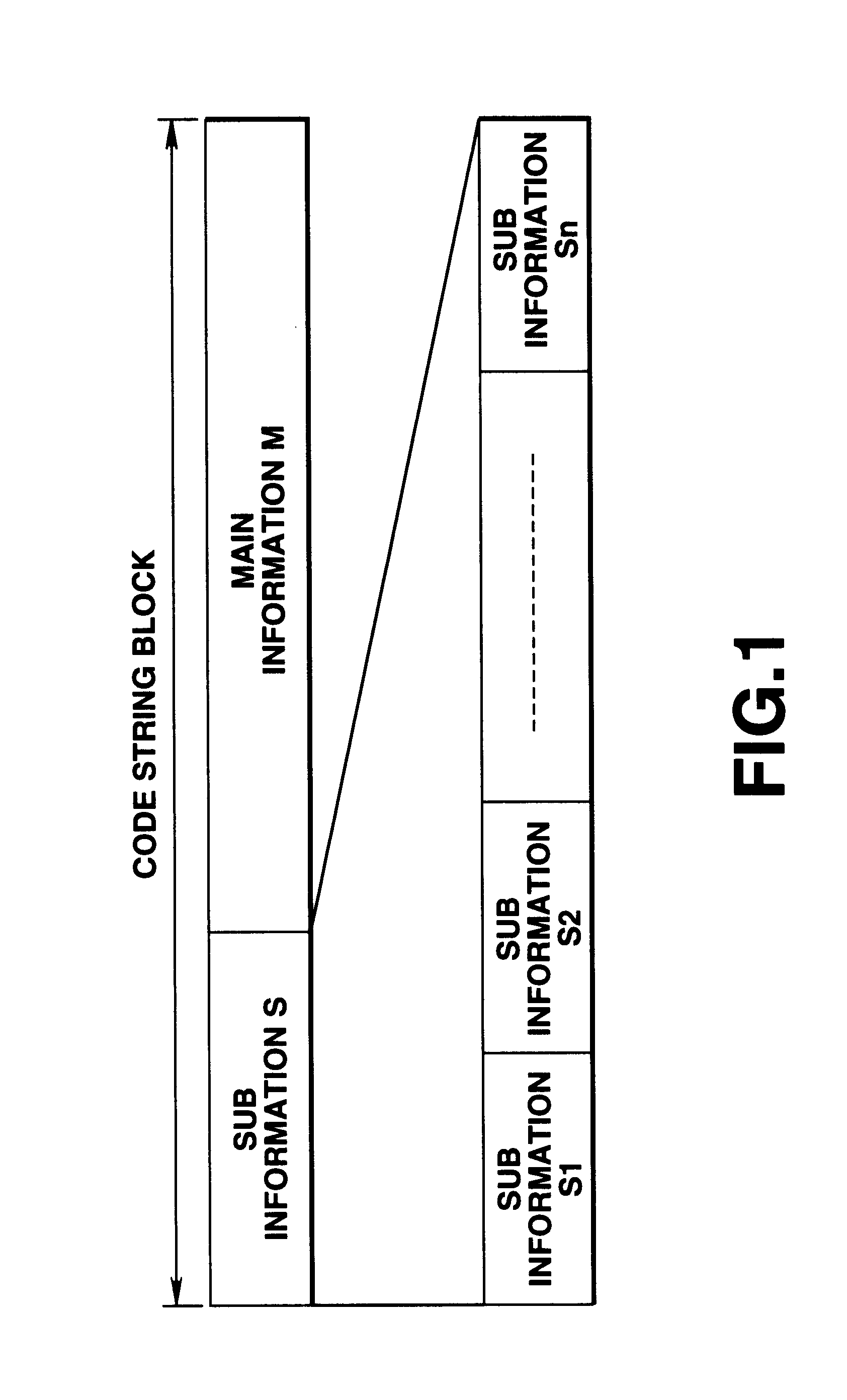
Patents
Literature
169 results about "String generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, string generation is the process of creating a set of strings from a collection of rules. This is an opposite process to that of parsing, which recognises a string based on some collection of rules.
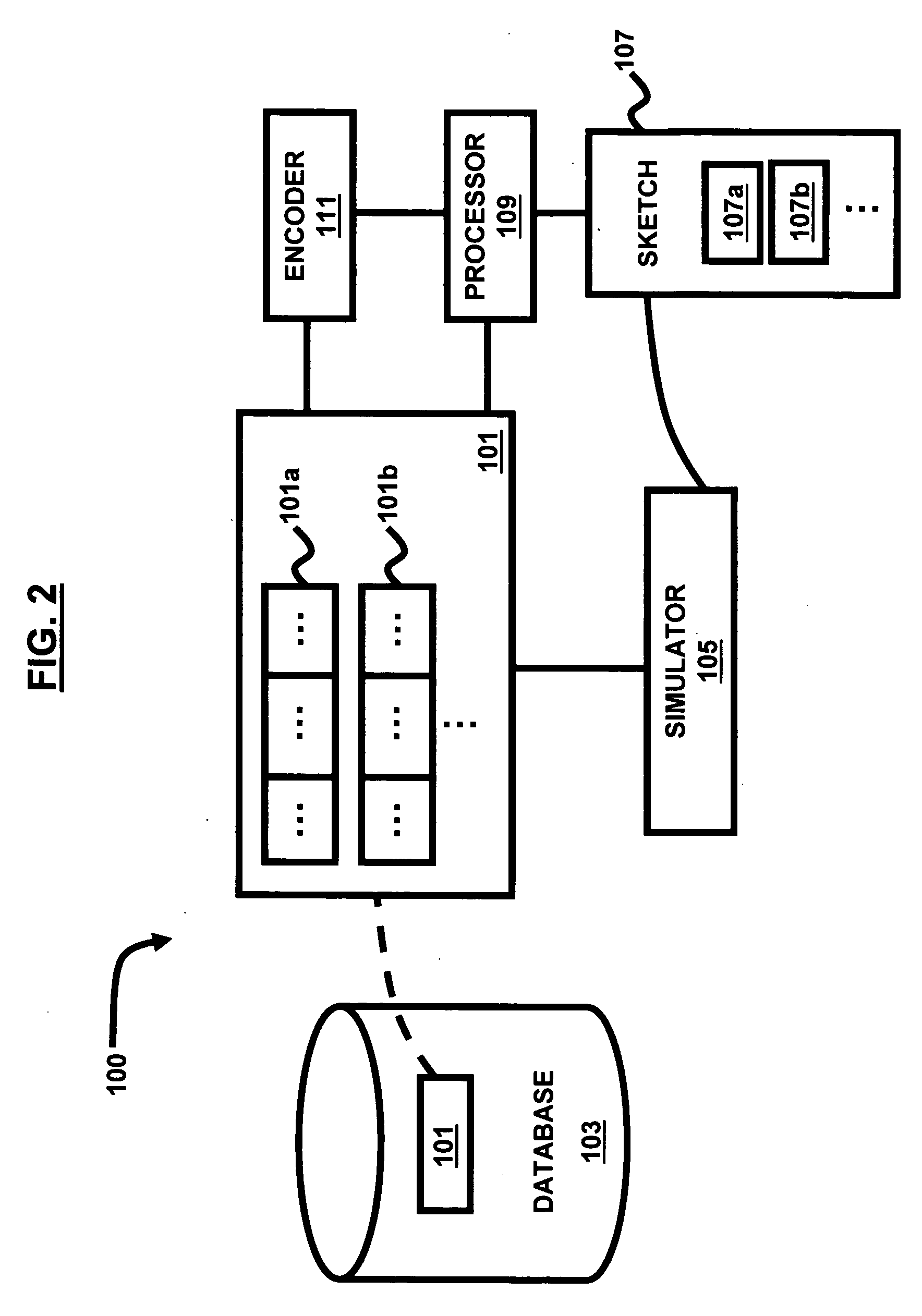
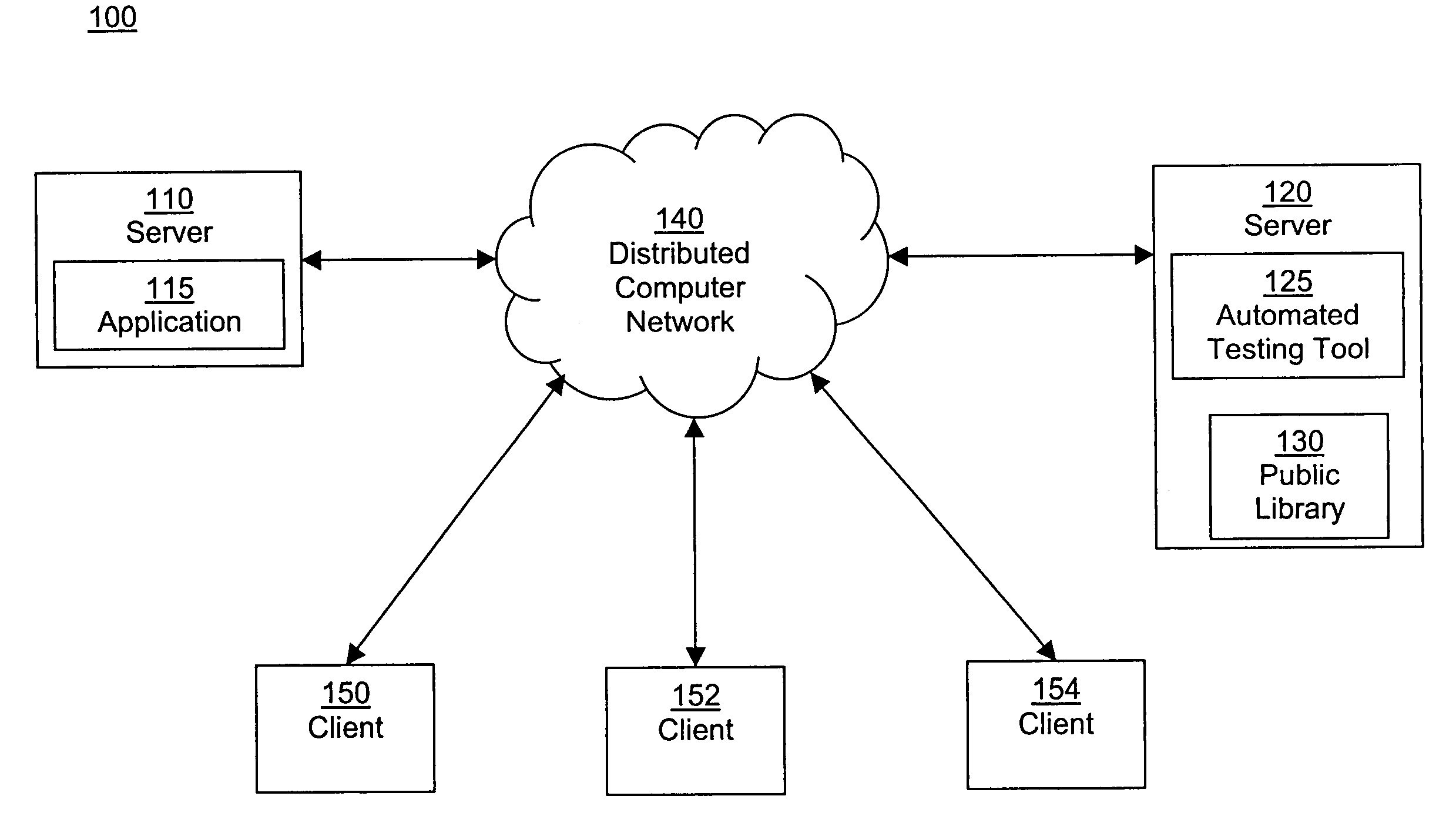
Methods and apparatus providing remote operation of an application programming interface
ActiveUS7010796B1Limited functionMultiprogramming arrangementsApplication programming interfaceApplication software
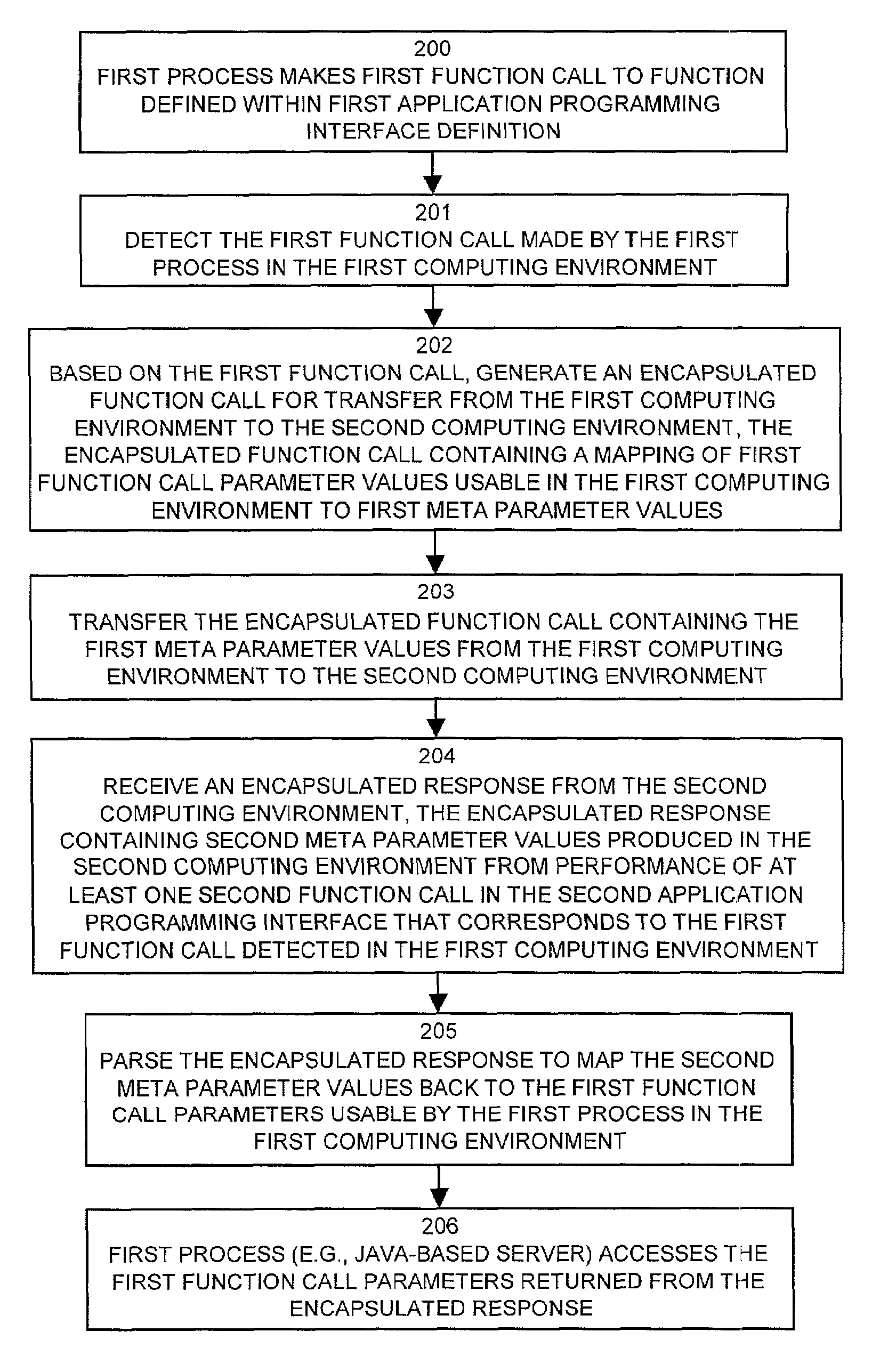
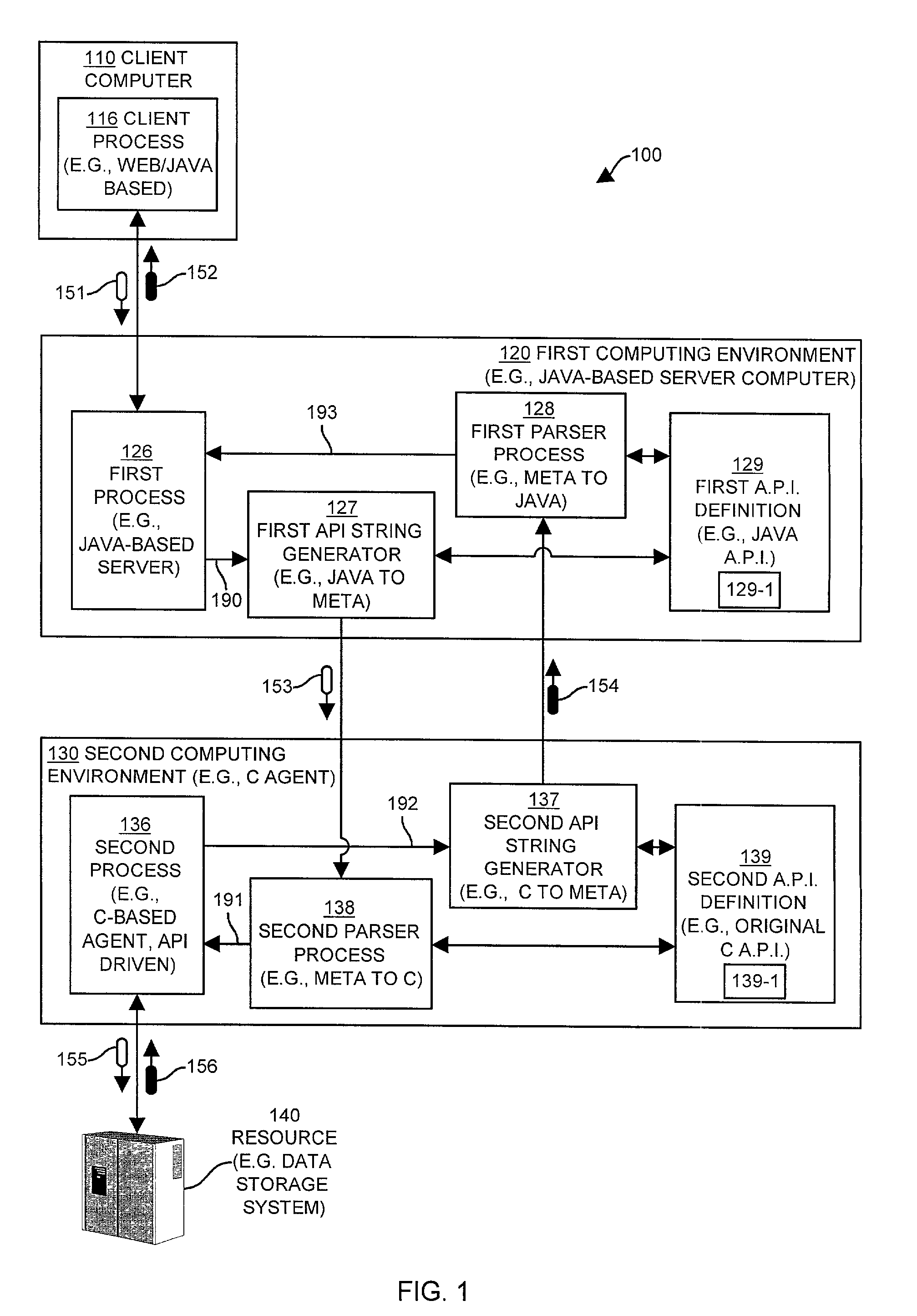
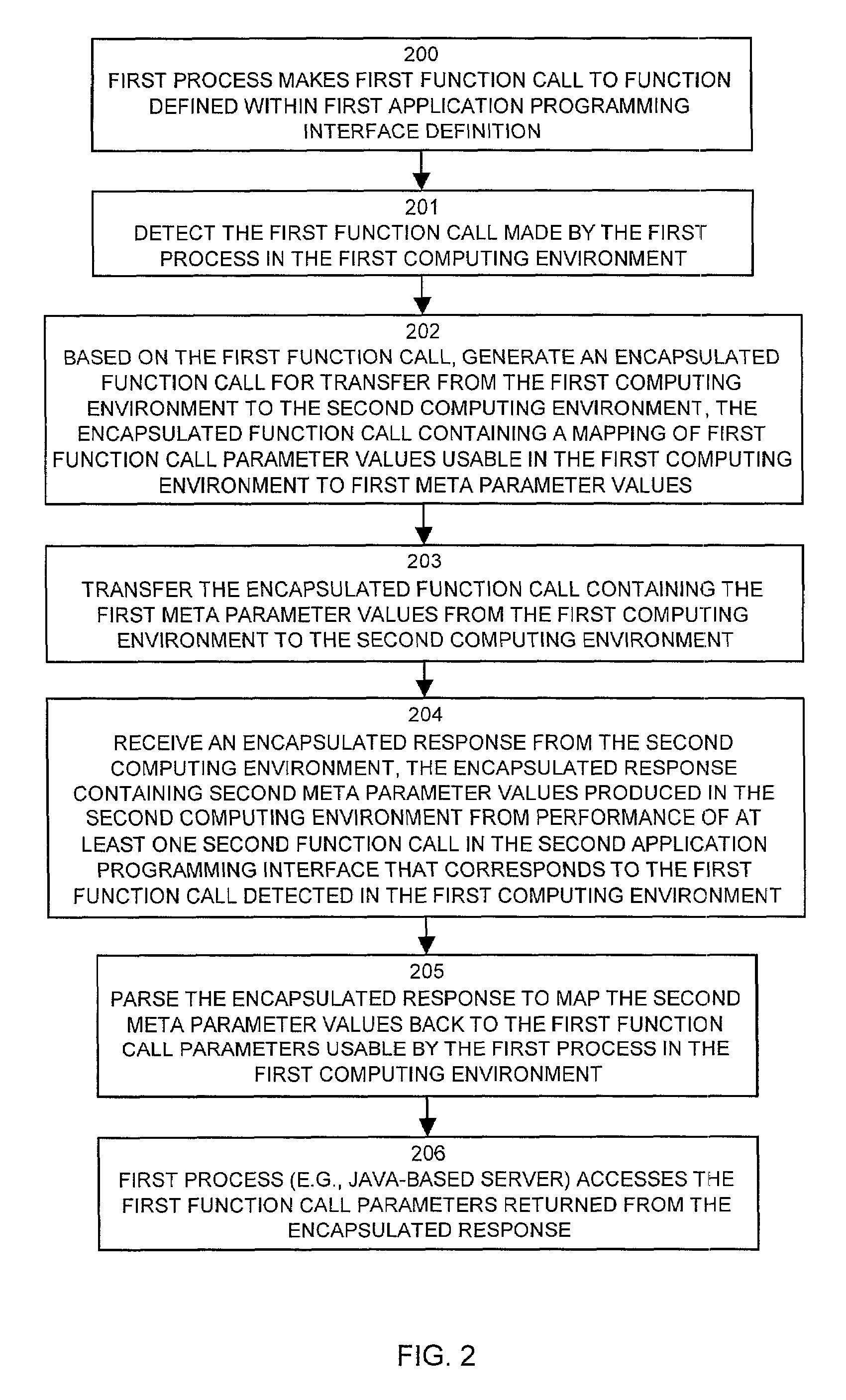
A system can analyze an application programming interface definition to automatically produce software string generator and parser software components allowing remote access to functions within the application programming interface definition by processes that are not natively compatible with the computing system environment in which the application programming interface operates. A first string generator processes can produce an encapsulated function call from a first process, such as a Java-based process, that calls a first function in a first computing environment. A second parser process operates in a second computing environment to receive the encapsulated function call and to invoke a second function call in a second process, such as a C-based process. Results from the second function call are returned to a second string generator which produces an encapsulated response that is returned to a first parser process. The first parser process maps the encapsulated response back into first function call parameters for return to the first process, thus providing access to second functions of the application programming interface by the first process.
