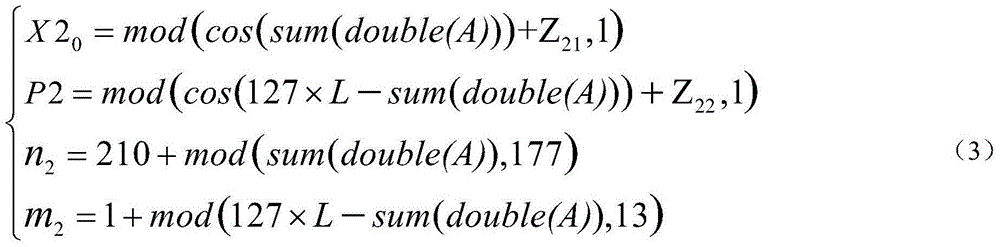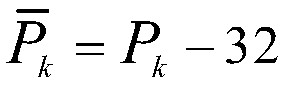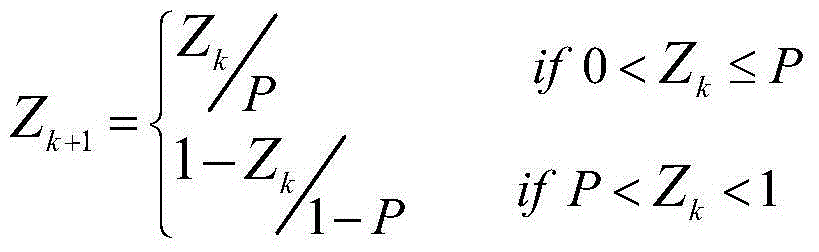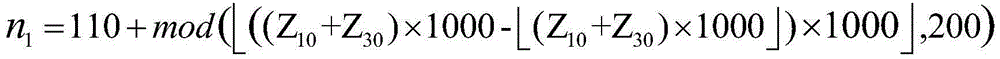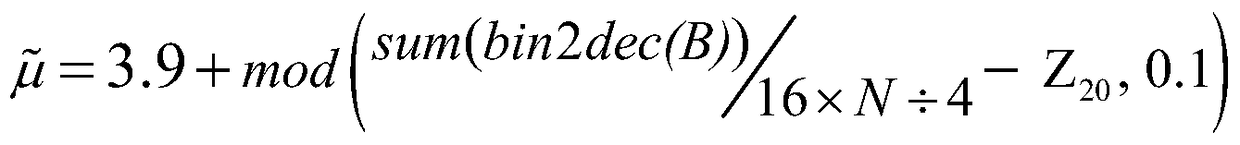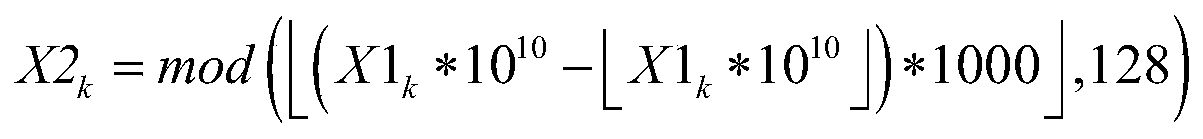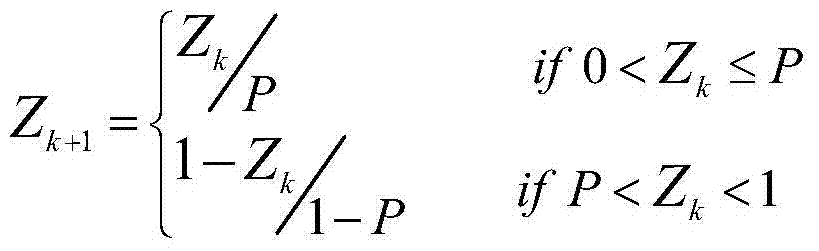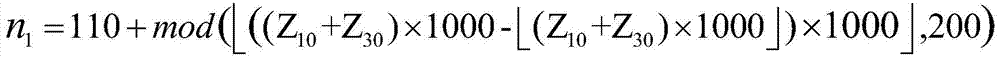Patents
Literature
47results about How to "Guaranteed unforgeability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
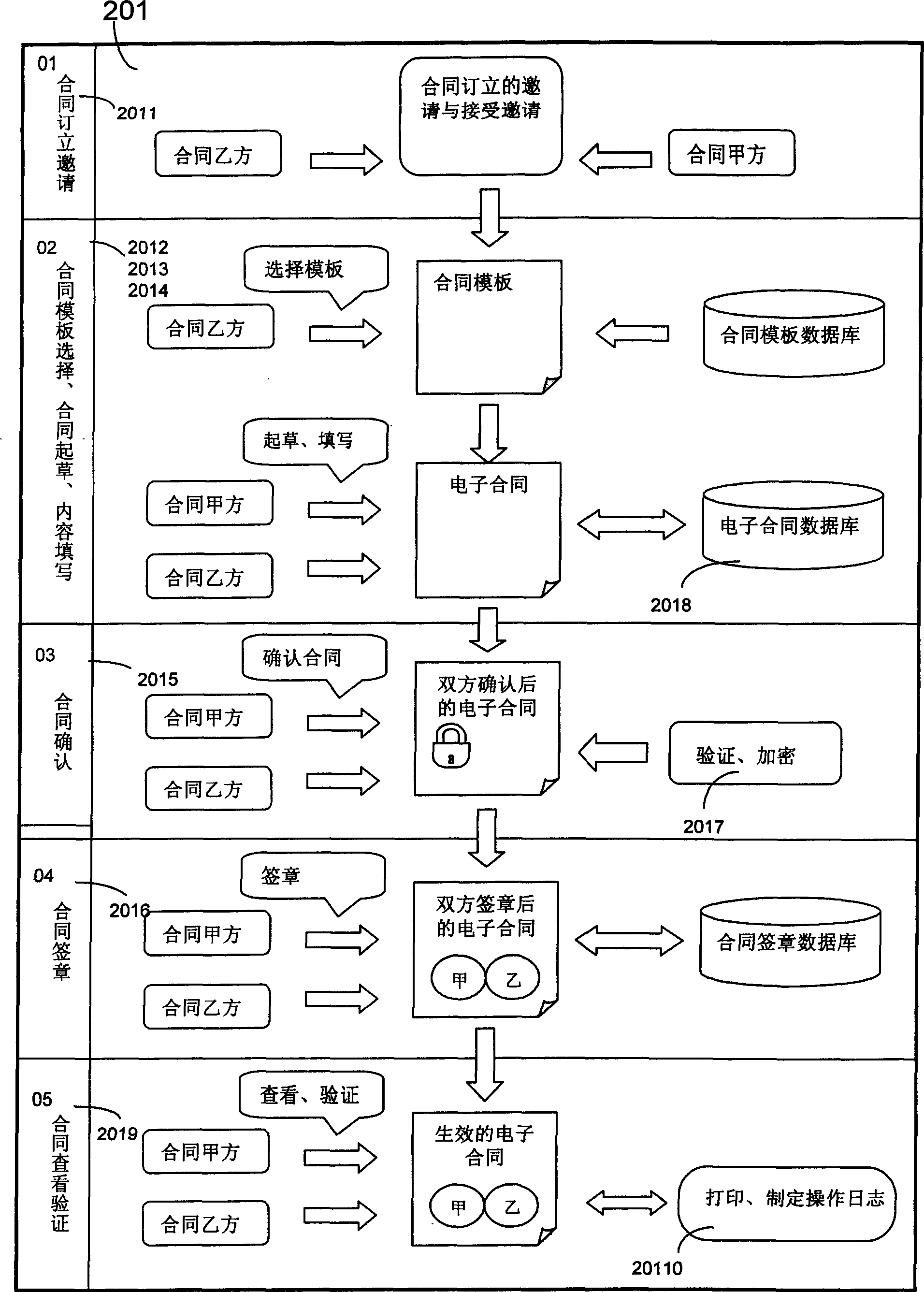
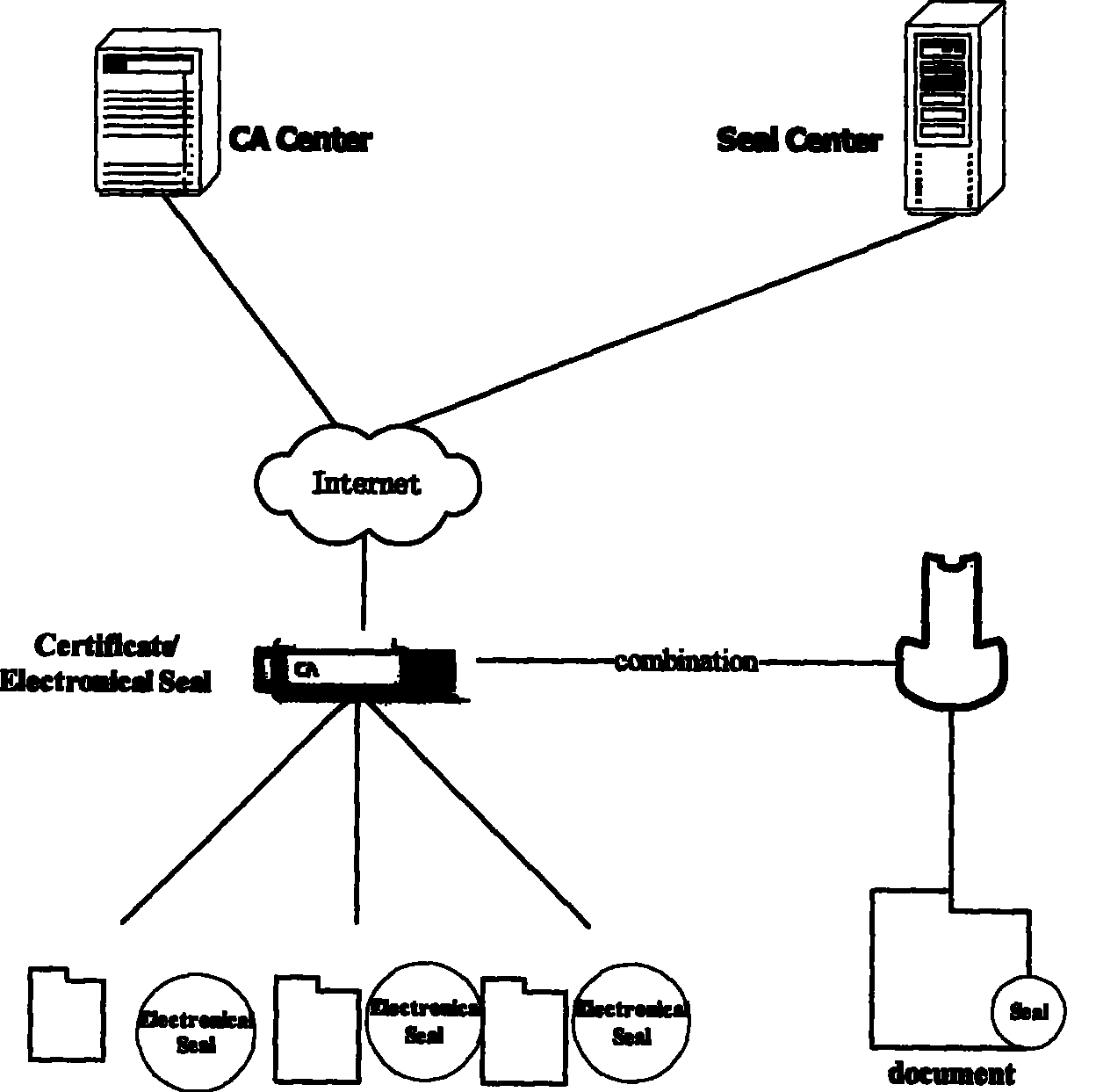
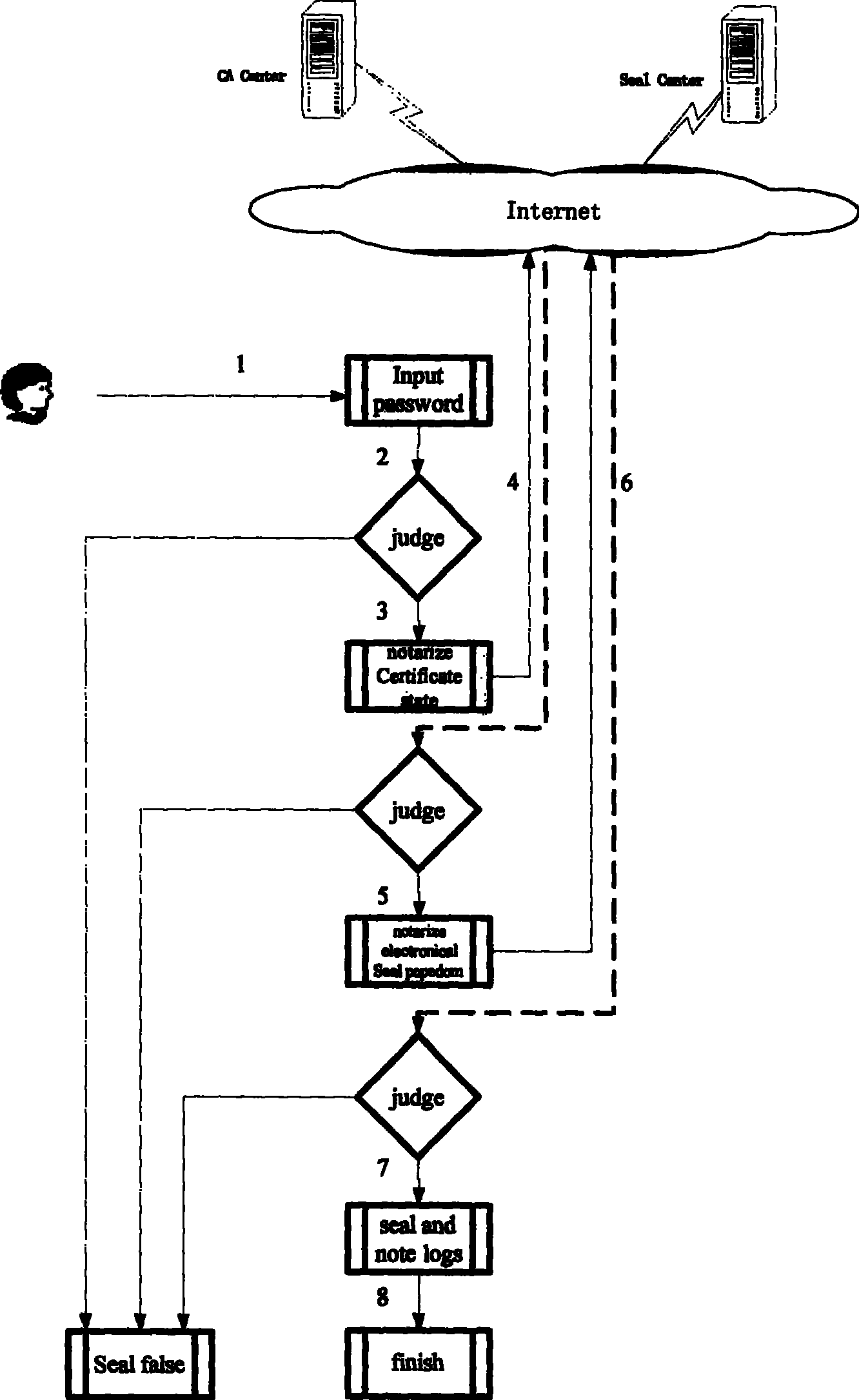
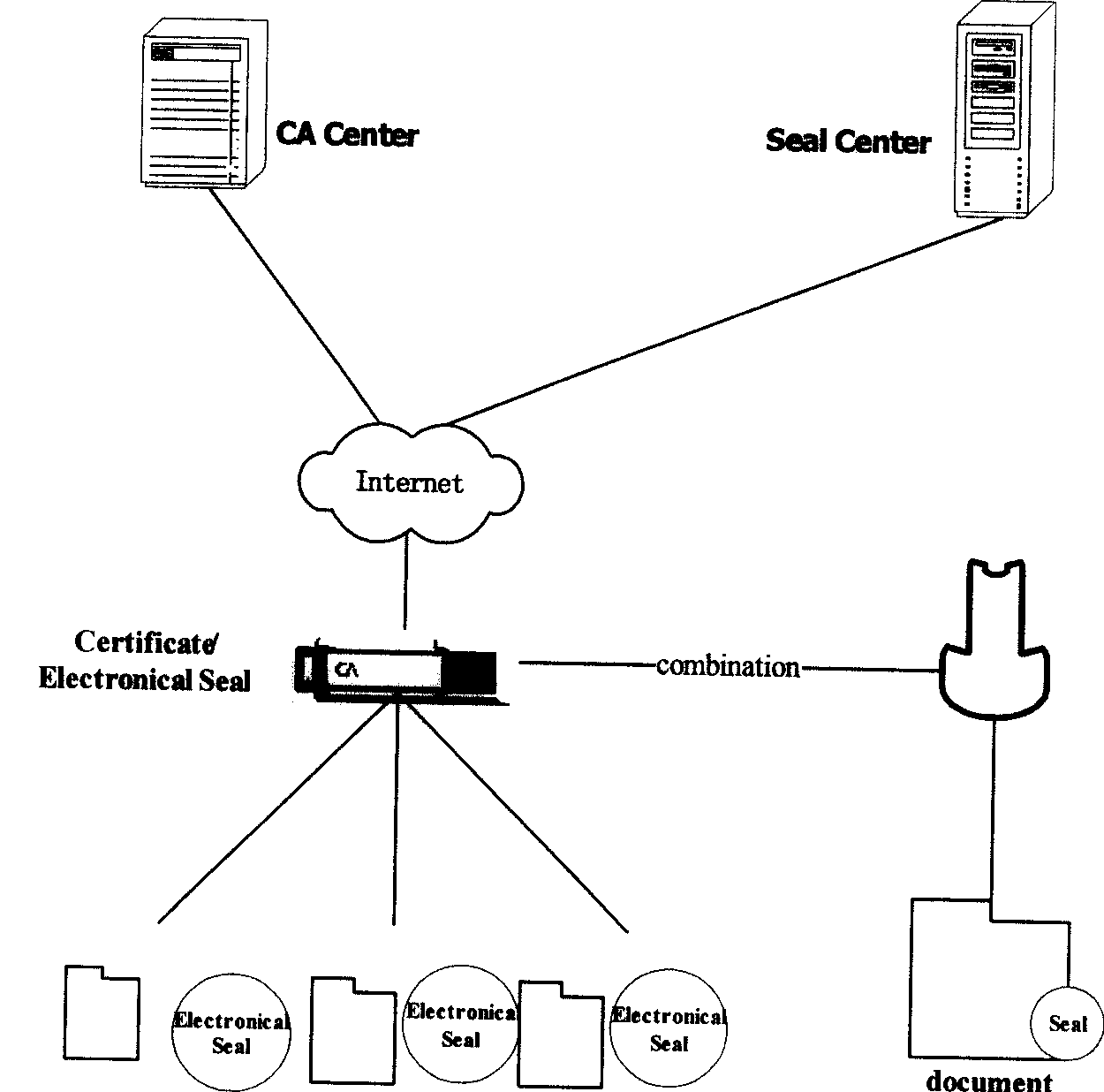
Conflated seal affix authentication method having electronic seal digital certification
InactiveCN101017544AEnsure unforgeableEnsure non-repudiationComputer security arrangementsOffice automationElectronic documentAffix
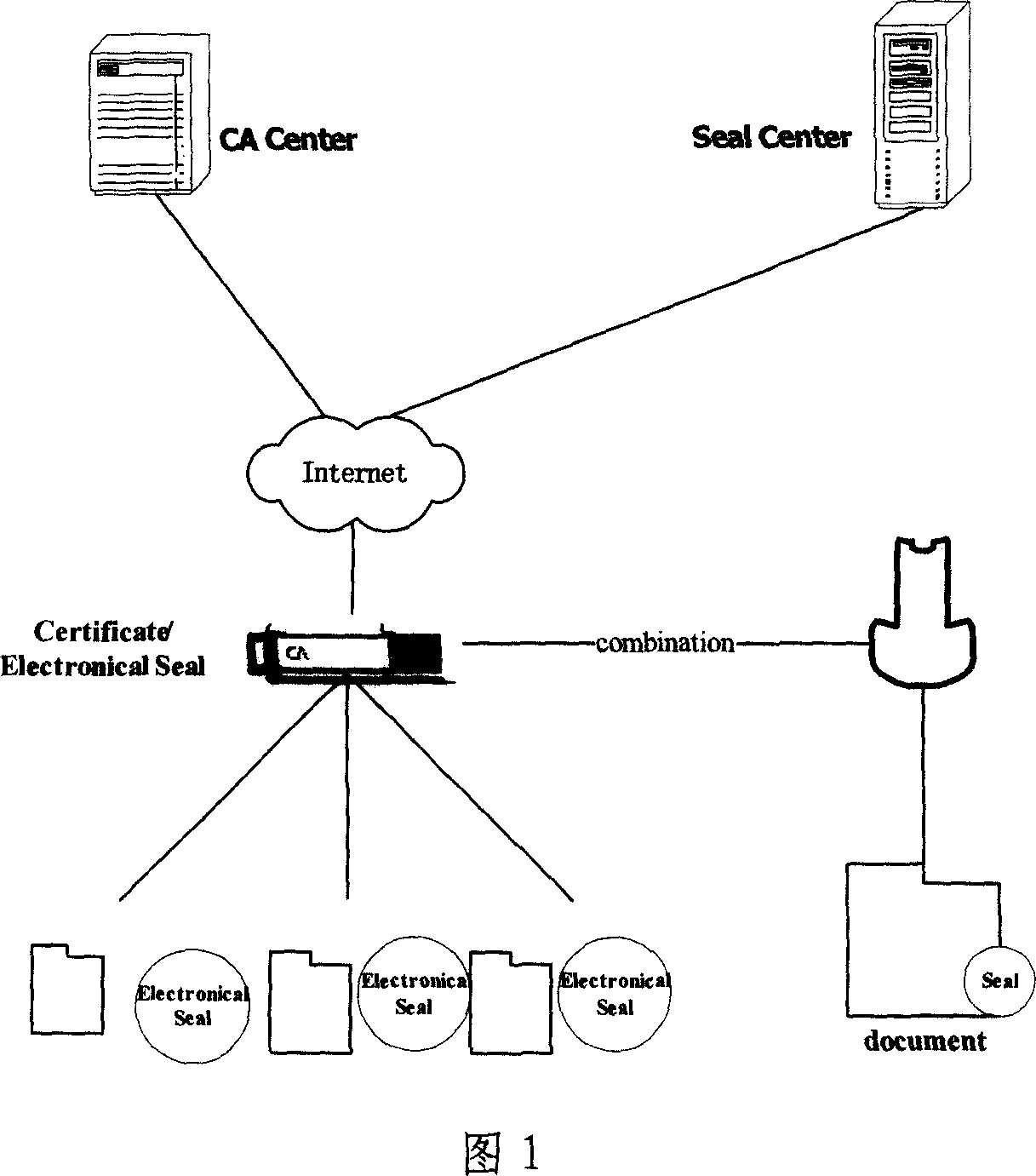
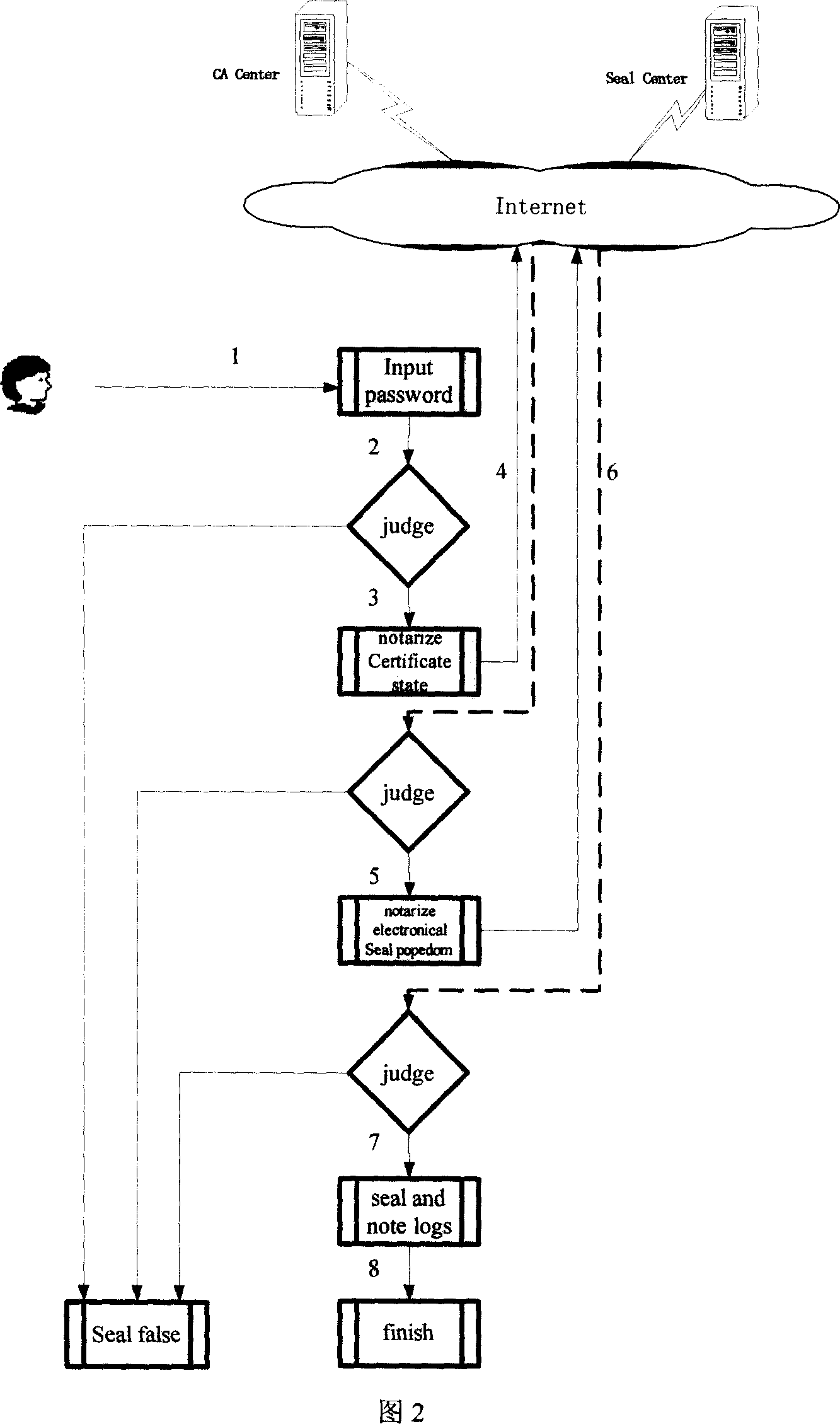
This invention relates to one legal seam signature method with electron stamp digital certificate in network identification technique field, which comprises the following steps: through opening, requiring, determining, transferring, sending and stamping steps to realize legal stamp, stamp customer end and servo, CA center certificate servo electron stamp signature operation; through receiving, separating, comparing to realize customer end and stamp servo validating steps to ensure the electron stamp and physical body integral part with combination by traditional physical stamp and modern digital certificate.
