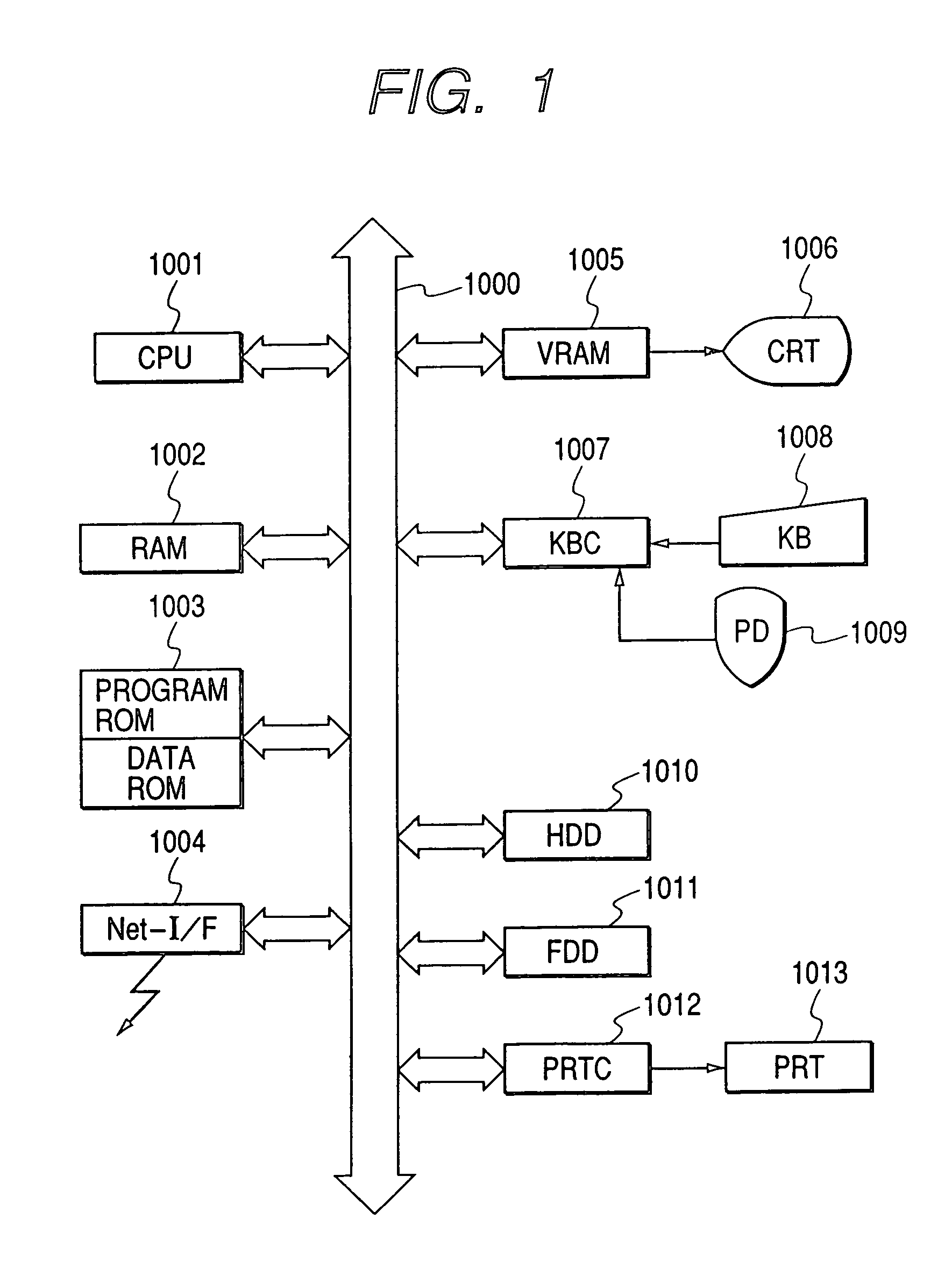
Patents
Literature
230 results about "Process function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
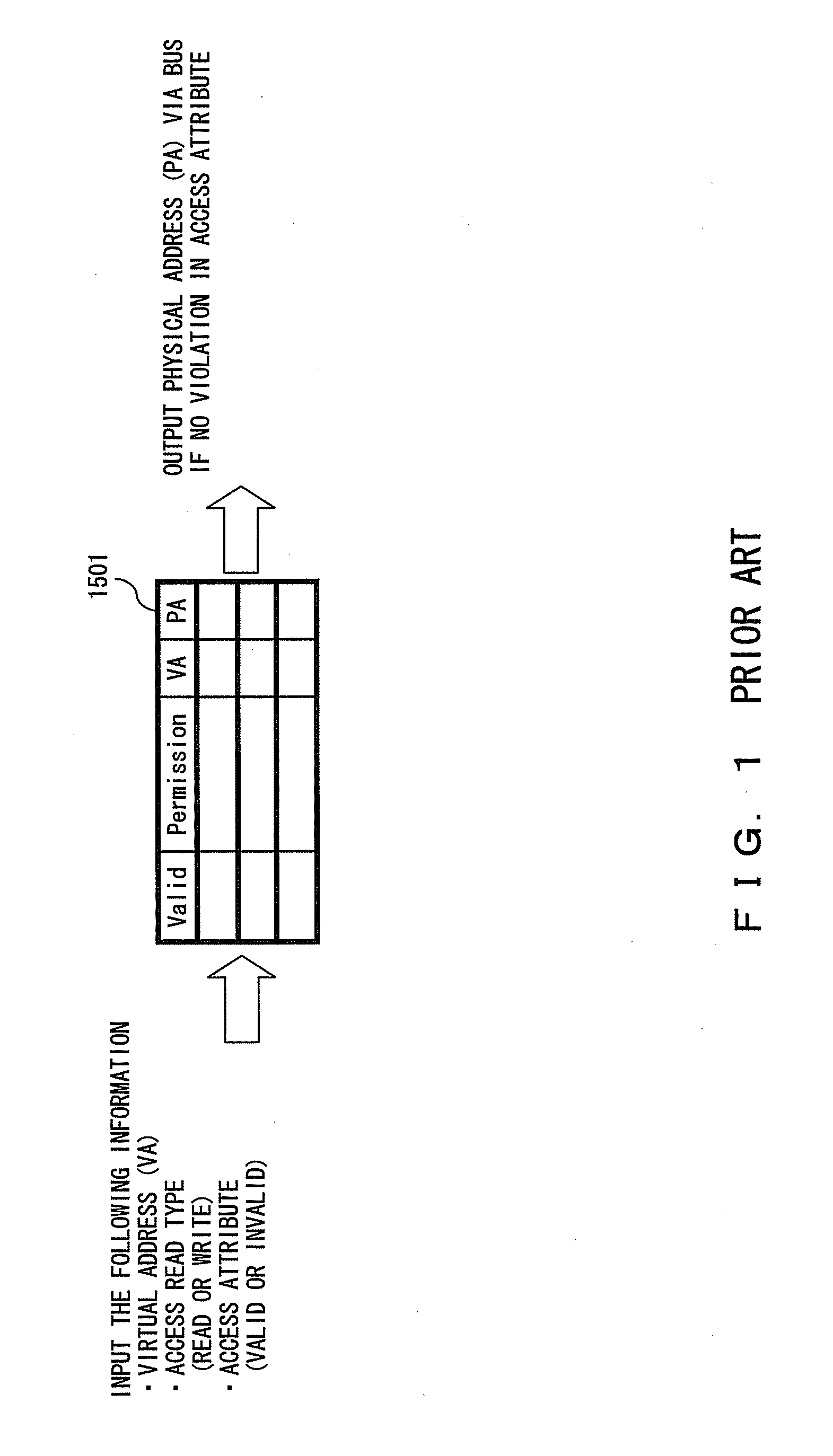
In thermodynamics, a quantity that is well defined so as to describe the path of a process through the equilibrium state space of a thermodynamic system is termed a process function, or, alternatively, a process quantity, or a path function. As an example, mechanical work and heat are process functions because they describe quantitatively the transition between equilibrium states of a thermodynamic system.
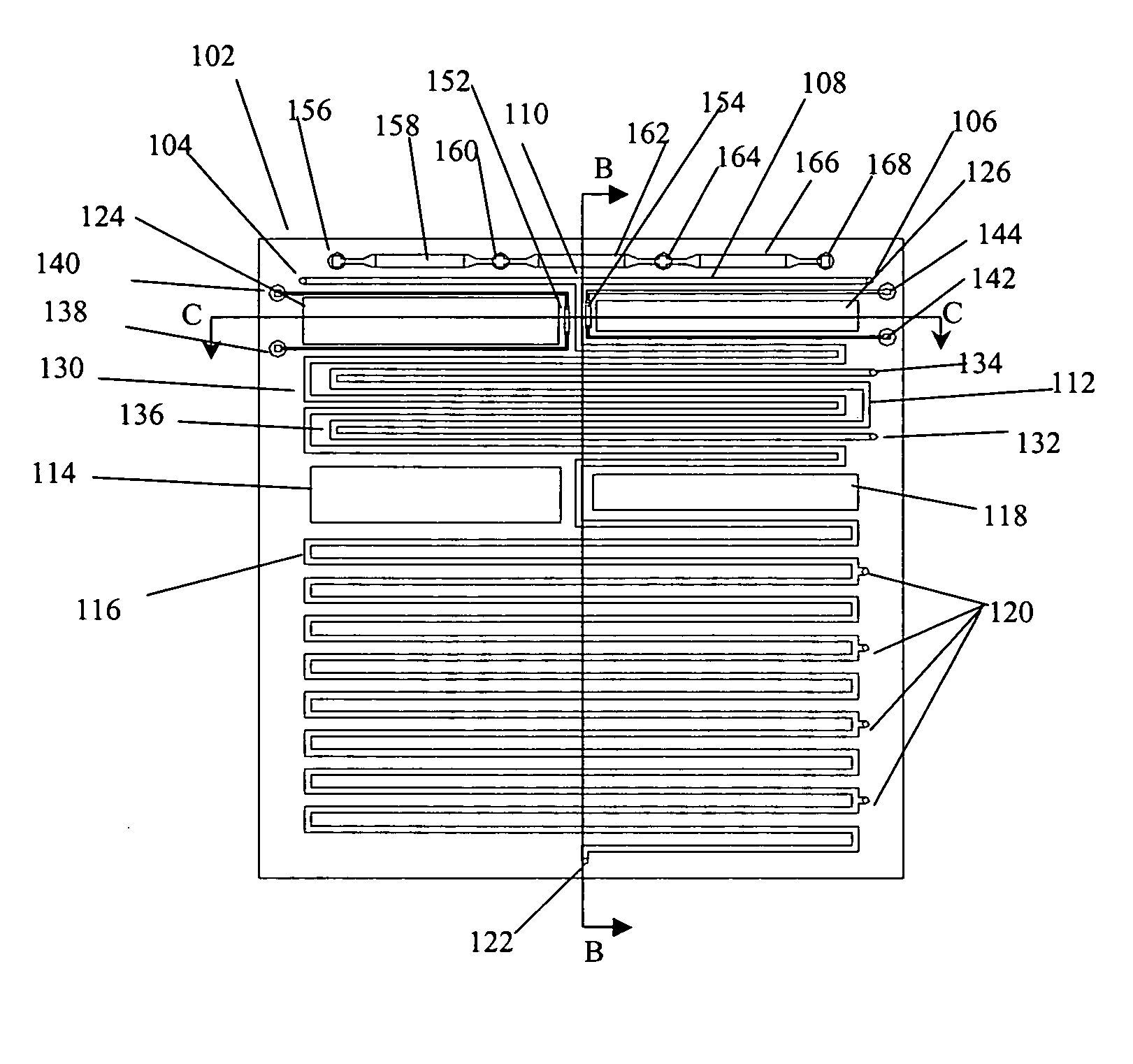
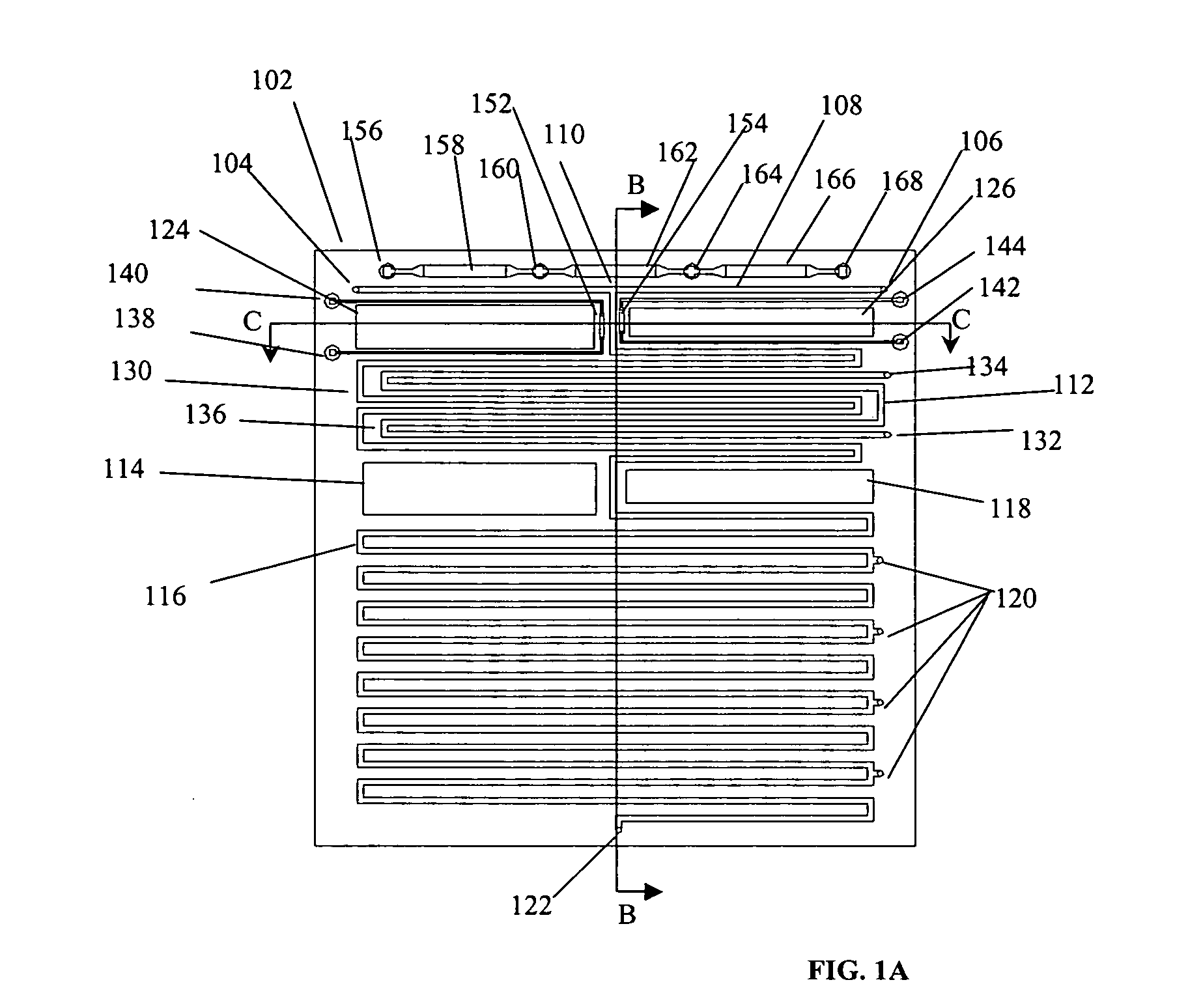
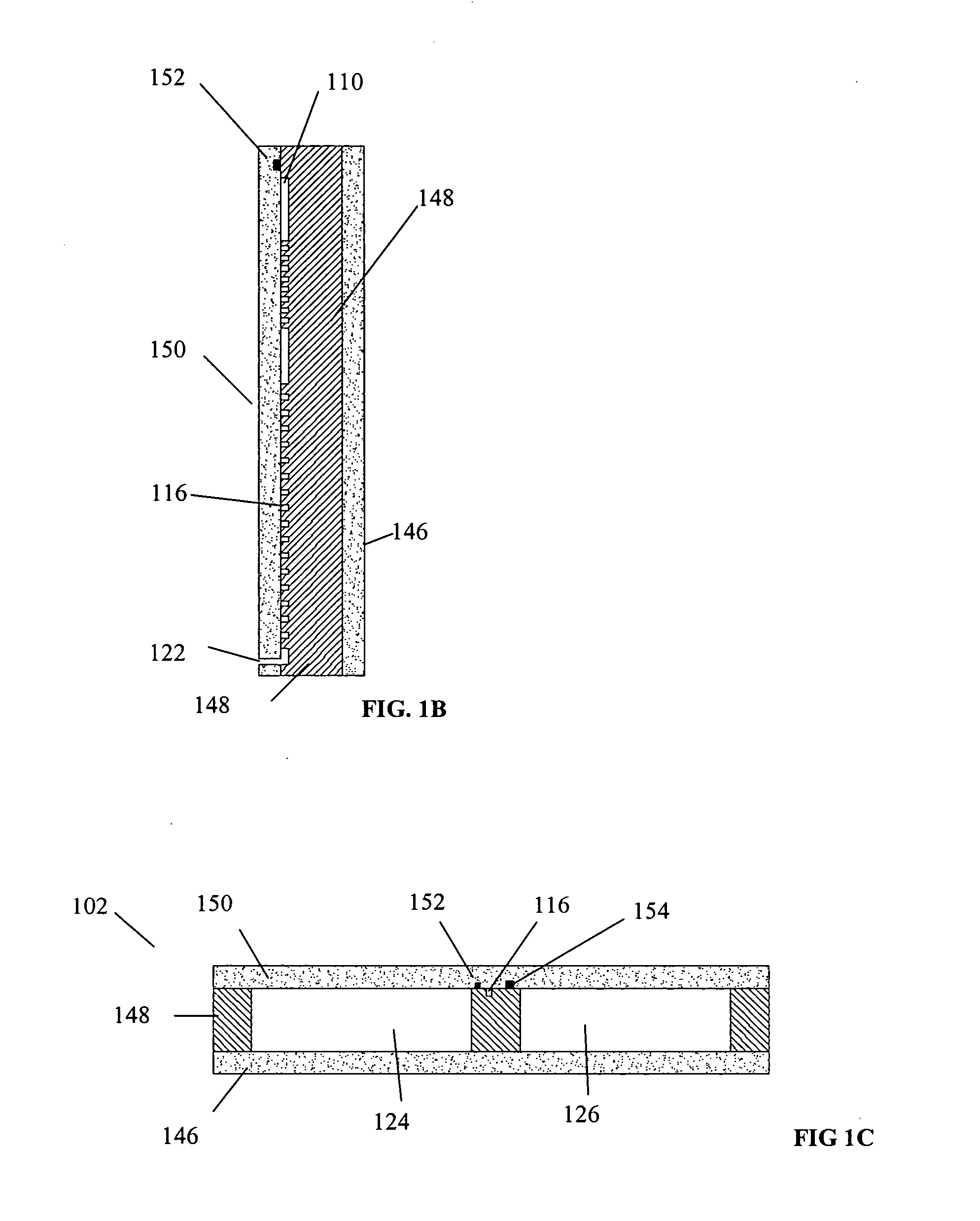
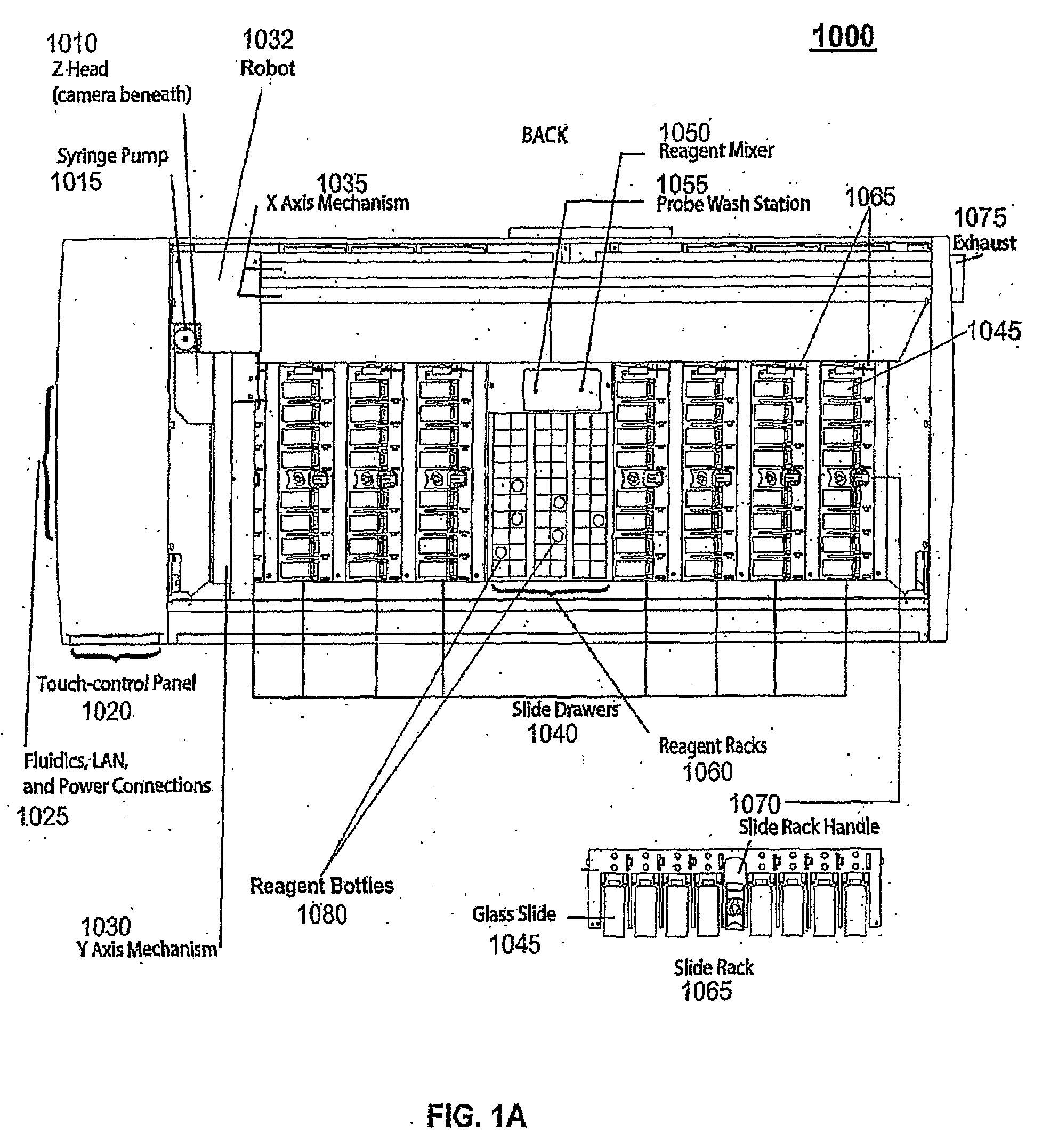
Microfluidic chemical reactor for the manufacture of chemically-produced nanoparticles
InactiveUS20050129580A1Maintain propertiesMaterial nanotechnologyPolycrystalline material growthProcess functionNanoparticle
The present invention discloses microfluidic modules for making nanocrystalline materials in a continuous flow process. The microfluidic modules include one or more flow path with mixing structures and one or more controlled heat exchangers to process the nanocrystalline materials and reagents in the flow path. The microfluidic modules can be interconnected to form microfluidic reactors that incorporate one or more process functions such as nucleation, growth, and purification.
Owner:LAKE SHORE CRYOTRONICS INC
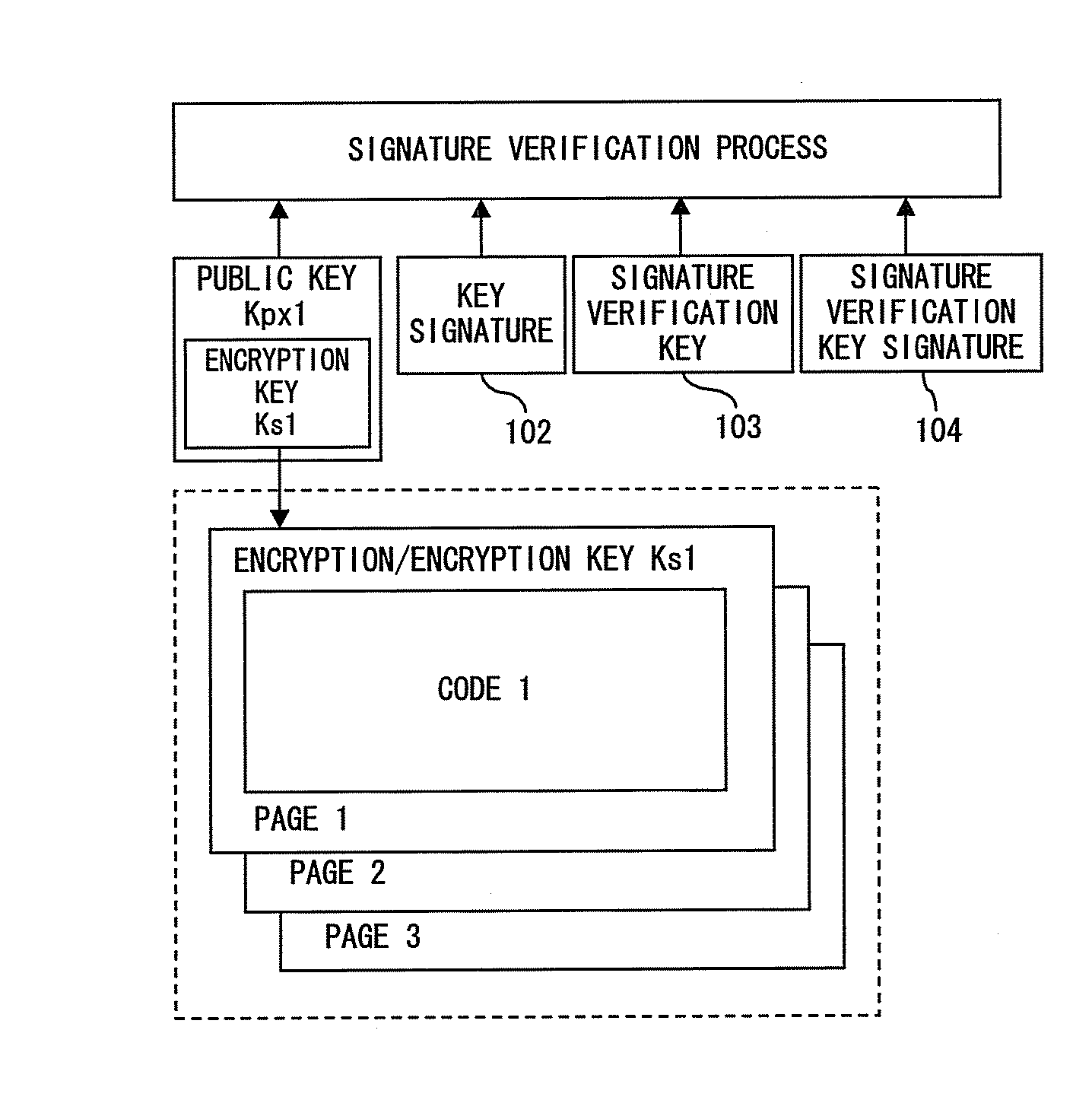
Secure processor
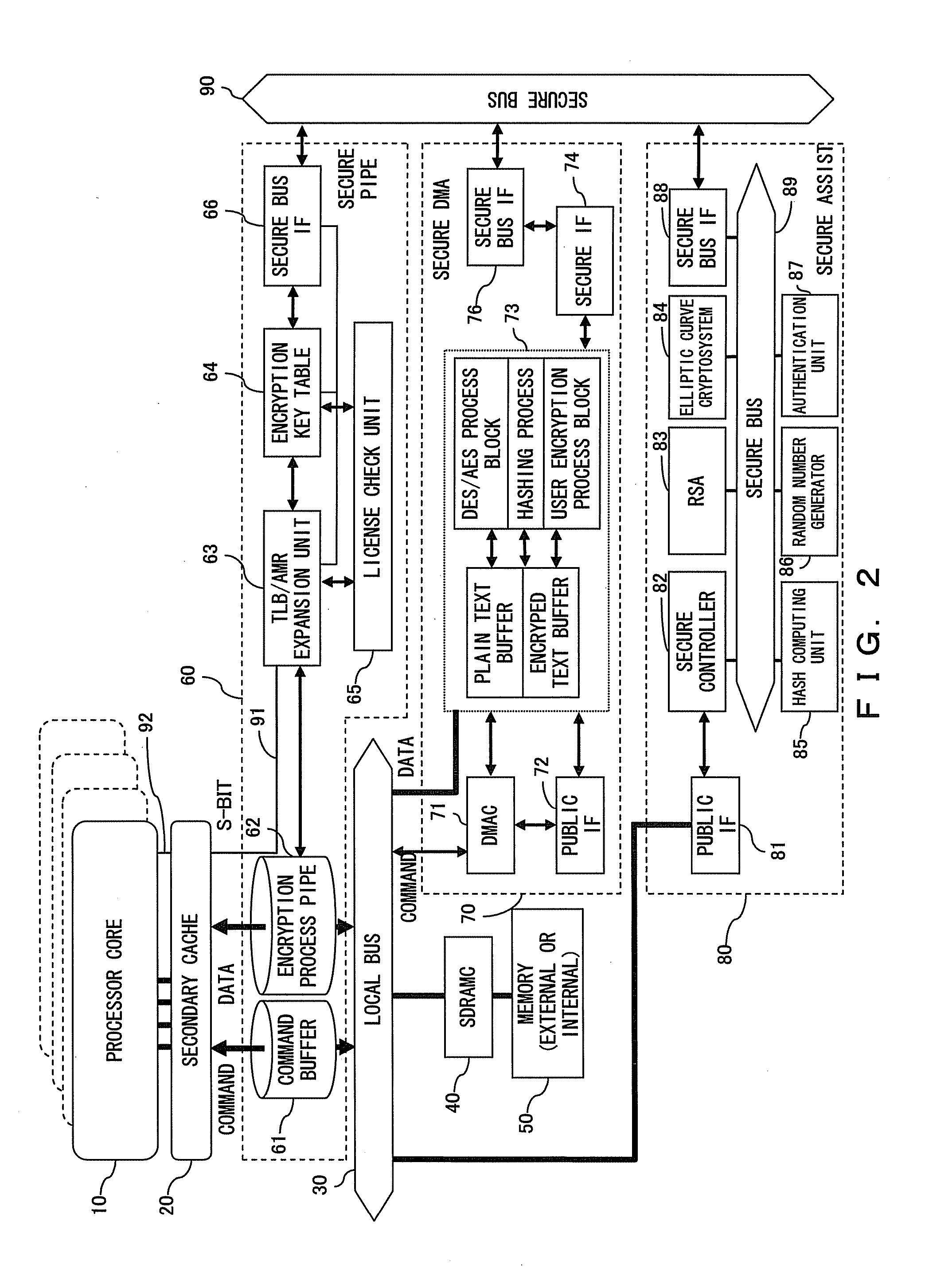
InactiveUS20070198851A1Improve securityImprove completenessUser identity/authority verificationDigital computer detailsProcess functionAuthentication
A secure hardware comprises a secure pipe, a secure DMA, a secure assist and a secure bus, which connects between those blocks. The secure pipe stores a common encryption key in an encryption key table so as not to be able to access from software. The secure DMA comprises a data common key system process function and a hashing process function. The secure assist comprises a common key system process function and an authentication process function, receives an issued command from a program executed by the processor core via a public IF, and performs setting / control of the secure pipe and the secure DMA via the secure bus.