Owner:EMC IP HLDG CO LLC
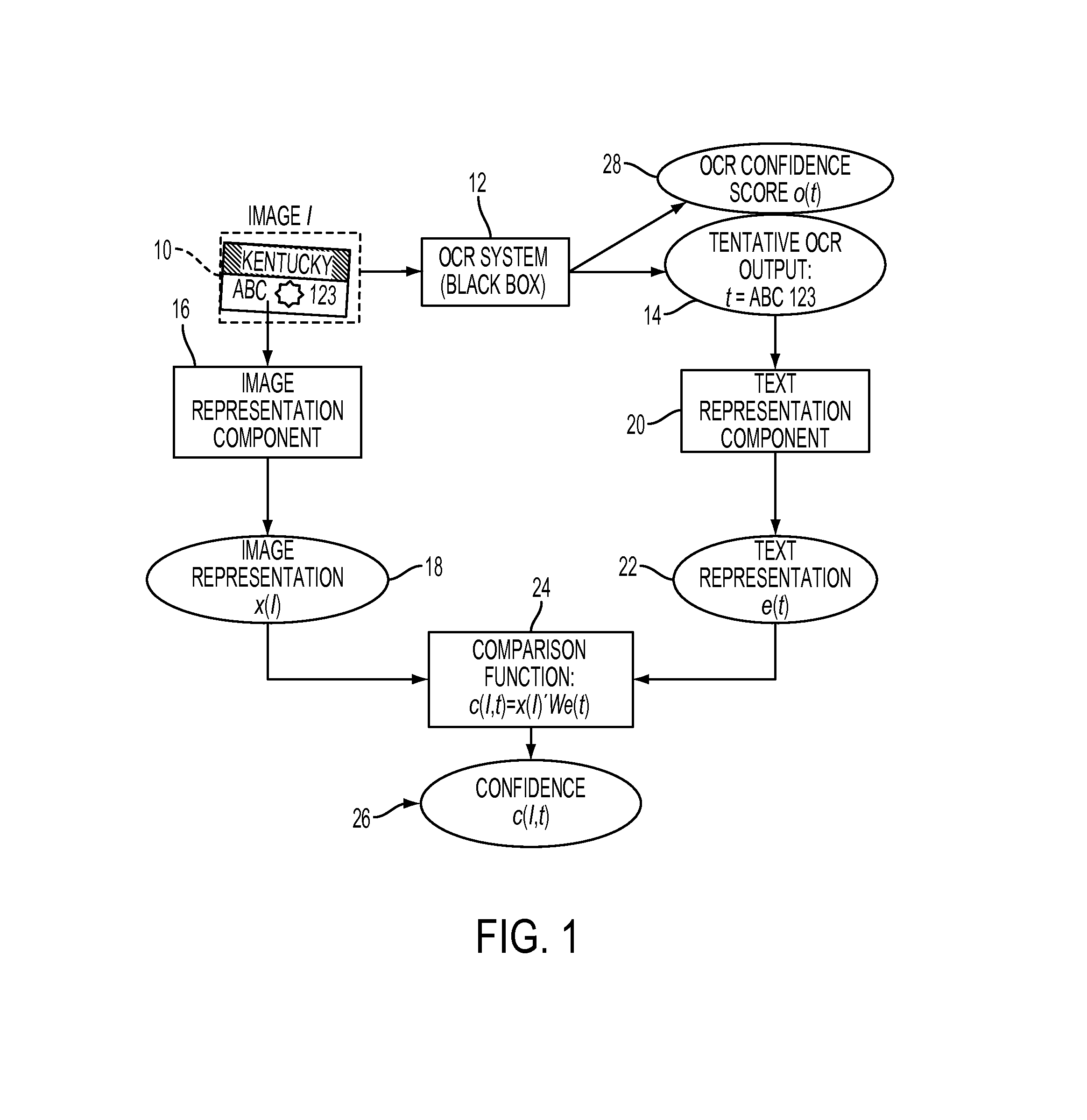
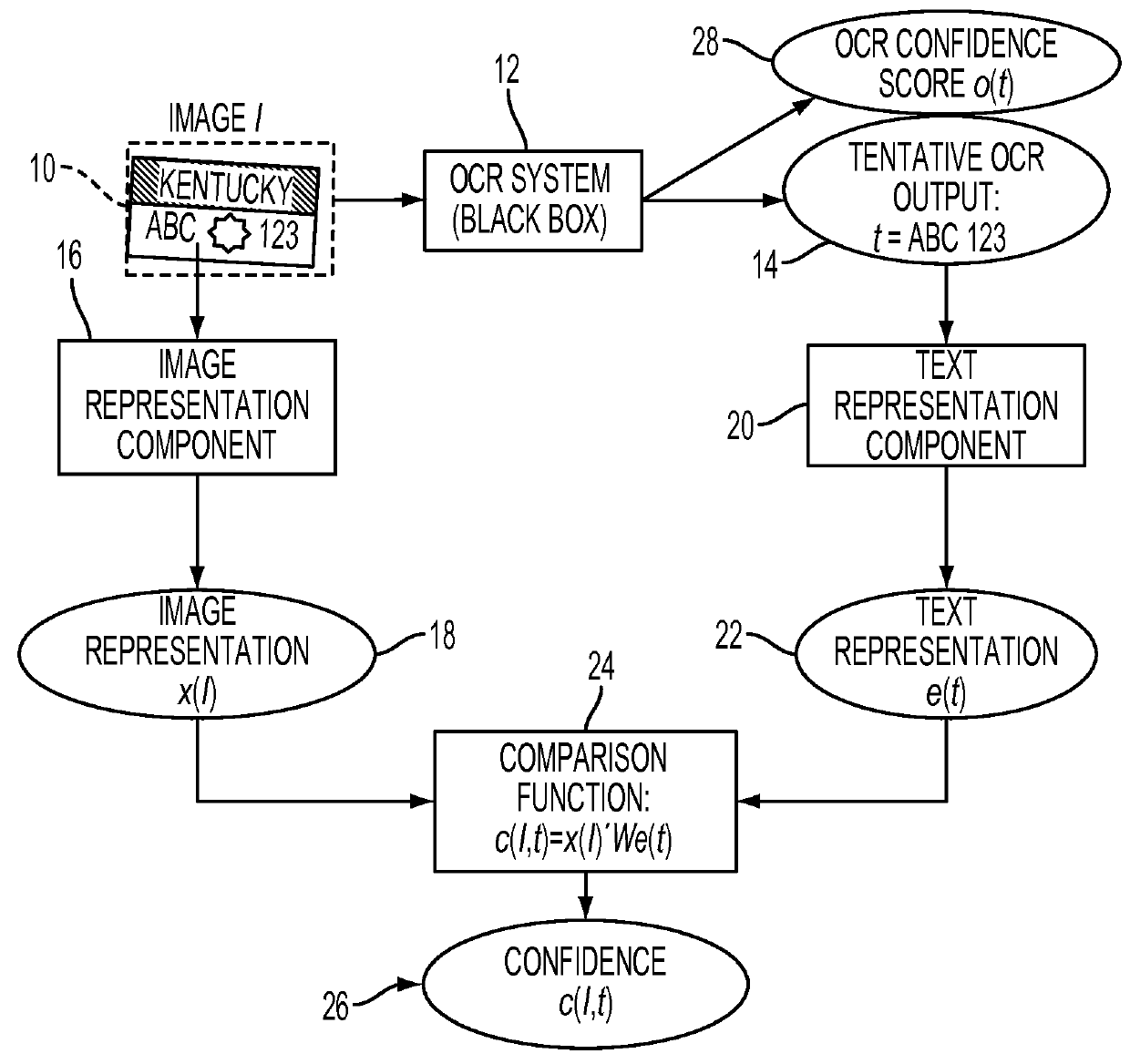
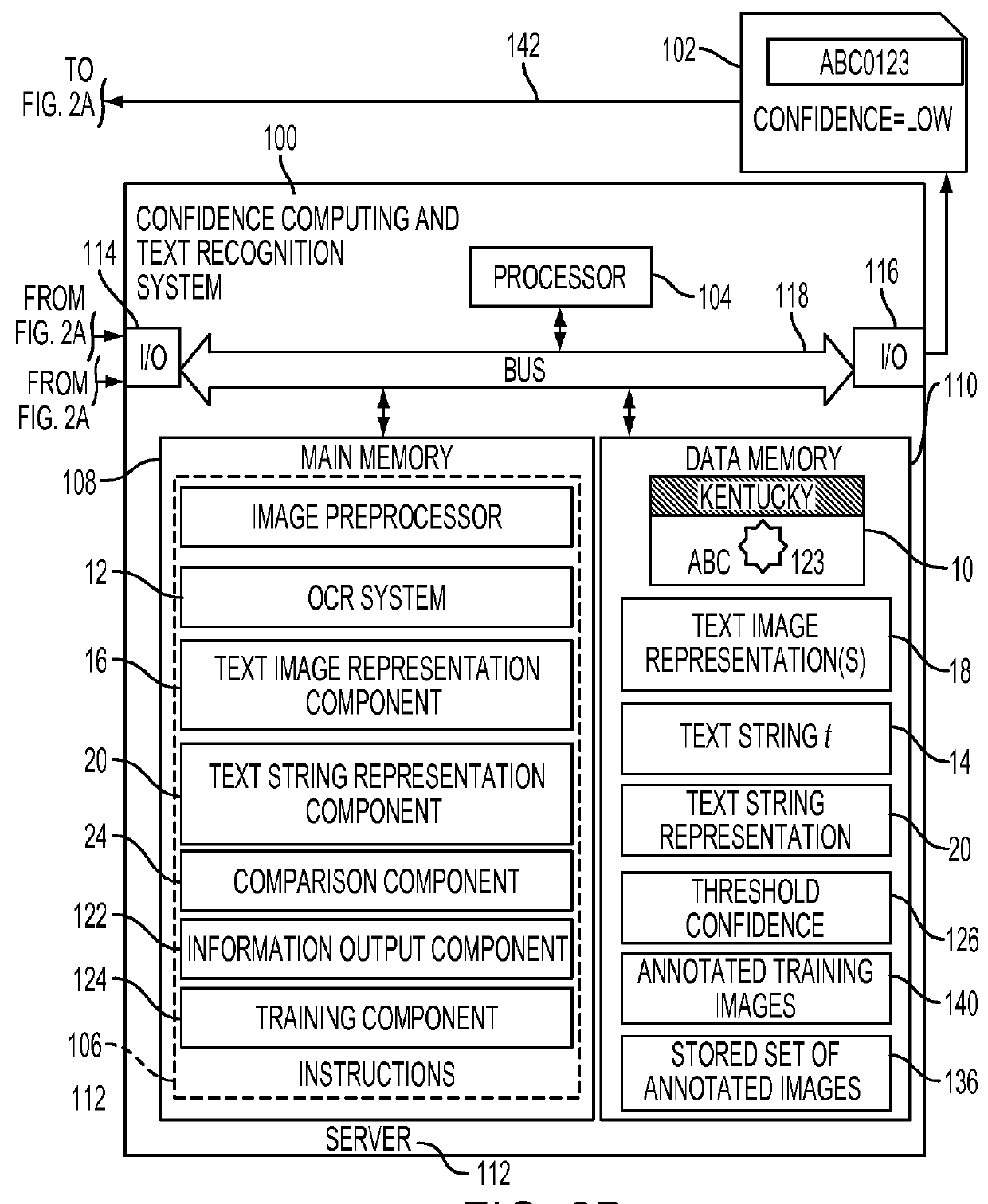
System and method for OCR output verification
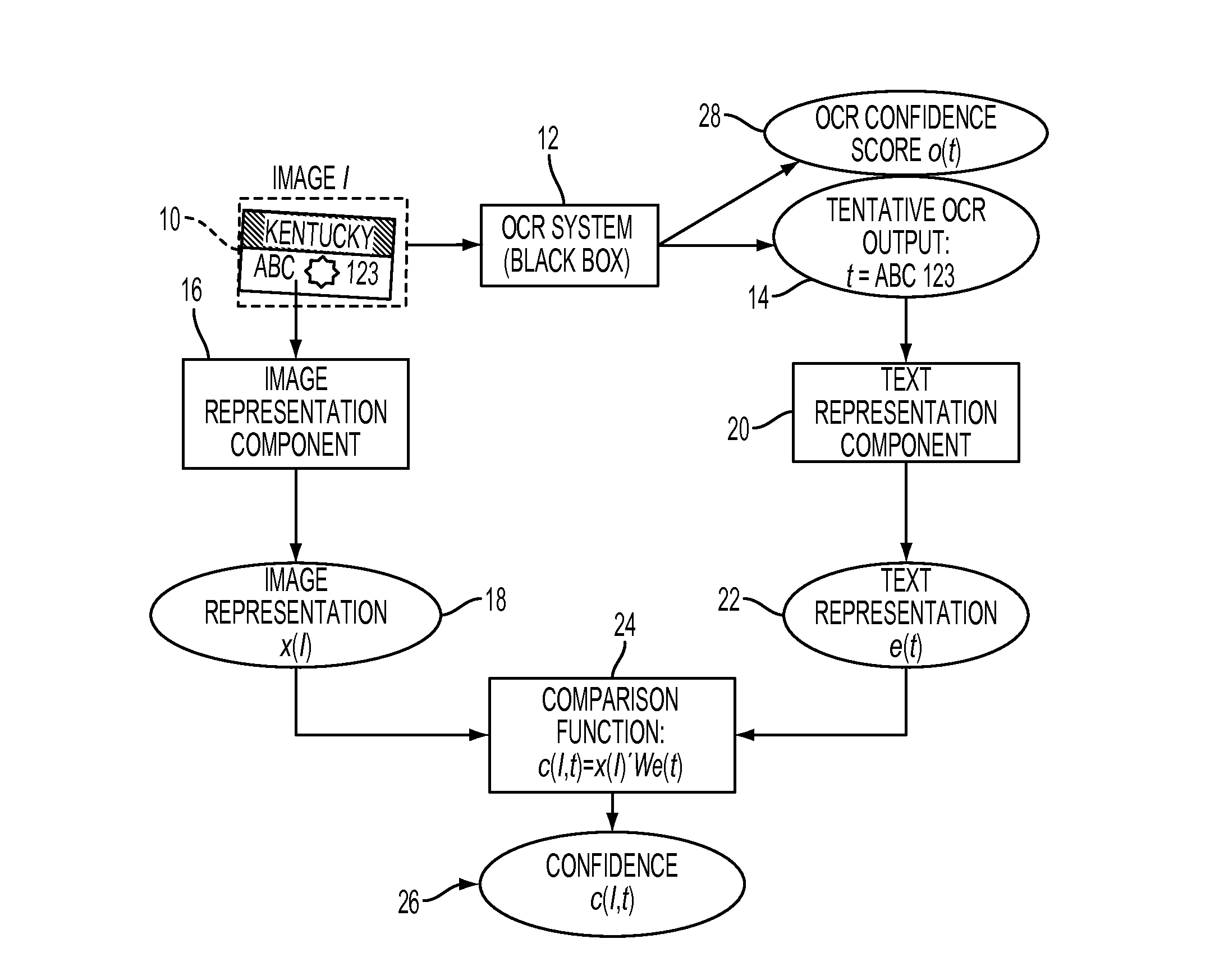
A system and method for computing confidence in an output of a text recognition system includes performing character recognition on an input text image with a text recognition system to generate a candidate string of characters. A first representation is generated, based on the candidate string of characters, and a second representation is generated based on the input text image. A confidence in the candidate string of characters is computed based on a computed similarity between the first and second representations in a common embedding space.
Owner:XEROX CORP
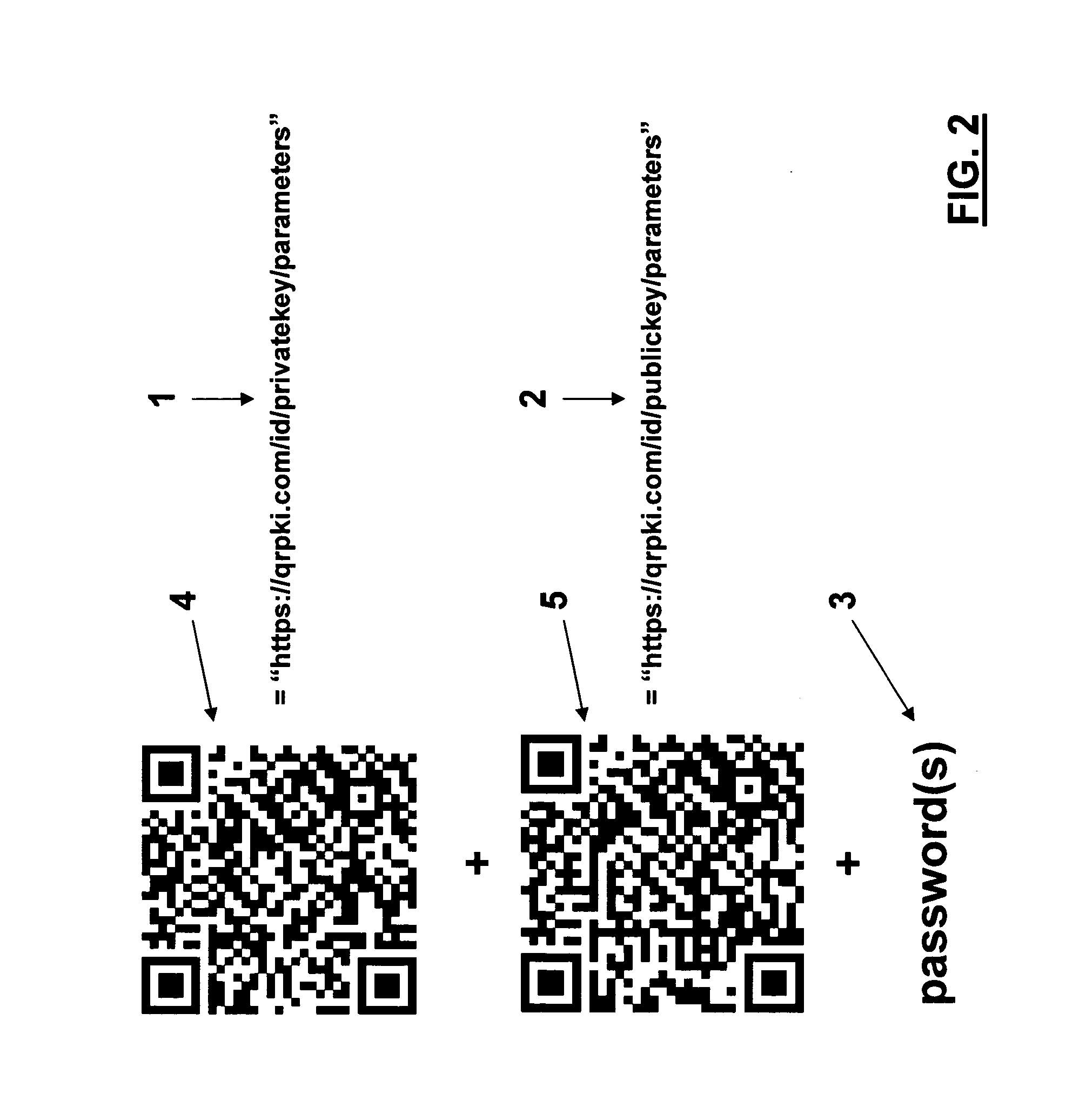
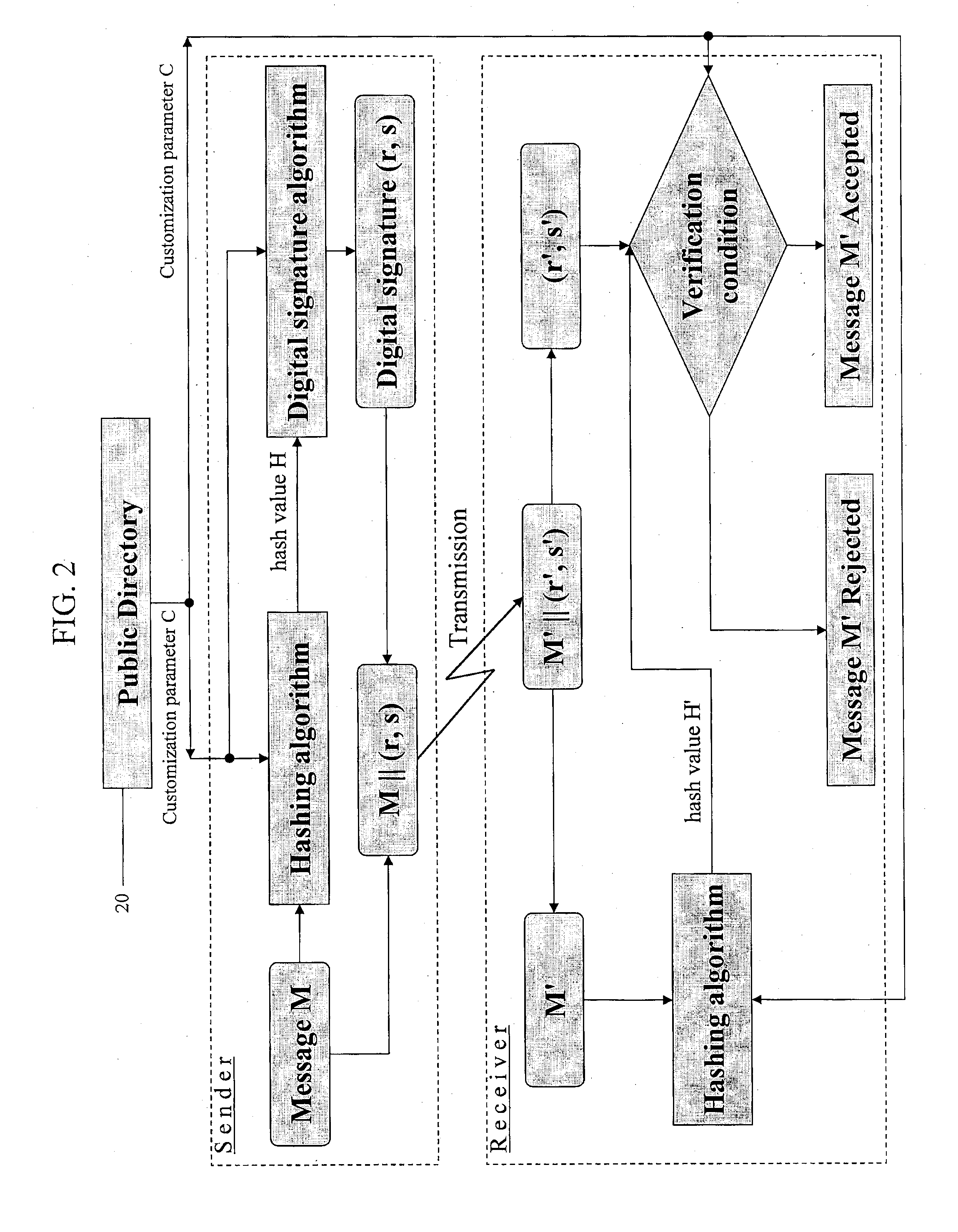
Method and system for authenticating entities by means of terminals
ActiveUS20140026204A1Easy to useDigital data processing detailsMultiple digital computer combinationsDomain nameUser input
In the disclosed method, users are provided with sets of authentication codes, each set includes a secret, a private key container and a matching public key container, the private and public key container are generated from respectively a first string including a domain name of an authentication server system and a PKI private key and a second string including the same domain name and a matching PKI public key. Upon receipt on the authentication server system of the first strings as a result of a first user reading the respective private key container, an action definition procedure is performed in which the first user is requested to enter a secret of the same set of authentication codes. If a check returns a positive result, the first user can define a set of actions to be performed upon receipt of the second string belonging to the same set of authentication codes.
Owner:BUNTINX
System and method for OCR output verification
A system and method for computing confidence in an output of a text recognition system includes performing character recognition on an input text image with a text recognition system to generate a candidate string of characters. A first representation is generated, based on the candidate string of characters, and a second representation is generated based on the input text image. A confidence in the candidate string of characters is computed based on a computed similarity between the first and second representations in a common embedding space.
Owner:XEROX CORP
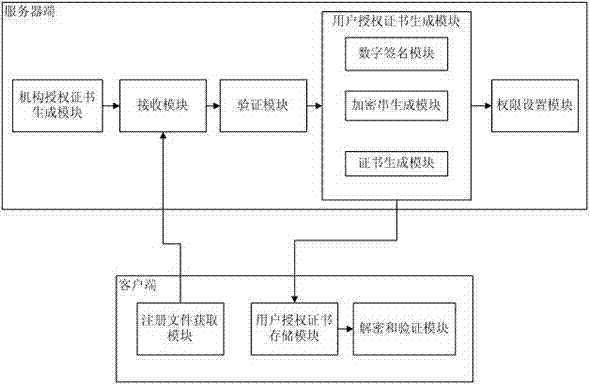
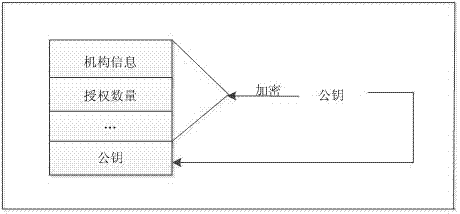
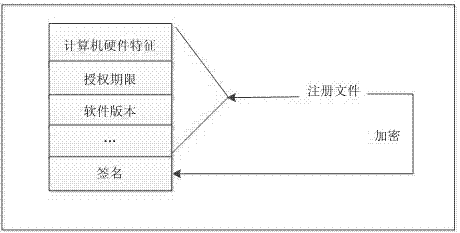
Software authorization system based on public key cryptosystem
ActiveCN103491097APrevent illegal copyingEasy to upgradeVersion controlUser identity/authority verificationAuthorization certificateAuthorization Mode
The invention discloses a software authorization system based on public key cryptosystem. The software authorization system comprises a server end and a client end, wherein the server end comprises an institution authorization certification generation module, a receiving module, a verification module and a user authorization certificate generation module. The user authorization certificate generation module comprises a digital signing module used for carrying out digital signing on computer hardware characteristics h0 in a user registration file with an RSA private key to generate S0, an encryption string generation module used for carrying out preset hybrid operations on obtained software version information v, user information u, an authorization term ex, current time cur and s0 to generate an encryption string signB64 and a certificate generation module used for generating a user authorization certificate with the encryption string signB64 and the RSA public key. The method can prevent software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
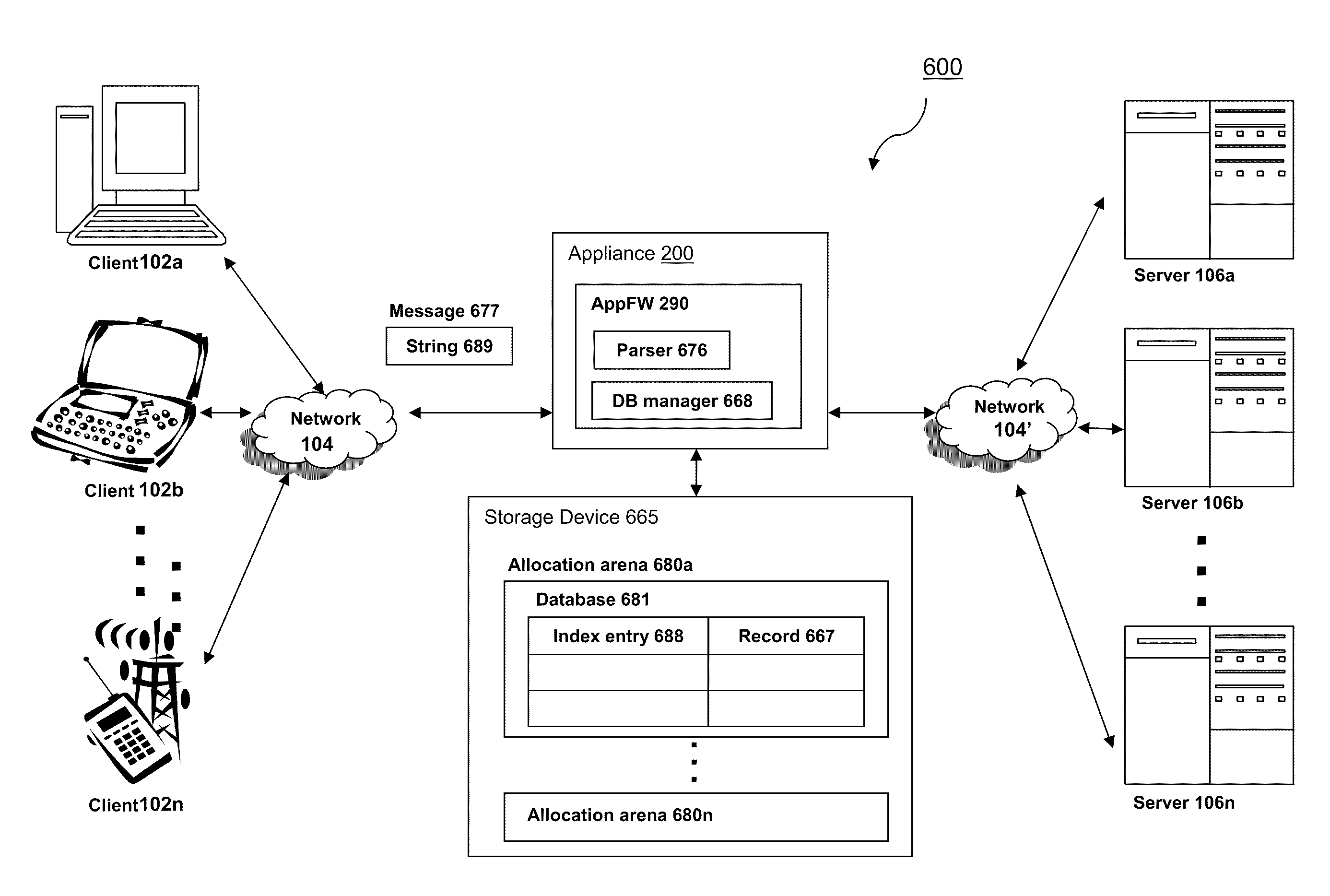
Systems and methods for management of common application firewall session data in a multiple core system
ActiveUS20110154461A1Efficient processingDigital data processing detailsComputer security arrangementsClient-sideUniform resource locator
The present invention is directed towards systems and methods for efficiently an intermediary device processing strings in web pages across a plurality of user sessions. A device intermediary to a plurality of clients and a server identifies a plurality of strings in forms and uniform resource locators (URLs) of web pages traversing the device across a plurality of user sessions. The device stores each string of the plurality of strings to one or more allocation arenas shared among a plurality of user session. Each string is indexed using a hash key generated from the string. The device recognizes that a received string transmitted from a webpage of a session of a user is eligible to be shared among the plurality of user sessions. The device determines that a copy of the received string is stored in an allocation arena using a hash generated from the received string. The device uses the copy of the received string stored in the allocation arena in place of the string in the web page of the session of the user to process the web page.