Owner:江苏国盾科技实业有限责任公司
Electronic contract managing system operation platform
InactiveCN1858793AEasy to manageEasy to divide authorityOffice automationElectronic contractsClient-side
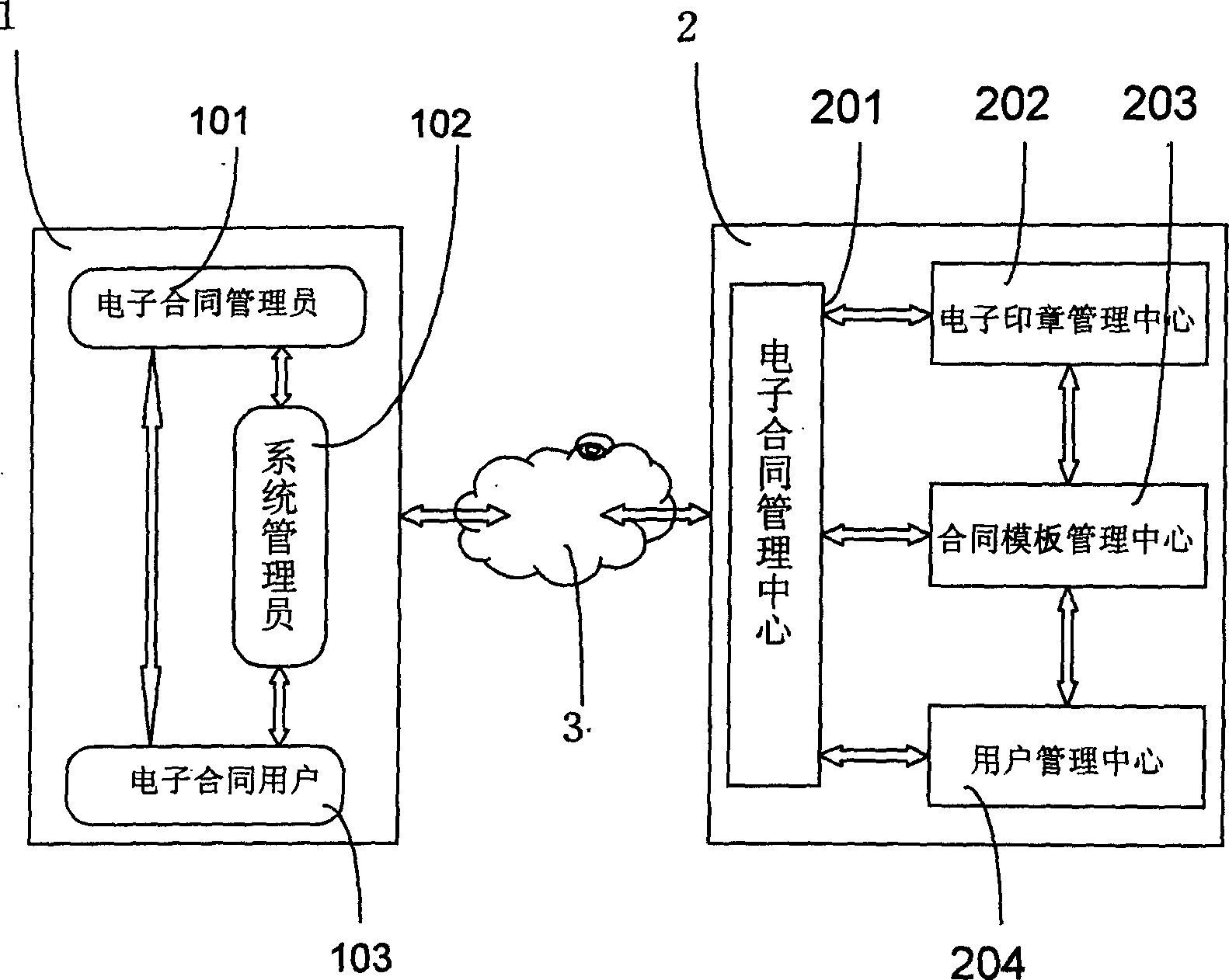
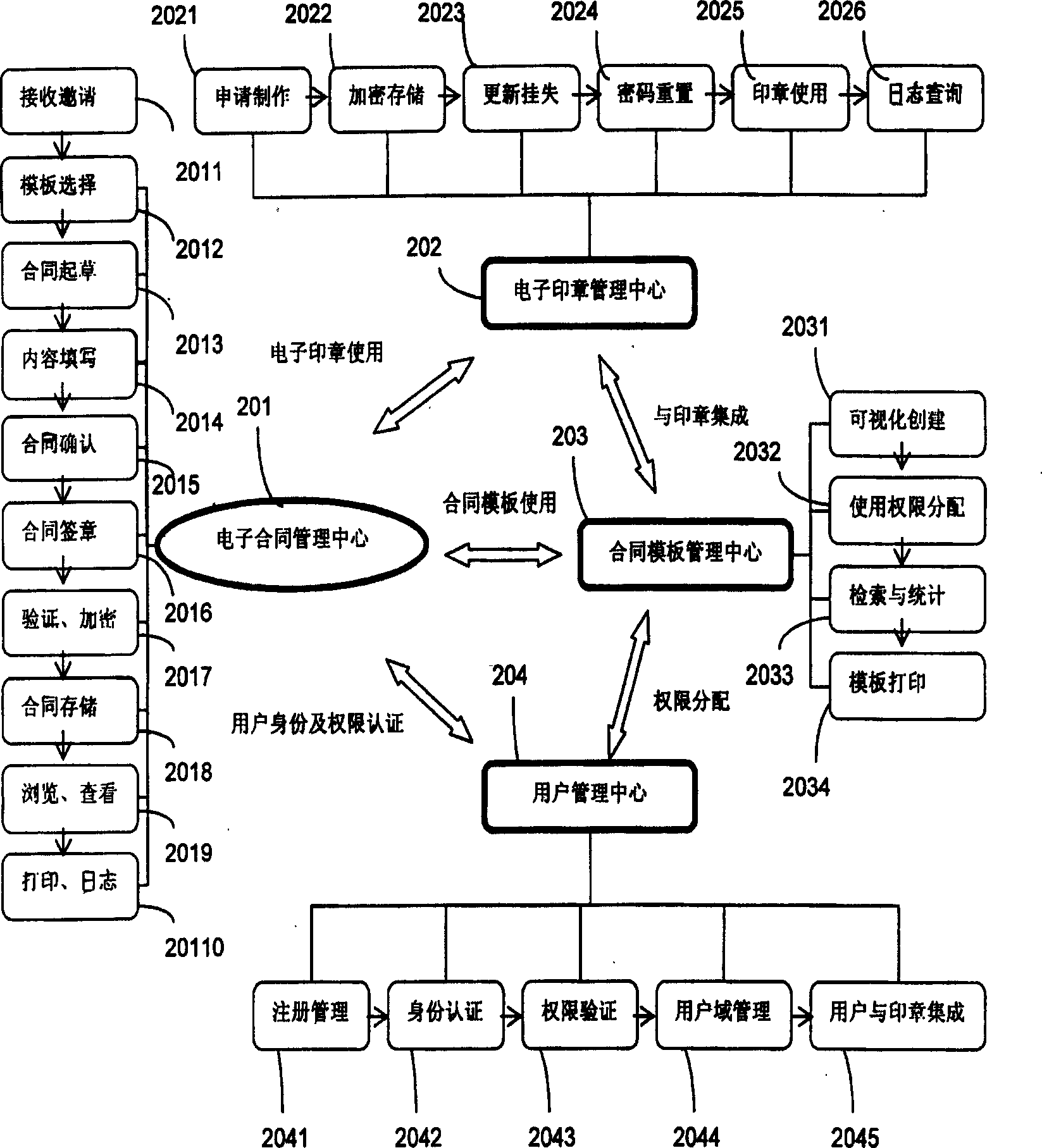
An operational platform for electronic contract management system includes a customer end and a server end mutually connected in network, in which, the server end includes: an electronic print center module, a contract template management center module and a user management center module mutually connected with the electronic contract management center module as the center, the customer end includes: a system manager module, an electronic contract manager module and an electronic contract user module mutually connected, the operation platform is completely based on the convenient and transparent network electronic contract solving plan, the electronic stamp is ciphered and integrated with intelligent key plates, the contract template is made dynamically by the template designer sawn and got according to the requirement of the user, the integrated cipher and digital waterprint cipher of the print of the enterprise, the personal print and handwriting signature guarantees the print un-fabricated.
Owner:孟繁波 +1
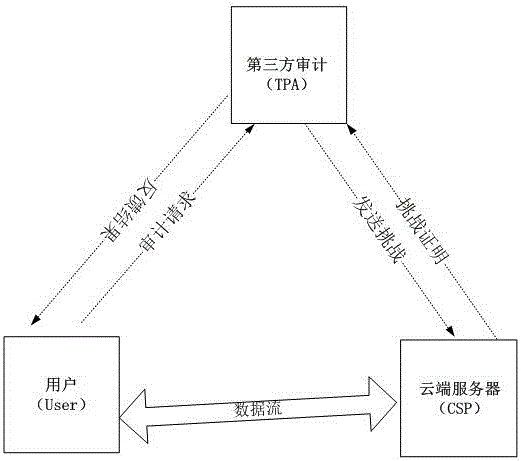
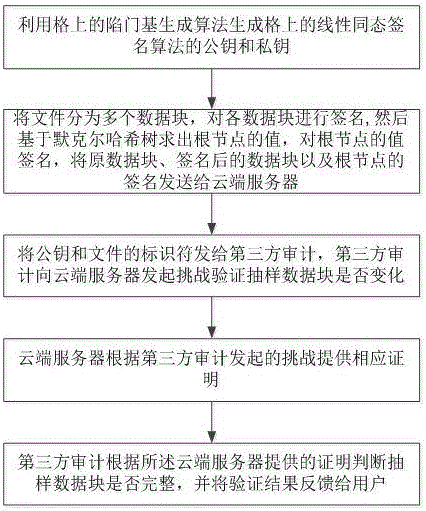
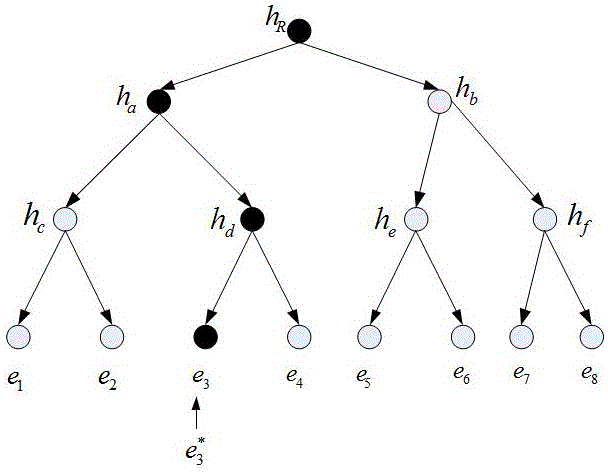
Dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures
ActiveCN106301789AGuaranteed unforgeabilityImprove computing efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyData integrity
The invention discloses a dynamic verification method of cloud storage data using lattice-based linearly homomorphic signatures. The method comprises data integrity verification including: a public key and a private key of a linearly homomorphic signature algorithm on a lattice are generated, a file is divided into a plurality of data blocks, each data block is signed, the value of a root node is calculated on the basis of a Merkle hash tree, the value of the root node is signed, and the data blocks, signatures of the data blocks and a signature of the root node are sent to a cloud server; IDs of the public key and the file are provided for a third-party audit, which initiates a challenge to the cloud server to verify whether the data blocks changed or not; the cloud server provides corresponding proof for the challenge initiated by the third-party audit; and the third-party audit judges whether the data blocks are complete according to the proof provided by the cloud server and feeds a verification result to a user. The method can resist quantum attacks initiated by quantum computers in the future and support cloud dynamic operation verification while protecting user private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
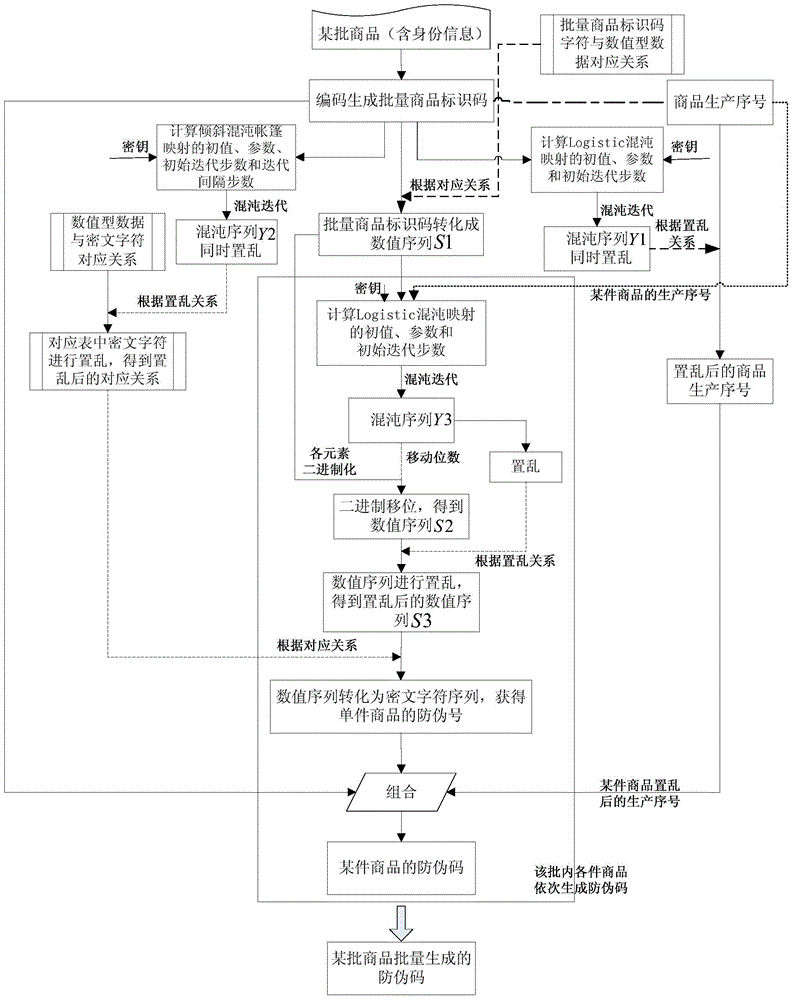
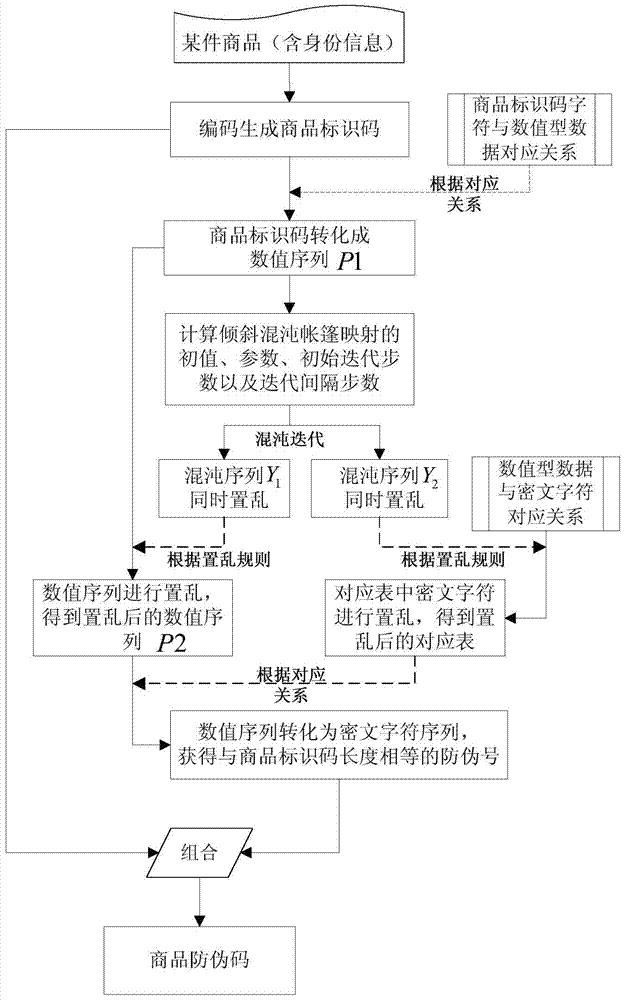
Commodity anti-counterfeiting code batch generation method
InactiveCN104680220ABatch generation method is simple and feasibleUniqueness guaranteedRecord carriers used with machinesCiphertextNumeric data
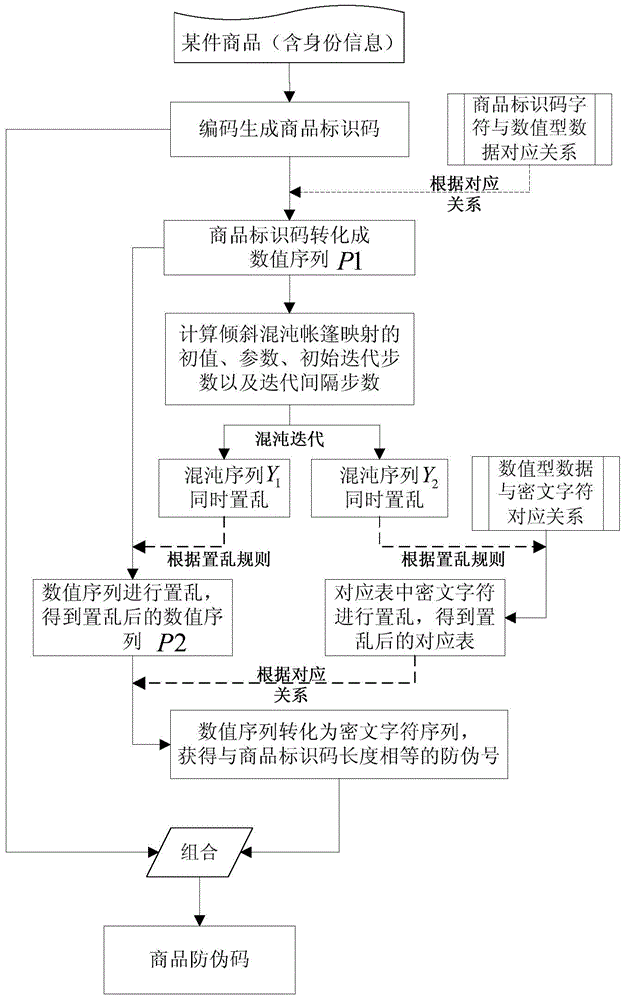
The invention discloses a commodity anti-counterfeiting code batch generation method which comprises the following steps: encoding identity information of a certain batch of commodities to generate a batch of commodity identification codes and setting a commodity production-sequence-number numerical sequence with a certain length; according to a corresponding relation of custom batch commodity identification code characters and numeric data, converting the batch of commodity identification codes into a numerical sequence; respectively carrying out scrambling on ciphertext characters in a corresponding relation among the production-sequence-number numerical sequence, the custom numeric data and the ciphertext characters of a certain batch of commodities by utilizing a position variation scrambling rule before and after chaos sequences are sorted; enabling each commodity in the batch of commodities to sequentially carry out displacement and scrambling on the transcoded numerical sequence according to the corresponding chaos sequences and the position variation scrambling rule before and after the chaos sequences are sorted and generating an anti-counterfeiting number of each commodity so as to combine and produce commodity anti-counterfeiting codes in batch. The method disclosed by the invention is simple and easy to operate, has high safety and is unlikely to crack; the commodity anti-counterfeiting codes generated in batch have uniqueness and unforgeability.
