Vulnerability detection method and terminal, storage medium
A vulnerability detection and detector technology, which is applied in the direction of instruments, electronic digital data processing, platform integrity maintenance, etc., can solve problems such as complex analysis structure, unsuitable for practical application, and low detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
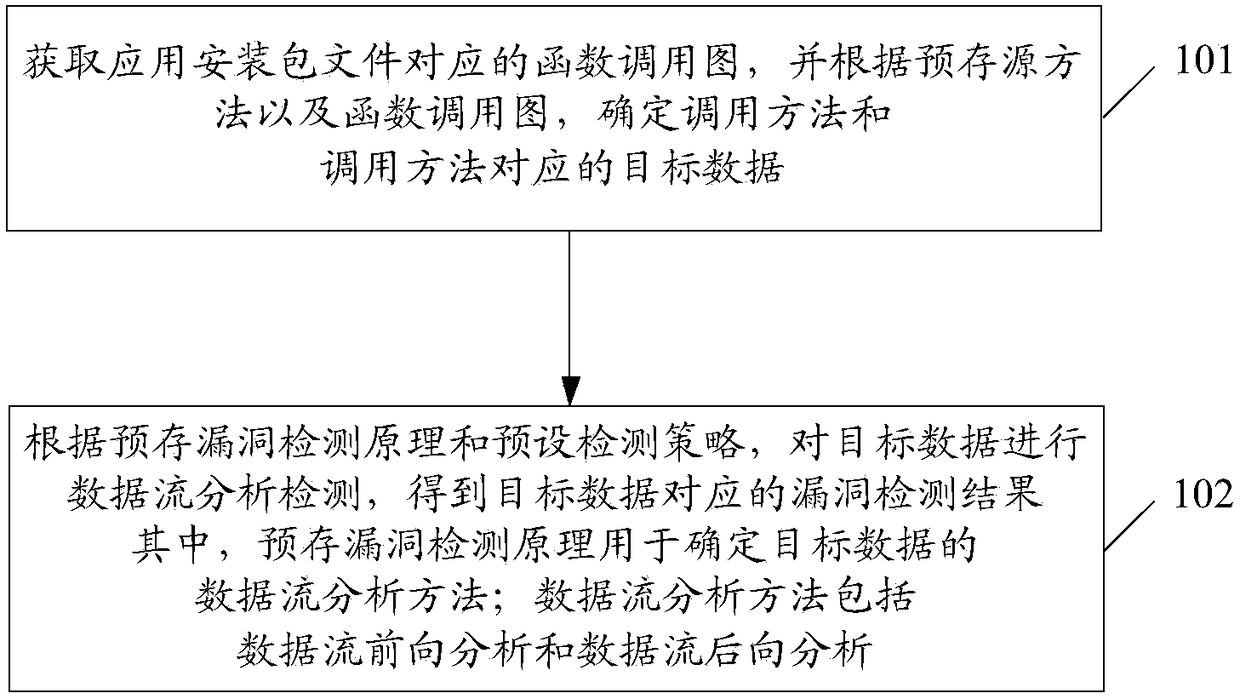
[0099] figure 1 A schematic diagram of an implementation process of a vulnerability detection method proposed by an embodiment of the present invention Figure 1 ,like figure 1 As shown, in the embodiment of the present invention, the method for performing vulnerability detection by a terminal may include the following steps:
[0100] Step 101: Obtain a function call graph corresponding to the application installation package file, and determine the calling method and target data corresponding to the calling method according to the pre-stored source method and the function call graph.
[0101] In the embodiment of the present invention, the terminal can first obtain the function call graph corresponding to the application installation package file, and then can determine the calling method and the target data corresponding to the calling method according to the pre-stored source method and the function call graph. It should be noted that, in the embodiment of the present inv...