Owner:CITRIX SYST INC
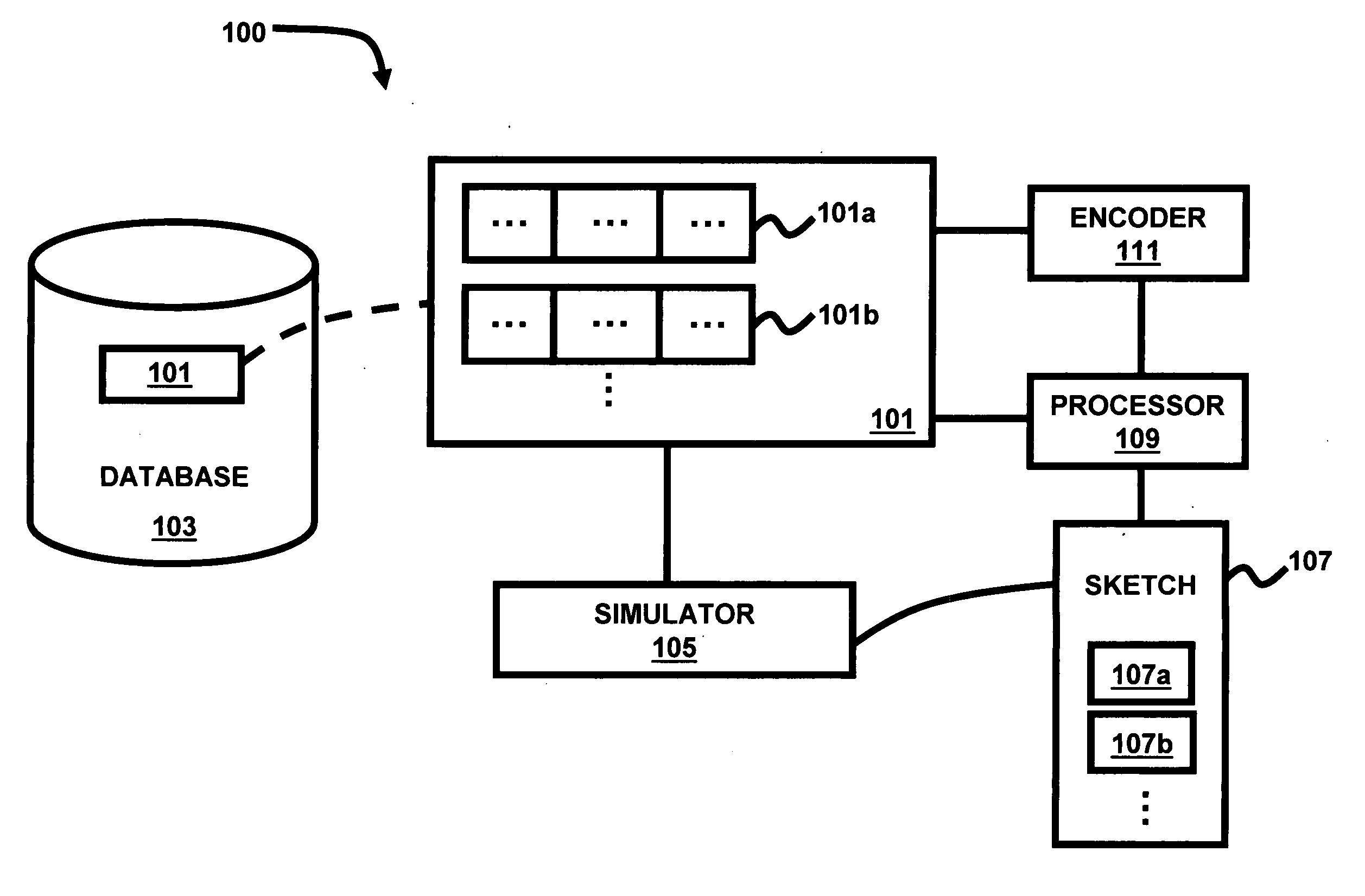
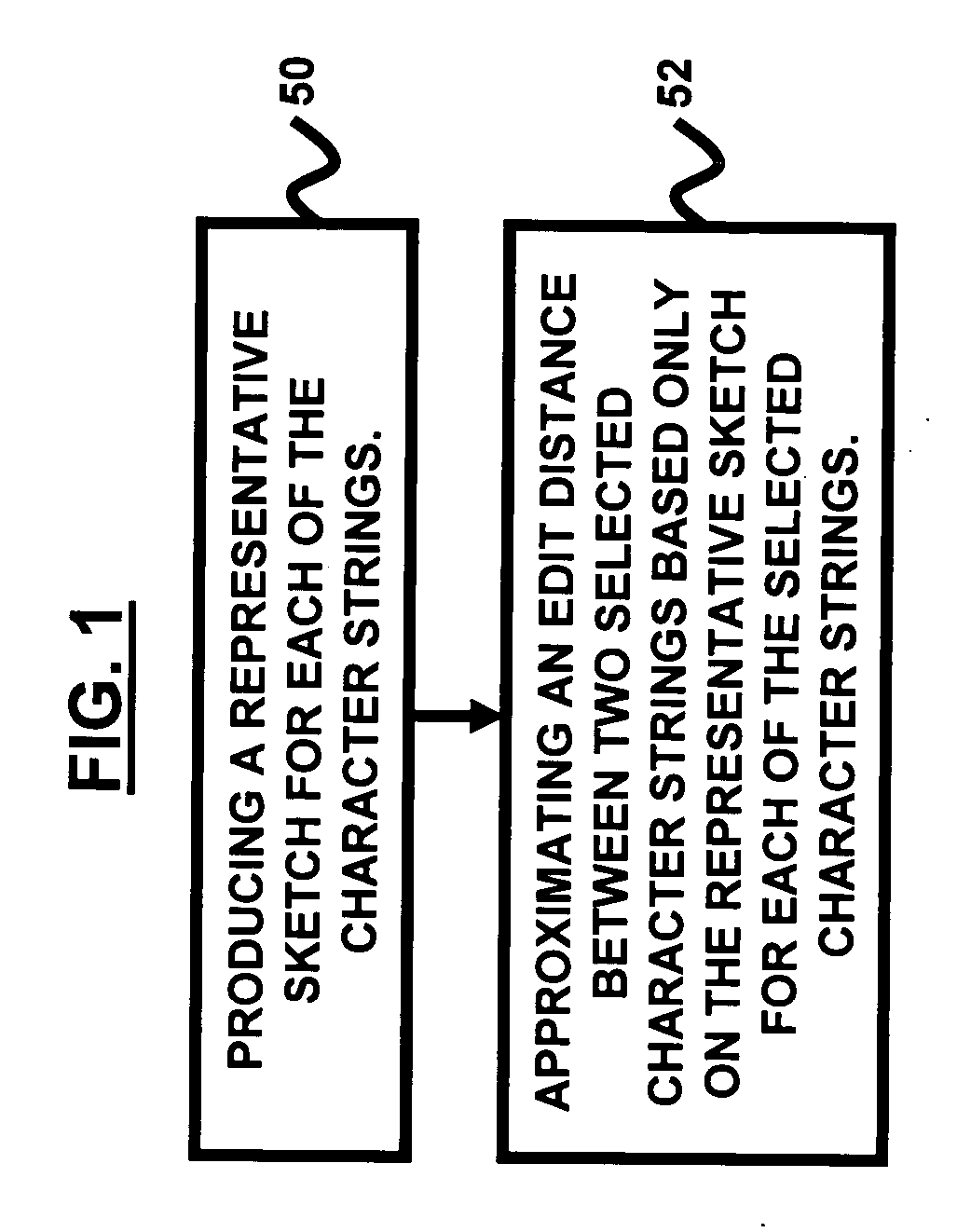
System and method for detecting matches of small edit distance
InactiveUS20070085716A1Digital data information retrievalCode conversionEdit distanceString generation
A system and method of approximating edit distance for a set of character strings in a database includes producing a representative sketch for each of the character strings; and approximating an edit distance between two selected character strings based only on the representative sketch for each of the selected character strings. The character strings may comprise text, wherein the method further comprises encoding positions of substrings in the text using anchors, wherein the anchors comprise identical substrings occurring in two input character strings at a nearby position. A set of anchors may be used in a correlated manner, wherein character strings with a sufficiently small edit distance are likely to use a same sequence of anchors. The character strings may be substantially non-repetitive. The representative sketch of a first character string is preferably constructed absent knowledge of a second character string. A size of the representative sketch may be constant.
Owner:IBM CORP
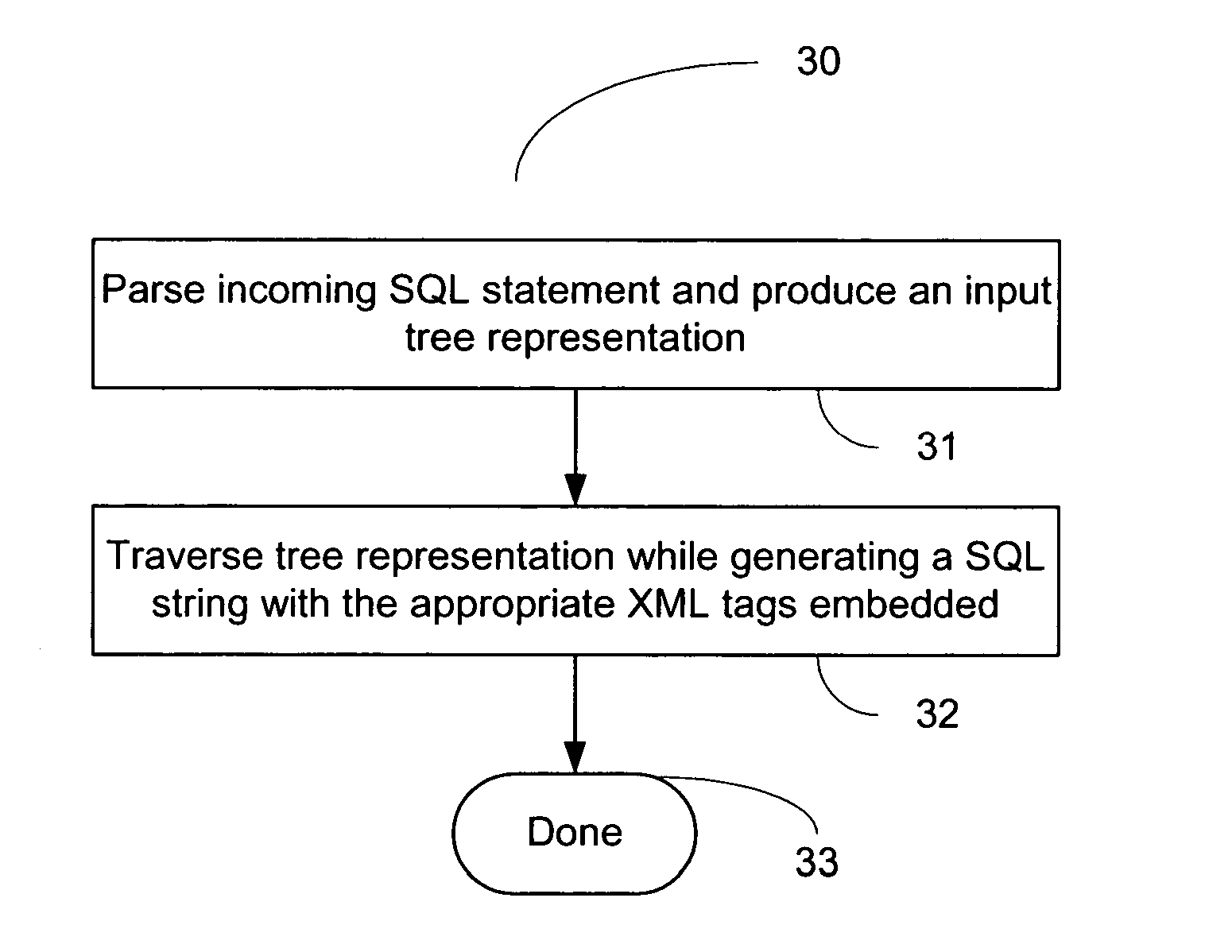
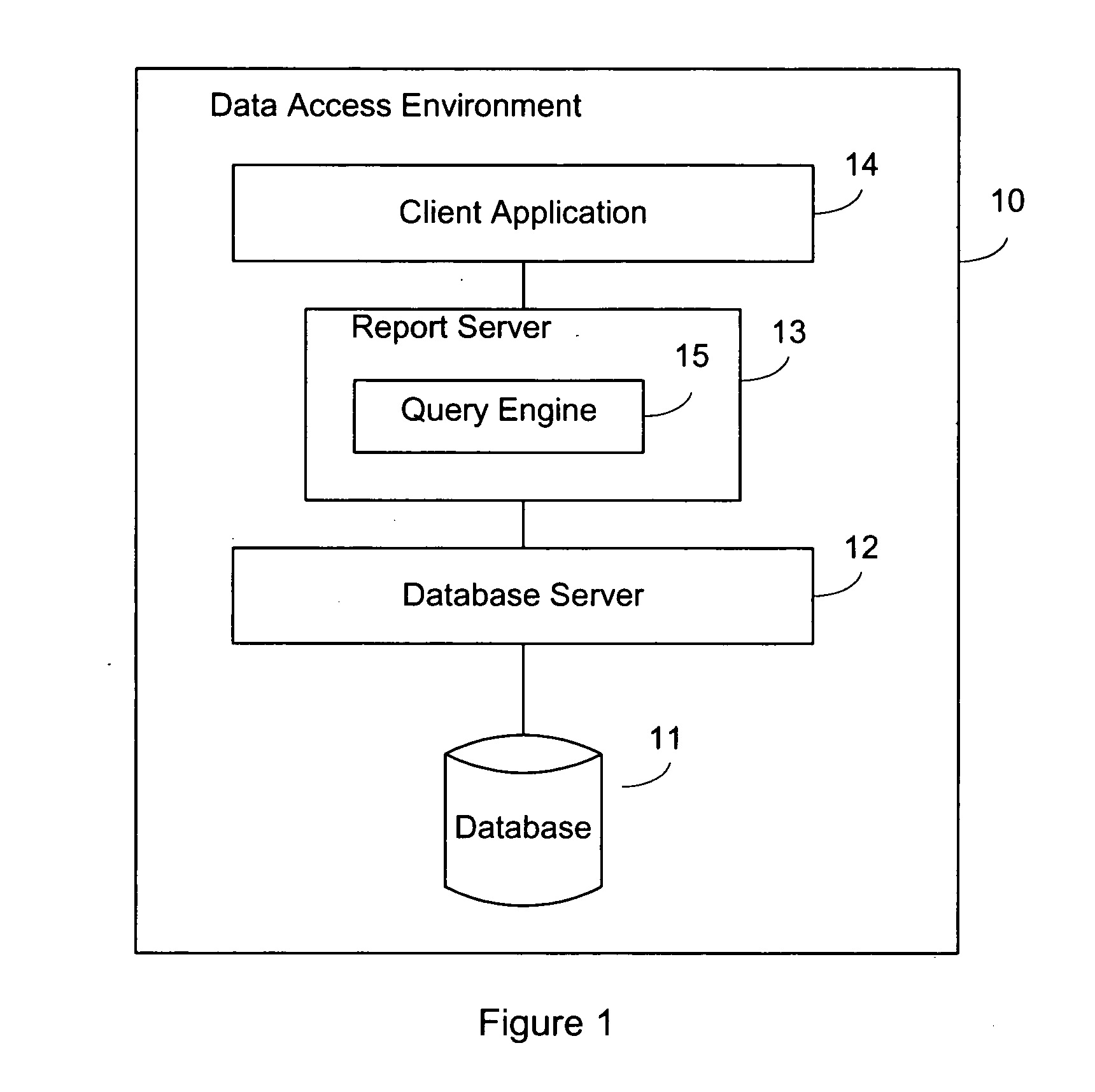
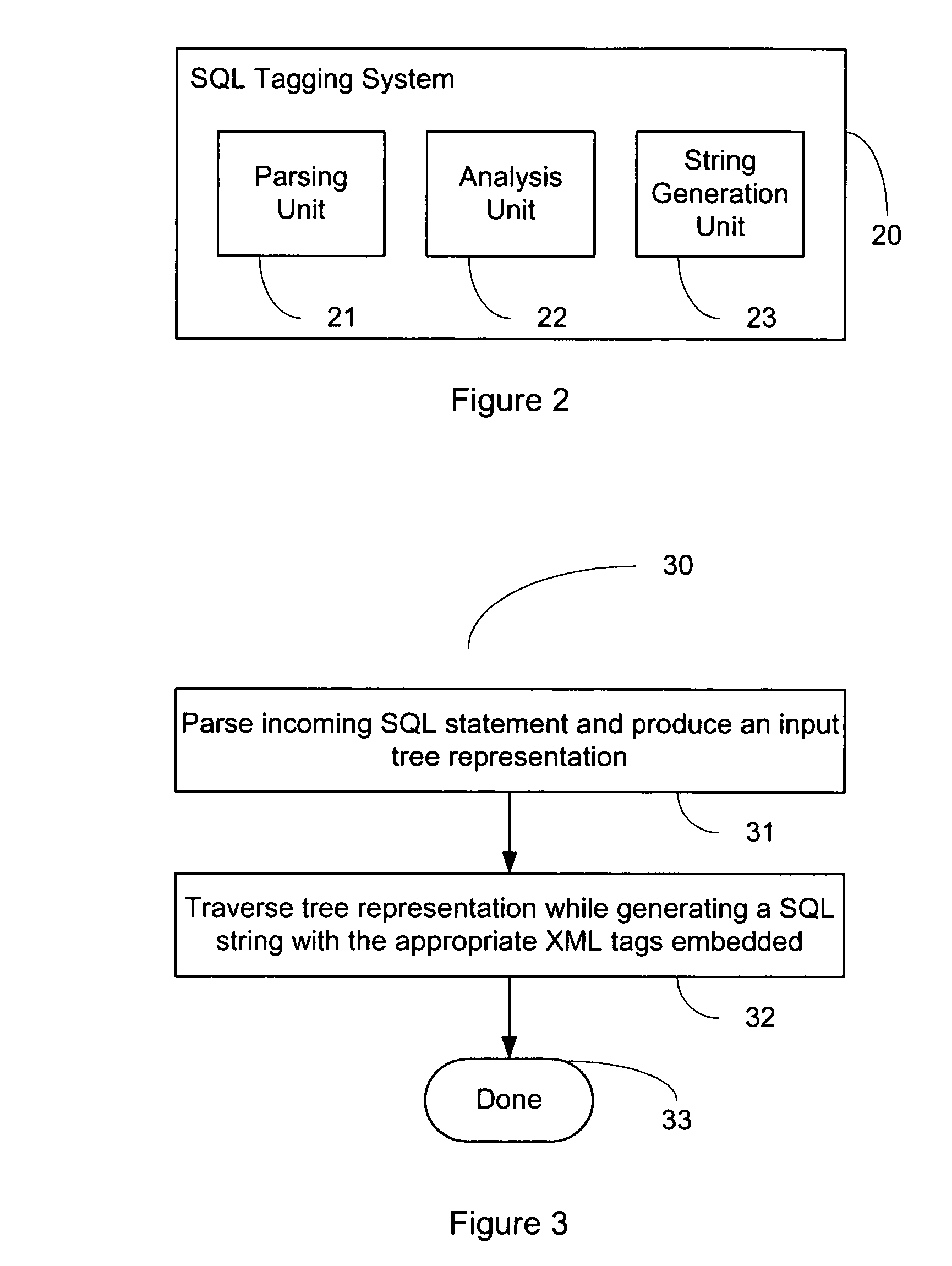
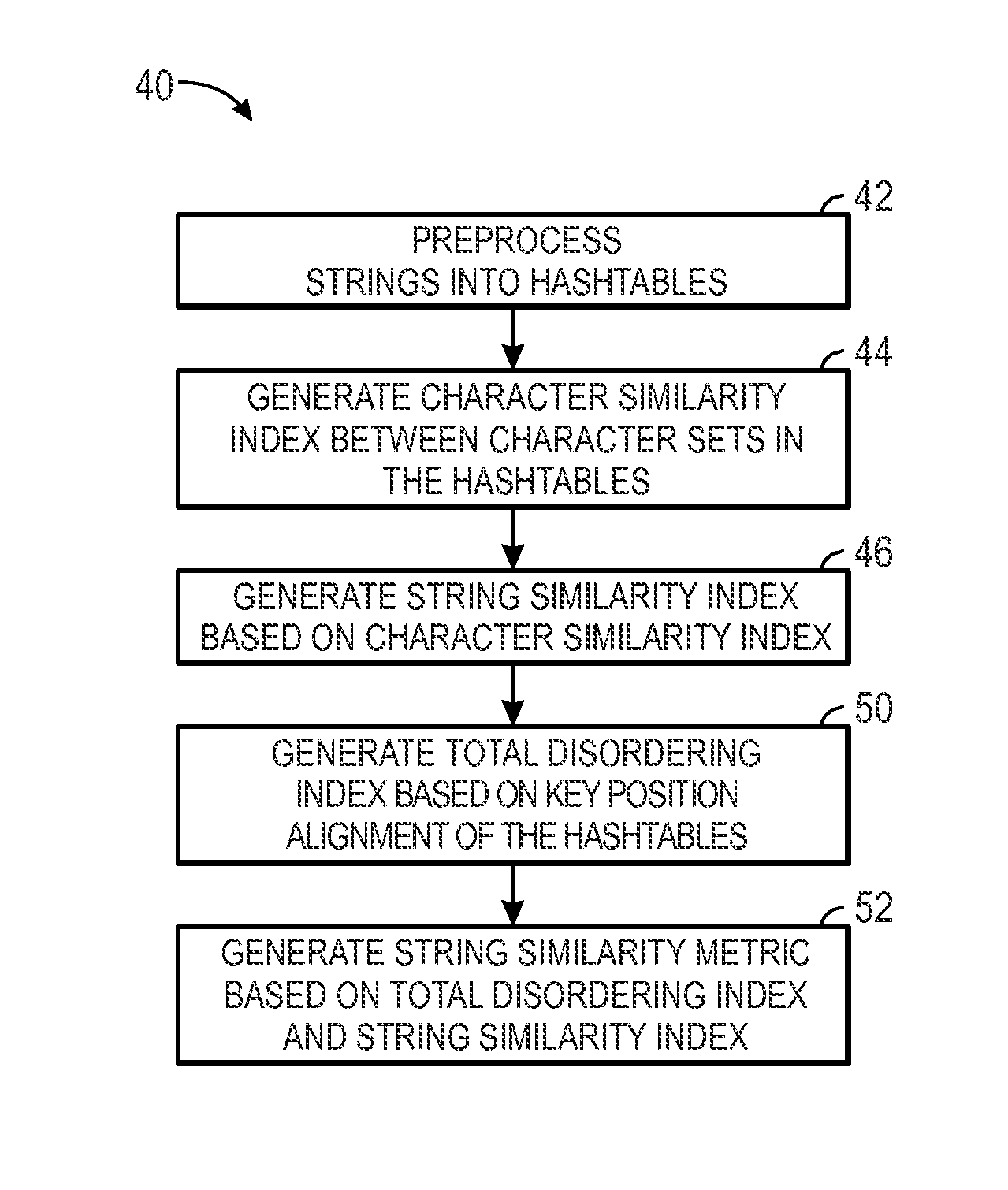
System and method of query transformation
ActiveUS20050015369A1Data processing applicationsDigital data processing detailsNatural language processingQuery transformation
A system for structured query language tagging is provided. The system comprises a parsing unit for parsing a structured query language string into components, an analysis unit for analyzing the components and applying associated tags to the components, and a string generation unit for concatenating the components with associated tags into a new string.
Owner:SAP AG
Method for generating a language-independent regression test script
ActiveUS20050137844A1Promote generationEasy to implementError detection/correctionSpeech analysisRegression testingTest script
A computer-implemented method for generating a language-independent regression test script. A language-specific regression test script comprising at least one object is received, wherein the language-specific regression test script is for use by an automated testing tool for testing an application in a first language. A translatable string of the object is identified, wherein the translatable string is represented in the first language. The translatable string is replaced with a language-independent string that can be represented in a plurality of languages, generating a language-independent regression test script that can be used for testing internationalized applications.
Owner:ORACLE INT CORP
Methods and systems for implementing approximate string matching within a database
ActiveUS7925652B2Digital data information retrievalDigital data processing detailsNatural language processingString generation
A computer-based method for character string matching of a candidate character string with a plurality of character string records stored in a database is provided. The method includes identifying a set of reference character strings in the database wherein the reference character strings are identified utilizing an optimization search for a set of dissimilar character strings and generating an n-gram representation for one of the reference character strings in the set of reference character strings. The method also includes generating an n-gram representation for the candidate character string determining a similarity between the n-gram representations, and indexing the candidate character string within the database based on the determined similarities between the n-gram representation of the candidate character string and the reference character strings in the identified set.
Owner:MASTERCARD INT INC
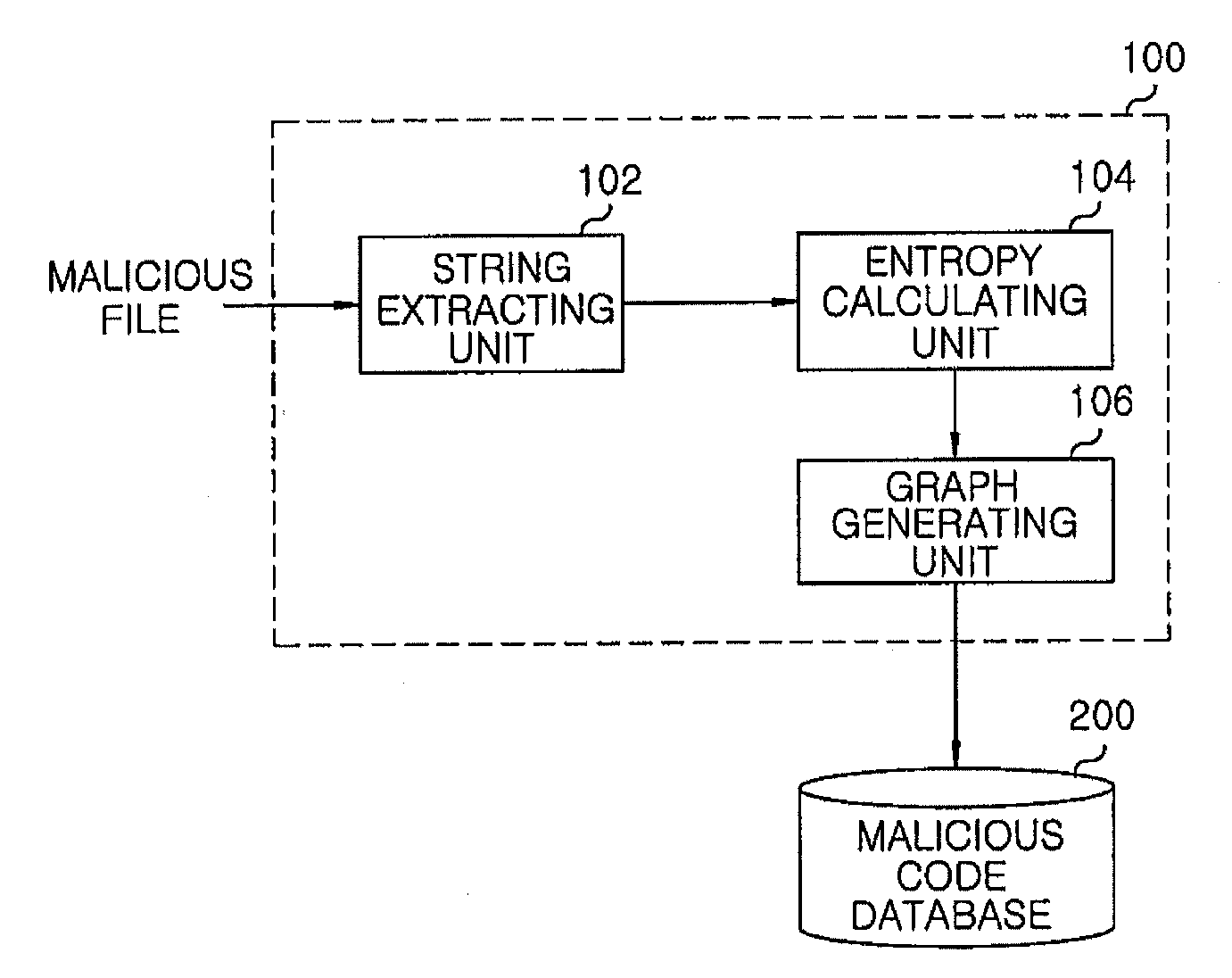
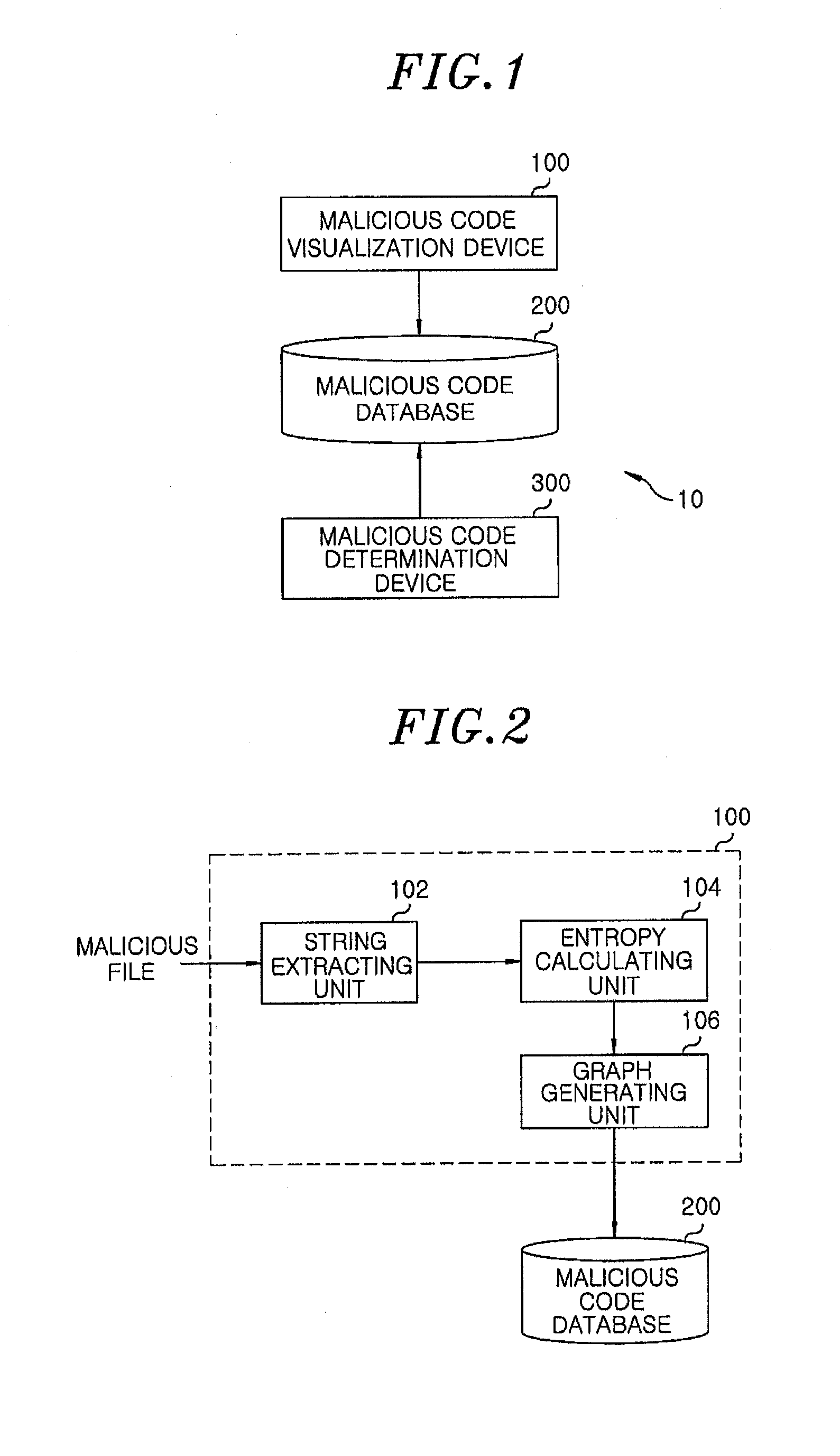
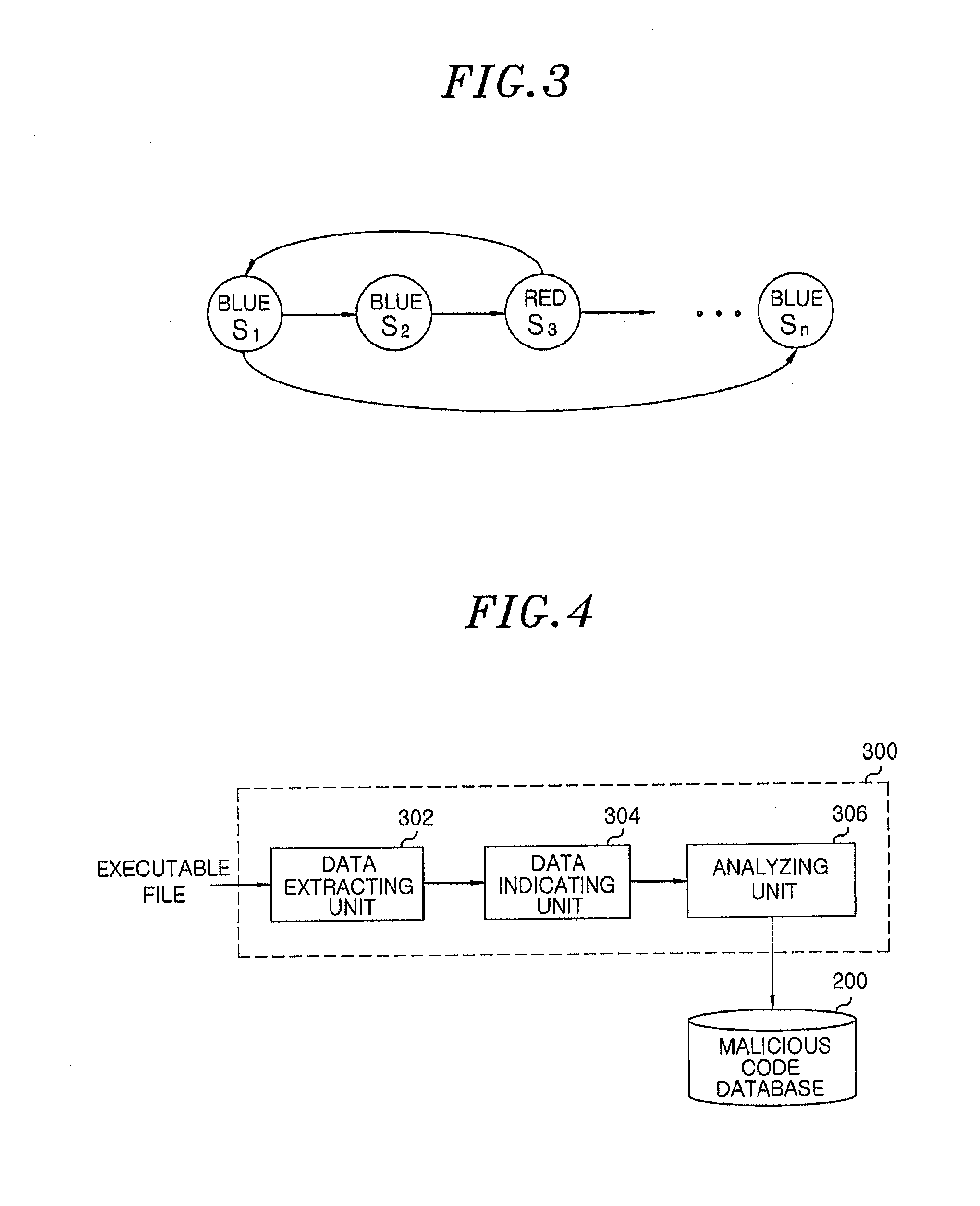
Apparatus and method for detecting malicious code, malicious code visualization device and malicious code determination device
An apparatus for detecting a malicious code includes: a malicious code visualization device for generating a graph for a malicious file by using strings in the malicious file, a connection among the strings and entropies for the strings and establishing a malicious code database with the generated graph for the malicious file. The apparatus further includes a malicious code determination device for generating a graph for a specific executable file and comparing the graph for the executable file with graphs for malicious files stored in the malicious code database to detect a malicious code in the executable file.