Owner:NANTONG UNIVERSITY
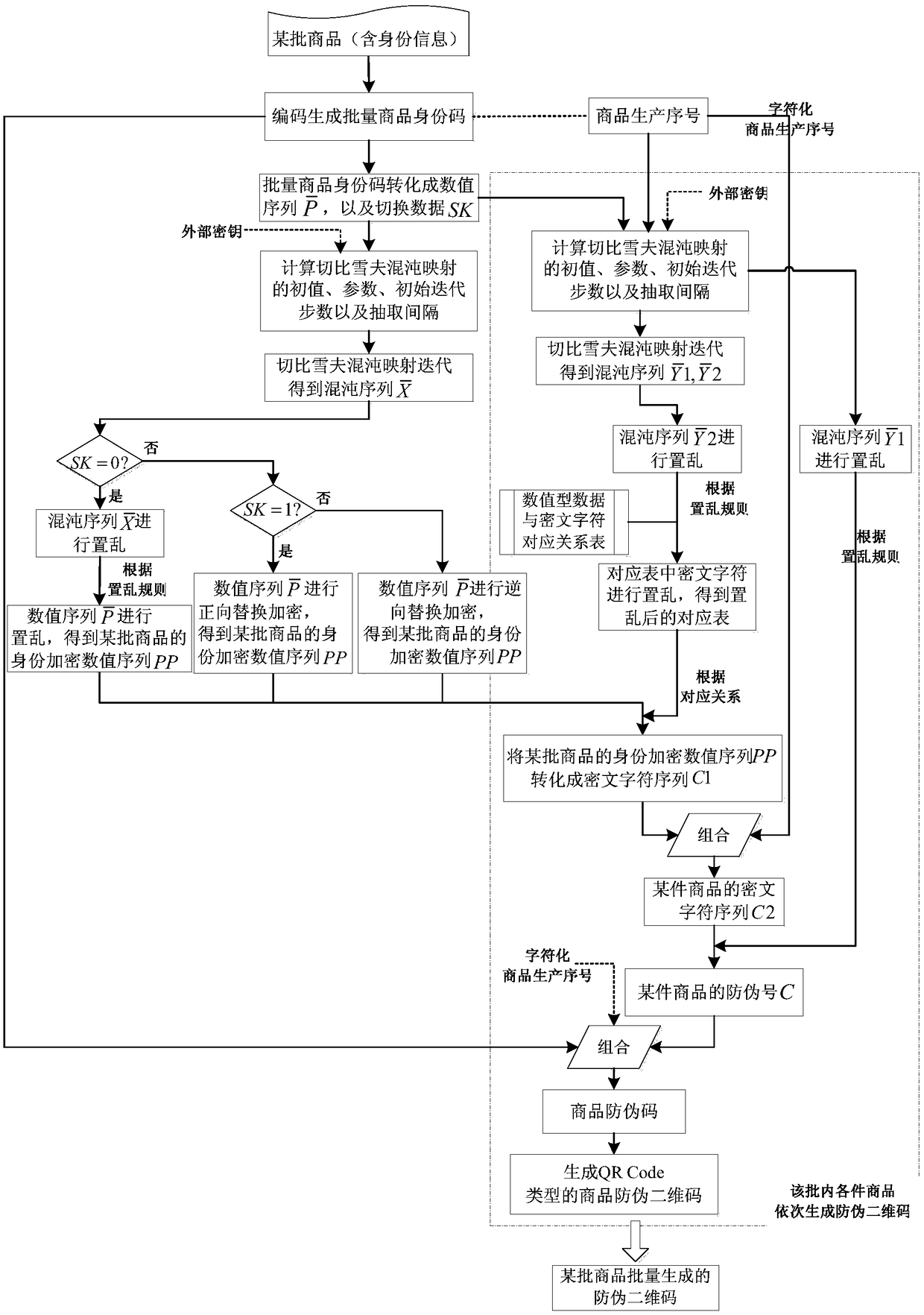
A method for batch generation of commodity anti-counterfeit two-dimensional code
ActiveCN109472338AUniqueness guaranteedGuaranteed unforgeabilityKey distribution for secure communicationSecuring communication by chaotic signalsCiphertextDimensional modeling
The invention discloses a batch generation method of commodity anti-counterfeit two-dimensional code, which comprises the following steps: encoding the identity information of a certain batch of commodity to generate batch commodity identity code; The batch commodity identification code is converted into numerical data, and the switching data is calculated; The chaotic sequence is generated by iterating the Chebyshev chaotic tent map with batch commodity identity information and external key, and some operations are selected respectively according to the switching data. A Chebyshev chaotic tent map is iteratively generate into a chaotic sequence by using a single commodity generate serial number and an external key, According to the scrambling rule of the position change, the cipher character sequence and the cipher character sequence converted according to the scrambled correspondence and the character-based commodity production serial number are scrambled respectively, and then the commodity anti-counterfeit two-dimensional code is combined and generated in batch. The method provided by the invention is simple and feasible, has strong safety, is not easy to crack, and the commodity anti-counterfeit code generated in batch has 'uniqueness and non-forgery'.
Owner:NANTONG UNIVERSITY
Generation method of commodity anti-counterfeiting code
InactiveCN104657871AThe generation method is simpleUniqueness guaranteedCommerceCiphertextChaotic systems
The invention discloses a generation method of a commodity anti-counterfeiting code. The generation method comprises the following steps: coding commodity identity information according to a certain preset rule to generate a unique commodity identification code; converting the commodity identification code into numeric data according to corresponding relation between a user-defined commodity identification code character and numeric data; respectively calculating by virtue of the commodity identity information and an external secret key to obtain an initial value, a parameter, a primary iteration step number and an iteration interval step number of a chaotic system, and carrying out iteration on an inclined chaos tent map to generate two groups of chaos sequences; respectively scrambling ciphertext characters in the corresponding relation among numeric data, user-defined numeric data and the ciphertext characters by virtue of a location changing scrambling rule before or after the sequencing of two groups of the chaos sequences to generate commodity anti-counterfeiting numbers, and combining to generate the commodity anti-counterfeiting code. The generation method of the commodity anti-counterfeiting code is simple and feasible, has very high security and does not easily hacked, and the generated commodity anti-counterfeiting code has uniqueness and unforgeability.
Owner:NANTONG UNIVERSITY
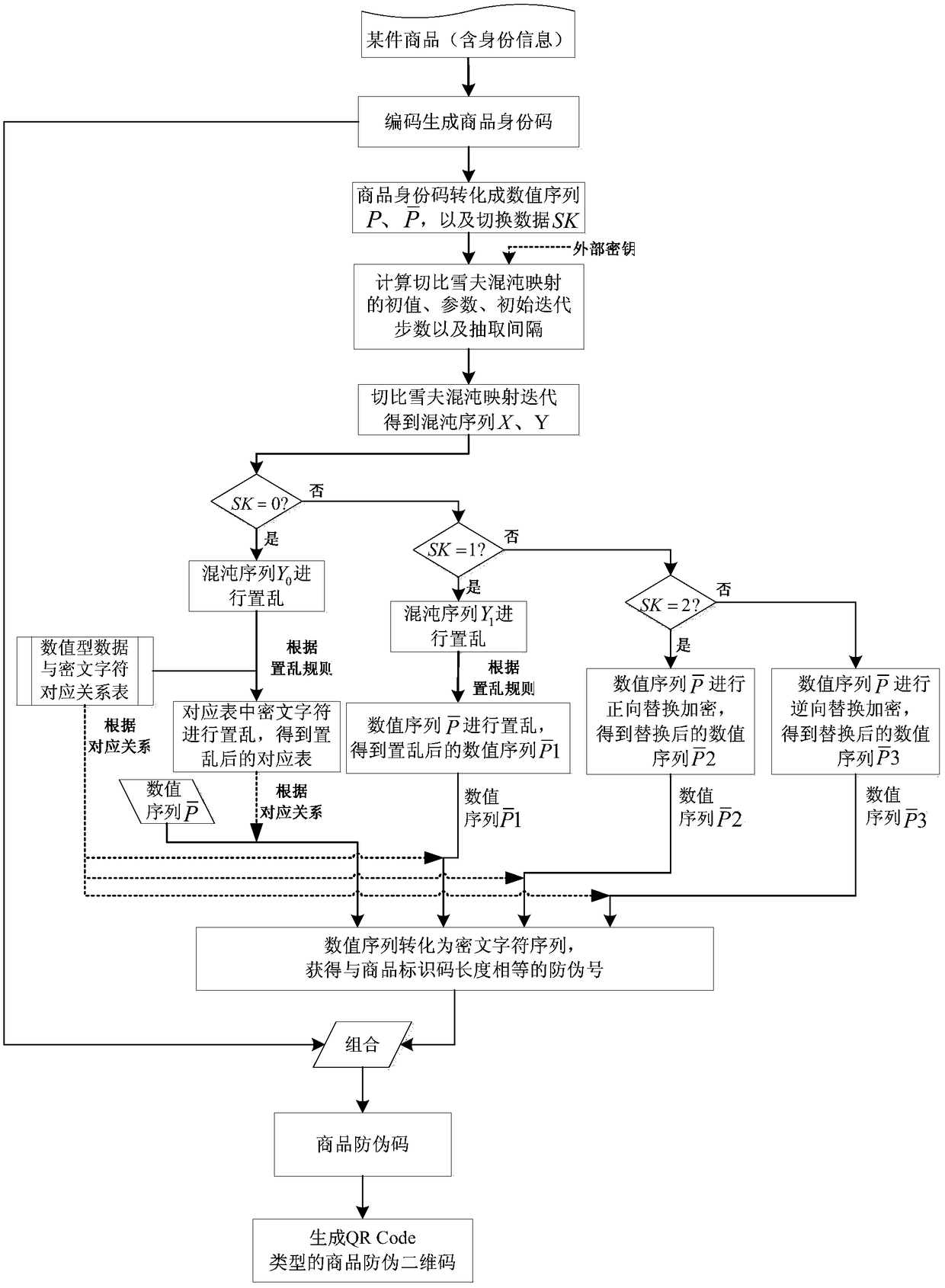
A method for generating commodity anti-counterfeit two-dimensional code
ActiveCN109284803AThe generation method is simpleUniqueness guaranteedRecord carriers used with machinesCiphertextChaotic systems
The invention discloses a method for generating a commodity anti-counterfeit two-dimensional code, which comprises the following steps: coding commodity identity information to generate a unique commodity identification code; converting the commodity identification code into numerical data and switching data; the initial value, parameters, initial iterative steps and iterative interval steps of the chaotic system are calculated by using commodity identity information and external key respectively, and the chaotic sequence is generated by iterating the Chebyshev chaotic tent map. According to the switching data, a certain operation is selected respectively, and the cipher characters in the corresponding relation table between the user-defined numerical data and the cipher characters are scrambled by using the scrambling rule of the position change before and after the chaotic signal sorting, thereby the commodity anti-counterfeit number is generated, and then the commodity anti-counterfeit two-dimensional code is combined to generate the commodity anti-counterfeit code. The method for generating that commodity anti-counterfeit two-dimensional code provided by the invention is simpleand feasible, has strong safety, is difficult to crack, and the generate commodity anti-counterfeit two-dimensional code has uniqueness and non-forgery.
Owner:NANTONG UNIVERSITY
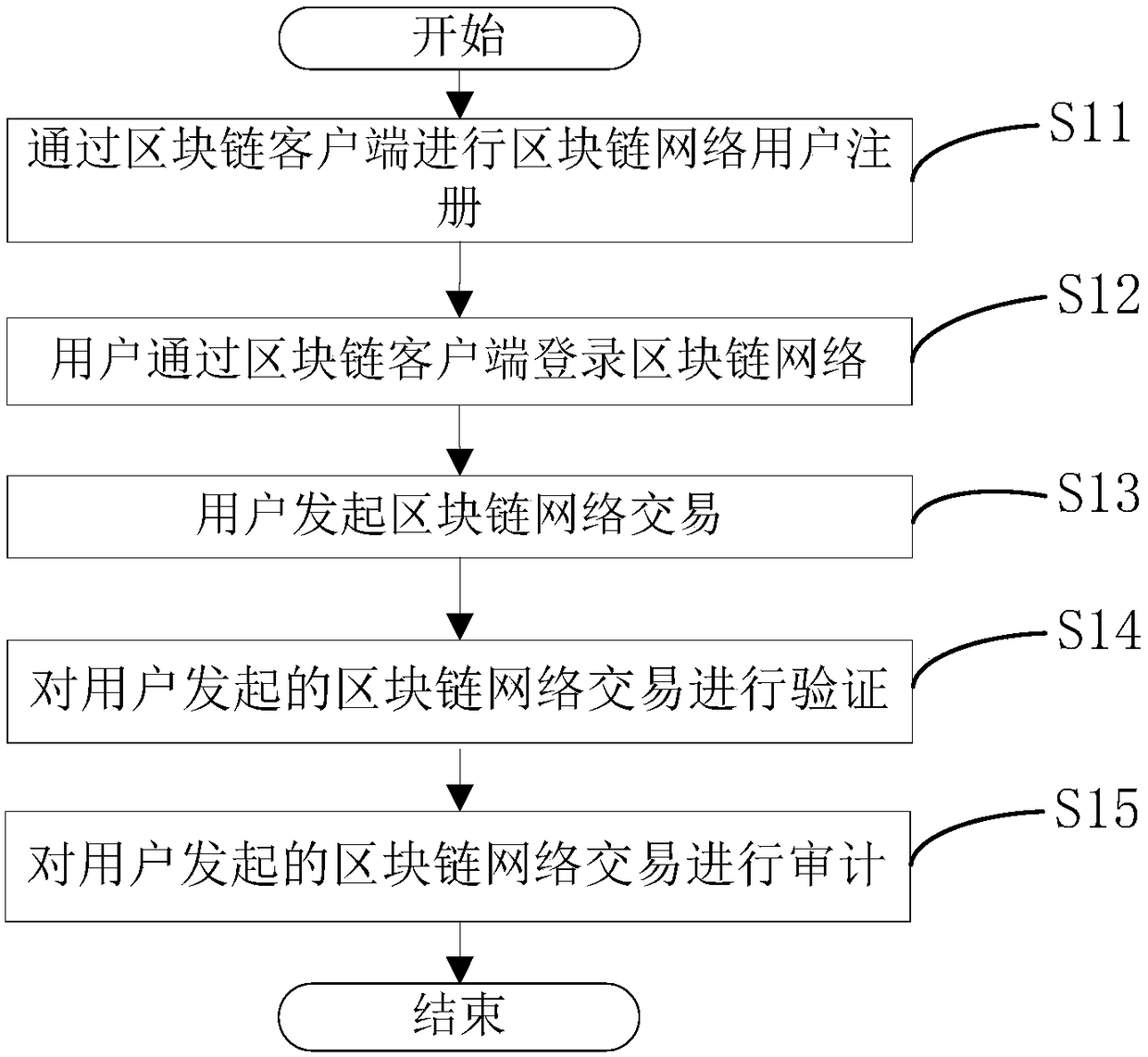
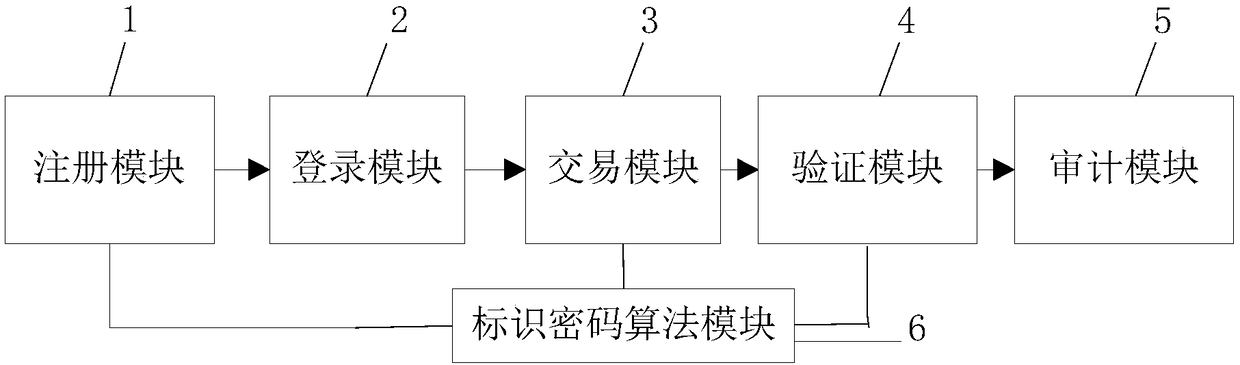
A block chain member management method and system based on an identification cryptographic algorithm
ActiveCN109005036AReduce complexityGuaranteed unforgeabilityKey distribution for secure communicationUser identity/authority verificationChain networkBlockchain
The invention relates to a block chain member management method and system based on an identification cryptographic algorithm. The method of the invention comprises the following steps: (1) registering a user of a block chain network through a block chain client, and generating a signature private key according to the user identity information by using an identification cryptographic algorithm; (2) loging in the block chain network through the block chain client by a user; 3) initiating a block chain network transaction by the user, and using an identification cryptographic algorithm to sign adigital summary of the transaction calculated by the user's block chain client end to generate signature information; (4) verifying the block chain network transaction initiated by the user, and verifying the correctness of the signature of the block chain network transaction by using the identification cryptography algorithm. The method and the system of the invention can reduce the complexityof the management of the members in the block chain network and facilitate the audit of the transaction.