Embodiment 2
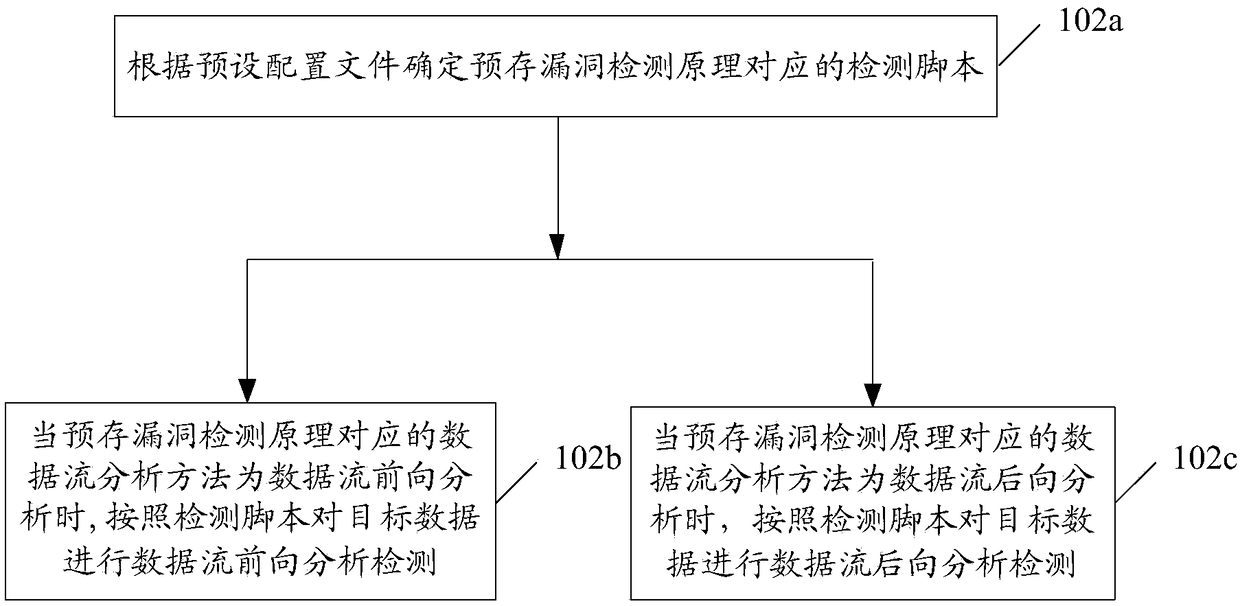
[0112] figure 2 A schematic diagram of an implementation process of a vulnerability detection method proposed by an embodiment of the present invention Figure II ,like figure 2 As shown, based on the first embodiment, in the embodiment of the present invention, further, the method for the terminal to perform data flow analysis and detection on the target data according to the pre-stored vulnerability detection principle and the preset detection strategy may include the following steps:
[0113] Step 102a: Determine a detection script corresponding to the pre-stored vulnerability detection principle according to the preset configuration file.
[0114] In the embodiment of the present invention, before performing data flow analysis and detection on the above target data, the terminal may first determine a detection script corresponding to the above pre-stored vulnerability detection principle according to a preset configuration file, and then may perform the above detection ...
Embodiment 3
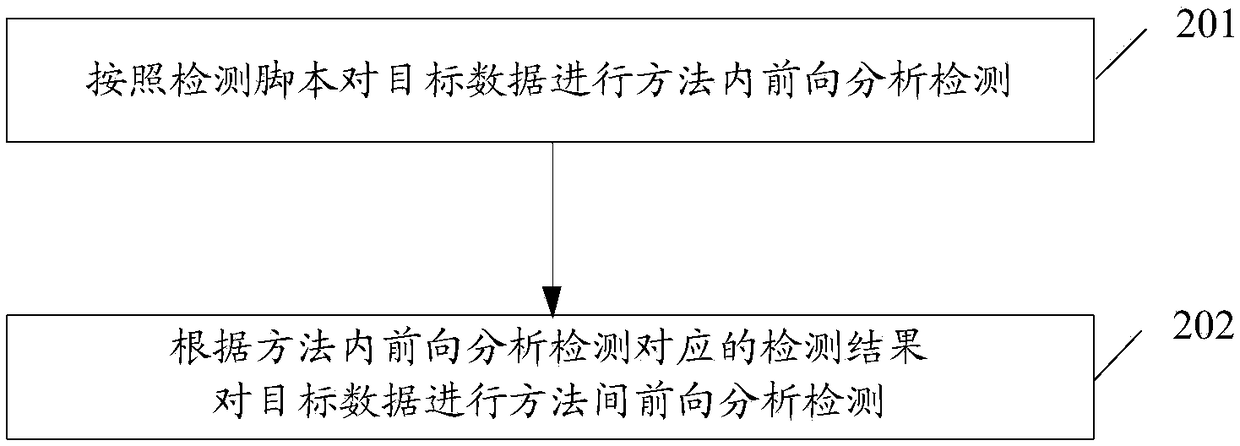
[0121] image 3 A schematic diagram of an implementation process of a vulnerability detection method proposed by an embodiment of the present invention Figure 3 ,like image 3 As shown, based on Embodiment 1 and Embodiment 2, in this embodiment of the present invention, the method for the terminal to perform data flow forward analysis and detection on target data according to a detection script may include the following steps:
[0122] Step 201: Perform in-method forward analysis and detection on the target data according to the detection script.
[0123] In the embodiment of the present invention, when it is determined that the data flow analysis method corresponding to the above-mentioned pre-stored vulnerability detection principle is a data flow forward analysis method, the terminal can perform in-method forward analysis and detection on the target data by executing the above detection script.
[0124] Further, in the embodiment of the present invention, when the termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com