Owner:SOCIONEXT INC
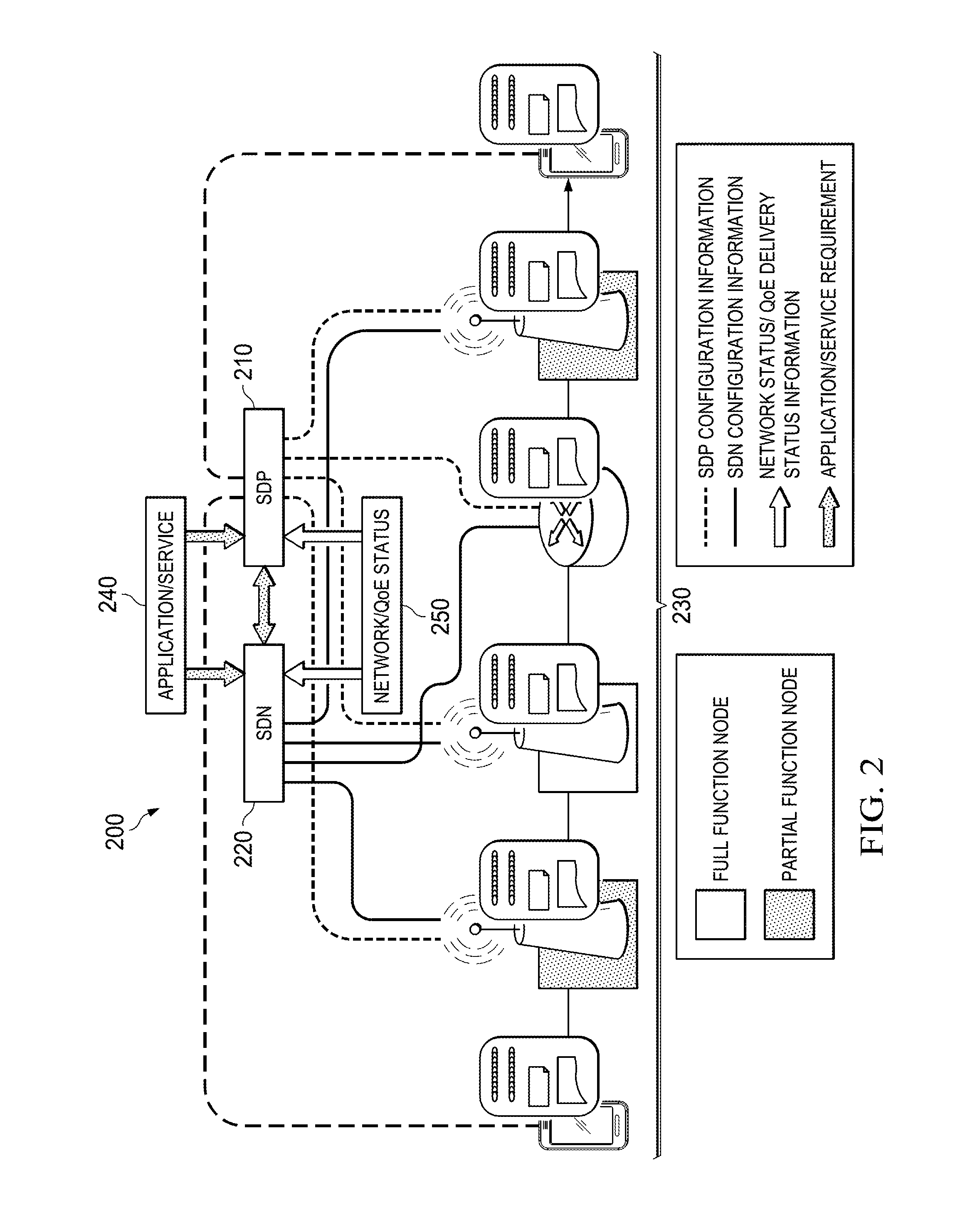
System and Method for Providing a Software Defined Protocol Stack
ActiveUS20140310388A1Digital computer detailsData switching networksQuality of serviceProcess function
Embodiments are provided for a framework for networks with software defined protocols (SDP) network nodes. The embodiments include a SDM controller component for managing and controlling a data plane protocol for SDP network nodes. The SDP controller also interacts with a software defined networking (SDN) controller for determining one or more paths in a network including the SDP network nodes. The SDP controller is configured to determining a break-down of data plane process functionality into a plurality of basic process function blocks for a service, traffic flow, or virtual network in accordance with network component capabilities or quality of service / experience requirement. A workflow and status information are also determined for one or more network components along a path allocated, by the SDN controller. The workflow and status information are indicated to the one or more components, which are configured to implement the workflow using the basic process function blocks.
Owner:HUAWEI TECH CO LTD
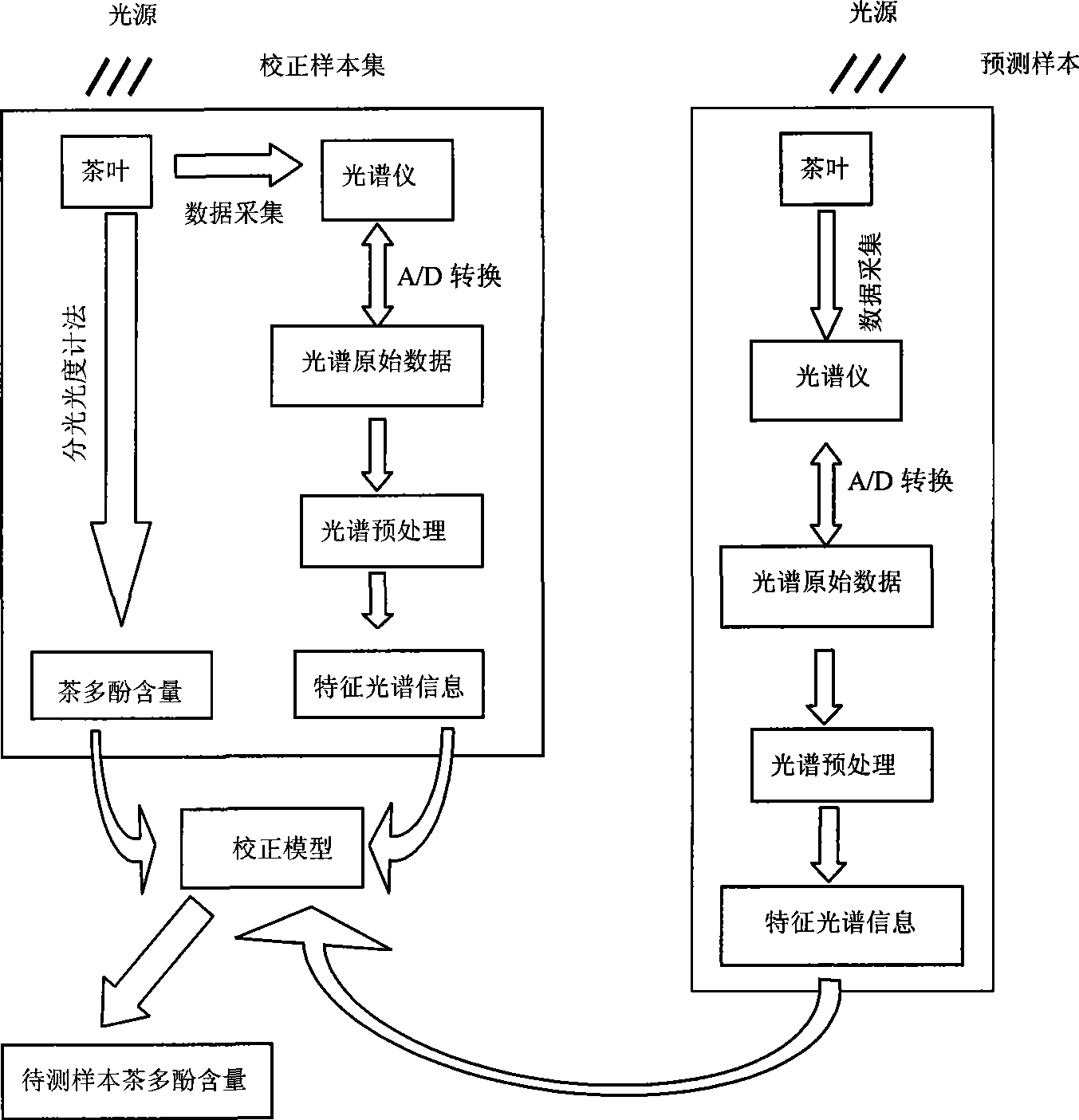
Method for non-destructive measurement for tea polyphenol content of tea based on near infrared spectrum technology
InactiveCN101059426AFast analysisNo pollutionColor/spectral properties measurementsSpecial data processing applicationsProcess functionPhenolic content in tea
The invention discloses a method for non-damage measuring the tea polyphenol content in tea, based on near-infrared spectrum technique, which comprises that first building a correct model, collecting tea sample as correct sample group, scanning the correct sample group to obtain visible light spectrum and near-infrared light spectrum (325-2500nm), processing spectrum pretreatment on the spectrum data, then using international standard method to measure the tea polyphenol content of correct sample, using multi-element correct regression algorism to build the quantitative relationship between the near-infrared spectrum and the tea polyphenol content of the correct sample, to build the correct model. The invention only needs to scan the near-infrared spectrum of object tea, and input pretreated spectrum data into the correct model which can test the tea polyphenol content. The whole process is controlled by a computer, to realize data pickup, store, display and process functions.
Owner:ZHEJIANG UNIV
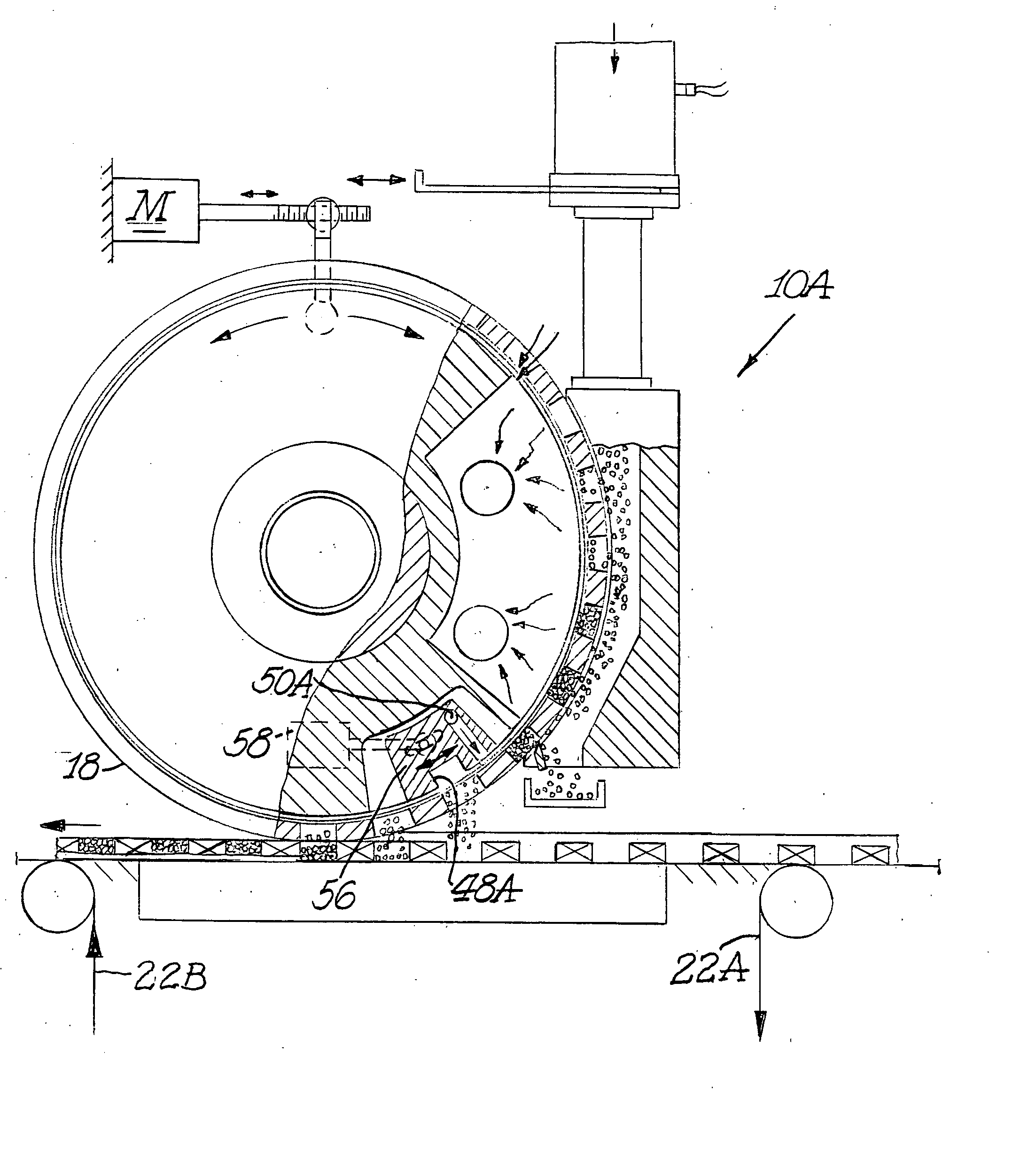
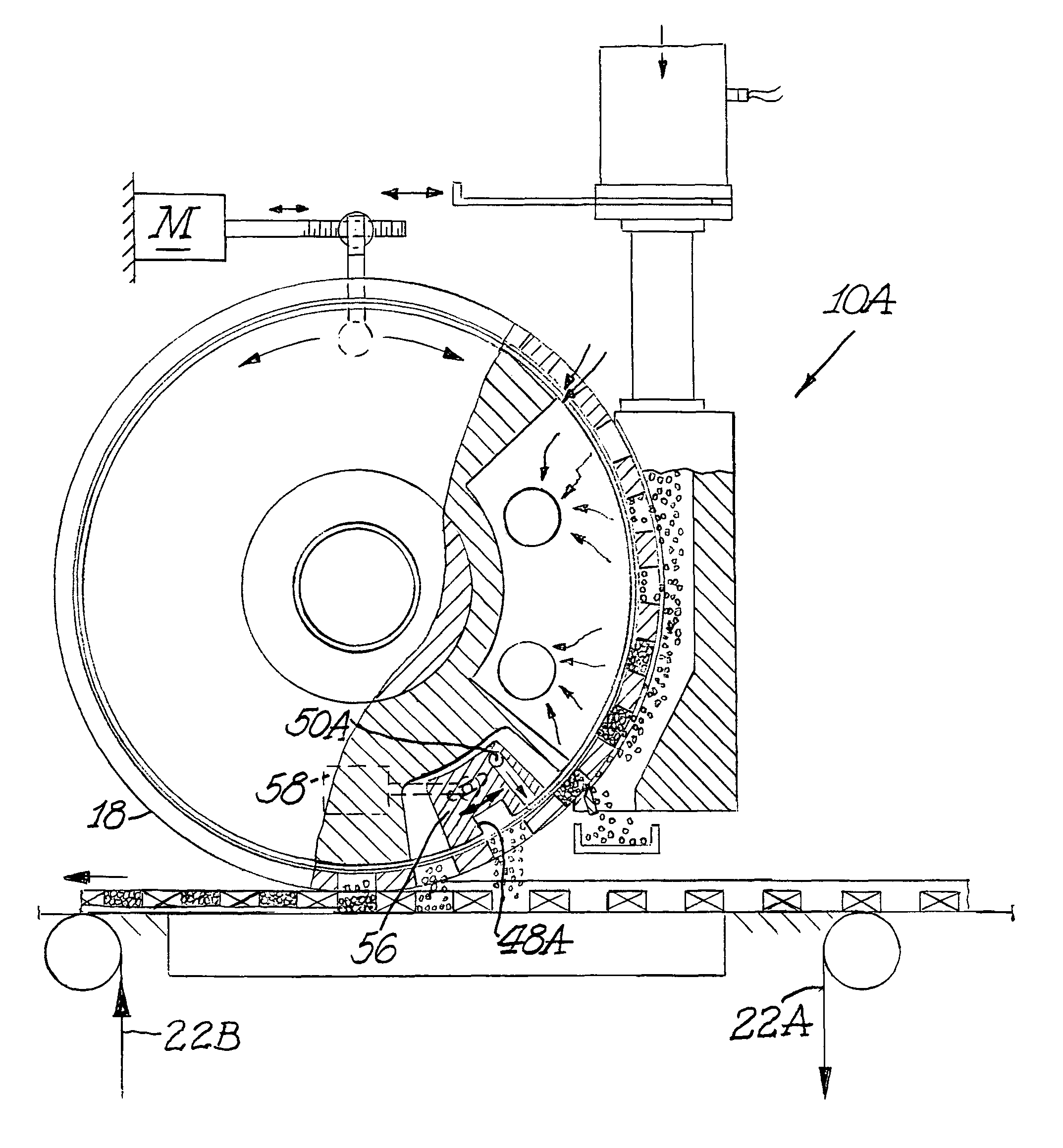
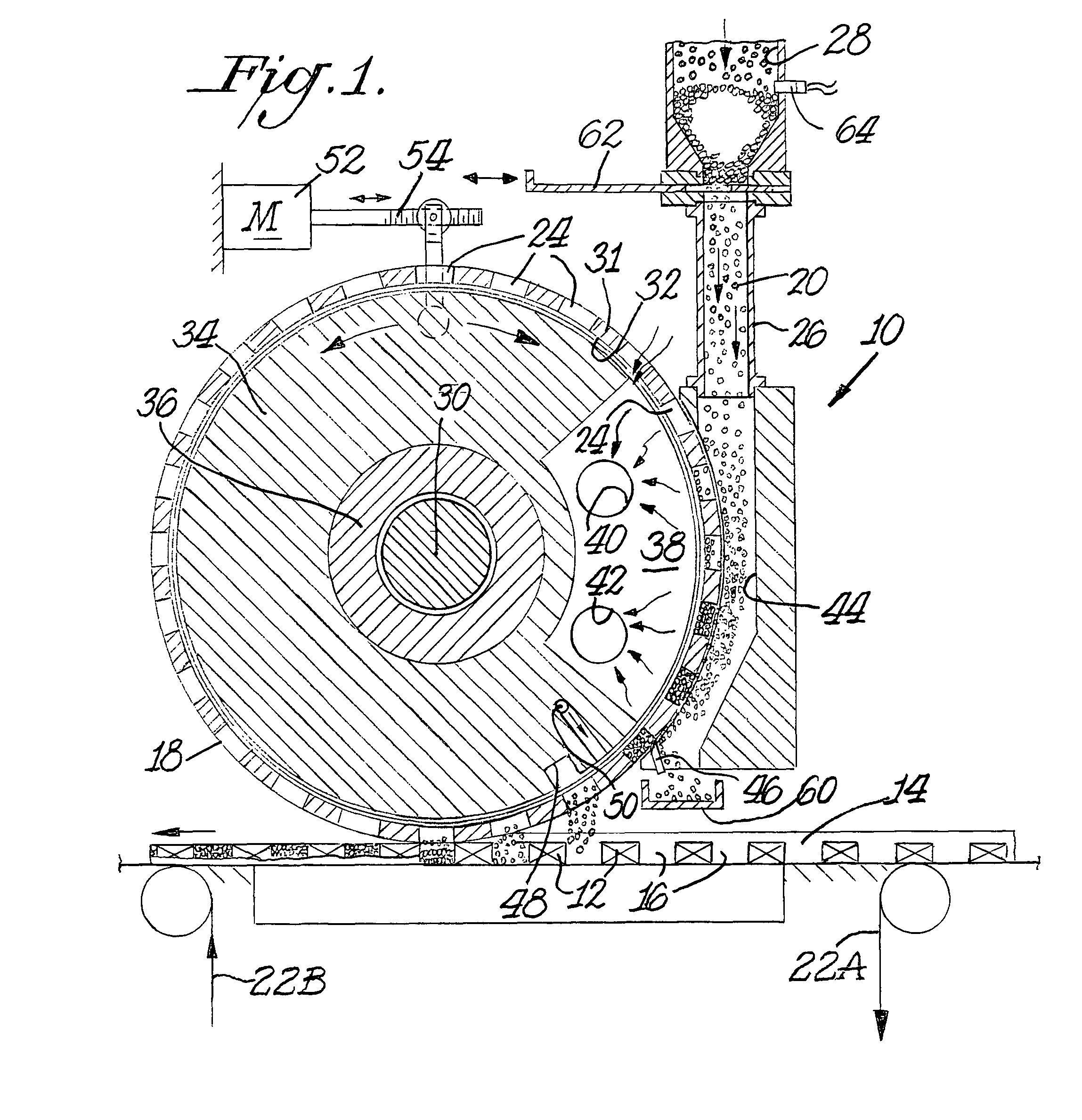
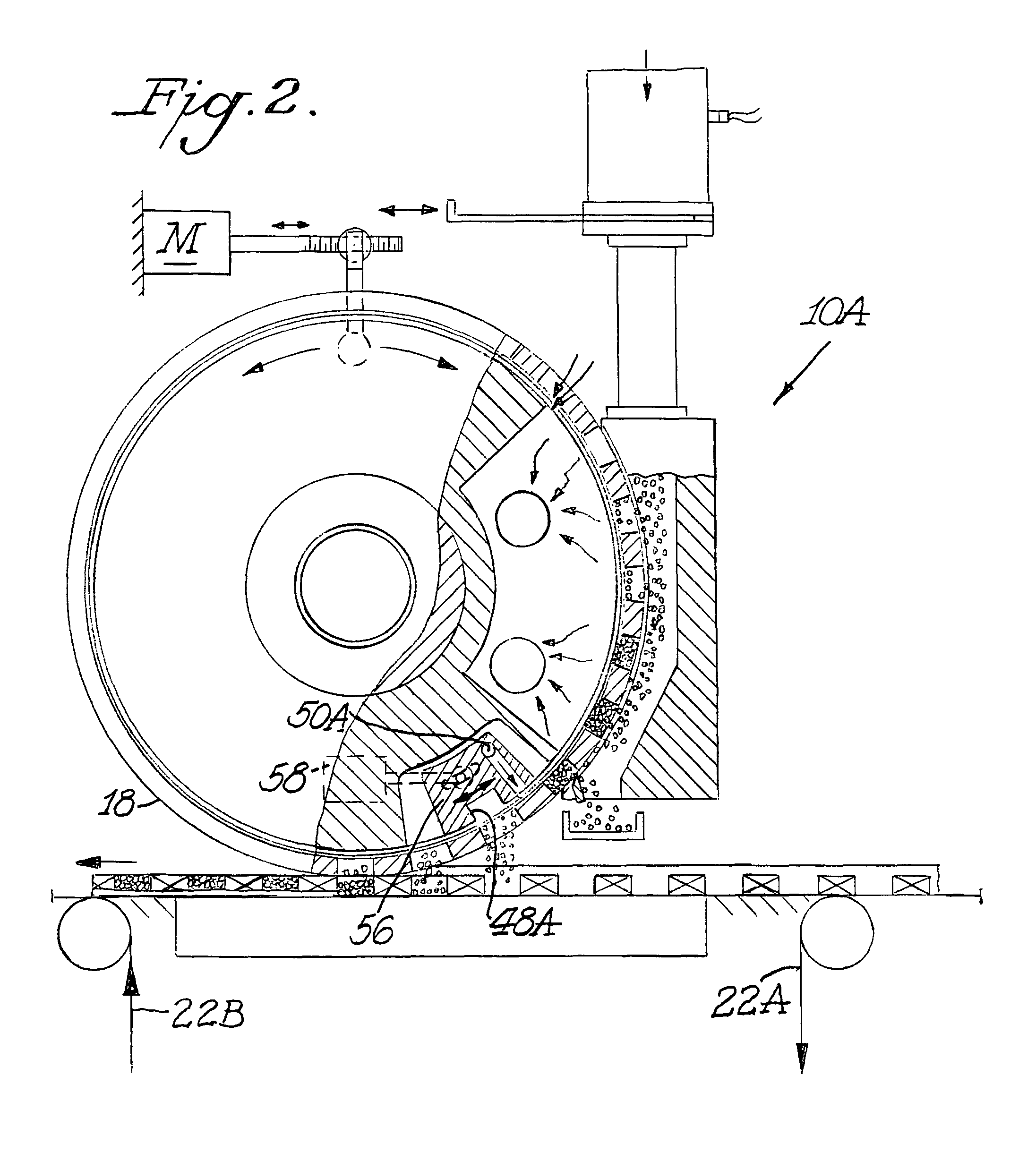
Applicator wheel for filling cavities with metered amounts of particulate material
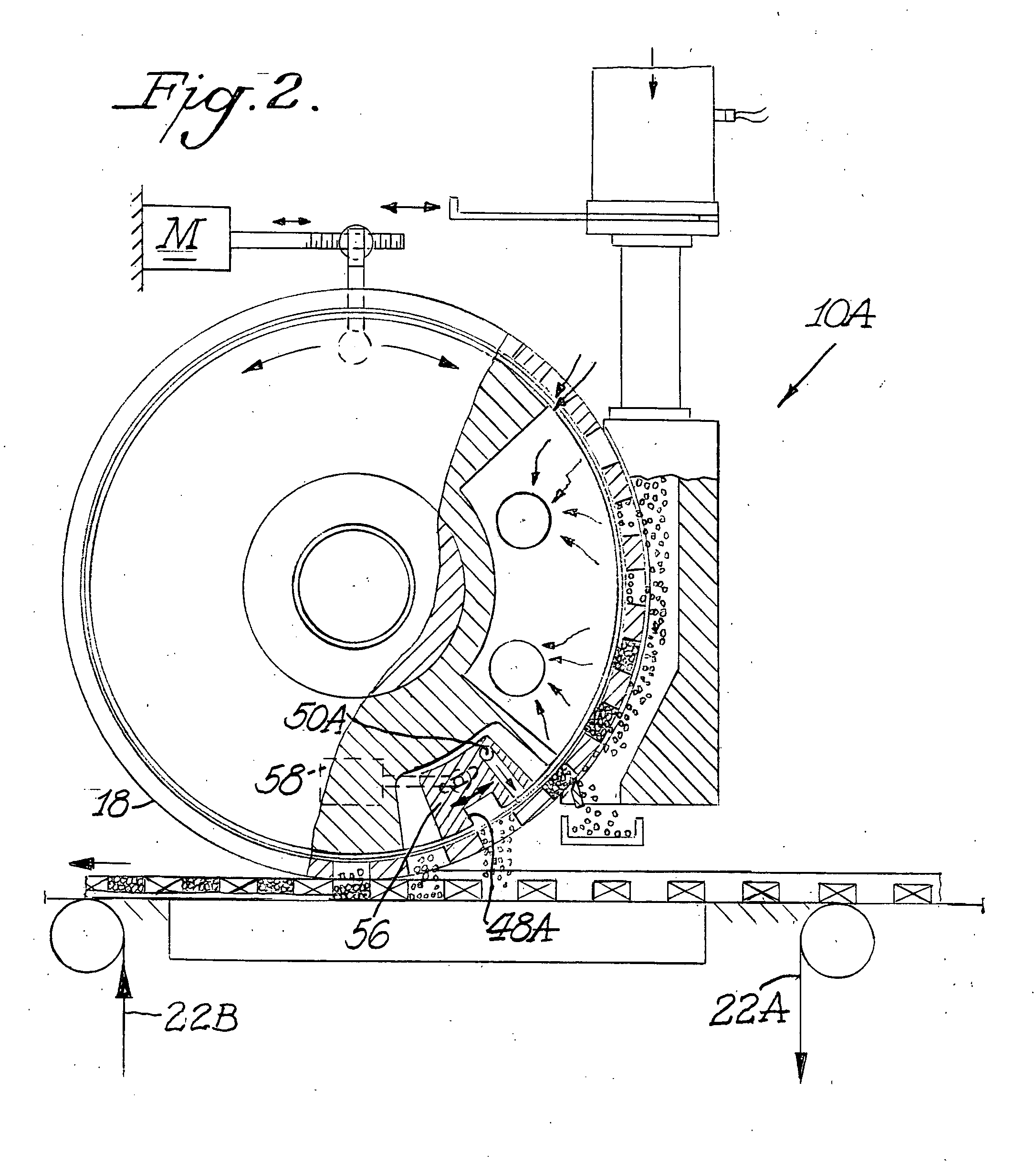
ActiveUS20070284012A1Efficient mannerEfficient and timelyLiquid fillingTobacco smoke filtersProcess functionEngineering
A machine and process function to fill cavities with metered amounts of particulate material. An applicator wheel includes a series of equally spaced apart peripheral pockets each having a perforated bottom wall, and a vacuum manifold inside the wheel includes a vacuum chamber for supplying vacuum to the perforated bottom walls of the pockets as the wheel rotates. Particulate material from a filling chamber of such material outside the wheel is withdrawn into the pockets by the vacuum chamber. A downstream vacuum relief on the vacuum manifold functions to discharge particulate material from the pockets into the cavities at a predetermined discharge location on the wheel. Adjustment structure is connected to rotatably adjust the position of the vacuum manifold within the applicator wheel to thereby advance or retard the discharge location depending upon the speed of the machine.