Owner:WATCHDATA SYST
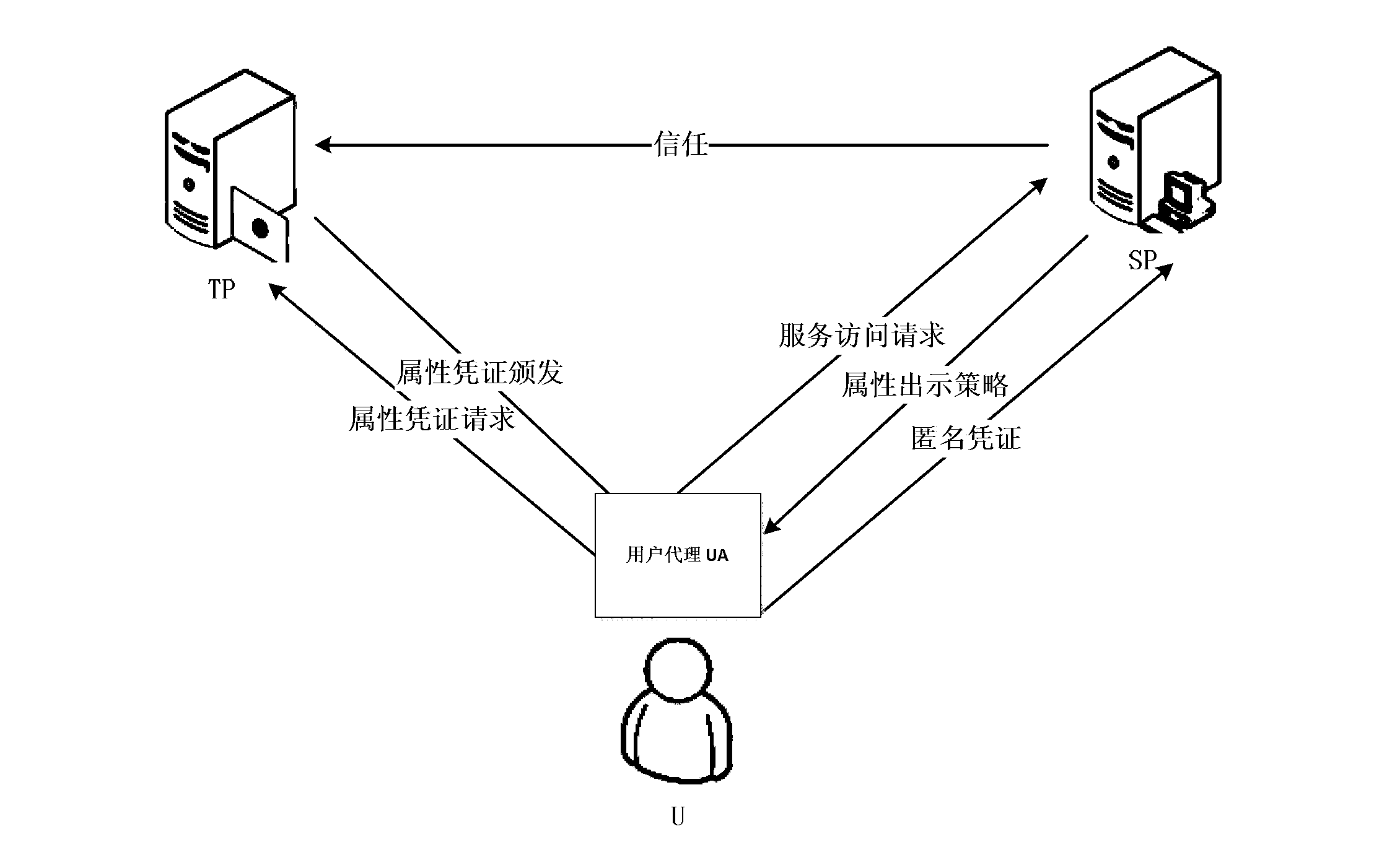
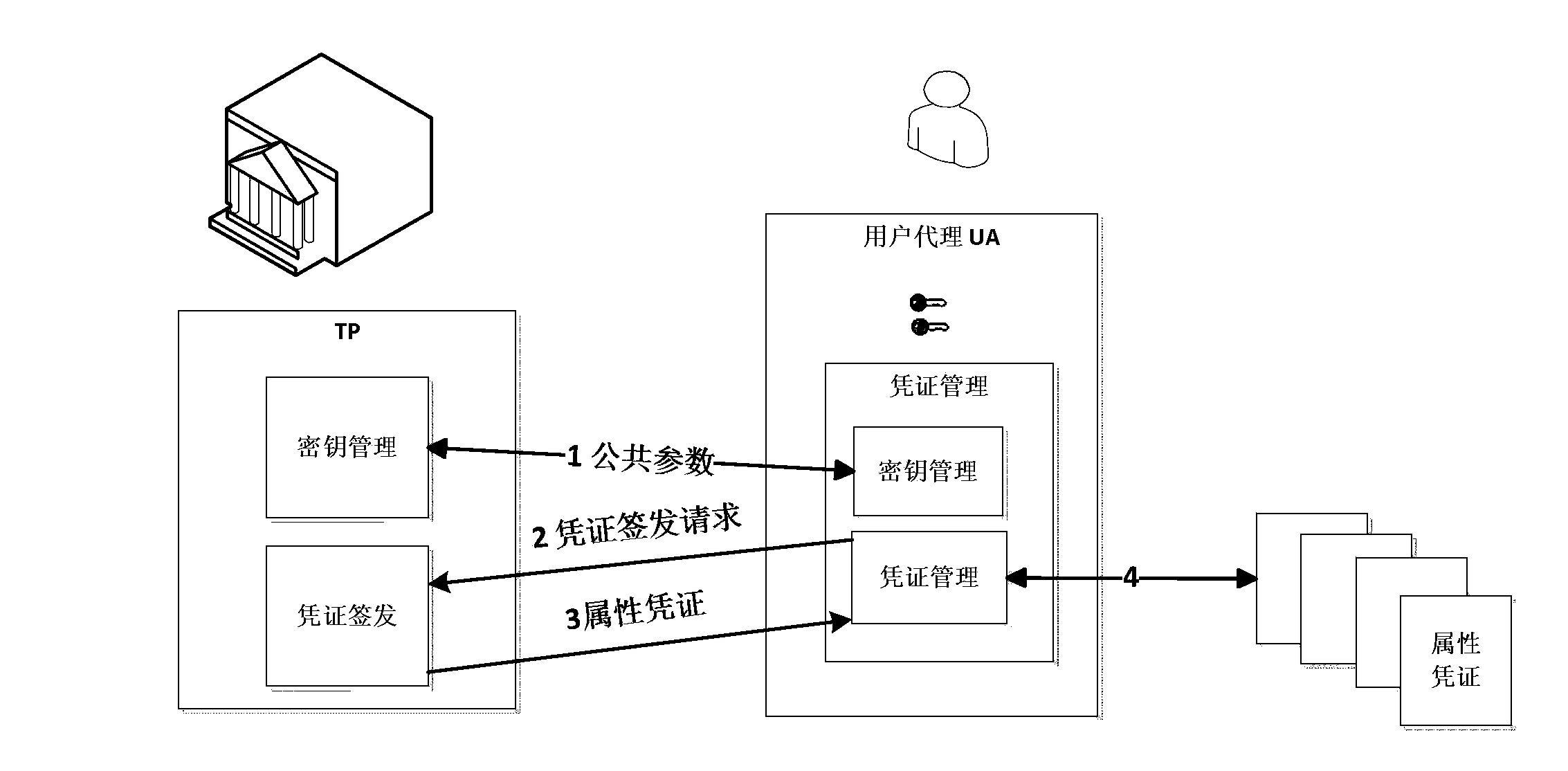
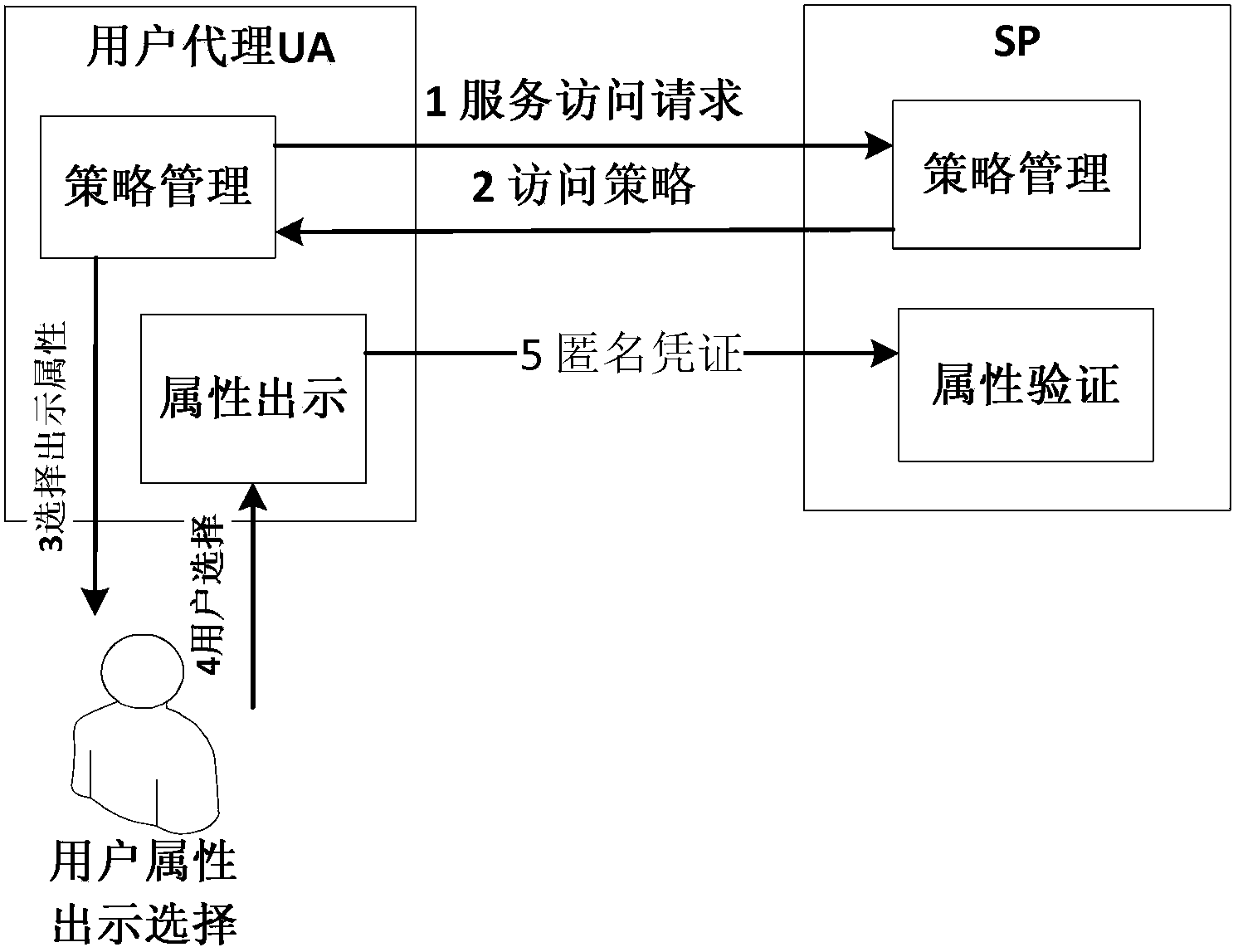
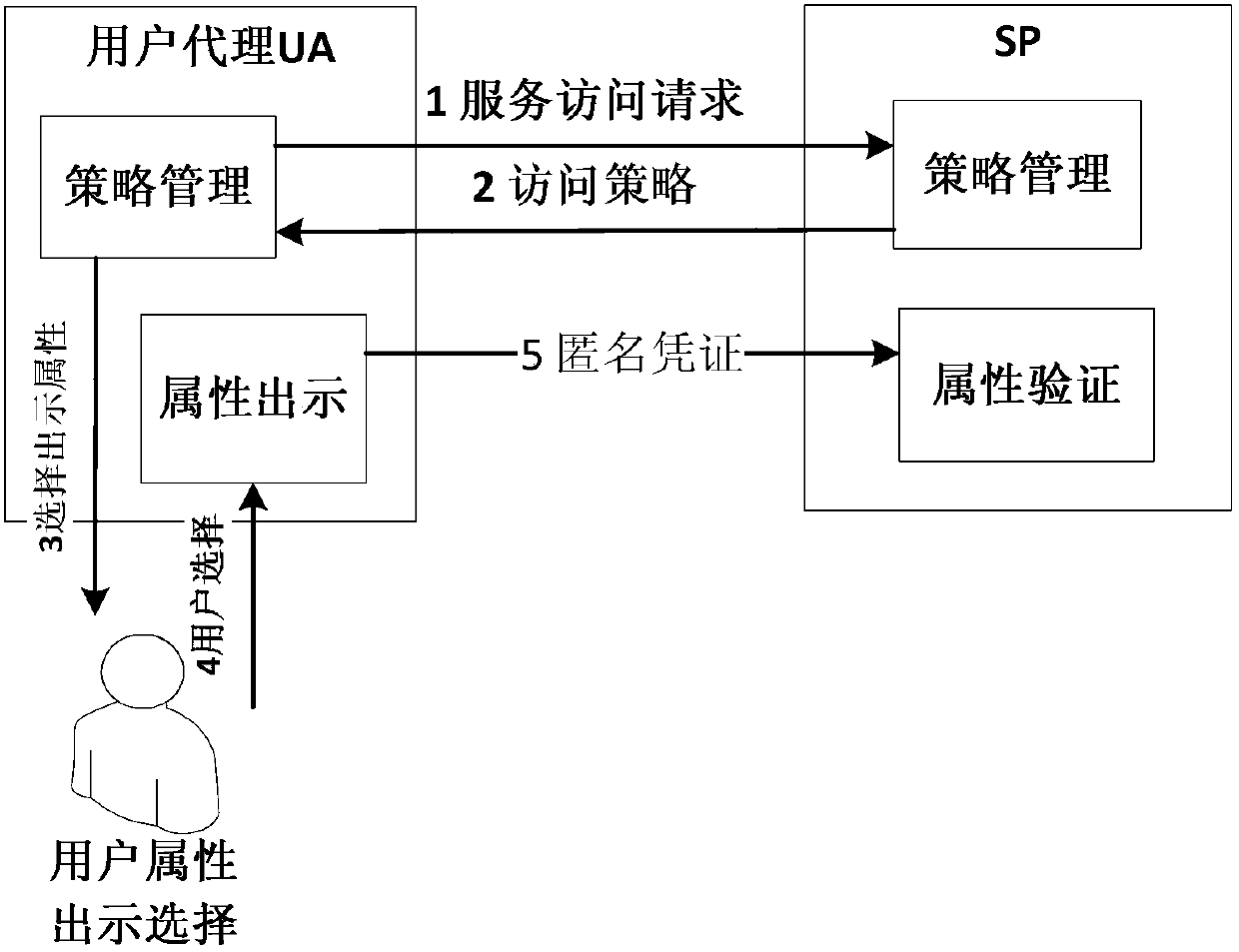
Attribute-based anonymous authentication method and system thereof
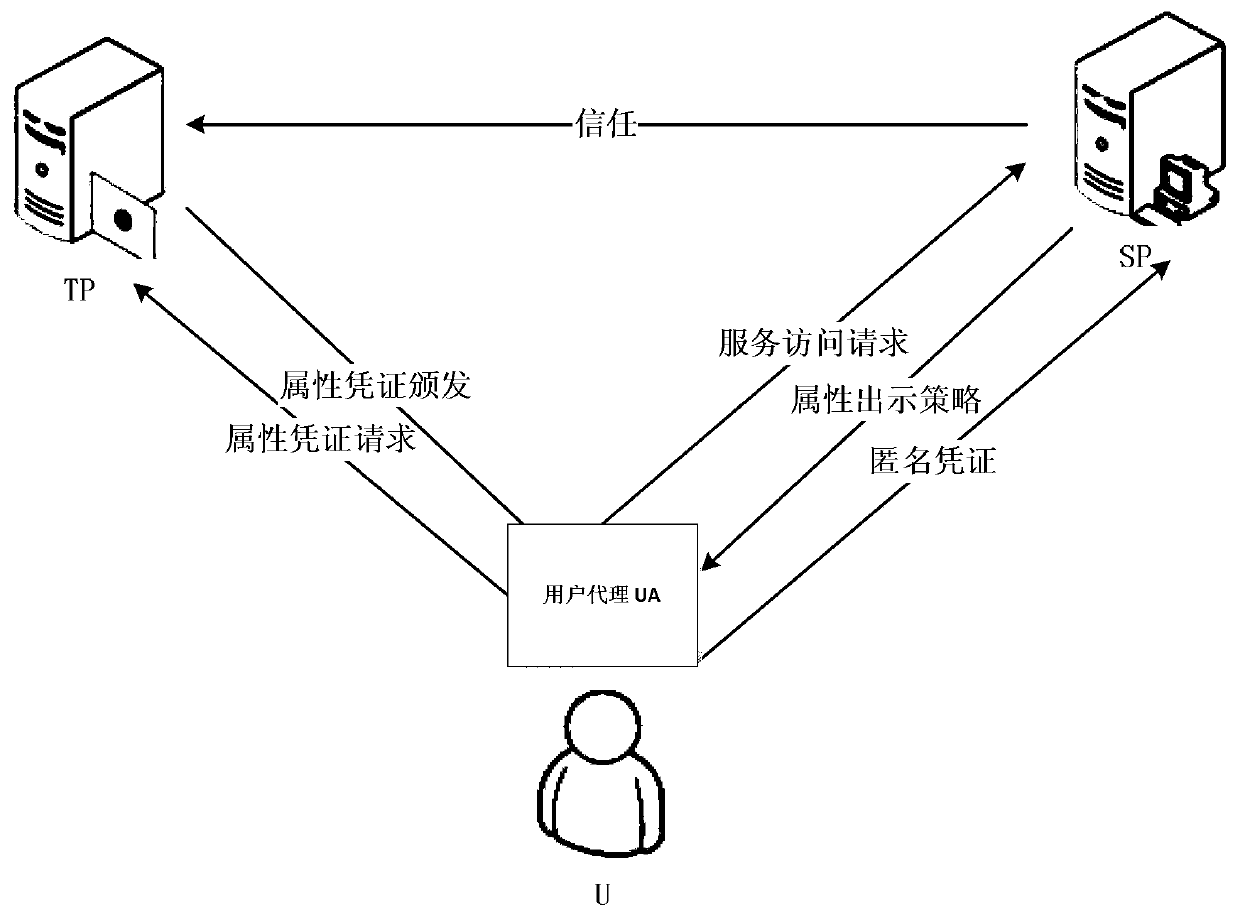
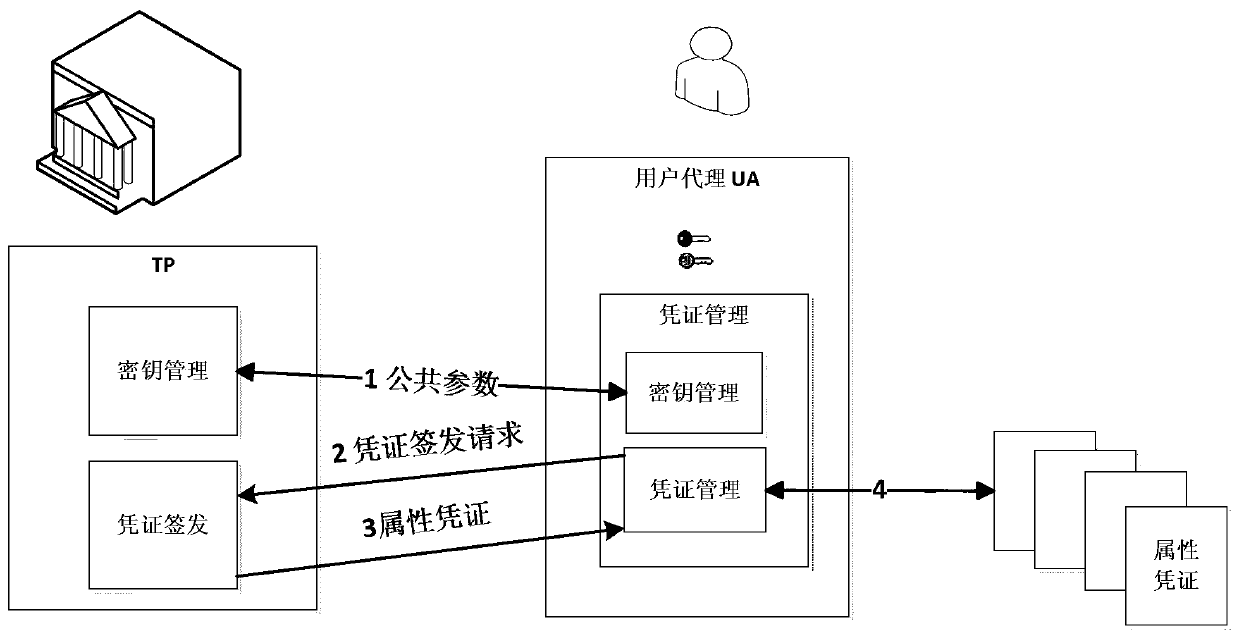
InactiveCN104125199AFlexible Threshold Attribute Selective Presentation SchemeImprove communication efficiencyTransmissionInternet privacyService provision
The invention discloses an attribute-based anonymous authentication method which contains the following steps: 1) a trusted party TP generates a master key x and system public parameters according to set safety parameters; 2) a user U registers with the TP to submit attributes and initiates an attribute certificate issue request; 3) the TP verifies the attributes of the user U and issues an attribute certificate for the user U according to the attributes of the U, the master key x and the system public parameters; 4) the user U initiates an access request to a service provider SP; 5) the SP looks up an access strategy corresponding to the access request and returns the access strategy to the user U; 6) the user U selects an attributes that the U wants to use according to the access strategy, and an anonymous certificate is calculated by the use of the attribute certificate and a private key r and is sent to the SP; and 7) the SP verifies the anonymous certificate, and accepts the access request and provides corresponding service to the user if verification is passed and the access strategy is satisfied. According to the invention, privacy of a user is guaranteed, and a more flexible threshold attribute selective showing scheme is supported.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
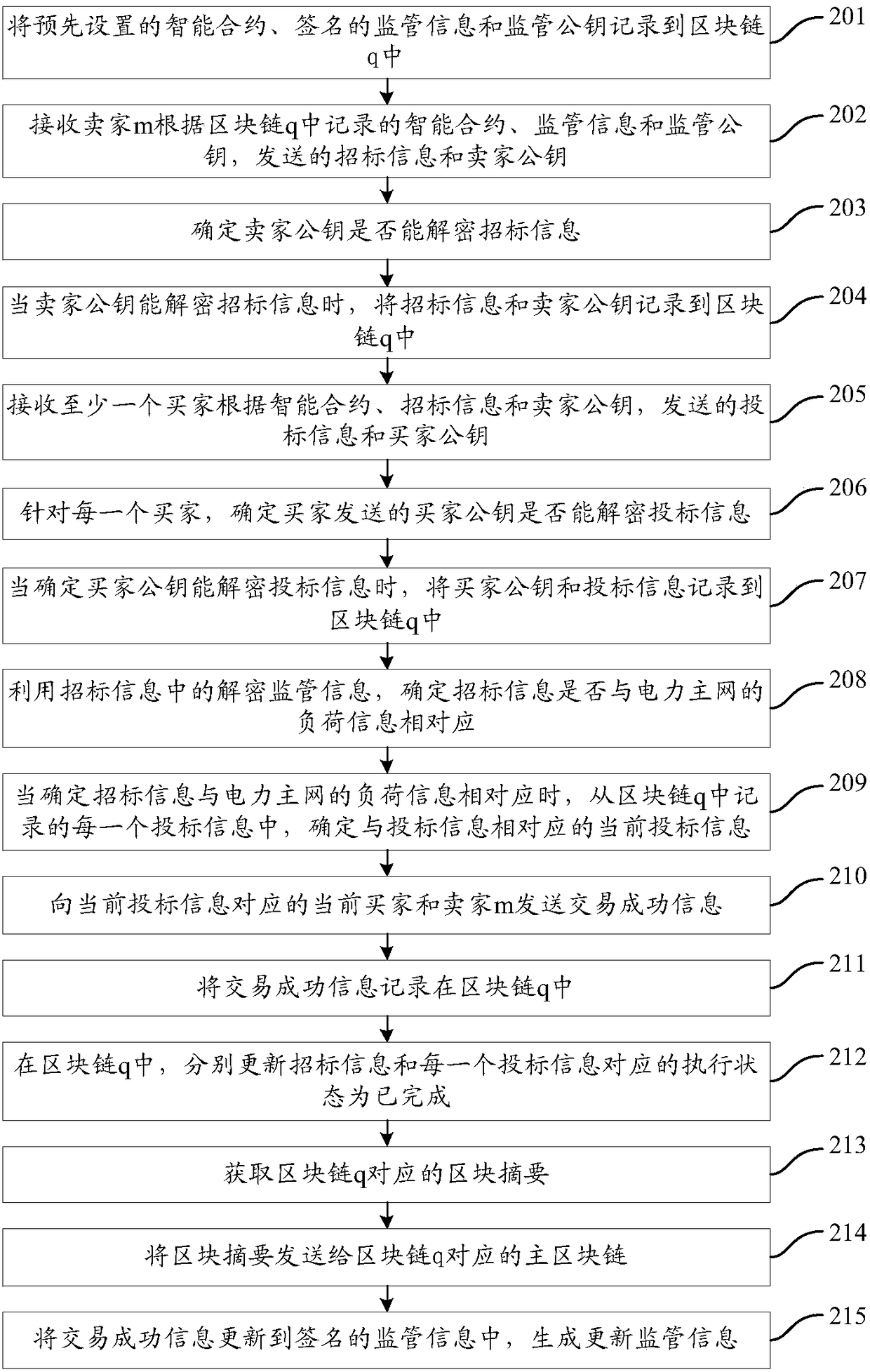
Transaction method and device based on blockchain
InactiveCN108520402AProtect interestsGuarantee opennessFinancePayment protocolsBlockchainReal-time computing
The invention provides a transaction method and device based on a blockchain, and the method comprises the steps: receiving at least one piece of bidding information sent by at least one seller; recording the bidding information into the blockchain; receiving at least one piece of bidding information sent by at least one buyer; recording the bidding information into the blockchain; performing thefollowing substeps for each piece of bidding information: determining current bidding information corresponding to the current bid inviting information; sending transaction success information to a current buyer corresponding to the current bidding information and a current seller corresponding to the current bid inviting information, wherein the transaction success information includes the current bid inviting information, the information of the current seller, the current bidding information, and the information of the current buyer; recording the transaction success information in the blockchain. The scheme can improve the transaction fairness.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Cryptography attribute-based access control method and system based on dynamic rule
