Software patch detection method and device based on data flow analysis
A technology of data flow analysis and detection method, applied in the computer field, can solve problems such as low efficiency, limited detection accuracy, and unsatisfactory practical applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
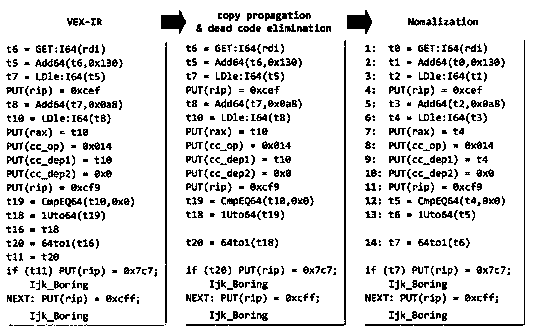
[0039] figure 1 It is a flowchart of a software patch detection method based on data flow analysis in an embodiment of the present invention, such as figure 1 As shown, a software patch detection method based on data flow analysis, including:
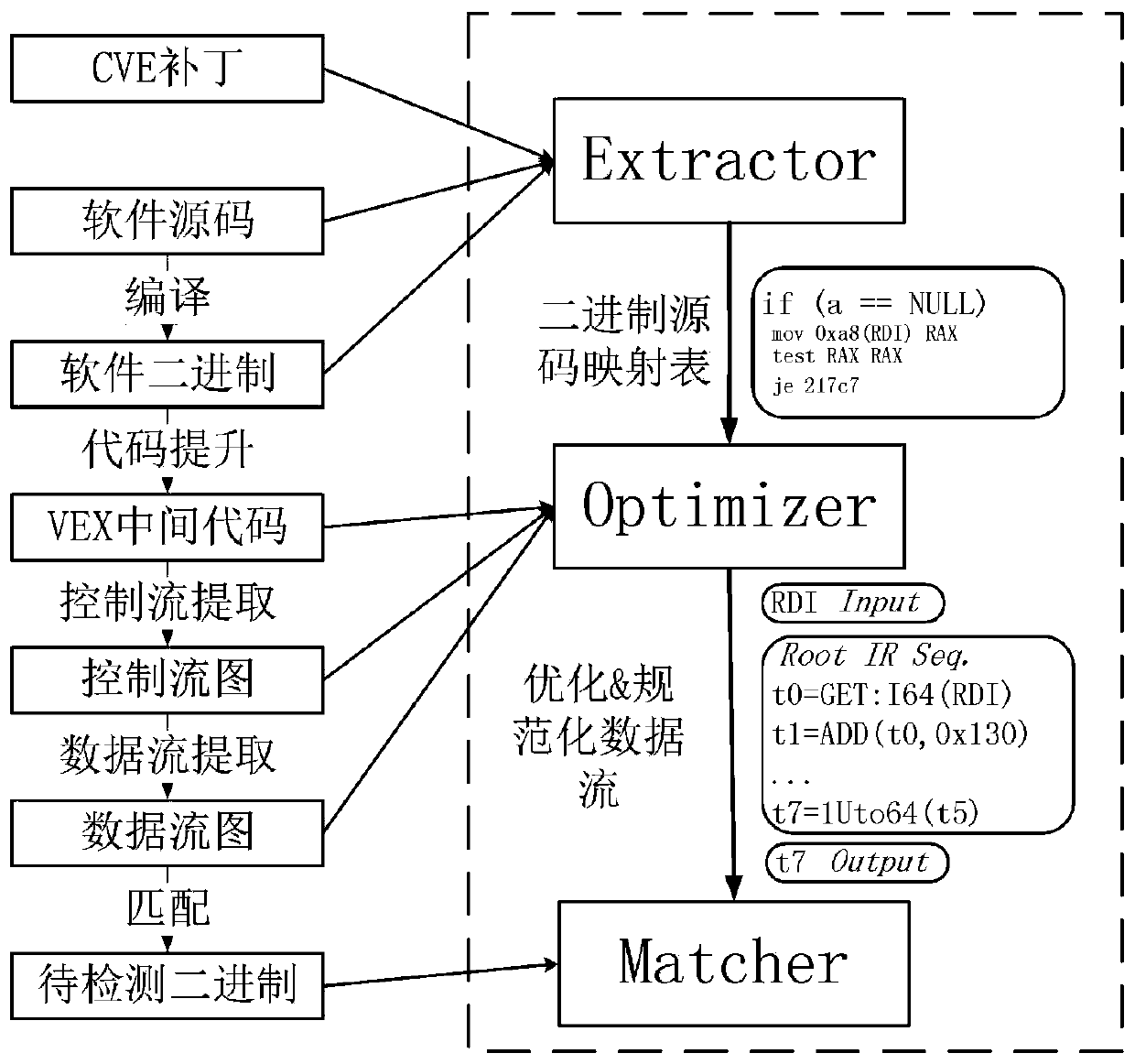
[0040] Step 1: Use Extractor to analyze the patch code, and select and detect the modification semantics of assignment statements and conditional statements, function call statements, type-related statements, and other types of statements in the patch code in sequence as the characteristics of the patch to be detected; establish a binary The mapping relationship between code and source code;
[0041] Step 2: Select VEX-IR as the intermediate code of the binary code promotion of the platform of the device in the Internet of Things environment, use the open source Angr to analyze the binary code, and extract the control flow, wherein the control flow is in the unit of function, Each of said functions contains a node as a basic block;
...