Owner:PHILIP MORRIS USA INC
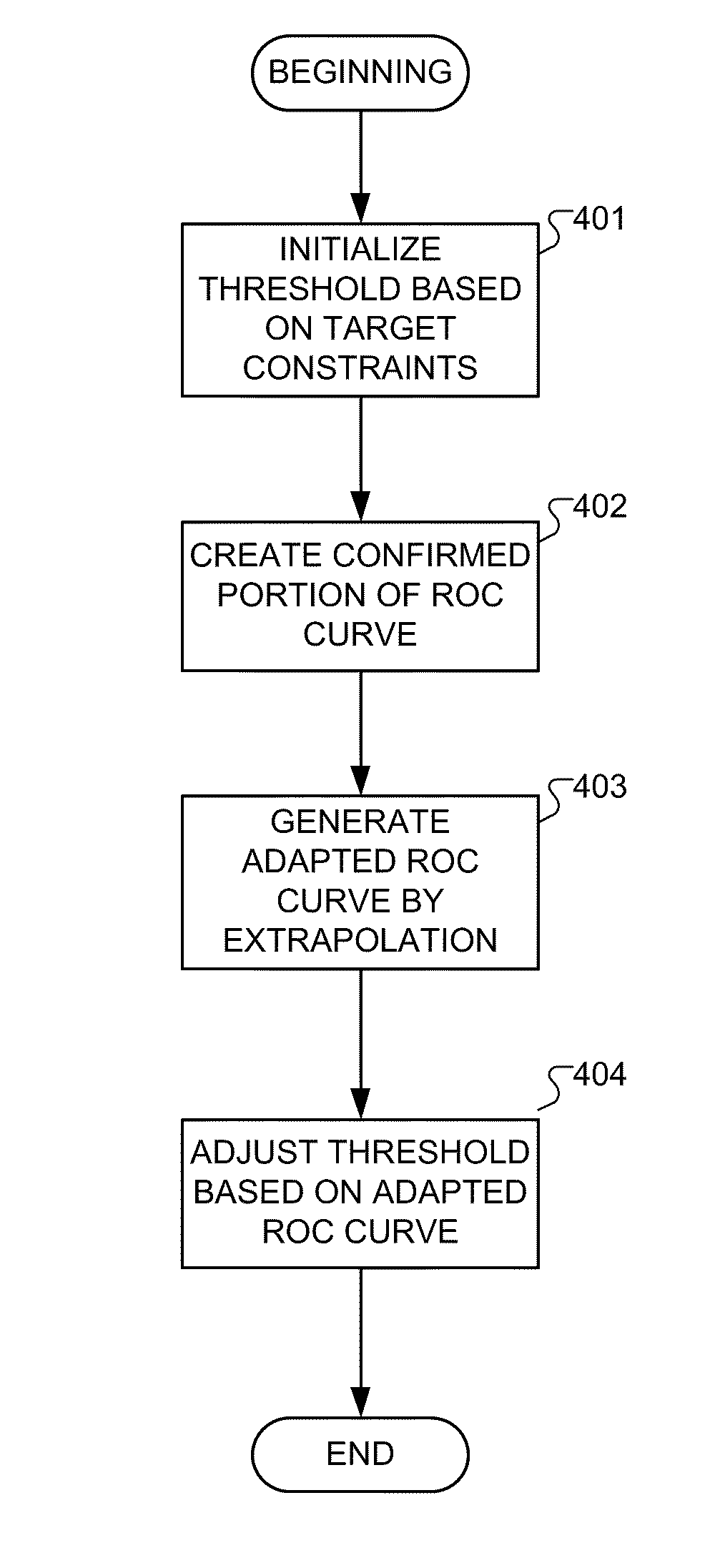
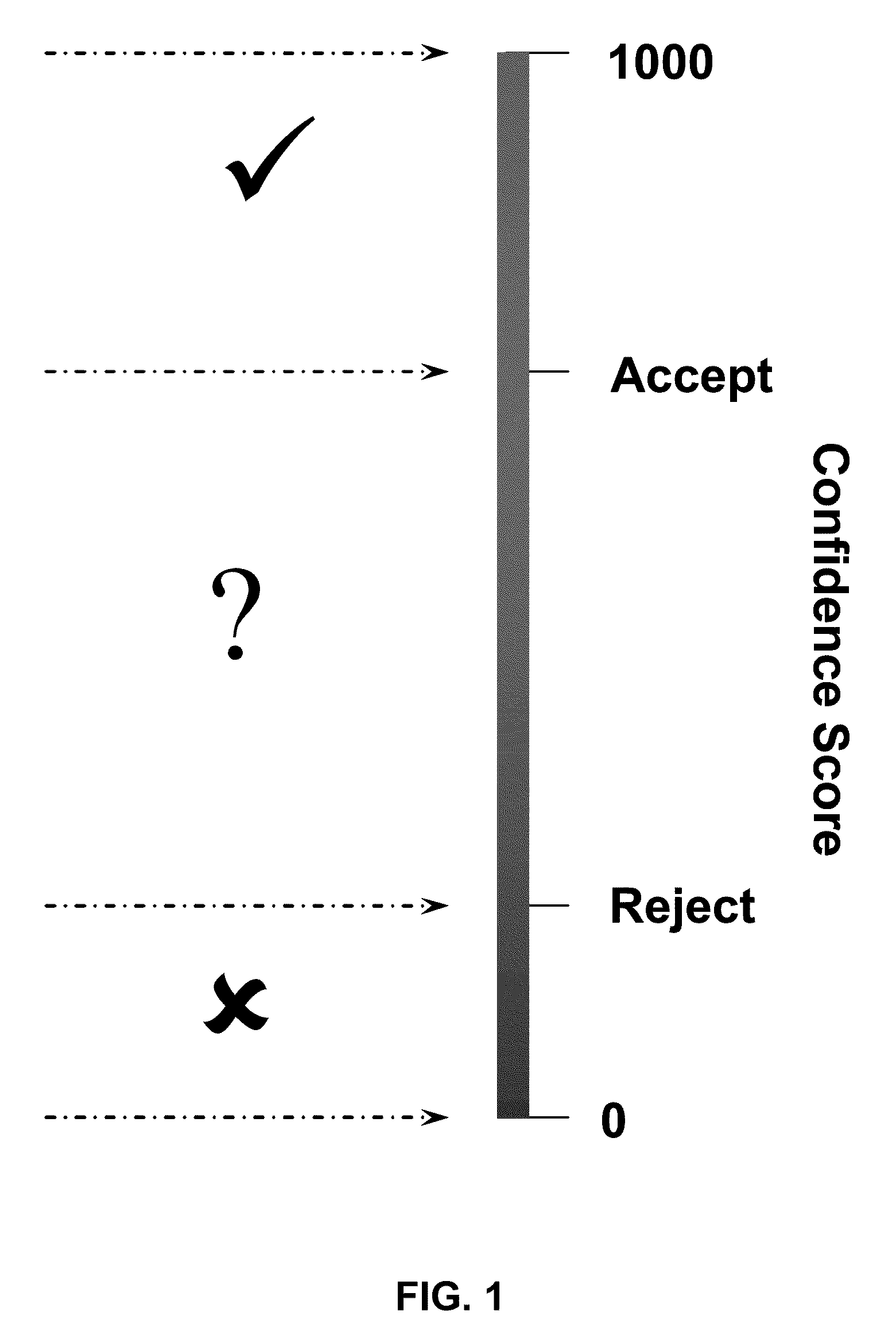
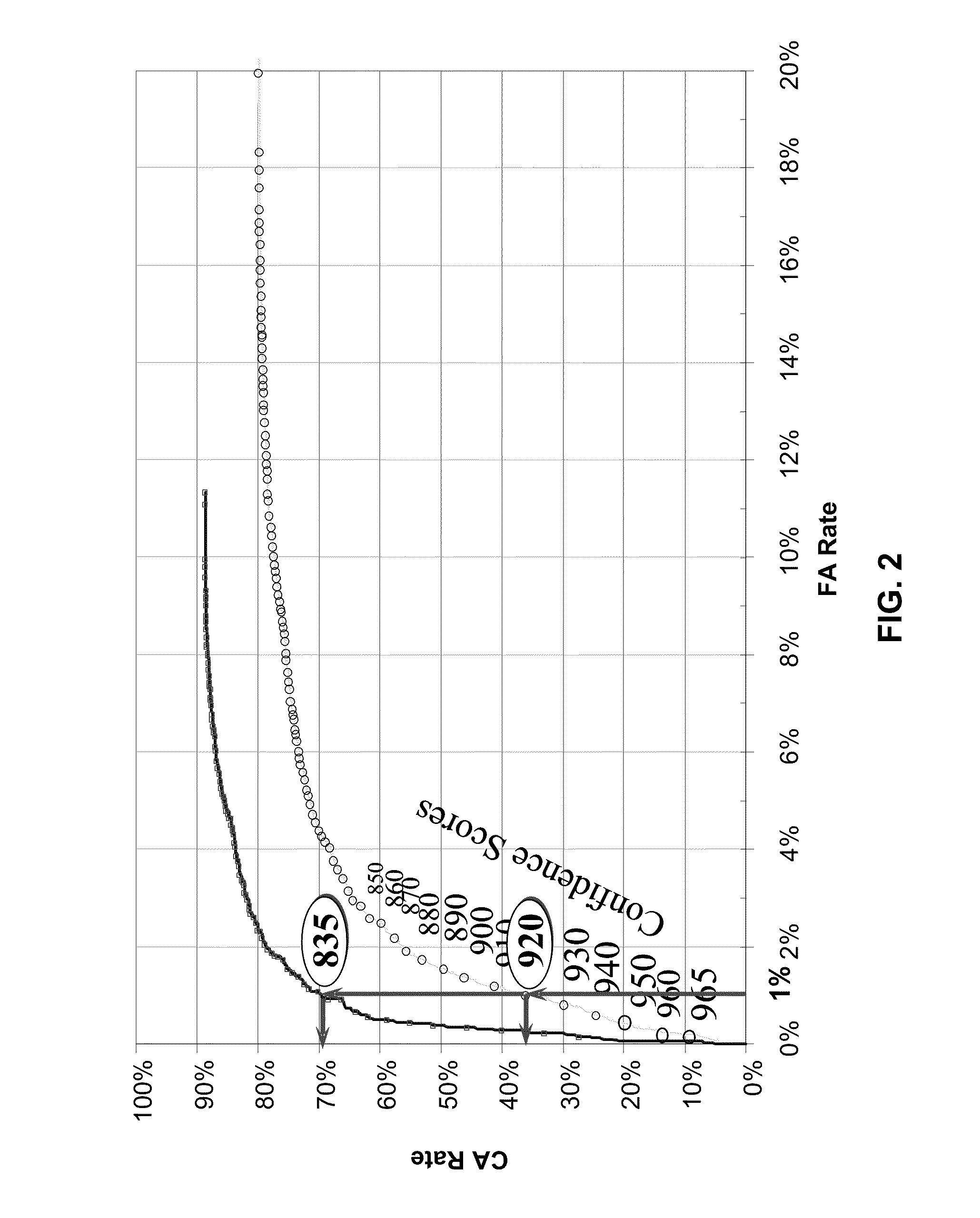
Adaptive Confidence Thresholds for Speech Recognition
Adjusting confidence score thresholds is described for a speech recognition engine. The speech recognition engine is implemented in multiple computer processes functioning in a computer processor, and is characterized by an associated receiver operating characteristic (ROC) curve. A results confirmation process interprets user confirmation of speech recognition results within a given confidence score threshold to create a confirmed portion of the ROC curve for the speech recognition engine. A curve extension process extends the confirmed portion of the ROC curve by extrapolation of unconfirmed speech recognition results beyond the confidence score threshold to generate an extended ROC curve. A threshold adjustment process adjusts the confidence score threshold based on the extended ROC curve to meet target operating constraints for operating the speech recognition engine to perform automatic speech recognition of user speech inputs.
Owner:NUANCE COMM INC
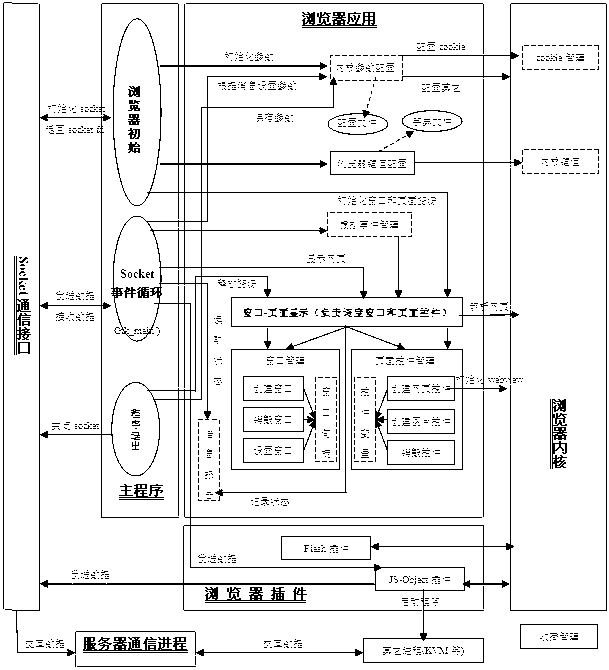
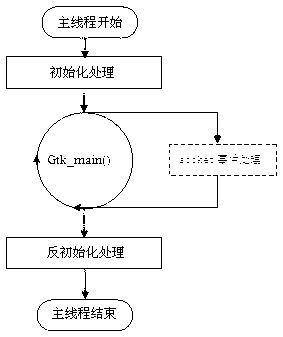
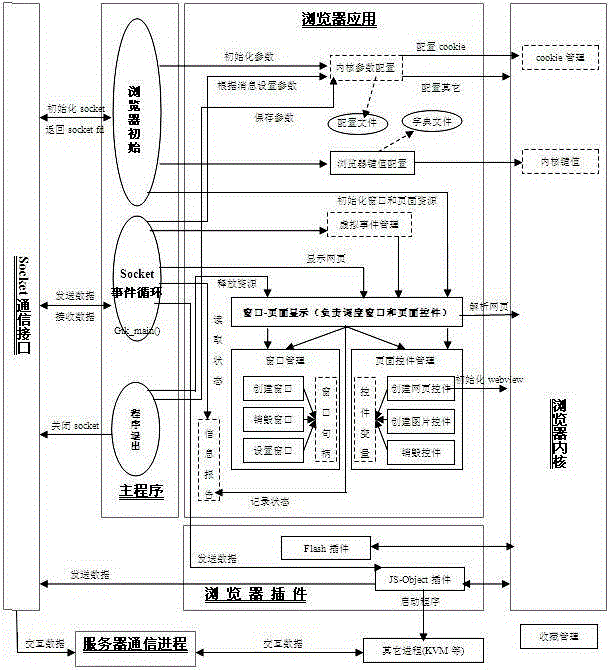
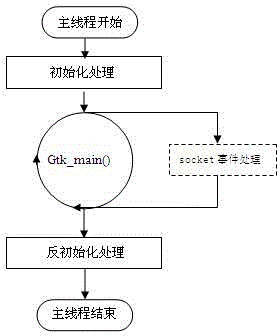
Embedded browser and implement method thereof
InactiveCN103177095AEasy to useEasy to upgradeSpecific program execution arrangementsSpecial data processing applicationsCommunication interfaceProcess function
The invention discloses an embedded browser and an implement method of the embedded browser. The embedded browser comprises a main program module, a communication interface module, a browser plug-in module, a browser application module and a browser kernel module. The main program module is composed of browser initialization, socket event cycling and a program quit submodule. The communication interface module carries out data interaction through a communication server process and other processes. The browser plug-in module is composed of a java script object (JS-Object) plug-in and a Flash plug-in submodule. The browser application module comprises kernel parameter configuration, browser key value configuration, virtual event management and a window and page control management submodule. The browser kernel module is composed of cookie management and a kernel key value submodule. The embedded browser achieves that a browser socket event process function monitors information periodically, has the functions of requesting information reports, displaying a progress window and cookie management according to a page loading progress, supports java script (JS) object extension and a soft keyboard, and is convenient to use, low in development cost, convenient to upgrade and maintain and good in user perception.
Owner:CHENGDU SANLING KAITIAN COMM IND
Miniature iris recognition module adopting active visual feedback
ActiveCN101369311ALow costAvoid security breachesCharacter and pattern recognitionProcess functionDisk controller
Provided is a miniaturization iris identification module adopting active vision feedback, which independently completes collection of eye iris images and process function, and can be used as a miniaturization module with independent iris identification function embedded into and connected to other devices, e.g. a safe box (a safe case), a lock, a finance safety-deposit box, a fire-arm storage box, a bag storage cabinet, a ATM, a POS, a work attendance machine, a gate inhibition controller, a channel controller, a lift controller, a radio set, a copier, a electrograph, a telephone, a printer, a mouse, a computer, a household electrical appliance, a cable TV remoter, a toy, a digital camera, a moving device, a car, a motor, a motor-assisted bicycle and the like, thereby upgrading to a product with iris identification and authentication function.
Owner:BEIJING IRISKING
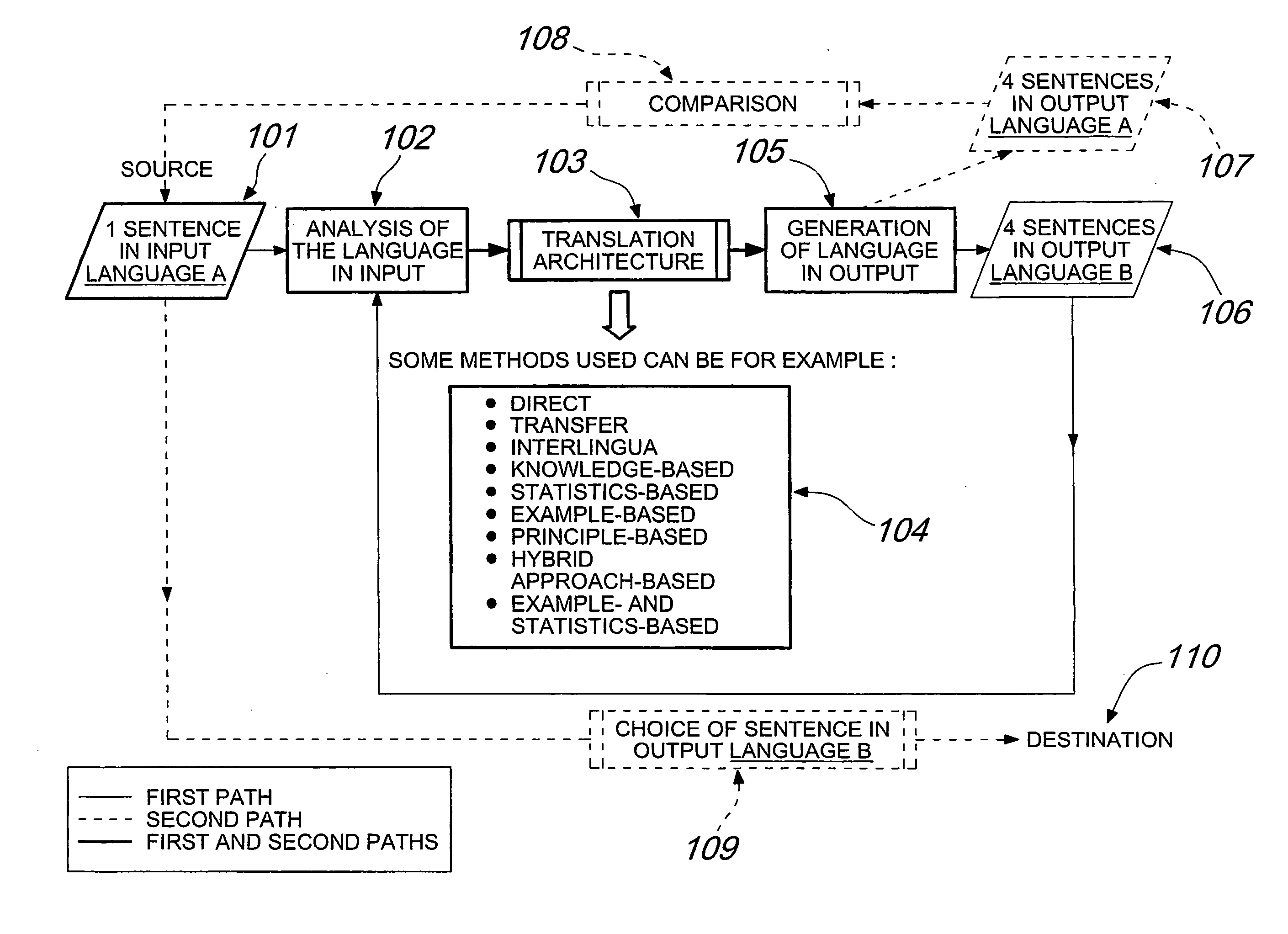
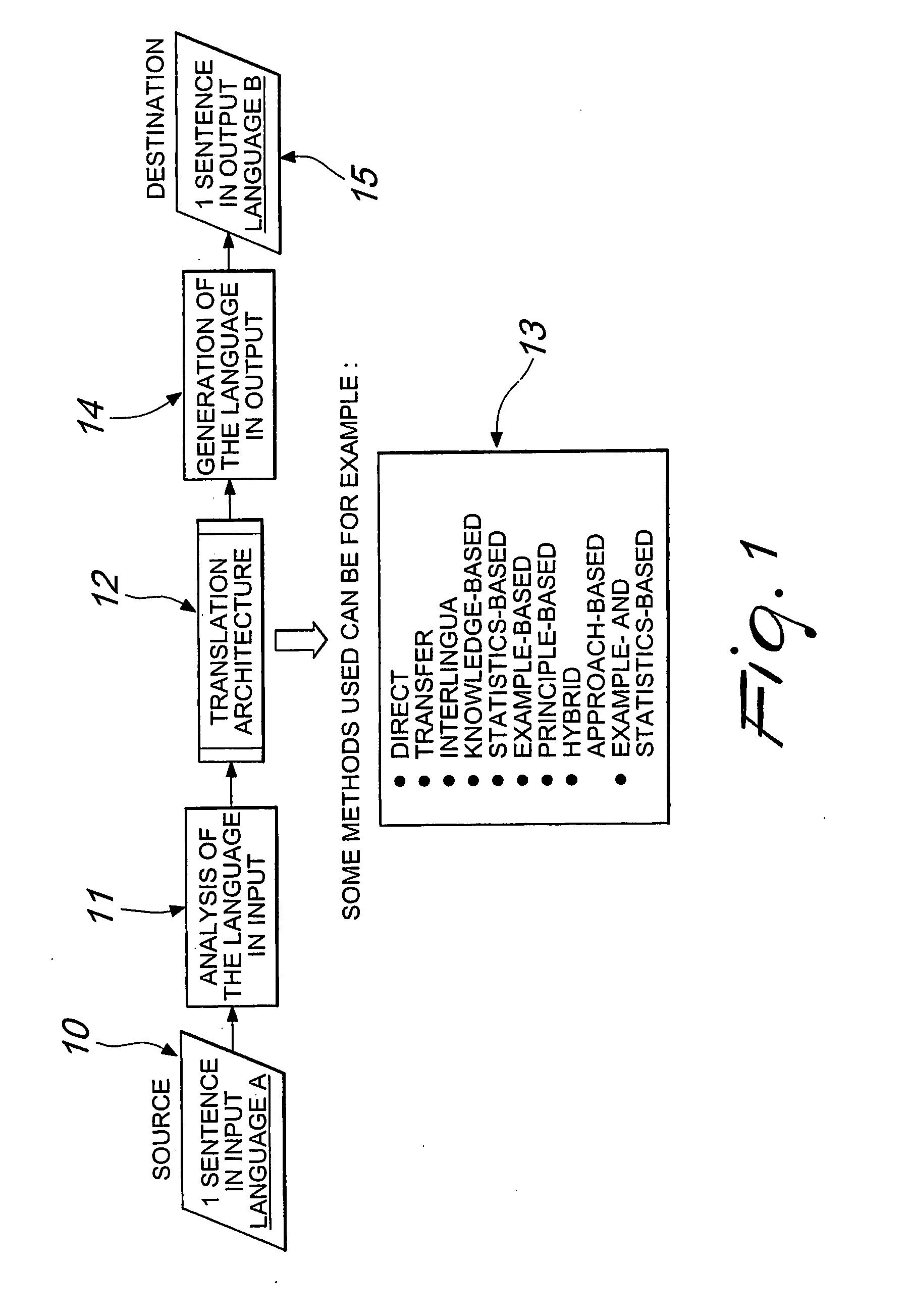
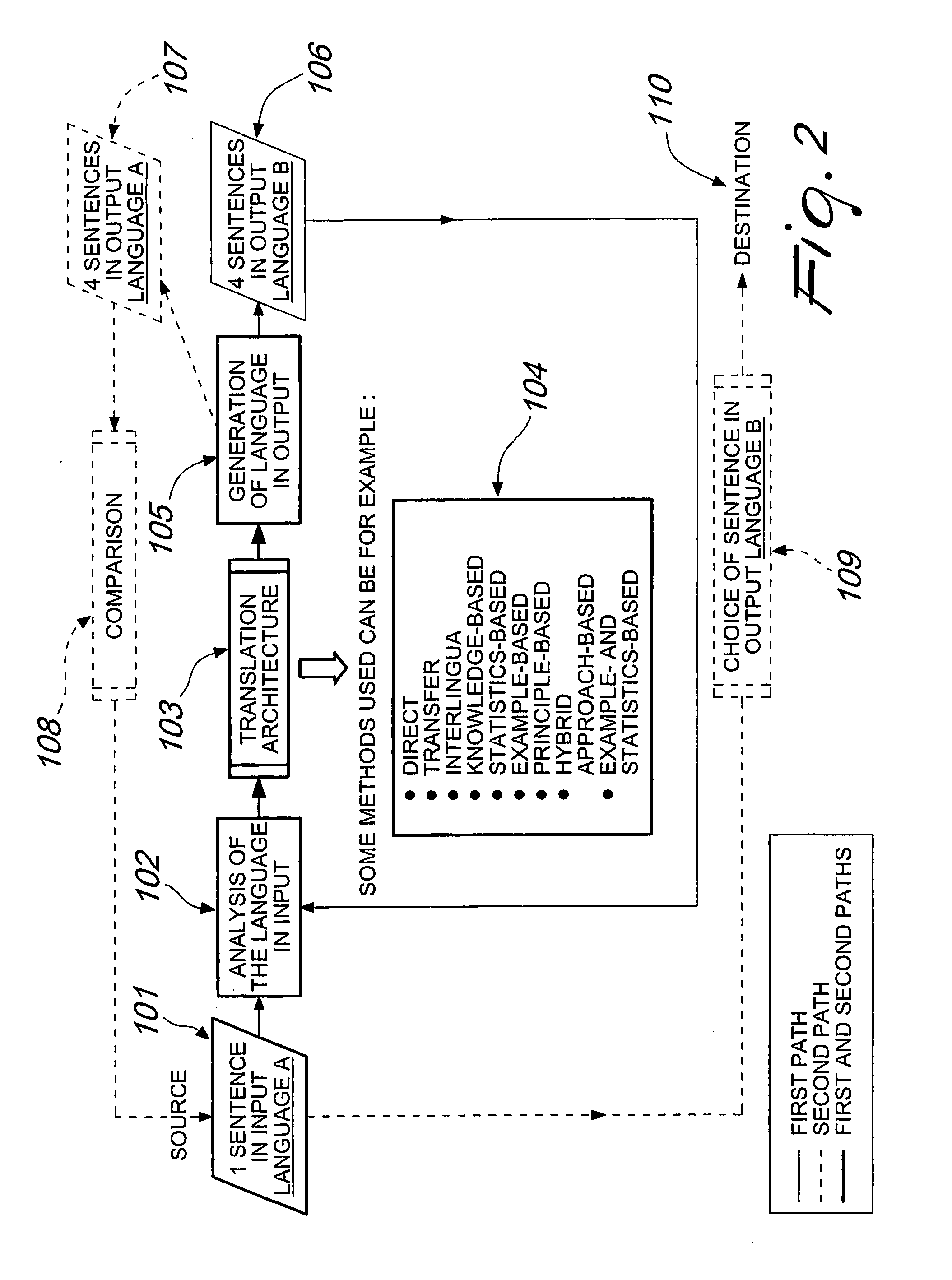
Method for Automatic Translation From a First Language to a Second Language and/or for Processing Functions in Integrated-Circuit Processing Units, and Apparatus for Performing the Method
InactiveUS20080208565A1Fast data processingLess-bulky and faster mannerNatural language translationSpecial data processing applicationsNatural language processingProcess function
A method for automatic translation from a first language to a second language, according to the invention, comprising the steps of:a) acquiring an initial sentence or text to be translated;b) selecting one or more automatic translation techniques;c) generating a plurality of translations of the initial sentence or text from the first language to the second language by means of the selected translation technique or techniques;d) for each one of the translations into the second language, generating a back-translation from the second language to the first language;e) comparing said back-translations into the first language with the initial sentence or text in the first language and generating a corresponding index of deviation;f) selecting, among the translations into the second language, the translation that corresponds to the back-translation for which the index of deviation is lowest or nil.