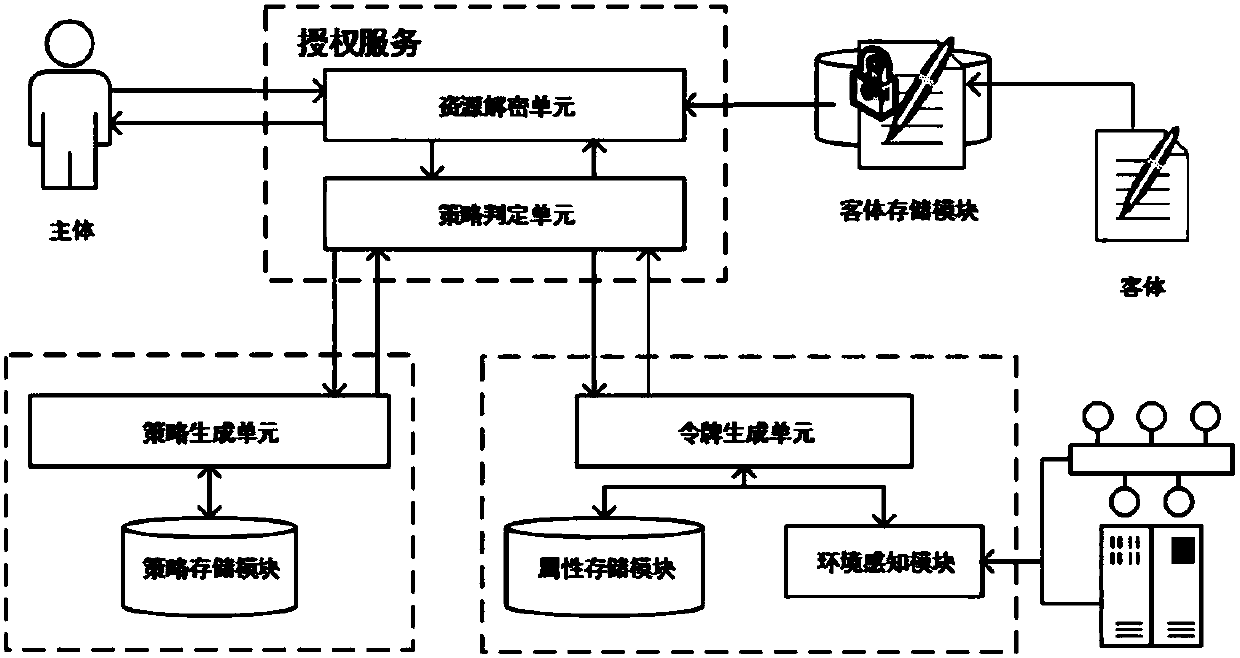
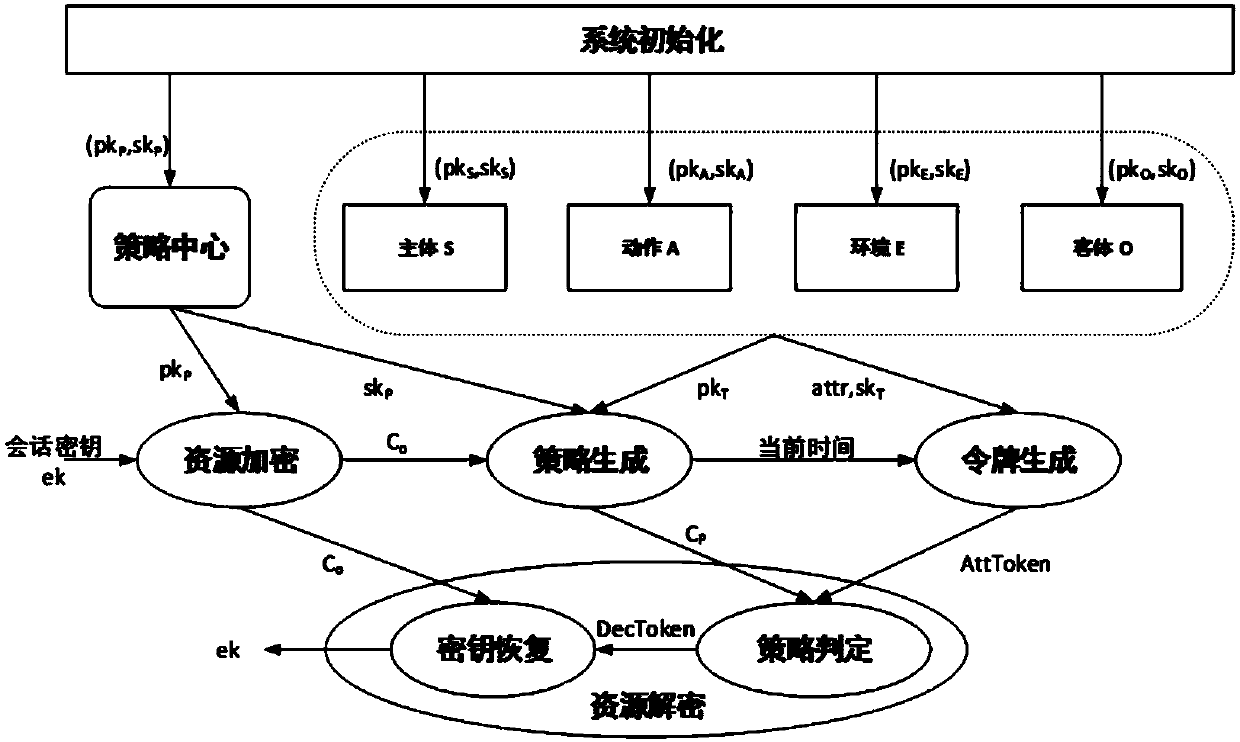
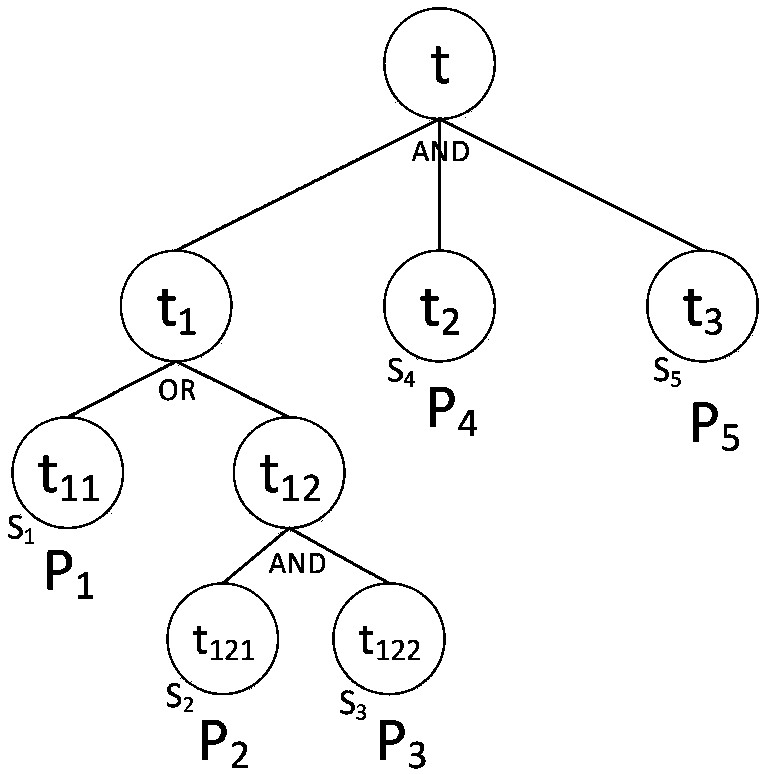
ActiveCN107864139AHigh security requirementsGuaranteed unforgeabilitySecuring communicationExtensibilityUnsafe environment
The invention relates to a cryptography attribute-based access control method and system based on a dynamic rule, mainly belonging to the technical field of information. In the cryptography attribute-based access control system based on the dynamic rule, protected objects are stored in a encrypted form, and only the requests satisfying the requirements of access policies in the attribute-based access control can be authorized to decrypt the objects, therefore, it can be ensured that data in an unsafe environment can be accessed with authorization according to a security policy, and meanwhile,the extensibility of the policies and the dynamic acquisition of the attributes are also supported. The cryptography attribute-based access control method and system based on the dynamic rule are divorced from the traditional encryption system framework, and are a new attribute-based access control model, method and system supporting the cryptography decision. The cryptography attribute-based access control method and system based on the dynamic rule can achieve more secure, diversified, dynamic and flexible access authorization, which are suitable for large-scale organizations or informationsystems, and can be applied to the environments such as cloud computing, grid computing, distributed computing, and so on.
Owner:UNIV OF SCI & TECH BEIJING
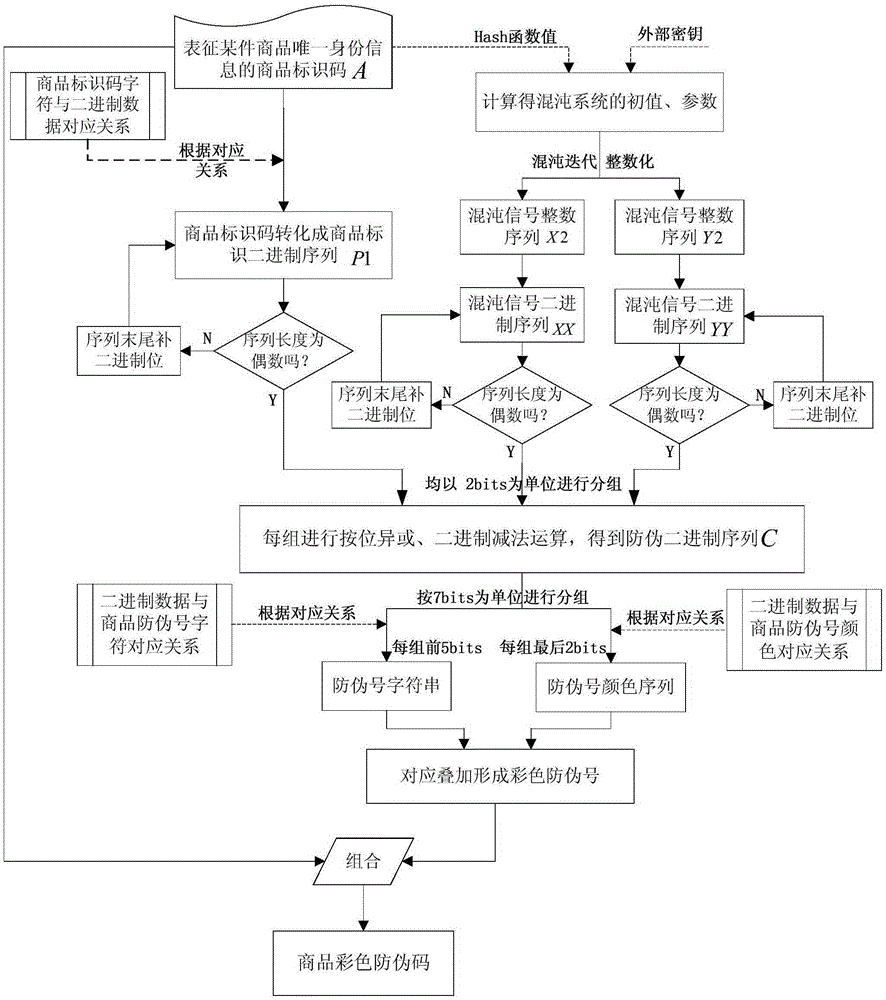
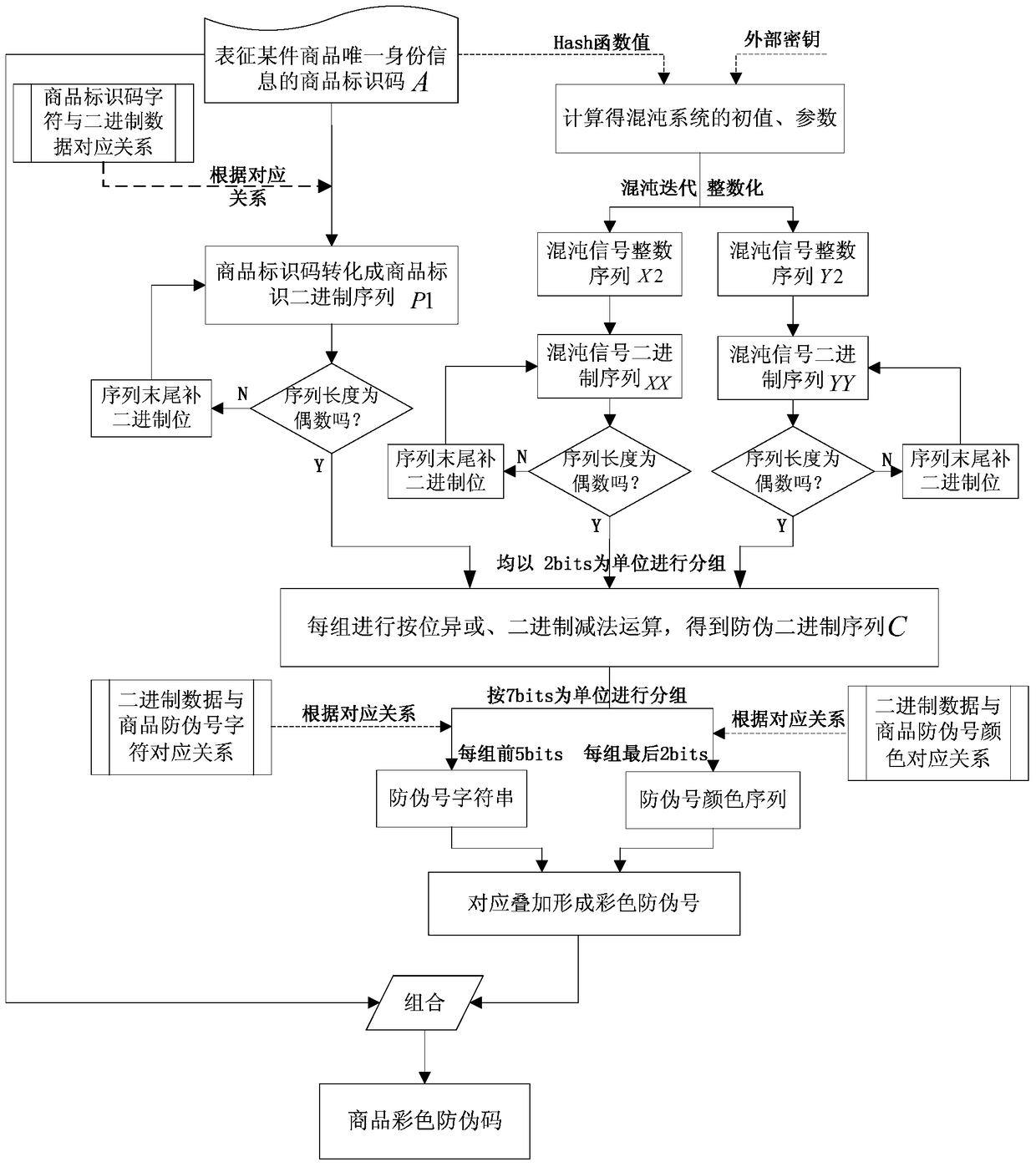
Colorful commodity anti-counterfeiting code generating method
ActiveCN105354717AThe generation method is simpleImprove securityCommerceChaotic systemsTheoretical computer science
The invention discloses a colorful commodity anti-counterfeiting code generating method. The colorful commodity anti-counterfeiting code generating method comprises the following steps: converting a commodity identification code for representing the unique identity information of a certain commodity into a binary data; obtaining an initial value and parameters of a chaotic system based on the commodity identity information and an external secret key through calculation, and performing iteration on a chaotic mapping to generate two groups of chaotic signal binary sequences; performing bit manipulation taking 2bits as a unit on the commodity identification code by the chaotic binary signals to generate an anti-counterfeiting number overlapped with a colorful background, and further combining the anti-counterfeiting number into the colorful commodity anti-counterfeiting code. The colorful commodity anti-counterfeiting code generating method provided by the invention is simple, feasible, high in safety, and difficult to be cracked; and in addition, the generated colorful commodity anti-counterfeiting code is has the uniqueness and unforgeability.
