Application abnormal behavior identification model building method and apparatus, and application abnormal behavior identification method and apparatus
A technology for identifying models and establishing methods, which is applied in character and pattern recognition, computer security devices, instruments, etc., and can solve problems such as triggering abnormal behaviors that cannot effectively cover the real machine environment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
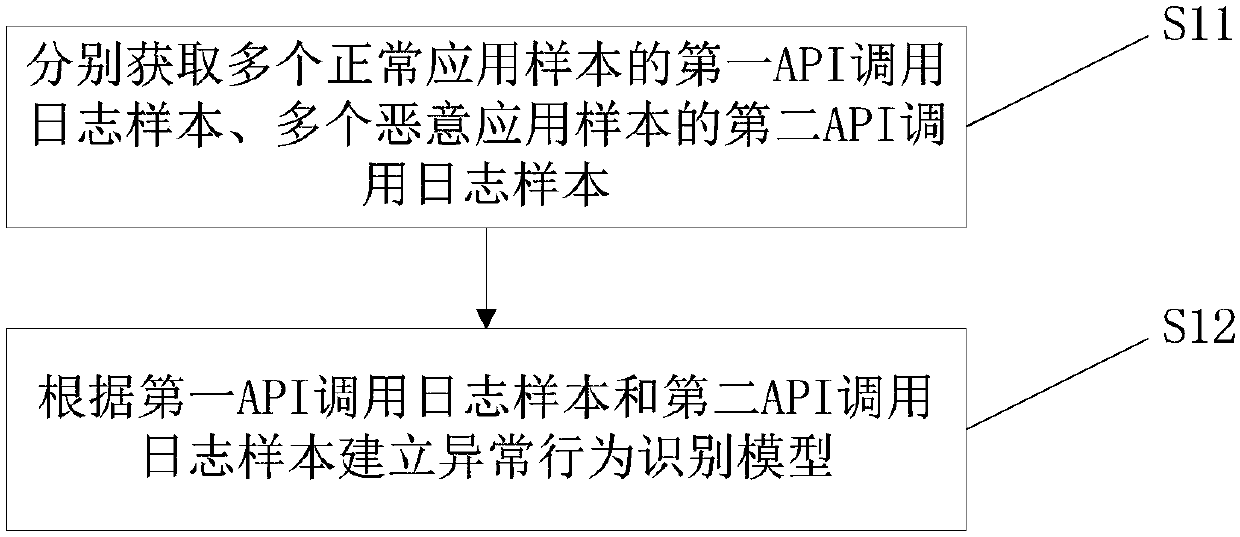
[0065] Such as figure 1 As shown, this embodiment provides a method for establishing an application abnormal behavior identification model, including the following steps:
[0066] S11: Respectively acquire first API (Application Programming Interface, application programming interface) call log samples of multiple normal application samples and second API call log samples of multiple malicious application samples. The normal application sample and the malicious application sample may be applications other than the application to be detected. The API interfaces corresponding to the first API call log sample and the second API call log sample are consistent with the API interfaces corresponding to the API call logs used in actual detection.
[0067] S12: Establish an abnormal behavior identification model according to the first API call log sample and the second API call log sample.
[0068] The method for establishing an application abnormal behavior identification model prov...
Embodiment 2
[0091] This embodiment provides a method for establishing an application abnormal behavior identification model, including the following steps:
[0092] Step 1: Obtain multiple normal application samples and multiple malicious application samples respectively.
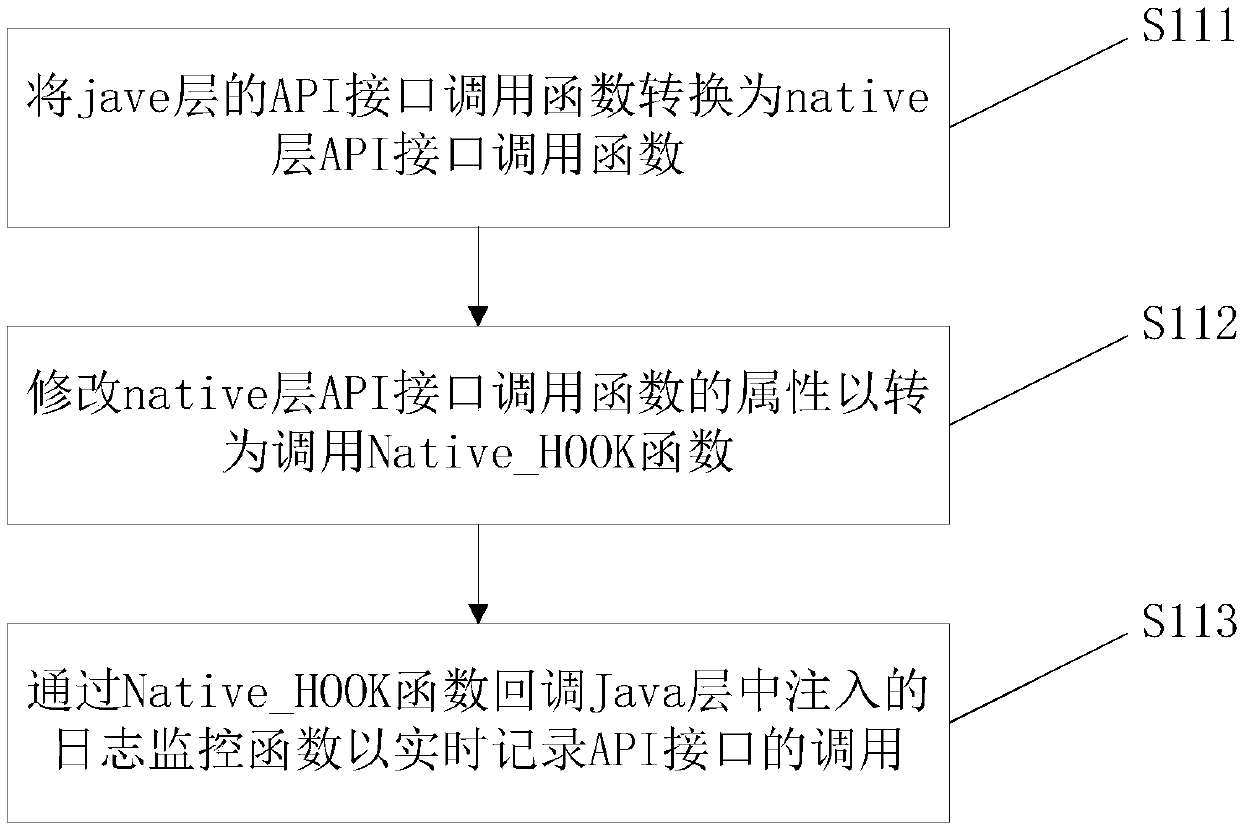