Owner:TECHMIND
Display device, driving method for display device, and electronic apparatus
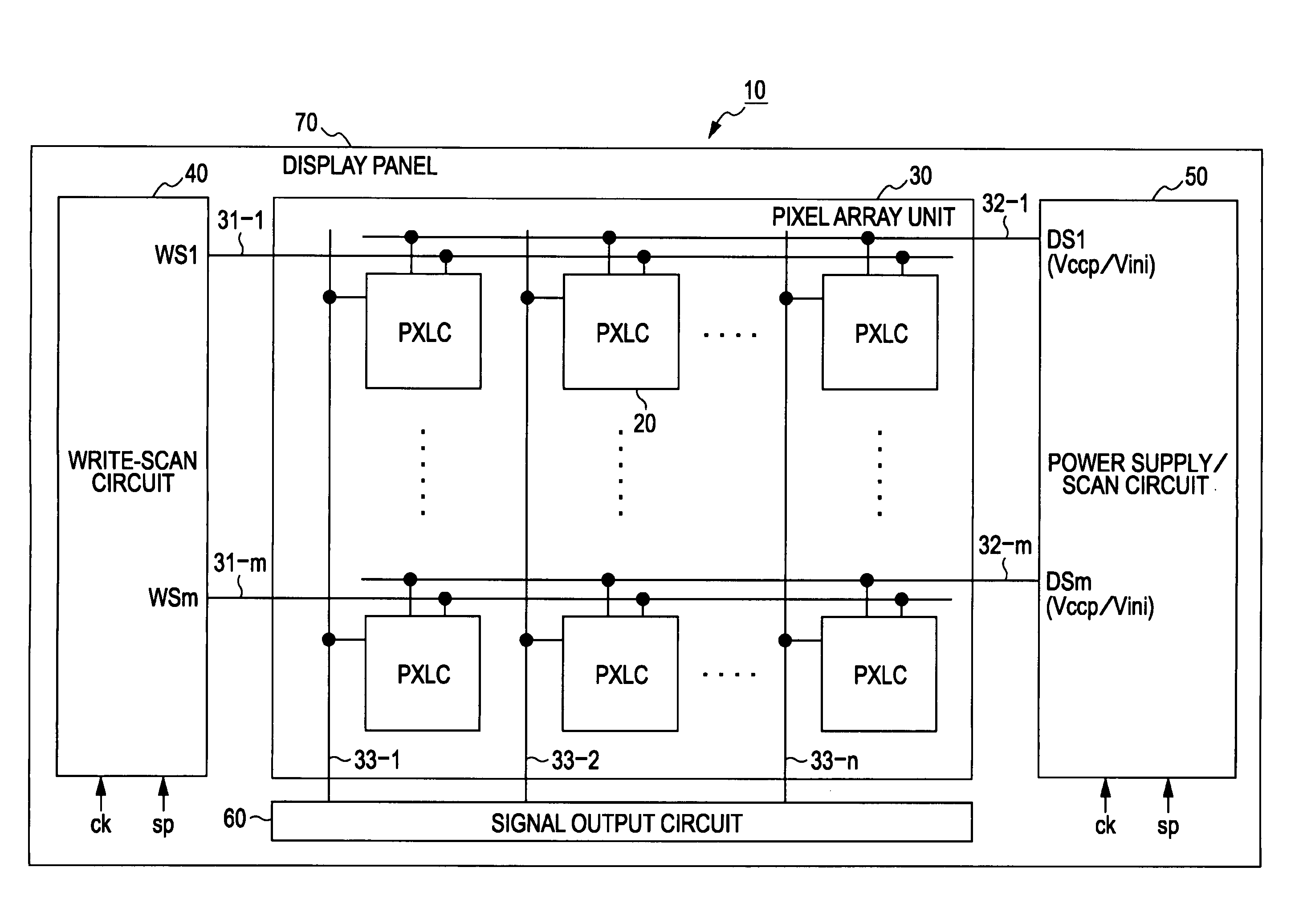
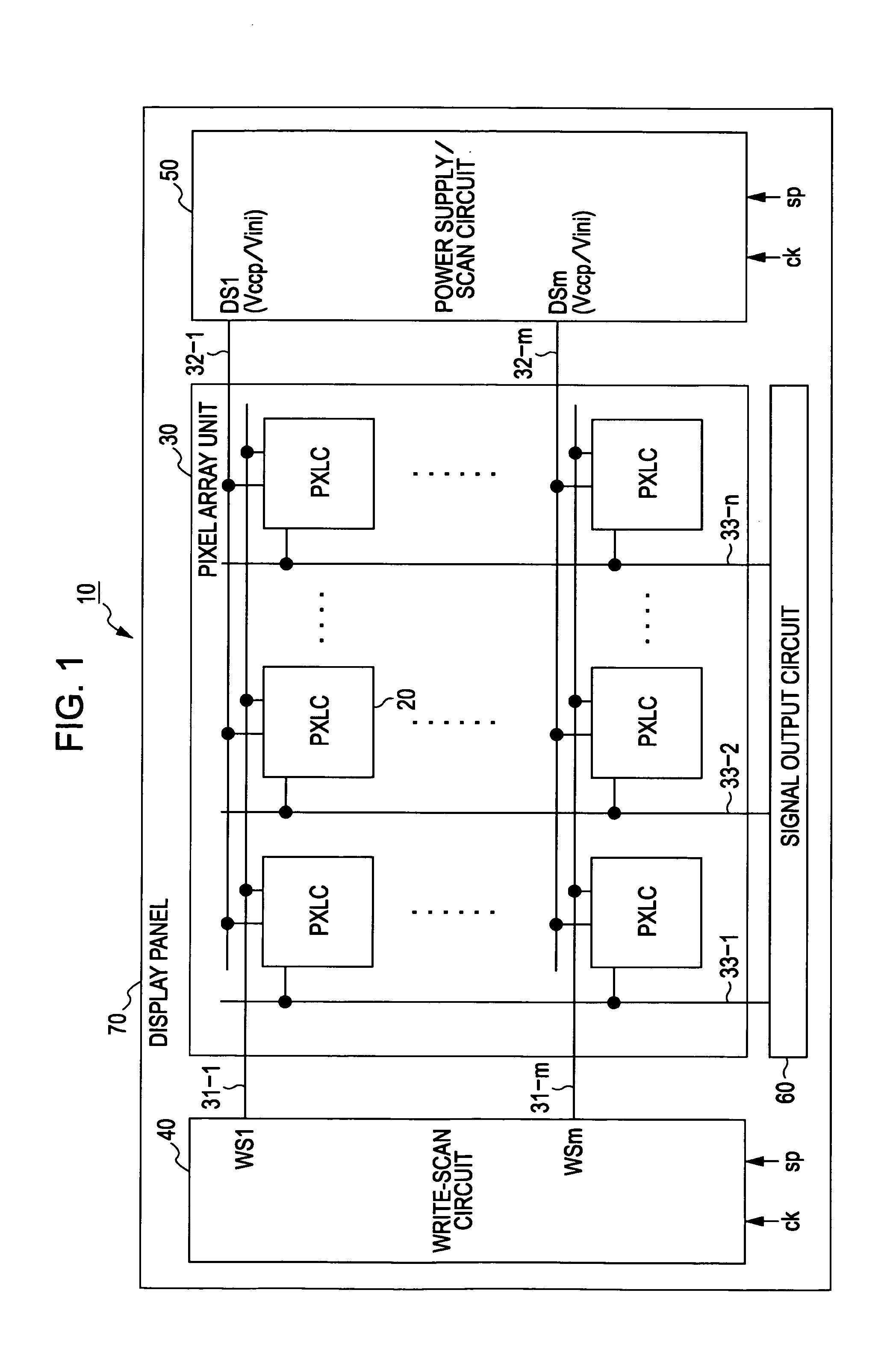
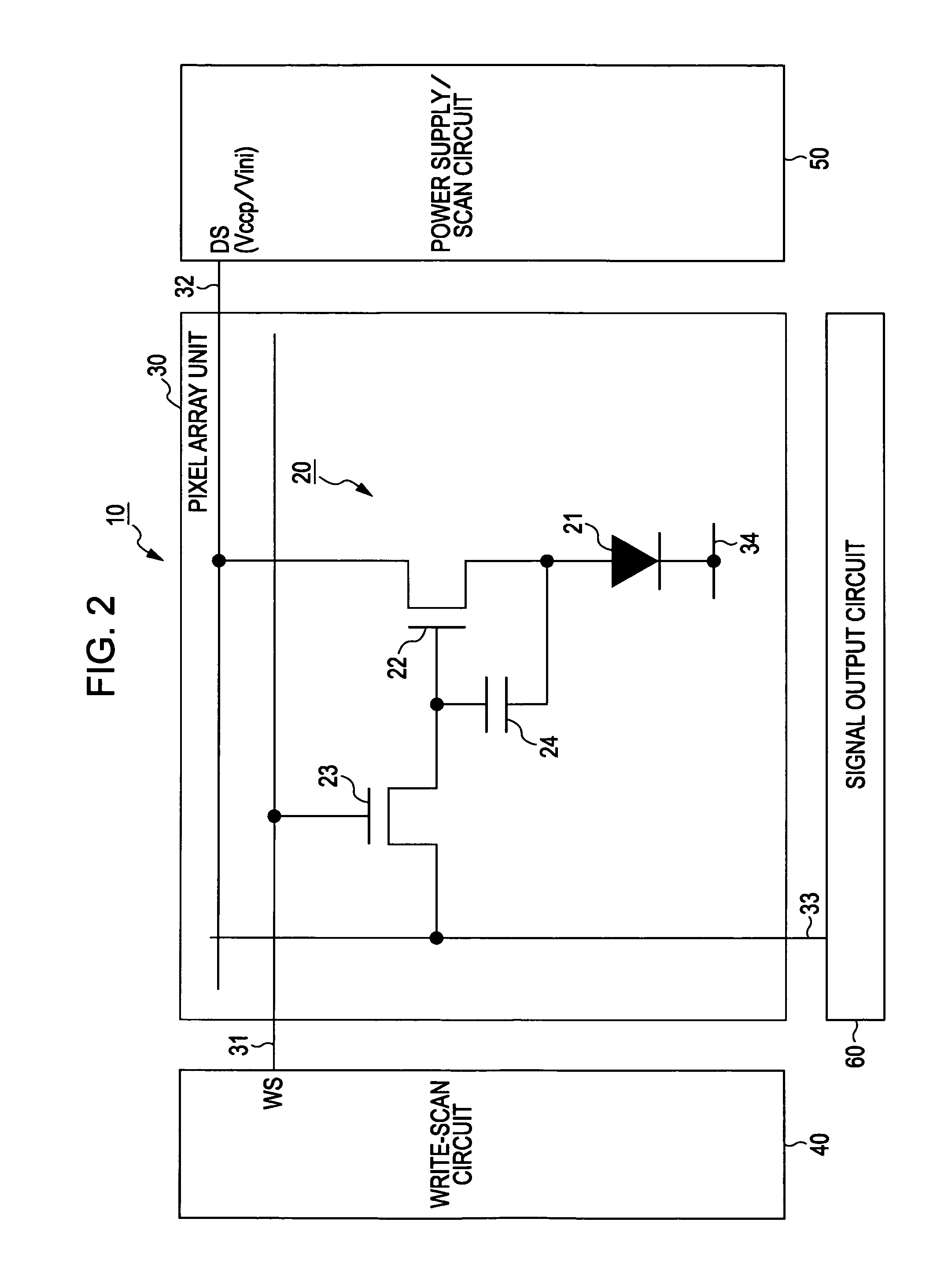
ActiveUS20100141626A1Reduce variationImprove display image qualitySolid-state devicesCathode-ray tube indicatorsProcess functionDisplay device
A display device includes a pixel array unit including pixels arranged in a matrix, the pixels each including an electrooptical element, a writing transistor for writing an image signal, a storage capacitor for storing the image signal, and a driving transistor for driving the electrooptical element in accordance with the image signal, the pixels each having a threshold correction process function for, before light emission of the electrooptical element, changing a source potential of the driving transistor to a potential obtained by subtracting a threshold voltage of the driving transistor from an initial gate potential of the driving transistor; and a power supply unit configured to set, as a power supply potential of a power supply line for supplying a current to the driving transistor, different potential values for a threshold correction period for execution of the threshold correction process and a light-emission period for the electrooptical element.
Owner:JOLED INC
Information processing apparatus and method for processing three-dimensional graphics using a second information processing unit for processing processed-related information
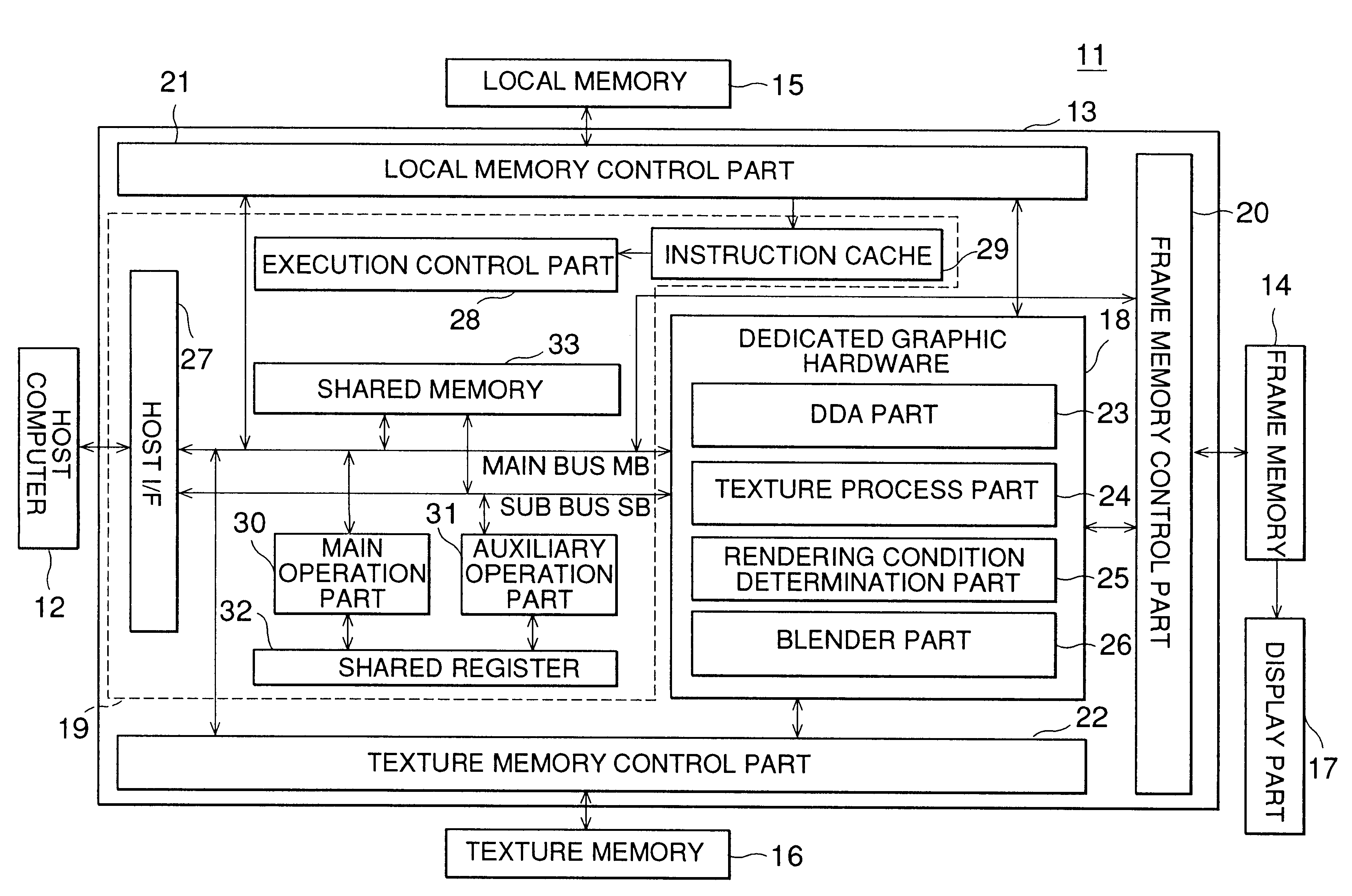
InactiveUS6388671B1Efficient processingComplete efficientlyDrawing from basic elementsMultiprogramming arrangementsInformation processingProcess function
An information processing apparatus includes a dedicated graphic hardware part dedicated to execution of a specific process function under a pipeline process scheme, and a microprogram execution part executing a process using a microprogram. When three-dimensional graphic information is processed, a process for determining endpoints is executed by the microprogram execution part, and an interpolation process started from an endpoint is executed by the dedicated graphic hardware part for each endpoint process. While the dedicated graphic hardware part is executing the interpolation process, the microprogram execution part is operated in parallel so as to execute the endpoint process for a next endpoint.
Owner:FUJITSU LTD
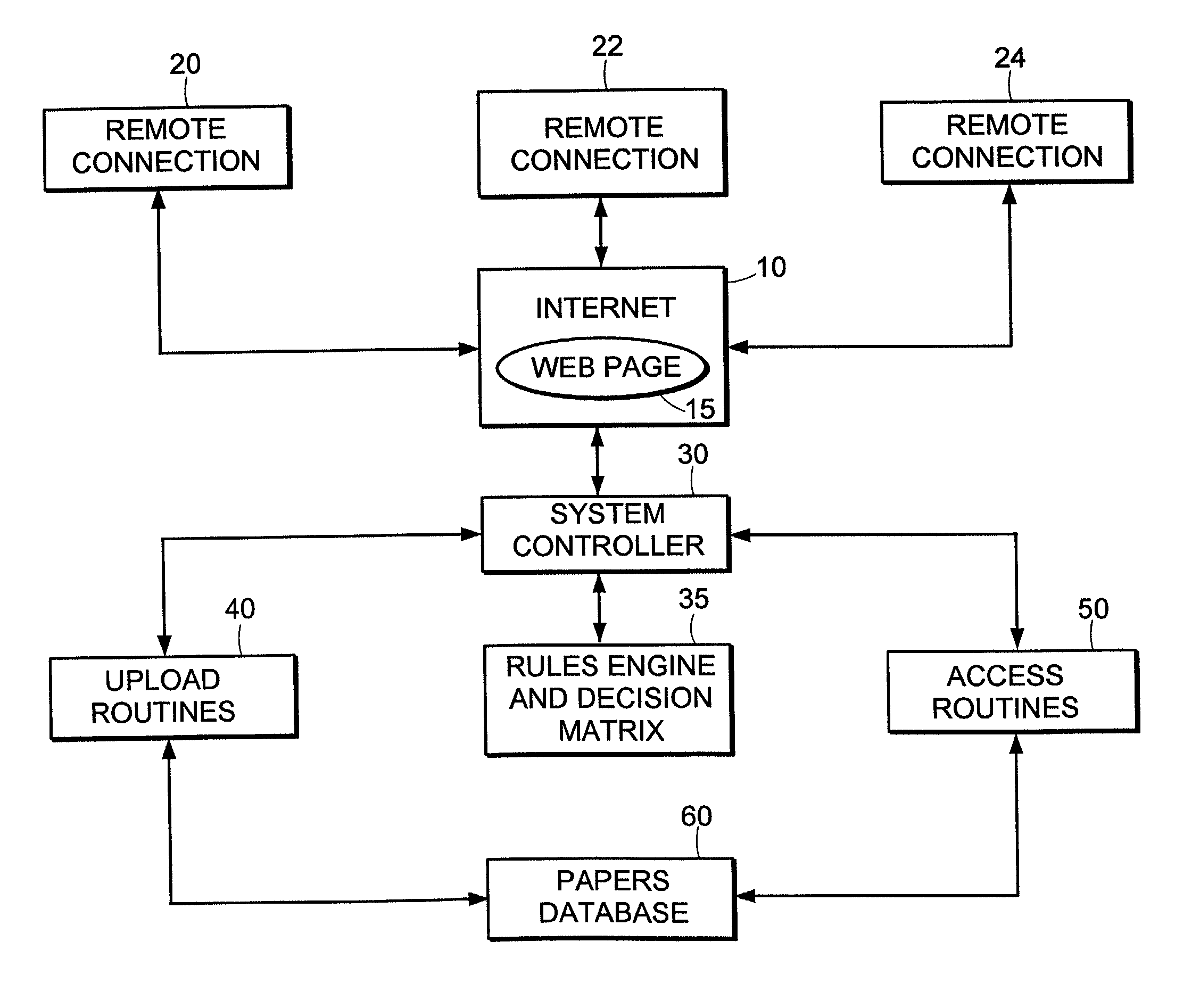
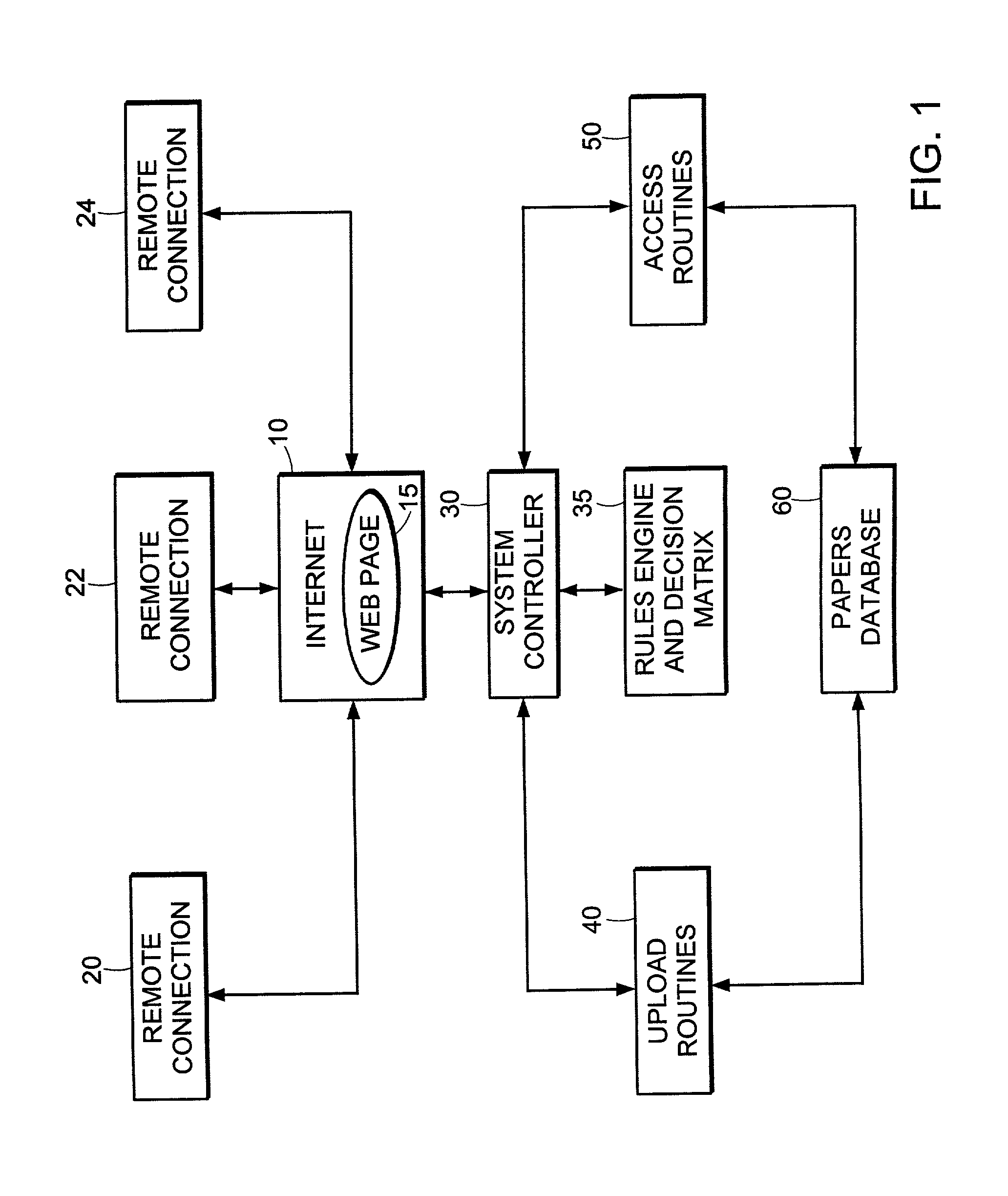
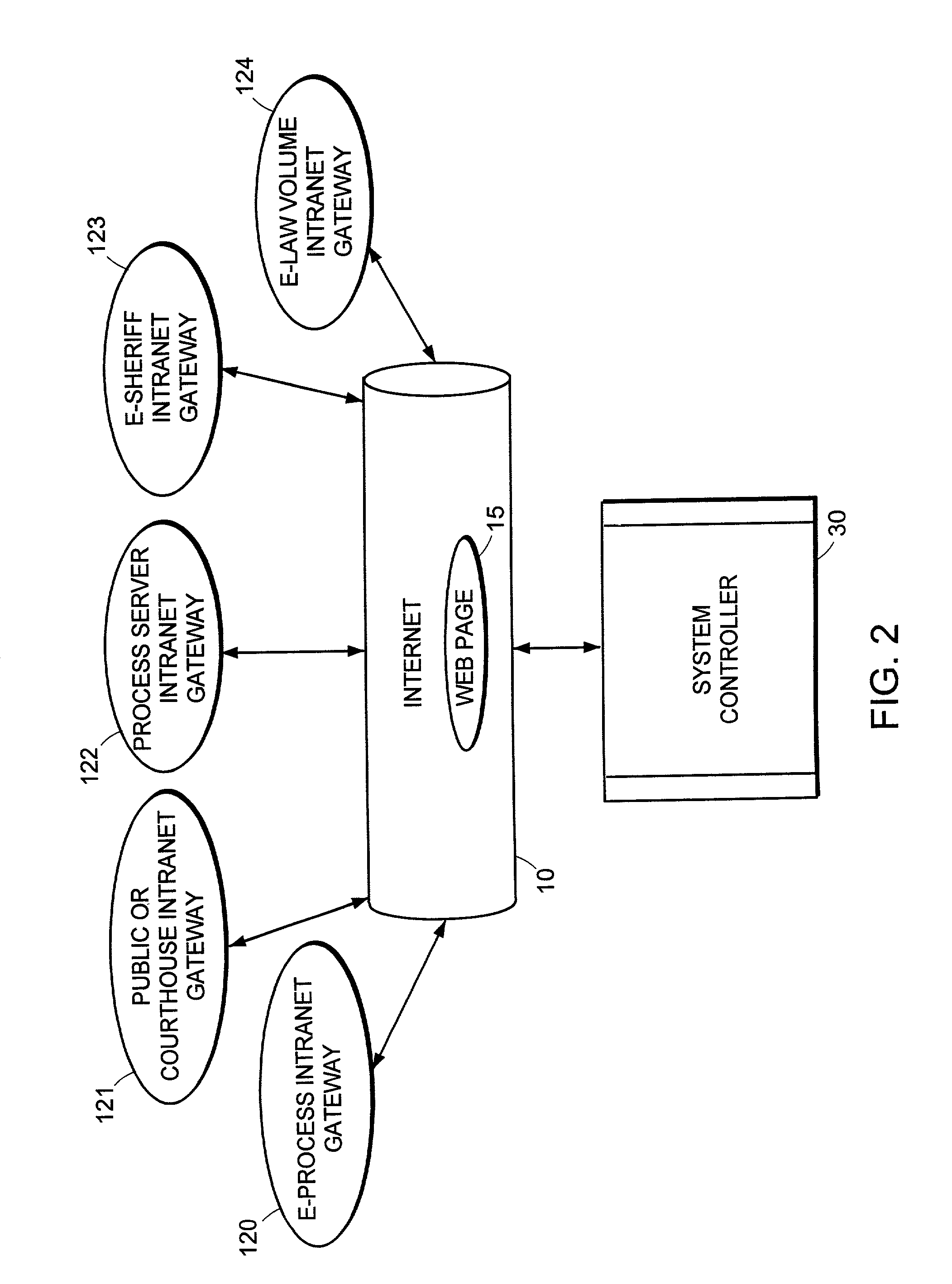
System and method for online creation and integration of service of process functions
A system and method for online creation and integration of service of process functions is provided, for use in conjunction with paper or electronic filing of court papers. By logging on to a web page, the user can access a rules and decision matrix database providing the rules and requirements for process service by jurisdiction and type. Such rules can be incorporated into process requests using online tools and document management software. Once entered, the requests are compiled in a database, and a system controller coordinates with affiliated process servers to procure process service in the desired jurisdiction.
Owner:CAPLAN DENNIS +1
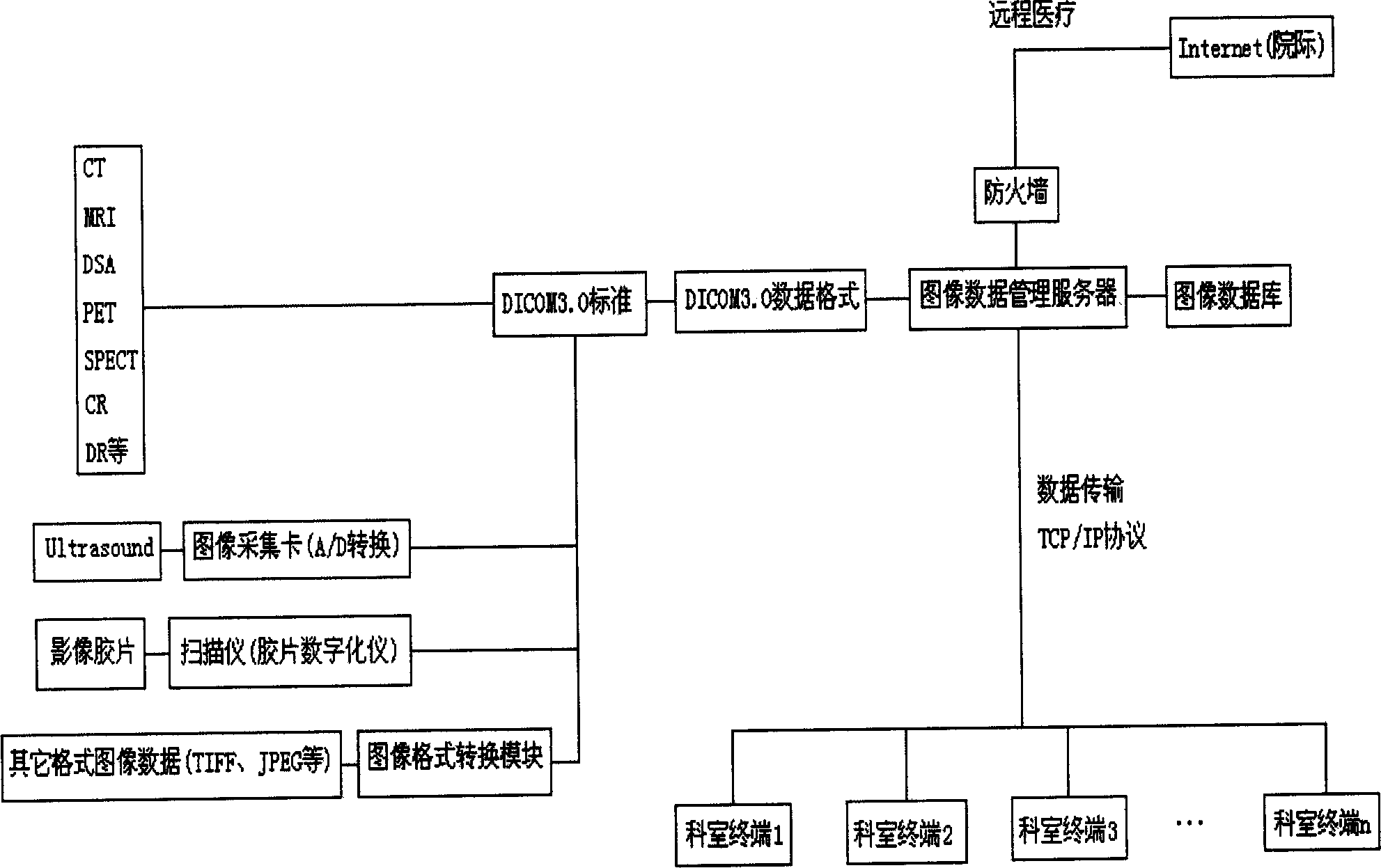
Medical image data transmission and three-dimension visible sysem and its implementing method
InactiveCN1794246AImprove efficiencyEasy to useTransmissionSpecial data processing applicationsProcess functionMedical imaging data
This invention discloses a medical image transmission and 3-D visual system and a realizing method, which develops an iconography diagnosis system operated by stand-alones and single persons to expand the image data process function of a radiation section or an image working station to computer terminals of hospitals, so that, doctors in hospitals can get the image data of patients directly from the terminals in their offices to carry out 3-D display interaction operations.
