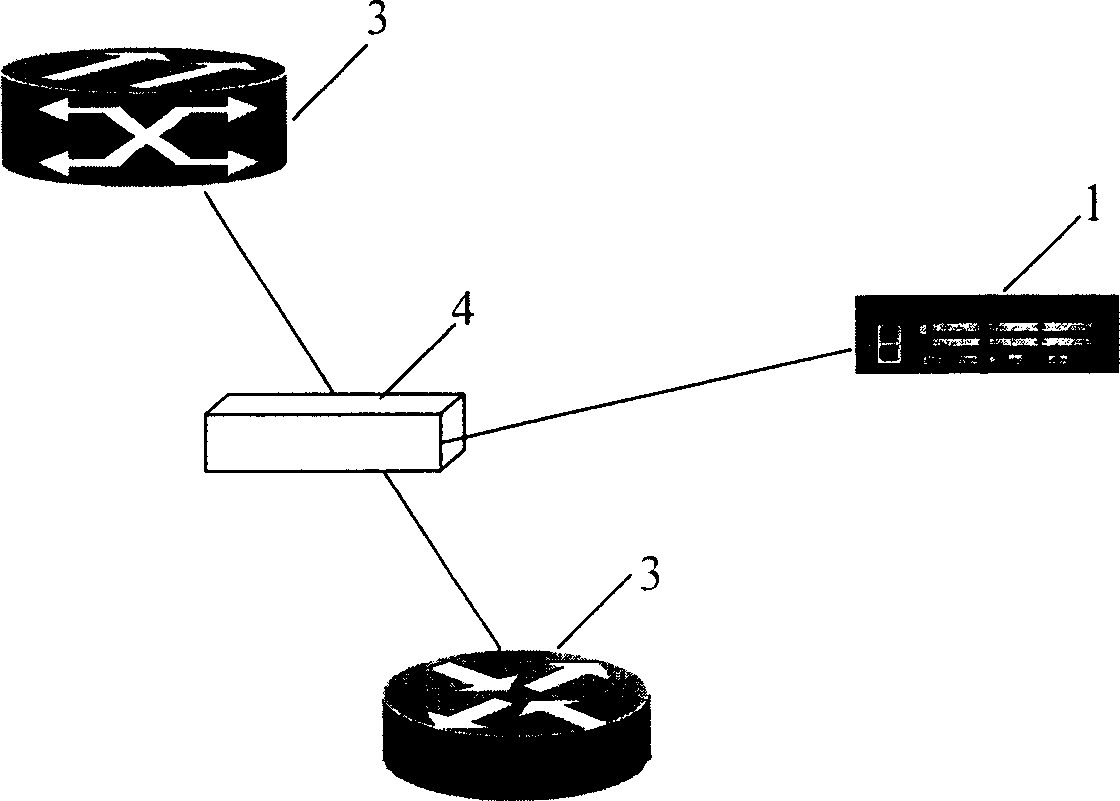
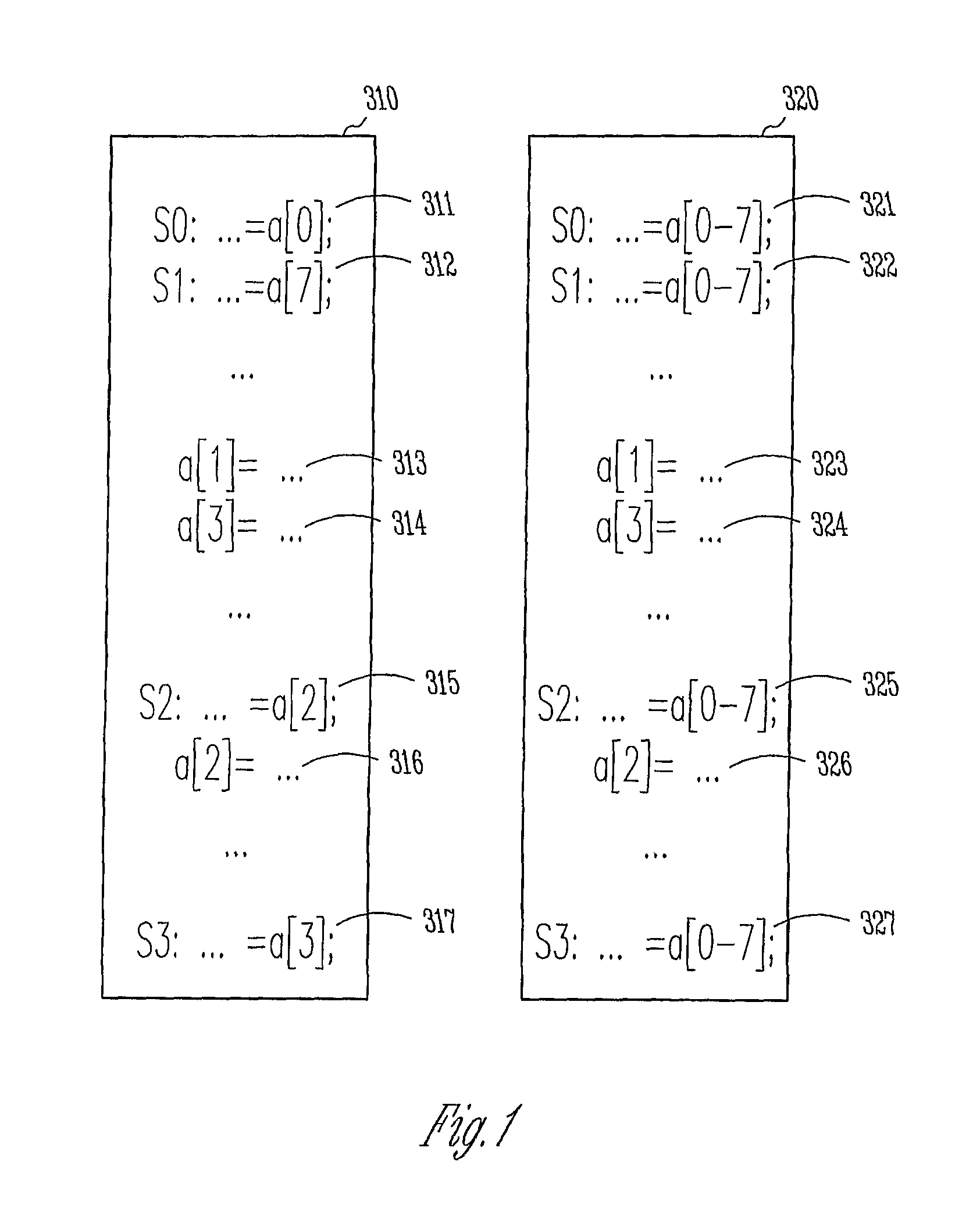Patents
Literature
81 results about "Data stream analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Streaming data is an analytic computing platform that is focused on speed. This is because these applications require a continuous stream of often unstructured data to be processed. Therefore, data is continuously analyzed and transformed in memory before it is stored on a disk.
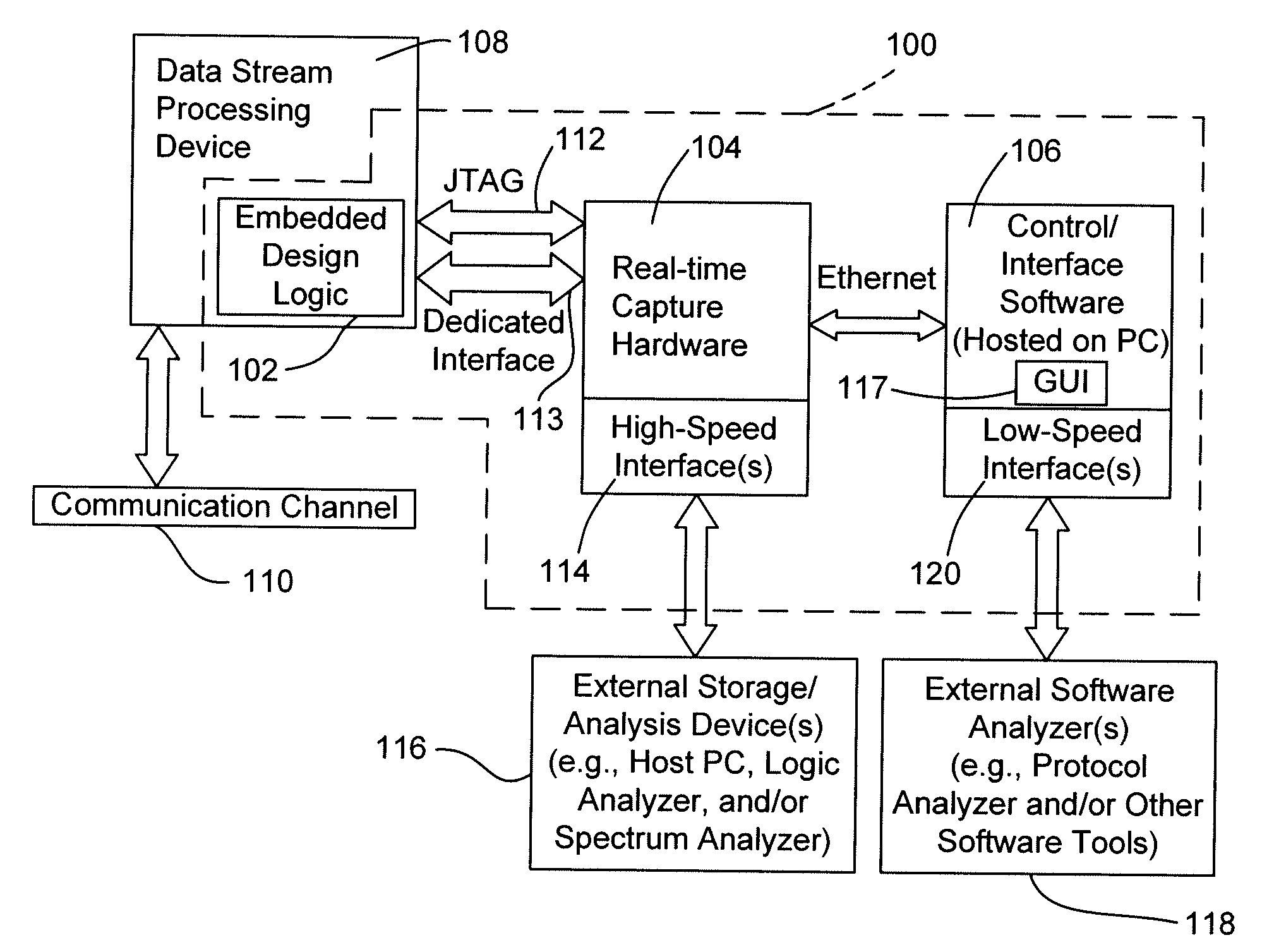
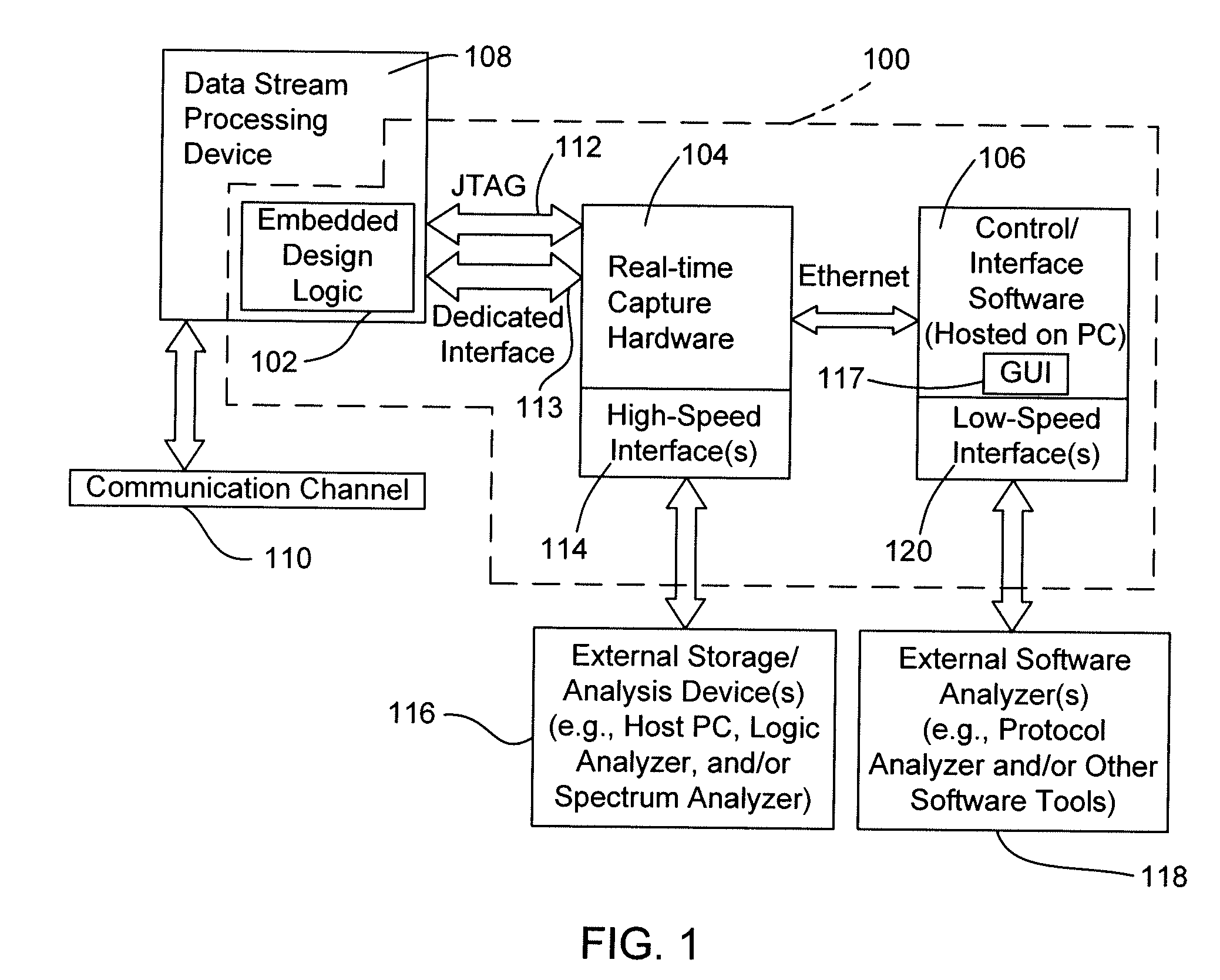
Systems and methods for data stream analysis using embedded design logic
Systems and methods are provided for analyzing a data stream device at a packet level. In one embodiment, design logic is embedded within a target data stream processing device such as a networking device or video device. The embedded design logic is configured to start and stop the target data stream processing device and to inject data into the target data stream processing device for evaluation. The embedded design may also be configured to detect a user selected data value in a packet within the target data stream processing device before the packet is transmitted through the device's physical layer or passed up the device's networking stack. In addition, or in another embodiment, at least a portion of the design logic, including the ability to detect the user selected value in the packet, may be located external to the data stream processing device. In one embodiment, a controlled client / server interfaces with the physical layer of the target data stream processing device and provides packet-level analysis of the data stream.
Owner:PACKET PLUS
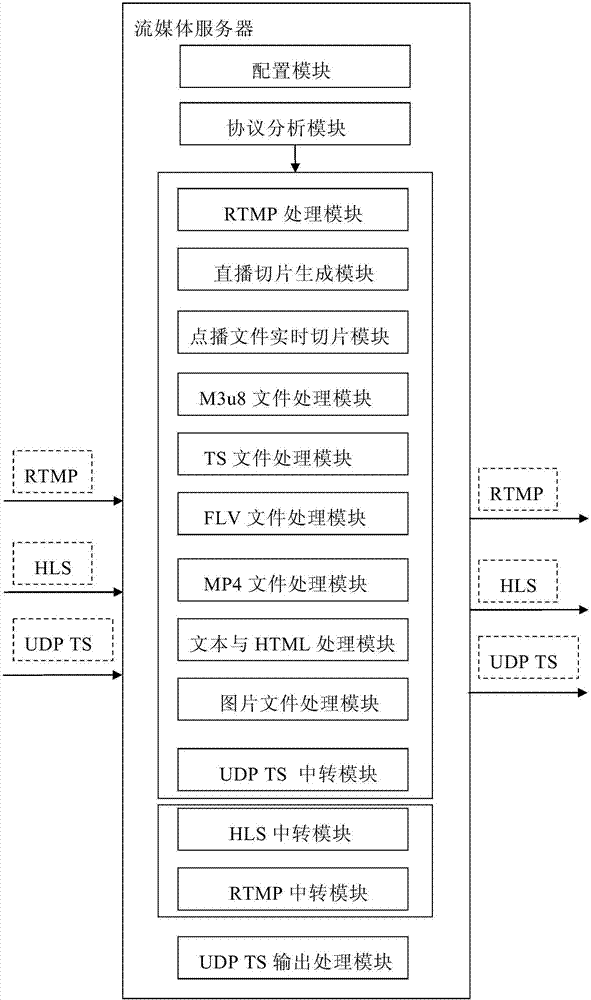
Streaming media server system supporting multi-protocol input and output
ActiveCN107222484AImprove experienceImplement adaptive playbackTransmissionMulti protocolMedia server
The invention discloses a streaming media server system supporting multi-protocol input and output. The streaming media server system comprises a protocol analysis module and a data stream analysis processing module; an access rule of a request message sent by a client is defined, the request message comprises the protocol type, the application type, the publishing point and the file name of a request, the application types comprise live broadcast and on-demand broadcast, and for a on-demand broadcast application, the request message further comprises a physical path corresponding to a request file; the data stream analysis processing module comprises an RTMP processing module, a live broadcast fragment generation module, a on-demand broadcast file real-time fragmentation module, an M3u8 file processing module, a TS file processing module, an FLV file processing module and an MP4 file processing module; the protocol analysis module is used for conducting analysis processing on the received request message according to the access rule and sending the request message to the corresponding data stream analysis processing module to be subjected to corresponding process according to an analysis result. The streaming media server system supports streaming media data broadcast of multiple terminals.
Owner:北京经纬中天信息技术有限公司
Privacy leakage vulnerability detection confirming method based on static stain data analysis
ActiveCN106940773ASmall scaleSolve the detection speed is slowDigital data protectionPlatform integrity maintainanceProcess functionSoftware engineering
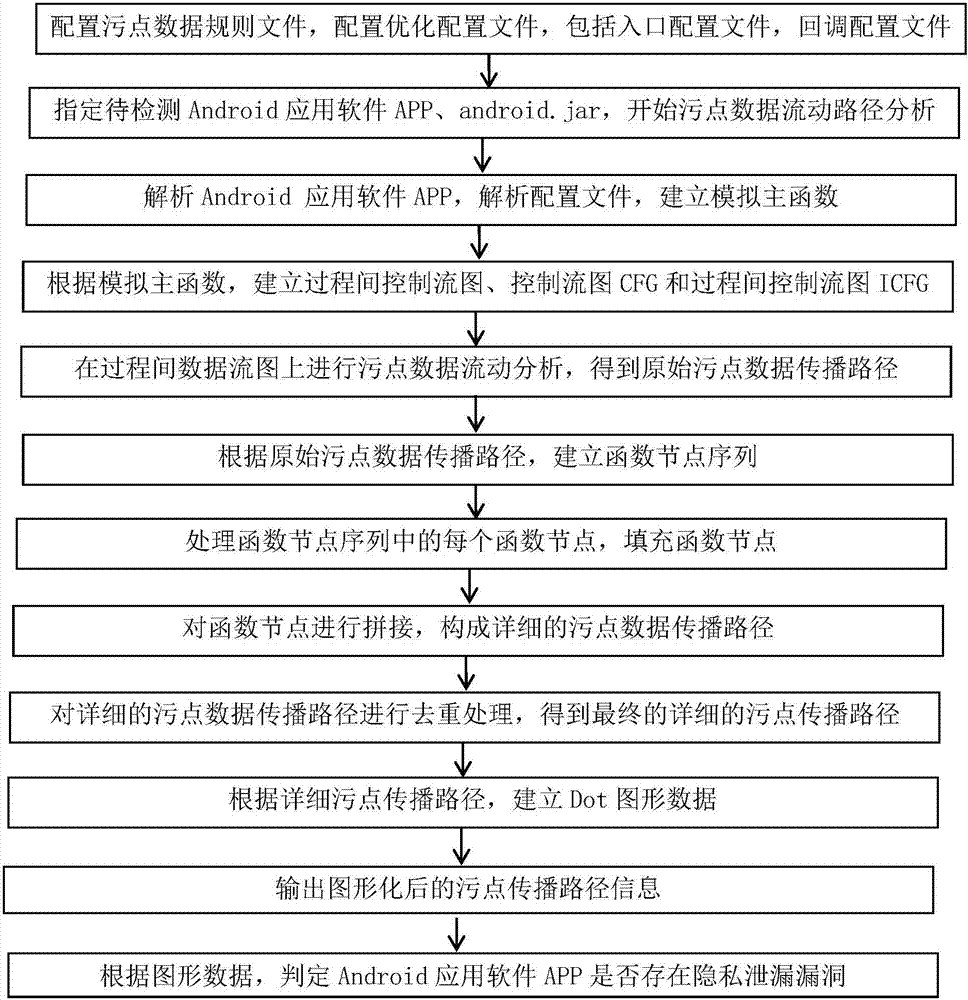
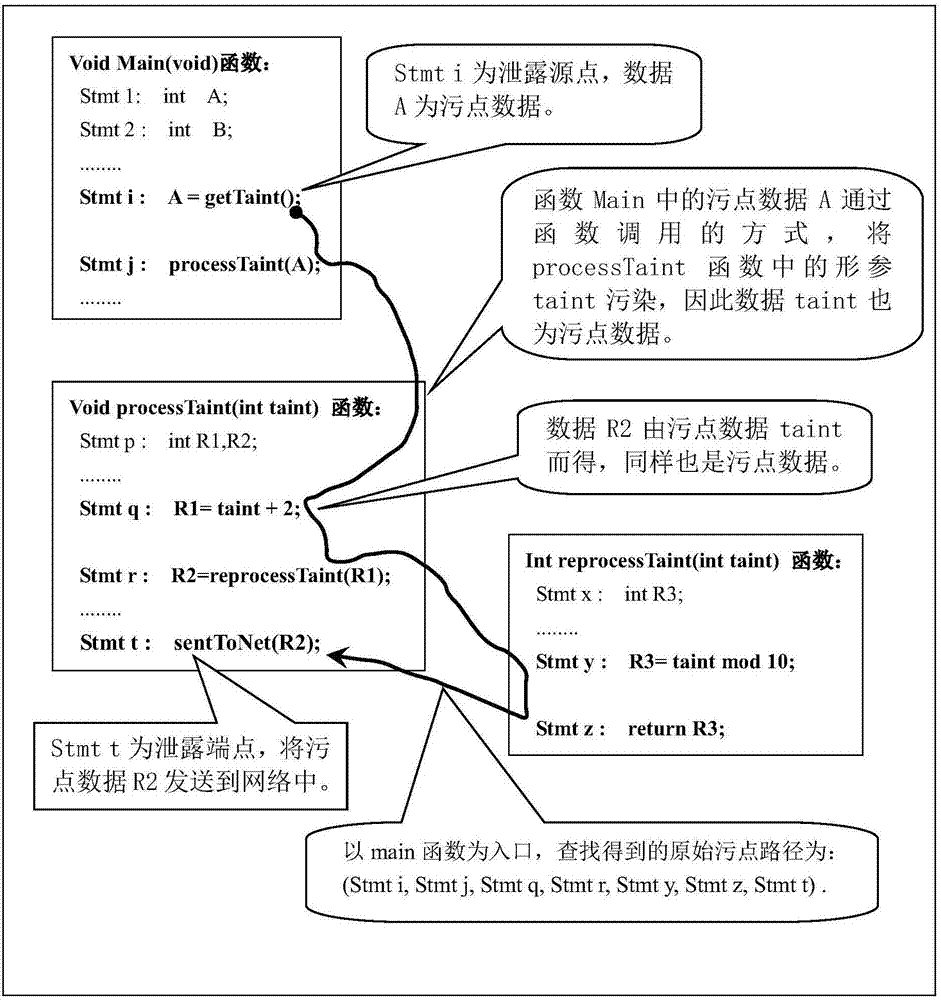
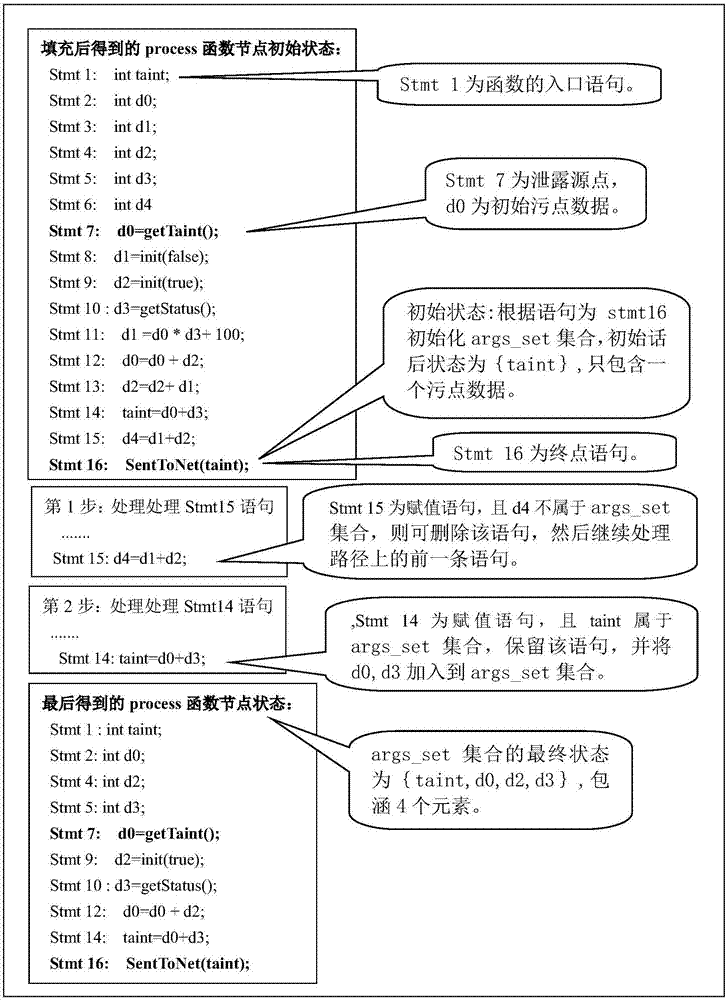
The invention discloses a method for detecting whether privacy leakage vulnerability exists in an Android application software APP or not. The method mainly solves the problems of low vulnerability detection speed, high detection environment requirements and low detection accuracy in the prior art. The method comprises the realization processes of configuring an optimization detection file; limiting an assembly and callback of the detected Android application software APP; performing static stain data stream analysis on the limited assembly and callback to obtain a stain data stream path; further processing the stain path, building a function node sequence; expanding and filling with function nodes, performing pruning and compression processing, and connecting the processed function nodes to form a detail stain data flowing path; performing deduplication processing on the detail stain data flowing path; then, performing graphical output. The method provided by the invention has the advantages that the speed of detecting the privacy leakage vulnerability of the Android application software APP is accelerated; the requirements on the detection environment and the vulnerability reproducing difficulty are reduced, so that the vulnerability analysis is faster and more accurate.