Owner:ELECTRONICS & TELECOMM RES INST
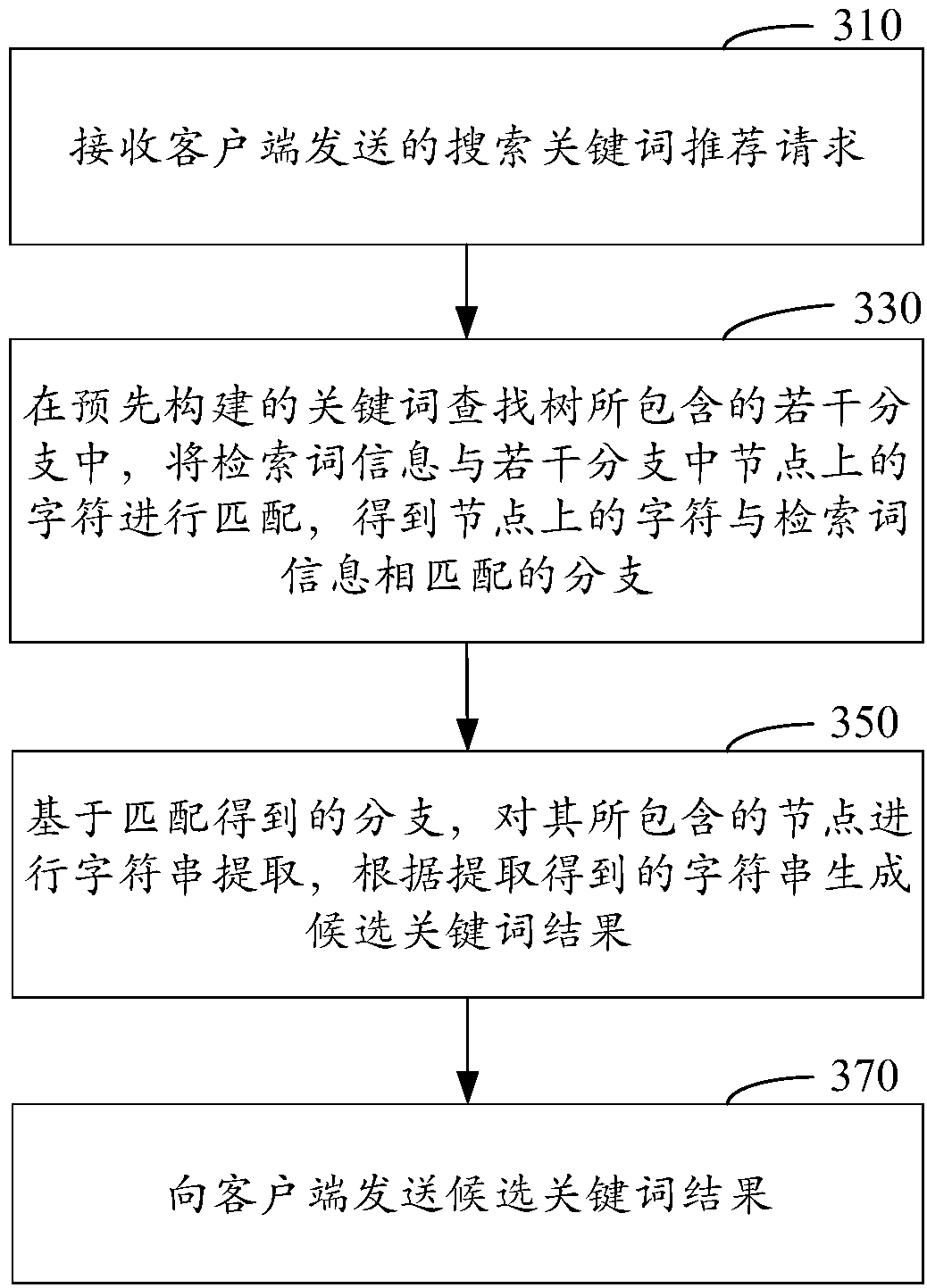
Recommendation method and device for search keyword, and electronic equipment
ActiveCN107590214AAchieve recommendationAvoid typingSpecial data processing applicationsSearch wordsUser input
The invention relates to a recommendation method and device for a search keyword. The recommendation method for the search keyword is applied to a server, and comprises the following steps: receivinga search keyword recommendation request transmitted by a client, wherein the search keyword recommendation request is transmitted by the client according to search word information inputted by a user;in a plurality of branches contained in a pre-built keyword search tree, matching the search word information with characters on nodes in the plurality of branches, and obtaining branches that the characters on the nodes are matched with the search word information; based on the branches obtained by matching, performing string extraction on the nodes included in the branches, and generating a candidate keyword result according to an extracted string; and transmitting the candidate keyword result to the client. The recommendation method and the device for the search keyword provided by the invention can effectively improve the accuracy of the search keyword, thereby helping to improve the searching accuracy.
Owner:TENCENT TECH (SHENZHEN) CO LTD
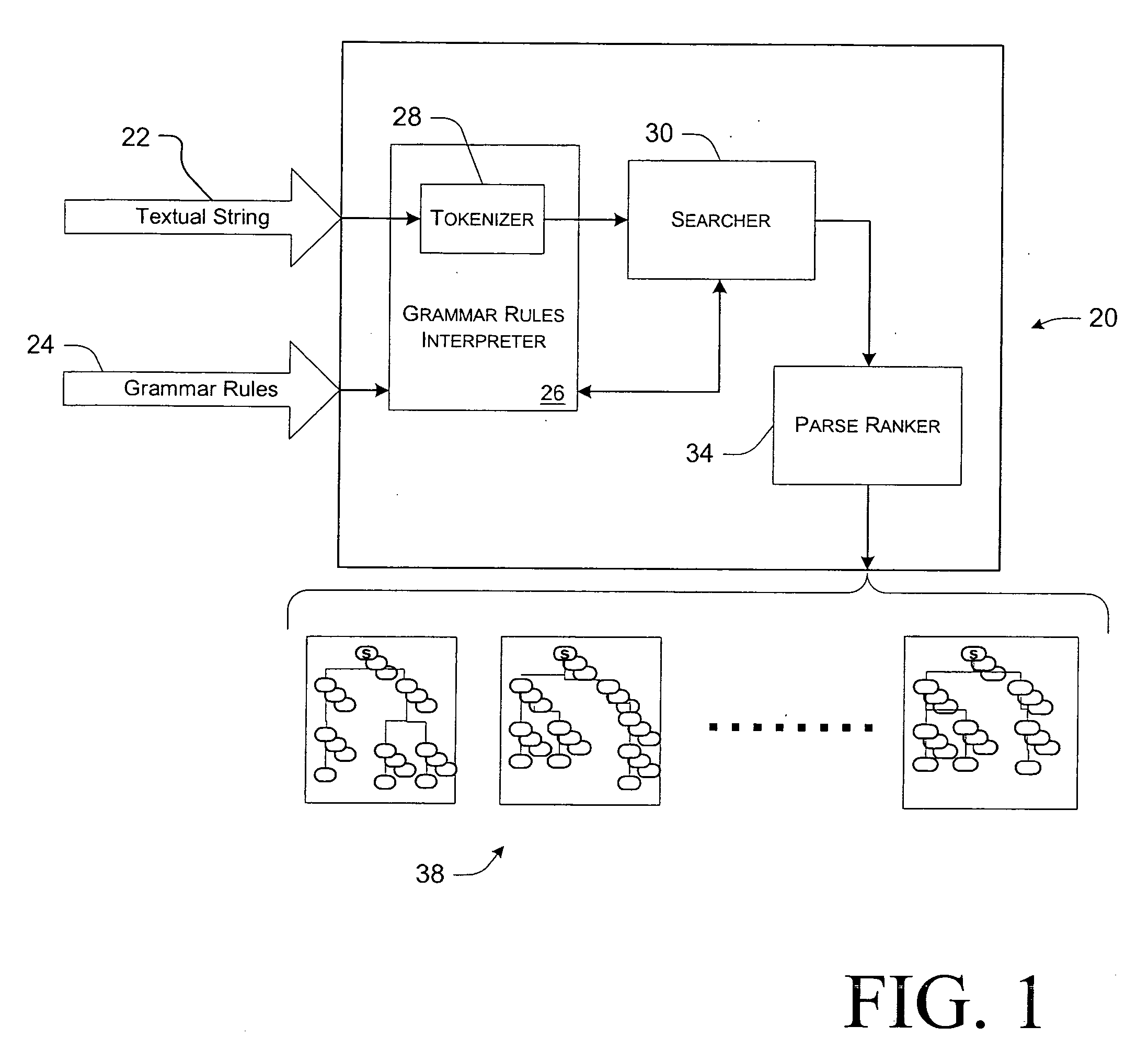
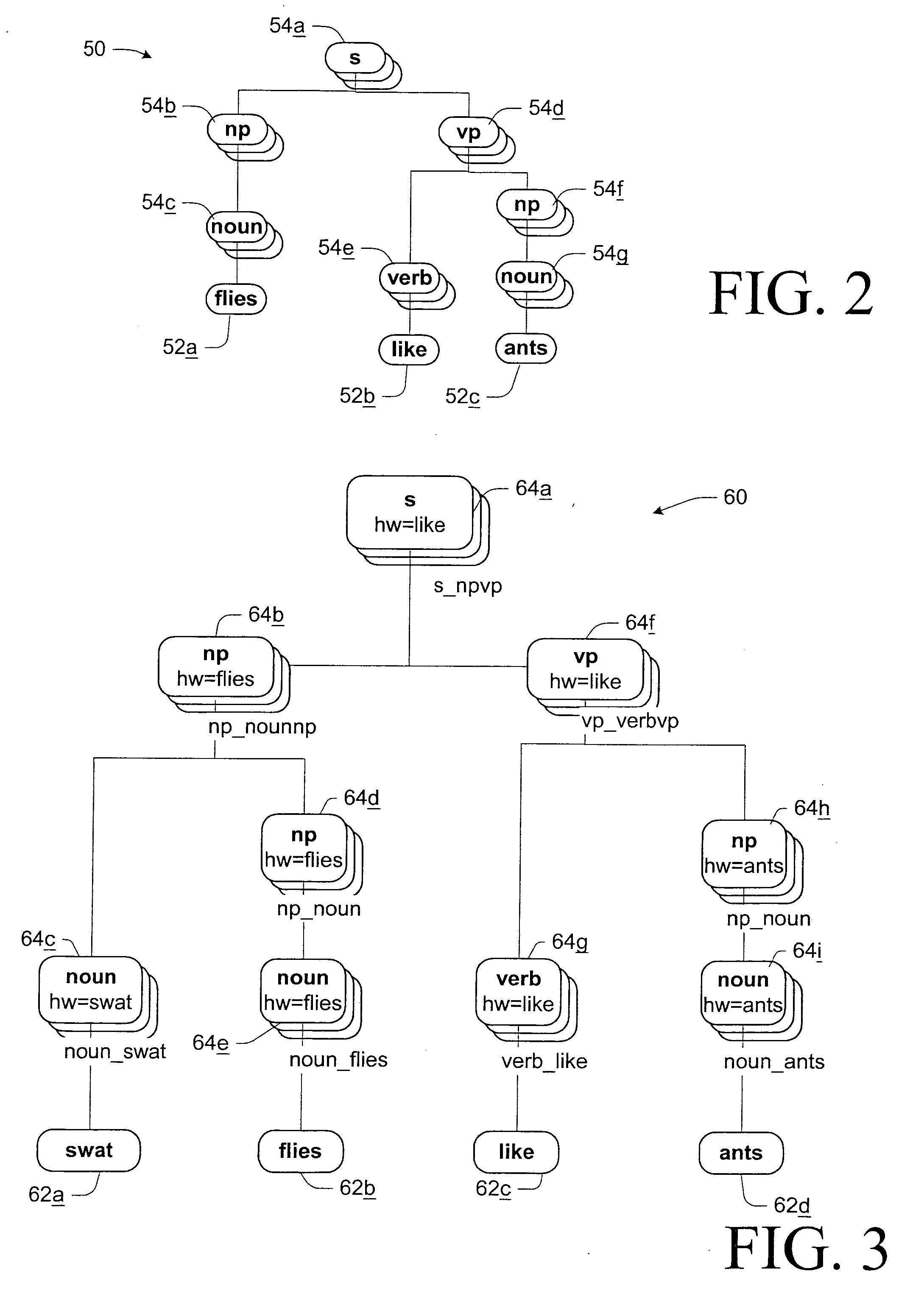
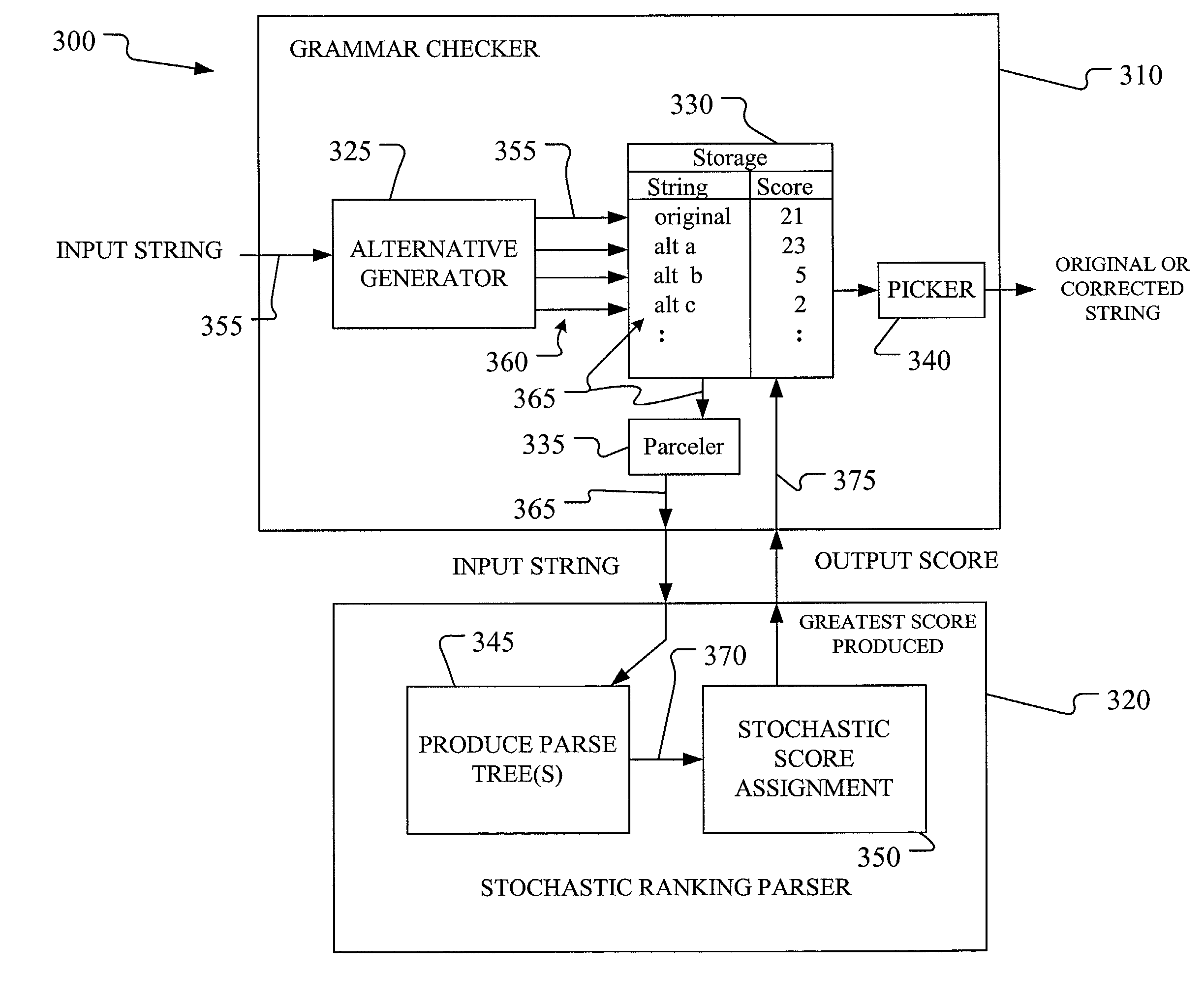
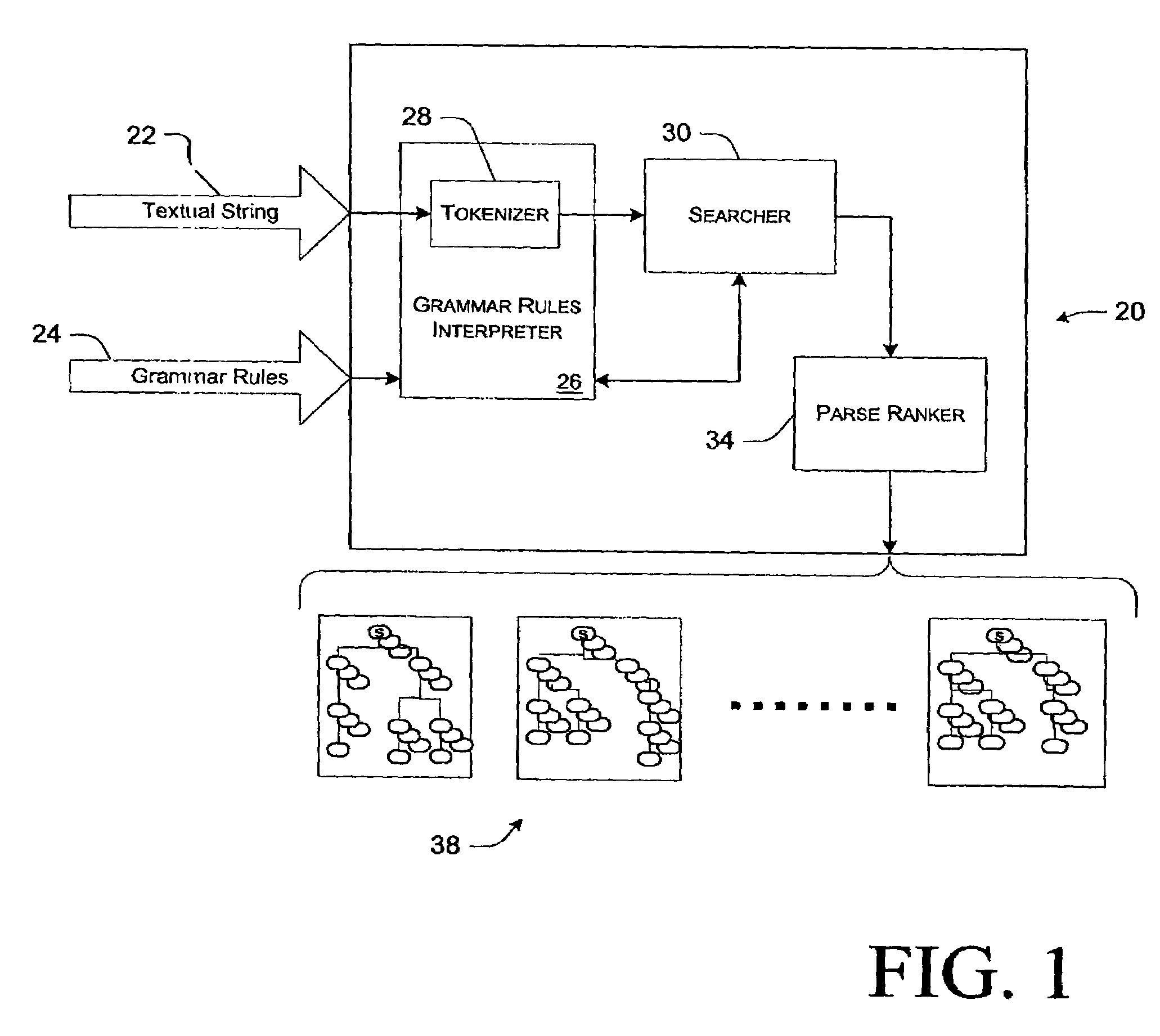
Method and apparatus for improved grammar checking using a stochastic parser
InactiveUS20050246158A1Natural language data processingSpecial data processing applicationsNatural language processingText string
A method and grammar checking system are provided that generate a stochastic score, or a statistical goodness measure, for each of an input string of text and one or more alternative strings of text. An alternative generator generates the alternative strings of text, and a ranking parser produces parse trees and corresponding statistical goodness measures for each of the strings. The string of text having the highest goodness measure is selected for recommendation to a user.
Owner:MICROSOFT TECH LICENSING LLC
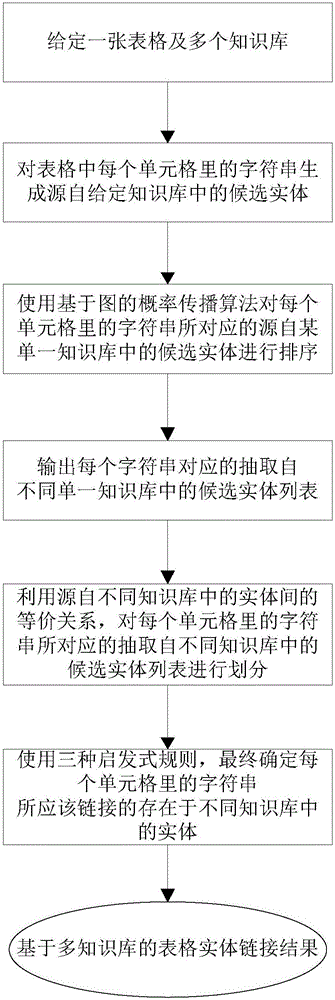
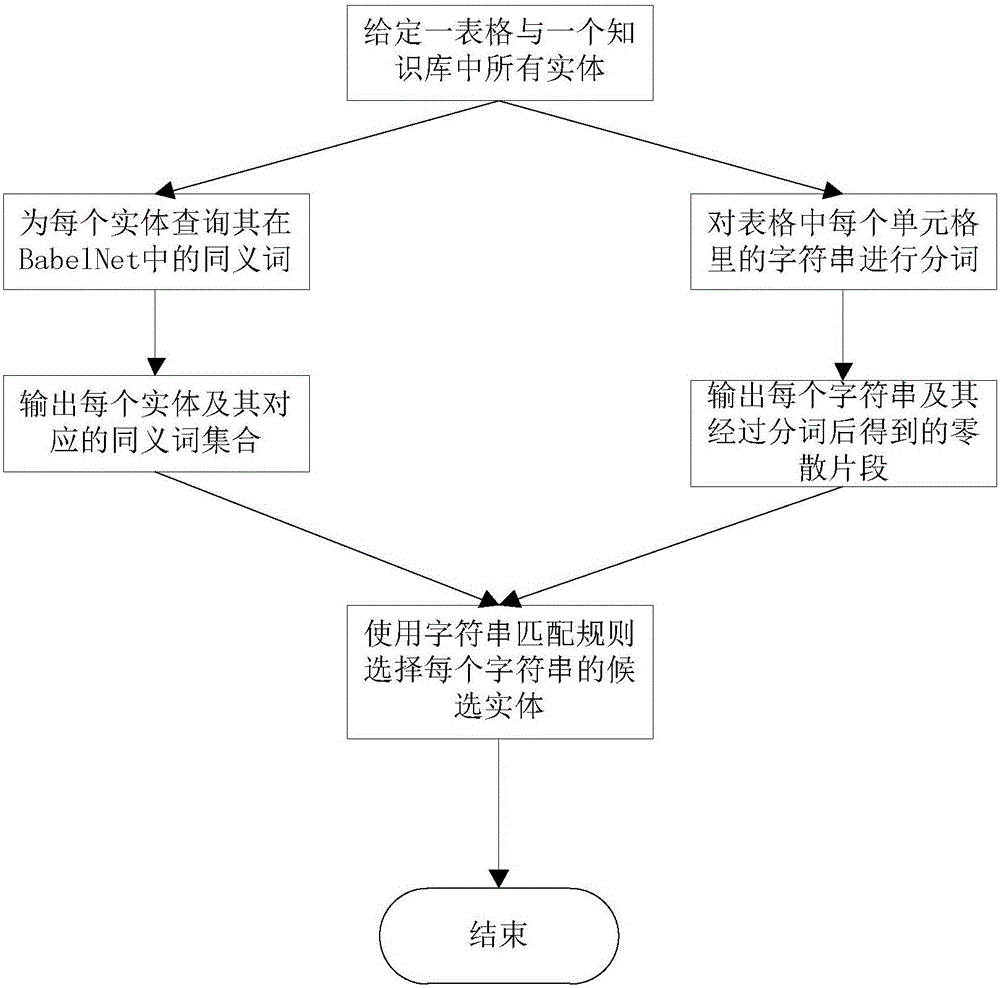
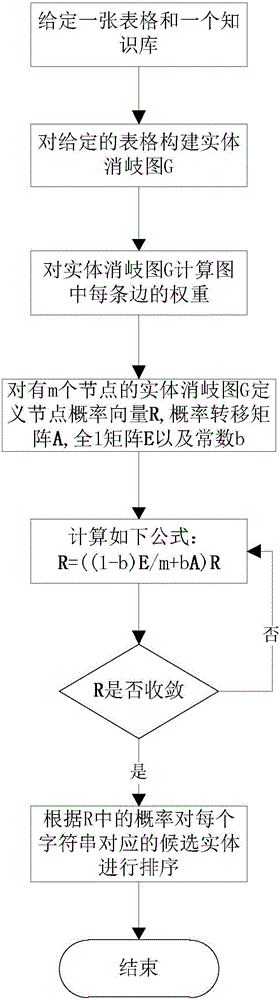
Form entity linking method based on multiple knowledge bases
ActiveCN106503148AReduce dependencePracticalRelational databasesKnowledge representationEntity linkingProbability propagation
The invention discloses a form entity linking method based on multiple knowledge bases. The method is mainly used for solving the problem of entity linking in a form. The method includes the steps that firstly, a candidate entity is generated for a character string in each cell in a given form, and the candidate entities are extracted from the self-given knowledge bases; then a universal probability propagation algorithm based on a map is provided to rank the candidate entities corresponding to the character strings in the cells. The method can act on any single knowledge base. According to the ranking result of the candidate entities based on the different single knowledge bases, by means of the equivalence relation among the entities from the different knowledge bases, the ranked candidate entities, extracted from the different knowledge bases, corresponding to the character strings in the cells are divided. Finally, three heuristic rules are used for finally determining the entities, existing in the different knowledge bases, needing to be linked with the character strings in the cells, and therefore tasks of form entity linking based on the multiple knowledge bases are completed.