Owner:RESEARCH INSTITUTE OF TSINGHUA UNIVERSITY IN SHENZHEN
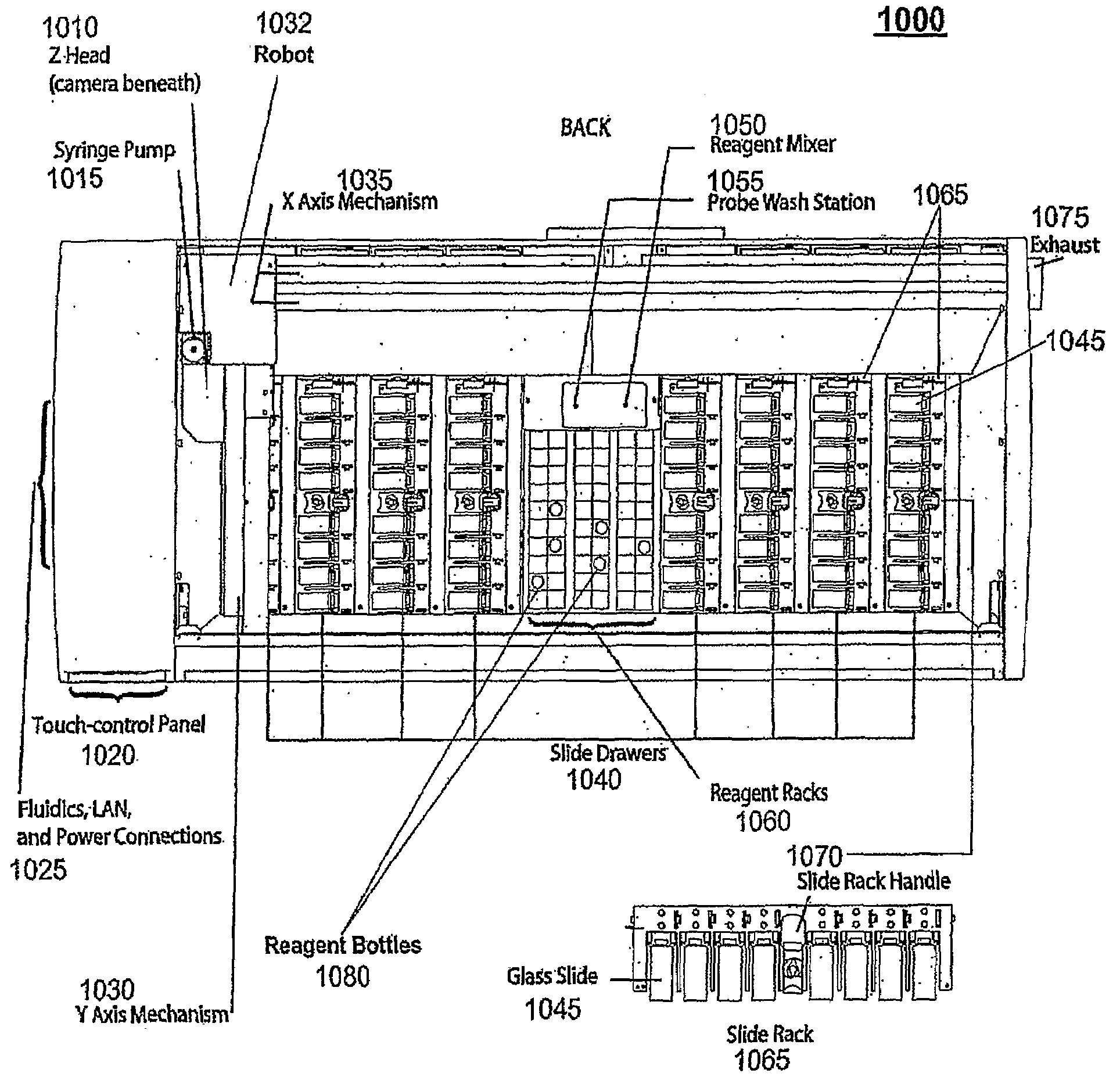
Removal of Embedding Medium
InactiveUS20090155907A1Simplified fast automatedLow melting pointBioreactor/fermenter combinationsBiological substance pretreatmentsProcess functionOrganic solvent
A method, apparatus and system for automated removal of an embedding medium from an embedded biological sample. The method comprising the steps of: providing an automated sample processing apparatus having an automated process operation capability that causes automated process operation events through robotic sample process functions; providing a clearing solvent, e.g. an organic solvent, capable of lowering the melting point of an embedding medium and / or dissolving an embedding medium; loading a plurality of carriers with embedded biological samples in the automated sample processing apparatus; exposing an embedded biological sample to the clearing solvent, whereby the embedding medium is liquefied; and providing a washing solution capable of removing the clearing solvent and the liquefied embedded medium from said biological sample, said clearing solvent and said washing solution being immiscible.
Owner:DAKOAS
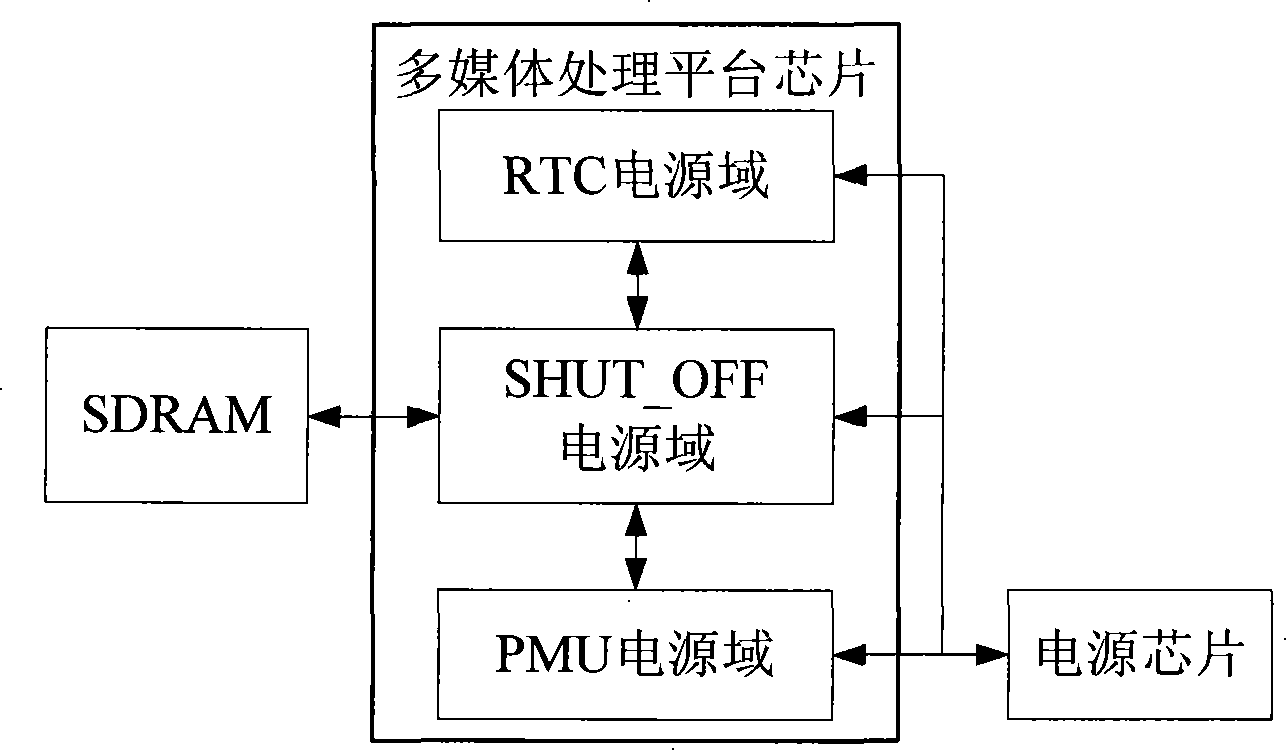
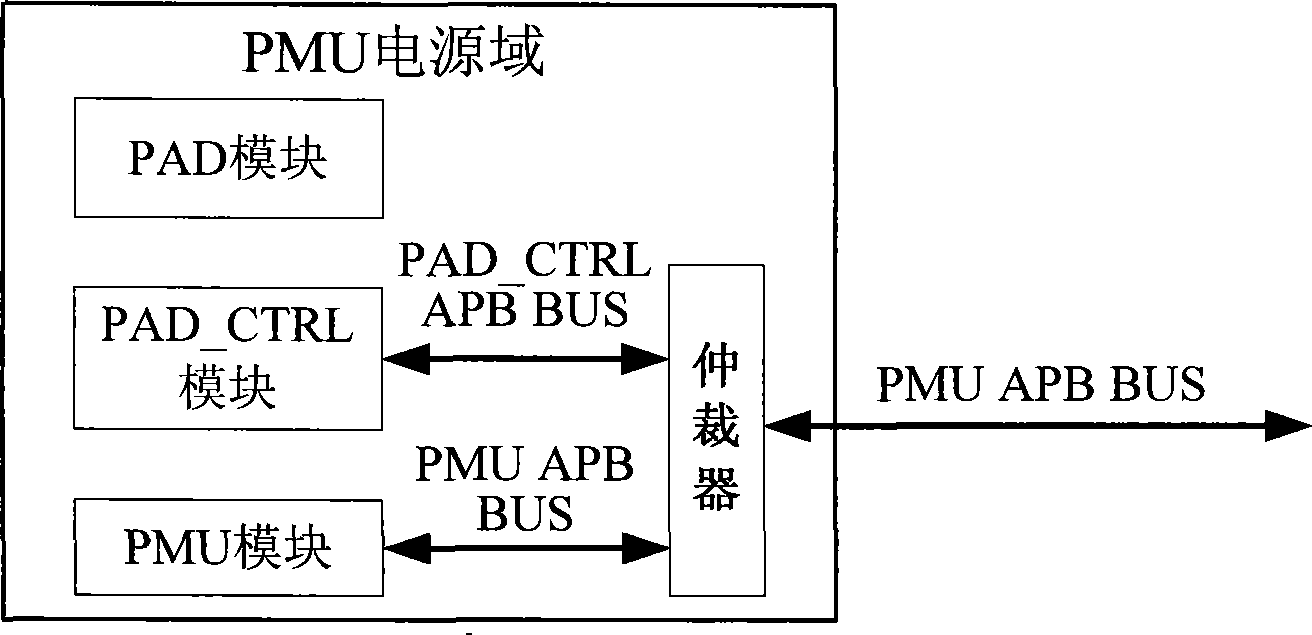
Multimedia processing platform chip
InactiveCN101251766AReduce energy consumptionStrong processing functionEnergy efficient ICTPulse modulation television signal transmissionProcess functionReal-time clock
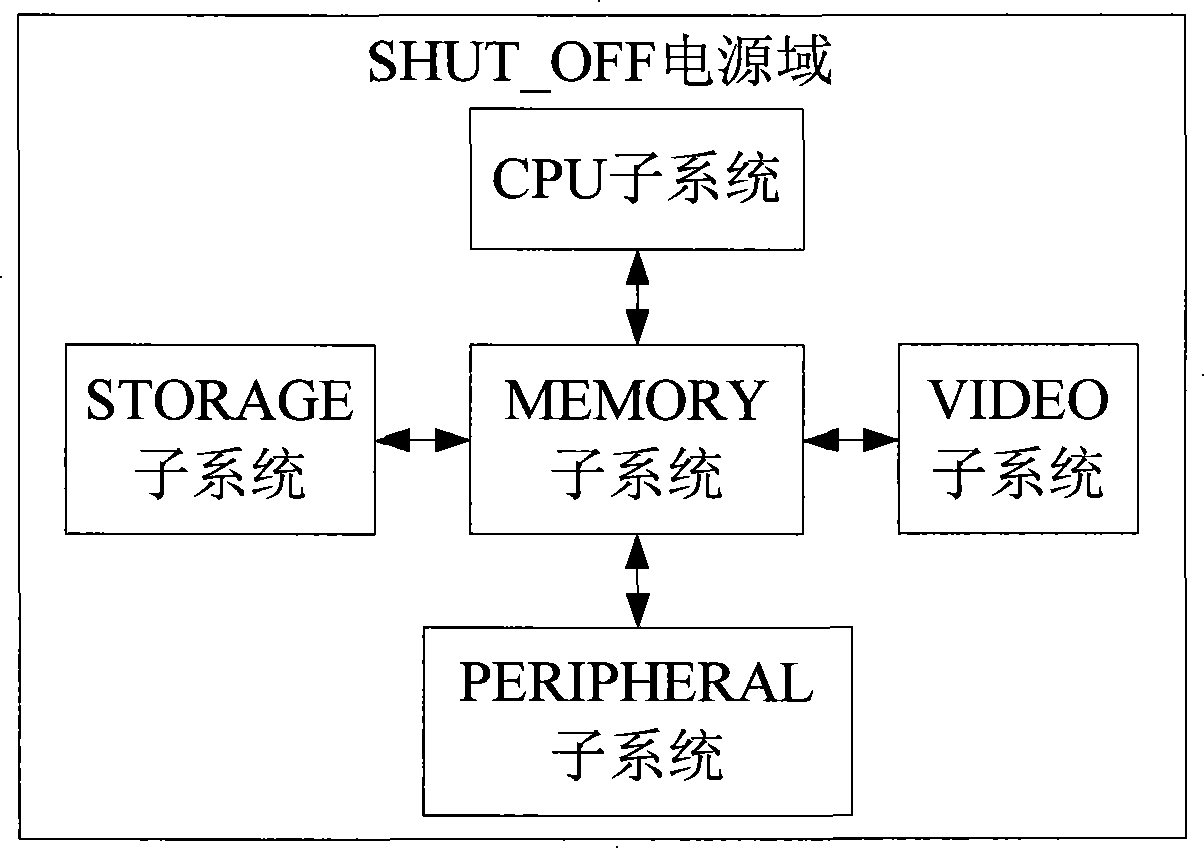
The invention provides a multimedia processing platform chip comprising a RTC power domain providing a real time clock, power on time and timer interruption; a SHUT_OFF power domain used for coding / decoding process to multimedia message and a PMU power domain used for controlling the SHUT_OFF power domain to switch among the three following modes: normal mode, sleep mode and shut down and controlling the power supply of a power supply chip to each power domain, namely supplying power to the RTC power domain all the time, supplying power to the PMU power domain in the normal mode and the sleep mode and supplying power to the SHUT_OFF power domain in the normal mode. The multimedia processing platform chip can reduce the energy consumption of the multimedia processing platform chip, has excellent production integrality and small DIE area, and also can lower the encapsulation cost. The multimedia processing platform chip can ultimately realize the whole system only using the own chip with a power supply chip and an SDRAM, which is easy to realize. The multimedia processing platform chip has strong process function and lower cost.
Owner:VIMICRO CORP
System and method for killing protected malicious computer process
ActiveCN102982283AAvoid attackBlock data securityPlatform integrity maintainanceProcess functionSoftware engineering
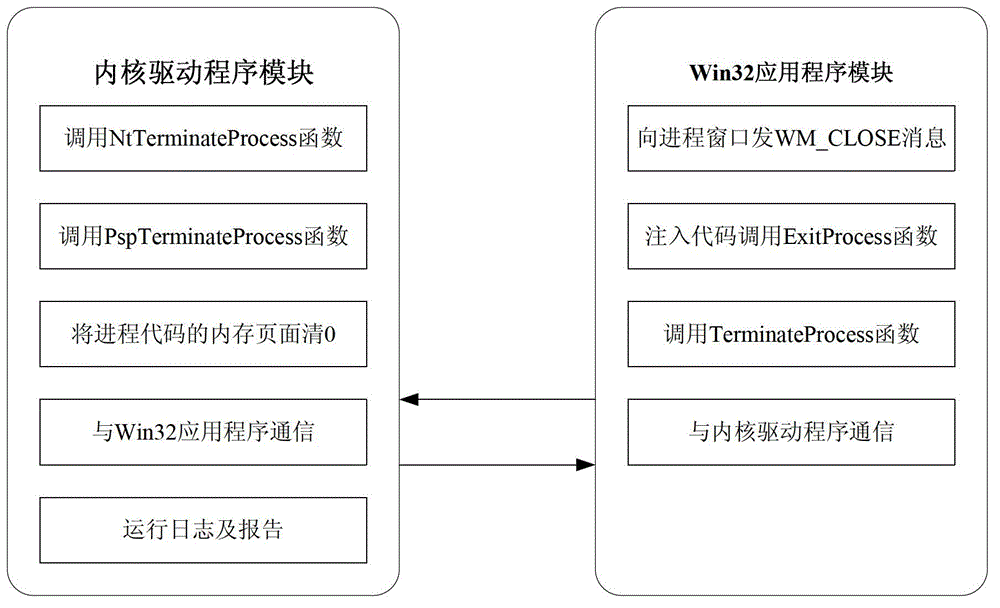
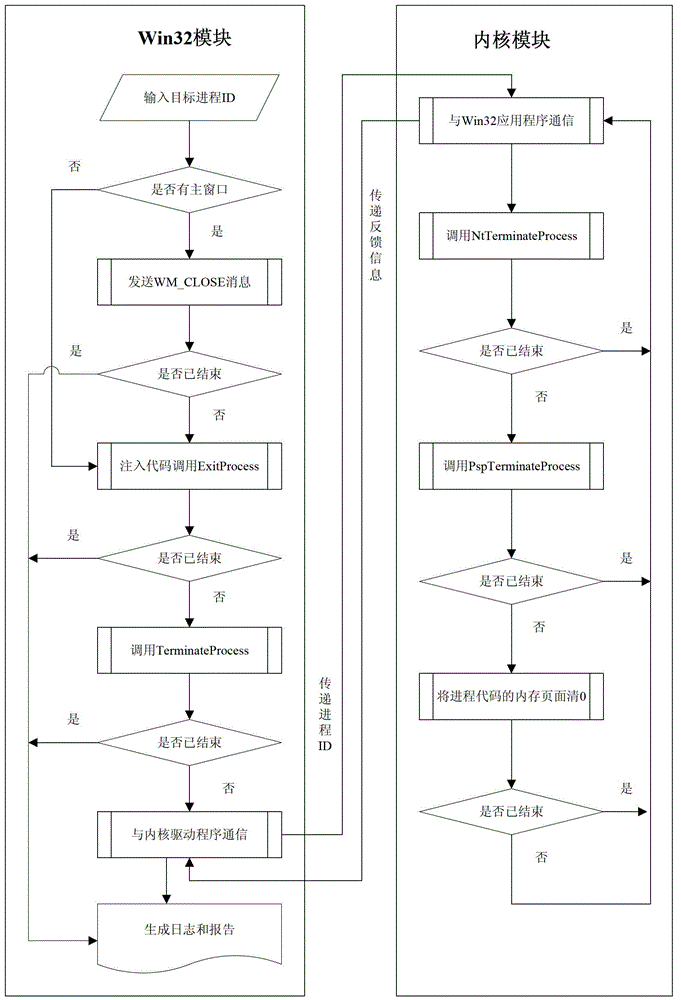
The invention discloses a system and a method for killing a protected malicious computer process. The system is realized by the two modules of a Win32 application program and a driving program. A Win32 application program module mainly comprises the functions of sending WM_CLOSE information to a progress window, injecting a code and calling an Exit Process function, calling a Terminate Process function, communicating with a core driving program, running logs and reporting. A core driving program module comprises the functions of communicating with the Win32 application program, calling an Nt Terminate Process function, calling a Psp Terminate Process function and resetting a RAM page of a process code. Meanwhile, the invention also discloses the method for killing the protected malicious computer process. A combined technology of the core driving program and the Win32 application program is adopted and various process-killing methods are tried, so that various malicious processes are basically killed, the attack of the malicious processes to a computer is avoided and the data safety is ensured.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
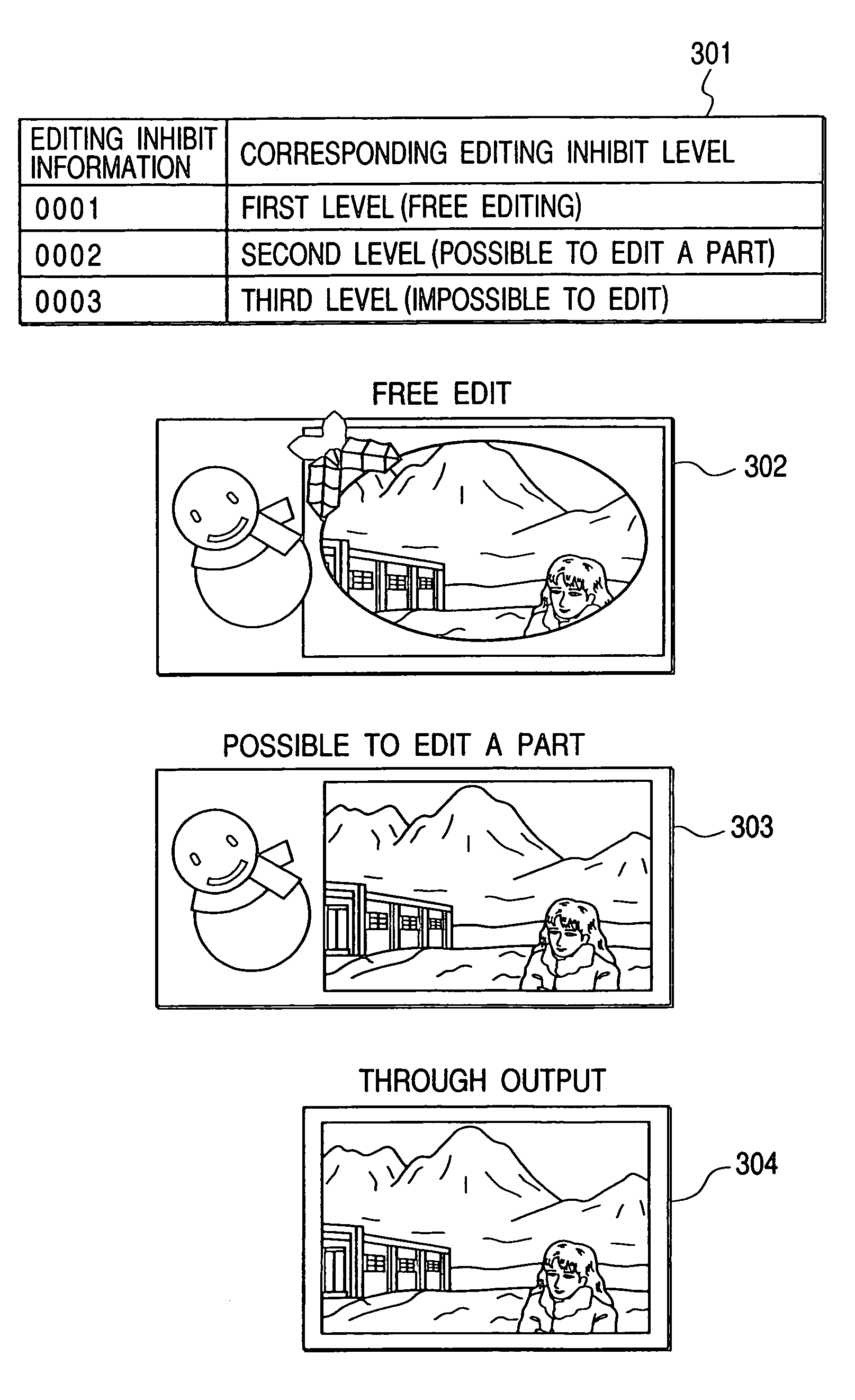
Display and control of permitted data processing based on control information extracted from the data
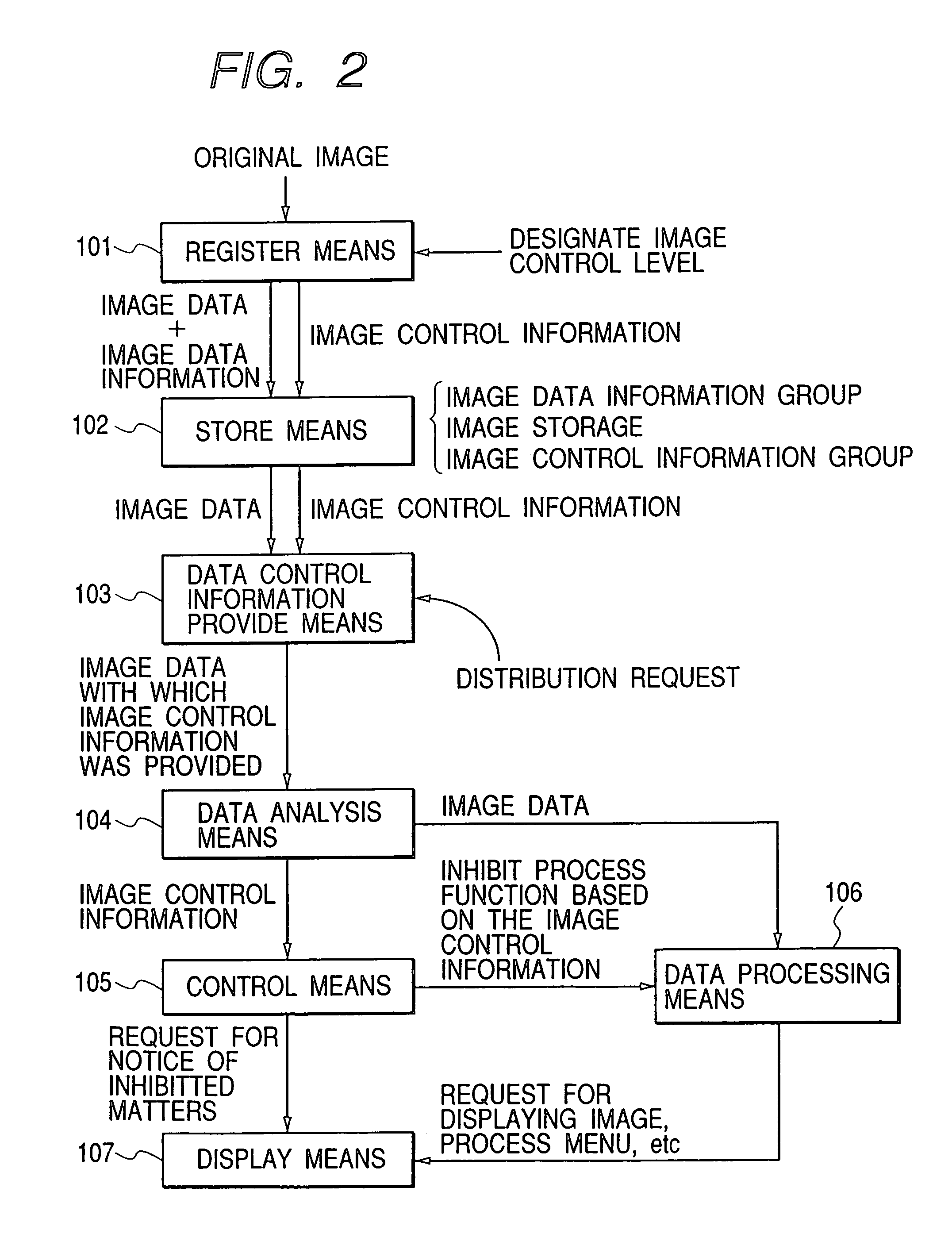
InactiveUS7046258B1Precise processingImage memory managementCathode-ray tube indicatorsData controlProcess function
A data processing apparatus having a data analysis circuit for extracting data control information from data provided with the data control information to be used for restricting various processes, a data processing circuit for performing various processes for the data added with the data control information, a display unit for displaying a process function of each of the various processes to be executed by the data processing circuit, and a control circuit for controlling the data processing circuit and the display unit in accordance with the data control information extracted by the data analysis circuit, wherein the control circuit inhibits to execute an inhibited process in accordance with the data control information extracted from the data and controls the display unit to change a display style of the process function of each of the various processes to an inhibition display style.
