Block-based method for scanning object code and replacing sensitive instruction
A technology of sensitive instructions and object codes, applied in the field of binary translation, can solve problems such as hardware exceptions and a large amount of system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
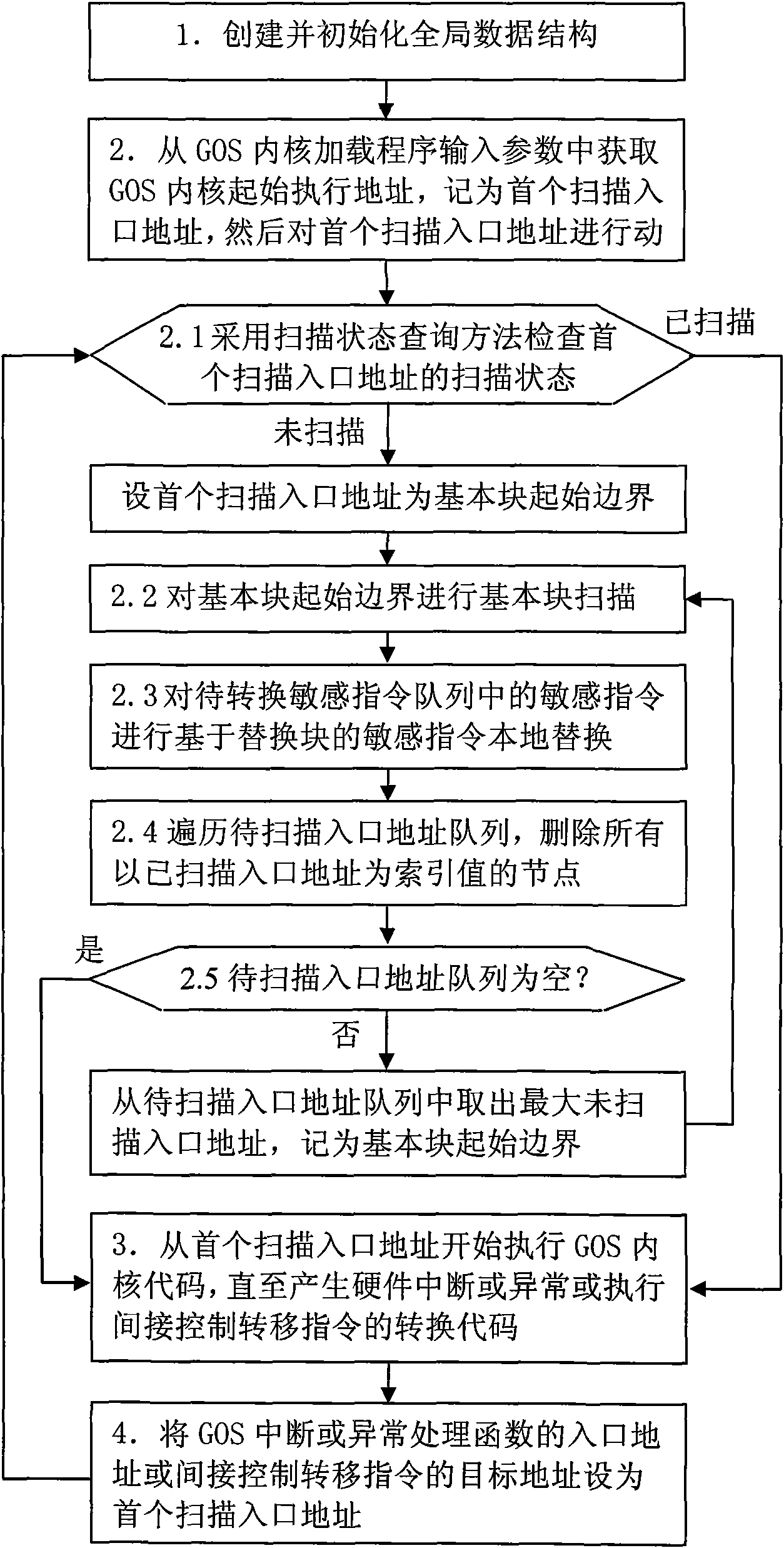
[0074] figure 1 It is the overall flowchart of the present invention
[0075] 1. Create and initialize a global data structure.