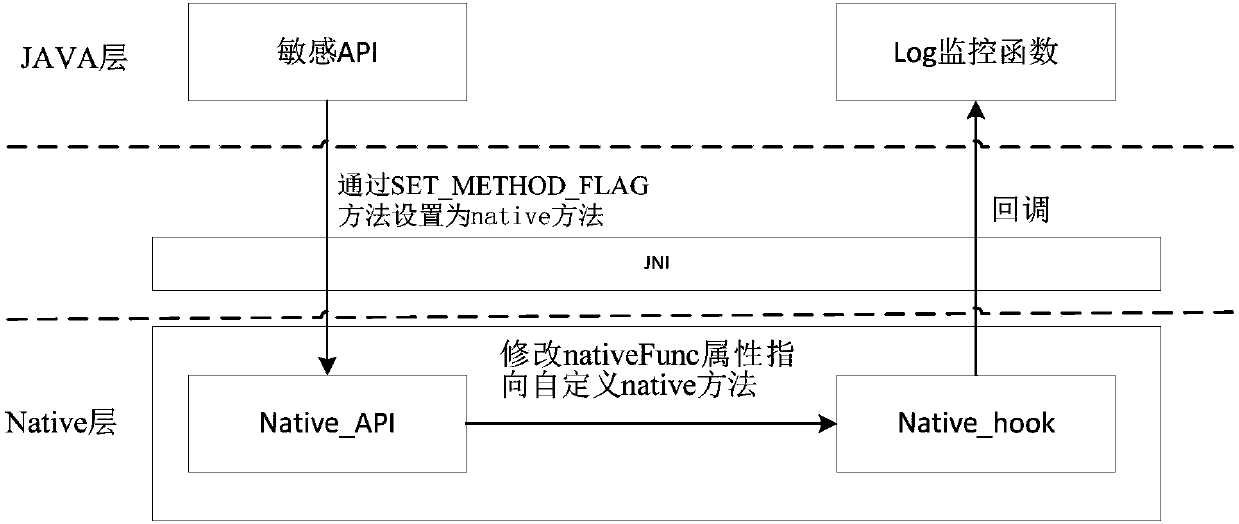
[0093] Step 2: Repackage and inject the nativeHook function and monitoring log function of the sensitive API interface into normal application samples and malicious application samples respectively.
[0094] Step 3: Run the normal application samples and malicious application samples injected with the monitoring log function in batches on the Android emulator, and collect the first API call log sample of the normal application sample and the second API call log sample of the malicious application sample respectively .
[0095] Step 4: Construct the membership function and select the kernel function.
[0096] Step 5: Take the first API call log sample of the normal application sample and the second API call log sample...
Embodiment 3
[0098] This embodiment provides a method for identifying abnormal behavior of an application, such as Figure 5 and 6 As shown, it can be applied to electric power enterprise mobile applications, including the following steps:
[0099] S31: Obtain an API call log when the application is running, where the API call log is a sensitive API call log when the application is actually running on a real device. The application may be a utility mobile application.
[0100] S32: Use the application abnormal behavior identification model established according to the method provided in the above embodiment 1 or 2 to classify the API call log to identify the abnormal behavior.
[0101] The abnormal behavior identification method of the application provided in this embodiment can identify whether the behavior of the application is abnormal in real time according to the API interface call log collected when the application is actually running on the real machine, so that the behavior of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com