Privacy leakage vulnerability detection confirming method based on static stain data analysis
A tainted data, static technology, applied in the field of privacy leak detection, can solve problems such as affecting vulnerability recurrence, difficulty in finding input data, detecting anomalies, etc., to reduce complexity and memory requirements, improve detection speed and accuracy, and reduce memory. the effect of demand
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in detail below in conjunction with the accompanying drawings.
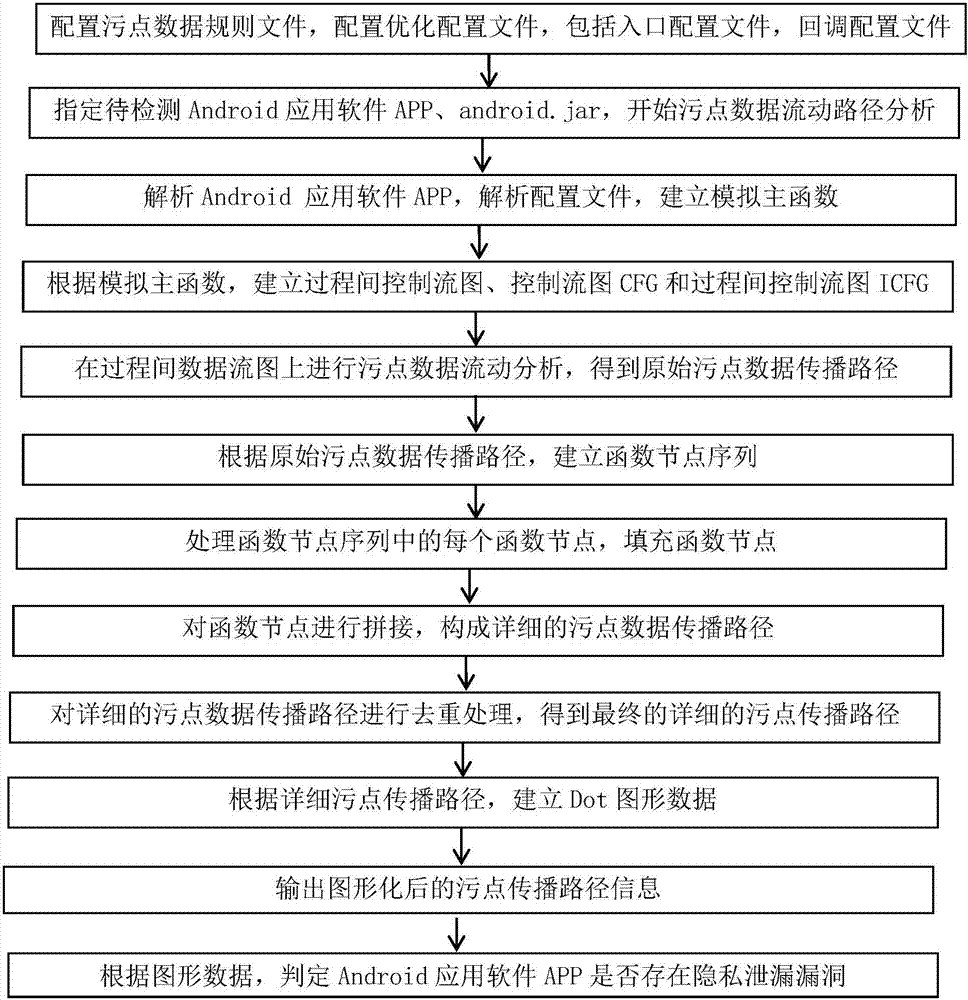
[0045] refer to figure 1 , the implementation steps of the present invention are as follows:
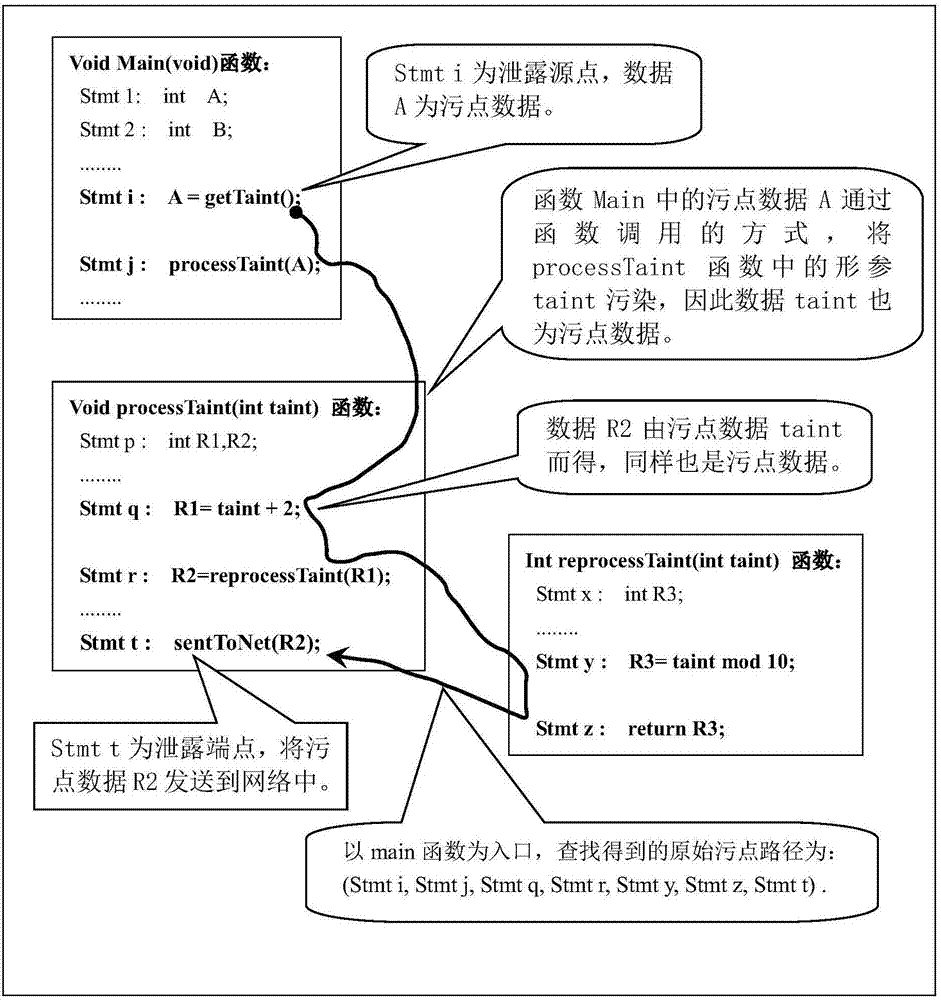
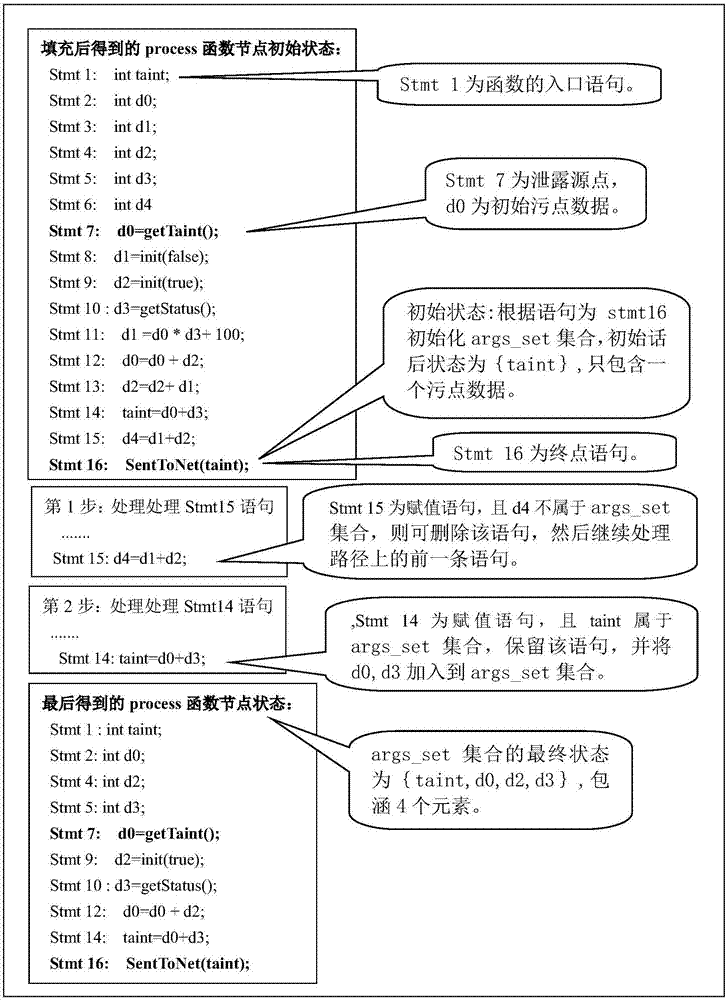
[0046] Step 1, find the tainted data flow path.
[0047] 1a) Configure the tainted data rule file, the configuration method is to specify the function signature and target endpoint function signature that introduces tainted data;
[0048] 1b) Configure the entry configuration file. The components in the configuration file are the components to be tested. When configuring the file, a configuration file can be automatically generated first. This configuration file contains a list of all components in the Android application software APP. Modify and customize the configuration on the basis of the automatically generated configuration file; the automatic generation of the configuration file can be carried out before detecting the Android application program APP, which belongs t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com