Owner:礼何科技(上海)有限公司
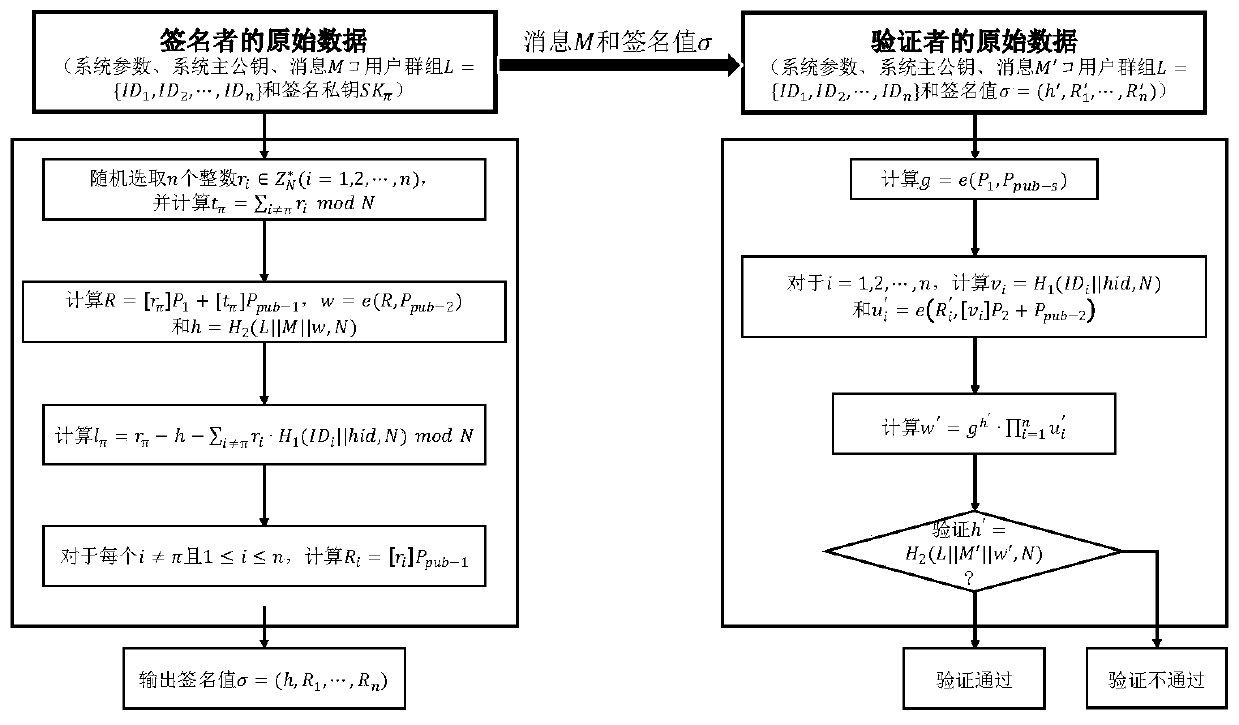
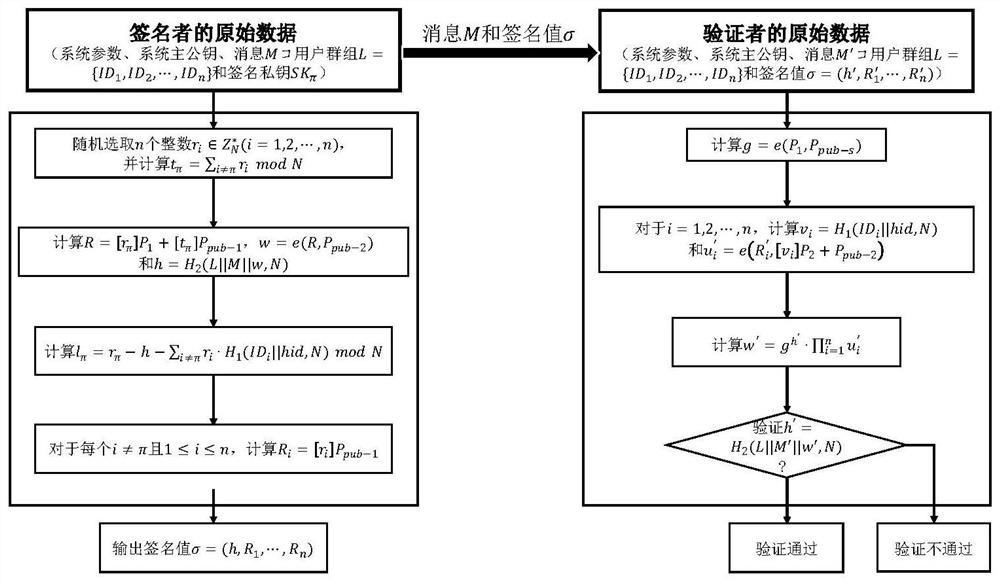
Safe and efficient SM9 ring signature generation and verification method
ActiveCN110880977AGuaranteed unforgeabilityGuaranteed anonymityKey distribution for secure communicationPublic key for secure communicationRing signatureTheoretical computer science
The invention discloses a safe and efficient SM9 ring signature generation and verification method, which comprises a key generation center KGC, a signer Siger and a verifier Verifier, and is characterized in that the KGC is responsible for generating a user private key of a signed user in a system; wherein the number of users is set to be n and a signer is the pi user in a user group. Themethod comprises the following steps: 1) generating a ring signature for a message M; and 2) performing legality verification on the signature obtained in the step 1), and judging whether the signer is an in-loop user or not. According to the ring signature generation and verification scheme based on an SM9 digital signature algorithm, the unforgeability of signatures and the anonymity of signersare guaranteed, the spontaneity of rge user group generated by the signers is guaranteed, and other user cooperation is not needed. The ring signature is realized by adopting an accumulation structure, so that the bilinear pair frequency of signature generation and verification algorithm execution is greatly reduced, and the signature and verification operation efficiency is effectively improved.
Owner:WUHAN UNIV
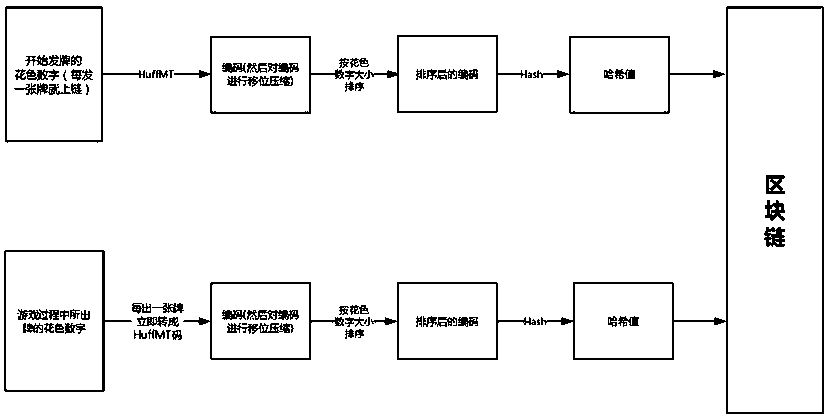
Card game anti-cheating method and system based on block chain intelligent contract
ActiveCN109985389AGuaranteed verifiabilityGuaranteed to be tamper-proofUser identity/authority verificationVideo gamesComputer hardwareEncryption
The invention provides a card game anti-cheating method and system based on a block chain intelligent contract. The method comprises the following steps of: storing card drawing information and card issuing information of a player on the block chain by using a coding method and an encryption method; comparing a Hash value A and a Hash value B of a winner in the block chain; if the two values are the same, that cheating behavior occurs is determined, if the two values are not the same, that cheating behavior does not occur is determined. According to the invention, the defect of the existing combination of the block chain and the game is considered, the application scene is changed, and the cheating behavior is effectively found out by utilizing a unique mechanism of the block chain for de-trust and de-centralization. Meanwhile, the chess and card game data is not complex, too much burden is not caused during operation, the cost is low, the effect is obvious, and the serious situation of cheating of the current card game can be effectively improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Lightweight digital signature method based on translog problem
InactiveCN102307102AImprove securityEnsure safetyPublic key for secure communicationUser identity/authority verificationDigital signatureE-commerce
The invention provides a lightweight digital signature method based on a translog problem, belonging to the fields of cryptographic technology and computer technology. The method comprises three parts, i.e. secret key generation, digital signature and authentication. A sending user in the method has two secret keys, i.e. a private key and a public key, wherein the private key cannot be deduced from the public key; the private key of the sending part is used to generate a name guide of a message; and the public key of the sending part is used for a receiving part to verify the name guide of the corresponding message. With the method provided by the invention, the attack of the existing analysis method can be effectively resisted. The method has the advantages of high calculation speed and the like, the modular length is less than 96 bits, and the technology can be published; and the method can be applied to the signature and the verification of any message in mobiles, computers and communication networks, also can be used for identity authentication and content confirmation in electronic banking, e-commerce and e-government affairs, and can be used for the anti-counterfeiting of bills, certificates and high order goods.
Owner:数字兵符(福州)科技有限公司
NFC-based secure payment system architecture design
InactiveCN107833047AGuaranteed unforgeabilityEnsure safetyPayment protocolsTransmissionThree levelSystems management
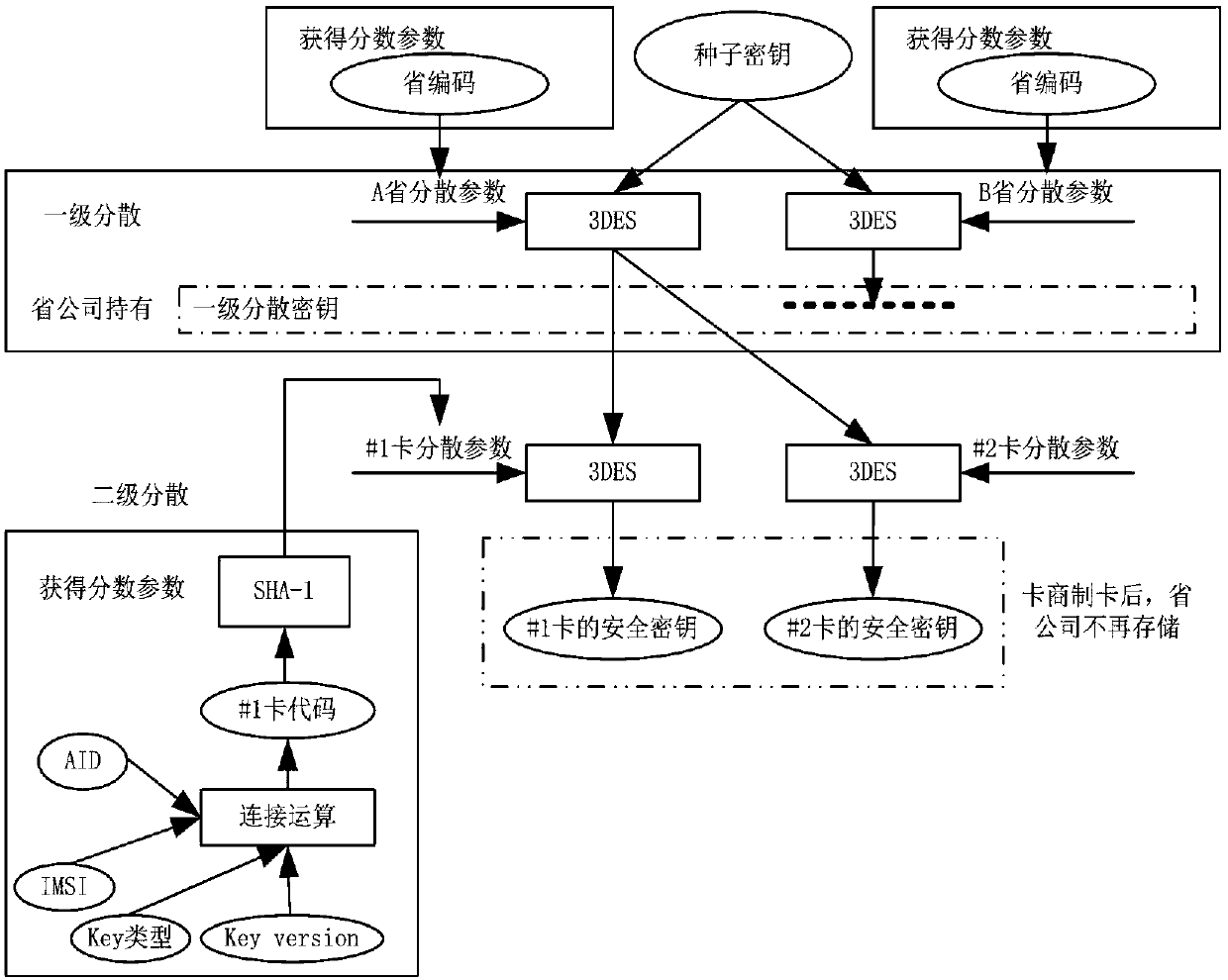
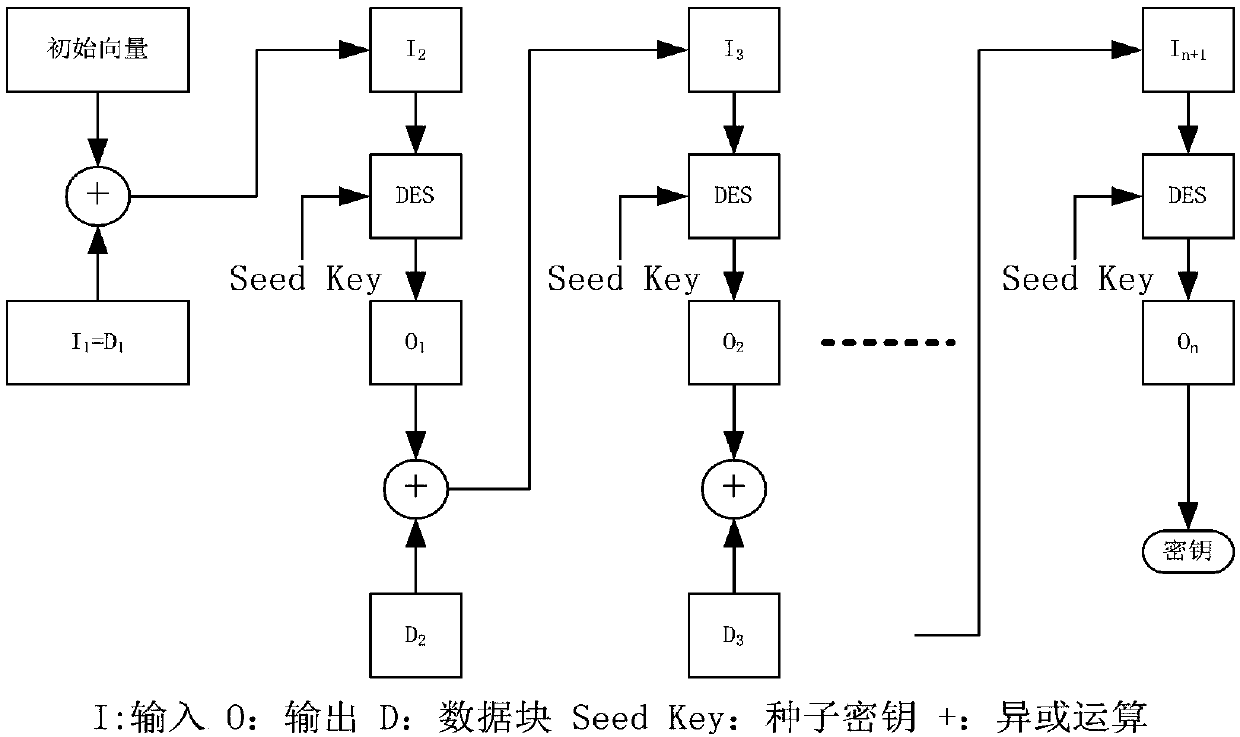
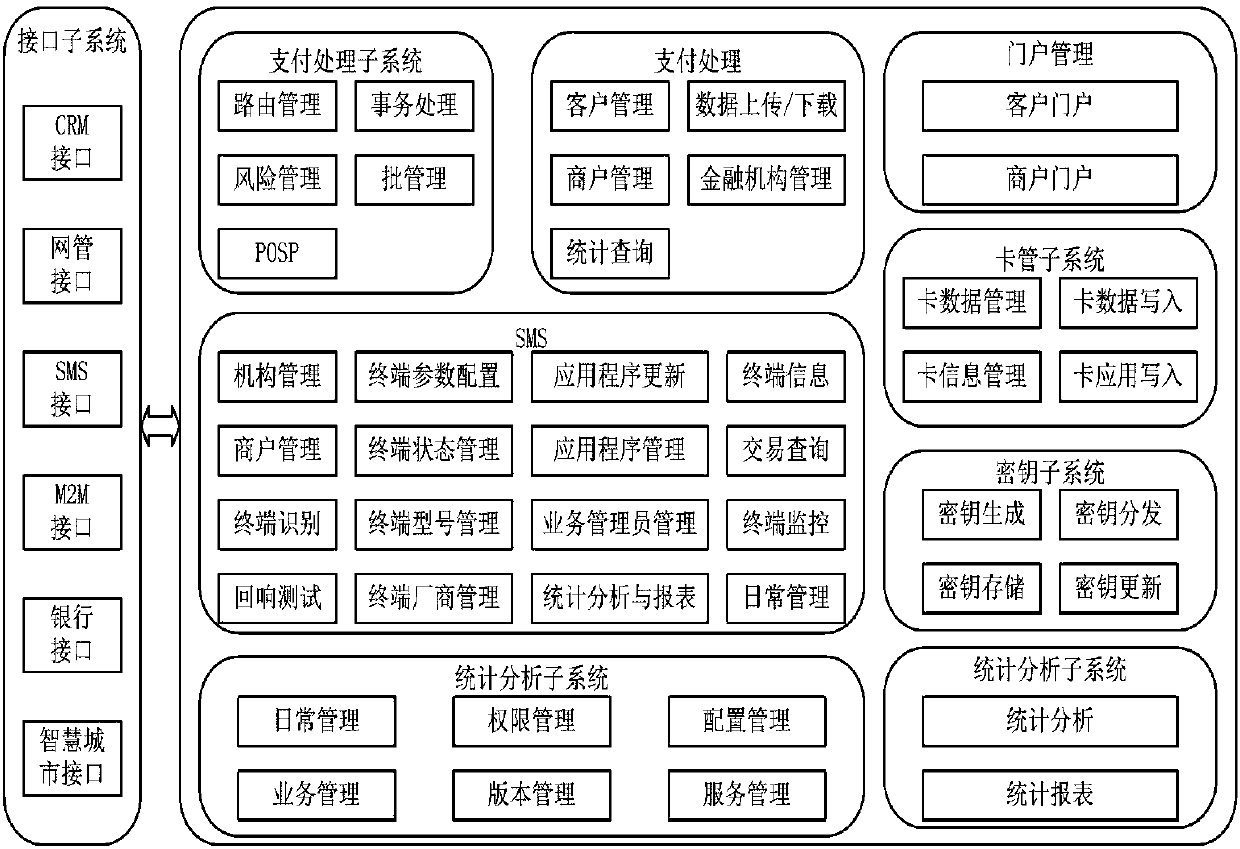
The present invention discloses an NFC-based secure payment system architecture design. The NFC-based secure payment system architecture design comprises a system management platform, a GPRS network,an internet of things system, other industry systems, and a mobile payment terminal. The system management platform comprises a mobile payment system and an NFC payment terminal system. The mobile payment system comprises two major business systems of mobile payment management and mobile settlement management; the mobile payment management comprises an interface subsystem, a payment subsystem, a portal management subsystem, a card management subsystem and a secret key subsystem; the mobile settlement management comprises an operation and maintenance subsystem and a statistics and analysis subsystem; and the secret key subsystem is designed by using a three-level key generation system.
Owner:CHANGZHOU AISUO ELECTRONICS
First-price sealed transaction method based on Bitcoin agreement
InactiveCN107330775AAvoid collusionEnsure fairnessEncryption apparatus with shift registers/memoriesUser identity/authority verificationPaymentThird party
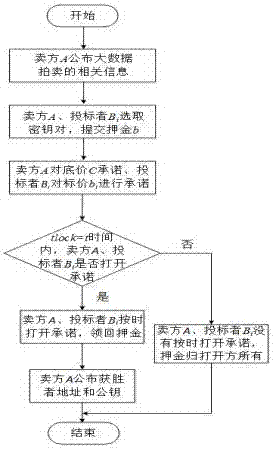
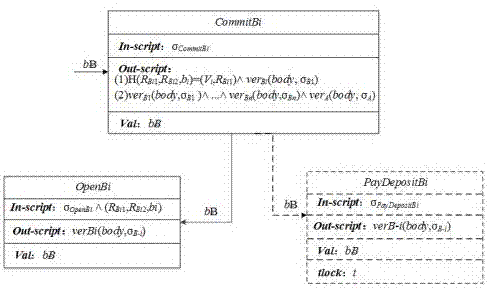
The invention discloses a first-price sealed transaction method based on the Bitcoin agreement. The method comprises the following steps: (1) the preparation stage, a vendor A publishes related information of big data of a to-be-performed transaction, the vendor A and a bidder B select a secret key pair, and the vendor A and the bidder B submit guarantee deposits; (2) the bidding stage, the vendor A gives a commitment for a floor price C, and the bidder B gives a commitment for a bid price b; (3) the bid opening stage, the vendor A / bidder B timely opens the commitment for the floor price C / bid price b within time tlock=t and takes the corresponding deposit back; (4) the bid verification stage, the vendor A publishes an address and a public key of a winner in the bidder B; and (5) the auction payment stage, the winner pays the bidden bid price. The method is advantageous in that an untrusted third part is removed, confidentiality is good, and the method is justice, fair, safe and risk-free.
