A Proxy Reassignment Verifier Signature Method
A designated verifier and re-signature technology, applied in the field of information security, can solve problems such as the non-existence of the designated verifier's signature
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
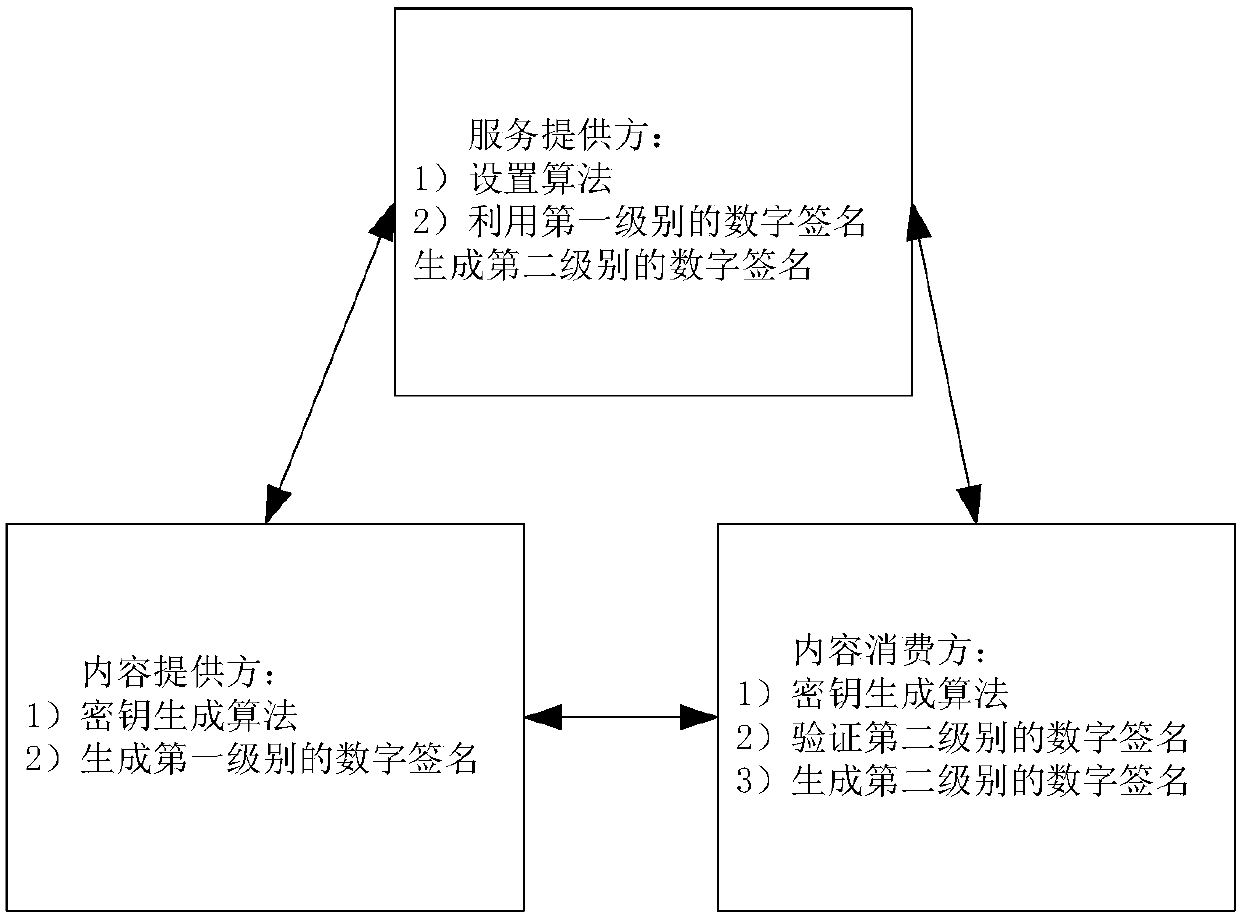
[0060] 1. The cloud storage platform runs the setting algorithm, and the steps to generate system parameters shared by all parties include:
[0061] 1)选择PBC软件库附带提供的A类型参数,其中素数阶q的取值为8780710799663312522437781984754049815806883199414208211028653399266475630880222957078625179422662221423155858769582317459277713367317481324925129998224791,生成元g是群G中的随机元素,对运算由PBC库所提供的“pairing”运算提供。
[0062] 2) Select the method disclosed by Tian et al. in the appendix of the ACISP 2012 paper "A short non-delegatable strongdesignated verifier signature" to set the symmetric encryption and decryption operations in which both the plaintext space and the ciphertext space are in the group;
[0063] 3) Select the SHA-256 algorithm as the hash function, set H 1 The initial message of the function is "function one", H 2 The initial message of the function is "function two", H 3 The initial message of the function is "function three", and all involved group elements are uniformly input into the hash function ...
Embodiment 2
[0098] Embodiment 2 is the same as Embodiment 1, except that the system parameters adopt other effective bilinear pairing mappings, such as other types of parameters in the PBC library.
Embodiment 3
[0100] Embodiment 3 is the same as Embodiment 1, except that other effective hash functions, such as SHA384, are adopted for the system parameters.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com