Owner:XIDIAN UNIV
Defensive installation for security of router, defense system and method
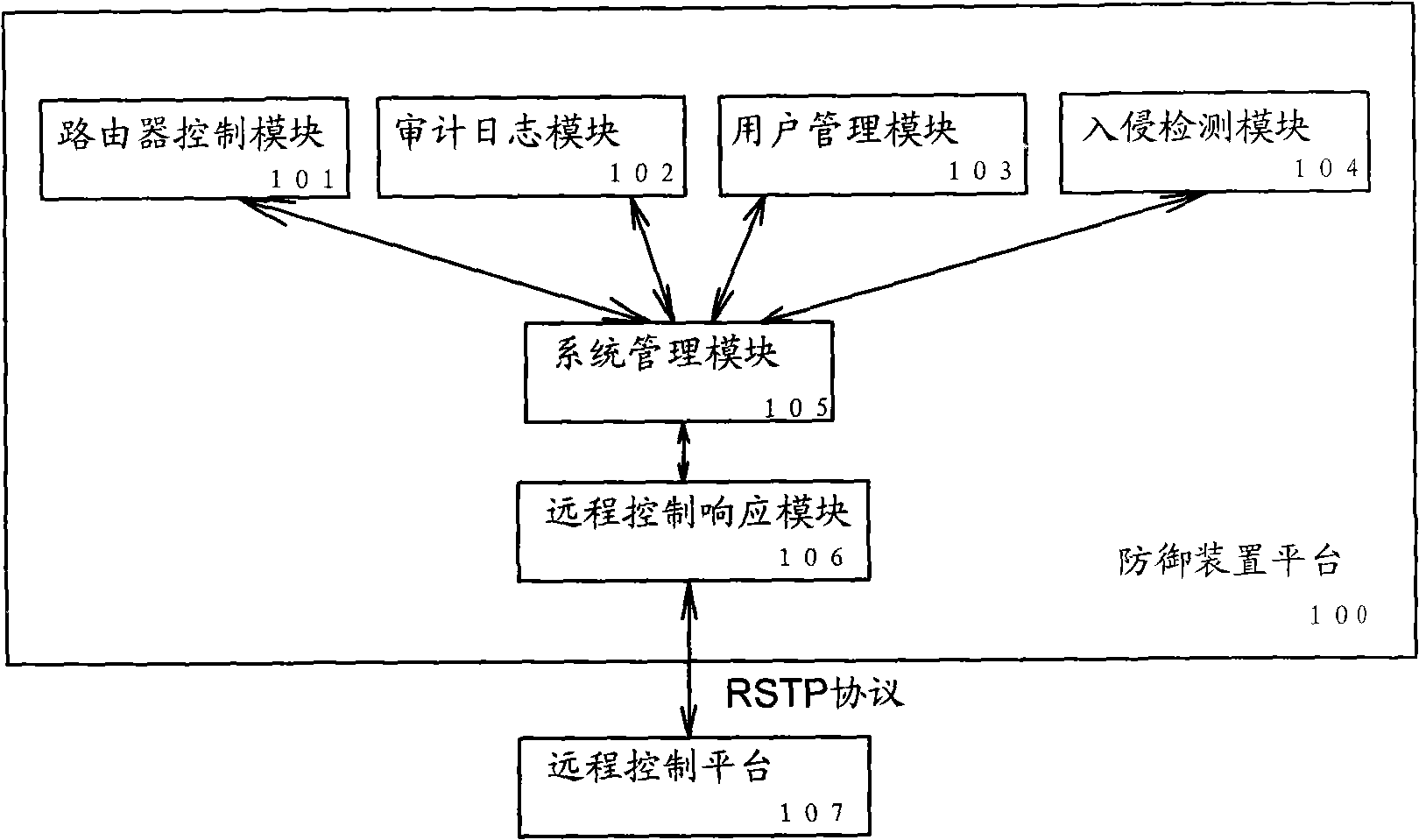
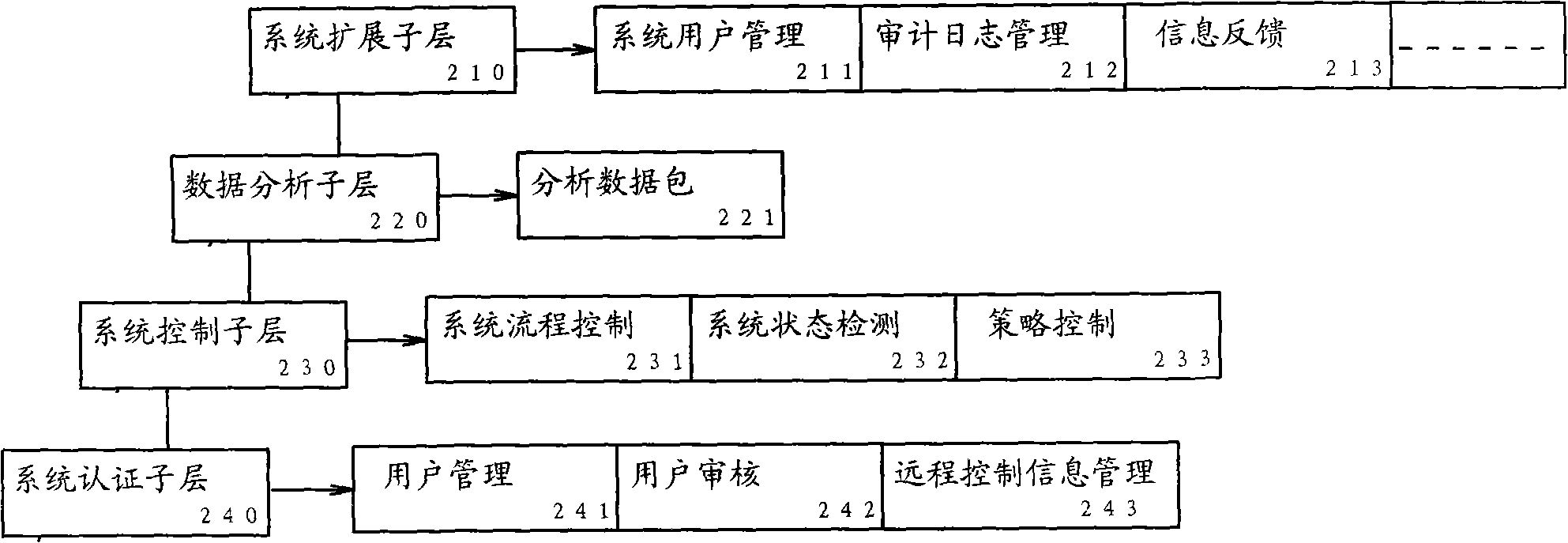
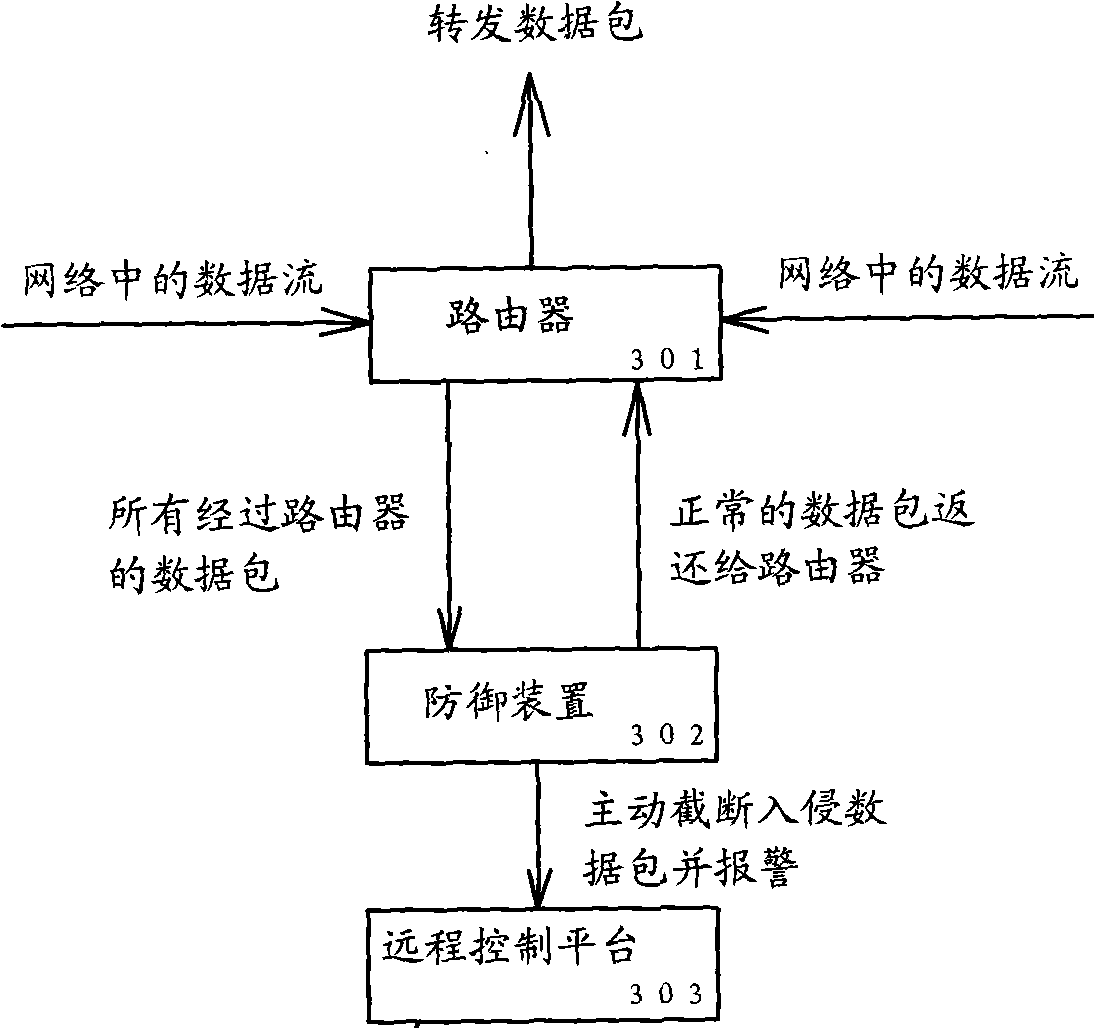
InactiveCN101286850AImprove securityImprove resistance to attackUser identity/authority verificationNetwork packetSystems management
The invention relates to a defending device which has active defense function for routers, a defending system which consists of the defending device, routers and a remote control platform and a method which can actively defend routers. The defending device of the invention comprises a system administration module, an intrusion detection module, a router control module, an audit logging module and a remote control response module. The defending device, system and platform of the invention utilize the Libpcap function library, adopt a bottom-layer packet capture technique which is integrated with an intrusion detection technique, parse whether the data packets are normal or not by a method of data stream analysis, monitor and obstruct the illegal data stream according to whether the data packets are normal or not and give an alarm to the administrators of the remote control platform by the audit logging module. The defending device, system and platform of the invention greatly increase the safety performance and the anti-attack performance of routers and effectively protect the normal operation of the whole network, thereby providing a network administration platform where the network administrators can detect potential safety hazards, receive the feedback of the information of potential safety hazards and process the information of potential safety hazards in time.
Owner:SHENZHEN POLYTECHNIC
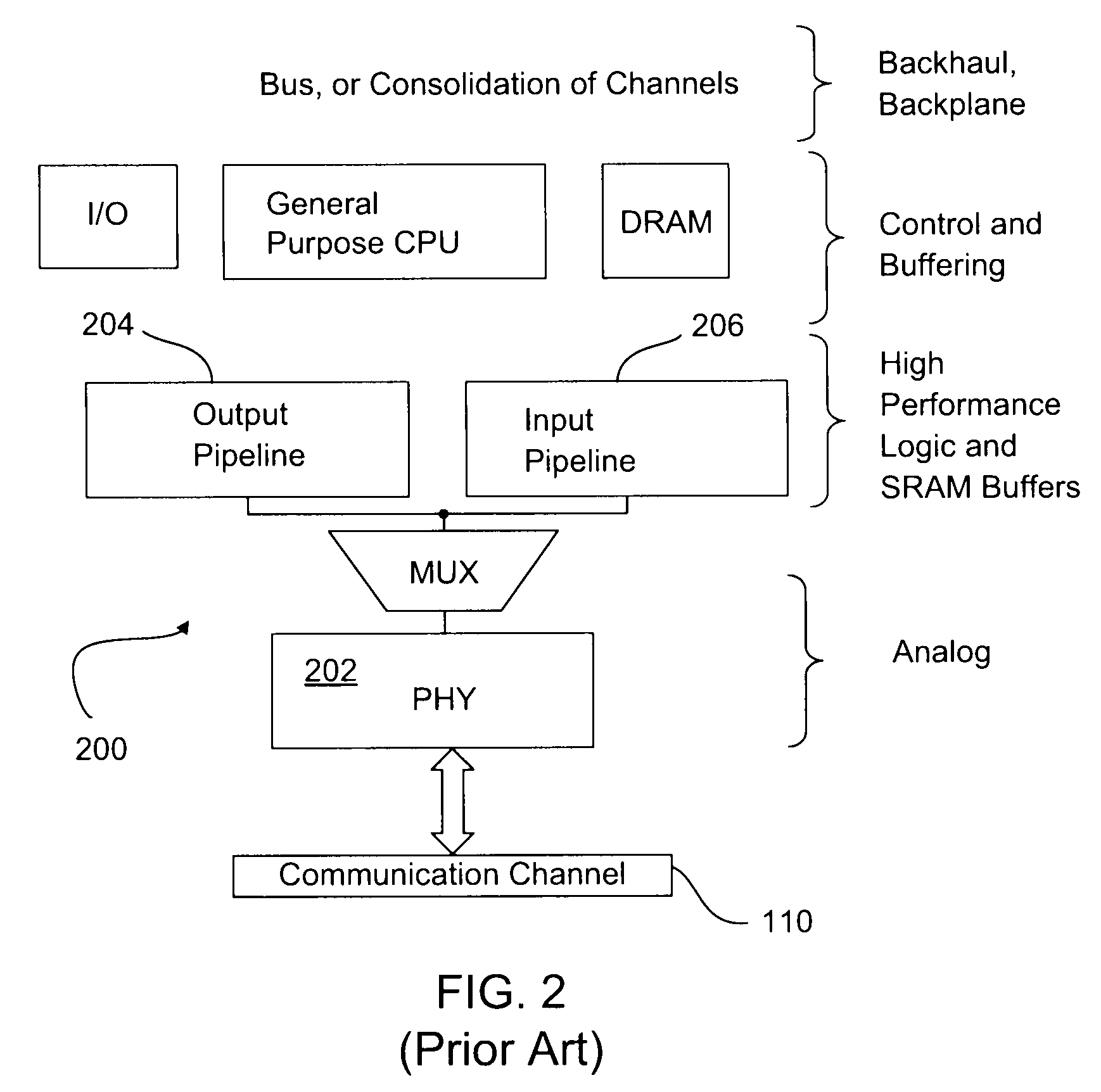
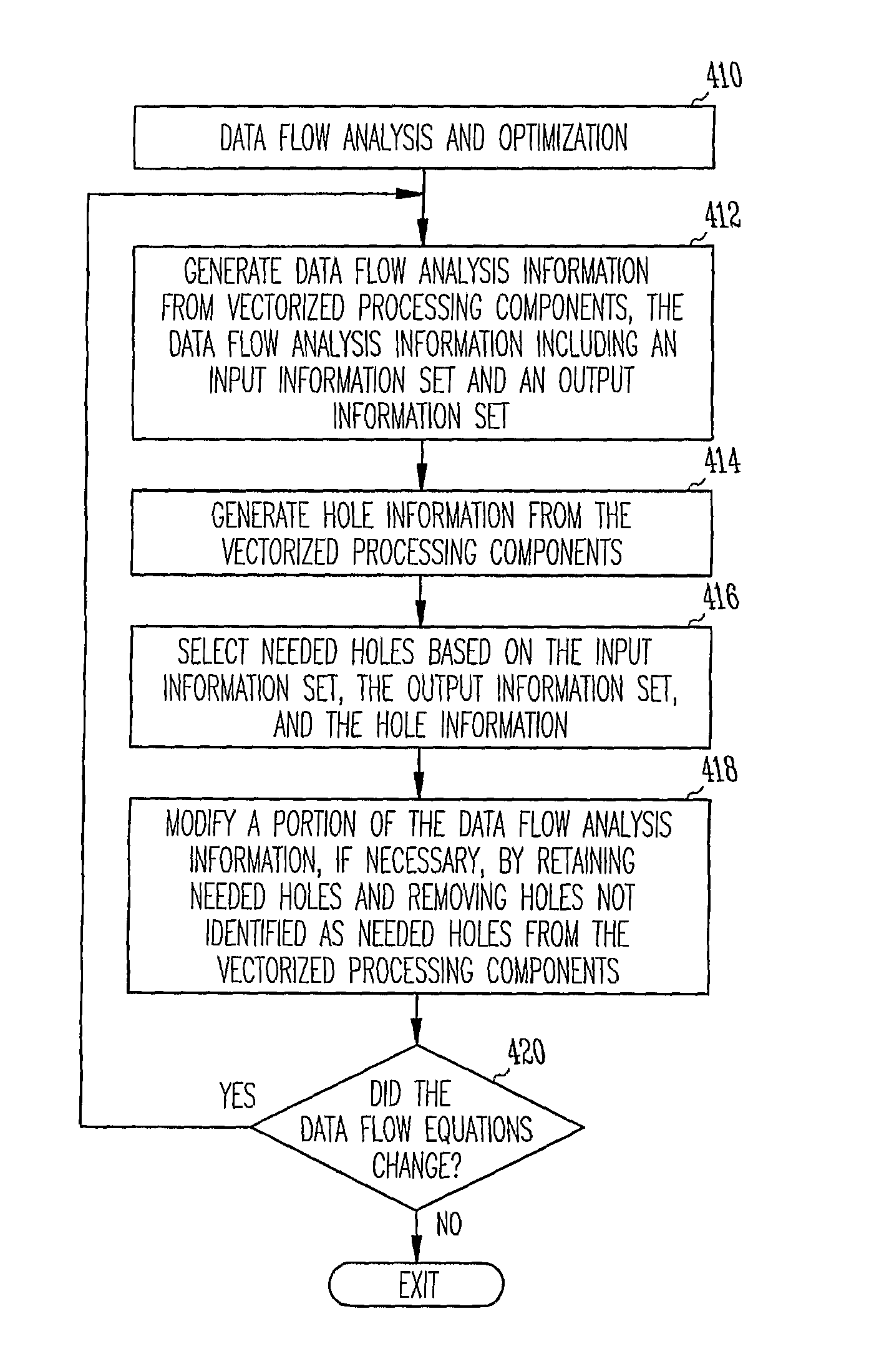
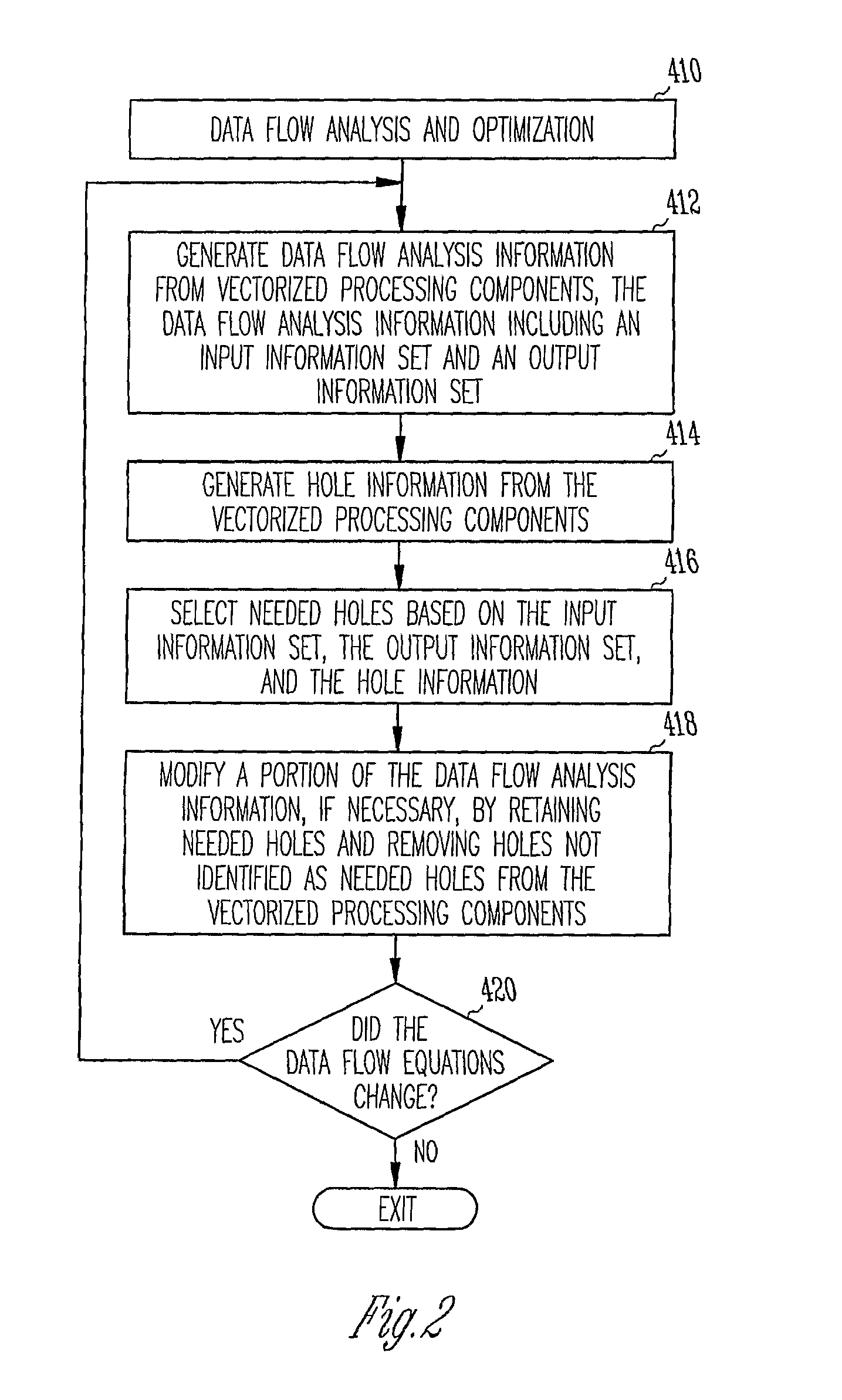
Computer-implemented method and system for improved data flow analysis and optimization
A computer-implemented method and system for improved data flow analysis and optimization are disclosed. The method and system generates data flow analysis information from vectorized processing components, the data flow analysis information including an input information set and an output information set, generates hole information from the vectorized processing components, selects needed holes based on the input information set, the output information set, and the hole information, and modifies a portion of the data flow analysis 10 information by retaining needed holes and removing holes not identified as needed holes from the vectorized processing components.
