Method for intercepting target progress with self-protection
A target process, program technology, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
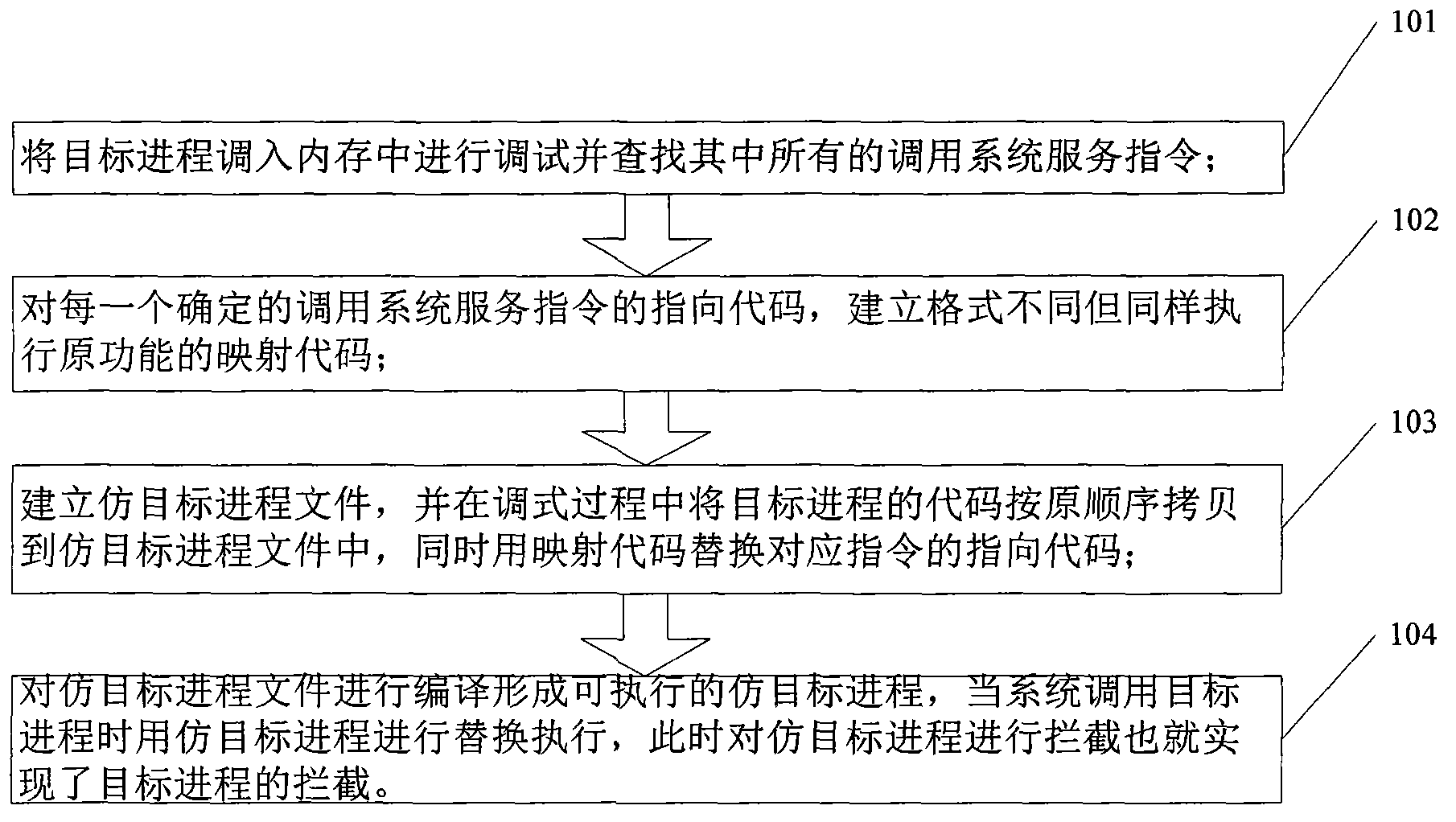
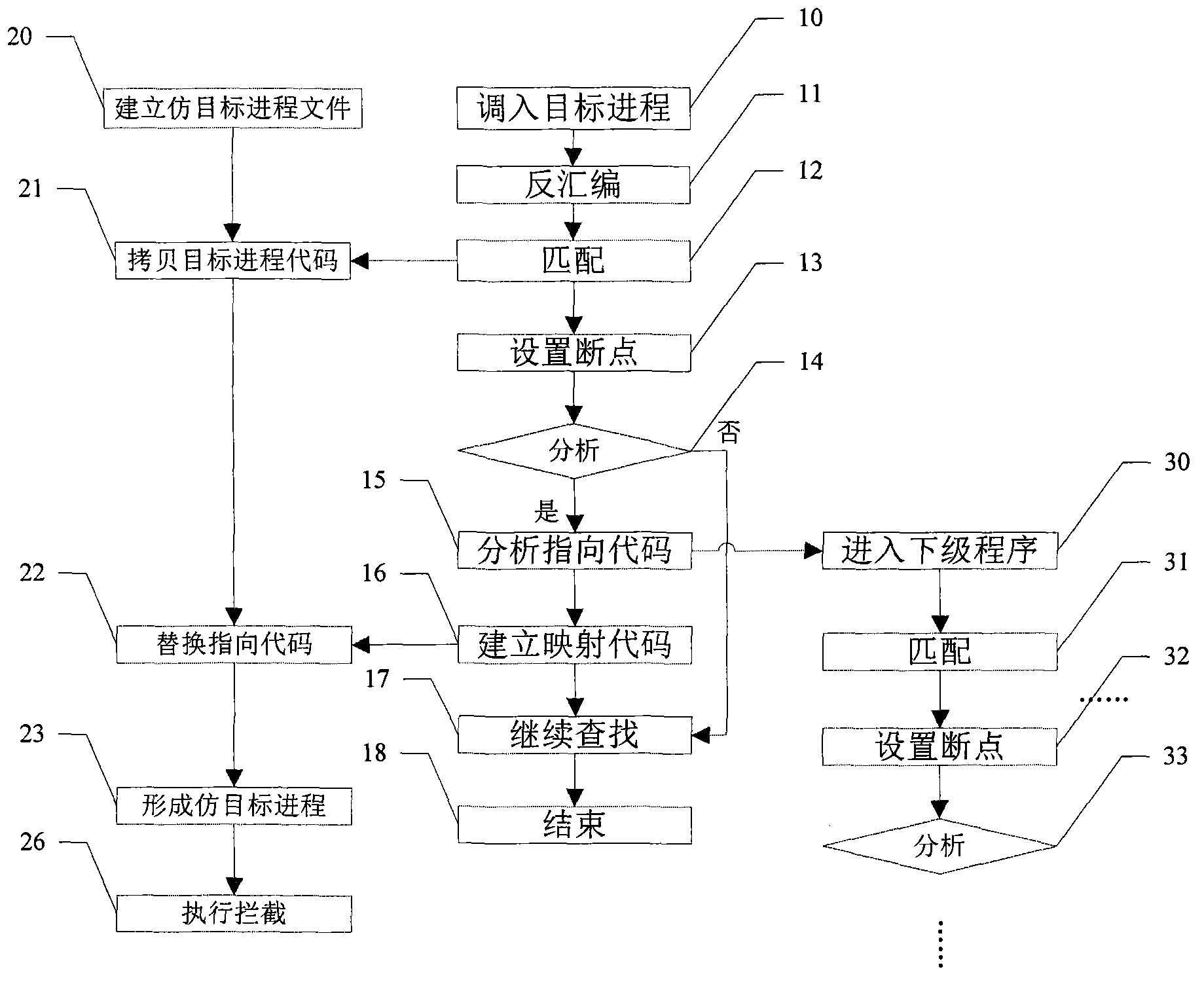
[0011] The technical solutions of the embodiments of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. Such as figure 1 Shown, the present invention comprises the steps:
[0012] 101. Transfer the target process into the memory for debugging and find the call system service instruction therein;
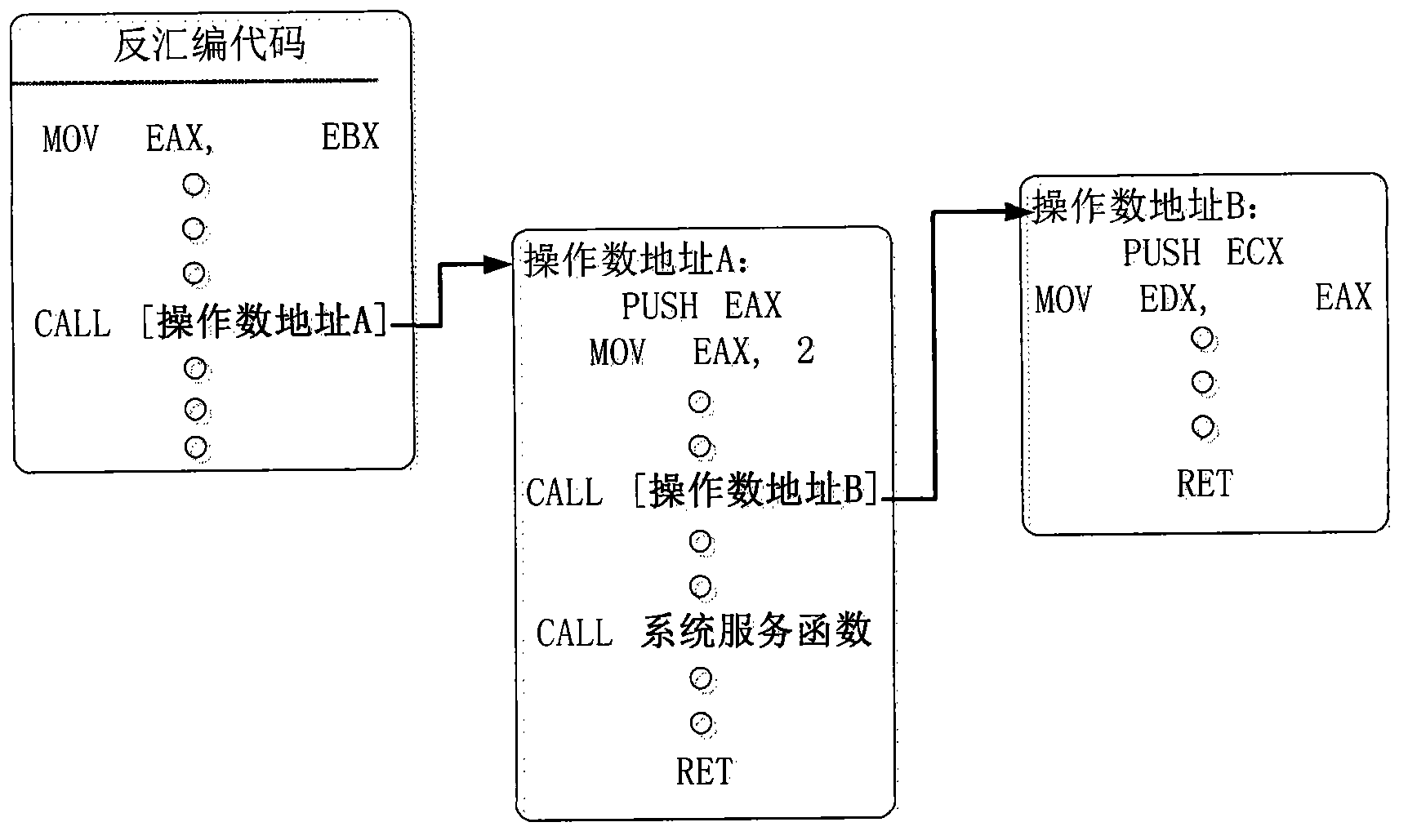
[0013] The method establishes a virtual environment in the memory, then transfers the target process into the virtual environment in the memory, disassembles the target process and obtains the disassembled code. Matching is performed in the disassembled code. The purpose of matching is to find out all calling system service instructions in the target process. The specific matching instructions are defined by the user. The defined standard is the instruction that is shielded according to the self-protection program of the target process. The routine is call, jmp, jz, jnz call instructions or jump instructions...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com