[0076] 2. Obtain the initial execution address of the GOS kernel from the input parameters of the GOS kernel loader, record it as the first scan entry address, and then dynamically scan the first scan entry address:
[0077] 2.1. Use the scan status query method to check the scan status of the first scan entry address: if it has been scanned, go to 3; if it has not been scanned, record the first scan entry address as the starting boundary of the basic block, and go to 2.2.
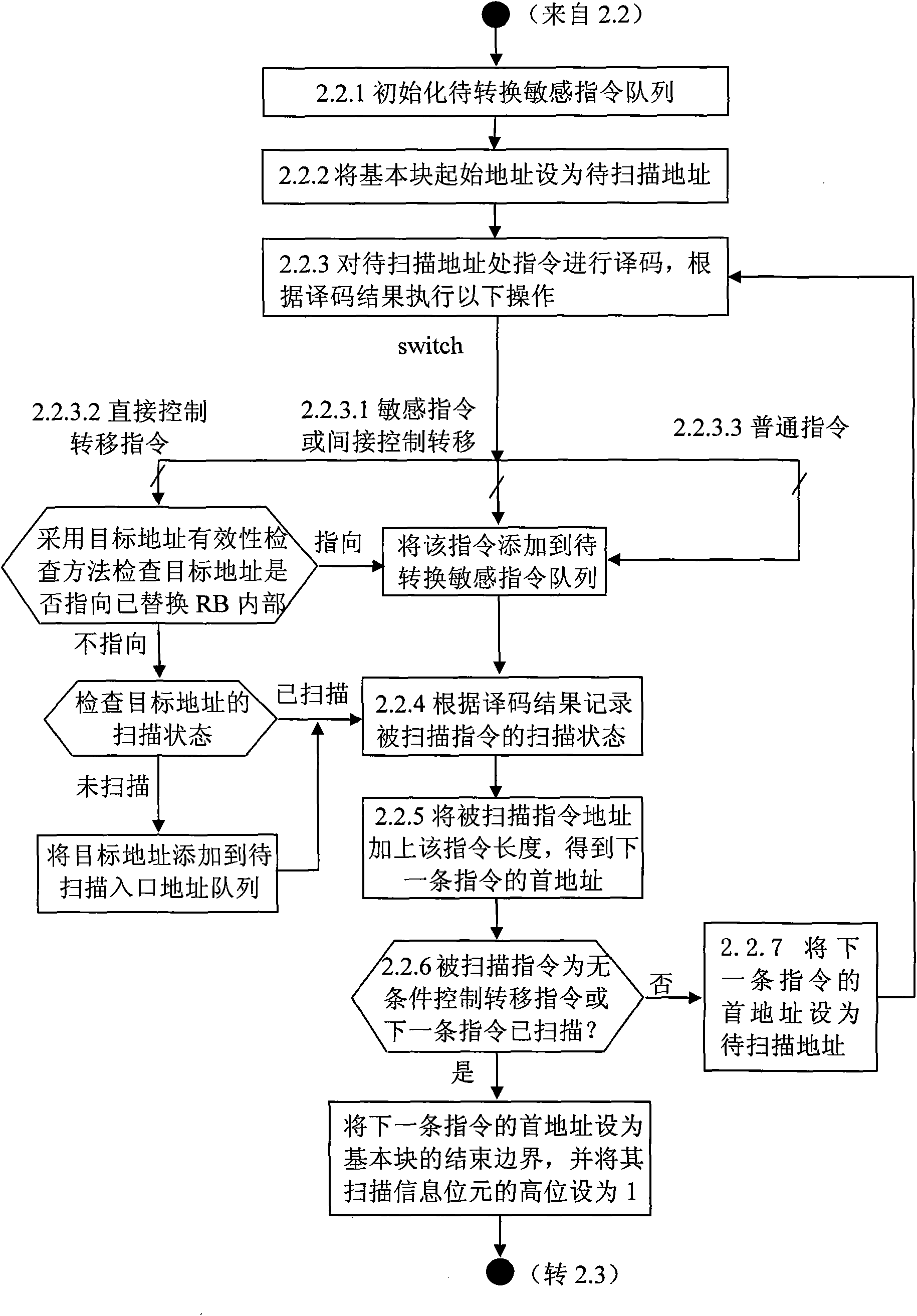
[0078] 2.2. Basic block scanning is performed on the starting boundary of the basic block.