Owner:INTEL CORP
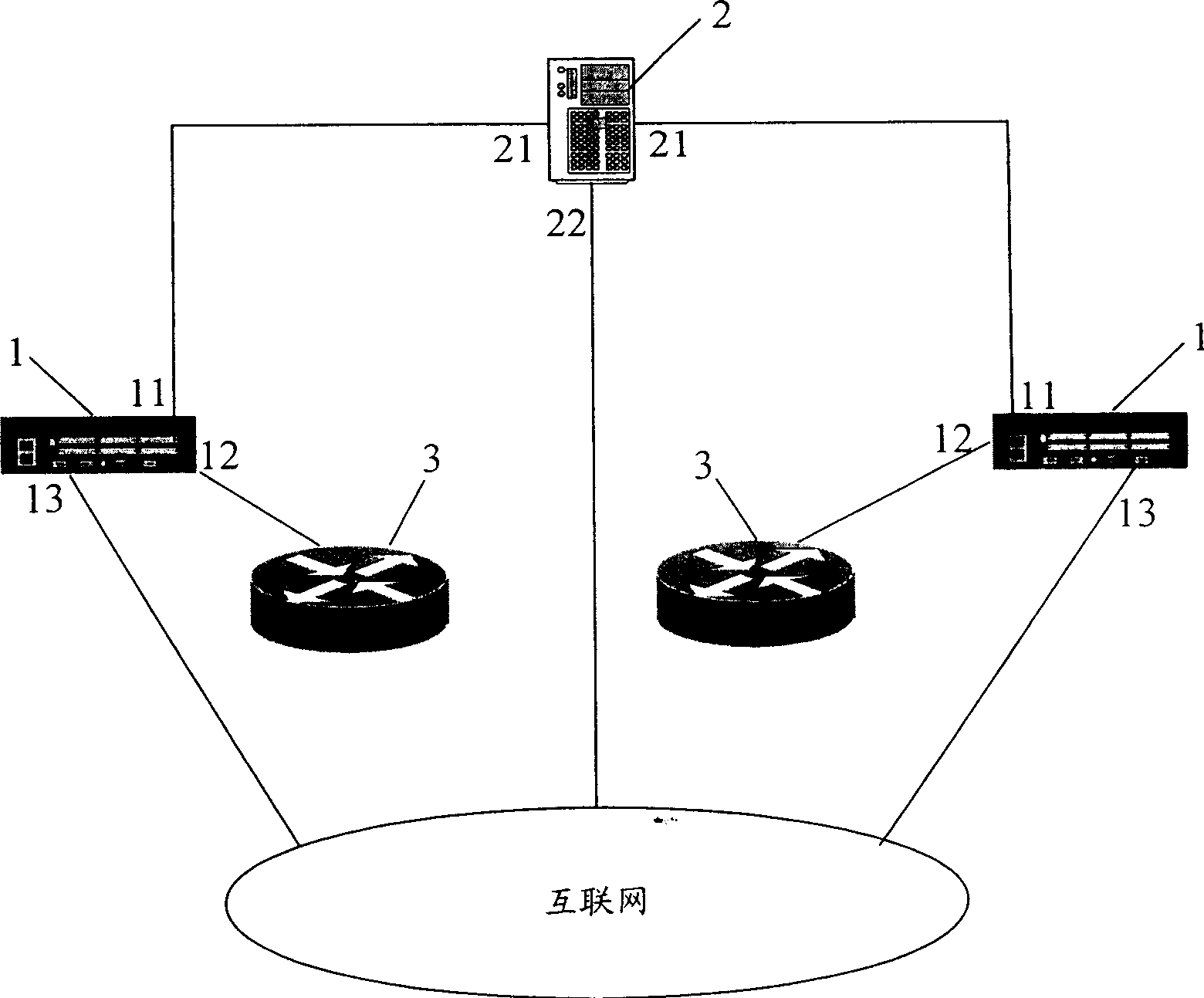
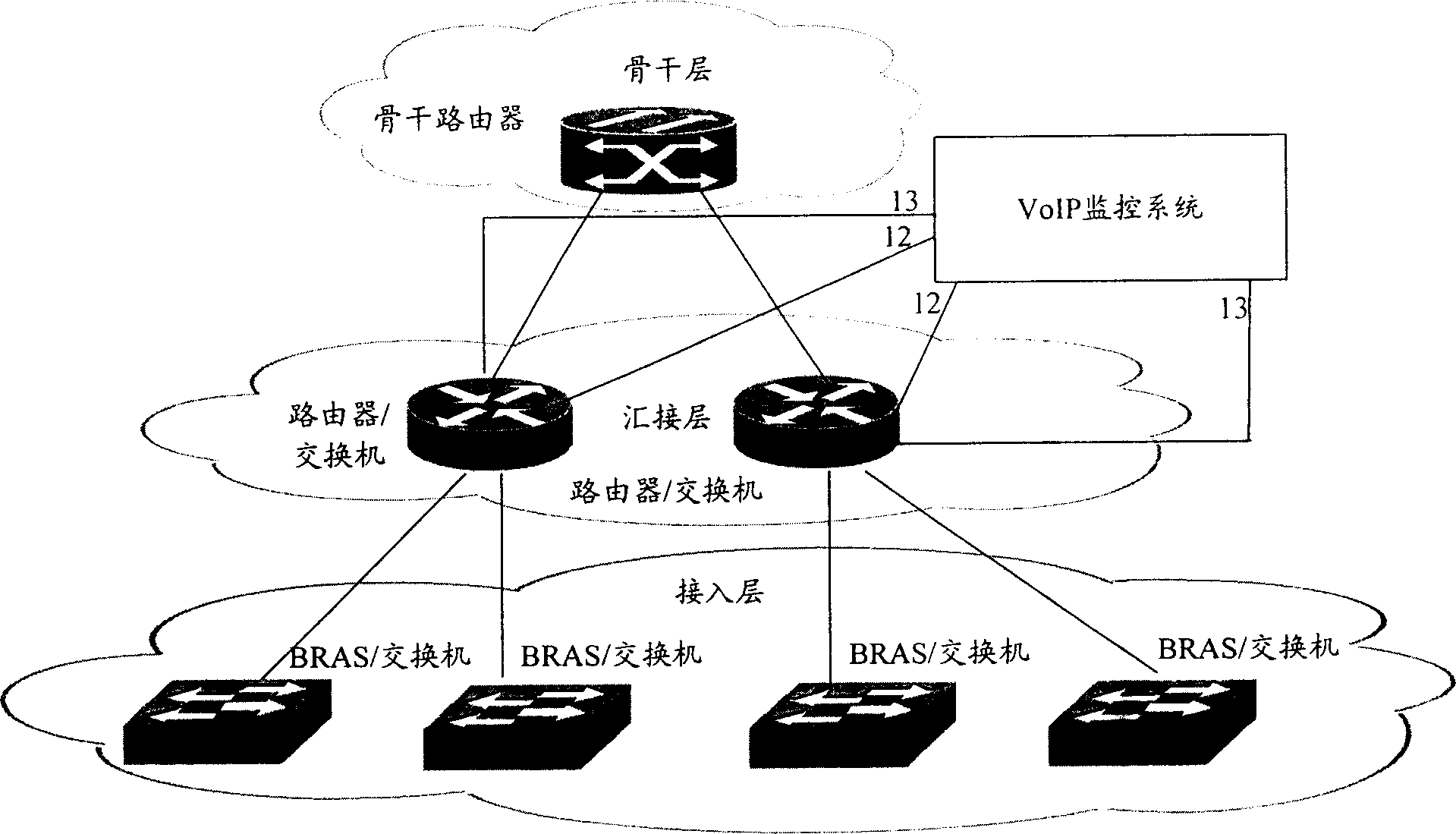
Monitor system and its monitor method for internet network telephone
ActiveCN1750488ASolve monitoring problemsRealize the purpose of value preservation and income generationData switching networksTraffic volumeTraffic capacity
A monitor system for network telephone, which contains one or plurality of VoIP monitor equipment and VoIP monitor centralized platform, the former sampling data stream of network equipment, analyzing VoIP flow, sending analyzed result to VoIP centralized platform and monitoring VoIP flow according to strategy sent from centralized platform, the latter including database, Web service software unit and monitor strategy software unit, adopting expandable customized protocol to communicate with VoIP monitor equipment, monitoring and controlling the data stream among each network equipment and main layers of network tandem layer. Said invention has simple structure and easy operation without complicate configuring to router or exchanger.
Owner:CHINA TELECOM CORP LTD
Automatic algorithm discovery using reverse dataflow analysis
ActiveUS20150047045A1Memory loss protectionError detection/correctionAutomated algorithmTheoretical computer science
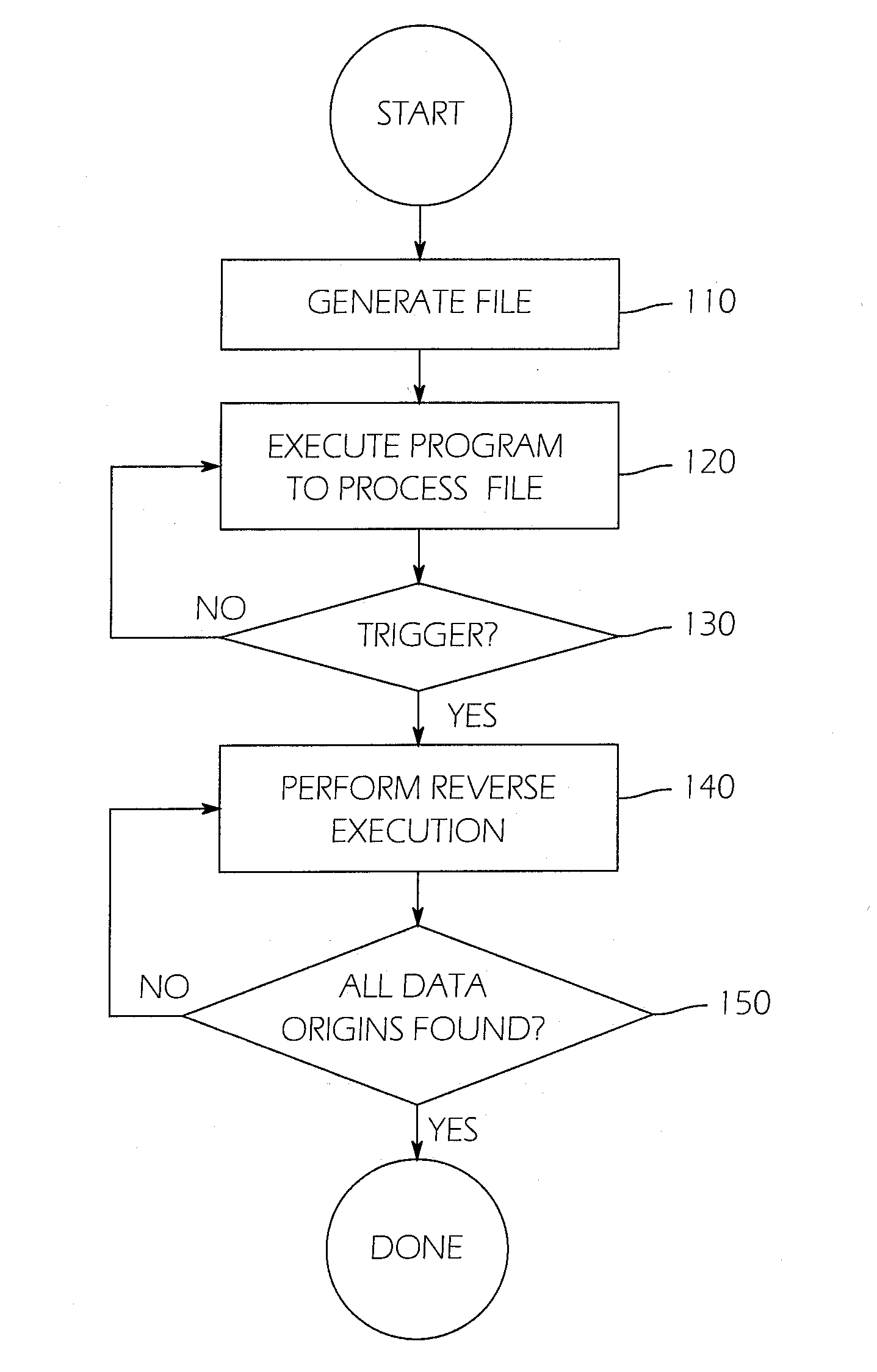
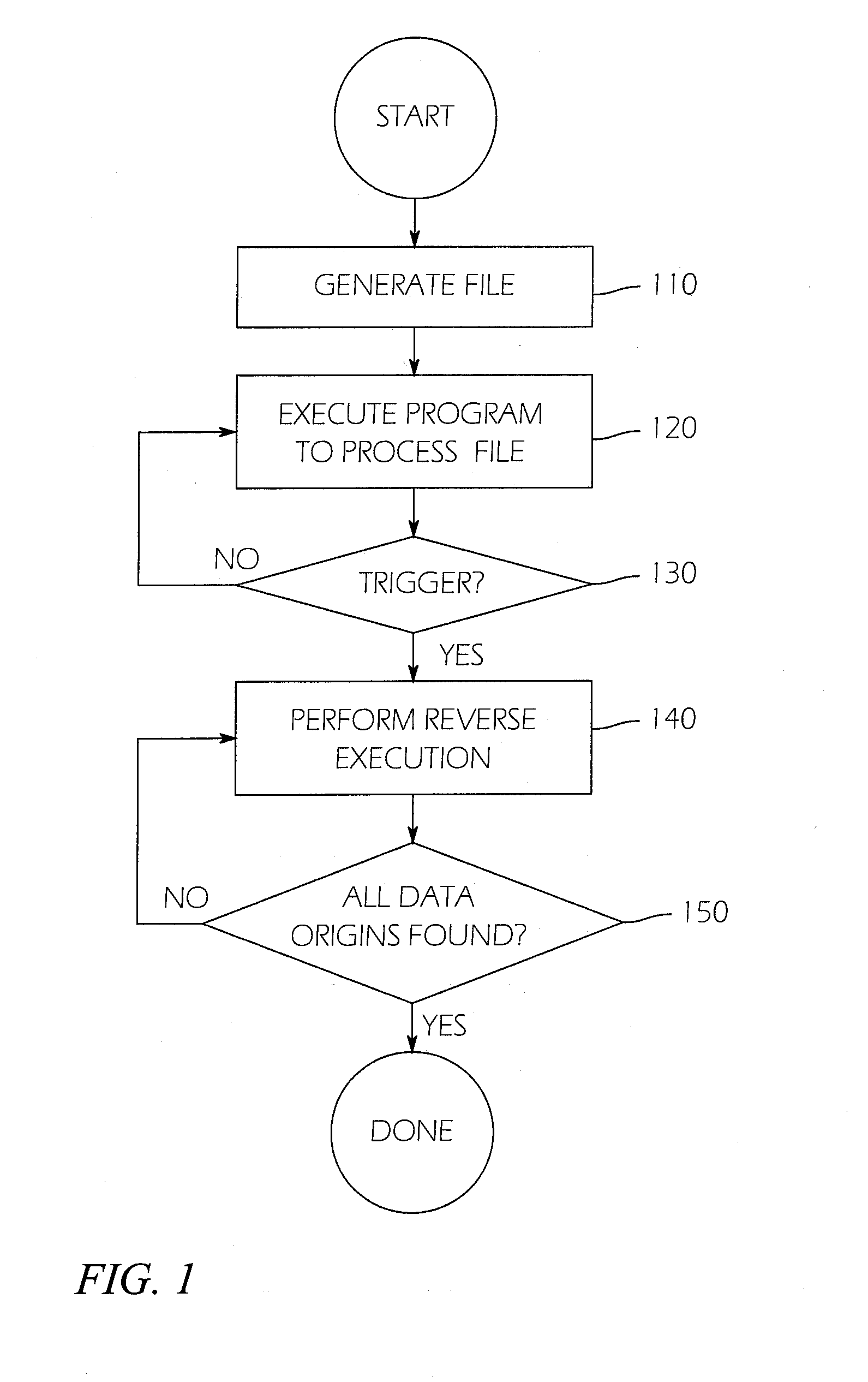
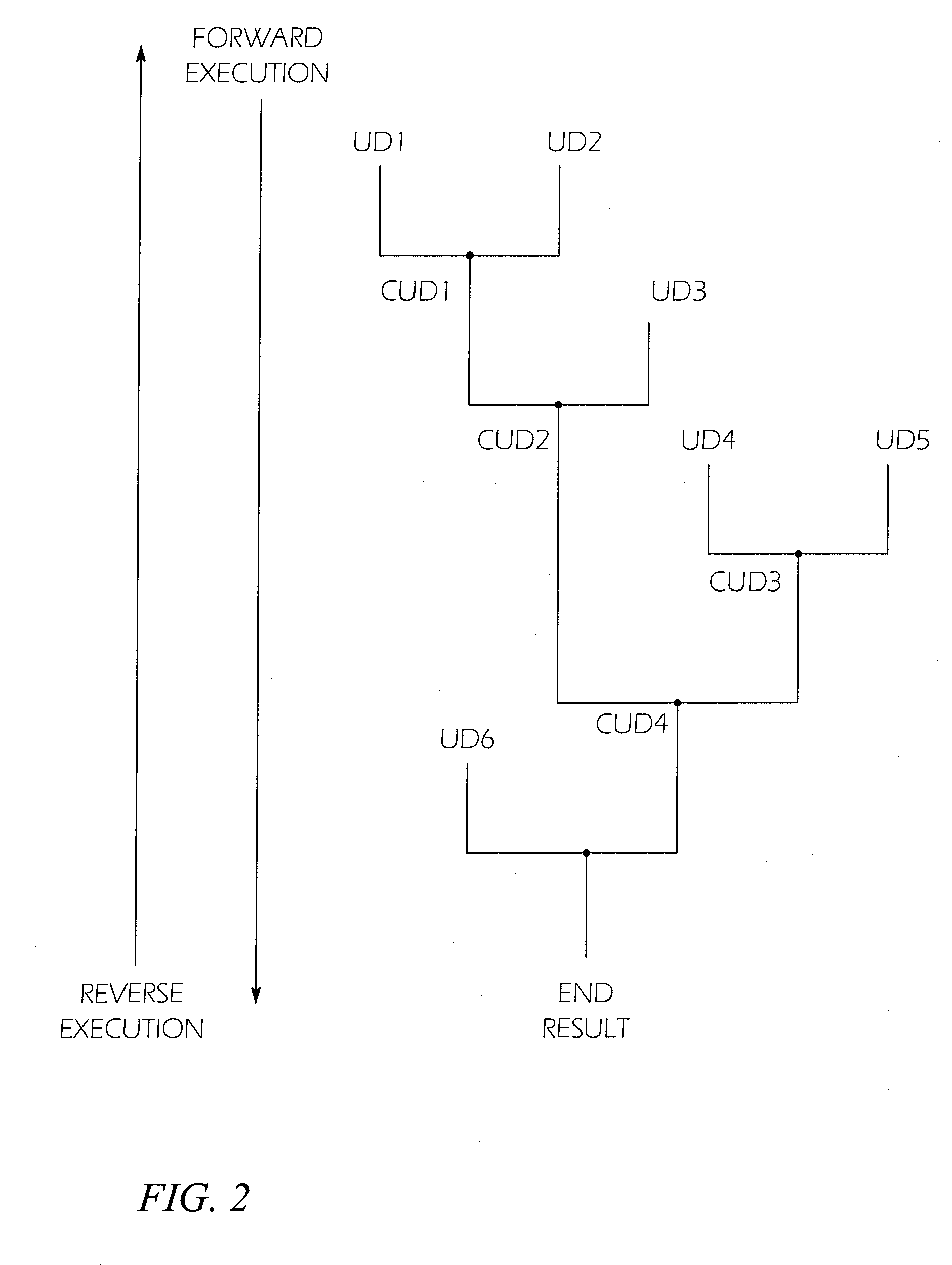
A system and method for finding vulnerabilities and tracing an end result associated with a vulnerability to its origins in user data. A user data source containing an ordered sequence of user data items may be a data file. In one embodiment the method for identifying, in the user data source, the origins of the end result, includes associating with each user data item a location identifier identifying the location of the user data item in the sequence of user data items executing instructions with a virtual machine, associating with each result the location identifier of the data item when one argument is a user data item and a tag when more than one argument is a user data item. This process may be continued until the end result is obtained. Subsequently, the method may include stepping through instructions with the virtual machine in reverse order, to tracing the origins of the end result to each of the user data items contributing to the result.
Owner:RAYTHEON CO
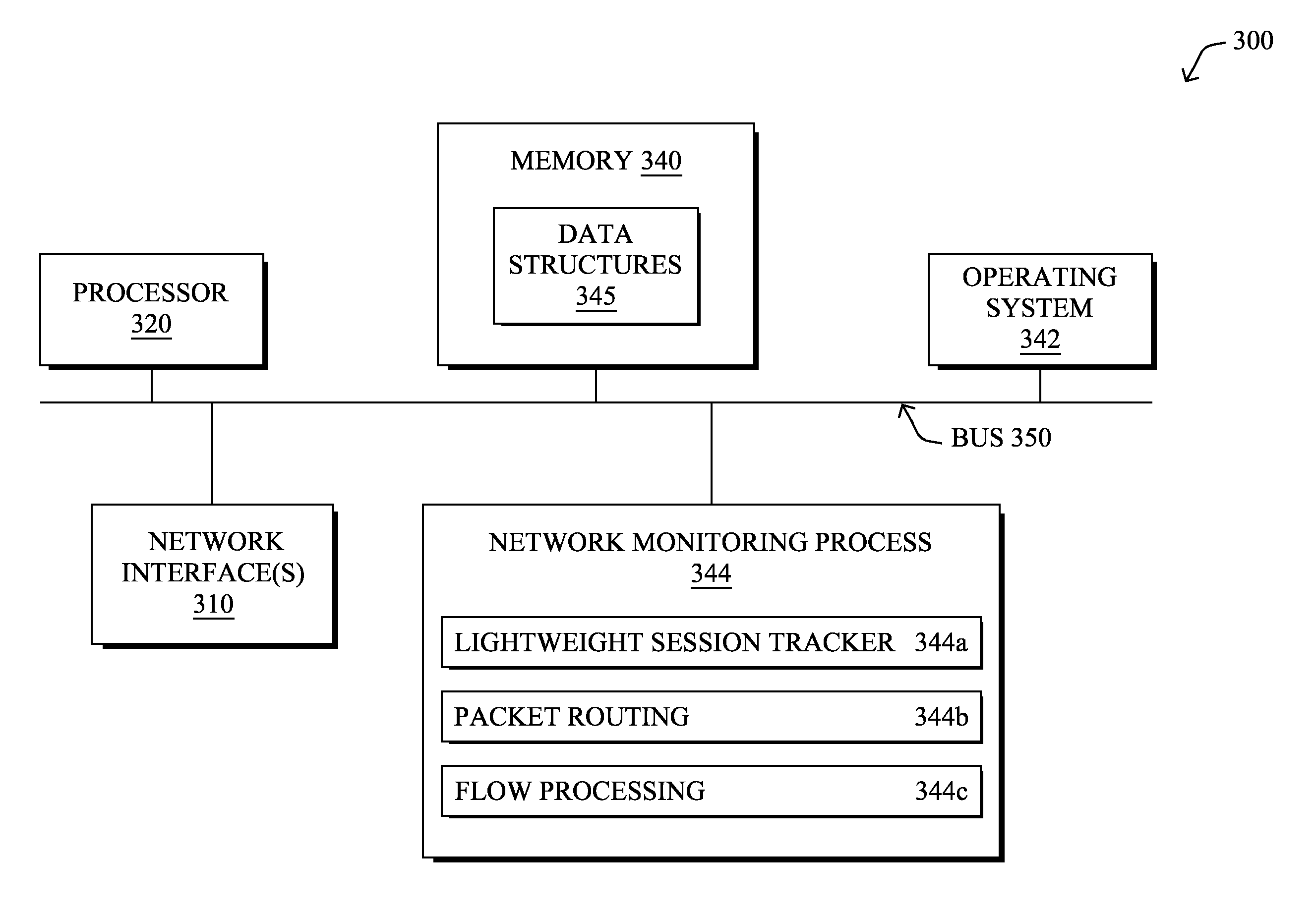
Selective real-time GTP session tracking using distributed processing techniques
ActiveUS20150327091A1Error preventionFrequency-division multiplex detailsDevice MonitorUser equipment
A distributed network monitoring device monitors via a lightweight session tracking module of a network monitoring device, control plane data for connectivity sessions of User Equipment (UE) in a communication network. The lightweight session tracking module selectively identifies at least one bearer for a corresponding connectivity session according to one or more control plane attributes and associates each selectively identified bearer for the corresponding connectivity session with a bearer routing rule for user plane data. A packet routing module receives user plane data for connectivity sessions of UE and transmits the user plane data of the connectivity sessions according to the bearer routing rule of the lightweight session tracking module to a flow processing module for subsequent data flow analysis.