Owner:GUIZHOU UNIV
Access control method for smart home environment based on private blockchain
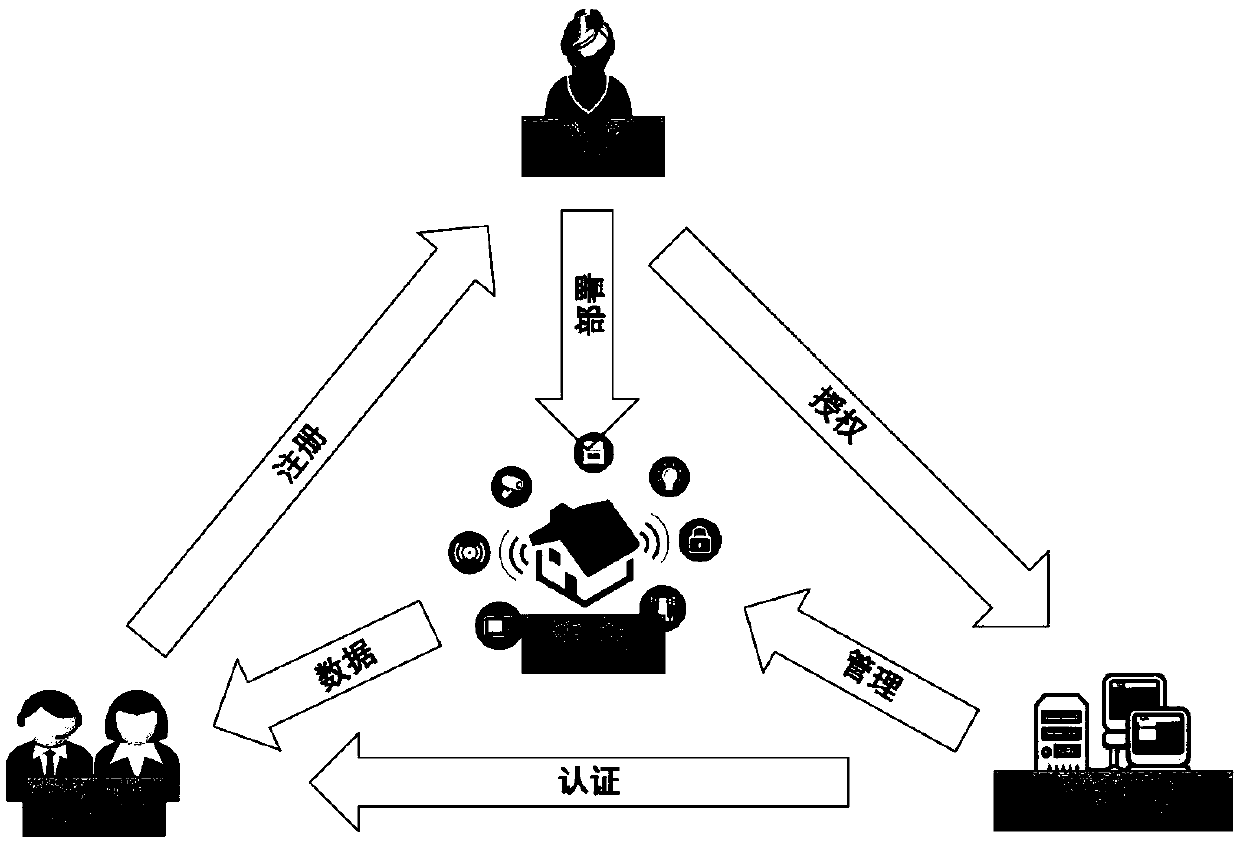
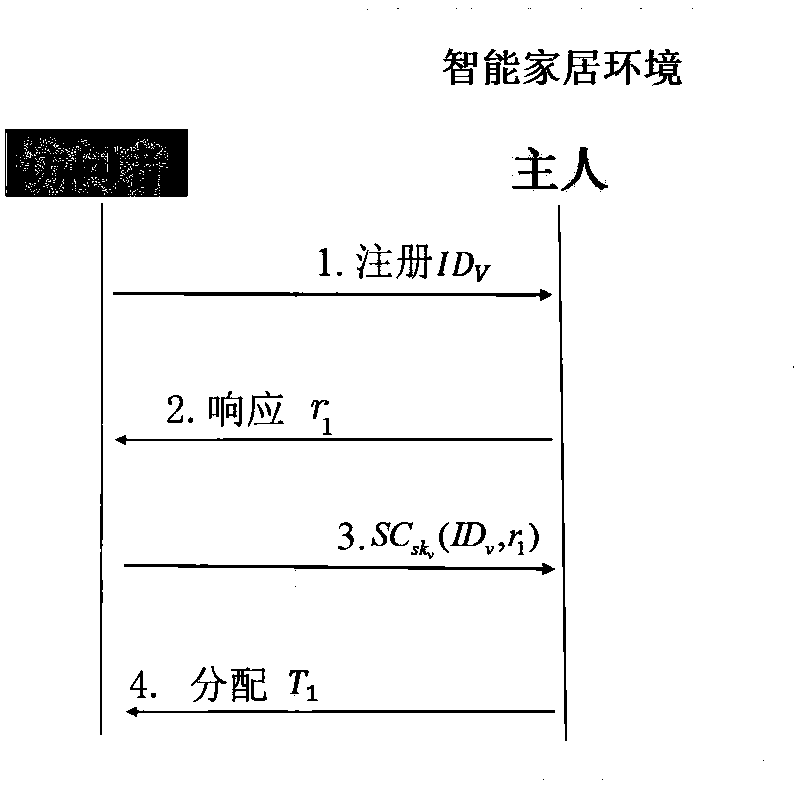
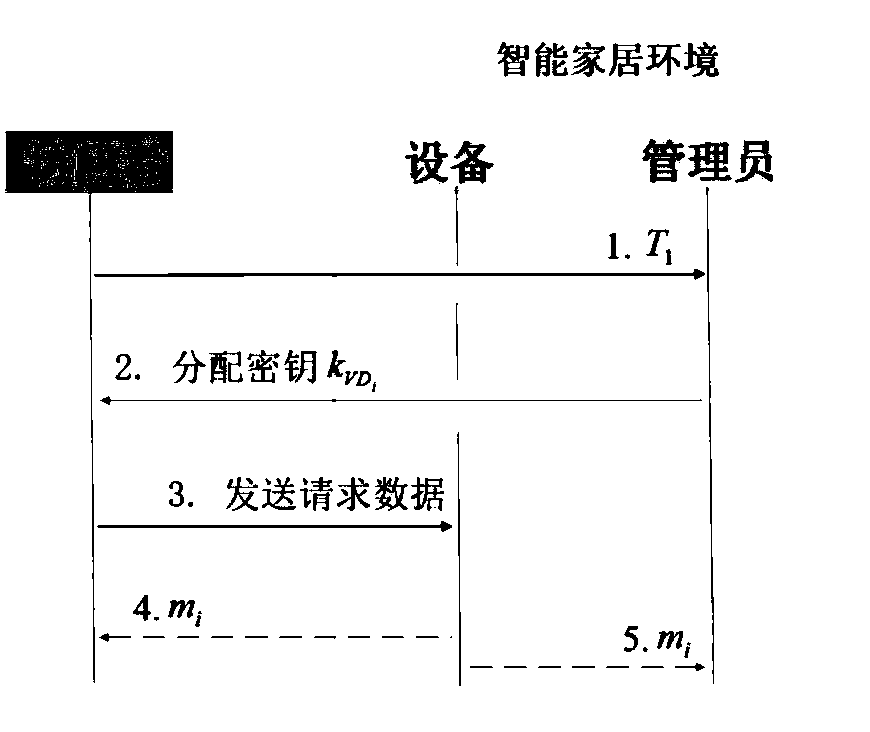
ActiveCN108632254AOvercoming several difficulties in combiningGuaranteed confidentialityUser identity/authority verificationData switching by path configurationAccess timeConfidentiality
The invention discloses an access control method for a smart home environment based on a private blockchain and belongs to the technical field of information security. The method provided by the invention comprises the steps of initialization, registration, authentication, verification and revocation. Compared with an access control scheme in the prior art, the method has the advantages that the confidentiality and integrality of accessed data can be ensured; the bidirectional identity authentication between an owner and an visitor can be ensured; a legal visitor cannot initiate an access request to device data after an access deadline arrives or the registration information is revoked compulsorily; and the non-repudiation of the visitor and the owner for an access behavior (comprising theaccessed data and access time) and the unforgeability of an access record are also ensured.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
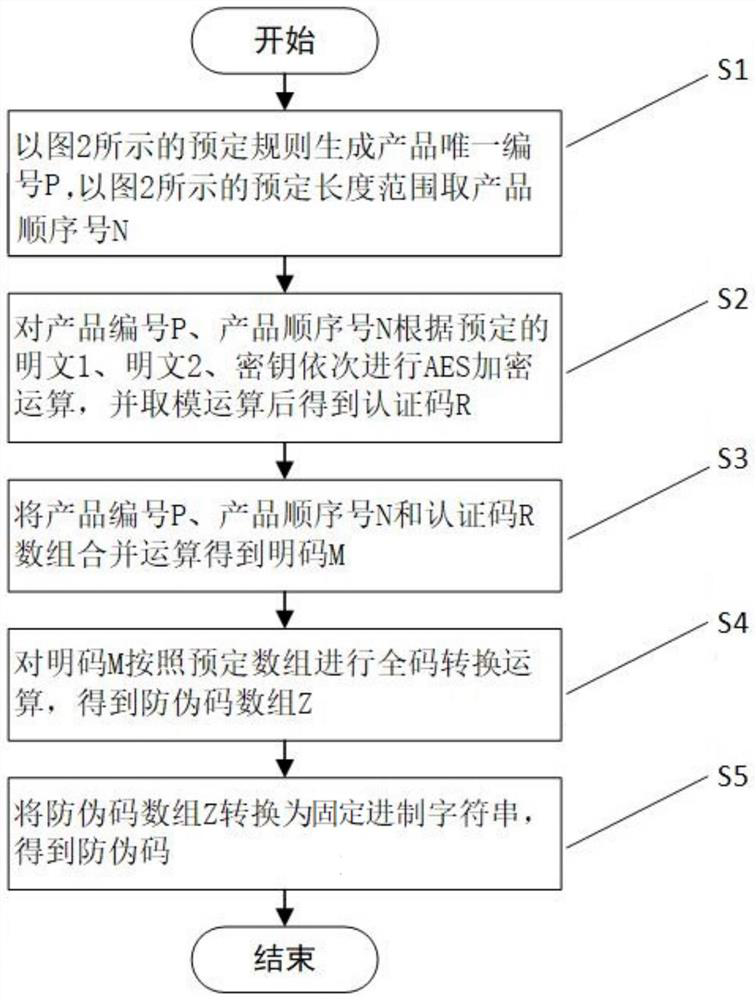
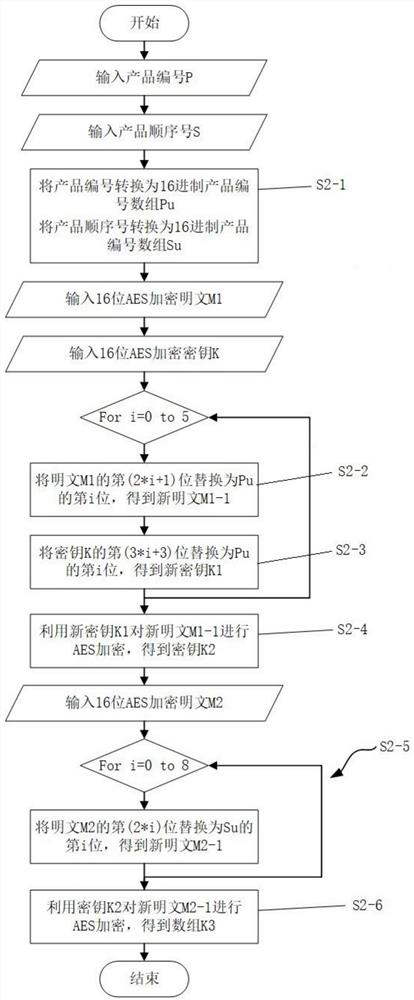
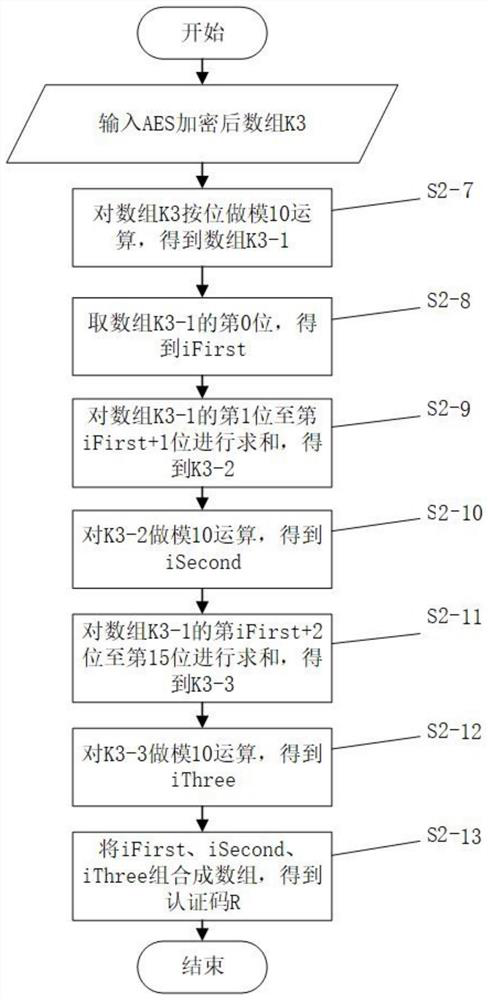
Method, system and equipment for generating anti-counterfeiting code from product number and storage medium
PendingCN114861237AUniqueness guaranteedGuaranteed unforgeabilityDigital data protectionInternal/peripheral component protectionCode generationCode conversion
The invention relates to a method, system and device for generating an anti-counterfeiting code through a product number and a storage medium, and belongs to the technical field of anti-counterfeiting code generation methods. The method comprises the following steps: S1, generating a unique number P for a product number according to a preset rule, and obtaining a value N for a product sequence number in a preset length range; s2, AES encryption operation is carried out on the product number P and the product sequence number N, and an authentication code is obtained after a modulo algorithm is carried out; s3, combining the product number, the product sequence number and the authentication code into a plain code; s4, performing full-code conversion on the plain code to obtain an anti-counterfeiting code array; step S5, converting the anti-counterfeiting code array into an anti-counterfeiting code; the system comprises a character string generation module, an authentication code generation module, a plain code generation module, an anti-counterfeiting code array generation module and an anti-counterfeiting code generation module. The device comprises a memory and a processor; a computer program is stored on the readable storage medium, and the steps of the method are implemented when the computer program is executed; the encryption strength is high, and cracking is not easy.
Owner:SHANDONG TAIBAO PREVENTING COUNTERFEIT
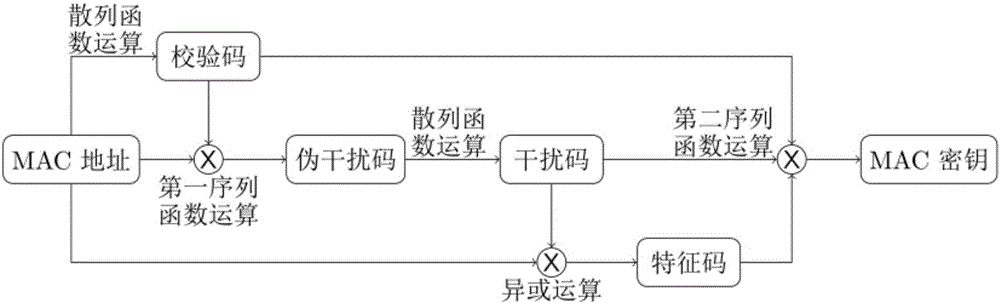
MAC address encryption and decryption methods and apparatuses
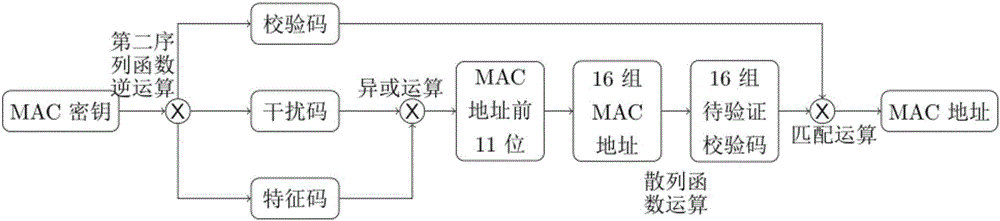
ActiveCN105868587AIncreased complexityGuaranteed unforgeabilityProgram/content distribution protectionFeature codeSoftware
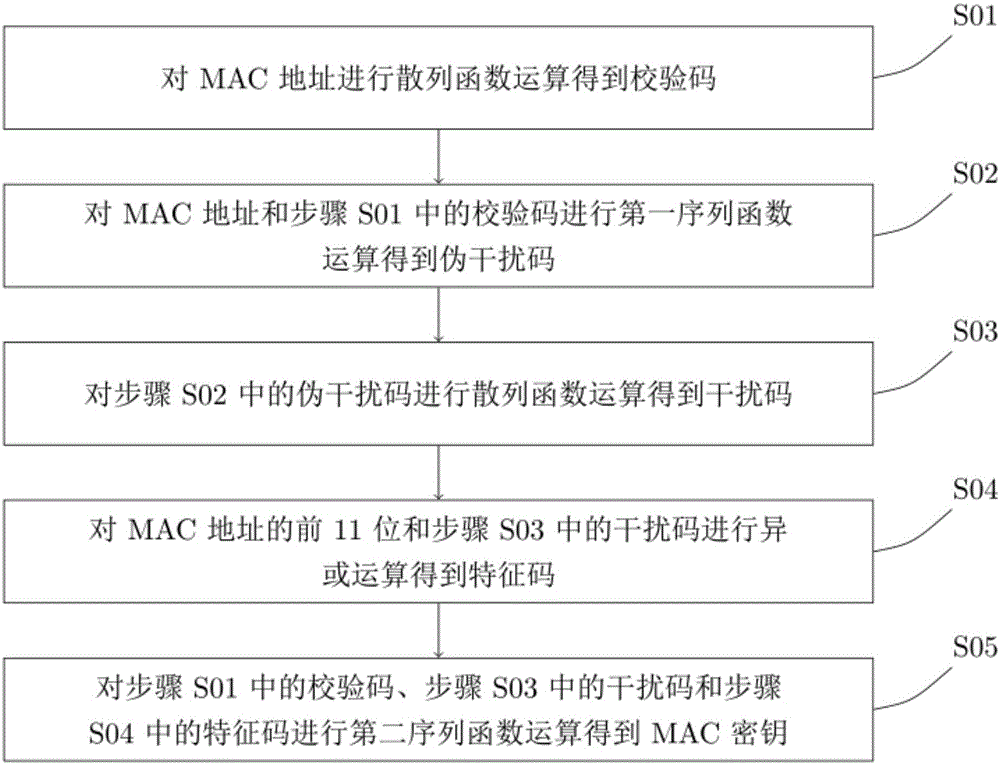
The present invention discloses MAC address encryption and decryption methods and apparatuses. The encryption method comprises the following steps: performing a hash function operation on an MAC address to obtain a check code; performing a first sequence function operation on the MAC address and the check code to obtain a pseudo-interference code; performing the hash function operation on the pseudo-interference code to obtain an interference code; performing an exclusive-OR operation on first eleven bits of the MAC address and the interference code to obtain a feature code; and performing a second sequence function operation on the check code, the interference code and the feature code to obtain an MAC key. The method and apparatus disclosed by the present invention free software owners from cumbersome steps of burning the Flash and modifying the MAC address, and a network connection is not required, and efficiency, security and flexibility are greatly improved in addition that the software copyright is protected.
Owner:SHENZHEN NEW GREENNET TECH +1
An attribute-based anonymous authentication method and system
InactiveCN104125199BFlexible Threshold Attribute Selective Presentation SchemeImprove communication efficiencyTransmissionAnonymous authenticationMaster key
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
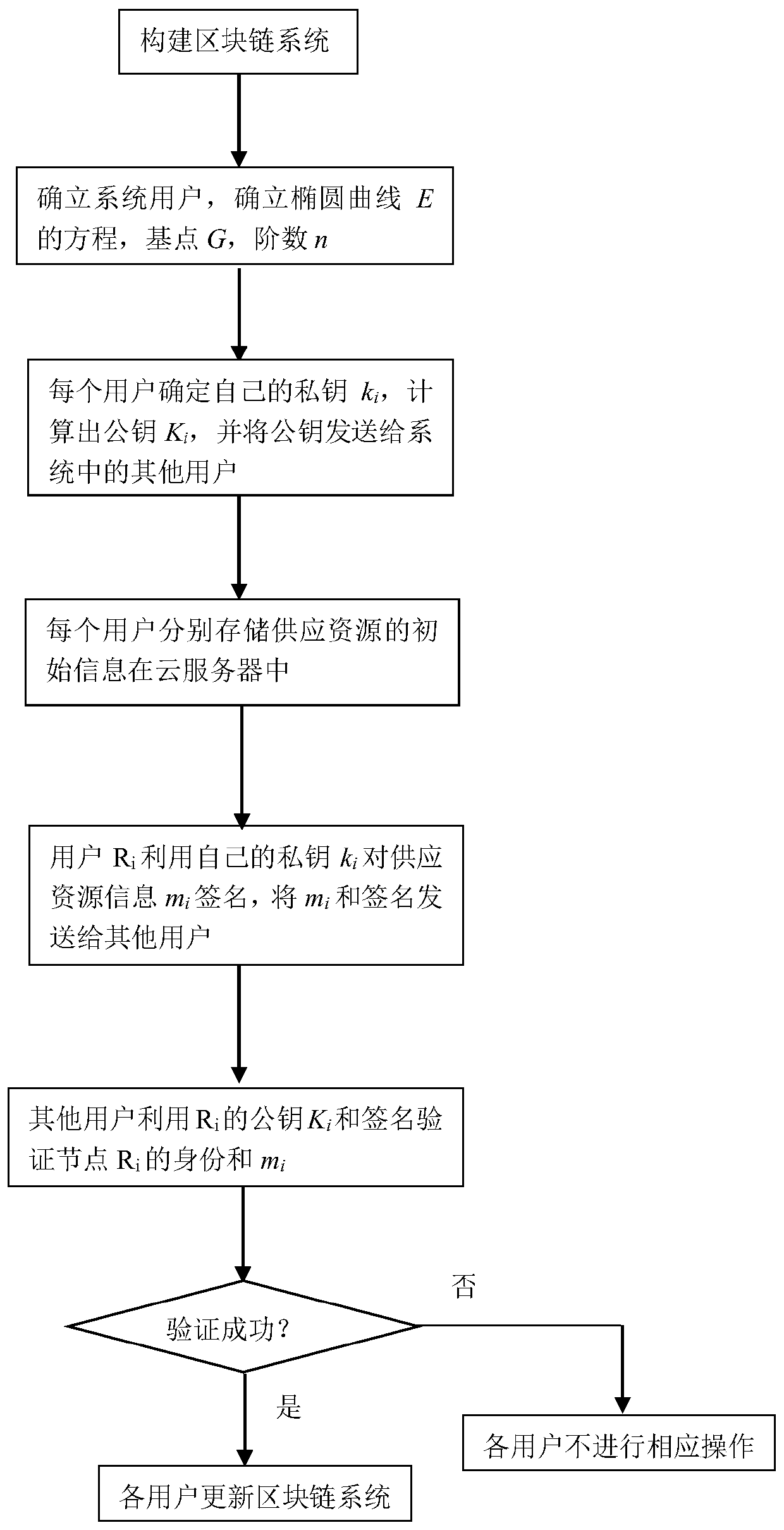
Supply guarantee management method based on block chain
ActiveCN110535916AAvoid mass storageEnsure safetyUser identity/authority verificationResource informationDependability
The invention discloses a supply guarantee management method based on a block chain. The method comprises the following specific steps: firstly, constructing a block chain system, allocating a privatekey to each user, calculating a public key, and sending the public key Ki to other users in the system; enabling each user respectively to store the initial information of the supply resources in thecloud server; when the user Ri needs to operate the supply resource information, signing the supply resource information by using the private key, and sending the obtained signature and resource information to other users; and enabling other users in the blockchain system to verify the identity and resource information of the user Ri by using the public key and signature of the Ri, enabling eachuser to update the blockchain system if the verification succeeds, and not performing corresponding operation if the verification fails. Compared with the prior art, the supply guarantee management isrealized by using the blockchain system, and the reliability, unforgeability and non-repudiation of the supply resources are ensured.