Embodiment 2
[0069] Such as Figure 5 As shown, a software patch detection device based on data flow analysis includes:
[0070] The selection unit is used to analyze the patch code by using the Extractor, select and detect the modification semantics of the assignment statement and the conditional statement, the function call statement, the type-related statement, and other types of statements in the patch code in sequence as the characteristics of the patch to be detected, and establish The mapping relationship between binary code and source code;
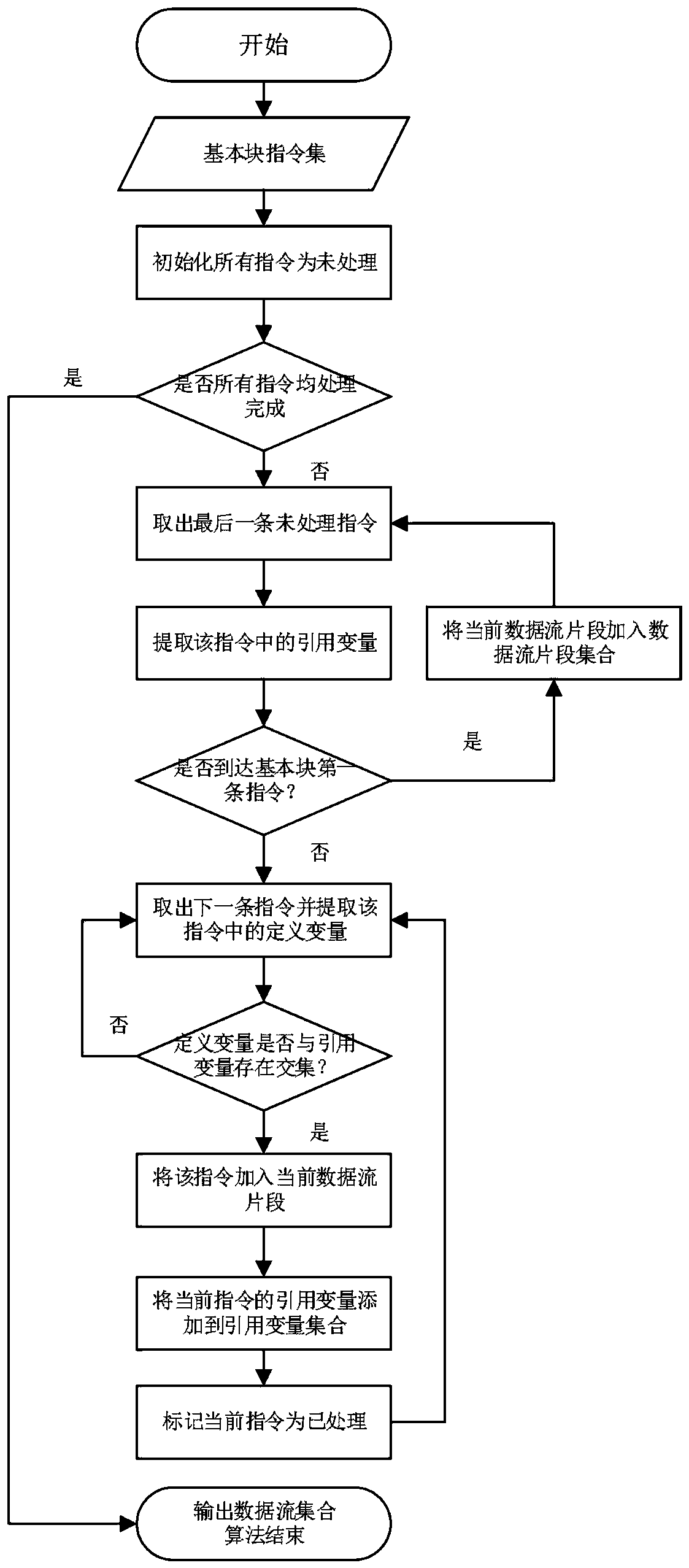
[0071] The analysis unit selects VEX-IR as the intermediate code for upgrading the binary code of the device firmware in the Internet of Things environment, uses the Optimizer to analyze the binary code using the open source Angr, extracts the control flow, and analyzes the data flow in the basic block and cross-basic The data flow of the block is analyzed;
[0072] The processing unit optimizes the extracted data flow; selects the ITL state...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com