Owner:NETSCOUT SYST TEXAS LLC
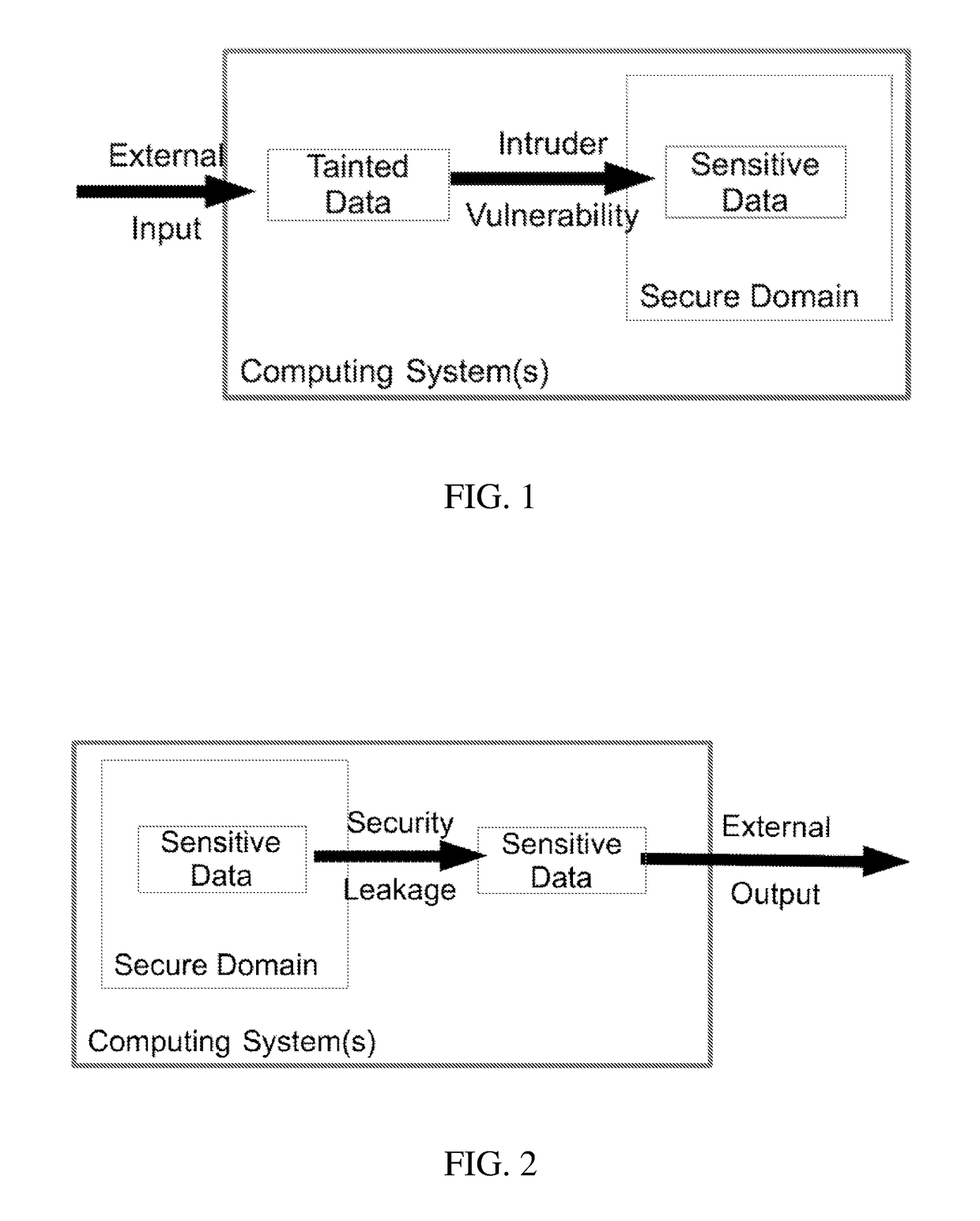
Dynamic security domain data flow analysis via passive monitoring
InactiveUS20190073473A1Reduced impact on system performanceDetects and prevents unauthorized data movementDigital data protectionPlatform integrity maintainanceProcessor registerPosition dependent
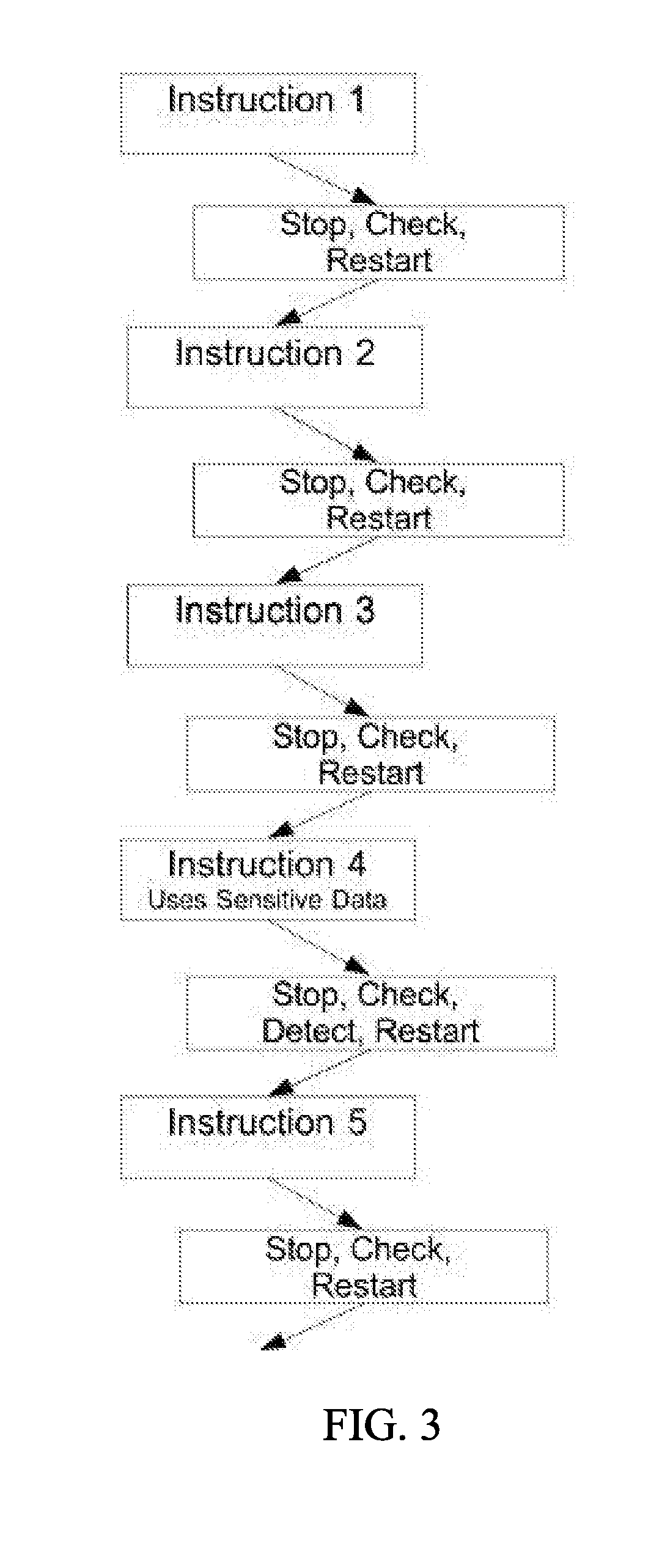
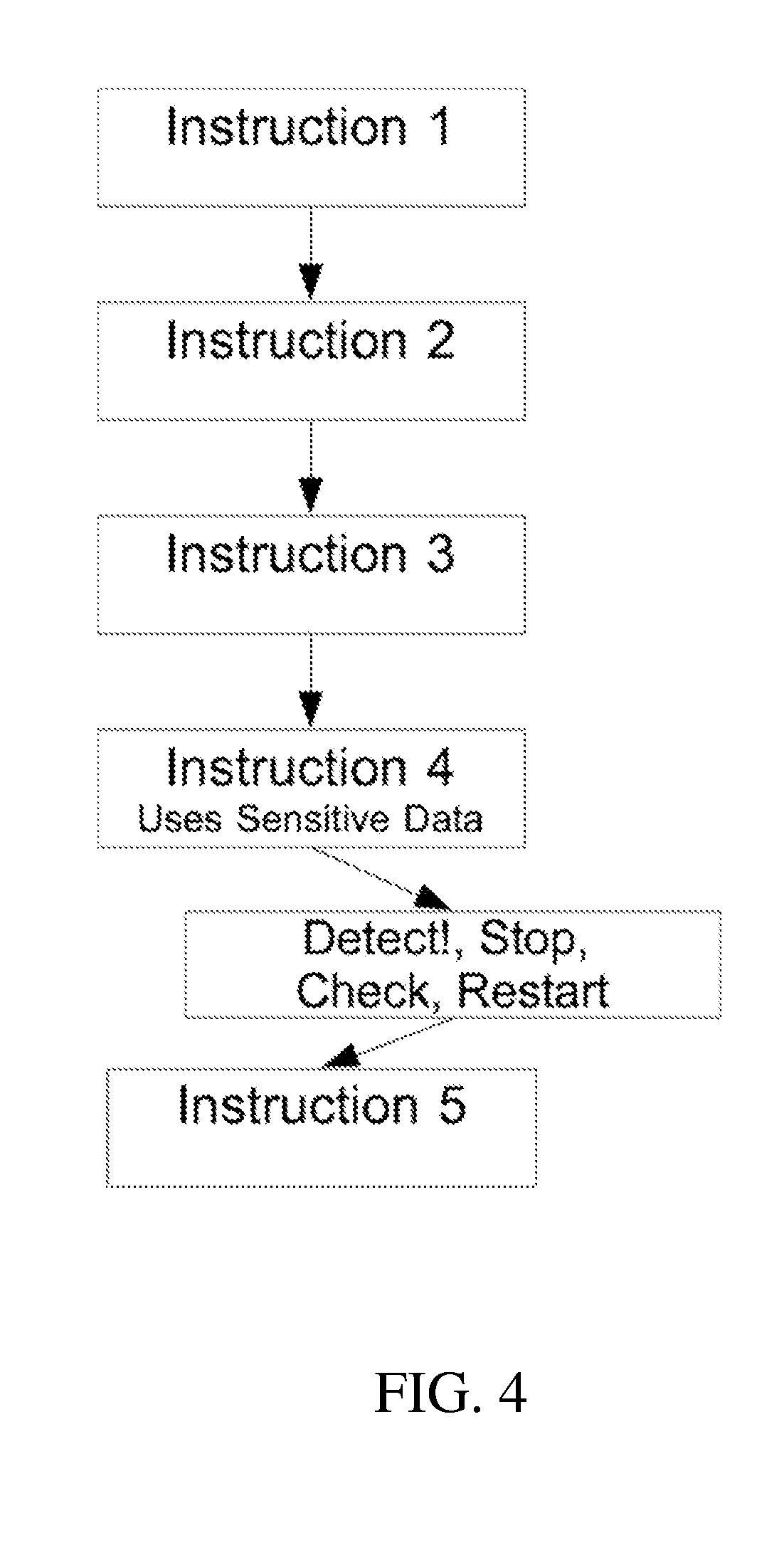
A system and method for dynamic security domain data protection through passive monitoring of data storage. The present invention may be implemented using data breakpoints to trigger invocation of the data flow analysis routines. A data breakpoint register may be associated with the memory location of each item of target data. Upon attempted access, a data breakpoint interrupt is triggered, which pauses execution and runs data flow analysis and security routines to determine the appropriate action. The present invention may be implemented using a virtual paging system having a memory management unit configured to generate a page fault upon any attempt to access target data. The virtual paging system may have a virtual page that contains target data and that page may be actively managed so that each attempted access to target data results in a page fault, which pauses execution and runs data flow analysis routines to determine appropriate action.
Owner:DORNERWORKS
Combination and optimization methods of access and storage based on analysis of data stream
ActiveCN1952897AAccurate and effective optimizationVersatilityProgram controlMemory systemsData miningByte
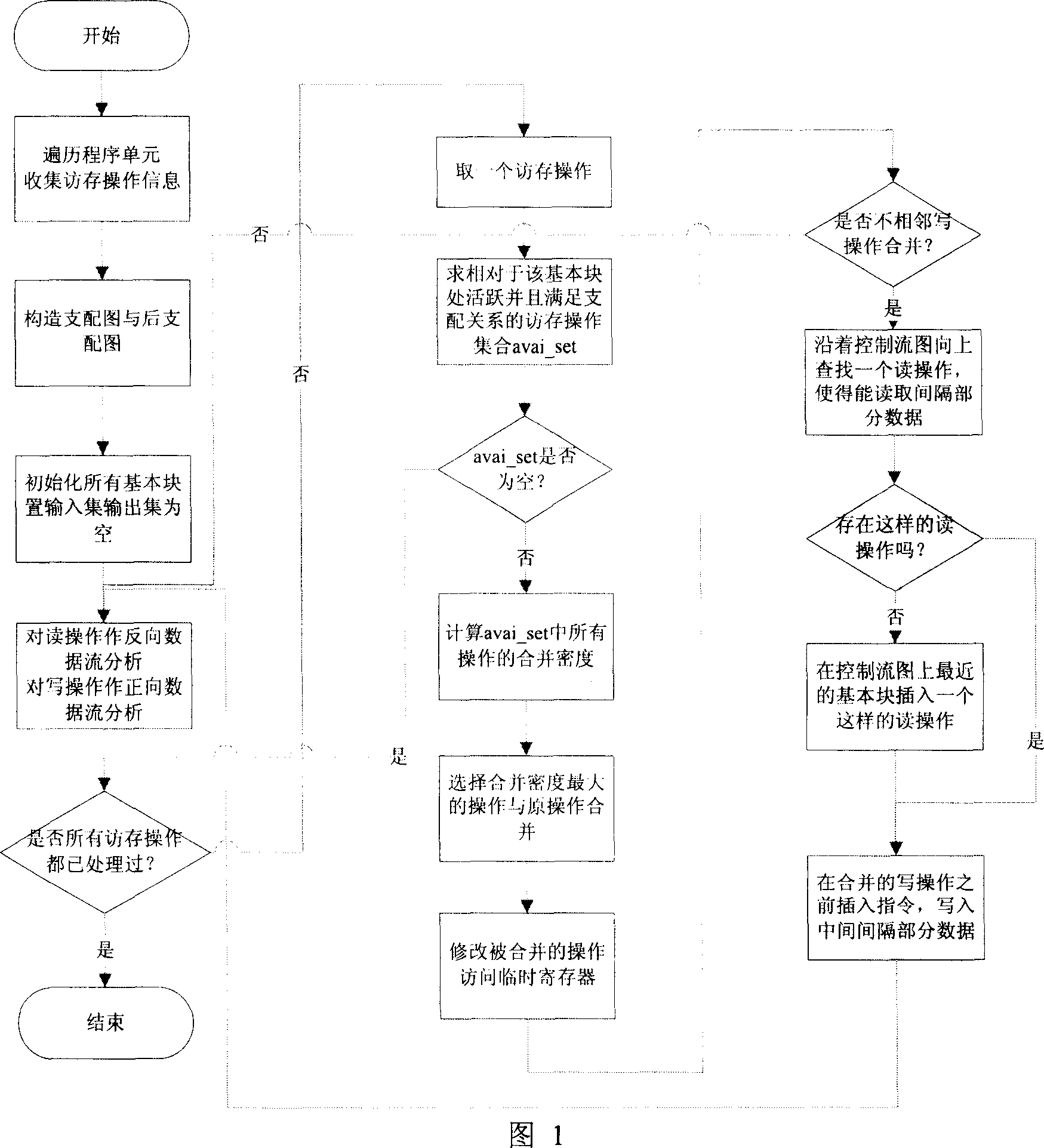
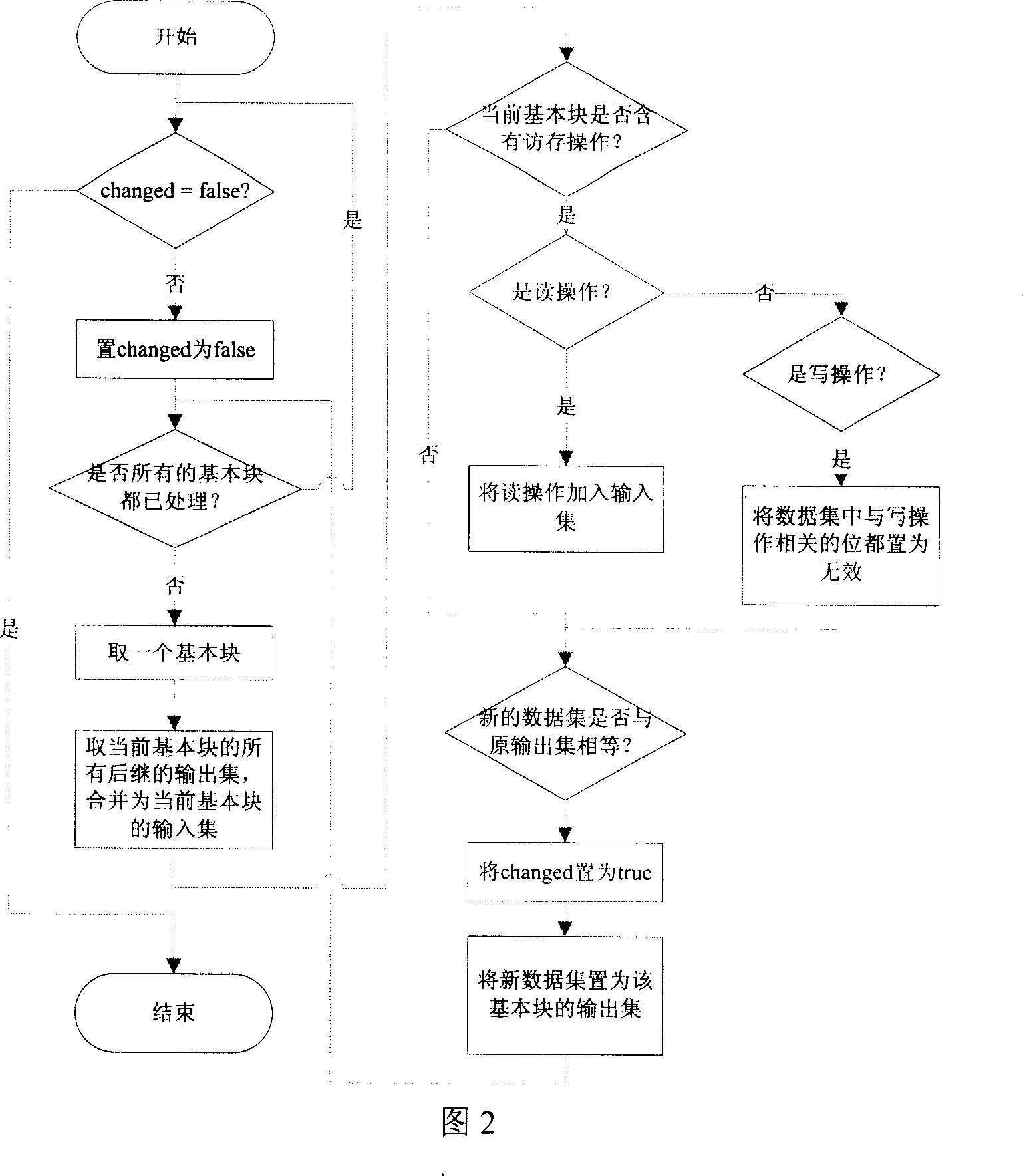
This invention provides one visit merge and optimization method based on data flow analysis, which merges two or more visit orders into one multi-bit visit order of adjacent address through total visit memory information for data flow analysis. The merged visit data is in register or local memory, the original visit memory order is taken place of register or local memory direct visit.
Owner:G CLOUD TECH
Method for realizing automatic pipeline parallelism
InactiveCN101944014ABalance workloadAdded optimization capabilities for automatic parallel optimizationConcurrent instruction executionArray data structureThread scheduling
The invention belongs to the technical field of program compilation and in particular relates to a method for realizing automatic pipeline parallelism. The method of the invention mainly comprises the following steps of: (1) identification of the pipeline parallelism, namely judging a loop structure which is provided with cross-loop iteration dependence and a dependence distance vector is a constant; (2) synchronization among threads, namely inserting the synchronization according to the dependence distance vector and deleting the redundant synchronization with the same distance vector; and (3) thread scheduling in a static step length, namely self-defining a thread scheduling strategy for balancing the workload of each thread and reducing the communication expense. The type identification of the loop structure is depended on the conventional array data stream analysis and dependence tests, while the pipeline parallelism only processes the regular loop structure with backward cross-loop iteration. The synchronization expense of the pipeline parallelism is high, so the pipeline parallelism is only performed on the outmost layer of a nested loop. Profit of the pipeline parallelism depends on programs, the number of the cyclic iteration is larger and the dependence distance is longer, the performance promotion is greater. The method for realizing the pipeline parallelism improvesthe capacity of automatic parallel optimization and contributes to further improving the performance of scientific calculation programs.
Owner:FUDAN UNIV
Peer-to-peer (P2P) botnet tracking at backbone level
A method, computer-readable medium, and system for analyzing backbone traffic to determine compromised hosts from among hosts on a network are provided. The backbone traffic includes data flows. Each of the data flows is analyzed to determine peer-to-peer data flows from among the data flows. Each of the peer-to-peer data flows is one of the data flows having a source address and a destination address that are each unassociated with a domain name. The peer-to-peer data flows are analyzed to determine the compromised hosts from among the hosts. Each of the compromised hosts is interconnected with another of the compromised hosts via at least one of the peer-to-peer data flows.
Owner:AT&T INTPROP I L P
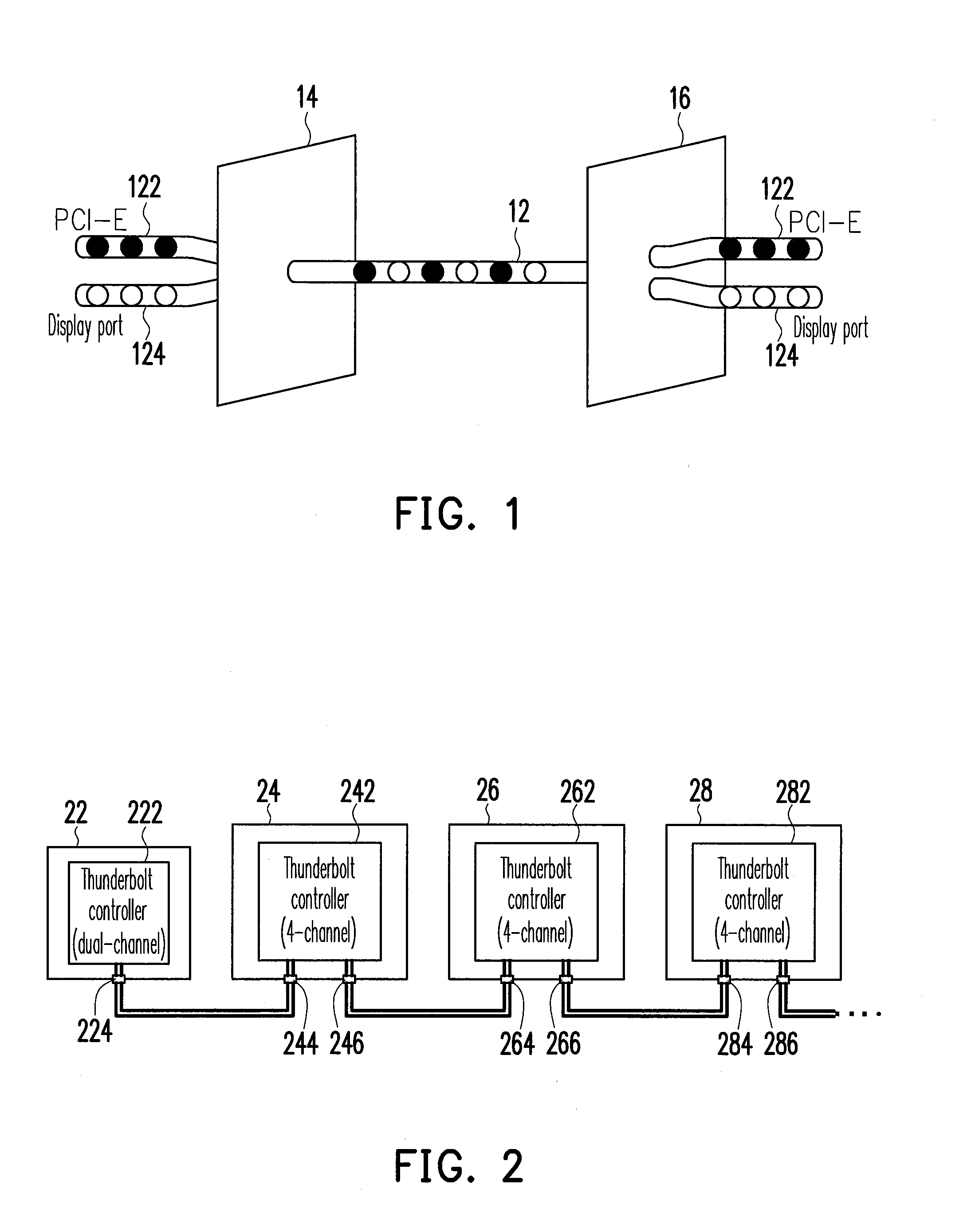
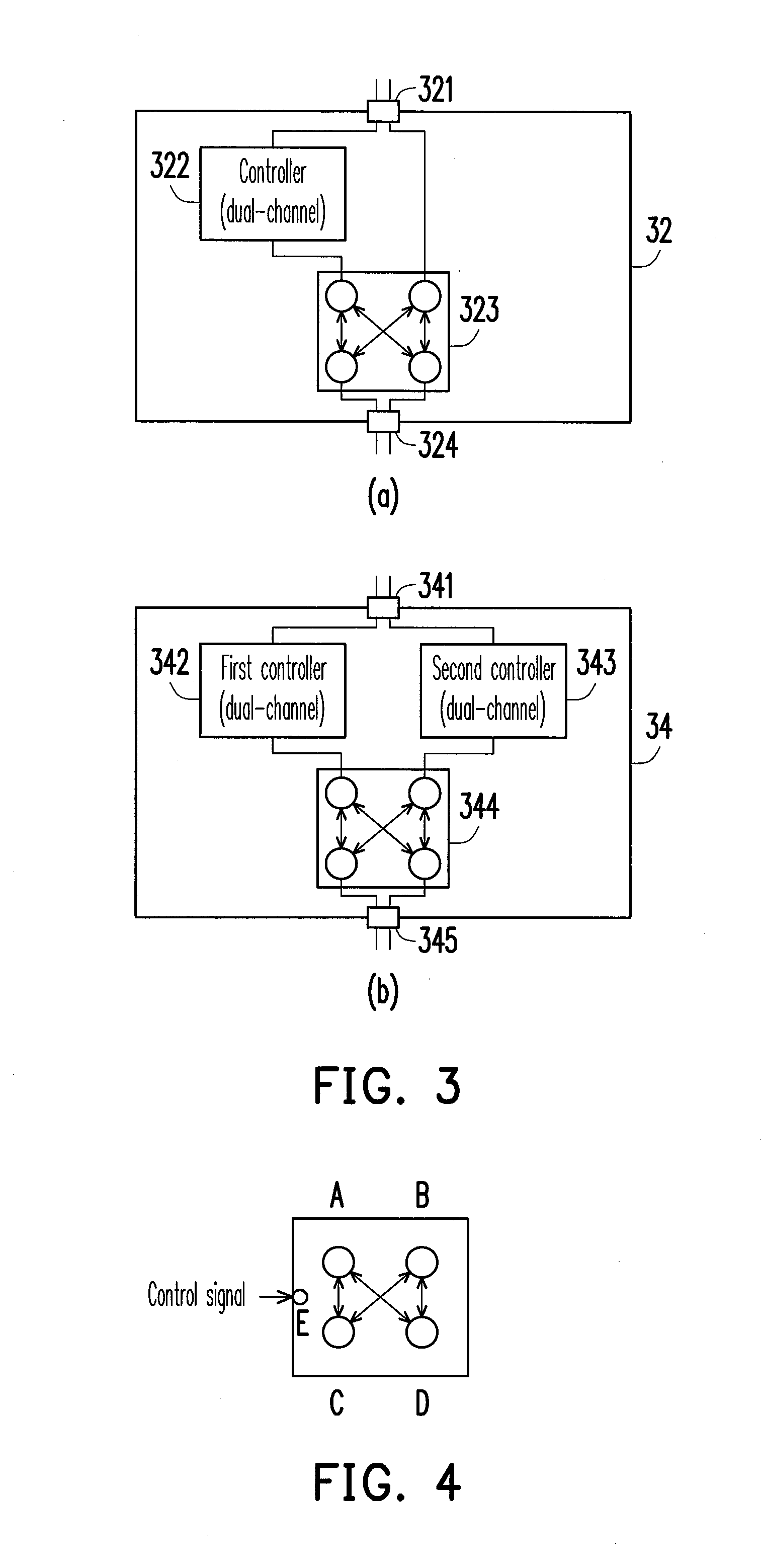
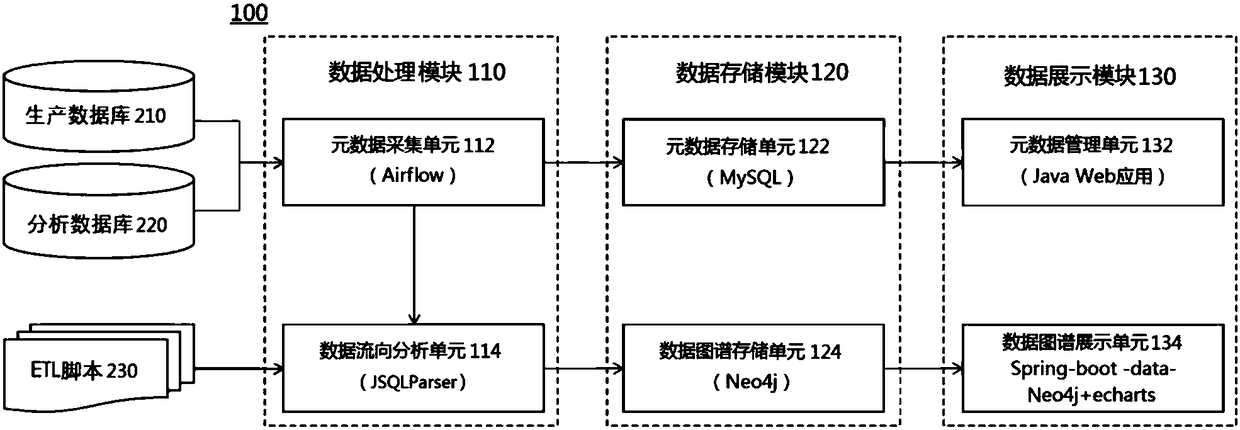
Apparatus, system, and method for analyzing and managing data flow of interface apapratuses
An apparatus, a system, and a method for analyzing and managing data flow of interface apparatuses are provided. The system includes a host and the interface apparatuses. In the host, a first controller provides data of a first channel and a second channel through a first interface port. Each interface apparatus has a second interface port, a second controller, a switch, and a third interface port. The second interface port serially connected to the first interface port receives data of the two channels and divides the same to be transmitted on a first transmission path and a second transmission path. The second controller processes data transmitted on the first transmission path. The switch switches data transmitted on the two transmission paths according to a control signal issued by the first controller. The third interface port is connected to the switch for outputting the switched data of the two channels.