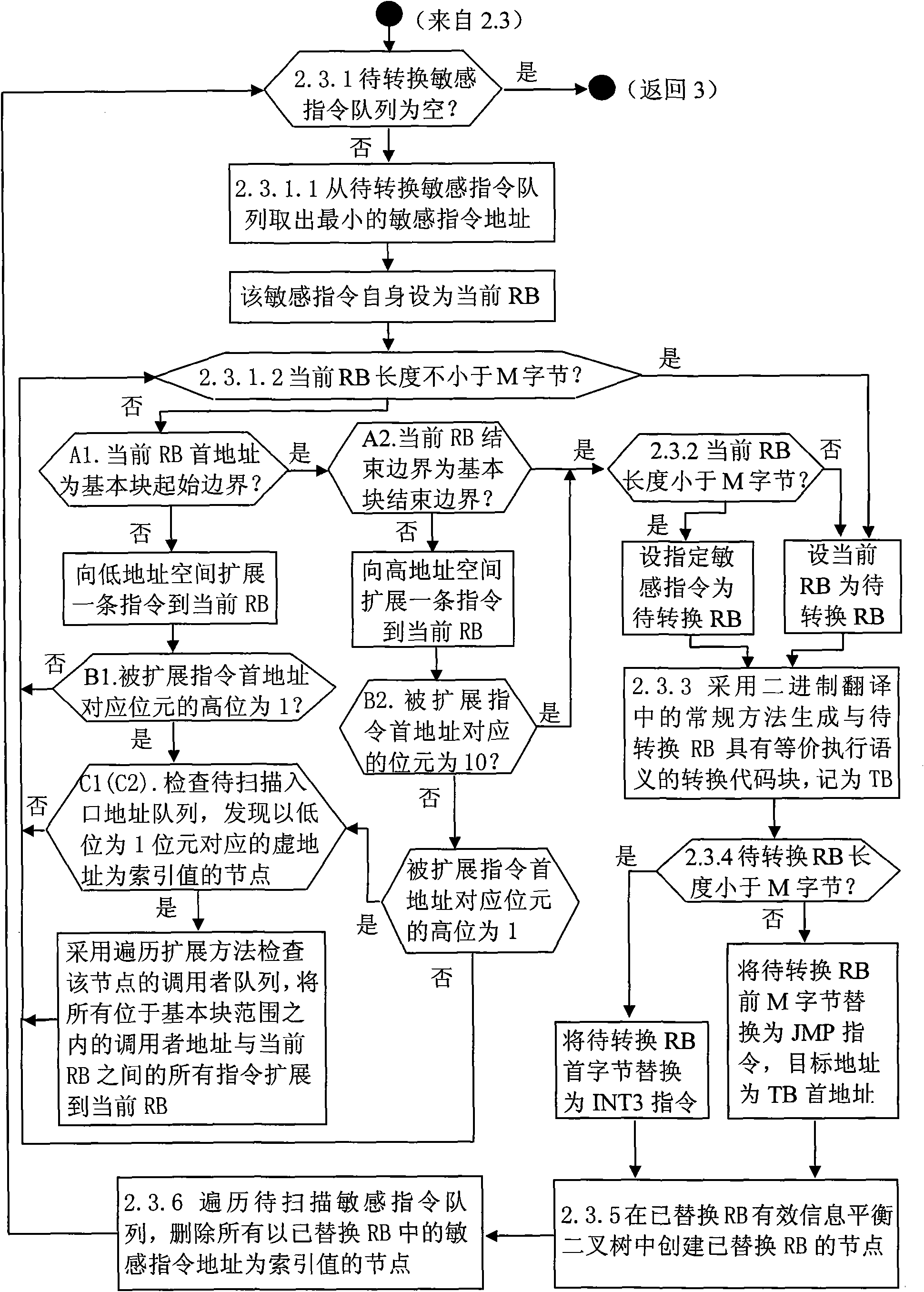
[0079] 2.3 Perform local replacement of sensitive instructions based on the replacement block for sensitive instructions in the queue of sensitive instructions to be converted.
[0080] 2.4 Traverse the entry address queue to be scanned, and delete all nodes whose index value is the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com