Blockchain-based distributed trusted network connection method
A network connection and blockchain technology, applied in the field of distributed trusted network connection based on blockchain, can solve the problems of high overhead cost, unreasonable, prolonged network communication transmission, etc., to ensure reliability and authenticity , the effect of resisting man-in-the-middle attacks and ensuring security and credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
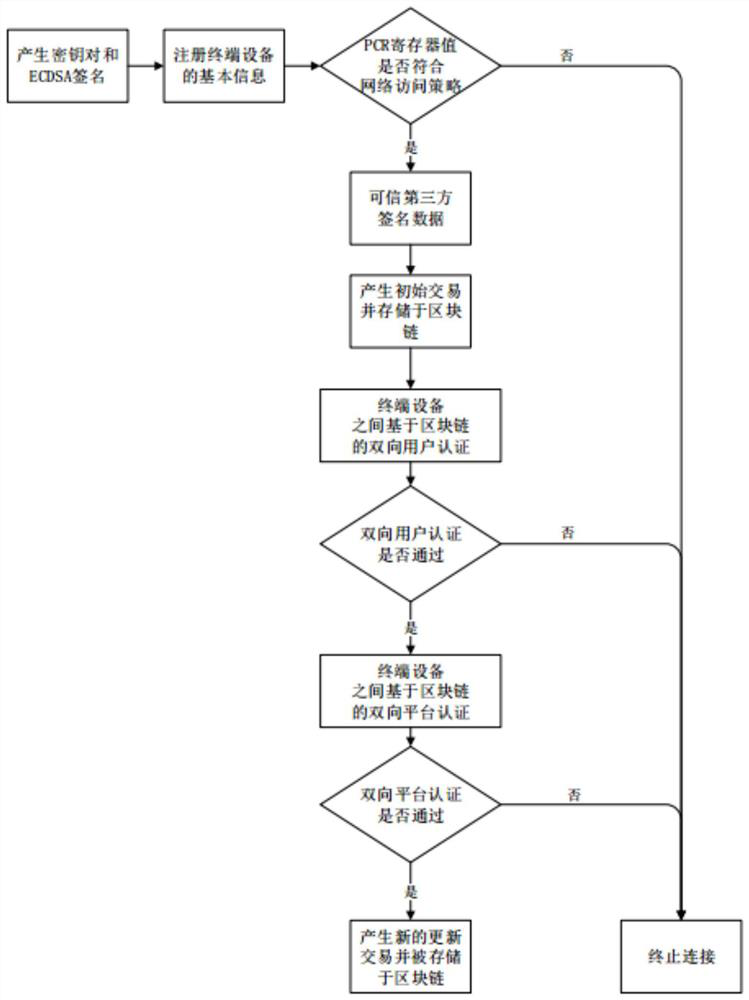
[0037]In network communication, with the development of centralized network structure to distributed network development environment and the application of Internet of Things technology, people are more dependent and frequent on the application of various terminal devices in life and work, but terminal devices are improving people's lives. Quality and work efficiency also have certain security risks. Once the terminal equipment in the network environment is maliciously attacked, people's privacy and property security will be greatly threatened. In order to solve this severe challenge, the world's Both researchers and developers are working together to find a safe and feasible solution.
[0038] The present invention carries out innovation and research on these problems, and proposes a distributed trusted network connection method based on blockchain. In order to ensure the security and credibility of terminal devices in a distributed network environment, two-way user authentic...
Embodiment 2
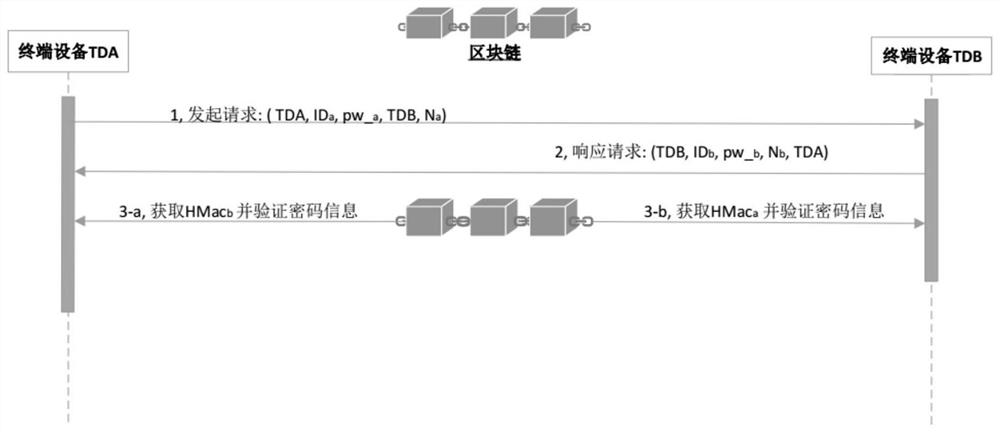
[0073] The blockchain-based distributed trusted network connection method is the same as in Embodiment 1, and the terminal devices described in step (2.1) perform two-way user authentication through the blockchain. In order to express this process more clearly and conveniently, the present invention Use TDA terminal device and TDB terminal device to represent any two terminal devices in the distributed network that are undergoing two-way user authentication, specifically including the following steps:
[0074] (2.11) In a distributed environment, the TDA terminal device sends request information to the TDB terminal device. The request information includes its own device identification ID number, random number Na, and the ciphertext value of the user password to which TDA belongs, wherein the ciphertext value is determined by TDA It is obtained by encrypting the plaintext value of the password of the user using the TDA public key Kpub_a.
[0075](2.12) When TDB receives the req...
Embodiment 3
[0079] The blockchain-based distributed trusted network connection method is the same as that of Embodiment 1-2, and the terminal devices described in step (2.2) perform two-way platform authentication through the blockchain. In order to express this process more clearly and conveniently, The present invention uses a TDA terminal device and a TDB terminal device to represent any two terminal devices in the distributed network that are undergoing two-way platform authentication, specifically including the following steps:
[0080] (2.21) The TDA terminal device calculates the private key Kpri_tsa of a specific transaction according to its own ECDSA signature data; the TDB terminal device calculates the private key Kpri_tsb of a specific transaction according to its own ECDSA signature data.
[0081] (2.22) TDA accesses the blockchain and obtains the ECDSA signature value in TDB's initial transaction; TDB accesses the blockchain and obtains the ECDSA signature value in TDA's init...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com