Owner:SOUTHEAST UNIV
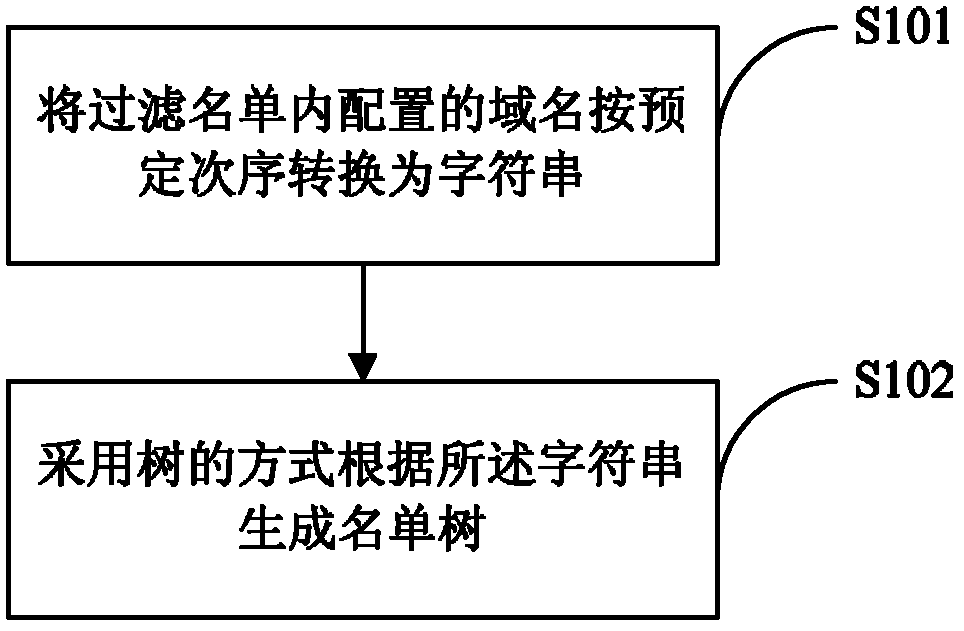
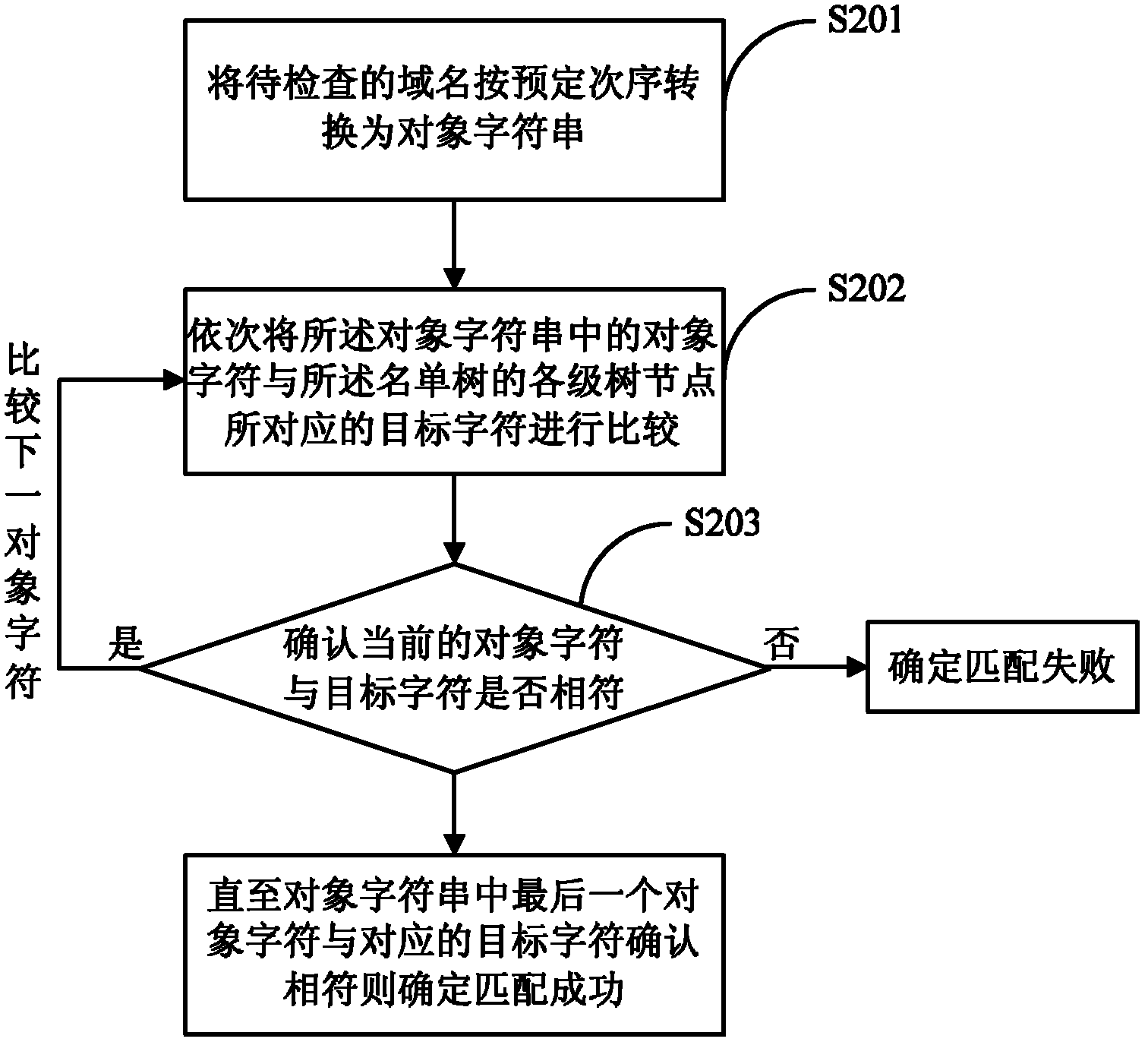
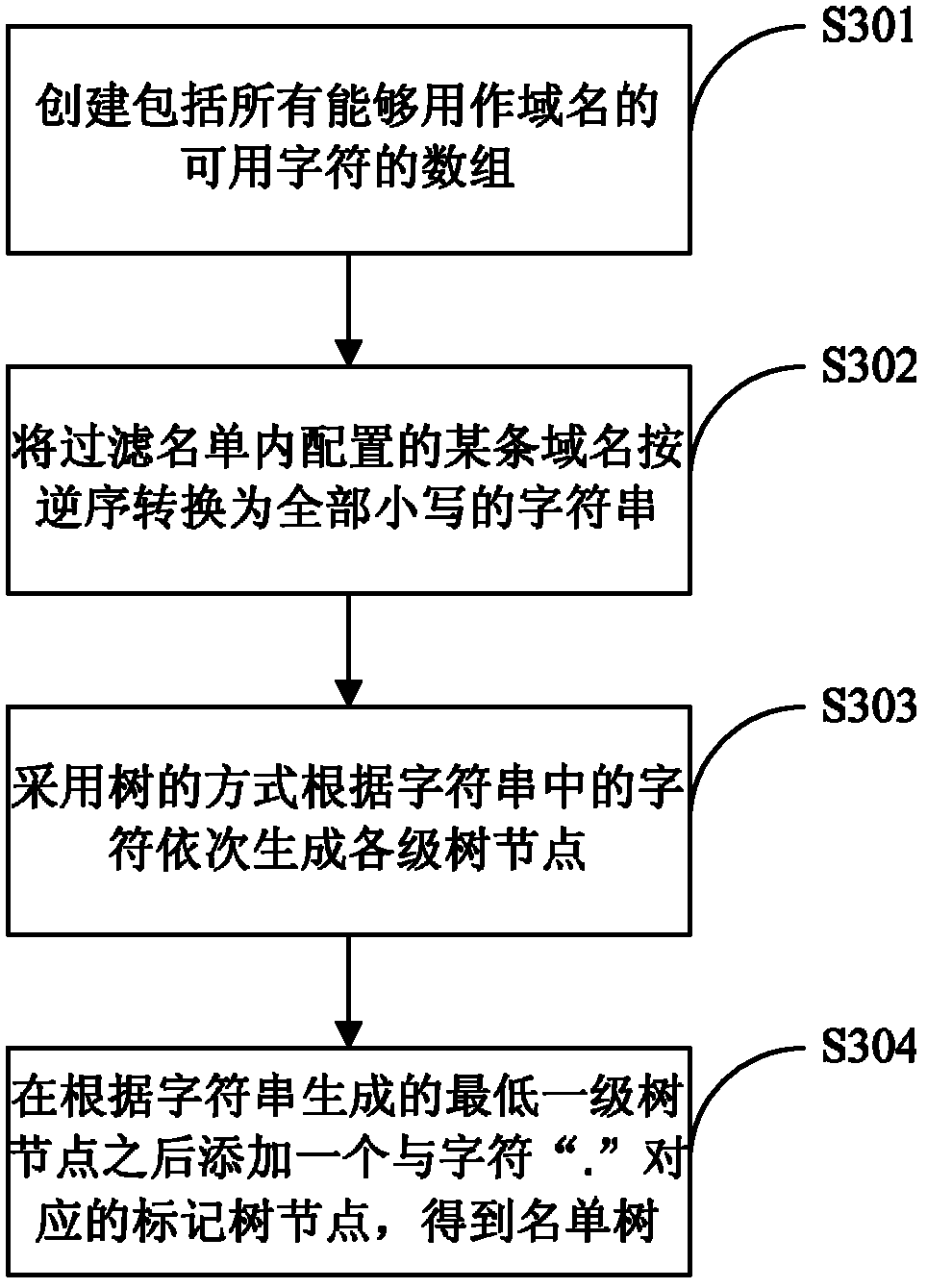
Domain filter list storing and matching method and device
The invention discloses a domain filter list storing method, which comprises the following steps of: converting domain names configured in a filter list to be a character string in a preset order; generating a list tree in a tree manner based on the character string; in the list tree, taking the characters in the character string as tree nodes in sequence, wherein each tree node has a first attribute and a second attribute, the first attribute is used for indicating a next level tree node corresponding to a character behind the current character, and the second attribute is used for indicating whether the character string is finished. The invention also discloses a domain filter list matching method, a domain filter list storing device and a domain filter list matching device. According to the embodiment of the invention, a tree structure is adopted to store the domain filter list, so that the time required by the domain matching can be effectively shortened, and the performance of the server can be improved; and meanwhile, the domain filter list mechanism in the tree structure can be suitable for any platform, the accuracy and good debugging performance can be ensured.
Owner:ALIBABA GRP HLDG LTD
Compression devices, decompression devices, compression methods, and decompression methods
The present invention is directed to a compression device including an identifier determination circuit configured to determine a first identifier value identifying a first communication terminal of a network, and a second identifier value identifying a second communication terminal of the network; a differential determination circuit configured to determine a differential value based on a difference between the first identifier value and the second identifier value; and a compressed string generation circuit configured to insert the differential value into a compressed string. A compression method, a decompression device and a decompression method are also disclosed.
Owner:AGENCY FOR SCI TECH & RES
Device and method for processing data
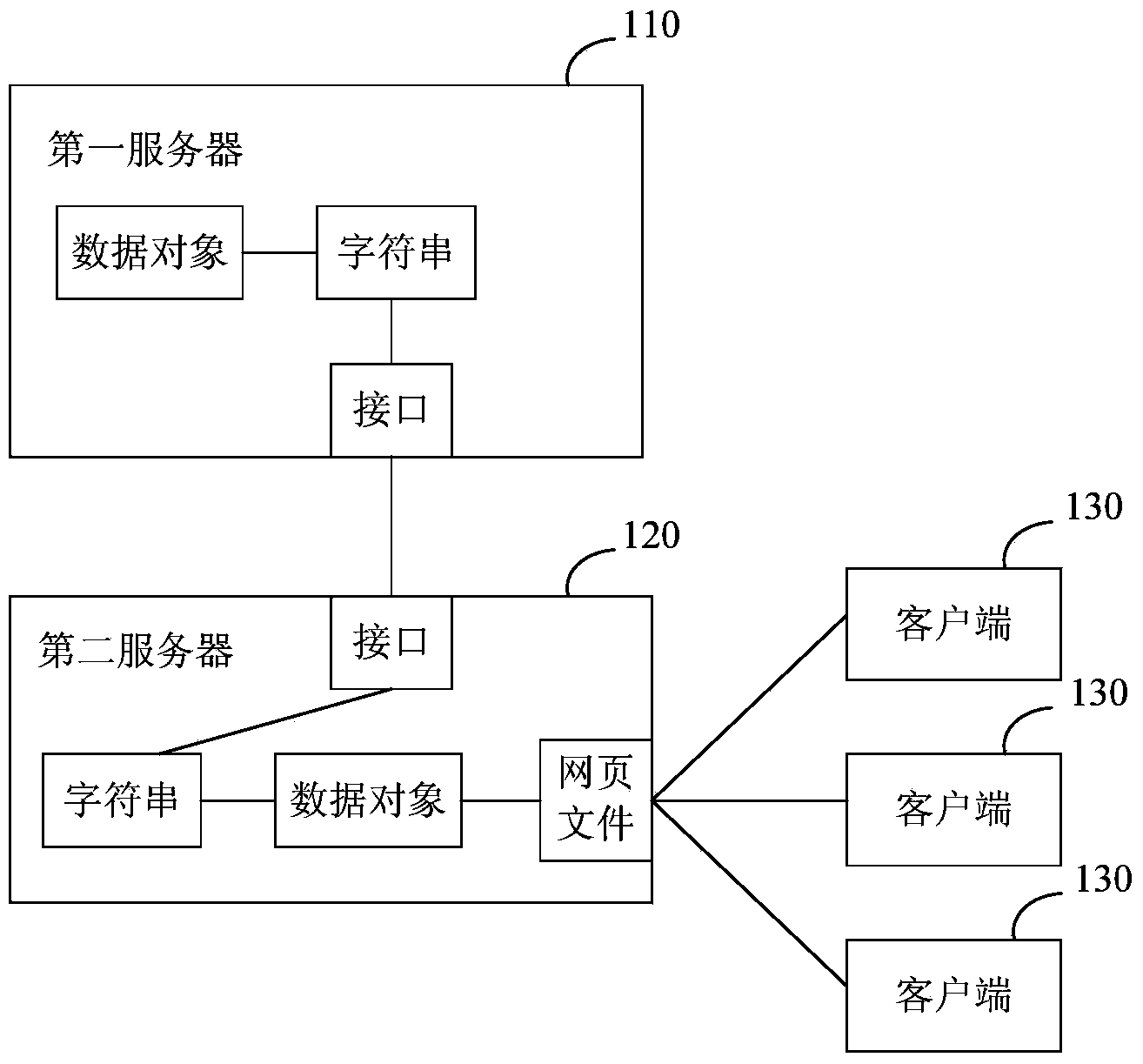
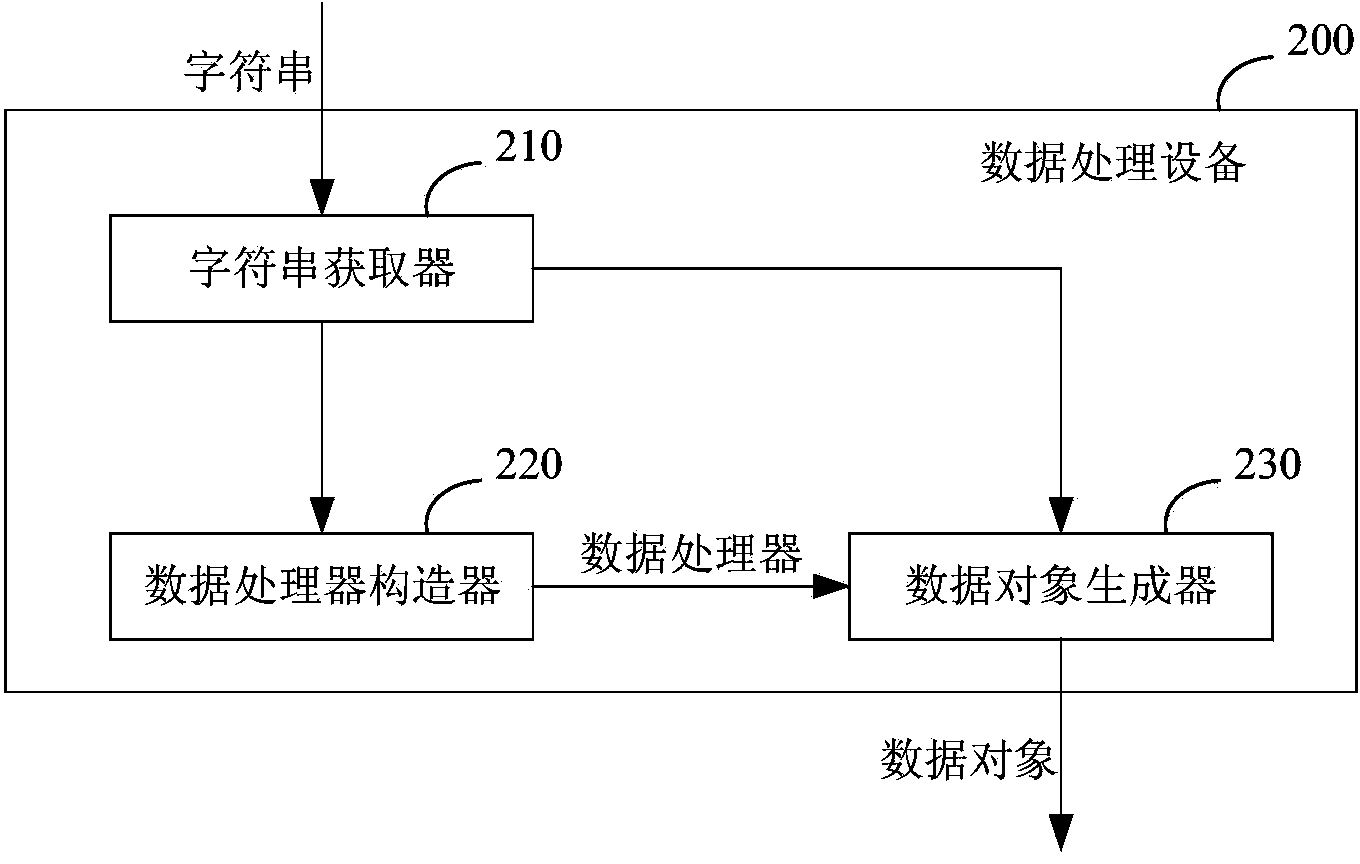
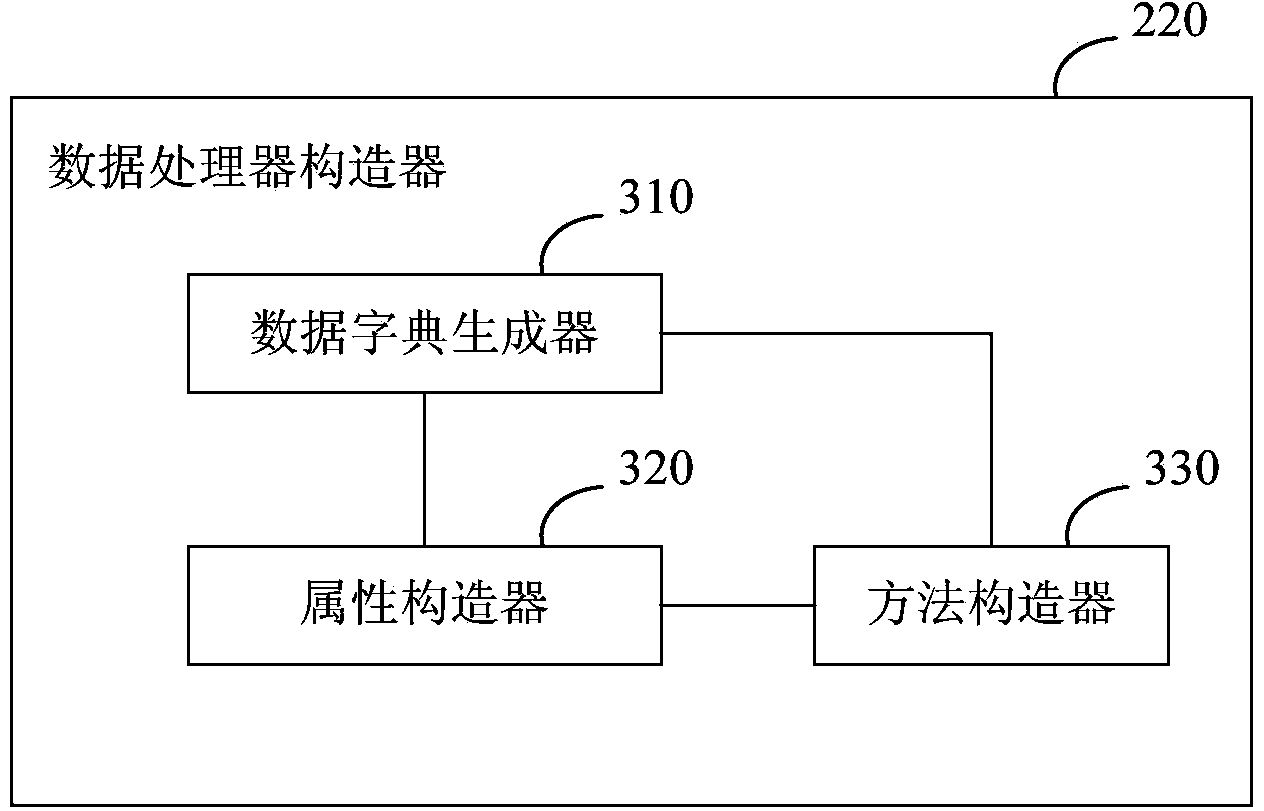
ActiveCN103970855AFast conversionQuick responseSpecial data processing applicationsThe InternetData format
The invention discloses a device and method for processing data, and belongs to the technical field of the Internet. The method for processing the data includes the steps of obtaining a character string from a specific interface of a server, wherein the character string is in a preset data format and comprises one or more data items, and each data item comprises a name of the data item and a related value; generating a data processor according to the character string, wherein the data processor is suitable for processing data, in the preset data format, of the character string to generate a data object; as for a target character string coming from the specific interface of the server, processing the target character string through the data processor to form a corresponding target data object. According to the device and method, the conversion speed at which the character string is converted into the data object is increased, and then the response speed of a website page is increased.
Owner:CHEZHI HULIAN BEIJING SCI & TECH CO LTD
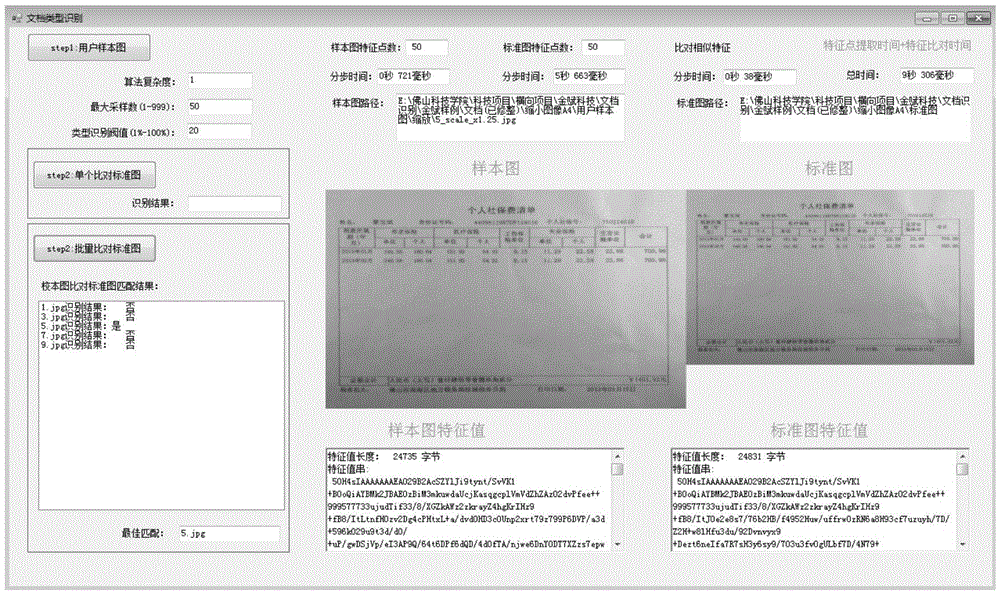
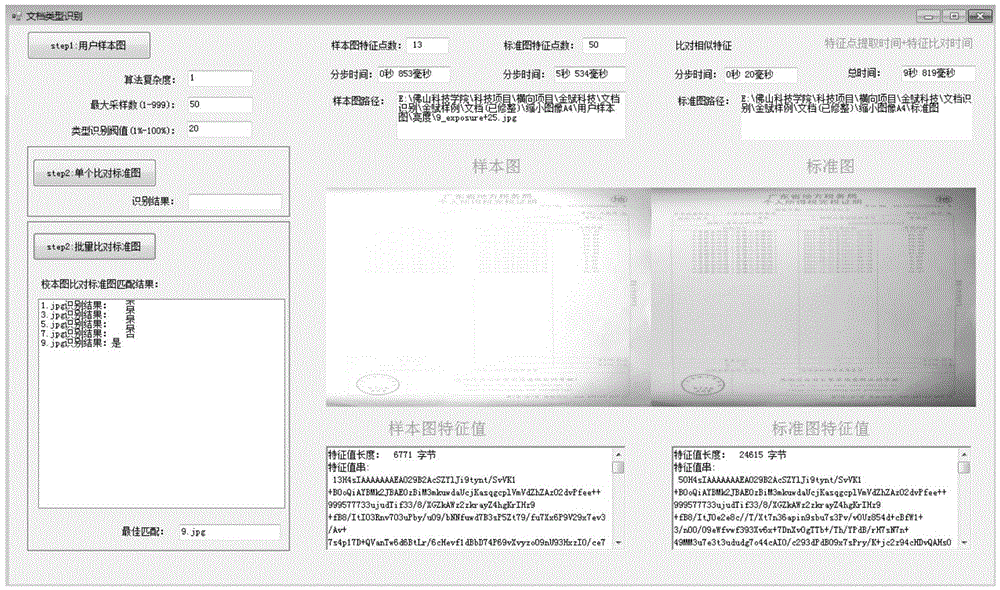
Fast document type recognition method based on full-sized feature extraction
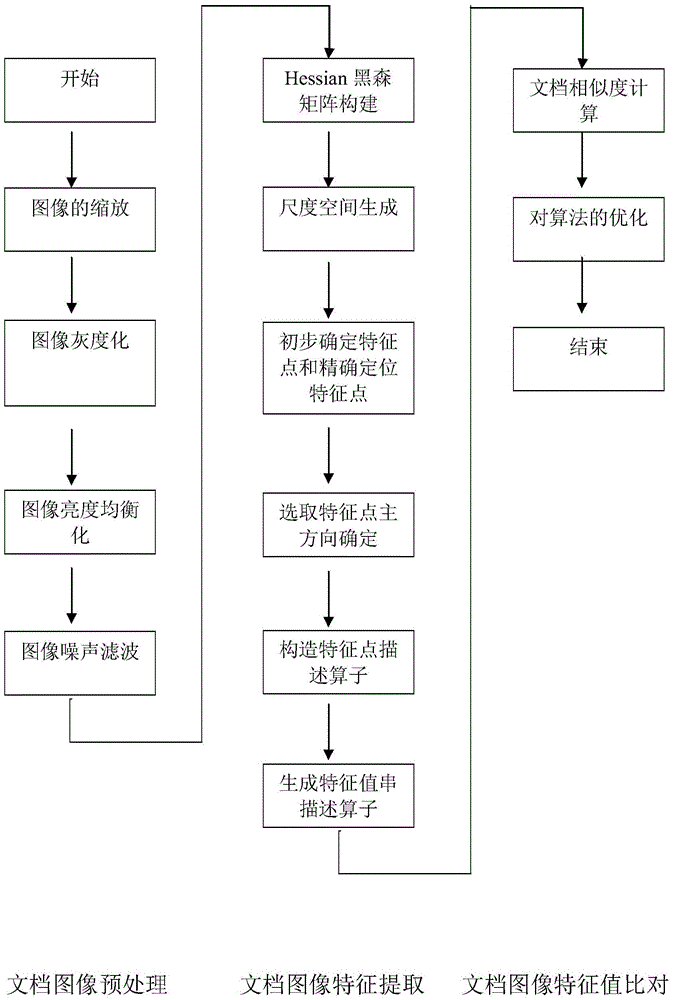
InactiveCN105426884AFast operationAvoid influenceCharacter and pattern recognitionDocument similarityScale variation
The invention provides a fast document type recognition method based on full-sized feature extraction. The method comprises the following steps of document image preprocessing, including image zooming, graying and noise filtering; document image feature extraction, including Hessian matrix building, scale space generation, primary determination of feature points, precise positioning of the feature points, main direction determination of selected feature points, feature point descriptor construction and feature value string generation; document image feature value comparison, including document similarity calculation and comparison algorithm optimization. According to the method, an image is preprocessed through software, and additional hardware equipment does not need to be added. According to the method, the scale-invariant feature is creatively introduced for improving a typical SURF feature extraction algorithm, so that the problem of matching failure due to error amplification of the SURF algorithm caused by scale variations is fundamentally solved. The method has the advantage that a multi-thread technology and a large cache are used for solving the problems of large data volume calculation during comparison and the harsh time requirement of a user on an electronic government affair platform.
