Malicious program detection method based on function characteristics
A technology of malicious programs and detection methods, applied in the field of identification and detection of malicious programs, can solve the problems of no longer effective detection mechanism, false negatives, wrong detection results, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below in conjunction with the accompanying drawings.
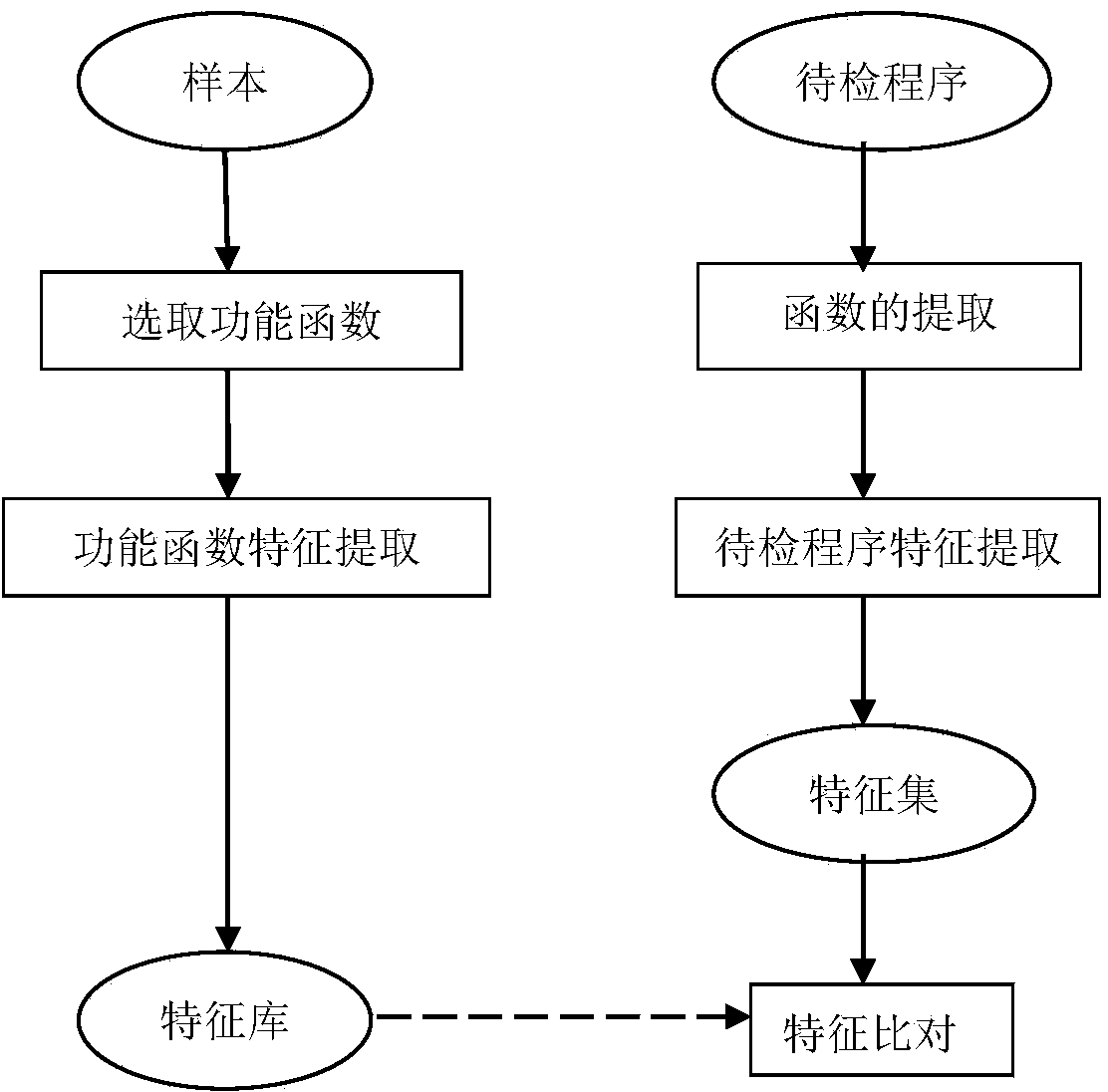
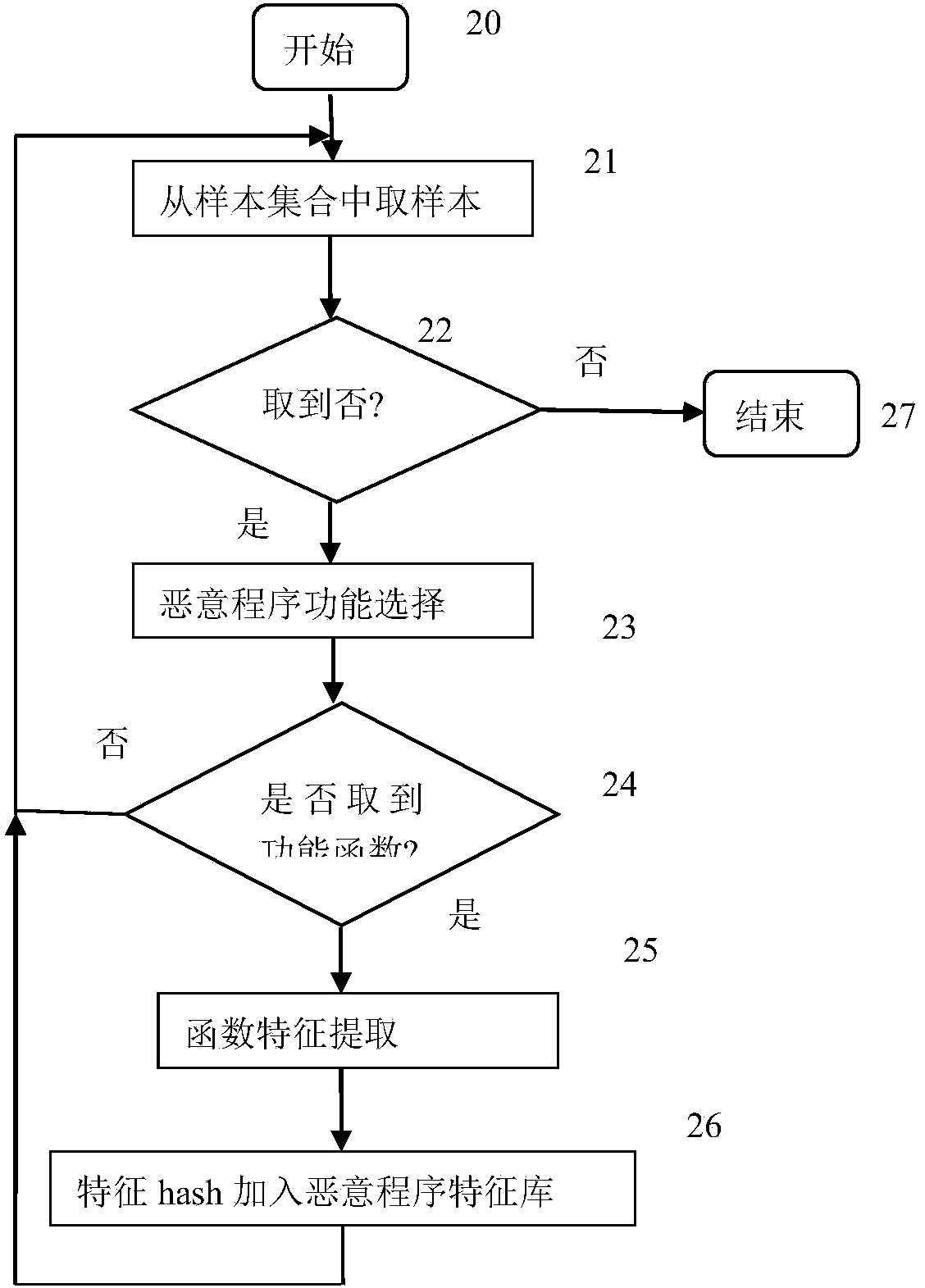
