Access control method for smart home environment based on private blockchain
A smart home and access control technology, applied in the field of information security, can solve problems such as deceiving smart home owners, denial, and owners' unwillingness to pay service fees
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below with reference to the drawings and embodiments.
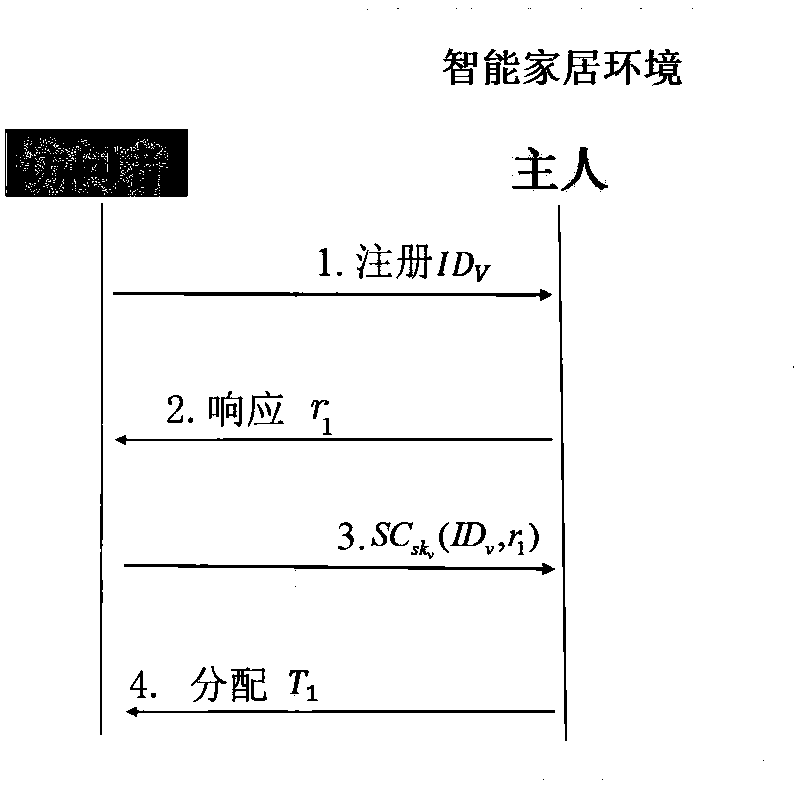
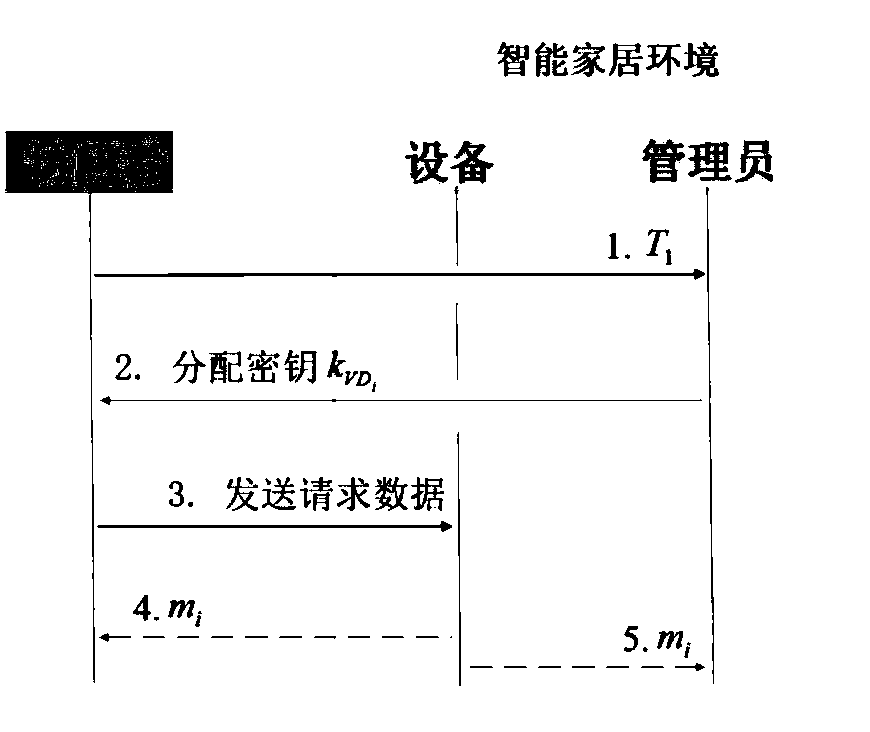
[0031] This embodiment provides a method for access control of a smart home environment based on a private chain. The flow chart of access control for a smart home environment based on a private chain is as follows: figure 1 Shown, including:
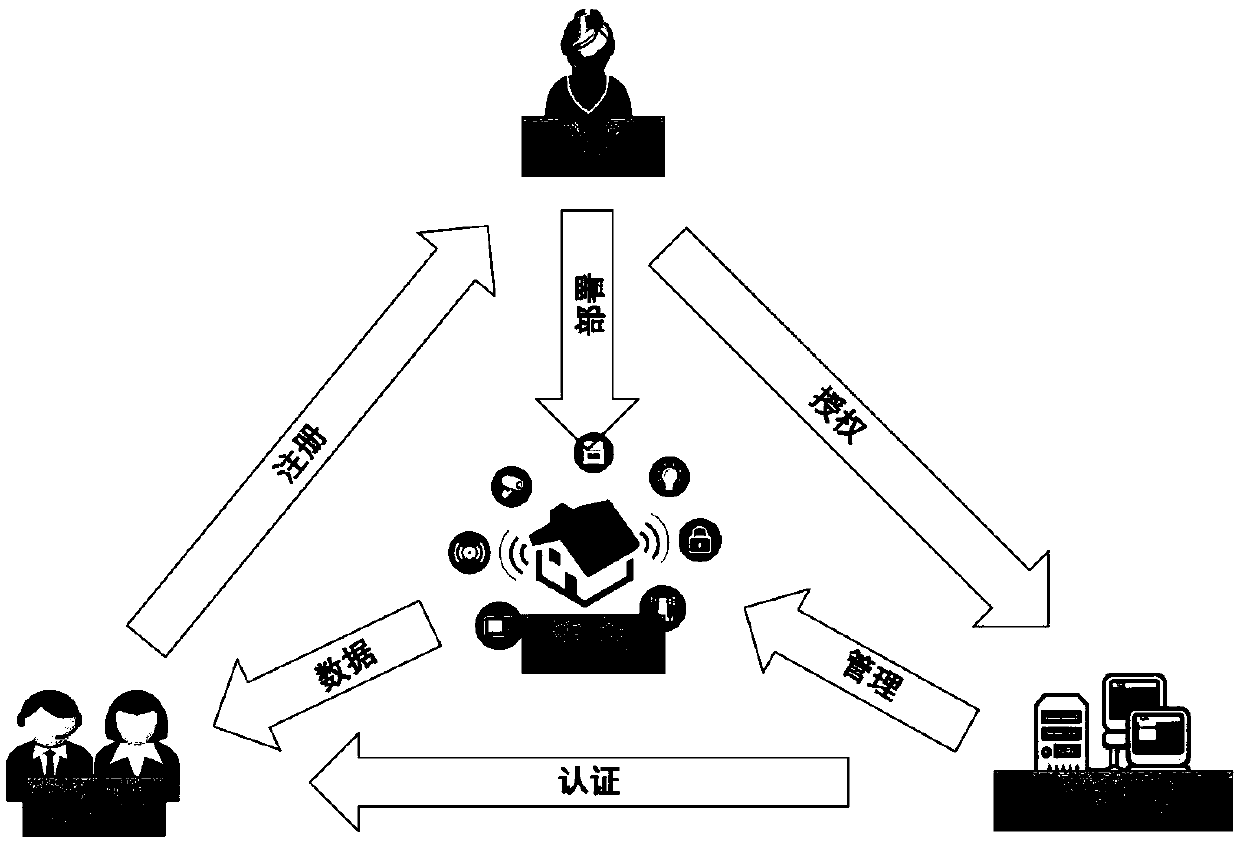
[0032] Initialization: first the smart home owner As a smart home manager Assign identity information and keys, and assign identity information to smart devices; then the owner writes the policy header into the first block of the private chain; finally, the smart home administrator and the smart device and smart home owner respectively Share different symmetric keys;
[0033] The specific method of initialization is:
[0034] The initialization algorithm selects a group G of prime order p 1 , A hash function H: {0, 1}*→Z p , A symmetric encryption algorithm E k′ (m) and a signcryption algorithm SC k′ (m), where the superscript * is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com