Owner:CANON KK
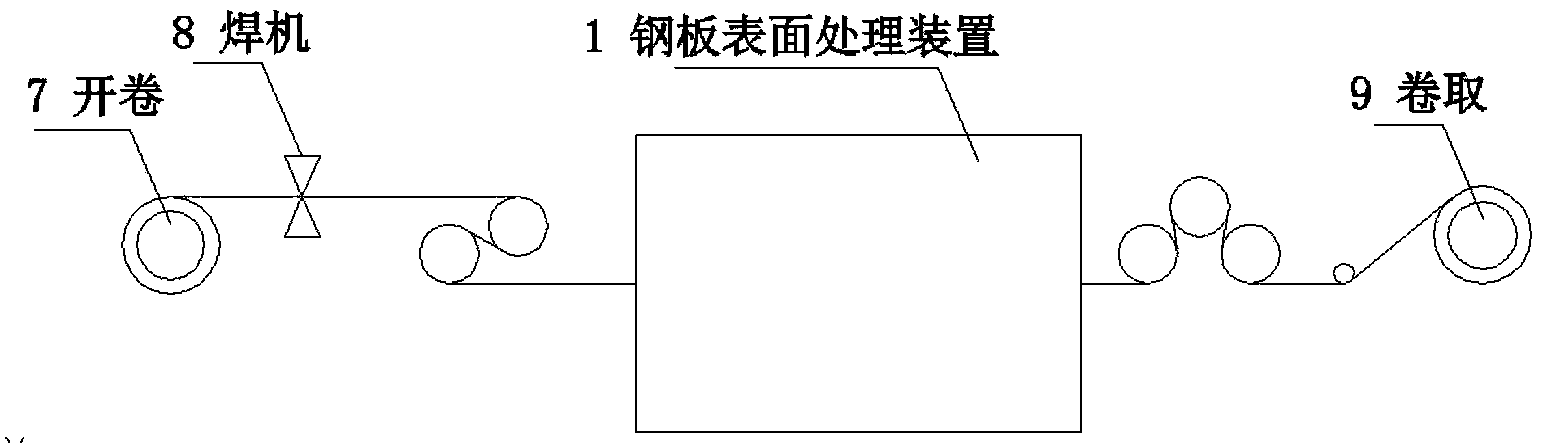
Steel plate surface treatment method and device
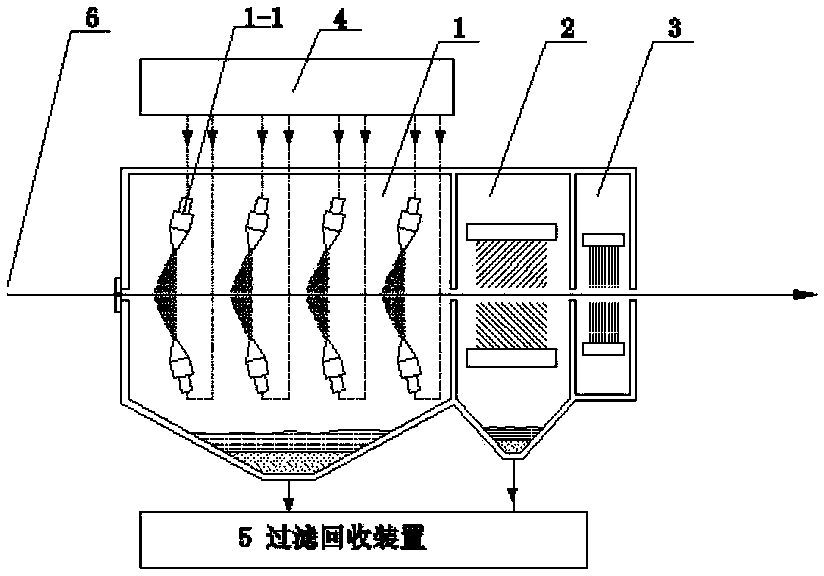
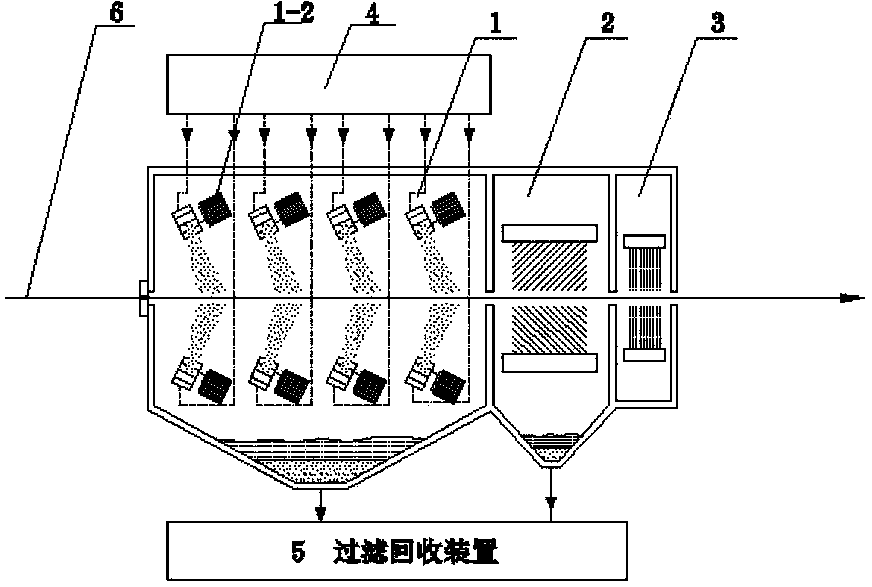
ActiveCN104056865AImprove cleanlinessReduce loadWork cleaning devicesMetal rolling arrangementsProcess functionSheet steel
An apparatus for treating a surface of a steal plate, sequentially comprising: a strip steel surface treatment unit (1) provided with a high-pressure ejection device (1-1) or a centrifugal throwing device (1-2), a strip steel surface cleaning unit (2), and a strip steel surface drying unit (3), one or both of the high-pressure ejection device and the centrifugal throwing device being arranged, and slurry, namely a mixture of solid abrasive and water, being sprayed onto the surface of the strip steel; and further comprising a slurry supply unit (4) and an abrasive filtering and recovery unit (5). Also disclosed is a method for treating a surface of a steal plate. In the treatment method, by spraying the solid mixed abrasive onto the surface of the strip steel, the surface roughness of the strip steel is controlled, and further, the oil, iron oxide scales and some dirty things on the surface of the strip steel can be cleared, thereby fully or partially replacing the smoothing process function.
Owner:BAOSHAN IRON & STEEL CO LTD
An embedded browser and its implementation method
InactiveCN103177095BEasy to useEasy to upgradeSpecific program execution arrangementsSpecial data processing applicationsProcess functionUser perception
Owner:CHENGDU SANLING KAITIAN COMM IND
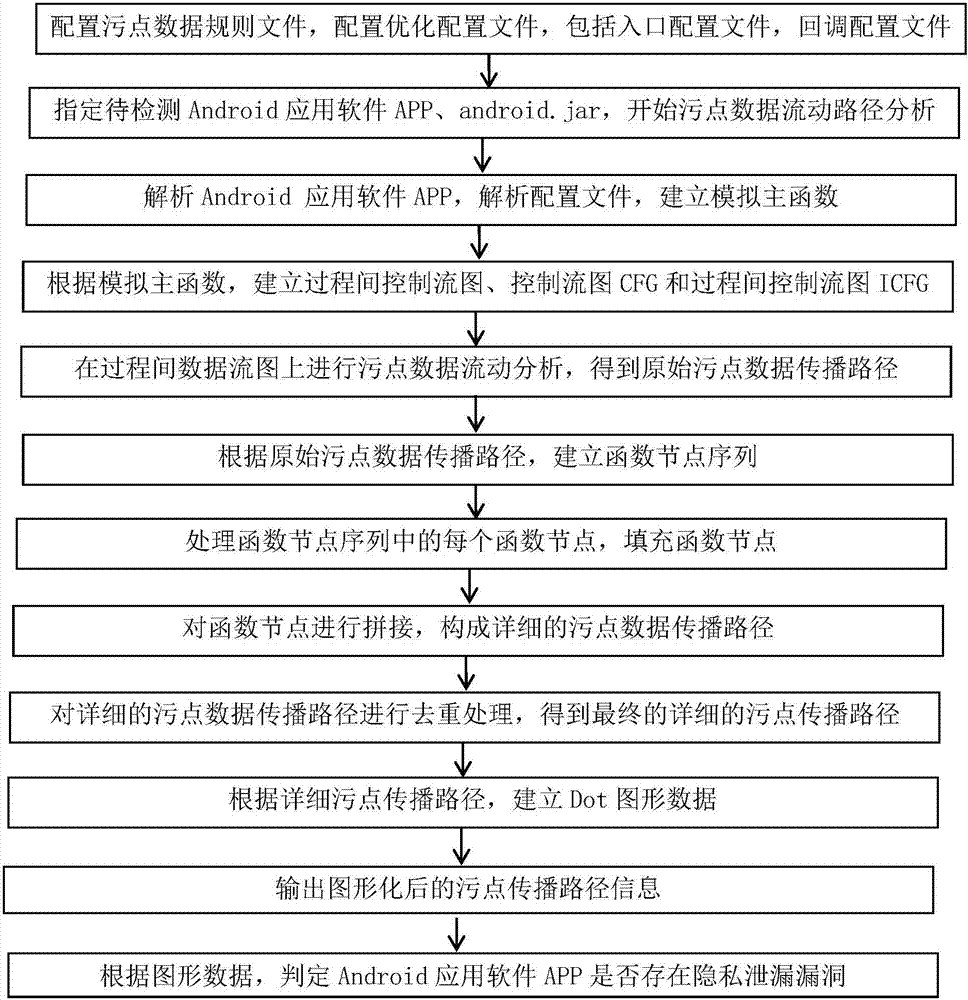
Privacy leakage vulnerability detection confirming method based on static stain data analysis
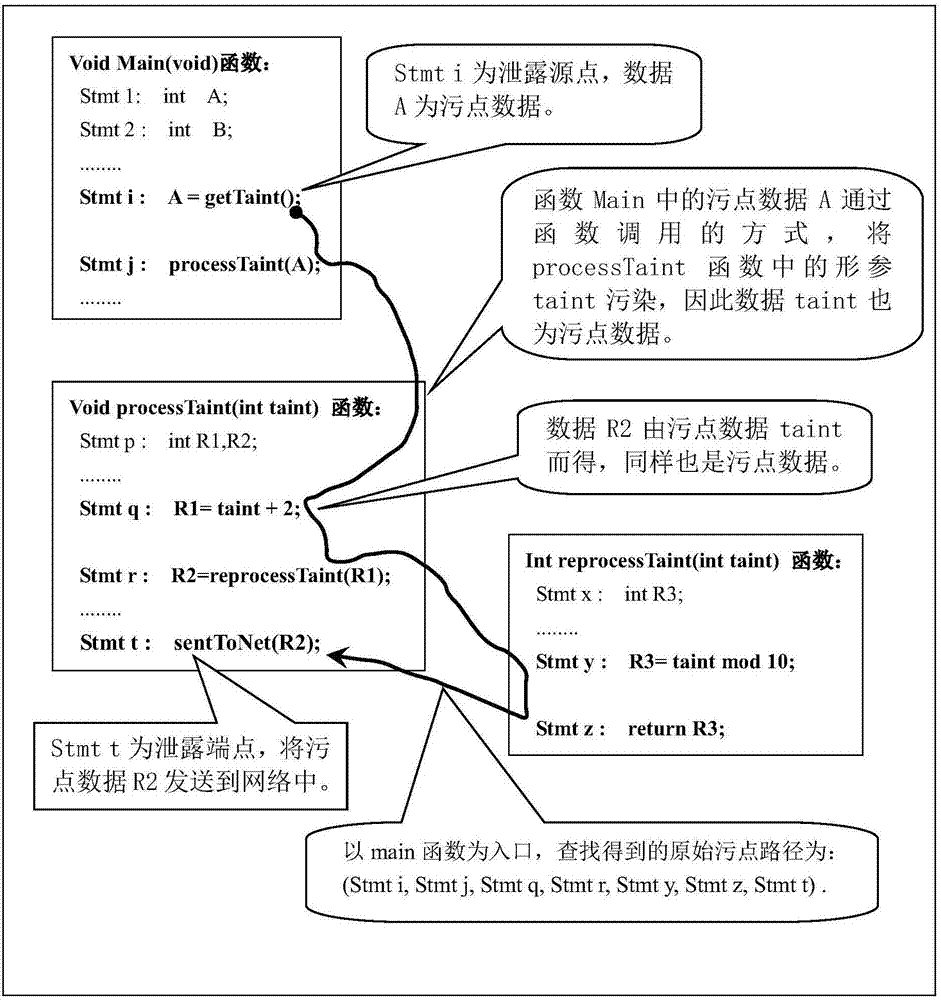
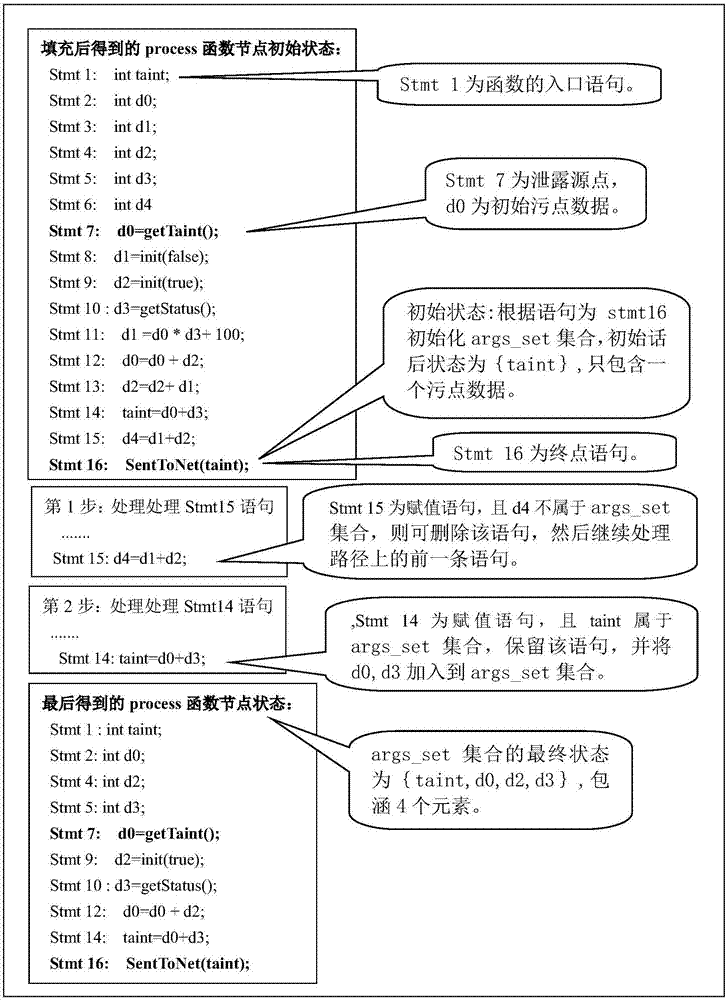
ActiveCN106940773ASmall scaleSolve the detection speed is slowDigital data protectionPlatform integrity maintainanceProcess functionSoftware engineering
The invention discloses a method for detecting whether privacy leakage vulnerability exists in an Android application software APP or not. The method mainly solves the problems of low vulnerability detection speed, high detection environment requirements and low detection accuracy in the prior art. The method comprises the realization processes of configuring an optimization detection file; limiting an assembly and callback of the detected Android application software APP; performing static stain data stream analysis on the limited assembly and callback to obtain a stain data stream path; further processing the stain path, building a function node sequence; expanding and filling with function nodes, performing pruning and compression processing, and connecting the processed function nodes to form a detail stain data flowing path; performing deduplication processing on the detail stain data flowing path; then, performing graphical output. The method provided by the invention has the advantages that the speed of detecting the privacy leakage vulnerability of the Android application software APP is accelerated; the requirements on the detection environment and the vulnerability reproducing difficulty are reduced, so that the vulnerability analysis is faster and more accurate.
Owner:XIDIAN UNIV
Novel method for wireless communication networking based on the cooperation mechanism
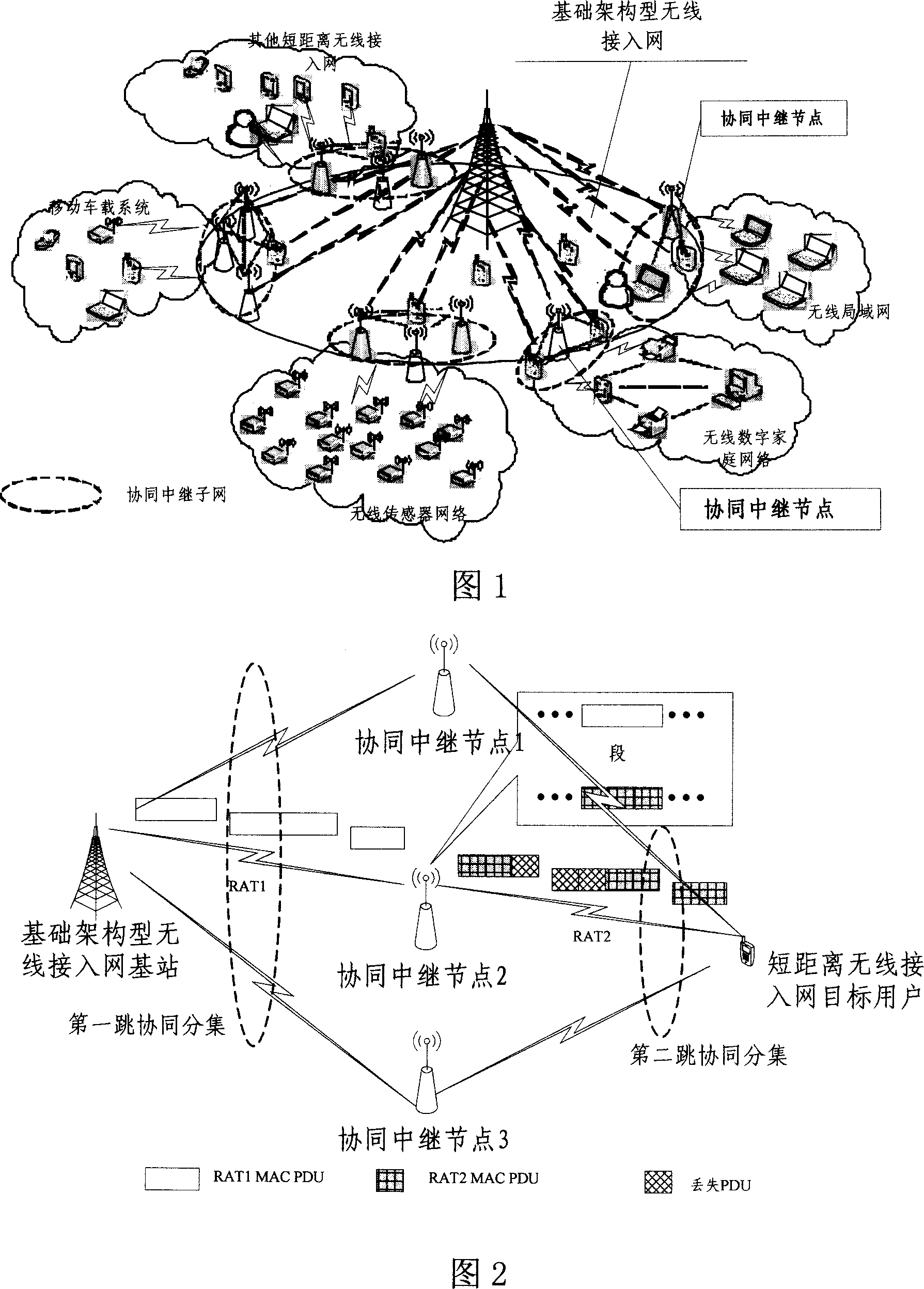
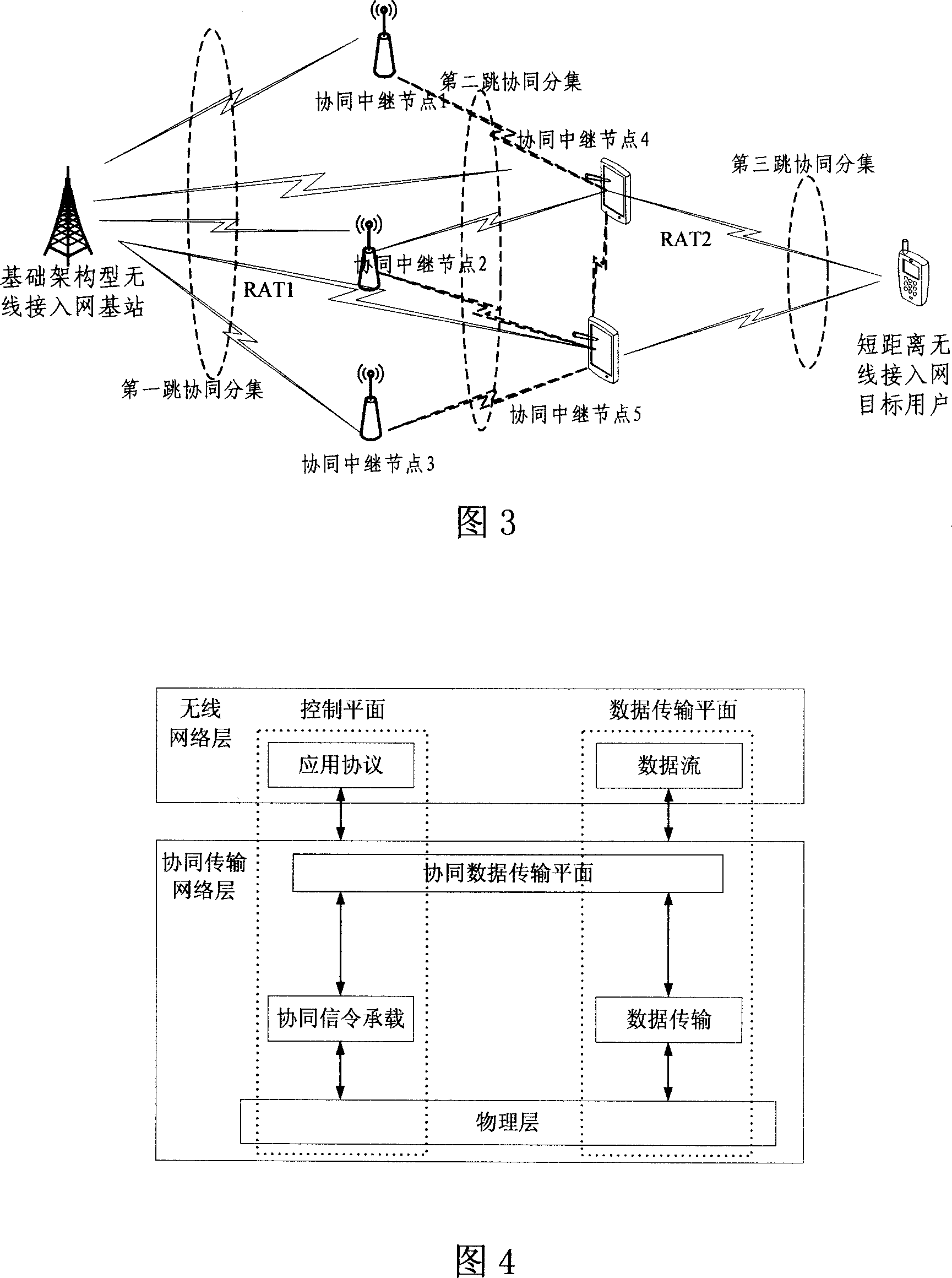
InactiveCN1996920ASolve integration bottlenecksHigh speed data transmissionHybrid switching systemsNetworks interconnectionProcess functionNetwork connection
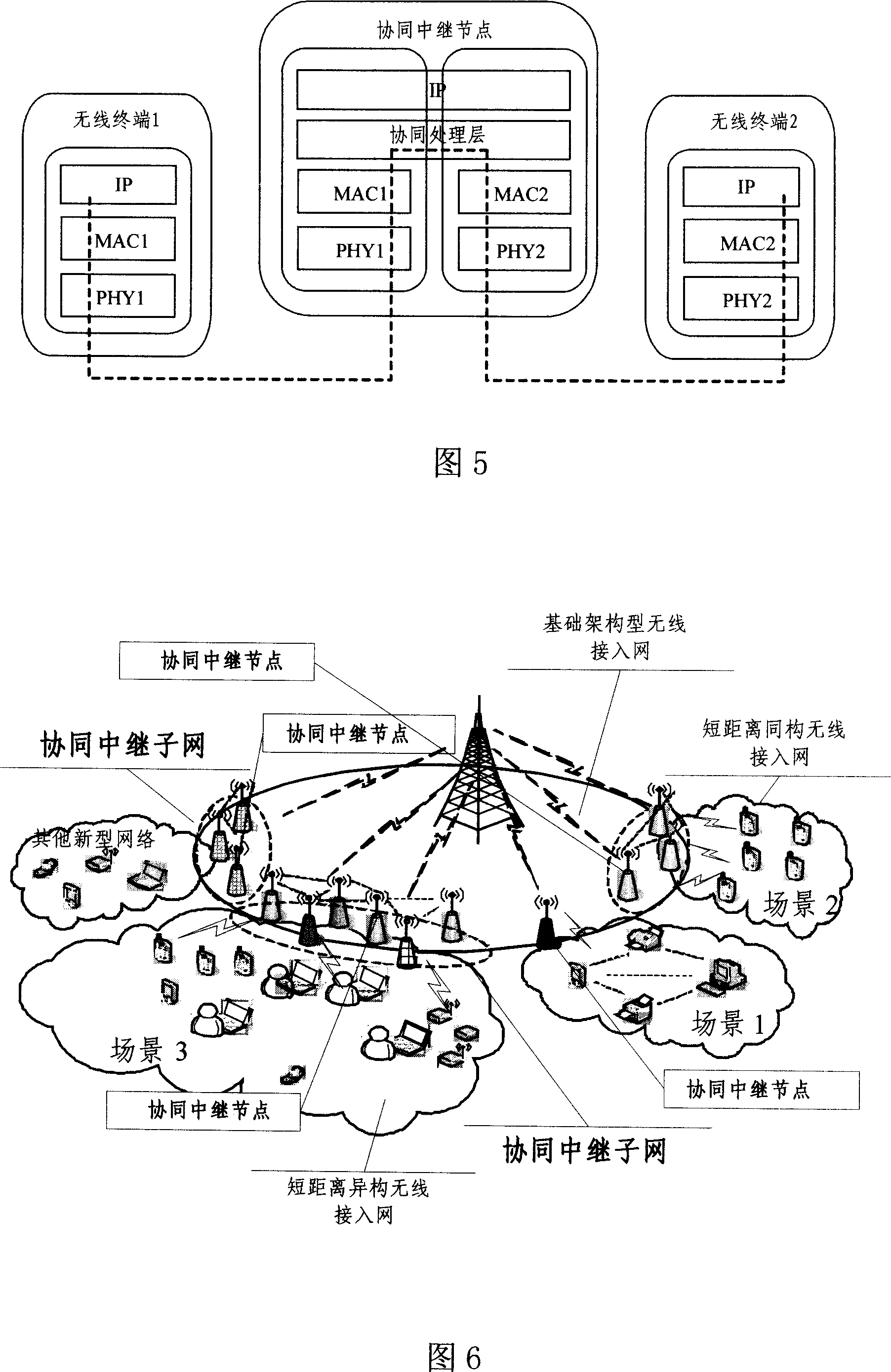
This invention relates to one new wireless communication network forming method based on association mechanism, which ensures the hater wireless interface network connection and to supply hater network association gains through point's association process. This invention relay point has the total functions of relay point and also with process function for self forming relay sub network. This invention also provides one relay sub network logic agreement reference mode and wireless hollow interface association agreement.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Intellectual property nucleus of optical fiber channel
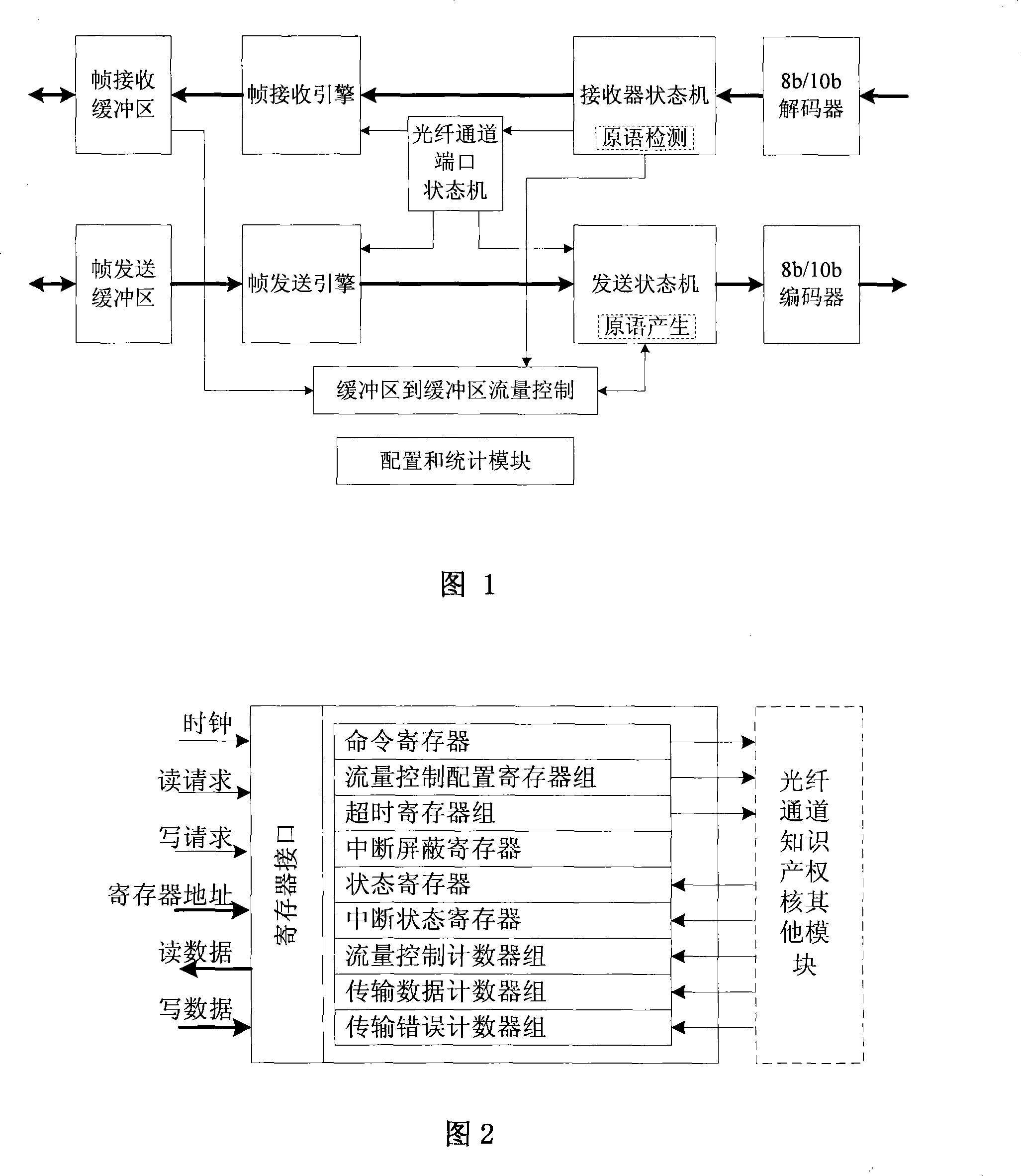
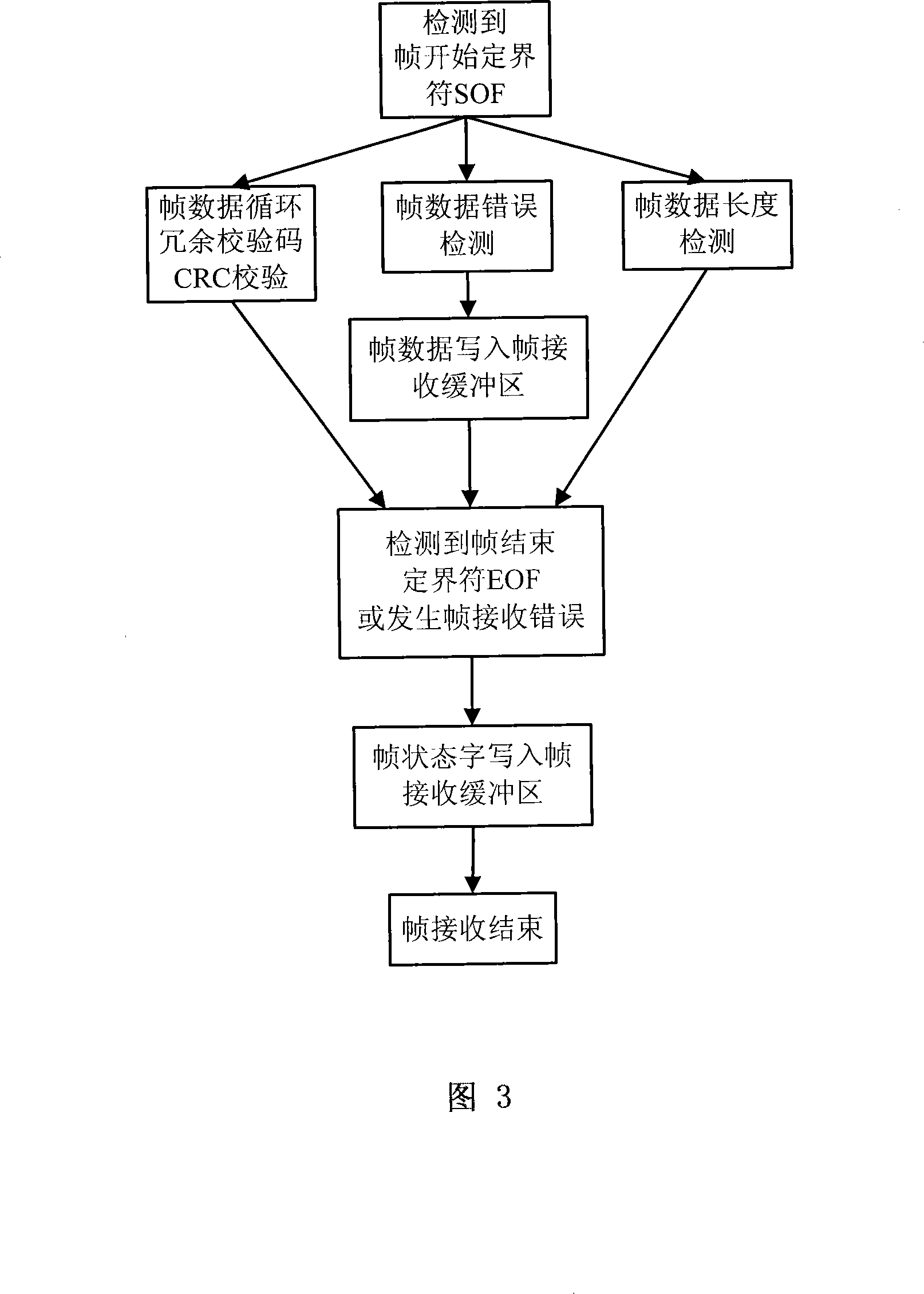
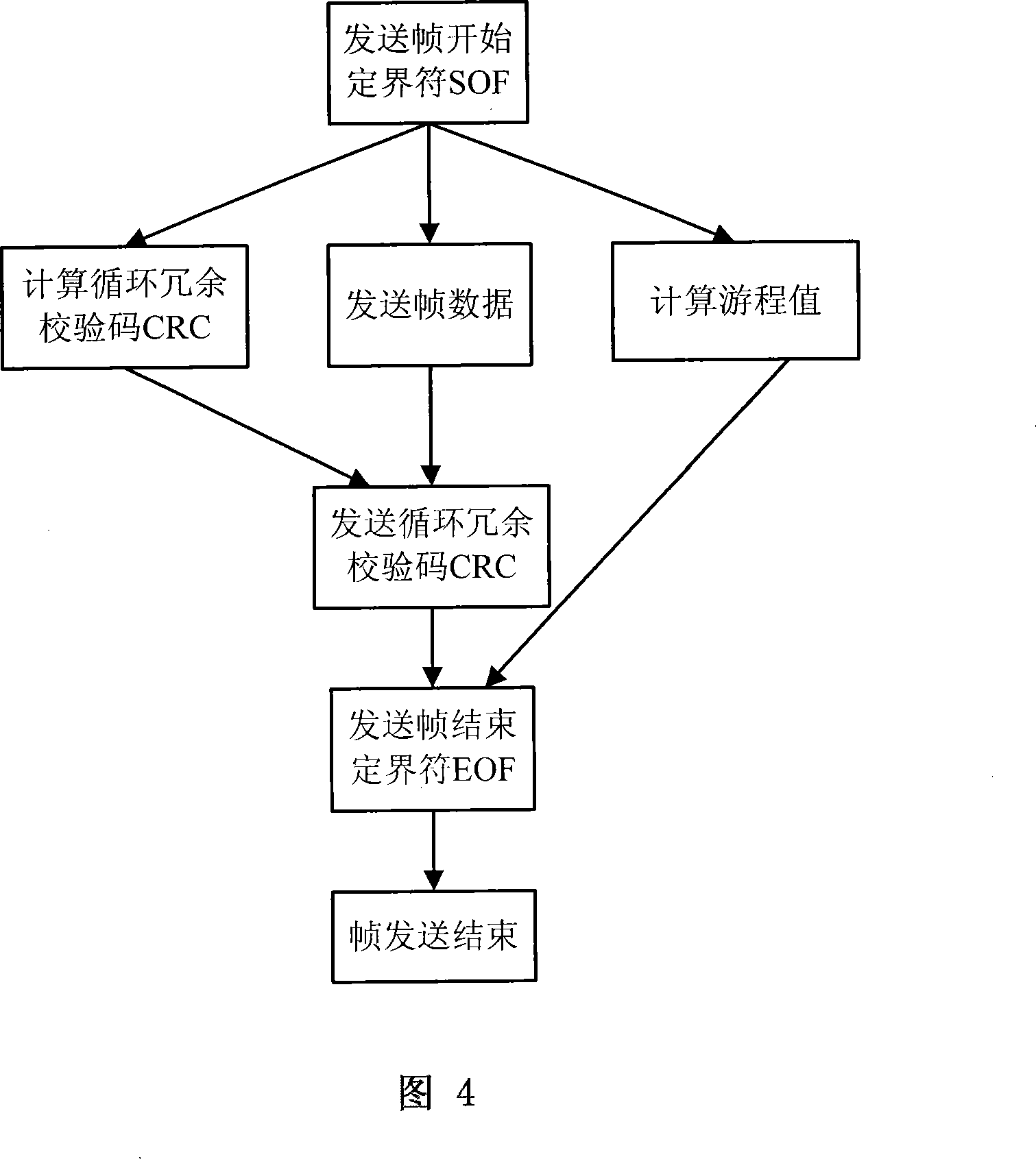
InactiveCN101175077AImprove collaborationFully configuredData switching networksFiberProcess function
The invention provides an intellectual property core of optical fiber channel, which pertains to the field of computer memory technology, resolves the imperfection of the function of the current intellectual property core, and realizes the protocol process function of FC-1 layer and the partial FC-2 layer of fiber channel. The invention comprises a 8b or 10 b decoder, a 8b or 10b coder, receiver state machine, a sending state machine, a fiber channel port state machine, a frame-receiving engine, a frame-sending engine, a frame-sending buffer area, a stream control module, configuration and a statistical module between buffer areas. The invention provides frame level user logical interface, adopts asynchronous FIFO queue as a frame-receiving buffer area and a frame sending buffer area, and provides perfect configuration and statistical function, thus improving the coordination capability of software and hardware.