Owner:ACER INC
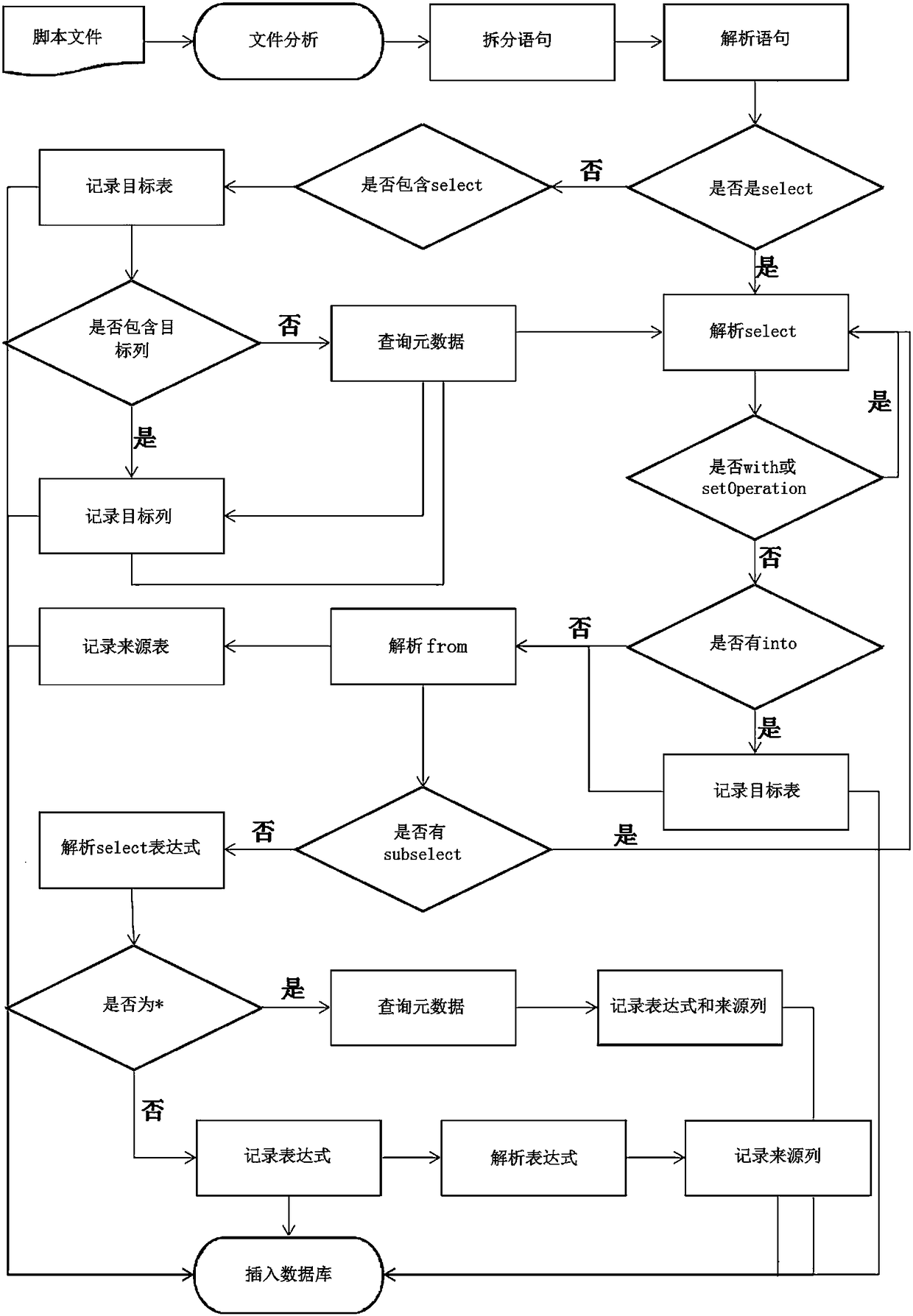
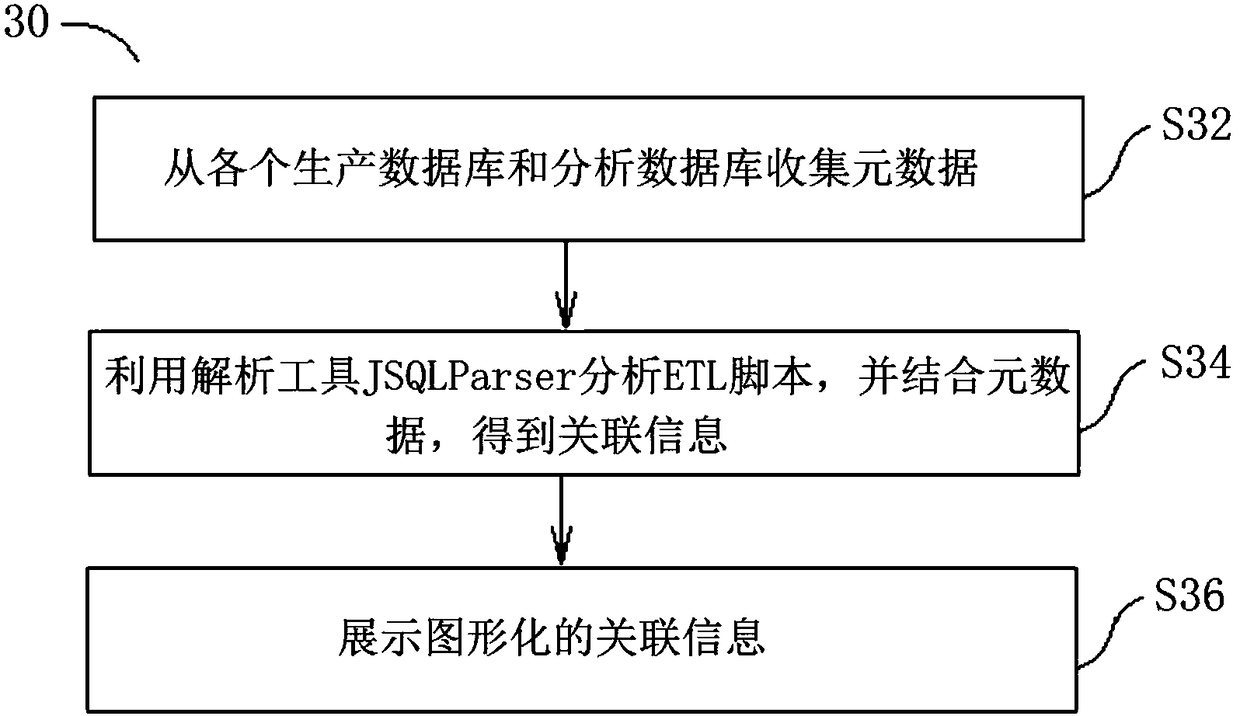
Data graph analysis system and method
InactiveCN108197182AHighly configurableImprove scalabilityRelational databasesSpecial data processing applicationsAnalysis dataData stream analysis
The invention discloses a data graph analysis system. The system includes: a data processing module, which includes a metadata collection unit and a data flow direction analysis unit connected with the metadata collection unit; a data storage module, which includes a data graph storage unit connected with the data flow direction analysis unit; and a data display module, which includes a data graphdisplay unit connected with the data graph storage unit. The metadata collection unit is used for collecting metadata from all production databases and analysis databases. The data flow direction analysis unit utilizes a parsing tool JSQLParser to analyze ETL scripts, and combines the metadata to obtain association information of table and field hierarchy among all the production database and theanalysis databases. The association information is stored into the data graph storage unit. The data graph display unit is used for displaying graphical association information. The above-mentioned technical solution of the invention can store and display association relationships among the metadata.
Owner:百味云科技股份有限公司
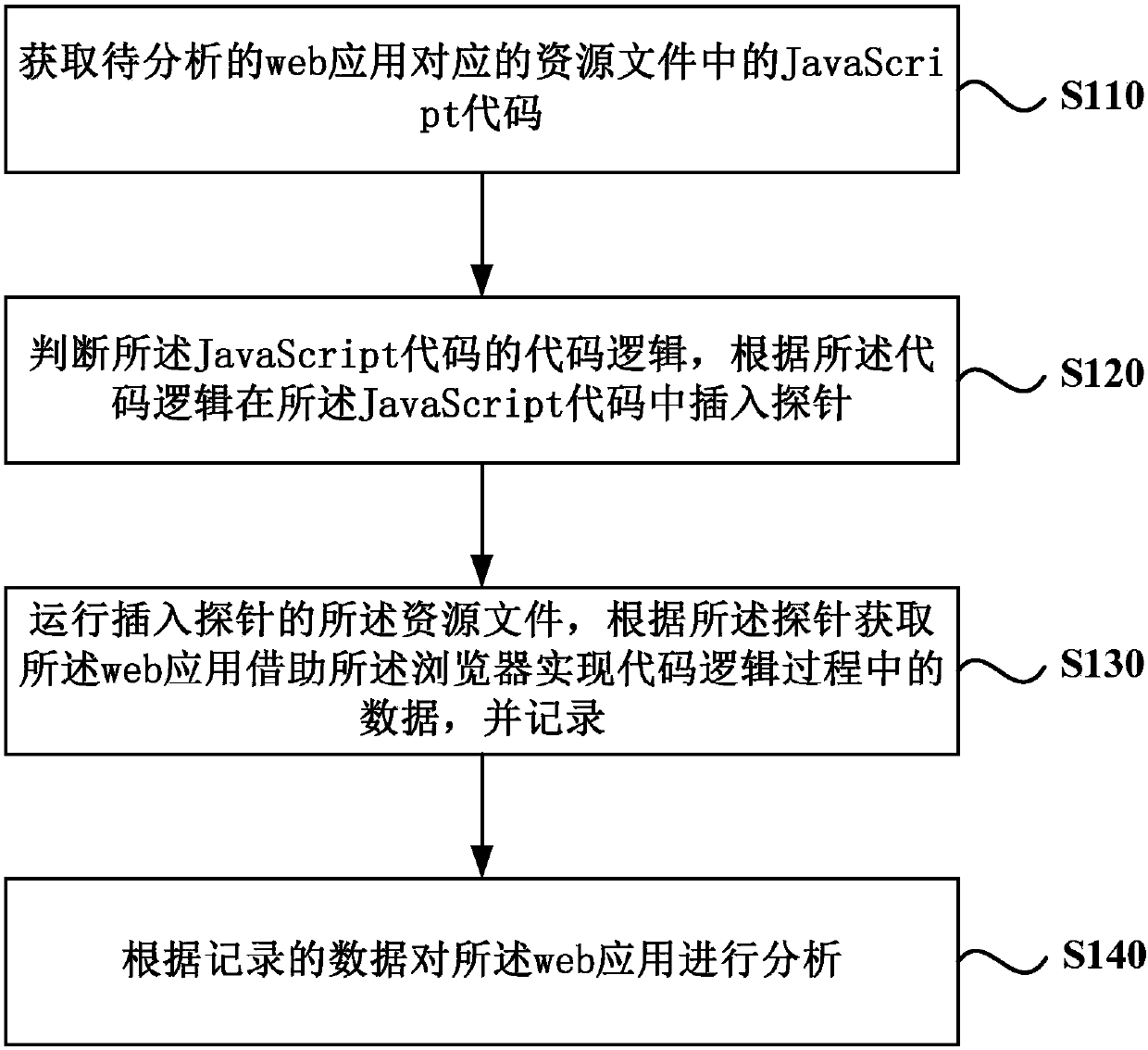
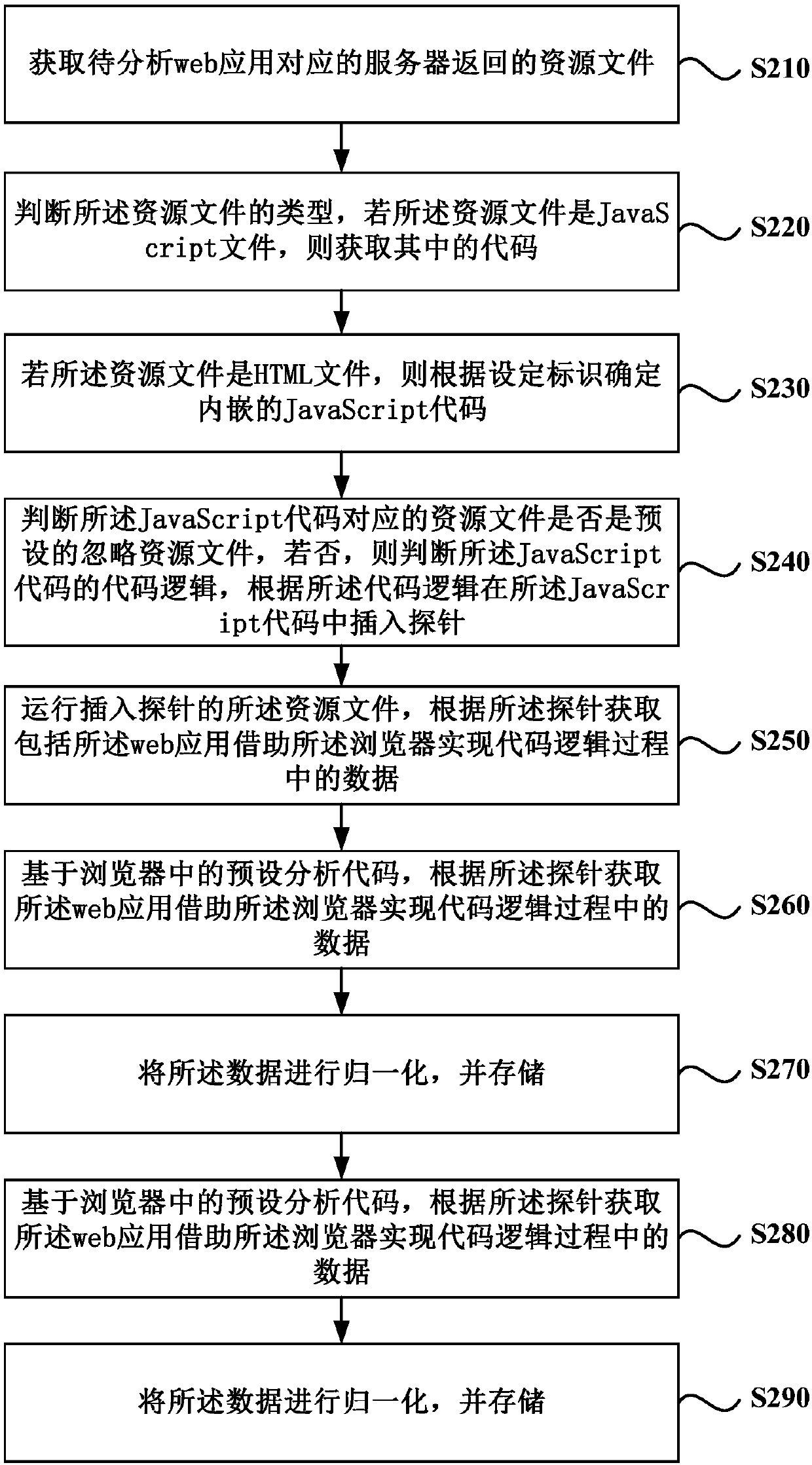
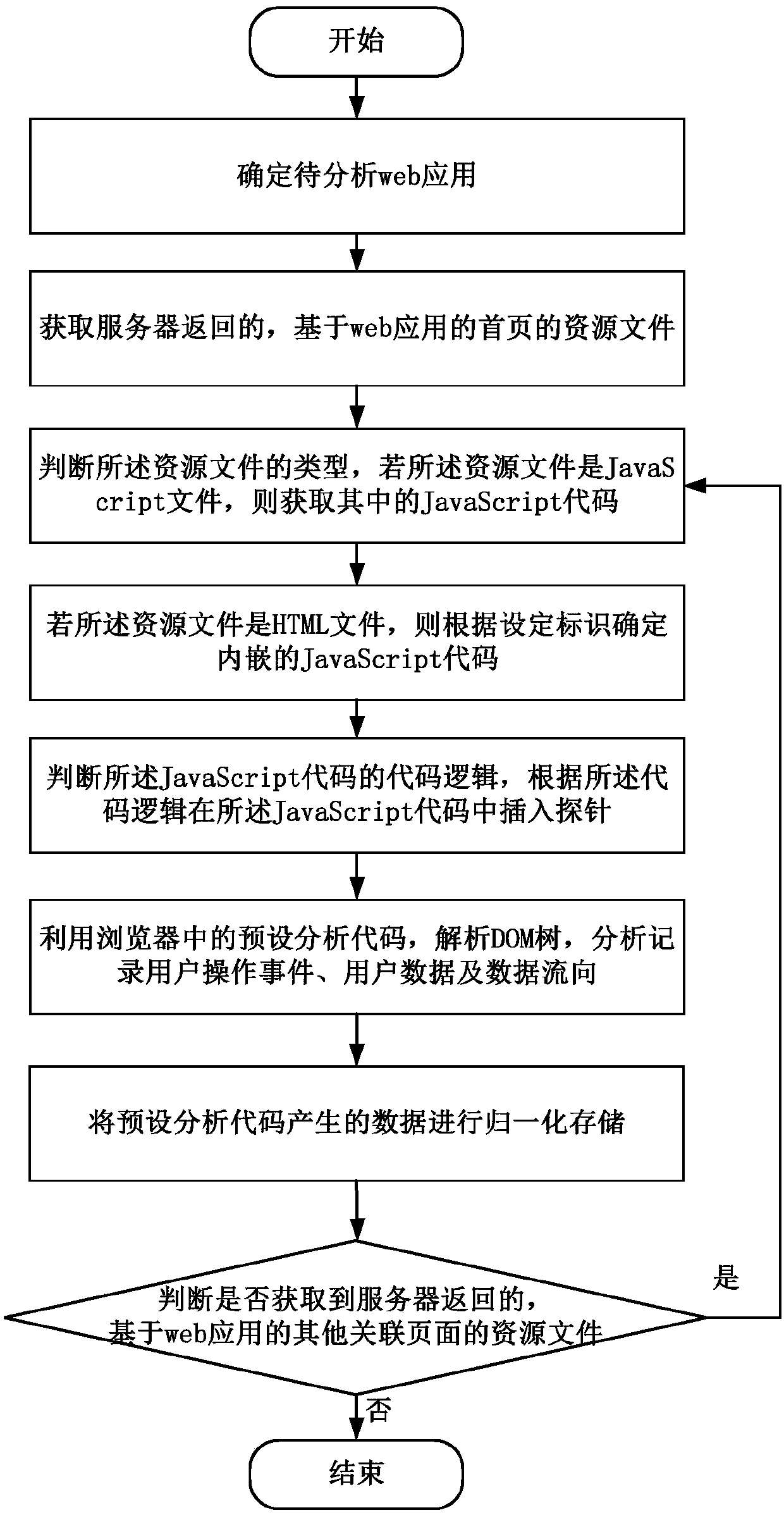
Data stream analysis method, apparatus and device, and medium
ActiveCN107622015ASolve inefficiencyTime consuming to solveReverse engineeringSoftware testing/debuggingWeb applicationLogical process
The present invention discloses a data stream analysis method, apparatus and device, and a medium, and relates to the data processing technology. The method comprises: obtaining a JavaScript code in aresource file corresponding to a to-be-analyzed web application; determining code logic of the JavaScript code, and inserting a probe into the JavaScript code according to the code logic, wherein theprobe is a segment of code; running the resource file inserted by a probe, according to the probe, obtaining data in the code logic process implemented by the web application by using the browser, and recording the data; and analyzing the web application according to the recorded data. According to the data stream analysis method, apparatus and device, and the medium provided by embodiments of the present invention, data obtaining and analysis in the code logic process implemented by the web application by using the browser are realized.
