A method for generating commodity anti-counterfeit two-dimensional code
A technology of two-dimensional codes and commodities, which is applied in the field of digital anti-counterfeiting and can solve problems such as the use of criminals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
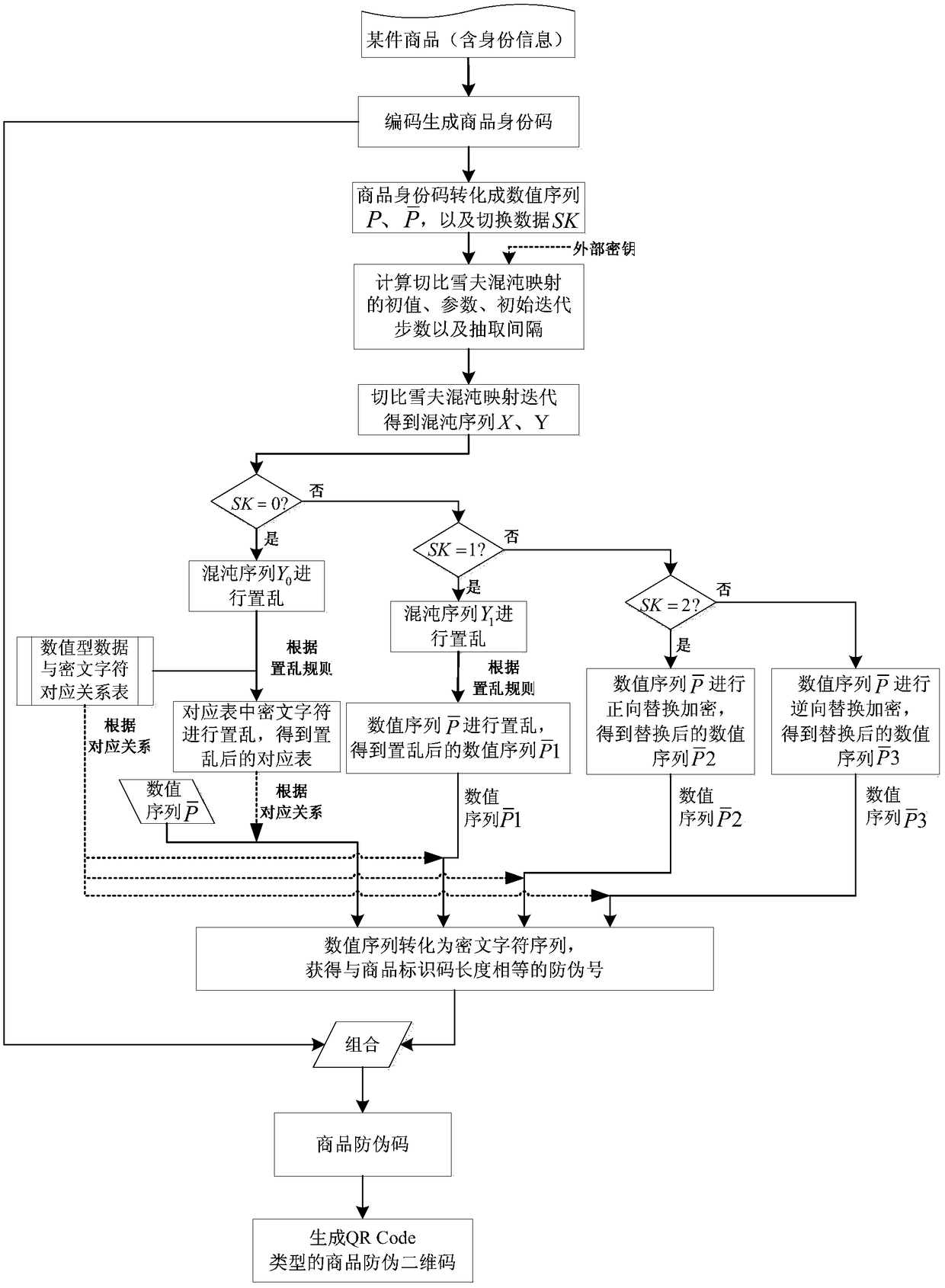
[0072] According to the method for generating an anti-counterfeiting QR code for a product in the above specific implementation, the steps are as follows:
[0073] (1) When the identity code of a commodity is coded as S="AB789 / ef12 2018-08-01 1234ab123456", the length L=34;
[0074] (2) Convert the commodity identity code S into ASCII code numeric data, and obtain the numeric sequence P={65,66,55,56,57,47,101,102,49,50,32,50,48,49,56,45, 48,56,45,48,49,32,49,50,51,52,97,98,49,50,51,52,53,54}, calculate the numerical sequence PP=24, switch data
[0075] (3) Use the Gost algorithm encryption value G of the product ID code = "A2188326467B7D393179C54AD9541CEC7280EB3F515925EED5F3CD4C3569027D" and the switching data SK = 0, take the external key (α = -0.12345, β = 3), according to the product anti-counterfeiting 2 in the above specific implementation The formula in step (3) of the dimensional code generation method calculates the initial value x of the chaotic system 1 , The parameter ...
Embodiment 2
[0087] According to the method for generating an anti-counterfeiting QR code for a product in the above specific implementation, the steps are as follows:
[0088] (1) When the identity code of a commodity is coded as S="aB789 / ef12 2018-08-01 1234ab123456", the length L=34;
[0089] (2) Convert the commodity identity code S into ASCII code numerical data, and obtain the numerical sequence P={97,66,55,56,57,47,101,102,49,50,32,50,48,49,56,45, 48,56,45,48,49,32,49,50,51,52,97,98,49,50,51,52,53,54}, calculate the numerical sequence PP=56, switch data
[0090] (3) Use the Gost algorithm encryption value G of the product identity code = "65513A6CA6140912C783794DD6117BDBD1C65B13E7A21B6DA0B568CF20E2AFF6" and the switching data SK = 1, take the external key (α = -0.12345, β = 3), according to the above specific implementation of the product anti-counterfeiting two The formula in step (3) of the dimensional code generation method calculates the initial value x of the chaotic system 1 , Th...
Embodiment 3
[0099] According to the method for generating an anti-counterfeiting QR code for a product in the above specific implementation, the steps are as follows:
[0100] (1) When the identity code of a commodity is coded as S="AB789\ef12 2018-08-01 1234ab123456", the length L=34;
[0101] (2) Convert the commodity identity code S into ASCII code numerical data, and obtain the numerical sequence P={65,66,55,56,57,92,101,102,49,50,32,50,48,49,56,45, 48,56,45,48,49,32,49,50,51,52,97,98,49,50,51,52,53,54}, calculate the numerical sequence PP=107, switch data
[0102] (3) Use the Gost algorithm encryption value G of the product ID code = "2D72181E2FB6BA4BE150BC18F5D3BF87CDD12B5BFFB1C2A0641DD9C405812836" and the switching data SK = 2, take the external key (α = -0.12345, β = 3), according to the above specific implementation of the product anti-counterfeiting two The formula in step (3) of the dimensional code generation method calculates the initial value x of the chaotic system 1 , The par...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com