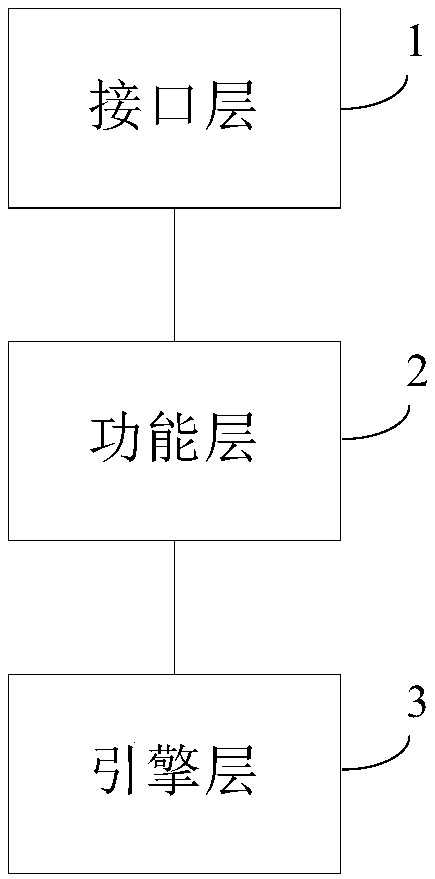
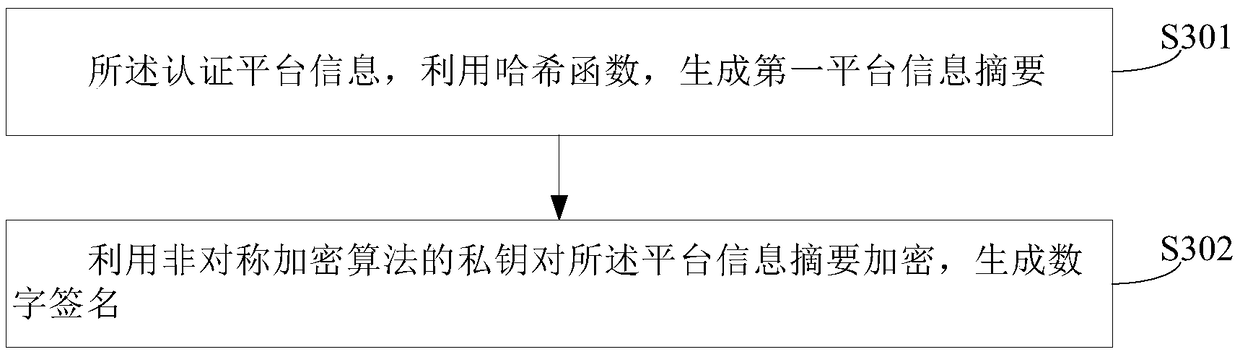
A security network middleware for identity authentication, and a method and apparatus for implementing the same
A security network, identity authentication technology, applied in computer security devices, digital data authentication, instruments, etc., can solve problems such as user identity information theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
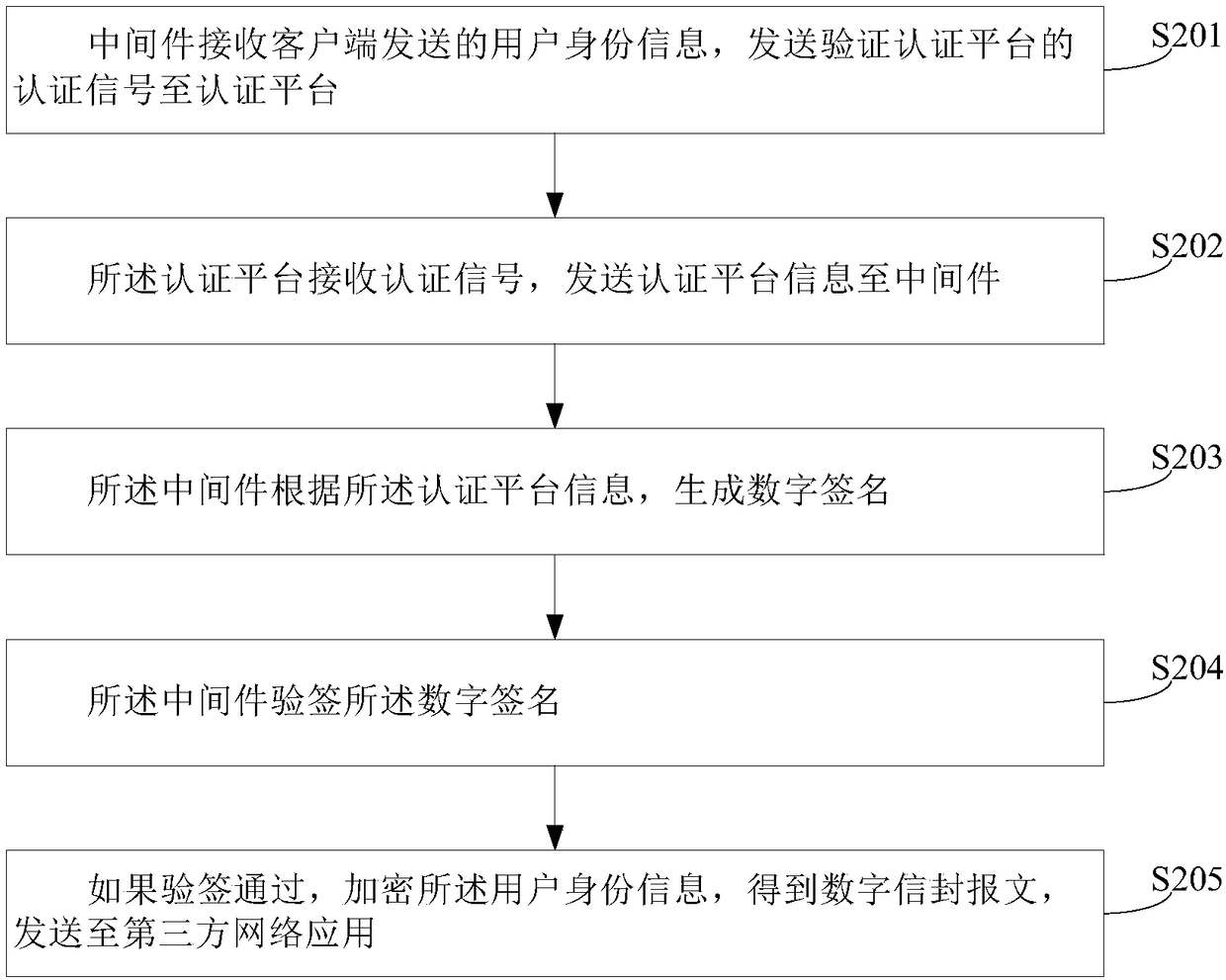
[0073] see figure 2 , which is a first embodiment of an implementation method of a secure network middleware for identity authentication provided by this application, the implementation method includes:
[0074] Step 201, the middleware receives the user identity information sent by the client, and sends an authentication signal for verifying the authentication platform to the authentication platform;
[0075] Specifically, when the middleware receives the user identity information sent by the client, it first needs to verify the identity of the authentication platform to verify whether the authentication platform is a real platform for verifying user identity information. The platform can ensure secure communication between the middleware and the authentication platform.
[0076] Step 202, the authentication platform receives the authentication signal, and sends the authentication platform information to the middleware;
[0077] It should be noted that the authentication p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com