Program monitoring method and defending method thereof, as well as relevant device
A monitoring device and program technology, applied in the direction of electrical digital data processing, instruments, platform integrity maintenance, etc., can solve problems such as memory access errors, improper recycling, process crashes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
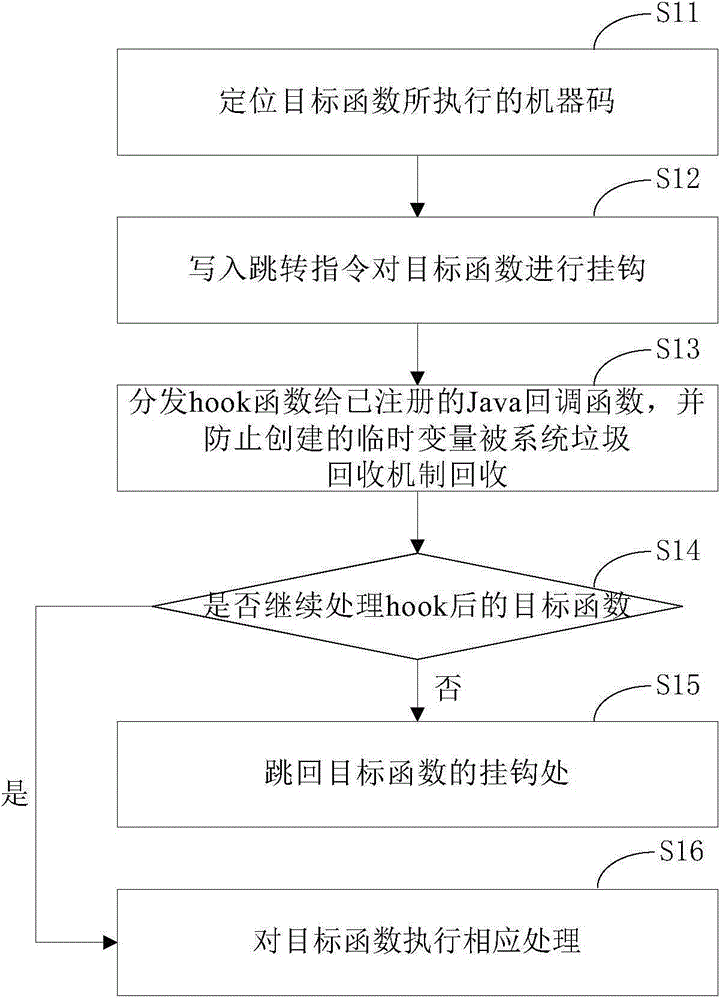
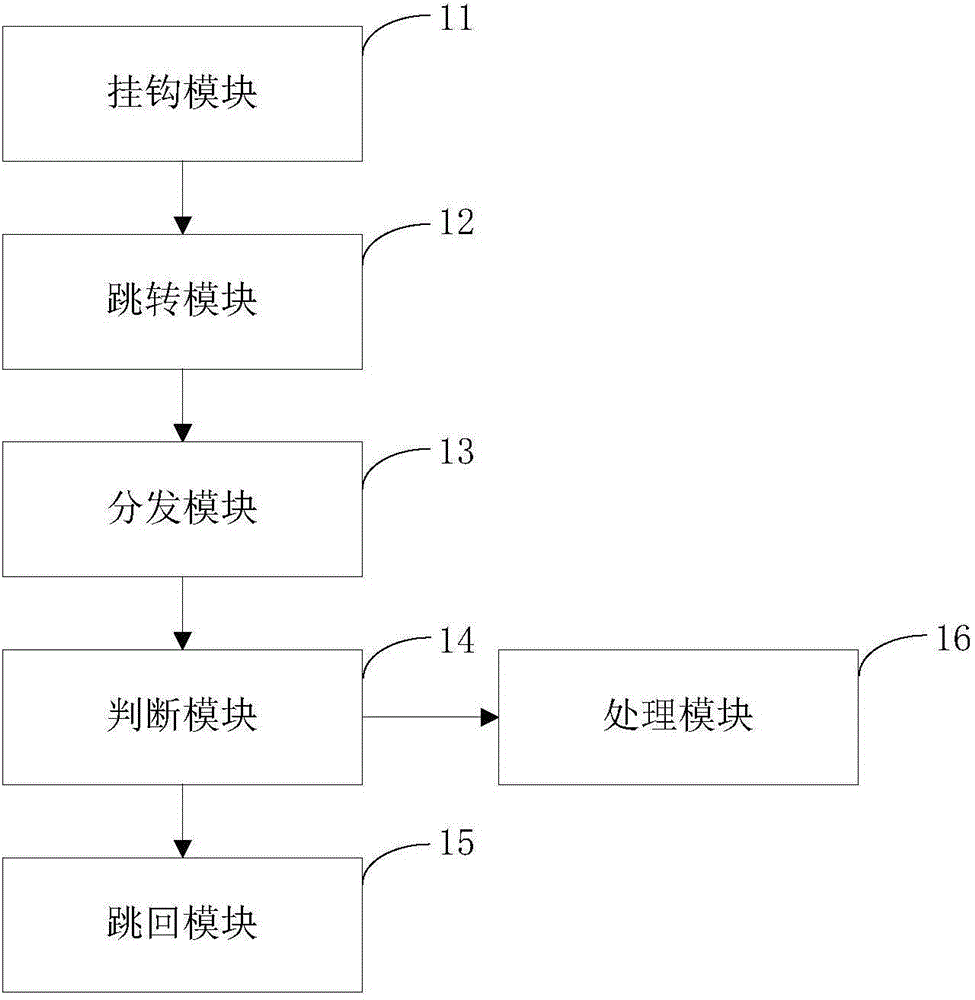
[0097] The jump module 12 is used for writing jump instructions to hook the target function. ARM is a 32-bit instruction set. The hooked target function is compiled into an ARM instruction set, and the target function jump instruction is written to make the target function jump to a custom hook function. The specific implementation method is as follows:
[0098] First save the custom hook function and the address of the hooked target function;
[0099] Generate hook code, specifically 12 bytes, and load the custom hook function address into the PC register;
[0100] Write jump instructions into the first 12 bytes of the target function.
[0101] When calling the hooked target function, execute the jump instruction to jump to the custom hook function.
[0102] After finding the machine code executed by the target function, use an inline hook (inline hook) method to hook it, and write a jump instruction in the first 12 bytes. The jump instruction uses an arm instruction, speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com