Owner:JIANGSU UNIV OF SCI & TECH
Conflated seal affix authentication method having electronic seal digital certification
InactiveCN101017544BEnsure unforgeableIntegrity guaranteedComputer security arrangementsOffice automationElectronic documentAffix
This invention relates to one legal seam signature method with electron stamp digital certificate in network identification technique field, which comprises the following steps: through opening, requiring, determining, transferring, sending and stamping steps to realize legal stamp, stamp customer end and servo, CA center certificate servo electron stamp signature operation; through receiving, separating, comparing to realize customer end and stamp servo validating steps to ensure the electron stamp and physical body integral part with combination by traditional physical stamp and modern digital certificate.
Owner:江苏国盾科技实业有限责任公司
A lightweight digital signature method based on the hyperlogarithm problem
InactiveCN102307102BEnsure safetyGuaranteed unforgeabilityPublic key for secure communicationUser identity/authority verificationDigital signatureE-commerce
The invention provides a lightweight digital signature method based on a translog problem, belonging to the fields of cryptographic technology and computer technology. The method comprises three parts, i.e. secret key generation, digital signature and authentication. A sending user in the method has two secret keys, i.e. a private key and a public key, wherein the private key cannot be deduced from the public key; the private key of the sending part is used to generate a name guide of a message; and the public key of the sending part is used for a receiving part to verify the name guide of the corresponding message. With the method provided by the invention, the attack of the existing analysis method can be effectively resisted. The method has the advantages of high calculation speed and the like, the modular length is less than 96 bits, and the technology can be published; and the method can be applied to the signature and the verification of any message in mobiles, computers and communication networks, also can be used for identity authentication and content confirmation in electronic banking, e-commerce and e-government affairs, and can be used for the anti-counterfeiting of bills, certificates and high order goods.
Owner:数字兵符(福州)科技有限公司
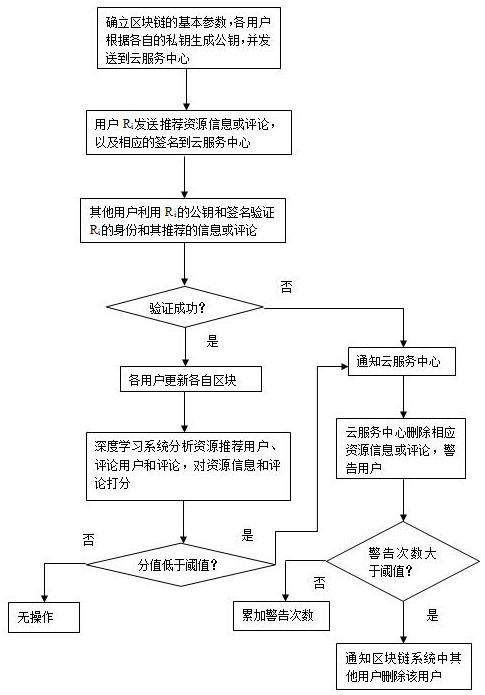
Intelligent learning chain system based on block chain and working method
PendingCN111723157AAvoid mass storageEnsure safetyDatabase updatingDatabase distribution/replicationSystem verificationResource information
The invention discloses an intelligent learning chain system based on a block chain and a working method. The system is composed of a block chain system, a cloud service center and a deep learning system. The working method comprises the following specific steps: firstly, constructing a block chain system, allocating a private key to each user in a block chain, calculating a public key, and sending a public key Ki to a cloud service center by a user Ri for other users to access; enabling the user Ri to sign the resource information and the comment by using a private key, and store the signed resource information and comment in a cloud server for other users to access and verify; verifying the identity and resource information of the user Ri by other users in the blockchain system by usingthe public key and signature of the Ri, updating the blockchain system by each user if the verification is successful, and feeding back to the cloud service center if the verification is unsuccessful;and enabling the deep learning system to analyze comments stored in the cloud service center and feed back non-compliant comments and resources with low comments to the cloud service center for processing. Compared with the prior art, the high-quality education resource service is realized by utilizing the block chain system and the deep learning system, and the reliability, the safety and the non-repudiation of education resources are ensured.
Owner:JIANGSU UNIV OF SCI & TECH
A safe and efficient sm9 ring signature generation and verification method
ActiveCN110880977BGuaranteed unforgeabilityGuaranteed anonymityKey distribution for secure communicationPublic key for secure communicationRing signatureTheoretical computer science
The invention discloses a safe and efficient SM9 ring signature generation and verification method, including a key generation center KGC, a signer Signer, and a verifier Verifier, wherein the KGC is responsible for generating the user private key of the signing user in the system; The number of users is n, and the signer is the πth user in the user group; the method includes the following steps: 1) generating a ring signature for the message M; 2) verifying the validity of the signature obtained in step 1), and judging the signature Whether the user is an in-ring user. The invention provides a ring signature generation and verification scheme based on the SM9 digital signature algorithm, which ensures the unforgeability of the signature and the anonymity of the signer. The scheme ensures the spontaneity of the signer to generate user groups without the cooperation of other users. The invention adopts an accumulative structure to realize the ring signature, so that the number of bilinear pairings performed by the signature generation and verification algorithm is greatly reduced, and the efficiency of the signature and verification operation is effectively improved.
Owner:WUHAN UNIV
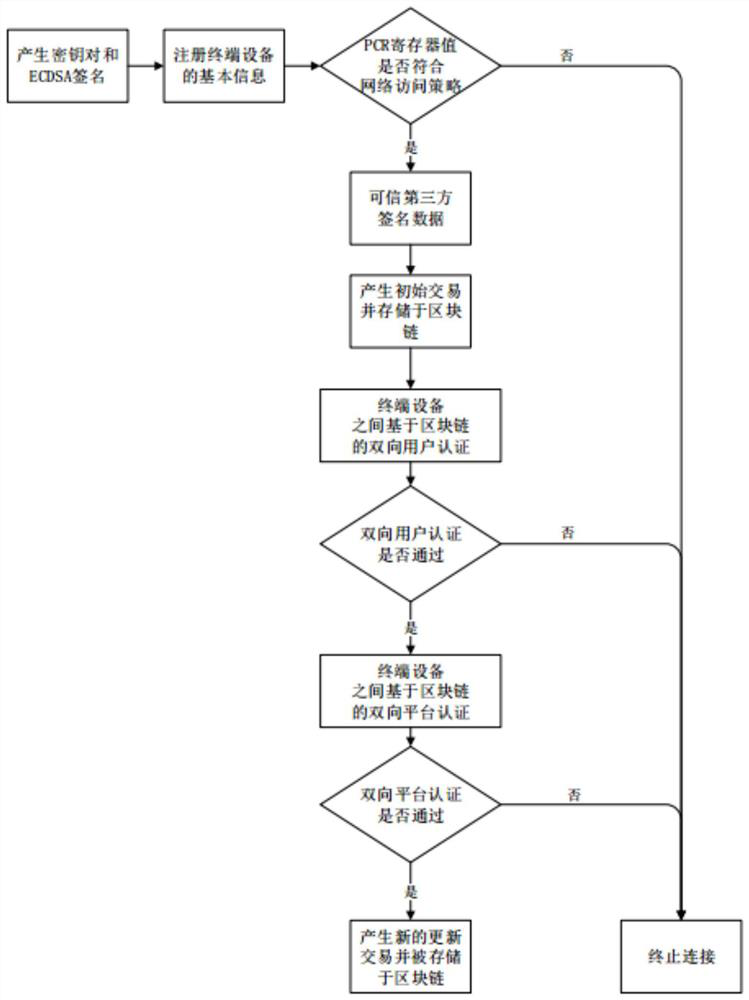
Blockchain-based distributed trusted network connection method
ActiveCN109981639BGuaranteed verifiabilityReduce riskKey distribution for secure communicationFinanceAttackEngineering
The invention discloses a blockchain-based distributed trusted network connection method. To solve the problem that the distributed network access control framework cannot be provided in the existing trusted network connection, the implementation plan is: in the initialization stage, the terminal device registers and sends the information; the trusted third party verifies the registration information; the terminal device generates the initial transaction and broadcasts; the initial The transaction is stored in the blockchain; in the trusted network connection stage, any two terminals pass the two-way user and platform authentication of the blockchain; after the authentication is passed, in the update transaction stage, the terminal device generates an update transaction and broadcasts it; the update transaction is stored in the blockchain . The present invention combines blockchain and TNC to form an overall framework, without the participation of a trusted third party, to ensure two-way security authentication between users and platforms between terminal devices. Effectively defend against man-in-the-middle attacks and prevent malicious nodes from accessing the network. The invention is safe and credible, and is used for safe and credible connections in distributed networks.
Owner:XIDIAN UNIV
A smart grid equipment safety diagnosis service system based on blockchain technology
ActiveCN108880863BGuaranteed permanenceGuaranteed to be tamper-proofFinancePower network operation systems integrationDiagnostic informationSmart grid network
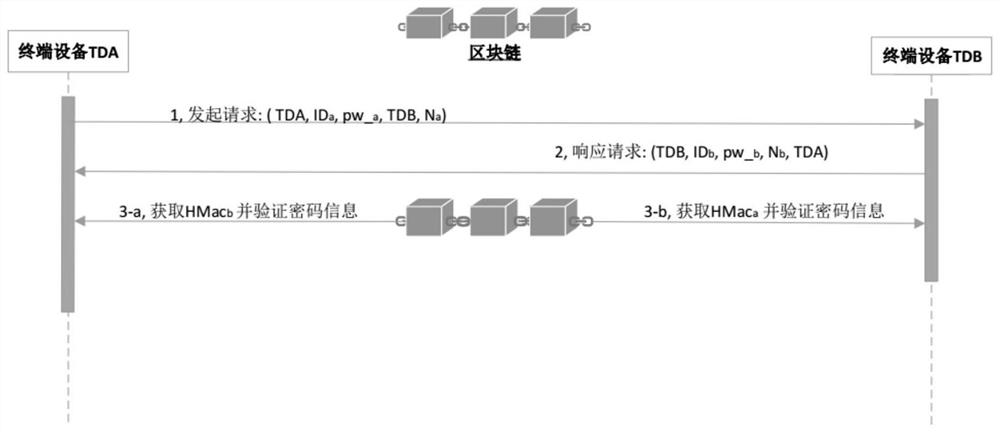
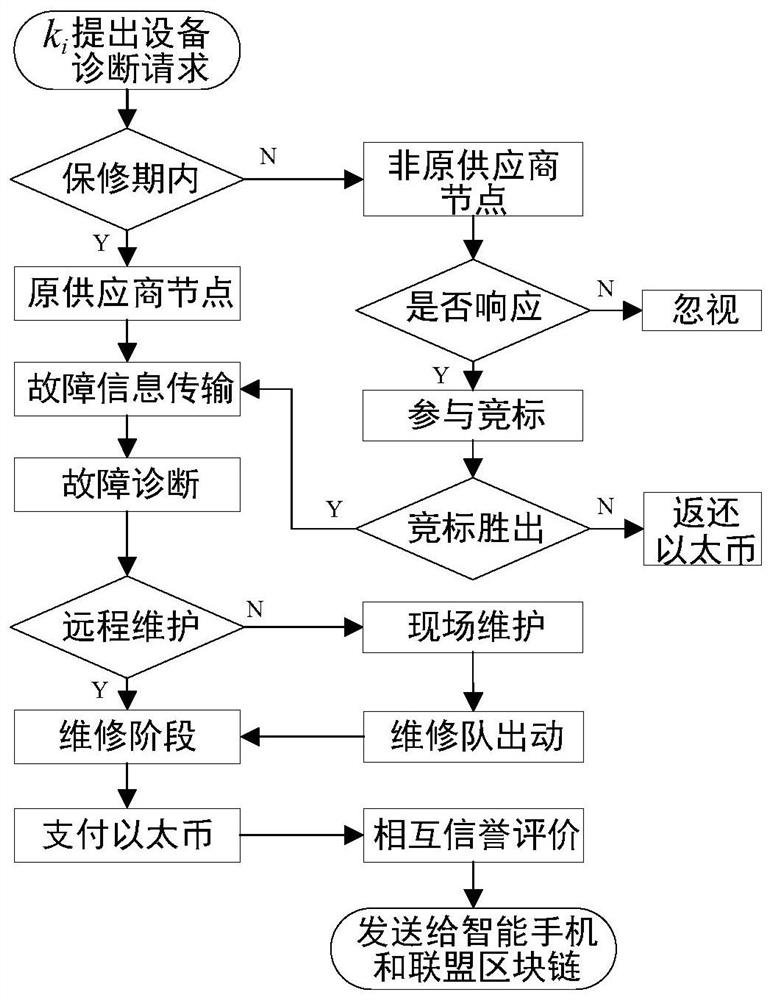
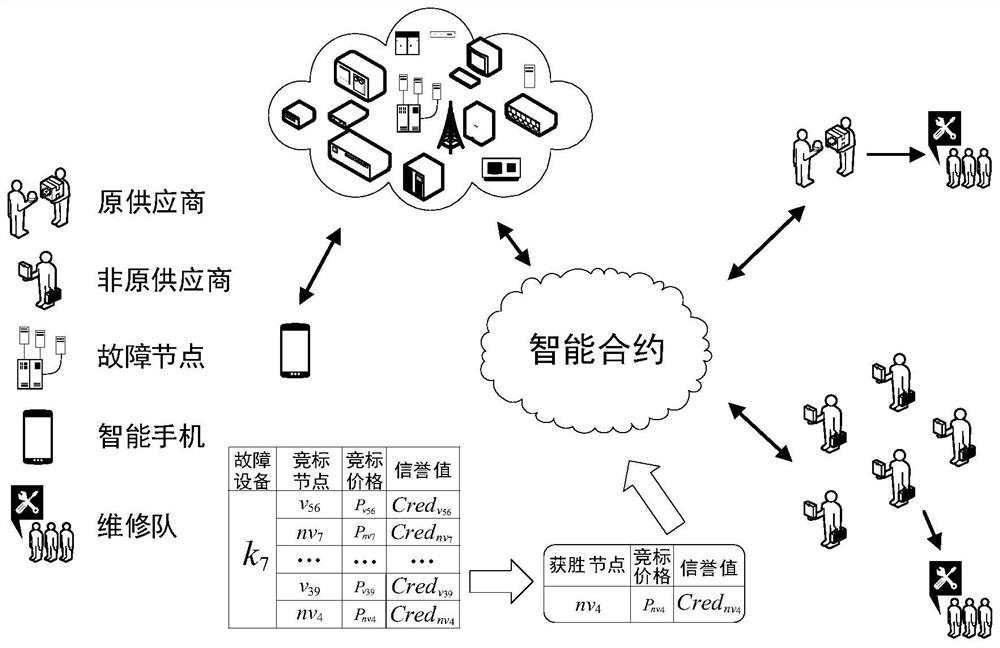
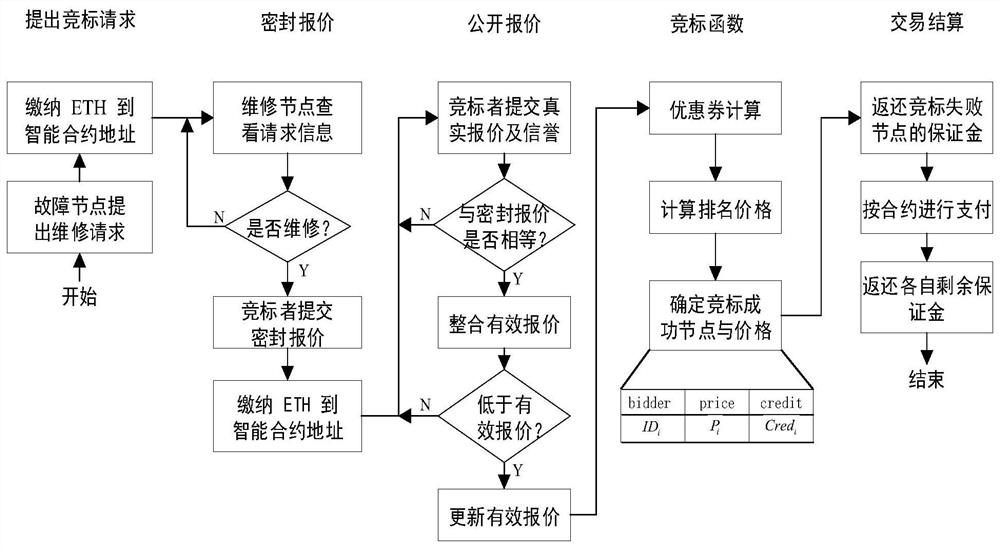
A security diagnosis service system for smart grid equipment based on blockchain technology, including three participants: faulty equipment, original and non-original suppliers of equipment, and smartphones owned by users. When the faulty device is within the warranty period, the original supplier node will provide free diagnostic services for it. Otherwise, the maintenance and diagnosis rights of the equipment will be decided by the original supplier node and non-original supplier nodes through the decentralized equipment security diagnosis smart contract. According to the bidding price and reputation value of the responding node, the contract uses a multi-dimensional reverse auction method to determine the successful bidding node and diagnosis price. After the device diagnosis is completed, the relevant diagnostic information will be packaged and sent to the smart phone. The user will formulate the device operation policy and control the smart contract through the smart phone and according to the received message, so as to realize the efficient operation of the device. In the process of information interaction, a homomorphic encryption algorithm is used to ensure the security of the interactive information, and to ensure that the diagnostic information and the privacy of both parties will not be leaked during the interaction.
Owner:JIANGXI UNIV OF SCI & TECH
A method for generating color commodity anti-counterfeiting code
ActiveCN105354717BThe generation method is simpleImprove securityCommerceChaotic systemsTheoretical computer science
The invention discloses a colorful commodity anti-counterfeiting code generating method. The colorful commodity anti-counterfeiting code generating method comprises the following steps: converting a commodity identification code for representing the unique identity information of a certain commodity into a binary data; obtaining an initial value and parameters of a chaotic system based on the commodity identity information and an external secret key through calculation, and performing iteration on a chaotic mapping to generate two groups of chaotic signal binary sequences; performing bit manipulation taking 2bits as a unit on the commodity identification code by the chaotic binary signals to generate an anti-counterfeiting number overlapped with a colorful background, and further combining the anti-counterfeiting number into the colorful commodity anti-counterfeiting code. The colorful commodity anti-counterfeiting code generating method provided by the invention is simple, feasible, high in safety, and difficult to be cracked; and in addition, the generated colorful commodity anti-counterfeiting code is has the uniqueness and unforgeability.
Owner:礼何科技(上海)有限公司
A method for generating a commodity anti-counterfeiting code
InactiveCN104657871BThe generation method is simpleUniqueness guaranteedCommerceCiphertextChaotic systems
The invention discloses a method for generating a commodity anti-counterfeiting code, which comprises the following steps: encoding commodity identity information according to certain predetermined rules to generate a unique commodity identification code; The identification code is converted into numerical data; the initial value, parameters, initial iteration steps and iteration interval steps of the chaotic system are calculated by using the commodity identity information and the external key, and two sets of chaotic sequences are generated after iterating the inclined chaotic tent map ; Use the position change scrambling rules before and after the two sets of chaotic signals to scramble the ciphertext characters in the corresponding relationship between numerical data, custom numerical data and ciphertext characters, generate commodity anti-counterfeiting numbers, and then combine to generate commodity anti-counterfeiting code. The method for generating the commodity anti-counterfeit code provided by the invention is simple and feasible, has strong security and is not easy to crack, and the generated commodity anti-counterfeit code has "uniqueness and unforgeability".
Owner:NANTONG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com