Owner:BEIJING INTERNETWARE LTD
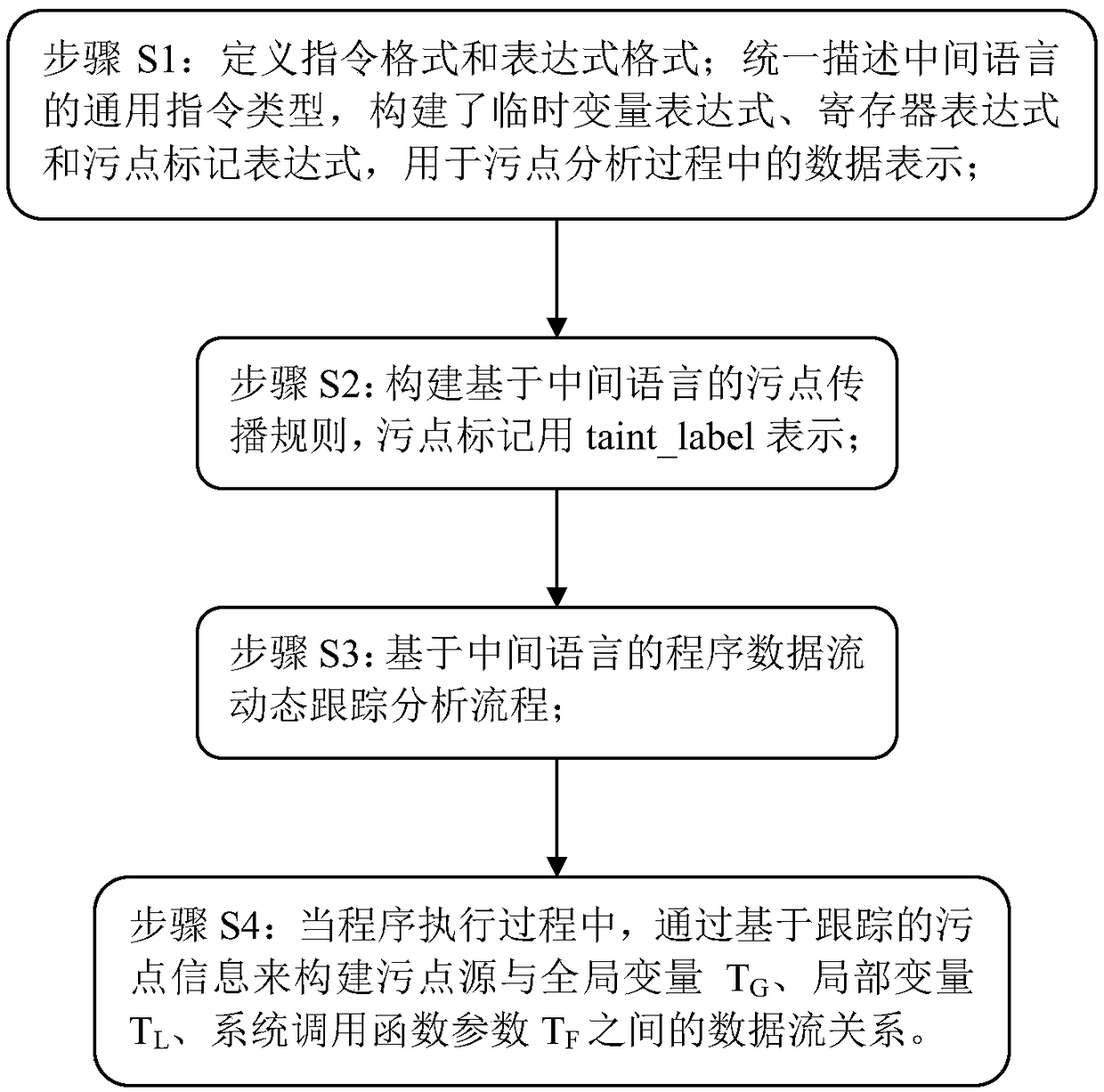
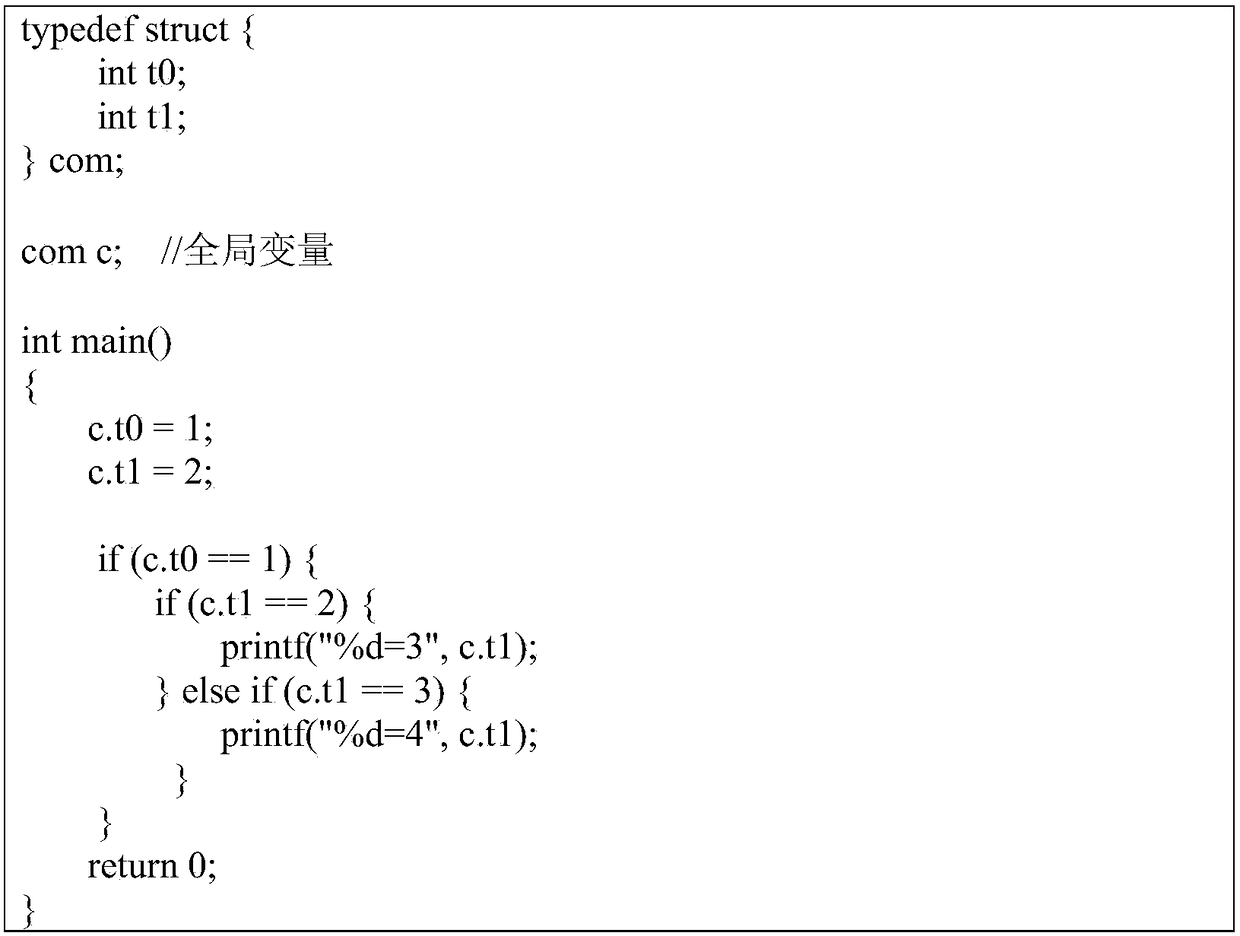
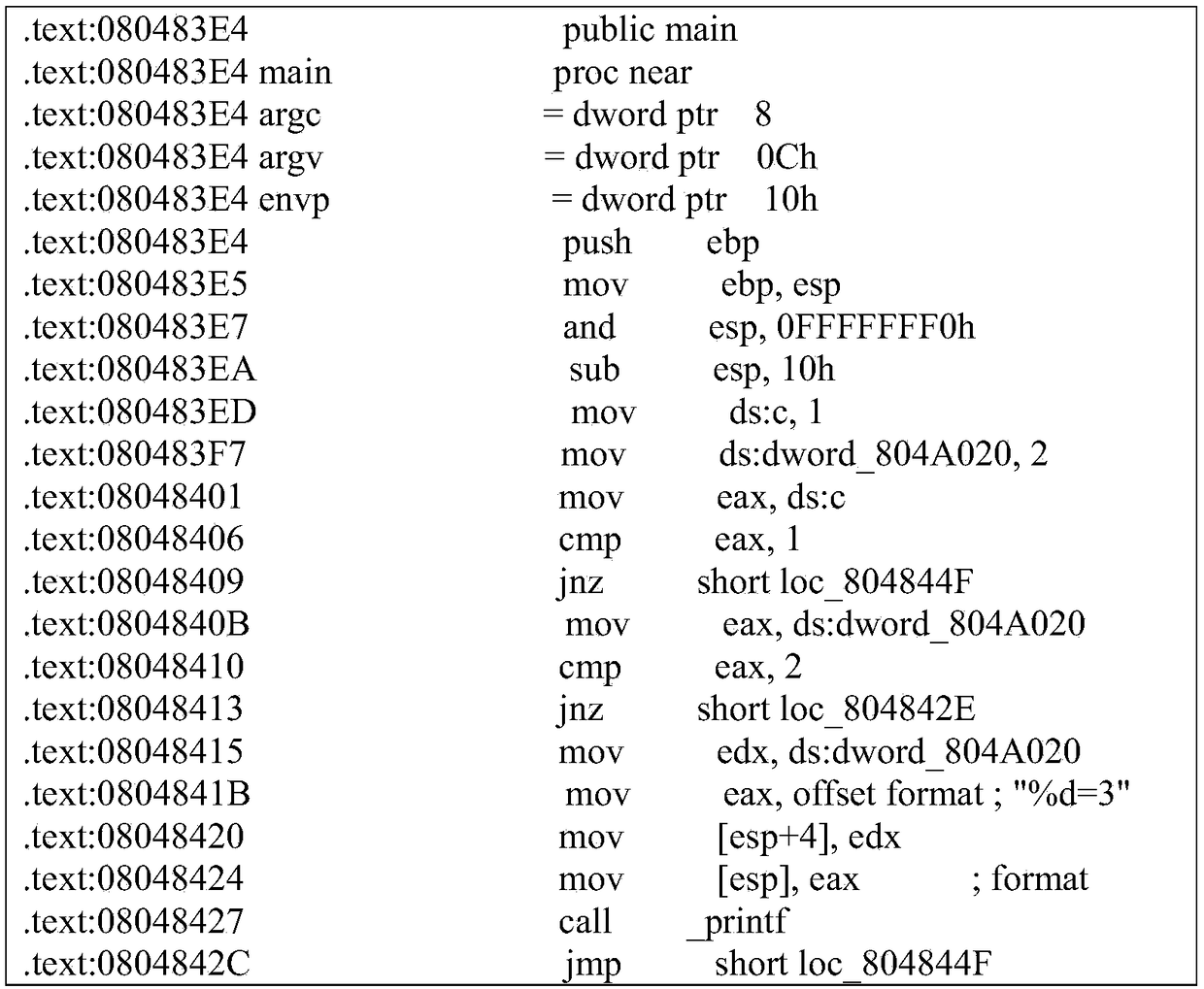
A software data stream analysis method based on intermediate language and stain analysis
ActiveCN109324971AEasy to captureRich expressive abilitySoftware testing/debuggingPlatform integrity maintainanceTemporary variableLocal variable
The invention discloses a software data flow analysis method based on intermediate language and stain analysis. The method comprises the following steps of S1 defining instruction format and expression format; uniformly describing the general instruction types of the intermediate languages, and construting the temporary variable expressions, register expressions and stain marker expressions for the data representation in stain analysis process; S2 constructing a stain propagation rule based on an intermediate language, wherein the stain mark is represented by a taint_label; S3 dynamic tracking an analysis flow based on a program data flow of the intermediate language; S4 when the program is executed, constructing the data flow relationship between the stain source and the global variableTG, the local variable TL, and the system call function parameter TF based on the tracked stain information. The method of the invention has the advantages of better accuracy, stronger comprehensiveness and richer information.
Owner:NAT UNIV OF DEFENSE TECH
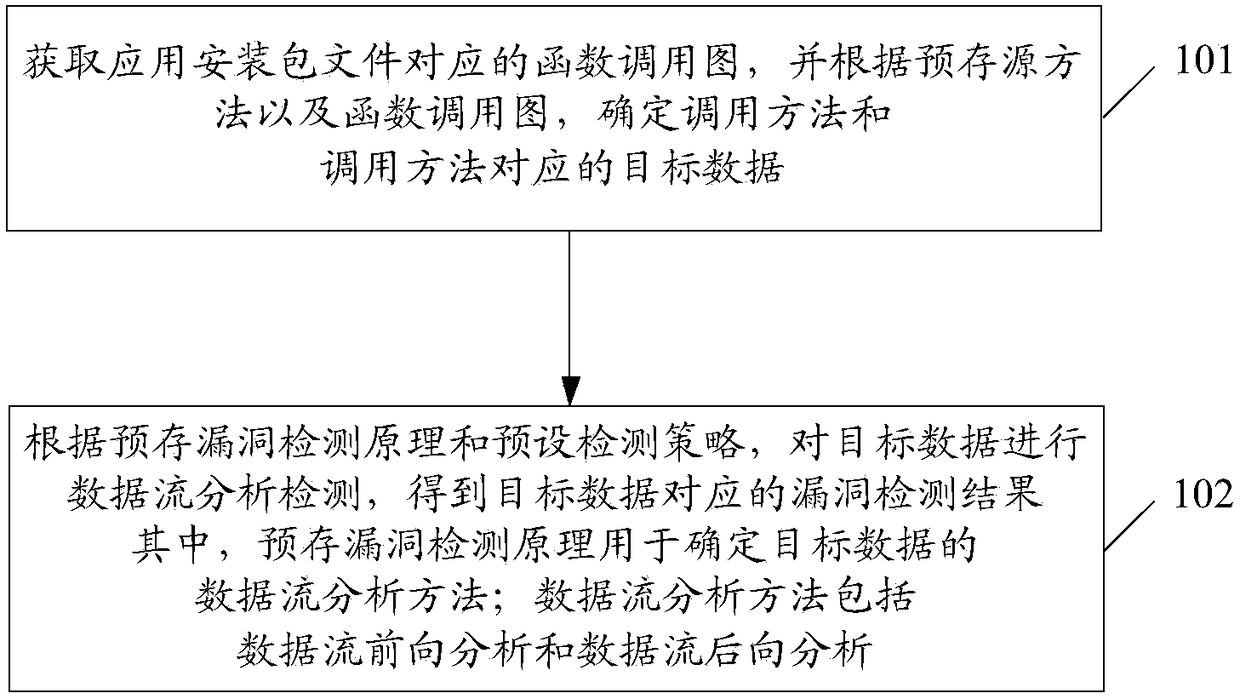
Vulnerability detection method and terminal, storage medium
PendingCN109101819AImprove detection efficiencyDetection is fast, accurate and comprehensivePlatform integrity maintainanceComputer terminalData stream analysis
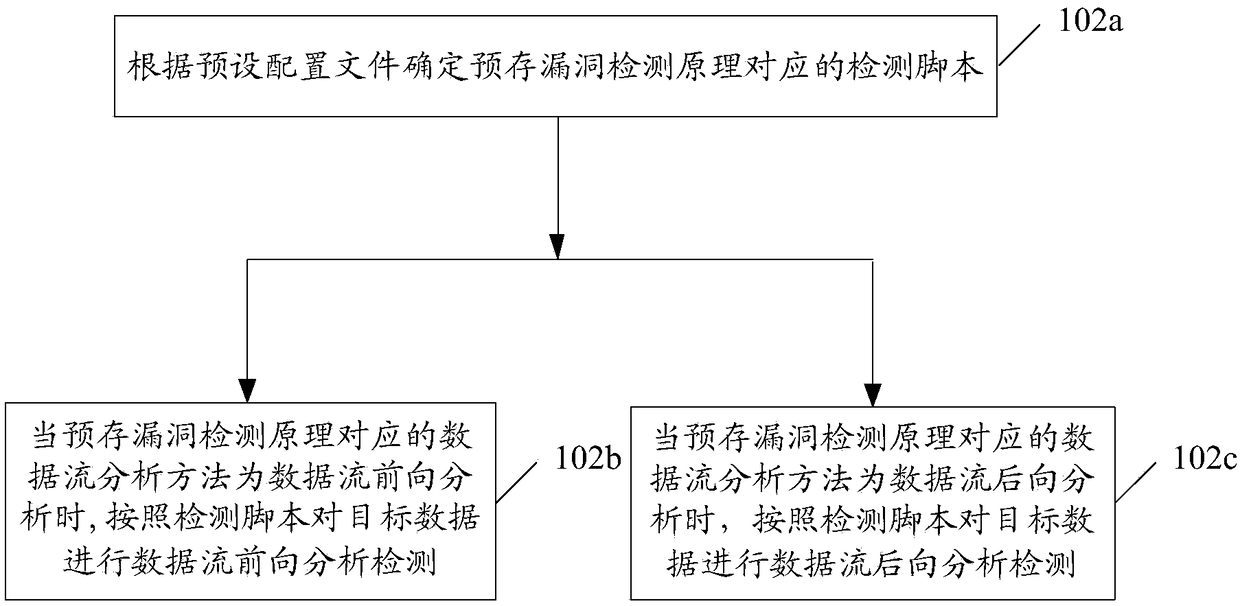
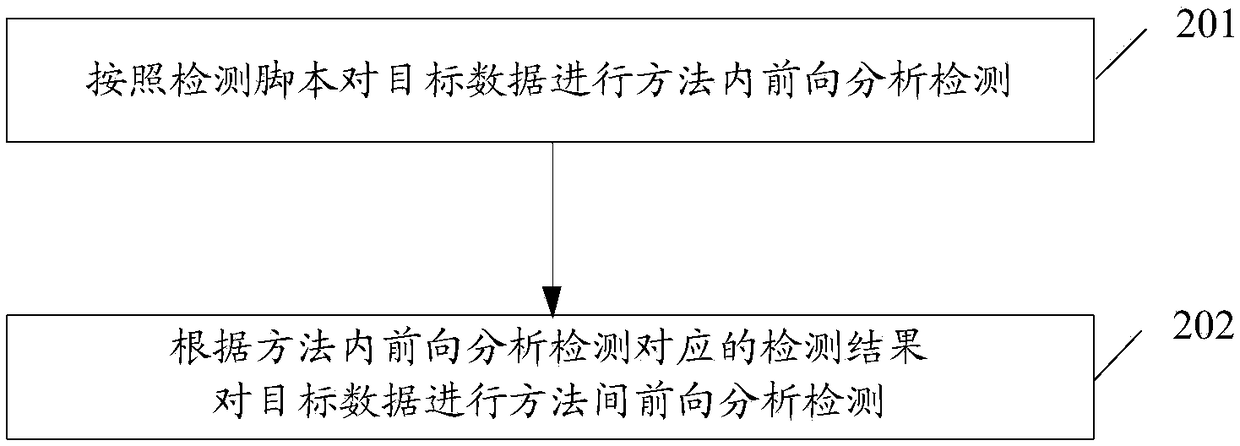
The embodiment of the invention discloses a vulnerability detection method and a terminal, and a storage medium. The method comprises the following steps: obtaining a function call diagram corresponding to an application installation package file; and according to the pre-stored source method and the function call diagram, determining the calling method and the target data corresponding to the calling method; obtaining a function call diagram corresponding to the application installation package file. According to the pre-stored vulnerability detection principle and the preset detection strategy, the target data is analyzed and detected by data stream, and the corresponding vulnerability detection results are obtained. Among them, the pre-stored vulnerability detection principle is used todetermine the data stream analysis method of the target data; Data stream analysis methods include data stream forward analysis and data stream backward analysis.
Owner:ZTE CORP +1
Software patch detection method and device based on data flow analysis
ActiveCN111177733AEliminate hard-to-recognize puzzlesImprove detection efficiencyPlatform integrity maintainanceAlgorithmTheoretical computer science
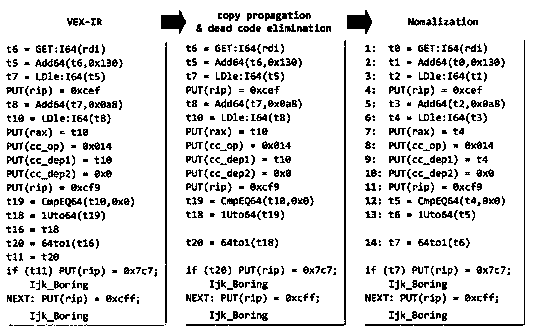
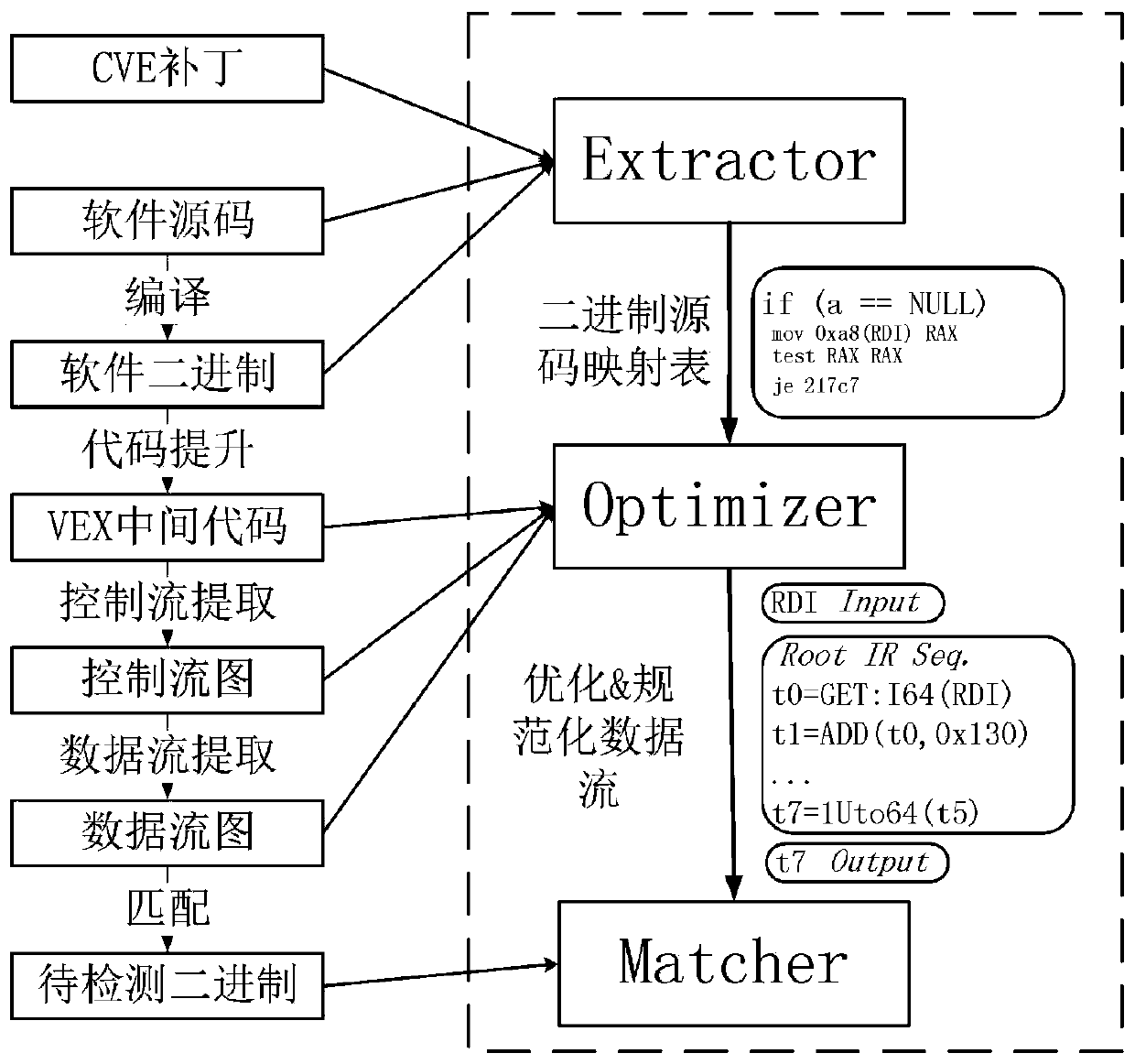
The invention relates to a software patch detection method based on data flow analysis. The software patch detection method comprises the following steps of: analyzing a patch code by using Extractor,and sequentially selecting and detecting modified semantics of an assignment statement, a conditional statement, a function call statement, a type related statement and other types of statements in the patch code as features of a patch to be detected; establishing a mapping relationship between a binary code and a source code; selecting VEX-IR as an intermediate code for binary code promotion ofequipment firmware in an Internet of Things environment, analyzing the binary code by using the open-source Angr, and extracting a control flow, wherein the control flow takes functions as units, andeach function comprises a control flow with nodes as basic blocks and program skip semanteme as sides; analyzing the data flow in the basic blocks, reversely analyzing codes of the basic blocks one byone, and extracting a use chain of a variable in each statement; analyzing the data flow across the basic blocks; optimizing the extracted data stream; and acquiring the patch features from the basicblocks, and performing multi-stage matching on the patch features.
Owner:BEIHANG UNIV
Information flow analysis method based on blockchain and mobile Internet, and cloud computing platform
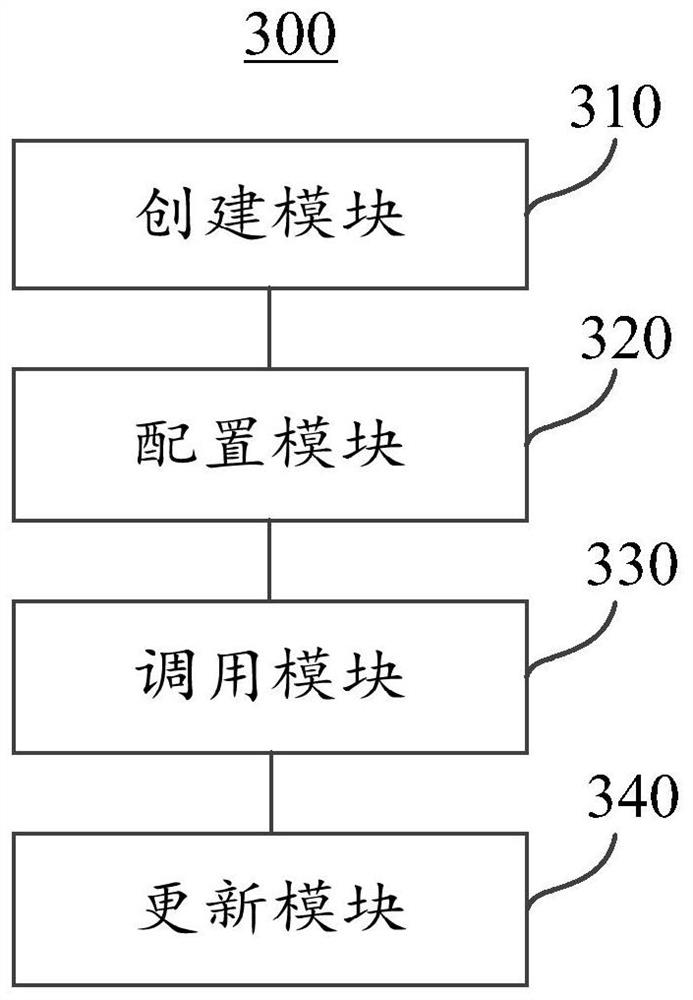
ActiveCN111695903APrecise Protection Analysis Rule MechanismImprove payment securityProgram loading/initiatingProtocol authorisationPaymentAnalysis data
The embodiment of the invention provides an information flow analysis method based on a blockchain and a mobile Internet, and a cloud computing platform. The method comprises the steps of according tothe protection label of each protection consensus verification project, creating a record dynamic link library file used for recording different protection analysis rule information of respective execution protection, analyzing rule information according to protection on the basis; configuring corresponding dynamic metric tables and payment verification metric rules for the protection consensus verification items, configuring the dynamic metric tables and the payment verification metric rules to the corresponding protection consensus verification items, executing protection data flow analysis, and further performing rule updating on the record dynamic link library file according to the obtained protection information flow analysis data. Thus, in the payment verification process, protection can be carried out based on the payment verification measurement rules of multiple different protection consensus verification items, rule updating is continuously carried out according to the protection information flow analysis data, a more accurate protection analysis rule mechanism can be realized, and the payment security can be improved.
Owner:上海百源嘉合信息技术有限公司
Android mobile attack traceability method
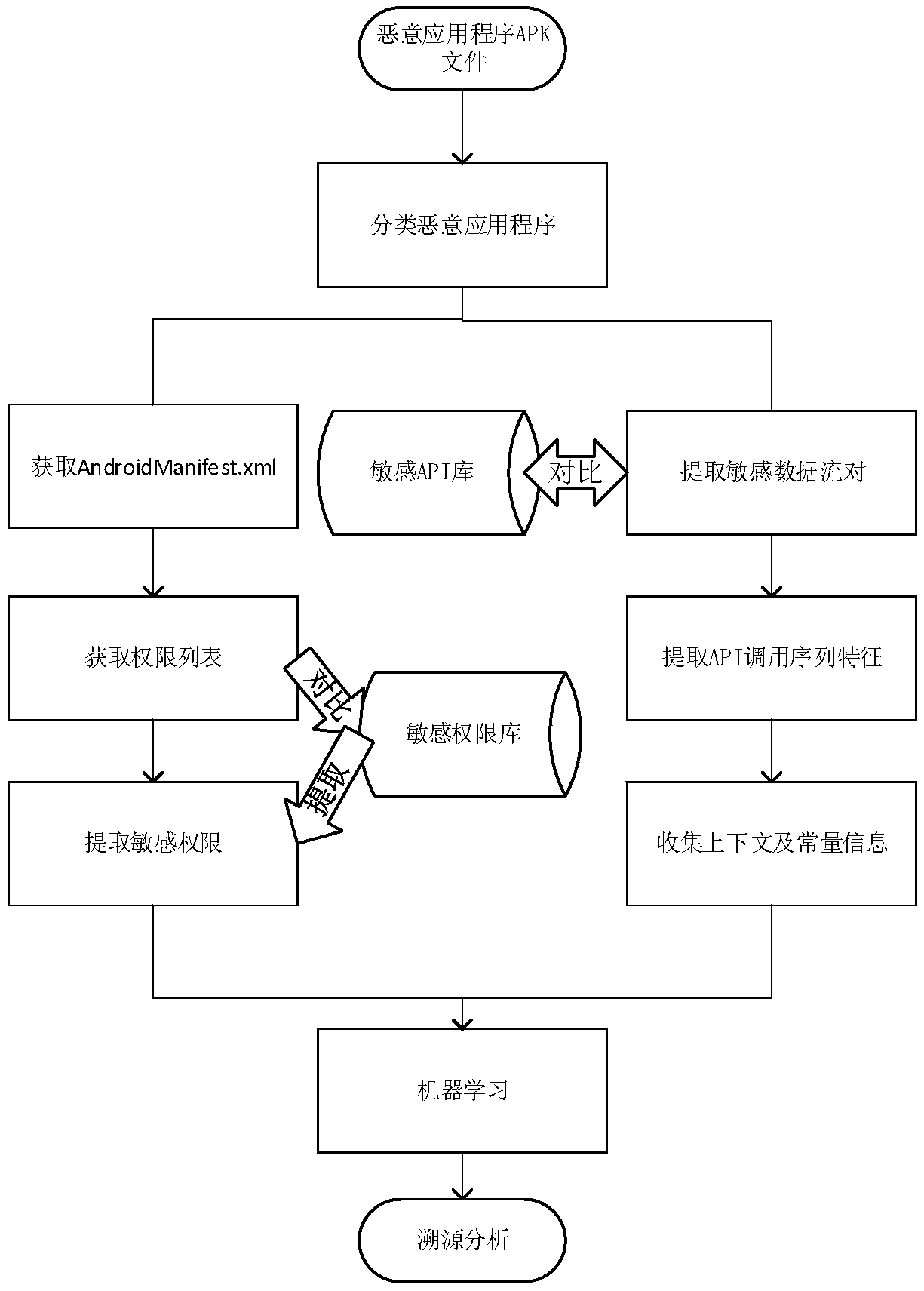
InactiveCN108681671AHigh precisionAccurate traceabilityComputing modelsCharacter and pattern recognitionApplication softwareTwo step
The invention discloses an android mobile attack traceability method, which comprises the following steps that: reading a claim list applied by a malicious application from the AndroidManifest.xml file of the malicious application, and matching with a sensitive permission library to determine sensitive permission; utilizing a data stream analysis tool to extract the sensitive data stream pair of the malicious application, and extracting a sensitive API calling sequence characteristic, context information and constant information between the API calling sequence and the sensitive data stream pair in the sensitive data stream pair; and combining with each piece of information obtained in the above two steps, and utilizing a clustering or classified machine learning method to carry out tracking and traceability on the malicious application. By use of the method, the traceability of the malicious application can be realized, and development personnel or organizations are tracked.