Owner:FOSHAN UNIVERSITY
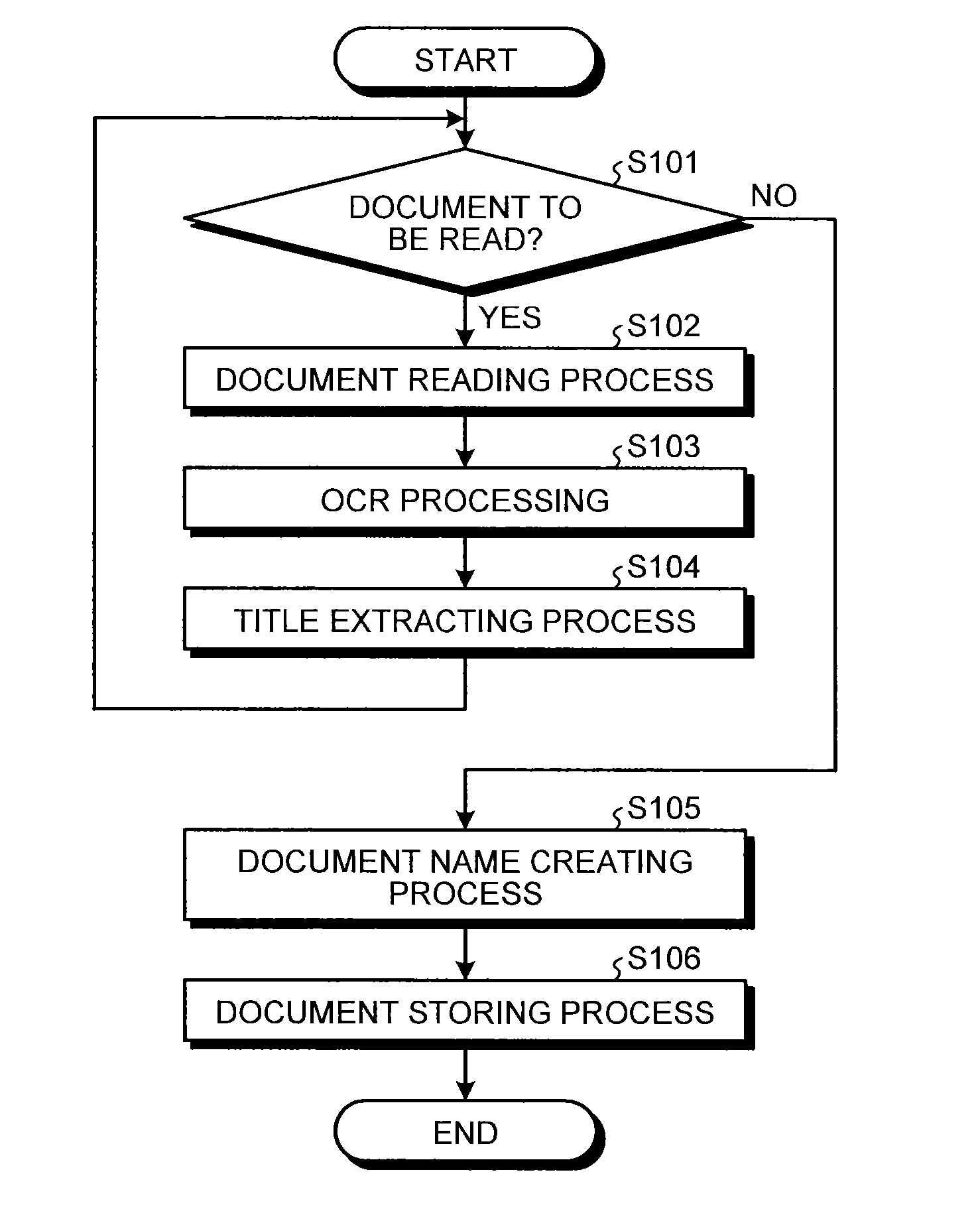
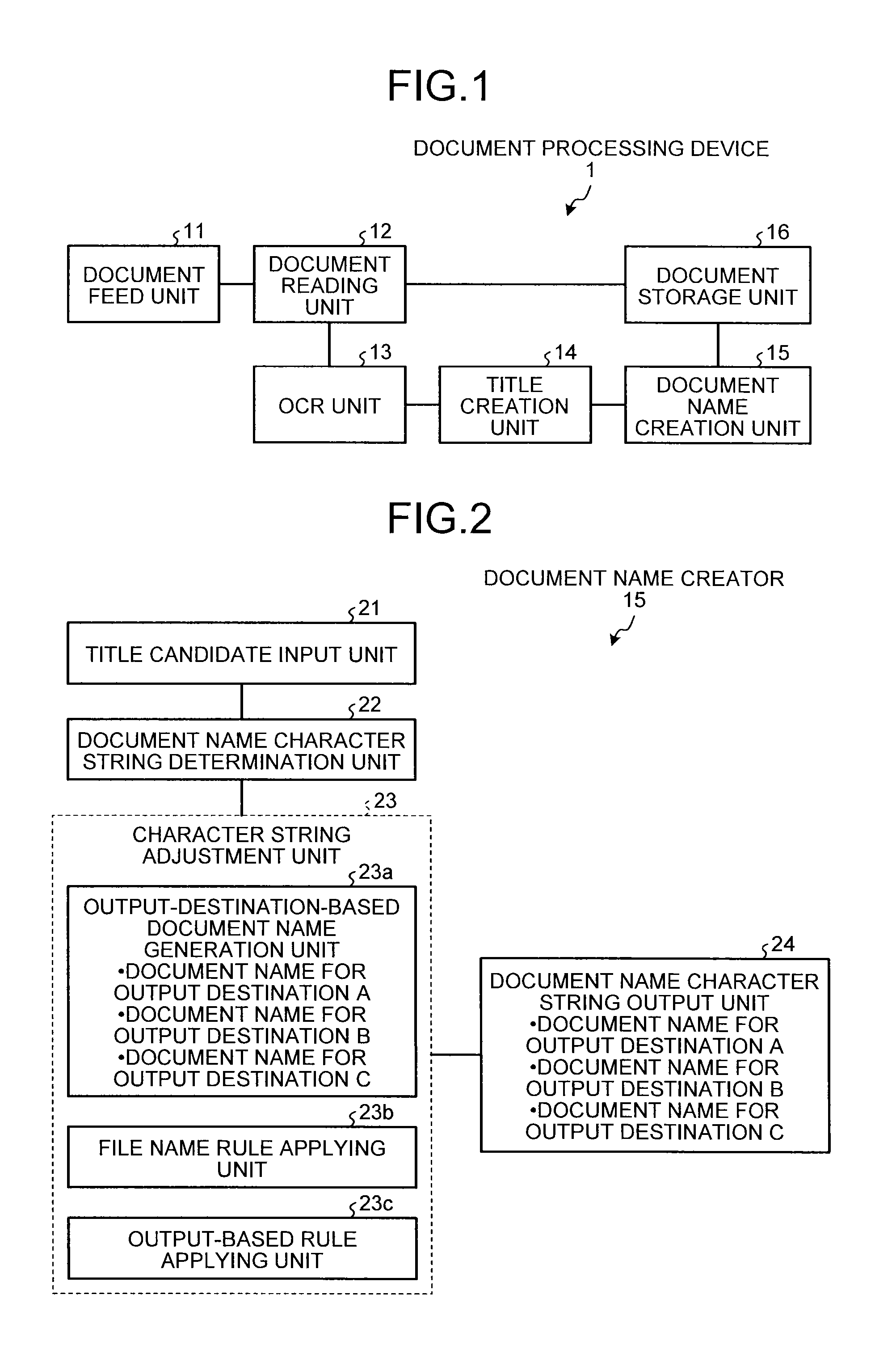
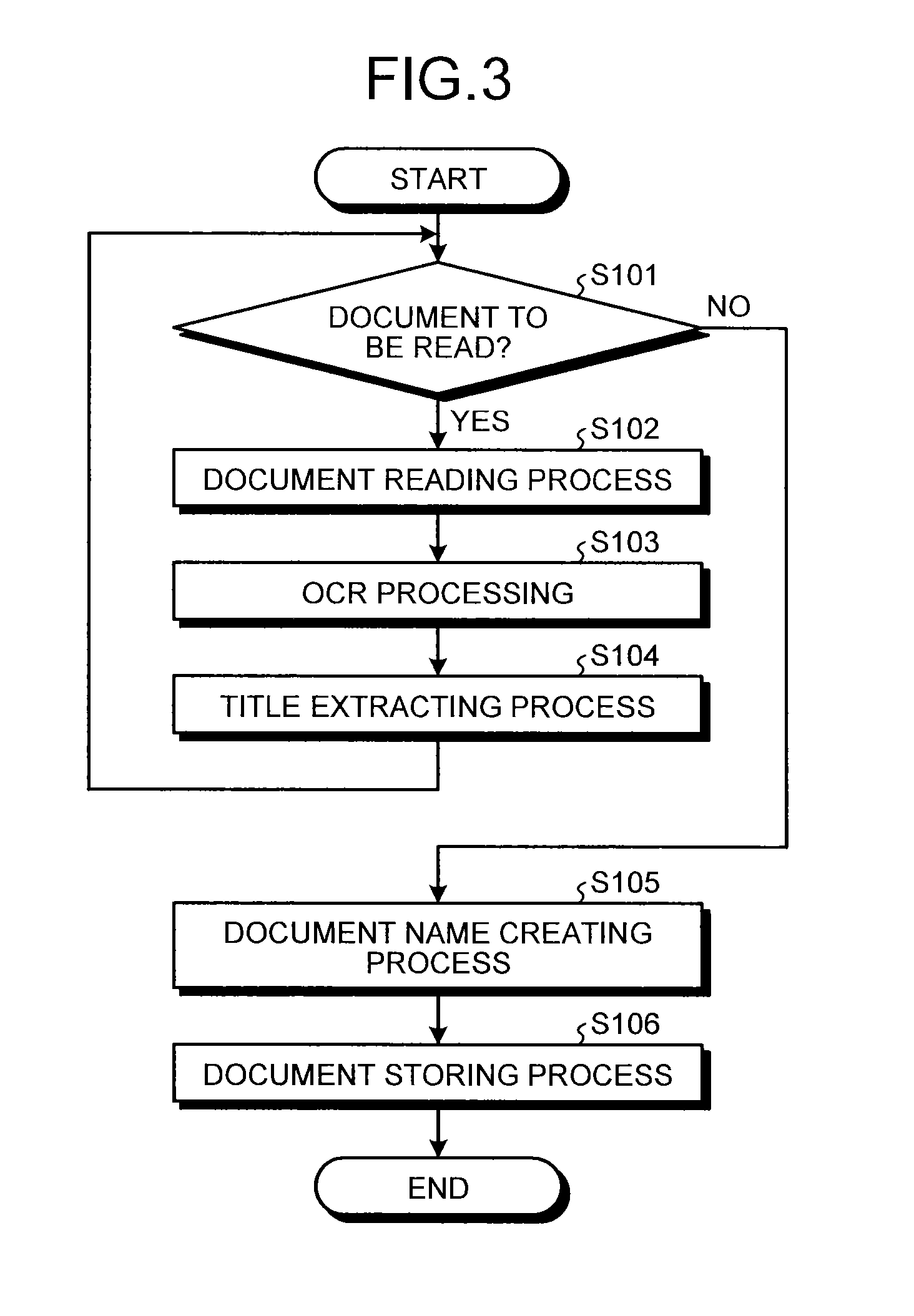
Document processing device, image processing apparatus, document processing method and computer program product
InactiveUS20140093170A1Solve problemsCharacter and pattern recognitionPattern recognitionComputer vision
A document processing device includes: a character information extracting unit that extracts character information from document image data; a feature character string extracting unit that extracts, as document name candidate character strings, a given number of character strings indicative of features of the document image data from the character information extracted by the character information extracting unit; an output condition acquiring unit that, when the document image data is processed by one of multiple processing methods involving an output of a document name of the document image data, acquires an output condition required for the output of the document name of the document image data; and a document name generating unit that generates the document name complying with a character condition corresponding to the output condition from the document name candidate character strings.
Owner:RICOH KK
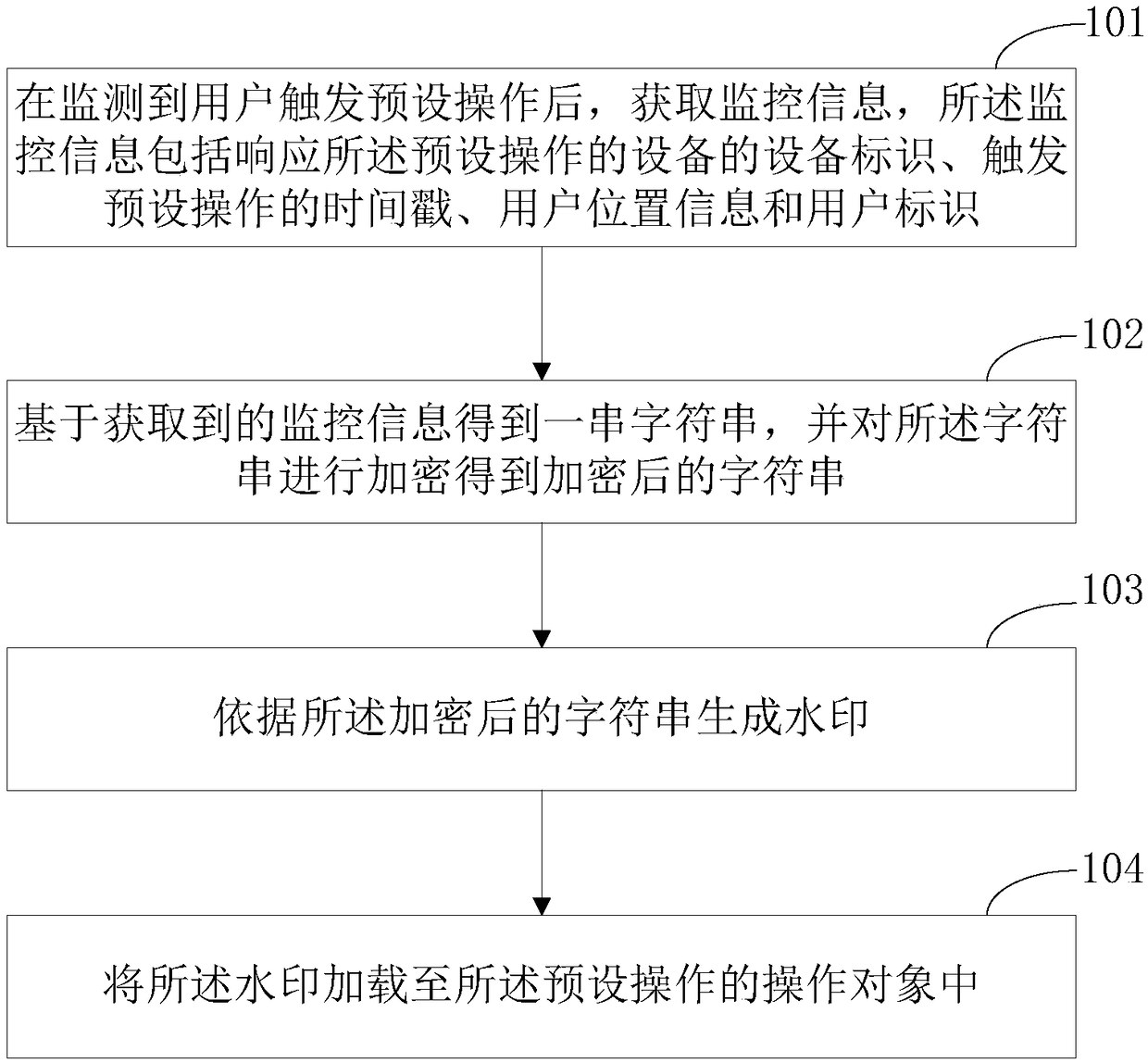
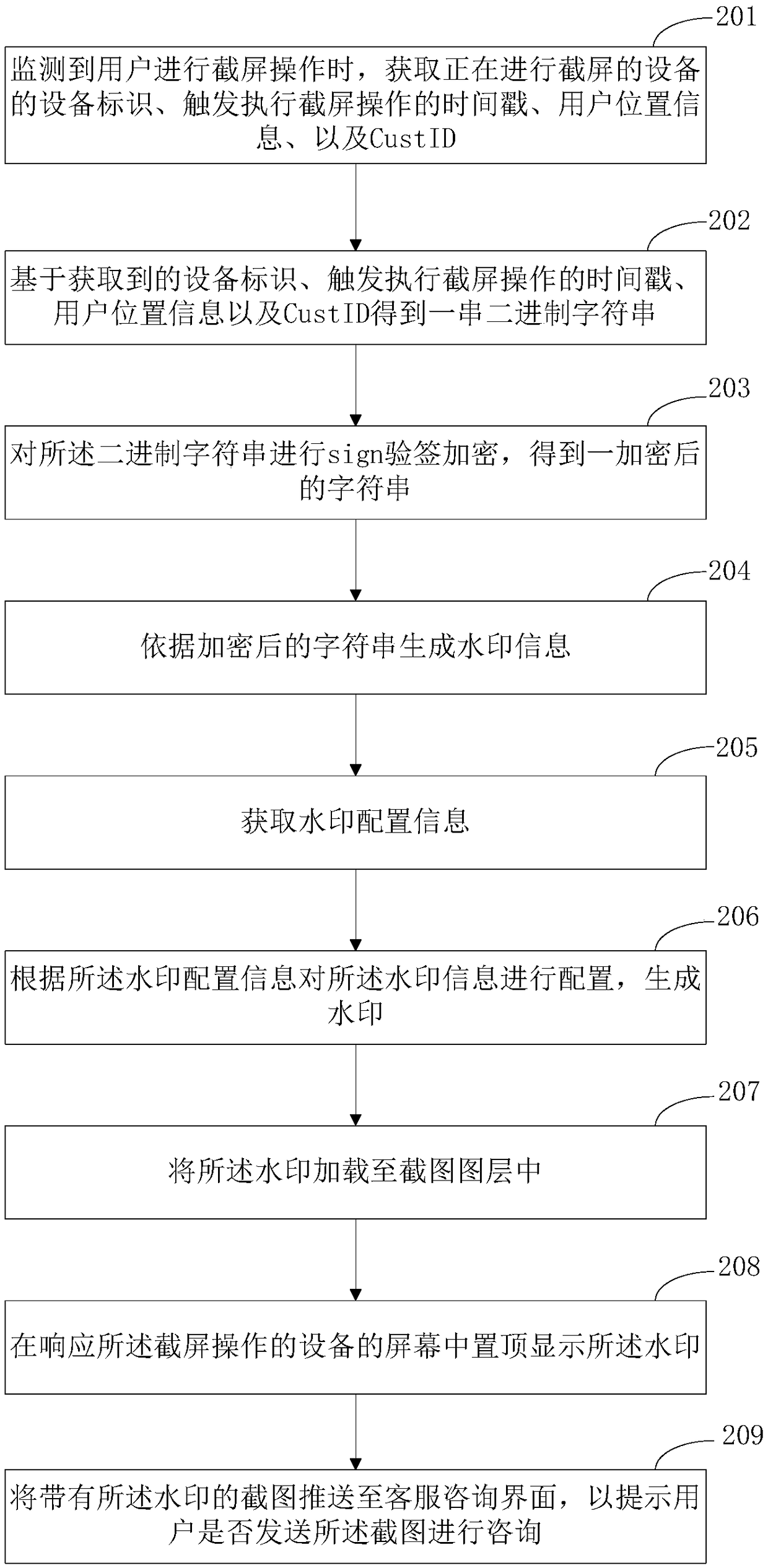
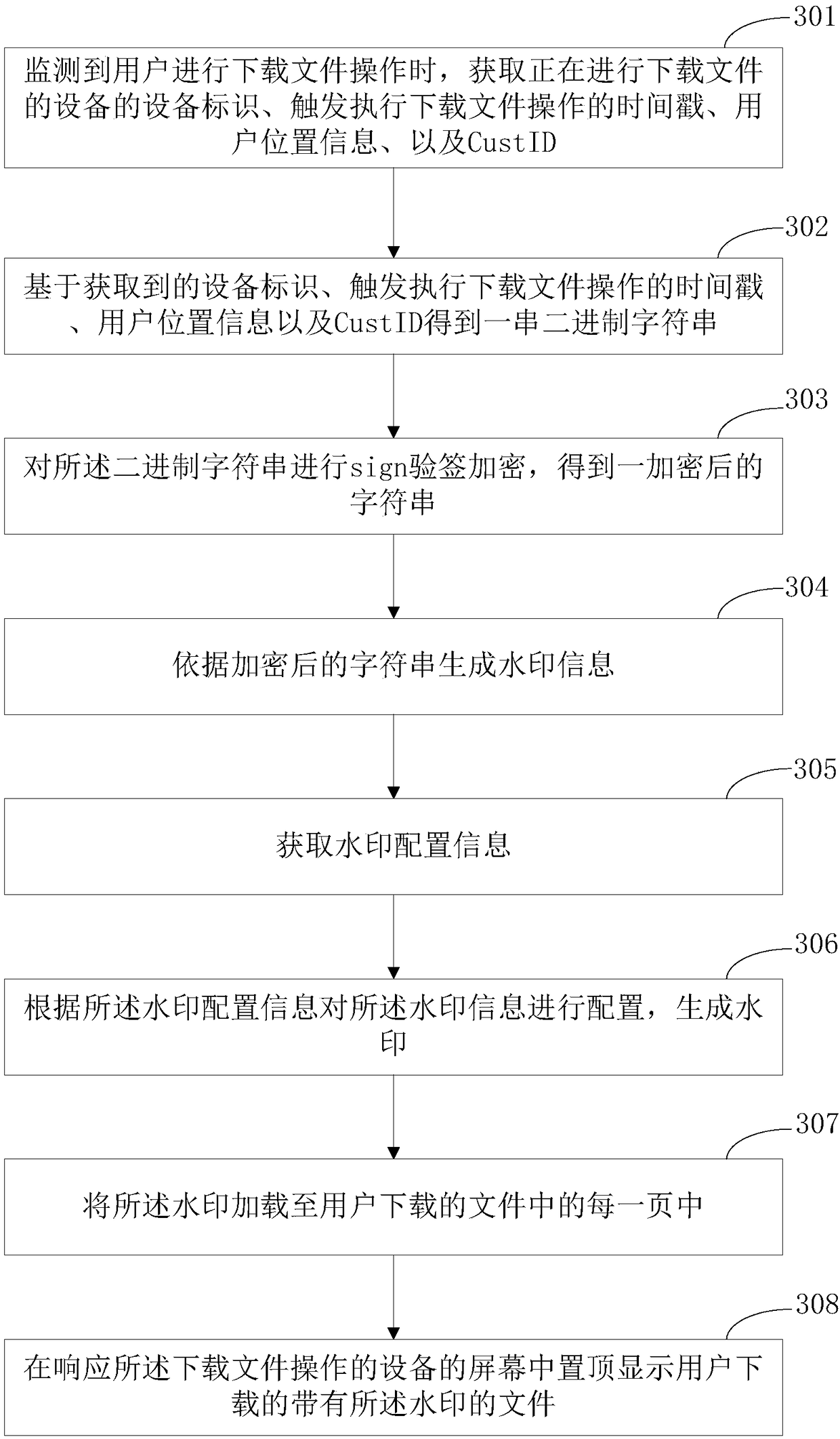
Watermark encryption method and device, medium and electronic device
ActiveCN108985081APrevent malicious tamperingFinanceDigital data protectionComputer hardwareTimestamp
Embodiments of the present invention provide a watermark encryption method and device, a medium, and an electronic device. The method comprises the following steps: obtaining monitoring information after monitoring a preset operation triggered by a user, wherein the monitoring information comprises a device identification of a device responsive to the preset operation, a timestamp for triggering the preset operation, user position information and a user identification; obtaining a string of strings based on the obtained monitoring information, and encrypting the strings to obtain the encryptedstrings; generating a watermark according to the encrypted string; loading the watermark into an operation object of the preset operation. The user behavior is monitored, and after the user triggersthe preset operation, the encrypted watermark is added to the operation object of the preset operation, thereby protecting the user's sensitive information and preventing the user's sensitive information from being leaked and being tampered with maliciously. At the same time, the information leaking behavior is traceable according to the traceable source of the monitoring information.
Owner:TAIKANG LIFE INSURANCE CO LTD +1
System and method for determining string similarity
ActiveUS20160004937A1Character and pattern recognitionSpecial data processing applicationsHash functionTheoretical computer science
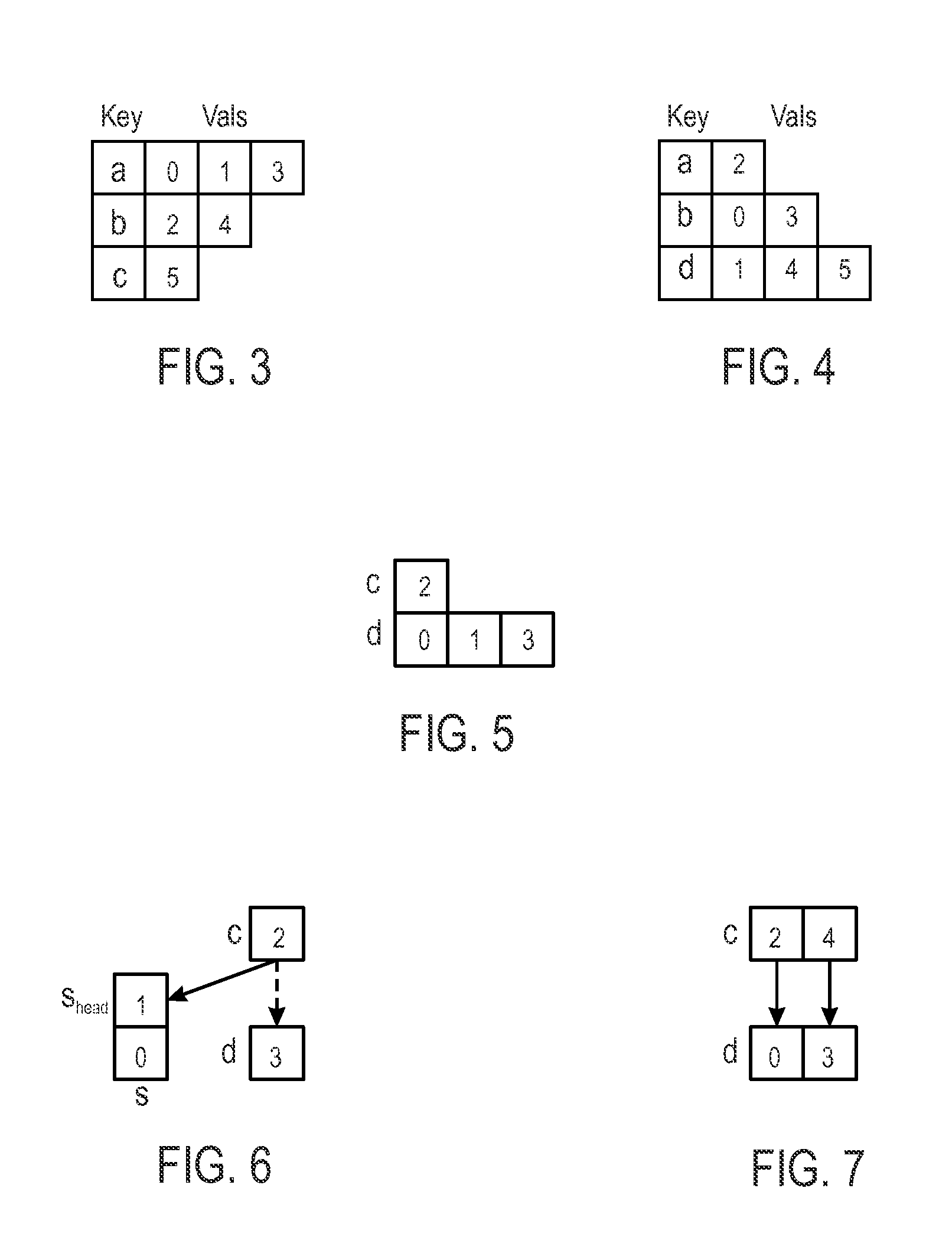
Provided are string similarity assessment techniques. In one embodiment, the techniques include receiving a plurality of input strings comprising characters from a character set and generating hashtables for each respective input string using a hash function that assigns the characters as keys and character positions in the strings as values. The techniques may also include determine a character similarity index for at least two of the input strings relative to each other by comparing a similarity of the values for each key in the their respective hashtables; determining a total disordering index based representative of an alignment of the at least two input strings by determining differences between a plurality of index values for each individual key in their respective hashtables and determining the total disordering index based on the differences; and determining a string similarity metric based on at least one character similarity index and the total disordering index.
