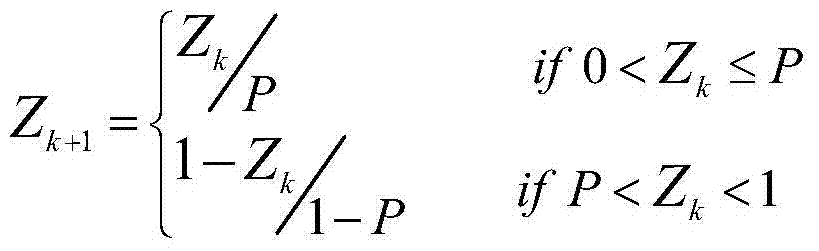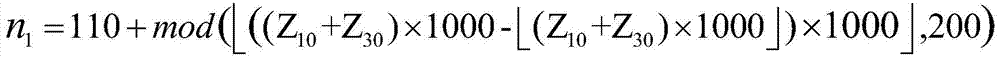A method for generating a commodity anti-counterfeiting code
A product anti-counterfeiting code and product technology, which is applied in commerce, equipment, data processing applications, etc., can solve problems such as complex calculations, low security, and limited codes of product identity information, and achieve strong security, difficult to crack, and generation methods Simple and Actionable Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
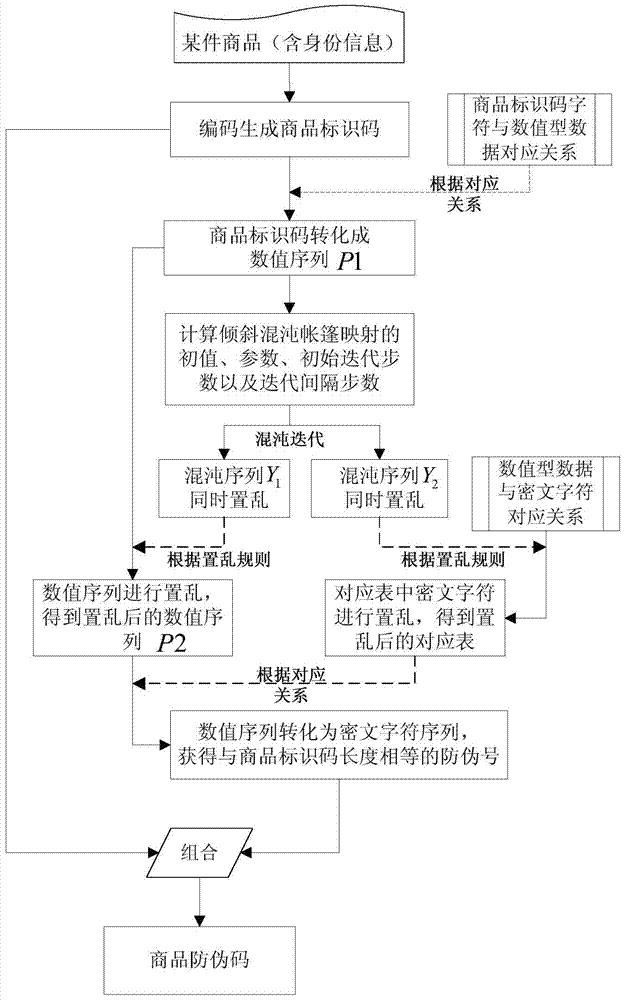
[0047] According to the above method of generating anti-counterfeiting codes for commodities, the steps are as follows:
[0048] (1) When the identification code of a commodity is coded as "A123E1212342014-12-26d1987654", the length L=30;
[0049] (2) According to the corresponding relationship between the custom product identification code characters and the numeric data in Table 1, the numeric sequence P1 is obtained as {10,1,2,3,14,1,2,1,2,3,4,2, 0,1,4,63,1,2,63,2,6,62,39,1,9,8,7,6,5,4};
[0050] (3) Take the external key (Z 10 = 0.12345, Z 20 =0.56789, Z 30 = -0.98765), using the product identity information (ie, the product identification code or numerical sequence P1 generated by the encoding) and the external key, the initial value X of the chaotic system is calculated according to the formula in step (3) of the above-mentioned product anti-counterfeiting code generation method 0 , Parameter P, initial iteration steps n 1 ,n 2 And the number of iteration steps m 1 ,m 2 Respect...
Embodiment 2
[0067] According to the above method for generating anti-counterfeiting codes for commodities, the steps for generating the identification code of a certain product and its anti-counterfeiting codes are similar to those in specific embodiment 1, except that a certain external key has a slight change: Z 10 =0.123450000000001; or Z 20 =0.567890000000001; or Z 30 = -0.987650000000001, the result of the product anti-counterfeiting code generation is shown in Table 4. It can be seen from the table below that once the external key changes even slightly, that is, "the smallest amount of loss", the generated product security number will be "a thousand miles away". It can be seen that the product security code generation method proposed by this patent has a key Sensitivity.
[0068] Table 4 When the external key changes slightly, the product anti-counterfeiting code generation result
[0069]
Embodiment 3
[0071] According to the above method for generating anti-counterfeiting codes for commodities, the external key and its anti-counterfeiting code generation steps are similar to those in specific embodiment 1, with slightly changed commodity identification codes (such as "A123E1212342014-12-26d1987653", "a123E1212342014-12-26d1987654" and "A123E1212342004" -12-26d1987654") generated product anti-counterfeiting code results are shown in Table 5. It can be seen from the following table that the slight change of the product identification code will cause the cipher text string (ie the product anti-counterfeiting number) to change greatly. It can be seen that the method for generating the product Identification code) is sensitive.
[0072] Table 5 The result of product anti-counterfeiting code generation when the product identification code changes slightly
[0073]
[0074] From the analysis of the above-mentioned specific embodiment 2 and example 3, it can be seen that the product an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com