Owner:UNIV OF SCI & TECH OF CHINA
System and Method for UAV Based Mobile Messaging
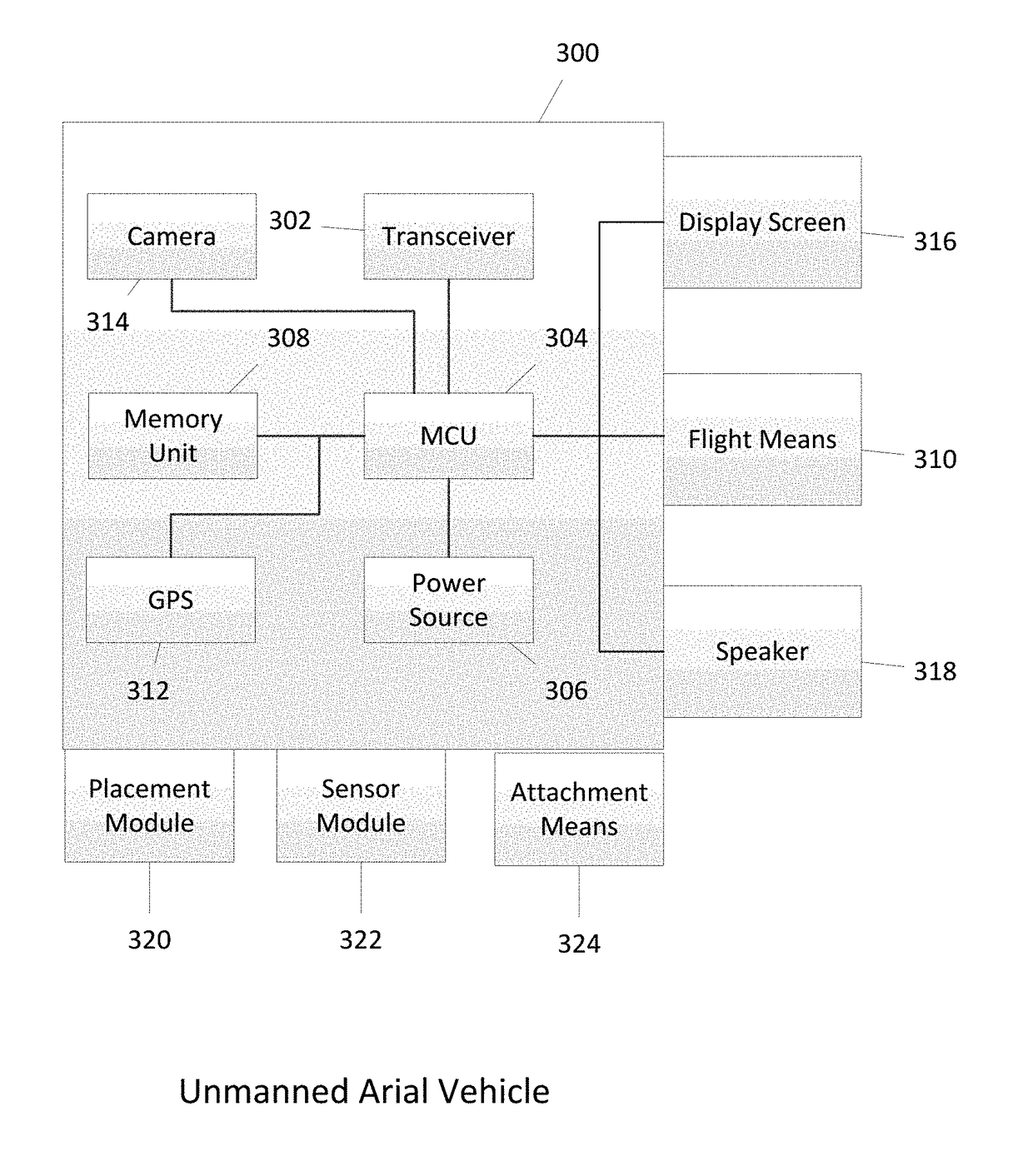
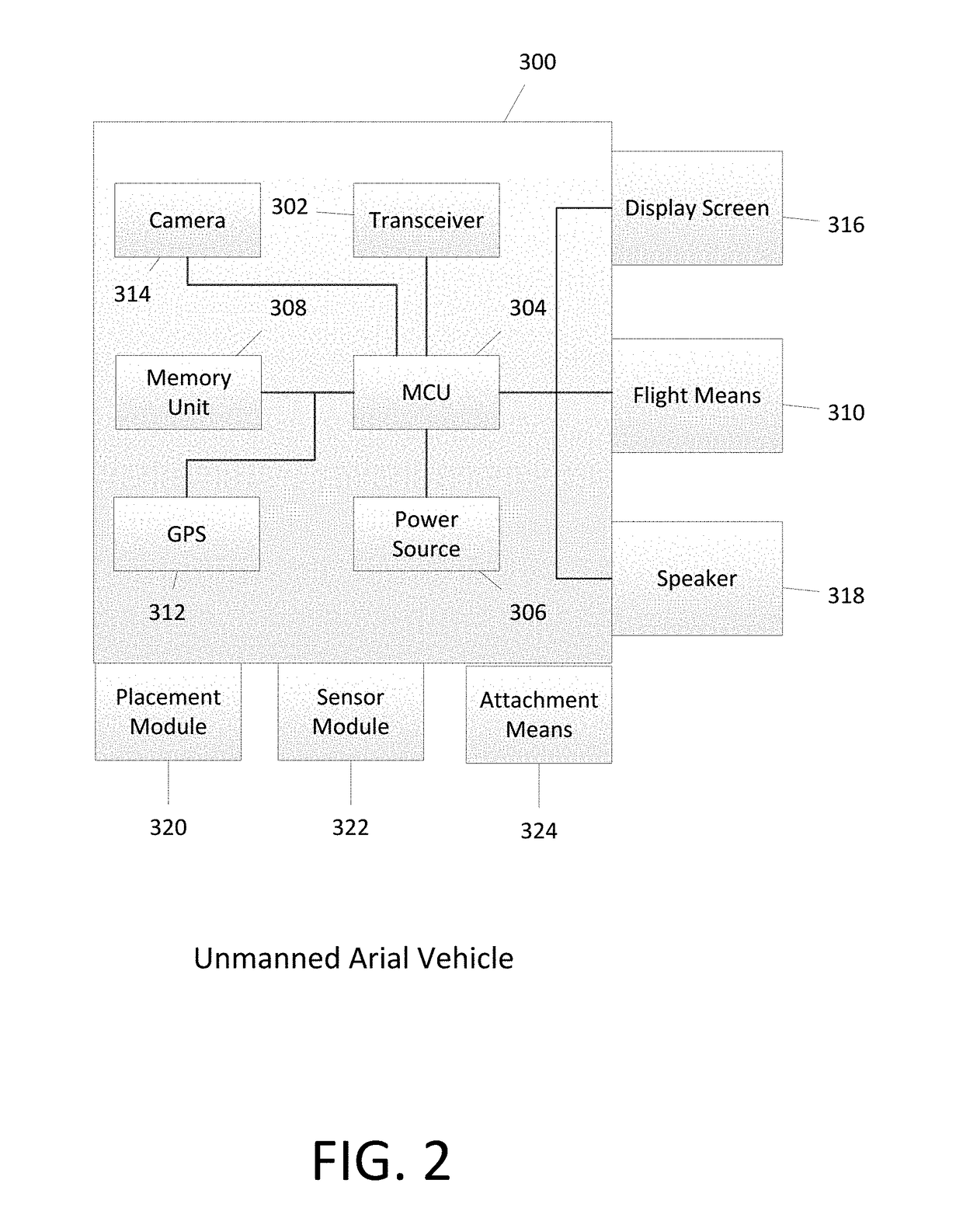
InactiveUS20180308130A1Well formedUnmanned aerial vehiclesRemote controlled aircraftData streamData file
A method for executing a flight mission by one or more unmanned aerial vehicles is disclosed. The method comprises receiving, from an unmanned aerial vehicle, a data stream containing audience location information; analyzing the audience location information to determine the presence of one or more people; receiving an instruction setting a predetermined number of people; determining whether a number of people at the location is equal to or greater than the predetermined number of people; retrieving a message data file; transmitting the message data file to the unmanned aerial vehicle; and displaying, by the unmanned aerial vehicle, the message data file on a display screen integral to the first unmanned aerial vehicle. In other embodiments, individuals may present visual information to the UAV. The system then selects a response based on the visual information presented to the UAV.
Owner:HAFEEZ USMAN +1
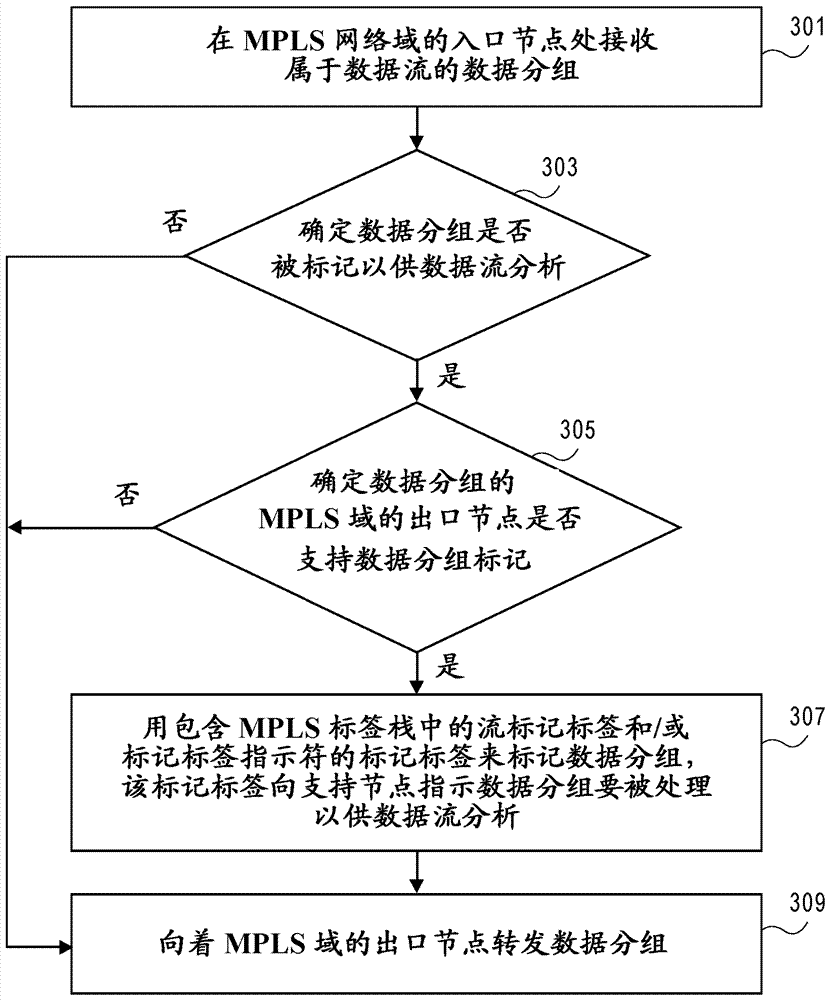
Method of packet marking for flow analytics
A method is implemented by a node of a network domain having a plurality of nodes, where the node functions as an ingress node of the network domain for a data flow. The method enables data flow analysis across the network domain. The method includes receiving a data packet belonging to a data flow at an ingress node of the network domain, determining whether the data packet is to be marked for the data flow analysis, determining whether an egress node of the network domain for the data flow supports data packet marking, marking the data packet with a marking label indicating to supporting nodes in the network domain that the data packet is to be processed for data flow analysis, and forwarding the data packet toward the egress node of the network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
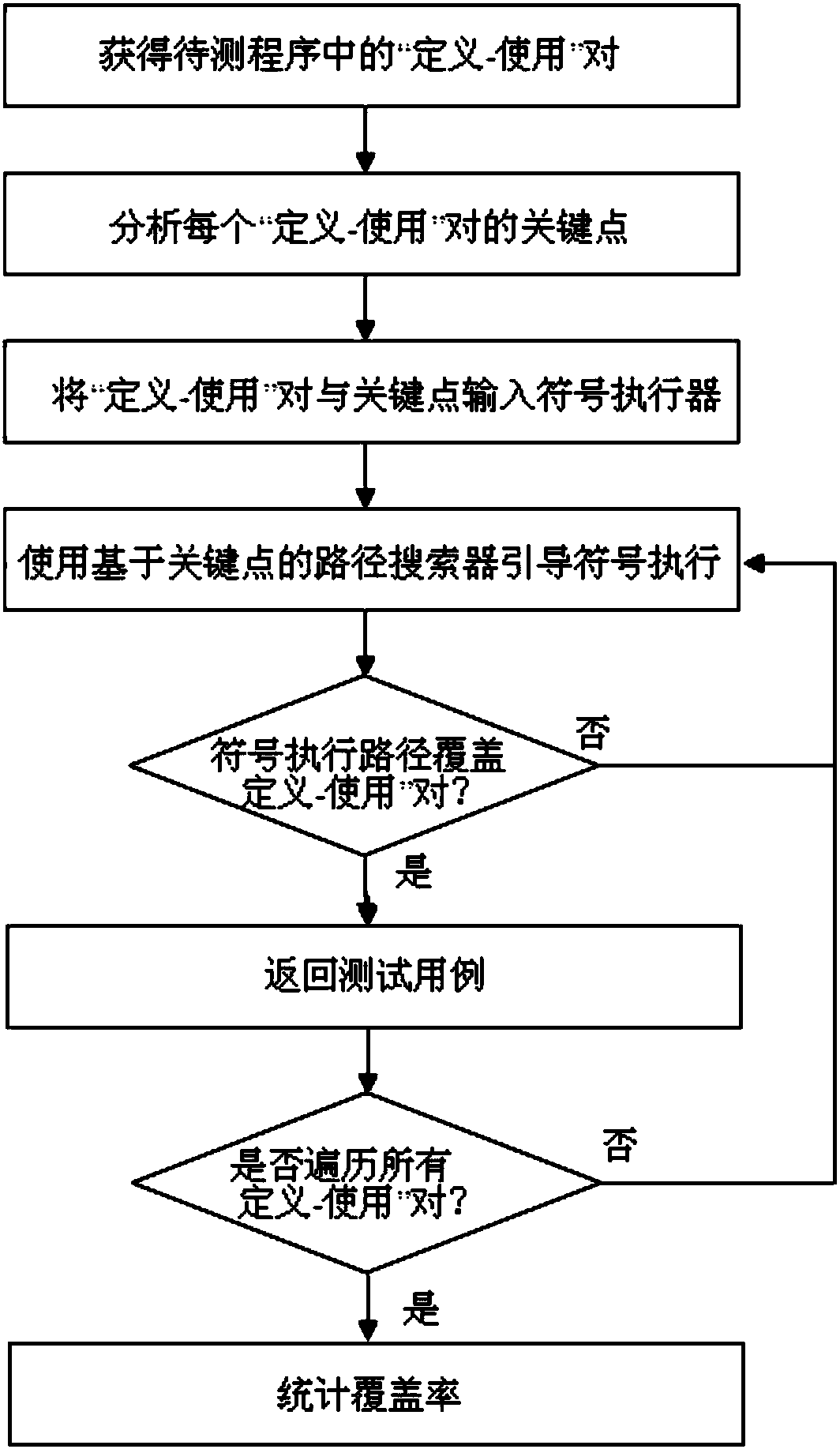
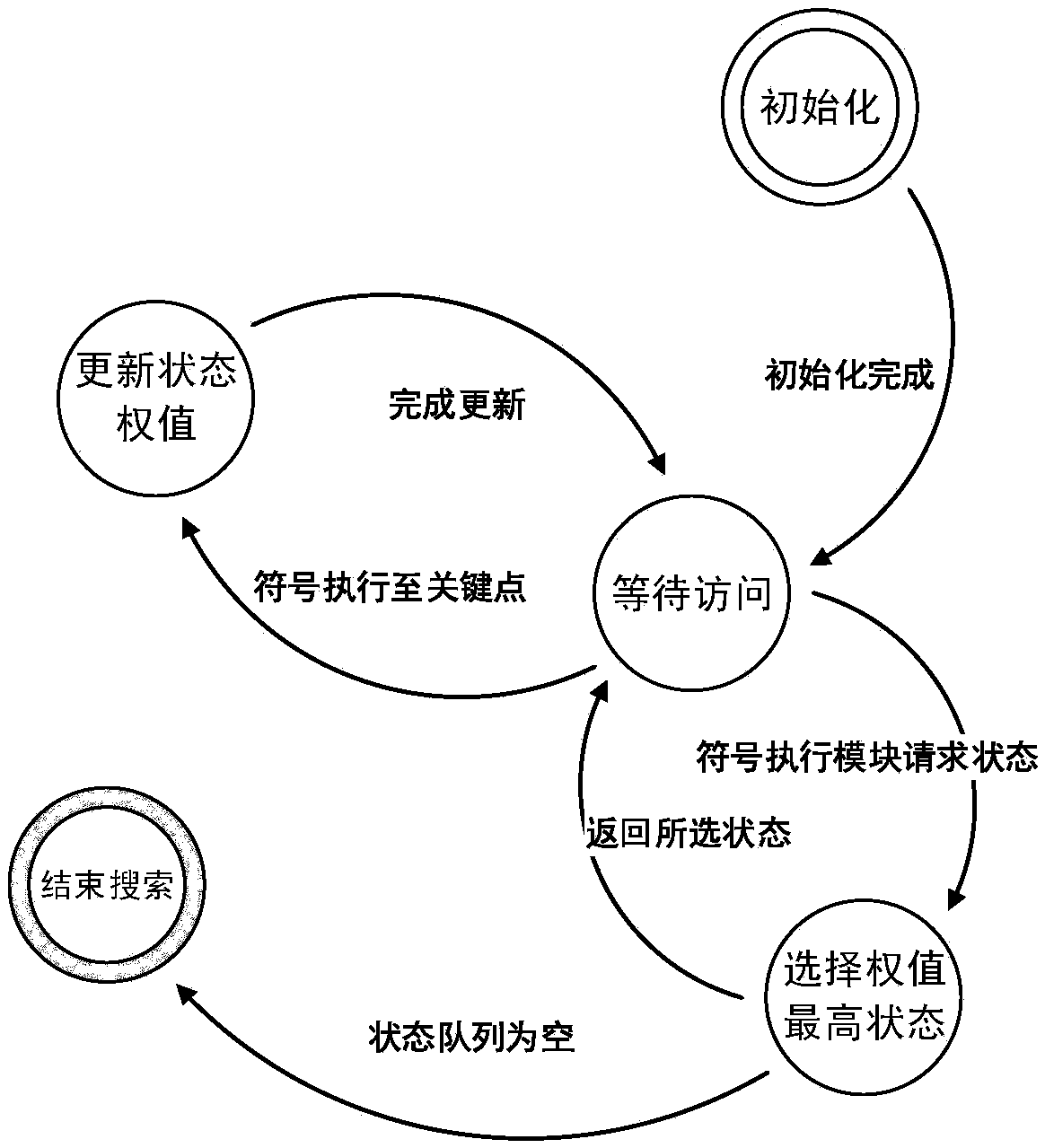
Data stream testing method and testing system based on key point guidance
InactiveCN107656863ASearch orientationEfficient coverage definitionSoftware testing/debuggingProgramming languagePath cover
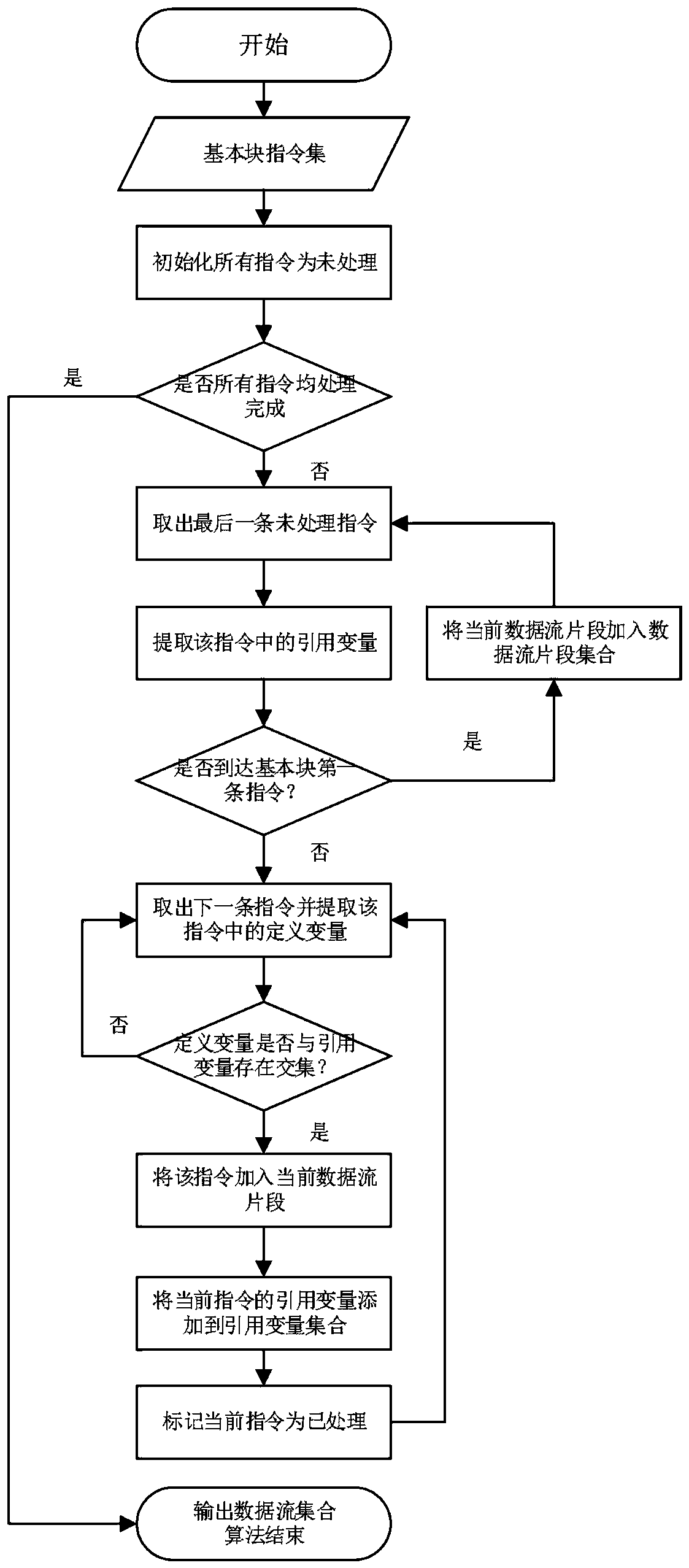
The invention discloses a data stream testing method based on key point guidance. The method comprises the following steps that: through a standard data stream analysis method, obtaining a definition-use pair in a program to be tested; according to a control stream analysis method, analyzing key points in the definition-use pair; inputting the definition-use pair and the key point into a symbol actuator; using a path searcher based on the key point to guide a symbol in execution by the symbol actuator; if a symbol execution path covers the definition-use pair, returning a test case corresponding to the symbol execution path, otherwise, continuously executing S4 until the corresponding test case is generated for all definition-use pairs or all symbol execution paths finish being executed, and ending the execution of the symbol actuator; and according to a symbol execution result, carrying out statistics on a coverage rate. The invention also discloses a data stream testing system basedon the key point guidance.