Owner:HUAZHONG UNIV OF SCI & TECH
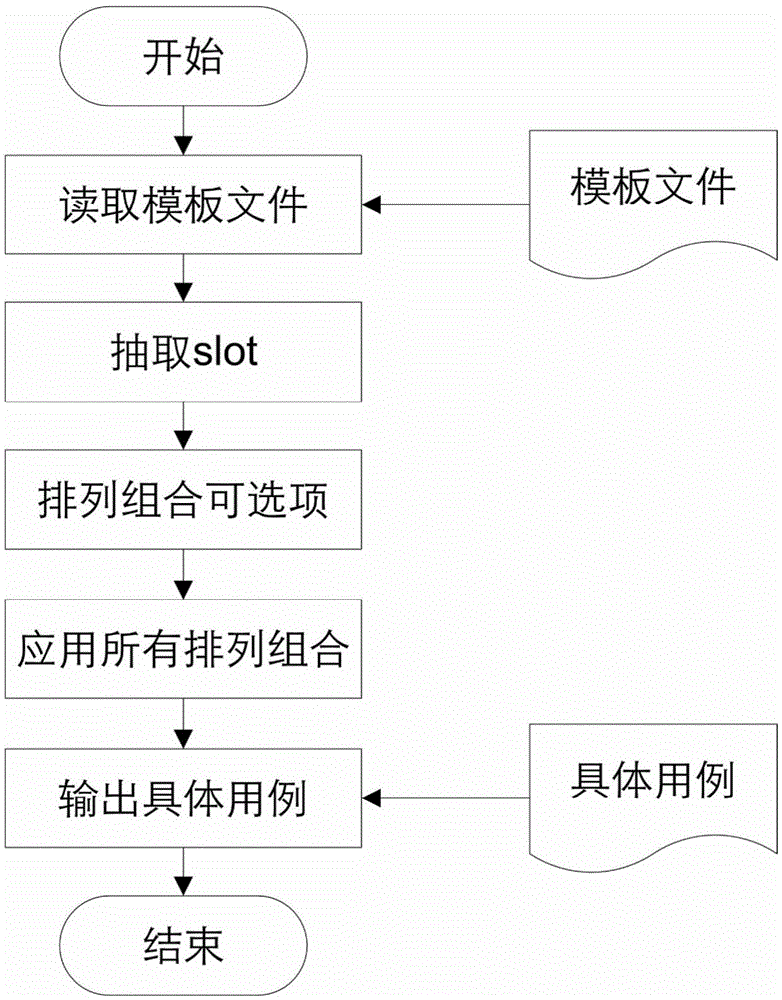
Test template for automatically generating test case according to preset rules and test method
InactiveCN105512036AAvoid duplication of workShorten the timeSoftware testing/debuggingSpecific testTest script
The invention discloses a test template for automatically generating a test case according to preset rules and a test method, and mainly relates to the field of databases. The test template comprises a parameter definition area and an execution step definition area, wherein parameters in the parameter definition area can be defined randomly, the execution step definition area assigns test scripts called by each step, each test script comprises a description function, a detail function and a process function, the description function is used for realizing output of summary information of the step, the detail function is used for realizing specific test steps executed in the step, and the process function is used for realizing the test process required to be executed in the step. According to the test template and the test method, the test case is automatically combined through an executable self-describing optional-parameter process, the test time can be greatly shortened, and manpower demand for a test is reduced.
Owner:TIANJIN NANKAI UNIV GENERAL DATA TECH
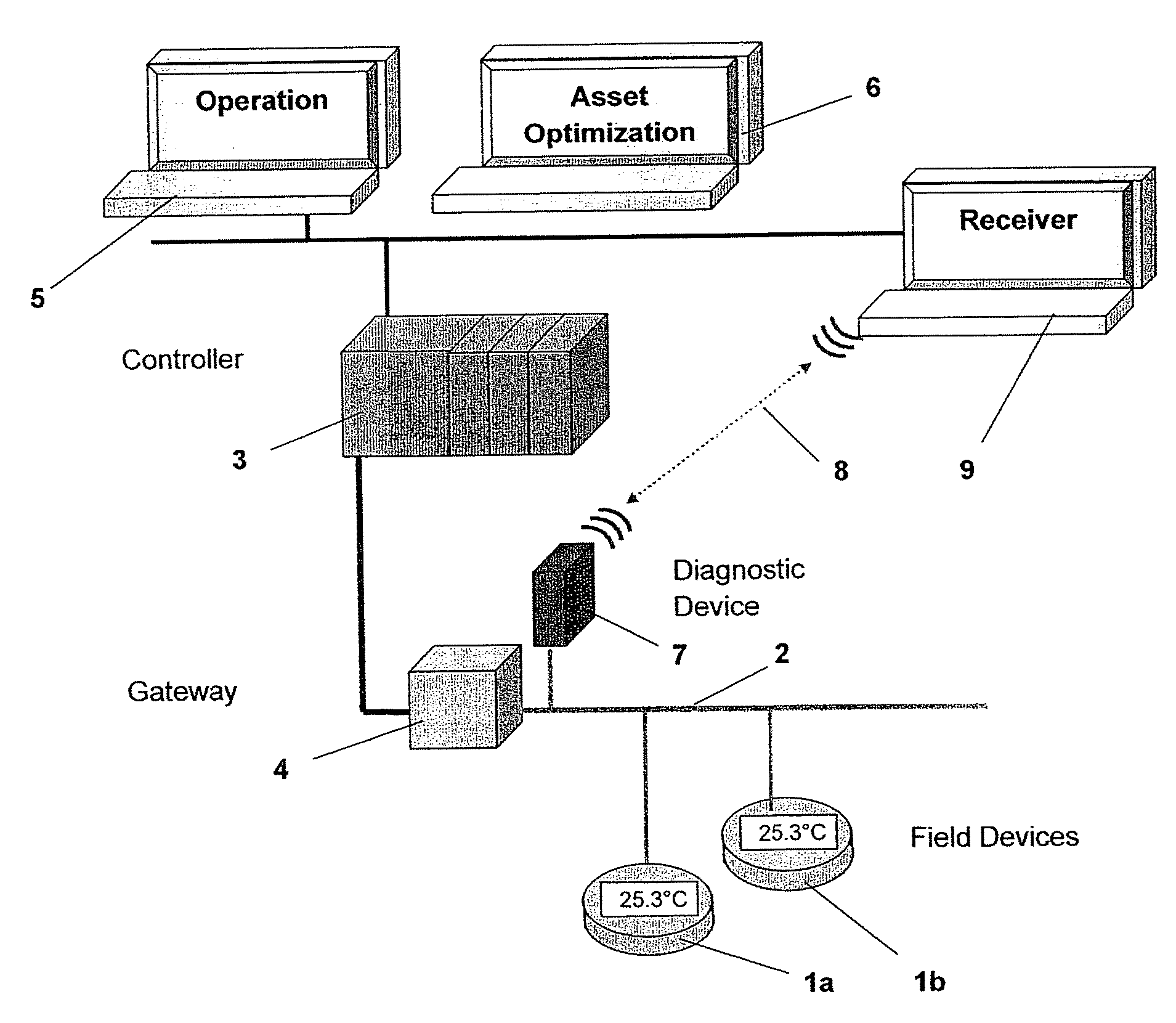
System and method for monitoring the data traffic on a fieldbus
InactiveUS20090018672A1Little technical complexityReliable monitoringError detection/prevention using signal quality detectorComputer controlProcess functionRadio channel
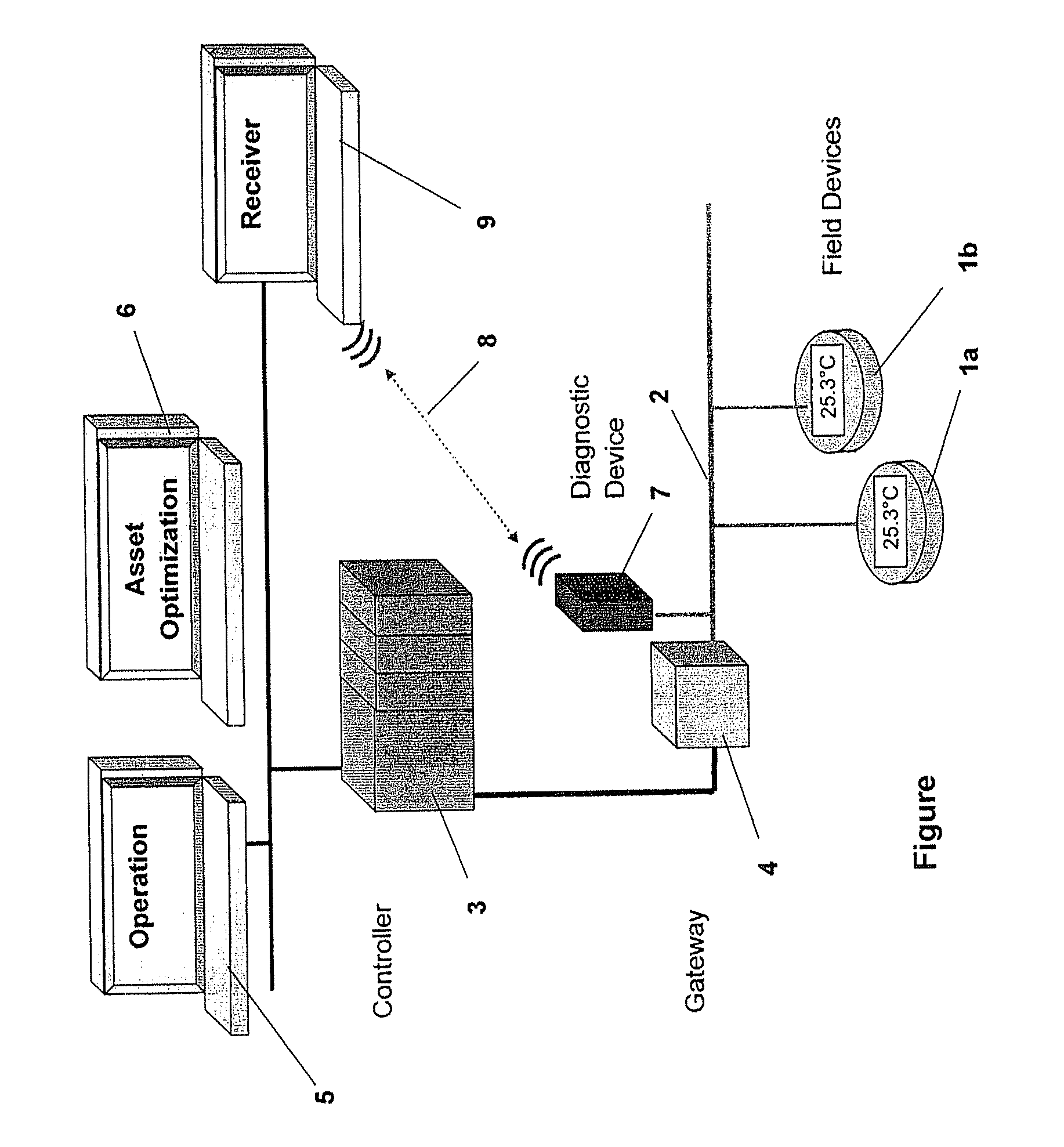
The disclosure relates to a device and a method for monitoring the data traffic on a fieldbus of a process automation system which comprises a plurality of field devices for carrying out a process function, which field devices can be controlled via at least one higher-level control unit, with a monitoring appliance for the data traffic and for passing on information contained in the data traffic to the higher-level control unit being connected to the fieldbus. The invention proposes that the monitoring appliance continuously records quality parameters of the data traffic and communicates them directly via a data radio channel to the level of the higher-level control unit which analyzes the quality parameters of the data traffic.
Owner:ABB (SCHWEIZ) AG
Multimedia home gateway and its implementation method for program recording, recovery, suspension
InactiveCN1972395APowerful data processing functionTelevision system detailsColor television detailsProcess functionOperational system
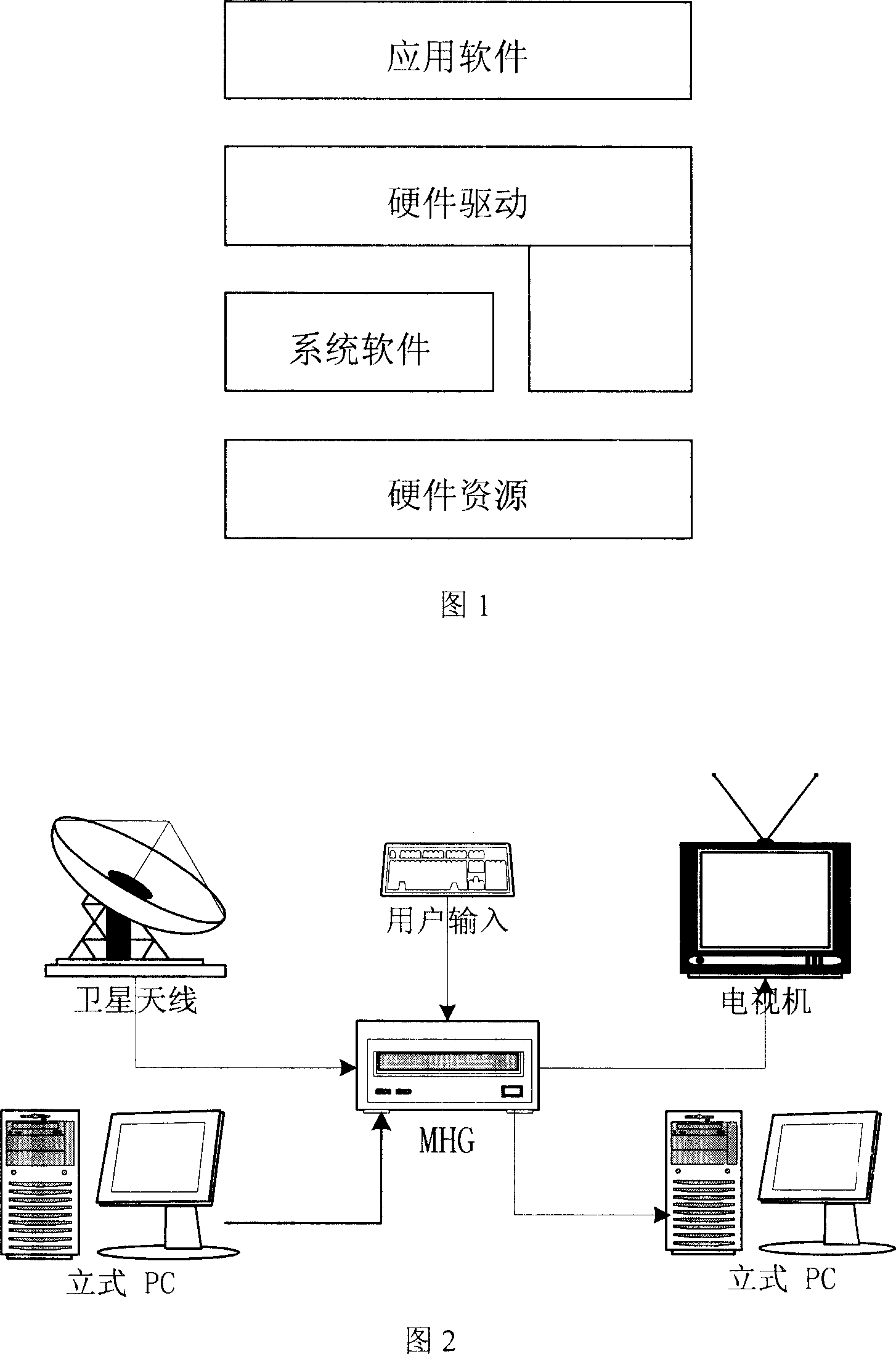
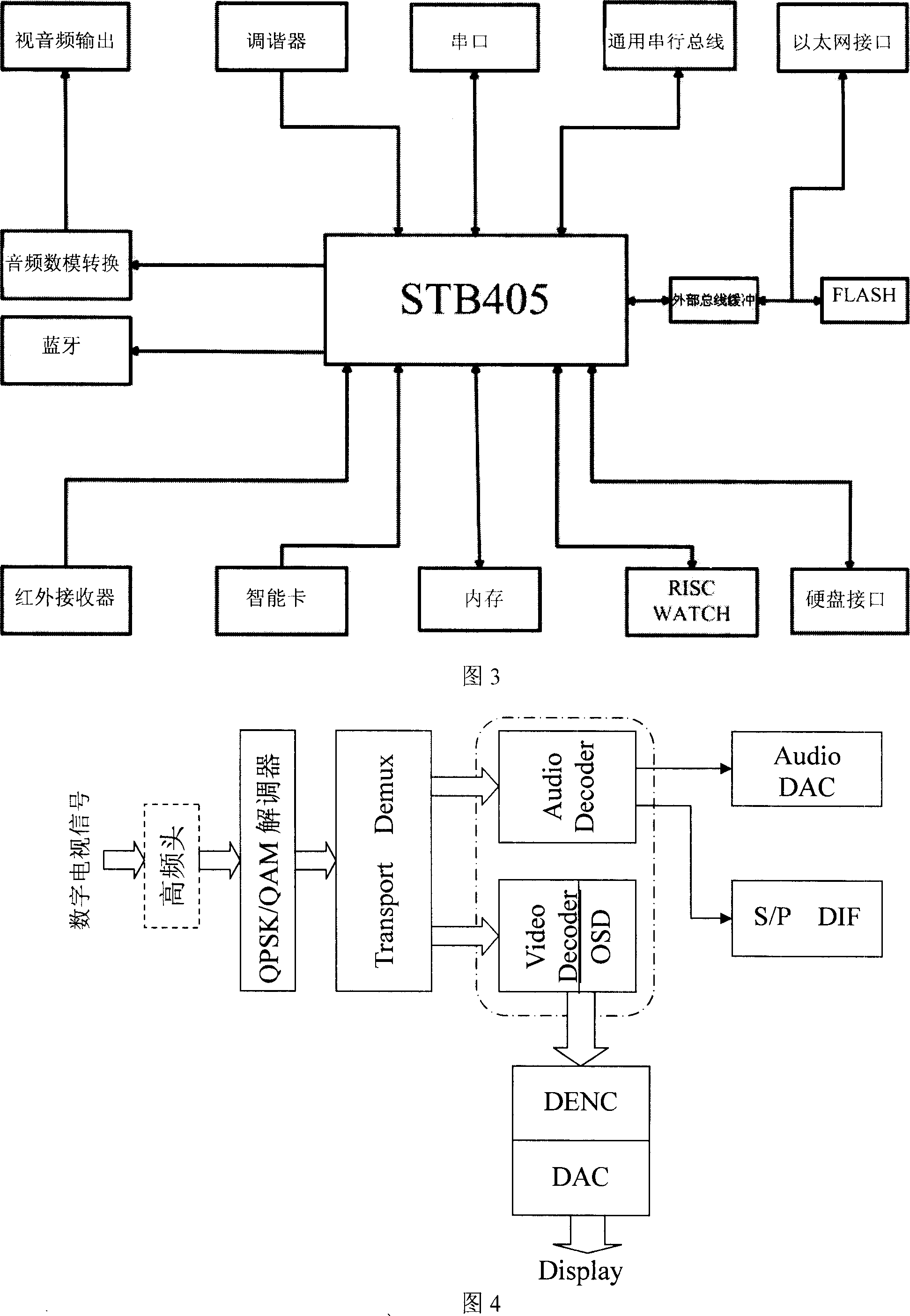
This invention relates to multi-media house network gate, which comprises the following parts: CPU, tuner, blue interface, AV output interface, FLASH memory with hardware initial codes and operation system core, Ethernet interface, infrared receiver, hardware, digital television receive module, record module, real-time program play back, step and pause module, multi-media management module, program index module, wireless connection module and middle parts. This invention adopts imbed operation system for strong data process function and establishes integral multi-media data process center for data transmission and memory.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
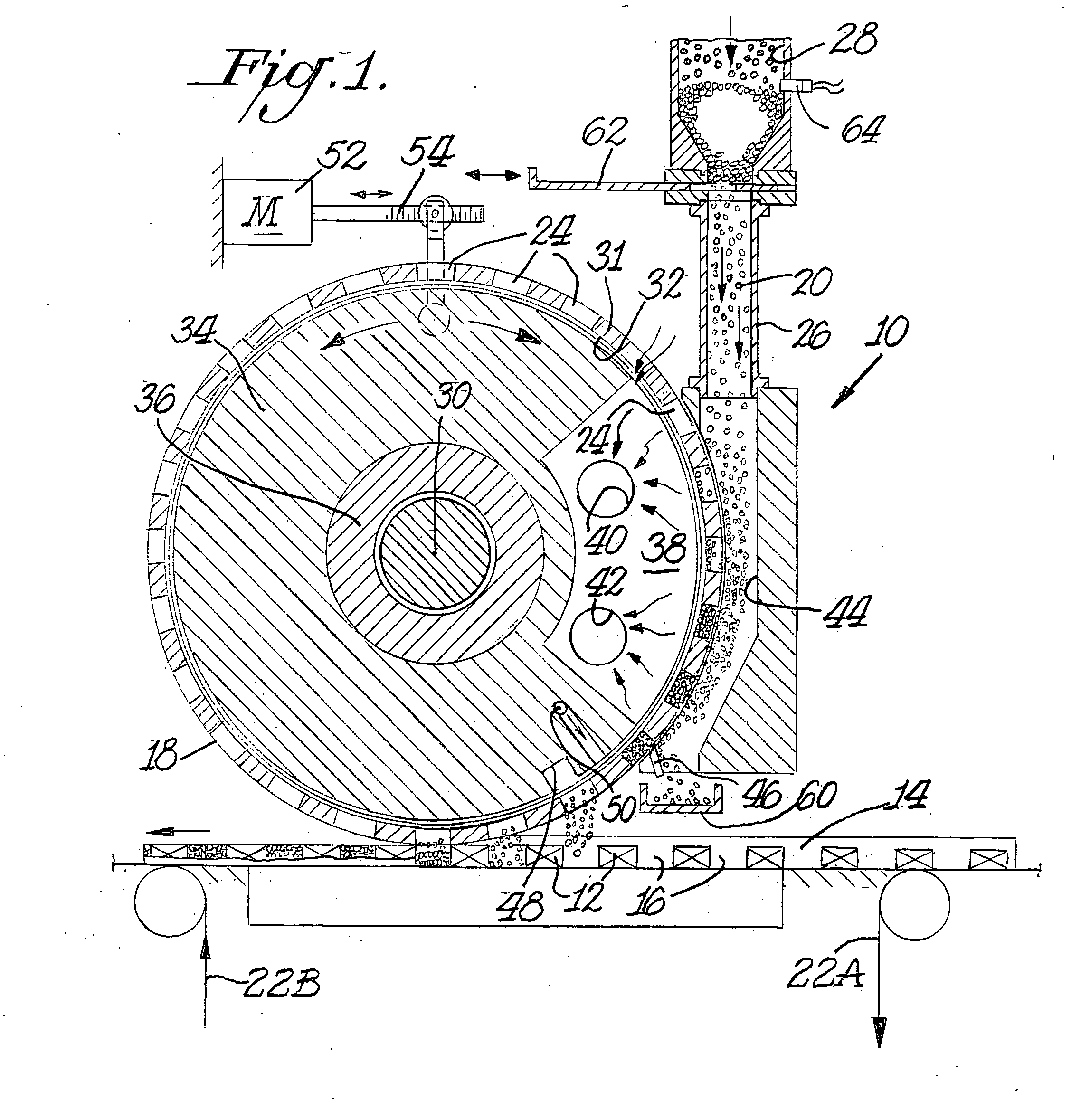
Applicator wheel for filling cavities with metered amounts of particulate material
A machine and process function to fill cavities with metered amounts of particulate material. An applicator wheel includes a series of equally spaced apart peripheral pockets each having a perforated bottom wall, and a vacuum manifold inside the wheel includes a vacuum chamber for supplying vacuum to the perforated bottom walls of the pockets as the wheel rotates. Particulate material from a filling chamber of such material outside the wheel is withdrawn into the pockets by the vacuum chamber. A downstream vacuum relief on the vacuum manifold functions to discharge particulate material from the pockets into the cavities at a predetermined discharge location on the wheel. Adjustment structure is connected to rotatably adjust the position of the vacuum manifold within the applicator wheel to thereby advance or retard the discharge location depending upon the speed of the machine.