Owner:GENERAL ELECTRIC CO
Character string input apparatus and method of controlling same
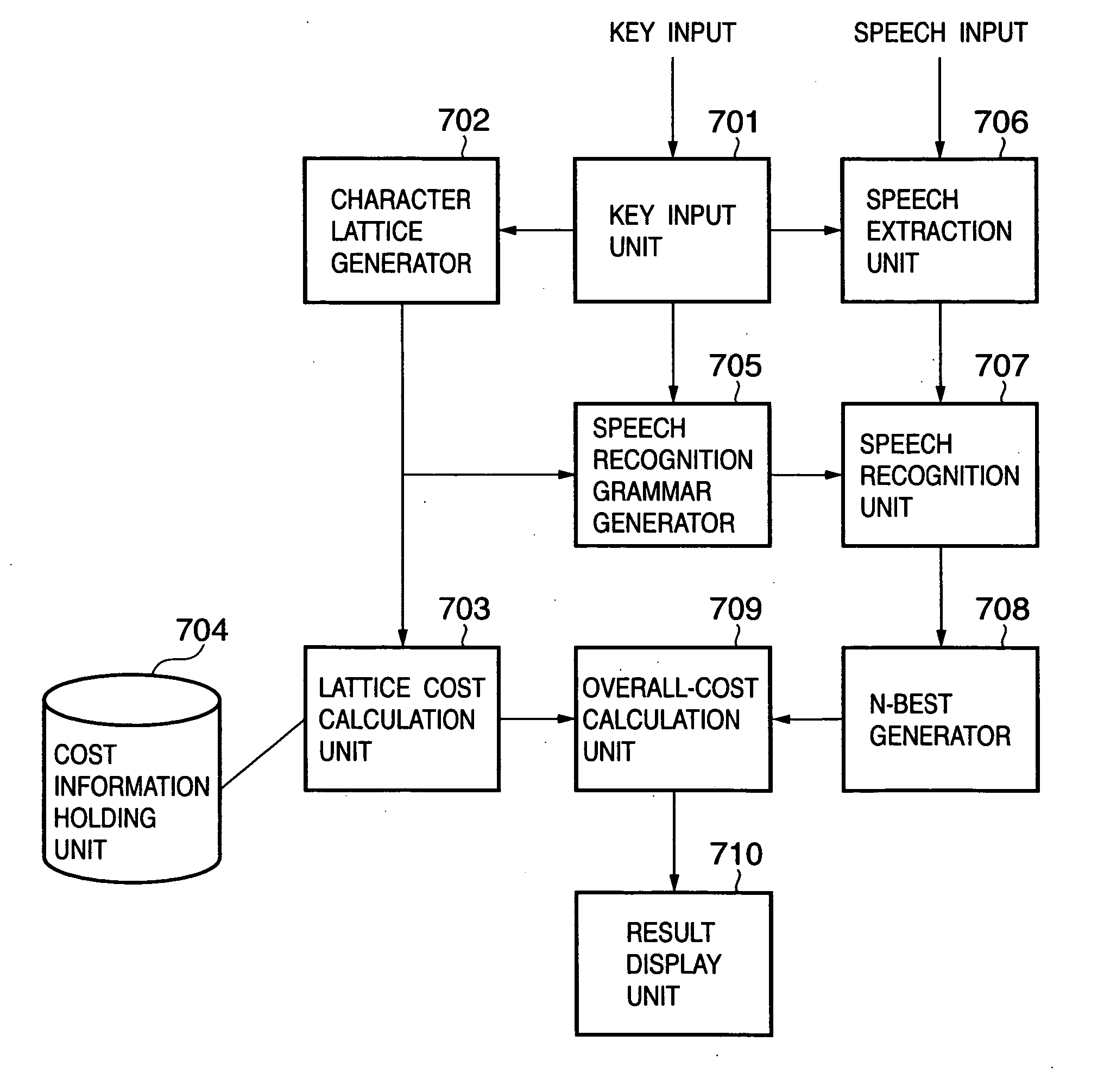
InactiveUS20060095263A1Improve operating efficiencyImprove naturalnessDevices with voice recognitionAlphabetical characters enteringIdentification deviceSpeech input
A character string input apparatus having specifying means for specifying a category of a character, and speech receiving means for receiving speech, wherein a character string is input based upon a specifying input from the specifying means and speech that has been received by the speech receiving means, is provided. Obtaining means obtains a plurality of character strings based-upon a series of specifying inputs by the specifying means. Generating means which, on the basis of the plurality of character strings obtained by the obtaining means, generates speech recognition grammar with respect to speech received by the speech receiving means following the series of specifying inputs. Speech recognition means performs speech recognition, using the speech recognition grammar generated by the generating means, with respect to the speech received by the speech receiving means following the series of specifying inputs.
Owner:CANON KK
Method and apparatus for improved grammar checking using a stochastic parser
InactiveUS7003444B2Natural language data processingSpeech recognitionNatural language processingText string
A method and grammar checking system are provided that generate a stochastic score, or a statistical goodness measure, for each of an input string of text and one or more alternative strings of text. An alternative generator generates the alternative strings of text, and a ranking parser produces parse trees and corresponding statistical goodness measures for each of the strings. The string of text having the highest goodness measure is selected for recommendation to a user.
Owner:MICROSOFT TECH LICENSING LLC
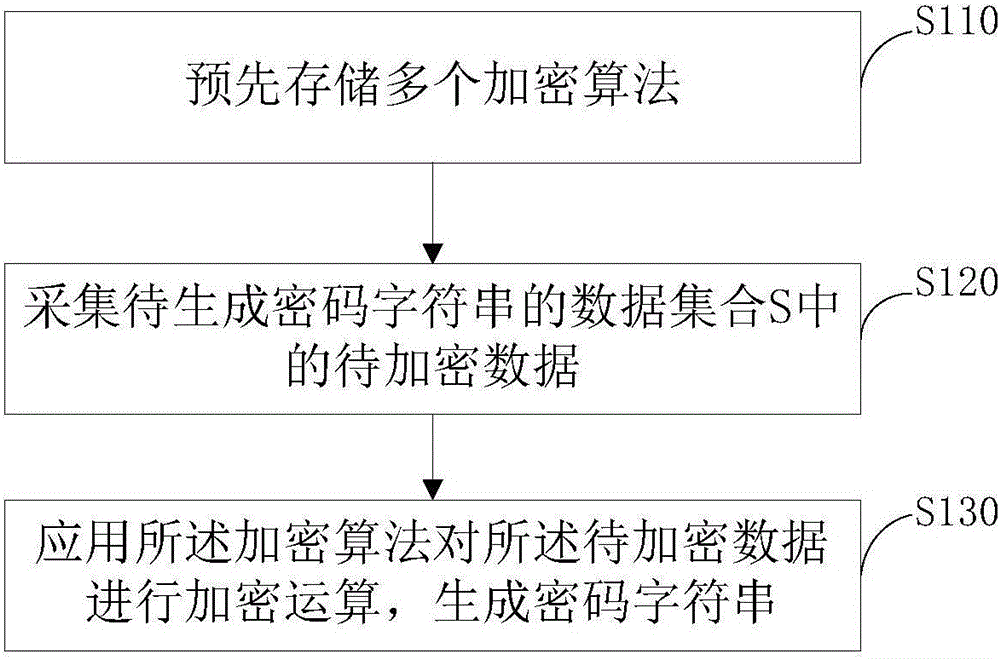
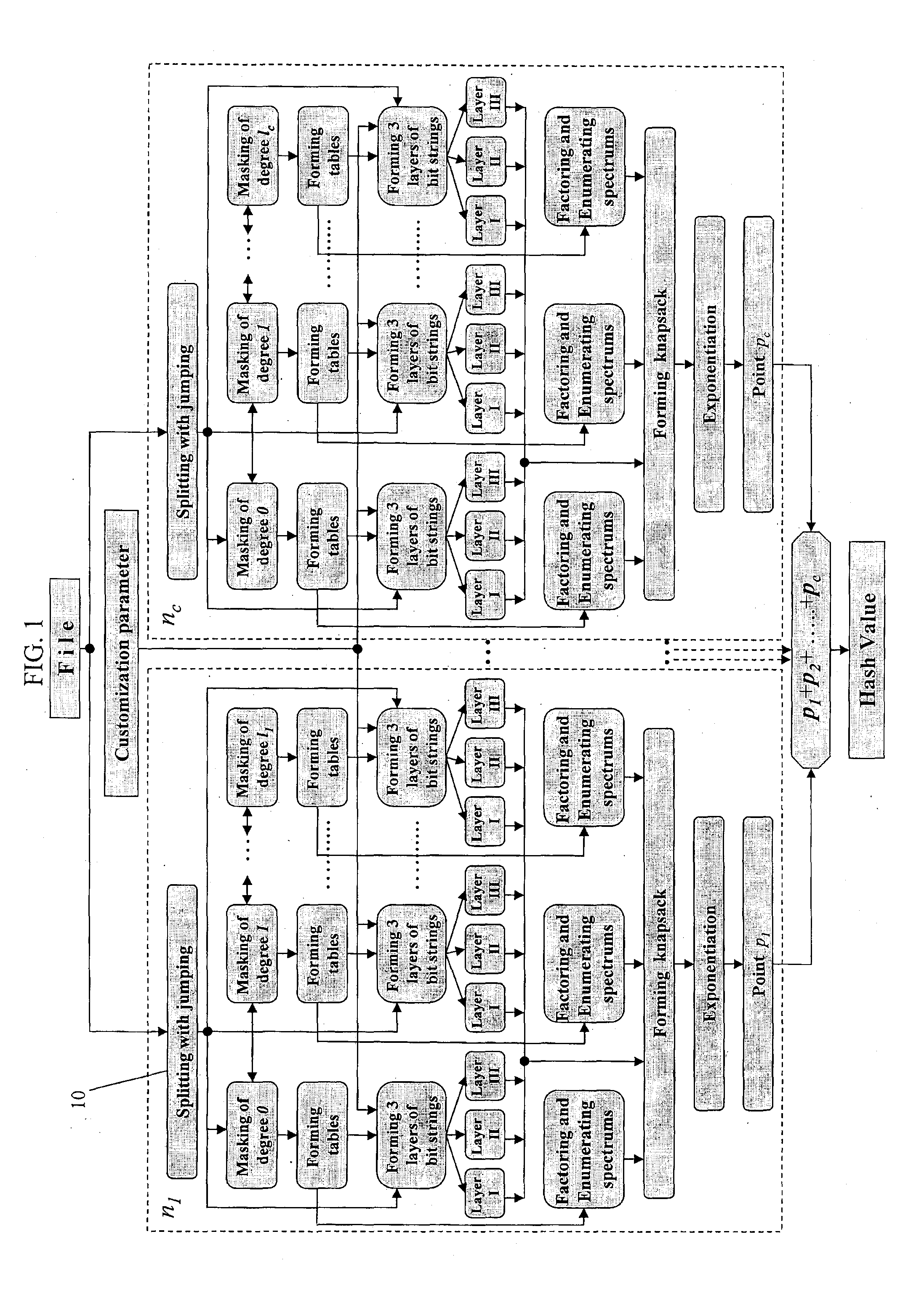
Cipher character string generation method and apparatus
InactiveCN106204038AOvercoming repetitivenessOvercome the flaws that are easy to be crackedPayment protocolsMultiple encryptionData set
The invention provides a cipher character string generation method. The method comprises the following steps: prestoring multiple encryption algorithms; acquiring data to be encrypted in a data set S of cipher character strings to be generated; and by use of the encryption algorithms, performing encryption operation on the data to be encrypted so as to generate the cipher character strings. According to the embodiments of the invention, the cipher character strings are generated through arrangement of the multiple encryption algorithms, and the method and apparatus have the positive effects of reducing the risk of cracking the cipher character strings and improving the security of the cipher character string.
Owner:GUANGZHOU ZHENGFENG ELECTRON TECH CO LTD
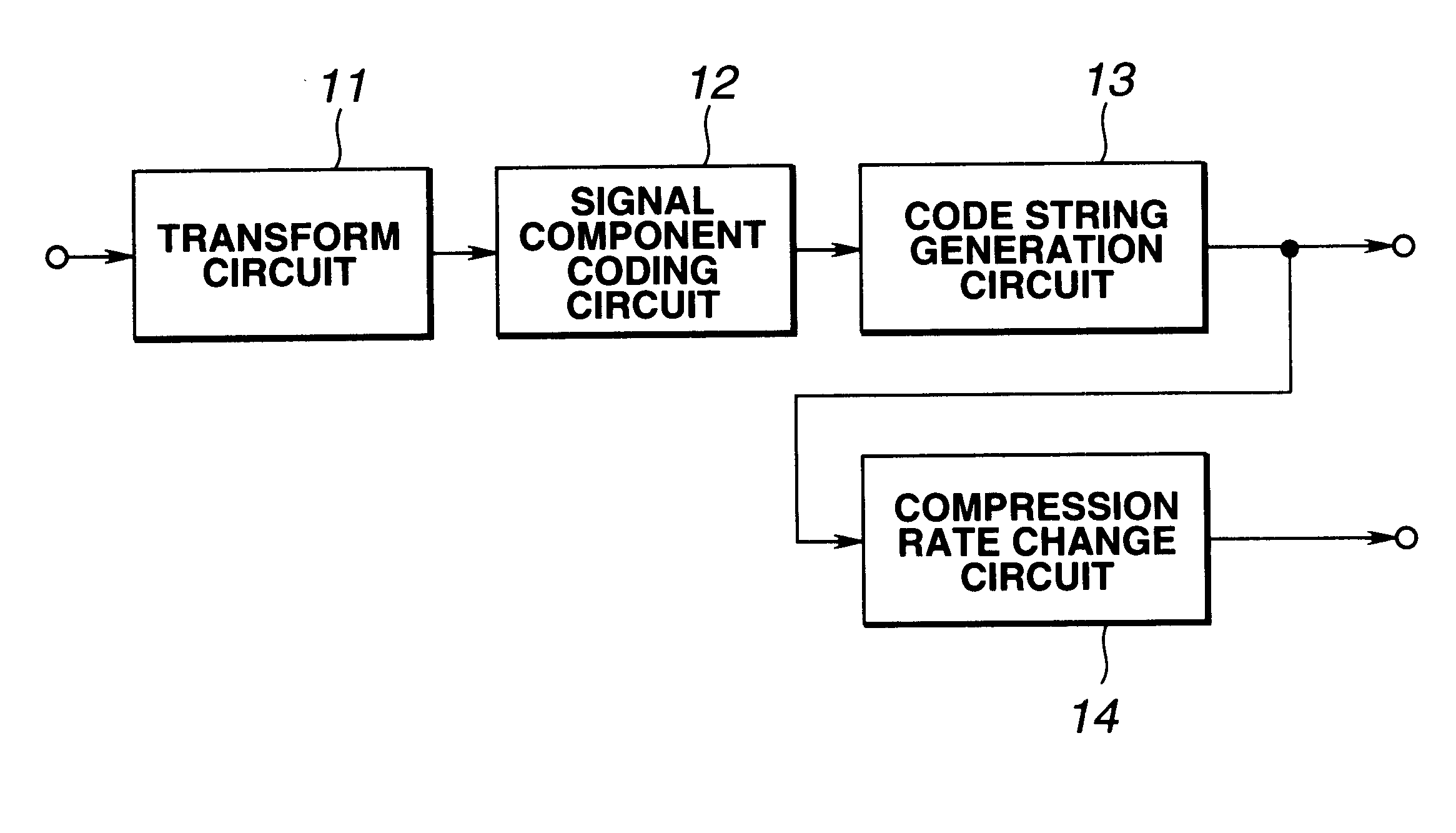
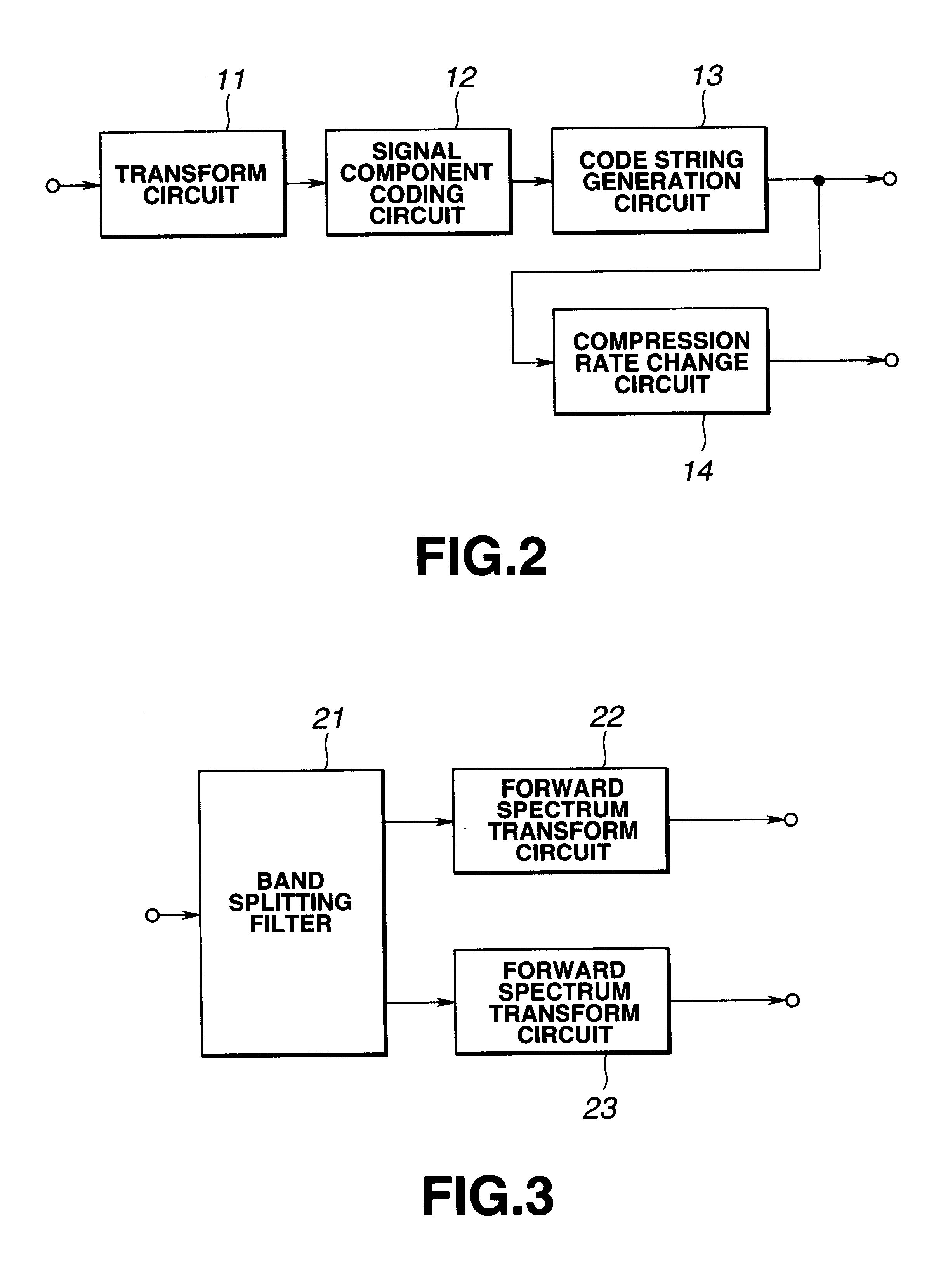
Coding device, coding method, decoding device, decoding method, program recording medium and data recording medium
InactiveUS6661923B1Avoid large quantitiesHigh-speed generationSpeech analysisCharacter and pattern recognitionDecoding methodsFrequency spectrum
A signal component coding circuit codes spectral components from a transform circuit for converting an audio signal to spectral components. A code string generation circuit generates a code string block of each unit time from the coded data from the signal component coding circuit. A compression rate change circuit changes the compression rate of the code string from the code string generation circuit, if necessary. For example, when the compression rate needs to be changed because of a change of the transmission capacity of a transmission line, the compression rate change circuit extracts codes of respective signal components from the code string, if necessary, and thus generates a code string having a changed compression rate. With such a structure, it is possible to solve the problem that processing to be carried out at a high speed such as real-time processing of compression rate change cannot be suitably carried out since an operation scale substantially similar to that of decoding and coding of an acoustic waveform signal is required in generating a code string having a changed compression rate from a code string outputted from a coding device.
Owner:SONY CORP
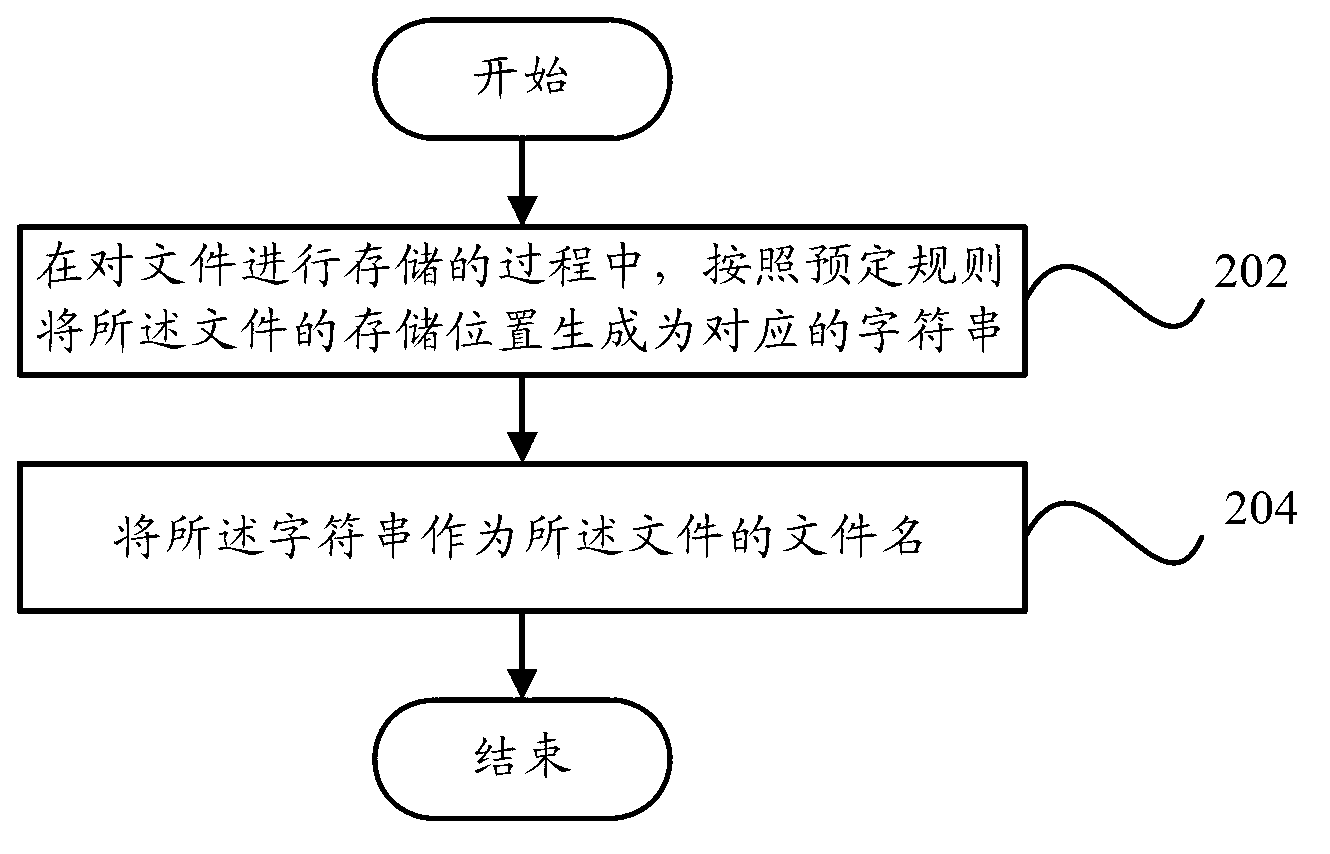
File management system and method
ActiveCN103020144AAvoid repetitionRealize managementSpecial data processing applicationsDocument handlingString generation
The invention provides a file management system. The file management system comprises a character string generation unit, a file processing unit and a storage unit, wherein the character string generation unit is used for generating the storage position of the file into the corresponding character string according to the preset rule in the process of storing the file; the file processing unit is used for taking the character string as the file name of the file; and the storage unit is used for storing the file processed by the file processing unit. The invention also provides a file management method. By the adoption of the technical scheme, repetition of the file names of the files at different storage positions can be avoided and management of distributed files is realized favorably.