Owner:EAST CHINA NORMAL UNIV
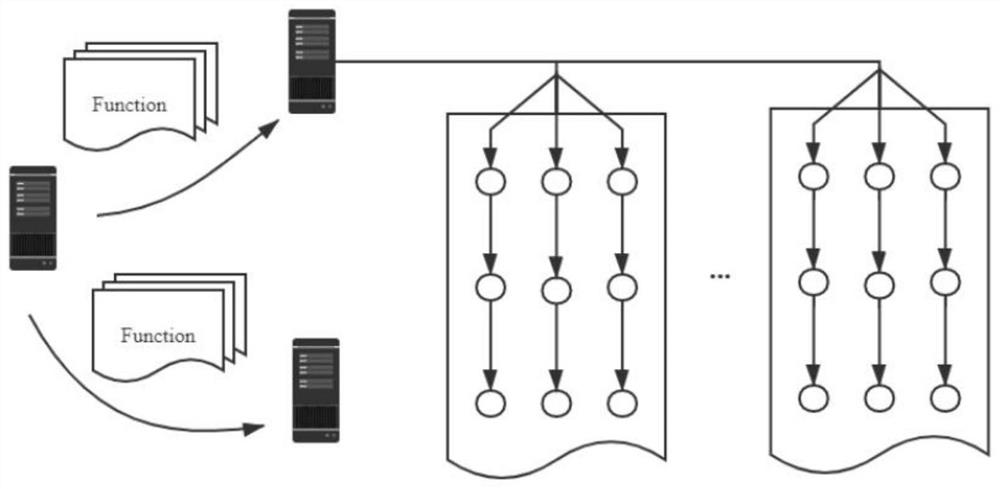
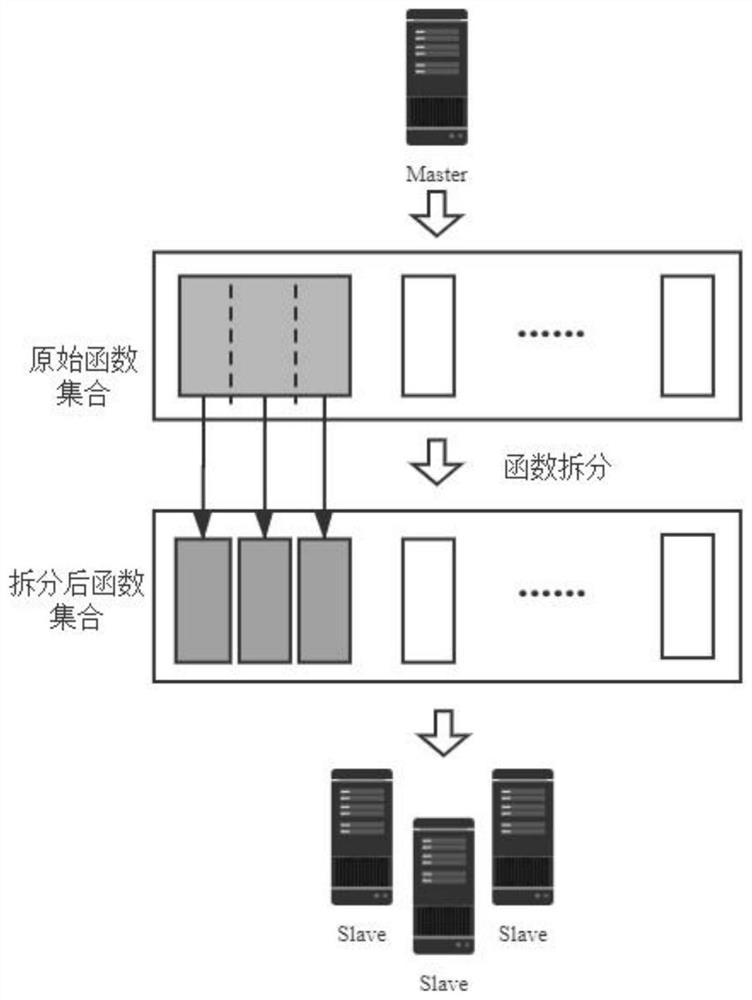
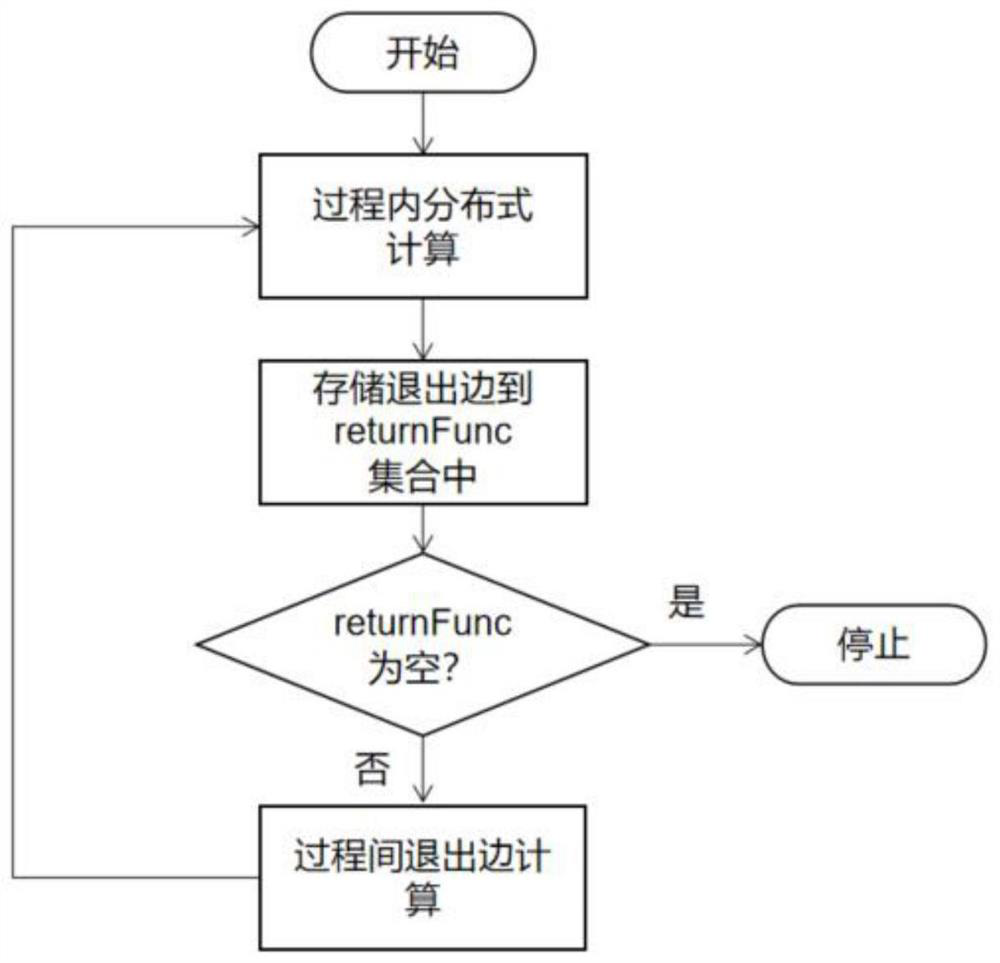
Large-scale data flow analysis method and system based on Spark
ActiveCN113434548AQuick analysisStrong scalabilityDigital data information retrievalInterprogram communicationComputational scienceData display
The invention discloses a large-scale data flow analysis method and system based on Spark, and the method comprises the steps: constructing a distributed calculation framework based on Spark, and carrying out the distributed data flow analysis of a target code through the distributed calculation framework, wherein the distributed data flow analysis comprises an intra-process preprocessing stage and a distributed inter-process data integration stage. The system comprises a data acquisition module, a data processing module, a data analysis module, a data storage module and a data display module. According to the method and system, a two-stage parallel strategy is adopted, parallel computing is carried out in a multi-entry mode, high expandability is achieved, meanwhile, the load balancing problem of distributed computing is considered, the computing power advantage of a distributed cluster can be fully utilized, and static data flow analysis is accelerated.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Real-time processing of data streams received from instrumented software
ActiveCN107430545ASoftware testing/debuggingSpecial data processing applicationsThresholdingData mining
An analysis system receives data streams generated by instances of instrumented software executing on external systems. The analysis system evaluates an expression using data values of the data streams over a plurality of time intervals. For example, the analysis system may aggregate data values of data streams for each time interval. The analysis system determines whether or not a data stream is considered for a time interval based on when the data value arrives during the time interval. The analysis system determines a maximum expected delay value for each data stream being processed. The analysis system evaluates the expression using data values that arrive before their maximum expected delay values. The analysis system also determines a failure threshold value for a data stream. If a data value of a data stream fails to arrive before the failure threshold value, the analysis system marks the data stream as dead.
Owner:SPLUNK INC
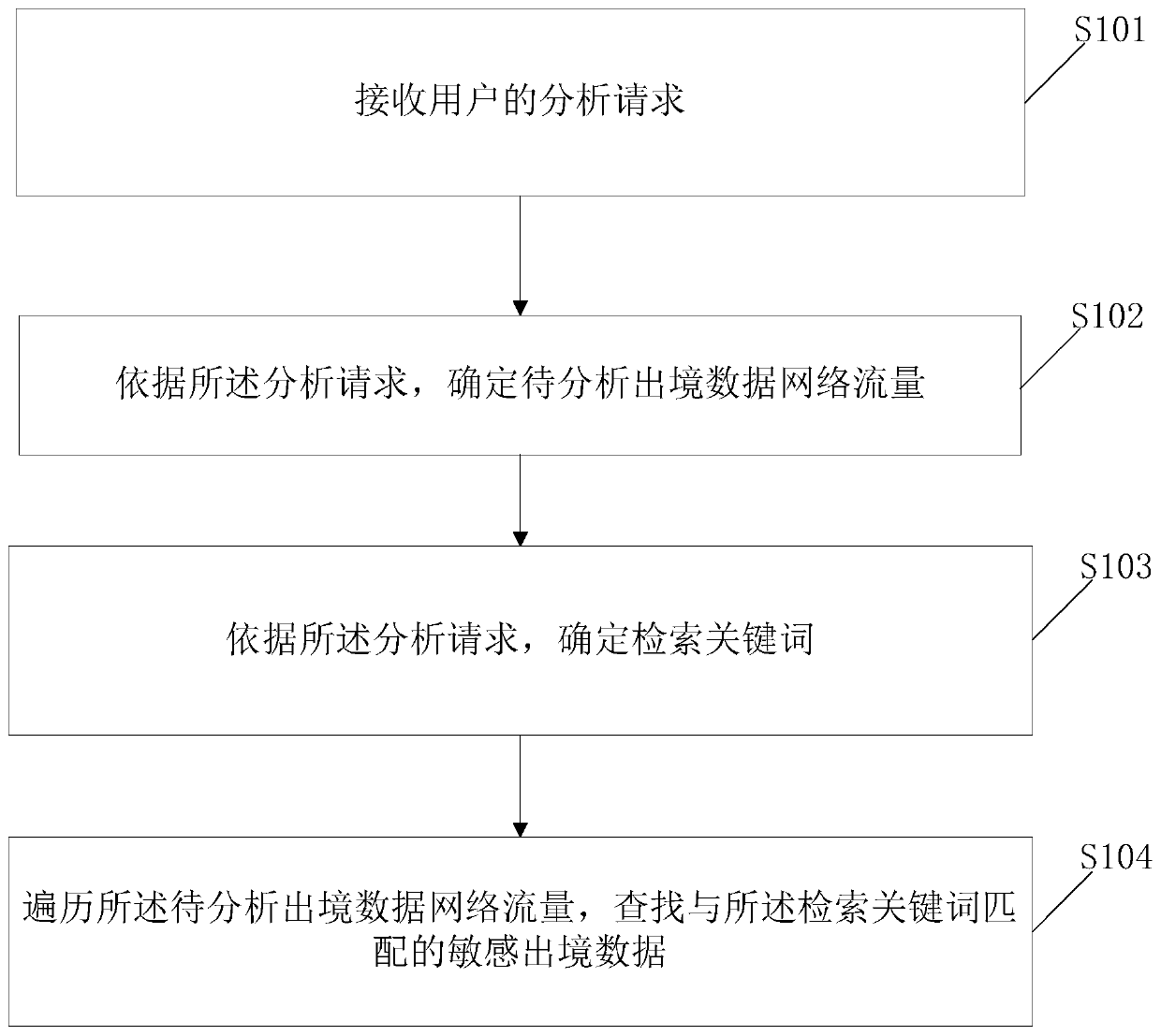
Network safety analysis method and device based on exit data network traffic
PendingCN111581371AImplementation of security analysisSpecial data processing applicationsWeb data queryingInternet trafficEngineering
The invention discloses a network safety analysis method based on exit data network traffic. The method comprises the following steps: receiving an analysis request of a user; determining to-be-analyzed exit data network flow and sum according to the analysis request; determining a retrieval keyword according to the analysis request; and traversing the to-be-analyzed exit data network traffic, andsearching for sensitive exit data matched with the retrieval keyword. The invention discloses a safety analysis method. The retrieval keywords and the to-be-analyzed exit data network flow in the analysis request are determined, the to-be-analyzed exit data network flow is traversed, and the sensitive exit data matched with the retrieval keywords is searched, so that the safety analysis of the to-be-analyzed exit data network flow from a bottom data flow analysis level is realized.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
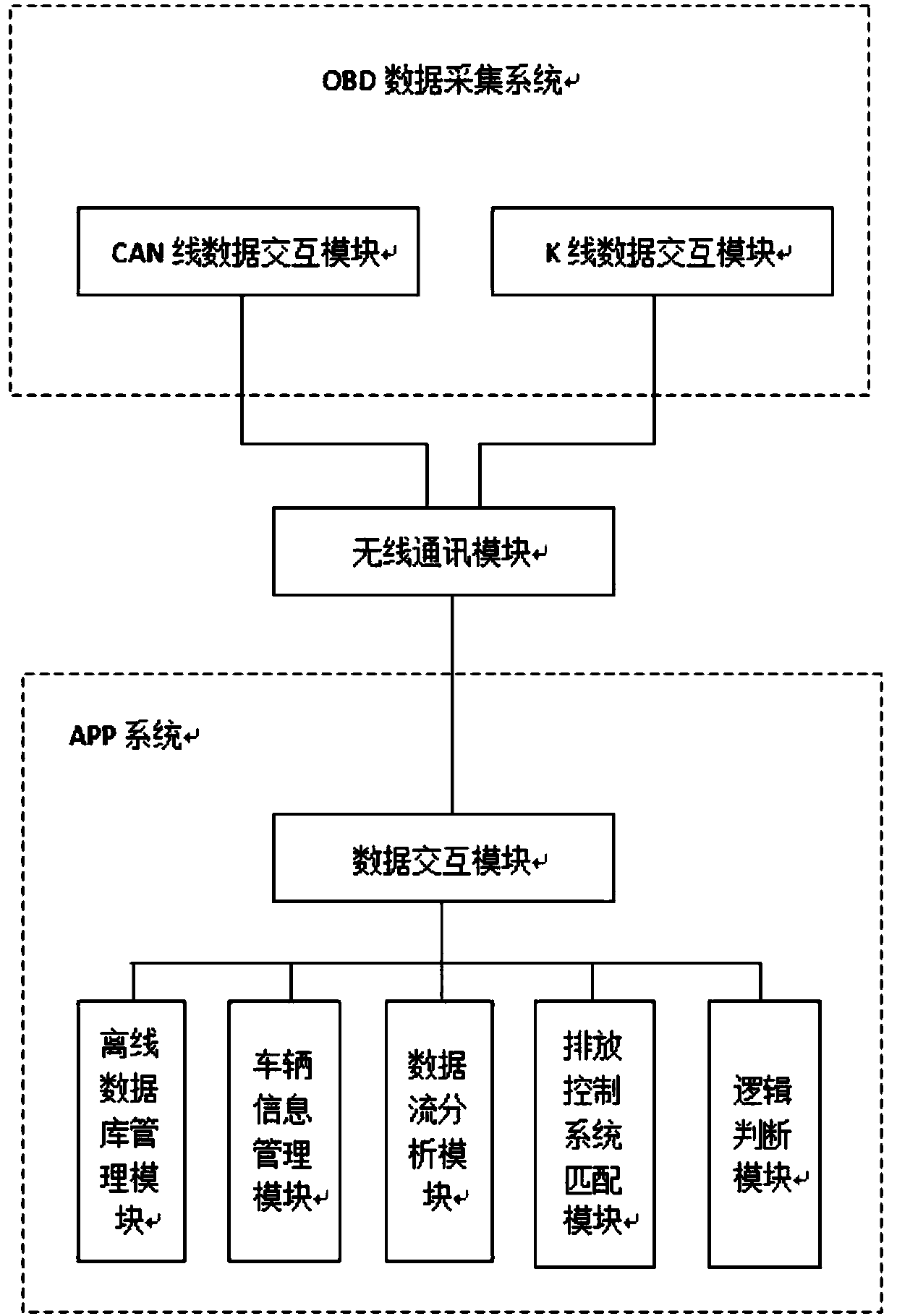
Detection system used for engine emission control system
The present invention discloses a detection system used for an engine emission control system. The detection system comprises an OBD data acquisition system and an APP system which are in signal connection via a wireless communication module A and a wireless communication module B, the OBD data acquisition system comprises a CAN wire data interaction module and a K wire data interaction module which are both connected with the wireless communication modules, and the APP system comprises a data interaction module, a vehicle information management module, an offline database management module, an emission control system matching module, a data stream analysis module and a logical judgment module. According to the detection system used for the engine emission control system provided by the present invention, aiming at different emission processing systems, and by a logical judgment method, whether the vehicles have the emission cheat means is inspected, thereby realizing an effective method of relieving the current air pollution condition.
Owner:CHINA AUTOMOTIVE TECH & RES CENT
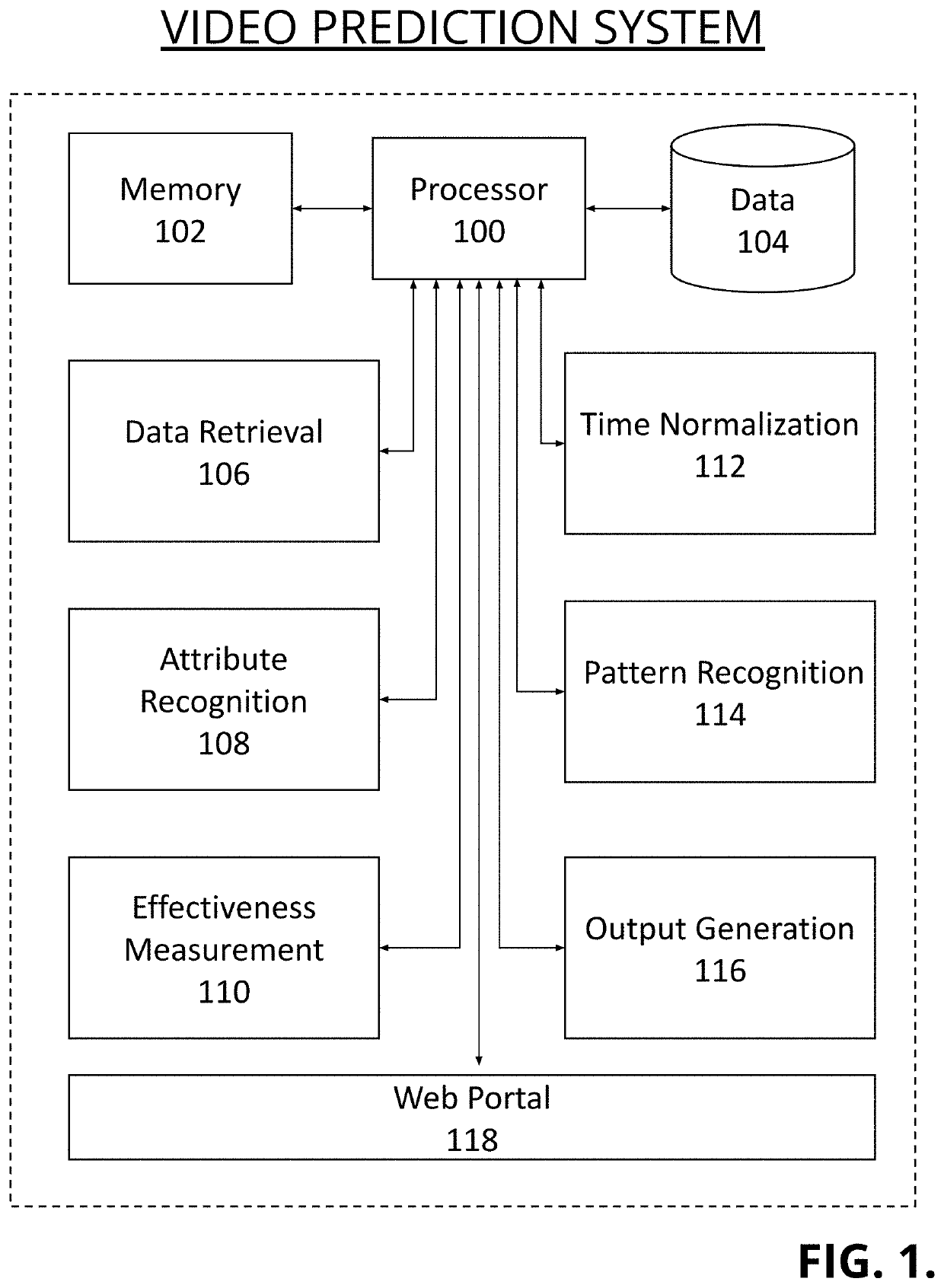
System and methods to predict winning TV ads, online videos, and other audiovisual content before production
PendingUS20220351236A1Performance of was minimizedImprove performanceSelective content distributionMarketingDigital videoEngineering
The invention discloses a system and methods for predicting attributes of effective television ads, digital video, and other audiovisual content before production. Output comprises instructions for producing videos optimized to achieve at least one performance objective. Some embodiments predict performance of existing video, such as predicting winning Super Bowl ads before they air. The system comprises one or more processors and a memory configured to receive at least one data stream of audiovisual content in at least one public and / or a private domain; analyze said data streams to determine one or more attributes associated with said data streams; analyze said data streams to determine one or more performance scores associated with said data streams; attribute at least a portion of one said performance score to at least a portion of one said attribute associated with said data streams, and output, to a memory, any or all combinations thereof.
Owner:VIDEOQUANT INC
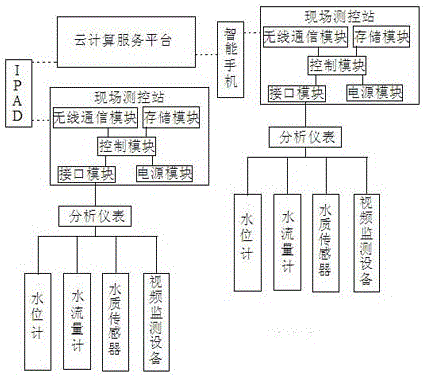
System and method for realizing water resource monitoring on basis of large-volume data stream analysis
InactiveCN105067787AReduce data processingImprove regulatory efficiencyTesting waterVideo monitoringStream gauge
The invention belongs to the technical field of water resource management and relates to a system and a method for realizing water resource monitoring on the basis of large-volume data stream analysis. The system comprises a site measurement and control station, a mobile terminal and a cloud computing service platform, wherein the site measurement and control station is provided with a water level meter, a water flow meter, a water quality sensor and a video monitoring device which are connected with a site intelligent controller through an analysis instrument; the mobile terminal has a data communication module and a GPS (global positioning system) positioning module; the cloud computing service platform adopts cloud storage and realizes distributive storage of massive data. Compared with the prior art, data information is acquired by the water level meter, the water flow meter, the water quality sensor and the video monitoring device and then simplified by the analysis instrument, the simplified data information is further screened through software in the mobile terminal, the data information exceeding a threshold value is uploaded to the cloud computing service platform, accordingly, the data processing load of the whole system is reduced, and the monitoring efficiency is improved.
Owner:BEIJING LIHESHUNDA ELECTRONICS TECH
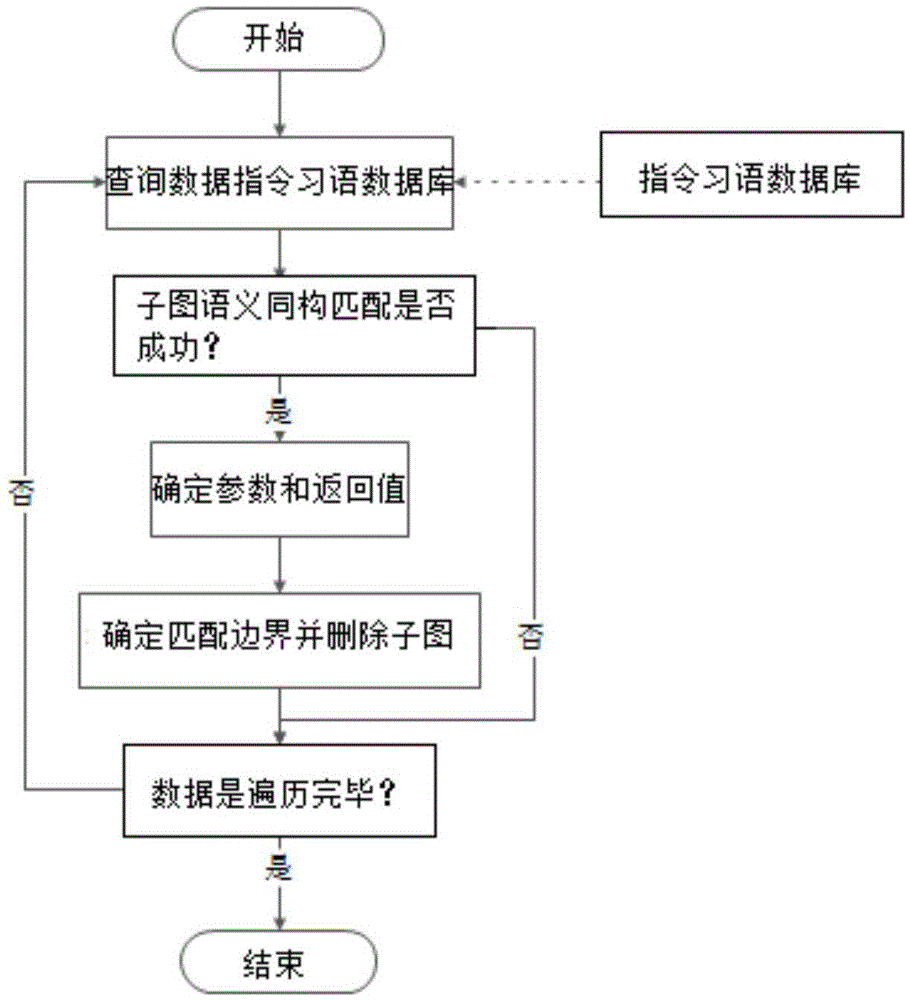
Sub-graph semantic isomorphism based instruction idiom identification method
ActiveCN105589728AHigh precisionImprove recognition accuracyDecompilation/disassemblyProgram controlData dependency graphReverse analysis
The invention discloses an analysis method of instruction idioms in reverse analysis. The analysis method of the instruction idioms in reverse analysis comprises the steps of performing data stream analysis for an assembly instruction sequence stream in a basic block; constructing a data dependence graph of the instruction sequence stream based on a definition-use relationship; then performing sub-graph semantic isomorphism matching for each connection sub-graph in the data dependence graph and a template in a template library; discovering a semantic isomorphism sub-graph; performing regulated reduction for the isomorphism sub-graph; and analyzing abstract operation of the sub-graph and corresponding operands. The analysis method of the instruction idioms in reverse analysis can efficiently increase the abstraction level of intermediate codes in the reverse analysis and improve code analysis efficiency.
Owner:弘毅视界(北京)科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com