MAC address encryption and decryption methods and apparatuses
A MAC address, encryption and decryption technology, applied in the field of embedded software copyright control in production, can solve the problems of low efficiency, poor flexibility, increased labor and time costs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described in detail with an embodiment below, but it should be noted that the protection scope of the present invention is not limited thereto.
[0049] In the production process of network equipment, the MAC address of the equipment is often modified with plaintext MAC address commands. In order to protect the copyright of embedded software, the MAC address needs to be encrypted before being set and saved to the equipment; the equipment is decrypted during operation. Get the real MAC address.
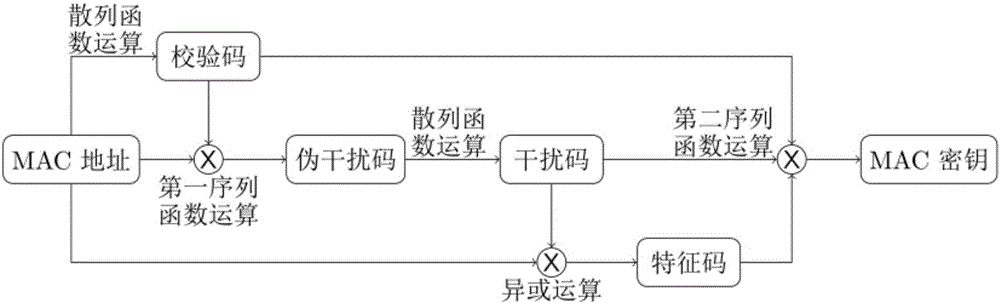
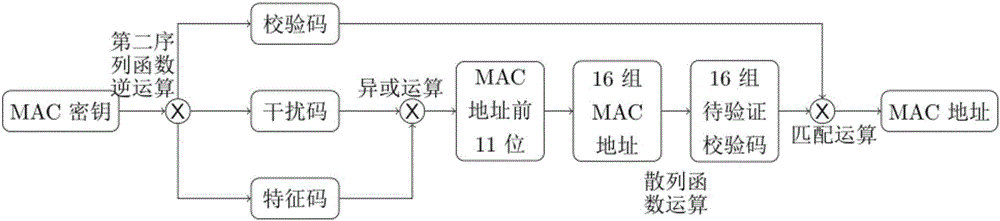
[0050] Such as figure 1 , image 3 Shown, the MAC address encryption method of the present invention is as follows:
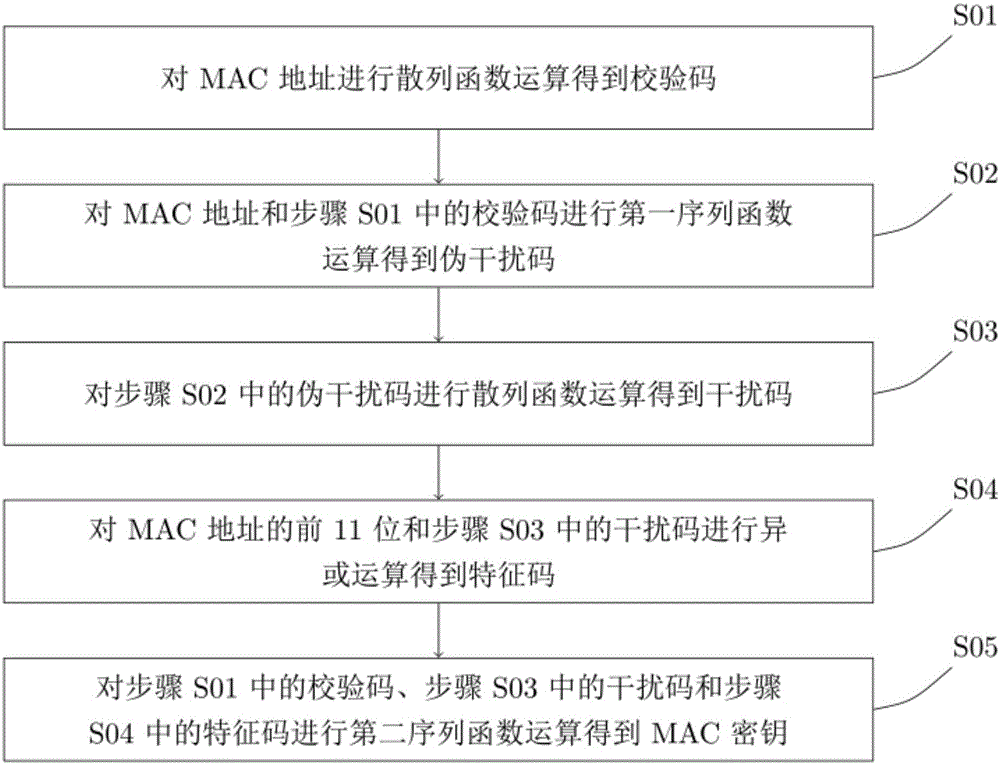
[0051] Step S01: performing a hash function operation on the MAC address to obtain a check code;
[0052] Step S02: performing a first sequence of functional operations on the MAC address and the check code in step S01 to obtain a pseudo-interference code;
[0053] Step S03: performing a hash function operation on the pse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com