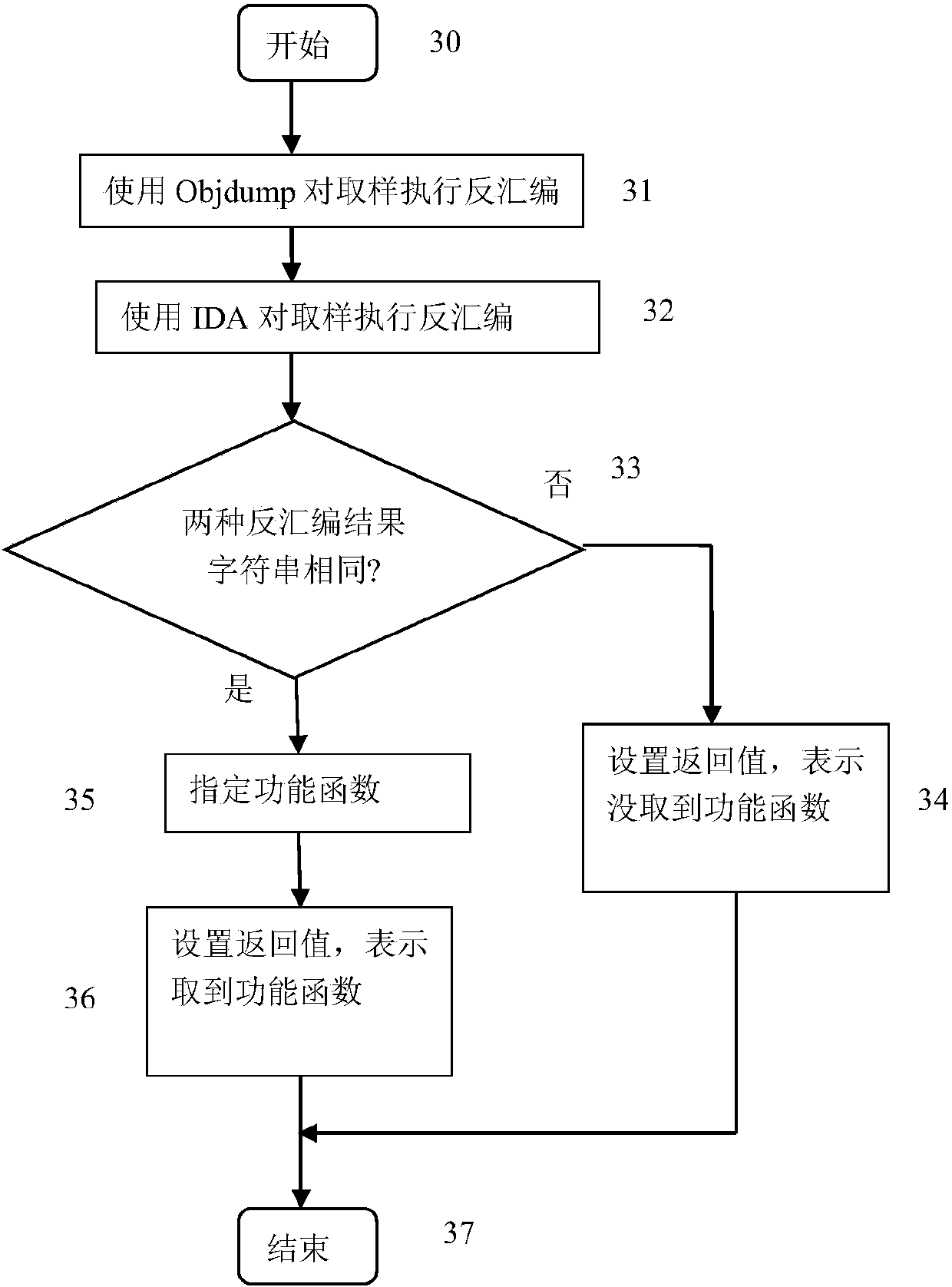
[0021] figure 1 Shown is the overall flow and working principle of this method implementation. Malicious program samples are a collection of malicious program samples collected for training, and have been named and classified according to specifications. A pending program is an unknown application program that is pending determination. Select malicious program samples from the malicious program sample set, manually select function functions, extract function features from function functions, and add them to the feature library. After the training process is over, a malicious program feature library is established. For checked programs, extract all functions. After these functions are preprocessed, deobfuscated, conditional statement and loop statement processing, and nested call processing, their function feature set is obtained. Compare the function features of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com