Owner:用友汽车信息科技(上海)股份有限公司
System and method for managing versions of electric drawing
ActiveCN104809189ASave bandwidthEncryption securitySpecial data processing applicationsComputer moduleComputer science
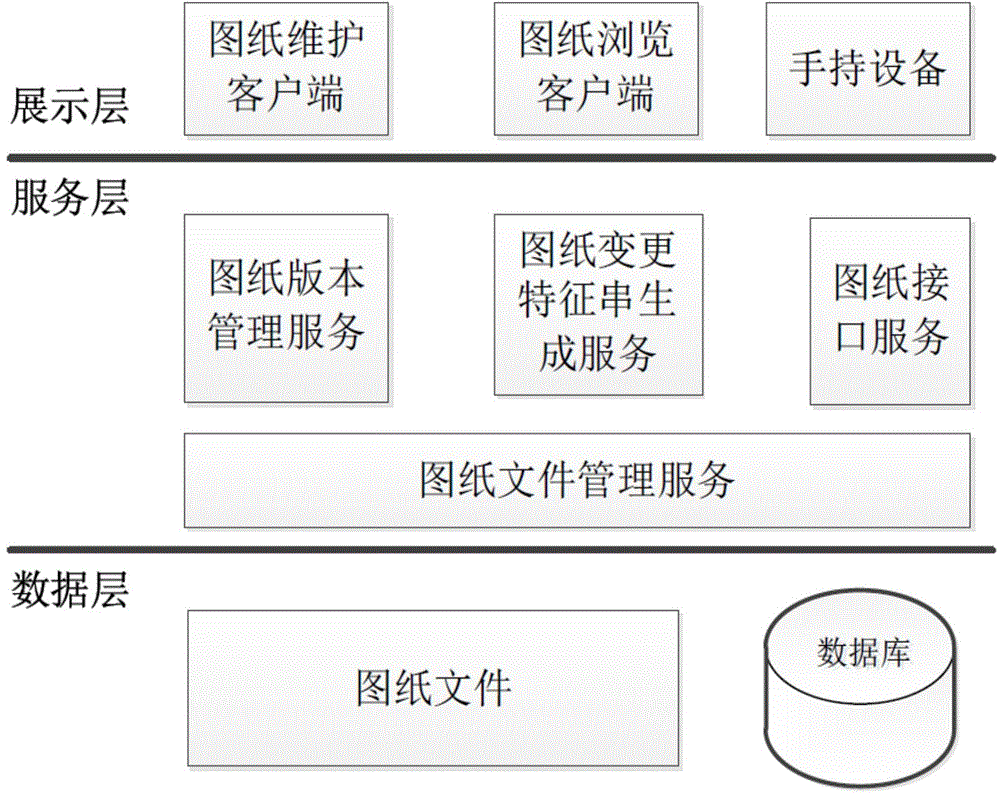
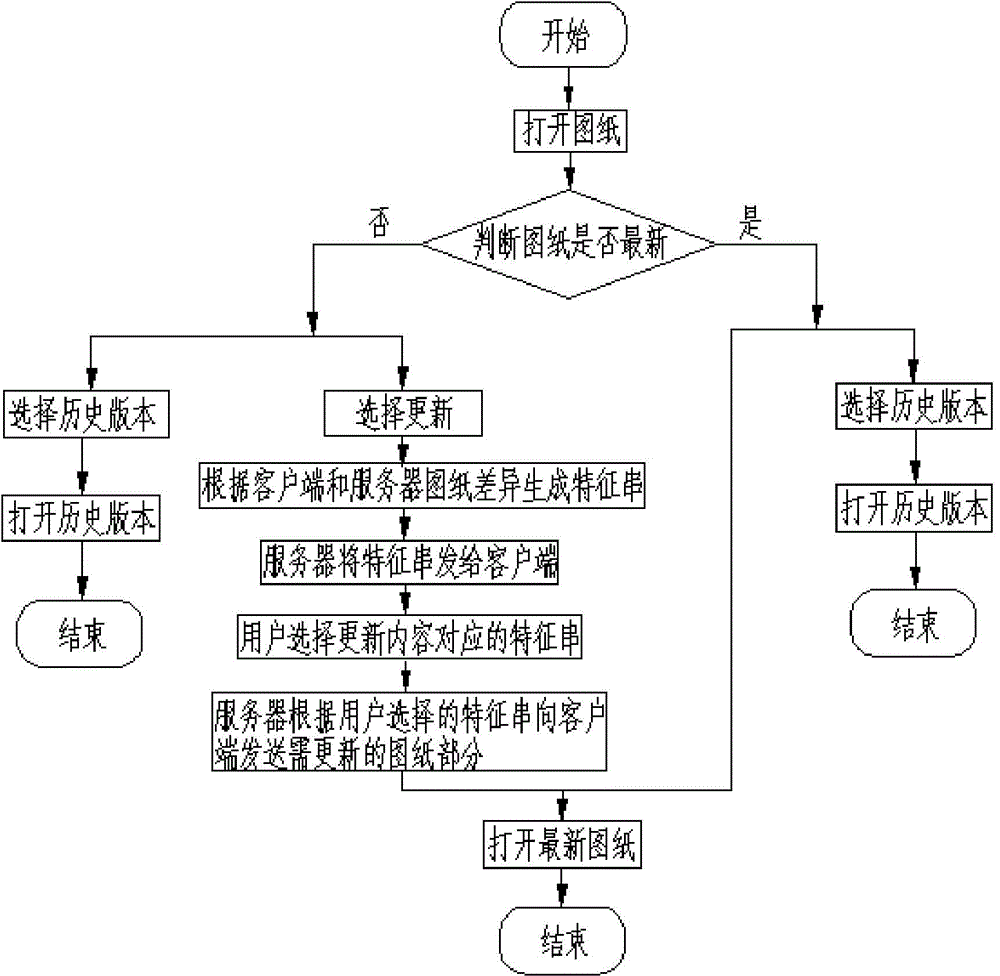
The invention relates to a system for managing versions of an electric drawing. An architecture of the system comprises a data layer, a service layer and a display layer, wherein a drawing version management service module of the service layer is used for managing a drawing file and a drawing version; a drawing change characteristic string generation service module is used for comparing the difference of a client end drawing and a server end drawing to generate a characteristic string of the difference, and partially updating according to the selection of the client end. A management method based on the system comprises the following steps of numbering the modified drawing versions; uniformly storing the history versions; enabling the client end to detect and update the to-be-updated drawing when the drawing file is opened; comparing the client end and the server end; generating the characteristic string; enabling the user to select updating according to the characteristic string. The system has the advantages that the process is simple, and the operation is convenient; the information is obtained by the characteristic string, so the bandwidth is saved, and more safety is realized.
Owner:STATE GRID CORP OF CHINA +1
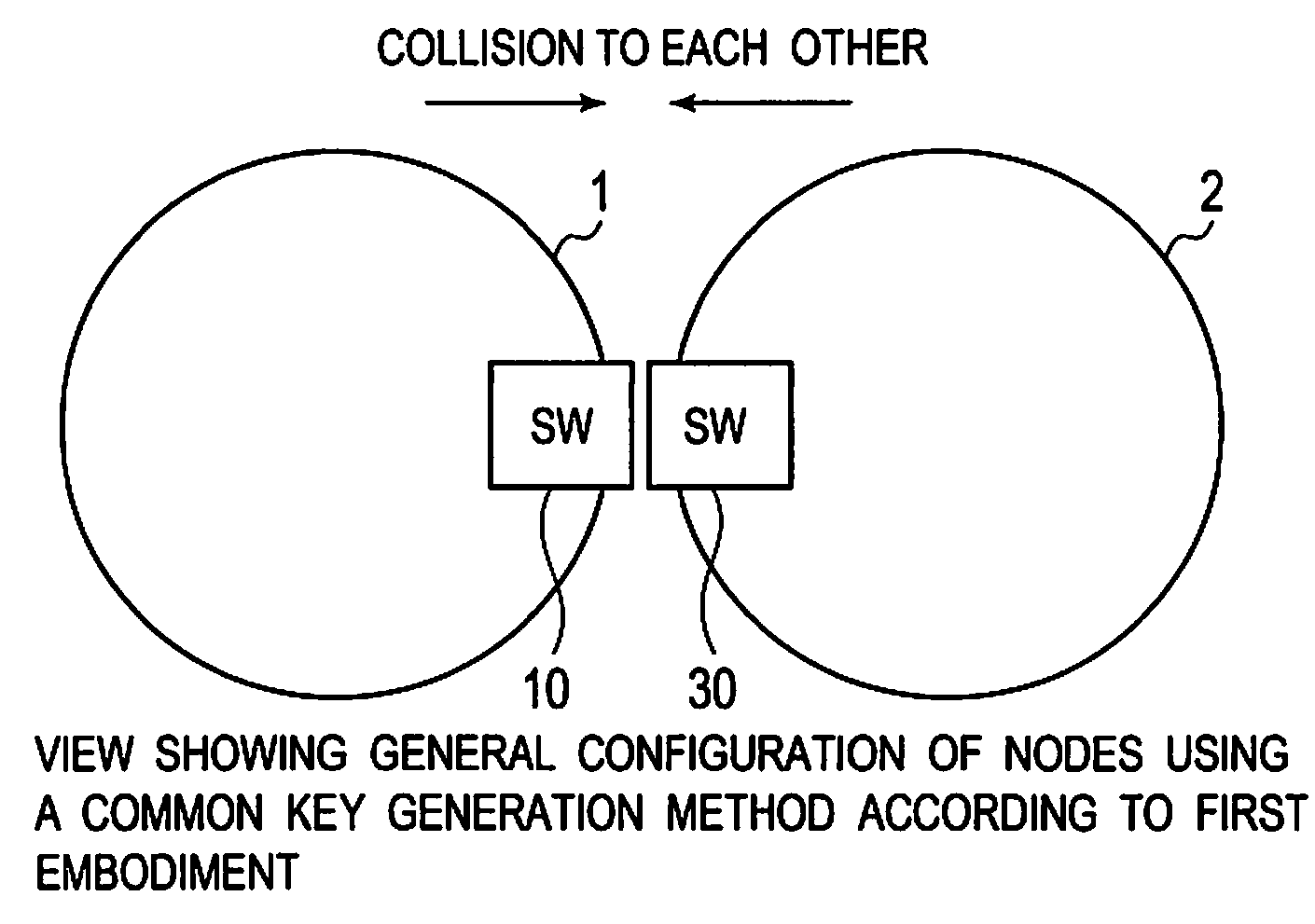
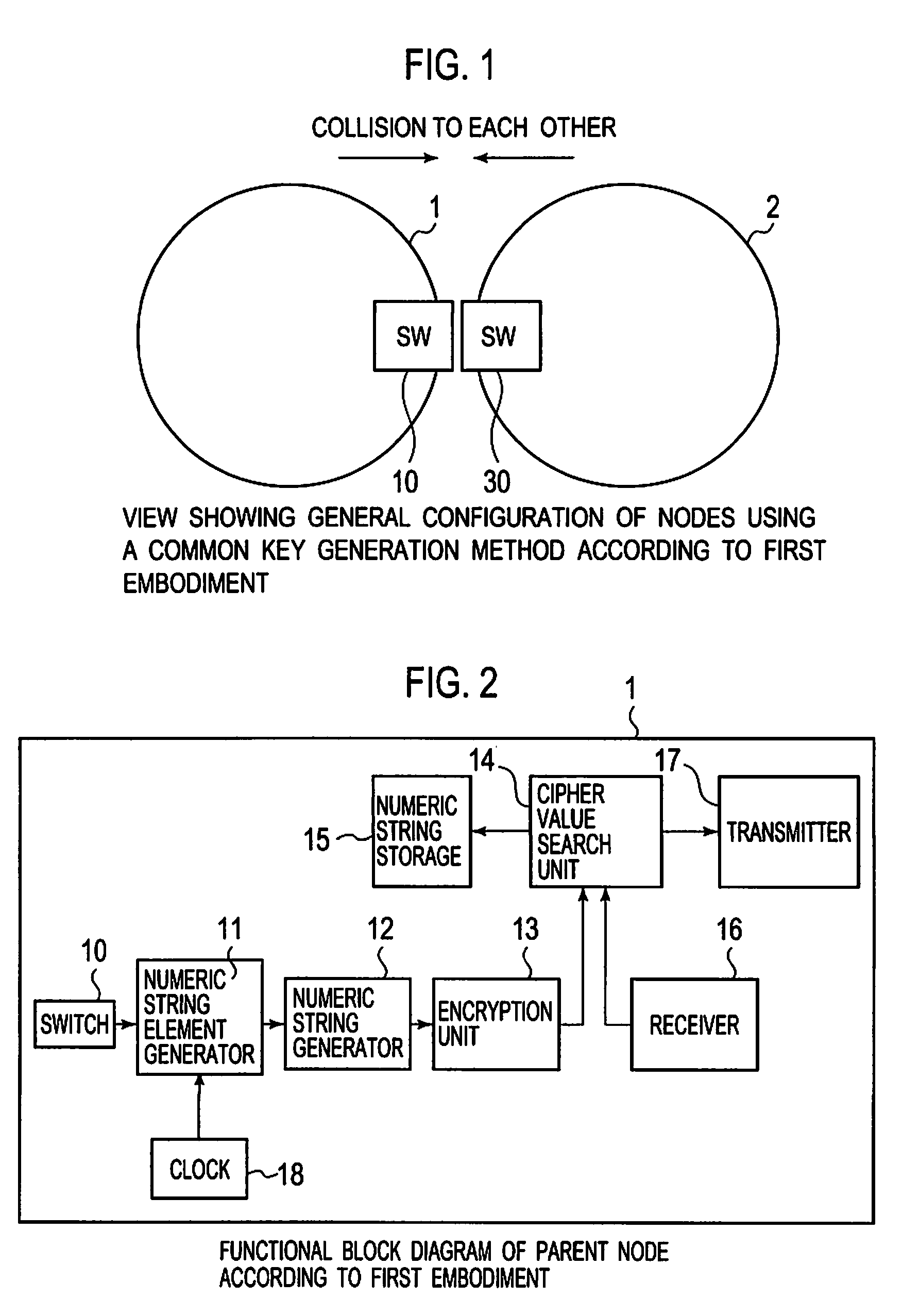
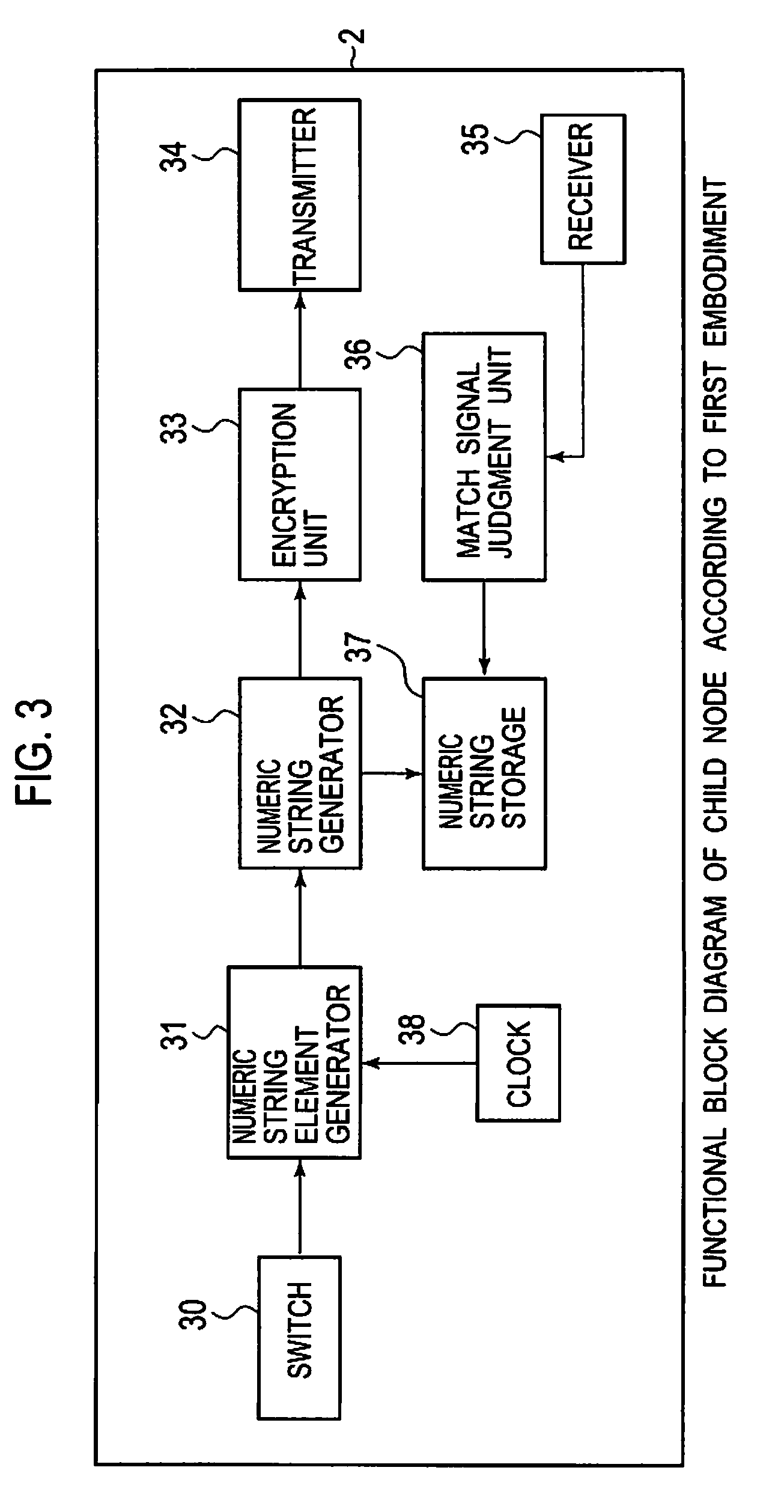
Common key generation system, common key generation method and node using the same
InactiveUS20090129590A1Stable generationEncryption apparatus with shift registers/memoriesInformation technology support systemTheoretical computer scienceKey generation
First and second nodes generate numeric string elements from time interval by their physical changes. The first node generates a basic numeric string from the numeric string elements and similar numeric strings, encrypts the generated basic numeric string and the similar numeric strings, and generates a cipher value list that stores the numeric strings with corresponding cipher values. The second node generates a basic numeric string based on the numeric string elements generated by the second node, encrypts the generated basic numeric string in accordance with the same encryption rule as that for the first node, and transmits the generated cipher value to the first node. The first node receives a cipher value from the second node, and compares the received cipher value with the cipher values in the cipher value list to find a match, and transmits a match signal if a match is found.
Owner:OKI ELECTRIC IND CO LTD
System and method for the calculation of a polynomial-based hash function and the erindale-plus hashing algorithm
ActiveUS20110211697A1User identity/authority verificationSecret communicationHash functionSpeed of processing
Owner:VOLKOVS NIKOLAJS
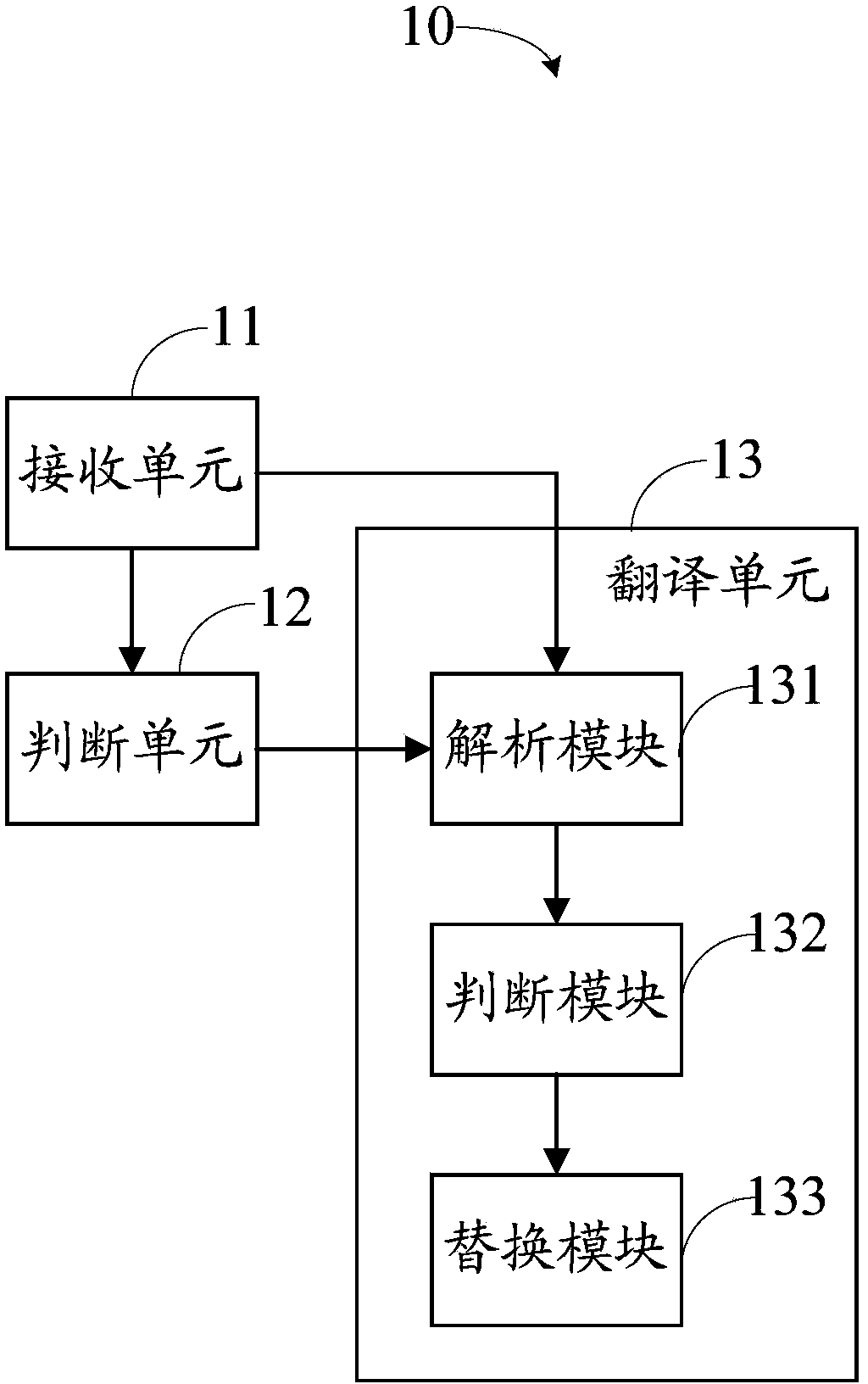
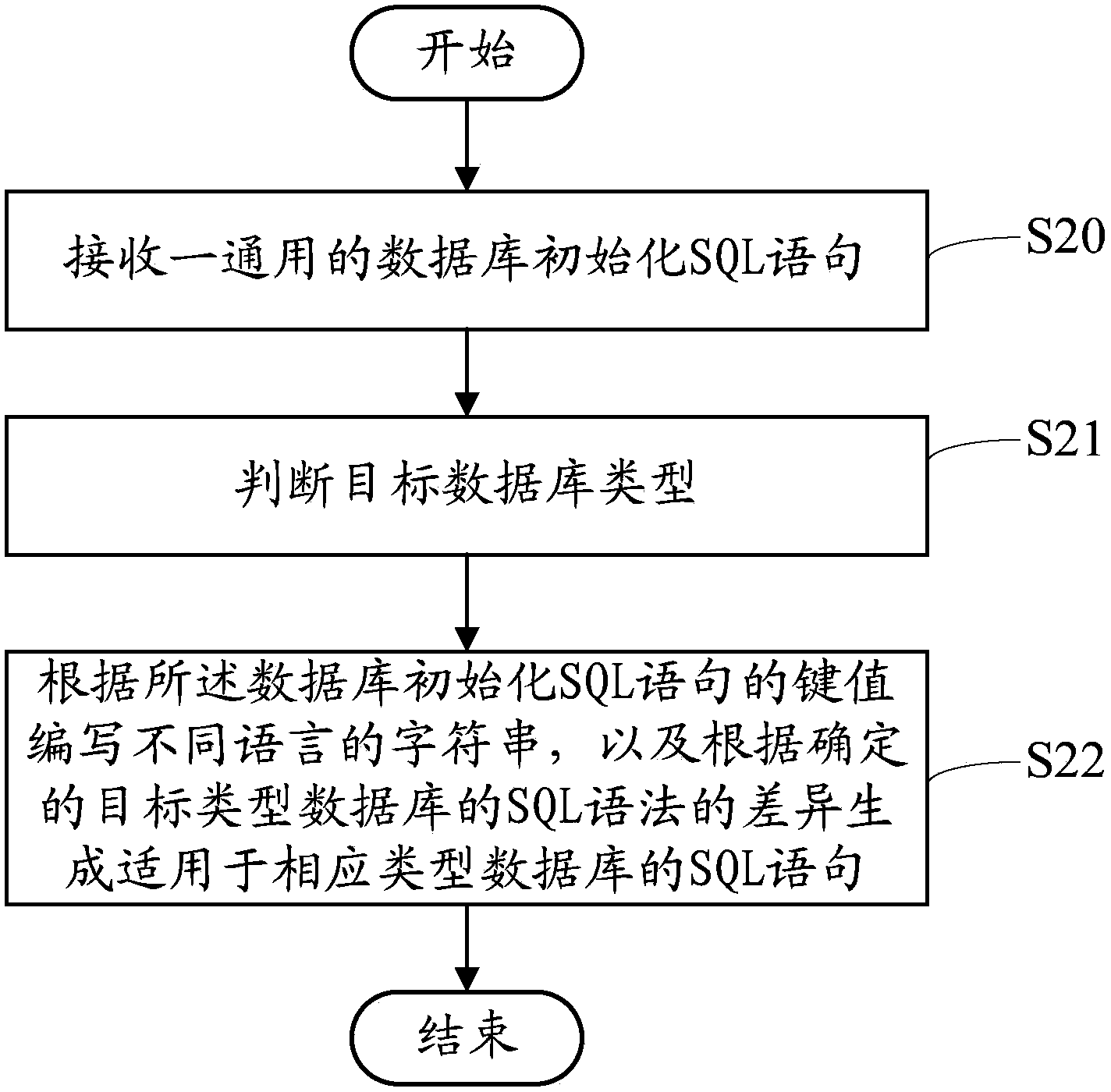
Database construction system, device and method
InactiveCN103914572AEasy maintenanceReduced risk of errorSpecial data processing applicationsDatabase design/maintainanceTarget databaseHuman language
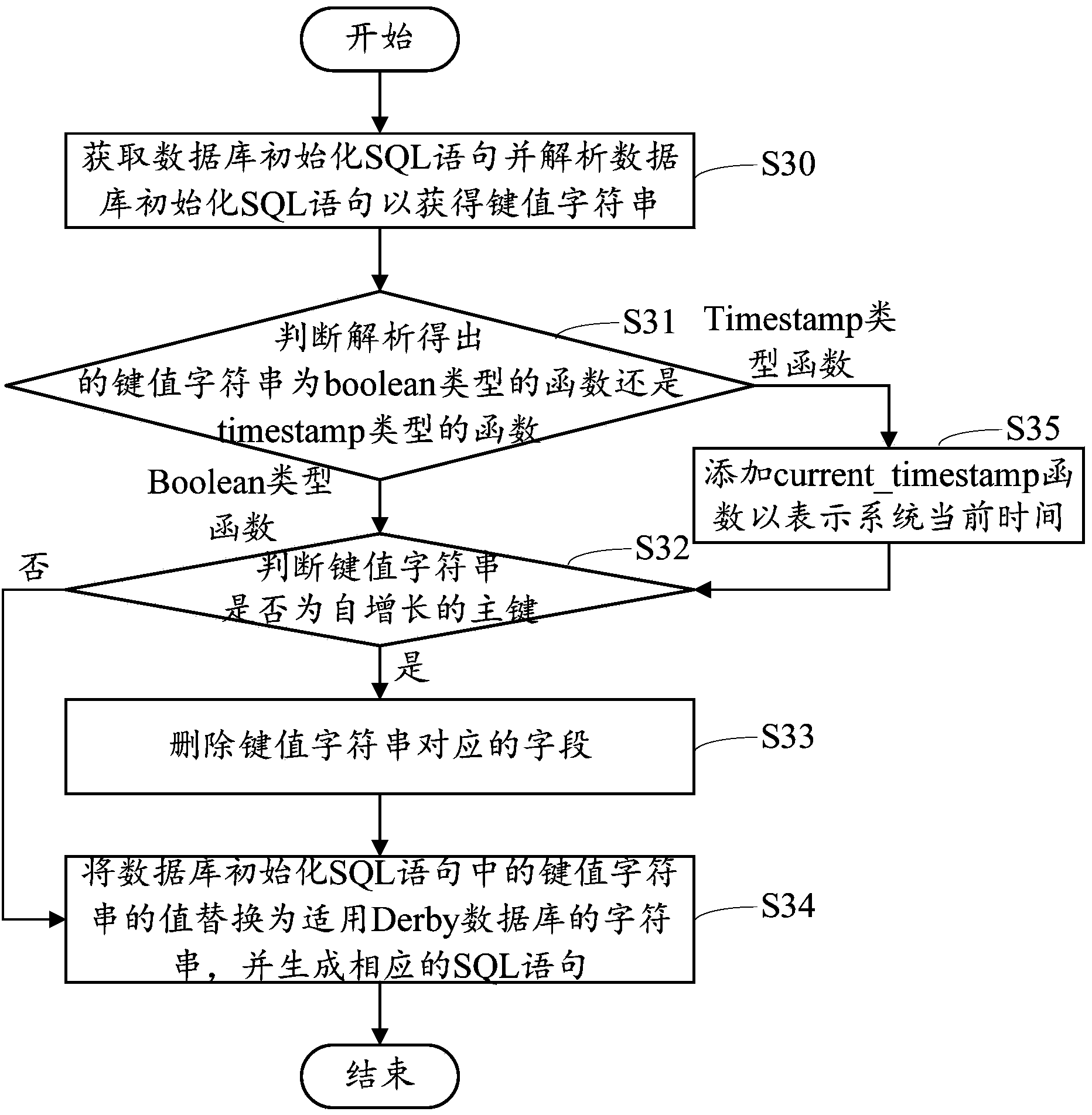
The invention provides a database construction system which is run in a compiling system and used for executing compiling and access to a database. The database construction system comprises a receiving unit, a judging unit and a translating unit. The receiving unit is used for receiving a universal initialization SQL statement of a database. The judging unit is used for judging the type of a target database. The translating unit is used for compiling character strings in different languages according to key values of the initialization SQL statement of the database and generating SQL statements executed in the target database according to the initialization SQL statement of the database and the key value character strings. The invention further provides a database construction method and device. By means of the database construction system, device and method, the SQL statements adapting to various types of databases and languages can be generated according to the universal SQL statement for initialization of data of the database, so that the initialization SQL statement is easy to maintain, and the risk that errors are generated in the maintenance process is reduced.
Owner:FUJIAN STAR NET EVIDEO INFORMATION SYST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com