Owner:PHILIP MORRIS USA INC
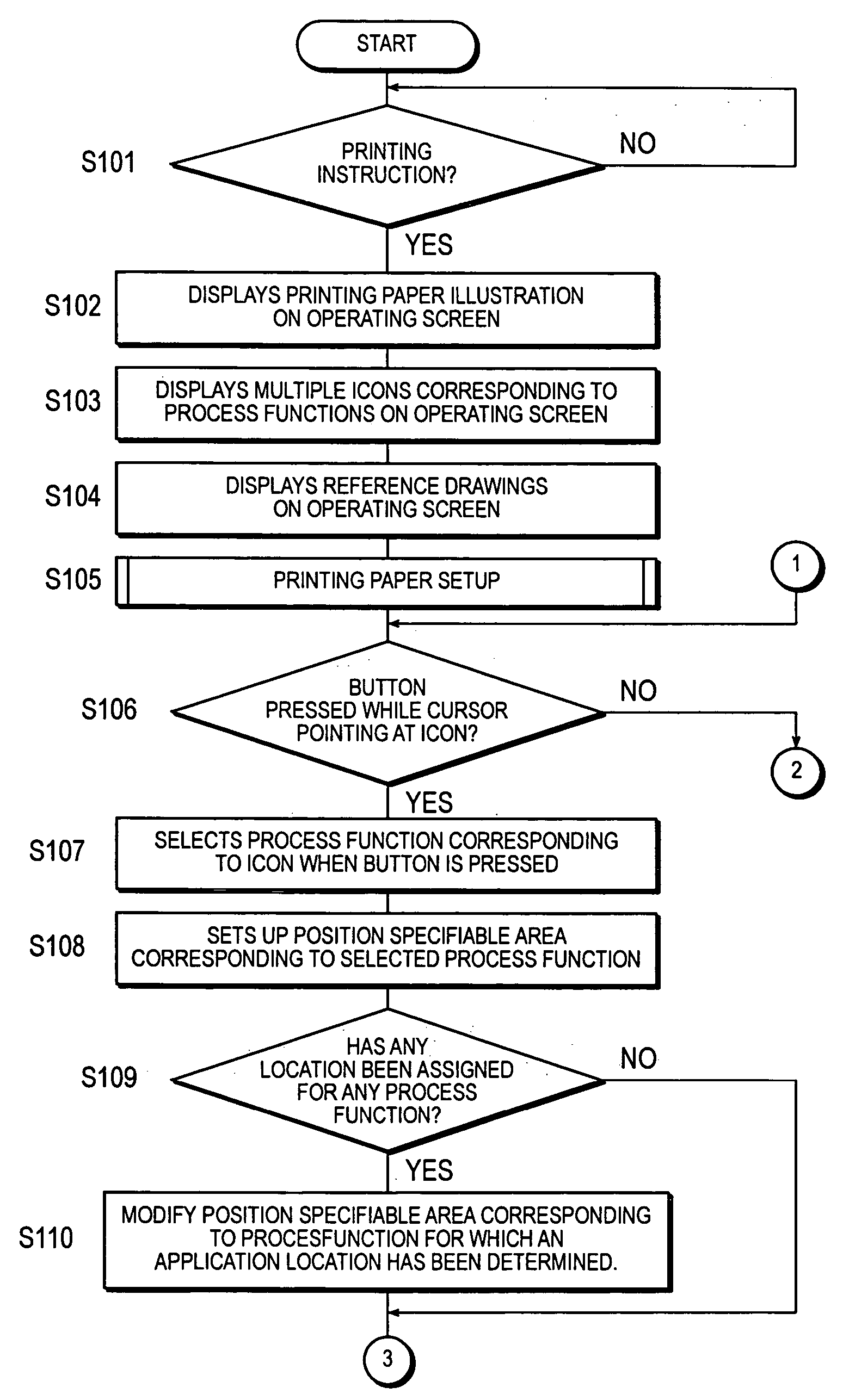
Controlling method for image forming apparatus
ActiveUS20060088331A1Reduce workloadEasy to operateElectrographic process apparatusInput/output processes for data processingProcess functionComputer graphics (images)
A controlling method for controlling an image forming apparatus has a step of displaying a prinnting paper illustration representing printing paper on an operating screen and a step of displaying at least one icon related to a process function of the image forming apparatus. The controlling method further has a step of selecting a process function that corresponds to the specified icon and a step of determining the location to which the selected process function is applied upon receiving an instruction for a position on the printing paper illustration.
Owner:KONICA MINOLTA BUSINESS TECH INC
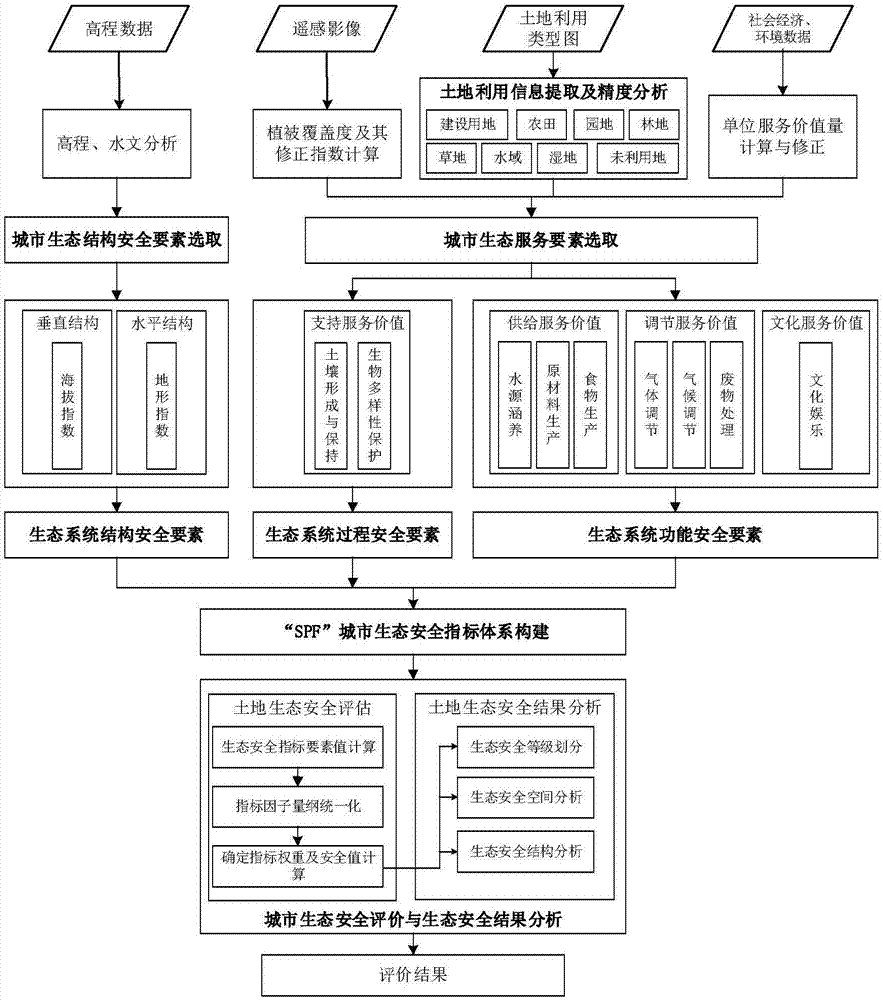
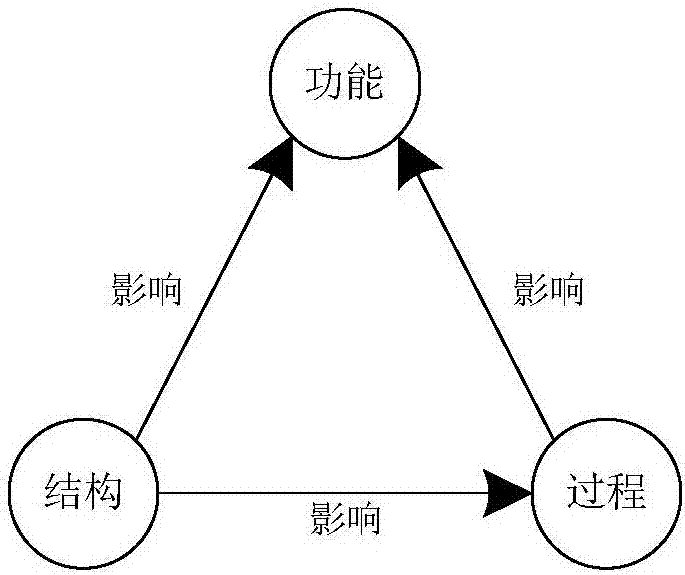
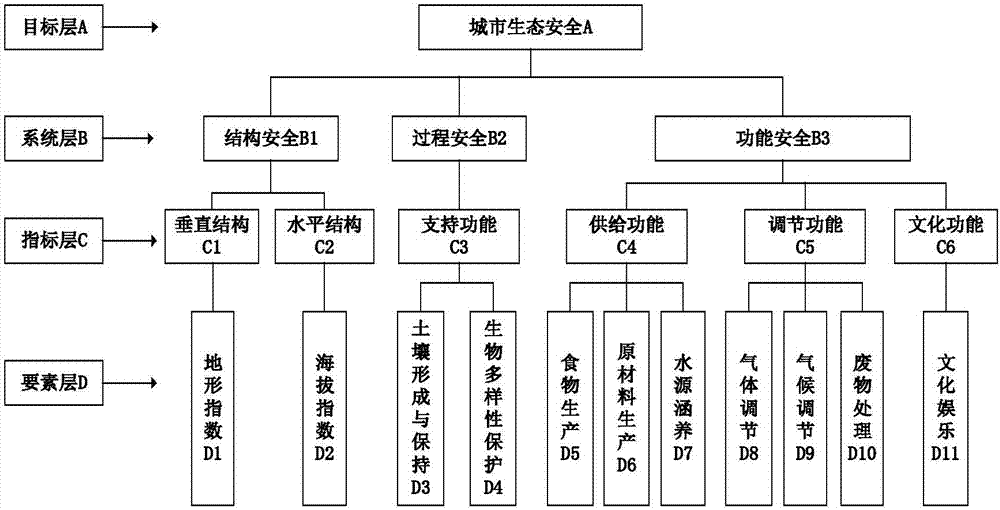
Structure-process-function model based urban ecology safety evaluation method
InactiveCN107194610AScientifically valid evaluationSimple calculationResourcesSafety indexProcess function
The invention discloses a method for evaluating urban ecological security based on a structure-process-function model, comprising the following steps: (1) constructing an ecological security index system by using the analytic hierarchy process; (2) using elevation data, remote sensing image data, land use Type data and socio-economic and environmental data calculate the value of each described ecological security index element in the element layer; (3) carry out dimensional unification to the value of each described ecological safety index element; (4) calculate each described The weight of the ecological security index element value; (5) by carrying out weighted summation to each described ecological security index element value to obtain the corresponding described ecological system comprehensive security value of the target layer; (6) according to the comprehensive The safety value divides the urban ecological security level. The calculation process of the method of the invention is simple, the parameters can be adjusted according to the actual situation, and the applicability is wide.
Owner:BEIJING NORMAL UNIVERSITY
Method for storing metadata of logic document system by adhesion property
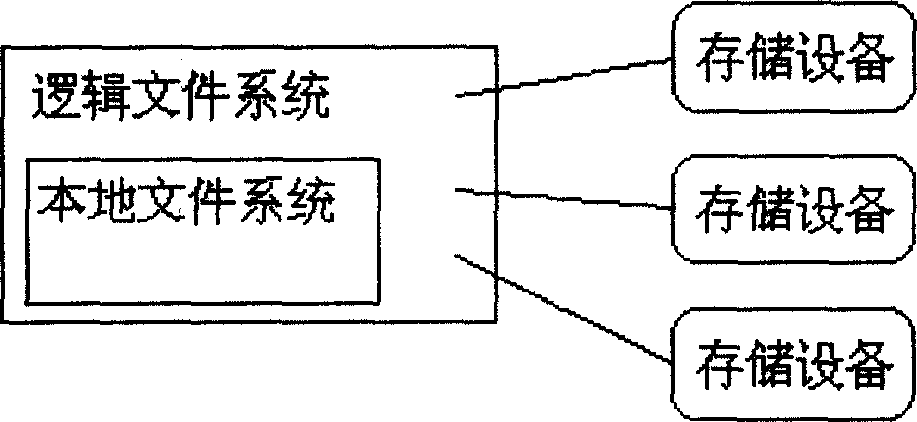
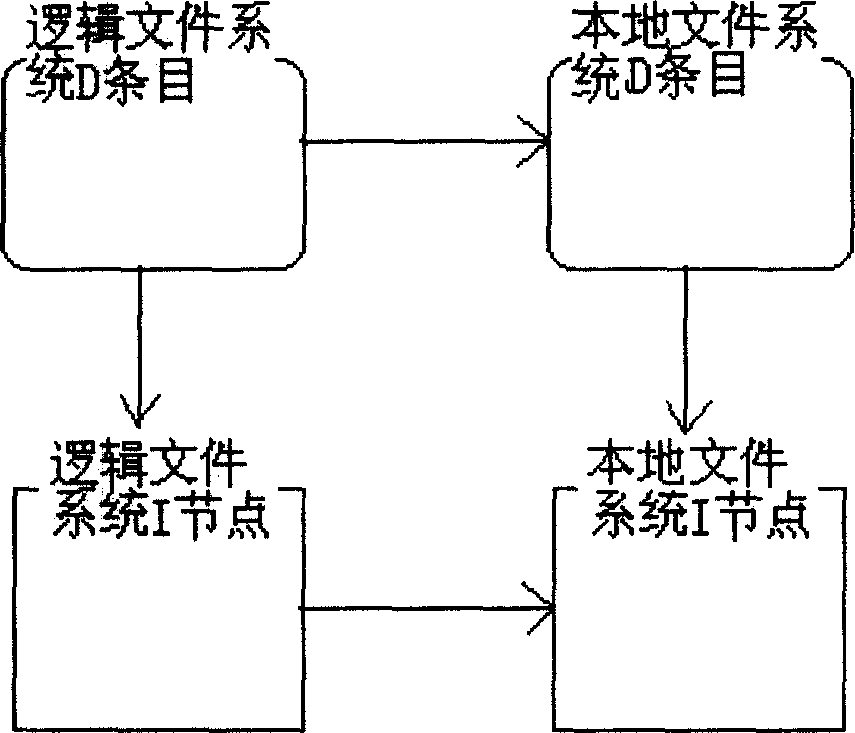
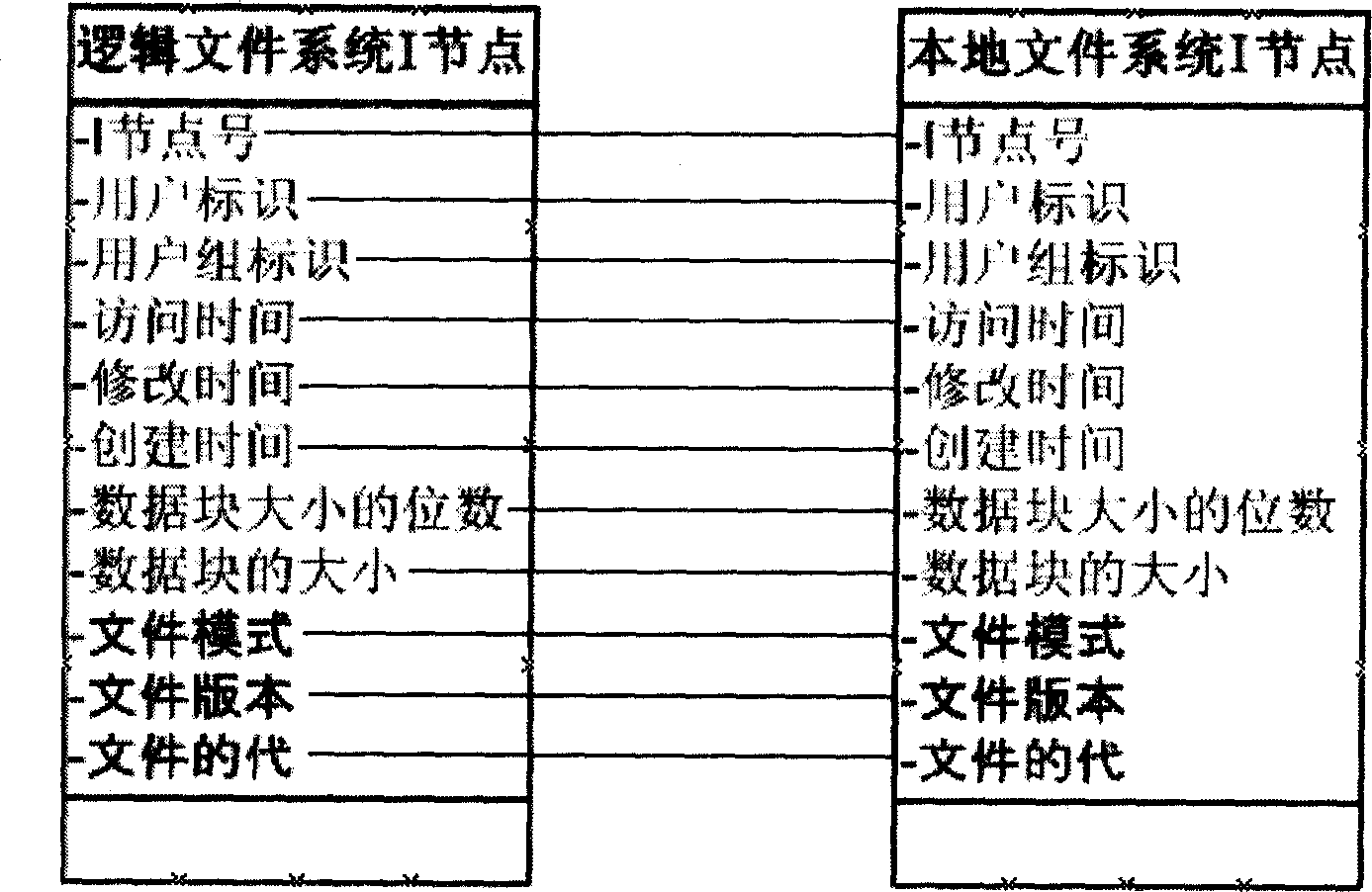
InactiveCN1904889AEasy to implementAdaptableSpecial data processing applicationsProcess functionFile system
The invention discloses a method to use adhering attribute storing logic file system metadata. It stores the metadata of logic file system on local file system as local file system file attribute. The method includes the following steps: creating file or catalog of the logic file system; deleting a file or catalog; modifying logic file system attribute; renaming the file or catalog on logic file system; acquiring the metadata of file or catalog on logic file system. By using the method, the logic file system could directly use the metadata process function by using the local file system to inhere the stability and performance of the local file system. It also has the advantages of easy to realize and strong adaptability.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
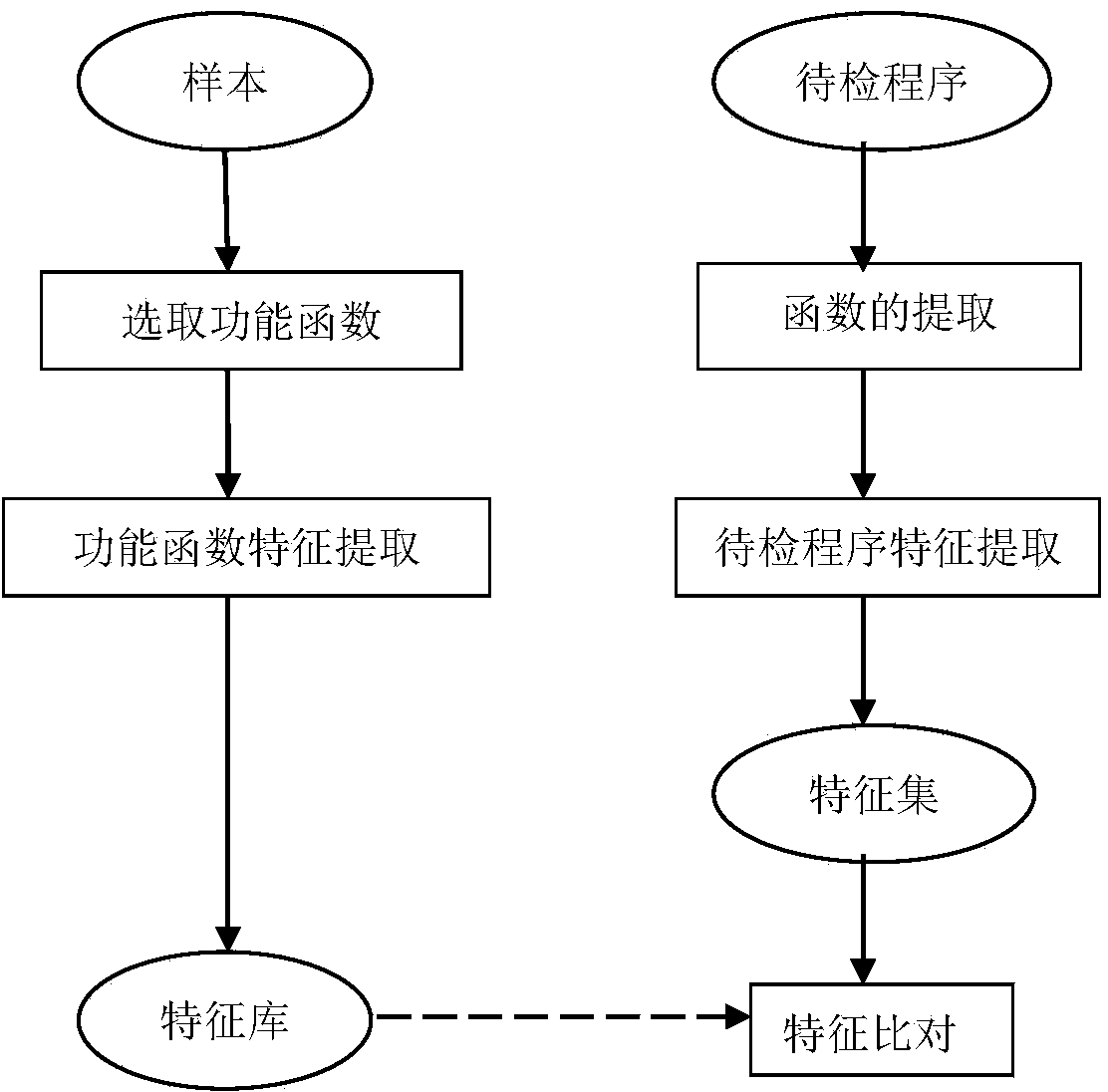
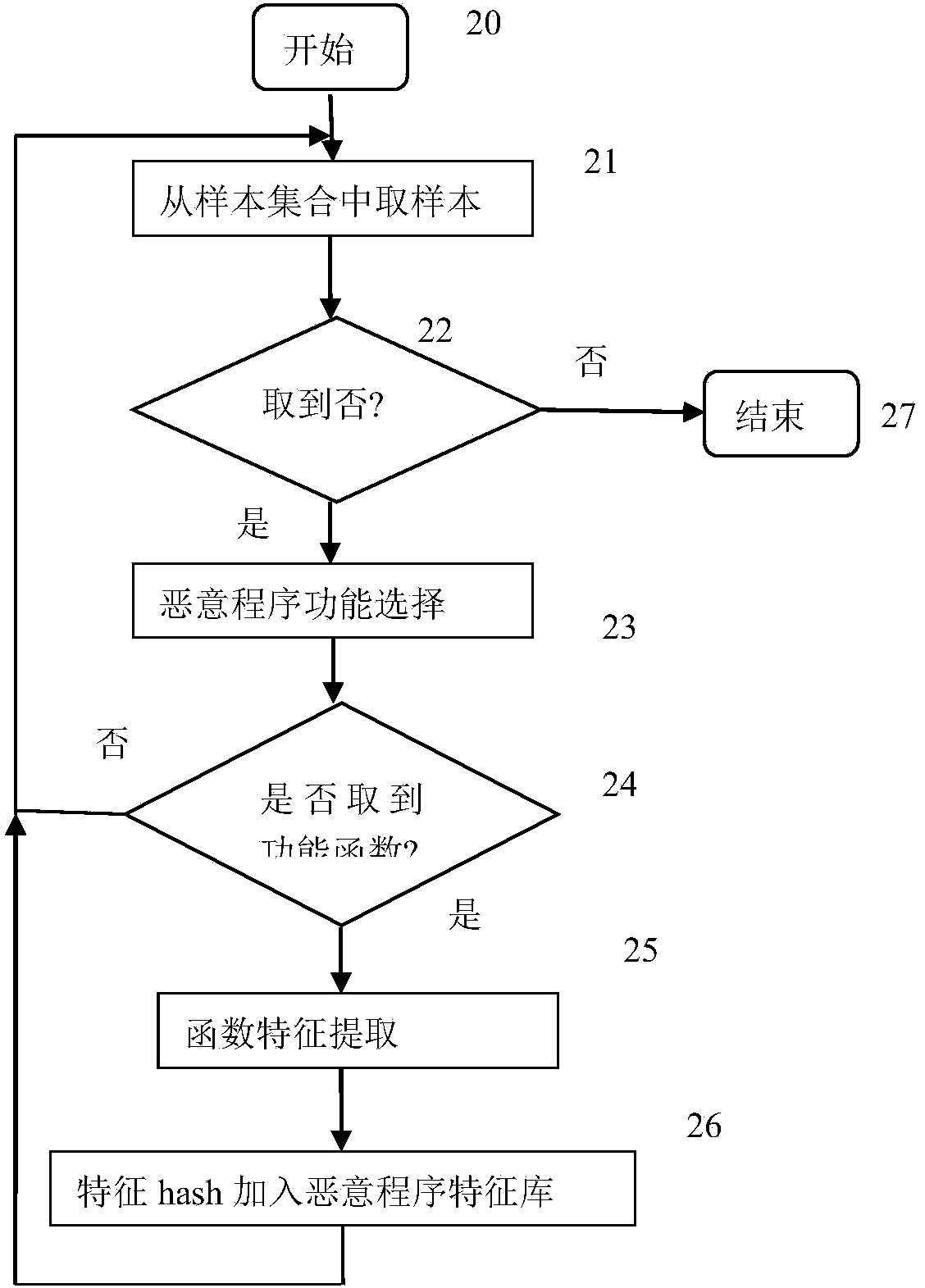
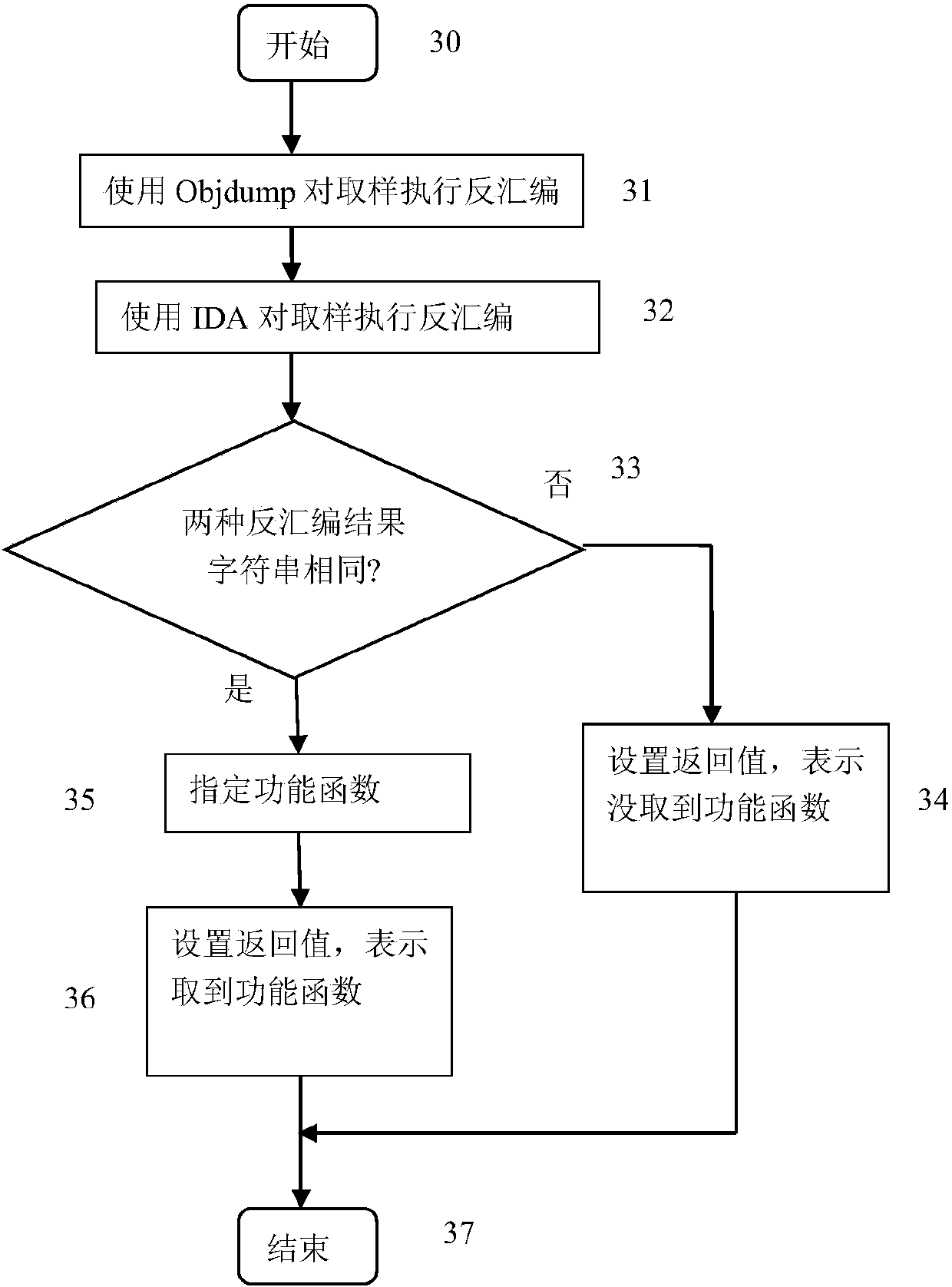
Malicious program detection method based on function characteristics
The invention provides a malicious program detection method based on function characteristics. The malicious program detection method includes the steps of (1) selection of performance functions of malicious programs, namely selecting malicious program samples, carrying out disassembling and manual analysis and specifying functions closely related to malicious behaviors as the performance functions, (2) extraction of function characteristics, namely processing function body codes of the functions closely related to malicious behaviors, removing interference instructions, identifying conditional judgment statements and loop statements, and converting all the statements into equivalent expression forms as the function characteristics, (3) establishment of malicious program characteristic library, namely establishing a malicious program characteristic library as a malicious program model by using the function characteristics of the performance functions of all the malicious program samples and by using of a malicious program sample library; and (4) detection of malicious programs, namely analyzing a function characteristic set of all functions of a program to be detected by using the malicious program characteristic library, and determining whether the function characteristic set is consistent with a characteristic model in the malicious program characteristic library or not to identify whether the program to be detected is the malicious program or not.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com